North Korean Labyrinth Chollima Malware Splits Into Three Entities: What This Means for Global Security [2025]
Here's something that should concern your security team: one of the most dangerous threat actor groups on the planet just reorganized itself. And not in a way that makes them easier to stop.
Labyrinth Chollima, a North Korean state-sponsored operation linked to some of the most sophisticated cyberattacks in recent memory, has split into three separate entities. Each one is specialized. Each one has different targets. And each one is designed to hit harder than before.
This isn't a collapse. It's an evolution.
When security researchers from CrowdStrike analyzed this shift, they found something striking: the North Korean regime had essentially taken a massive criminal operation and broken it into three specialized divisions, each optimized for maximum impact. Golden Chollima focuses on fintech theft. Pressure Chollima targets centralized crypto exchanges. Original Labyrinth Chollima runs espionage against military and government targets.
It's a playbook straight out of corporate management—except the stakes are nuclear weapons programs and billions in stolen cryptocurrency.
TL; DR
- Labyrinth Chollima split into three units: Original Labyrinth Chollima (espionage), Golden Chollima (fintech targeting), and Pressure Chollima (crypto exchange attacks)
- Pressure Chollima led two of the largest crypto heists on record: Including thefts ranging from 120 million USD
- Targets span globally: US, Europe, South Korea, Canada, India, and Western Europe across military, government, fintech, and nuclear sectors
- Specialization increases efficiency: Each unit now has dedicated tools, tactics, and objectives rather than spreading resources thin
- Crypto theft funds nuclear ambitions: Stolen digital assets directly fund North Korea's weapons development and military expansion programs
- Fake job schemes are their entry point: LinkedIn fake jobs and fake applicants remain the primary social engineering tactic for initial access
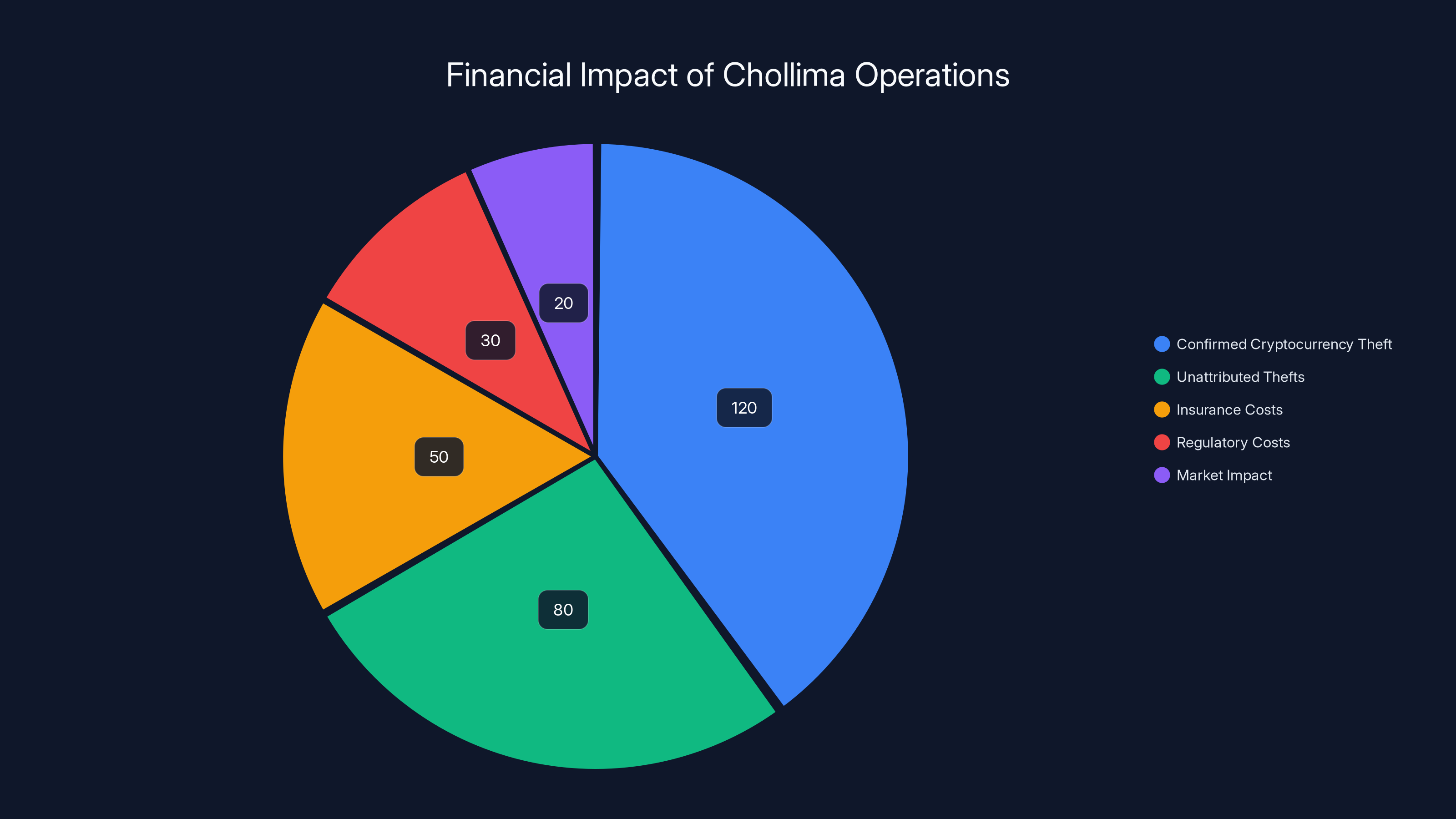
The confirmed cryptocurrency thefts by Chollima account for the largest portion of financial impact, but unattributed thefts and increased costs due to insurance and regulation also contribute significantly. Estimated data.
Understanding the Original Labyrinth Chollima Operation
Before the split, Labyrinth Chollima was a massive, all-purpose threat actor. They did everything. Espionage. Theft. Sabotage. The problem with that approach, however, is focus. When you're trying to pull off military espionage while simultaneously stealing cryptocurrency while also conducting financial fraud, something gets deprioritized.
The North Korean regime understood this. They recognized that their most valuable state actors were spread too thin.
Security researchers had tracked Labyrinth Chollima's operations dating back several years. The group had demonstrated exceptional sophistication in their attack methodology. They developed custom malware. They maintained persistent access to high-value targets. They exfiltrated sensitive information at scale.
But here's where the story gets interesting: the regime didn't disband the group. They restructured it.
The original Labyrinth Chollima unit now focuses exclusively on what it does best: intelligence gathering against military, defense, government, logistics, and nuclear organizations. Their geographic focus includes the United States, Europe, and South Korea. These are targets that require long-term access, careful operational security, and the kind of patience that only nation-state actors can afford.
The techniques they use reflect this specialization. Rather than using commodity malware that might be detected and burned quickly, they developed custom tools. Rather than conducting smash-and-grab attacks, they establish foothold access and maintain it for months or years.
What makes this unit particularly dangerous is their targeting of nuclear facilities. A successful intrusion into nuclear command and control systems could provide intelligence that informs geopolitical strategy or could enable kinetic attacks. The fact that they're willing to take this risk tells you something about how seriously the regime takes cyber capabilities.
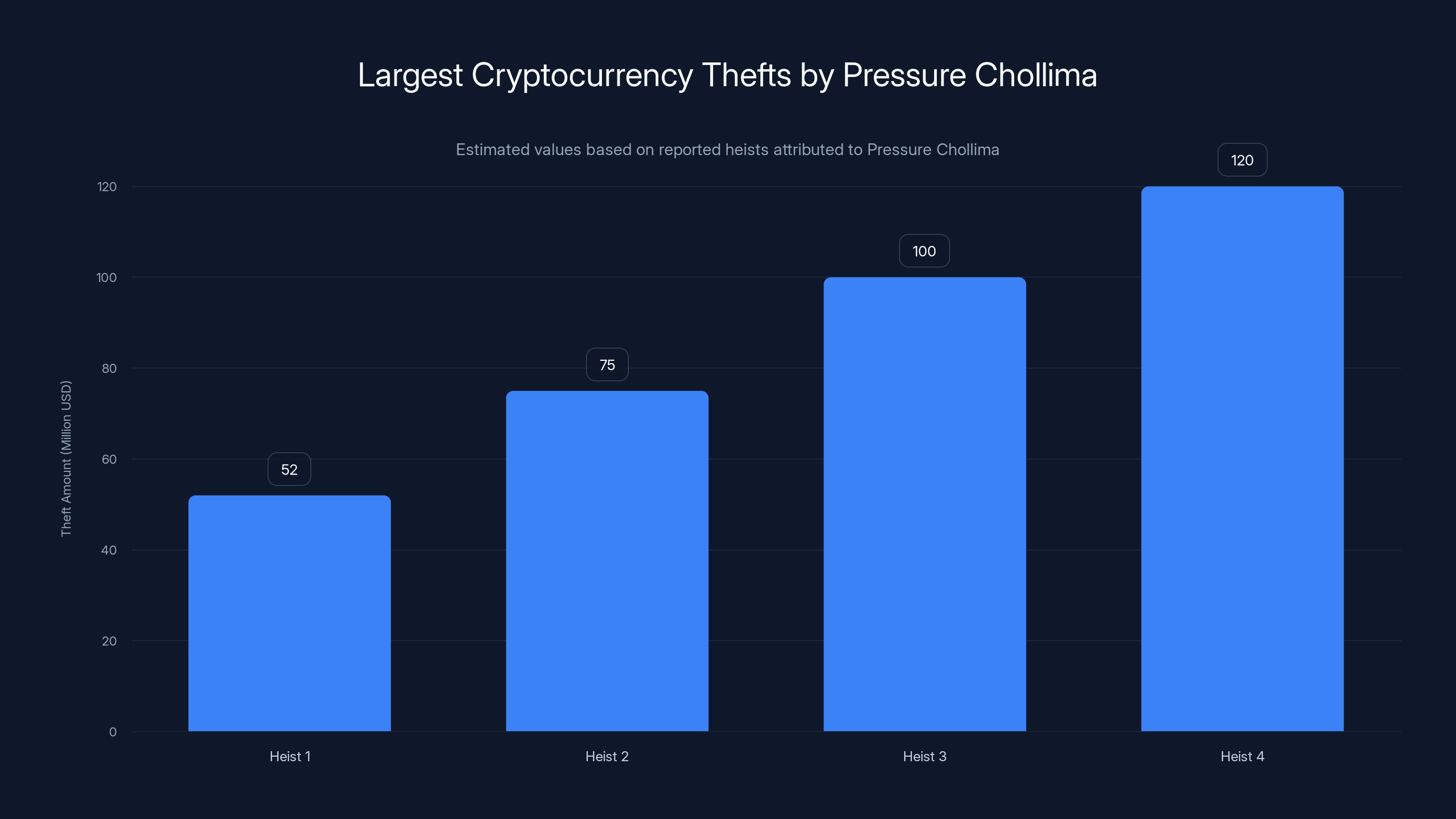
Pressure Chollima's thefts range from
The Rise of Golden Chollima: Fintech Targeting for Cryptocurrency Theft
Golden Chollima is the unit designed for a different kind of conquest: financial technology companies. This specialized branch targets smaller fintech firms across the United States, Canada, South Korea, India, and Western Europe. The objective is straightforward: steal cryptocurrency at scale.
What's notable here is the specificity of their targeting. They're not going after massive exchanges like Binance or Coinbase (that's Pressure Chollima's job). Instead, they're targeting smaller, sometimes less-defended fintech startups. These companies often have cryptocurrency holdings, customer funds, or access to blockchain systems that can be exploited.
The methodology is sophisticated. Golden Chollima doesn't just brute force their way into these targets. They use social engineering, credential compromise, and supply chain attacks. They establish persistent access and live off the land using legitimate administrative tools that won't trigger security alerts.
Once inside, they move laterally through the network. They identify where cryptocurrency is stored, how it's accessed, and what systems control the keys. They establish backup access points so that even if one entry vector is discovered, they can return.
Then they steal.
The financial impact is real. While Pressure Chollima made headlines for massive exchange heists, Golden Chollima's distributed theft across many smaller targets aggregates into substantial losses. Victims often don't disclose theft publicly due to regulatory or business reasons, so the true financial impact remains hidden.
What makes Golden Chollima's focus on fintech significant is that it represents a deliberate strategy. The regime recognized that smaller targets are easier to compromise than massive exchanges with robust security. By diversifying their target set, they've actually increased their overall success rate and reduced the risk of a single failure.

Pressure Chollima: The Crypto Exchange Specialists
Pressure Chollima is where things get serious. This unit is responsible for the North Korean regime's most ambitious cryptocurrency heists. We're talking about the two largest cryptocurrency thefts on record, period.
Unlike Golden Chollima, which targets fintech firms, Pressure Chollima goes straight for the exchanges themselves. Centralized cryptocurrency exchanges handle billions in digital assets. They have substantial security budgets. They employ security professionals. And yet, Pressure Chollima has still managed to compromise them repeatedly.
The confirmed thefts attributed to Pressure Chollima range from
The techniques Pressure Chollima uses reflect the scale of the challenge they're facing. These aren't simple SQL injections or default credentials. They're conducting sophisticated reconnaissance. They're identifying third-party vendors that connect to exchange infrastructure. They're finding zero-day vulnerabilities in systems that exchanges rely on.
Once they've established initial access, they conduct what's called "living off the land" operations. They use legitimate tools built into Windows, Linux, or the exchange's own infrastructure to move laterally. This makes them incredibly difficult to detect because every action looks like normal administrative activity.
Once they've located cryptocurrency holdings, they face another challenge: how do you move billions in digital assets without triggering security alerts? The answer is staging. They move cryptocurrency in small batches to intermediary wallets. They wait. They route it through various exchanges and mixing services. They eventually get it to North Korean-controlled addresses where it can be converted to fiat currency or used directly.
What makes Pressure Chollima distinct from other cryptocurrency-focused threat actors is their willingness to conduct smash-and-grab operations. Many cybercriminals prefer stealth. They establish persistent access and slowly exfiltrate data. Pressure Chollima sometimes just takes what they need and disappears. This suggests they have operational objectives beyond pure financial gain, likely related to time-sensitive military or geopolitical goals.
The psychological impact on the exchange industry is substantial. When a major exchange gets hit, it affects market confidence. Insurance costs rise. Security budgets increase industry-wide. Customers move funds to what they perceive as safer platforms. This ripple effect amplifies the impact beyond just the immediate financial theft.
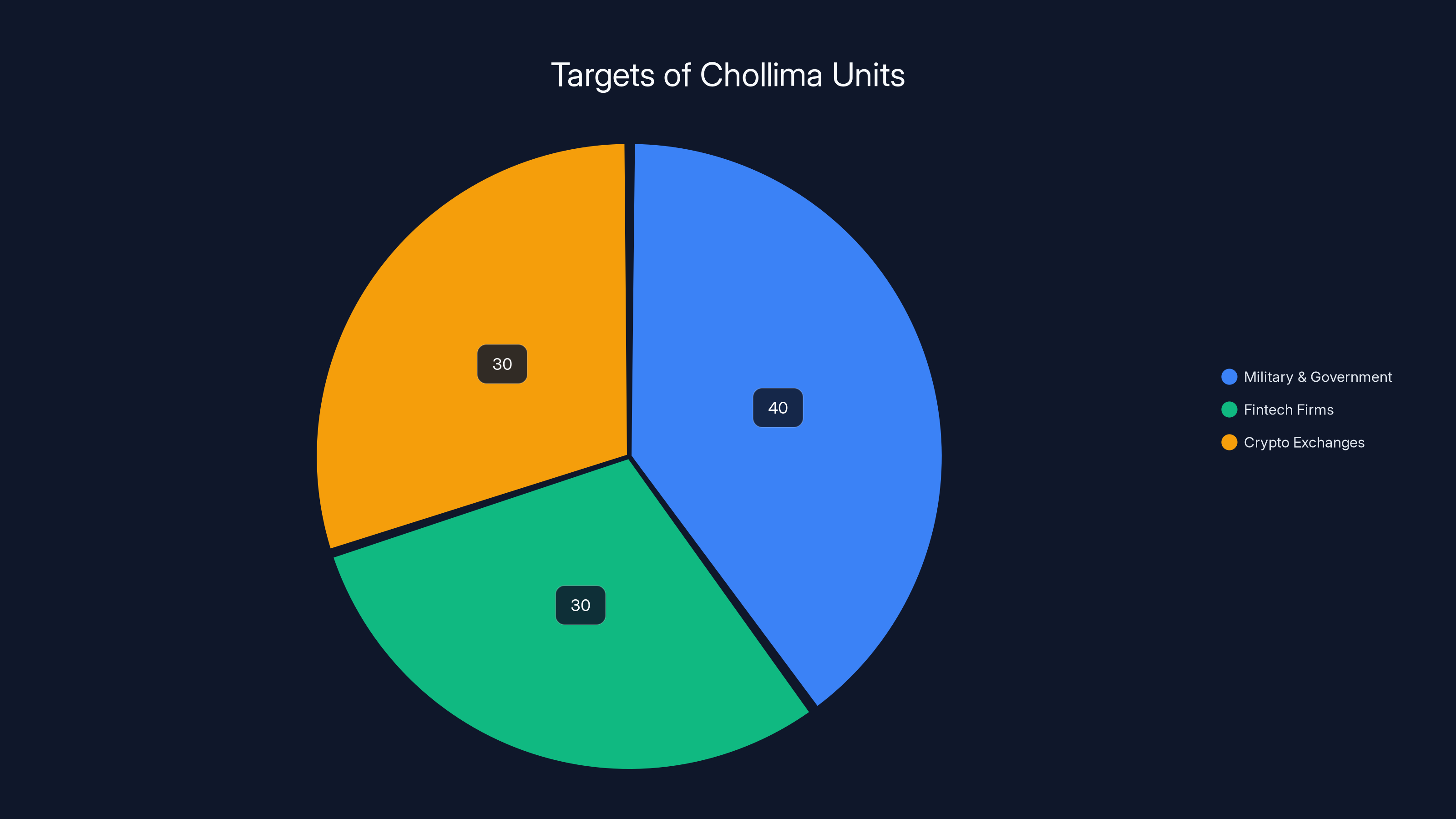
The Chollima units have diversified their focus with Labyrinth Chollima targeting military and government, Golden Chollima focusing on fintech firms, and Pressure Chollima attacking cryptocurrency exchanges. Estimated data.
Why North Korea Needed This Reorganization
The strategic decision to split Labyrinth Chollima into three units reflects several sophisticated calculations made by North Korean leadership.
First, specialization improves efficiency. A team focused exclusively on military espionage can develop expertise in that specific domain. They learn the defensive postures of military networks. They study the personnel who work in those environments. They identify the vendors and contractors that have access. This depth of knowledge translates directly to higher success rates.
Second, operational security improves when operations are compartmentalized. If Pressure Chollima gets partially burned by a law enforcement takedown or intelligence agency exposure, Golden Chollima and original Labyrinth Chollima operations continue uninterrupted. The compromise of one unit doesn't cascade to the others.
Third, and perhaps most importantly, it allows for simultaneous operations at different scales. Original Labyrinth Chollima can conduct months-long espionage operations that require patience and subtlety. Meanwhile, Golden Chollima and Pressure Chollima can execute faster, more aggressive theft operations. Both approaches serve different strategic objectives.
North Korea's economic situation makes this crystal clear. The regime faces substantial international sanctions. Traditional revenue sources are blocked. The regime requires hard currency to fund its military programs. These include building new destroyers, constructing nuclear-powered submarines, and launching reconnaissance satellites.
These aren't small expenses. A modern naval destroyer costs hundreds of millions of dollars. Submarine construction requires multi-year, multi-billion dollar investments. Satellite programs demand sustained R&D funding. Cryptocurrency theft is one of the few revenue streams available to the regime that doesn't rely on traditional trade or sanctions evasion.
The reorganization also sends a message internally within the regime. It shows competent management. It shows optimization and strategic thinking. In the North Korean context, where perceptions of strength and competence influence domestic political stability, this kind of organizational restructuring demonstrates that the regime's cyber capabilities are growing, not stagnating.

The Malware Arsenal: Tools of the Trade
Each of the three Chollima units uses specific malware and tools tailored to their operational objectives. Understanding these tools provides insight into how sophisticated the North Korean cyber program has become.
Original Labyrinth Chollima relies heavily on custom-developed espionage tools. These are often fileless malware, meaning they execute in memory without touching the disk, making them much harder to detect and analyze. They develop backdoors that allow for remote command execution. They create credential harvesters that steal usernames and passwords.
But what's particularly interesting is how they package these tools. They don't just dump malware onto a system and hope it works. They customize it for specific targets. If they're infiltrating a government network running Windows 2012 R2, they ensure their tools work on that specific operating system version. If they're targeting a Unix-based nuclear facility, they develop appropriate tools for that environment.
Golden Chollima's toolkit is somewhat different. They rely more heavily on legitimate security tools that have been repurposed for attack. They use PowerShell scripts to execute commands. They use Windows Scheduled Tasks to establish persistence. They might use legitimate remote access tools like TeamViewer or AnyDesk that they've compromised to maintain access to fintech networks.
The advantage here is that these tools are noisy in terms of security event logs, but they're not suspicious in themselves. When a security analyst sees a PowerShell script running on a server, it might trigger an alert, but it's not necessarily malicious. Golden Chollima banks on the fact that security teams are overwhelmed with alerts and might deprioritize this one.
Pressure Chollima's toolset is specifically designed for speed and cryptographic operations. They need tools that can interact with blockchain systems. They need cryptocurrency wallet management capabilities. They need tools that can identify and exfiltrate private keys. They've developed custom tools that interface with exchange APIs and blockchain networks in ways that optimize for quick theft and movement of stolen assets.
They also use proxy and VPN services extensively. Every connection they make to a target is routed through multiple proxy layers, often using legitimate commercial VPN services mixed with compromised infrastructure. This makes attribution difficult and makes it harder for defenders to block their traffic at the network perimeter.
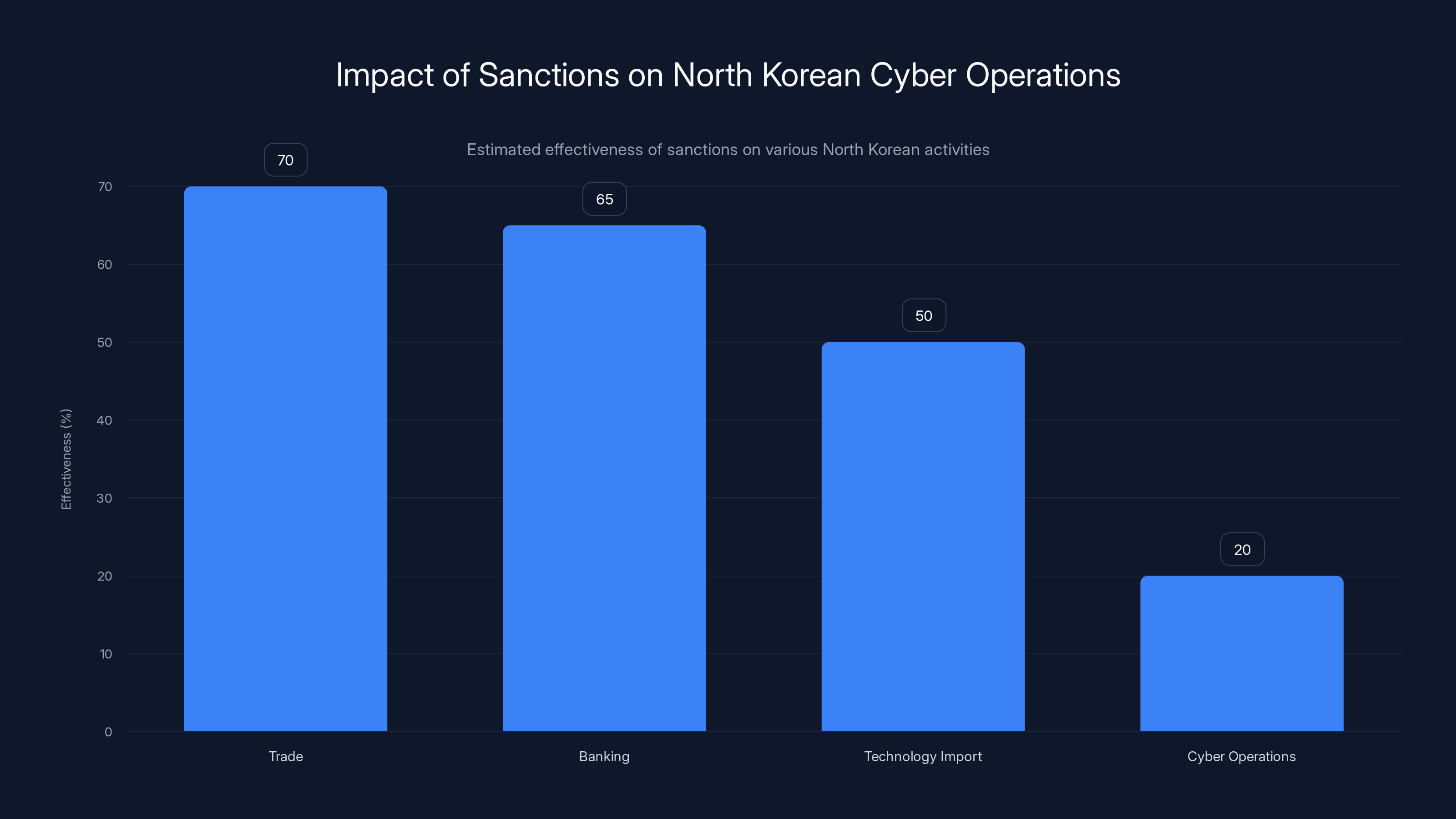
Sanctions are more effective on traditional economic activities like trade and banking than on cyber operations, which remain largely unaffected. Estimated data.
The Social Engineering Foundation: Fake Jobs and Fake Employees
Here's the thing that often gets overlooked in discussions of advanced nation-state cyber operations: they all start with something remarkably simple. A fake job posting.
Labyrinth Chollima, like other North Korean threat actors including the Lazarus Group, runs extensive social engineering campaigns on LinkedIn. They create fake company profiles. They post fake job openings. They're hiring for "security researchers," "cloud engineers," or "DevOps specialists." These positions don't exist. But the profiles look real.
They also create fake employee profiles. These are accounts that impersonate legitimate employees at target companies. A hacker might create an account that looks like it belongs to a mid-level engineer at a fintech company, complete with fabricated work history and stolen profile photos.
When legitimate employees at fintech companies or technology firms see these fake job postings, they click through. They see an opportunity. Maybe they're looking for a new role. Maybe they're just curious. The hackers strike up a conversation. They build rapport. They discuss the fake job opportunity in detail.
Then they send the candidate a link. "Please fill out this pre-screening form." The link leads to a website that looks identical to LinkedIn, but it's actually controlled by the attackers. The target enters their credentials. The attackers capture them.
Alternatively, the link might download a file. "Here's our standard employment contract for review." The file is actually a trojanized document or executable that installs malware when opened.
Once the attackers have credentials or malware access, the real exploitation begins. They use stolen credentials to access company systems. They move laterally through networks. They identify systems of interest. They establish persistent access.
The genius of this approach is that it relies on human psychology, not software vulnerabilities. You can patch a security vulnerability. You can't patch human curiosity about a job opportunity. The attackers are exploiting a fundamental aspect of how humans evaluate employment opportunities.
What's particularly concerning is that this approach works across all three Chollima units. Original Labyrinth Chollima uses fake job postings to target government and military employees. Golden Chollima uses it to target fintech employees. Pressure Chollima uses it to target exchange employees. It's not specialized. It's fundamental.
Defense against this requires continuous security awareness training. It requires explaining to employees that legitimate job opportunities won't start with unsolicited LinkedIn messages. It requires teaching people to independently verify job postings by going directly to company websites rather than clicking links from unsolicited contacts.
But honestly, this is an uphill battle. The attackers are patient. They conduct reconnaissance on LinkedIn to identify targets. They study company org charts. They identify who has access to what systems. Then they craft custom social engineering campaigns targeting specific individuals.

Geographic and Sectoral Distribution of Attacks
The geographic spread of Chollima operations is genuinely global. Original Labyrinth Chollima maintains a foothold in military and government networks across the United States, Europe, and South Korea. These are the regime's primary geopolitical adversaries, so penetrating their networks makes strategic sense.
Golden Chollima operates with a slightly different geographic profile. They target fintech companies in the US, Canada, South Korea, India, and Western Europe. The inclusion of India is interesting because it suggests they're exploiting the fintech boom happening in India. As more fintech companies are established in India, and as Indian fintech platforms gain prominence, these companies attract attention from threat actors seeking to steal cryptocurrency.
Pressure Chollima's targeting of centralized exchanges is more globally distributed. They don't care where an exchange is physically located. If it has cryptocurrency holdings worth stealing, it's a target. This means they have operations spanning North America, Europe, and Asia.
The sectoral distribution is also instructive. Original Labyrinth Chollima targets military, defense, government, logistics, and nuclear sectors. These are sectors critical to national security. Penetrating these networks provides intelligence that informs military strategy, defensive posture, and weapons development.
Golden Chollima targets fintech firms specifically. Not banks. Not cryptocurrency exchanges necessarily. Fintech firms. These companies often have growing cryptocurrency holdings, less mature security postures than established financial institutions, and often hold customer funds or manage customer assets.
Pressure Chollima targets the exchanges themselves, plus technology companies in the west. The technology company targeting makes sense because tech companies might have cryptocurrency holdings, might conduct business with crypto clients, or might have developed tools that could be leveraged for further attacks.

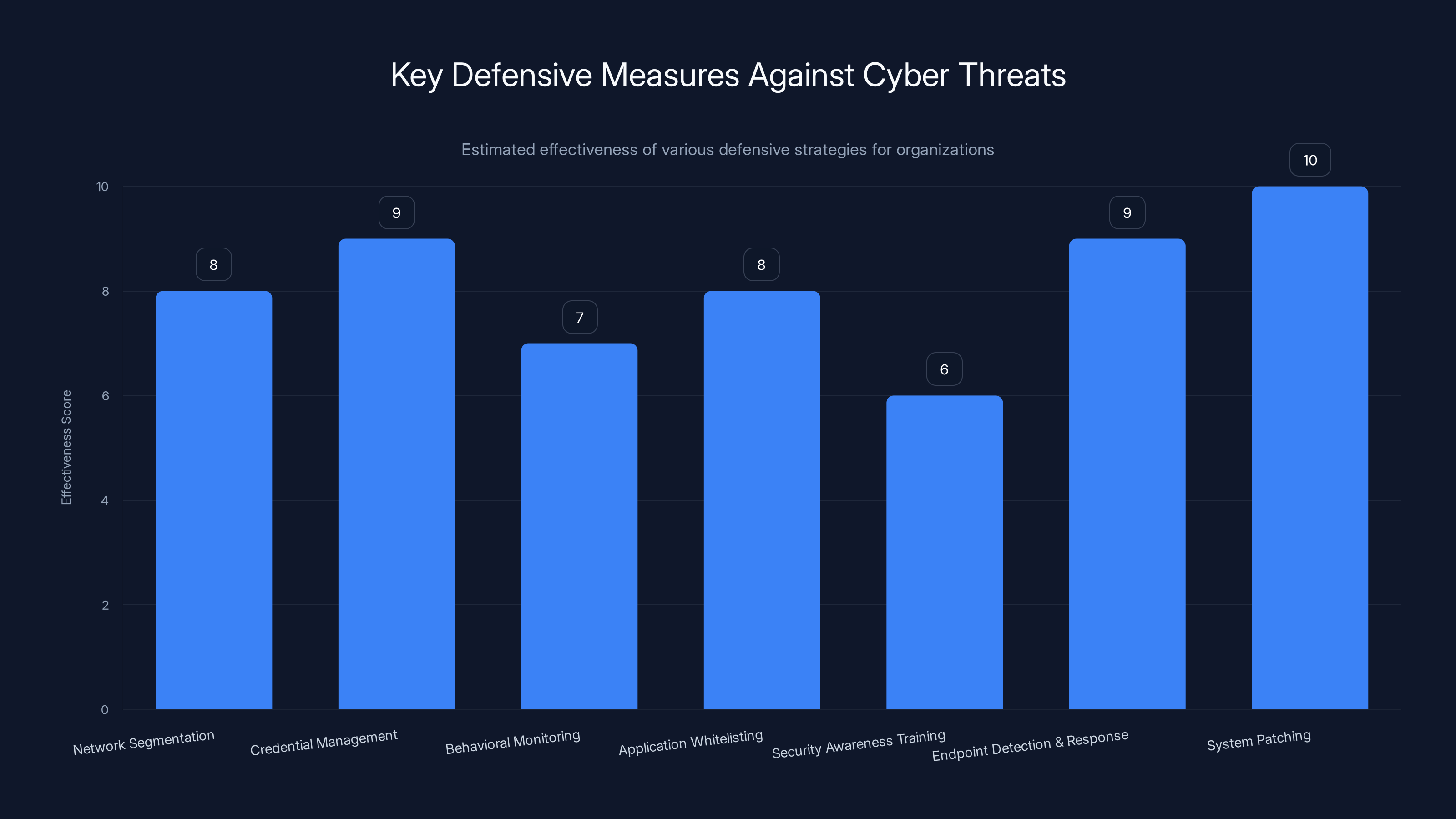
Implementing system patching and credential management are among the most effective strategies, scoring 10 and 9 respectively. Estimated data based on typical cybersecurity practices.
The Financial Impact and Damage Assessment
Quantifying the financial impact of Chollima operations is challenging because not all theft is publicly disclosed. However, the confirmed figures are staggering.
Pressure Chollima alone is responsible for the two largest cryptocurrency thefts on record. The exact amounts vary by source, but confirmed theft attributions range from
But cryptocurrency theft is just the direct financial impact. There are secondary impacts that ripple through the ecosystem.
When an exchange gets compromised, it typically has to halt trading temporarily while it assesses the breach. This creates market uncertainty. Trading volumes drop across the industry. Customers move funds to perceived safer exchanges, which creates capital flight that disadvantages the compromised exchange.
Insurance costs rise. Exchanges now carry cyber insurance policies that are significantly more expensive than they were before widespread nation-state attacks. These costs get passed to customers in the form of higher trading fees or reduced features.
Regulatory costs also increase. Exchanges that have been breached face increased regulatory scrutiny. They have to hire security consultants. They have to implement additional monitoring. They have to file breach disclosure reports. All of this costs money.
From the perspective of the broader cryptocurrency ecosystem, nation-state theft reduces confidence in decentralized finance security. It suggests that even the largest, best-funded exchanges can't necessarily prevent nation-state attacks. This creates hesitation among institutional investors considering cryptocurrency investments.
For North Korea specifically, the stolen cryptocurrency represents liquidity that can be converted to fiat currency and used to purchase goods and services that circumvent international sanctions. It can fund military development. It can support the regime's leadership. In this sense, the financial impact extends far beyond simple theft into geopolitical consequences.
How Each Unit Maintains Operational Security
Operational security is paramount for state-sponsored threat actors. Getting caught doesn't just mean legal consequences. It means diplomatic incidents. It means potential military response. It means loss of capability that took years to develop.
Each Chollima unit uses different operational security practices tailored to their specific risk profile.
Original Labyrinth Chollima uses traditional spy craft operational security measures. They minimize digital footprints. They use proxy infrastructure heavily. They route all traffic through multiple layers of anonymization. They avoid using the same malware tools across different targets because burning a tool means rewriting it from scratch.
They also use a "clean hand" approach where different teams within the unit operate entirely separately. If one team is discovered, the others continue unaffected. They share no tools. They use no shared infrastructure. They communicate rarely if at all.
Golden Chollima operates with slightly less restriction because the targets are less likely to have military-grade defensive capabilities. However, they still use proxy infrastructure. They route their traffic through VPNs and compromised systems. They instrument their malware with kill switches that activate if they detect they're being analyzed in a sandbox environment.
Pressure Chollima faces the highest security risk because exchanges are specifically focused on identifying and blocking attacks. They use cryptocurrency mixing services that tumble stolen assets through multiple transactions before moving them to final addresses. This makes tracing the origin of the theft difficult.
They also use cryptocurrency exchanges themselves as intermediaries. They move stolen assets to exchanges, convert them to different cryptocurrencies, move them to different exchanges, and repeat the process multiple times. Each exchange acts as a washing machine for the assets, obscuring the original theft source.
All three units use what's called "infrastructure diversification." Rather than using a single set of servers for command and control, they use dozens or hundreds of compromised systems. They rotate through these systems regularly. They make sure that taking down one server doesn't significantly impact their operations.

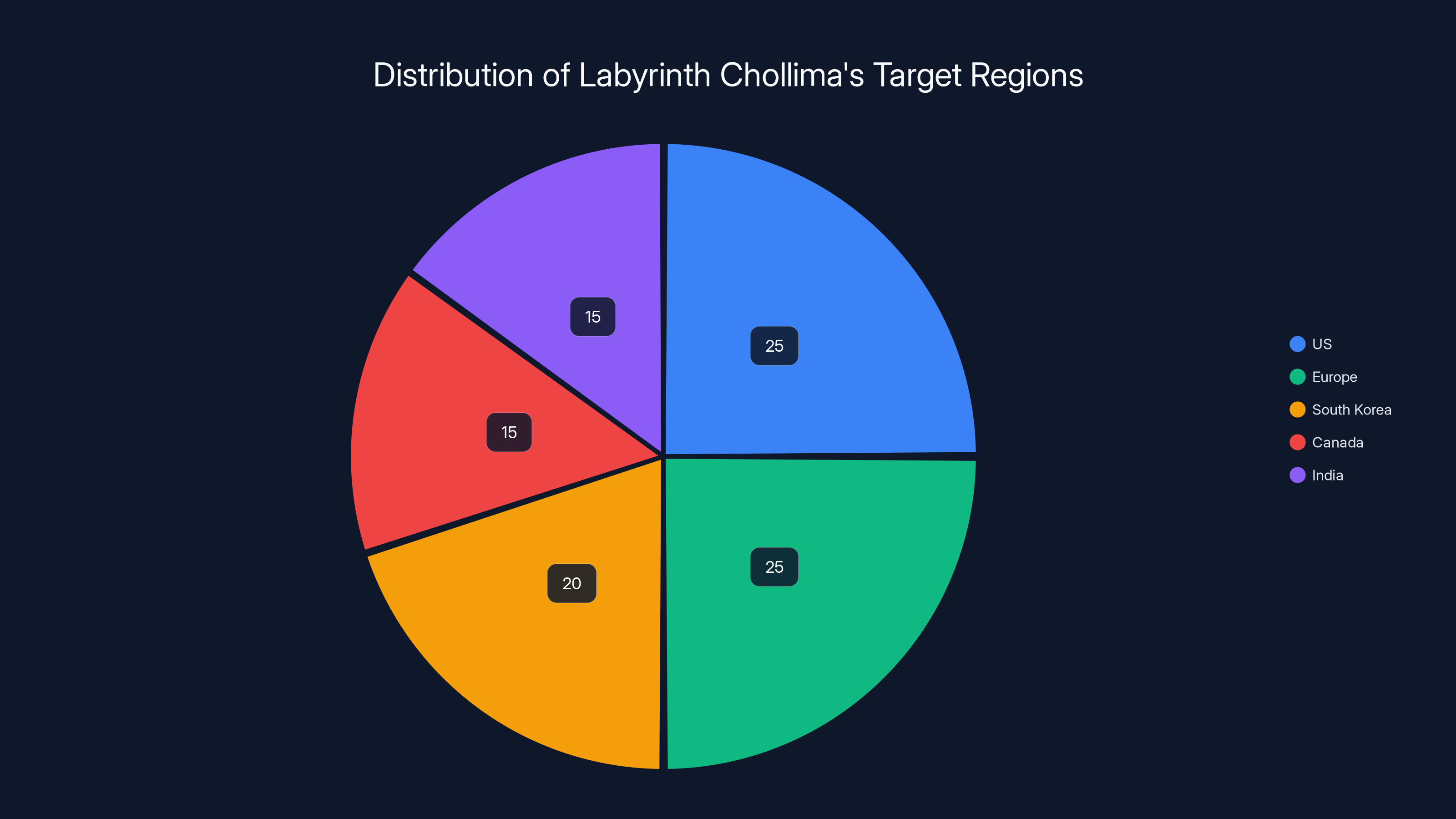
Estimated data suggests that Labyrinth Chollima's operations are evenly distributed across the US and Europe, with significant activities in South Korea, Canada, and India.
Detection and Attribution Challenges
One of the reasons Chollima has been so successful is that detection and attribution are genuinely difficult.
Detection is hard because each unit has grown increasingly sophisticated in avoiding detection mechanisms. Original Labyrinth Chollima uses fileless malware and legitimate administrative tools. Golden Chollima does the same. Defensive systems are tuned to detect suspicious files and unusual network traffic. When attackers avoid creating new files and use legitimate administrative tools, detection becomes much harder.
Attribution is hard because Chollima uses proxy infrastructure that obscures the origin of attacks. An attack on a fintech company might appear to come from an IP address in Eastern Europe. But that IP address is actually a compromised system in an Eastern European hosting provider. Tracing it back to the true origin requires following multiple layers of proxy infrastructure.
However, there are attribution techniques that work. One is malware analysis. Even when malware is obfuscated and encrypted, security researchers can analyze it to find commonalities with previous attacks. They can identify coding patterns, architectural choices, and functional elements that are unique to specific threat actors.
Another attribution technique is infrastructure analysis. Even though Chollima uses proxy infrastructure, analysts can sometimes identify patterns in how that infrastructure is registered, maintained, and used. If the same infrastructure is used across multiple attacks, it provides a thread of attribution.
A third technique is targeting pattern analysis. If attacks on fintech companies in specific regions follow patterns consistent with Golden Chollima's previous targeting, analysts can make attribution based on the pattern rather than the attack itself.
A fourth technique, which is more controversial, is linguistic analysis. Threat actors sometimes leave text strings, comments, or messages in their malware. These can be analyzed for language patterns, time zone indicators, or other clues that point to the threat actor's origin.

The Broader North Korean Cyber Ecosystem
Labyrinth Chollima exists within a broader North Korean cyber ecosystem that includes other threat actors. The most prominent is the Lazarus Group, which is actually an overarching name for multiple North Korean threat actors including Chollima units.
Lazarus is known for the Sony Pictures hack in 2014, the Bangladesh Bank heist in 2016, and WannaCry ransomware in 2017. Lazarus operations are generally flashier and more destructive than Chollima operations. They're willing to cause damage just for publicity or political purposes.
Chollima is more surgical. The objective is to steal assets or gather intelligence without being detected. They're less interested in causing embarrassment to the target and more interested in sustained exploitation.
There's likely command and control relationships between Lazarus and Chollima, but the exact organizational structure isn't public. It's possible that Lazarus is a more aggressive unit and Chollima is a more conservative unit, and they coordinate at higher levels within the North Korean regime.
Other North Korean threat actors include Kimsuky, which focuses on espionage, and Andariel, which focuses on financially motivated attacks. Together, these groups represent a comprehensive threat to virtually every sector of every nation's economy.
The coordination between these groups is what makes the North Korean cyber threat so formidable. They don't compete for targets. They appear to coordinate to avoid stepping on each other's operations. They likely share intelligence and capabilities.
The regime has invested substantial resources into developing this cyber capability over more than a decade. The sophistication level is now comparable to or exceeding the capabilities of many private cybersecurity firms. The difference is that these state-sponsored actors have unlimited patience and funding.

Defensive Implications and How Organizations Should Respond
Understanding how Chollima operates provides concrete guidance for defensive measures.
First, implement network segmentation. Don't have all your critical systems on a flat network where an attacker can move laterally from one compromised system to any other. Segment critical infrastructure. Segment cryptocurrency systems. Segment financial systems. Make lateral movement as difficult and time-consuming as possible.
Second, implement credential management solutions. Use single sign-on where possible. Use multi-factor authentication for critical systems. Use passwordless authentication where it's technically feasible. Force password changes on reasonable intervals. Monitor for suspicious credential usage patterns.
Third, implement behavioral monitoring. Watch for unusual administrative activity. Watch for large data exfiltration. Watch for connections to unusual external systems. Use machine learning-based tools that can identify patterns that deviate from normal operational baselines.
Fourth, implement application whitelisting. If only approved applications are allowed to run, then malware that requires execution of new binaries can't function. This forces attackers to use legitimate administrative tools, but at least you can monitor which legitimate tools are being used and when.
Fifth, conduct security awareness training specifically focused on social engineering. Make it clear to employees that legitimate job opportunities won't start with LinkedIn messages. Teach them to verify job opportunities independently.
Sixth, implement endpoint detection and response solutions. These tools monitor system behavior and can detect malware-like activity even if the specific malware isn't known. They can detect process injection, privilege escalation, and other suspicious behaviors.
Seventh, keep systems patched. Many attacks exploit known vulnerabilities. If systems are patched promptly, many attack vectors are eliminated. This won't stop determined nation-state actors, but it raises their cost and effort.
Eighth, implement incident response planning before you need it. Know who to call if you suspect a breach. Know what forensic preservation measures need to be taken. Know how to communicate with incident response teams, law enforcement, and regulatory bodies.
Ninth, conduct regular penetration testing. Bring in third-party experts to try to break into your systems. Learn where your weaknesses are before attackers do.
Tenth, implement cryptocurrency-specific security measures if your organization handles cryptocurrency. Use hardware security modules. Use threshold cryptography where no single person or system can move assets. Implement multi-signature requirements. Require additional approval layers for unusual transactions.
The Role of International Sanctions and Their Limitations
The international community has imposed extensive sanctions on North Korea in an attempt to constrain the regime's behavior. But here's the frustrating reality: sanctions have had limited impact on cyber operations.
Traditional sanctions focus on trade, banking relationships, and specific sectors. But cyber operations require minimal traditional resources. You need a few hundred skilled computer scientists. You need internet connectivity. You need some server infrastructure. These can be obtained even under sanctions.
North Korea maintains internet connectivity through Chinese internet service providers and other backdoor channels. They can acquire used servers and networking equipment on the gray market. They can recruit computer science talent from outside North Korea. The regime has been doing this for years.
Sanctions might prevent North Korea from importing certain technologies or conducting certain types of trade, but they don't prevent cyber operations. If anything, cyber operations are part of the regime's response to sanctions. When traditional economic resources are blocked, the regime turns to cyber theft.
Law enforcement agencies in the US, Europe, and other countries have indicted North Korean hackers and issued arrest warrants. But extradition is impossible because North Korea doesn't have extradition treaties with the countries pursuing them. The indictments serve more as warnings and ways to alert allies to the threat than as actual enforcement mechanisms.
The more effective response, arguably, is intelligence sharing. When one country detects Chollima operations, sharing that information with allies allows them to harden their defenses. When multiple countries are aware of a specific attack methodology, they can deploy defensive measures simultaneously.
Another response is attribution and public shaming. When the US or other countries publicly attribute attacks to North Korean actors, it raises the reputational cost to the regime. It makes it harder for North Korea to deny responsibility for malicious cyber activities. It potentially influences other nations' perceptions of North Korea's intentions and threat level.

Future Evolution and Emerging Threats
The split of Labyrinth Chollima into three units suggests that North Korea is thinking strategically about long-term cyber operations. They're not trying to smash and grab. They're trying to build sustainable capabilities.
Looking forward, we can expect several developments.
First, further specialization. North Korea might eventually create additional units focused on specific sectors or specific attack methodologies. They might create a unit focused exclusively on supply chain attacks. They might create a unit focused on IoT device compromise. They might create a unit focused on cryptocurrency wallet compromise. Each specialization increases efficiency and effectiveness.
Second, increased use of artificial intelligence. Threat actors are already using machine learning for malware development, defense evasion, and targeting optimization. North Korea is likely investing in AI capabilities to automate parts of their attack pipeline. This would allow them to scale their operations beyond what's currently possible with human-only operations.
Third, more supply chain attacks. Rather than attacking targets directly, attackers are increasingly targeting the software and services that those targets depend on. North Korea might target a cryptocurrency wallet provider, a cryptocurrency hardware manufacturer, or a cloud service provider that exchanges rely on. This provides access to a large target set with a single attack.
Fourth, more cryptocurrency innovation targeting. As the cryptocurrency industry innovates, threat actors like Pressure Chollima will develop new attack methodologies to target those innovations. As decentralized finance grows, it will become a new target area. As cross-chain bridges are developed, those will be targeted.
Fifth, increased targeting of critical infrastructure. Currently, Original Labyrinth Chollima focuses on military and government. But critical infrastructure like power grids, water treatment plants, and transportation systems are also attractive targets. A successful attack on critical infrastructure could cause physical damage and loss of life.
This evolution will require that defenders also evolve. It's an arms race, and there's no indication it's slowing down.

Industry-Specific Implications
Different industries face different risks from Chollima operations.
For the cryptocurrency and fintech industry, the risk is existential. If exchanges can't secure customer funds against nation-state attacks, customer confidence erodes. This could eventually drive customers away from centralized exchanges toward decentralized alternatives, which has its own set of tradeoffs.
For the defense and military sectors, the risk is intelligence loss. Compromised networks could expose military strategies, weapons capabilities, personnel information, and logistical details. This information can inform North Korean military planning.
For the nuclear industry, the risk is operational compromise. A successful attack on nuclear command and control systems could provide opportunities for sabotage or could inform North Korean nuclear strategy.
For government agencies, the risk is similar to the military: intelligence loss and potential operational compromise.
For other technology companies, the risk is being used as a stepping stone to other targets. North Korea might compromise a cloud provider not because they care about the provider's data, but because the provider has connectivity to other targets of interest.
For logistics and supply chain companies, the risk is operational disruption and intelligence loss about supply chains that support government or military operations.
Each industry needs to understand its specific risk profile and implement defenses accordingly.
The Economics of State-Sponsored Cyber Operations
One question that often doesn't get asked is: what's the return on investment for these operations?
For Pressure Chollima, the ROI is clear. They steal billions of dollars. The investment required to conduct these operations is trivial compared to the return. Even if it costs millions of dollars per year to maintain the Pressure Chollima unit, the return is 100x or more on that investment.
For Golden Chollima, the ROI is also positive but smaller in scale. The thefts are smaller and more distributed, but the investment required is also smaller. A successful compromise of a fintech company might yield millions of dollars.
For Original Labyrinth Chollima, the ROI is harder to quantify because the benefit isn't direct financial gain. The benefit is intelligence. How much is intelligence about US military capabilities worth? How much is intelligence about nuclear weapons programs worth? These are strategic questions that are difficult to answer in purely financial terms.
But from the regime's perspective, the total ROI is clearly positive. The regime is willing to fund these operations extensively, which suggests they believe the returns justify the investment.
This also explains why the regime hasn't reduced cyber operations in response to international pressure. The operations are profitable. They're strategically valuable. They're sustainable. There's no incentive to stop.
Conclusion: The New Normal of State-Sponsored Cyber Operations
The split of Labyrinth Chollima into three entities represents a milestone in state-sponsored cyber operations. It's not the first time a threat actor has specialized. But it's one of the most prominent and well-documented examples of a massive state-sponsored operation deliberately restructuring for maximum impact.
This reorganization tells us several important things about the future of cyber threats.
First, nation-states are serious about cyber operations. They're investing in long-term capability development. They're optimizing their operations. They're thinking strategically about how to achieve their objectives efficiently.
Second, specialization works. By breaking into three units with distinct objectives, North Korea has likely increased their overall success rate and reduced their operational risk.
Third, cyber theft is a viable revenue stream for sanctioned nations. As long as cryptocurrency exists and can be stolen and converted to fiat currency or used directly to purchase goods and services, North Korea will continue to operate these cyber units.
Fourth, defending against nation-state cyber operations is incredibly difficult. You're defending against opponents with unlimited patience, substantial resources, advanced skills, and nothing to lose if they fail.
But here's the thing that should drive action: defenders have advantages too. They control the network. They control the systems. They can implement multiple layers of defense. They can require attackers to have perfect operational security indefinitely. Eventually, that breaks down. They slip up. They get caught.
The question isn't whether the threat is real. It is. The question is whether organizations will take the necessary steps to defend themselves. The technical solutions exist. The frameworks exist. What's required is commitment. Commitment to implementing defense in depth. Commitment to continuous monitoring. Commitment to keeping systems patched and updated. Commitment to security awareness training.
Labyrinth Chollima's reorganization is a shot across the bow. It says: "We're getting better. We're optimizing. We're coming for your cryptocurrency, your military secrets, your nuclear intelligence."
The right response is to take that threat seriously and implement defenses accordingly.

FAQ
What is Labyrinth Chollima?
Labyrinth Chollima is a North Korean state-sponsored threat actor group that conducts sophisticated cyberattacks targeting military, government, fintech, and cryptocurrency exchange organizations worldwide. The group recently split into three specialized units: original Labyrinth Chollima (espionage), Golden Chollima (fintech targeting), and Pressure Chollima (crypto exchange attacks) to improve operational efficiency and specialization.
Why did Labyrinth Chollima split into three separate entities?
The reorganization represents a strategic evolution that allows each unit to specialize in specific targets and objectives. Specialization improves operational focus, reduces risk through compartmentalization, enables simultaneous operations at different scales and tempos, and ultimately increases the success rate and efficiency of North Korean cyber operations. Each unit can now develop deeper expertise in their specific domain.
What are the three new Chollima units and their targets?
The original Labyrinth Chollima unit conducts cyber-espionage against military, defense, government, logistics, and nuclear organizations primarily in the US, Europe, and South Korea. Golden Chollima targets small fintech firms across the US, Canada, South Korea, India, and Western Europe to steal cryptocurrency. Pressure Chollima attacks centralized cryptocurrency exchanges and technology companies worldwide, and has conducted the two largest cryptocurrency heists on record with confirmed thefts ranging from
How much money has Pressure Chollima stolen from cryptocurrency exchanges?
Pressure Chollima has been confirmed responsible for the two largest cryptocurrency thefts on record, with documented theft amounts ranging from
What social engineering tactics do Chollima groups use?
Chollima units extensively use fake job postings and fake employee profiles on LinkedIn to target employees at government agencies, military organizations, fintech companies, and cryptocurrency exchanges. They create convincing company profiles and job postings, initiate conversations with targets, build rapport, and then either trick targets into entering credentials on fake login pages or send trojanized documents and files that install malware when opened.
Why does North Korea conduct cyberattacks if they're heavily sanctioned?
North Korea uses cyber operations as a primary revenue generation method to circumvent international sanctions and fund its military programs, including building new destroyers, constructing nuclear-powered submarines, and launching reconnaissance satellites. Cryptocurrency theft generates an estimated $200 million annually for the regime, making it one of the few viable revenue streams available to the sanctioned nation-state.
How can organizations defend against Labyrinth Chollima attacks?
Organizations should implement network segmentation to prevent lateral movement, deploy multi-factor authentication for critical systems, use behavioral monitoring and endpoint detection and response solutions, implement application whitelisting, provide targeted social engineering training to employees, keep systems patched and updated promptly, conduct regular penetration testing, develop incident response plans before breaches occur, and implement cryptocurrency-specific security measures if handling digital assets.
What makes detecting Chollima operations difficult?
Chollima units avoid detection by using fileless malware that executes in memory without touching disk, leveraging legitimate administrative tools that appear normal in security logs, routing traffic through multiple proxy layers and compromised infrastructure to obscure origin, and using infrastructure diversification with dozens of command and control nodes rotated regularly. These tactics make both detection and attribution significantly more challenging for defensive teams.
Is attribution of Chollima attacks possible?
Yes, attribution is possible through several techniques including malware analysis to identify coding patterns and architectural signatures, infrastructure analysis to find patterns in command and control node registration and usage, targeting pattern analysis to match attacks with historical Chollima operations, and linguistic analysis of text strings and comments in malware code. However, attribution requires sophisticated technical analysis and is often confirmed through international intelligence cooperation rather than public disclosure.
What are the broader implications of Chollima's reorganization?
The split into three specialized units suggests North Korea is committing to long-term sustainable cyber operations with increasing sophistication. It demonstrates the regime views cyber capability as strategically vital. It indicates future operations will likely include further specialization, increased AI and machine learning integration, more supply chain attacks, greater focus on critical infrastructure, and expanded cryptocurrency-targeting methodologies as the industry evolves.
Key Takeaways
- Labyrinth Chollima reorganized into three specialized units, each with distinct targets: original Labyrinth (military/government espionage), Golden Chollima (fintech theft), Pressure Chollima (centralized exchange attacks)
- Pressure Chollima responsible for two largest cryptocurrency thefts on record, ranging from 120 million USD per operation, funding North Korea's military programs
- Social engineering via fake LinkedIn jobs remains primary attack vector across all three units, exploiting human psychology rather than technical vulnerabilities
- Specialization improves operational efficiency while compartmentalization reduces risk, allowing simultaneous operations at different scales and geographic regions
- Defending against state-sponsored attacks requires multi-layered approach including network segmentation, behavioral monitoring, credential management, and continuous security awareness training
Related Articles
- Google's War on Residential Proxies: How IPIDEA's Network Collapsed [2025]
- WinRAR Security Flaw CVE-2025-8088: Complete Defense Guide [2025]
- 800,000 Telnet Servers Exposed: Complete Security Guide [2025]
- Fake Moltbot AI Assistant Malware Scam: What You Need to Know [2025]
- Microsoft Teams Phishing Attacks: How Hackers Steal Email Credentials [2025]
- I Tested a VPN for 24 Hours. Here's What Actually Happened [2025]
![North Korean Labyrinth Chollima Malware Splits Into Three Entities [2025]](https://tryrunable.com/blog/north-korean-labyrinth-chollima-malware-splits-into-three-en/image-1-1769792975708.jpg)



