The $120 Million Bet on Broken Cybersecurity
Enterprise cybersecurity is broken, and everyone knows it. Companies spend millions on security infrastructure, hire teams of specialists, and collect mountains of data. Yet threats still slip through. Attackers still find their way in. The problem isn't that enterprises lack data—it's that they're drowning in it, suffocating under the weight of information they can't properly analyze.
Vega Security just raised $120 million in Series B funding, and the startup's core thesis is deceptively simple: the way enterprises detect cyber threats needs to fundamentally change. Not incrementally improve. Not get slightly faster. Change.
For two decades, the security information and event management (SIEM) model has dominated enterprise threat detection. Companies like Splunk built empires on the promise that if you centralize all your security data in one place, you can spot threats. But that model breaks down in modern cloud environments where data volumes are exploding, where information lives across dozens of systems, and where moving everything to a central repository becomes prohibitively expensive and operationally complex.
Vega's answer: run threat detection where the data already lives. Don't force centralization. Instead, implement security analysis directly in cloud services, data lakes, and existing storage systems. Process data where it sits. Detect threats at the source.
The funding round, led by Accel and including participation from Cyberstarts, Redpoint, and CRV, values the two-year-old startup at $700 million. This isn't just validation from smart investors. It's recognition that enterprise cybersecurity—a market already dominated by entrenched players—is ripe for disruption.
Understanding the SIEM Problem
Before you can understand why Vega matters, you need to understand what's broken about the existing approach.
Security information and event management platforms emerged in the early 2000s as a solution to a real problem: enterprises were generating security data across multiple systems, and nobody had a unified way to search, correlate, and analyze it. Splunk's innovation was building a platform that could ingest, index, and search massive volumes of machine-generated data. For its time, it was revolutionary.
But here's what happened. As companies expanded cloud adoption, as IoT devices proliferated, as mobile workforces became the norm, the volume of security data exploded exponentially. We're talking about increases of 500%, 1000%, or more in the span of a few years.
That explosion created an economic problem. Storing all that data in a centralized SIEM is expensive. Really expensive. Some companies report security operations costs that consume 40-50% of their entire IT budget. And much of that money goes to data storage and processing costs tied to the SIEM architecture.
But the cost problem is only half the picture. The bigger issue is operational complexity. Moving all your security data to a central repository means you need to instrument each data source to send information to that repository. You need to standardize formats. You need to build connectors. You need to manage authentication and ensure data quality. All of that adds friction.
For enterprises with complex, multi-cloud environments, this friction becomes paralyzing. A typical large enterprise might have:
- AWS, Azure, and Google Cloud environments
- On-premises data centers
- SaaS applications like Salesforce, ServiceNow, and Workday
- Custom applications running in Kubernetes clusters
- Legacy systems still generating security logs
Instead of one system to instrument, you have a dozen. Instead of one connection to manage, you have hundreds. The complexity explodes. And as complexity increases, security actually decreases, not because of any single failure point, but because the sheer operational burden creates blind spots.
Vega's founders recognized this pattern. Shay Sandler, the CEO, spent time as a founding employee at Granulate—a performance optimization startup that Intel acquired for $650 million in 2022. That experience taught him something crucial: the best solutions don't fight the architecture of your systems. They work with it.
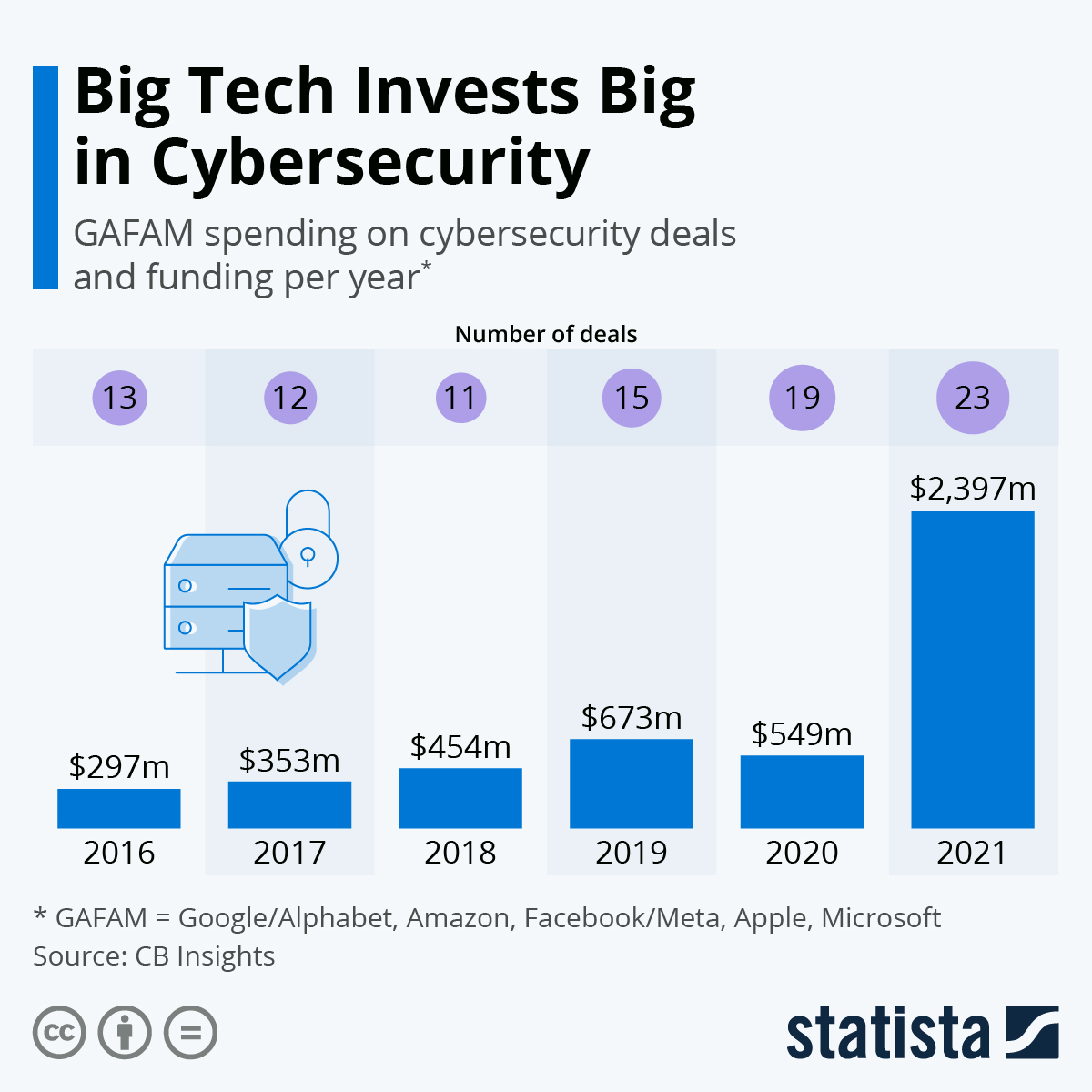
Enterprises often allocate 40-50% of their IT budget to security operations, with significant portions dedicated to SIEM data storage and processing. Estimated data.
The Vega Approach: Detection as a Distributed Function
Vega flips the SIEM model on its head.
Instead of centralizing data, Vega implements threat detection algorithms directly in the systems where data already lives. Think of it as moving security intelligence to the edge, where edge means your data lakes, your cloud storage, your existing infrastructure.
This matters more than it sounds. Here's why:
Cost reduction: You don't need to ingest and store all your security data in a separate system. Your AWS S3 buckets can run threat detection locally. Your cloud-native databases can process security analysis natively. You pay for what you use, not for a centralized repository that stores everything.
Reduced latency: Threat detection happens instantly, at the source. No network latency. No queue delays. No waiting for data to be shipped, indexed, and then processed.
Better data privacy: When you don't centralize data, you reduce the attack surface. Data stays closer to where it's generated. You have more granular control over who can access it.
Operational simplicity: There's no connector nightmare. No standardization burden. No months-long data migration projects. Vega claims enterprises can get operational in minutes, not months.
The AI component is crucial here. Vega doesn't just distribute threat detection—it uses machine learning to understand patterns, correlate events across systems, and identify anomalies that human analysts might miss. The AI can learn what normal looks like in your specific environment and flag deviations without generating false positives.
Andrei Brasoveanu, the Accel partner who led the Series B investment, emphasizes this point. He noted that legacy SIEM companies have always centralized data, which essentially puts customers in a difficult position. You become dependent on the vendor. Switching costs become astronomical because migrating all your historical data is a multi-year project. You're locked in.
Vega's model creates customer optionality. Because threat detection runs distributed across your existing systems, you're not dependent on Vega's infrastructure. You're using Vega's intelligence layer on top of your own systems. That's a fundamentally different relationship.

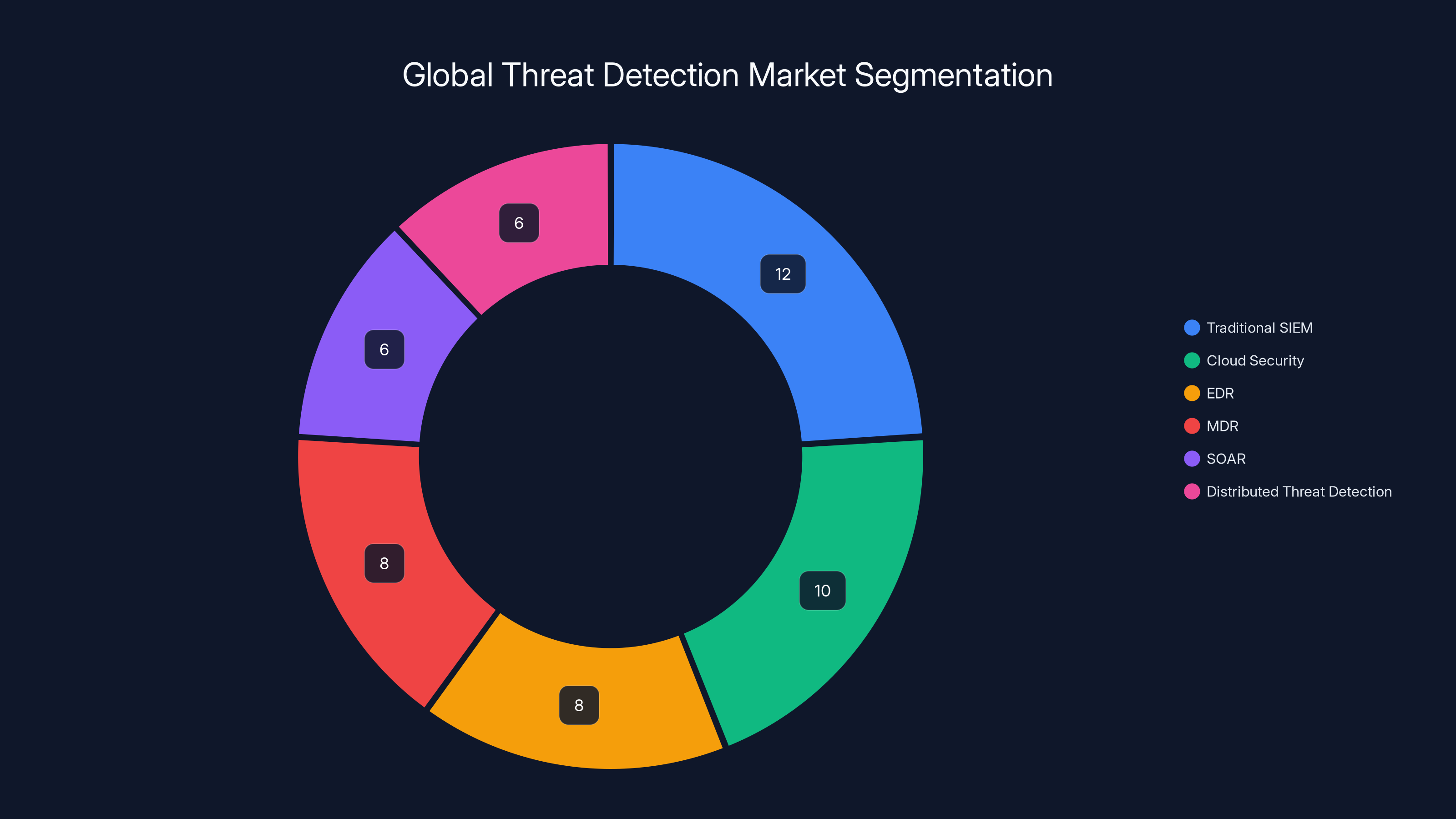
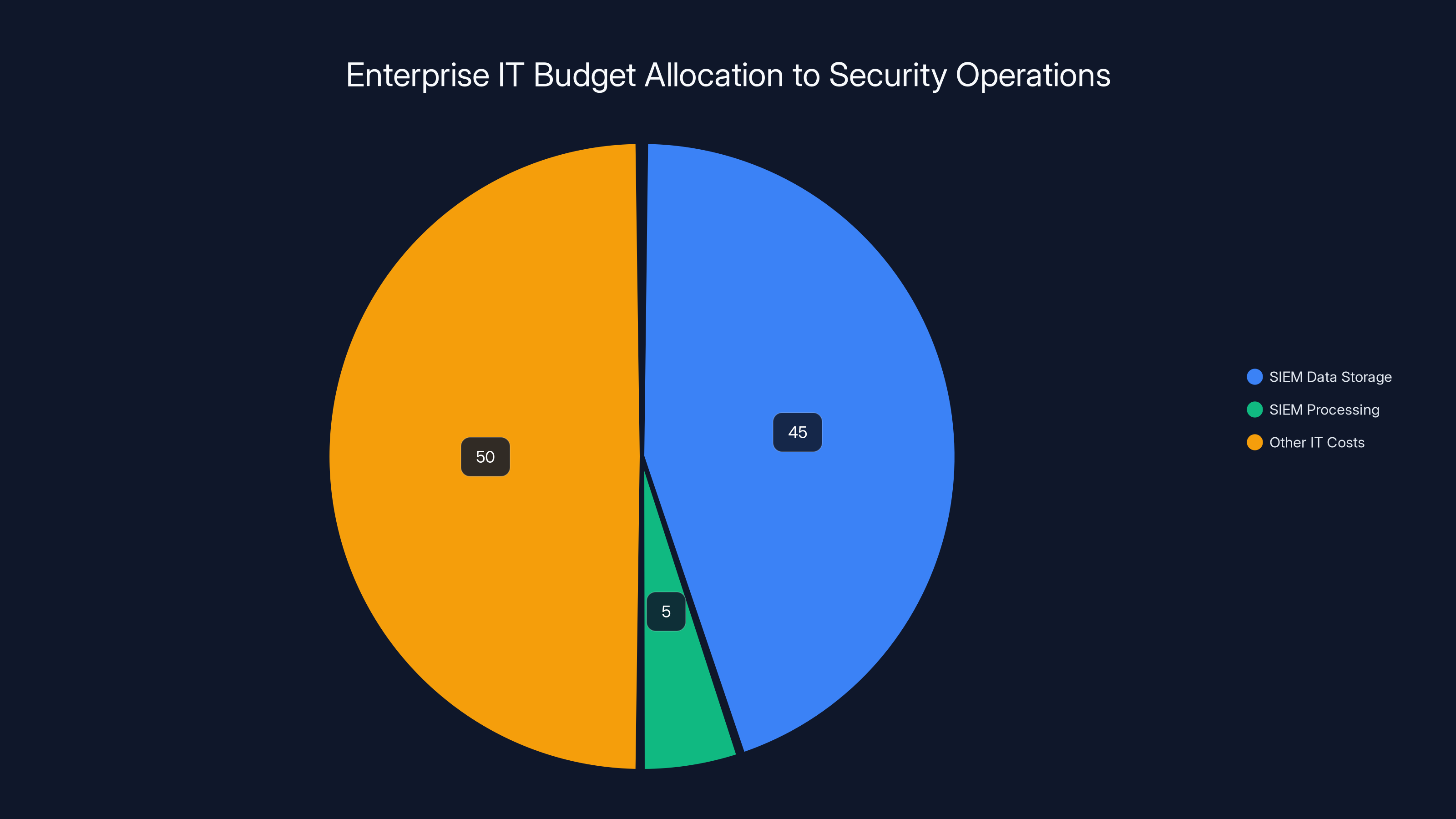
The global threat detection market is estimated at $50 billion, with distributed threat detection representing a significant portion. Estimated data.
Why This Matters in 2025
Timing matters in cybersecurity innovation.
The SIEM market has been dominated by the same players for nearly two decades. Splunk was acquired by Cisco for $28 billion in 2024, a deal that didn't address the underlying architectural problems—it just transferred them to a larger company. IBM, Elastic, Sumo Logic, and others all operate variations on the same centralized model.
But several trends have converged to create an opening for a different approach:
Cloud adoption is mandatory: The pandemic accelerated cloud migration by 5-10 years. Most enterprises now run hybrid or multi-cloud environments. Forcing all that data back to a central SIEM is working against the grain of how systems are actually built.
AI adoption is creating data explosion: Every AI implementation generates logs. Every machine learning model produces telemetry. Every generative AI API call creates records. The volume of data is growing faster than enterprises can centralize it.
Security requirements are getting stricter: Regulations like GDPR, CCPA, and industry-specific standards require granular data governance. Some organizations aren't allowed to move sensitive data outside certain geographic regions. Centralized SIEMs conflict with these requirements.
The cost problem is becoming critical: As companies face economic pressure, security budgets are under scrutiny. If you can cut security operations costs by 50-70% without reducing effectiveness, that's compelling.
Vega is entering the market at the moment when the SIEM model isn't just inconvenient—it's becoming untenable.

The Customer Validation Story
Here's what makes Vega's Series B noteworthy: the company didn't raise this round on slides and projections.
Vega has already signed multi-million-dollar contracts with banks, healthcare companies, and Fortune 500 firms. Customers include cloud-heavy companies like Instacart. These aren't startups willing to take risks. These are massive, complex enterprises making conscious decisions to migrate away from traditional SIEMs.
Shay Sandler shared insight into why these customers made the switch: "The only reason they would do that with a two-year-old startup is because the problem is so painful and other solutions on the market require an unrealistic expectation that the enterprise change the way they operate or do two years of data migrations."
Let's unpack what that means. An enterprise considering Vega has already tried everything else. They've tried Splunk. They've tried competitors. They've experienced the pain firsthand:
-
The cost: A typical Splunk deployment for a large enterprise costs $5-15 million annually. That's not just software licensing—it's engineering time to maintain the system, storage costs for all that indexed data, and network bandwidth to ship data to the central repository.
-
The complexity: Implementing a traditional SIEM takes 6-24 months. You need data connectors for every system. You need to normalize data formats. You need to build detection rules. You need to tune out false positives. It's an engineering project, not a configuration.
-
The lock-in: Once you've invested years and millions of dollars in a SIEM, switching is nearly impossible. You're stuck with vendor decisions, pricing increases, and whatever direction the vendor chooses to take.
Vega's value proposition eliminates all three problems. Enterprises can deploy Vega in weeks, not months. They can achieve immediate detection value without waiting for months of tuning. And they're not locked in—they're using Vega's intelligence on top of their own infrastructure.

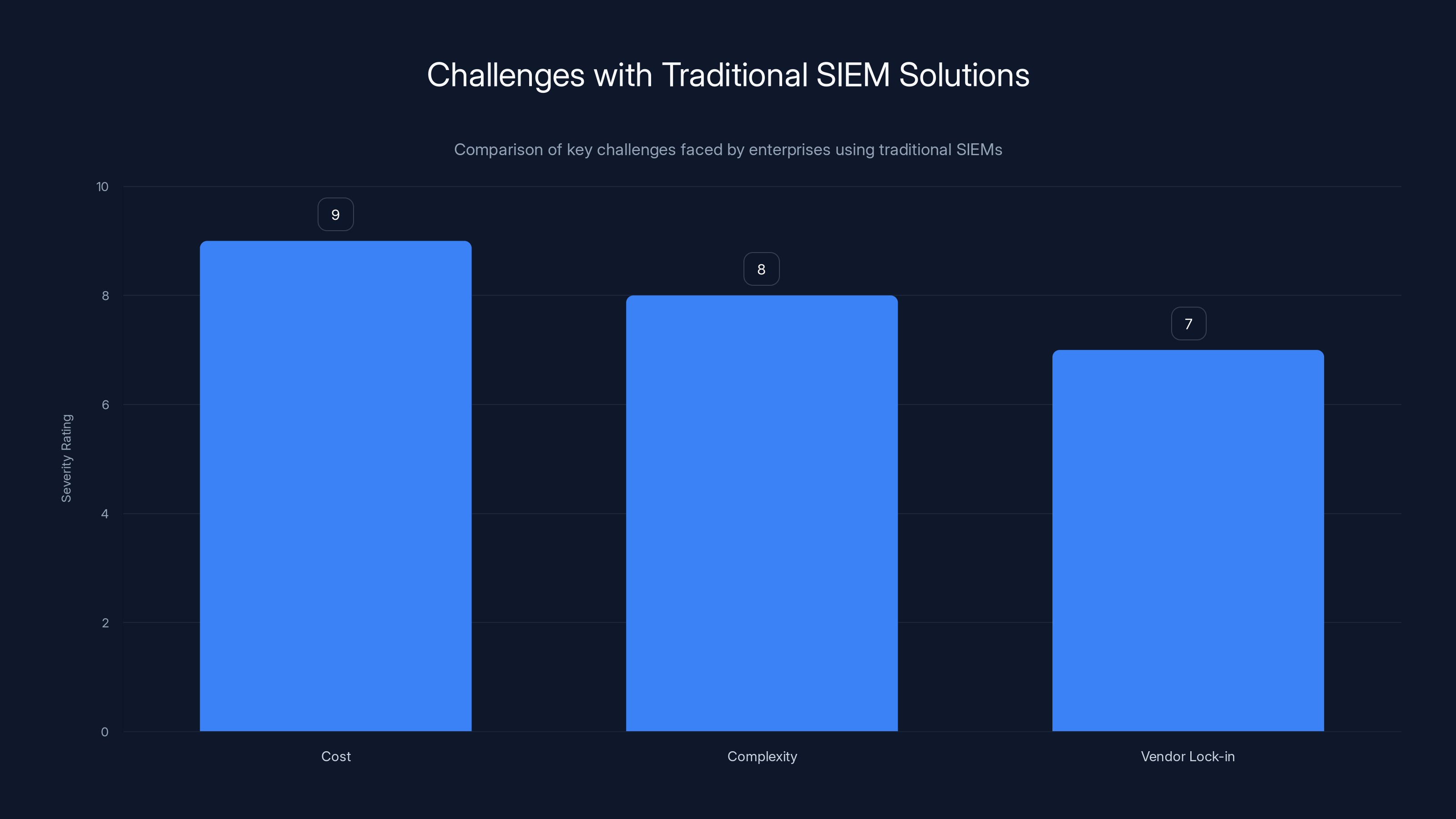
Traditional SIEM solutions pose significant challenges in terms of cost, complexity, and vendor lock-in, with high severity ratings across these areas. Estimated data based on narrative insights.
The Competitive Landscape
Vega isn't competing directly with Splunk in the traditional sense.
Splunk is a $28 billion acquisition now embedded inside Cisco. It's not going anywhere. But that doesn't mean Splunk's market position is secure. Instead, Vega is establishing a new category.
The threat detection market is fragmenting. Companies are no longer asking "which SIEM should we use?" They're asking "how do we detect threats across our distributed systems?" That's a different question, and it opens space for different answers.
Vega faces competition from several directions:
SIEM incumbents are adapting. Elastic, Sumo Logic, and others are building distributed architectures. But they're building on top of existing centralized systems, which means they're still fighting the cost and complexity problems inherent in that model.
Cloud-native security providers like Wiz, Snyk, and others are building threat detection for cloud environments specifically. But they focus on container and infrastructure vulnerabilities, not the broader threat detection problem.
Data lake analytics platforms like Databricks and Snowflake are adding security capabilities. But security is adjacent to their core mission, not central.
Vega's advantage is that it's purpose-built for distributed threat detection from the ground up. It's not a SIEM trying to adapt to clouds. It's not a cloud tool trying to add security. It's a security tool designed for the architecture that actually exists today.

How Vega's AI Actually Works
Vega's AI component is doing a lot of heavy lifting, and it's worth understanding what that actually means.
The startup uses machine learning to accomplish several things:
Anomaly detection: The AI learns what normal behavior looks like in your specific environment. It understands normal access patterns, normal data flows, normal API usage. When something deviates from those patterns, it flags it. This is more sophisticated than signature-based detection because it adapts to your environment.
Event correlation: Security events don't happen in isolation. An attacker might make multiple small moves that individually look innocent but collectively indicate a breach. AI can correlate events across systems and identify these chains.
Threat intelligence integration: Vega integrates with threat intelligence feeds that identify known malicious IPs, domains, and signatures. The AI can correlate these indicators with your environment data to identify compromise.
False positive reduction: Traditional SIEM detection rules generate tons of noise. The AI learns to distinguish between normal operational activity and actual security threats, reducing the alert volume that security analysts need to triage.
The key difference from traditional SIEMs is that this AI runs distributed. You're not sending all your data to a central system where a generic AI model processes it. Instead, Vega's intelligence is tailored to your specific environment, running on your data where it lives.
Vega's architecture is designed to maximize detection effectiveness while minimizing false positives, a key metric for security operations teams.
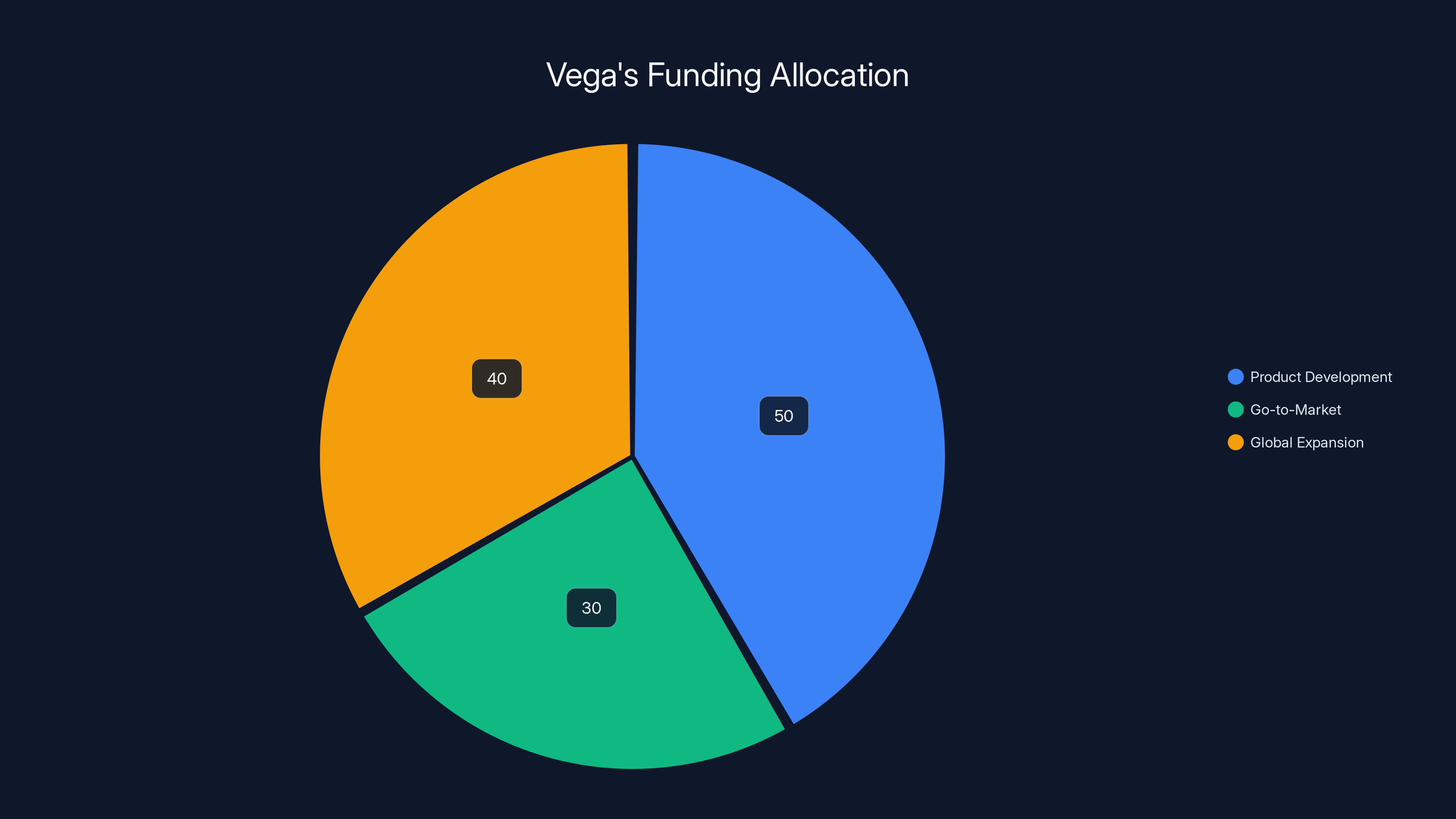
Estimated data shows Vega allocates
The Funding Details and What They Mean
A $120 million Series B represents significant capital, but the composition of the round tells you something important about how investors view the company.
Accel led the round. Accel is a major venture firm known for backing infrastructure and platform companies. They backed Slack, Figma, and Notion. Accel betting on Vega signals confidence that this isn't a niche security tool—it's a foundational platform that enterprises will build around.
Cyberstarts participated. That's a specialist investor focused entirely on cybersecurity. Having a cyber-focused investor on the round means Vega passed expert-level diligence from people who understand the space deeply.
Redpoint and CRV also participated. Both are tier-one venture firms. The participation of multiple quality investors indicates this wasn't a heavily competitive round—investors wanted in.
That
The global SIEM market alone is worth over
Vega is using the capital for three primary purposes:
Product development: Further building out the AI capabilities, expanding support for different data sources and cloud platforms, and improving the user experience.
Go-to-market: Hiring sales, marketing, and customer success teams to help enterprises adopt the platform. This is crucial because enterprises don't buy security tools casually—they need consultative sales and strong support.
Global expansion: Vega started in North America but needs presence in Europe, APAC, and other regions where large enterprises operate.

The Broader Implications for Enterprise Security
Vega's funding matters beyond the company itself. It signals something important about the direction of enterprise security.
For two decades, enterprise security has been defined by centralization. The idea was that security is most effective when you have complete visibility, and complete visibility requires centralizing all your data. That's a reasonable hypothesis, and it drove a multi-billion-dollar industry.
But the hypothesis was built on constraints that no longer exist. When security data volumes were manageable, centralization made sense. When enterprises ran primarily on-premises, centralization was technically feasible. When cloud adoption was optional, you could justify the expense.
None of that is true anymore. The constraints have changed, which means the architecture needs to change.
Vega represents a shift toward "defense in depth" at the data layer. Instead of one centralized system that detects everything, enterprises will increasingly use distributed threat detection across their systems, complemented by specialized tools for specific domains (cloud security, endpoint protection, network monitoring).
This shift has implications beyond Vega:
For enterprises: You'll have more options for how to organize your security infrastructure. You won't be forced to standardize everything into a single platform. You'll be able to optimize different parts of your infrastructure independently.
For security teams: The skillset required will shift. Instead of SIEM expertise, you'll need broader cloud architecture knowledge and data engineering skills. You'll be working across multiple systems rather than managing a single platform.
For other vendors: Companies building security tools will need to think about how their products integrate with distributed threat detection architectures. The ecosystem will become more modular.
For security effectiveness: Theoretically, distributed threat detection can be more effective because it catches threats faster and produces fewer false positives. The hypothesis is that local context improves detection accuracy.

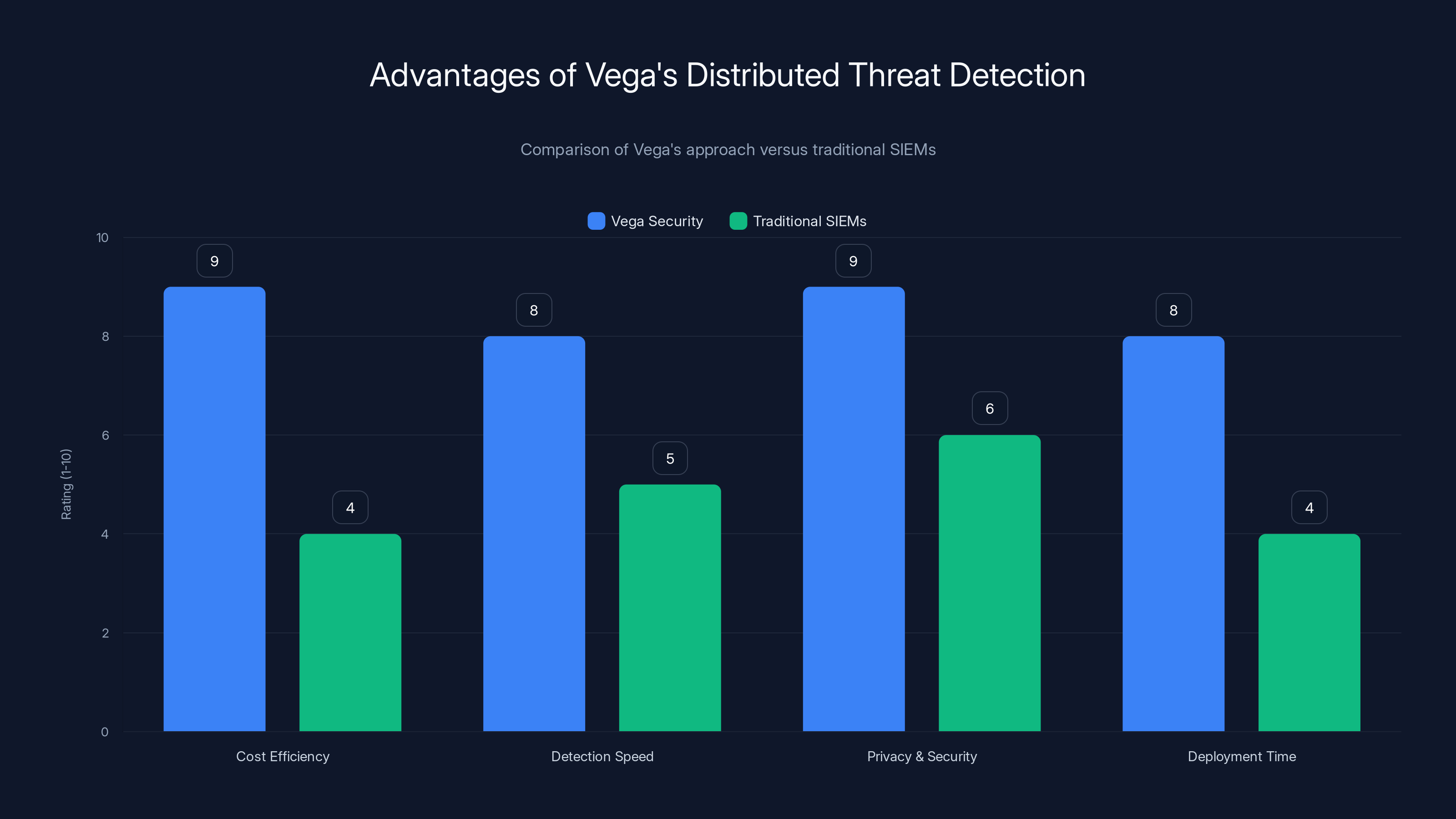
Vega Security's distributed approach offers superior cost efficiency, faster detection, enhanced privacy, and quicker deployment compared to traditional SIEMs. Estimated data.
Implementation Challenges and Realistic Expectations
Vega's value proposition is compelling, but we should be honest about implementation realities.
Any significant security infrastructure change requires change management. Even if Vega can reduce implementation time from months to weeks, that's still meaningful disruption. You're changing how your security team works. You're modifying monitoring and alerting processes. You're potentially changing who owns responsibility for different security functions.
Vega claims "no drama" implementation, and faster is definitely better than slower. But implementation time is only one dimension. Other challenges include:
Integration complexity: Even though Vega doesn't require centralizing data, you still need to integrate it with your existing systems. That integration is different from traditional SIEM integration, but it's not zero friction.
Team training: Your security operations team needs to learn a new platform. If they've spent five years becoming experts in Splunk, they're starting over with Vega. That's not an insuperable problem, but it's a real cost.
Process redesign: Threat detection and response processes might change. Your incident response playbooks might need updating. Your escalation procedures might need modification.
Legacy system support: Some enterprises have older systems that only produce logs in old formats. Getting those systems to work with a modern threat detection platform might require custom integration work.
These challenges aren't unique to Vega—they apply to any major security platform change. But they're worth acknowledging. The fastest possible implementation is still faster than the alternative, but it's not instant.

The Technology Behind Distributed Threat Detection
Understanding how Vega's technology actually works requires getting into the technical details.
Traditionally, threat detection follows a pipeline: data collection, data ingestion, data indexing, data search, threat analysis, alert generation, and incident response. Each stage involves moving data through a system.
Vega's architecture is different. Instead of that linear pipeline, threat detection algorithms run directly on data as it exists. The process looks more like:
-
Data stays in place: AWS S3 data stays in S3. Azure data stays in Azure. On-premises logs stay on-premises. No centralized repository.
-
Intelligence moves to data: Rather than moving data to the intelligence, Vega moves the intelligence to the data. Detection algorithms run in the same system where the data exists.
-
Results aggregate back: When threats are detected, the findings are aggregated into a central console for security analysts to review and act on.
-
Closed-loop response: Security teams can take action (block an IP, kill a process, disable an account) and the action propagates back to the system where the threat was detected.
This architecture is enabled by several technical trends:
Serverless computing: AWS Lambda, Azure Functions, Google Cloud Functions make it possible to run code (including threat detection algorithms) without provisioning servers. You pay for execution time, not infrastructure.
API-driven platforms: Modern cloud services expose APIs that let you query data and run logic. This enables threat detection to be integrated as an API service.
Edge computing: The concept of running intelligence at the edge—where data originates—is becoming standard architecture practice. Threat detection is one application of that principle.
Data lake standards: Formats like Parquet and Arrow, combined with systems like Iceberg and Delta Lake, make it possible to query massive data volumes without specialized indexing. You can run analytical queries directly on data lakes.
Vega's technology is built on top of these trends. They're not inventing anything fundamentally new—they're applying existing technologies in a novel way specifically to threat detection.

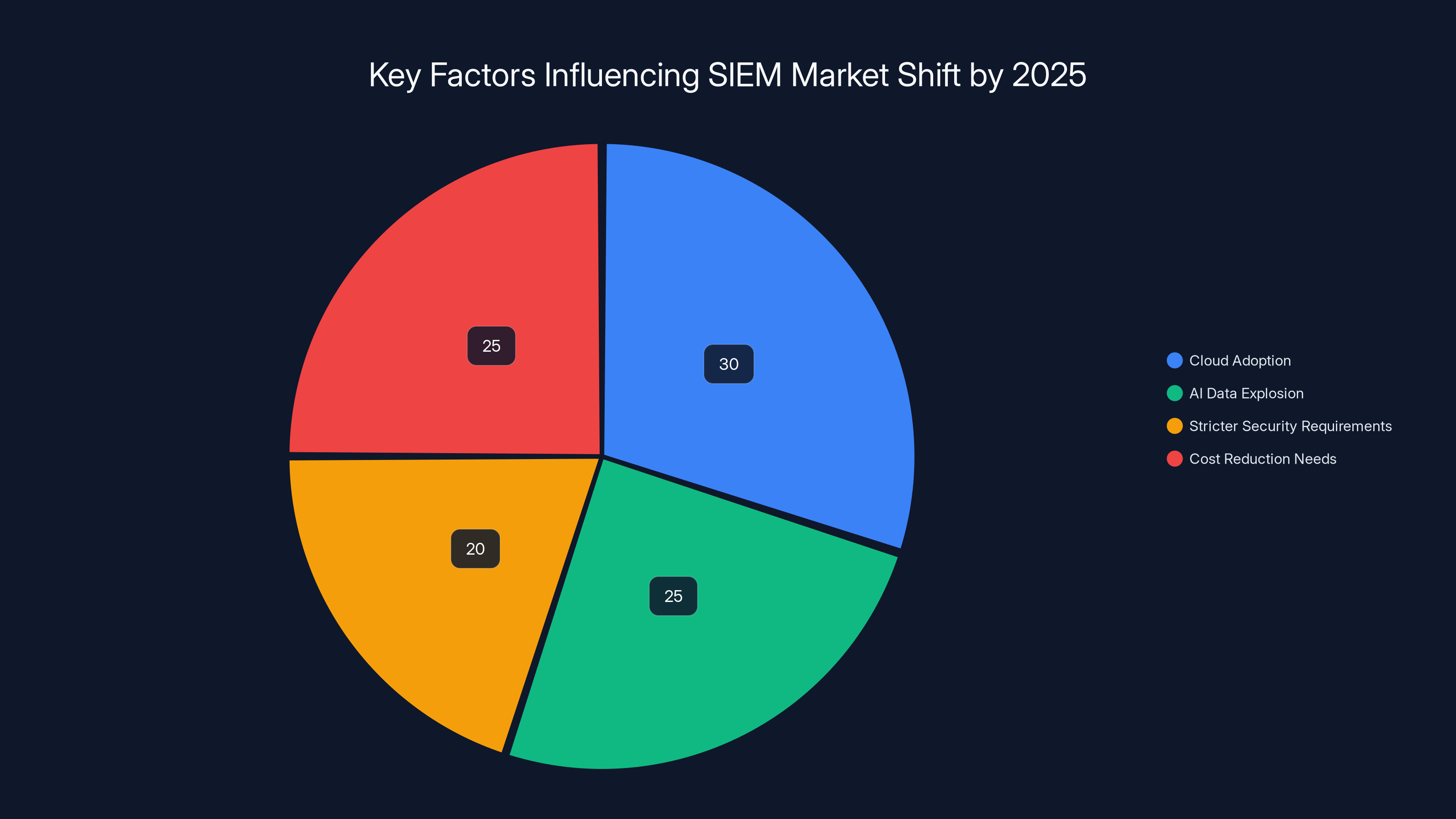
Estimated data shows that cloud adoption and cost reduction needs are the most significant factors driving changes in the SIEM market by 2025.
Market Size and Growth Trajectory
Vega is entering a market that's expanding rapidly for multiple reasons.
The global SIEM market is worth approximately $10-12 billion annually and growing at 10-15% per year. But that number underestimates the total market Vega can address because it only counts traditional SIEM products.
If you expand the definition to "threat detection and response platforms of all kinds," the market is significantly larger. Add cloud security, endpoint detection and response (EDR), managed detection and response (MDR), security orchestration automation and response (SOAR), and you're looking at a $50+ billion market globally.
Vega's specific positioning is in the "distributed threat detection" subset of this market. How big is that subset?
Estimates suggest that 40-60% of enterprise security workloads will migrate from traditional SIEMs to distributed or cloud-native architectures within the next 3-5 years. If that's true, and if Vega captures even 10% of that migration, the company is looking at a multi-billion-dollar business.
The growth trajectory makes sense because:
- Cloud adoption continues accelerating: More data lives in cloud every quarter
- Data volumes continue exploding: AI, IoT, and operational monitoring all generate more logs
- Cost pressure remains constant: Enterprises never stop trying to optimize security spending
- New regulations keep emerging: Each new regulation increases the need for better threat detection
Vega is surfing multiple waves simultaneously, which is why the funding round makes sense.
The Competition Response and Market Evolution
Vega won't face an empty market. Incumbents are aware of these trends and are responding.
Splunk (now part of Cisco) is building cloud-native features, but they're building them on top of a platform designed for centralization. It's like adding electric motors to horse carriages—it helps, but it doesn't solve the fundamental architectural problem.
Elastic has invested heavily in cloud deployments and API-first design. They're closer to Vega's model than Splunk, but they're still fundamentally a search-and-indexing platform trying to do threat detection, rather than a threat detection platform.
New entrants are arriving. Companies like Datadog are expanding from monitoring into security. Others are building specialized threat detection for specific cloud platforms. The market is becoming crowded.
But here's what's important: Vega isn't fighting to be the only threat detection solution. In a distributed architecture world, enterprises will use multiple specialized tools. Vega is fighting to be the foundational platform that ties those tools together and provides the core threat detection capability across your data infrastructure.
That's a different market position than traditional SIEMs occupied, and it's a more defensible position because it's aligned with how enterprise infrastructure is actually being built.

What This Means for Security Teams
If you're responsible for enterprise security, Vega's existence and funding signals something important: the threat detection tools available to you are getting better and becoming more cost-effective.
You're no longer forced to choose between:
- A comprehensive but expensive SIEM
- Fragmented point solutions that don't talk to each other
- Accepting blind spots and hoping attackers don't find them
You now have options. You can build threat detection architectures that:
- Cost less than traditional SIEMs
- Get deployed faster
- Require less operational overhead
- Actually match how your infrastructure is built
That's powerful. For security teams that have felt trapped by existing solutions, Vega and similar platforms represent genuine optionality.
The practical implication: if you're evaluating threat detection solutions right now, expand your consideration set. Don't assume you need another traditional SIEM. Consider distributed approaches. Consider cloud-native platforms. Consider vendors that are challenging assumptions you've accepted as unchangeable.

The Broader Story About Enterprise Software Innovation
Vega's Series B is noteworthy for reasons beyond cybersecurity.
It's another example of how markets dominated by large incumbents can be disrupted when underlying technology changes enable new architectures. Splunk was dominant because centralization made sense given the constraints of the time. But those constraints changed.
This pattern repeats across enterprise software. Infrastructure-as-a-service disrupted hardware companies. Cloud-native databases disrupted traditional database vendors. Managed services disrupted server software. In each case, the incumbents didn't lose because they were incompetent. They lost because the architecture that made them dominant became suboptimal.
Vega is another chapter in that story. And the cycle will continue. Vega won't be the final answer to threat detection. Something will eventually disrupt Vega just as Vega is disrupting Splunk. That's how markets evolve.
What matters is recognizing when an architectural shift is happening and positioning your organization accordingly. Right now, in threat detection, the shift is real. Distributed threat detection is becoming the preferred architecture for modern enterprises.

Looking Forward: What's Next for Vega
With
The priorities for the next 18-24 months will likely be:
Product expansion: Extending support to more cloud platforms, more data sources, and more specialized threat types. The core distributed detection model is proven. Now it's about covering more use cases.
Customer expansion: Moving from the early adopter stage to mainstream enterprise adoption. That requires building sales teams, customer success organizations, and partner programs.
Integration ecosystem: Building connectors and integrations with other security tools. Even in a distributed threat detection world, enterprises use multiple tools. Vega needs to play nicely with the ecosystem.
International expansion: Most current customers are probably in North America. Global enterprises operate globally. Vega needs presence and expertise in other regions.
Potential acquisition targets: There are smaller security companies whose capabilities would enhance Vega's platform. Some acquisition activity is likely as Vega tries to accelerate product development.
These priorities are typical for a venture-backed company at this stage. What matters is execution.

Key Takeaways
Vega's $120 million Series B represents more than just funding for one company. It signals fundamental shifts in how enterprise security is being architected:
-
Centralization is ending: The era of centralizing all security data in a single system is over. Distributed threat detection is becoming the standard architecture.
-
Cost and complexity matter: Enterprises are no longer willing to accept the cost and operational burden of traditional SIEMs when better alternatives exist.
-
Cloud changes everything: The shift to cloud infrastructure fundamentally changes what security architecture should look like. Distributed detection is aligned with cloud-native architecture.
-
AI enables new approaches: Machine learning makes it possible to run sophisticated threat detection without centralizing data, reducing false positives while improving detection effectiveness.
-
Incumbents face real disruption: Splunk at $28 billion is large, but Vega's model addresses problems Splunk's architecture can't solve efficiently. Disruption is genuinely possible.

FAQ
What is Vega Security?
Vega Security is an AI-powered cybersecurity startup that helps enterprises detect threats using a distributed architecture rather than centralized threat detection systems. Founded in 2022, the company raised a
How does Vega's threat detection work differently from traditional SIEMs?
Instead of requiring enterprises to centralize all security data in a single repository (the traditional SIEM approach), Vega runs threat detection where data already lives. The platform uses machine learning algorithms deployed across cloud environments, data lakes, and storage systems to identify anomalies and threats locally, then aggregates findings into a central console for security analysts to review and respond to.
What are the main advantages of Vega's distributed approach?
Distributed threat detection offers several significant advantages: dramatically lower costs since data doesn't need to be ingested into an expensive central repository, faster threat detection with reduced latency since analysis happens at the source, better privacy and security posture since sensitive data isn't centralized, and simpler operations since there's no complex data migration or connector infrastructure required. Enterprises can typically deploy Vega in weeks rather than months.
Why is the SIEM model becoming problematic for modern enterprises?
Traditional SIEMs were designed when enterprise security data volumes were manageable and most systems were on-premises. Today, enterprises operate across multiple cloud providers, generate exponentially more data from AI systems and IoT devices, and face increasingly complex regulatory requirements. Forcing all this data into a centralized repository becomes prohibitively expensive, operationally complex, and often violates data residency requirements. Vega's distributed approach solves these problems by working with modern infrastructure rather than against it.
What is the market opportunity for distributed threat detection?
The traditional SIEM market is worth
How does Vega's AI actually prevent false positives and improve detection?
Vega's machine learning models learn what normal behavior looks like in your specific environment by analyzing historical data and patterns. The system understands normal access patterns, typical data flows, and expected API usage. When activity deviates from these learned baselines, the system flags it as a potential threat. This context-aware approach dramatically reduces false positives compared to signature-based detection while improving detection effectiveness since the system is tuned to your specific environment rather than applying generic rules.
What does Vega's funding mean for the broader security industry?
Vega's
How long does Vega implementation actually take?
Vega claims to enable enterprises to achieve detection and response capability in minutes to weeks rather than the 6-24 months typical for traditional SIEM implementations. This acceleration is possible because Vega doesn't require centralizing data, building connectors for every system, or normalizing data formats. Organizations deploy Vega on top of existing infrastructure without major architectural changes, significantly reducing implementation burden and time to value.

The Bottom Line
Vega Security's $120 million Series B isn't just a funding milestone for a single startup—it's a signal that enterprise threat detection is undergoing a fundamental architectural shift.
For two decades, centralized SIEMs defined how enterprises approached security. They were expensive, complex to implement, and increasingly misaligned with cloud-native infrastructure. But they were the default because no better alternative existed.
Now a better alternative does exist, and enterprises are adopting it. Vega's Series B validates what progressive security teams already understand: distributed threat detection is the future, and the companies that get there first will capture significant market share.
For enterprises, this is good news. Your threat detection options are improving, becoming more cost-effective, and getting easier to implement. You're no longer forced to choose between expensive incumbents and fragmented point solutions.
For Vega, the $120 million gives the company the capital to execute on this opportunity. With intelligent investors and proven customer traction, the company has a credible path to becoming a major force in enterprise security.
The threat detection market has been dominated by the same players for too long. That's changing now.

Related Articles
- Authentication Beyond MFA in 2026: Phishing-Resistant Methods [2025]
- Proton VPN 70% Off Deal: Complete Breakdown [2025]
- Stalkerware Data Breach: 500,000 Records Leaked by Hacktivists [2025]
- Stalkerware Apps Hacked: 27 Data Breaches & Why You Should Never Use Them [2025]
- Proton VPN Windows Split Tunneling + Kill Switch: Complete Guide [2025]
- Flickr Data Breach 2025: What Was Stolen & How to Protect Yourself [2025]
![Vega Security Raises $120M Series B: Rethinking Enterprise Threat Detection [2025]](https://tryrunable.com/blog/vega-security-raises-120m-series-b-rethinking-enterprise-thr/image-1-1770741614073.jpg)



