Password Security for UK Businesses: Beyond Weak Passwords [2025]
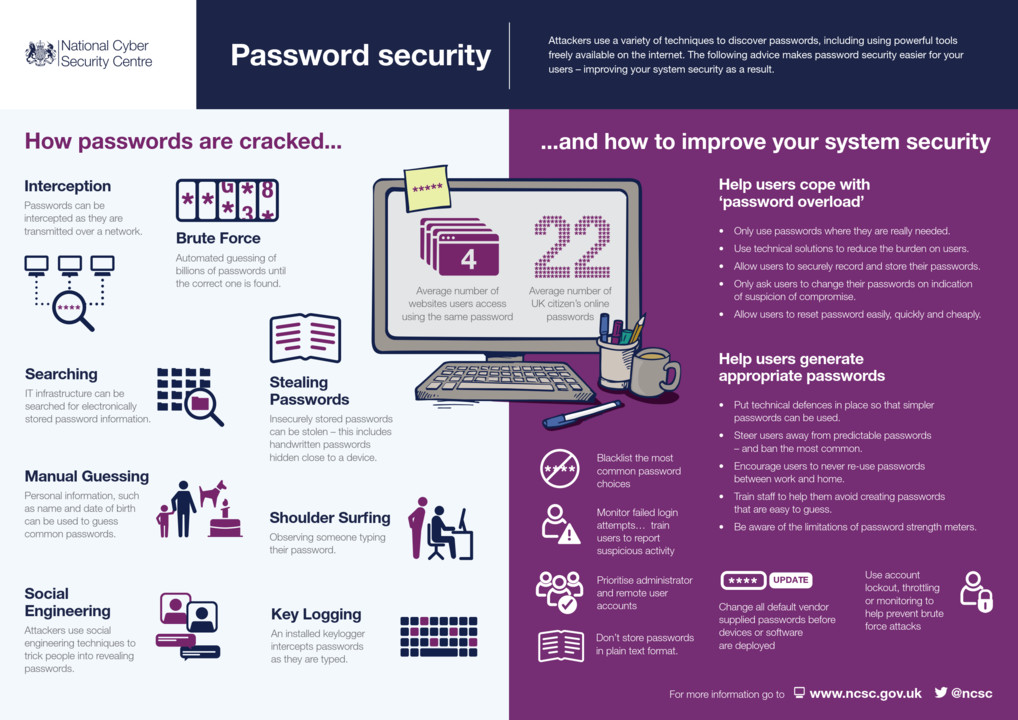
Your IT team probably has nightmares about the password "admin." Or "123456." Or worse, the one someone wrote on a sticky note under their keyboard.
It's 2025, and we're still fighting this battle. Weak, guessable passwords remain one of the easiest entry points for attackers into UK organizations. Despite years of awareness campaigns, regulatory pressure, and high-profile data breaches that make headlines for weeks, businesses across the country continue to rely on human memory and outdated practices to protect some of their most critical assets.
Here's what makes this particularly frustrating: it's not primarily a failure of education or awareness. Your employees probably know that "password 123" isn't secure. The real problem is systemic. It's organizational culture, it's policy enforcement, it's the sheer cognitive overload of managing dozens of accounts, and it's the legacy systems that still demand password-based access when better alternatives exist.
The good news? The UK National Cyber Security Centre recently published updated guidance that finally acknowledges this reality. It's shifting the burden away from individual users and toward organizations to build systems that work with human psychology, not against it. This guidance represents a fundamental rethinking of how credential management should work in 2025.
Let's break down what's actually happening in UK organizations, why passwords alone are failing, and what security leaders need to do right now to move their teams forward.
TL; DR
- Nearly 20% of UK organizations operate without formal credential management controls, using spreadsheets or hardcoded passwords instead, as highlighted by Security Boulevard.
- The average person manages 250 accounts but relies on just a handful of passwords across them, creating massive security risk, according to TechRadar.
- The NCSC's 2024 guidance explicitly recommends moving beyond password-centric security to include technical defenses, multi-factor authentication, and passwordless solutions, as noted by Industrial Cyber.
- Privileged Access Management (PAM) is critical for UK organizations but remains underdeployed across mid-market and smaller enterprises, as discussed in HIPAA Journal.
- Passkeys and passwordless authentication are finally mature enough for enterprise deployment and should be your next security investment, according to Herald Tribune.

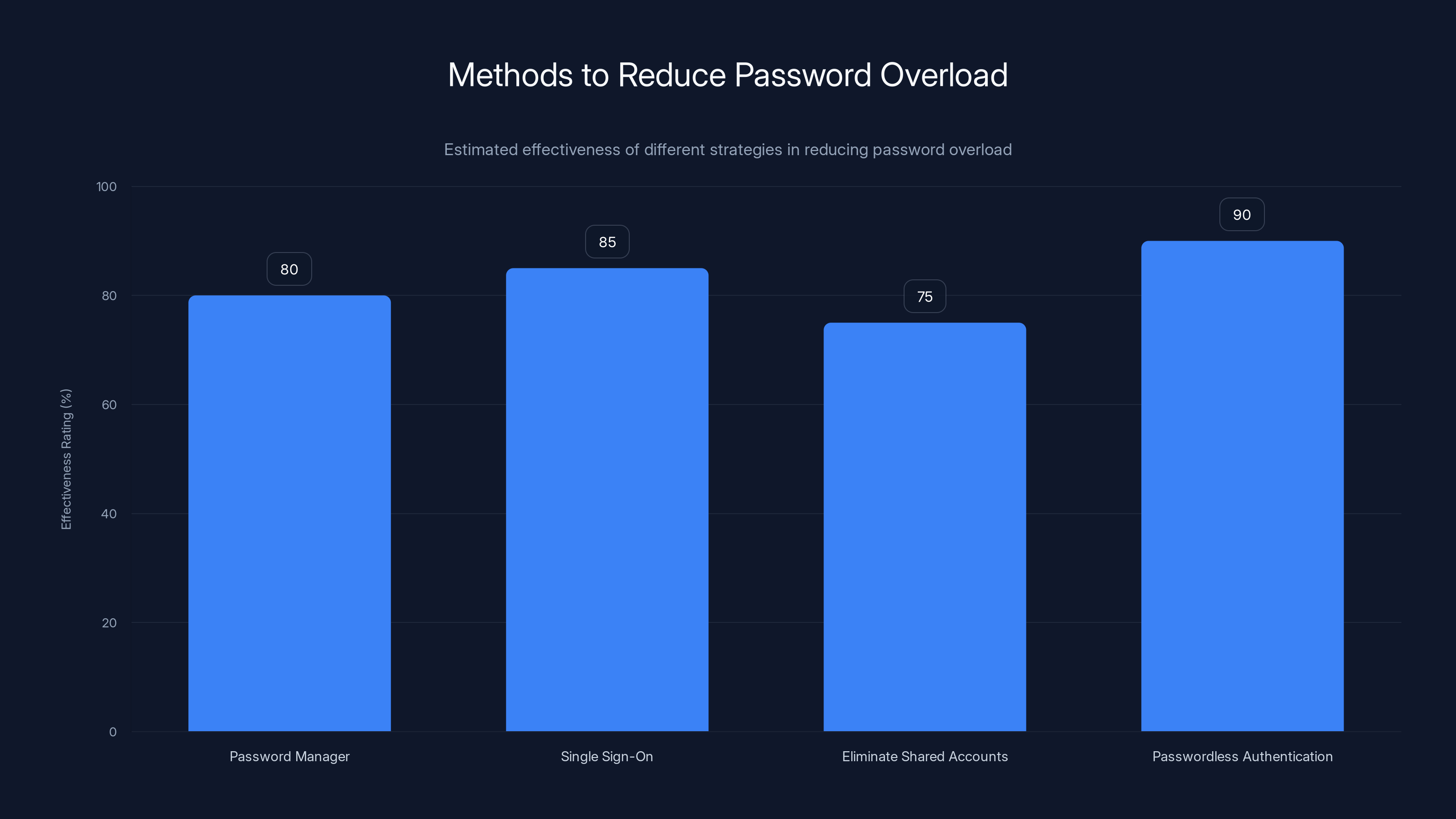
Implementing passwordless authentication and single sign-on are highly effective strategies for reducing password overload. Estimated data.
The Password Problem Is Actually a Systems Problem
When a security leader tells you that their organization has a "password problem," they're usually describing a symptom, not a cause. The real issues are hiding one level deeper.
Weaknesses in password security don't happen because people are careless. They happen because organizations have built systems that demand passwords everywhere, create impossible conditions for managing them, and then blame users when those impossible conditions create risky behaviors.
Consider what an average knowledge worker faces. They need access to email, their company's primary business application, Slack, cloud storage, project management tools, HR systems, expense management platforms, customer relationship management software, and a dozen specialized tools for their specific department. That's just the work stuff. Add in personal banking, social media, shopping sites, streaming services, and subscriptions, and you're looking at the average person managing somewhere between 100 and 250 accounts.
No human can remember 250 unique, complex passwords. It's not a character flaw. It's a mathematical impossibility.
When you build a system that demands the impossible, people will find coping mechanisms. They'll reuse passwords. They'll make patterns (Company 1!, Company 2!, Company 3!). They'll write them down. They'll use browser password managers that aren't designed for enterprise security. Some will just use the path of least resistance and choose something easy to remember.
The organizations that understand this aren't blaming their users. They're redesigning their systems.
Recent research shows that nearly one in five UK organizations still operate without any formal credential management controls whatsoever. These aren't small operations either. Many of these are established businesses managing sensitive data. Instead of using proper credential management systems, they're storing passwords in shared spreadsheets, embedding them directly in code, or maintaining no system at all. That's not a user education problem. That's a governance failure.
The password problem in UK organizations is fundamentally a leadership problem. It's about prioritizing convenience and cost savings over security architecture. It's about making system-level investments in proper controls rather than expecting users to perform magic.
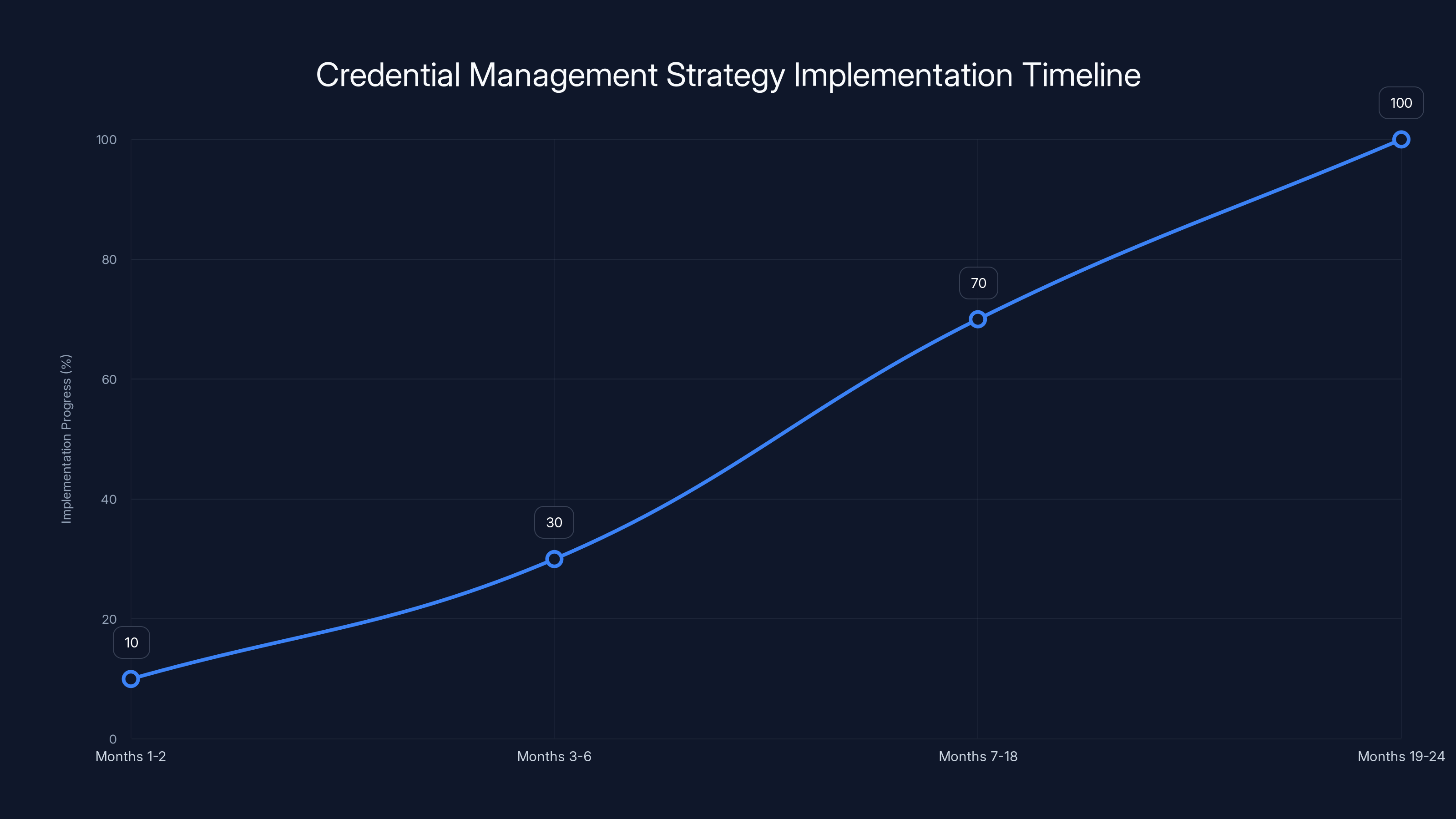
The chart illustrates the estimated timeline for implementing a credential management strategy, showing progress from initial assessment to full deployment over a two-year period. Estimated data.
What the NCSC's 2024 Guidance Actually Changed
In early December 2024, the National Cyber Security Centre released updated guidance on credential management that represents a significant shift in how UK organizations should think about access control. Understanding this guidance matters because it's shaping regulatory expectations and, increasingly, what auditors and risk committees will be looking for.
The core message of the NCSC guidance is deceptively simple: stop relying primarily on user behavior to secure credentials. Instead, implement technical defenses and organizational processes that handle the security work automatically.
This is a major departure from the user-centric security model that dominated the previous decade. For years, security leaders heard a consistent message: train users better, enforce stronger passwords, educate people about phishing. The assumption was that security failures were fundamentally user failures that could be fixed with better training and policy.
The NCSC's guidance acknowledges what security practitioners have known for years: that model doesn't work at scale. Users will always be the weakest link in a system designed to require perfect human behavior.
Instead, the guidance advocates for:
- Reducing reliance on passwords through technical alternatives like passkeys and multi-factor authentication
- Helping users cope with password overload by implementing centralized credential management that handles the cognitive load
- Managing shared access through formal processes, audit trails, and least-privilege access controls
- Protecting credentials at rest by ensuring they're encrypted, centrally stored, and never transmitted in plaintext
For UK security leaders, this guidance is important because it reframes the conversation with boards and executives. You're no longer arguing for security improvements on principle. You're following government guidance. You're managing regulatory risk. You're implementing controls that auditors expect to see.
The guidance also explicitly addresses governance and accountability, which matters significantly in the UK context where regulatory bodies like the Financial Conduct Authority, Information Commissioner's Office, and sector-specific regulators are increasingly examining how organizations manage access controls. If your organization can't demonstrate formal credential management processes, you're creating audit findings.
The Password Overload Crisis
Let's get specific about the math of password overload, because the numbers are what really illustrate the problem.
The average UK knowledge worker maintains around 168 passwords across business accounts and another 87 across personal accounts. Some individuals manage far more. Security researchers working at large enterprises report managing 300-400+ unique credentials when you count all the systems, databases, legacy applications, and cloud services they need to access.
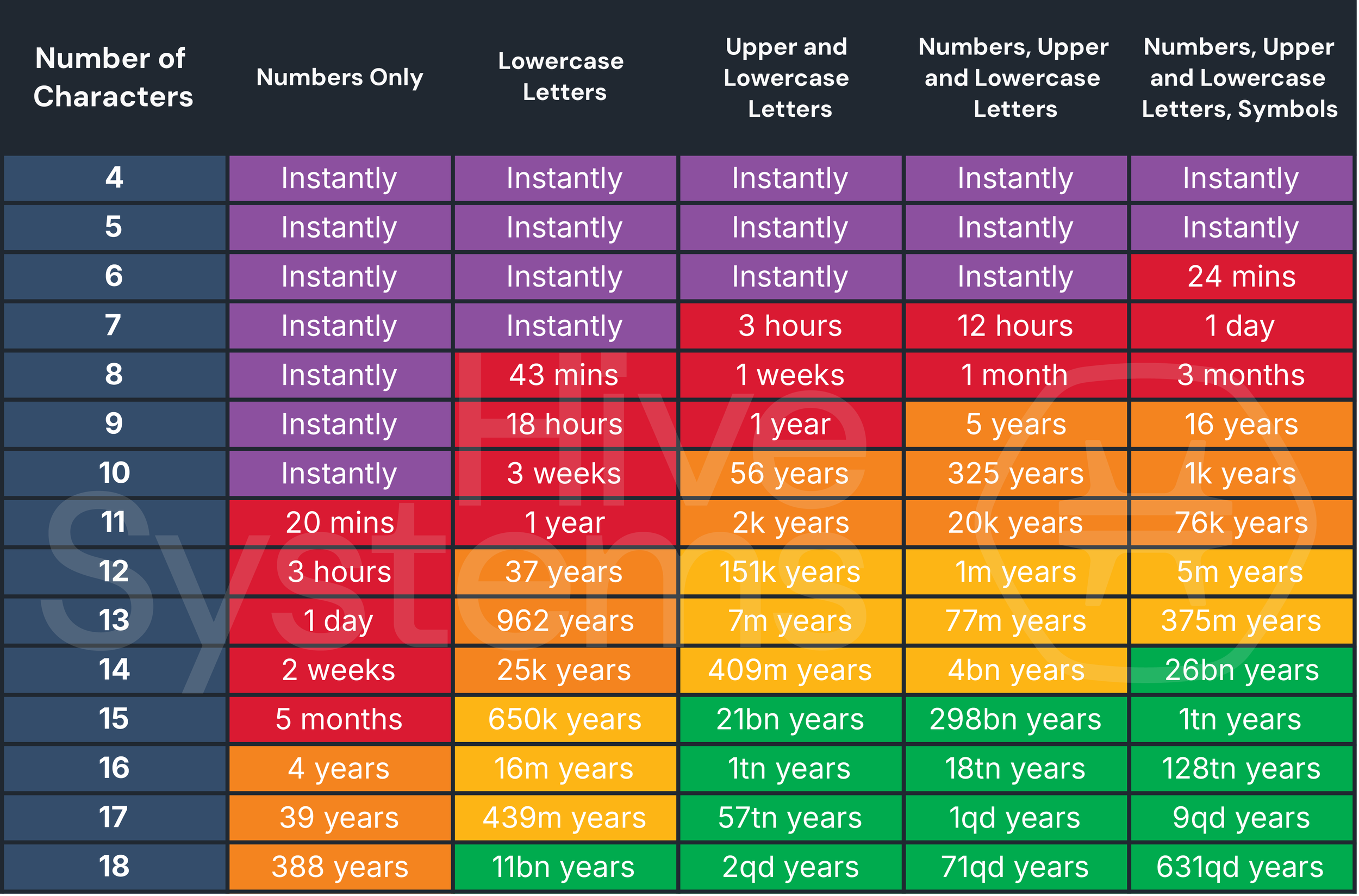
Now consider what password security best practices demand: each password should be unique, at least 12 characters long, include uppercase and lowercase letters, numbers, and special characters, and be changed every 90 days (though modern guidance is shifting toward longer change intervals for passwords used with multi-factor authentication).
The cognitive load is astronomical. You're asking humans to create and remember hundreds of increasingly complex strings with no patterns or logic they can latch onto. Some research suggests that the average person can only hold about 7 distinct pieces of information in working memory at any given time. Asking them to reliably manage hundreds of unique passwords isn't a security strategy. It's security theater that creates failure.
When people hit the limits of what their brain can manage, they adopt coping mechanisms. These coping mechanisms are predictable and, from a security perspective, terrible:
Password reuse: An employee uses variations of the same password across multiple systems. They might use "Company 2024!" for their work email, then try "Company 2024!" for the VPN, then slightly tweak it to "VPN-Company 2024!" for systems that enforce different character requirements. When an attacker compromises one system and obtains password hashes, they can crack them and try the variations against other systems.
Predictable patterns: People create rules for themselves to make passwords more manageable. "I'll use [Company Name] + [Year] + [!]" or "[Site] + Birth Year + [#]". These patterns look complex to humans but are trivial for attackers to predict, especially once one password is compromised and the pattern becomes obvious.
Writing things down: Passwords get written on sticky notes, in plaintext in documents, in shared notebook files. Some get saved in insecure note-taking apps. A single lost laptop or careless photo of a desk becomes a credential leak.
Browser password manager reliance: Many employees rely exclusively on their browser's password manager (Chrome, Safari, Firefox). While these tools are convenient, they weren't designed for enterprise security governance. They offer limited visibility, inconsistent policy enforcement, and create vendor lock-in. If an attacker gains access to the user's browser session or if the browser password manager is compromised, all credentials are exposed simultaneously.
Extreme simplification: Some users just give up. They choose passwords that are easy to remember and easy to guess. "Password 1" accounts for millions of breaches. It's not because people are stupid. It's because they've hit the limit of what they can manage.
The solution to password overload isn't better training or stricter policies. It's removing the need to manage passwords at all, or dramatically reducing that burden through proper tooling and architecture.

Estimated data shows that users manage 250 accounts by reusing passwords (30%), creating patterns (25%), writing them down (20%), or using browser managers (12%). Only 13% of accounts have unique passwords.
Why Passwords Remain the Primary Target for Attackers
Attackers continue to target passwords with relentless focus because the return on investment is extraordinary. Passwords remain the path of least resistance to access systems and data.
Consider the economics from an attacker's perspective. They can:
- Deploy credential stuffing attacks, trying known username-password combinations from previous breaches against new systems. This requires minimal skill and works at scale because password reuse is so common.
- Use AI-accelerated cracking tools to attack password hashes obtained from breached systems. Modern GPU clusters can guess billions of passwords per second. A password that would have been secure five years ago might be crackable in hours now.
- Conduct phishing campaigns that harvest credentials directly. A single phishing email that tricks a user into entering their password on a fake login page gives attackers the legitimate credential without any technical hacking required.
- Conduct brute-force attacks against systems with weak lockout policies. If a system allows unlimited password attempts without delays, attackers can simply try thousands of combinations until one works.
- Exploit password storage vulnerabilities. Systems that store passwords with weak hashing algorithms, insufficient salt, or no hashing at all become massive liability when breached.
All of these attacks work because passwords have fundamental weaknesses:
They're transferable: Unlike a biometric factor or a device-based factor, a password can be stolen, guessed, or intercepted and used by someone else. The system has no way to know whether the person entering the password is the actual account owner.
They're brute-forceable: Given enough computing power and time, any password can be guessed. The only question is how long it takes.
They're compromised at scale: Password breaches are endemic. Major platforms are breached regularly. Attackers maintain massive databases of billions of username-password combinations that they can test against other systems.
They depend on perfect consistency: One weak password somewhere in a user's ecosystem can lead to compromise. One human error can undermine an otherwise solid security posture.
For attackers, passwords are the gift that keeps giving. They're ubiquitous, they're often weak, they're frequently reused, and compromised ones are for sale on the dark web by the thousands.
The industry's shift toward passwordless authentication and passkeys isn't happening because passwords are slightly inconvenient. It's happening because passwords have fundamental security properties that make them vulnerable at scale in ways that modern authentication factors simply aren't.
Multi-Factor Authentication: The Immediate Practical Defense
While the long-term solution to password problems is moving beyond passwords entirely, multi-factor authentication (MFA) is the practical defense that UK organizations can and should deploy today.
MFA works by requiring users to prove their identity through multiple independent factors. Instead of just knowing something (a password), users must also have something (a phone, a hardware key) or be something (a fingerprint, face recognition).
The security principle is sound: even if an attacker compromises a password through phishing, credential stuffing, or cracking, they still can't access the account without the second factor. The attacker would need to compromise multiple independent systems or factors simultaneously, which dramatically increases their effort and risk.
For UK organizations, MFA deployment should be happening in this sequence:
Phase 1: Critical systems first - Implement MFA on email accounts, VPN access, and administrative systems immediately. These are the accounts that control access to everything else. If an attacker compromises an administrator's email account, they can reset other passwords and escalate their access across the entire organization.
Phase 2: Identity provider integration - Implement MFA at your centralized identity provider (Active Directory, Azure AD, Okta, etc.). This provides consistent MFA enforcement across all integrated applications with minimal per-application configuration.
Phase 3: Application-specific MFA - For applications that don't integrate with your centralized identity provider, implement MFA within the application itself or through a third-party MFA service.
Phase 4: Risk-based MFA - Implement adaptive MFA policies that require additional authentication factors for high-risk scenarios (login from a new location, unusual time of access, etc.).
The practical challenge with MFA deployment isn't technical. It's adoption. Users find it inconvenient. Help desk tickets spike. Support costs increase. But these are temporary friction points in a transition that makes your organization dramatically more secure.
For MFA delivery methods, UK organizations have several options, each with different security properties and user experience trade-offs:
SMS-based codes: Users receive a text message with a one-time code. This is easy to implement and works with any phone, but SMS is vulnerable to SIM swapping attacks where criminals convince mobile carriers to transfer the victim's phone number to a device they control.
Time-based one-time passwords (TOTP): Users install an authenticator app (Google Authenticator, Microsoft Authenticator, Authy) that generates time-synchronized codes. This is more secure than SMS, works offline, and doesn't depend on telecommunications infrastructure, but it requires users to maintain the app and can be problematic if they lose their phone.
Push notifications: The authenticator app sends a push notification asking the user to approve or deny the login attempt. This is more user-friendly than entering codes manually and provides better security properties because it includes device verification.
Hardware security keys: Users carry a small hardware device (USB key, NFC tag) that generates cryptographic proofs of identity. This is the most secure option but requires users to carry another device and remember to bring it with them.
Biometric factors: Fingerprint, facial recognition, or other biometric methods. These are secure, convenient, and increasingly built into modern devices, but they require appropriate hardware and face adoption challenges in some organizations.
The most practical recommendation for most UK organizations is a combination approach: implement push notifications or TOTP as the primary MFA method, provide hardware security keys as an option for high-risk accounts, and have a secure backup method (like backup codes stored in a safe location) for account recovery if users lose their primary MFA device.
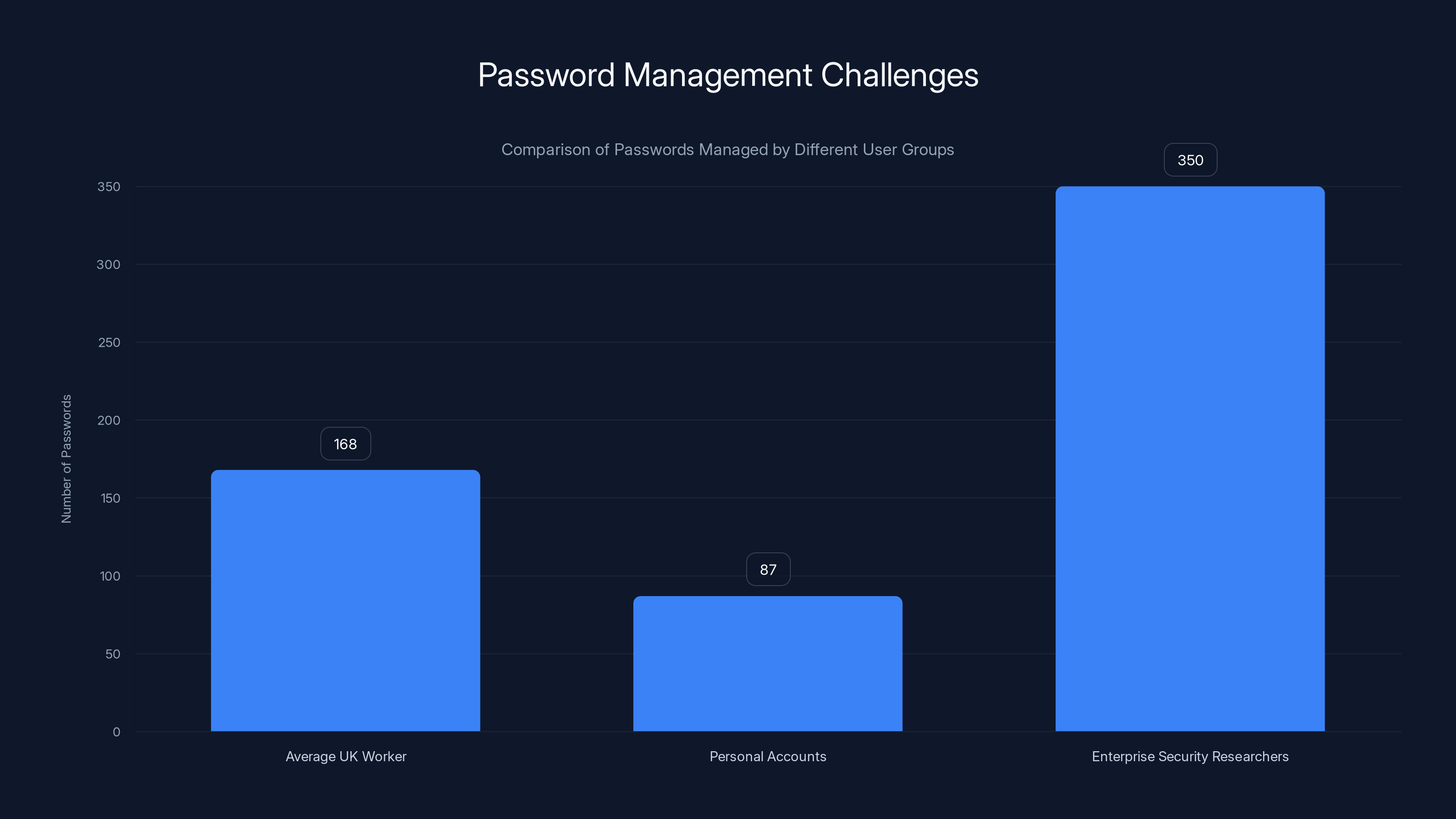
Enterprise security researchers manage significantly more passwords (350 on average) compared to the average UK knowledge worker (168) and personal accounts (87). Estimated data.
Privileged Access Management: The Enterprise Control Layer
Once you've protected standard user accounts with MFA, the next critical layer is managing privileged access. This is where security leaders often find enormous risk hiding in plain sight.
Privileged accounts are different from standard user accounts. They have broad permissions that allow users to make system-level changes, access sensitive data across multiple systems, configure security controls, and potentially compromise the entire organization if compromised. Database administrator accounts, system administrator accounts, application service accounts, shared team accounts, and emergency access accounts all fall into this category.
In many UK organizations, privileged access management is genuinely chaotic:
- Privileged passwords are shared among team members with no audit trail of who accessed them or when
- System passwords are hardcoded in application configuration files or scripts
- Privileged accounts are accessed by individuals logging in with those credentials directly rather than through formal elevation mechanisms
- There's no automatic password rotation, so compromised privileged passwords remain active indefinitely
- There's no logging of what privileged users actually did with their access, making incident investigation and audit trails impossible
- Emergency access accounts created years ago for "just in case" scenarios remain active without any monitoring
This situation creates a regulatory and security nightmare. From a security perspective, a single compromised privileged credential can give an attacker the access they need to steal data, destroy systems, pivot to other environments, and cover their tracks. From a regulatory perspective, the lack of audit trails and access controls represents a governance failure.
Privileged Access Management (PAM) solutions address this by:
Centralizing privileged credential storage: All privileged passwords are stored in a central vault with strong encryption rather than scattered across scripts, spreadsheets, and people's brains.
Implementing credential rotation: Passwords are automatically changed on a schedule or after each use, ensuring that even if someone steals a password, it's no longer valid.
Enforcing least-privilege access: Users get the minimum privileged access they need for their specific role, not blanket administrative access to everything.
Providing session recording and logging: Every action taken with privileged access is recorded, logged, and auditable, creating a complete record of what happened and who did it.
Implementing approval workflows: High-risk privileged access requires approval from a designated approver, creating accountability and preventing unauthorized access.
Enabling just-in-time access: Rather than permanently granting elevated privileges, access is granted temporarily for specific sessions and automatically revoked afterward.
For UK organizations, implementing PAM is increasingly a regulatory expectation. Financial institutions face expectations from the FCA, healthcare organizations from NHS cybersecurity teams, and all organizations from the Information Commissioner's Office regarding how they manage access to sensitive data. A board-level security review that shows "we have no system for managing or auditing privileged access" creates liability and regulatory risk.
The practical challenge with PAM isn't the concept. It's the scope of implementation. Organizations often underestimate how many privileged accounts exist in their environment. Once you start auditing, you find:
- Service accounts for applications running batch jobs
- Database accounts for scheduled tasks
- Backup system accounts
- Network device admin accounts
- Virtualization platform admin accounts
- Cloud platform service accounts
- Emergency access accounts created years ago
- Personal accounts that were granted administrative privileges for historical reasons
- Shared team accounts where multiple people know the password
Implementing PAM across all of these requires project management, coordination between teams, and careful change management to avoid disrupting business operations.
Passkeys and Passwordless Authentication: The Future State
The practical limitations of passwords are driving the industry toward passwordless authentication, and passkeys are finally mature enough for enterprise deployment.
Passkeys represent a fundamentally different approach to proving identity online. Instead of proving that you know something (a password), passkeys prove that you possess a specific device and can unlock it (through biometric authentication or a PIN). They use modern cryptography based on public-key infrastructure rather than shared secrets that can be stolen and reused.
Here's how passkeys work in practice:
When you create a passkey for a service, your device generates a unique cryptographic key pair. The private key stays on your device (secured by your device's biometric or PIN). The public key is sent to the service and stored in their database. When you sign in, the service sends a cryptographic challenge. Your device uses your private key to sign the challenge (after verifying your biometric or PIN), and the service verifies your signature using the stored public key.
This approach has security properties that passwords simply can't match:
Phishing resistance: A phishing attack that tricks you into entering your password on a fake website won't work with passkeys. The fake website can't prove it's the legitimate service, so your device won't sign their challenge.
No shared secrets: Unlike passwords, passkeys never require you to share a secret that the service knows. The private key never leaves your device, so even if the service is breached, nothing of value is stolen.
Device binding: Your passkey is tied to your specific device and secured by your device's biometric or PIN. An attacker can't reuse the credential on a different device.
Automatic backup and recovery: Modern passkey systems (Apple's iCloud Keychain, Google's Password Manager, Microsoft's Entra ecosystem) provide secure backup and synchronization across devices, making account recovery possible if you lose a device.
For UK organizations, passkey adoption is happening in stages. Early adopters are enabling passkeys as an optional authentication method alongside passwords, allowing users to gradually transition. More mature implementations make passkeys the primary authentication method with passwords as a fallback, then eventually eliminate passwords entirely for standard user accounts.
The practical benefits of passkey adoption extend beyond security:
Reduced support costs: Users don't forget passkeys or lock accounts through failed password attempts. Help desk tickets related to password resets drop dramatically.
Improved user experience: Rather than typing complex passwords, users unlock their passkey with their face or fingerprint, which is often faster and more natural.
Audit trail improvements: Passkey authentication logs are cleaner and more reliable because they don't suffer from password sharing or informal credential delegation.
Regulatory alignment: Passkeys align with regulatory guidance advocating for strong, phishing-resistant authentication methods.
The current challenge with passkeys is ecosystem maturity. Not all services support them yet. Organizations need a transition period where passwords and passkeys coexist. Users need education about how passkeys work. Mobile device management policies need updates to support passkey recovery and management.
But the trajectory is clear. Organizations that begin passkey pilots in 2025 will be well-positioned for adoption as the technology matures and becomes the default authentication mechanism across enterprise platforms.
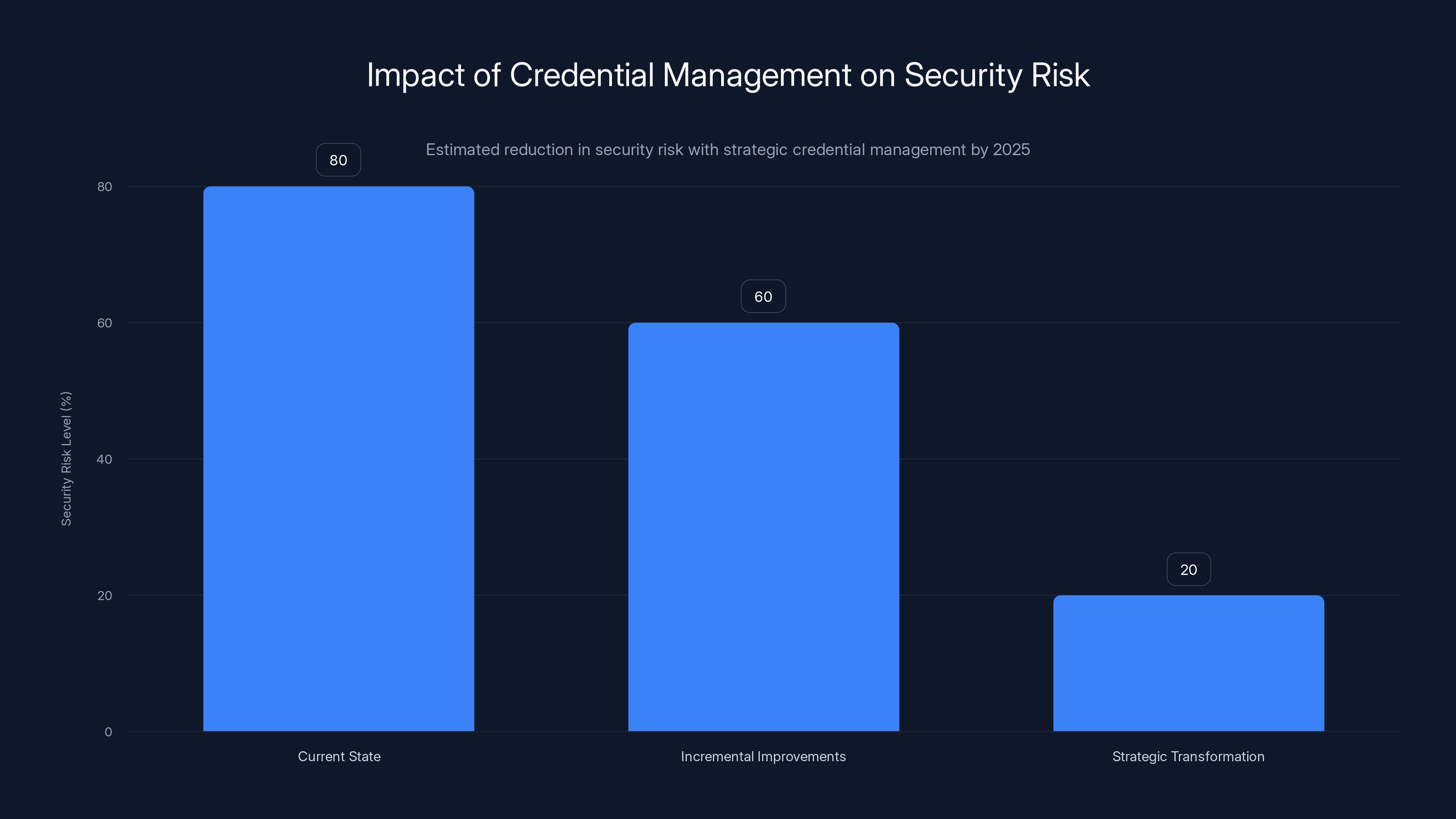
Organizations adopting strategic credential management by 2025 can reduce security risk significantly compared to incremental improvements. Estimated data.
Managing Shared Access: Beyond the Spreadsheet
One of the persistent problems in UK organizations is the management of shared credentials. These are accounts that multiple people need to access: shared mailboxes, service accounts, emergency access accounts, and team administration credentials.
The current state of shared credential management in many organizations is genuinely problematic:
- Shared passwords are stored in Excel spreadsheets with limited access controls
- Credentials are shared via email or messaging apps, creating copies scattered across the organization
- When someone leaves the organization, nobody remembers to change the shared password
- There's no audit trail showing who accessed the shared credential and when
- Different team members with access to the shared credential might be using it from different locations with different intentions, making investigation impossible
From a security perspective, shared credentials are particularly dangerous because they violate the fundamental principle of accountability. If a shared database administrator password is compromised, you can't determine which team member was using it when data was accessed or modified. If a shared service account is used to access sensitive systems, you can't prove who initiated the access.
From a regulatory perspective, the lack of accountability is even more concerning. Auditors expect to see a clear audit trail showing who accessed what, when, and what they did. Shared credentials that can be used by multiple people make this audit trail impossible.
The solution is implementing proper credential management and access controls for shared access:
Eliminate shared credentials where possible: Rather than multiple people knowing a single password, issue individual credentials to each person and implement authorization rules that control what each credential can access.
Use service accounts for applications: Applications that need to access databases or other systems should use dedicated service accounts, not human credentials. The service account credentials are stored securely in the application configuration, and the account has only the permissions the application needs.
Implement just-in-time access for emergency scenarios: Emergency access accounts should grant temporary elevated permissions that automatically expire rather than persistent shared credentials that anyone with the password can use anytime.
Use API keys and tokens instead of passwords: Modern applications and cloud platforms increasingly support API-based authentication using tokens or keys instead of passwords. These can be issued to individual users or applications, automatically rotated, and revoked when no longer needed.
Log all access to shared credentials: Any time a shared credential is accessed, that access should be logged with the identity of who accessed it and what they did. This requires proper credential management tooling.

Credential Management in Cloud Environments
Cloud adoption has dramatically changed how organizations manage credentials, and many teams are still working through the challenges.
In traditional on-premises environments, credential management is relatively straightforward. All systems are on your internal network, behind your firewalls, managed by your teams. Credentials can be tightly controlled.
Cloud environments introduce new complexity:
Multiple cloud providers: Organizations increasingly use AWS, Azure, and Google Cloud, each with different credential management approaches and permission models.
Federated identity: Rather than managing credentials directly in each cloud platform, organizations delegate identity management to a central provider (Azure AD, Okta, etc.) and use federation to provide access to cloud resources.
API keys and service principals: Cloud platforms require API keys, service principals, or other machine credentials for applications and automated processes to authenticate. These credentials need to be managed, rotated, and protected.
Secrets management: Applications running in cloud environments often need database passwords, API keys, certificates, and other secrets. Managing these secrets securely requires dedicated tooling.
Cross-account access: In larger cloud deployments, organizations use multiple cloud accounts or subscriptions. Credentials need to be managed across these boundaries with proper audit trails.
The emerging best practice for credential management in cloud environments is a layered approach:
Centralized identity provider: Use a cloud-native identity provider (Azure AD, Google Cloud Identity, or AWS Identity Center) as the central source of truth for user identity and access control.
Federated access: Use federation to connect applications and resources to the centralized identity provider, eliminating the need for separate credentials in each system.
Dedicated secrets management: Use cloud-native secrets management services (AWS Secrets Manager, Azure Key Vault, Google Secret Manager) to securely store and rotate machine credentials.
Workload identity: Use native cloud platform capabilities that allow applications and workloads to authenticate without embedded credentials (AWS IAM roles, Azure managed identities, Google Workload Identity).
Audit and logging: Ensure that all credential usage is logged to cloud-native logging services for audit trails and compliance.
For UK organizations, cloud credential management is increasingly a compliance requirement. If your organization processes personal data subject to UK GDPR, handles health information, or operates in regulated industries, auditors will examine how you're managing access to cloud resources.

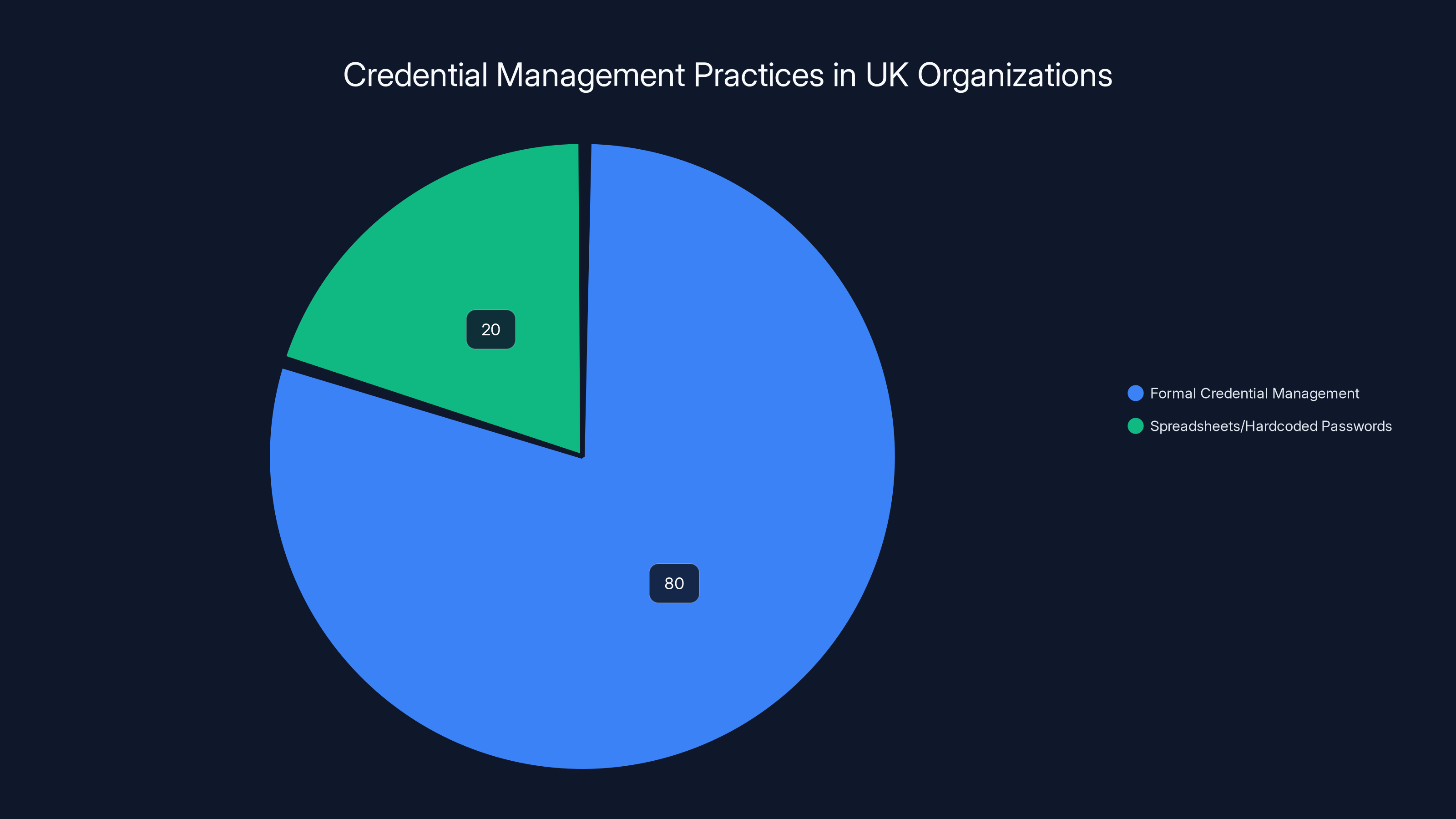
Nearly 20% of UK organizations still use spreadsheets or hardcoded passwords for credential management, posing significant security risks.
Implementing a Credential Management Strategy
Moving from the current state (passwords everywhere, weak controls, limited audit trails) to a more secure state (centralized management, strong authentication, full auditability) requires a structured approach.
This isn't something you can deploy overnight. It's a multi-year transformation that requires planning, governance, and sustained commitment.
Phase 1: Assessment and Planning (Months 1-2)
First, understand your current state. This means:
- Inventorying all credential storage locations (how many places store passwords or keys?)
- Identifying all systems that support alternative authentication methods
- Documenting current credential management policies and where they're not being followed
- Assessing the maturity of your identity platform and access management capabilities
- Determining regulatory and compliance requirements specific to your organization
From this assessment, develop a credential management strategy that's specific to your organization. Every organization is different, and the sequence matters.
Phase 2: Foundation (Months 3-6)
Build the foundational layer:
- Implement or upgrade your centralized identity platform (Azure AD, Okta, etc.)
- Deploy a password manager or credential vault for corporate credentials
- Establish credential management policies and governance processes
- Implement automated password rotation for service accounts and system credentials
- Begin deploying MFA to critical systems
Phase 3: Core System Migration (Months 7-18)
Migrate core systems to modern credential management:
- Deploy MFA to email and identity provider accounts (Phase 1 of MFA rollout)
- Migrate applications to use centralized identity provider for authentication
- Implement PAM for privileged accounts and administrators
- Begin eliminating shared credentials by implementing individual accounts with proper authorization
- Introduce API-based authentication for cloud platforms
Phase 4: Passwordless Transition (Months 19-36)
Transition to passwordless where feasible:
- Enable passkeys as an option for standard user accounts
- Migrate high-risk accounts (executives, security team) to passkeys
- Provide clear communication and training to users
- Gradually increase passkey adoption as comfort and capability increase
- Consider making passkeys the default authentication method
Phase 5: Optimization and Monitoring (Ongoing)
- Monitor credential usage and access patterns for anomalies
- Continuously improve processes based on lessons learned
- Stay current with emerging authentication standards and capabilities
- Regularly review and update credential management policies
Each phase has specific objectives, deliverables, and milestones. Success requires executive sponsorship, dedicated resources, and clear communication to affected teams.

Governance and Compliance Considerations for UK Organizations
For UK organizations, credential management sits at the intersection of security best practice and regulatory requirement.
Multiple regulatory frameworks expect robust credential management:
UK GDPR: If your organization processes personal data, UK GDPR article 32 requires "appropriate technical and organizational measures" to ensure the security of personal data. This includes administrative access controls, audit trails, and protection of authentication credentials.
Financial Conduct Authority (FCA): If you operate in financial services, SYSC 3.2.6R explicitly requires "access control measures to ensure that system users are authenticated... and maintain appropriate audit trails." The FCA's guidance clearly expects organizations to demonstrate proper credential management and access control.
NHS Data Security and Protection Toolkit: Healthcare organizations must demonstrate compliant credential management as part of their DSP Toolkit submission.
PCI DSS (if applicable): If you process payment card data, PCI DSS requirements 8 and 10 require strong user authentication, regularly changed passwords, and complete audit trails of access to card data.
BS ISO/IEC 27001: The international information security standard expects organizations to document access control policies, implement user identification and authentication, and maintain audit logs.
Beyond regulatory requirements, auditors examining credential management typically look for:
- Documented credential management policies and standards
- Evidence of policy compliance (are the policies actually being followed?)
- Centralized credential storage with access controls and audit trails
- Automated password rotation for service accounts
- Multi-factor authentication on sensitive accounts
- Elimination of hardcoded or shared credentials
- Privileged access management with logging
- Regular access reviews and certification
The gap between policy and reality is where most organizations stumble. Having a documented password policy is necessary but not sufficient. The real test is whether those policies are actually enforced. Do you know that all production database accounts have strong passwords? Do you know that nobody is sharing administrator credentials? Do you have complete audit trails showing who accessed what?
Common Mistakes in Credential Management Implementation
Organizations implementing credential management solutions often make predictable mistakes. Understanding these helps you avoid them:
Mistake 1: Treating it purely as a technology problem
Many organizations buy a password manager or PAM solution and expect the technology to solve the problem. The technology is necessary but not sufficient. You also need updated policies, governance processes, training, and cultural reinforcement.
Mistake 2: Deploying without proper change management
Introducing new authentication methods (MFA, passkeys) without clear communication and training creates resistance and poor adoption. Users who don't understand why the change is necessary or how to use the new system will resist it.
Mistake 3: Exempting powerful groups from the controls
If executives or the technical team are exempted from MFA or credential management policies, you create governance failures and security risks. The controls need to be universal.
Mistake 4: Implementing without considering usability
If your credential management approach is too cumbersome, users will find workarounds. The most secure system that nobody uses is worthless. Design for security and usability together.
Mistake 5: Not implementing proper backup and recovery
When users lose access to their authentication credentials (lost phone, forgotten PIN), you need reliable recovery processes. Without these, users will either be locked out or will bypass controls to regain access.
Mistake 6: Assuming one solution fits everything
Different parts of your organization have different needs. Your cloud platform access might use different credential management approaches than your on-premises databases, which might differ from your application credentials. This is normal and acceptable as long as they're all well-managed.
Mistake 7: Treating compliance checkboxes as security
Some organizations implement credential management controls purely to satisfy auditors. Once the audit is passed, interest wanes and enforcement lapses. Effective credential management requires sustained commitment.

Emerging Technologies and Future Directions
The landscape of credential management is changing rapidly. Several technologies are emerging that will reshape how organizations approach the problem:
Zero Trust Architecture: Rather than assuming that users inside the corporate network are trustworthy, zero trust requires authentication and authorization for every access request, regardless of location or network. This makes credential management even more critical because every access must be authenticated.
Decentralized Identity: Projects like Verifiable Credentials and self-sovereign identity aim to give individuals control over their credentials without requiring a centralized identity provider. This is still emerging but could fundamentally change identity infrastructure in the coming years.
Behavioral biometrics: Rather than just verifying that a user knows a password or possesses a device, emerging systems analyze user behavior (typing patterns, mouse movement, navigation patterns) to continuously verify identity during a session.
Cryptographic identity: Rather than passwords or biometrics, some emerging systems use purely cryptographic authentication where the user's identity is derived from cryptographic keys they control.
AI-driven threat detection: Credential theft and misuse detection systems are becoming more sophisticated at identifying when a credential is being used in ways inconsistent with the account owner's normal behavior.
For most UK organizations in 2025, these emerging technologies are not yet ready for production deployment. The immediate opportunity is implementing passwordless authentication (passkeys), completing MFA rollout, and establishing proper PAM controls. That's where the security bang for your buck exists right now.
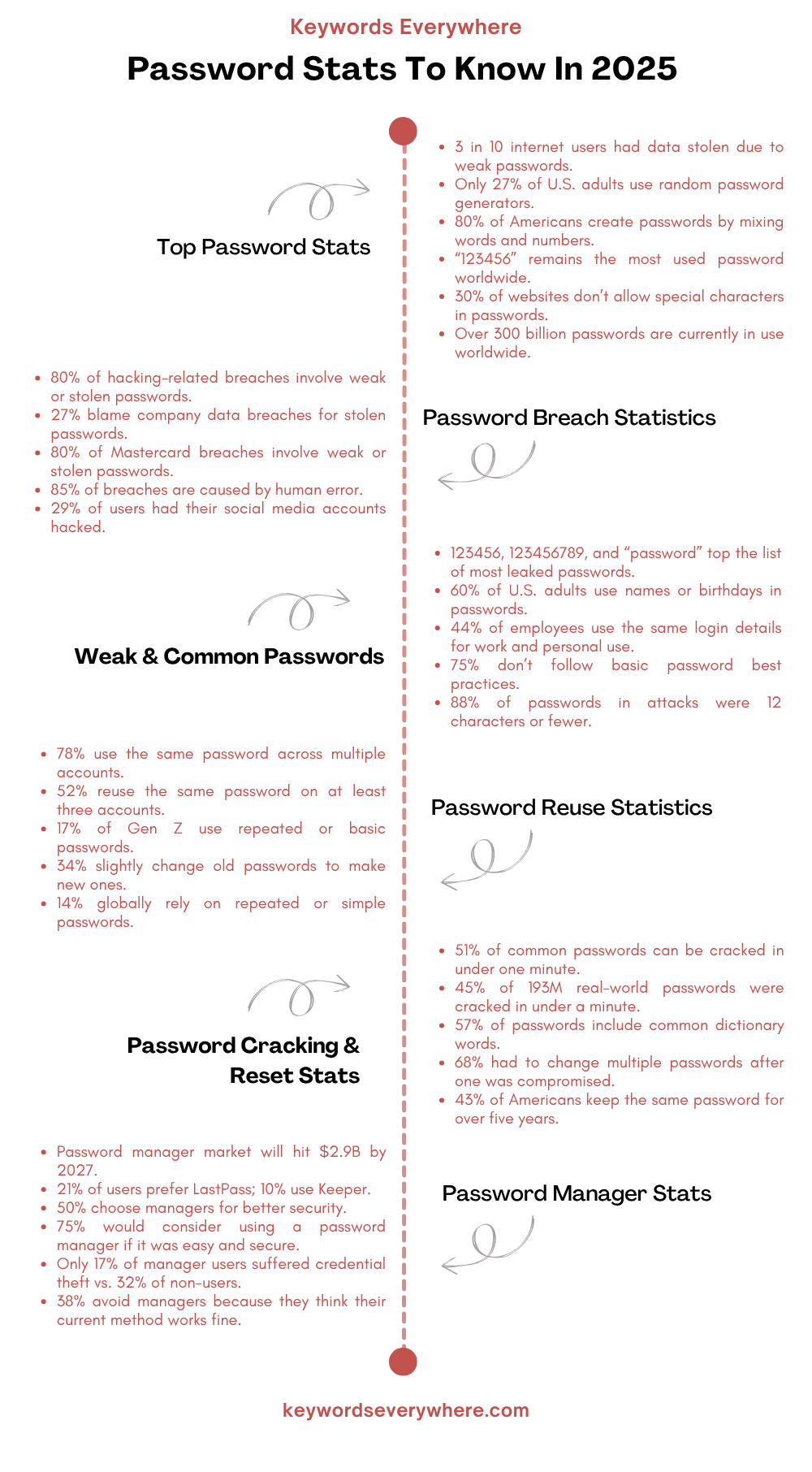
FAQ
What exactly is a passkey and how is it different from a password?
A passkey is a cryptographic credential that proves you own a specific device without requiring you to share a secret that the service knows. When you set up a passkey, your device generates a unique private key that never leaves your device. You prove your identity by unlocking your device (through biometric or PIN) and allowing it to sign a cryptographic challenge from the service. Passwords are shared secrets that you must prove you know—they can be guessed, stolen, or phished. Passkeys are fundamentally more secure because they're not shareable and they're phishing-resistant.
How can we reduce password overload in our organization?
Password overload is best addressed through a combination of approaches: implement a centralized password manager so users don't need to remember passwords, deploy single sign-on (SSO) or federated authentication to reduce the number of separate credentials users need, eliminate shared accounts by issuing individual credentials instead, and begin transitioning to passwordless authentication methods like passkeys. The goal is to remove the burden of managing multiple passwords rather than expecting users to overcome the cognitive limitations of remembering hundreds of unique complex strings.
Why is Privileged Access Management (PAM) important for UK organizations?
Privileged accounts have broad permissions that could compromise your entire organization if compromised. PAM provides centralized storage of privileged credentials, automatic password rotation, detailed logging of all privileged access, and enforcement of least-privilege principles. This is increasingly expected by UK regulators and auditors, particularly in regulated industries like financial services and healthcare. PAM implementation significantly limits the damage potential from a compromised privileged credential and provides accountability through audit trails.
How long does it take to implement a credential management transformation?
A comprehensive credential management transformation typically takes 18-36 months depending on your organization's size, complexity, and current maturity. You're looking at roughly 2 months for assessment, 4 months for foundation, 12 months for core system migration, 12-18 months for passwordless transition, with ongoing optimization. This is a strategic transformation, not a one-time project. Organizations that attempt to rush the process create more problems than they solve.
What's the business case for investing in credential management?
The business case includes reduced security incident costs, lower help desk support costs, improved regulatory compliance, reduced audit findings, faster incident investigation and response, and reduced lateral movement in breach scenarios. Organizations that have implemented comprehensive credential management report 60-70% reductions in credential-related incidents and significant reductions in breaches involving compromised credentials. The investment pays for itself within 18-24 months through reduced incident response costs alone.
How do we handle emergency access situations if we eliminate shared credentials?
Emergency access is handled through just-in-time access processes rather than permanently shared credentials. When emergency access is needed, the system creates temporary elevated privileges that are automatically logged, automatically expire after a set period, and require audit trails showing what was accessed and modified. This maintains both security and accountability, whereas permanently shared credentials achieve neither.
What's the realistic adoption curve for passkeys in enterprise environments?
Current projections suggest passkeys will become the default authentication method for new consumer and enterprise applications by 2026-2027, with legacy system support extending beyond that. For UK organizations, the realistic adoption curve involves 2025 as a piloting and education phase, 2026-2027 for expanding passkey support to standard user accounts, and 2028+ for making passkeys the primary method with passwords as a legacy fallback. The timeline depends heavily on your organization's system landscape and how quickly you can update applications to support passkeys.
How do we measure the effectiveness of our credential management program?
Key metrics include: percentage of accounts protected by MFA, percentage of shared credentials eliminated, number of automated password rotation failures, average time to detect and respond to credential compromise, number of audit findings related to access controls, help desk tickets related to passwords and access, and incident investigation time. You're measuring both security outcomes (fewer incidents) and operational efficiency (lower support costs, faster investigations).

Conclusion: The Shift from User Behavior to System Design
The password problem in UK organizations isn't fundamentally about users being careless or passwords being unpopular. It's about systems that demand the impossible and then blame users when impossible conditions create risky behavior.
The shift that the NCSC's 2024 guidance represents is crucial: moving away from the assumption that better user training and stricter policies will solve the problem, and toward the reality that organizational systems need to be redesigned to work with human psychology rather than against it.
For UK security leaders, the message is clear. Your organization doesn't have a password problem. You have a credential management and access control problem. Those are solvable. They require investment, planning, and sustained commitment, but the technology exists and the path forward is clear.
The organizations that treat this as a strategic priority in 2025 will have dramatically lower security risk, better regulatory compliance, and lower operational costs than organizations that continue relying on passwords and hope. That's not a security prediction. It's a business decision disguised as a security decision.
The time for incremental improvements has passed. The time for strategic credential management transformation is now.
Consider these next steps: Conduct a credential management maturity assessment, document your current state (where are credentials stored, how are they protected, what audit trails exist?), develop a multi-year credential management strategy with clear phases and objectives, secure executive sponsorship, and begin implementation with your highest-risk systems first.
Credential management isn't glamorous. It doesn't generate exciting headlines about zero-day exploits or nation-state actors. But in 99% of real organizational breaches, it's the difference between an attacker gaining access in minutes or never gaining access at all. Build the right system, and you'll sleep better at night. Continue with the status quo, and you're not managing risk—you're managing the timeline until your breach.
The NCSC has given you permission. Your regulators expect it. Your competitors who move first will have better security and lower costs. The only question is whether your organization will lead or follow this transformation.
Key Takeaways
- Password overload affects 250+ accounts managed by the average person; the problem is systemic design failure, not user negligence
- Nearly 20% of UK organizations lack formal credential management controls, using spreadsheets and hardcoded passwords instead
- The NCSC's 2024 guidance explicitly shifts security responsibility from individuals to organizations to design systems that work with human behavior
- Multi-factor authentication is the immediate practical defense; deployment should prioritize critical systems first then extend organization-wide
- Privileged Access Management (PAM) is increasingly a regulatory expectation in UK financial services, healthcare, and data-intensive organizations
- Passkeys represent a fundamentally more secure alternative to passwords through device-binding and phishing resistance; adoption will accelerate through 2025-2027
- Credential management transformation requires 18-36 months and involves assessment, foundation-building, system migration, passwordless transition, and continuous optimization
Related Articles
- 1Password Coupons & Free Trial: Complete Savings Guide [2025]
- 1Password Deal: Save 50% on Premium Password Manager [2025]
- AWS CodeBuild Supply Chain Vulnerability: What You Need to Know [2025]
- WordPress Plugin Security Flaw: Complete Guide to Staying Safe [2025]
- LinkedIn Comment Phishing: How to Spot and Stop Malware Scams [2025]
- Target Data Breach 2025: 860GB Source Code Leak Explained [2025]
![Password Security for UK Businesses: Beyond Weak Passwords [2025]](https://tryrunable.com/blog/password-security-for-uk-businesses-beyond-weak-passwords-20/image-1-1768750583038.jpg)



