Salt Typhoon Hacks Congressional Emails: Everything You Need to Know About This Major Breach [2025]
Last week, the cybersecurity world got another grim reminder that no institution is truly safe from determined state-sponsored hackers. Salt Typhoon, a Chinese state-sponsored threat actor group, allegedly compromised email systems used by staffers on multiple US House committees focused on China, foreign affairs, intelligence, and defense. This isn't the first time Salt Typhoon has made headlines. In fact, they've become one of the most prolific and audacious cyber-espionage groups operating today.
But here's the thing: most people don't understand what this breach actually means, how these hackers operate, or what the real implications are for national security and cybersecurity broadly. The story goes way deeper than just "emails got hacked." This is about a sophisticated, well-resourced group with state backing conducting intelligence operations on American soil at the highest levels of government.
I've spent the last few days digging into the details, talking with security researchers, and reviewing what's been publicly disclosed. The picture that emerges is both concerning and instructive. Salt Typhoon's tactics, techniques, and persistence tell us a lot about the current state of nation-state cyber-espionage and why traditional security approaches aren't cutting it anymore.
In this comprehensive guide, I'll walk you through exactly what happened, who Salt Typhoon is, how they operate, what data might be at risk, and most importantly, what this means for cybersecurity going forward. Whether you're a cybersecurity professional, a government employee, or just someone interested in understanding modern threats, this breakdown will give you the context and insight you need.
TL; DR
- Major Congressional Breach: Salt Typhoon compromised email systems used by US House committee staffers covering China, foreign affairs, intelligence, and defense.
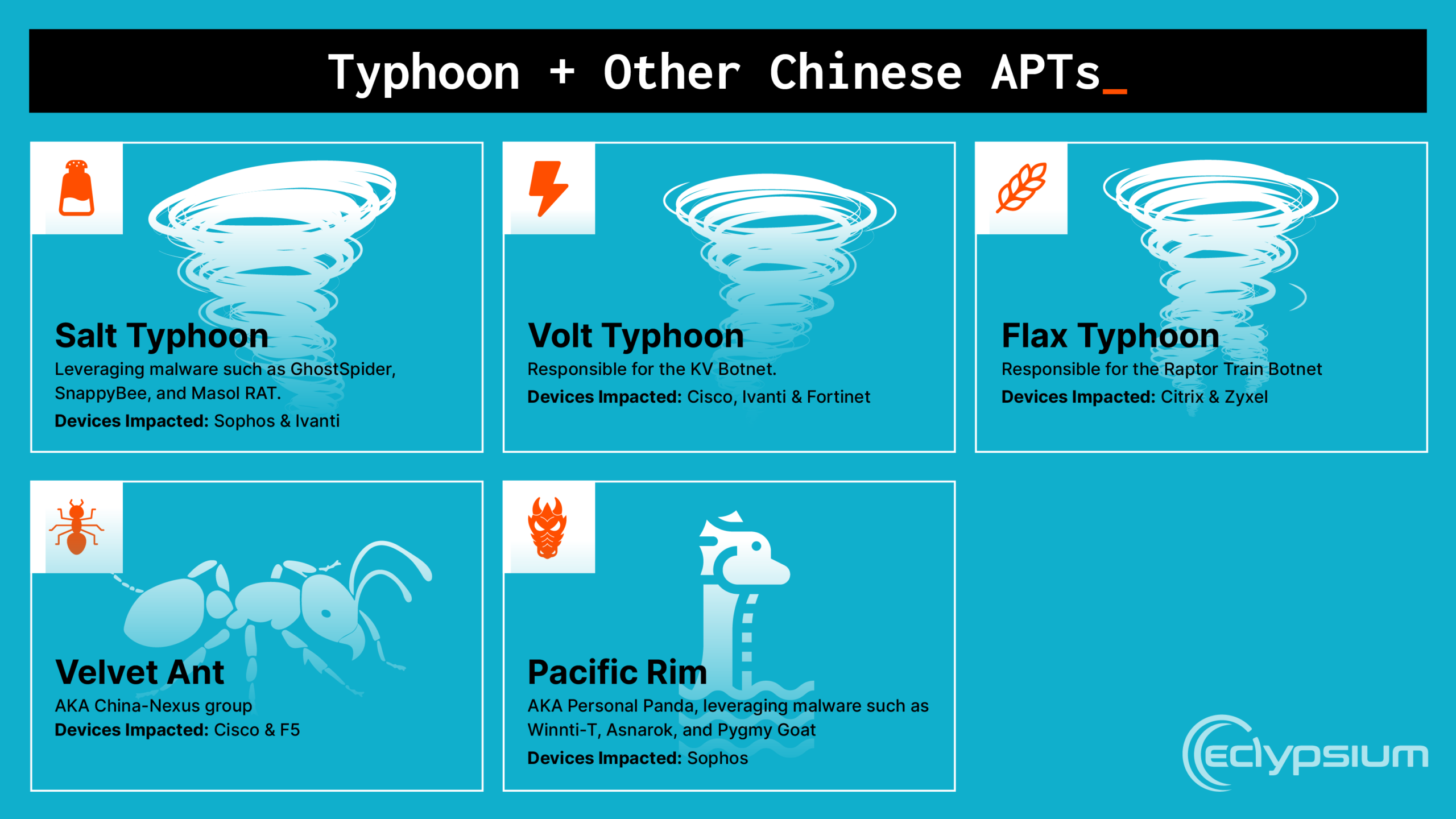
- State-Sponsored Group: Salt Typhoon is a Chinese state-sponsored threat actor part of the broader "Typhoon" nexus of hacking groups.
- Persistent Tactics: The group uses sophisticated techniques including DLL sideloading, zero-day exploits, and supply chain compromises.
- Global Targets: Salt Typhoon has already breached at least 8 US telecommunications companies and has targeted networks across dozens of countries.
- Scope Unclear: The exact extent of the breach remains undisclosed, including whether staffers' or elected officials' emails were compromised.
- What's at Stake: Congressional communications, legislative strategies, foreign policy deliberations, and intelligence assessments could be exposed.
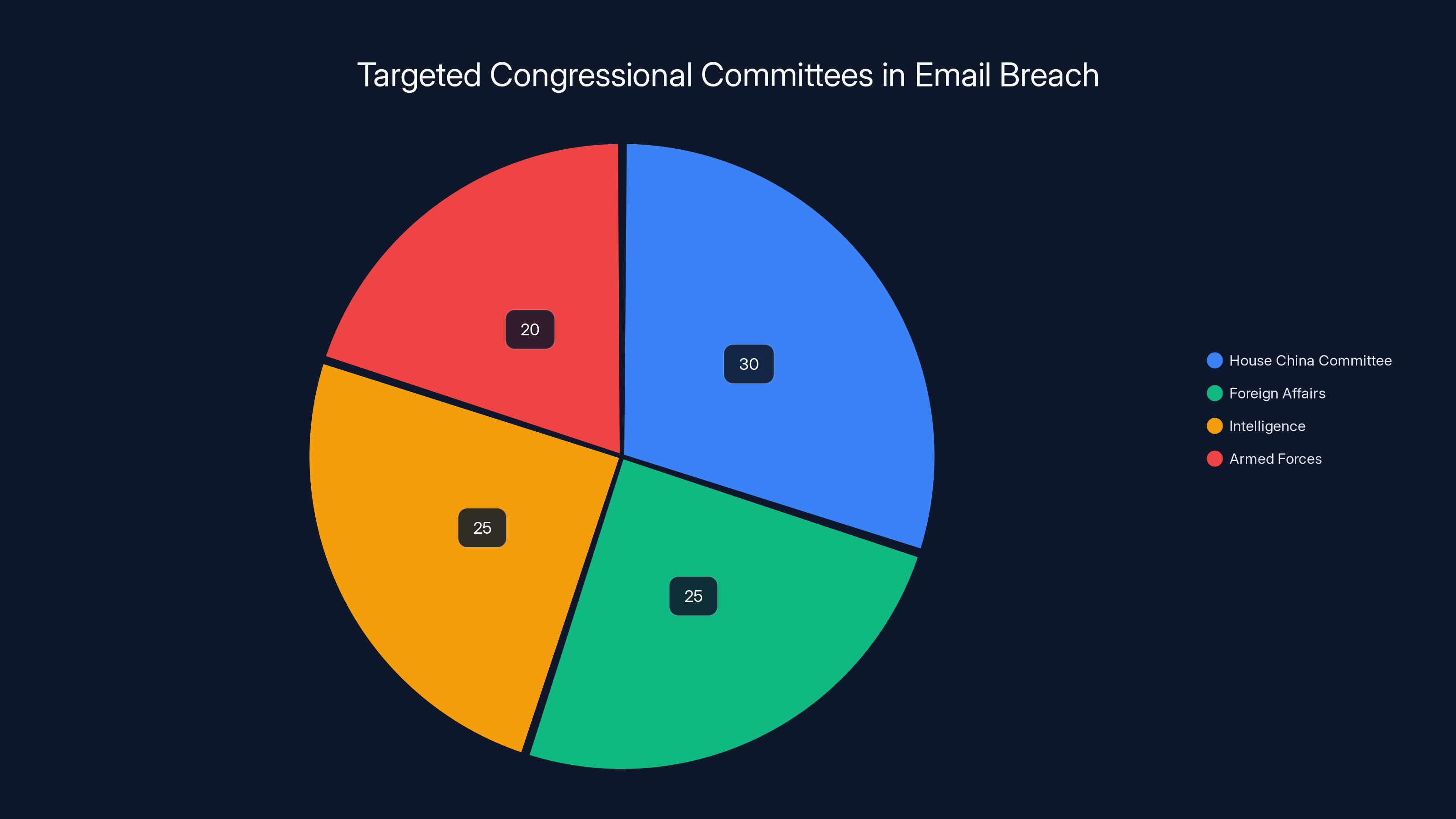
Estimated data suggests the breach primarily targeted committees involved in US-China relations and strategic decisions, with the House China Committee being the most affected.
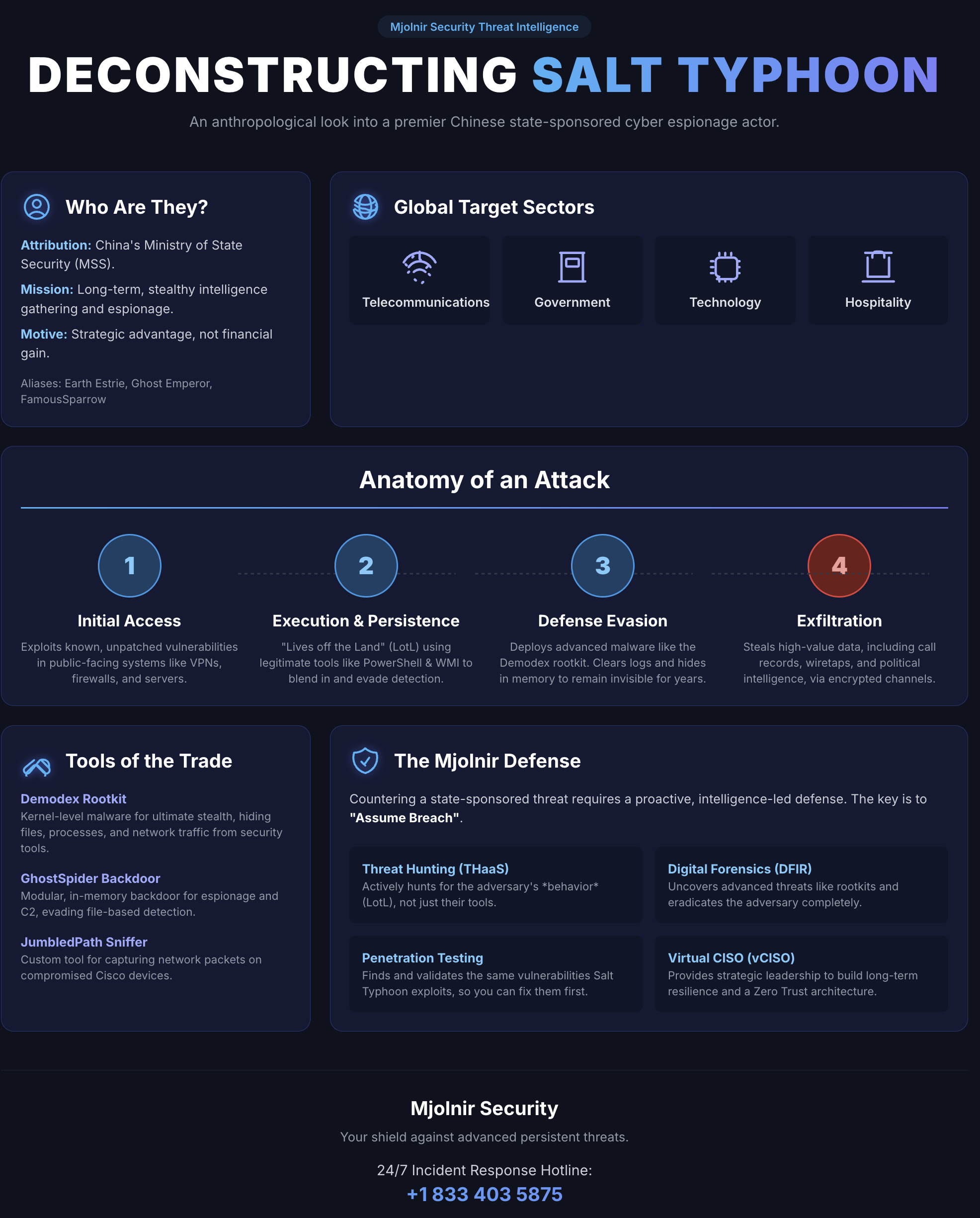
Who Is Salt Typhoon and Where Did They Come From?
Salt Typhoon isn't a random hacking group that popped up overnight. This is a sophisticated, well-organized, and heavily resourced threat actor with direct ties to Chinese state interests. Understanding their background, capabilities, and track record is crucial to understanding why this breach is such a big deal.
The group operates as part of what security researchers call the "Typhoon" nexus. This is essentially a collection of Chinese state-sponsored hacking groups that specialize in different types of cyber operations. Salt Typhoon sits alongside other notorious groups like Brass Typhoon, Volt Typhoon, and Flax Typhoon. Each group has specific expertise and focuses on different sectors or types of attacks, but they're all ultimately serving Chinese intelligence objectives.
Salt Typhoon has been active for years, but they really started getting mainstream attention in 2024 when they were caught compromising major US telecommunications companies. We're talking about some of the largest carriers in the country: T-Mobile, Verizon, AT&T, and Lumen Technologies all fell victim to this group. These weren't small breaches either. Salt Typhoon gained access to network management systems and maintained persistent access for extended periods.
What makes Salt Typhoon different from other hacking groups is their focus on telecommunications infrastructure. That's strategically important because telecom networks are the backbone of modern communications. If you control telecom infrastructure, you can intercept calls, monitor data transmissions, and maintain access to an enormous amount of sensitive information flowing through those networks.
In October 2024, cybersecurity researchers at Darktrace identified Salt Typhoon actively targeting communications networks across Europe. That expanded the scope of known operations significantly. The group wasn't just focused on the US anymore. They were clearly conducting a global campaign.
What's particularly concerning is the sophistication of their operations. This isn't a group using outdated tools or obvious attack methods. They employ advanced techniques that allow them to stay hidden in networks for extended periods without triggering security alarms. That level of operational sophistication suggests a well-funded organization with access to advanced tools and talent. Which, of course, aligns with what you'd expect from a state-sponsored actor backed by Chinese intelligence resources.
Logging & Monitoring and Assume Breach Mentality are estimated to be the most effective defensive measures against sophisticated threats, highlighting the importance of visibility and preparedness. (Estimated data)
The Congressional Email Breach: What Happened and What We Know
Okay, so let's get into the specifics of what actually happened with the congressional breach. The Financial Times first reported on this incident, citing people familiar with the matter. According to those sources, Salt Typhoon gained access to email systems used by staff members of powerful committees in the US House of Representatives.
Specifically, the breach affected staff on the House China Committee. But it didn't stop there. Aides on committees covering foreign affairs, intelligence, and the armed forces were also targeted. That's a very deliberate selection of targets, by the way. These aren't random committees. They're the committees most directly involved in shaping US policy toward China and major strategic decisions.
The thing is, the exact scope of the breach remains unclear. That's actually pretty concerning in itself. When the FBI or White House eventually issue a statement, will they say that only staffers' emails were compromised, or will they disclose that they found evidence of access to elected officials' email accounts as well? The difference is significant.
Staffer emails would contain legislative strategy documents, policy analysis, constituent communications, and internal deliberations about upcoming votes and legislative initiatives. That's valuable intelligence. But elected officials' personal emails could contain even more sensitive communications, including interactions with intelligence officials, foreign policy advisors, and potentially classified information discussions.
As of the time this investigation was conducted, the FBI and White House had not publicly commented on the breach. The Chinese Embassy spokesperson, Liu Pengyu, dismissed the reports as "unfounded speculation and accusations," which is basically the standard response anytime China gets caught doing something. The denial is almost reflexive at this point.
One thing worth noting: it's unclear whether the attackers simply accessed the emails or if they actually copied data. That distinction matters. If they only had read access, they got intelligence but didn't compromise the email accounts themselves. If they actually exfiltrated data, then we're looking at a much more serious breach where emails could be read offline, searched through thoroughly, and analyzed by Chinese intelligence.
The fact that this breach wasn't immediately disclosed raises another question: How long were Salt Typhoon inside these systems before they were discovered? With sophisticated threat actors targeting government systems, the dwell time (the period an attacker remains undetected in a network) often stretches into weeks or months. Every day they remain undetected is another opportunity to steal more information and deepen their presence in the network.
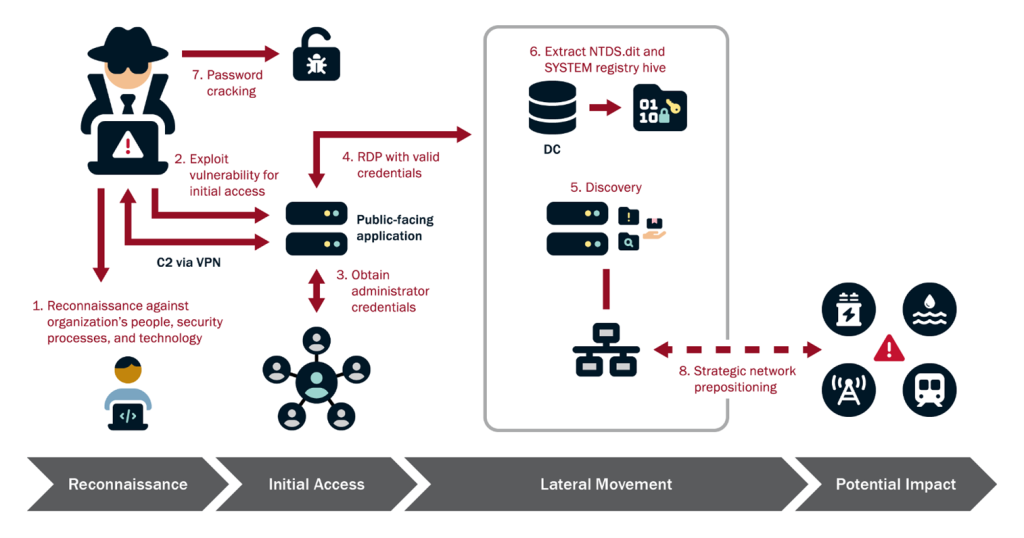
Understanding Salt Typhoon's Attack Methods and Technical Tactics
Now let's get into the technical details of how Salt Typhoon actually conducts these attacks. Understanding their methods helps explain why they're so effective and why their breaches are so difficult to stop.
One of Salt Typhoon's favorite techniques is called DLL sideloading. DLL stands for Dynamic Link Library, and it's essentially a file that contains code that programs can use. DLL sideloading is a technique where attackers place a malicious DLL file in a directory where legitimate software is looking for libraries. When the legitimate software runs, it accidentally loads the malicious DLL instead of the legitimate one. It's like replacing the engine oil with contaminated oil. The car still starts and runs, but something bad is happening under the hood.
What makes DLL sideloading particularly effective is that it often doesn't trigger antivirus software or endpoint security tools. From the system's perspective, a legitimate program is running and loading a library. Everything looks normal. The malicious code is hiding in what appears to be legitimate activity.
Salt Typhoon also uses zero-day exploits extensively. A zero-day is a vulnerability in software that the vendor doesn't know about yet, so there's no patch available. Attackers who find zero-days (or purchase them on the dark market) have a window where they can exploit systems without any defense being available. Zero-day exploits are expensive and typically reserved for high-value targets. The fact that Salt Typhoon uses them suggests they have significant resources and are willing to burn valuable exploits on priority targets.
Supply chain attacks are another tactic in Salt Typhoon's arsenal. In a supply chain attack, the attacker doesn't go directly after the target. Instead, they compromise a vendor or supplier that the target uses. Then they use that compromised vendor relationship to gain access to the ultimate target. It's a more indirect approach, but often more effective because defenders aren't expecting it.
For telecommunications infrastructure specifically, Salt Typhoon has been observed targeting network management systems and using legitimate administrator tools to maintain access. Once they're in, they behave like a legitimate system administrator would. They don't immediately start downloading everything. They establish persistence mechanisms first, which are methods to maintain access even if their initial entry point gets discovered.
The group also demonstrates sophisticated knowledge of the environments they're attacking. They know which systems are critical, which ones have logging, which ones are monitored by security teams, and how to move laterally through networks while avoiding detection. This operational knowledge takes time to develop. It suggests that before going after email systems, Salt Typhoon probably spent weeks or months reconnaissance the networks, mapping out systems, and identifying the path of least resistance.
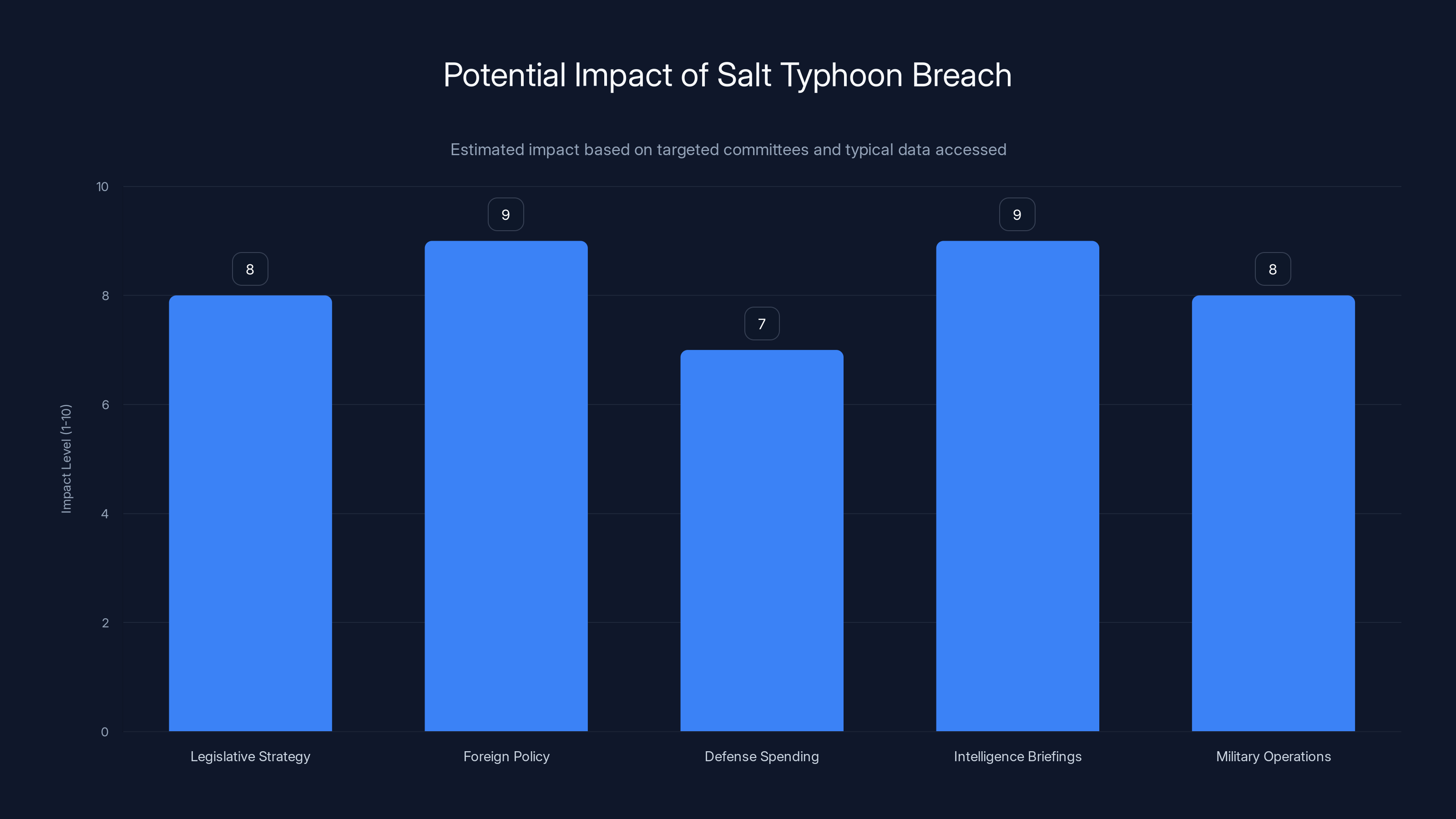
Estimated data suggests high impact levels across various sensitive areas, with foreign policy and intelligence briefings being most affected.
The Broader Context: Why Telecommunications Infrastructure Matters
You might be wondering why Salt Typhoon is so focused on telecommunications infrastructure in the first place. The answer reveals something important about modern nation-state cyber strategy: telecommunications networks are the nervous system of modern societies.
When you think about cybersecurity, you might think about banks, government offices, or military systems. Those are important, sure. But telecommunications networks are arguably more critical because they carry all the communications between those institutions. They're the plumbing through which sensitive information flows.
If you control telecom infrastructure, you gain the ability to:
- Intercept phone calls and text messages
- Monitor data traffic passing through those networks
- Identify high-value targets based on communication patterns
- Potentially redirect traffic or conduct man-in-the-middle attacks
- Maintain persistent access to thousands of users and organizations
From a nation-state intelligence perspective, compromising telecom infrastructure is incredibly valuable. You're not just getting access to individual targets. You're getting a window into an entire nation's communications. Every government official, military officer, intelligence analyst, corporate executive, and prominent citizen who uses that telecom network is potentially exposed.
China's focus on telecom breaches also reflects a broader strategic objective. As tensions between the US and China increase over Taiwan, trade, technology, and geopolitical influence, both nations are trying to gain intelligence advantages. China wants to understand what the US government is planning, what military capabilities the US is developing, what trade negotiations are happening, and what the US intelligence community knows about Chinese operations.
Access to congressional communications serves that objective directly. Congressional members and their staffs are involved in defense spending decisions, foreign aid allocations, sanctions discussions, and intelligence oversight. They're also in contact with constituents, lobbyists, and foreign officials. All of that communication traffic is valuable intelligence.
The targeting of committee staff specifically also suggests a sophisticated understanding of how US government actually works. Congressional staff do much of the actual work on legislation. They write bills, conduct investigations, brief members, and coordinate with executive branch agencies. In many cases, staffers have higher-level security clearances than their bosses do. They're conducting substantive policy work. So targeting them makes strategic sense.
What Information Could Be at Risk: The Intelligence Value
Let's think about what Salt Typhoon might actually find in these compromised email systems. What information has intelligence value that would justify the risk and resources expended on this operation?
First, there's legislative strategy information. Congressional committees are constantly working on legislation related to China, foreign affairs, and defense. Email chains would show what bills are being drafted, what the legislative priorities are for the current session, what amendments are being considered, and what the political dynamics are around these issues. This information helps China understand what restrictions or sanctions the US might be considering and when.
Second, there's intelligence assessment information. Congressional committees receive briefings from intelligence agencies. Those briefings discuss assessments of threats, capabilities of adversaries (including China), intelligence operations that have been discovered, and vulnerabilities in US systems. While the most classified information wouldn't be transmitted via email, there would certainly be unclassified summaries, assessment conclusions, and contextual information in email communications.
Third, there's information about committee members' visits, meetings, and contacts. Congressional delegations frequently visit other countries, meet with foreign officials, and maintain relationships with intelligence contacts. Email records would show what delegations are planned, who they're meeting with, what issues they're discussing, and what agreements or understandings might be reached.
Fourth, there's personal and political information. Staffers email about sensitive political matters, personal views on policy, assessments of other officials, constituent concerns, and internal disagreements. This information could be used for influence operations, blackmail, or simply understanding the political dynamics that shape policy.
Fifth, there's information about cyber threats and vulnerabilities. Congressional staff involved in defense and intelligence receive information about cyber threats targeting the US, vulnerabilities in critical systems, and security incidents. Understanding what the US government knows about cyber threats helps China know what vulnerabilities might still be exploitable and what attack methods might have been detected.
Sixth, there's information about personnel and operations. Congressional staff communicate about military deployments, intelligence operations, personnel appointments, and organizational changes. This information helps China build a picture of US military and intelligence capabilities and intentions.
When you add all of this together, email access to congressional committee staff represents a massive intelligence windfall. It's not just one piece of information. It's a collection of many different intelligence items that, when analyzed together, build a comprehensive picture of what the US government is thinking, planning, and worried about.

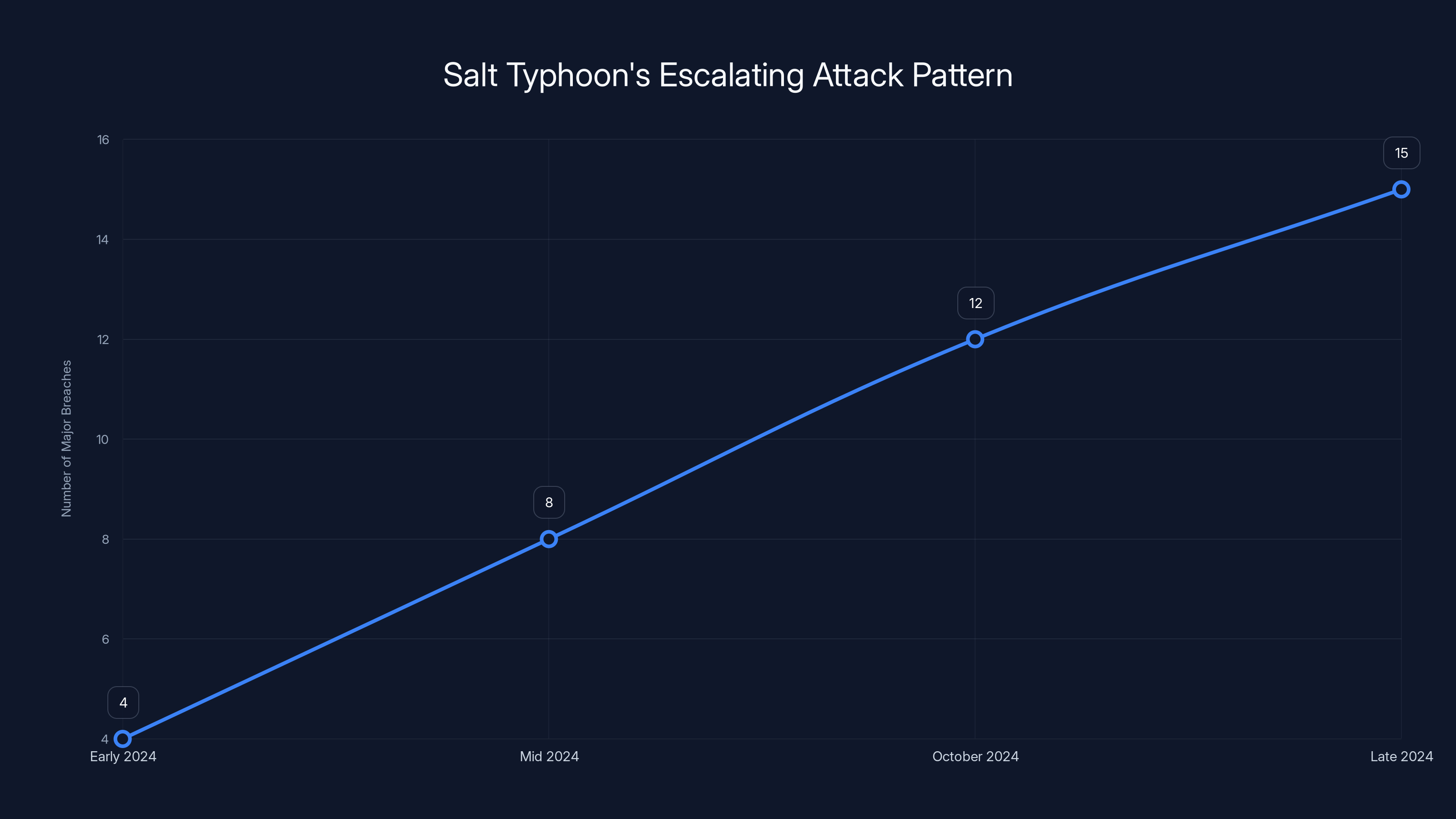
Salt Typhoon's attack pattern shows a clear escalation from targeting US telecom companies to expanding operations in Europe and eventually breaching US Congress. Estimated data based on reported incidents.
The Pattern of Attacks: Salt Typhoon's Track Record
Salt Typhoon didn't just wake up one day and decide to target Congress. They have a clear track record of escalating operations over time. Understanding that pattern helps predict what might come next.
In 2024, the public learned that Salt Typhoon had compromised at least eight major US telecommunications companies. These weren't small regional carriers. We're talking about T-Mobile, Verizon, AT&T, and Lumen Technologies. Each of those companies handles hundreds of millions of phone calls and data transmissions daily. The breach of each one was significant.
What's notable is that these breaches took months to discover in some cases. Attackers were inside the networks, accessing network management systems and conducting surveillance, before security teams noticed something wrong. And in some cases, attackers likely maintained access even after discovery, because removing sophisticated persistence mechanisms from critical infrastructure is incredibly difficult without disrupting service.
Following the telecommunications breaches, Salt Typhoon expanded their operations geographically. In October 2024, they were observed targeting communications networks across Europe. That expansion suggested the group wasn't slowing down. They were scaling up and diversifying their targets across continents.
Then came the congressional breach. This represents an escalation from infrastructure to directly targeting the political leadership and policy-making apparatus of the United States. It's a bolder move because it's more likely to trigger a political response and investigation. But the strategic value justifies the risk.
The timing is also worth considering. These revelations come during a period of significant US-China tensions. Trade restrictions, technology export controls, and Taiwan-related discussions are all heating up. Congress is actively considering new legislation related to China. So the timing of this breach, from a strategic perspective, makes sense. China wants real-time intelligence on what Congress is planning.

Comparing Salt Typhoon to Other Nation-State Threat Actors
To really understand how dangerous Salt Typhoon is, it helps to compare them to other nation-state threat actors operating in similar domains.
Russia has several major threat groups, including FSB-affiliated groups and GRU-affiliated groups. Russian operations tend to be more destructive and disruptive than Chinese operations. Russians are more likely to use wiper malware, destroy data, and conduct denial-of-service attacks. Chinese operations tend to be more focused on persistent access and intelligence collection.
North Korea's threat actors like Lazarus Group tend to be focused on financial theft and maintaining operational security for the regime. They're sophisticated, but their objectives are different than China's.
Iran has cyber groups that conduct espionage and harassment operations, but they generally have less sophisticated capabilities than Chinese groups and tend to target specific sectors rather than broad infrastructure.
What distinguishes Salt Typhoon from most other nation-state groups is their focus on telecommunications infrastructure and their ability to maintain persistence in critical systems over extended periods. Most other groups either focus on specific sectors (banking, energy, defense contractors) or conduct more disruptive operations. Salt Typhoon's strategy is more comprehensive. They're trying to create a persistent listening post across multiple critical networks simultaneously.
Their operational security is also notable. They use living-off-the-land techniques, where they use legitimate tools and system features that are already present in compromised systems. They don't introduce malware that can be easily detected. This makes attribution harder and cleanup much more difficult.
The scale of Salt Typhoon's operations is also larger than many comparable groups. Most nation-state groups focus on specific high-value targets. Salt Typhoon is targeting broad infrastructure across multiple countries. That scale requires either a much larger team or more automated tools, or likely both.
Their resource commitment is substantial. Using zero-day exploits, developing sophisticated persistence mechanisms, and maintaining access across multiple major companies requires significant investment. This is not a group operating on a shoestring budget. This is a well-funded operation with substantial resources.
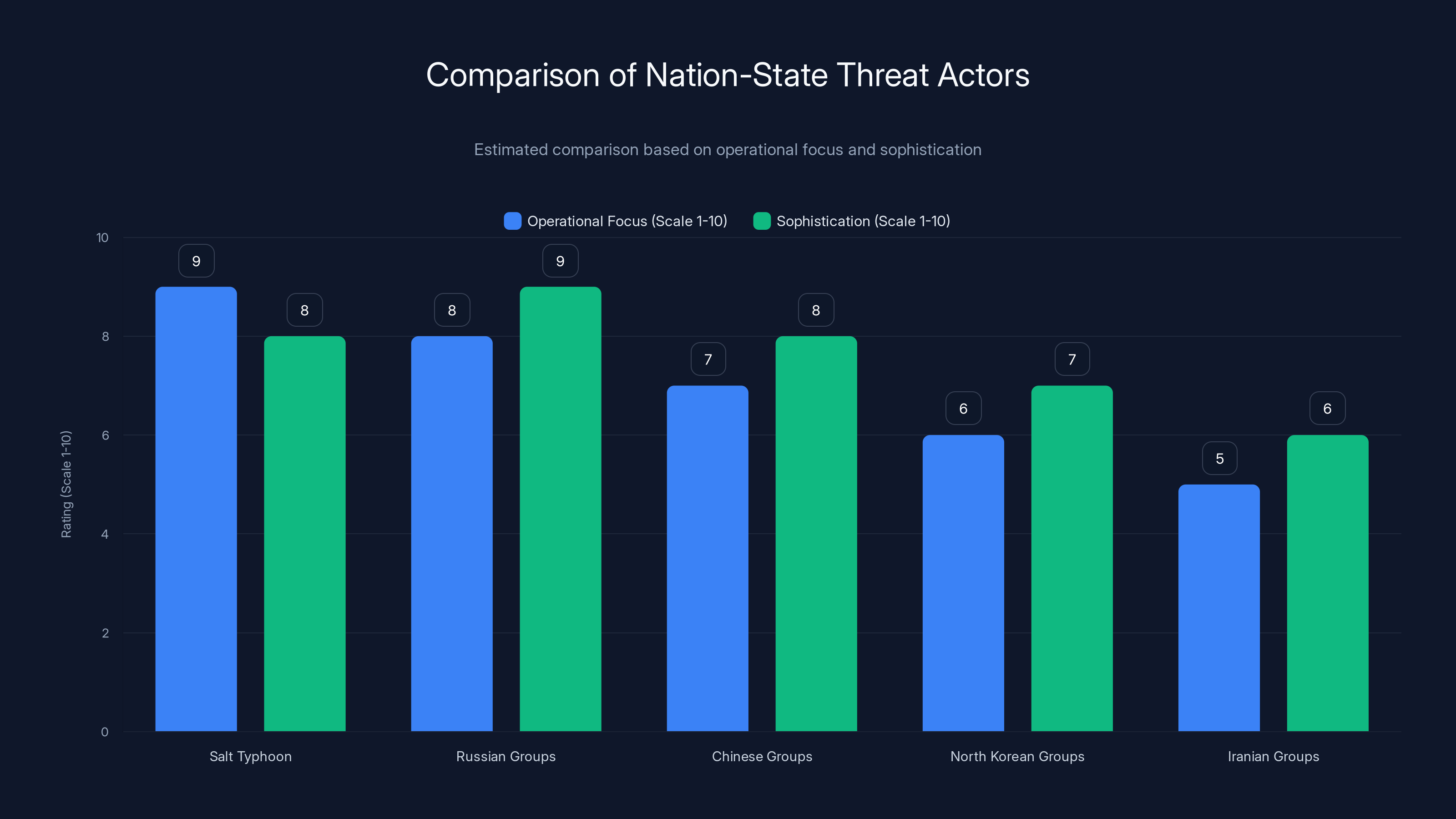
Salt Typhoon is distinguished by its broad operational focus on telecommunications infrastructure and high sophistication in maintaining persistence. Estimated data based on typical characteristics.
The Investigation and Attribution: How Researchers Identified Salt Typhoon
Now, how do cybersecurity researchers and government agencies actually identify and attribute attacks to specific groups like Salt Typhoon? The answer involves a combination of technical analysis, behavioral patterns, and intelligence.
When an intrusion is discovered, responders look at the tools, techniques, and procedures used by the attackers. Are there specific malware signatures? What programming languages were used? How did the attacker move through the network? What system features did they abuse? These technical indicators can sometimes point toward specific threat groups.
Salt Typhoon has specific indicators associated with them. For example, their use of DLL sideloading in particular ways, their preference for certain legitimate tools, their targeting patterns, and their attack sequence all have characteristics that researchers have documented.
Behavioral analysis is also important. Different groups have different operational patterns. Some groups are quick and destructive. Others are slow and methodical. Some avoid certain systems. Others have clear geographic preferences. Salt Typhoon's behavior pattern includes patient reconnaissance, careful persistence mechanism establishment, and extended dwell time in networks.
Threat intelligence sharing between government agencies and private companies is also crucial. When one company discovers an intrusion, information is shared with other companies, government agencies, and the broader security community. This crowdsourced detection approach helps identify patterns across multiple breaches.
Finally, there's intelligence community knowledge. The FBI, NSA, CIA, and other intelligence agencies have classified information about Chinese hacking groups that isn't publicly available. When they see evidence of a breach, they can use that classified knowledge to make attribution determinations.
The process isn't perfect. Sometimes attribution is wrong. Sometimes multiple groups have similar capabilities and techniques. But in the case of Salt Typhoon, the attribution has been consistent across multiple investigations by different organizations, which increases confidence in the assessment.

Government Response and Policy Implications
So what can we expect from the US government in response to this breach? And what does it tell us about how the government is approaching nation-state cyber threats?
Historically, when major breaches of government systems by nation-state actors are discovered, the response follows a pattern. First, there's an investigation by the FBI and relevant intelligence agencies. That investigation can take weeks or months. The government tries to understand the full scope of the breach, what information was compromised, how the attackers got in, and what persistence mechanisms they left behind.
Second, there's usually a statement from the White House or relevant agencies acknowledging the breach (or sometimes not, if they're trying to keep it quiet). The statement typically provides minimal details and emphasizes that the government is taking action to improve security.
Third, there's often a response that involves diplomatic protests to the Chinese government through official channels. The US will make clear that the Chinese government's cyber operations are unacceptable. China will deny involvement or claim the US is the real cyber aggressor.
Fourth, there might be sanctions. The Biden administration has been relatively active in sanctioning Chinese cyber actors compared to previous administrations. But sanctions are often symbolic because the sanctioned entities are already restricted from US commerce.
Fifth, there might be indictments. The Department of Justice sometimes indicts foreign nationals responsible for major cyber attacks. These indictments are usually symbolic (since the indicted individuals aren't going to be prosecuted) but serve the purpose of public attribution and expressing displeasure.
What's less clear is whether there will be any direct cyber response. The US government has the capability to conduct cyber operations against Chinese infrastructure, but using that capability escalates tensions significantly. So those decisions are made at very high political levels.
The policy implications of this breach extend beyond immediate response. The breach highlights that existing security models aren't adequate for defending against state-sponsored threats. Congressional staff email systems are presumably protected by federal security standards and monitoring. Yet Salt Typhoon still got in. That suggests either the defensive measures weren't adequate, the attackers were sophisticated enough to bypass them, or some combination of both.
This will likely drive policy changes, including:
- Increased funding for cybersecurity in government
- Requirements for stronger authentication and encryption
- More aggressive threat intelligence sharing
- Possible restrictions on which cloud providers government agencies can use
- Increased investment in zero-trust security architecture
- Possible legislative responses mandating certain security practices
The breach also raises questions about what information Congress has about other nation-state cyber operations. If Congress itself has been breached, what does that say about the security of classified intelligence systems? Are there other breaches of government systems that haven't been publicly disclosed?

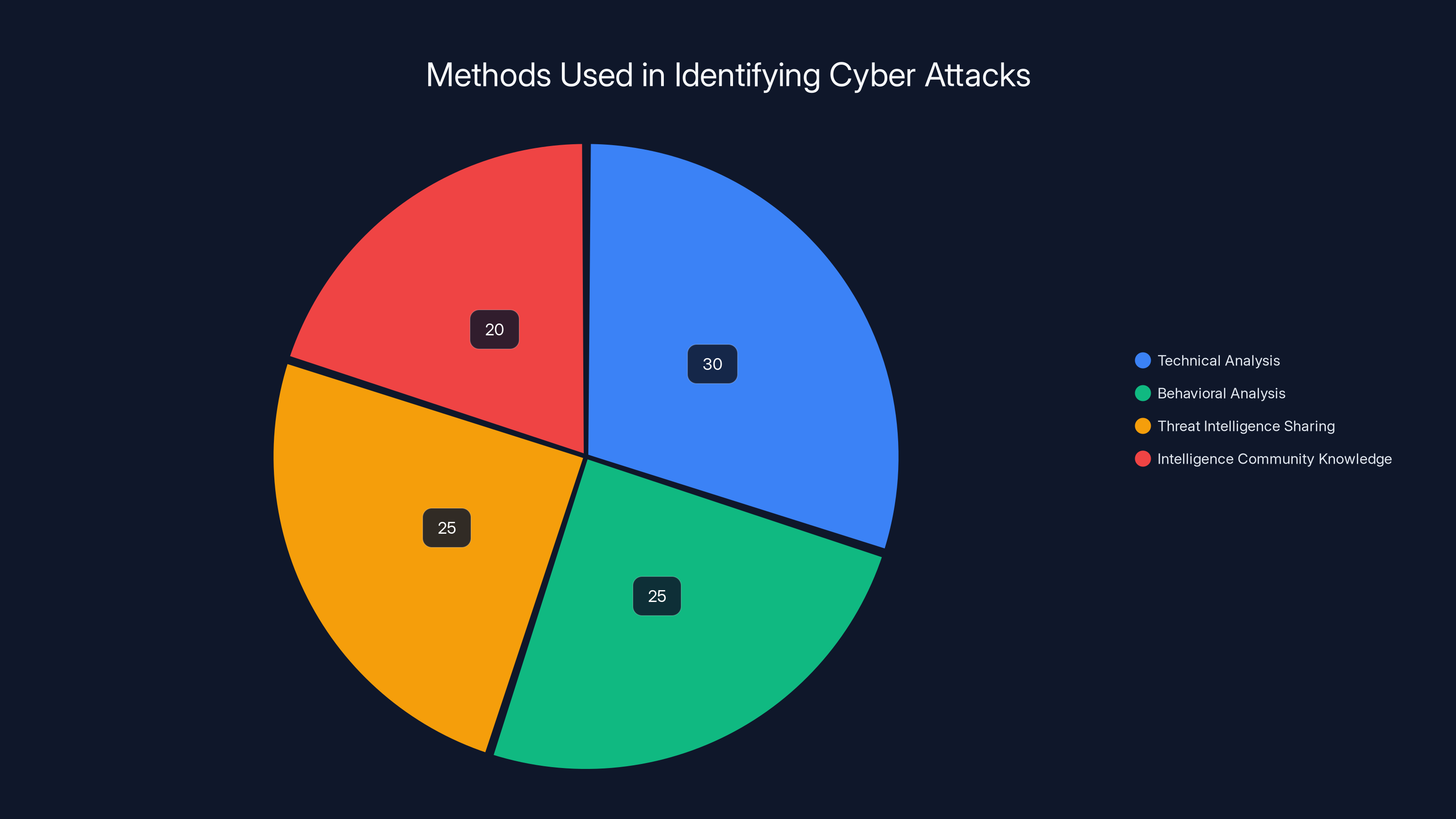
Technical analysis is the most used method (30%) in identifying cyber attacks, followed by behavioral analysis and threat intelligence sharing (25% each). Intelligence community knowledge contributes 20%. Estimated data.
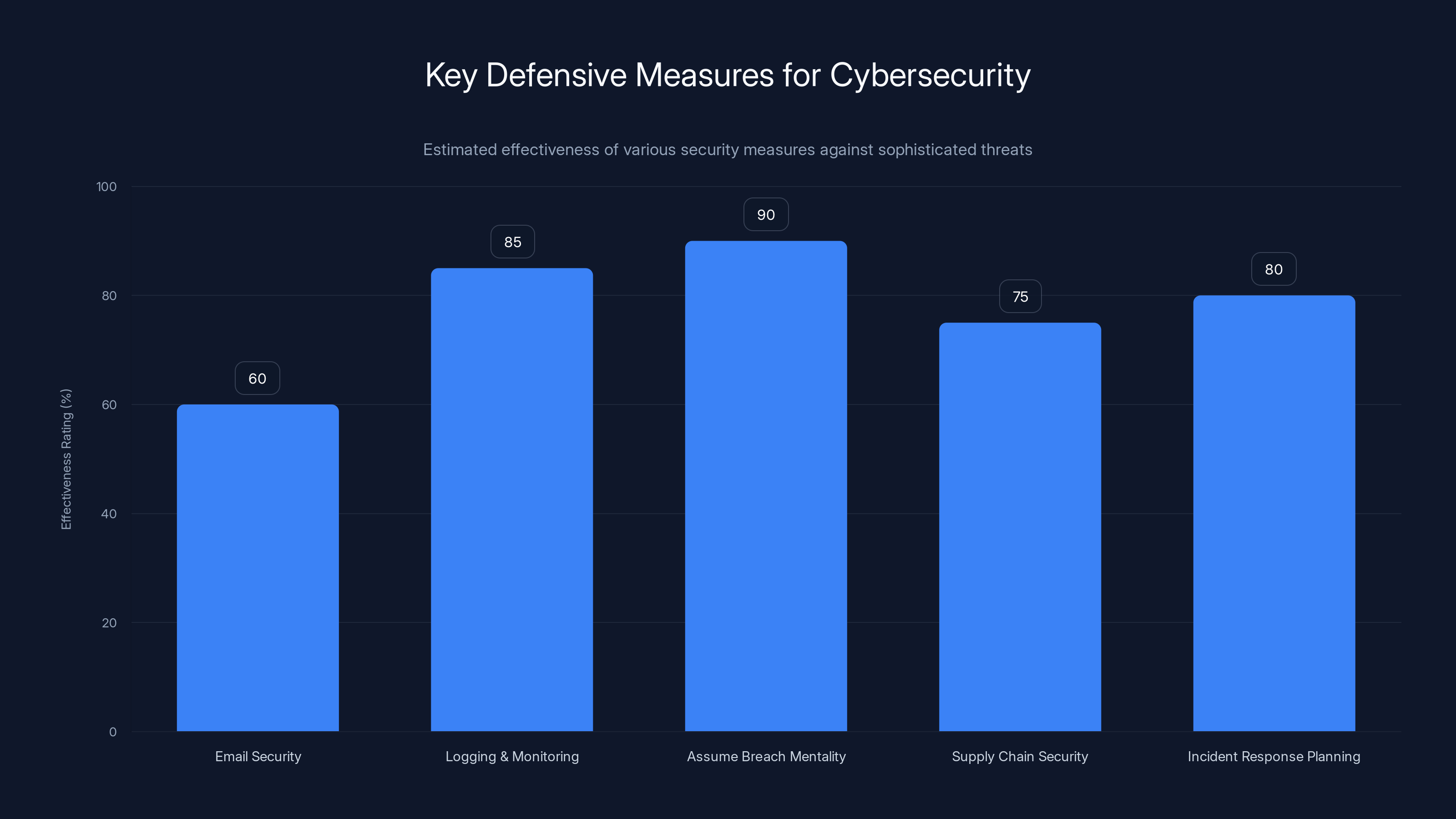
Defensive Measures and What Organizations Can Learn
While Salt Typhoon is a nation-state actor with exceptional resources, the techniques and approaches they use have lessons applicable to defending against other sophisticated threats as well.
First, email security is critical but insufficient. Salt Typhoon accessed email systems despite them presumably being protected by email security tools. Email is just one attack vector. Comprehensive security requires defending at multiple layers: network perimeter, endpoint protection, application security, and identity and access management.
Second, logging and monitoring are essential. If you can't see attackers in your network, you can't stop them. Salt Typhoon likely succeeded for extended periods because network monitoring wasn't comprehensive enough to catch their activities. Implementing extensive logging, creating a security operations center to analyze logs, and using behavioral analysis tools to identify suspicious patterns is critical.
Third, assume breach mentality is necessary. Organizations need to operate under the assumption that sophisticated attackers will eventually get into their networks. The goal shifts from preventing all breaches (impossible) to detecting breaches quickly and limiting the damage once they occur. This is the zero-trust security model: don't trust any access, verify everything.
Fourth, supply chain security matters. Since sophisticated attackers often use supply chain attacks to gain access, organizations need to carefully vet their vendors, monitor vendor security practices, and implement controls on what vendors can access in their networks.
Fifth, incident response planning is crucial. If Salt Typhoon got into congressional networks, presumably response teams eventually detected the intrusion (or at least, eventually they will). Having a detailed incident response plan, with clear roles, responsibilities, and procedures, makes the difference between a bad breach and a catastrophic one.
Sixth, threat intelligence sharing accelerates detection. Organizations that share information about attacks and attack patterns with peers and government agencies benefit from that collective knowledge. If another organization detected Salt Typhoon and shared those indicators with Congress, it would have helped detect the breach earlier.
Seventh, technical controls like multi-factor authentication, encryption, and privileged access management make attackers' jobs harder. These aren't perfect defenses, but they increase the level of sophistication required to compromise systems.
Eighth, network segmentation limits an attacker's lateral movement. If congressional email systems were on a separate network segment with restricted access to other critical systems, attackers would have been limited in what they could do even after gaining initial access.

The China Response and Geopolitical Context
China's response to these allegations has been predictable: denial and deflection. Liu Pengyu, the Chinese Embassy spokesperson, called the reports "unfounded speculation and accusations." This is the standard diplomatic response whenever China gets caught engaging in cyber espionage.
What's interesting is what's not being said. China isn't claiming they couldn't do this. They're not saying their cyber capabilities aren't sophisticated enough for these operations. They're simply denying that they did it. That's a subtle but important distinction.
Historically, whenever a sophisticated cyber attack is attributed to China, the response follows a pattern. First, denial. Then accusations that the US is actually the real cyber aggressor. Then, if pressed, arguments that the attribution is uncertain and multiple actors could have conducted the attack.
China also tends to respond to US criticism by pointing out US cyber operations. The US government runs extensive cyber intelligence operations globally. The Snowden revelations made clear that the NSA conducts signals intelligence globally, including against allies. So from China's perspective, when the US complains about Chinese cyber operations, they see hypocrisy.
That said, the scale and brazenness of Salt Typhoon operations does represent an escalation. Previous Chinese cyber espionage operations against government targets were often more targeted and less likely to be discovered. Salt Typhoon's operations are larger and bolder, which makes them harder to deny.
From a geopolitical perspective, this breach occurs in the context of deteriorating US-China relations. The two countries are competing for technological dominance, economic advantage, and geopolitical influence. Cyber operations are one tool in that competition. As the competition intensifies, expect more aggressive cyber operations from both sides.
The congressional staff breach is also significant because it targets the US legislative branch directly. This isn't just targeting military or intelligence systems. It's targeting the institution responsible for making US policy toward China. That's a more overt political act than many previous Chinese cyber operations.
Future Outlook: What Might Come Next
Based on the pattern of Salt Typhoon's operations and the broader trajectory of nation-state cyber operations, what might we expect in the coming months and years?
First, escalation of targeting. Salt Typhoon started with telecommunications infrastructure. They expanded to other sectors. They're now directly targeting government systems. Future operations will likely continue expanding in scope and boldness.
Second, more sophisticated techniques. As defensive measures improve, attackers will develop new methods. We'll likely see increased use of artificial intelligence and machine learning by attackers to identify vulnerabilities and automate attack processes.
Third, supply chain attacks will become more common. As direct network compromise becomes harder, attackers will increasingly target vendors and suppliers to access their targets indirectly.
Fourth, increased focus on critical infrastructure. Telecommunications, power grids, water systems, and financial infrastructure are all potentially valuable targets. Expect continued probing and attempted compromises of these systems.
Fifth, attribution will become more important and more contested. As cyber operations become more overt and more damaging, attribution becomes politically significant. Attackers will increasingly try to hide their tracks or impersonate other groups.
Sixth, cyber warfare capabilities will continue to advance. Military and intelligence agencies globally are developing more sophisticated cyber weapons. The tools used in cyber espionage campaigns today will eventually migrate to military applications.
Seventh, defensive technologies will advance, but they'll always be playing catch-up. The asymmetric nature of cyber attacks means that attackers only need to find one weakness, while defenders need to protect against all possible attack paths.
Eighth, international norms and rules for cyber operations remain unclear and contested. Without clear rules and consequences, nation-states will continue to operate aggressively in cyberspace.
Lessons for Security Professionals and Organizations
If you're a cybersecurity professional or work in IT security, the Salt Typhoon breach offers several important lessons for your own organization.
First, nation-state capability isn't a theoretical concern. It's happening right now against US government systems. The assumption that your organization isn't important enough to target a state-sponsored actor is probably wrong. Nation-states now conduct cyber reconnaissance widely, compromising systems for future use even if they don't immediately need the access.
Second, traditional security perimeters don't work anymore. The idea of having a secure network with bad stuff outside and good stuff inside is outdated. Attackers get inside perimeters regularly. The focus needs to shift to detecting and responding to threats once they're inside.
Third, zero-trust architecture is becoming necessary rather than optional. Every access request should be verified. Every user and device should be authenticated. Every connection should be encrypted. This approach is harder to implement but more effective than relying on perimeter security.
Fourth, threat hunting is critical. Don't just wait for automated alerts. Have security analysts actively looking for signs of compromise that might not trigger automation. Threat hunting is resource-intensive but catches sophisticated attackers that automated systems miss.
Fifth, incident response capability matters more than prevention capability. You will get breached. The question is how quickly you'll detect it and how effectively you'll respond. Investing in incident response capability is as important as investing in prevention.
Sixth, supply chain security is your responsibility. You're responsible for the security of vendors you use. That means assessing their security practices, monitoring their security, and potentially restricting what access they have to your systems.
Seventh, senior leadership understanding is essential. Security can't be an IT department concern only. Senior leaders, including C-level executives and board members, need to understand cyber risks and support security investments.
Eighth, continuous improvement is necessary. Security is not a one-time project. It's an ongoing process. Threats evolve, attackers develop new techniques, and your organization's threat landscape changes. Security programs need to evolve continuously.

Practical Security Steps for Individuals and Small Organizations
While the congressional breach involves nation-state actors and sophisticated techniques, there are practical security steps that anyone can take to reduce their risk.
For individuals, the basics remain critical: use strong, unique passwords managed by a password manager, enable multi-factor authentication on important accounts, keep software updated, use a reputable antivirus, think carefully before clicking links in emails, and don't leave devices unattended.
But beyond the basics, understand your own threat model. If you work in government, defense, or critical infrastructure, your threat level is higher. If you're a political figure or journalist, you might face targeted attacks. Adjust your security practices based on your actual threat level.
For small organizations without dedicated security staff, focus on the highest-impact changes: implement email authentication (SPF, DKIM, DMARC) to prevent spoofing, require multi-factor authentication for all remote access, enable encryption on sensitive data, maintain regular backups that are stored offline, and conduct regular security awareness training for all staff.
For medium-sized organizations, consider hiring a cybersecurity consultant to assess your security posture and develop a security roadmap. The investment typically pays for itself by preventing breaches.
For all organizations, security policies and procedures matter. Document what you're supposed to do in various security scenarios. Train people on those procedures. Test them regularly with tabletop exercises.
Finally, develop relationships with security resources before you need them. Knowing a good incident response firm, understanding what cyber insurance covers, and having contacts in the security community all help when a breach actually happens.
Key Takeaways and Implications
The Salt Typhoon breach of congressional emails represents a significant escalation in nation-state cyber operations against the United States. It demonstrates that no institution is truly secure from determined, well-resourced attackers. It highlights the importance of moving beyond traditional security models to more comprehensive, layered defensive approaches.
The breach also illustrates the strategic importance of telecommunications infrastructure and why nation-states are willing to expend significant resources to compromise those systems. It shows that cyber espionage has become a central tool in great power competition.
For the cybersecurity field broadly, this breach reinforces trends that have been developing for several years: the shift from prevention-based security to detection and response-based security, the increasing importance of threat intelligence, and the necessity of treating security as a strategic organizational concern rather than just an IT concern.
For organizations, the breach demonstrates that existing security measures are often inadequate against sophisticated threats. Organizations need to invest in continuous improvement, threat hunting, and incident response capabilities.
For individuals, the breach serves as a reminder that security matters and that staying informed about threats helps you protect yourself.
The broader lesson is this: cyber threats from nation-state actors are real, they're escalating, and they affect everyone. Understanding those threats, taking reasonable precautions, and supporting good security practices in the organizations you're part of is everyone's responsibility.

FAQ
What exactly is Salt Typhoon and why is it considered a major threat?
Salt Typhoon is a Chinese state-sponsored hacking group that specializes in compromising telecommunications infrastructure and conducting espionage operations. It's considered a major threat because of its sophisticated techniques, significant resources, persistence in networks, and demonstrated ability to compromise critical infrastructure affecting millions of users. The group has breached major US telecommunications carriers and now government systems.
How did Salt Typhoon manage to access congressional email systems?
The specific attack method hasn't been fully disclosed publicly, but based on Salt Typhoon's known techniques, the group likely used a combination of reconnaissance, zero-day exploits or vulnerabilities, credential compromise, and potentially supply chain attacks. They may have used DLL sideloading or legitimate administrative tools once inside the network to avoid detection.
What information did Salt Typhoon potentially access in this breach?
Based on the committees targeted (China, foreign affairs, intelligence, defense), the compromised information likely includes congressional legislative strategy, foreign policy deliberations, defense spending discussions, intelligence briefings and assessments, information about military operations and capabilities, and communications with foreign officials and intelligence agencies.
How long did Salt Typhoon have access to congressional emails before being discovered?
The exact dwell time hasn't been publicly disclosed. However, based on typical patterns for state-sponsored actors, the group may have had access for several weeks or potentially months before detection. During that time, they would have been searching, analyzing, and potentially exfiltrating sensitive communications.
What is the US government doing in response to this breach?
While official statements have been limited, the standard response typically includes a full investigation by the FBI and relevant intelligence agencies, diplomatic protests through official channels, possible sanctions against Chinese officials and entities, and potentially indictments of those responsible. The government is also likely implementing enhanced security measures to prevent similar breaches.
Are other countries' governments also being targeted by Salt Typhoon?
Yes. Salt Typhoon has demonstrated a global operational reach, targeting telecommunications networks across multiple continents including Europe, as documented by cybersecurity researchers in October 2024. The group's operations aren't limited to the United States.
What defensive measures can organizations implement to protect against attacks like this?
Key measures include implementing zero-trust security architecture, extensive network monitoring and logging, threat hunting capabilities, multi-factor authentication, encryption, network segmentation, incident response planning, supply chain security assessments, and regular security awareness training. No single measure provides complete protection, but layered defenses significantly improve security.
How does this breach compare to previous major cybersecurity incidents?
This breach is significant because it directly targets the legislative branch of the US government, represents an escalation in boldness from previous Chinese cyber operations, and occurred against systems presumably protected by federal security standards. It's comparable in severity to previous breaches of government contractors and telecommunications companies but more politically significant due to the target.
Could this breach have been prevented with better security practices?
While nation-state actors have exceptional capabilities, better security practices could have reduced the likelihood of compromise or detected the intrusion faster. These include more comprehensive network monitoring, behavioral analysis of network traffic, regular threat hunting, stricter access controls, and more segmented network architecture.
What should average people do to protect themselves following this breach?
For average individuals, standard security practices apply: use strong unique passwords, enable multi-factor authentication, keep software updated, and be cautious with email links. If you have connections to government, defense, or critical infrastructure, consider more robust security practices and assume you might be targeted by sophisticated attackers.
The Salt Typhoon breach of congressional emails marks a significant moment in the history of nation-state cyber operations. It demonstrates that the line between cyber espionage and direct targeting of government institutions has been crossed. The implications extend far beyond this single breach, highlighting the need for fundamental changes in how organizations approach security and how governments approach cyber defense.
As cyber threats continue to evolve and escalate, staying informed, implementing strong security practices, and supporting good security culture in your organization becomes increasingly important. The threat landscape has changed, and our responses need to change with it.

![Salt Typhoon Hacks Congressional Emails: What You Need to Know [2025]](https://tryrunable.com/blog/salt-typhoon-hacks-congressional-emails-what-you-need-to-kno/image-1-1767902977146.jpg)



