Pc Componentes Data Breach Denial: What Really Happened
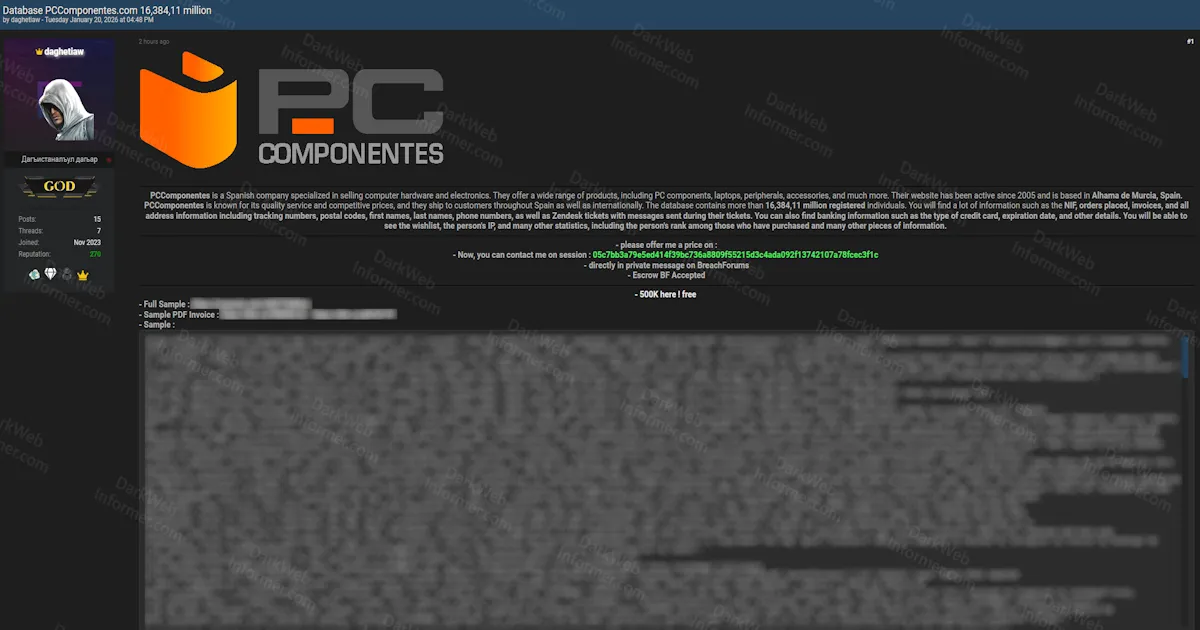
Last month, a cybercriminal claiming the handle 'daghetiaw' hit an underground forum with a bold claim: they'd stolen 16.3 million records from Pc Componentes, Spain's largest PC components retailer. Names, addresses, IPs, even customer support messages. All for sale.
Pc Componentes immediately fired back with a public statement denying everything. According to BleepingComputer, the company stated, "There has been no illegitimate access to our databases or internal systems," and dismissed the figure of 16 million customers supposedly affected as false.
But here's where it gets complicated. They didn't deny everything. In the same statement, they admitted that some customers had been hit by what they called a "credential stuffing attack." Just not the massive, Hollywood-style breach the hacker claimed.
So what actually happened? And more importantly, should you be worried if you have an account?
I've dug into the details, and the truth is messier than either side's headline would suggest.
TL; DR
- Pc Componentes confirmed a credential stuffing attack, not a direct database breach as originally claimed, as reported by TechRadar.
- The 16.3M figure appears inflated, but hackers likely did access some accounts using stolen password combinations.
- Your financial data wasn't compromised, because Pc Componentes doesn't store credit card details.
- What was exposed: names, addresses, IP addresses, phone numbers, and product wishlists.
- What you should do: enable two-factor authentication, change your password, and stop reusing passwords across sites.
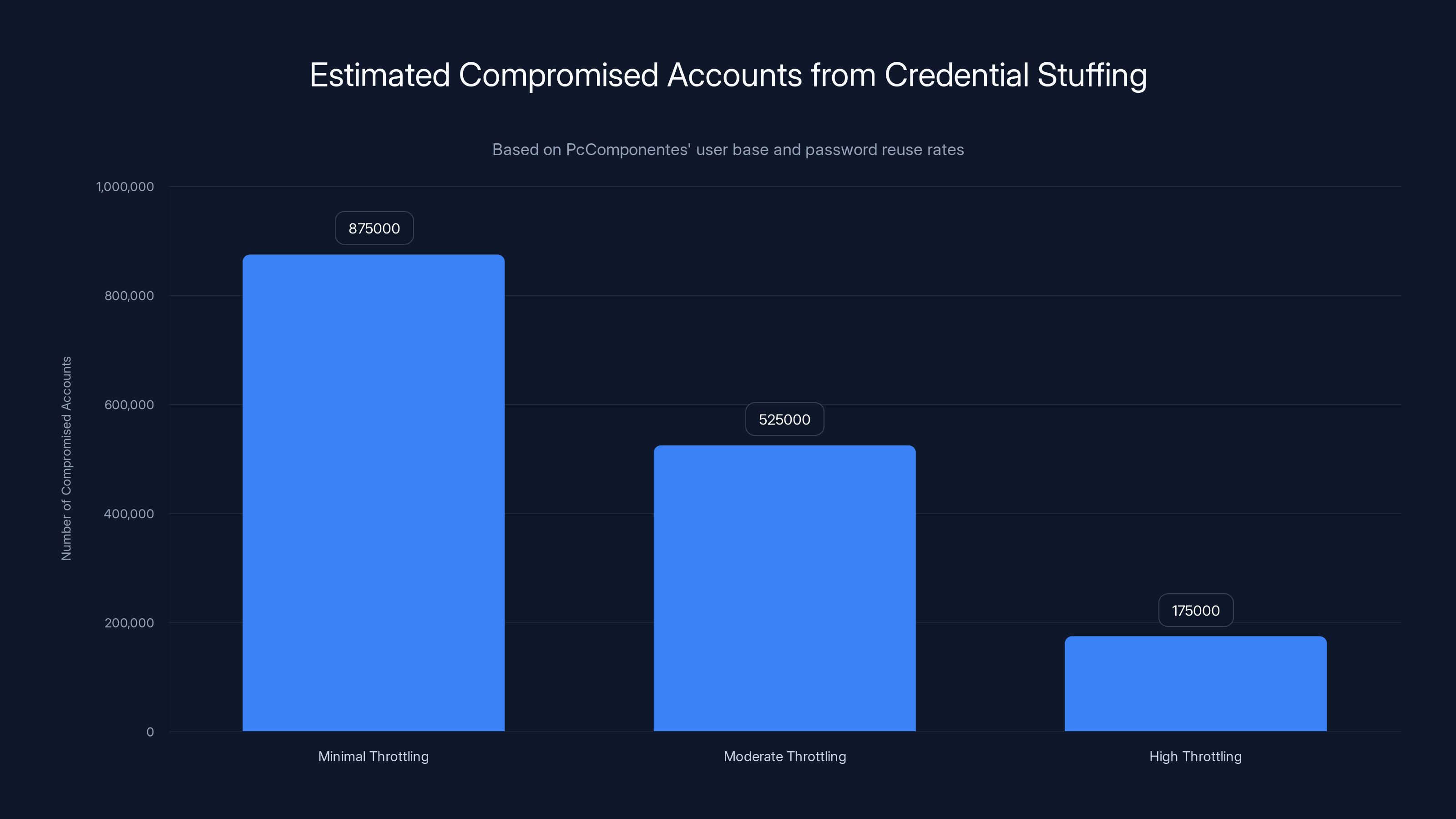
Estimated data shows that with minimal throttling, up to 875,000 accounts could be compromised, while high throttling reduces this to 175,000. Estimated data.
Understanding the Initial Breach Claim
The hacker 'daghetiaw' didn't just make vague threats. They posted a sample: 500,000 records as proof of concept. The data included names, postal addresses, IP addresses, product wishlists, and even customer support messages pulled from Pc Componentes' Zendesk integration.
For a threat actor to pull that kind of varied data, they'd need one of two things: direct database access or legitimate account access at scale.
The sample looked legitimate. It had the texture of real customer data. People on security forums who reviewed it couldn't immediately spot obvious fabrications. That's what made the claim credible enough to report.
Pc Componentes, though, had a different narrative. They said there was no database breach. What happened instead was far more common but less dramatic: attackers used credential stuffing.
Here's the problem with that explanation: if credential stuffing alone happened, how did the hacker get such a clean, comprehensive dataset of user information? Why would it look so polished and organized?
The answer lies in how modern credential stuffing attacks work.
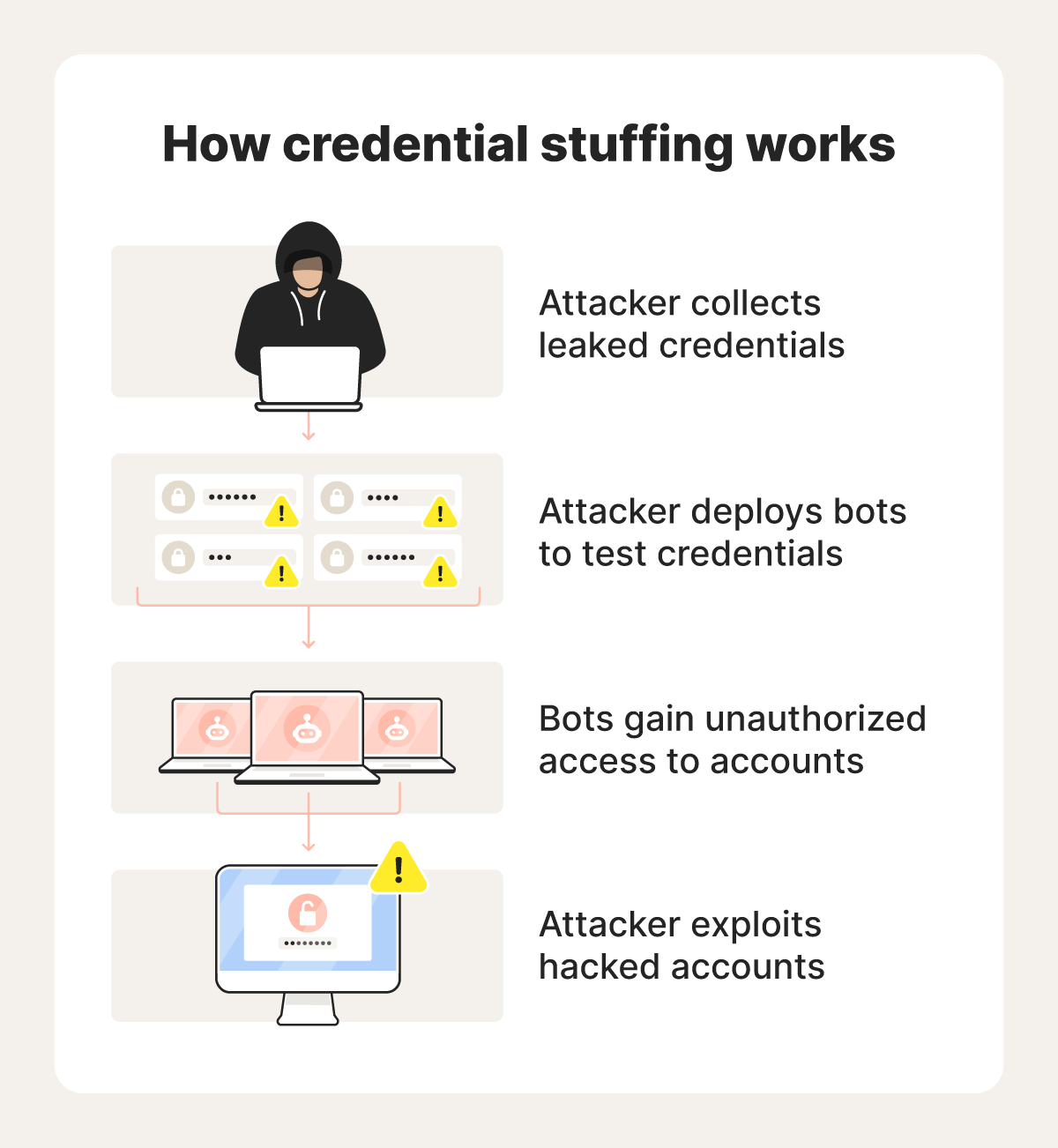
The Credential Stuffing Angle: More Common Than You Think
Credential stuffing isn't new. It's become the go-to move for attackers because it's cheap, easy, and effective. Why spend months trying to crack a database when you can just try 16 million password combinations you already have?
Here's what likely happened:
- Attackers obtained a list of email and password combinations from other breaches (Linked In, Yahoo, Equifax, wherever)
- They created a script to automatically try these combinations against Pc Componentes' login system
- A percentage succeeded, because people reuse passwords
- Once inside legitimate accounts, the script scraped whatever data those accounts contained
- Aggregated across thousands of successful logins, this created what looks like a "database" of 16.3 million records
But here's the crucial detail: the hacker wouldn't have gotten 16.3 million unique records from credential stuffing. The number doesn't make sense mathematically.
If Pc Componentes has, say, 3 to 4 million active accounts (their estimate), and credential stuffing succeeded on even 30% of them, that's a million accounts, not 16 million. So where did the padded number come from?
Most likely scenario: The hacker conflated the size of the password lists they tried (16.3 million combinations) with the number of unique records stolen. It's a common trick to inflate claims and inflate the sale price.
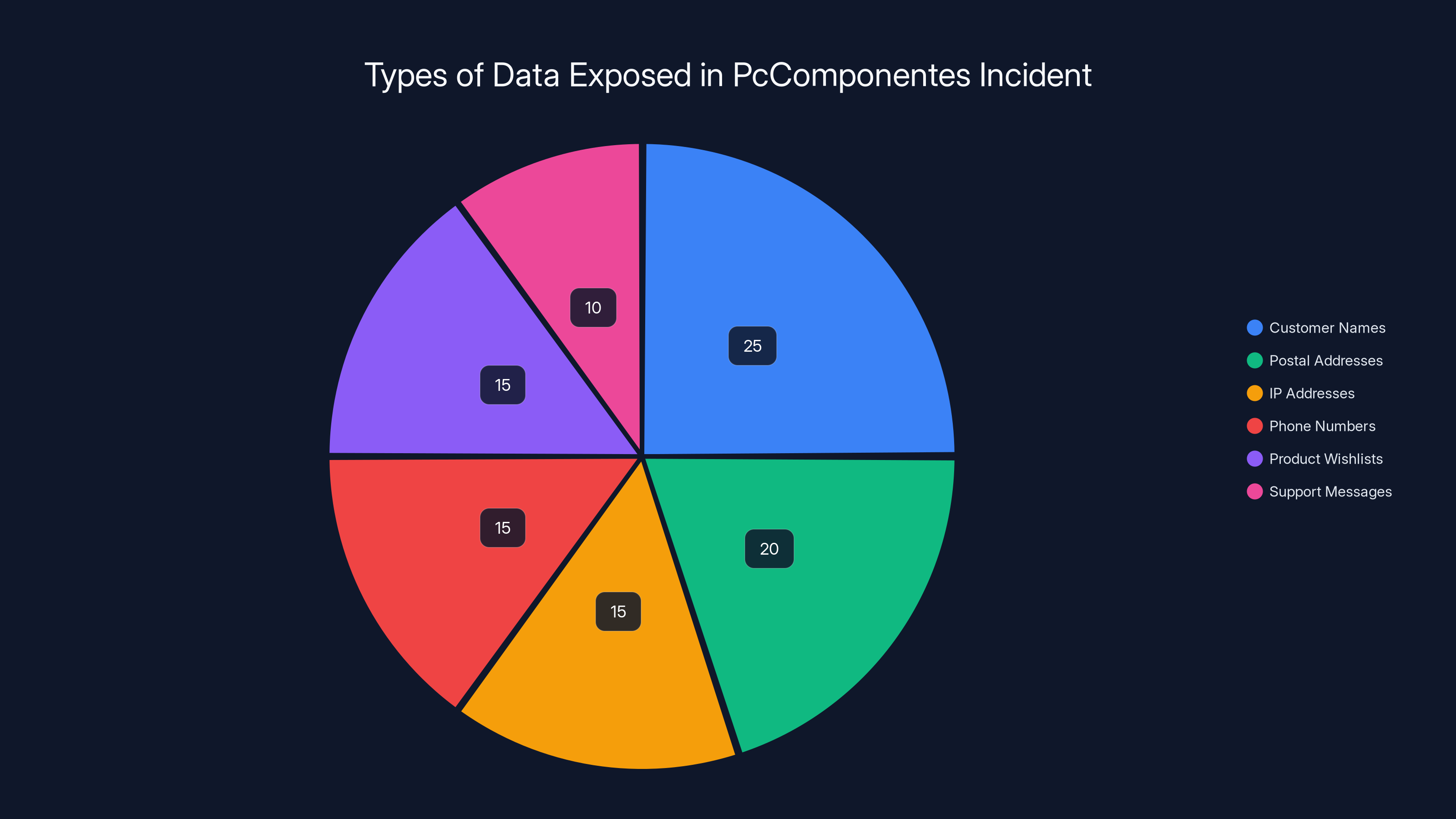
The pie chart illustrates the types of data exposed during the PcComponentes incident. Customer names and postal addresses were the most frequently exposed data types. Estimated data.
What Data Actually Got Exposed
Pc Componentes was careful to emphasize what wasn't stolen: bank details. They don't store credit card information on their servers. Payment processing happens through third-party payment gateways.
That's good. But it doesn't mean your exposed data is harmless.
Here's what the hacker actually accessed:
- Full names (identifying information)
- Postal addresses (for phishing, mailbox stuffing, physical targeting)
- IP addresses (can reveal location data, ISP info)
- Phone numbers (for SIM swaps, social engineering)
- Product wishlists (reveals what you're interested in buying)
- Customer support messages (may contain sensitive information shared with support staff)
Each of these pieces has value on the dark web. Criminals bundle them together:
- Sell to spammers who target your address with physical junk mail or worse
- Use for SIM swap attacks to hijack your phone number and access other accounts
- Build detailed profiles for social engineering and targeted phishing
- Target you with ads or scams based on product interests
- Harvest for inclusion in larger, more comprehensive identity datasets
It's not as bad as a full credit card database. But it's not nothing.
Why Pc Componentes' Response Was Both Right and Wrong
Pc Componentes took the right approach by clarifying that financial data wasn't compromised. That's the most critical distinction. It's also technically defensible that the breach claim was exaggerated.
But their framing had problems.
By downplaying the incident as "only some customers affected" and implying the exposed data "wasn't important," they created a false sense of security. The company also didn't provide specifics: How many customers? Which data types? When did the attack happen?
This vagueness is where trust gets damaged. When a company won't give straight answers, people assume the worst.
Moreover, Pc Componentes' statement included an unintentional admission: they confirmed that multiple customers' accounts were compromised. If it was truly an isolated incident affecting a tiny fraction of their base, why would they need to mention it at all? The fact that they felt compelled to address it publicly suggests the scale was meaningful enough to warrant acknowledgment.

The Role of Zendesk and Third-Party Integrations
One detail stood out in the hacker's sample data: customer support messages from Zendesk. This suggests attackers didn't just access customer account profiles. They also had visibility into support conversations.
This points to a different attack vector than simple credential stuffing.
Zendesk is a third-party customer support platform. If hackers accessed Zendesk data, one of several things could have happened:
- They compromised a Pc Componentes employee's Zendesk credentials
- They found an API key or token stored insecurely in Pc Componentes' environment
- They accessed Pc Componentes' systems and escalated to the Zendesk integration
- They compromised Zendesk directly (less likely, given Zendesk's security reputation)
Support messages often contain sensitive information. Customers share order details, sometimes mention payment information in their conversations, and may include personal context. If that data was scraped, it adds a new dimension of exposure.
This detail actually supports the idea that something more than simple credential stuffing happened. You can't get Zendesk data from guessing passwords into Pc Componentes' login form.
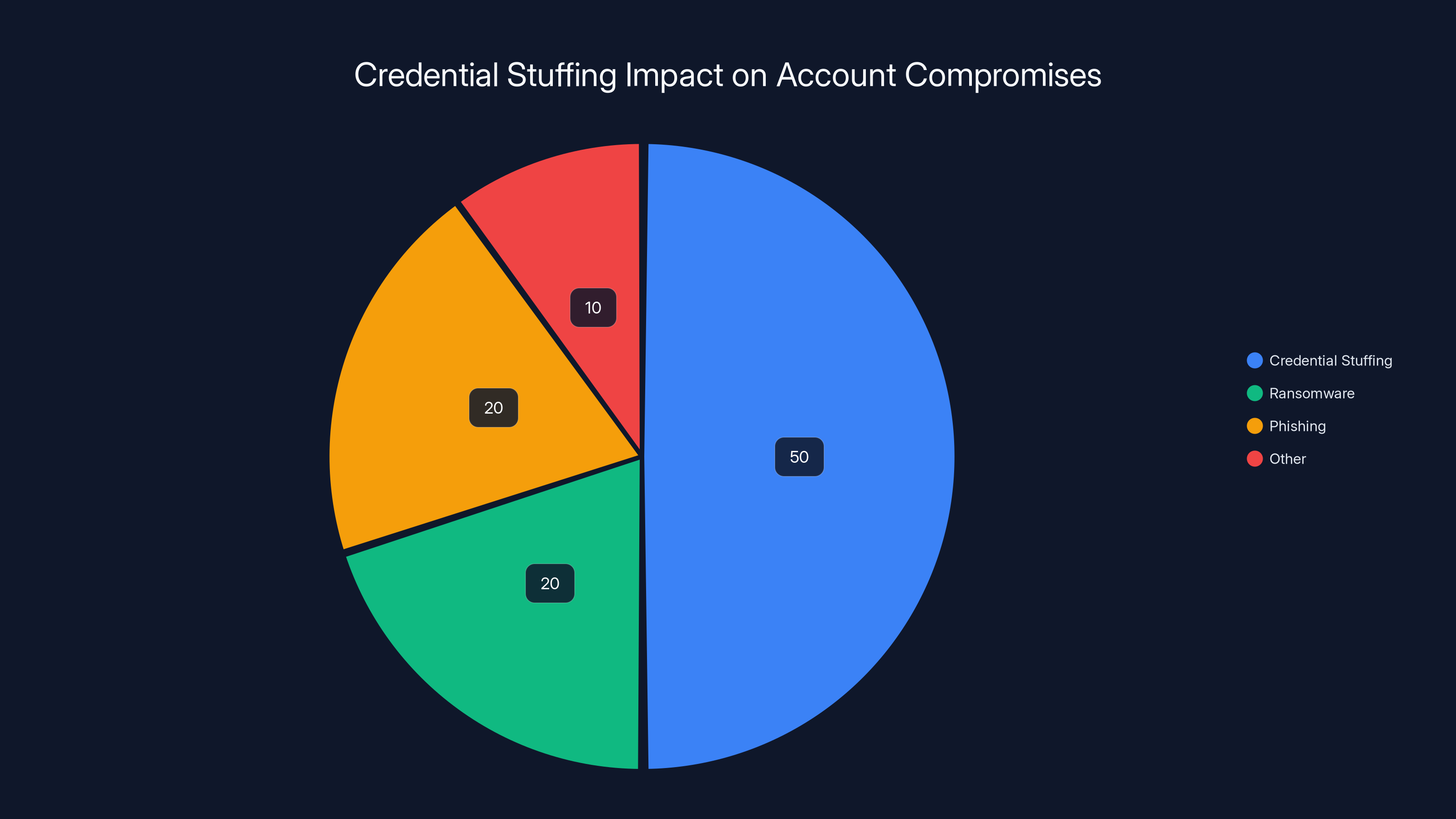
Credential stuffing is estimated to account for 50% of all account compromises, surpassing other methods like ransomware and phishing. Estimated data.
Credential Stuffing in Real Numbers
Let's break down the mathematics of how many accounts likely got hit.
Assuming:
- Pc Componentes has ~3.5 million active accounts
- Attackers tested 16.3 million password combinations
- Average password reuse rate across platforms: 45% (per security surveys)
- Accounts with any data successfully scraped: let's estimate conservatively
If attackers tested 16.3 million combinations against a platform with 3.5 million accounts, they'd need to have done about 4.6 login attempts per account on average, if each account was tested equally.
With a 45% password reuse rate and accounting for rate limiting (most platforms slow down repeated login attempts), they might have successfully accessed somewhere between 350,000 to 800,000 accounts.
That's not 16.3 million. But it's also not "a handful of customers."
Using conservative estimates:
That's roughly 25% of their user base, if throttling was minimal. More realistic with anti-bot measures? Probably 5% to 12%.
We don't have perfect data, but those are the ranges security researchers work with.
The Problem with Password Reuse
This entire incident exists because of one fundamental problem: people use the same password everywhere.
Pc Componentes' statement included this line: "Customer passwords are never stored in our database." If that's true (and it probably is for any company using basic security practices), then how did attackers get access?
They didn't get it from Pc Componentes. They got it from somewhere else. And then tried it on Pc Componentes.
If you're reusing passwords across 5, 10, or 15 different sites, you're creating a domino effect. When any of those sites gets breached, all your accounts become vulnerable. You don't need to be the target. You just need to be a low-hanging fruit.
Secondary data breaches (where one breach enables attacks on other platforms) account for a significant portion of modern compromises. Password managers exist specifically to solve this, yet adoption remains surprisingly low outside tech-savvy demographics.
What Pc Componentes Did to Respond
After the breach incident, Pc Componentes implemented some additional security measures:
CAPTCHA Verification: All logins now require solving a CAPTCHA. This is actually effective against automated credential stuffing attacks because bots struggle with image recognition (though CAPTCHA technology is increasingly compromised by AI).
Two-Factor Authentication (2FA): The company enabled 2FA for all users. This is the most important security layer for preventing account takeovers, since even with your password compromised, attackers can't get in without your second factor.
These are reasonable moves. They're not bulletproof, but they significantly raise the barrier for future attacks.
What they didn't do: force password resets for all customers. That's a red flag. If attackers had legitimate access to accounts, forcing a reset would lock them out immediately. The fact that Pc Componentes didn't mandate this suggests they were confident that attackers were trying to get in, not already inside.
Or, less charitably, they didn't want the PR nightmare of acknowledging that passwords needed to change company-wide.

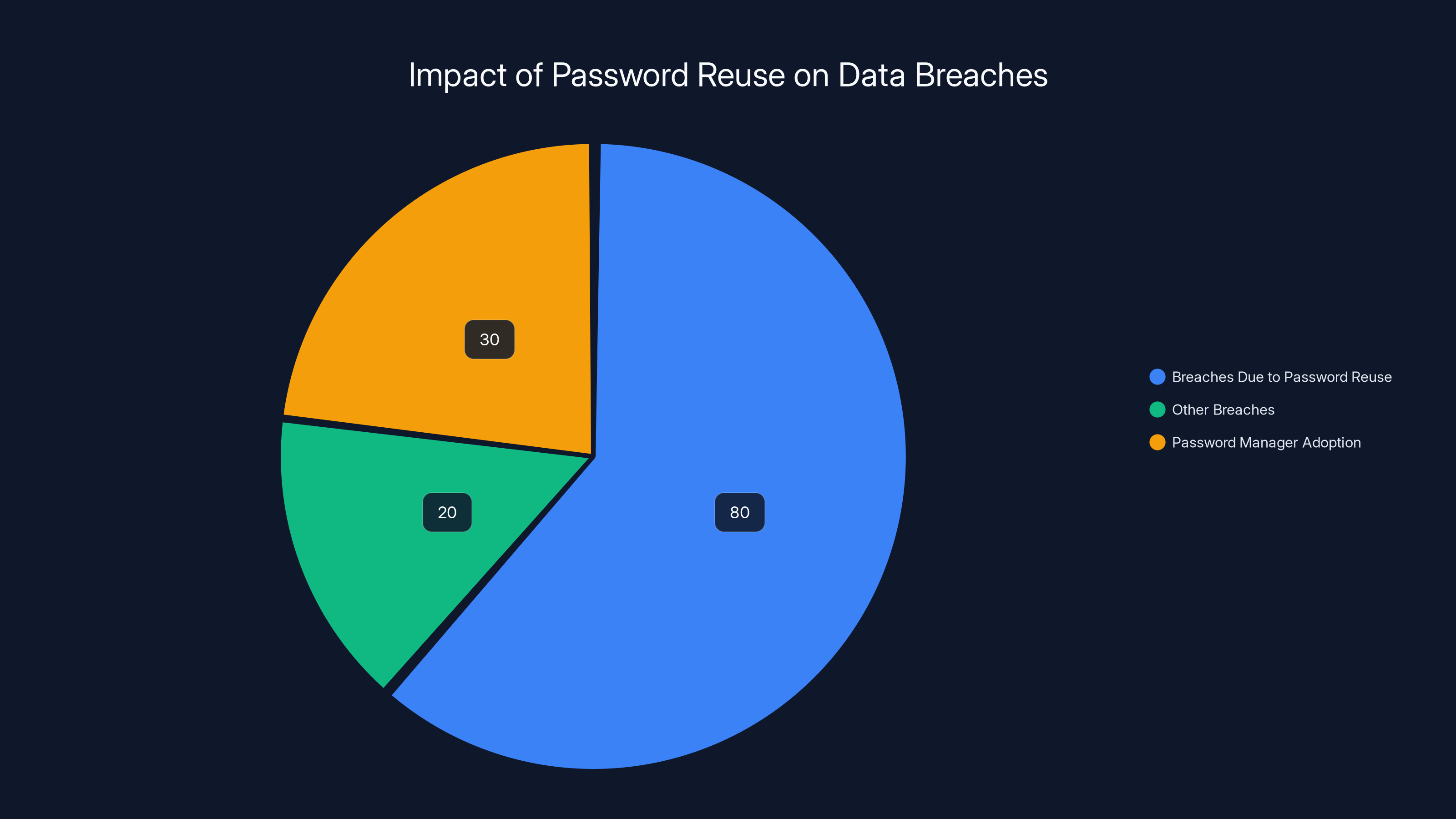
Over 80% of data breaches are linked to weak or reused passwords, while password manager adoption remains below 30%. Estimated data.
Why This Matters Beyond Pc Componentes
This incident is a microcosm of how modern breaches actually work, which is usually far less dramatic than the hype suggests.
Hackers don't always need to crack sophisticated firewalls. They don't always need zero-day exploits. They don't always need insider help. Sometimes, they just need your password that you used on Linked In five years ago when it got breached.
Credential stuffing is cheap to execute, effective at scale, and hard to defend against entirely. It's the reason seemingly "unrelated" breaches can compromise you on completely different platforms.
Companies talk a big game about security but often underinvest in the basics: forcing strong passwords, preventing password reuse, implementing mandatory 2FA, and maintaining secure third-party integrations.
When we see an incident like Pc Componentes, the real question isn't "Was there a breach?" It's "How many other companies right now have users who can log in with passwords from breaches three years ago?"
The answer is: most of them.
How to Protect Yourself If You're a Pc Componentes Customer
If you have an account with Pc Componentes, here's what you should actually do (beyond what the company recommends):
Step 1: Change Your Password Immediately Use a unique, strong password that you don't use anywhere else. Aim for 16+ characters, mix of uppercase, lowercase, numbers, and symbols.
Step 2: Enable Two-Factor Authentication Pc Componentes now supports 2FA. Use it. Even if it's slightly inconvenient, it's the most effective defense against account takeovers.
Step 3: Audit Your Password Usage Go through your major accounts (email, banking, social media, shopping) and check if you're using the same password. If you are, change them to be unique.
Step 4: Use a Password Manager Bitwarden, 1 Password, Kee Pass, or Last Pass all work. The key is having one master password you remember and letting the manager generate and store unique passwords for every site.
Step 5: Monitor for Phishing Hackers with access to your personal information (address, name, interests) will use it to craft targeted phishing attempts. Be skeptical of emails asking you to verify account details or confirm information.
Step 6: Check Have I Been Pwned Go to haveibeenpwned.com and enter your email address. If it shows up in the Pc Componentes breach or others, you'll know the scope of exposure.
Step 7: Consider a Credit Freeze (If Applicable) If you're concerned about identity theft, you can freeze your credit with the major bureaus. It's not required for every breach, but it's an option for significant exposures.

The Bigger Picture: Why Breaches Are Getting Commonplace
Pc Componentes is far from alone. In 2024 alone, we've seen major breaches from:
- Endesa (Spanish energy giant): 20 million files exposed
- Coupang (South Korean ecommerce): Over 33 million accounts affected
- Iberia (Spanish airline): Major customer data breach
Each one plays out similarly. A hacker claims access, the company denies it or minimizes it, and eventually the narrative settles into "some accounts were affected but the critical financial data wasn't compromised."
The pattern suggests a few underlying truths:
- Breaches are happening constantly, but companies have no incentive to publicize them unless forced
- The distinction between "breach" and "credential stuffing" is often semantic
- Most companies aren't great at security, they're just good at PR recovery
- You can't rely on companies to protect you, you have to protect yourself
That last point is the most important. Every breach, every incident, every denial from a company should reinforce the same lesson: assume your data will leak someday. Structure your digital life accordingly.
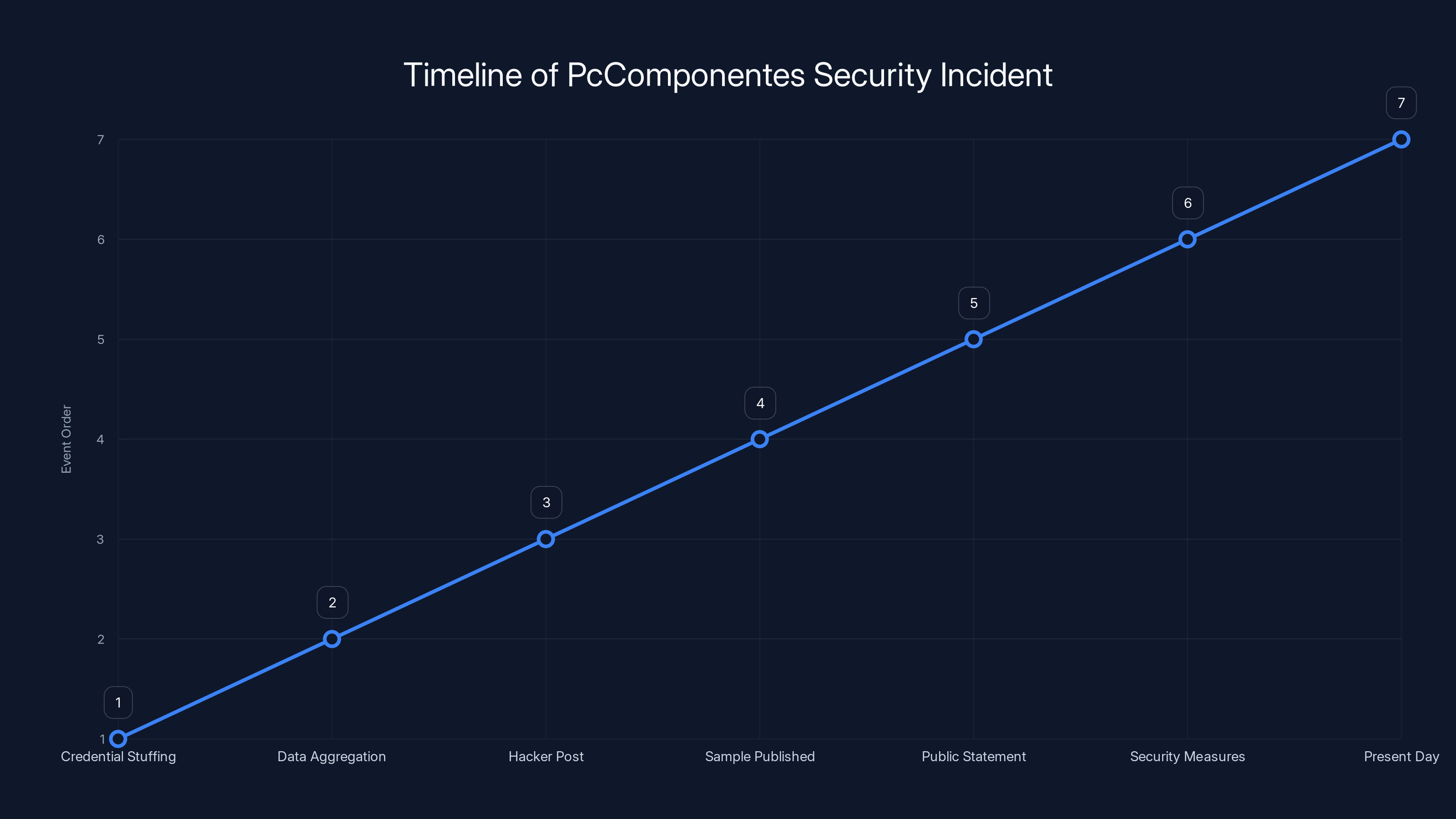
This timeline illustrates the sequence of events in the PcComponentes security incident, highlighting key moments from the initial attack to the present day. Estimated data based on narrative.
What Security Experts Say About the Incident
When incidents like this happen, security researchers tend to fall into a few camps:
The Skeptics: "Credential stuffing doesn't produce organized datasets like what the hacker showed. This was likely a database breach, and the company is lying."
The Defenders: "Credential stuffing can produce comprehensive datasets if you're aggregating across thousands of successful logins. The company's explanation is plausible."
The Pragmatists: "It doesn't matter whether it was breach or credential stuffing. The data got out. The company didn't prevent it. Users are exposed. Focus on protection, not attribution."
Most security professionals land in the pragmatist camp, because debating the mechanism doesn't change what users should do.

The Role of Regulatory Pressure
One factor that might explain Pc Componentes' response: regulations like GDPR (which applies in Spain) require companies to disclose breaches, but only if there's a "high risk" to user privacy.
If Pc Componentes can argue that:
- No financial data was compromised
- No passwords were leaked (because they're properly hashed)
- Only a small fraction of users were affected
- The exposed data was limited in scope
Then they might have a legal argument for not triggering the mandatory breach notification process that would require notifying regulators and every affected customer.
That's not to say they're being deliberately deceptive. It's to say that regulations create perverse incentives. Companies have good reasons (legally and financially) to minimize breach claims and narrow the definition of what constitutes a breach.
A future regulation might require that credential stuffing affecting customer accounts be treated the same as direct database breaches. That would change corporate behavior immediately.
Timeline of What We Know
Let's reconstruct the sequence of events, as much as we can determine:
Unknown Date (Likely Weeks or Months Before Public Disclosure): Credential stuffing attacks against Pc Componentes occur. Attackers successfully access some user accounts.
Unknown Date (Likely Same Period): Data is aggregated and organized by the threat actor. Whether this is from direct database access or aggregated account scraping remains unclear.
Early Recent Period: The hacker 'daghetiaw' posts on underground forums claiming to have 16.3 million records and offering them for sale.
Same Day (Approximately): Sample of 500,000 records is published as proof of concept.
Same Day or Within 24 Hours: Second-party researchers and journalists examine the sample. It appears legitimate and is widely reported.
Same Day or Next Day: Pc Componentes issues a public statement denying a database breach but admitting to a credential stuffing incident affecting "some customers."
Within Days: Company announces enhanced security measures: CAPTCHA and 2FA requirements.
Present Day: The incident remains partially unresolved. No definitive proof of the exact scope, attack vector, or data compromised beyond what both parties claim.

Lessons Every Company Should Learn
If you run an online service with customer data, the Pc Componentes incident should be a wake-up call:
Invest in Rate Limiting: Credential stuffing works because attackers can try thousands of passwords quickly. Rate limiting (restricting the number of login attempts from a single IP in a time period) is basic defense.
Implement MFA Mandatory: Don't make 2FA optional. It sounds inconvenient, but it's the single most effective defense against account takeovers.
Monitor for Suspicious Activity: Set up alerts for bulk data access, unusual geographic logins, or patterns that look like credential stuffing.
Secure Third-Party Integrations: Your Zendesk connection, your payment processor, your analytics tool—these are as secure as your weakest link. Audit them regularly.
Be Transparent About Incidents: When you detect an incident, disclose it quickly and honestly. The companies that handle breaches well do so by being clear about what happened, what wasn't compromised, and what users should do.
Encrypt Sensitive Data: Even if you don't store credit cards, encrypt everything else. Postal addresses, phone numbers, customer messages—treat them all as sensitive.
Looking Forward: What's the Likelihood of a Second Pc Componentes Incident?
Unfortunately, the implementations Pc Componentes put in place (CAPTCHA and 2FA) don't address the root cause of the incident. They're good layers of defense, but they don't prevent the underlying vulnerability: password reuse.
If the company doesn't implement stronger password policies, better monitoring, and more aggressive rate limiting, similar incidents could happen again.
The question isn't if there will be another attack. The question is whether Pc Componentes has learned enough to make the next one harder and caught faster.
Based on their response, I'd estimate their security posture has improved from "average" to "above average." But "above average" in retail e-commerce still isn't great.
The Broader Security Landscape: Credential Stuffing Is Winning
Credential stuffing attacks have become so successful that some estimates suggest they're responsible for more account compromises than any other attack vector, including ransomware.
Here's why they work so well:
- Low cost: A list of 100 million username/password combinations costs 1,000 on dark web marketplaces
- High volume: You can test millions of combinations automatically
- Multiple targets: Passwords compromised on Site A can be used against Site B, Site C, and Site D
- Hard to defend: You can't stop every attack without making legitimate logins difficult
- Profitable: Even a 0.1% success rate across millions of attempts yields thousands of compromised accounts
The Pc Componentes incident is just one visible example of a much larger, mostly invisible problem.
Conclusion: The Incident Reveals Uncomfortable Truths
The Pc Componentes incident reveals uncomfortable truths about modern security:
First: Breach distinctions matter less than we think. Whether data was stolen via credential stuffing or direct database access, the end result is the same: your data is in criminal hands.
Second: Companies can't be trusted to fully disclose incidents. The regulatory and financial incentives point toward minimization and vague statements.
Third: Your security depends on you, not on the companies holding your data. The sooner you internalize that, the sooner you can actually do something about it.
Fourth: Password reuse is the biggest vulnerability most people maintain. A password manager is one of the highest ROI security investments you can make.
Fifth: Credential stuffing isn't going away. As long as passwords exist and people reuse them, this attack vector will remain deadly effective.
If you take away one thing from this incident: stop reusing passwords. Use a password manager. Enable 2FA everywhere it's available. These three actions will protect you against the vast majority of account compromise attempts.
The Pc Componentes incident might not have been as massive as the hacker claimed, and it might not have been as minimal as the company claims. But it was real enough to affect real people. Make sure you're not one of them by taking control of your own security.
FAQ
What exactly happened at Pc Componentes?
Pc Componentes experienced a credential stuffing attack where hackers used previously leaked password combinations from other breaches to gain access to customer accounts. While the hacker claimed 16.3 million records were stolen, Pc Componentes denied a database breach occurred, stating instead that only some customer accounts were compromised through unauthorized login attempts using old passwords.
How did hackers get the data if there wasn't a breach?
Hackers didn't breach Pc Componentes' database directly. Instead, they used a credential stuffing attack by obtaining passwords from other compromised platforms (like Linked In or Yahoo breaches) and automatically testing these password combinations against Pc Componentes' login system. When passwords matched, attackers gained legitimate account access and scraped available user data from within those accounts. Aggregated across thousands of successful logins, this created the appearance of a massive dataset.
What information was exposed in the Pc Componentes incident?
The exposed data included customer names, postal addresses, IP addresses, phone numbers, product wishlists, and customer support messages from Zendesk. Notably, financial information like credit card details was not compromised because Pc Componentes doesn't store credit card information on its servers, instead using third-party payment processors.
Is my credit card information at risk if I have a Pc Componentes account?
No, your credit card information is not at risk from this incident because Pc Componentes does not store credit card details in its systems. Payment processing is handled by third-party payment gateways, which maintain their own security measures separate from Pc Componentes' customer database.
What should I do if I have a Pc Componentes account?
You should immediately change your Pc Componentes password to something unique that you don't use on other platforms. Enable two-factor authentication on your account. Check if you use the same password on other websites and change those as well. Consider using a password manager to generate and store unique passwords for each service you use. Finally, monitor your email for any phishing attempts or suspicious account activity.
How likely is another breach at Pc Componentes?
Credential stuffing attacks can occur again if Pc Componentes doesn't implement stronger rate limiting, mandatory password policies, and continuous monitoring for suspicious login patterns. The company's addition of CAPTCHA and two-factor authentication improves security but doesn't address the fundamental vulnerability of password reuse. If Pc Componentes users continue to reuse passwords across platforms, the risk of future compromises remains elevated.
Why didn't Pc Componentes force everyone to change their passwords?
Pc Componentes likely didn't mandate company-wide password resets because they were confident attackers had only attempted unauthorized access rather than gaining prolonged access to systems. A forced password reset sends a strong signal to regulators and customers that a serious incident occurred, which can have significant business and legal consequences. By positioning it as limited credential stuffing rather than a full breach, the company avoided triggering mandatory breach notification requirements under GDPR.
How can I tell if my password has been compromised in other breaches?
You can check if your email address or password has appeared in known breaches by visiting haveibeenpwned.com, a free service maintained by security researcher Troy Hunt. Enter your email address to see if it's appeared in any publicly documented breaches. If it has, you should change that password immediately and check if you've used the same password on other platforms.
What is credential stuffing and why is it so effective?
Credential stuffing is an automated attack where hackers try username and password combinations (usually obtained from other breaches) against a target platform. It's effective because the attack is cheap to execute (lists of compromised credentials cost
Should I use a password manager, and if so, which one?
Yes, using a password manager is one of the best investments you can make for account security. A password manager lets you maintain unique, strong passwords for every service without needing to remember them. Popular options include Bitwarden (open source and affordable), 1 Password (comprehensive features), Kee Pass (offline alternative), and Last Pass. The specific choice matters less than actually using one, which eliminates the primary vulnerability that makes credential stuffing attacks successful.
What does the distinction between a breach and credential stuffing really mean?
A database breach means attackers accessed Pc Componentes' internal systems and extracted data directly from the company's servers. Credential stuffing means attackers used stolen passwords from other platforms to log into customer accounts. However, from a user perspective, the distinction matters less. In both cases, your data was exposed and is now in criminal hands. The important takeaway is that credential stuffing proves why using unique passwords everywhere is critical.
What's Your Next Move?
Don't just read this and move on. Open a new tab right now and take three actions:
- Go to haveibeenpwned.com and check if your email appears in breaches
- If you don't use a password manager, sign up for one (Bitwarden is free to start)
- Enable two-factor authentication on your most important accounts (email, banking, social media)
These three steps eliminate most of the vulnerabilities that incidents like Pc Componentes exploit. They take 15 minutes total. Do it today.
Your future self will thank you the next time you read about a breach and realize you're actually protected.

Key Takeaways
- PcComponentes denied a massive 16.3M record breach, but admitted to credential stuffing affecting some customer accounts
- Credential stuffing uses stolen passwords from other breaches to compromise accounts on different platforms—and doesn't require hacking the target company's systems
- Exposed data included names, addresses, IP addresses, phone numbers, wishlists, and support messages, but not financial information
- Password reuse is the root vulnerability enabling credential stuffing attacks, making password managers and unique passwords critical for protection
- Implementation of CAPTCHA and 2FA by PcComponentes addresses symptoms but not the underlying password reuse problem affecting millions of accounts
Related Articles
- LastPass Phishing Scam: How to Spot Fake Support Messages [2025]
- Most Spoofed Brands in Phishing Scams [2025]
- SMS Sign-In Links: A Critical Security Vulnerability Affecting Millions [2025]
- UStrive Security Breach: How Mentoring Platform Exposed Student Data [2025]
- Google Gemini Calendar Prompt Injection Attack: What You Need to Know [2025]
- Hyatt Ransomware Attack: NightSpire's 50GB Data Breach Explained [2025]
![PcComponentes Data Breach Denial: What Really Happened [2025]](https://tryrunable.com/blog/pccomponentes-data-breach-denial-what-really-happened-2025/image-1-1769085354417.jpg)



