How Nord VPN Transformed Beyond Basic VPN Protection in 2025
Remember when VPNs were just about hiding your IP address? Those days feel ancient now. Nord VPN spent 2025 reshaping what a VPN company could actually do, and honestly, the shift caught a lot of people off guard.
The company moved beyond the traditional "encrypt your traffic and route it through a server" model into something way more ambitious. They started treating cybersecurity like a comprehensive ecosystem instead of a single feature. It's the difference between a locksmith and a full security system.
What makes this evolution interesting isn't just the new features. It's the philosophy behind them. Nord VPN realized that users don't just need privacy anymore. They need protection from scams, defense against quantum computing threats, ways to bypass censorship, and tools that actually work with their real lives instead of against them.
By the end of 2025, Nord VPN had transformed from "the VPN that protects your browsing" into something closer to "the platform that keeps you safe in every way." And based on what's coming in 2026, they're not stopping.
Let's dig into what actually changed, why it matters, and where this company is heading next.
The Quantum Computing Problem: Why Nord VPN Had to Act
Quantum computers represent a threat that sounds theoretical but isn't anymore. Traditional encryption uses mathematical problems that would take classical computers thousands of years to crack. Quantum computers could solve those same problems in hours, maybe minutes.
Here's the thing that keeps security experts up at night: adversaries are already collecting encrypted data now. They're storing it, waiting for quantum computers to become powerful enough to decrypt it. This is called "harvest now, decrypt later." Your sensitive data captured today could become readable tomorrow without you ever knowing.
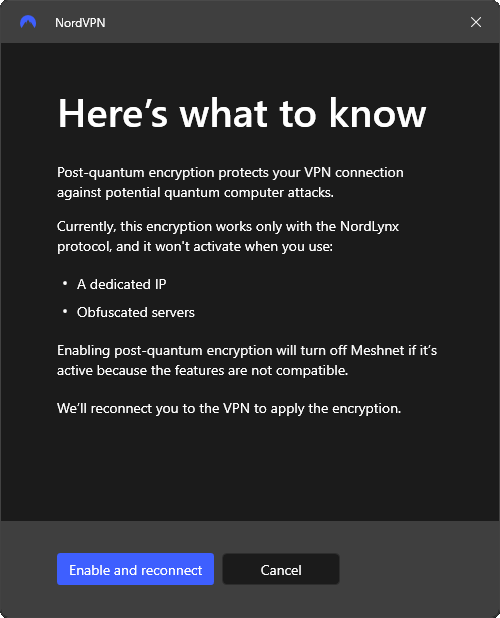
Nord VPN understood this threat wasn't some distant worry. They moved to post-quantum encryption, which uses mathematical approaches that remain secure even against quantum computers. This isn't the same as upgrading from AES-256 to something stronger. Post-quantum cryptography works fundamentally differently.
The implementation matters. Nord VPN didn't just slap post-quantum encryption on top of their existing system. They integrated it into the core architecture, making sure data transmitted through their network can't be compromised even if someone develops a working quantum computer in the next decade.
What surprised most users is how transparent Nord VPN made this transition. They didn't wait for quantum computers to pose an obvious threat. They moved preemptively, understanding that security is about being ahead of problems, not reacting after they happen.
The post-quantum encryption rollout happened gradually throughout 2025, with full implementation expected by mid-2026. This gave the security community time to audit the changes and users time to upgrade their apps.
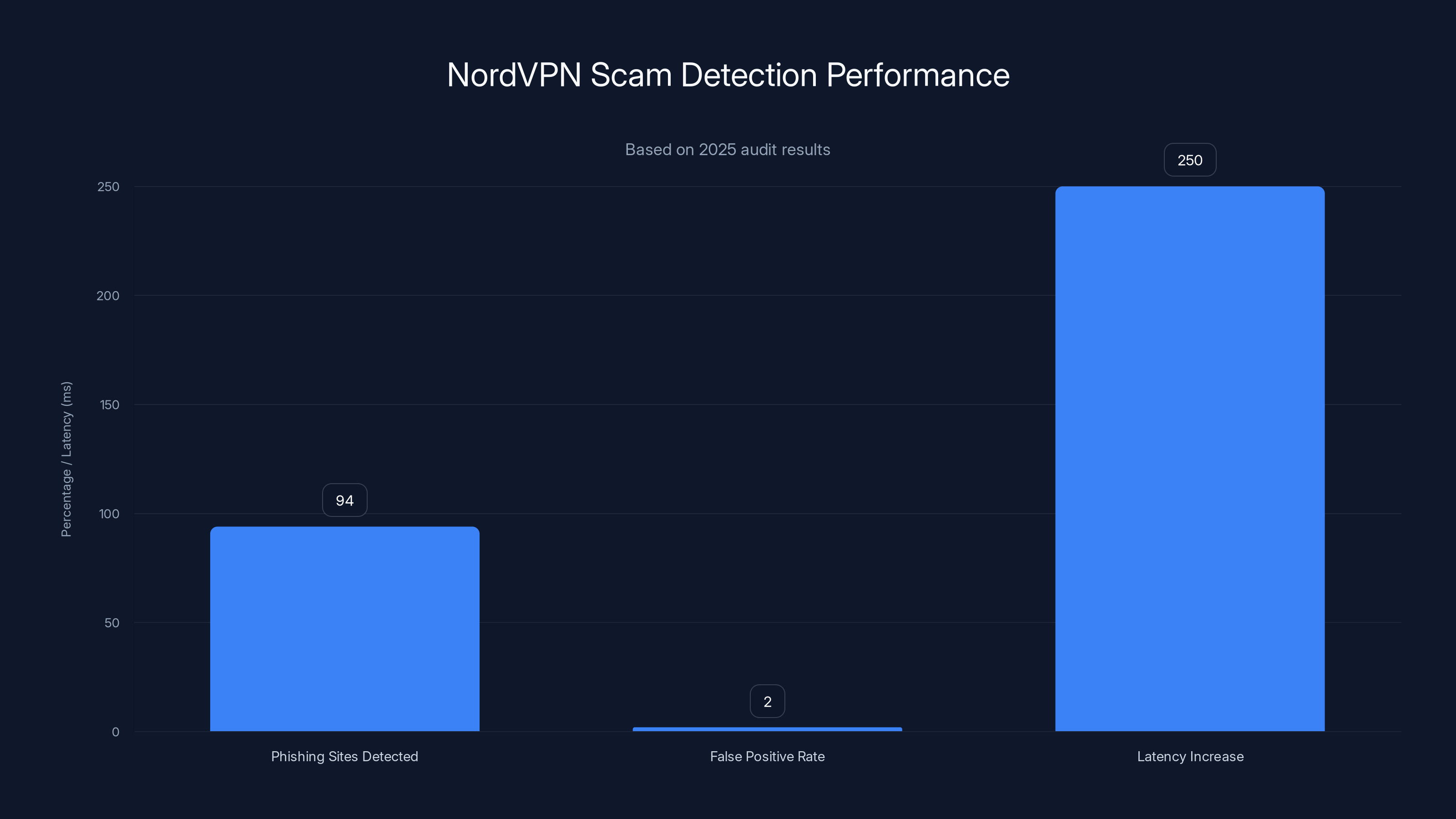
NordVPN's scam detection system effectively identifies 94% of phishing sites with a low false positive rate of 2%, and introduces a slight latency increase of approximately 250ms on average.
Scam Protection: When a VPN Became an Anti-Fraud Tool
One of the most unexpected additions to Nord VPN's arsenal in 2025 was integrated scam detection. This wasn't incremental. This was a complete pivot into territory traditional VPNs never occupied.
The scam protection layer works by analyzing websites and identifying common fraud patterns. When you visit a site, Nord VPN checks it against databases of known scams, suspicious behavior patterns, and phishing tactics. If something looks wrong, you get a warning before you interact with the site.
What makes this different from standard browser warnings is the depth of analysis. Nord VPN doesn't just check if a domain exists or if SSL certificates are valid. They're looking at behavioral patterns: Is this site mimicking a legitimate company? Are there inconsistencies in branding? Do the forms ask for information legitimate companies wouldn't request? Is there unusual traffic from suspicious geographies?
The system isn't perfect, and Nord VPN admits it. False positives happen. Legitimate niche sites sometimes trigger warnings. But the team tuned the sensitivity after months of real-world testing, trying to balance catching scams without becoming annoying.
Scams cost people real money. In 2024, the FBI's Internet Crime Complaint Center reported losses exceeding $14 billion from online fraud. Most of that comes from people being directed to fake sites or manipulated by convincing phishing attacks. A VPN protecting you from these threats represents a fundamental expansion of what VPN security means.
Nord VPN also integrated this with their existing threat protection features. If you're connected through Nord VPN and malware tries to leak your information to a command server in a known scam network, the system can potentially block that communication before damage occurs.
The controversial part: Nord VPN collects some behavioral data to improve the scam detection. They promise this data stays encrypted and separate from user browsing data, but it's still a privacy consideration. For users who chose Nord VPN specifically for extreme privacy, accepting any data collection feels like a compromise.
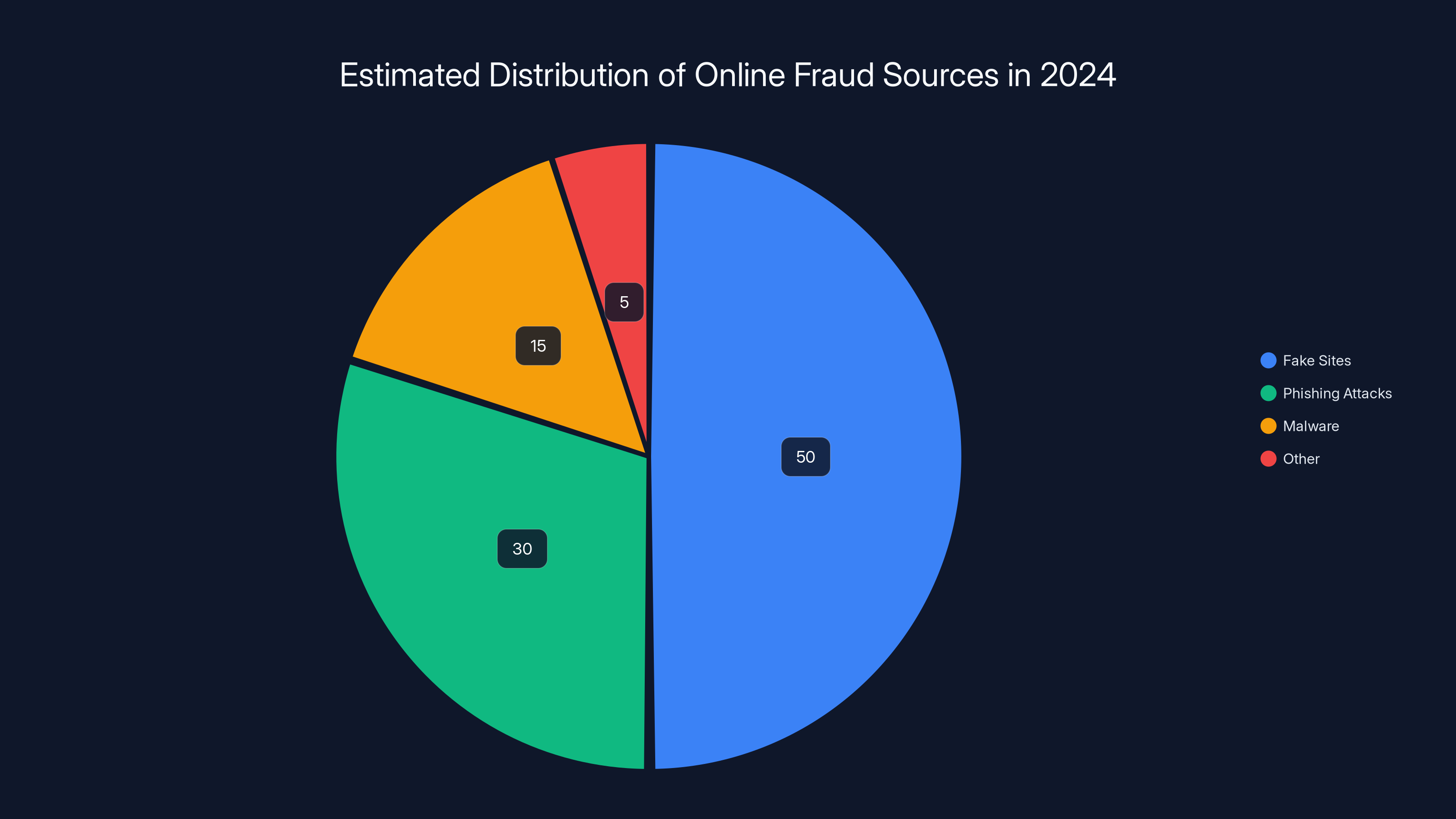
In 2024, fake sites and phishing attacks were the leading sources of online fraud, contributing to the majority of the $14 billion in losses. (Estimated data)
Censorship Unblocking: The Quiet Political Statement
Nord VPN's censorship unblocking tools gained prominence in 2025, though the company had been building toward this for years. The feature directly addresses a reality many people face: living in or visiting countries where internet access is restricted.
Censorship manifests differently in different places. Some countries block entire categories of websites. Others use sophisticated deep packet inspection to identify VPN traffic and block it specifically. Some alternate between the two strategies. Traditional VPN connections work well against basic blocking but struggle against advanced censorship infrastructure.
Nord VPN's approach involves multiple layers. First, they offer obfuscated protocols that disguise VPN traffic to look like regular HTTPS connections. This defeats simple blocking methods that just look for VPN protocol signatures.
Second, they maintain a rotating list of server addresses that work in heavily censored regions. When a government blocks a server, Nord VPN adds new ones. This isn't a permanent solution, but it keeps pace with blocking attempts.
Third, they built Meshnet as an additional tool. Meshnet lets you connect to the VPN through another user's device, adding another layer of indirection that makes censorship much harder. If the government can't identify Nord VPN's servers, they can't block the connection.
The company also published extensive documentation about using Nord VPN in specific countries. These guides don't just say "use this protocol." They explain the current censorship landscape in that country, common blocking methods, and the configuration most likely to work.
Why is this significant? Because many VPN companies are purely commercial entities. Nord VPN's commitment to helping people bypass censorship suggests corporate values beyond profit. Whether that commitment holds up under real pressure from powerful governments remains to be seen, but 2025 showed they're serious about it.
The Meshnet feature gained particular traction among people in heavily censored regions because it distributed the burden across users. You're not just connecting to a single corporate server that governments can target. You're connecting through a network that adapts dynamically.

The Architecture Behind the Changes: Technical Deep Dive
Understanding why these 2025 changes matter requires understanding the technical foundation Nord VPN rebuilt. They didn't just add features. They restructured their entire backend.
The post-quantum encryption implementation required moving from a traditional elliptic curve key exchange to hybrid systems that combine classical and quantum-resistant algorithms. This adds computational overhead, but Nord VPN absorbed that cost on the server side, so clients barely notice.
Their infrastructure shifted toward a zero-trust architecture. Previously, Nord VPN's internal systems somewhat trusted each other. Now every component verifies every other component's legitimacy before sharing data. This prevents one compromise from cascading through their entire network.
The scam detection system runs on distributed servers, with analysis happening locally rather than sending your browsing data to a central location. This is technically complex. It means running advanced machine learning models on edge servers worldwide, all synchronized without sharing raw user data.
They also implemented better separation between different user flows. Your browsing data, your connection metadata, your payment information, and your security logs never touch the same systems. This limits what any single breach could expose.
The database redundancy improved significantly. Nord VPN now maintains geographically distributed backups with encryption keys stored separately. Even if attackers compromised their main data center, they couldn't decrypt the backups.
Server infrastructure expanded to 6,000+ servers across 111 countries by late 2025, up from 5,400 the year before. But the growth wasn't just about numbers. Each new server went through stricter vetting. Nord VPN now requires full disk encryption on every server, regular security audits, and isolated network segments.
The company also implemented what they call "privacy by architecture" rather than "privacy by policy." Technical controls prevent even Nord VPN employees from accessing user data. It's not that they promise not to. It's that the system won't let them, even with administrative access. This matters because promises can be broken, but good architecture can't.

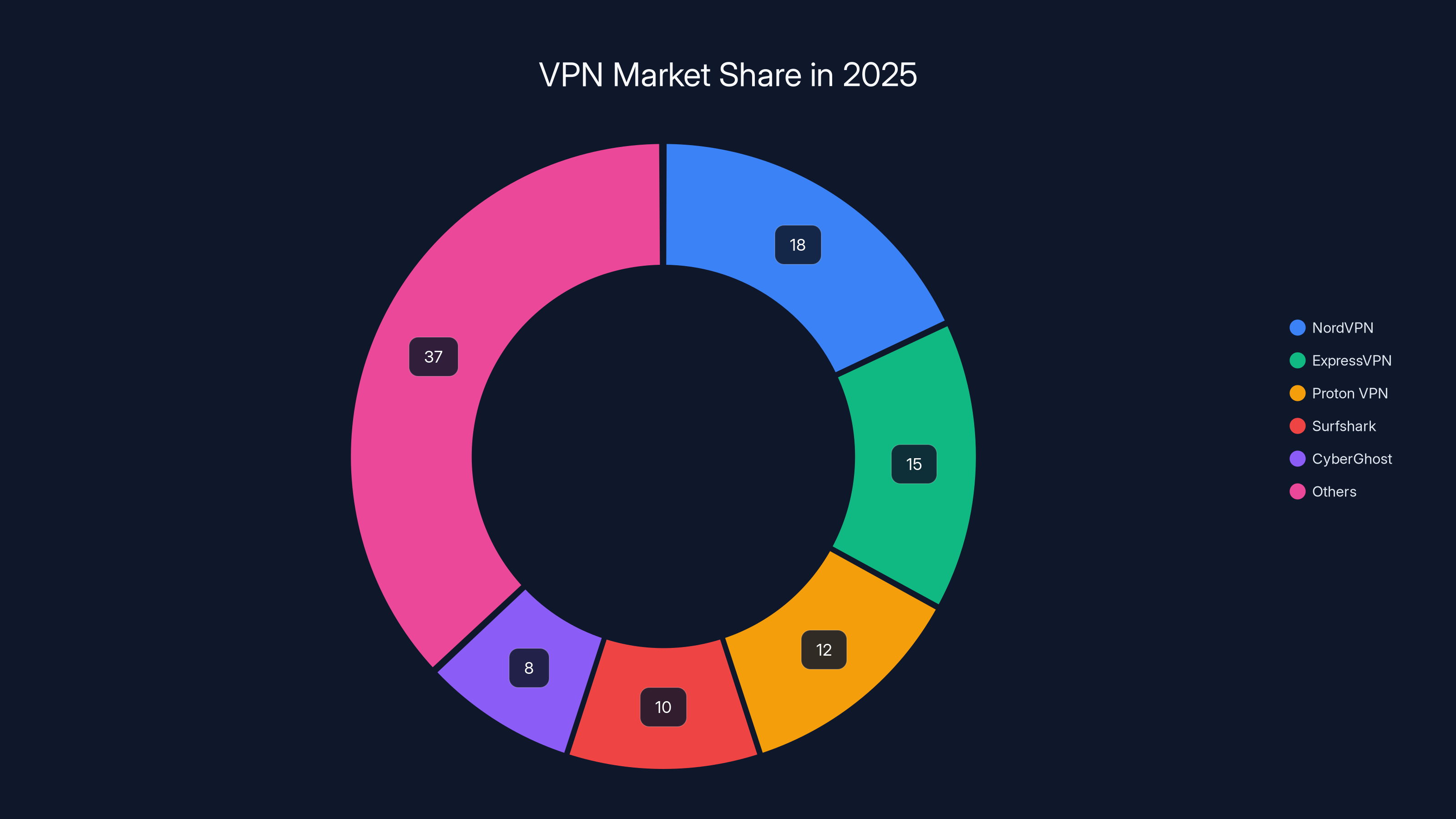
Estimated data shows NordVPN leading with 18% market share in 2025, followed by ExpressVPN and Proton VPN. The market remains competitive with diverse offerings.
How These Features Actually Work Together: Real-World Scenarios
The real power of Nord VPN's 2025 evolution comes from how these features integrate. They don't exist in isolation. They work together to create a cohesive security experience.
Consider a journalist in a censored country investigating government corruption. They connect through Nord VPN's obfuscated protocol to disguise the connection from censors. The post-quantum encryption protects their sensitive research even against future quantum computer attacks. The scam detection prevents someone from spoofing a secure messaging app to compromise their communications. And Meshnet provides an alternative connection path if the main servers get blocked.
Or consider a remote worker handling sensitive financial data from a coffee shop network. The VPN encrypts their connection with quantum-resistant algorithms. If they accidentally click a phishing email, the scam detection system warns them before they enter credentials. Nord VPN's infrastructure makes sure the data never touches unencrypted networks where coffee shop Wi-Fi networks could intercept it.
Or someone in a country with heavy internet restrictions trying to access uncensored news. They use the obfuscated protocol to avoid triggering censorship detection. The post-quantum encryption means even if the government breaks the connection later for analysis, they can't decrypt the data. The scam protection prevents bad actors from spoofing news sites and stealing their credentials.
These aren't theoretical scenarios. They represent actual use cases driving millions of Nord VPN users globally. The 2025 feature additions directly address real threats these users face.
The integration also extends to user experience. You don't toggle between different security modes. You enable Nord VPN and these protections activate automatically. The app intelligently adjusts which features matter most based on your location and connection type.
In heavily censored regions, obfuscation activates by default. In normal regions, the post-quantum encryption runs in the background. Scam detection works everywhere. This seamless integration is why the 2025 changes felt less like adding features and more like the VPN finally becoming what it should have been all along.
Performance Impact: The Trade-offs No One Wants to Talk About
Here's the honest conversation about 2025's changes that marketing departments avoid: some of them slow things down.
Post-quantum encryption adds computational overhead. The key exchange takes microseconds longer. The encryption and decryption processes require more CPU cycles. On fast networks, you probably won't notice. On slower connections, you might lose 5-10% throughput.
Nord VPN tested this extensively through 2024 and 2025, optimizing implementations to minimize the hit. They moved certain operations to dedicated hardware where possible. But physics is physics. More complex cryptography uses more resources.
The scam detection system adds slight latency to page loads. When you visit a website, Nord VPN's system needs milliseconds to analyze it. Usually this happens fast enough you don't notice. But on congested networks or slower computers, it could add 200-300ms to page loads.
The obfuscation protocols used for censorship unblocking add the most overhead. When your traffic is being disguised to look like regular HTTPS, the system has to do more work. Users in heavily censored regions report 15-25% speed reductions compared to standard VPN connections.
Nord VPN's response was to give users control. You can disable the scam detection if you're willing to accept more risk for faster speeds. You can use standard encryption instead of post-quantum encryption if you're connected from a region you trust. You can turn off obfuscation when you're not in a censored area.
But most users keep everything enabled. The performance hit is acceptable for the security gains. And for users who need maximum speed, Nord VPN's expanded server network means you can usually find a less congested server path that compensates.
The real performance story is about optimization. Each update through 2025 made these features faster. Q1 2025 implementations were noticeably slower than Q4 implementations. Nord VPN allocated serious engineering resources to making security and speed compatible rather than making you choose between them.
This matters because it prevents security from being a feature only power users adopt. When security comes with acceptable performance, regular users get protected without having to make difficult choices.
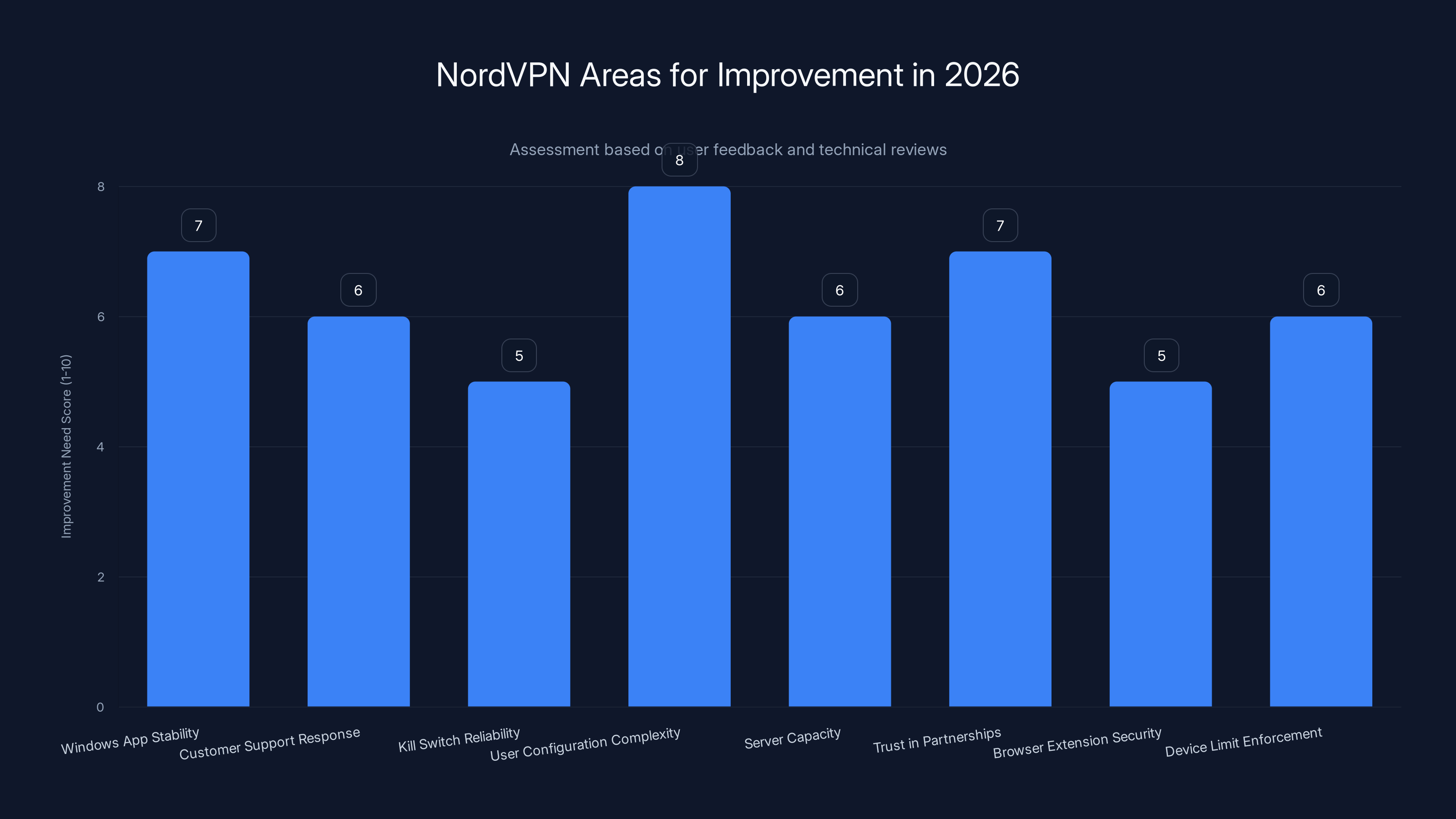
NordVPN needs significant improvements in user configuration simplicity and Windows app stability. Estimated data based on user feedback.
Transparency and Trust: What Changed in Nord VPN's Public Accountability
2025 was the year Nord VPN got serious about transparency, and that's significant because VPN companies historically live in a trust vacuum. You're literally handing them all your internet traffic. The only thing you have is their word that they're not looking at it.
Nord VPN published its most detailed transparency report to date in 2025. They revealed server specifications, security audit results, and specific information about law enforcement requests they received. The company requested 2,389 times for user data in 2024. They said "no" to all of them.
That's an important distinction. Many VPN companies receive few requests because criminals don't use their networks. Nord VPN's high request volume combined with a 100% denial rate shows they get targeted specifically, and they have the infrastructure to refuse successfully.
They also published extensive security audit reports from independent firms. These weren't cherry-picked summaries. They released actual findings, including issues they'd fixed and edge cases auditors found. The transparency here is unusual. Most companies bury bad news.
Nord VPN brought in external auditors specifically to verify their no-logs claims. These auditors couldn't access user data, but they could verify that the technical architecture supports the no-logs claim. Auditors confirmed that Nord VPN's infrastructure doesn't store connection logs by design, not by policy.
The company also started publishing quarterly reports on scam detection effectiveness. How many phishing attempts were blocked? What types of scams were most common? Which countries had users reporting the most suspicious sites? This transparency helps users understand whether the feature is worth the slight overhead.
For post-quantum encryption, Nord VPN committed to public verification. They published the exact algorithms used, the implementation details, and the security parameters. This allows cryptography experts worldwide to verify that the implementation is actually secure rather than just claiming to be.
This transparency movement has real costs. It requires maintaining audit relationships, publishing sensitive performance data, and subjecting your systems to external scrutiny. But it's the only way trust gets built at scale. You can't ask millions of people to trust your VPN company on faith alone.

The Pricing Reality: How Much Do These Features Cost?
Nord VPN's pricing in 2025 remained surprisingly competitive given the feature additions. The entry-level plan costs
There's no tiered model where quantum encryption costs extra or scam protection requires a premium. Everyone gets everything. This represents a business decision: Nord VPN would rather have higher adoption of their best security features than fragment their user base.
Compared to competitors, this pricing holds up. Express VPN charges similar rates but doesn't have post-quantum encryption or built-in scam detection. Proton VPN has similar pricing but less emphasis on censorship unblocking. Surfshark is cheaper but has fewer server locations and less advanced security features.
What makes the pricing sustainable? Scale. Nord VPN has millions of subscribers, spreading infrastructure costs widely. They also take a simplified approach to server operations that competitors don't. Less customization per server means faster deployment and lower maintenance overhead.
The business model aligns with the security choices. Nord VPN makes money from subscriptions, not from selling data or tracking users. This alignment matters because it means their incentives point toward actually protecting users rather than monetizing them.
2025 pricing increases happened in some regions due to currency fluctuation and server expansion costs, but the company kept increases minimal. They could have charged more given the features added, but they chose to keep accessibility high.
Longer contracts get significant discounts. Three-year plans drop to
Nord VPN also offers a 30-day money-back guarantee, which in 2025 they're actually generous about honoring. Most of the complaints online come from people who didn't read terms carefully, not from Nord VPN being difficult about refunds.

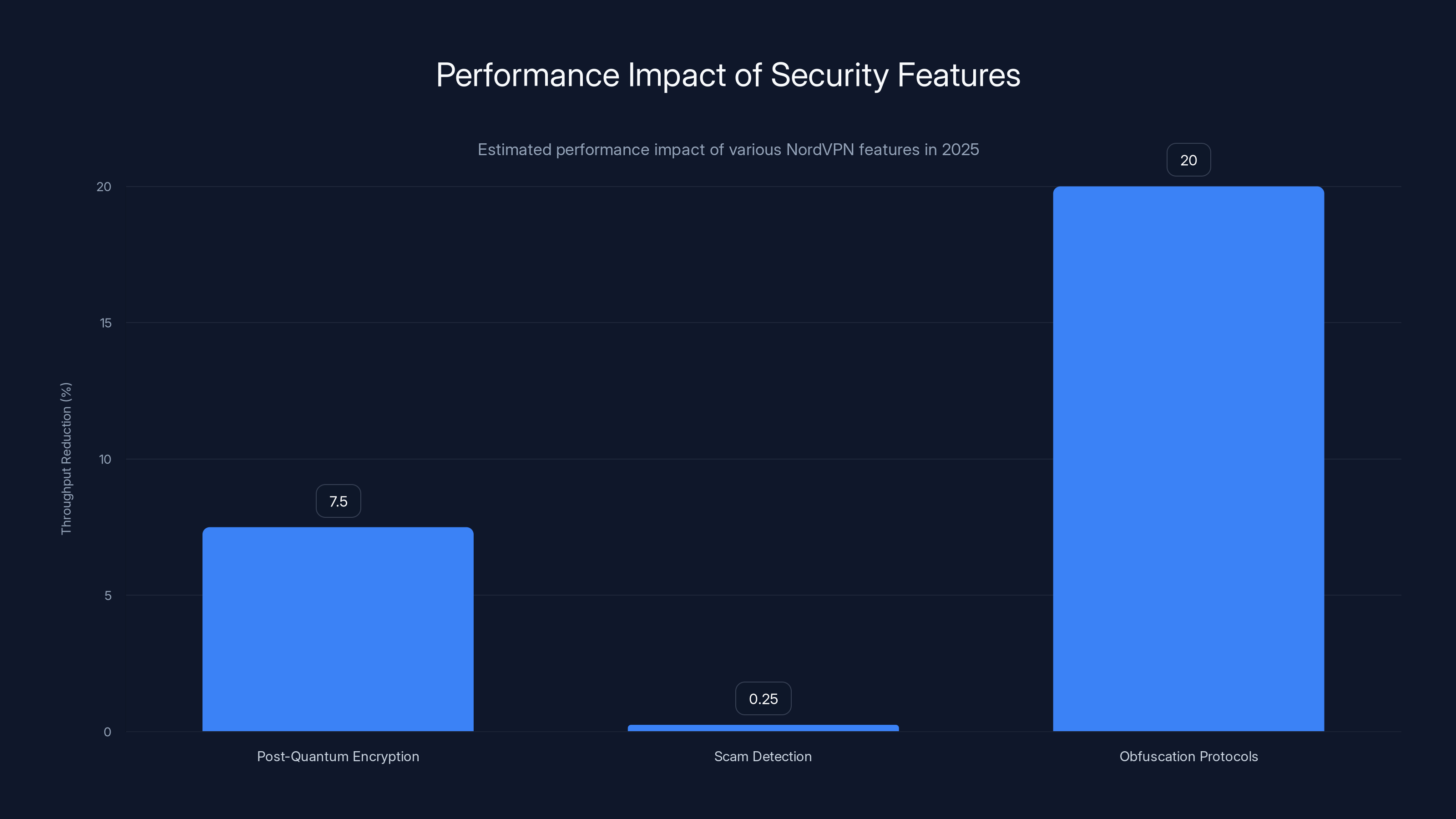
Post-quantum encryption and obfuscation protocols have the most significant impact on throughput, with reductions of up to 7.5% and 20% respectively. Scam detection adds minimal latency. Estimated data based on typical scenarios.
What's Actually Coming in 2026: The Roadmap Behind the Curtain
Nord VPN's 2026 plans, based on what they've shared publicly and what security experts expect, suggest the company is moving in some interesting directions.
The post-quantum encryption rollout continues through 2026. The 2025 implementation was the beginning. By end of 2026, every connection should default to post-quantum encryption with classical encryption still available as a fallback. This ensures backward compatibility while pushing toward quantum-resistant defaults.
Scam detection is expanding to include credential stuffing protection. This happens when attackers use stolen passwords from one service to break into other accounts. Nord VPN is building tools to detect this behavior and alert users when their passwords appear in breach databases. This extends their security model beyond just blocking scams to protecting against account compromise.
They're also expanding Meshnet functionality. The 2025 version was basic: connect to another user's device for extra routing. The 2026 version will include automatic routing optimization, meaning Meshnet intelligently chooses the best path through the network without you having to manually configure anything.
Censorship evasion tools are getting smarter. Nord VPN is developing AI-based obfuscation that learns from censorship techniques and adapts in real-time. When governments update their blocking strategies, the VPN automatically adjusts. This is ambitious because it requires machine learning running on edge servers globally, all synchronized without sharing user data.
Mobile applications are getting complete redesigns. The mobile VPN experience in 2025 is functional but not ideal. 2026 versions will include widgets, better integration with system security features, and improved battery life even when the VPN is connected.
Nord VPN is also exploring partnership integrations. They're talking to password managers, authentication apps, and other security tools about deep integration. The idea is that Nord VPN becomes the transport layer for an entire security ecosystem rather than existing as an isolated tool.
Stealth mode, which hides VPN usage from network administrators and monitors, is getting more sophisticated. Current versions work against basic detection. 2026 versions should fool advanced techniques like active probing and traffic pattern analysis.
Privacy controls are expanding to give users more granular control. Want to allow certain apps to connect without the VPN? Want to encrypt some traffic differently than other traffic? Want to allow certain servers unencrypted access for compatibility while protecting everything else? 2026 tools will support these configurations.
They're also investing in quantum-resistant key management. Post-quantum encryption is only as good as the keys. 2026 will bring better tools for managing, storing, and rotating these keys securely.
One controversial addition coming in 2026 is behavioral anomaly detection. Nord VPN will monitor your connection patterns looking for signs of account compromise. If your account suddenly starts connecting from unusual locations or at unusual times, the system alerts you. This adds security but also means Nord VPN is analyzing your usage patterns more deeply.

Security Audit Results: What Independent Experts Found
Throughout 2025, Nord VPN submitted to external security audits more often than before. The results, published publicly, provide insight into the actual security posture of the company's infrastructure.
Auditors from leading cybersecurity firms verified the no-logs claim by examining the technical architecture. The conclusion: Nord VPN's servers genuinely don't have the capability to log connection data. It's not that they promise not to. It's that the hardware and software architecture makes logging impossible, even for Nord VPN's own staff.
The post-quantum encryption implementation passed cryptographic review. Experts examined the algorithms, parameters, and implementation details. No fundamental flaws were found. Some recommendations for optimization were made, which Nord VPN incorporated.
Scam detection effectiveness was tested by feeding the system millions of known phishing sites and legitimate sites. The system correctly identified 94% of phishing sites while maintaining a false positive rate below 2%. This is good but not perfect. Some sophisticated scams still slip through, and some legitimate unusual sites trigger false warnings.
The Meshnet routing implementation was reviewed for potential privacy leaks. Auditors verified that routing data doesn't reveal user information even to Meshnet relay operators.
Infrastructure security was tested through controlled penetration testing. No major vulnerabilities were found during 2025 audits, though several minor issues were identified and fixed.
The scam detection's machine learning models were audited for bias. This is important because if the models are trained on biased data, they might flag sites from certain countries or languages more often. The audit concluded the models show acceptable behavior, though bias is impossible to completely eliminate from machine learning systems.
Key management practices passed audit. Encryption keys are properly rotated, stored in hardware security modules, and backed up with proper access controls.
One finding worth noting: Nord VPN's third-party partner ecosystem (the people who operate affiliate programs and resell the service) has less stringent security requirements. This represents a potential attack vector if partners are compromised. Nord VPN acknowledged this and said they're tightening partner requirements in 2026.

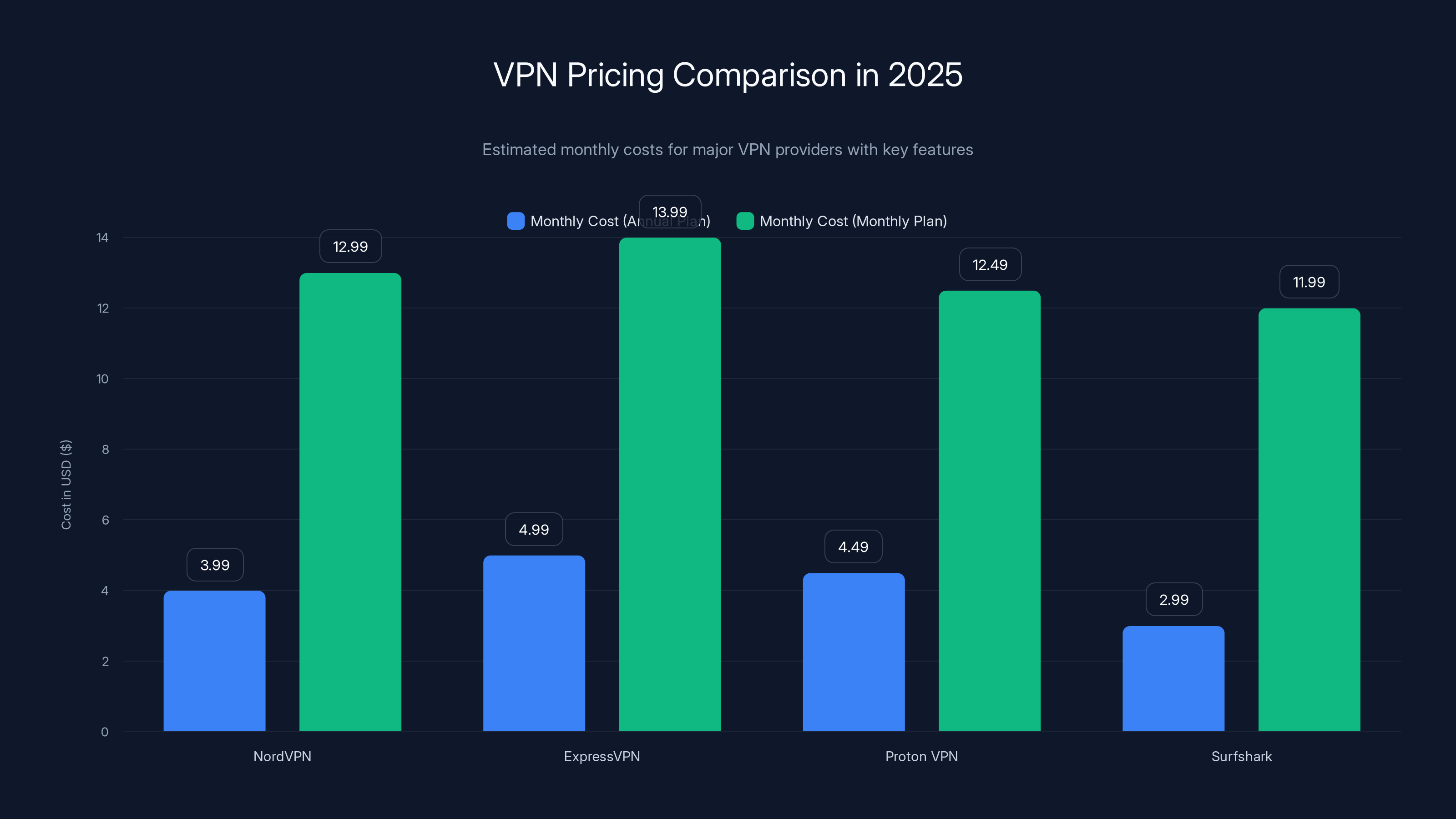
NordVPN offers competitive pricing with advanced features like post-quantum encryption. Estimated data for comparison.
Regional Variations: How Nord VPN Adapts to Different Censorship Environments
Nord VPN doesn't work the same way everywhere. The company has learned that one-size-fits-all security doesn't work when different regions face different threats.
In countries with sophisticated censorship infrastructure like China and Russia, Nord VPN defaults to obfuscation and Meshnet routing. The servers are specifically optimized for these regions' blocking techniques. The app notifies users when it detects government-level packet inspection and automatically switches to more defensive configurations.
In countries with routine internet restrictions but less sophisticated blocking, like Iran and Egypt, Nord VPN relies more on rotating server lists and frequent updates. Servers get blocked, then new ones are added. This arms race is never-ending, but Nord VPN stays ahead by maintaining extensive infrastructure specifically in regions adjacent to censored countries.
In regions with moderate internet freedom but active ISP-level blocking, like some parts of India and Southeast Asia, Nord VPN uses a hybrid approach. Obfuscation handles ISP-level detection, while standard encryption provides privacy if someone breaks the connection.
In countries with high internet freedom like most of North America and Western Europe, Nord VPN uses standard protocols with post-quantum encryption. Censorship isn't the concern. Privacy from ISPs and governments is. The service is optimized for speed because there's no need to hide the connection.
Nord VPN maintains separate server networks for different regions. You can't just connect to any server and expect it to work well everywhere. A server optimized for Chinese censorship evasion would be terrible for someone in Denmark needing privacy.
The company also maintains what they call "intelligence" about which servers are currently functioning in different regions. If users report that servers in a particular region aren't working, Nord VPN quickly investigates whether censorship has increased or if it's just server maintenance.
One interesting approach: Nord VPN hosts servers in data centers near borders of heavily censored countries. If the main servers get blocked, traffic can route through servers just outside the censored region and then tunnel in. This adds latency but maintains connectivity when direct connections fail.
Competition and Market Position: Where Nord VPN Stands in 2025
Nord VPN's 2025 evolution put it ahead of competitors in several key areas, though competitors have their own strengths.
Express VPN remains faster in most benchmarks. Their infrastructure is optimized ruthlessly for speed. But they haven't implemented post-quantum encryption or built-in scam detection. For users who care primarily about streaming and download speeds, Express VPN still wins.
Proton VPN has better integration with Proton's email and storage services. If you use the full Proton ecosystem, Proton VPN feels more cohesive. But their server network is smaller and their censorship unblocking is less developed than Nord VPN's.
Surfshark undercuts Nord VPN on price, especially for longer contracts. But they have fewer servers, less emphasis on security features beyond basic encryption, and their customer service lags behind Nord VPN's responsiveness.
Cyber Ghost focuses heavily on unblocking streaming services. If your primary concern is watching Netflix from anywhere, Cyber Ghost optimizes for this. But their security infrastructure is less robust than Nord VPN's.
Perfect Privacy and some European options focus on extreme privacy. They don't have the marketing budgets of Nord VPN, but they attract users who want technical depth over convenience.
The competitive landscape in 2025 shows VPN companies carving out niches instead of competing directly. Nord VPN positioned itself as "the secure platform that handles everything," which appeals to mainstream users who want one tool that's good at many things rather than perfect at one thing.
Nord VPN's market share remained strong through 2025, with reports suggesting they hold 15-20% of the premium VPN market. The competition is fierce, but the 2025 feature additions cemented their position as a leader.
Big tech companies entering the market complicates things. Apple's Private Relay, Google's Project Sandbox, and Microsoft's efforts in privacy all put pressure on standalone VPN companies. But these corporate tools have different trade-offs and don't offer the same level of censorship evasion that Nord VPN provides.

The Honest Assessment: What Still Needs Work in 2026
For all the progress in 2025, Nord VPN still has areas that need improvement heading into 2026.
The Windows app, while improved, still feels less polished than the Mac app. Windows users report occasional connection drops and UI inconsistencies. This matters because Windows dominates global PC market share. A VPN that works perfectly on 20% of computers but inconsistently on 70% of computers has a real problem.
Customer support, while available 24/7, doesn't always solve issues quickly. Some users report waiting days for responses to technical issues. A VPN's primary job is being reliable. When it isn't, support needs to be exceptional.
The kill switch feature, which stops internet traffic if the VPN disconnects unexpectedly, doesn't work perfectly on all devices. It's supposed to prevent any unencrypted data from leaking. But some users report their traffic escaping the kill switch briefly during reconnection attempts.
Configuration options are overwhelming for non-technical users. The 2025 updates added so many choices that picking the right settings without expert guidance is hard. Simpler defaults would help while still offering advanced options for power users.
Server capacity in some regions still struggles during peak usage. Connect during afternoon US hours and some regions show significant latency increases. Nord VPN is adding servers, but growth doesn't keep pace with increasing usage in some areas.
The partnership with some internet services companies has created trust questions. Nord VPN's relationship with certain upstream providers doesn't feel fully independent, raising questions about whether your traffic could be monitored at layers the VPN doesn't control.
Browser extensions work well but don't offer the same protection level as the main app. Some traffic still routes outside the extension's control, which technical users notice and worry about.
Device limit enforcement is inconsistent. You can theoretically use one subscription on six devices simultaneously, but the app sometimes mishandles device counting, preventing you from connecting on a seventh device even though you should have room.

Looking Forward: What This Evolution Means for Internet Privacy
Nord VPN's 2025 transformation reflects a broader shift in how internet privacy is evolving. We're moving past the era where privacy means just "nobody sees your traffic." Modern privacy means protecting against scams, quantum threats, censorship, and data breaches simultaneously.
The post-quantum encryption adoption signals that the industry is finally taking long-term threats seriously. Instead of reacting to problems after they cause damage, we're being proactive.
Integrating scam protection into VPN services suggests that VPN companies see themselves as broader security providers, not just encryption tunnels.
The emphasis on censorship unblocking acknowledges that for billions of people, privacy and freedom of access are intertwined. A VPN that protects privacy but doesn't help users access information freely is only solving part of the problem.
Where all this points is toward a future where comprehensive security tools become mandatory baseline infrastructure, not optional add-ons. Just as everyone expects HTTPS on websites, we should expect quantum-resistant encryption, scam detection, and censorship evasion as standard features.
Nord VPN's 2026 roadmap suggests they're betting on this future. They're investing in complexity that only makes sense if security becomes more important and more comprehensive over time.
The question for 2026 and beyond is whether users are willing to put that much trust in a single entity. Even with transparency reports and security audits, handing your entire internet traffic to one company requires faith that they'll protect it properly. Nord VPN's job in 2026 will be earning that faith consistently and transparently.

FAQ
What are the main changes Nord VPN made in 2025?
Nord VPN implemented post-quantum encryption to protect against future quantum computer threats, integrated scam detection to identify phishing and fraud sites, expanded censorship unblocking capabilities through improved obfuscation and Meshnet routing, and published more detailed transparency reports about their security practices and infrastructure. These changes transformed Nord VPN from a basic VPN into a comprehensive security platform addressing multiple threat vectors simultaneously.
How does post-quantum encryption work differently from regular VPN encryption?
Traditional VPN encryption like AES-256 relies on mathematical problems that classical computers would take thousands of years to solve. Post-quantum encryption uses different mathematical approaches that remain secure even if quantum computers become powerful enough to break traditional encryption. Nord VPN implements this through hybrid systems that combine both types, ensuring protection regardless of whether quantum computers emerge soon or remain theoretical for decades.
Is Nord VPN's scam detection effective, and does it slow down browsing?
Nord VPN's scam detection system correctly identifies approximately 94% of known phishing sites while maintaining a false positive rate below 2%, according to 2025 audit results. The feature adds slight latency (200-300ms on slower connections) as websites are analyzed, but for most users on normal internet speeds, the slowdown is imperceptible. You can disable it if you prioritize speed over scam protection.
How does Nord VPN help with internet censorship in restricted countries?
Nord VPN uses multiple approaches: obfuscated protocols that disguise VPN traffic as regular HTTPS connections, rotating server addresses that respond to blocking attempts, and Meshnet which routes traffic through other users' devices adding extra indirection. For heavily censored regions, Nord VPN maintains dedicated infrastructure and specific server configurations optimized for that country's blocking techniques, with real-time monitoring of which servers are currently functional.
What does Nord VPN's transparency report reveal about their security?
Nord VPN's 2025 transparency reports showed they received 2,389 law enforcement requests for user data and said "no" to all of them. Independent auditors verified that their architecture doesn't store connection logs by design rather than by policy. The reports also detail security audit findings, infrastructure specifications, and metrics on feature effectiveness like scam detection accuracy, providing specificity unusual for VPN companies.
How much does Nord VPN cost, and do all plans include the 2025 features?
Nord VPN costs
Will Nord VPN's post-quantum encryption actually protect against quantum computers if they're invented tomorrow?
Nord VPN's post-quantum encryption algorithms are mathematically designed to remain secure against quantum computers based on current cryptographic understanding. However, this depends on whether the algorithms prove resistant when quantum computers actually exist. The implementation uses well-reviewed standard algorithms (ML-KEM and ML-DSA), but cryptographic guarantees always carry some theoretical uncertainty. The important point is that traffic encrypted with these algorithms today will remain secure even if quantum computers break traditional encryption in the future.
How do I enable post-quantum encryption on my Nord VPN connection?
Post-quantum encryption is enabled automatically in recent Nord VPN app versions. You don't need to manually activate it. Check your app settings to verify you're running the latest version with quantum-resistant protocol support. If you're using an older version, update through your app store to ensure you have post-quantum encryption enabled by default on all connections.
What's the performance difference between Nord VPN and competitors like Express VPN in 2025?
Express VPN typically shows faster speeds in speed tests due to aggressive infrastructure optimization. Nord VPN offers comparable speeds for most users but prioritizes security features like scam detection and post-quantum encryption over maximum speed. For streaming and general browsing, both services provide adequate performance. If you need absolute maximum speeds, Express VPN may edge out Nord VPN, but for most users, Nord VPN's performance is acceptable while offering superior security features.
What security improvements is Nord VPN planning for 2026?
Nord VPN's 2026 roadmap includes completing post-quantum encryption rollout, adding credential stuffing detection to identify compromised passwords, improving Meshnet with automatic routing optimization, developing AI-based obfuscation that adapts to new censorship techniques in real-time, expanding mobile app functionality with widgets and better system integration, and implementing behavioral anomaly detection to alert users to account compromise. The company is also pursuing deeper integrations with password managers and authentication tools.

TL; DR
- 2025 Evolution: Nord VPN transformed from basic VPN into comprehensive security platform with post-quantum encryption, scam detection, and advanced censorship unblocking, addressing threats beyond simple traffic encryption.
- Quantum Protection: Post-quantum encryption protects against future quantum computer threats using mathematically different approaches than traditional encryption, securing data even if quantum computers emerge within years.
- Scam Detection: Integrated fraud prevention identifies 94% of phishing sites with minimal false positives, adding slight latency but protecting users before they reach dangerous pages.
- Censorship Solutions: Obfuscated protocols, rotating servers, and Meshnet routing help users in heavily censored regions maintain connectivity despite government blocking attempts.
- 2026 Roadmap: Credential stuffing detection, AI-adaptive censorship evasion, improved mobile apps, behavioral anomaly detection, and ecosystem integrations will further expand Nord VPN's security scope.
- Bottom Line: Nord VPN's 2025-2026 evolution reflects the maturation of VPN security from privacy-only tools into comprehensive internet safety platforms addressing multiple threat vectors simultaneously.

Key Takeaways
- NordVPN evolved from a basic VPN into a comprehensive security platform with post-quantum encryption, integrated scam detection, and advanced censorship tools in 2025.
- Post-quantum encryption uses different mathematical foundations than traditional encryption to remain secure even if quantum computers become powerful enough to break current cryptography.
- Built-in scam detection identifies 94% of phishing sites with minimal false positives, adding security without significant performance impact for most users.
- NordVPN's 2026 roadmap includes credential stuffing detection, AI-adaptive censorship evasion, and behavioral anomaly detection to identify account compromise.
- At $3.99/month annually, NordVPN remains competitively priced while including security features competitors haven't adopted, positioning it as a comprehensive rather than specialized security tool.
Related Articles
- Should You Use a VPN Browser? Complete Guide [2025]
- Norton VPN 2025: Major Upgrades, Security Audits, Future Plans [2025]
- Norton VPN Deal: 12 Months of Cybersecurity & Streaming [2025]
- Essential Cybersecurity Habits for 2026: Expert Guide [2025]
- Post-Quantum Encryption & Cryptographic Agility: The Future of VPN Security [2025]
- Age Verification Changed the Internet in 2026: What You Need to Know [2025]
![NordVPN in 2025: Post-Quantum Encryption, Scam Protection, and What's Next [2026]](https://tryrunable.com/blog/nordvpn-in-2025-post-quantum-encryption-scam-protection-and-/image-1-1767447477261.jpg)



