Target Data Breach 2025: 860GB Source Code Leak Explained
In what's being described as one of the most alarming retail cybersecurity incidents in recent memory, unknown hackers claimed to have stolen approximately 860 gigabytes of source code and internal documentation directly from Target's systems. The threat actors posted their claims in underground hacking communities and provided sample evidence by uploading repositories to Gitea, a self-hosted Git platform, to prove they possessed the stolen data. According to Bleeping Computer, the breach has raised significant concerns about the security of internal systems.
This wasn't just customer payment information. This was the crown jewels: internal source code, configuration files, developer documentation, wallet service implementations, identity management systems, and gift card processing tools. Real talk, this is the kind of breach that keeps Chief Information Security Officers awake at night because it exposes the actual architecture of critical systems.
The incident raises urgent questions about how one of America's largest retailers could have exposed 860GB of sensitive internal data, how long it remained accessible, and what exactly threat actors can do with complete access to source code. For every developer, security professional, and business leader responsible for protecting data at scale, this breach is a wake-up call.
Let's break down what happened, why it matters, and what the retail industry needs to do right now to prevent the next Target-sized disaster.
TL; DR
- The Breach Size: Attackers allegedly stole approximately 860GB of Target internal source code, configuration files, and developer documentation
- Systems Compromised: Included wallet services, identity management tools, gift card systems, store networking infrastructure, and developer metadata
- Evidence Provided: Threat actors uploaded sample repositories to Gitea totaling over 57,000 files across multiple repositories
- Response Time: Target locked down servers and removed the exposed repositories after the breach became public
- Current Status: Authenticity remains unverified, but Target's quick defensive response suggests the breach is credible
- Industry Impact: Exposes critical vulnerabilities in how retailers store and access sensitive internal systems

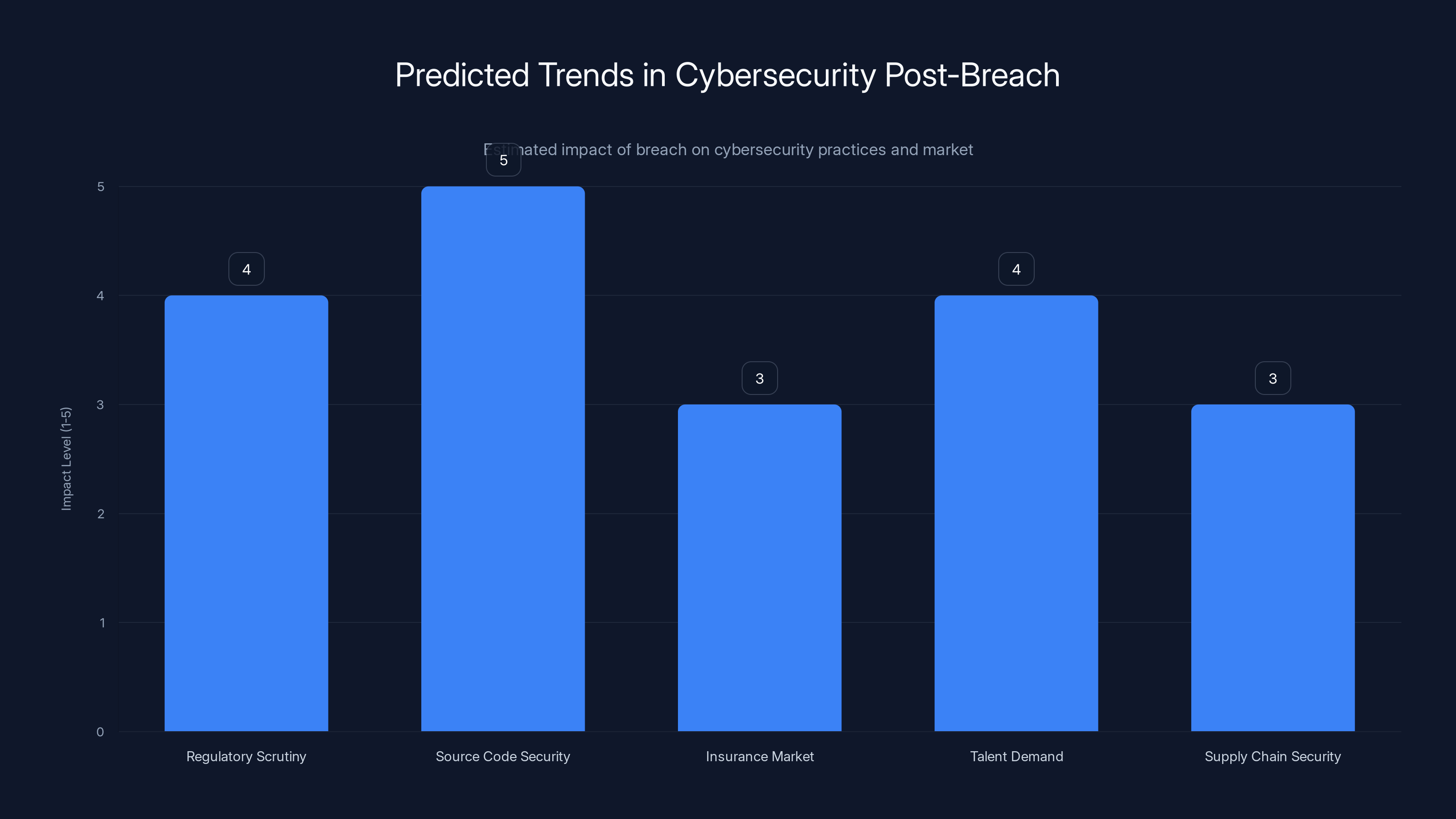
Predicted trends indicate a high impact on source code security and regulatory scrutiny, with increased demand for security talent. Estimated data based on current trends.
Understanding the Scope: What Was Actually Stolen
The claimed breach is massive not just in raw gigabytes, but in the strategic value of what was taken. Hackers don't go after source code for the same reason they chase payment card data. This is different. This is architectural intelligence.
According to the initial posting, the stolen data includes:
- Wallet services source code: The complete implementation of Target's payment wallet system, which processes millions of transactions
- Identity and access management tools: Systems that control who can access what within Target's infrastructure
- Gift card processing systems: The backend that manages gift card creation, redemption, and fraud detection
- Store networking infrastructure: Tools and configurations for how individual store systems communicate with corporate systems
- Developer documentation and secrets files: Information about APIs, authentication mechanisms, and internal workflows
- Commit metadata: Git history showing which engineers worked on specific systems and when
When you piece this together, you don't have just code. You have a detailed blueprint of how Target's critical systems actually work.
The repositories uploaded as proof were massive. A SALE. MD file (essentially a product listing for the stolen goods) exceeded 57,000 lines and detailed tens of thousands of files allegedly included in the full dataset. The index alone advertised a total archive size of approximately 860GB. For context, that's roughly equivalent to 215,000 standard feature-length movies, or about 1.7 million high-resolution photos.
Repository names referenced internal Target systems directly: wallet services, identity management, store networking tools, secrets documentation, and gift card systems. This wasn't obfuscated or hidden. The threat actors were literally advertising the contents by naming the repositories after the systems they contained.
The stolen data also included commit metadata with references to internal Target development servers (like confluence.target.com) and named current Target lead and senior engineers. This kind of metadata is gold for social engineering attacks or targeted recruitment of engineers who understand the systems.
Here's what makes this particularly severe: if the source code is real and complete, attackers now have months or years of development time condensed into instant understanding. They can audit the code for vulnerabilities without any time pressure. They can find backdoors. They can identify weak authentication mechanisms. They can see exactly how security controls were implemented and where they might fail.
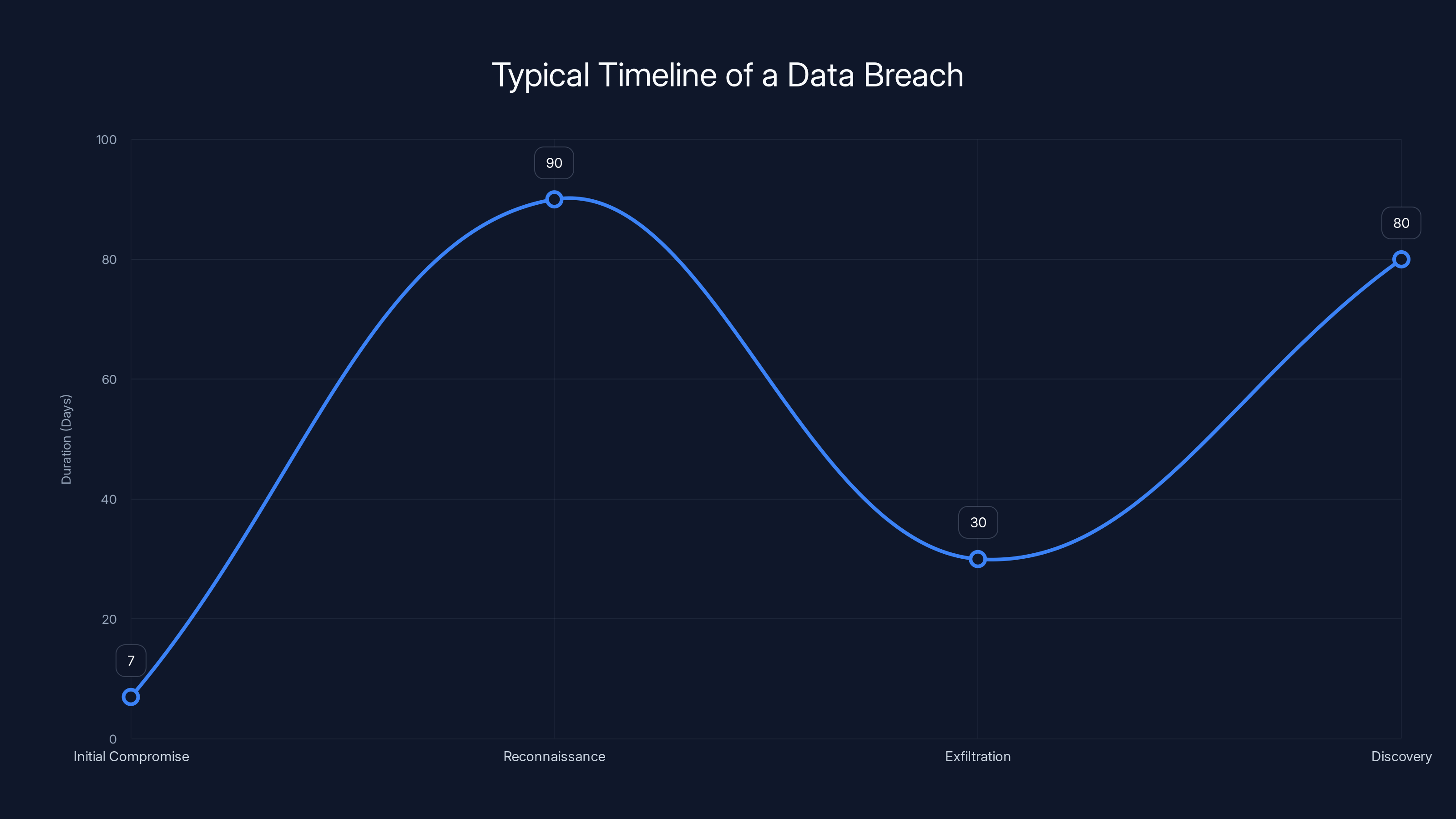
Estimated data shows that reconnaissance typically takes the longest, with discovery often delayed, averaging 207 days to detect a breach.
The Timeline: How the Breach Unfolded
This breach didn't happen overnight, and the full timeline is still being pieced together. What we know is that the incident likely followed a predictable pattern for large-scale retail cybersecurity failures.
First, there's the initial compromise. This typically happens through one of several vectors: compromised credentials, unpatched vulnerabilities in internet-facing systems, supply chain compromises, or insider access. Target hasn't disclosed which vector was used in this case, but given the scope of data accessed, the attacker almost certainly had legitimate or semi-legitimate access at some point.
Once inside Target's network, attackers would have conducted reconnaissance, moving laterally through systems and escalating privileges. This reconnaissance phase can take weeks or months. Attackers are looking for where the source code repositories are stored, how they're accessed, and which systems are least monitored.
Second comes the exfiltration phase. Moving 860GB of data out of a network leaves traces. Bandwidth usage spikes. Unusual data flows to external IP addresses. Network intrusion detection systems should have flagged this, but apparently didn't. Or if they did flag it, the alerts weren't acted upon in time.
Third comes discovery. In this case, discovery happened when the threat actor posted in an underground hacking community and created repositories on Gitea as proof. This was a deliberate, public claim. The threat actor was advertising the data for sale, which means they wanted to create a market for it.
When Bleeping Computer reached out to Target to notify them about the incident, Target's response was swift. The Gitea repositories came offline. Target's internal Git server (accessible from the internet) was locked down. Search engines had previously indexed and cached some content from git.target.com, suggesting that at least some stolen data may have been publicly accessible at some point through normal search indexing.
The big question no one can yet answer: for how long was git.target.com accessible to the internet without proper authentication? Days? Weeks? Months? That timeline matters because it determines how many other threat actors may have downloaded the data before Target locked it down.
Attack Vectors: How Attackers Likely Got Access
While Target hasn't disclosed the initial compromise vector, large-scale retail cybersecurity incidents typically follow predictable patterns. Understanding these patterns helps other organizations defend against similar attacks.
Unpatched Remote Access Systems
One of the most common entry points for attackers is outdated or unpatched remote access infrastructure. Retail companies maintain VPN systems, remote management tools, and external APIs for various business purposes. These systems are frequently targeted because they're internet-facing and can provide direct access to internal networks.
Attackers scan for outdated VPN clients, unpatched remote desktop services, or publicly exposed management interfaces. A single unpatched vulnerability in a remote access system can provide complete network access. Companies that don't patch promptly or maintain an inventory of external systems are sitting ducks.
Compromised Credentials
The second most common vector is compromised employee credentials. These can be obtained through phishing campaigns, credential stuffing attacks, or data breaches at third-party services where employees reused passwords. A developer, system administrator, or Dev Ops engineer with credentials is an attacker's dream because these roles typically have broad access to source code repositories, configuration files, and development systems.
Once an attacker compromises a single set of valid credentials, they can move laterally through the network using those permissions until they reach source code repositories. Many organizations don't monitor for unusual access patterns from legitimate credentials, making this vector particularly dangerous.
Supply Chain or Third-Party Compromise
Retail companies depend on countless third-party integrations: payment processors, logistics systems, inventory management platforms, and cybersecurity tools. If any of these third parties is compromised, attackers can pivot into the main Target network. This supply chain attack vector has become increasingly common and is extremely difficult to defend against because the trust boundary extends beyond your organization.
Insider Threats
While less common than external attacks, insider threats are worth considering. A current or former employee with access to source code repositories could directly exfiltrate data. The commit metadata in the stolen repositories named current Target engineers, suggesting these weren't historical employees but active staff members.
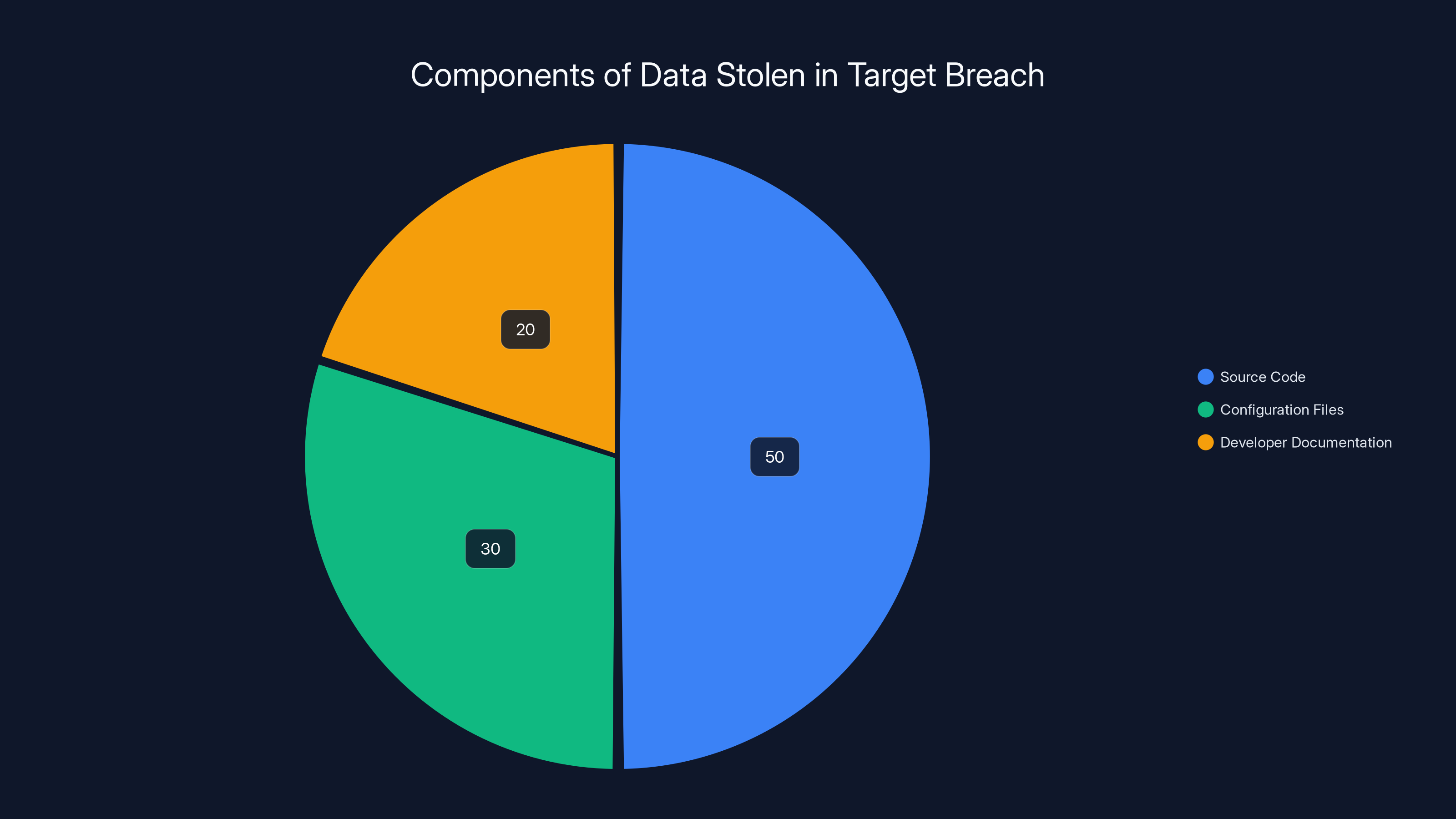
Estimated data distribution shows source code as the largest component of the stolen data, highlighting its critical value.
The Gitea Repository Evidence: Proof or Posturing?
The threat actor provided their proof of possession by uploading repositories to Gitea, a self-hosted Git platform. This is an interesting choice because it shows some sophistication about operational security but also indicates confidence that the data was already copied elsewhere.
Gitea is a lightweight, self-hosted Git service that anyone can set up. The threat actor created multiple repositories, each containing a portion of the allegedly stolen Target data. This distribution approach serves several purposes:
First, it creates multiple proof points. Instead of one large file that could be a fabrication, there are multiple repositories with consistent internal references. The repository names matched actual Target internal systems. The commit messages referenced real Target infrastructure.
Second, it demonstrates scale without exposing everything. Uploading the full 860GB would have been logistically difficult and would have increased the risk of law enforcement intervention. Instead, the attacker uploaded enough to be credible but retained the full dataset for the actual sale.
The repositories included SALE. MD files that functioned as product listings. These files detailed what was included in the full dataset, serving as marketing material for potential buyers in the underground hacking community. The file exceeded 57,000 lines, indicating an extremely comprehensive listing.
Third, it provides targeting information. The commit metadata included names of current Target engineers. This information could be used for future social engineering attacks, recruitment of insiders, or blackmail. When attackers have names and information about who wrote specific code, they can target those individuals for further compromise.
The question of authenticity is still open. Could the Gitea repositories be a sophisticated fake designed to extort Target? Theoretically, yes. But the specificity of internal references, the consistency across repositories, and Target's rapid response (locking down their servers) suggest the threat actor likely had real access to the data.
Why Source Code Is More Dangerous Than Credit Cards
This is the part that security professionals are most worried about, and rightfully so. If an attacker has your source code, they have something far more valuable than customer payment information.
Credit card data has an expiration date, literally and figuratively. A stolen credit card can be cancelled. Fraudulent charges can be disputed. The damage is measured in dollars and is relatively finite. Organizations pay ransom, increase fraud monitoring, and move on.
Source code doesn't expire. It's the genetic code of your digital infrastructure. With your source code, an attacker can:
Identify Zero-Day Vulnerabilities: Instead of discovering vulnerabilities through blind fuzzing or educated guessing, attackers can read the actual code and understand exactly how security controls work. They can find flaws that would take months of external research to discover. A zero-day vulnerability in a critical system could be worth millions on the dark market.
Understand Authentication Mechanisms: Security is only as strong as the implementation. Attackers can see exactly how authentication tokens are generated, validated, and refreshed. They can identify weaknesses in the implementation that aren't apparent from outside.
Locate Secrets and Credentials: Developers sometimes hardcode API keys, database credentials, or other secrets in comments or configuration. These secrets might provide direct access to critical systems without needing to exploit vulnerabilities.
Plan Targeted Attacks: With complete understanding of how systems work, attackers can plan multi-stage attacks that would be impossible without this insider knowledge. They can exploit subtle race conditions, timing issues, or logical flaws that external attackers would never discover.
Develop Undetectable Exploits: When writing exploits against unknown targets, attackers have to worry about detection systems, rate limiting, and anomalous behavior. With source code, they can craft exploits that blend seamlessly with normal operations because they understand exactly what normal looks like.
Create Backdoors: Knowing the source code, an attacker can create subtle backdoors that wouldn't be noticed during code review because they understand the codebase so thoroughly. A single modified line in a library used everywhere could provide persistent access.
For Target specifically, the wallet services code is particularly valuable. This code handles financial transactions and likely contains logic for authorization, fraud detection, and payment processing. Understanding this code would allow an attacker to potentially bypass fraud controls or manipulate transactions.
The identity management code is equally dangerous because it controls access to other systems. If an attacker understands how identity and access management works, they can potentially escalate privileges or create backdoor accounts that survive normal security remediation.
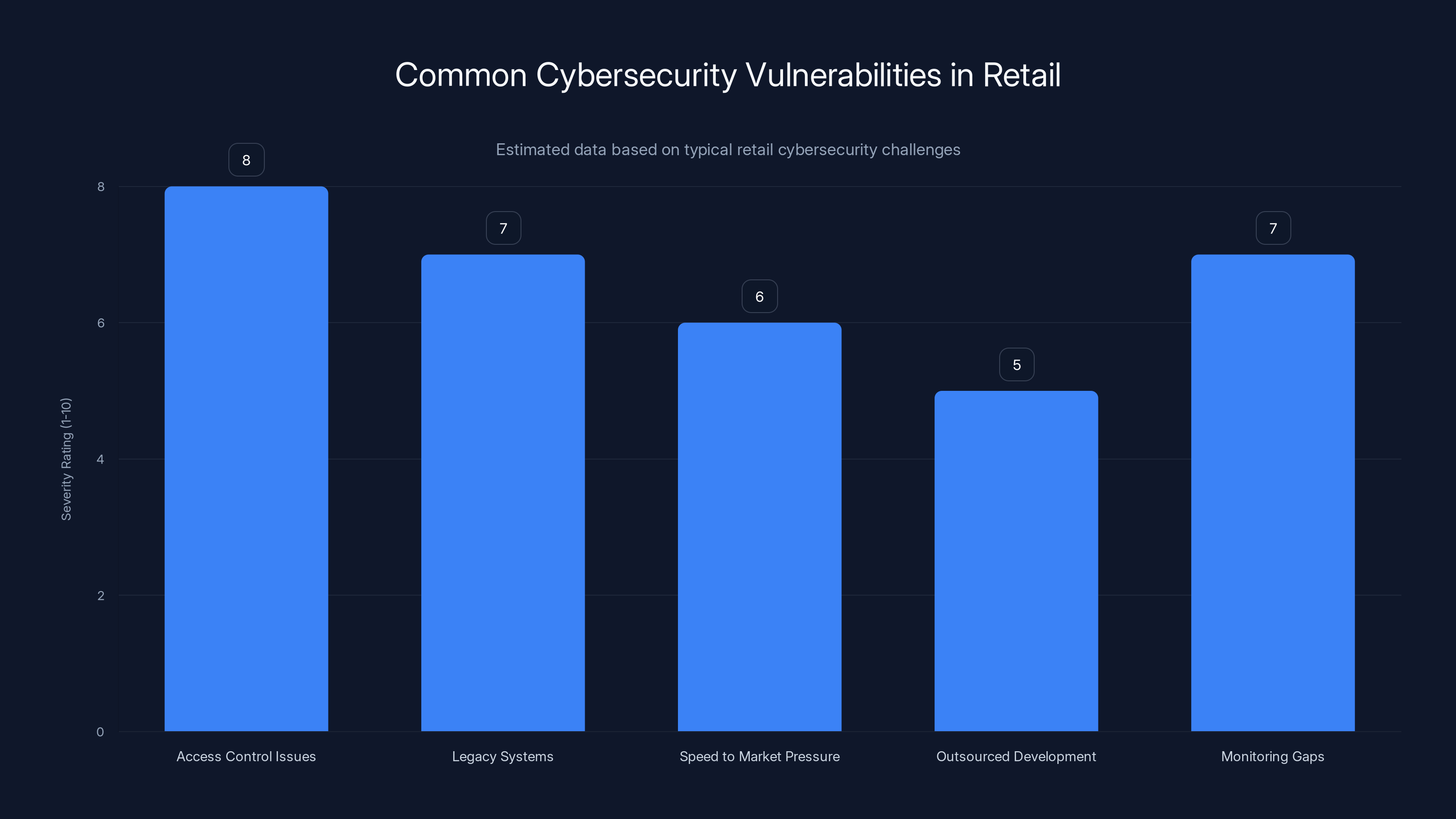
Access control issues and monitoring gaps are the most severe vulnerabilities in retail cybersecurity. Estimated data.
Target's Response: Damage Control in Real Time
Target's response to this breach has been reactive, which is to be expected when you're responding to a public claim in an underground hacking community. Here's what we know they've done:
First, they secured the exposed repositories. The Gitea repositories where the threat actor posted proof came offline. This prevents casual downloading and makes the data less accessible, but doesn't recover it since the full dataset presumably remains with the attacker.
Second, they locked down git.target.com, their internal Git server. The fact that this was accessible from the internet without proper access controls is itself a red flag. Internal Git servers should never be directly accessible from the public internet. Access should be mediated through VPN or other authentication mechanisms.
Third, they presumably launched an incident response process: forensic investigation to determine the scope of the compromise, notification to relevant parties, and security remediation to prevent similar breaches.
What hasn't been publicly disclosed:
- The initial entry vector
- How long the data was being exfiltrated
- Whether the attacker still has active access to Target systems
- If other datasets were compromised beyond what was advertised
- Whether customer data was accessed during this incident
- The timeline from initial compromise to discovery

Industry Implications: This Isn't Just Target's Problem
If Target was vulnerable to this attack, so are most major retailers. The retail industry as a whole has struggled with cybersecurity for years. Retailers are high-value targets because they process payments and maintain customer data at massive scale, but many have treated cybersecurity as a cost center rather than a critical function.
Source code repositories are particularly vulnerable in retail organizations because:
Developers Have Access: Retail IT departments struggle to maintain proper access controls. A single compromised developer's credentials can expose entire source code repositories. Many organizations don't have mature privilege access management (PAM) systems that would prevent a compromised developer credential from accessing everything.
Legacy Systems: Many retailers run legacy systems that weren't designed with modern security in mind. These systems are difficult to secure and often lack proper monitoring.
Speed to Market Pressure: Retailers operate under constant pressure to release new features and systems. This creates pressure to cut corners on security testing and access controls.
Outsourced Development: Many retailers outsource software development to agencies or offshore teams. This distributed development model makes it harder to maintain consistent security practices.
Monitoring Gaps: Most retailers lack comprehensive monitoring of data exfiltration. They monitor for intrusions but often fail to monitor what happens after an intrusion.
Other major retailers are likely running similar architectures with similar vulnerabilities. The difference between Target getting breached and other retailers is not necessarily better security, just luck that they haven't been targeted yet.

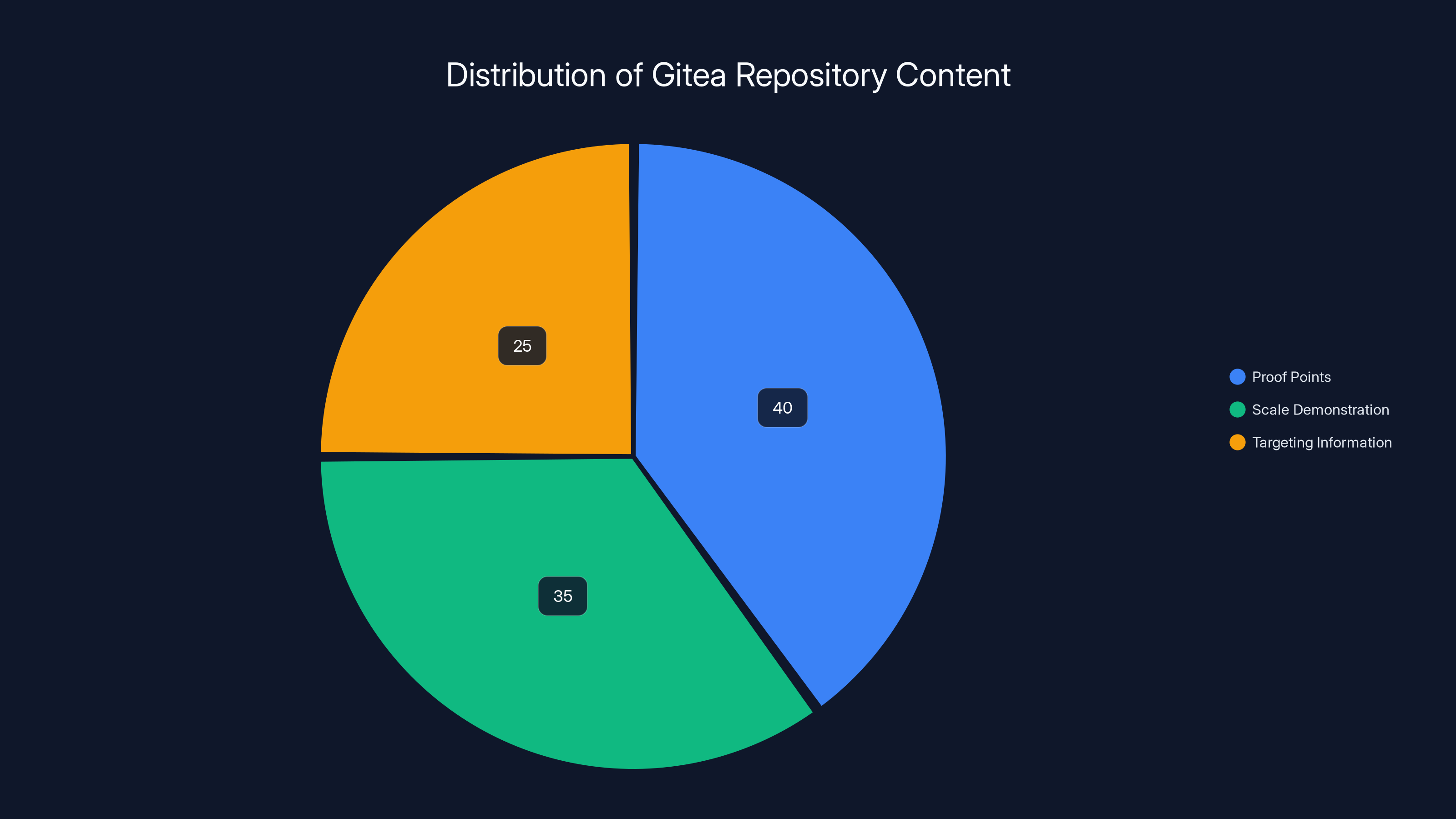
The Gitea repositories are estimated to contain 40% proof points, 35% scale demonstration data, and 25% targeting information. Estimated data based on narrative context.
Technical Deep Dive: Git Repository Security
The fact that threat actors could exfiltrate 860GB of source code from Git repositories points to fundamental security failures in how these repositories were configured and protected.
Git repositories are designed for collaboration, which means they need to be accessible to development teams. This accessibility is their weakness. A Git repository contains the complete history of code changes, every commit message, every author attribution, and every experimental branch. For an attacker with access, it's an archaeological dig into the entire development process.
Proper Git security requires:
Network Access Controls: Git repositories should never be directly accessible from the internet. Access should be mediated through a VPN or other authentication mechanism that sits between the internet and the Git server. A properly secured Git server requires authentication before you can even see that it exists.
Authentication and Authorization: Everyone accessing the repository should have unique credentials that can be audited. Shared credentials, default passwords, or missing authentication are unacceptable.
Encryption in Transit: All communication with Git repositories should be over HTTPS with proper certificate validation. Man-in-the-middle attacks should be impossible.
Access Logging: Every access, every download, every list of files should be logged with timestamps and user identifiers. These logs should be reviewed regularly for anomalous patterns.
Data Segmentation: Not all developers need access to all code. Sensitive code (payment processing, identity management, fraud detection) should have restricted access. A compromised developer's account shouldn't automatically grant access to everything.
Secret Scanning: Git repositories should be scanned for secrets (API keys, database passwords, credentials) that developers might have accidentally committed. These secrets are goldmines for attackers.
The size of the exfiltrated data (860GB) suggests either the attacker had complete unrestricted access or exfiltration happened over an extended period without detection. This points to failures in network monitoring, data exfiltration detection, or both.
Ransomware and Extortion: The Business Model
Understanding why the threat actor is selling this data requires understanding the modern extortion economy. This isn't just about selling data for a one-time payment. This is about creating a market and leveraging competition.
When a threat actor posts in underground communities claiming to have Target source code, they're not just selling to one buyer. They're creating an auction environment where multiple buyers compete. The threat actor can sell the data multiple times to different buyers, or sell it once to the highest bidder.
For retailers, the nightmare scenario is that the source code is now accessible to:
- Competitors: Who could use the code to understand Target's systems and technology choices
- Nation states: Who are interested in critical infrastructure and large US companies
- Cybercrime syndicates: Who will use the code to find vulnerabilities to exploit for ransomware or fraud
- Insider threat groups: Who will use the information to recruit employees or craft social engineering attacks
The underground hacking community operates with some structure. Threat actors with credible claims can auction data. Buyers verify the sample before making full payment. The threat actor has reputational incentive to deliver what they promised because future sales depend on credibility.
For Target, the extortion doesn't necessarily end with selling the source code. Threat actors may also:
Demand ransom directly: Contact Target and demand payment to prevent public sale or release of the data
Threaten regulatory notification: Suggest they'll notify regulators or the media if Target doesn't pay
Sell multiple times: Sell to different buyers simultaneously, multiplying their revenue
Use information for targeted attacks: Sell the data to other criminal groups who will use the code to identify vulnerabilities for ransomware campaigns
Target's public response (or lack thereof) will be carefully calculated. Pay the ransom and you incentivize future attacks. Don't pay and the data gets sold to everyone. Some organizations choose to publicly dismiss the breach as fake (even if it's real) to discourage the sale.
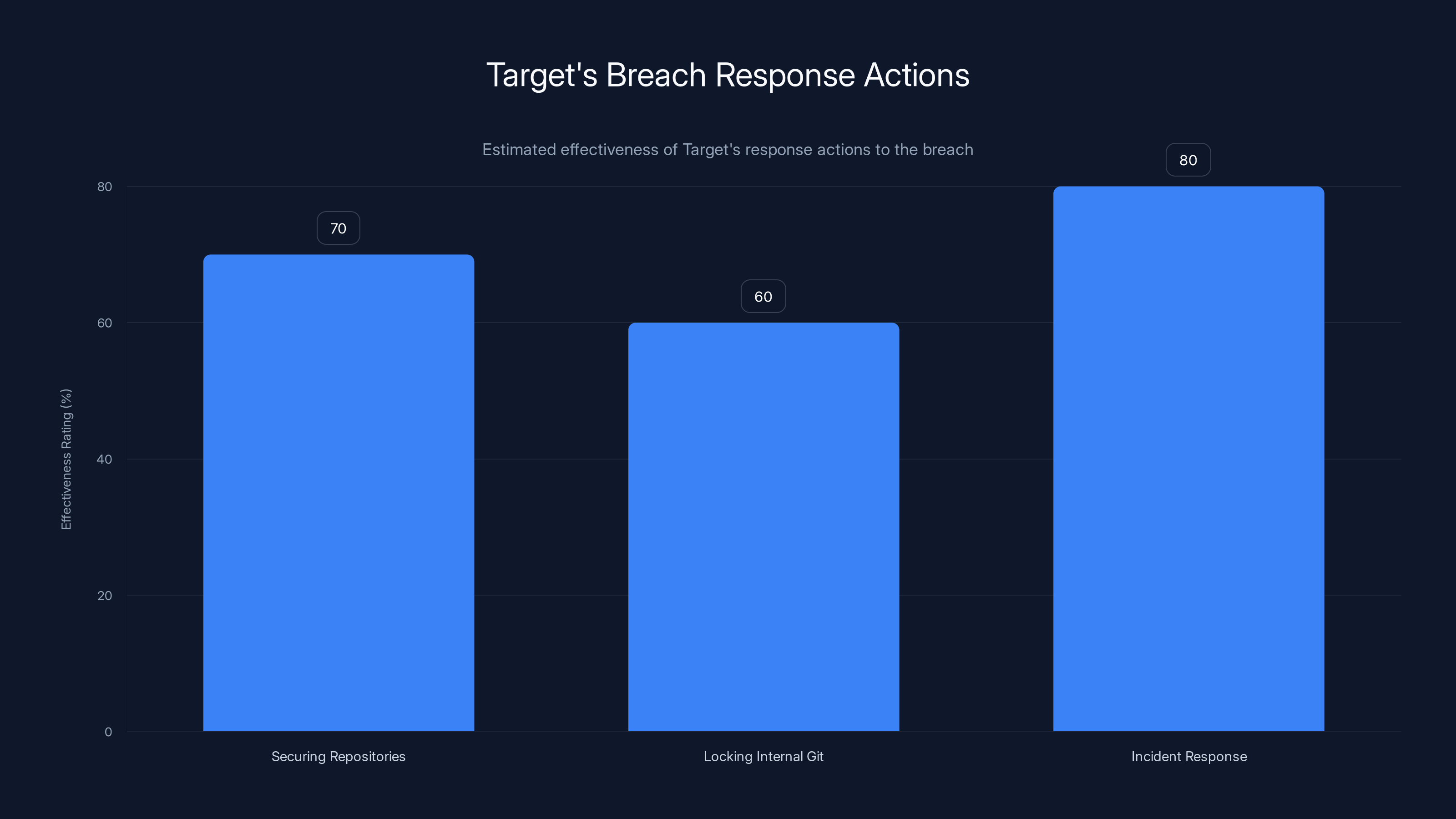
Target's response actions have varying effectiveness, with incident response being the most effective. Estimated data.
Regulatory and Legal Consequences
This breach will trigger a cascade of regulatory and legal processes that will affect Target for years.
SEC Disclosure Requirements: As a publicly traded company, Target must disclose material security incidents to the SEC. Executives must certify that disclosure. If the disclosure is incomplete or materially misleading, executives can face personal liability.
State Attorney General Investigations: All 50 states have data breach notification laws. Some states have specific requirements about what must be disclosed and how quickly. Massachusetts and California have particularly strict requirements.
FTC Enforcement: The Federal Trade Commission will likely investigate whether Target's cybersecurity practices were adequate. If the FTC determines that Target failed to implement reasonable security measures, they can impose significant penalties and mandatory security improvements.
Lawsuits: Target will likely face class action lawsuits from customers and employees. Even if no customer data was directly compromised, lawyers can argue that the breach exposes customers to increased fraud risk from zero-day vulnerabilities discovered using the source code.
Insurance Claims: Cyber liability insurance may cover some costs, but the policy will be scrutinized for exclusions. Insurance companies will investigate whether Target failed to implement basic security controls (like Git server access restrictions) that would void coverage.
Payment Card Industry (PCI) Compliance Review: If any payment processing code was compromised, this triggers deep PCI compliance investigations. Target may face increased audit requirements and mandatory security controls.
International Data Protection Laws: If Target serves European customers (which they do), the General Data Protection Regulation (GDPR) applies. EU data protection authorities can impose fines of up to 4% of annual revenue for security failures.
The financial consequences will be measured in hundreds of millions of dollars across settlements, remediation, insurance deductibles, and operational costs.
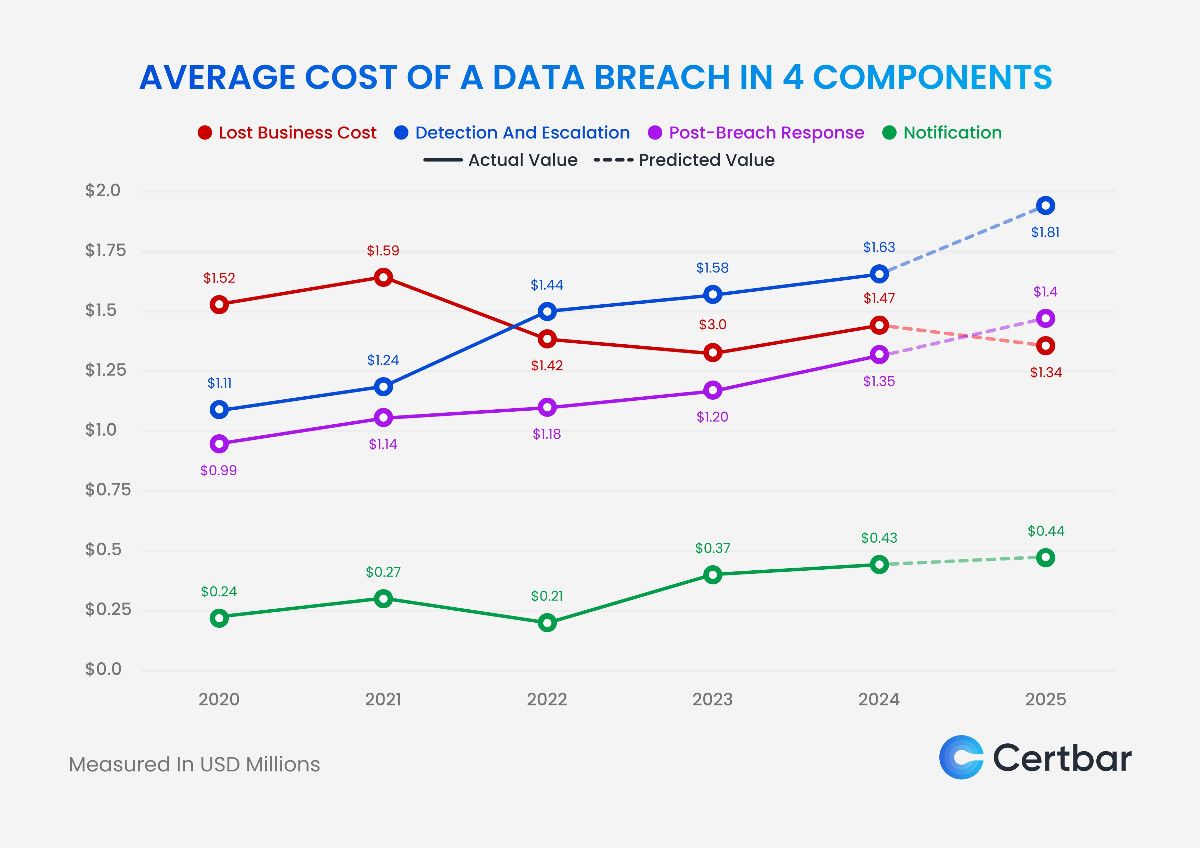
Best Practices: How Other Retailers Should Respond
If you're responsible for security at a retail company, this breach should trigger immediate action. Here are the critical steps:
Immediate Actions (This Week)
Inventory all internet-facing systems. Document every system that's accessible from the internet without VPN authentication. For each system, verify that it has proper authentication, encryption, and access logging.
If you find systems like git.target.com that should be internal but are internet-accessible, take them offline immediately or put them behind VPN.
Review access to your source code repositories. Who has access? Why do they have access? Are there shared credentials or default passwords? Can you generate an audit trail of who accessed what and when?
Short-Term Actions (This Month)
Implement secret scanning on all Git repositories. Scan for API keys, database passwords, private keys, and other secrets that developers might have committed. Remove any secrets found and rotate the actual credentials immediately.
Enable multifactor authentication (MFA) on all Git repository access. A compromised password shouldn't grant access without an additional authentication factor.
Implement granular access controls on sensitive repositories. Not all developers need access to payment processing code or identity management systems. Restrict access to those who absolutely need it.
Medium-Term Actions (This Quarter)
Deploy a Data Loss Prevention (DLP) system that monitors for large data exfiltration. If someone tries to copy 860GB of data, the system should block it or at least alert you immediately.
Implement comprehensive network monitoring and anomaly detection. Look for unusual patterns: a user accessing source code they normally don't access, accessing it at unusual times, or accessing unusually large amounts of data.
Conduct a comprehensive security audit of all external systems. Hire a qualified penetration testing firm to attempt to access your source code repositories from the internet. If they succeed, you have a serious problem.
Long-Term Actions (This Year)
Move to a zero-trust security model. Don't assume that anyone inside your network is trustworthy. Require authentication and authorization for everything. Segment your network so that a compromise of one system doesn't automatically grant access to everything.
Implement proper change management and code review processes. Even if attackers get your source code, they won't be able to exploit it if you have strong security practices for deploying changes.
Build security into development processes from the start. Security shouldn't be an afterthought or an audit requirement. It should be integral to how code is written, reviewed, and deployed.
Establish an incident response plan specific to source code theft. Know exactly what you'll do if this happens to you. Practice the plan regularly.
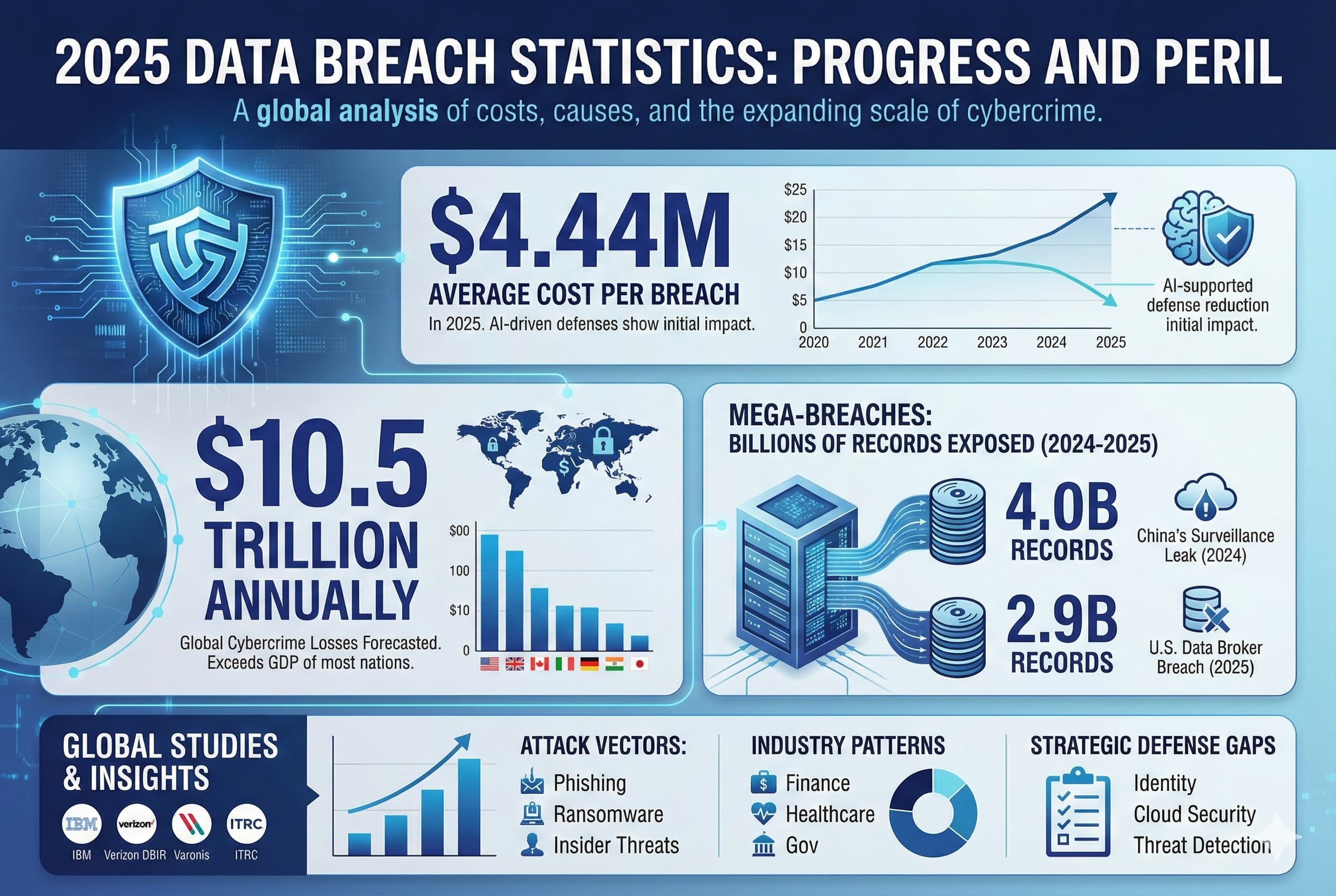
The Broader Cybersecurity Landscape
The Target breach is one of many recent incidents affecting large retailers and enterprises. The pattern is clear: attackers are getting better at finding and exploiting security gaps, and organizations are struggling to defend at the necessary scale.
Source code theft is becoming increasingly common because:
Value Appreciation: As organizations digitize operations, source code becomes more valuable. The code that runs your business is now a tradeable commodity.
Vulnerability Discovery: Source code is the ultimate vulnerability discovery tool. Why fuzz and probe when you can just read the code?
Skill Availability: The underground ecosystem has developed sophisticated tools and techniques for finding and exploiting source code. This expertise is democratized and available to many threat groups.
Monetization Paths: There are now established markets for selling source code, trading it for access to other systems, or using it as leverage for extortion.
For companies like Target, the response will determine their security posture for years to come. Half-measures and band-aids won't be sufficient. The breach points to fundamental failures in network segmentation, access control, and monitoring. Fixing these failures requires investment and architectural changes.

Looking Forward: Predictions and Recommendations
Based on this breach and similar incidents, several trends are likely:
Increased Regulatory Scrutiny: Regulators will demand stricter requirements for protecting source code. Expect new regulations requiring encryption, access logging, and incident response capabilities for source code repositories.
Source Code Becomes a Critical Asset: Organizations will start treating source code repositories with the same security controls they apply to their most critical systems. This means network segmentation, advanced monitoring, and stringent access controls.
Insurance Market Tightening: Cyber liability insurance will become more expensive and more selective. Organizations with weak security controls will face higher premiums or exclusions for certain types of incidents.
Talent Shortage Worsens: Good security talent is already scarce. This breach will create increased demand for security professionals who understand infrastructure, networking, and incident response. Expect salary increases and competition for talent.
Supply Chain Risk Focus: Organizations will demand security improvements from vendors and partners. If you're a vendor to Target, expect increased audit requirements and security certifications.
For Target specifically, the breach is an opportunity to demonstrate that large organizations can respond to security incidents seriously. If Target significantly improves their security posture, it sends a message to other retailers. If they engage in minimal remediation, it suggests that even billion-dollar companies don't take security seriously.
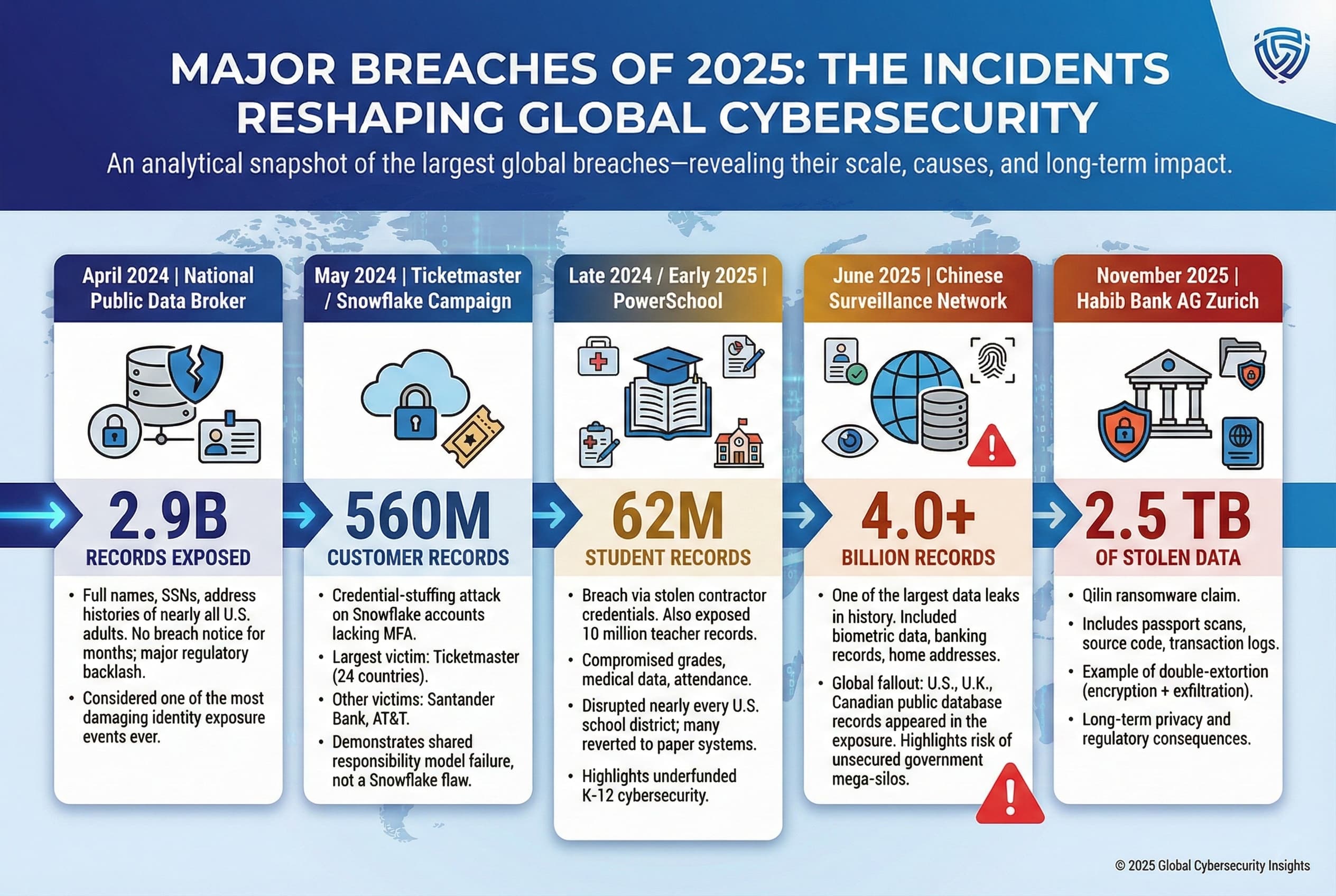
FAQ
What exactly was stolen in the Target breach?
Approximately 860GB of source code, configuration files, and developer documentation were allegedly stolen. The data includes implementation code for wallet services, identity management systems, gift card processing, store networking tools, and internal documentation. The threat actor provided samples by uploading repositories to Gitea that contained 57,000+ files as proof.
How did the breach happen and when was it discovered?
The exact entry vector hasn't been publicly disclosed by Target, but common vectors include unpatched remote access systems, compromised credentials, or supply chain compromises. The breach was discovered when the threat actor publicly posted claims in underground hacking communities and provided samples. The exact timeline from initial compromise to discovery remains unknown.
Why is source code more dangerous than payment card data?
Source code is more valuable than payment card data because it reveals exactly how systems work. With source code, attackers can identify zero-day vulnerabilities, understand authentication mechanisms, find hardcoded secrets, and craft undetectable exploits. Payment card data expires; source code is permanent and reveals the infrastructure for future attacks.
How can retailers prevent similar breaches?
Retailers should implement network access controls restricting source code repositories from internet access, require multifactor authentication for all Git access, scan repositories for hardcoded secrets, implement data loss prevention systems to detect large exfiltrations, and deploy comprehensive network monitoring for anomalous access patterns. Most importantly, they need to treat source code repositories as critical assets worthy of the highest security controls.
Is the breach authenticity verified?
The authenticity cannot be definitively verified from public information, but several factors suggest it's credible: the specific internal references in the sample repositories, the consistency across multiple repositories, the naming of current Target engineers, and Target's rapid response to lock down their servers. These would be difficult to fake convincingly.
What are the long-term consequences for Target?
Target will face SEC disclosure requirements, state attorney general investigations, FTC enforcement actions, class action lawsuits, cyber liability insurance claims, PCI compliance reviews, and potential GDPR violations if European customers' data was accessed. The total financial and operational impact could reach hundreds of millions of dollars over several years.
Should other companies be concerned about similar breaches?
Absolutely. If Target was vulnerable, most retailers likely are as well. The retail industry as a whole has struggled with cybersecurity. Organizations should immediately inventory internet-facing systems, review Git repository access controls, implement secret scanning, enable MFA, and conduct comprehensive security audits to identify and remediate similar vulnerabilities.
How does this breach compare to Target's 2013 breach?
The 2013 breach involved 40 million credit card numbers and 70 million records of personal information, costing approximately $18.5 million in settlements and remediation. This breach is more dangerous because source code is more valuable than the data compromised in 2013, but the financial consequences depend on how the code is used. If vulnerabilities discovered in the code are exploited at scale, consequences could far exceed the 2013 breach.
What should customers do if they're concerned?
Customers should monitor their accounts for suspicious activity, consider using Target's mobile wallet instead of credit cards (the implementation might be compromised but payment networks will still provide fraud protection), enable multifactor authentication on their Target account if available, and watch for regulatory notifications from Target about recommended actions. Most of the risk accrues to Target, not to customers directly.
How long might it take for Target's response and recovery?
A comprehensive response to source code theft typically takes 6-12 months for forensic investigation, remediation, and infrastructure improvements. But full recovery—restoring customer confidence and implementing all necessary security improvements—typically takes 18-24 months or longer. Target will likely be dealing with regulatory investigations and lawsuits for years.
Conclusion: The Retail Cybersecurity Reckoning
The Target breach, if verified, represents a watershed moment for retail cybersecurity. For too long, retailers treated security as a compliance checkbox rather than a fundamental business requirement. They invested minimally in infrastructure hardening while maximizing pressure on development teams to move fast.
This breach exposes that approach as unsustainable. When 860GB of internal source code is exfiltrated and advertised for sale in underground hacking communities, the problem isn't isolated. It's systemic. It reflects fundamental failures in network architecture, access controls, security monitoring, and incident response.
The numbers tell the story. Target's external Git server was accessible from the internet. That's not a sophisticated attack circumventing advanced defenses. That's basic negligence in fundamental security hygiene. If git.target.com was internet-accessible without proper authentication, what about the other 50 or 100 or 500 internet-facing systems Target operates?
For Target's leadership, this breach is an inflection point. They can respond with minimal measures, implement surface-level fixes, and hope regulators are lenient. Or they can recognize this as an opportunity to fundamentally rebuild their security posture and demonstrate that large organizations can take security seriously.
For other retailers, the message is urgent: audit your infrastructure now. Document every internet-facing system. Verify that every system has proper authentication, encryption, and access logging. If you find gaps, address them immediately. This isn't theoretical anymore. The blueprint for exploiting retail infrastructure is publicly available, and threat actors are actively targeting the industry.
The retail cybersecurity landscape is changing. Organizations that move quickly will be ahead of the curve. Those that delay will find themselves explaining breaches to regulators, prosecutors, and angry customers. The Target breach is a warning shot. How the industry responds will determine whether retail cybersecurity improves or continues its downward spiral.
The technology exists to prevent breaches like this. Network segmentation, proper access controls, encryption, monitoring, and incident response capabilities are all mature and well-understood. The question isn't whether retailers can secure their infrastructure. The question is whether they will. The Target breach suggests the answer has been no. That needs to change, immediately.

Key Takeaways
- Target's 860GB source code breach exposes internal systems including wallet services, identity management, and gift card processing
- Source code is more dangerous than payment data because it enables zero-day vulnerability discovery and custom exploit development
- Target's internet-accessible Git server (git.target.com) represents basic security failure in infrastructure hardening
- Retailers must immediately audit external systems, restrict Git access, implement secret scanning, and deploy data loss prevention
- Long-term consequences span 18-24 months of regulatory investigations, lawsuits, and mandatory security improvements costing hundreds of millions
Related Articles
- Why Cybercriminals Are Getting Younger: The Crisis of 2025 [2025]
- Scattered Lapsus$ Hunters Caught in Honeypot: Inside the Bust [2025]
- ExpressVPN macOS Update 2025: Split Tunneling and 5 Major Features Explained [2025]
- ExpressVPN 78% Off Deal: Is It Worth It in 2025?
- Hackers Targeting LLM Services Through Misconfigured Proxies [2025]
- IBM Bob AI Security Vulnerabilities: Prompt Injection & Malware Risks [2025]
![Target Data Breach 2025: 860GB Source Code Leak Explained [2025]](https://tryrunable.com/blog/target-data-breach-2025-860gb-source-code-leak-explained-202/image-1-1768322170979.jpg)



