NGINX Server Hijacking: The Global Traffic Redirect Campaign Explained
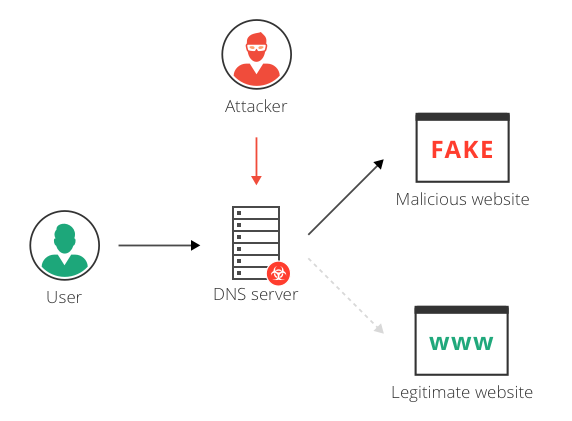
A sophisticated attack campaign targeting NGINX servers has been quietly rerouting legitimate web traffic through attacker-controlled infrastructure across the globe. Cybercriminals aren't exploiting a vulnerability in NGINX itself. Instead, they're gaining access to server configurations, modifying them to intercept traffic, and channeling it through malicious domains they control. It's clever because your users never know they've been compromised. They land on the pages they expect. But attackers see everything.
Security researchers at Data Dog Security Labs have been tracking this campaign for months, and what they've discovered is alarming. The attackers are primarily targeting government agencies and educational institutions across Asia, but the infrastructure suggests this could expand anywhere. The impact isn't just about stolen data. Hijacked traffic can be weaponized for phishing attacks, malware injection, ad fraud, and even launching attacks against other targets while masking the attacker's true origin.
This isn't a zero-day exploit. It's not a breakthrough in cryptography or network protocols. Instead, it's a reminder that security often comes down to basics: access control, configuration hardening, and monitoring. And right now, thousands of organizations aren't getting those basics right.
TL; DR
- Attack Vector: Attackers modify NGINX configuration files to intercept and reroute traffic through attacker-controlled domains
- Primary Targets: Government and educational institutions in Asia, particularly Singapore, Denmark, and Nordic countries
- Data at Risk: Session tokens, cookies, IP addresses, user agents, referrer headers, and sometimes credentials or API keys
- Monetization Methods: Stolen traffic sold for ad fraud, SEO manipulation, click fraud, and proxy services for other attacks
- Why It Works: No vulnerability exploited, victims see legitimate pages, and HTTP headers are preserved making data theft invisible
- Bottom Line: Organizations need immediate configuration audits, access controls, and continuous monitoring of NGINX instances
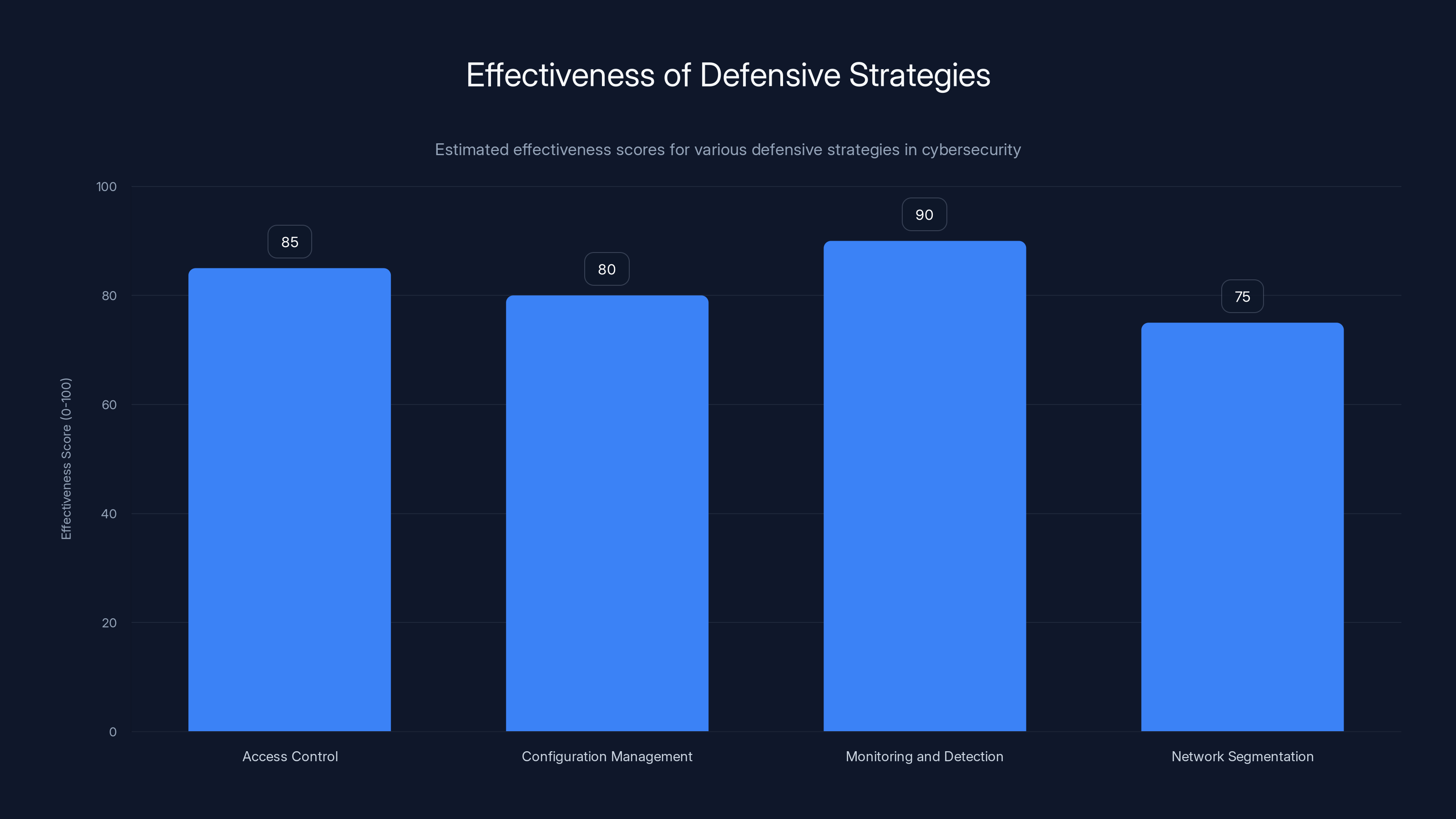
Monitoring and Detection strategies are estimated to be the most effective in preventing compromises, with a score of 90 out of 100. Estimated data.
What Is NGINX and Why It Matters
NGINX is one of the most critical pieces of infrastructure on the internet. Started in 2004 by Igor Sysoev as a solution to the C10K problem (how to handle 10,000 concurrent connections), NGINX has become the reverse proxy and web server of choice for millions of websites worldwide.
When you visit a major website, NGINX is often the first piece of software that touches your request. It sits in front of backend applications and decides where your traffic goes. It balances load across multiple servers. It caches content. It terminates SSL connections. It handles compression. NGINX does the heavy lifting so your actual application servers can focus on business logic.
According to W3 Techs data, NGINX powers approximately 33% of all websites with a known web server. That's roughly one in three websites you visit today. The only web server more common is Apache HTTP Server, and the gap is closing.
Because NGINX operates at the edge of your infrastructure, it sees everything. Every HTTP header. Every cookie. Every request parameter. Every URL. It's positioned perfectly to act as a gatekeeper, but it's also positioned perfectly as a target for attackers who want to intercept traffic.
NGINX configuration files are plain text. They're human-readable. And they're often stored on servers with insufficient access controls. If an attacker can modify these files, they can reshape how traffic flows through your entire infrastructure.
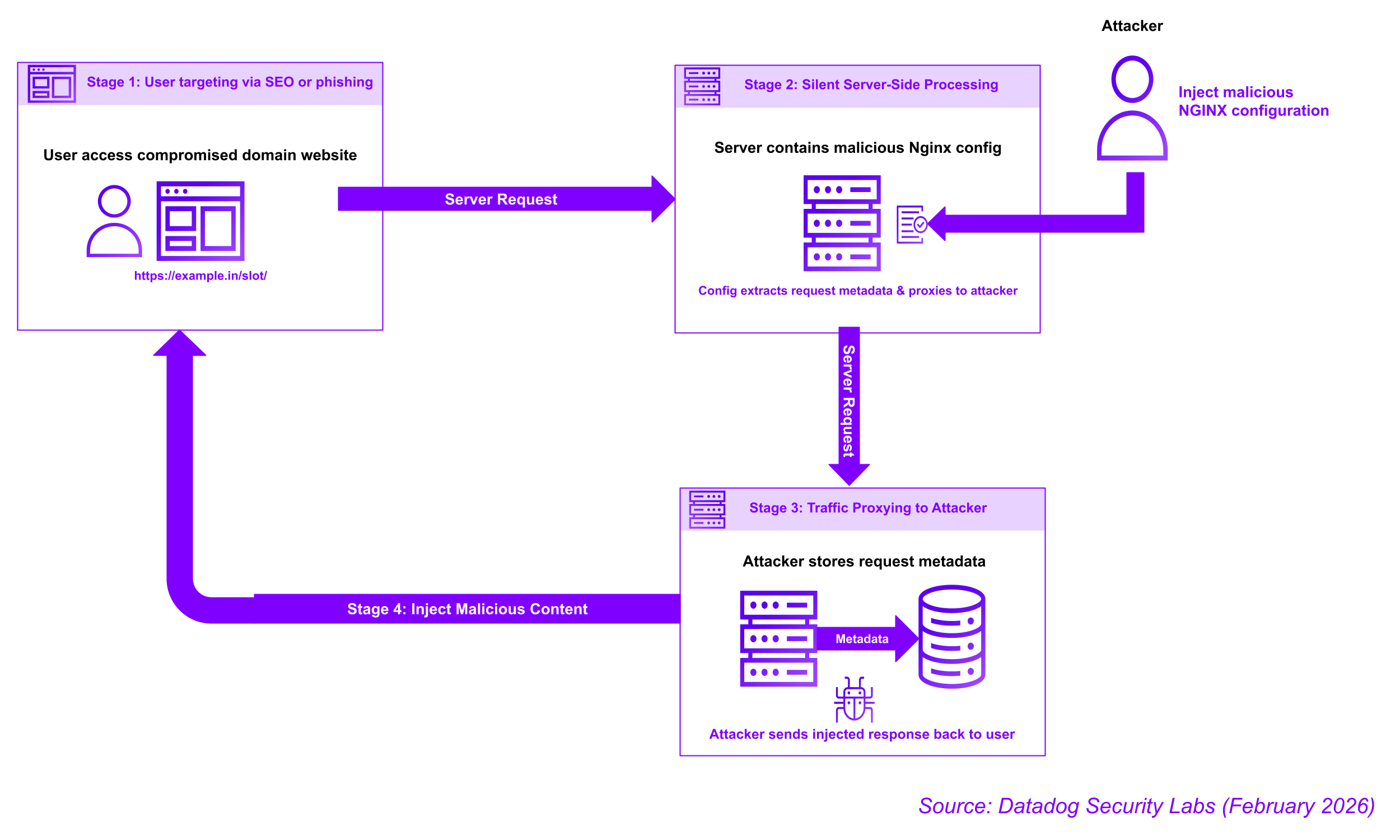
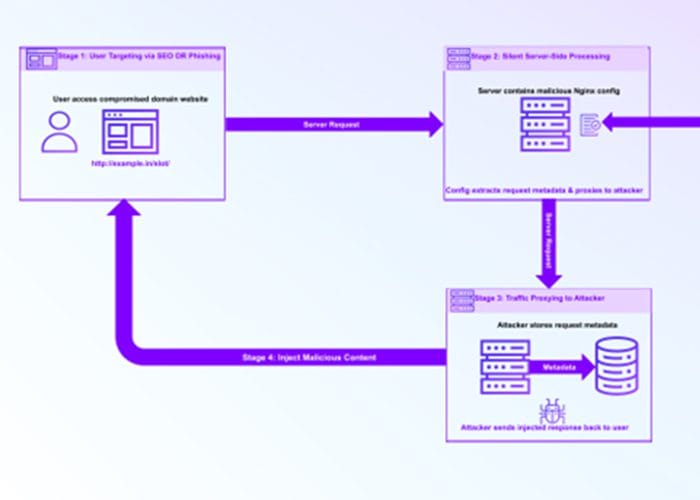
How the Attack Works: A Five-Stage Campaign
The attackers behind this campaign have developed a methodical five-stage process. Understanding each stage helps defenders build better protections.
Stage 1: Gaining Initial Access
The campaign begins with gaining administrative or privileged access to NGINX servers. This can happen through multiple vectors. Weak SSH credentials. Unpatched vulnerabilities in other services running on the server. Supply chain attacks. Phishing campaigns targeting system administrators. SQL injection leading to credential theft. The researchers didn't specify exactly how initial compromise occurs, but the targets suggest these aren't random attacks. Someone is specifically hunting for government and educational sector infrastructure.
Once inside, attackers establish persistence. They create backdoor accounts. They modify SSH keys. They install persistence mechanisms that survive server reboots. This isn't a smash-and-grab attack. These are patient, methodical compromise operations.
Stage 2: Configuration Injection
After gaining access, attackers modify the NGINX configuration files, typically found at /etc/nginx/nginx.conf or in configuration directories like /etc/nginx/sites-enabled/. These plain text files define how NGINX behaves. They specify which ports to listen on, which SSL certificates to use, where to route traffic, and how to rewrite URLs.
The attackers add malicious configuration blocks that intercept incoming requests. These blocks don't delete legitimate configurations. They supplement them. The attacker inserts rules that match certain traffic patterns and intercept them before legitimate routing rules process the request.
This is where the attack gets clever. They're not breaking NGINX. They're extending its functionality. They're using NGINX's own features, specifically the proxy_pass directive and URL rewriting rules, to achieve their goals.
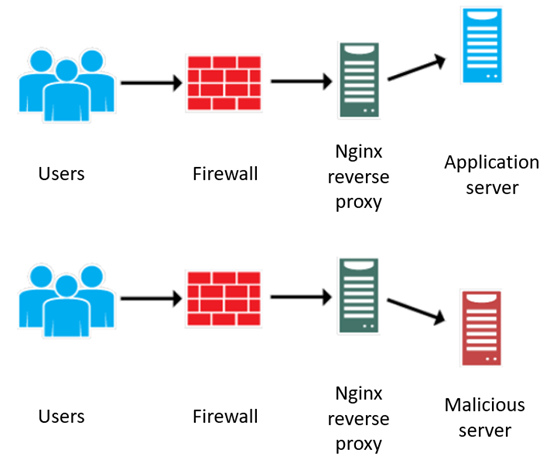
Stage 3: Traffic Interception and Redirection
When a legitimate user makes a request, NGINX processes it according to the modified configuration. The malicious rules intercept the request and rewrite it. The original URL is preserved. The destination is changed. The traffic gets forwarded to an attacker-controlled domain instead of the legitimate backend server.
From the user's perspective, nothing is wrong. The page eventually loads correctly. The attacker's infrastructure receives the request, extracts the valuable data from headers, and then forwards it to the legitimate destination. There's a slight delay, but nothing that raises alarm bells.
The attackers use infrastructure they control to observe all traffic passing through. They can log everything. Analyze patterns. Extract credentials from request headers.
Stage 4: Data Exfiltration
Because HTTP headers are preserved during the traffic interception, attackers collect valuable data:
- Session tokens (often stored in
Set-Cookieheaders) - User authentication cookies
- API keys (if they appear in request headers)
- IP addresses (from
X-Forwarded-Forheaders or source IP) - User agents (revealing device types and browsers)
- Referrer headers (showing where users came from)
- Custom headers that applications use for authentication
For government and educational sectors, this data is particularly valuable. Educational institutions often use simple cookie-based authentication systems. Government agencies sometimes store API keys in headers. Researchers accessing sensitive databases often have their authentication tokens visible in request headers.
The attackers don't need to break encryption or crack passwords. They're just observing legitimate authentication mechanisms and collecting the credentials in transit.
Stage 5: Data Monetization and Secondary Attacks
Once attackers have collected this data, they have multiple revenue streams. They can sell stolen session tokens to other cybercriminals who will use them for account takeover attacks. They can use credentials to access protected databases. They can monetize the intercepted traffic itself.
Clean, legitimate user traffic is valuable. Ad fraud networks will pay for it. SEO manipulation services need real traffic to boost search rankings. Click-fraud schemes need legitimate user clicks. Botnets need residential IP addresses to hide malicious traffic. Attackers can proxy legitimate user traffic through criminal networks, effectively monetizing your infrastructure.
Moreover, compromised NGINX servers become proxies for attacking other targets. Attackers can mask their true origin by routing attacks through your hijacked server. If an attacker wants to DDo S a government agency but doesn't want to be traced, they route the attack traffic through your compromised NGINX server. When investigators trace the source, they find your infrastructure, not the attacker.
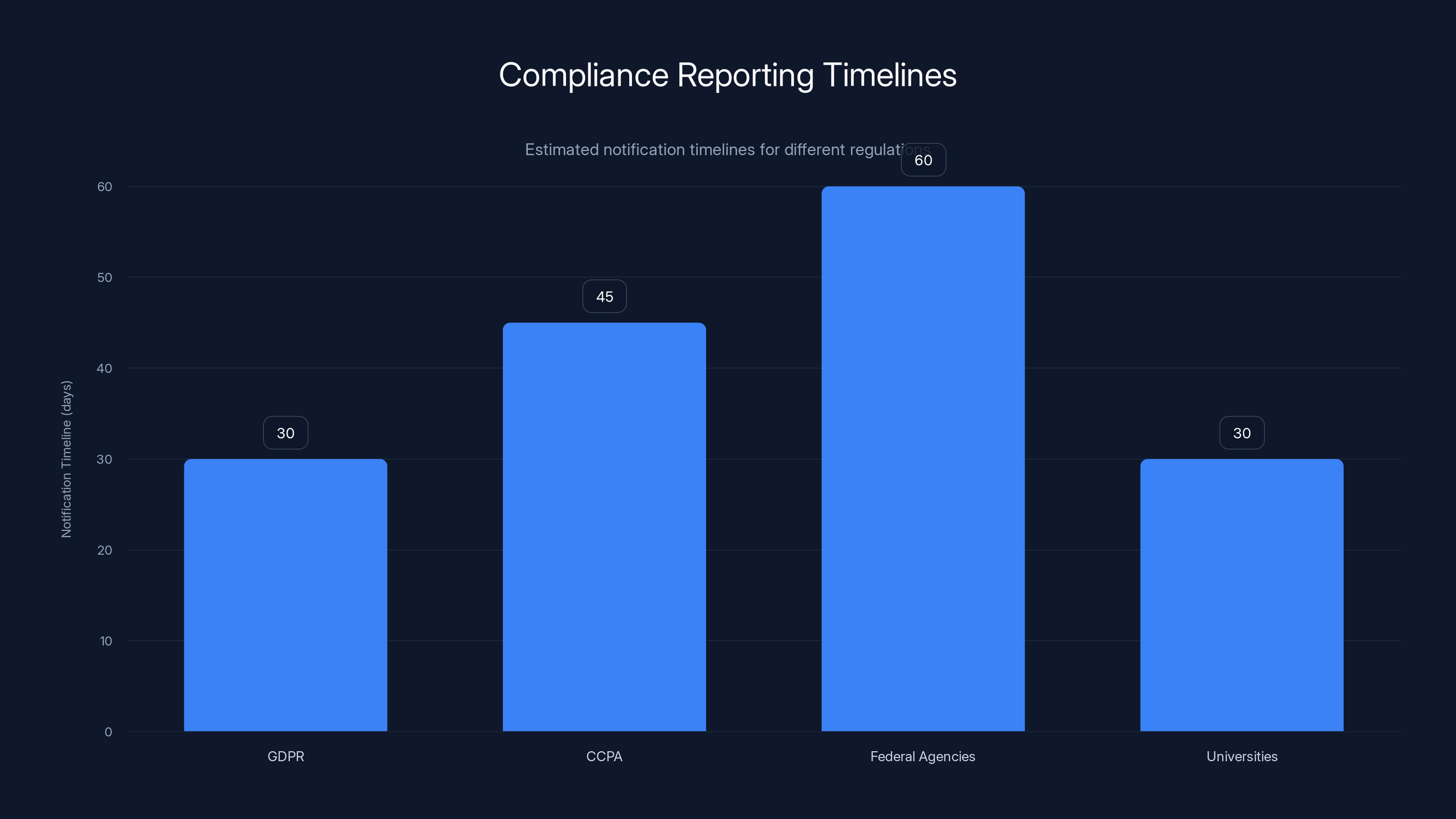
Estimated data shows varying notification timelines for breach disclosures, with GDPR and CCPA requiring quicker responses compared to federal agencies.
Geographic Distribution and Targeting Patterns
Data Dog's research identified victims across multiple continents, but with clear geographic clustering. The most heavily targeted regions include:
Asia-Pacific Region: Singapore represents a significant concentration of targets. Researchers also identified compromised servers in Japan, South Korea, and Hong Kong. These are all major technology and finance hubs with critical infrastructure. Singapore's position as a Southeast Asian tech center makes it particularly valuable for attackers seeking access to regional government and educational networks.
Nordic Countries: Denmark, Finland, Norway, and Sweden show surprising numbers of compromised servers. These countries host significant portions of European government and university infrastructure. The Nordic countries invest heavily in digital government services, making them attractive targets for attackers seeking to intercept government communications.
Western Europe: The United Kingdom, Italy, Netherlands, Belgium, France, and Germany all appear in the victim list. These countries represent major technology centers and host critical infrastructure. EU regulations like GDPR make certain government and educational data particularly valuable.
North America: The United States, Canada, and Mexico show compromised servers, though in smaller numbers than Asia-Pacific.
Oceania: Australia and New Zealand report some affected infrastructure.
The geographic distribution suggests this isn't a random spray-and-pray attack. The targeting appears strategic. Attackers are hunting for specific sectors: government agencies and educational institutions. These sectors are valuable because they often handle sensitive data, use simple authentication mechanisms, and have long-lived sessions.
Educational institutions are particularly attractive. Universities operate networks with thousands of users. Students and researchers access databases containing academic research, often including government-funded research or research with national security implications. A single compromised NGINX server on a university network might provide access to thousands of researcher accounts.
Why This Attack Vector Is So Effective
Traditional security defenses focus on preventing unauthorized access or detecting malware. But this attack bypasses many standard defenses because it leverages legitimate NGINX functionality.
Legitimate Functionality Abuse
NGINX configuration injection isn't exploiting a bug. It's using NGINX exactly as designed. The proxy_pass directive exists to forward traffic to backend servers. URL rewriting exists to transform URLs. These features are essential for how NGINX works. Disabling them would break legitimate use cases.
Security tools looking for malware won't find anything. There's no injected binary. There's no malicious process. There's no shellcode. Just modified text in a configuration file.
Invisible to End Users
The attack preserves the user experience. A user who requests a page gets the page they expect. The only difference is that somewhere in the middle, their request was intercepted. The slight latency increase might be attributed to normal network conditions. Most users won't notice.
This means the attack can continue for months or years before discovery. The attacker might have weeks or months to exfiltrate data before anyone notices something is wrong.
Preserves Network Traffic Patterns
When defenders investigate security incidents, they often look at network traffic logs. They search for unusual outbound connections. They hunt for suspicious IP addresses.
But this attack doesn't create obviously suspicious traffic. The attacker's infrastructure receives a copy of legitimate traffic and then forwards it to the real destination. From a network monitoring perspective, it looks like normal traffic is flowing through the system. The unusual part (the temporary copy) happens silently in the proxy layer.
Works Even With HTTPS
You might think that HTTPS encryption would protect against this. But NGINX terminates SSL connections. It receives unencrypted traffic from clients, processes it, and then re-encrypts it for backend communication. The interception happens at the layer where NGINX sees unencrypted data.
An attacker with write access to NGINX configuration files can read and manipulate traffic before it's encrypted for transmission to backends.
No Vulnerability to Patch
When a security vulnerability is discovered, organizations issue patches. Security teams deploy them. Vulnerability scanners verify remediation. But this attack doesn't rely on a vulnerability. There's no CVE number. There's no security patch that fixes it.
The only fix is better access control, better monitoring, and better detection of unauthorized configuration changes.
The Data Collection Arsenal
When attackers intercept traffic through compromised NGINX servers, they gain access to far more than just passwords. Every HTTP header becomes a potential data source.
Session Tokens and Authentication Cookies
Most web applications use session tokens stored in cookies. When a user logs in, the application issues a token. The user's browser stores it and includes it in every subsequent request. If an attacker captures the session token, they can impersonate the user without knowing their password.
Educational institutions often use simple session token systems with long expiration times. A research who logs into the university's digital library might have a session that lasts weeks. An attacker who intercepts that session token can access the library's research databases for weeks without detection.
Government agencies sometimes use similar mechanisms. A civil servant logging into a government portal might have a long-lived session. If that session token is captured, an attacker has access to government systems.
API Keys and Credentials in Headers
Some applications pass authentication credentials in custom HTTP headers. This is technically violating best practices, but it happens. Some legacy systems store API keys in headers. Some internal services use this pattern. An attacker intercepting traffic sees these credentials immediately.
Researchers using the university's high-performance computing cluster might pass API keys in headers. An attacker intercepting these requests could use those keys to access the computing cluster and steal research data.
Metadata That Reveals User Behavior
HTTP headers contain metadata about users and their behavior. The User-Agent header reveals the device type, operating system, and browser. The Referer header shows where the user came from. The Accept-Language header reveals preferred languages. The X-Forwarded-For header reveals the user's IP address.
When combined, this metadata can identify specific individuals. An attacker might not know "Dr. Smith's" password, but by observing that a specific user agent accessing research databases from a specific IP address at a specific time each day is accessing files related to sensitive government research, they can profile that individual and target them for social engineering or credential theft.
Query Parameters Containing Sensitive Data
Sometimes URLs contain sensitive parameters. Search queries, for instance. A researcher searching for "anthrax vaccine effectiveness" is revealing the topic of their research. An employee searching for "cancer treatment efficacy data" is revealing their organization's research interests.
When URLs are intercepted, attackers see these query parameters. They learn what their targets are researching, which can inform further attacks.
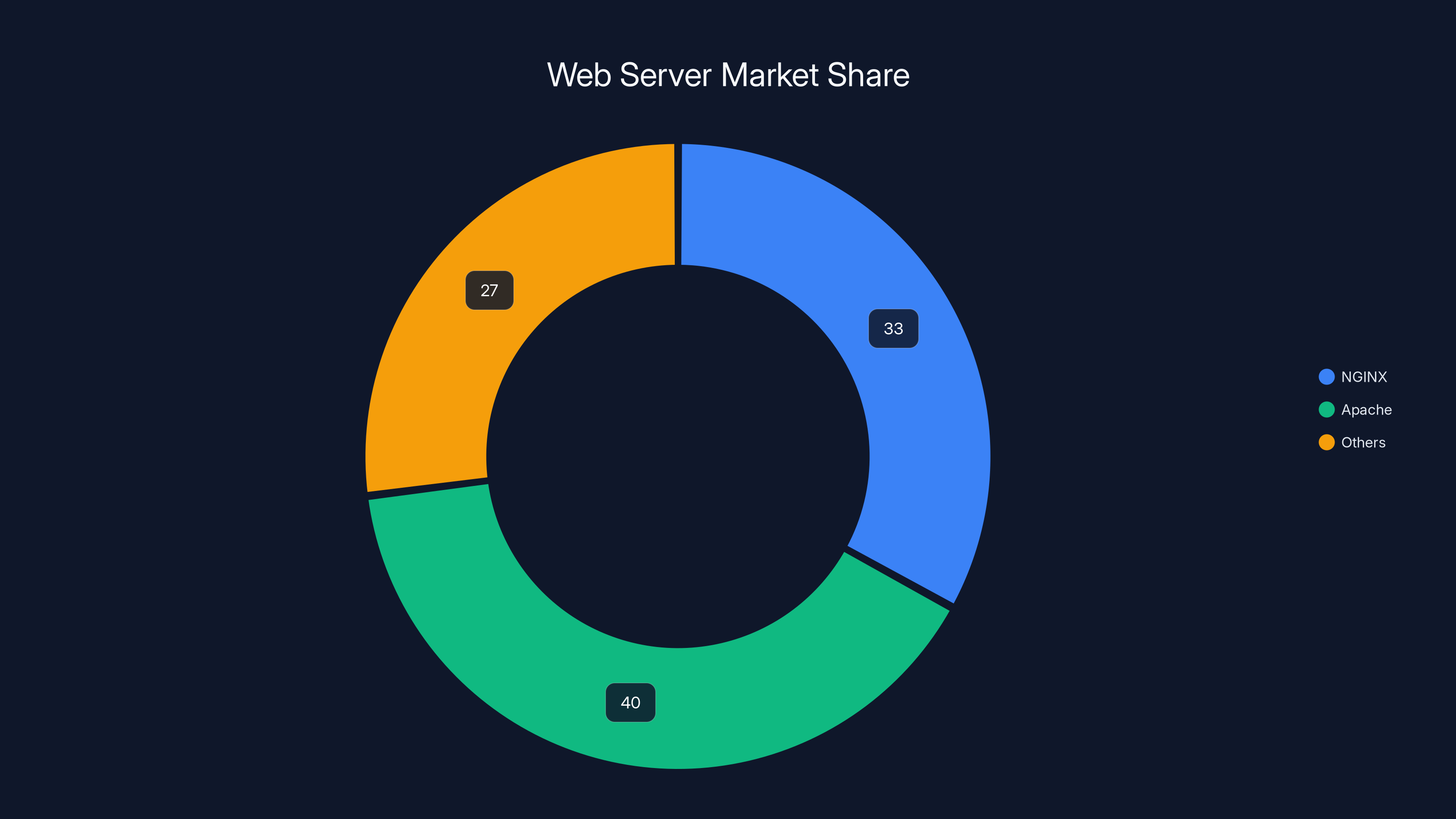
NGINX powers approximately 33% of all websites with a known web server, closely following Apache at 40%.
Monetization Strategies for Stolen Traffic
For attackers, compromised NGINX servers aren't just tools for data theft. They're profitable assets that can be monetized through multiple channels.
Ad Fraud Networks
Clean, legitimate user traffic is valuable to ad fraud networks. These networks need real users visiting websites so they can generate fraudulent ad impressions. An ad fraud network might pay an attacker for access to legitimate user traffic, then route that traffic through websites running ads, generating fraudulent ad revenue.
A compromised NGINX server handling thousands of requests per day represents thousands of potential ad impressions. Attackers can sell this traffic to ad fraud networks for pennies per thousand impressions, creating a steady revenue stream.
SEO Manipulation Services
Search engines like Google rank websites partly based on the number of clicks they receive. SEO manipulation services artificially boost click counts to improve search rankings. They need real users clicking on links. Legitimate user traffic intercepted from government and educational websites is perfect for this.
An attacker with access to thousands of legitimate user requests can inject links or redirect users to specific websites, artificially boosting their click counts and search rankings. They can sell this service to black-hat SEO practitioners.
Click Fraud Schemes
Pay-per-click advertising networks pay website owners for each user who clicks on ads. Click fraud networks artificially generate clicks to defraud advertisers. They need real traffic and real clicks to make the fraud convincing.
Legitimate user traffic is more valuable than bot traffic for click fraud because it's harder to detect. An attacker with access to legitimate government or educational user traffic can redirect those users to click ads, generating fraudulent revenue.
Residential Proxy Services
Cybercriminals often need to mask their true IP addresses. Residential proxy services hide malicious traffic behind legitimate user IP addresses, making it appear as though the traffic originated from real, home internet users rather than data centers.
Compromised NGINX servers provide the perfect infrastructure for operating residential proxies. Attackers can channel malicious traffic through the server, making it appear as though it originated from the legitimate users whose traffic is being intercepted. They can then sell access to this proxy infrastructure to other cybercriminals.
Botnet Infrastructure
DDo S botnets need proxy points to launch attacks while hiding their true origin. A compromised NGINX server representing legitimate government or educational infrastructure is ideal. Attackers can use it to proxy DDo S traffic or malware distribution, all while appearing to come from trusted infrastructure.
Attack Surface: How Attackers Gain Initial Access
The attack campaign doesn't provide details about initial compromise vectors, but infrastructure targeting suggests specific attack methodologies.
Brute Force and Weak Credentials
SSH brute force attacks remain common. Attackers use dictionary attacks against default usernames (root, admin, ubuntu) with common passwords. Organizations running NGINX servers on virtual machines or cloud instances sometimes use weak default credentials. Attackers systematically scan for open SSH ports and attempt default credentials.
Educational institutions often have less stringent credential policies than government agencies. Graduate students setting up servers might use simple passwords. These servers become entry points for broader attacks.
Unpatched Vulnerabilities
NGINX itself rarely has vulnerabilities, but the servers running NGINX often run other software. An unpatched PHP application, an outdated web framework, or a vulnerable Content Management System can provide entry points. Attackers exploit these vulnerabilities to gain command execution, which they then use to escalate privileges to access NGINX configuration files.
Supply Chain and Managed Service Attacks
Some organizations use managed hosting providers or outsource infrastructure management. If an attacker compromises the managed service provider, they gain access to all customer infrastructure. A single compromise of a managed hosting provider's admin panel could provide access to hundreds of NGINX instances.
Third-Party Software and Plugins
Some NGINX configurations include third-party modules or plugins. If these are outdated or vulnerable, they can provide entry points. Attackers exploiting vulnerabilities in third-party modules could gain code execution and configuration file access.
Insider Threats
Some compromises might involve insiders. A disgruntled system administrator with legitimate access to NGINX configuration files could modify them on behalf of attackers. An IT contractor with temporary access could plant configuration changes. This requires less technical sophistication than hacking but is harder to detect because the access is legitimate.
Detection Strategies and Red Flags
Organizations need proactive detection mechanisms to identify compromised NGINX servers before attackers exfiltrate significant data.
Configuration File Integrity Monitoring
The most direct detection method is monitoring NGINX configuration files for unauthorized changes. Host-based file integrity monitoring tools can hash configuration files and alert when hashes change. This detects modifications quickly, sometimes within minutes.
A comprehensive approach involves:
- Creating baseline hashes of all NGINX configuration files
- Storing hashes in a centralized, protected location
- Continuously monitoring for hash changes
- Alerting administrators immediately when changes are detected
- Requiring approval for any configuration changes
Suspicious Proxy Rules
Administrators should regularly review NGINX configuration files for rules they didn't create. Look for unexpected proxy_pass directives pointing to unfamiliar domains, unusual URL rewrite rules, or access log references to suspicious IP addresses.
Any proxy_pass directive that doesn't align with documented application architecture should be investigated. If you know your NGINX server forwards traffic only to three backend servers but you find a proxy_pass directive pointing to an external domain, that's a major red flag.
Outbound Traffic Analysis
Monitor outbound traffic from NGINX servers to domains outside your organization. If your NGINX server suddenly starts making requests to external domains, and those domains aren't in your approved list, investigate.
Network monitoring tools should flag unexpected outbound connections from NGINX servers. This is particularly important for government and educational institutions where outbound traffic might be restricted or monitored.
Log Analysis and Unusual Patterns
NGINX access logs can reveal suspicious patterns. Look for:
- Requests to unusual backend destinations
- Requests with suspicious headers or parameters
- Patterns suggesting credential collection
- Traffic spikes to unexpected destinations
- Requests from internal IP addresses to external domains
Log analysis tools should baseline normal traffic patterns and alert on deviations. If NGINX suddenly starts receiving traffic from a new IP address range, or traffic volume to a specific backend suddenly increases, investigate.
Process Monitoring and Execution
Monitor the NGINX process for suspicious behavior. If the NGINX process suddenly starts making network connections it didn't previously make, or if child processes spawn from the NGINX worker process, alert.
Host-based process monitoring tools can track system calls and network connections made by NGINX. Unexpected behavior could indicate compromise.
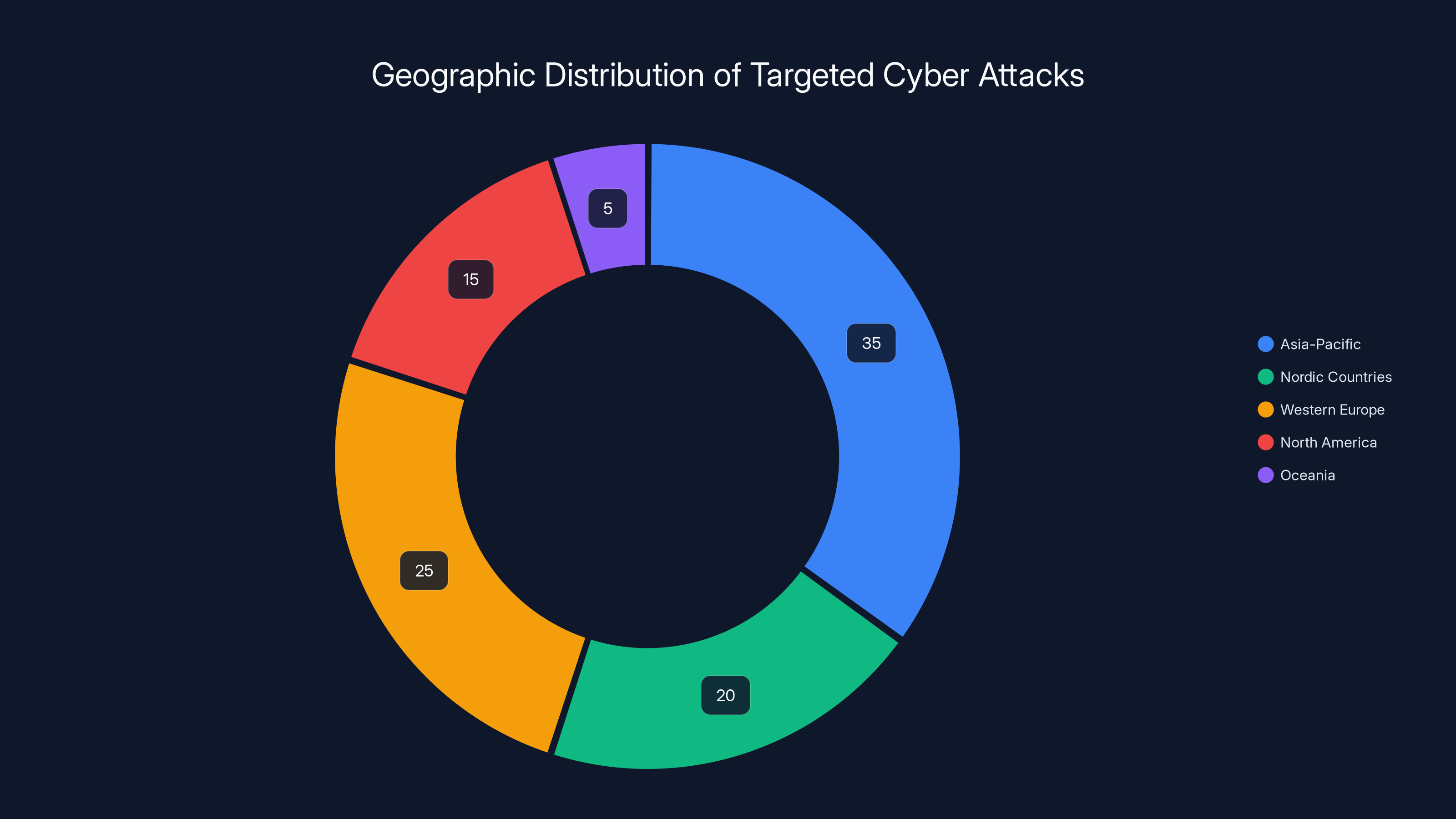
Asia-Pacific leads with 35% of targeted attacks, followed by Western Europe at 25%. The strategic targeting focuses on government and educational sectors. (Estimated data)
Remediation and Recovery Procedures
If an organization discovers compromised NGINX configuration files, response must be swift and thorough.
Immediate Containment
First, stop the bleeding. The priority is preventing further data exfiltration:
- Immediately restart NGINX from clean configuration files to stop interception
- Revoke all active sessions to invalidate stolen session tokens
- Force password resets for all users who might have accessed the system while compromised
- Revoke and rotate API keys that might have been exposed
- Block attacker-controlled domains at the firewall and DNS level
- Monitor all accounts for unauthorized access attempts using stolen credentials
Investigation and Forensics
After containment, investigate the compromise:
- Preserve evidence by creating forensic images of affected systems
- Identify compromise timeline by reviewing log files and file timestamps
- Determine scope of access: what data was accessed, what systems were touched
- Identify attacker infrastructure (C2 servers, proxy servers, command and control)
- Trace attacker activity through log files to understand their objectives
- Identify initial compromise vector to prevent recurrence
System Hardening
After forensic investigation, rebuild systems from scratch:
- Wipe compromised systems and reinstall operating systems
- Apply all security patches before putting systems back online
- Implement strong access controls restricting configuration file access
- Enable audit logging for all configuration changes
- Deploy monitoring for configuration changes
- Implement two-factor authentication for administrative access
Communication and Disclosure
Depending on the data compromised and applicable regulations, organizations may need to disclose the breach:
- Determine regulatory obligations (GDPR, HIPAA, state breach notification laws)
- Assess damage to determine who needs notification
- Prepare disclosure communications to affected parties
- Notify relevant authorities as required by law
- Provide credit monitoring or remediation services if personal data was compromised
Defensive Strategies and Best Practices
Organizations should implement layered defenses to prevent similar compromises.
Access Control Fundamentals
Prevent unauthorized configuration file modification:
- Restrict file permissions on NGINX configuration files (chmod 644 or more restrictive)
- Use role-based access control (RBAC) to limit who can modify configurations
- Require approval workflows for configuration changes
- Implement multi-factor authentication for administrative access
- Use SSH keys instead of passwords for command-line access
- Disable root login and use sudo with audit logging
Configuration Management
Track and control configuration changes systematically:
- Use a configuration management system (Ansible, Puppet, Chef)
- Store configurations in version control (Git) with change history
- Require code reviews for configuration changes before deployment
- Implement configuration validation to prevent syntax errors
- Test changes in staging before production deployment
- Document all configuration changes with business rationale
Monitoring and Detection
Detect compromise attempts early:
- Enable audit logging at the operating system level
- Monitor file changes using AIDE or similar tools
- Alert on unexpected outbound connections from NGINX servers
- Monitor NGINX error logs for unexpected directives or errors
- Baseline network traffic and alert on deviations
- Implement intrusion detection systems (IDS) monitoring network traffic
Network Segmentation
Limit potential damage from compromise:
- Segment networks so NGINX servers can't directly access sensitive data
- Restrict outbound traffic from NGINX servers to approved destinations
- Use firewalls to control what systems NGINX can communicate with
- Implement proxy controls to log and restrict proxy traffic
- Isolate development and production NGINX instances
Incident Response Planning
Prepare for compromise:
- Develop incident response plans specific to NGINX compromise
- Document forensic procedures for collecting evidence
- Create playbooks for common attack scenarios
- Conduct regular drills to test incident response procedures
- Maintain offline backups of configuration files
- Pre-stage recovery media and clean configuration files
The Role of Cloud Infrastructure and Managed Services
Many organizations now run NGINX in cloud environments like AWS, Azure, or Google Cloud. Does this change the attack surface?
Cloud Native Vulnerabilities
Cloud infrastructure introduces new considerations. Instances can be created and destroyed rapidly. Images are often templated. If an attacker compromises a template, every instance created from that template inherits the compromise.
Cloud providers offer configuration management tools, but organizations must use them. An NGINX instance created from a default image might have weak SSH credentials or default configurations. If multiple instances are created from the same image, a single compromise provides entry to multiple systems.
Cloud Access and Credentials
Cloud administration typically happens through API credentials or web consoles. If an attacker gains access to cloud credentials, they can modify instances, create new instances, delete backups, and generally wreak havoc.
The attack campaign targets NGINX specifically, but cloud-based NGINX instances are vulnerable to the same configuration injection attacks. The difference is that cloud providers often provide better auditing and logging, which can help with detection.
Serverless Alternatives
Some organizations are moving away from NGINX entirely, using cloud-native load balancers and serverless computing. AWS Application Load Balancer, Azure Front Door, and Google Cloud Load Balancer provide similar functionality without managing NGINX instances.
These managed services reduce operational burden and can provide better security through built-in protections. However, they introduce different attack surfaces and dependencies on cloud provider security.
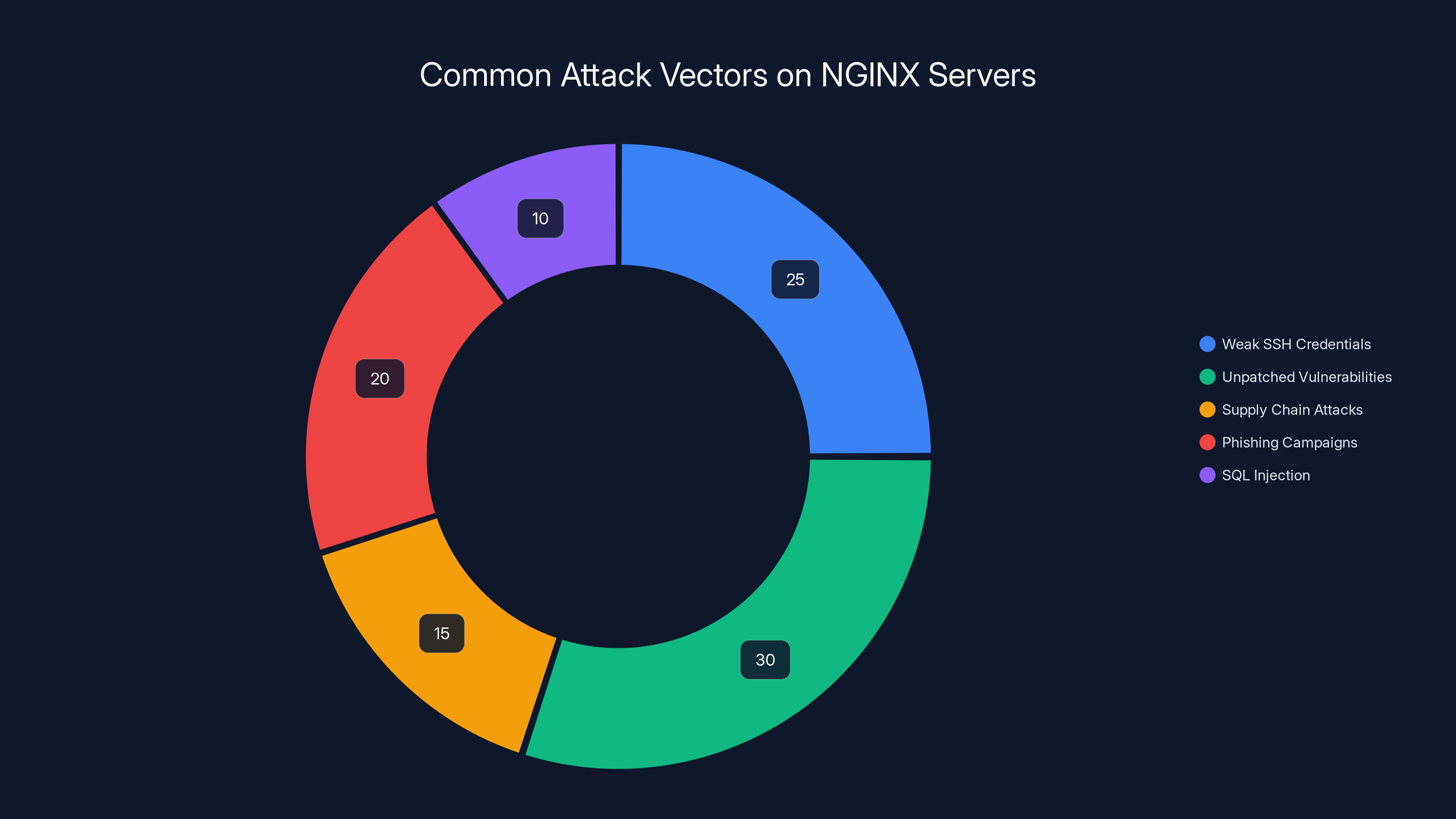
Estimated data shows that unpatched vulnerabilities and weak SSH credentials are the most common vectors for initial access to NGINX servers, highlighting the importance of regular updates and strong password policies.
Government and Educational Sector Implications
The attack campaign specifically targets government and educational institutions. Why are these sectors particularly vulnerable?
Diverse Infrastructure
Government agencies often operate heterogeneous infrastructure. Different departments run their own IT systems. University systems vary dramatically. This diversity makes standardized security controls difficult. Some departments might have strong security practices while others lag. An attacker needs only one weak link.
Budget Constraints
Educational institutions operate with limited budgets. Many universities run on shoestring IT budgets. System administrators manage thousands of servers with minimal staff. Government agencies sometimes face budget constraints limiting security investments. These constraints mean infrastructure goes unmaintained, patches go uninstalled, monitoring remains minimal.
Bureaucratic Processes
Government procurement and change management processes are often slow. Deploying security tools requires approval from multiple layers. A vulnerability discovered today might take months to remediate through official channels. This delay gives attackers time to exploit vulnerabilities before they're patched.
Data Value
Government and educational institutions hold valuable data. Government databases contain personal information about citizens, intelligence data, and strategic information. Educational databases contain research data, some with national security implications. Researchers often work on government-funded projects. The data is valuable not just for direct monetization but for espionage.
Researcher and Government Worker Targeting
Researchers and government employees are targeted for information valuable to nation states. Compromised NGINX servers provide a collection point for activity data about specific researchers or agencies. An attacker might not care about the data flowing through a specific NGINX server, but rather about identifying which researchers access which databases at what times.
Long-Term Defensive Architecture
Preventing this type of attack requires architectural changes, not just tactical responses.
Zero Trust Architecture
Instead of trusting anything inside the network, Zero Trust treats every request as potentially malicious. This applies to configuration files too. System components should verify the integrity of configuration files before using them. If a configuration file hash doesn't match the expected value, the system should refuse to load it.
NGINX could be modified to refuse loading configuration files unless they're signed with a private key held by the organization. This prevents attackers from modifying configurations even if they gain file system access.
Configuration as Immutable Infrastructure
Instead of modifying configuration files on running systems, configuration should be immutable. Instances are created from images with embedded configurations. To change configuration, you create new instances. Old instances are destroyed. This prevents configuration drift and makes unauthorized modifications obvious.
Tools like Docker containerization and Kubernetes orchestration support this model. NGINX runs in a container with immutable configuration. To change configuration, you rebuild the container image and deploy new instances.
Separation of Configuration and Execution
Configuration and code execution should be separated. Configuration should be read from a secure configuration service, not stored on the server. NGINX instances should fetch configuration from a central configuration server at startup. If the configuration changes, NGINX reloads it, but the actual configuration file is protected.
Services like Hashi Corp Consul, Spring Cloud Config, or cloud provider configuration services provide this capability. Configuration is stored in a protected service. Instances request configuration with authentication. The configuration service logs all access. Unauthorized configuration changes are immediately visible.
Encrypted Configuration Delivery
Configuration should be encrypted in transit and at rest. When NGINX fetches configuration from a central service, the connection should be encrypted. Configuration files should be encrypted on disk. Only authorized services should have decryption keys.
Emerging Technologies for Better Detection
New technologies are emerging to help detect infrastructure compromise.
Behavioral Analytics
Machine learning systems can learn normal NGINX behavior and alert on deviations. Normal traffic patterns, request volumes, request types, and destination servers are baseline. Significant deviations might indicate compromise. If NGINX suddenly starts forwarding traffic to new destinations, behavioral analytics systems can detect this.
Continuous Compliance Monitoring
Tools can continuously verify that infrastructure meets compliance standards and organizational policies. Configuration can be continuously scanned for compliance with standards. If a configuration diverges from approved standards, alerts trigger automatically.
Blockchain-Based Configuration Verification
Experimental approaches use blockchain to create immutable records of configuration changes. Each configuration change is recorded in a blockchain. Queries can verify the complete history of changes. This makes configuration modification traceable and auditable.
AI-Powered Threat Detection
Advanced AI systems can detect compromised infrastructure by learning traffic patterns. Normal traffic flows have characteristics that malicious interception disrupts. AI systems can detect subtle changes in latency distribution, packet sizes, or traffic timing that might indicate interception.
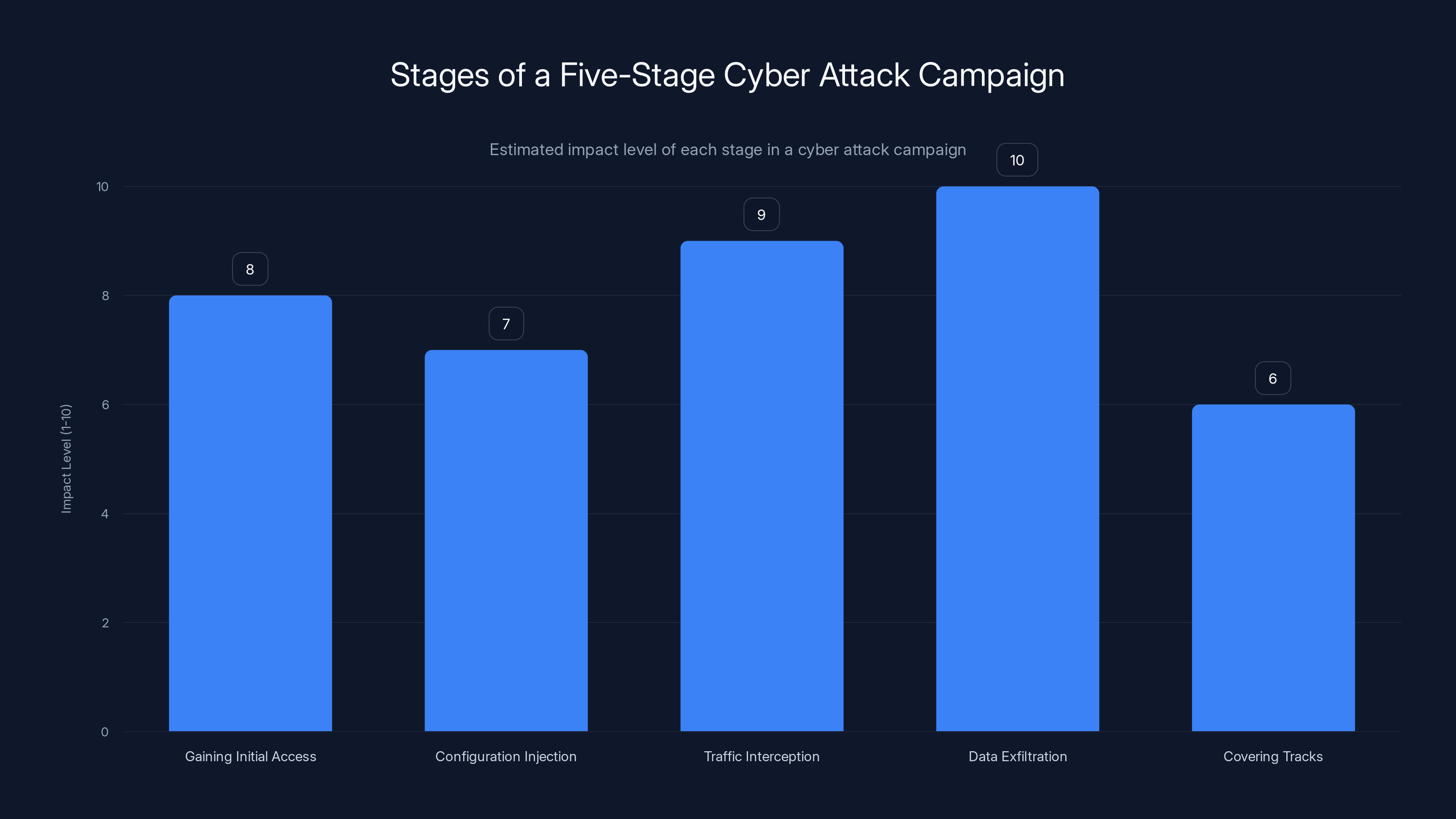
The most critical stages in the attack are Traffic Interception and Data Exfiltration, with impact levels of 9 and 10 respectively. Estimated data based on typical cyber attack progression.
Industry Response and Vendor Patches
How have software vendors and infrastructure providers responded to this attack campaign?
NGINX itself hasn't issued patches because there's no vulnerability to patch. The attack leverages legitimate functionality. However, vendors offering security tools have created detection signatures. Intrusion detection systems can flag traffic patterns consistent with this attack. Log analysis tools can identify suspicious configuration rules.
Cloud providers have enhanced their monitoring. AWS, Azure, and Google Cloud have updated their security advisories to warn customers about configuration file monitoring. They recommend using file integrity monitoring services and configuration change alerts.
Security vendors have released guidance. SIEM vendors have created detection rules. Configuration management platforms have enhanced their change approval workflows. But these are reactive measures. Fundamental architectural changes are needed for better prevention.
Regulatory and Compliance Implications
This attack raises important compliance questions.
Breach Disclosure Obligations
If attackers accessed personal data through compromised NGINX servers, organizations must disclose the breach under GDPR, CCPA, and similar regulations. The notification timeline depends on the regulation, but many require notification within 30 to 60 days.
Government agencies also have reporting obligations. Federal agencies must report cybersecurity incidents to CISA. Universities must often report incidents to their institutional review boards or research sponsors.
Auditing and Logging Requirements
Many regulatory frameworks require logging of security-relevant events. Configurations changes should be logged. Access to sensitive systems should be logged. If these logs aren't maintained, demonstrating breach mitigation becomes difficult. Regulators expect organizations to maintain detailed logs.
Security Assessment Standards
This attack highlights the importance of regular security assessments. Auditing standards like SOC 2, ISO 27001, and NIST Cybersecurity Framework all require regular configuration reviews. Organizations subject to these standards should conduct assessments identifying compromised NGINX servers.
Secure Development and Deployment
Many standards require secure development and deployment processes. Configuration management should follow established procedures. Changes should be approved and tested. This attack shows that organizations failing to implement these processes are vulnerable.

Looking Forward: Future Iterations and Attack Evolution
As organizations implement defenses against this specific attack, attackers will evolve their techniques.
Obfuscated Configuration Changes
Instead of directly modifying configuration files, attackers might use configuration management tools themselves. If they gain access to Ansible playbooks or Puppet manifests, they can inject malicious rules that deploy across all NGINX instances. These changes would appear legitimate because they came through official change management.
Runtime Interception Without Configuration Files
Advanced attackers might inject code directly into the NGINX process memory without modifying configuration files. This would bypass file integrity monitoring. Detecting this requires runtime application self-protection (RASP) or process memory monitoring.
Supply Chain Attacks on NGINX Modules
Attackers might compromise third-party NGINX modules. Organizations installing these compromised modules would unknowingly deploy malicious functionality. Supply chain attacks are increasingly common. Verifying the integrity of all components is essential.
Distributed Interception Networks
Instead of routing traffic to a single attacker domain, attackers might distribute traffic across multiple points. This distributes the load, makes detection harder, and creates redundancy. A distributed interception network would be more resilient than a centralized one.
Encrypted Traffic Manipulation
As HTTPS becomes more prevalent, attackers will target encrypted traffic handling. Modern attacks might inject malicious certificates, perform man-in-the-middle attacks on encrypted connections, or manipulate encrypted data without decryption.
Recommendations for Organizations
Organizations should implement a comprehensive defense strategy:
Immediate Actions (Weeks 1-4)
- Audit NGINX configuration files on all systems
- Review for unexpected proxy rules or URL rewriting
- Enable file integrity monitoring on configuration files
- Implement change notifications for configuration modifications
- Review recent access logs for unusual patterns
- Force password resets for administrative accounts
- Rotate API keys used for administrative access
Short-Term Actions (Months 1-3)
- Implement configuration management for all NGINX instances
- Deploy centralized logging aggregating NGINX logs
- Implement network segmentation limiting NGINX outbound access
- Deploy intrusion detection systems monitoring NGINX traffic
- Conduct security assessments of all NGINX infrastructure
- Implement multi-factor authentication for administrative access
- Create incident response procedures for NGINX compromise
Long-Term Actions (Months 3-12)
- Migrate to container-based infrastructure with immutable configurations
- Implement centralized configuration service for dynamic configuration
- Deploy behavioral analytics for anomaly detection
- Implement continuous compliance monitoring for configuration standards
- Establish zero trust architecture for all infrastructure
- Conduct quarterly penetration testing of NGINX infrastructure
- Implement security training for administrators

Conclusion
The NGINX server hijacking campaign reveals fundamental truths about modern cybersecurity. Sophisticated attacks don't require exploiting exotic vulnerabilities. They require exploiting common mistakes: weak access controls, insufficient monitoring, and configuration management failures.
Thousands of organizations worldwide are running NGINX servers without basic protections. Configuration files sit on servers with insufficient access controls. Changes go unmonitored. Outbound traffic goes unwatched. For attackers, these are not sophisticated targets. They're low-hanging fruit.
The campaign targets government and educational institutions not because these sectors have superior security, but because they have valuable data and, often, less mature security practices than the private sector. A single compromised university NGINX server might provide access to research databases. A compromised government server might provide access to citizen data.
But this attack is preventable. Organizations that implement configuration management, access controls, monitoring, and incident response procedures dramatically reduce their risk. It's not expensive. It's not complicated. It's fundamental security hygiene that many organizations are simply not doing.
The NGINX hijacking campaign will likely continue and evolve. Attackers will refine their techniques. They'll develop new payloads. They'll target new sectors. But the fundamentals will remain: gain access, modify configuration, intercept and exfiltrate data, monetize the compromise.
Defending against this requires a shift in thinking. Security can't be an afterthought. Configuration management, access controls, and monitoring must be built into infrastructure from day one. Organizations must treat infrastructure as code, subject to the same version control, testing, and review processes as application code.
For government and educational institutions specifically, the implications are serious. If you haven't audited your NGINX configuration lately, do it now. If you're not monitoring for configuration changes, implement monitoring immediately. If you haven't forced administrative password resets in recent months, do it. The attackers behind this campaign are patient, methodical, and actively hunting for servers like yours.
FAQ
What exactly is an NGINX server and why do attackers target it?
NGINX is a reverse proxy and web server software that sits in front of web applications to handle incoming traffic, distribute load, and manage connections. Attackers target NGINX specifically because it's positioned at the network edge where it sees all incoming requests, making it perfect for intercepting data. Additionally, NGINX is incredibly common—running roughly one-third of all websites—which means compromising a single NGINX server potentially provides access to valuable data flowing through it.
How do attackers initially access NGINX servers to modify configuration files?
Attackers typically gain initial access through multiple vectors including weak SSH credentials, unpatched vulnerabilities in other software running on the server, supply chain attacks, phishing campaigns targeting administrators, or SQL injection in web applications. Once they achieve any level of system access, they work to escalate privileges and gain write access to NGINX configuration files. The research didn't specify exact methods but targeting patterns suggest attackers are hunting for specific sectors, not randomly scanning.
Can this attack be detected with standard intrusion detection systems?
Standard intrusion detection systems (IDS) can be effective but have limitations. IDS tools can detect unusual outbound connections to attacker infrastructure and flag suspicious traffic patterns. However, since the attack preserves user experience and doesn't generate obviously malicious network signatures, detection relies more on file integrity monitoring and configuration change alerts than traditional IDS. Organizations need layered detection combining network monitoring, log analysis, behavioral analytics, and configuration monitoring.
If my NGINX configuration was modified by attackers, what data am I most at risk of losing?
Attackers can collect HTTP headers including session tokens, authentication cookies, IP addresses, user agents, referrer information, and sometimes API keys or credentials if they appear in request headers. For government and educational organizations specifically, this might include research data access patterns, user identities of researchers accessing sensitive databases, and potentially authentication credentials for accessing protected systems. The specific risk depends on what data flows through your NGINX server and what authentication mechanisms are in use.
What's the difference between detecting this attack and preventing it?
Detection focuses on identifying that compromise has occurred, which is critical but comes too late to prevent data exfiltration. Prevention requires preventing unauthorized modification of configuration files in the first place through strict access controls, configuration management systems, and architectural changes like immutable infrastructure. The best defense combines both: prevent modification through access controls, but also assume compromise might occur and implement detection mechanisms to catch breaches quickly if they do happen.
How long might attackers have been operating through compromised NGINX servers before being detected?
This is the scary part: potentially months or years. Because the attack preserves user experience and doesn't generate obvious red flags, organizations might not notice compromise for extended periods. Attackers could collect data continuously without raising suspicion. This is why proactive monitoring for configuration changes and regular security audits are critical. The longer attackers operate undetected, the more data they exfiltrate and the more entrenched they become in your infrastructure.
Should organizations shut down all NGINX servers until they verify security?
No—NGINX itself is not the problem. Disabling all NGINX servers would break web services. Instead, organizations should conduct rapid configuration audits of all NGINX instances, implement file integrity monitoring, enable configuration change alerts, and review recent logs for suspicious activity. These actions can be completed in parallel while services remain operational. A phased approach to security improvements is more practical than shutting down critical infrastructure.
What security tools or services should organizations implement to protect against NGINX hijacking?
A comprehensive defense combines file integrity monitoring (AIDE, Tripwire), configuration management systems (Ansible, Puppet, Chef), centralized logging and SIEM platforms, intrusion detection systems, endpoint detection and response (EDR) tools, and behavioral analytics. Cloud-native organizations should also use cloud provider security monitoring services. The key is layered defense: access control prevents modification, configuration management prevents unauthorized changes from persisting, monitoring detects changes that do occur, and incident response procedures handle breaches quickly.
Are there specific NGINX versions more vulnerable to this type of compromise?
NGINX versions themselves aren't specifically vulnerable since the attack uses legitimate functionality, not vulnerabilities. However, older versions might lack security features or might run on systems with known vulnerabilities. Best practice is to run current NGINX versions on fully patched systems. More important than NGINX version is the surrounding security infrastructure: access controls, monitoring, and configuration management.
How does this attack differ from other infrastructure attacks like ransomware or lateral movement campaigns?
Unlike ransomware which encrypts data or lateral movement attacks which jump between systems, this attack is stealthy and focused on data collection. It doesn't destroy or encrypt data, so victims might not realize they've been compromised. It doesn't try to move laterally through the network. It simply sits in place, observing and exfiltrating data. This stealth is both why it's so effective and why traditional security tools designed to detect malware or destructive attacks might miss it entirely.
Summary of Key Takeaways
The NGINX hijacking campaign demonstrates that sophisticated attacks don't require complex exploits. By gaining administrative access to servers and modifying configuration files, attackers can intercept traffic, steal credentials, and monetize the compromise through ad fraud, proxy services, and credential resale. The attack is particularly effective because it leverages legitimate NGINX functionality, preserves user experience, and generates minimal suspicious activity. Organizations running NGINX—whether in cloud or on-premises—must implement configuration management, access controls, file integrity monitoring, and behavioral analytics to detect and prevent this type of attack. The geographic targeting of government and educational institutions suggests well-funded, patient attackers specifically hunting for valuable data sources. Remediation requires immediate configuration audits, behavioral monitoring implementation, and architectural changes toward immutable infrastructure and zero trust security models.
Key Takeaways
- NGINX hijacking doesn't exploit vulnerabilities—it abuses legitimate functionality through modified configuration files injected by attackers with administrative access
- Attackers intercept HTTP traffic, capture session tokens and credentials from headers, and forward legitimate requests to victims' intended destinations—remaining invisible to end users
- Government agencies and educational institutions are primary targets, with significant concentrations in Asia-Pacific, Nordic, and Western European countries
- Stolen traffic generates revenue through ad fraud networks, SEO manipulation services, click fraud schemes, residential proxies, and direct credential sales to other cybercriminals
- Organizations must implement file integrity monitoring, configuration management systems, strict access controls, and behavioral analytics to detect and prevent this attack
- No NGINX security patch exists because the attack uses legitimate features—defense requires architectural changes toward immutable infrastructure and zero trust principles
Related Articles
- Harvard & UPenn Data Breaches: Inside ShinyHunters' Attack [2025]
- OpenClaw AI Assistant Security Threats: How Hackers Exploit Skills to Steal Data [2025]
- Password Security Guide: Why Strong Credentials Matter in 2025
- Notepad++ China Hack: What Happened & How to Protect Yourself [2025]
- OpenClaw AI Security Risks: How Malicious Extensions Threaten Users [2025]
- Infostealer Malware Now Targets Mac as Threats Expand [2025]
![NGINX Server Hijacking: Global Traffic Redirect Campaign [2025]](https://tryrunable.com/blog/nginx-server-hijacking-global-traffic-redirect-campaign-2025/image-1-1770306012609.jpg)



