Notepad++ China Hack: What Happened & How to Protect Yourself [2025]
In mid-2024, one of the world's most popular free text editors became a weapon. Not because the developers wanted it that way, but because attackers with nation-state resources knew exactly where to strike.
Notepad++ has been around since 2003. It's lightweight, powerful, and beloved by developers, system administrators, and coders everywhere who need something better than Windows' built-in Notepad. Millions of people use it daily without thinking twice about security. Why would they? It's open source. It's free. It's been around for two decades.
Then, without warning, Chinese government-linked hackers hijacked the entire update infrastructure.
For six months, from June 2024 through December 2024, the attackers had complete control. They didn't just slip malware into a single release. They selectively targeted specific users, redirecting them to malicious servers where they'd download a custom-built backdoor called Chrysalis. Three organizations experienced "hands on keyboard" incidents, meaning actual humans sitting at keyboards taking direct control of their systems.
This wasn't a data breach. This was something far more sophisticated: a surgical strike disguised as a routine software update.
What makes this attack different from other supply chain compromises you've heard about is the precision. The attackers didn't blanket the world with infected updates. They picked their targets carefully. They weaponized the update process itself. And for six months, almost nobody noticed.
Here's what you need to know, why it matters, and what to do right now.
TL; DR
- The Attack Window: Chinese state-backed hackers compromised Notepad++ update infrastructure from June to December 2024, with attacker credentials persisting until mid-December
- The Weapon: They deployed a custom backdoor called Chrysalis that gave attackers persistent remote access and capability for hands-on keyboard control
- The Victims: At least three organizations with East Asia interests experienced direct control incidents, but the true scope remains unknown
- The Vulnerability: Older versions of Notepad++ had weak update verification, allowing man-in-the-middle attacks at the ISP level
- Your Action: Update to version 8.9.1 or higher immediately, and consider blocking the GUP updater process from internet access on corporate networks


Estimated data suggests tech companies and government contractors are the primary targets, reflecting common patterns in cyber attacks. Estimated data.
How the Attack Actually Happened: The Technical Deep Dive
Understanding this attack requires understanding how Notepad++ updates work. It's not complicated, but the weaknesses are elegant in their simplicity.
Every time you launch Notepad++, a small executable called gup.exe (or Win GUP) checks for updates. It connects to notepad-plus-plus.org/update/get Download Url.php and asks a simple question: "Is there a new version?"
The server responds with a file called gup.xml. This file contains a URL pointing to the actual installer. The client downloads whatever file is at that URL and executes it.
That's the entire process.
Now, here's where it gets dangerous. In older versions of Notepad++, this traffic wasn't encrypted. It was plain HTTP, not HTTPS. Even when it was encrypted, the certificate validation wasn't strict. The code checked that a file was signed, but older versions used a self-signed certificate stored publicly on Git Hub. If you had access to the ISP-level traffic flow, you could intercept the request, modify the URL in the gup.xml response, and redirect users to download whatever you wanted.
The Chinese attackers did exactly this. They compromised the update infrastructure itself, gaining direct control of the servers hosting these critical files. From June 2024 onward, they could intercept update requests and selectively redirect certain targets to malicious servers.
What's crucial to understand is that this wasn't a random, spray-and-pray malware distribution. The attackers had list. They knew who to target. Organizations with interests in East Asia received backdoored updates. Organizations without those interests? They got the legitimate software.
This level of targeting capability requires significant infrastructure and intelligence. It requires knowing which IP addresses belong to your targets. It requires being confident enough in your position that you can be selective. Nation-states have that capability. Cybercriminals typically don't.
The attack used what researchers call an "infrastructure-level compromise." The attackers didn't just modify one update file. They compromised the entire system delivering updates. They maintained persistence through December 2, 2024, using stolen credentials to keep access even after the initial compromise was partially remediated in September.
Think about that timeline. The compromise began in June. In September, the hosting provider discovered something was wrong and began remediation. By September 2, the attackers could no longer directly modify files. But they still had valid credentials. They still had access to internal systems. They could still redirect traffic to malicious servers until December.
That's not an oversight. That's intentional architecture for persistence.
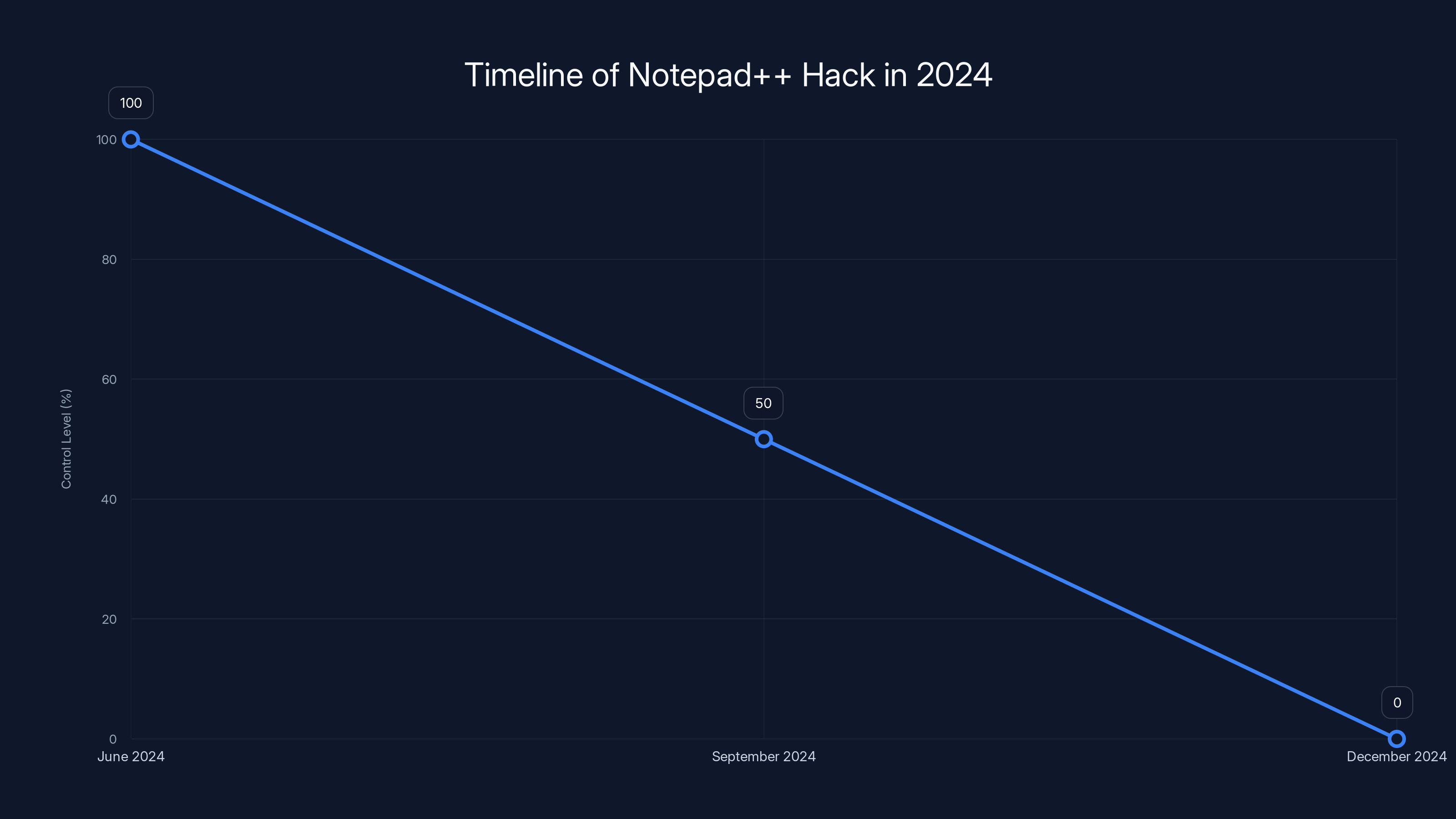
The Notepad++ hack lasted six months, with full control from June to September 2024, and partial control until December 2024.
The Chrysalis Backdoor: What the Attackers Actually Installed
When someone gets infected with a backdoor, they usually don't know it. The malware doesn't announce itself. It doesn't slow down their system. It whispers in the background while the victim works normally.
The Chrysalis backdoor is sophisticated enough to be exactly that kind of threat.
Researchers at Rapid 7, a security firm, described Chrysalis as a "custom, feature-rich backdoor" with "a wide array of capabilities." Translation: the attackers built this specifically for this job. It's not repurposed code. It's not a commercial tool bought from the dark web. This is handcrafted malware engineered for persistence and control.
The backdoor gives attackers several critical capabilities:
Remote Command Execution: Once installed, Chrysalis allows attackers to run arbitrary commands on the infected machine. They're not limited to executing programs that come with Windows. They can download and run anything they want.
File System Access: The backdoor can read, write, and delete files anywhere on the system that the infected user has permission to access. On a developer's machine with admin rights, that's everything.
System Reconnaissance: Chrysalis can gather information about the infected system: installed software, network configuration, user accounts, running processes. This intelligence helps attackers understand what they've compromised and plan next moves.
Persistence Mechanisms: The backdoor includes techniques to survive system reboots and remain active across updates. Once installed, it's not easy to remove without sophisticated forensics.
Lateral Movement Capabilities: This is the scary part. Once a machine is infected, Chrysalis can potentially reach out to other machines on the same network, spreading to other systems without any additional user interaction.
Rapid 7 researchers found indicators showing that the backdoor was "not a simple throwaway utility." This wasn't malware designed to steal one thing and disappear. This was permanent infrastructure. An attacker could install Chrysalis on a target's system in June, do nothing with it for months, and then activate it in September when they wanted to conduct espionage, steal data, or disrupt operations.
The three organizations that experienced "hands on keyboard" incidents are particularly telling. This means human attackers actually logged into systems and navigated around, using Chrysalis as their entry point. They weren't running automated malware. They were conducting active operations. They were looking for specific things: source code, configurations, credentials, intelligence.
All three organizations had interests in East Asia. That's not random. That's targeting based on geopolitical interest.

Who Actually Got Hacked: The Targeting Strategy
One of the most unsettling aspects of this attack is that we still don't know the full scope.
We know three organizations were directly compromised. We know all three had East Asia interests. We don't know if there were four, five, or forty more. We don't know the nature of their interests. Were they tech companies? Government contractors? Journalists? Investors? The authorities haven't disclosed details, and for obvious reasons: those organizations probably want to keep it quiet.
What we can infer is this: the attackers had intelligence about their targets. They knew which IP addresses belonged to interesting organizations. They had enough confidence in their position that they could be surgical about it.
Consider the mechanics. The attackers had to intercept update traffic. They had to modify it in real time. They had to do this selectively, only for certain IP addresses. This requires either:
- Network-level access: Sitting on ISP infrastructure or backbone routers
- DNS compromise: Controlling what notepad-plus-plus.org resolved to for certain users
- BGP hijacking: Announcing routes to certain IP addresses and intercepting their traffic
Each of these requires significant technical capability. You can't do this from your bedroom. You need resources, infrastructure, and the ability to operate without getting caught. Nation-states have this. Most cybercriminal groups don't.
The fact that the attackers maintained credentials even after being partially ejected in September speaks to planning. They didn't expect to keep physical access forever. They knew they'd likely be discovered. So they created backdoor access through stolen credentials. When the primary compromise was detected and partially cleaned up, they still had a way in.
The selectivity of targeting is actually reassuring in one sense. If you're running Notepad++ and you're not a government contractor, major tech company, or organization with East Asia operations, you were probably not the target of Chrysalis installation. You might have received a malicious update hit the initial compromise was detected, but getting the backdoor installed requires hitting the right targets at the right time.
But here's the thing: we'll never know for sure. The Rapid 7 report includes indicators of compromise, but those only help you find obvious infections. A sophisticated backdoor, properly operated, can be nearly invisible. If you're worried, your only real option is to update to a patched version and monitor for suspicious activity.
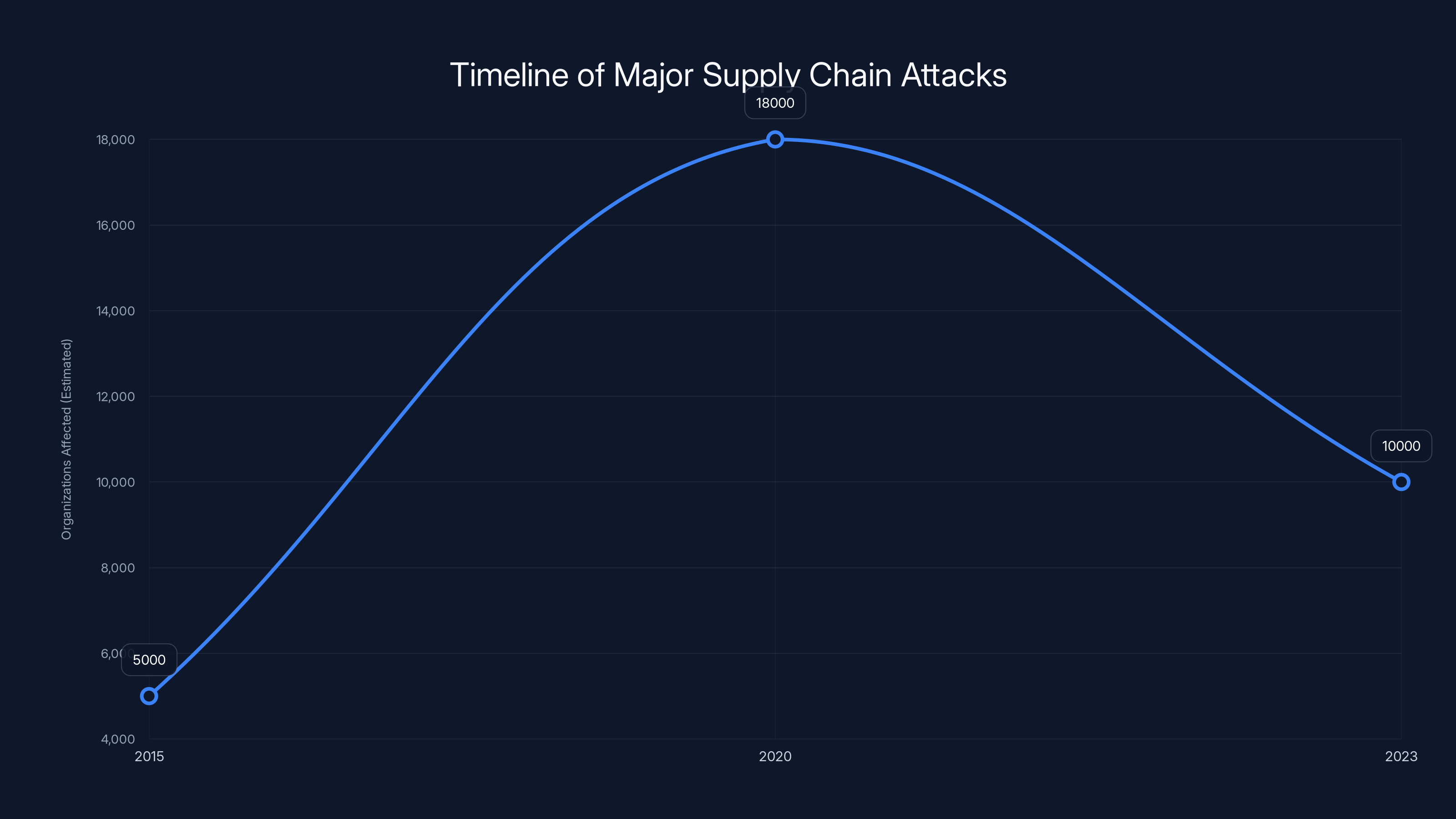
Estimated data shows a significant impact of supply chain attacks over the years, with notable incidents in 2015, 2020, and 2023. The trend highlights the increasing sophistication and reach of such attacks.
The Timeline: How Long This Went Undetected
The attack began in June 2024. That's when attackers first compromised the update infrastructure.
For two months, the attackers had complete control. They could intercept updates. They could modify responses. They could redirect traffic to malicious servers. No one knew.
In early September, someone at the hosting provider noticed something wrong. The indicators aren't entirely clear from public disclosures, but something triggered an investigation. Maybe unusual network traffic. Maybe file integrity checks that failed. Maybe someone noticed modifications they didn't authorize.
On September 2, 2024, the hosting provider took action. They began remediation. They probably revoked some credentials. They probably restored systems from backup. The most obvious attack vectors were closed.
But the attackers had prepared for this. They had created additional accounts with legitimate credentials. Even after the primary compromise was discovered and partially cleaned, they still had access. They could still redirect update traffic. They could still deliver malicious updates.
This persistence lasted until December 2, 2024. Six months total. Four months of undetected control. Two months of partial control after discovery.
On December 2, Notepad++ developers published version 8.8.8, which included significant hardening of the update process. The new version checks digital signatures more strictly. It validates certificate chains properly. It no longer trusts self-signed certificates from Git Hub. Suddenly, the attackers' ability to redirect traffic became much less useful.
But the real notification didn't come until much later. In mid-December, researcher Kevin Beaumont published his analysis suggesting exactly what we now know happened. His theory was based on reverse engineering the changes in version 8.8.8 and talking to organizations that had experienced incidents.
Notepad++ developers remained quiet until the Monday that this story broke publicly. That's when they published their official statement confirming that their update infrastructure had been compromised and that three organizations had experienced incidents.
The delay in public disclosure is understandable but concerning. The attackers had months to operate undetected. Even after partial remediation, they had weeks to continue. The developers were probably investigating, contacting affected organizations, and preparing a response. But during that entire time, millions of users didn't know their update process was compromised.

Infrastructure Weaknesses: Why Notepad++ Was Vulnerable
This attack exposed fundamental weaknesses in how Notepad++ handles updates. Some of these weaknesses are now fixed. Some are inherent to how the update system was designed.
The core issue is that older versions of Notepad++ trusted the network too much. They assumed that if data came from notepad-plus-plus.org, it was legitimate. They didn't verify carefully enough that the data hadn't been modified in transit.
Specifically:
Weak Certificate Validation: The old update process used a self-signed certificate stored on Git Hub. Self-signed certificates offer encryption but not authentication. Anyone with access to that Git Hub repository could generate their own self-signed certificate and use it to intercept traffic. The code didn't verify that the certificate came from a trusted authority.
HTTP Instead of HTTPS: Earlier versions used unencrypted HTTP for parts of the update process. This makes man-in-the-middle attacks trivial. If you can see the traffic, you can modify it.
Insufficient Update Verification: Even when files were signed, the signature verification wasn't strict. The code checked that a signature existed but didn't properly validate the entire chain of trust.
Network-Level Vulnerability: The biggest weakness is that traffic from notepad-plus-plus.org is relatively rare. If an attacker sits on ISP infrastructure with access to BGP or DNS, they can intercept these rare queries. Most ISPs don't check for these kinds of attacks on individual applications. They're looking for bulk traffic manipulation, not surgical targeting of specific software update queries.
Version 8.8.8 addressed the immediate weaknesses. The new code:
- Uses proper HTTPS with certificate pinning
- Verifies signatures against Global Sign (a trusted certificate authority)
- Implements stricter validation of the entire certificate chain
- Checks that the downloaded file matches its signed hash before execution
But even these fixes don't solve the fundamental problem: if an attacker has access to your ISP or backbone routers, they can still intercept and modify HTTPS traffic. They can do this by intercepting the TLS handshake before encryption happens.
This is why Notepad++ developers now recommend that organizations:
Block the GUP.exe Process: Prevent the updater from having internet access on corporate networks. Users can still update manually if needed.
Block notepad-plus-plus.org: Restrict DNS resolution to the Notepad++ website.
Monitor the notepad++.exe Process: Watch for unexpected network connections or unusual activity from the editor itself.
These are good practices, but they're not foolproof. They're acknowledgments that the update process will always be a potential attack vector.
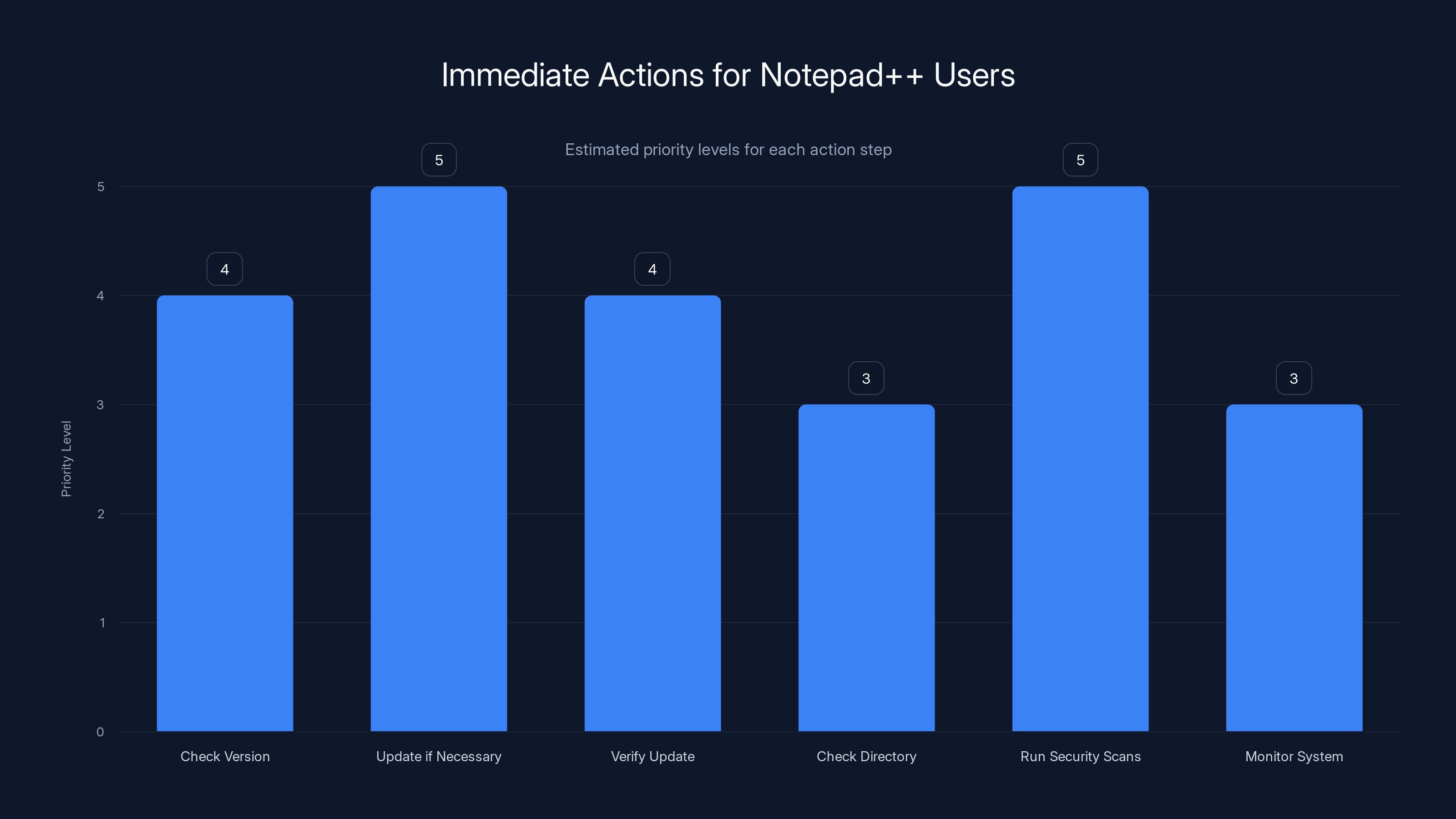
Updating Notepad++ and running security scans are the highest priority actions. Estimated data based on typical security practices.
Rapid 7's Investigation: What Security Researchers Found
Rapid 7 is one of the world's leading security research firms. When they looked at Chrysalis, they found something sophisticated and concerning.
The backdoor includes functionality for:
Process Enumeration: List all running processes and gather information about them File System Exploration: Navigate directories and read file contents Registry Access: Read and modify Windows registry entries (where system configuration is stored) Network Configuration Discovery: Understand the network the machine is connected to User Privilege Escalation: Attempt to gain administrative access if the user isn't already an administrator Lateral Movement: Propagate to other machines on the network C2 Communication: Communicate with attacker-controlled servers using encrypted channels
The malware was written to be stealthy. It doesn't create obvious files. It doesn't spawn visible processes. It integrates with the system quietly and waits for instructions.
This is where it differs from typical malware. Most malware is aggressive. It wants to steal credentials quickly or encrypt files for ransomware. Chrysalis doesn't care about speed. It cares about persistence and control.
The researchers couldn't determine exactly when each organization was infected because the malware's installation left minimal forensic traces. But based on the hardening changes in version 8.8.8, they estimate the vulnerable window lasted from June through early December 2024.
One critical finding: the three organizations that experienced hands-on keyboard incidents all had the malware active and maintained by the attackers for weeks or months. They weren't getting random infected updates. They were specifically targeted and kept infected.
This suggests an operational security posture by the attackers. They weren't running fully automated attacks. They had intelligence analysts determining which machines to target. They had operators actively managing the infection once it was in place.

Kevin Beaumont's December Prediction: How This Was Discovered
Kevin Beaumont is an independent security researcher and consultant. In December 2024, before the official disclosure, he published a detailed technical analysis predicting exactly what had happened.
Beaumont noticed something suspicious about version 8.8.8. The changelog mentioned "hardening the Notepad++ Updater from being hijacked to deliver something... not Notepad++." That's an unusual way to phrase a bug fix. It suggested the developers knew about a specific vulnerability.
He reverse-engineered the changes and realized the update process had been significantly hardened. He studied what weaknesses existed in older versions. And he came to a conclusion: someone had tried to hijack the update infrastructure.
Beaumont then reached out to organizations and security researchers. Three organizations told him they'd experienced "security incidents" resulting in "hands on keyboard threat actors." All three had interests in East Asia.
He published his findings in December with a working hypothesis: Chinese state-backed actors had compromised the update infrastructure and selectively targeted specific organizations.
Two months later, that hypothesis was confirmed.
What's remarkable about Beaumont's analysis is that he did it without inside access. He didn't work with Notepad++ developers. He didn't have forensic data from infected machines. He reverse-engineered the code changes, talked to victims, and assembled the narrative.
His December post probably accelerated the public disclosure. Once a well-known security researcher published the theory, staying quiet became harder. The developers probably decided it was better to confirm what was true rather than let speculation continue.
Beaumont's recommendations were practical:
- Update to the latest version immediately
- Block the GUP.exe process from internet access on corporate networks
- Monitor for any Chrysalis indicators of compromise
- If you're a large organization, consider DNS-level blocking of notepad-plus-plus.org
These recommendations remain valid today.
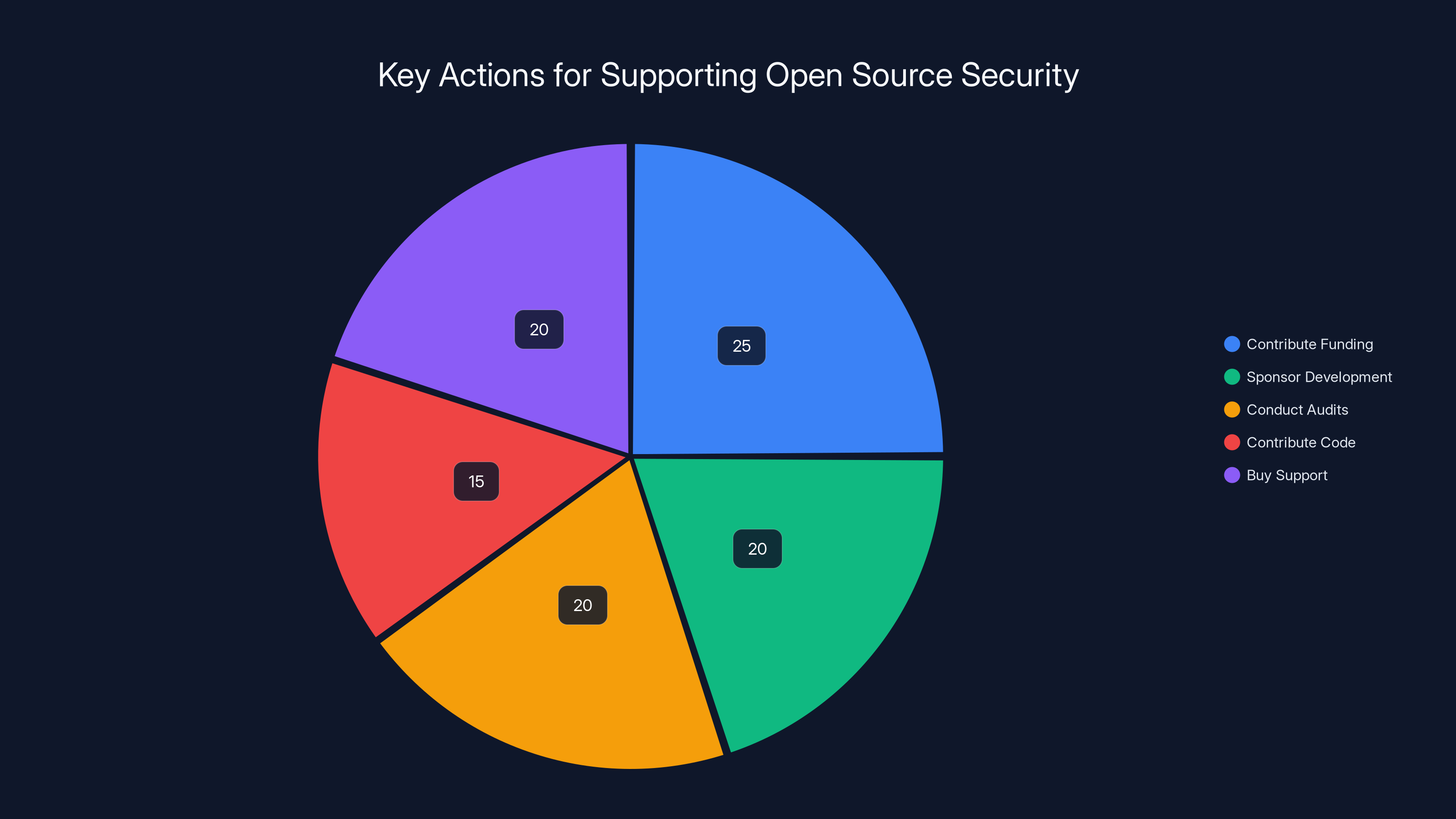
Estimated distribution of efforts needed to enhance security in open source projects. Funding and development sponsorship are crucial, but audits, code contributions, and commercial support also play significant roles.
The Broader Implications: Supply Chain Attacks Are Escalating
This isn't the first time an open source project has been compromised. But it might be the most sophisticated.
We've seen supply chain attacks before. Xcode Ghost in 2015 inserted malware into Apple's development tools. Solarwinds in 2020 compromised network management software used by tens of thousands of organizations. The 3CX software supply chain was compromised in 2023.
But those attacks either affected millions of people indiscriminately or compromised enterprise software that organizations carefully manage.
Notepad++ is different. It's used by individual developers, system administrators, consultants, and contractors. It's often installed outside of corporate IT management. People just download it and use it without thinking about security implications.
Yet it was precisely the kind of target a nation-state would want to compromise. Developers using Notepad++ often have access to source code, configurations, and infrastructure. If you can infect a developer's machine, you can potentially reach the code repositories, systems, and sensitive data they touch.
The attack also highlights the resource crisis in open source. Notepad++ is used by millions but maintained by a handful of volunteers. Upgrading security infrastructure costs money. Maintaining proper cryptographic signing of releases costs money. 24/7 incident response costs money.
Notepad++ gets none of that funding. The developers were probably shocked to discover their infrastructure had been compromised for six months.
This is becoming a pattern. High-impact open source projects are consistently targeted because they're valuable targets but poorly resourced.

Attribution: Why Researchers Believe This Was China
Attribution is hard in cybersecurity. Attackers try to hide their tracks. They use proxies. They steal tools from other groups. They try to make attacks look like someone else did them.
But in this case, multiple independent researchers came to the same conclusion: this was Chinese government-backed.
The reasoning includes:
Capability Requirements: This attack required access to ISP-level infrastructure or BGP hijacking capabilities. Only nation-states consistently have this level of access.
Targeting Pattern: Three organizations with East Asia interests were targeted. That's not random. That's geopolitical targeting.
Operational Security: The attackers maintained a six-month campaign with selective targeting, suggesting planning and resources. They installed a custom-built backdoor rather than repurposing existing malware.
Persistence After Discovery: Even after being partially ejected, the attackers maintained access through September, October, and November. This suggests persistence is more important than quick exploitation.
Custom Tooling: Chrysalis was purpose-built for this attack. It's not a cracked version of some other malware. The attackers had resources to develop custom tools.
Chinese intelligence services are known to conduct supply chain attacks targeting organizations with geopolitical interest. The Shadow Hammer campaign in 2019 compromised ASUS software updates. The Equation Group (believed to be the NSA) has done similar things.
But attribution is never 100% certain. Other nation-states have similar capabilities. It's possible this was Russia, Iran, or another state actor. It's also possible, though unlikely, that this was a sophisticated cybercriminal group with nation-state level resources.
What matters more than attribution is defense. Regardless of who did this, users and organizations need to respond by updating, monitoring, and improving their security posture.
Kevin Beaumont's analysis in December 2024 led to increased awareness and accelerated public disclosure by February 2025. (Estimated data)
What You Should Do Right Now: Immediate Actions
If you use Notepad++, here's your immediate action plan:
1. Check Your Version: Open Notepad++. Go to Help > About Notepad++. Note your version number.
2. Update if Necessary: If you're below version 8.9.1, update immediately. Go to Notepad++ official website and download the latest version directly. Don't wait for the auto-updater.
3. Verify Manual Update: When you download, verify you're getting it from the official website. Check the domain carefully. Look for HTTPS and a valid security certificate.
4. Check Installation Directory: Open your Notepad++ installation directory (usually C:\Program Files\Notepad++ or C:\Program Files (x 86)\Notepad++). Look for any suspicious executable files or DLLs you don't recognize.
5. Run Security Scans: Use your antivirus or malware scanner to scan your system. Rapid 7 published indicators of compromise that security tools can use to identify Chrysalis infections.
6. Monitor Your System: Watch for unusual network connections from your system. Use Windows Event Viewer or a network monitoring tool to check what processes are connecting to the internet.
If You're a System Administrator:
1. Audit Installed Versions: Check all machines in your organization for Notepad++ version numbers. Create a list of machines running older versions.
2. Block GUP.exe: Add GUP.exe to your application whitelisting or block it from having internet access. Users can still update manually if needed.
3. Block notepad-plus-plus.org: Add this domain to your DNS block list. This prevents automatic updates but forces manual updates through your controlled channels.
4. Hunt for Indicators: Check the Rapid 7 report for indicators of compromise. Look for suspicious processes, network connections, or file modifications.
5. Require Manual Updates: Distribute version 8.9.1 through your standard software deployment process rather than relying on the auto-updater.
6. Monitor and Log: Enable process monitoring and network logging. Watch for any suspicious activity on machines that were running Notepad++ during the vulnerable window.
These steps won't guarantee you're safe, but they'll significantly reduce your risk.

Long-Term Hardening: Preventing Future Supply Chain Attacks
This attack exposed weaknesses. The good news is that long-term solutions exist.
Better Signature Verification: Software should always be signed with strong cryptographic keys from trusted certificate authorities. Those keys should be protected with hardware security modules. The code should verify entire certificate chains, not just check that a signature exists.
Update Channel Diversification: Instead of having one update source, projects could use multiple channels. Updates from Git Hub, updates from CDNs, updates from mirrors. Attackers would need to compromise multiple channels simultaneously.
Reproducible Builds: Developers should be able to verify that binary releases were built from specific source code. This prevents attackers from injecting malware while the source code remains clean.
Security Investment: Open source projects need funding for security. Bug bounties, security audits, incident response planning. Notepad++ gets virtually none of this.
User Education: Developers need to understand that software updates are attack vectors. Don't assume updates are always safe. Verify sources. Monitor for unusual behavior.
Network Segmentation: Organizations should isolate development machines from production networks. If a development machine gets compromised, damage is limited.
Zero Trust Architecture: Don't trust any component until it's verified. Verify signatures. Verify sources. Verify behavior. Assume compromise and operate accordingly.
None of these are silver bullets. The most important thing is treating software supply chain security as a real problem that needs resources and attention.
The Open Source Crisis: Why This Keeps Happening
Notepad++ is maintained by volunteers. They receive no meaningful funding. They're supposed to maintain security infrastructure, conduct incident response, and operate as a professional software company, all for free.
This is the open source crisis in a nutshell.
Millions of people depend on open source software. Organizations build companies on top of it. Internet infrastructure relies on it. But the people maintaining it are often working nights and weekends without compensation.
When something goes wrong, we blame the developers. We demand they do better. We expect professional security practices from volunteers.
But security infrastructure costs money. Proper code review costs time. Incident response means being available 24/7. This isn't sustainable for unfunded projects.
Solarwinds spent millions on security after 2020 and was compromised anyway. Notepad++ has a fraction of that budget and is somehow expected to maintain similar security standards.
This isn't fair, and it's not sustainable.
The solution requires action from organizations that benefit from open source:
- Contribute Funding: If your organization uses open source, contribute to security improvements
- Sponsor Development: Pay developers to work on security upgrades
- Conduct Audits: Hire security firms to audit projects you depend on
- Contribute Code: If you have security expertise, contribute patches
- Buy Support: Some projects offer commercial support. Use it.
Notepad++ developers didn't want this to happen. They probably didn't know how vulnerable their infrastructure was. They probably didn't have bandwidth to audit it regularly. Now they're dealing with the fallout from a nation-state attack.
This will happen again to other projects unless something changes.

Detection and Forensics: How to Know If You Were Compromised
If you were infected during the vulnerable window, how would you know?
Chrysalis was designed to be stealthy. It doesn't create obvious files or processes. It doesn't announce itself. It just sits quietly and waits for commands from the attacker.
But sophisticated malware always leaves traces. Finding them requires careful forensic analysis.
File System Indicators: Chrysalis creates files with specific names and locations. Rapid 7 published a list of indicators. Security tools can scan for these files. But if the malware was properly maintained, these files might not exist. Attackers might command it to delete forensic traces if they think they've been discovered.
Registry Entries: The malware modifies Windows registry to establish persistence. Forensic tools can examine registry hives to look for suspicious entries. But again, if attackers discovered they were compromised, they might have cleaned this up.
Network Connections: If Chrysalis was actively running, it would communicate with command and control servers. Network monitoring tools can log these connections. But Chrysalis might not have been actively running. It might have been dormant, waiting for activation.
Process Analysis: If the malware was running, analyzing running processes might reveal it. But most versions of Chrysalis hide themselves from obvious process listing.
Behavioral Analysis: If you run suspicious executables through a sandbox, you can watch their behavior. But most users don't have access to sophisticated sandboxing.
For most people and organizations, the practical reality is this: if you were compromised with Chrysalis and the attackers were careful, you probably won't know through direct detection. You'll know if:
- Authorities Contact You: Organizations that were targeted have probably already been contacted by law enforcement or intelligence agencies
- You Notice Security Breaches: If the attackers used your machine to steal data or breach other systems, you'll eventually detect the impact
- Passive Indicators: You notice unusual network traffic, system slowdowns, or other behavioral changes
This is why prevention through updating is so important. You can't detect sophisticated malware reliably, but you can prevent infection by staying current.
Looking Forward: The Future of Supply Chain Security
This attack changes the threat landscape. Developers, organizations, and security professionals are rethinking how software updates work.
In the short term, expect:
Increased Scrutiny of Update Mechanisms: Every popular open source project is now reviewing its update infrastructure. Weaknesses will be patched across the ecosystem.
Adoption of Better Signing Practices: More projects will implement strong cryptographic signing with hardware-backed keys.
Organizational Changes: Organizations will implement stricter controls on automated updates. More manual review. More staged rollouts.
Security Tool Evolution: Antivirus and monitoring tools will adapt to detect supply chain attacks more effectively.
In the longer term, the conversation needs to shift. The open source community, organizations that benefit from open source, and governments need to discuss how to properly fund security in open source.
This is a national security issue. Strategic infrastructure depends on open source software. If state actors can easily compromise it, that's a systemic vulnerability.
Some government agencies are starting to fund open source security. The NSF awarded $5 million to improve security in critical open source projects. The EU is investing in open source security through Open SSF.
But this is still far below what's needed.
Expect to see:
- Mandatory Security Audits: Large organizations will require security audits before adopting open source
- Supply Chain Frameworks: Industry standards will evolve for securing software supply chains
- Increased Funding: More organizations will invest in open source security
- Policy Changes: Governments might regulate supply chain security
The Notepad++ attack will be a reference point for these discussions. It will be cited as evidence that the current approach is insufficient.
Lessons for Developers: Building Secure Update Systems
If you maintain an open source project, here are the lessons from this attack:
1. Strong Cryptography: Use industry-standard encryption and signing. Don't invent your own. Don't use self-signed certificates from public repositories.
2. Hardware-Backed Keys: Store your signing keys in hardware security modules. Don't keep them on servers that can be hacked.
3. Multiple Verification: Verify signatures at multiple points. Verify the source. Verify the destination. Verify the chain of custody.
4. Minimize Update Surface: Don't make updates automatic if possible. Give users the option to review updates before applying them.
5. Monitor Infrastructure: Watch your update infrastructure for suspicious activity. Set up alerts for unusual traffic patterns or modifications.
6. Plan for Compromise: Assume you will be compromised eventually. Plan for how you'll respond. Have backups. Have ways to revoke compromised keys. Have communication plans.
7. Communicate Early: If you discover a compromise, communicate with users immediately. Don't wait for perfect information. Give people what they need to protect themselves.
8. Security By Default: Newer versions should have security improvements that make older compromise techniques ineffective.
Notepad++ was vulnerable because its security infrastructure wasn't prioritized. This is common in open source. Security is considered a feature, not a foundation.
If you maintain a project that people depend on, treating security as foundational isn't optional. It's essential.
Real-World Impact: What This Attack Means in Practice
For most users, the impact is indirect. If you updated to version 8.9.1 or higher, you were never at serious risk. The attack was selective. It targeted specific organizations.
But for those specific organizations, the impact could be significant.
Imagine you're a developer at a tech company with East Asia operations. You download Notepad++ in June 2024. You use it for code reviews, configuration edits, and other development work. Unbeknownst to you, a backdoor is installed.
For six months, attackers have access to your system. They can see every file you touch. They can read your source code. They can capture your keystrokes. They can see credentials you use. They can see communications you have over your terminal.
If you're working on proprietary algorithms, security systems, or strategic technology, that's months of intellectual property theft.
Now imagine that company's CISO discovering this six months later. They don't know how much was stolen. They don't know what attackers accessed. They have to assume the worst and implement damage control.
They have to revoke credentials. They have to audit code repositories. They have to check if source code was accessed. They have to notify vendors who might have received leaked information. They have to check if attackers used the access to breach other systems.
The investigation might take months. The damage might be extensive. The costs could run into millions.
This is why supply chain attacks are so dangerous. They're not one-off data breaches. They're persistent access that can be exploited over time for maximum damage.

Comparative Risk Assessment: How Serious Is This?
On a scale of cybersecurity incidents, where does this rank?
Compared to Solar Winds: Notepad++ has more users, but Solar Winds directly targeted critical infrastructure. Solar Winds was more serious.
Compared to Log 4 Shell: Log 4 Shell was more widespread and easier to exploit. But the Notepad++ attack was more sophisticated in terms of targeting and persistence.
Compared to Xcode Ghost: Both targeted developers specifically. Notepad++ was more selective in targeting.
In terms of sophistication, this ranks high. The attackers demonstrated:
- ISP-level access or BGP hijacking capability
- Custom malware development
- Selective targeting based on intelligence
- Persistence planning
- Operational security
In terms of impact, it's more limited than some other attacks because it was selective. But for targeted organizations, it could be severe.
The key takeaway is this: if you were targeted, this was very serious. If you weren't targeted, the risk was minimal. But determining whether you were targeted is difficult.
FAQ
What exactly is Notepad++ and why do people use it?
Notepad++ is a free, open source text editor for Windows that's been around since 2003. It's beloved by developers, system administrators, and programmers because it offers advanced features that Windows' built-in Notepad doesn't have, including syntax highlighting for multiple programming languages, tabbed editing, powerful find-and-replace functionality, plugins, and a lightweight interface that doesn't require much system resources. It has millions of active users worldwide and is one of the most popular development tools available.
When exactly did the Notepad++ hack happen and how long did it last?
The attack began in June 2024 when Chinese state-backed hackers compromised Notepad++'s update infrastructure. The attackers maintained full control until September 2, 2024, when the hosting provider discovered the compromise and began remediation. However, the attackers had created backup access methods, allowing them to continue redirecting update traffic to malicious servers until December 2, 2024. In total, the attack lasted six months, with four months of completely undetected control and two months of partial control after discovery. Notepad++ didn't publicly disclose the incident until the story broke in the media in 2025.
How did the attackers actually hijack the update infrastructure?
The attackers exploited weaknesses in how Notepad++ delivered updates. When users launched Notepad++, it would check for updates by connecting to a server, downloading a file (gup.xml) that contained a URL to the actual installer, and then downloading and executing that installer. The attackers either gained access to the ISP infrastructure carrying this traffic or used DNS/BGP hijacking to intercept these update requests. Once intercepted, they could modify the URL in the gup.xml file to point to their own malicious servers instead of the legitimate ones. Older versions of Notepad++ had weak cryptographic verification, making this possible. The attackers then selectively redirected certain targeted IP addresses to malicious servers while allowing others to receive legitimate updates.
What is Chrysalis and what can it do?
Chrysalis is a custom-built backdoor malware that researchers at Rapid 7 described as "feature-rich" and "sophisticated." Once installed on a system, it gives attackers the ability to run arbitrary commands, access files anywhere on the system, gather system information, maintain persistence across reboots, and potentially spread to other machines on the same network. The backdoor communicates with attacker-controlled command and control servers using encrypted channels, and it's designed to be stealthy, leaving minimal forensic traces. Three organizations that were targeted experienced "hands on keyboard" incidents, meaning human attackers used the backdoor access to directly control their systems, likely conducting espionage and data theft.
How can I tell if my system was compromised?
Determining if your system was infected is extremely difficult because Chrysalis was designed to be stealthy. However, you can take several steps: check your Notepad++ version (Help > About) and make sure you're on 8.9.1 or higher, run a malware scan using your antivirus software to check for known Chrysalis indicators, examine your Notepad++ installation directory for suspicious files or executables, monitor your system for unusual network traffic or unexpected slowdowns, and review Windows Event Viewer for suspicious process activity. If your organization was targeted during the vulnerable window, law enforcement or intelligence agencies would likely have already contacted you. For most individual users, the best protection is updating to the latest version immediately.
What should I do if I was running Notepad++ during the vulnerable period?
First, update immediately to version 8.9.1 or higher by downloading directly from Notepad++ official website. Don't rely on the auto-updater during this transition. Next, run a full system malware scan using your antivirus or anti-malware software. Check your installation directory (usually C:\Program Files\Notepad++) for any suspicious files. Review Windows Event Viewer for any unusual process activity or network connections. If you work at an organization with sensitive data, inform your security team immediately. If you handle classified information or work in government, treat this as a serious security incident. For most individual users, updating to the latest version significantly reduces your risk, especially if you weren't a specific target.
Who was responsible for this attack and why?
Multiple security researchers attributed the attack to Chinese state-backed actors based on several factors: the attack required nation-state level technical capabilities like ISP-level access or BGP hijacking, the selective targeting focused on three organizations with East Asia interests suggesting geopolitical motivation, the custom-built Chrysalis backdoor indicated significant resources and planning, and the operational security practices (maintaining persistence, selective targeting, using stolen credentials) align with known Chinese intelligence operations. However, final attribution is never 100% certain in cybersecurity. What matters more is defending against the attack regardless of the specific attribution.
What does this attack reveal about open source security?
This attack highlights the critical crisis in open source security: millions of people depend on open source software maintained by underfunded volunteers. Notepad++ is used by millions globally but maintained by fewer than 10 core developers working largely without compensation. These developers can't afford enterprise-grade security infrastructure, 24/7 incident response, or regular security audits. The project was vulnerable not because the developers were incompetent, but because security requires resources they don't have. This is a systemic problem affecting the entire open source ecosystem. Many critical projects that internet infrastructure depends on are chronically underfunded and undertrained in security practices.
What changes did Notepad++ make to prevent future attacks?
Version 8.8.8 and later versions included significant security hardening: proper HTTPS with certificate pinning (trusting only specific certificates, not just any from a trusted authority), stricter certificate chain validation, verification that downloaded files match their signed hashes before execution, and better signature verification against Global Sign (a trusted certificate authority) instead of self-signed certificates. These changes make it much harder for attackers to intercept and modify update traffic. However, complete protection against nation-state level attackers requires additional organizational controls like network segmentation, process monitoring, and in some cases, blocking the GUP.exe updater from internet access entirely.

Conclusion: Why This Attack Matters Beyond Notepad++
The Notepad++ attack isn't just a story about one text editor getting hacked. It's a warning about how we've built the internet.
We've created a system where millions of people depend on software maintained by volunteers with no budget. We've accepted that open source security is underfunded and undertrained. We've assumed that because code is transparent, it must be secure.
None of that is true.
Transparency helps, but it doesn't replace resources. Code review helps, but not when reviewers are volunteers working in their spare time. Open source is incredible and has driven innovation that commercial companies never could have achieved. But the security model is broken.
The Notepad++ attack was successful not because the developers were incompetent, but because they were under-resourced. A professional software company with dedicated security staff would have caught this compromise faster. But Notepad++ gets a fraction of the funding that commercial software gets.
Now the developers are dealing with the aftermath of a nation-state attack. They're probably fielding calls from organizations that were compromised. They're implementing security improvements. They're probably questioning whether they should continue maintaining the project.
And millions of users are updating their software, wondering if they were targeted.
The solutions are clear but require action:
Organizations must fund open source security. If you use open source software in production, you have a responsibility to support its security. This means contributing code, funding security improvements, sponsoring development, or paying for professional support.
Individuals must take supply chain security seriously. You can't assume software updates are always safe. Verify sources. Keep systems updated. Monitor for unusual activity. Assume compromise and operate accordingly.
Policymakers must recognize this as critical infrastructure. If software supply chains are national security issues (and they are), then governments need to invest in securing them. This means funding open source projects, requiring security standards, and building capabilities to detect and prevent supply chain attacks.
Developers must prioritize security from the beginning. If you maintain software that others depend on, security isn't optional. It's foundational. This means strong cryptography, secure infrastructure, incident response planning, and regular audits.
The Notepad++ attack is a window into how vulnerable our software supply chain really is. It's a reminder that the attackers are sophisticated, well-resourced, and patient. They'll compromise infrastructure and wait months for the right moment to strike.
The only defense is taking this seriously. Updating. Monitoring. Funding. Building security into the foundation.
The next supply chain attack is already in progress. Someone's update infrastructure is probably already compromised. Someone's developers are probably already being targeted. The question isn't whether this will happen again. The question is whether we'll finally invest in preventing it.
Notepad++ gave us a clear warning. Let's hope we listen.
Key Takeaways
- Chinese state-backed attackers compromised Notepad++ update infrastructure for 6 months (June-December 2024), selectively targeting organizations with East Asia interests
- Chrysalis custom-built backdoor provides attackers with remote command execution, file access, persistence mechanisms, and lateral movement capabilities
- Vulnerable to compromise were Notepad++ versions below 8.9.1, which lacked proper certificate validation and used weak cryptographic verification
- Version 8.8.8 introduced security hardening with certificate pinning, HTTPS enforcement, and stricter signature validation to prevent future MITM attacks
- The broader supply chain security crisis reflects underfunded open source projects with insufficient resources for enterprise-grade security infrastructure and incident response
- Users should immediately update to 8.9.1+, verify installation integrity, and organizations should block GUP.exe from internet access and monitor for Chrysalis indicators
Related Articles
- Notepad++ Supply Chain Attack: Chinese Hackers Hijack Updates [2025]
- Notepad++ Supply Chain Attack: What You Need to Know [2025]
- Notepad++ Server Hijacking: Inside the Six-Month Supply Chain Attack [2025]
- Software Integrity vs Data Sovereignty: Why Code Matters More [2025]
- Notepad++ Supply Chain Attack: Chinese State Hackers Explained [2025]
- Nord Security's 400 Patents: The Future of Cybersecurity [2025]
![Notepad++ China Hack: What Happened & How to Protect Yourself [2025]](https://tryrunable.com/blog/notepad-china-hack-what-happened-how-to-protect-yourself-202/image-1-1770235653229.jpg)



