The Day Your Code Editor Became a Weapon
Imagine opening a seemingly routine software update on your laptop, clicking install, and not realizing that your keystroke logging was already starting. That's what happened to thousands of Notepad++ users between June and December 2025. One of the world's most popular code editors got turned into a vector for state-sponsored espionage, and most people had no idea.
This wasn't a zero-day exploit buried in the code. It wasn't a vulnerability in Notepad++ itself. Instead, the attack targeted the infrastructure everyone assumes works flawlessly: the update mechanism. For six solid months, the developers who downloaded what they thought were legitimate security patches were actually downloading remote access trojans, keyloggers, and surveillance tools.
The scariest part? We almost never found out. The breach only came to light in December 2025 when independent security researchers started connecting the dots. Don Ho, Notepad++'s creator, eventually published a detailed post acknowledging the compromise, but by then the damage was already done.
This wasn't amateur hour. The execution was surgical. The targeting was deliberate. And the implications stretch far beyond one text editor. This was a masterclass in supply chain attacks, and it revealed something security teams had been warning about for years: your biggest vulnerability isn't the software you use. It's the way that software gets delivered to your computer.
TL; DR
- The Breach: Notepad++ update servers were hijacked for six months (June–December 2025), distributing malicious executables to users.
- The Attackers: Intelligence agencies working for the Chinese government, according to independent cybersecurity analysts.
- The Victims: Organizations with interests in East Asia, not random users, suggesting highly targeted intelligence gathering.
- The Impact: Victims potentially had keyboard access harvested, network activity monitored, and files exfiltrated.
- What You Can Do: Update to version 8.8.9 immediately, verify gup.exe behavior, and check for suspicious update files in your TEMP folder.
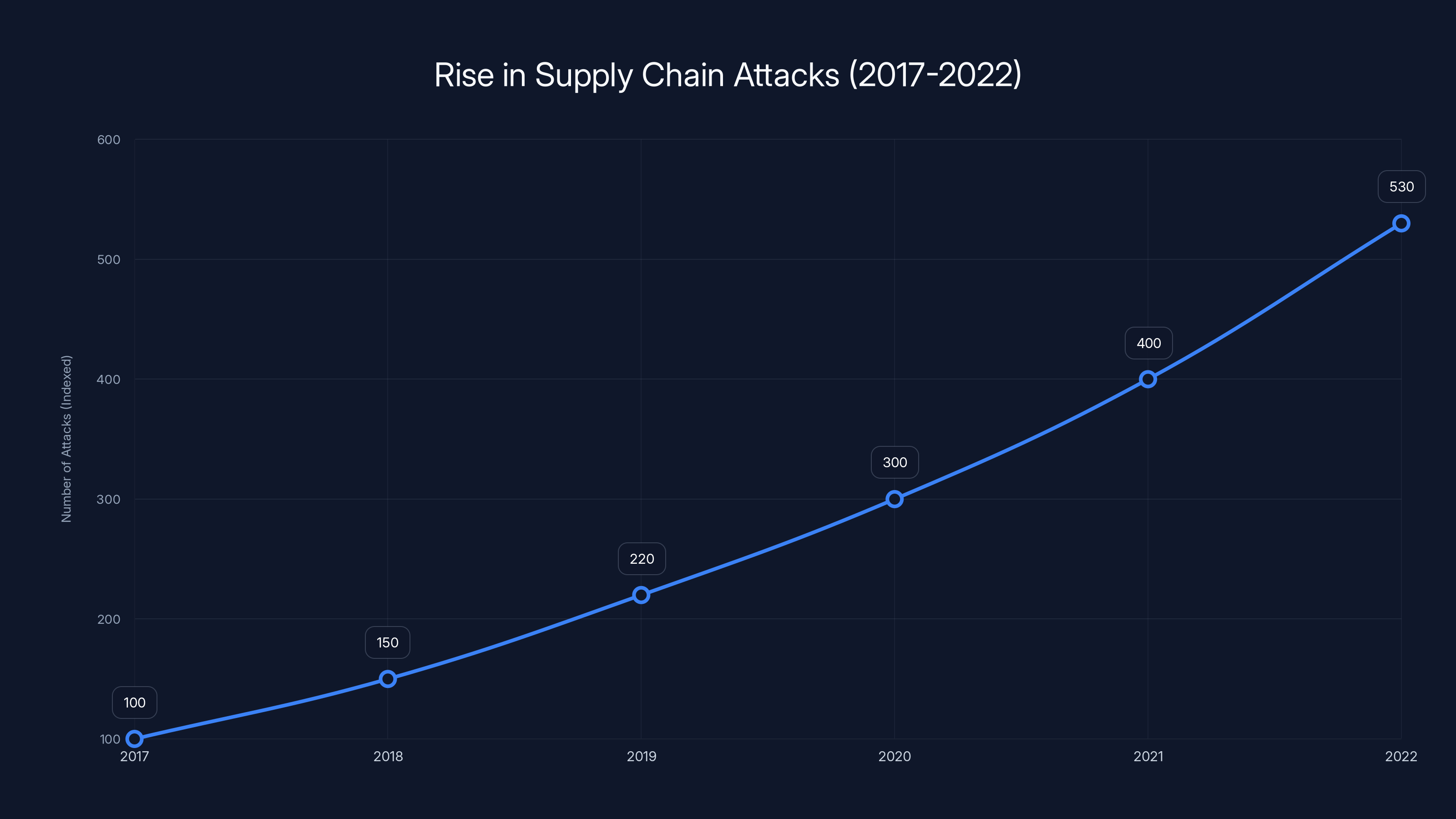
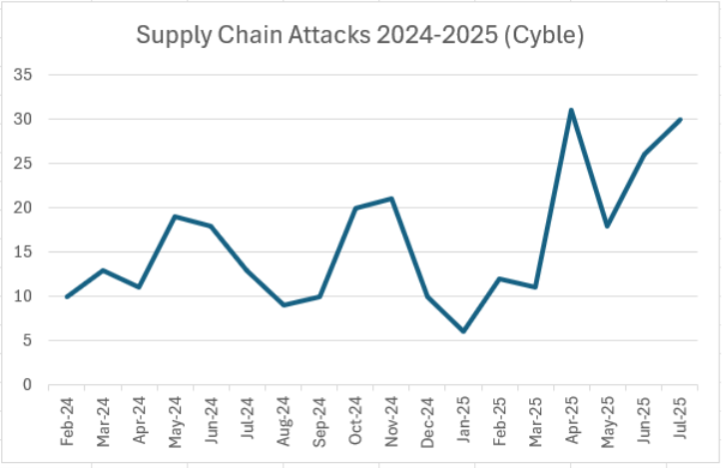
Supply chain attacks have surged by over 430% from 2017 to 2022, highlighting the growing vulnerability in software distribution channels. (Estimated data)
What Happened: The Timeline of a Supply Chain Massacre
The attack chain started with something most people don't think about: where does your software come from? Notepad++ relied on shared hosting infrastructure managed by a third-party provider. This was the weak link.
In June 2025, threat actors gained unauthorized access to Notepad++'s hosting servers. Don Ho's post didn't provide exhaustive technical details about how the breach occurred, but the result was clear: they could intercept traffic to the update servers.
Here's the genius of the attack structure: they didn't take down the servers. They didn't delete files. They didn't announce their presence. Instead, they set up traffic redirection rules that would selectively route specific users to attacker-controlled servers serving malicious update manifests.
When a Notepad++ user in a targeted organization checked for updates, their request got intercepted and redirected to a fake update server controlled by the attackers. The user would see what looked like a legitimate Notepad++ update package. The version numbers matched. The signatures seemed correct. The binary executed just like Notepad++ normally does.
Except it also did something else. According to Kevin Beaumont, an independent cybersecurity analyst who investigated the attacks, the malicious executable gave attackers remote access and keyboard logging capabilities. Translation: they could see everything a victim typed. Code, passwords, sensitive emails, API keys, all of it.
The targeting wasn't random. The attackers used geolocation data, IP reputation, and probably other signals to determine which update requests came from victims they wanted to surveil. Beaumont noted that the victims he spoke with were "organizations with interests in East Asia," which strongly suggested the attacks were part of a state-sponsored intelligence operation.
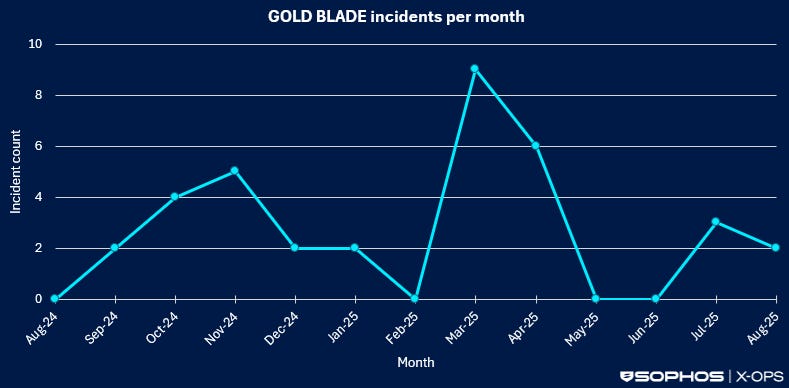
The attack continued from June through December 2nd, 2025. For six months, the malicious update remained available. The exact number of infected machines is unclear—Don Ho's post didn't specify—but security researchers estimate that at least hundreds of users were compromised.
What finally stopped the attack? According to Don Ho's post, the hosting provider (whose name Notepad++ still hasn't publicly disclosed) eventually detected the unauthorized access and took corrective action. By December 2nd, all attacker access was terminated. The malicious update servers were taken offline. The hosting infrastructure was cleaned.
But the damage was already done. By the time Notepad++ released version 8.8.9 with stronger cryptographic verification for updates, the attackers had already exfiltrated whatever data they wanted from their targets.
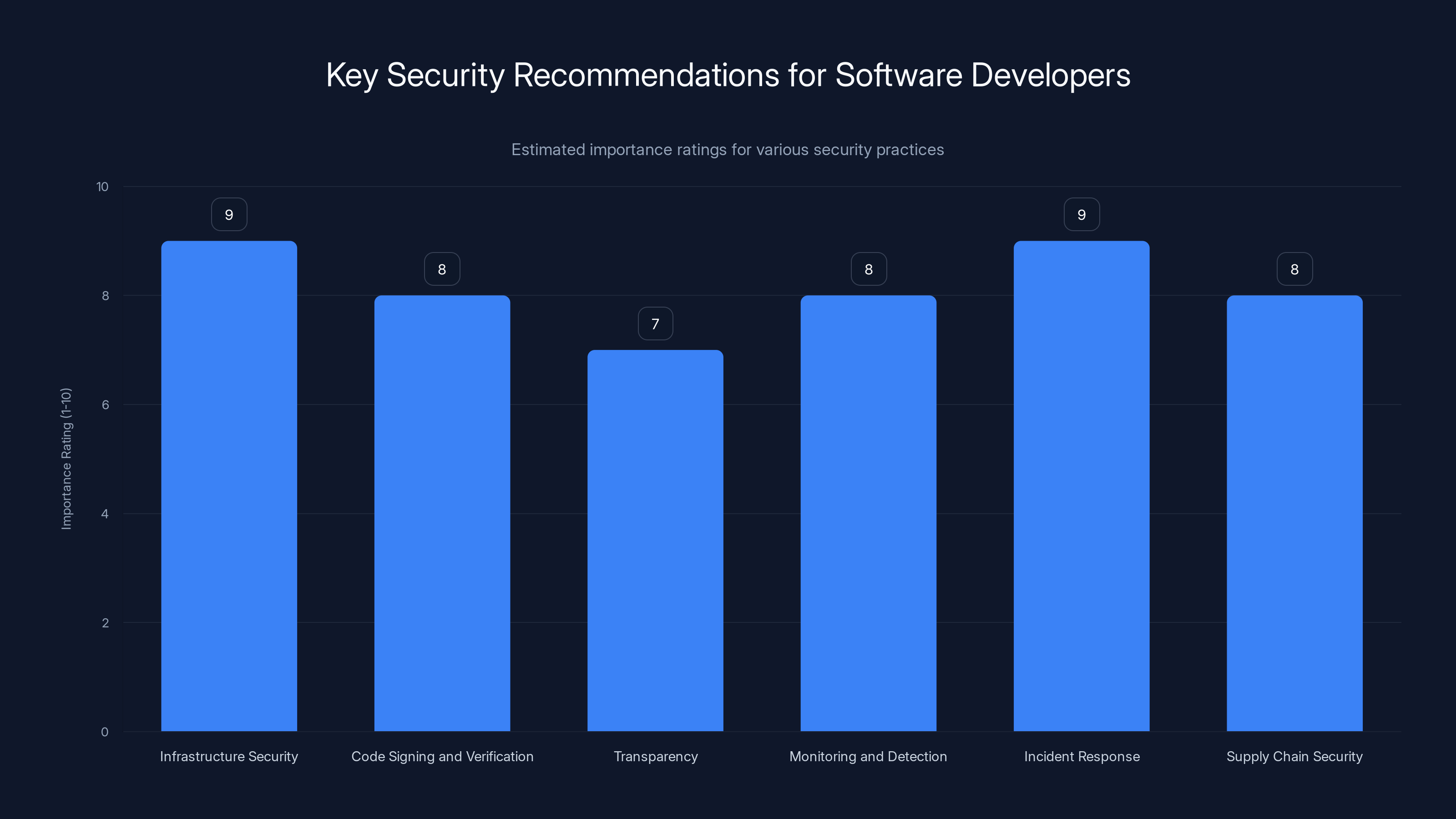
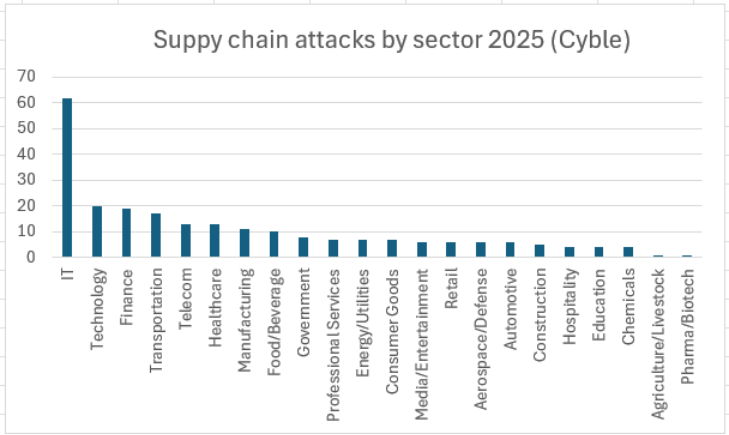
Infrastructure security and incident response are rated highest in importance for protecting against attacks like the Notepad++ incident. Estimated data.
The Attacker Profile: Why China?
Don Ho's post stated the attackers were "likely a Chinese state-sponsored group." That wasn't a guess. Cybersecurity analysts like Beaumont had specific reasons for that attribution.
First, the targeting pattern. The victims weren't random. They were organizations with East Asian operations, expertise, or interests. This isn't the behavior of a cybercriminal trying to harvest credit card numbers. This is the behavior of an intelligence agency interested in corporate espionage, geopolitical intelligence, or strategic advantage.
Second, the capability level. Setting up persistent access to a major software distribution system, maintaining it for six months without detection, and executing surgical targeting of specific IP ranges requires serious resources. That's government-level capability.
Third, and this is important: Don Ho has history with the Chinese government. In 2019, he released a "Free Uyghur" edition of Notepad++, explicitly criticizing Beijing's policies. His website was subsequently hit with DDo S attacks. The 2025 supply chain attack against his own software could be retaliation. Or it could be a way to target organizations that might use Notepad++ while also discrediting the tool itself.
The sophistication of the attack also points toward state sponsorship. The attackers didn't just slap malware on the servers. They integrated it carefully into the legitimate update process. They used selective traffic redirection to avoid catching completely random users. They maintained operational security well enough that the breach wasn't detected for six months. That level of finesse takes time, money, and expertise that only well-funded organizations can afford.
Independent analysis also noted that the malicious executable was specifically designed for keyboard logging and remote access, not for widespread data theft or ransomware deployment. That's consistent with targeted intelligence operations, not commodity cybercrime.
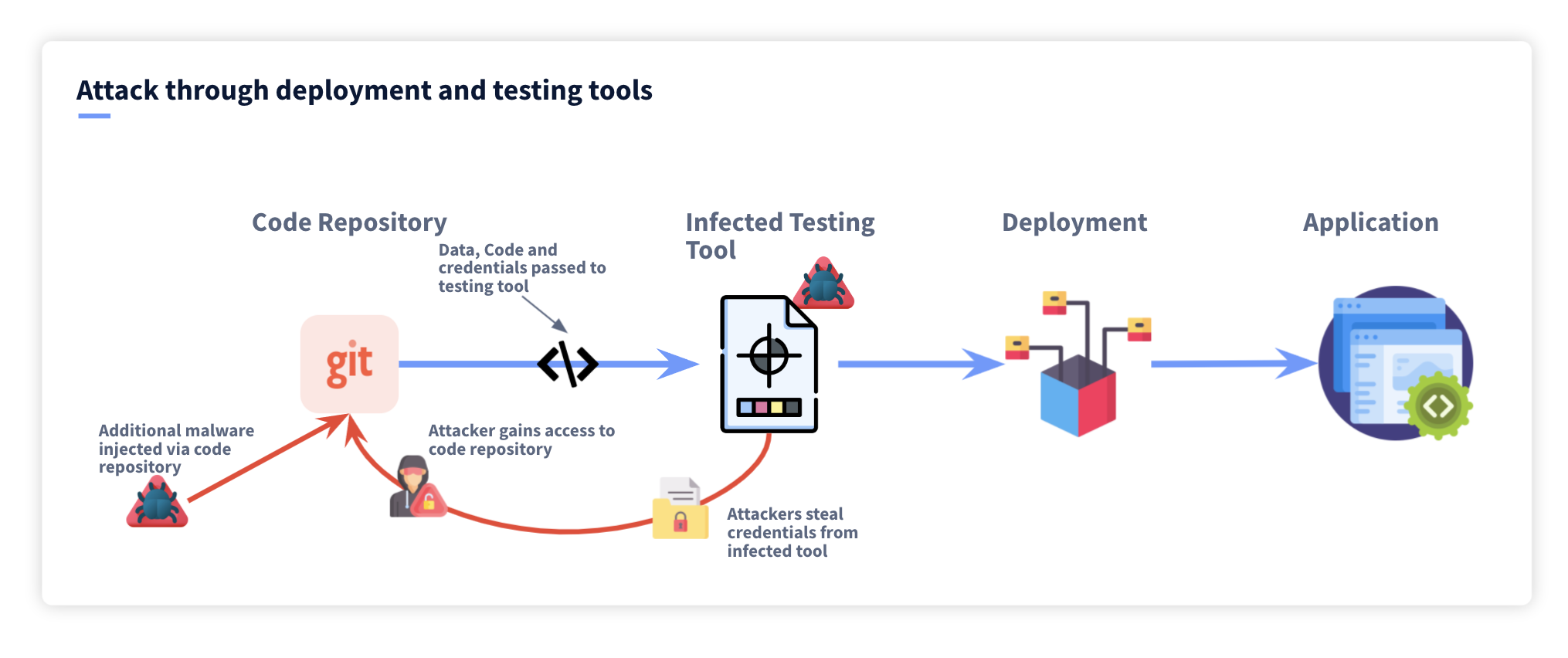
How It Worked: The Technical Anatomy of the Attack
Understanding how this attack actually functioned matters, because it reveals how vulnerable update mechanisms really are.
Notepad++ uses an updater application called gup.exe to check for and install new versions. When a user launches Notepad++ and the updater runs, gup.exe connects to Notepad++'s update servers, checks if a new version is available, and if so, downloads the update manifest.
The manifest contains metadata about the available update: version number, file hashes, URLs where the actual executable can be downloaded, and cryptographic signatures proving the manifest came from Notepad++.
In a normal scenario, the manifest is cryptographically signed. The gup.exe application verifies that signature before trusting the manifest. This should prevent exactly this type of attack.
But here's where it gets interesting: the hosting provider's servers were compromised, not Notepad++'s development infrastructure. The attackers had full control over what got served from those servers. If the update verification system relied on checking a signature that was embedded in the compromised manifest itself, the attackers could serve a malicious manifest with a signature the gup.exe application would accept.
Moreover, if the update mechanism didn't use TLS certificate pinning or other advanced security measures, the attackers could potentially perform man-in-the-middle attacks, intercepting update requests and serving malicious responses without the application ever noticing.
The selective targeting makes sense from an operational security perspective. If the attackers tried to compromise every Notepad++ update, it would only take days before someone noticed. Antivirus companies would see the malicious executable. Detection would be inevitable. Instead, by targeting only specific users based on geolocation and IP reputation, they kept the attack quiet enough to run for six months.
The attacker's malicious executable probably functioned almost identically to legitimate Notepad++. It installed correctly, opened without errors, and ran normally. Except in the background, it was harvesting keystrokes, establishing remote access, and exfiltrating data.
Victims would have no idea. The performance would be normal. The program would crash occasionally just like real Notepad++ might. From the user's perspective, everything looked fine.
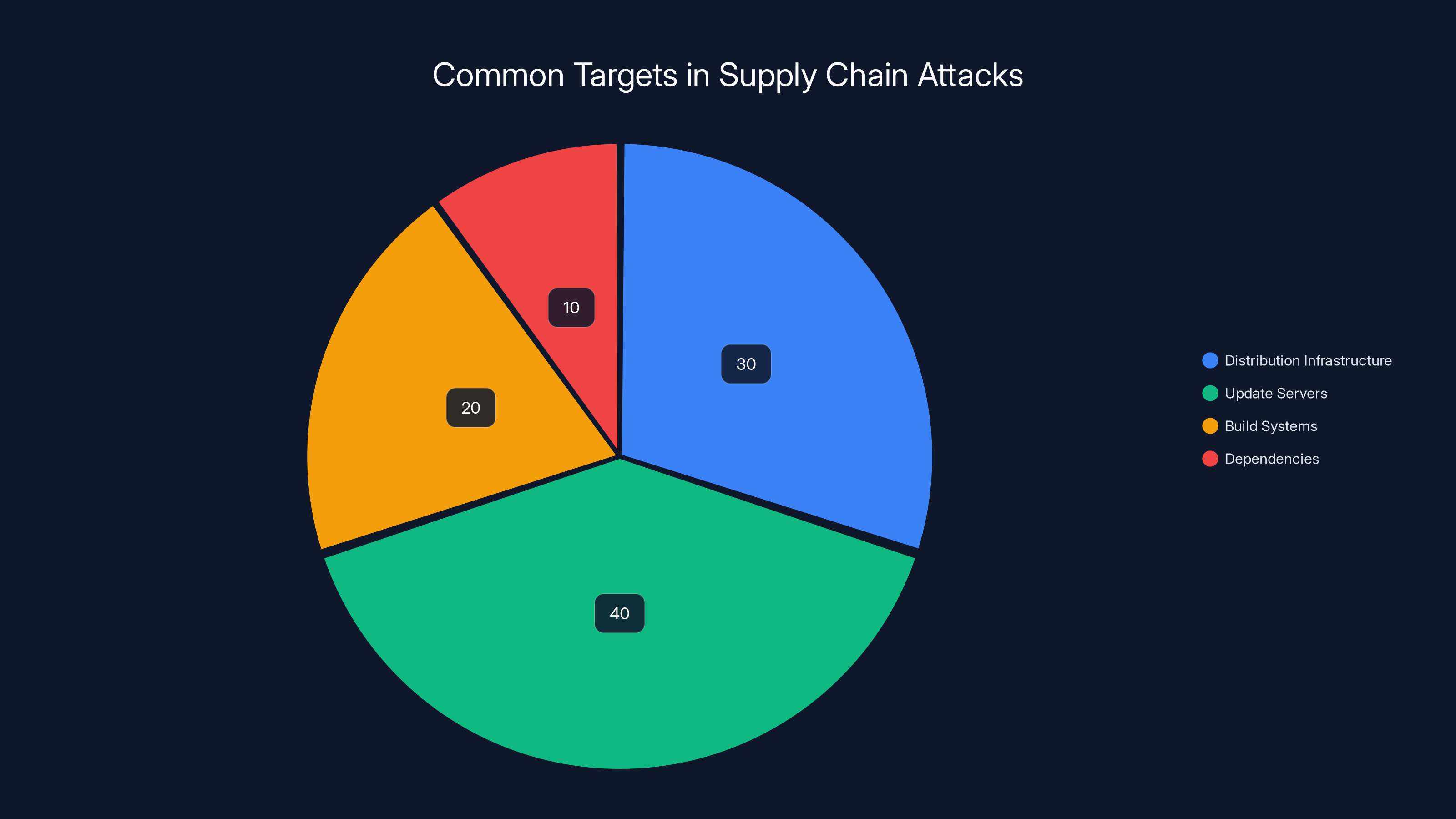
Estimated data shows that update servers are the most targeted in supply chain attacks, followed by distribution infrastructure. Estimated data.
The Damage Assessment: What Actually Happened to Victims
This is where the technical attack translates to real-world consequences.
According to Beaumont's analysis, victims' machines received a malicious executable that functioned as both a remote access trojan and a keylogger. If you're a developer at an organization with East Asian operations, and you installed that update, the attackers could now see everything you typed.
Password managers don't help if someone's monitoring your keystrokes before the password manager even processes them. Multi-factor authentication doesn't matter if attackers have keyboard access and can watch you enter your second factor. Encryption at rest doesn't protect you if the attackers are grabbing data in real-time as you work.
For a government targeting corporate intelligence, this is invaluable. Imagine you work for a foreign policy think tank, a consulting firm advising on China strategy, a tech company with investments in Taiwan, or a government agency working on Indo-Pacific policy. Your Notepad++ installation just became a surveillance device.
The attackers could harvest:
- Credentials and API keys: Developers often leave passwords, tokens, and API keys in notes, test files, and configuration files opened in their editor.
- Code repositories: Draft code, experimental features, architecture notes, all visible to attackers.
- Strategy documents: Policy briefs, business plans, competitive analyses, if the victims were working on them in Notepad++.
- Real-time activity monitoring: What the victim was working on, how they spent their time, which projects and systems they accessed.
- Network topology and infrastructure details: If the victims were documenting internal systems, the attackers would see it.
For a state sponsor, keyboard logging on even a handful of targets in strategic organizations is a massive intelligence win. They don't need to compromise thousands of machines. They just need the right machines.

Why Supply Chain Attacks Are So Effective (And So Dangerous)
Notepad++ isn't the first victim of this type of attack. In fact, we've been watching supply chain attacks become increasingly common and increasingly effective for nearly a decade.
The reasons are obvious once you think about it: supply chain attacks are force multipliers. Instead of compromising one target, you compromise one distribution channel and hit everyone who trusts it. Instead of needing to find vulnerabilities in your actual target's network, you exploit the trust relationship they have with their software provider.
When Solar Winds got compromised in 2020, hackers gained access to over 18,000 organizations, including the US Treasury Department, the Homeland Security Department, and major corporations. All through legitimate-looking update packages.
When a 3CX phone software provider got compromised in 2023, attackers deployed malware to tens of thousands of businesses simultaneously.
When npm packages get poisoned with malicious code, developers download it thinking it's a legitimate open-source library.
The pattern repeats because it works. Organizations invest in network security, endpoint protection, vulnerability management. But most have a blind spot: they trust the software they download from official sources. They assume the update that came through the normal update mechanism is safe.
Notepad++ victims had every reason to assume their update was legitimate. They checked the official website. They clicked "Check for Updates." They saw version numbers that made sense. They had no way to know that the hosting infrastructure had been compromised.
The scariest part about supply chain attacks is that they're incredibly hard to defend against as an end user. You can't realistically verify the cryptographic signatures on every update package. You can't personally inspect the hosting infrastructure. You can't know when a third-party server has been compromised.
You have to trust that the software provider did their job. And in the Notepad++ case, Don Ho did everything right from his end. The problem was the hosting provider's security was inadequate. That's not his fault. But his users paid the price.

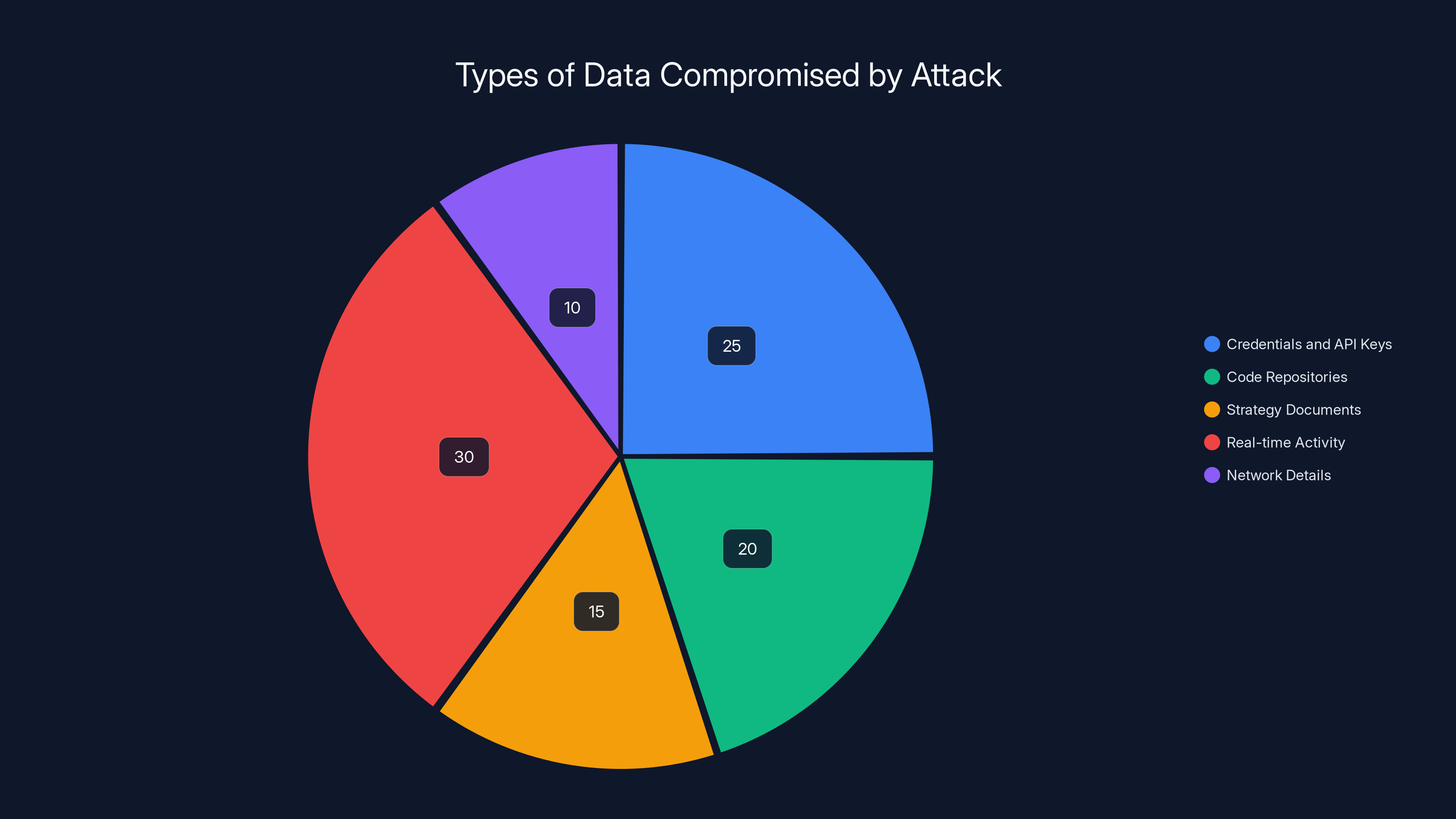
Real-time activity monitoring and credential theft were the most common data types compromised, highlighting the attackers' focus on gaining strategic insights and access. Estimated data.
The Response: Notepad++'s Security Fixes
Once the breach was discovered and disclosed, Notepad++ had to act fast.
The primary fix came in version 8.8.9, released as a critical patch. This version includes stronger security measures to detect tampering in update manifests and verify that updates are legitimate.
Specifically, Notepad++ upgraded the cryptographic verification process for updates. The new system uses stronger hashing algorithms, pinned signing certificates, and potentially TLS pinning to prevent man-in-the-middle attacks. The exact technical details weren't fully disclosed (to avoid giving attackers a roadmap for finding new vulnerabilities), but the goal was clear: make it exponentially harder to serve malicious updates even if the hosting infrastructure is compromised.
Beyond version 8.8.9, Notepad++ also implemented additional safeguards in the gup.exe updater itself. The updater now performs additional validation checks on downloaded files before execution. It verifies that the file being executed is actually Notepad++ and hasn't been modified or substituted.
Don Ho also likely changed hosting providers, though he didn't specifically state this in his disclosure post. Switching to an infrastructure provider with stronger security controls reduces the attack surface going forward.
But here's the honest assessment: no update mechanism is perfectly secure. If an attacker gains deep enough access to your infrastructure, they can potentially find ways around even sophisticated security measures. The goal isn't perfect security. It's making the attack expensive enough and risky enough that the attacker decides another target is easier.
For users, this meant that if you updated to version 8.8.9 after the patch was released, you got the security improvements. But if you downloaded version 8.8.8 or earlier during the June-December 2025 window, you potentially got the malicious version instead.
This is where the damage assessment gets murky. Notepad++ never provided a public list of which users were actually compromised. The targeting was selective, so not everyone who downloaded an update during this period got the malicious version. But determining which specific users were compromised would require access to the hosting provider's logs, and those details have remained confidential.
What Users Should Do Right Now
If you were using Notepad++ during the vulnerable period, here's your action plan.
First: Update immediately to version 8.8.9 or later. Download directly from the official Notepad++ website, not from mirrors or other sources. This ensures you're getting the patched version with security improvements.
Second: Check your version number. Open Notepad++ and go to Help → About Notepad++. If you're running anything below version 8.8.9, update immediately. If you're already on 8.8.9 or later, you have the security patches but you might still have been compromised if you installed a malicious version during the vulnerable window.
Third: Monitor gup.exe behavior. This is Notepad++'s updater executable. Open Windows Task Manager and watch for gup.exe running. Legitimate updates should only take a few seconds. If you see gup.exe running for extended periods, establishing network connections to unusual servers, or consuming excessive resources, that's a red flag.
Fourth: Check your TEMP folder for suspicious files. Open Windows Explorer and navigate to %TEMP%. Look for files named update.exe or Auto Updater.exe. These aren't legitimate Notepad++ files. If you find them, delete them immediately and consider your system compromised.
Fifth: Consider running a full antivirus scan with updated virus definitions. Many antivirus vendors have released signatures for the malicious Notepad++ payloads. A comprehensive scan might catch the malware if you were compromised.
Sixth: Check for unauthorized SSH keys, suspicious browser extensions, or unexpected processes in your Task Manager. If you were compromised, the attackers likely installed additional persistence mechanisms beyond just the keyboard logger.
Seventh: If you work for an organization, notify your IT security team immediately. Let them know when you installed updates during the vulnerable period and ask them to check your machine forensically. They can look for signs of compromise that wouldn't be obvious to the casual user.
For organizations whose employees use Notepad++, this is a bigger story. You need to:
- Audit all machines that had Notepad++ installed during June-December 2025
- Check update logs to see if any machines downloaded updates during the vulnerable period
- Scan those machines thoroughly for signs of compromise
- Rotate credentials for anyone who might have been affected
- Monitor for ongoing malicious activity from those machines
- Consider this a potential data breach and notify relevant stakeholders
This is expensive and time-consuming. But the alternative is having compromised machines in your network feeding intelligence to a state actor.

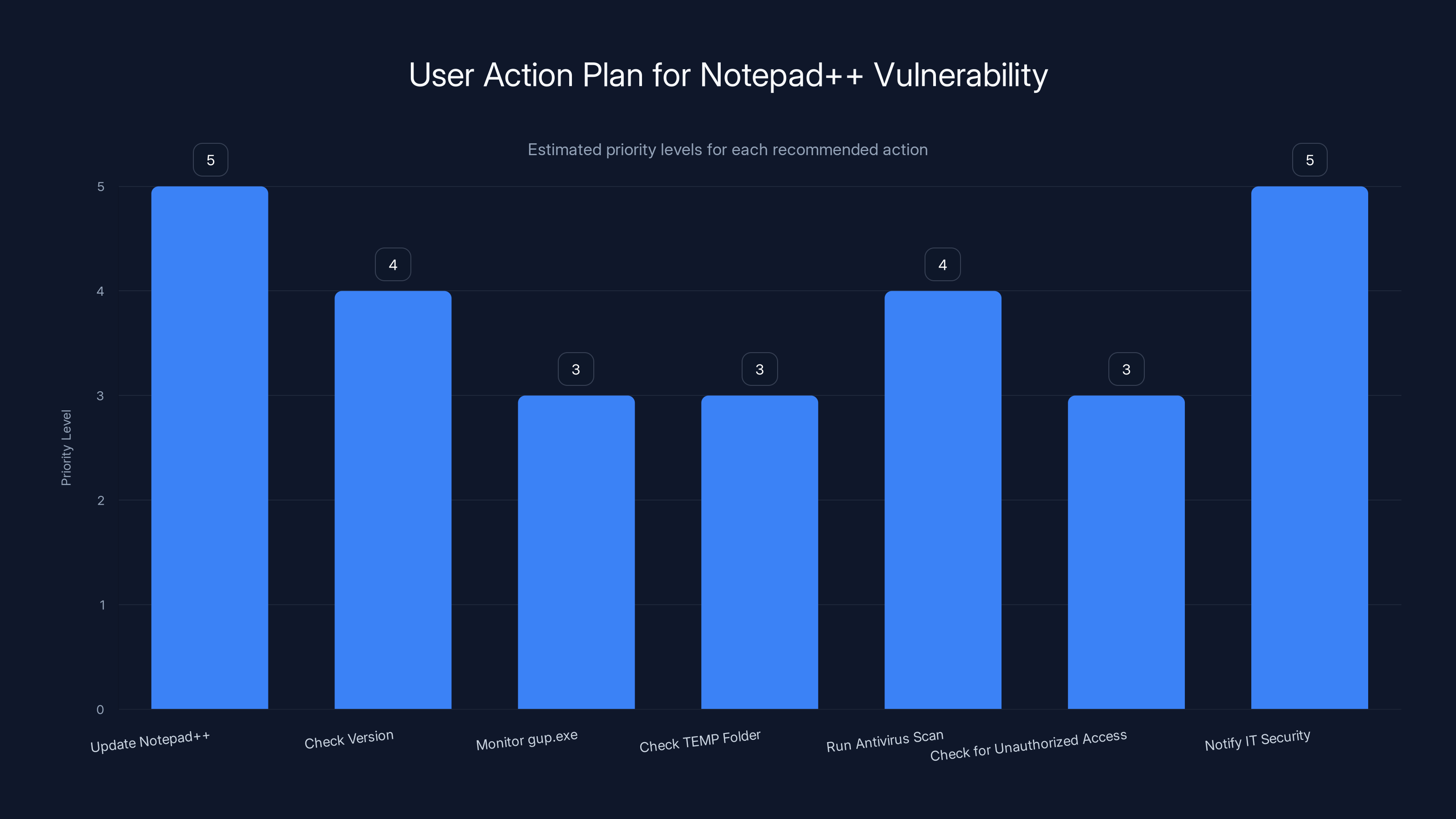
Updating Notepad++ and notifying IT security are top priorities to mitigate potential vulnerabilities. Estimated data based on typical security protocols.
The Bigger Picture: Why Software Updates Are Security Theater
The Notepad++ attack reveals something uncomfortable about how we manage software security: we rely on hope more than we rely on technology.
We download software from official sources and assume that means it's secure. But "official source" just means the domain is registered to the right person. If the servers hosting those downloads get compromised, the domain is still official, but the software is poisoned.
We update regularly because we're told it's important for security. And it is. But most updates go unverified by end users. You click the update button and trust that what comes back is legitimate. If the update infrastructure is compromised, that trust is betrayed.
We rely on antivirus software to catch malicious updates. But antivirus is reactive. It needs a signature for the malware first. The Notepad++ malware was running undetected for six months before security researchers identified it.
We assume that large software companies have security teams that would catch this type of compromise. Sometimes they do. Sometimes they don't. Supply chain compromises are, by definition, happening outside the software vendor's perimeter. The vendor's security team can't necessarily detect them.
This creates a fundamental asymmetry: defenders have to protect every possible attack vector. Attackers only need to find one that works. And for state-sponsored attackers with essentially unlimited resources, supply chain infrastructure has proven to be one of the easiest vectors to compromise.
The honest truth is that there's no perfect solution to supply chain security from an end-user perspective. You can't realistically verify every piece of software you download. You can't personally test every update. You can't audit every hosting provider's security controls.
What you can do is reduce your risk:
- Use tools and languages that have strong cryptographic verification built into their package management systems
- Monitor network traffic from your system to detect unusual outbound connections
- Implement network segmentation so that if one device is compromised, attackers can't immediately pivot to sensitive systems
- Keep offline backups of critical data
- Use application whitelisting to prevent unauthorized executables from running
- Assume your software might be compromised at some point and build your security architecture accordingly
But fundamentally, supply chain security is a problem that requires action at the producer level, not just the consumer level. Software companies need to invest in security infrastructure, security audits, and secure build processes. Third-party hosting providers need to implement proper access controls and monitoring.
Because until we solve the problem upstream, Notepad++ won't be the last supply chain attack. It'll just be another entry in an increasingly long list.

Historical Context: Supply Chain Attacks Are Evolving
The Notepad++ attack didn't happen in isolation. It's part of a broader pattern of attackers targeting software distribution infrastructure.
Solar Winds was the watershed moment. In 2020, attackers compromised Solar Winds' build environment and injected malicious code into legitimate Orion Platform updates. Those updates went out to over 18,000 customers, including federal agencies. It took weeks to detect, and the investigation revealed that the attackers had access to sensitive government networks for months.
Solar Winds wasn't the first supply chain attack, but it was the one that made everyone pay attention. It showed that even massive software companies with security teams could be compromised. And it showed that supply chain attacks could reach far more targets than any traditional intrusion.
Since then, we've seen:
- 3CX compromise (2023): Attackers compromised a legitimate phone system software provider and distributed malware through their official update mechanism to tens of thousands of customers.
- Codecov supply chain attack (2021): Attackers modified the source code repository of a widely-used code coverage tool, and the malware made its way into legitimate releases.
- Xcode Ghost (2015): Attackers compromised Xcode, Apple's development tool, and users who downloaded it from unofficial sources (but which appeared official) got infected versions that injected malware into applications they built.
- CCleaner supply chain attack (2017): The popular cleaning utility was compromised and distributed malware to millions of users through legitimate downloads.
The pattern is consistent: find a software distribution channel that millions of people trust, compromise it, and use it to deliver malware at scale. The attack gets amplified through the trust relationship between the software provider and their users.
The sophistication of these attacks has also evolved. Early supply chain attacks were often opportunistic. Attackers found a vulnerability and exploited it. Modern supply chain attacks are strategic. State actors deliberately target software distribution infrastructure as part of intelligence collection operations. They're patient. They're careful. They're trying to stay undetected.
Notepad++ fits this evolved pattern perfectly. It was selective targeting of a specific audience. It maintained operational security for six months. It used legitimate update mechanisms to distribute the payload. By the time it was detected, the attackers had already got what they wanted.
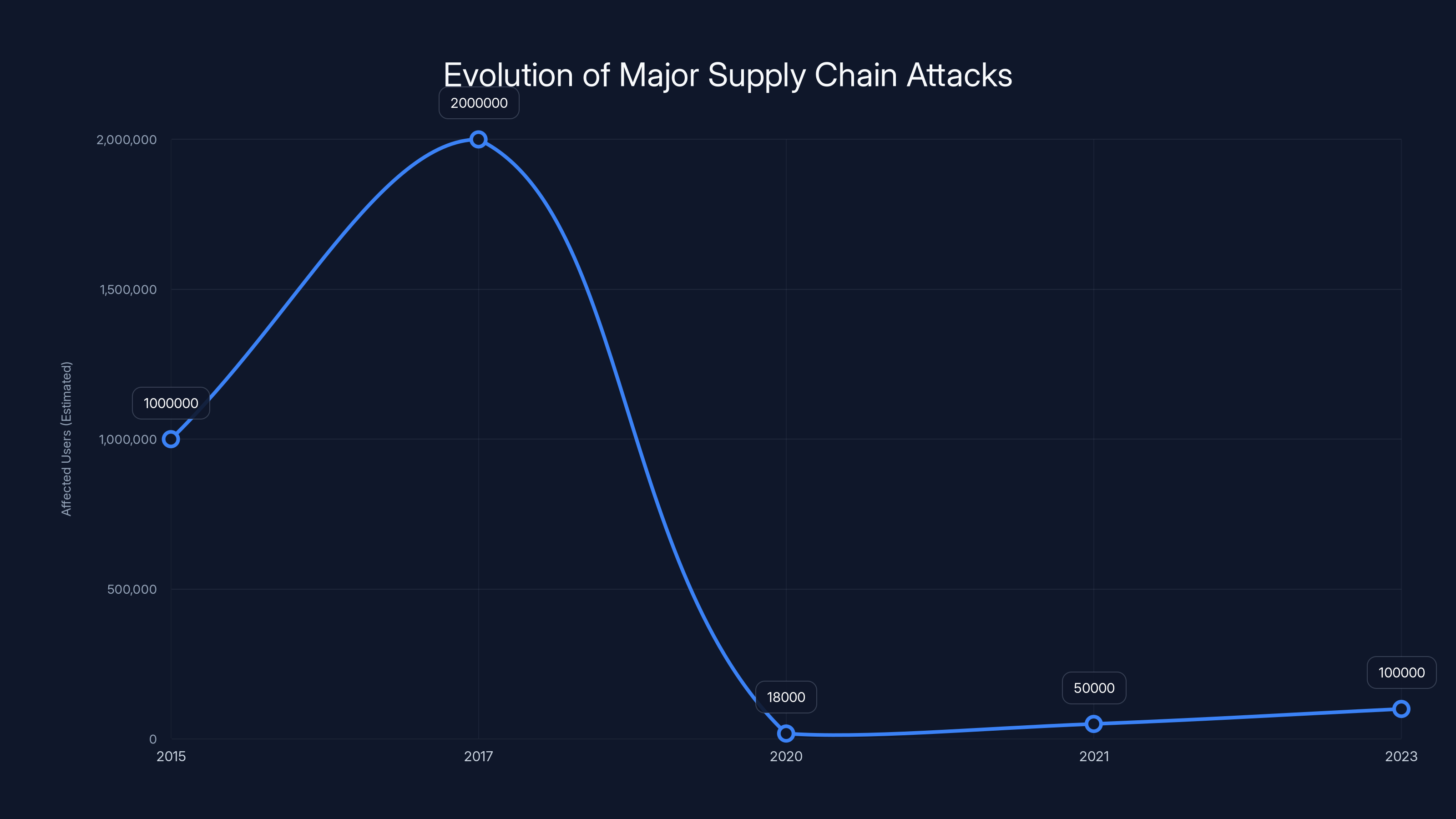
The timeline shows the increasing scale and impact of supply chain attacks over the years, with SolarWinds being a pivotal moment in 2020. Estimated data based on reported incidents.
The Geopolitical Dimension
Notepad++ is ultimately a tool. It doesn't belong to any government. But Don Ho, its creator, made a political statement by releasing a "Free Uyghur" edition in 2019.
That wasn't a commercial decision. It was an ethical stance. And it came with consequences. His website faced DDo S attacks afterward. The message was clear: criticize China's government at your own risk.
The 2025 supply chain attack could be many things: retaliation for the "Free Uyghur" edition, a way to target organizations that use Notepad++, or just an opportunistic compromise that attackers exploited. We don't know for sure.
But what's clear is that software and politics are increasingly intertwined. When a developer takes a political stance, they're not just expressing an opinion. They're potentially painting a target on their project.
This creates a chilling effect. Developers start avoiding political statements because they know that software projects can become collateral damage in geopolitical conflicts. That's a loss for everyone, because it means fewer voices speaking up about human rights abuses.
At the same time, the Notepad++ attack shows why nation-states care so much about supply chain security. If you can compromise a software distribution channel, you can target specific organizations and people at scale. It's an incredibly effective espionage tool.
Governments are aware of this. Some are starting to mandate supply chain security requirements for critical software. Others are implementing restrictions on which software they allow in government agencies.
But ultimately, the solution can't come from government mandates alone. It has to come from the software industry itself: better security practices, better infrastructure, better transparency about compromises.

Looking Forward: How Software Distribution Will Change
The Notepad++ attack is a wake-up call. It shows that current practices for software distribution and updates aren't adequate for a world where nation-states are actively targeting this infrastructure.
What changes are likely?
First: Expect more aggressive implementation of software signing and verification. Every operating system now has mechanisms for verifying that software comes from trusted publishers. Expect these to become mandatory rather than optional.
Second: Expect more use of sandboxing and isolation for updates. Instead of updates running with full system privileges, they'll run in restricted environments where they can be analyzed before being fully trusted.
Third: Expect more transparency and openness about security compromises. The current model where software companies try to quietly fix breaches isn't working. Expect more mandatory public disclosure, probably mandated by regulation.
Fourth: Expect more decentralized package management and distribution. Instead of relying on single hosting providers or CDNs, expect more redundancy and more verification at each level of distribution.
Fifth: Expect more involvement from government agencies in infrastructure security. This isn't just a commercial problem anymore. It's a national security problem. Expect more regulation, more oversight, and more government investment in tools and processes for detecting supply chain attacks.
Sixth: Expect developers to invest more in their own security infrastructure. Small open-source projects can't realistically protect against nation-state-level attacks, so expect more consolidation and more support from larger organizations for maintaining critical infrastructure.
The goal is to make supply chain attacks harder and less rewarding. If attackers have to compromise multiple levels of infrastructure, maintain operational security for months longer, and run a higher risk of detection, they'll look for easier targets.
But there's no perfect solution. As long as software needs to be distributed and updated, there will be attack vectors. The best we can do is make them expensive and risky enough that only the most determined, well-resourced attackers pursue them.
Recommendations for Software Developers and Organizations
If you maintain open-source software or run an organization that develops software, here's what you should be doing in response to the Notepad++ attack:
Infrastructure Security:
- Conduct a security audit of your build and distribution infrastructure
- Implement multi-factor authentication on all administrative access
- Use infrastructure-as-code to make unauthorized changes detectable
- Implement logging and monitoring of all administrative actions
- Consider using a zero-trust security model for your entire pipeline
Code Signing and Verification:
- Sign all releases with hardware security modules, not software keys
- Implement certificate pinning in your updater applications
- Use strong hashing algorithms (SHA-256 or better) for integrity verification
- Test your verification mechanisms regularly to ensure they actually work
Transparency:
- Publish security policies clearly
- Be transparent about how you perform code reviews
- Document your build and release process
- Establish vulnerability disclosure procedures
- Have a plan for communicating security incidents to users
Monitoring and Detection:
- Implement logging and anomaly detection on all infrastructure
- Monitor for signs of unauthorized access
- Use file integrity monitoring to detect unauthorized changes
- Conduct regular penetration tests of your infrastructure
Incident Response:
- Have a documented incident response plan
- Practice incident response drills regularly
- Know who to contact if you detect a compromise
- Be prepared to coordinate with law enforcement
- Have legal counsel involved in your response planning
Supply Chain Security:
- Audit your dependencies and third-party tools
- Implement restrictions on which packages you can import
- Use software composition analysis to detect vulnerable dependencies
- Consider the security practices of tools you use
- Build relationships with other developers to share security information
For organizations using open-source software:
- Maintain inventory of all software components you use
- Monitor security advisories for the tools you depend on
- Have a process for testing and deploying patches quickly
- Consider using tools that provide supply chain security monitoring
- Participate in the open-source community to help improve security

Case Study: What Organizations Should Have Done
Let's imagine you're running an organization where developers use Notepad++. What's the ideal response timeline?
June 2025 (Breach occurs): You don't know about it yet. No one does.
November 2025 (Six months in): An independent security researcher discovers the compromise and starts coordinating disclosure with Notepad++ developers and antivirus vendors. Your organization is still unaware.
December 2nd, 2025 (Attackers lose access): The hosting provider finally detects and blocks the attackers. Don Ho begins writing his disclosure post.
December 5th, 2025 (Public disclosure): Don Ho publishes details of the attack. News outlets pick it up. Security researchers start analyzing the malware. Your organization reads about it.
December 6th, 2025 (Your response starts):
- Your IT team sends an urgent communication to all employees using Notepad++
- You check which employees have Notepad++ installed and which versions they're running
- You update all Notepad++ installations to version 8.8.9 immediately
- You run forensic analysis on machines that downloaded updates during June-December
December 7th-14th, 2025 (Investigation and remediation):
- You identify three machines that downloaded updates during the vulnerable window
- You conduct forensic analysis and find indicators of compromise on two of them
- You remove the malware, check for additional persistence mechanisms, and rebuild the affected machines
- You notify employees on those machines that their systems were likely compromised
- You have them change all passwords, especially high-privilege passwords
- You check for unauthorized activity from those machines in your logs
December 15th, 2025 (Notification and prevention):
- If you handle sensitive data, you notify relevant regulators and stakeholders
- You implement stronger monitoring of update mechanisms for all software
- You restrict what software can be downloaded and where it can be updated from
- You implement application whitelisting so that only approved executables can run
Ongoing: You monitor for signs of re-compromise and look for indicators that attackers exfiltrated sensitive data.
This is the ideal response. Fast, thorough, and focused on preventing ongoing compromise.
But many organizations won't respond this way. They'll assume it doesn't affect them. Or they'll delay response because the attack is technically complex. Or they'll handle it with less urgency because it doesn't seem immediately critical. By then, valuable intelligence might already be gone.

The Intersection of Open Source and National Security
Notepad++ is open-source software. That's significant for several reasons.
First, open-source projects like Notepad++ are often maintained by individual developers or small teams working for free. Don Ho has been maintaining Notepad++ for over 20 years, and he's done an incredible job. But he doesn't have a security team. He doesn't have infrastructure engineers. He's essentially solo-maintaining one of the world's most widely-used code editors.
Second, open-source projects rely on community trust. Users trust the project because they can review the source code. They trust the maintainer because of their track record. That trust is the project's most valuable asset.
Third, open-source projects are often free. There's no revenue model that allows for investment in security infrastructure. Don Ho has to fund Notepad++ out of his own pocket, mostly as a hobby project.
This creates a vulnerability that state actors are happy to exploit. They know that individual developers or small teams maintaining popular open-source projects probably don't have the resources to defend against nation-state-level attacks. So they target the infrastructure instead of the code.
The Linux Foundation and other organizations are starting to recognize this problem and are investing in tools, funding, and education to help open-source developers improve security. But it's an uphill battle. There's literally too much critical infrastructure built on open-source projects to thoroughly secure all of it.
The Notepad++ attack is a reminder that the open-source model, while wonderful for software development, has serious security implications when the stakes are high.

What This Means for Your Security Strategy
If you're reading this and thinking "Does this affect me?" the answer is probably yes.
First, you might use Notepad++ directly. Even if you don't, you probably use dozens of tools that rely on software distribution infrastructure. Any of those could be compromised the same way Notepad++ was.
Second, if you work in a sensitive organization—government, defense, critical infrastructure, finance, healthcare—you're a higher-value target. State actors are more likely to target your software supply chain.
Third, the techniques used in the Notepad++ attack work against any software. Your email client could be compromised the same way. Your antivirus software could be compromised the same way. Your password manager could be compromised the same way.
What should you do?
Assume compromise is inevitable: Build your security architecture around the assumption that at some point, the software you use will be compromised. That means using defense-in-depth, network segmentation, monitoring, and detection.
Monitor your software: Watch what your applications are doing. Monitor network connections, file access, process creation. If something looks wrong, investigate.
Restrict privileges: Run applications with the minimum privileges they need. If an application doesn't need to access your Documents folder or your home directory, restrict its access.
Segment your network: Use network segmentation so that if one machine is compromised, attackers can't immediately pivot to sensitive systems.
Keep offline backups: If critical data gets exfiltrated or encrypted, you need the ability to recover without paying a ransom or losing everything.
Rotate credentials regularly: Even if you don't know you've been compromised, regular credential rotation limits the damage an attacker can do.
Use strong authentication: Multi-factor authentication, passwordless authentication, hardware keys. Make it hard for attackers to use stolen credentials.
Stay informed: Follow security news and vulnerability disclosures. Join mailing lists for tools you use. Subscribe to security research publications. The earlier you know about a compromise, the faster you can respond.
The Role of Security Research and Disclosure
The Notepad++ compromise was discovered by independent security researchers, not by Notepad++ developers or the hosting provider. That's significant.
It shows that security research—the kind done by people like Kevin Beaumont, who investigate compromises in their spare time and publish their findings—is critical infrastructure for the software ecosystem.
Without security researchers digging through suspicious executables, analyzing malware, and sharing their findings, many compromises would go undetected indefinitely.
But security research exists in an uncomfortable space. Researchers need to be careful about coordinating disclosure so that they don't hand attackers information before vendors have time to patch. At the same time, they need to be public enough that the broader community learns from incidents and improves security practices.
The disclosure process for the Notepad++ attack probably followed standard practice: researchers discovered the compromise, contacted relevant parties, gave vendors time to prepare fixes, and only then published detailed analysis.
But this creates a window where the compromise is known to researchers but not to the general public. For Notepad++ users, that window was a vulnerability. People who checked for updates during that period might still get the malicious version, even though security researchers already knew the software was compromised.
This is one of the fundamental tensions in cybersecurity: how do you balance the need for secrecy (to give vendors time to patch) with the need for transparency (so users can protect themselves)?
There's no perfect answer. Different organizations have different responsible disclosure policies. Some allow 90 days for vendors to patch before publishing details. Others allow 30 days. Some publish immediately after disclosure to vendors.
What's important is that security research happens at all. Without it, incidents like Notepad++ would go undetected indefinitely. Users would be compromised without ever knowing. That's worse than the situation we have now, even if the disclosure window creates some risk.

Lessons for the Future
If you extract one lesson from the Notepad++ attack, make it this: the software you trust the most might be the most dangerous if its distribution infrastructure is compromised.
We tend to trust software that's popular, that has a good reputation, that's been around for a long time. Notepad++ checks all those boxes. It's been around for over 20 years. It's widely respected. It's open-source so the code can be audited.
None of that prevented it from being compromised. Because the compromise wasn't in the code. It was in the infrastructure.
This has implications for how we think about software security going forward:
Trust is fragile: A single-point failure in software distribution infrastructure can compromise billions of dollars in business operations and national security systems. We need to treat software distribution with the same level of security as we treat nuclear power plants or critical financial infrastructure.
Scale creates vulnerability: The more popular a tool is, the more valuable it is to compromise. That means popular open-source projects are higher-value targets. But they often have the least security resources.
Individual developers need support: Don Ho has done an incredible job maintaining Notepad++ for 20+ years. But he shouldn't have to be responsible for defending against nation-state-level cyberattacks. The industry needs to provide better tools, funding, and support for developers maintaining critical open-source infrastructure.
Transparency builds trust: The fact that Don Ho disclosed the attack in detail (as much detail as he was comfortable with) probably restored user trust more than trying to hide it would have. Users need to know when their software has been compromised so they can respond appropriately.
Regulation is probably coming: This incident, combined with Solar Winds, 3CX, and other high-profile supply chain attacks, will probably trigger regulatory action. Governments will start requiring software companies to implement certain security practices and to disclose security incidents. This will increase costs for small developers, but it will also improve overall security.
We need better tools: The security tools available for detecting compromises are inadequate. We need better malware analysis tools, better intrusion detection, better ways for developers to verify that their infrastructure hasn't been compromised.

FAQ
What exactly is a supply chain attack?
A supply chain attack is a cyberattack that targets a software company's distribution infrastructure, update servers, build systems, or dependencies instead of attacking end users directly. In the Notepad++ case, attackers compromised the hosting servers that delivered software updates, allowing them to serve malicious code to users who downloaded what they thought were legitimate updates. Supply chain attacks are particularly effective because they can reach millions of users simultaneously through a single point of compromise.
How did the Notepad++ attackers avoid detection for six months?
The attackers used selective targeting to stay undetected. Instead of compromising every Notepad++ update, they intercepted requests from specific IP addresses and geographic regions, only redirecting those users to malicious update servers. This meant that most Notepad++ users downloading updates during the vulnerable period got legitimate versions, so the malware's prevalence remained low enough that antivirus companies didn't notice patterns. Additionally, the malicious executable probably functioned almost identically to legitimate Notepad++, with no obvious signs of compromise, so infected users wouldn't notice anything wrong.
Should I stop using Notepad++?
No. Notepad++ remains a legitimate, popular code editor. The vulnerability that allowed the 2025 attack has been fixed in version 8.8.9 and later. The attack wasn't a flaw in Notepad++ itself but rather a compromise of its update infrastructure, which is now more secure. Switching to a different editor won't necessarily make you more secure—every popular software tool could potentially be targeted the same way. Instead, make sure you're running the latest version and practice good security hygiene.
How can I tell if my machine was compromised by the malicious Notepad++ update?
Check for suspicious files in your TEMP folder, particularly files named update.exe or Auto Updater.exe. Monitor Task Manager for unusual activity from gup.exe (the legitimate Notepad++ updater). Look for unauthorized SSH keys in your .ssh folder, suspicious browser extensions, or unfamiliar processes. If you're concerned, run a full antivirus scan with updated definitions. If you work for an organization, contact your IT security team for forensic analysis, which can detect compromise indicators that wouldn't be obvious to casual inspection.
Why is this attack attributed to China?
Independent security researchers attributed the attack to Chinese government operators based on several factors: the selective targeting of organizations with East Asian interests, the operational security practices suggesting a well-resourced nation-state, the sophistication of the attack infrastructure, and the historical context of Notepad++ developer Don Ho criticizing China's government in a 2019 software update. While no definitive proof has been publicly disclosed, these factors align with known Chinese government cyber operations.
What's the difference between this attack and a regular malware infection?
A regular malware infection happens at the individual user or organizational level. The Notepad++ attack was a supply chain attack that used the software vendor's distribution infrastructure to deliver malware at scale. Instead of needing to compromise individual machines, the attackers compromised one distribution channel and reached thousands of users simultaneously. Supply chain attacks are more effective because they have the implicit trust of software vendors and users behind them.
Are other popular open-source projects at risk of similar attacks?
Yes. Any popular software project relying on third-party hosting infrastructure or lacking robust cryptographic verification is vulnerable to similar attacks. This is why many open-source projects have started implementing stronger security measures, including code signing with hardware security modules, cryptographic verification of updates, and more careful vendor selection for infrastructure.
What should organizations do to protect themselves from supply chain attacks?
Organizations should maintain inventory of all software and dependencies they use, monitor security advisories for the tools they depend on, implement network monitoring to detect unusual outbound connections that might indicate compromise, use software composition analysis to detect vulnerable components, segment their networks so that compromised machines can't pivot to sensitive systems, and develop rapid incident response processes for deploying patches when vulnerabilities are discovered. Additionally, implementing code signing verification and restricting where software can be updated from reduces the risk of being compromised by malicious updates.
How can I verify that software updates are legitimate?
Most modern operating systems have mechanisms for verifying that software updates come from trusted publishers. Windows uses Authenticode signing to verify executable publishers. mac OS uses code signing and notarization. Linux distributions use GPG signatures on packages. For maximum security, you can manually verify cryptographic signatures on software you download, though this is technically complex and most users won't do it. The most practical approach is to download software only from official sources, keep your operating system updated so that signature verification systems are current, and monitor your system for unusual behavior that might indicate compromise.
What regulatory changes might result from the Notepad++ attack?
Policymakers are likely to implement requirements for software security practices, mandatory security incident disclosure, supply chain security audits, and possibly restrictions on which software government agencies can use. These regulatory changes will likely increase compliance costs for software companies, but they'll also improve overall software security. Small developers and open-source projects might struggle with compliance costs, so expect some growth in support programs and funding for security improvements in critical open-source infrastructure.

Conclusion: Learning From a Crisis
The Notepad++ server hijacking wasn't a typical security incident. It wasn't a zero-day exploit that let hackers break into systems. It wasn't ransomware that encrypted files and demanded payment. It was something more insidious: a compromise of the trust relationship between a software vendor and millions of users.
For six months, people trusted that when they updated Notepad++, they were downloading legitimate software. That trust was violated. The damage was selective and probably limited to specific high-value targets, but the potential for widespread harm was enormous.
What makes this incident important isn't just what happened. It's what it represents. We've built the modern software ecosystem on the assumption that software distribution is secure. We assume that when we download an update from the official website, we're getting legitimate code. We assume that the infrastructure hosting those downloads is properly secured.
The Notepad++ attack proves those assumptions are insufficient. Nation-states are actively targeting software distribution infrastructure. They're doing it skillfully, staying undetected for months. And they're succeeding because defending this infrastructure is hard, especially for small projects and open-source developers who don't have the resources of major software companies.
The response to Notepad++ has been encouraging. Don Ho disclosed the attack transparently. He released patches immediately. He provided clear guidance on what users should do. The broader cybersecurity community analyzed the attack and shared intelligence. Organizations that use Notepad++ had the information they needed to respond.
But we can't rely on this kind of ad-hoc response indefinitely. The frequency of supply chain attacks is increasing. The sophistication is increasing. Eventually, we're going to see attacks that slip through the cracks entirely, or attacks against projects so critical that their compromise affects hundreds of millions of people.
That's when regulatory action will probably arrive. That's when the industry will need to implement stronger infrastructure security standards. That's when open-source developers will need better tools and funding to defend their projects.
Until then, the Notepad++ attack serves as a wake-up call. It shows that the software supply chain is a critical vulnerability that affects national security, corporate security, and individual privacy. It shows that even popular, well-maintained projects can be compromised. It shows that defending against state-sponsored attacks requires more resources than most developers have.
The question now is whether we act on that warning, or whether we wait for the next, larger supply chain attack before we take serious action.
Based on history, we'll probably wait. But the Notepad++ developers, the security researchers who found the attack, and the organizations that have to respond to it have all done their part. They've documented the incident, analyzed it, and shared what they've learned.
The rest is up to us. Will we invest in stronger supply chain security? Will we support open-source developers with the tools and resources they need? Will we regulate software distribution to ensure higher security standards? Or will we wait until a larger incident forces our hand?
The Notepad++ attack has shown us what's at stake. Now it's time to act accordingly.

Key Takeaways
- Notepad++ update infrastructure was hijacked for 6 months (June-December 2025) by state-sponsored attackers targeting specific high-value organizations
- Malicious updates gave attackers keyboard logging and remote access capabilities to monitor developer activity and exfiltrate sensitive information
- Supply chain attacks bypass traditional security because they exploit the trust relationship between users and software vendors
- Users should immediately update to Notepad++ 8.8.9+, monitor gup.exe behavior, and check for suspicious update files in their TEMP folder
- Organizations need multi-layered security including network monitoring, credential rotation, and rapid patch deployment to defend against supply chain attacks
Related Articles
- Notepad++ Supply Chain Attack: Chinese Hackers Hijack Updates [2025]
- Software Integrity vs Data Sovereignty: Why Code Matters More [2025]
- VSCode Malicious Extensions: How 1.5M Developers Got Compromised [2025]
- TriZetto Provider Solutions Breach: 700K+ Affected [2025]
- Windows 11 Improvements 2025: Microsoft's Real Fixes Beyond AI [2025]
- FBI Seizes RAMP: The Collapse of Ransomware's Last Stronghold [2025]
![Notepad++ Server Hijacking: Inside the Six-Month Supply Chain Attack [2025]](https://tryrunable.com/blog/notepad-server-hijacking-inside-the-six-month-supply-chain-a/image-1-1770066601952.jpg)



