Sonic Wall Breach Hits Marquis Fintech: What Banks Need to Know [2025]
It's mid-September 2025. Your firewall vendor just sent a quiet notification. Someone broke into their cloud backup system. Not a big deal, right? Wrong.
That breach at Sonic Wall ended up compromising sensitive data at Marquis, a fintech platform used by over 70 US banks and credit unions. Personal information, financial records, Social Security numbers, account credentials—all of it leaked.
Here's what makes this worse: Marquis is blaming Sonic Wall. Sonic Wall is denying responsibility. And caught in the middle are hundreds of financial institutions whose customers' data got exposed.
This isn't just another data breach. This is a breakdown in the supply chain security that banks depend on. And it reveals something uncomfortable: firewalls—the perimeter defense every organization trusts—can become the attack vector itself.
Let me walk you through exactly what happened, why it matters, and what you need to do about it.
TL; DR
- Sonic Wall suffered a cloud breach in September 2025 affecting its My Sonic Wall backup service, potentially compromising configuration files and credentials for thousands of customers
- Marquis fintech was hit hard: The platform lost sensitive banking customer data including personal information, financial details, and SSNs affecting 70+ US financial institutions
- Blame game begins: Marquis wants Sonic Wall to pay for damages, but Sonic Wall claims no direct connection to the ransomware attack
- Akira ransomware group is suspected behind the breach, a Russian state-sponsored operation that targets Sonic Wall infrastructure specifically
- This exposes supply chain risk: Your firewall vendor's security directly impacts your security, and configuration backups can become a goldmine for attackers
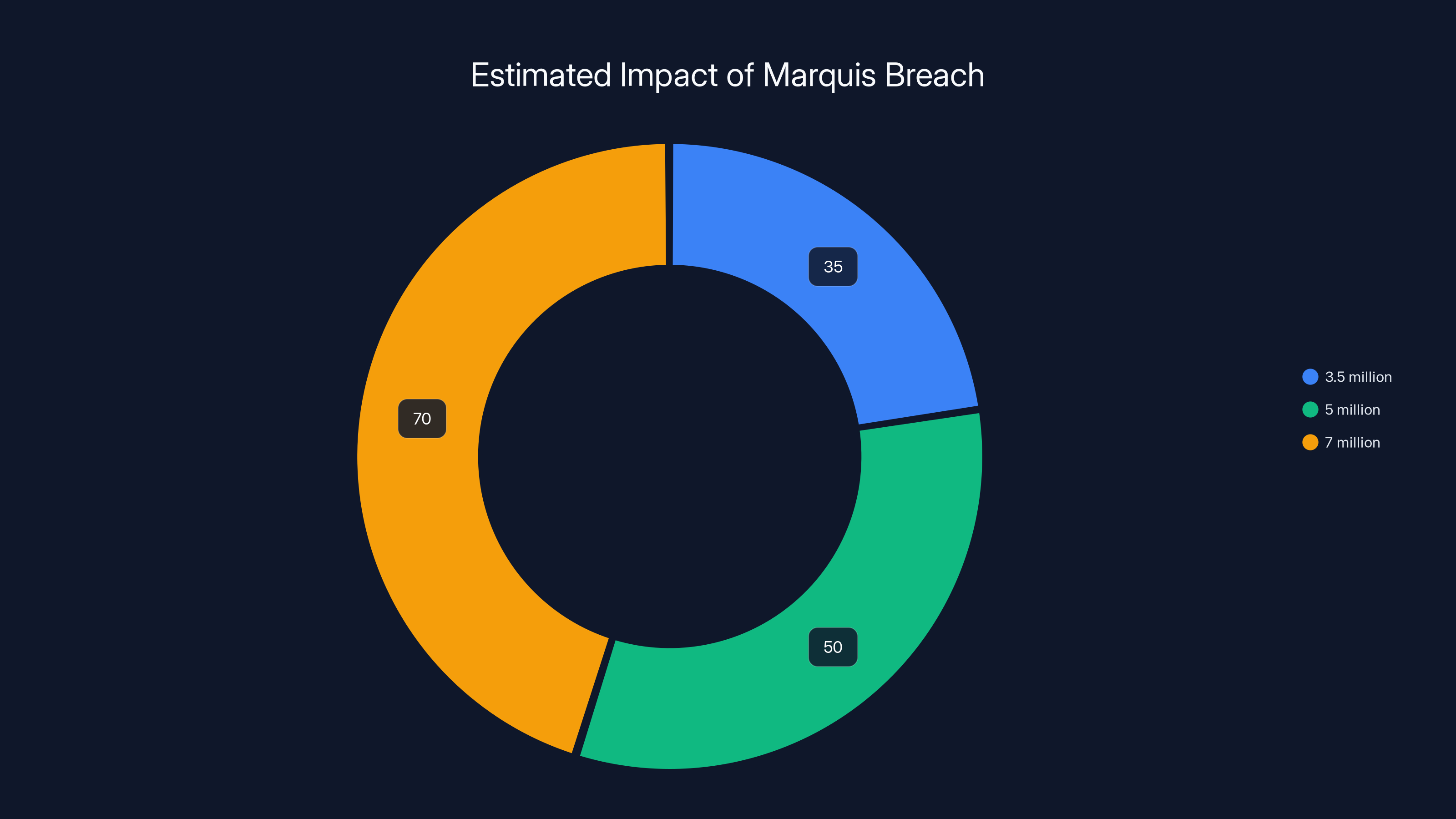
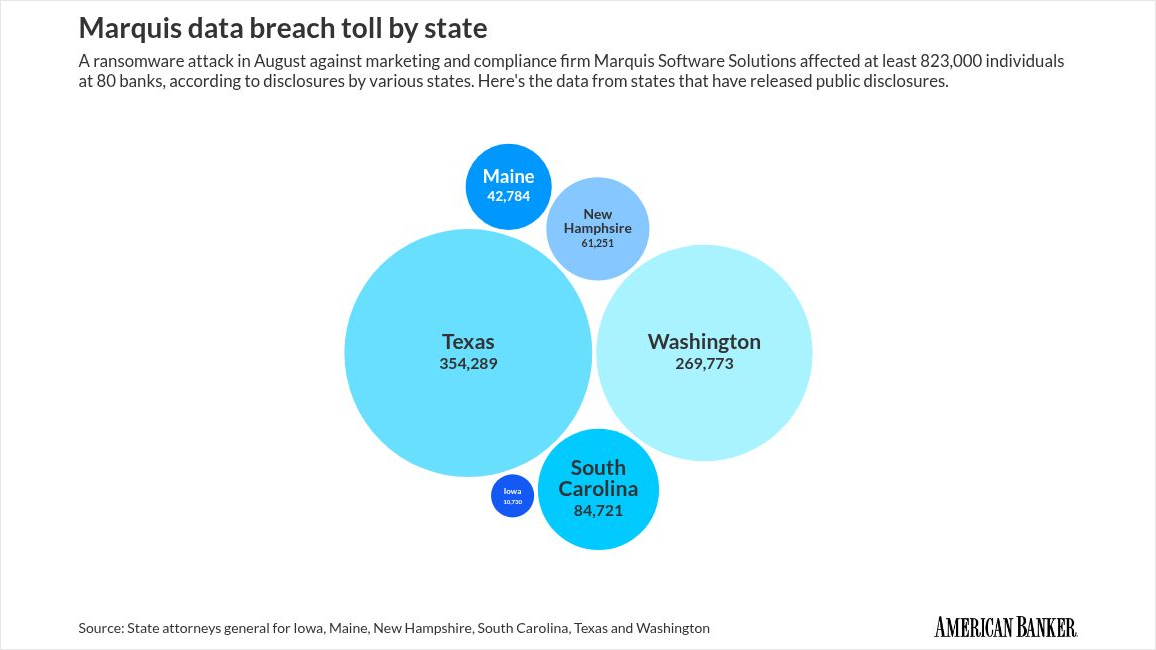
The Marquis breach potentially exposed between 3.5 million and 7 million individuals' data, with the exact number depending on the data stored by each institution. Estimated data.
How the Sonic Wall Breach Actually Happened
The attack started simple: brute force.
In mid-September 2025, threat actors tried thousands of username-and-password combinations against Sonic Wall's My Sonic Wall cloud service. That tool lets firewall administrators back up their configuration files to the cloud—something that sounds secure until you realize what's inside those backups.
Think about what a firewall configuration file contains. It's basically a treasure map of your entire network infrastructure. VPN credentials. LDAP settings. RADIUS configurations. SNMP community strings. Sometimes even plaintext admin passwords if someone stored them in the config.
For an attacker, this is jackpot material.
Sonic Wall's first response was damage control: only 5% of the customer base was affected. But that number kept growing as the investigation deepened. Eventually, the company admitted everyone—all customers—lost their backups to the hackers.
Let that sink in. Every Sonic Wall customer's firewall configuration was potentially accessible to unknown threat actors.
The attack itself wasn't sophisticated. No zero-day exploits. No advanced malware. Just patient credential stuffing until something stuck. But that simplicity is actually terrifying—it means basic security hygiene failures at a critical infrastructure vendor cascaded into a financial system attack.
Sonic Wall confirmed the breach. Customers reset passwords. And then the investigation got weird.
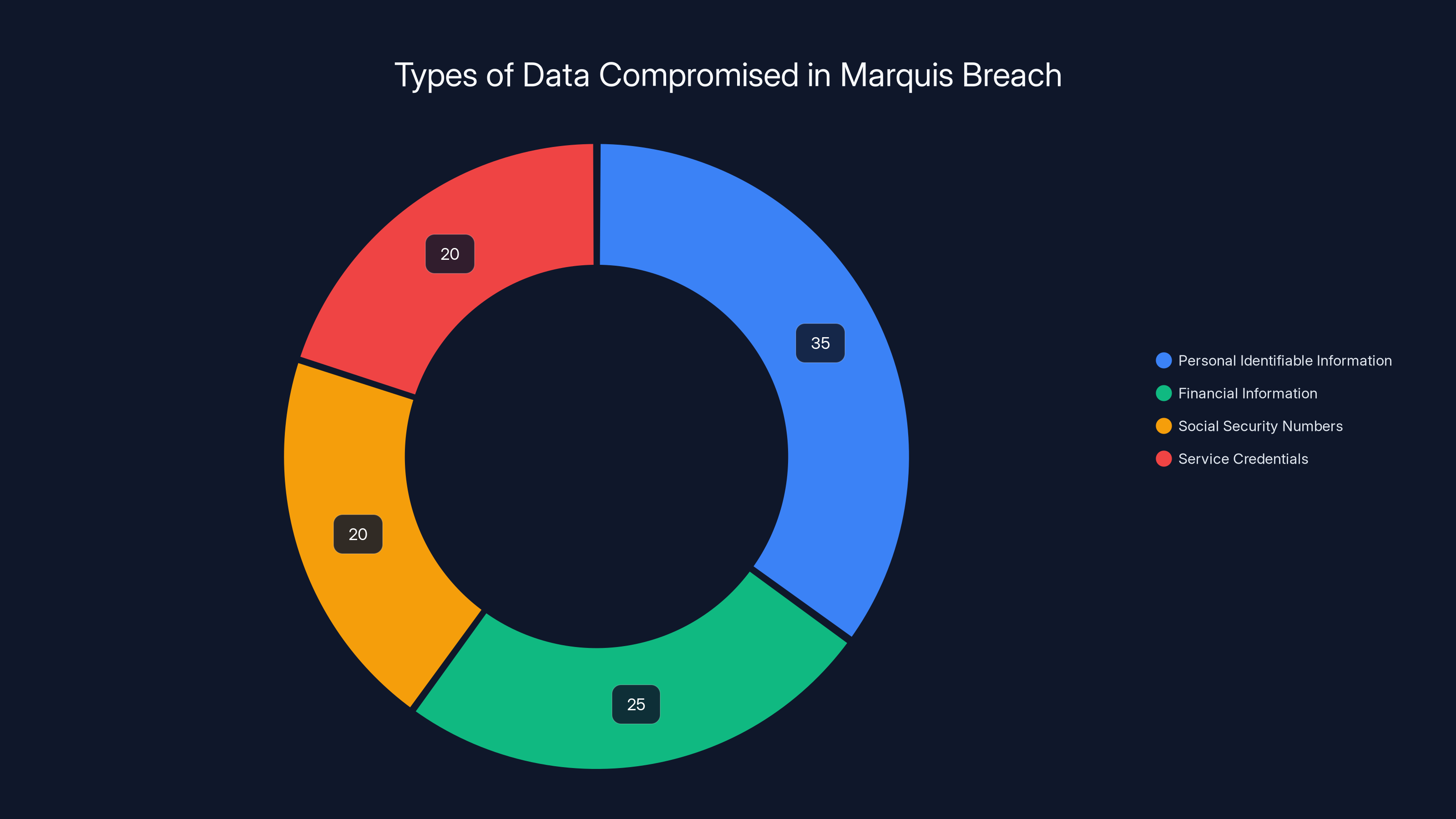
Estimated data shows a balanced compromise across PII, financial info, SSNs, and credentials, each representing a significant risk. Estimated data.
The Supply Chain Unravels: Marquis Gets Hit
Marquis is a software platform that banks and credit unions use to manage and visualize customer data. Not a household name, but essential infrastructure in American banking. Hundreds of financial institutions depend on it.
When cybercriminals accessed Marquis's systems, they didn't just steal data from one bank. They got access to the centralized repository holding sensitive information from dozens of institutions simultaneously. Personal details. Financial records. Social Security numbers. Months or years of transaction history.
Over 70 US banks and credit unions were affected. We don't have exact numbers on how many individual customer records were compromised, but we're talking about potentially millions of people whose information is now in criminal hands.
The attack hit Marquis hard, and the company had to make a choice: absorb the losses or sue the company whose product failure enabled the breach in the first place.
Marquis chose the latter.
In a memo shared with customers, Marquis basically said: "We're evaluating our options to have Sonic Wall compensate for the damages." Translation: We're considering a lawsuit.
But here's where it gets messy. Proving that a specific breach was directly caused by a specific vendor is legally complicated. Was Marquis really compromised because of the Sonic Wall breach? Or was that just one attack vector among many?
Sonic Wall's Response: Deny, Deny, Deny
Sonic Wall's official statement was careful. They said they have "no new evidence to establish a connection between the Sonic Wall security incident reported in September 2025 and ongoing global ransomware attacks on firewalls and other edge devices."
Let's parse that language. "No new evidence." Not "no evidence." "No new evidence." As if they're aware of existing evidence but haven't found anything new.
Their argument is essentially: Yes, we got breached. Yes, we store customer backup configurations. Yes, those configs contain credentials. But we have no proof that the Marquis ransomware attack came from our breach.
Technically, that might be true. But it's also missing the point.
When you're the vendor handling firewall configurations for thousands of organizations, and you get breached, and then a fintech platform gets ransomwared, the onus is on you to prove the attacks weren't connected. Not on everyone else to prove they were.
Instead, Sonic Wall leaned on plausible deniability.
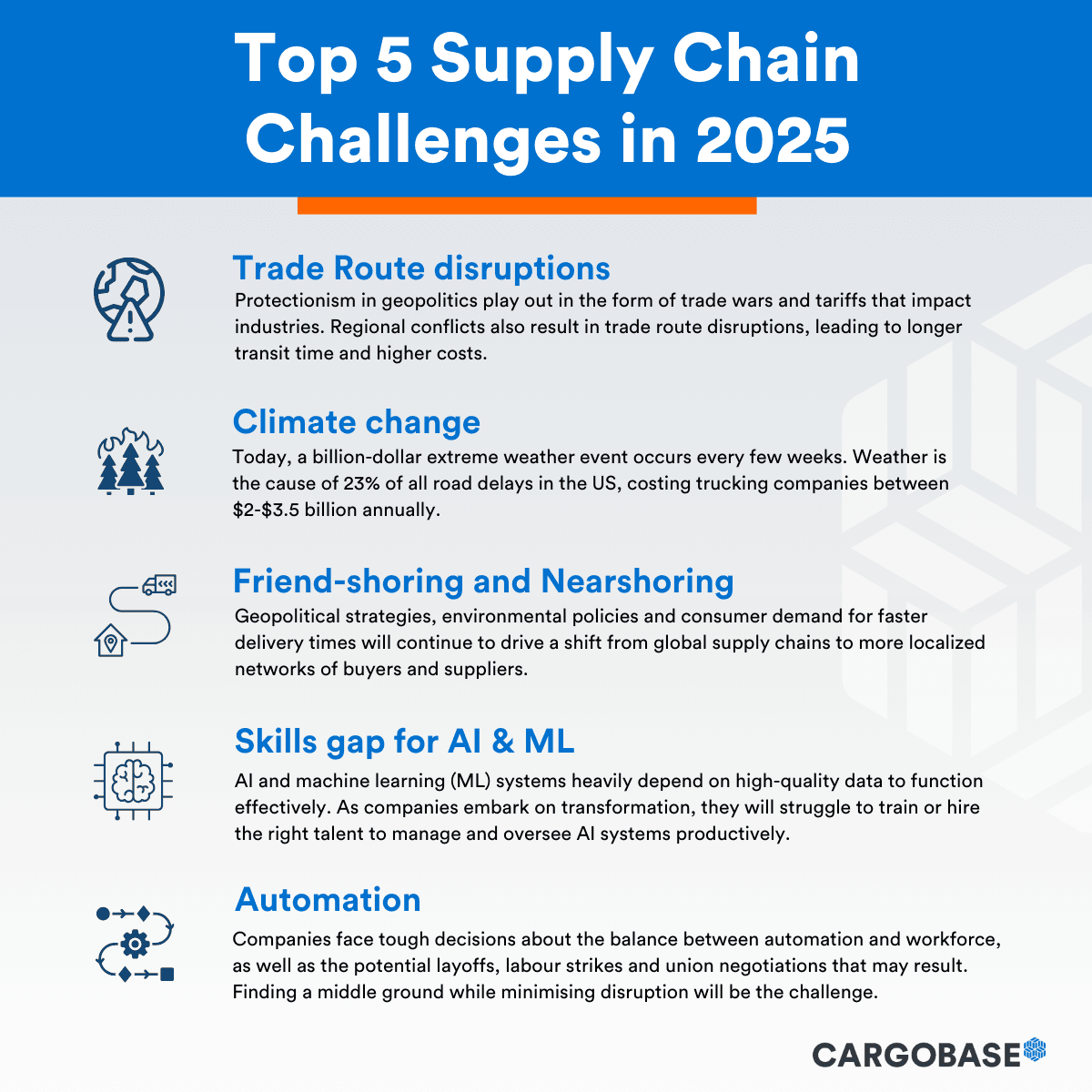
The average time to detect a data breach is 207 days. For complex breaches like Marquis, detection can span several months. (Estimated data)
The Ransomware Attribution: Akira and State-Sponsored Hackers
Figuring out who attacked Marquis requires some detective work.
Sonic Wall itself admitted the initial breach was likely a state-sponsored threat actor, though they never named names publicly. That's the kind of statement that usually means someone high-level got involved before the PR team could speak.
Multiple security researchers and outlets pointed fingers at a ransomware group called Akira. Here's what we know about them: they're Russian state-sponsored (or state-adjacent), they specialize in targeting Sonic Wall infrastructure specifically, and they've been active since at least 2023.
Akira's pattern is consistent with the Marquis attack. They break into Sonic Wall firewalls, escalate privileges, move laterally through the network, and ultimately deploy ransomware. They don't just encrypt data and demand payment. They exfiltrate sensitive information first, then use the threat of public disclosure as additional leverage.
The fact that Akira specifically targets Sonic Wall infrastructure isn't coincidental. They've likely spent months or years reverse-engineering Sonic Wall's architecture, finding vulnerabilities, and developing exploit chains. When a cloud service like My Sonic Wall gets breached, it's an opportunity to access hundreds of organizations at once.
State-sponsored ransomware groups operate differently than criminal crews. They're patient. They're strategic. They're looking for maximum economic disruption, not just quick paydays. Hitting the US financial system through a fintech platform is exactly the kind of target that would interest Russian threat actors.
But here's the thing: attribution in cybersecurity is messy. A group might use another group's tools. Someone might use Akira's playbook without being Akira. The cybersecurity community tends toward consensus rather than absolute certainty.
So when security researchers say "probably Akira," that's as close to a confirmed attribution as you usually get in the public domain.

The Attack Timeline: How Long Were Systems Compromised?
Understanding the timeline matters because it determines what data was at risk and for how long.
Sonic Wall discovered the My Sonic Wall breach in September 2025 and publicly disclosed it within days. That's actually relatively fast for a large vendor. But "discovering" a breach isn't the same as knowing when it started.
Breach investigations typically reveal that attackers were inside systems for weeks or months before detection. You don't know when they got in. You just know when you finally noticed them.
For the Sonic Wall breach, we don't have exact timelines. But we know:
- Threat actors successfully brute-forced credentials into My Sonic Wall
- They gained access to customer backup files
- They likely exfiltrated configuration data
- Months may have passed before anyone noticed
- Marquis was subsequently attacked, either using credentials from the Sonic Wall breach or separately
Each of those steps takes time. A competent attacker might spend weeks just exploring what they have access to before deciding what to steal or exploit.
If Marquis was compromised using credentials from the Sonic Wall breach, those credentials existed in the wild for weeks or months before the actual attack on Marquis. That's a huge exposure window.

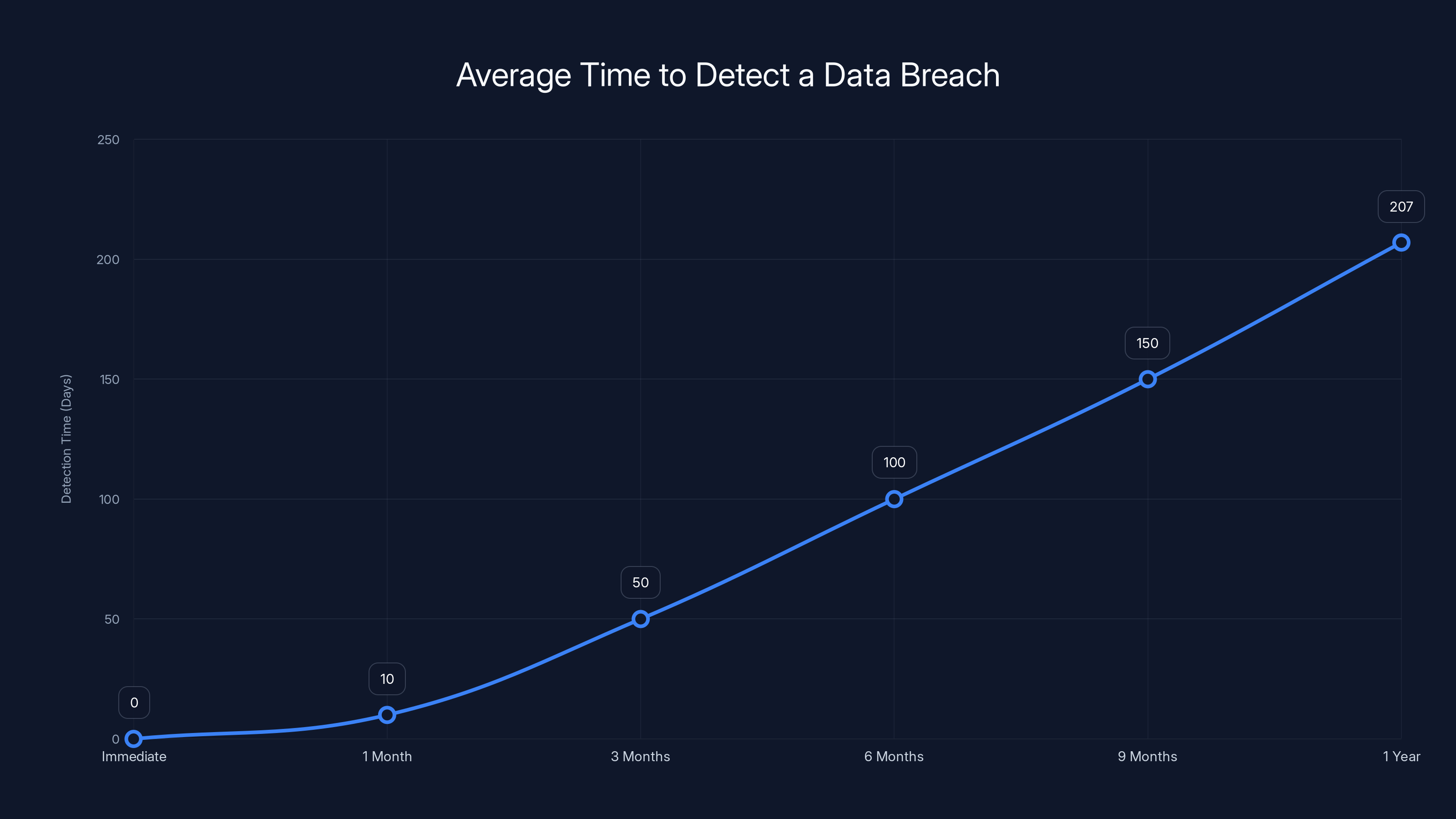
Estimated data shows that the majority of breach reports are filed with the Office of the Comptroller of the Currency, followed by the Federal Reserve and FDIC.
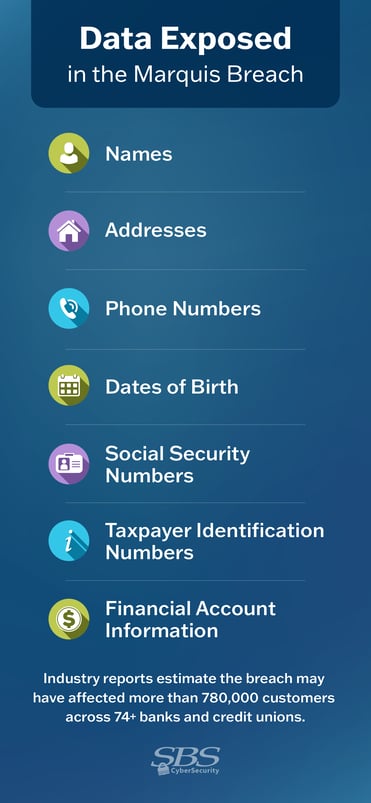
What Data Got Stolen? The Full Picture
When Marquis admitted the breach, they revealed what information was compromised:
- Personal identifiable information (PII): Names, addresses, contact details
- Financial information: Account balances, transaction history, account numbers
- Social Security numbers (SSNs): The gold standard of identity theft material
- Service credentials: Login information for Marquis itself and potentially other systems
For the banks affected, this is a liability nightmare. Their customers' most sensitive information is now in criminal hands. Identity thieves can use SSNs and financial data to commit fraud. Hackers can use credentials to pivot into other systems.
The fact that data from 70+ institutions was compromised simultaneously means this isn't a minor data leak. This is a significant breach affecting potentially millions of individuals.
A rough calculation: if the average bank affected had 50,000 to 100,000 customers in their Marquis records, and 70+ banks were hit, we're looking at somewhere between 3.5 million and 7 million people whose sensitive financial data was compromised.
For reference, the 2017 Equifax breach affected 147 million people and cost Equifax

The Legal Liability Question: Who Pays?
This is where things get interesting and complicated.
Marquis's argument is straightforward: "Sonic Wall's negligent security allowed our data to be stolen. Sonic Wall should cover the costs."
Those costs include:
- Notification and credit monitoring services for affected individuals
- Legal and investigation fees
- Potential regulatory fines
- Class action lawsuit settlements
- Reputational damage
- Lost revenue from customers switching platforms
Total damages could reach tens of millions of dollars. For a fintech company, that's an existential liability.
Sonic Wall's position is that they can't be held liable for what someone did with the stolen data. They'll argue: "Yes, our service was breached. But we didn't attack Marquis. Someone else did. Their security failed, not ours."
Legally, this gets into territory around negligence versus causation. A US court would need to answer: Did Sonic Wall owe Marquis a duty of care? Did Sonic Wall breach that duty? Did the breach directly cause Marquis's losses? Were those losses foreseeable?
All four elements need to be satisfied for negligence liability. Sonic Wall will argue on at least one of them—most likely causation.
There's also the question of insurance. Sonic Wall likely carries errors-and-omissions insurance and cyber liability insurance that might cover breach-related claims. Marquis probably does too. Insurers will fight over whose policy applies and at what limits.
This could drag through courts for years. Or it could settle quickly if Sonic Wall's insurance is substantial enough.
What probably won't happen: Sonic Wall admitting fault. That opens them up to liability not just from Marquis but from every other affected customer. They'll maintain that no causal connection was proven, and they'll settle if forced to, but they won't concede liability.

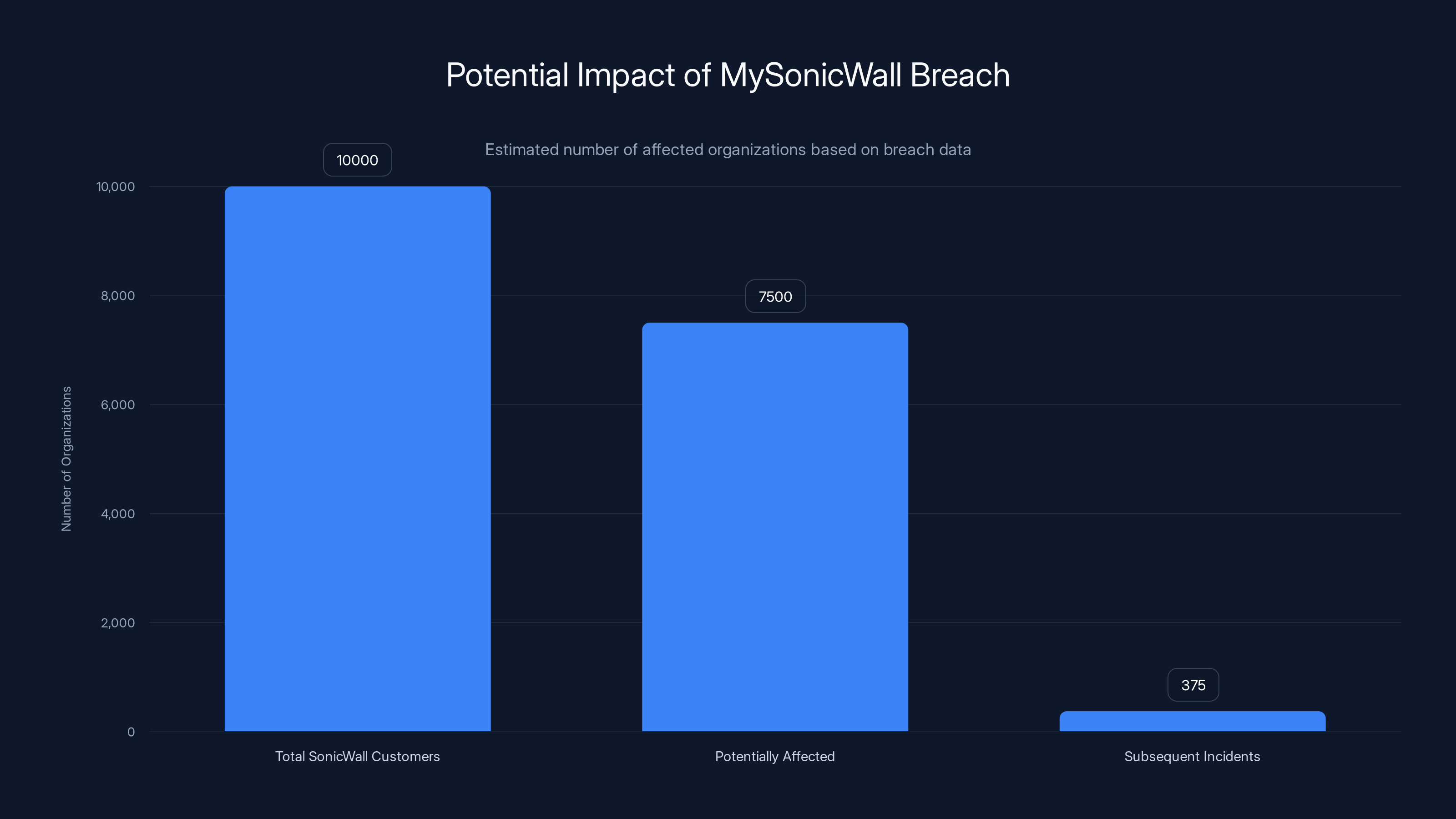
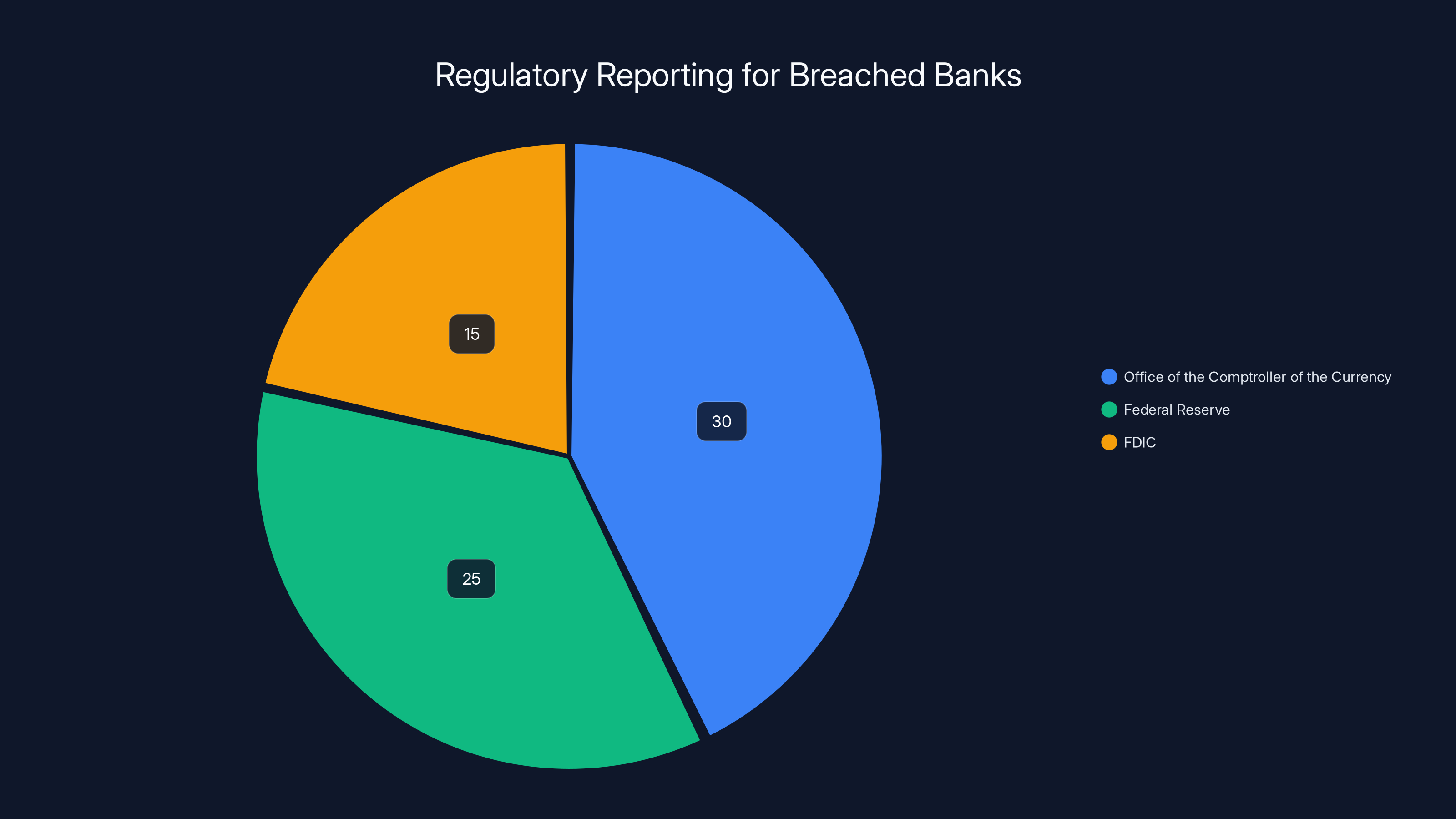
Estimated data suggests that out of 10,000 SonicWall customers, around 7,500 could be affected by the breach, with 375 experiencing further incidents.
The Bigger Picture: Supply Chain Risk in Financial Services
This breach reveals a fundamental vulnerability in how we've structured digital financial infrastructure.
Banks depend on multiple vendors for essential services: firewalls, backups, monitoring, authentication, data platforms. Each vendor is a potential weak point. And unlike internal security, you can't directly control a vendor's security practices. You can audit them, set requirements, monitor their compliance, but ultimately, you're trusting their engineering and operations teams.
When that trust gets violated at scale—when one vendor breach cascades into attacks on hundreds of customers simultaneously—it exposes the fragility of the entire ecosystem.
The Sonic Wall breach is particularly serious because firewalls are supposed to be the perimeter defense. They're the thing that keeps bad guys out. When the firewall vendor's own systems become the entry point, the entire defensive model breaks down.
It's like discovering that the lock manufacturer had a master key hidden in their factory, and criminals found it.
What makes this worse for the financial sector specifically: banking regulations require specific security controls. Your firewall configuration is probably part of your compliance documentation. If that configuration gets stolen, regulators want to know about it, and they want to know what you're doing to address it.
Marquis and the affected banks will likely face regulatory scrutiny, potentially fines, and definitely mandatory security assessments. The vendor failure becomes your compliance problem.
The Detection Problem: When Did Anyone Actually Know?
One of the most frustrating aspects of this breach is the detection timeline.
Sonic Wall discovered the My Sonic Wall breach in September and disclosed it publicly, which was responsible. But discovering a cloud service breach is different from discovering who accessed what and when.
Their investigation probably went something like: "Our logs show this IP accessing customer backups... and this one... and this one." Then they realized the breach was larger than initially thought. Then they concluded all customers were potentially affected.
But identifying that Marquis specifically was breached? That requires Marquis to notice they've been compromised. That could take weeks or months.
Databreaches are hard to detect when the attacker is patient. If someone steals backup files and quietly exfiltrates them, there might be no obvious indicator—no malware, no weird network traffic, nothing unusual in system logs.
Marquis likely discovered the breach when either:
- Customer complaints started rolling in ("I've been seeing fraudulent charges")
- Forensic investigation found lateral movement in their systems
- Ransom demands arrived claiming they had customer data
- A security researcher or law enforcement tipped them off
That delay between when data was stolen and when it was discovered is the real problem. Every day of delay is another day attackers have to sell the data, use it for fraud, or demand ransom.

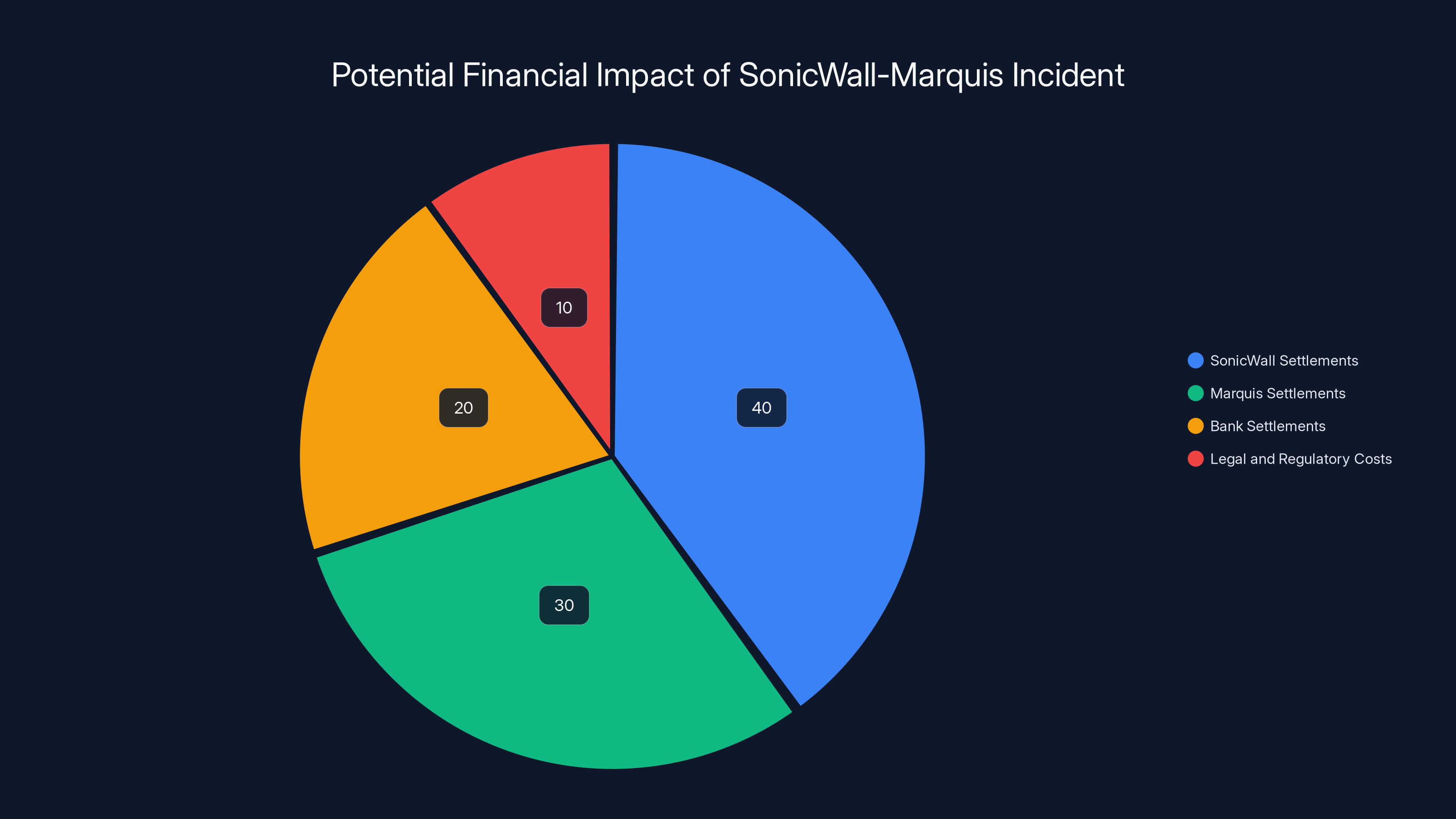
Estimated data suggests SonicWall could face the largest settlement costs, with significant additional costs for Marquis and affected banks. Total costs could exceed $100 million.
Credential Exposure: The Keys to the Kingdom
One detail that deserves special attention: Sonic Wall's backup service stored service credentials in configuration files.
LDAP passwords. RADIUS secrets. SNMP community strings. Sometimes even plaintext admin passwords.
If an attacker has these credentials from one firewall, they can potentially access the systems that firewall protects. More importantly, if the same credentials are reused across multiple firewalls (which many organizations do), the attacker gets a master key to potentially dozens of networks.
Marquis's security team probably faced a nightmare scenario: we have to assume our firewall credentials were stolen, which means we have to rotate every service credential on our network immediately. That's not a quick process.
For every service using those credentials, you need to:
- Generate new credentials
- Update configurations everywhere those credentials are used
- Verify services still function correctly
- Document the change
- Test failover and recovery scenarios
In a fintech environment, you can't just take systems offline to change credentials. You need to do it with zero downtime. That requires careful orchestration.
And the whole time, you're also dealing with the active ransomware attack. Your team is splitting focus between stopping the immediate threat and remediating the underlying credential exposure.
The Banking Industry's Exposure: 70+ Institutions at Risk
The fact that over 70 banks and credit unions were affected tells you something important about Marquis's market position.
Marquis isn't a small niche platform. It's trusted infrastructure for major financial institutions. Which means when it gets breached, the impact is enormous and concentrated in the sector that regulators care most about.
Banks are heavily regulated. They have to file breach reports with the Office of the Comptroller of the Currency, the Federal Reserve, and FDIC depending on their charter. They have to notify customers. They face potential enforcement actions.
The regulatory response to a breach affecting 70+ banks simultaneously is serious. You're looking at potential mandatory security audits, corrective action plans, and fines if regulators decide the banks weren't sufficiently diligent in vendor risk management.
For bank customers, the practical impact is that their financial institution is now dealing with a major incident. That means resources getting diverted from normal operations. It means heightened scrutiny of the bank's security practices. It might even mean some customers deciding to move their money to institutions they perceive as more secure.
Reputational damage in banking is a currency crisis waiting to happen. If people lose confidence in a bank's security, they withdraw money, and suddenly you have a bank run. That's why banks invest heavily in making sure breaches don't happen and that they respond credibly when they do.

The Sonic Wall Ecosystem: How Many More Are Affected?
Sonic Wall has thousands of customers. The My Sonic Wall breach potentially affected all of them, not just Marquis.
Other fintech companies might have been compromised. Other banks might have backup files stolen. Other critical infrastructure providers might have had their configurations exposed.
We know about Marquis and the ransomware attack because it was public and significant enough that the companies had to disclose it. But how many other breaches might have resulted from the Sonic Wall compromise that we don't know about?
A conservative estimate: if 5,000 to 10,000 Sonic Wall customers were affected by the My Sonic Wall breach, and even 5% of them experienced subsequent incidents, that's 250 to 500 additional organizations that might have been compromised.
We might never know the true scope of this incident because most breaches either get covered up quietly or settled under nondisclosure agreements.
What we do know: Sonic Wall's reputation took a significant hit. Organizations now have to decide: Can we trust Sonic Wall's cloud services? Should we pull our configurations offline and manage backups ourselves?
For Sonic Wall, that's a product crisis. Their My Sonic Wall service was supposed to be a convenience feature. Now it's a liability.

Incident Response: What Should Have Happened
Let's walk through what competent incident response would have looked like for each organization involved.
Sonic Wall's Response:
- Immediate shutdown of public access to My Sonic Wall (done)
- Audit of all access logs to identify unauthorized activity (essential)
- Forced password resets for all customers (done)
- Analysis of what data was accessed and by whom (unclear if fully completed)
- Detailed disclosure to all affected customers (done, but initially understated)
- Compensation framework for affected customers (not publicly announced)
- Post-mortem and remediation plan (not fully transparent)
Marquis's Response:
- Detect the breach (took weeks or months)
- Contain the breach (stop attackers' access)
- Eradicate the threat (remove malware and close attack vectors)
- Recover systems to known-good state
- Notify all affected customers within required timeframes
- Offer credit monitoring and identity protection
- Launch forensic investigation to understand attack vectors
- Implement remediation to prevent recurrence
The problem is transparency in this process. As customers and outsiders, we mostly don't see what's happening inside these incident response efforts. We get official statements that are carefully lawyered and don't admit fault.
What we needed: clear communication about what happened, when it happened, how long the exposure lasted, and what specifically each organization is doing differently now.
What we got: careful corporate statements that maintain legal defensibility.

Preventing Supply Chain Breaches: What Actually Works
So how do you prevent this from happening to your organization?
The honest answer: you can't completely prevent it. But you can significantly reduce your risk.
1. Vendor Risk Assessment Before adopting any critical service, you need to understand that vendor's security posture. That means:
- Regular security audits (SOC 2, ISO 27001)
- Questionnaires about their incident response capabilities
- Understanding their infrastructure and how they store your data
- Clarity on encryption, access controls, and monitoring
For critical services like firewalls, you need to go deeper. You should understand:
- How their cloud services are architected
- What credentials they store and how
- Their patch management practices
- Their incident response SLAs
- Their cyber insurance coverage
2. Zero Trust for Vendor Access Don't give vendors blanket access to your systems. Implement:
- Time-limited access tokens that expire after each use
- Multi-factor authentication for all vendor access
- Separate service accounts with minimal required permissions
- Audit logging for all vendor access
- Regular access reviews and removal of unnecessary access
3. Configuration Management Your firewall configuration is not something you store in someone else's cloud backup. Instead:
- Maintain your own encrypted backups
- Version control your configurations
- Test backup restoration regularly
- Rotate credentials regularly, separate from backups
- Never store plaintext passwords in configurations
4. Threat Intelligence Sharing If a vendor gets breached, you want to know as soon as possible. Join:
- CISA alerts for US critical infrastructure
- Industry-specific information sharing groups
- Your vendor's security mailing list
- Threat intelligence feeds focused on your infrastructure
Early warning gives you time to respond before an attack happens.
5. Segmentation and Defense in Depth Assume your firewall will be compromised. Then design your network assuming that:
- Internal networks are not automatically trusted
- Services authenticate each other
- Lateral movement is difficult
- Critical systems have additional monitoring
- Data at rest is encrypted
6. Incident Response Planning Before a breach happens, you need a plan:
- Who gets notified first?
- What's the escalation path?
- Who communicates with customers?
- What's your credential rotation playbook?
- How do you maintain operations during recovery?
- Who coordinates with law enforcement?
The Marquis incident probably would have had less impact if their incident response plan was already written and practiced.

The Regulatory Response: What Happens Next
Regulators are not happy about the Sonic Wall-Marquis incident. Here's what will probably happen:
From the FTC:
- Investigation into Sonic Wall's security practices
- Potential enforcement action for unfair or deceptive practices
- Public guidance to organizations using Sonic Wall about their responsibility to vendor security
From Banking Regulators:
- Scrutiny of how banks chose and monitored Sonic Wall
- Reviews of banks' vendor risk management programs
- Potential citations for inadequate vendor due diligence
- Enforcement actions if banks didn't have adequate incident response plans
From Congress:
- Possible hearings about supply chain security
- Potential legislation requiring stronger vendor security standards
- Requirements for critical infrastructure providers to report breaches faster
From Customers:
- Class action lawsuits against both Sonic Wall and Marquis
- Credit monitoring claims
- Identity theft settlements
- Potential punitive damages if negligence is proven
Based on historical precedent, Sonic Wall will probably settle for tens of millions. Marquis and affected banks will face additional enforcement and will probably settle their own class actions for more tens of millions.
Total cost for this incident: potentially $100+ million across all parties involved.

What Organizations Should Do Right Now
If your organization uses Sonic Wall or any vendor affected by this incident, here's your action plan:
Immediate (Next 24 Hours):
- Verify whether your organization uses Sonic Wall My Sonic Wall or affected Marquis services
- Contact your vendor to confirm exposure status
- Review your incident response plan and key contacts
- Alert your cybersecurity team to increase monitoring
Short Term (This Week):
- Rotate all credentials that might have been exposed
- Implement additional monitoring for lateral movement and data exfiltration
- Review recent access logs for suspicious activity
- Brief executive leadership on potential exposure and costs
- Contact your cyber insurance provider
Medium Term (Next 30 Days):
- Complete forensic investigation if you were affected
- Implement compensatory controls if vendor systems remain compromised
- Review vendor contracts for liability and insurance requirements
- Begin formal vendor risk reassessment
- Document your incident response for regulatory compliance
Long Term (Next 90 Days):
- Re-architect systems to reduce reliance on potentially compromised vendor services
- Implement zero trust controls for all vendor access
- Update incident response plans based on lessons learned
- Conduct security awareness training on supply chain risks
- Consider vendor alternatives or diversification
The Larger Cybersecurity Lesson
The Sonic Wall breach and its cascade into the Marquis attack teaches us something uncomfortable about modern security.
We've built complex interdependent systems where a single vendor's failure can compromise hundreds of organizations simultaneously. We've outsourced critical functions to vendors without fully understanding the security implications. We've created supply chains where one weak link breaks everything.
Solving this requires:
-
Stronger vendor security requirements: The critical infrastructure vendors we depend on need higher security standards than they currently have. That means regulatory requirements, not just market incentives.
-
Better supply chain visibility: Organizations need to know what their vendors have access to and what risks that creates. That requires standardized disclosure, not vendor handwaving.
-
Accountability for vendor breaches: When a vendor's negligence causes customer harm, there need to be real consequences. Settlements help, but they're not prevention.
-
Architectural resilience: Systems should be designed assuming vendors will be compromised. That means encryption, segmentation, and zero trust principles from the ground up.
-
Information sharing: The only way to improve the entire ecosystem is if organizations share what they learn from breaches. That requires changing culture from "hide it" to "protect others."
The Marquis breach is expensive and painful for the organizations involved. But hopefully it's the shock that the financial services industry needs to take supply chain security seriously.

FAQ
What exactly is the Sonic Wall My Sonic Wall service?
My Sonic Wall is a cloud-based backup and management service that allows Sonic Wall firewall users to store their firewall configurations in the cloud. This includes network rules, access policies, VPN configurations, and service credentials. It's designed for convenience and disaster recovery, but the September 2025 breach showed how dangerous storing sensitive configuration data in the cloud can be if that service gets compromised.
How many people were actually affected by the Marquis breach?
We don't have exact numbers, but the breach affected 70+ US banks and credit unions. If each affected institution had 50,000 to 100,000 customers whose data was stored in Marquis, the total exposure is likely between 3.5 million and 7 million individuals. The actual number could be higher or lower depending on how much customer data each bank had stored in the Marquis platform.
Can I trust Sonic Wall firewalls after this breach?
The breach at Sonic Wall's cloud backup service doesn't necessarily mean their firewall hardware or software is compromised. However, it does raise questions about Sonic Wall's overall security practices and their ability to protect customer data. Organizations should reassess their vendor risk, consider using local backups instead of cloud backups for critical firewall configurations, and implement additional security controls. Whether you continue using Sonic Wall depends on your specific security requirements and risk tolerance.
Who is Akira and why do they target Sonic Wall?
Akira is a Russian state-sponsored or state-adjacent ransomware group that specializes in targeting Sonic Wall firewalls. They likely target Sonic Wall because they've reverse-engineered Sonic Wall's architecture and developed exploit chains that work reliably. By compromising firewalls, they can pivot into the networks those firewalls protect. The Sonic Wall cloud breach gave them an additional attack vector: stolen firewall configurations containing credentials and network topology information.
Will Sonic Wall have to pay damages to Marquis and affected customers?
Probably, but not necessarily through direct liability. Sonic Wall will likely argue they can't be held liable for ransomware attacks that happened after the breach. However, they may settle to avoid costly litigation. Their cyber liability insurance and errors-and-omissions insurance might cover claims, which would shift the cost to their insurers. Total settlements could reach tens of millions or more depending on class action results and regulatory actions.
What credentials were stolen in the Sonic Wall breach?
The exact credentials vary by customer, but Sonic Wall's backup service stored service credentials including LDAP passwords, RADIUS shared secrets, SNMP community strings, and sometimes plaintext admin passwords. These credentials can be used to access the systems that the firewall protects, making them extremely valuable to attackers. Any organization using Sonic Wall should assume these types of credentials were potentially exposed.
How long were systems compromised before anyone discovered it?
That's unclear and probably varies by customer. Sonic Wall discovered the My Sonic Wall breach in September 2025 and publicly disclosed it relatively quickly. However, the initial compromise probably happened weeks or months earlier. For Marquis specifically, they may not have discovered the breach until much later—possibly when customers reported suspicious activity or when ransom demands appeared. This delay between compromise and discovery is a major security problem.
What should banks do if they were affected by the Marquis breach?
Affected banks should: notify all customers whose data was exposed, offer credit monitoring and identity theft protection services, conduct a complete forensic investigation, rotate all credentials that might have been compromised, implement additional monitoring for fraud activity, file breach reports with regulators, and assess whether their vendor risk management process failed in identifying the risk from Marquis's inadequate security controls. They should also review their firewall configurations and vendor relationships to prevent similar incidents.
Is this the largest data breach of 2025?
Not necessarily. We only know about this breach because multiple organizations were affected and it couldn't be kept quiet. Many breaches of similar or larger scale probably happen annually but stay private. However, because it affected the US financial system and involved state-sponsored actors, this is definitely one of the significant security incidents of 2025.
How does this breach compare to other major breaches like Equifax or Target?
The Equifax breach affected 147 million people and resulted in
What's changed in Sonic Wall's security practices since the breach?
Sonic Wall has been relatively quiet about specific remediation steps. They advised customers to change passwords and reviewed their access controls. However, they've maintained that their services are secure going forward. Independent verification of these claims is ongoing. The larger issue is that many organizations are now reevaluating whether cloud-based backup for sensitive firewall configurations is worth the risk, regardless of Sonic Wall's claims about improved security.
Use Case: Streamline your breach notification and incident response documentation by automating report generation with AI.
Try Runable For Free
Conclusion
The Sonic Wall breach and its cascade into the Marquis fintech attack reveals something we've known intellectually but often fail to act on in practice: you're only as secure as your least secure vendor.
Marquis built a service that banks depended on. Those banks placed trust in that service. That service relied on Sonic Wall's infrastructure. Sonic Wall's cloud backup got breached. And suddenly, millions of people's financial data is in criminal hands.
Every organization in that chain could have done better. Sonic Wall could have implemented stronger authentication. Marquis could have run their own backups. Banks could have demanded stronger security requirements and auditing rights.
But the deeper issue is systemic: we've created technology infrastructure where single points of failure cascade into failures affecting hundreds of organizations and millions of people. And we've mostly accepted that as normal.
The good news is that this is solvable. It requires:
- Stronger security requirements for vendors handling critical data
- Better visibility into vendor security practices
- Network architecture assuming vendors will be compromised
- Actual accountability when vendors fail
- Better information sharing about threats and vulnerabilities
The Sonic Wall breach will cost tens of millions or more. Hopefully, that cost is enough to motivate the changes we need. If not, we'll keep seeing similar incidents with bigger price tags.
For your organization right now: review your vendor dependencies. Understand which vendors have access to your critical data. Audit their security. Build your architecture assuming they'll be compromised. Make incident response drills a regular practice. And maintain your own backups of anything critical, independent of what your vendors promise.
Because the next supply chain attack could be targeting you.

Key Takeaways
- SonicWall's MySonicWall cloud backup service was breached in September 2025, exposing firewall configurations containing credentials and network topology information from potentially thousands of customers
- Marquis fintech platform, used by 70+ US banks and credit unions, was subsequently compromised likely using stolen SonicWall credentials, affecting millions of individuals' sensitive financial data
- The attack is attributed to Akira, a Russian state-sponsored ransomware group that specifically targets SonicWall infrastructure, indicating sophisticated supply chain targeting
- Marquis is pursuing legal action against SonicWall for damages, though proving direct causation between the two breaches is complex and will likely result in protracted litigation
- This incident exposes critical vulnerabilities in how organizations manage vendor security and store sensitive backup data, demonstrating the need for zero trust principles and vendor risk management
Related Articles
- Bumble & Match Cyberattack: What Happened & How to Protect Your Data [2025]
- Nike Data Breach: What We Know About the 1.4TB WorldLeaks Hack [2025]
- Microsoft Teams Phishing Attacks: How Hackers Steal Email Credentials [2025]
- Enterprise AI Security Vulnerabilities: How Hackers Breach Systems in 90 Minutes [2025]
- Okta SSO Under Attack: Scattered LAPSUS$ Hunters Target 100+ Firms [2025]
- TikTok US Outage Recovery: What Happened and What's Next [2025]



