Why Cybercriminals Are Getting Younger: The Generational Shift in Digital Crime [2025]
Seventeen. Nineteen. Twenty.
Those are the ages of suspects arrested after the recent Kido nursery hack and the coordinated attacks that devastated British retailers Marks & Spencer and The Co-operative grocery chain in April. The same gang responsible for the M&S breach went on to target Jaguar Land Rover in August, halting global production and disrupting thousands of businesses dependent on JLR supply chains.
Read that again. Teenagers orchestrated attacks that cost Fortune 500 companies millions of dollars and disrupted entire supply chains across the UK.
This isn't an outlier. This is becoming the norm.
For decades, high-profile cyberattacks were the domain of state-sponsored hackers from Russia, North Korea, Iran, and China. These were sophisticated operations backed by nation-states with resources, infrastructure, and geopolitical motivation. But something fundamental has shifted in the cybercrime landscape. The perpetrators of today's most destructive attacks share two striking characteristics: they're predominantly English-speaking, and they're frighteningly young.
The generational shift happening right now represents one of the most underestimated security crises facing organizations globally. It's not just that attackers are younger. It's why they're younger, how they're becoming capable of enterprise-level attacks, and what systemic failures have created an environment where cybercrime appeals to teenagers more than legitimate cybersecurity careers.
This article dives deep into the mechanics of youth cybercrime, explores the root causes driving teenagers toward criminal hacking, and presents concrete strategies organizations need to implement right now to defend themselves against a threat that's only going to get worse.
TL; DR
- Teen hackers are leading major attacks: Suspects in recent high-profile breaches (M&S, Co-op, Kido) range from ages 17-20, suggesting a dramatic shift from state-sponsored attackers to young English-speaking criminals.
- Ransomware-as-a-Service (Raa S) democratized hacking: These platforms let teenagers access professional-grade attack infrastructure without needing advanced technical skills, reducing barriers to entry.
- Four primary motivations drive youth cybercrime: Fame (notoriety), frustration (dissatisfaction), finances (quick money), and friends (community/belonging) create powerful incentives for young people to turn criminal.
- Cybersecurity has a serious image problem: Legitimate security careers are perceived as dull and technical while underground hacking carries prestige, causing talented youth to choose crime over career.
- Traditional recruitment excludes neurodiverse talent: The cybersecurity industry overlooks self-taught and neurodivergent individuals who don't follow conventional education paths, pushing capable hackers toward cybercrime.
- Organizations must shift from perimeter security to recruitment strategy: Defending against youth cybercrime requires addressing why young people are attracted to it in the first place, not just building better firewalls.

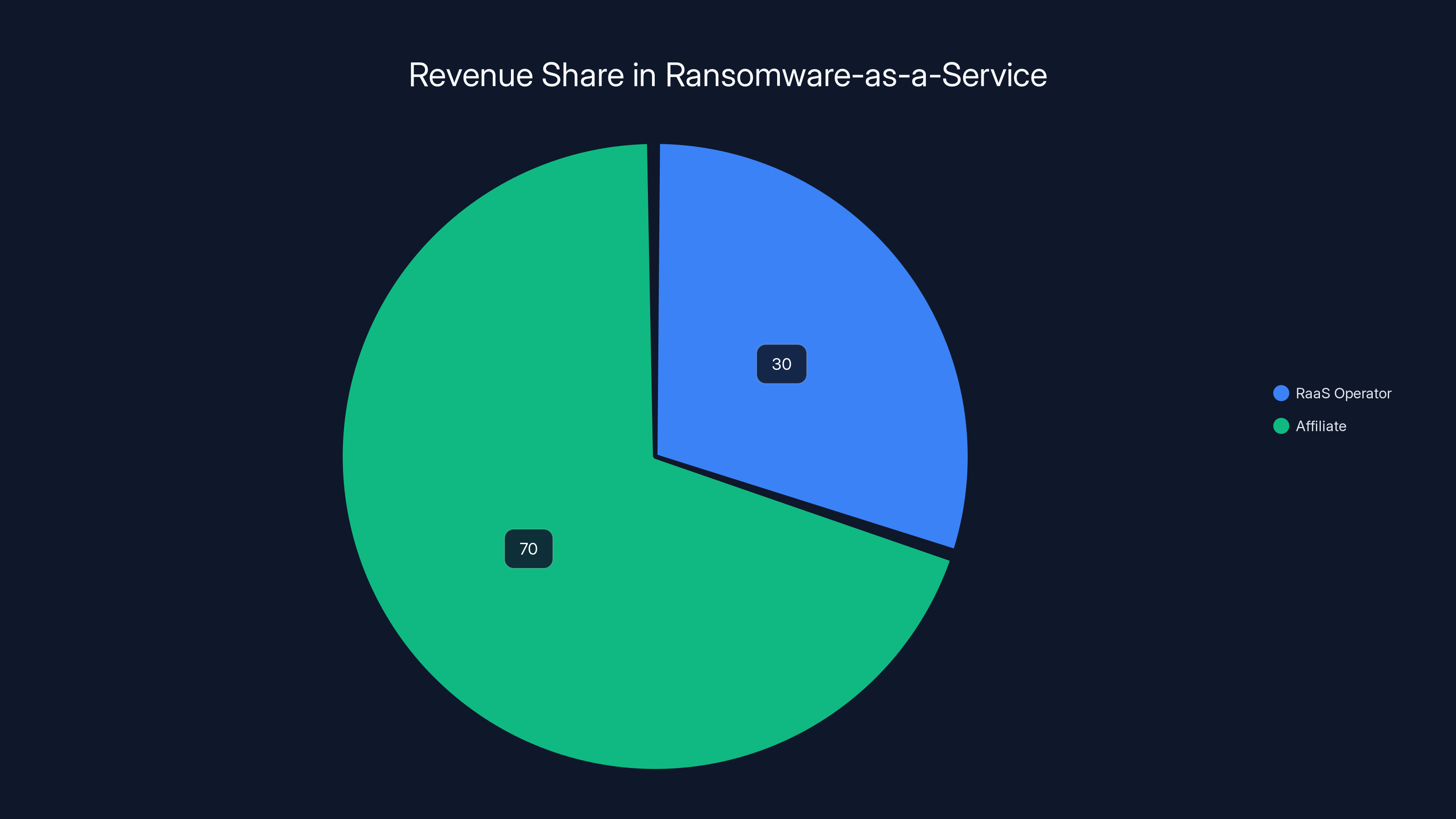
Ransomware-as-a-Service operators typically take 20-40% of the ransom payment, with affiliates keeping the majority share. Estimated data based on typical RaaS models.
The New Face of Cybercrime: Understanding the Youth Takeover
When most people think about major cyberattacks, they envision a cinematic scenario: shadowy operatives in Moscow or Pyongyang, sitting in government-funded facilities, orchestrating attacks on critical infrastructure. The reality of 2024-2025 is radically different.
The suspects arrested in connection with the M&S hack weren't hardened cybercriminals with decades of experience. They were teenagers. Young people who, just a few years ago, were sitting in high school classrooms learning algebra and history. Yet they possessed the technical sophistication and operational discipline to breach one of the UK's largest retail operations, extract massive amounts of data, and negotiate ransom payments.
What's particularly striking is the pattern. These aren't isolated incidents. Law enforcement across the UK, Europe, and North America have documented a sharp increase in youth involvement in major cybercrimes over the past 18-24 months. The age of perpetrators has dropped significantly from historical averages.
This generational shift has profound implications for how organizations think about cybersecurity. When threats primarily came from nation-states and organized crime syndicates, the security calculus was straightforward: these attackers had resources, motivation, and infrastructure. They targeted high-value victims strategic to their interests.
But young hackers operate under different logic. They're nimbler, less risk-averse, and driven by completely different motivations than state-sponsored actors. They also represent a virtually infinite supply of fresh talent. Nations are finite. Teenagers? There are billions globally with internet access and growing technical skills.
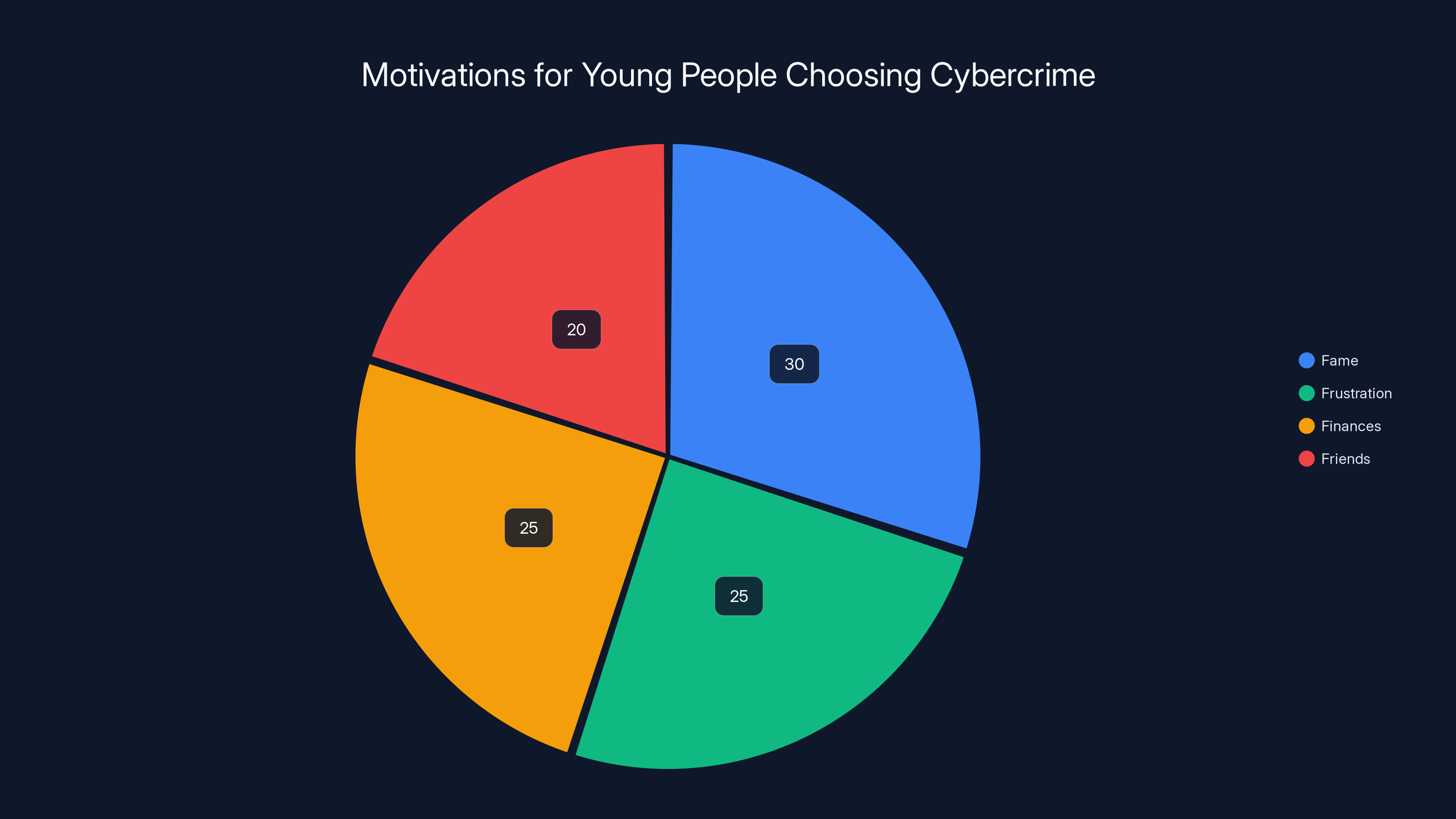
Fame is the leading motivation for young people engaging in cybercrime, followed closely by frustration and financial incentives. Estimated data based on the 'Four Fs' framework.
The Accessibility Explosion: How Ransomware-as-a-Service Changed Everything
Here's the crucial point that separates today's youth cybercrime wave from previous eras: you don't need to be a genius hacker anymore to launch enterprise-grade attacks.
This fundamental shift is driven by the explosive growth of Ransomware-as-a-Service (Raa S) platforms.
Traditionally, launching a sophisticated cyberattack required deep technical expertise. You needed to understand network architecture, exploit development, privilege escalation, data exfiltration techniques, encryption protocols, and operational security at an advanced level. These skills took years to develop and were possessed by relatively few people globally.
Raa S platforms obliterated that skill barrier.
Think of it like the difference between building a car engine from scratch versus buying a car and driving it. With a car, you don't need to understand combustion engines, metallurgy, or electrical systems. You just need to know how to operate it.
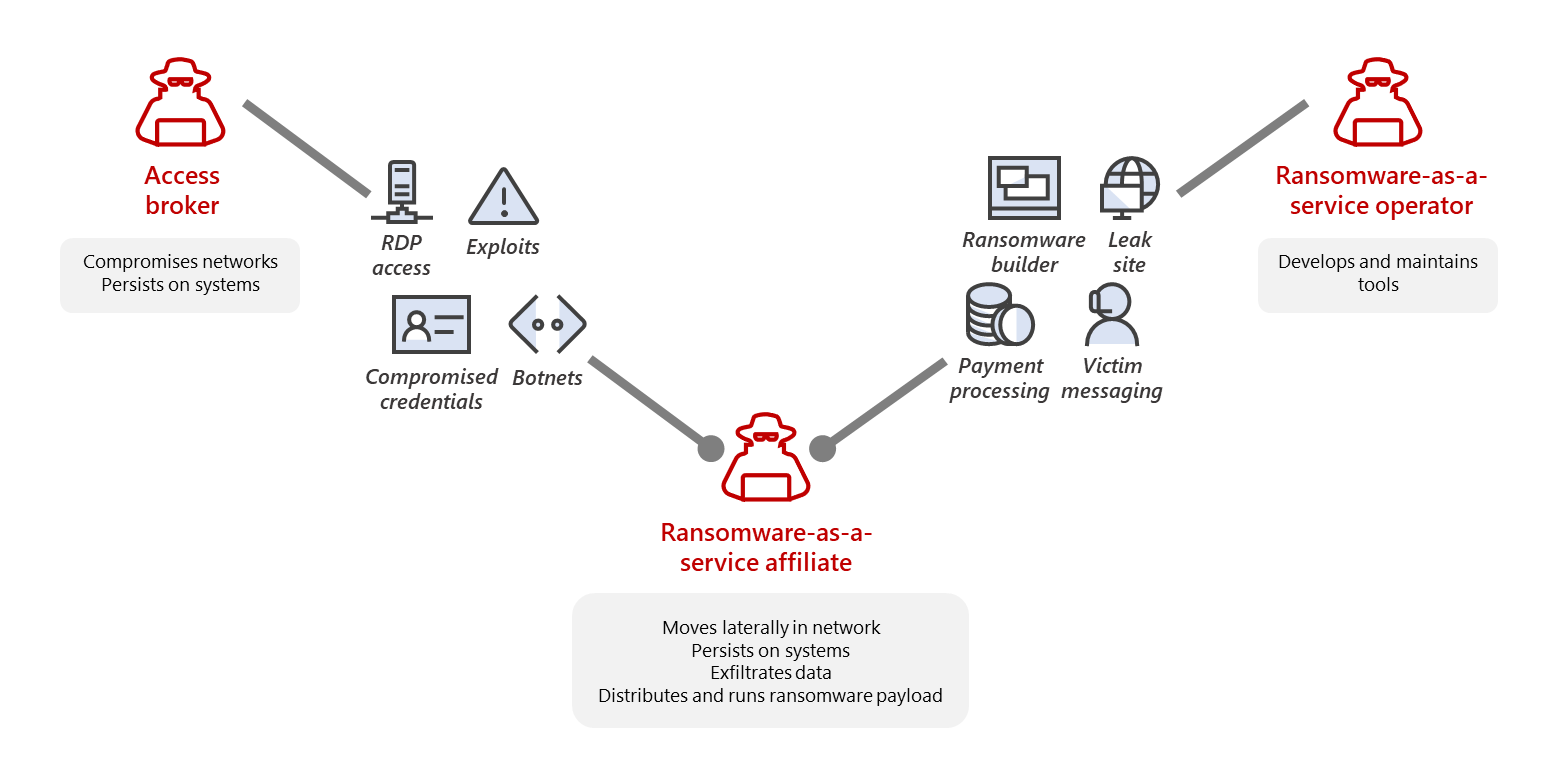
Raa S platforms work identically. A criminal organization that controls sophisticated attack infrastructure now packages that infrastructure as a service. They provide the tools, the command-and-control infrastructure, the hosting for stolen data, the payment processing, and often the technical support. Affiliates (the actual attackers) then rent access to this platform and use it to target organizations.
The economics are straightforward: when an attack succeeds and generates a ransom payment, the Raa S operator takes a cut—typically 20-40% of the payout. The affiliate keeps the rest. For the affiliate, this is revolutionary. They get professional-grade infrastructure without needing to build it themselves. They get anonymity and operational security provided by the platform. They get a revenue share model that distributes risk.
And they get it with minimal barrier to entry.
The teenagers arrested in the M&S and Co-op breaches didn't build their own ransomware. They didn't develop custom exploit code or create infrastructure. They accessed an existing Raa S platform, selected their targets, launched attacks, and negotiated ransoms. The technical complexity was handled by the platform. Their contribution was social engineering, reconnaissance, and execution.
What this means is obvious: accessibility has increased exponentially while skill requirements have decreased dramatically. A teenager with basic hacking knowledge and an internet connection can now access the same attack infrastructure that once required years of expertise to assemble.
Raa S platforms have effectively democratized enterprise-grade cyberattacks.
The Four Fs: Understanding Why Young People Choose Cybercrime
Accessibility explains how teenagers can launch sophisticated attacks. But it doesn't explain why they're choosing to do so. What motivates a 17-year-old to participate in ransomware attacks?
Fergus Hay, co-founder of the Hacking Games—a youth cybersecurity initiative aimed at channeling young talent into legitimate security careers—articulated the answer in a framework he calls "the four Fs": fame, frustration, finances, and friends.
Let's examine each:
Fame: The Notoriety Factor
Humans are status-seeking creatures. We crave recognition, notoriety, and the feeling of mattering. In the physical world, this might manifest as wanting to be a famous athlete, musician, or actor. In the digital world, it manifests differently.
When a teenager participates in a major cyberattack that hits a Fortune 500 company or a well-known retailer, they achieve instant notoriety. News articles feature the breach. Social media discusses it. The attack becomes legendary in underground forums and hacking communities. The perpetrators become folk heroes.
Contrast this with legitimate cybersecurity work. A teenager with exceptional hacking skills who pursues a legitimate career might spend five years working as an analyst, then five more years climbing toward a senior security role. Even when they reach the top, their accomplishments remain relatively anonymous. Their company might brag about security improvements, but their personal contributions stay hidden behind corporate anonymity and NDA agreements.
The risk-reward calculation looks terrible from a status perspective.
But orchestrate a high-profile ransomware attack? Suddenly you're the subject of international news coverage, forum discussions, and myth-building within the hacking community. Other young hackers know your name. You've proven yourself capable of the technical sophistication they aspire to. That's intoxicating for teenagers.
Frustration: Channeling Dissatisfaction
Every human experiences frustration. Teenagers experience it acutely. School systems that feel restrictive. Teachers who don't understand them. Societal pressures and expectations that don't align with their values. Boredom with the mundane expectations placed on them.
For neurodiverse teenagers—which represents a disproportionately high percentage of those with exceptional hacking skills—frustration often runs deeper. They may feel fundamentally misunderstood by educational systems designed for neurotypical learners. They may find conventional career paths inaccessible because hiring practices don't recognize their unconventional skill development. They may experience legitimate discrimination based on how they're neurologically different.
Cybercrime provides an outlet for this frustration. Major attacks can be framed (to themselves and others) as pushback against systems and institutions seen as unjust or oppressive. They're not just stealing money. They're sticking it to big corporations, to institutions they perceive as corrupt or exploitative.
This narrative is seductive. It transforms cybercrime from simple theft into something with ideological weight. It makes perpetrators feel like they're part of a movement, not just criminals.
Finances: The Money Problem
This one is straightforward but crucial: cybercrimes are often highly profitable.
A ransomware attack that successfully exfiltrates data and encrypts systems can generate ransom payments ranging from hundreds of thousands to tens of millions of dollars. Even when the Raa S operator takes their cut, individual affiliates can walk away with life-changing amounts of money.
For a teenager or young adult, this represents an earning opportunity that's literally impossible to access through legitimate work. At 19 years old, even high-paying jobs max out at
The financial incentive isn't just about money. It's about the rapid accumulation of wealth that completely reframes a young person's life possibilities. It's the ability to buy a house, support family members, build status and security, all before age 25. Traditional careers don't offer anything remotely comparable.
For young people facing economic uncertainty—which describes most of the post-2008 generation dealing with student debt, housing costs, and stagnant wages—the financial appeal of cybercrime is staggering.
Friends: The Community Pull
The final F is perhaps the most psychologically powerful: the need for community and belonging.
Young people are fundamentally social creatures. They want to belong to groups that matter, to be part of something bigger than themselves, to have their contributions valued and recognized by peers. This is normal developmental psychology.
But where are these communities forming? Increasingly, they're forming in gaming environments, Discord servers, and underground forums where hacking is not just accepted but actively celebrated and encouraged.
Fergus Hay noted that gaming communities serve as incubators for hacking skills and hacking culture. In games like Roblox, Fortnite, and Minecraft, young players experiment with modifying game code, creating aimbots, duping items, and "hacking" game mechanics. None of this is technically illegal (when done in the game's terms-of-service-violating but civil context), but it develops the same skills and mindset that translate directly to real hacking.
More importantly, in gaming communities, this behavior is rewarded. Players who successfully hack games get XP, status, notoriety, and recognition from peers. The community celebrates sophisticated hacks and clever exploits. Gaming culture has normalized and rewarded breaking rules and challenging authority in ways that traditional society hasn't.
When young people with hacking skills transition from gaming communities to actual cybercrime networks, the psychological framework is already in place. The community aspects that made gaming fun are replicated. The status and recognition are replicated. The collaborative problem-solving that's celebrated in gaming is now applied to criminal enterprises.
They're not just committing crimes. They're participating in a community that values their skills, celebrates their contributions, and makes them feel like they matter.
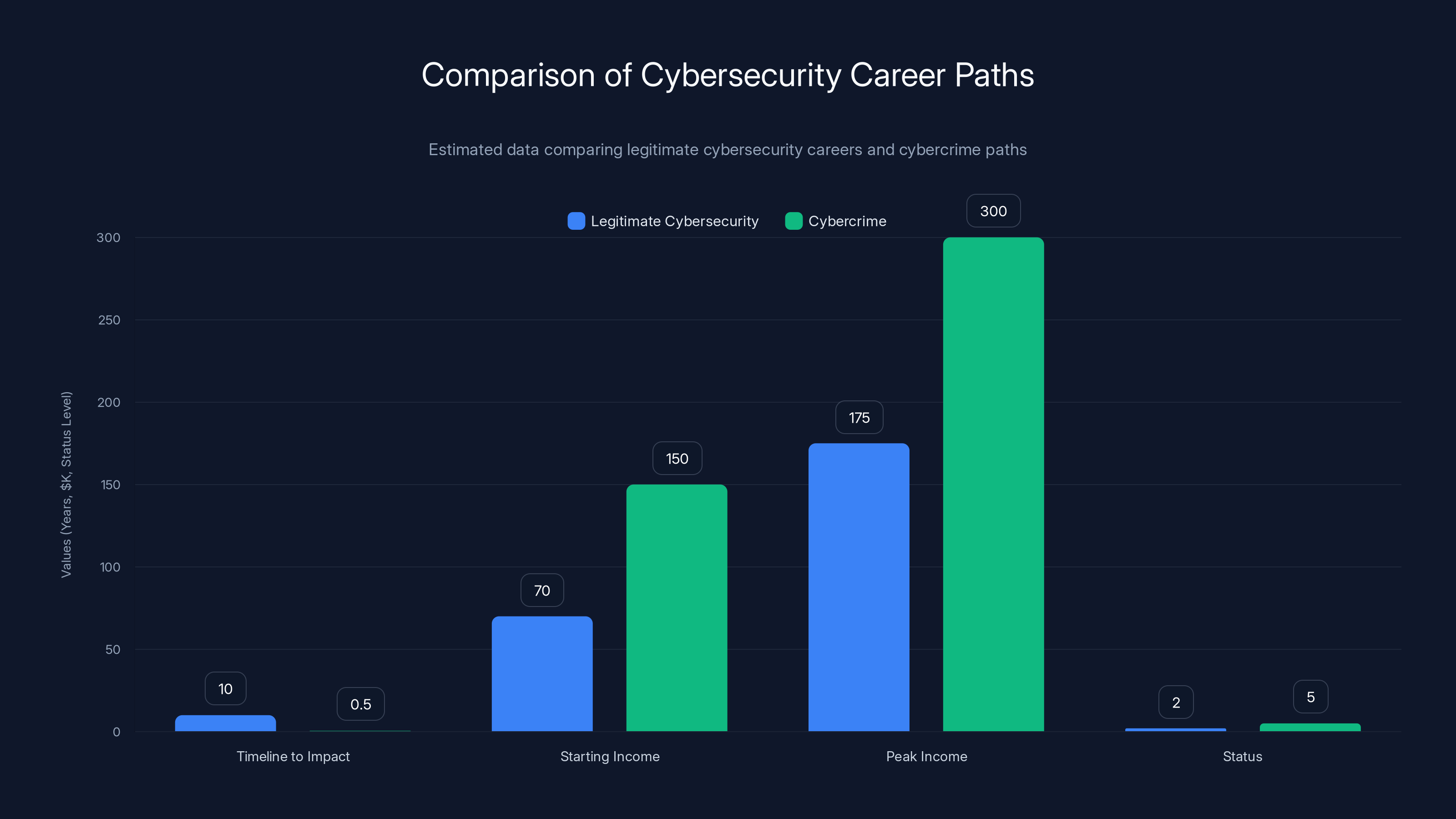
Estimated data shows cybercrime offers quicker impact and higher initial rewards compared to legitimate cybersecurity careers, highlighting the appeal to young talent.
The Broken Pipeline: Why Legitimate Cybersecurity Can't Compete
Now we arrive at the systemic root of the youth cybercrime crisis: the cybersecurity industry has completely failed to compete for young talent.
Understand what's happening from a young person's perspective. If they have exceptional hacking skills, they face two paths:
Path 1: Legitimate Cybersecurity Career
- Years of formal education or self-taught skill development
- Entry-level positions that may involve ticket triage, basic analysis, or menial security tasks
- Slow progression through mid-level roles requiring experience
- Eventually reaching senior positions with genuine autonomy and impact
- Timeline: 8-12 years to meaningful impact
- Income: Starting at 150-200k at peak
- Status: Invisible to most people, known only within industry circles
- Work environment: Corporate, risk-averse, compliance-focused
Path 2: Cybercrime
- Immediate access to professional infrastructure through Raa S platforms
- Direct participation in high-impact operations
- Quick financial rewards (hundreds of thousands in successful campaigns)
- Instant notoriety within hacking communities
- Community of peers who celebrate and value the work
- Timeline: Months to significant impact
- Income: Six figures from single campaigns
- Status: Folk hero in underground circles
- Work environment: Peer-driven, high-autonomy, thrill-seeking
For a young person with exceptional skills and limited patience, Path 2 is obviously superior.
The Image Problem
Cybersecurity suffers from a catastrophic image problem among young people. It's seen as dull, technical, compliance-heavy, and boring. The stereotypical cybersecurity professional in pop culture is either a paranoid basement dweller or a corporate compliance officer enforcing password policies that annoy everyone.
Contrast this with the pop culture image of hackers: brilliant, rebellious, capable of anything, operating on their own terms, fighting against oppressive systems. Movies and television have built a mythology around hacking that's immensely appealing to young people who feel constrained by conventional structures.
The cybersecurity industry has done almost nothing to counter this narrative. There's no mythology built around legitimate security careers. There's no celebration of the security researcher who found a critical vulnerability or the incident responder who saved a company. Cybersecurity has ceded the narrative entirely to underground hacking culture.
The Recruitment Problem
Cybersecurity recruitment practices are designed to screen out exactly the people most likely to excel in security roles.
Traditional hiring practices in cybersecurity emphasize formal credentials: degrees in computer science, certifications like CEH or CISSP, work history showing conventional career progression. These requirements systematically exclude self-taught prodigies, neurodiverse individuals who learn differently, and people who don't follow traditional education paths.
Yet an overwhelming majority of people with exceptional hacking skills are self-taught or neurodiverse. They learned by tinkering, by experimentation, by following their curiosity rather than curriculum. They may never pursue formal education because they find traditional schooling incompatible with how they learn.
By excluding this population, the industry eliminates its potential to recruit the most talented individuals. Simultaneously, these excluded individuals are exactly the people most vulnerable to recruitment by cybercriminals who actively value self-taught skills and don't care about credentials.
The Neurodiverse Talent Gap
There's substantial research suggesting that neurodiverse individuals—people with autism, ADHD, dyslexia, and other neurodevelopmental differences—are disproportionately represented among those with exceptional technical and hacking skills.
This creates a cruel symmetry: the traits that make someone exceptional at hacking (pattern recognition, systematic thinking, attention to detail, ability to hyperfocus, thinking in non-neurotypical ways) also often make it harder to navigate traditional education systems, pass conventional interviews, and function in rigid corporate hierarchies.
A neurodiverse 18-year-old with phenomenal hacking skills faces a situation where legitimate career paths are genuinely inaccessible. They can't land jobs because they can't navigate conventional interviews. They can't succeed in traditional education. But they absolutely can participate in hacking communities and cybercrime networks that accept them as-is, value their skills, and don't care about social conformity.
This isn't a personal failure on the part of young people. It's a systemic failure of the cybersecurity industry to build inclusive pathways for recruiting its most talented potential workforce.

The Skills Gap That's Actually Getting Worse
Paradoxically, even as youth participation in cybercrime has exploded, the cybersecurity industry is experiencing a worsening skills shortage.
In September 2024, the UK Government released a comprehensive skills study finding that nearly half of all UK businesses struggle with critical skills gaps in cybersecurity. The top three areas where young talent could make immediate impact—auditing and assurance, digital forensics, and cryptography and communications security—show persistent shortages.
Here's what's happening: as more talented young people are recruited into cybercrime, fewer are available for legitimate security work. Meanwhile, the industry has done nothing to make legitimate careers more attractive or more accessible. The pipeline is collapsing.
This creates a vicious cycle. As the skills shortage worsens, organizations have to cut security budgets, reduce security initiatives, and accept higher risk. Weaker security postures make organizations more vulnerable to attacks from the very young attackers now dominating the threat landscape. This drives more breaches, more notoriety for the young criminals, and more recruitment into cybercrime.
Meanwhile, legitimate security careers become even less appealing because organizations are stretched thin and can't invest in developing junior talent. Entry-level security positions disappear or become extremely competitive, making it harder for young people to break in legitimately.
The cycle accelerates.

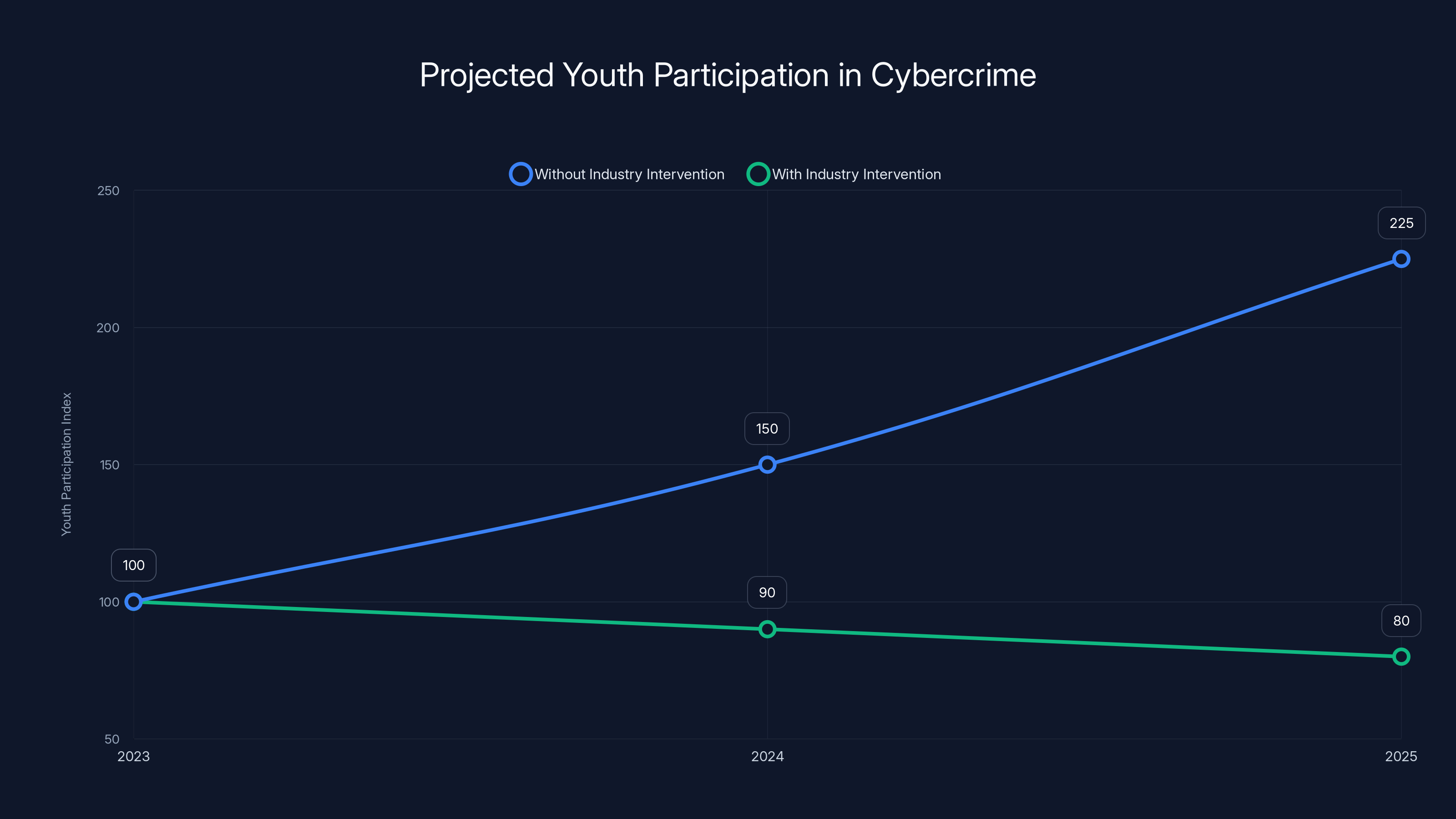
Estimated data shows that without industry intervention, youth participation in cybercrime could increase by 125% over the next two years. With proactive measures, this trend could be reversed.
How Young Hackers Operate: The Actual Attack Mechanics
Understanding how young attackers actually execute modern cyberattacks provides crucial insight into how to defend against them.
Unlike stereotypical hacker scenarios involving exotic zero-day exploits and custom malware, modern youth-led attacks typically follow a predictable pattern.
Initial Access: The Human Layer
Most attacks don't start with sophisticated technical exploits. They start with people.
Attackers use social engineering to obtain initial access: phishing emails targeting employees, credential stuffing using leaked password databases, exploiting public information to build convincing social engineering scenarios. They might pose as vendors, customers, or IT support staff to convince someone with access to provide credentials or install backdoors.
This is the one area where youth attackers actually have an advantage over state-sponsored actors. Teenagers often understand social dynamics and manipulation better than older operatives. They can sound convincing as peers, sympathetic IT support staff, or concerned colleagues.
Once they have legitimate credentials, the rest of the attack becomes technically straightforward. They use legitimate remote access tools (Microsoft Remote Desktop, Team Viewer, etc.) to access systems. They move through the network laterally, identifying valuable data. They avoid triggering security alerts by using legitimate administrative tools rather than malicious malware.
The entire attack relies on the principle that security research has repeatedly confirmed: the human layer is the weakest part of virtually every organization's security posture. And exploiting it requires social skills more than technical genius.
Lateral Movement: Hiding in Plain Sight
Once inside the network, attackers execute lateral movement using techniques that often evade detection because they rely on legitimate system functionality.
They might use built-in Windows tools like Ps Exec or Kerberoasting to move between systems and escalate privileges. They use credential harvesting to collect valid account credentials from compromised systems. They might exploit legitimate administrative tools or known security misconfigurations.
The key insight: modern attacks look like normal network activity because they ARE normal network activity, just executed by unauthorized people. This is why signature-based detection has become nearly ineffective.
Young attackers learned these techniques from public courses, You Tube tutorials, and community forums. They didn't invent anything novel. They're executing well-documented attack chains that every security professional knows exist.
But knowing an attack exists and successfully defending against it are completely different things.
Data Exfiltration: The Proving Ground
Once attackers have access to valuable data, they exfiltrate it. The purpose of data exfiltration in modern ransomware operations is crucial to understand: it's not primarily about stealing data for resale. It's about having leverage.
Ransomware operators want organizations to pay. The threat isn't just "we'll encrypt your systems." Many organizations have good backups and can recover from encryption. The real threat is "we have your data. If you don't pay, we'll publish everything: customer data, financial records, intellectual property, private communications."
For many organizations, the threat of public data publication is more damaging than the encryption itself. It drives ransom payments.
Young attackers understand this leverage. They identify high-value data (customer PII, financial records, proprietary information), exfiltrate it to attacker-controlled servers, and weaponize the threat of publication.
Encryption and Ransom Negotiation
The final phase involves deploying ransomware to encrypt systems and initiating ransom negotiations.
The Raa S platform handles most of this technically. The platform automatically generates the encryption key, encrypts target systems, displays the ransom note, and provides a portal for ransom negotiations. Young attackers coordinate with the targeted organization, negotiate payment, and manage the process.
Negotiation is where youth attackers demonstrate surprising sophistication. They understand payment psychology, currency considerations (ransoms in Bitcoin or other cryptocurrency to prevent seizure), and risk management. They use intermediaries and shell companies to distance themselves from payment flows.
What's remarkable is how this entire attack chain requires almost no novel technical knowledge. Every technique is documented, every tool is publicly available, and every phase has been repeated thousands of times. Young attackers succeed not because they're technical geniuses but because they're executing known techniques against organizations with inadequate defenses.

How Raa S Platforms Work: The Business Model of Modern Cybercrime
Ransomware-as-a-Service platforms represent the most significant shift in cybercrime economics in the past decade. Understanding how they work is essential for understanding why youth participation has exploded.
The Platform Architecture
A typical Raa S operation consists of several key components:
The Command and Control Infrastructure: Servers that host the ransomware payload, handle encryption operations, and provide dashboards for operators to track attacks. This infrastructure is typically distributed globally across compromised servers and bulletproof hosting providers to prevent law enforcement takedown.
The Data Hosting: Servers where exfiltrated data is stored before publication. These servers are typically located in jurisdictions with weak law enforcement cooperation (Russia, Eastern Europe, etc.) to minimize seizure risk.
The Ransom Portal: A web-based system where attackers communicate with victims, negotiate ransoms, and handle payment. These portals are often sophisticated, including live chat support, payment tracking, and detailed information about what data was stolen.
The Administrative Dashboard: A backend system where the Raa S operator manages affiliate accounts, tracks campaign performance, handles payouts, and maintains platform security.
The Leaks Site: A publicly accessible (but anonymized) website where the Raa S operator publishes data from victims who refuse to pay. This serves as a threat and a reputation mechanism within criminal circles.
The Economic Model
The financial structure of Raa S operations is remarkably transparent, at least to people inside the criminal ecosystem.
The Raa S operator sets an affiliate fee (typically 20-40% of ransom payments) that the operator retains. The affiliate keeps the remainder. The operator handles all infrastructure, technical complexity, and significant operational risk (maintaining infrastructure, law enforcement avoidance, handling disputes).
Affiliates handle reconnaissance, initial access, lateral movement, and ransom negotiation. In exchange for lower technical burden, affiliates give up a percentage of profits.
This is essentially venture capital for cybercrime. The operator funds the infrastructure; affiliates provide execution. Success is shared.
For young affiliates, this arrangement is revolutionary. They can participate in lucrative attacks without needing to build infrastructure or possess advanced technical skills. They can start with small operations and scale up as they prove themselves.
The Reputation Economy
Within Raa S communities, reputation is currency.
Operators track affiliate performance: How many successful attacks? How reliable are they? Do they execute professional operations? Do they handle disputes maturely? How much revenue have they generated for the platform?
Affiliates with strong reputations get offered better targets, higher-value opportunities, and preferential treatment. This reputation system drives professionalism and accountability within the criminal ecosystem.
Interestingly, this creates incentives for competence and reliability that often exceed what legitimate employers offer. A young affiliate who consistently executes high-quality attacks might earn more money, have more autonomy, and gain more recognition than a security professional of similar age in the legitimate sector.
Operational Security for Affiliates
Successful Raa S platforms invest heavily in operational security infrastructure for their affiliates.
They provide guidelines for avoiding detection. They offer infrastructure for anonymizing communications and payments. They facilitate dispute resolution when disagreements arise. They sometimes offer insurance-like guarantees protecting affiliates if law enforcement disrupts operations.
The level of sophistication in operational security within major Raa S networks often exceeds what individual threat actors could manage alone. Young affiliates benefit from this infrastructure without needing to build it themselves.

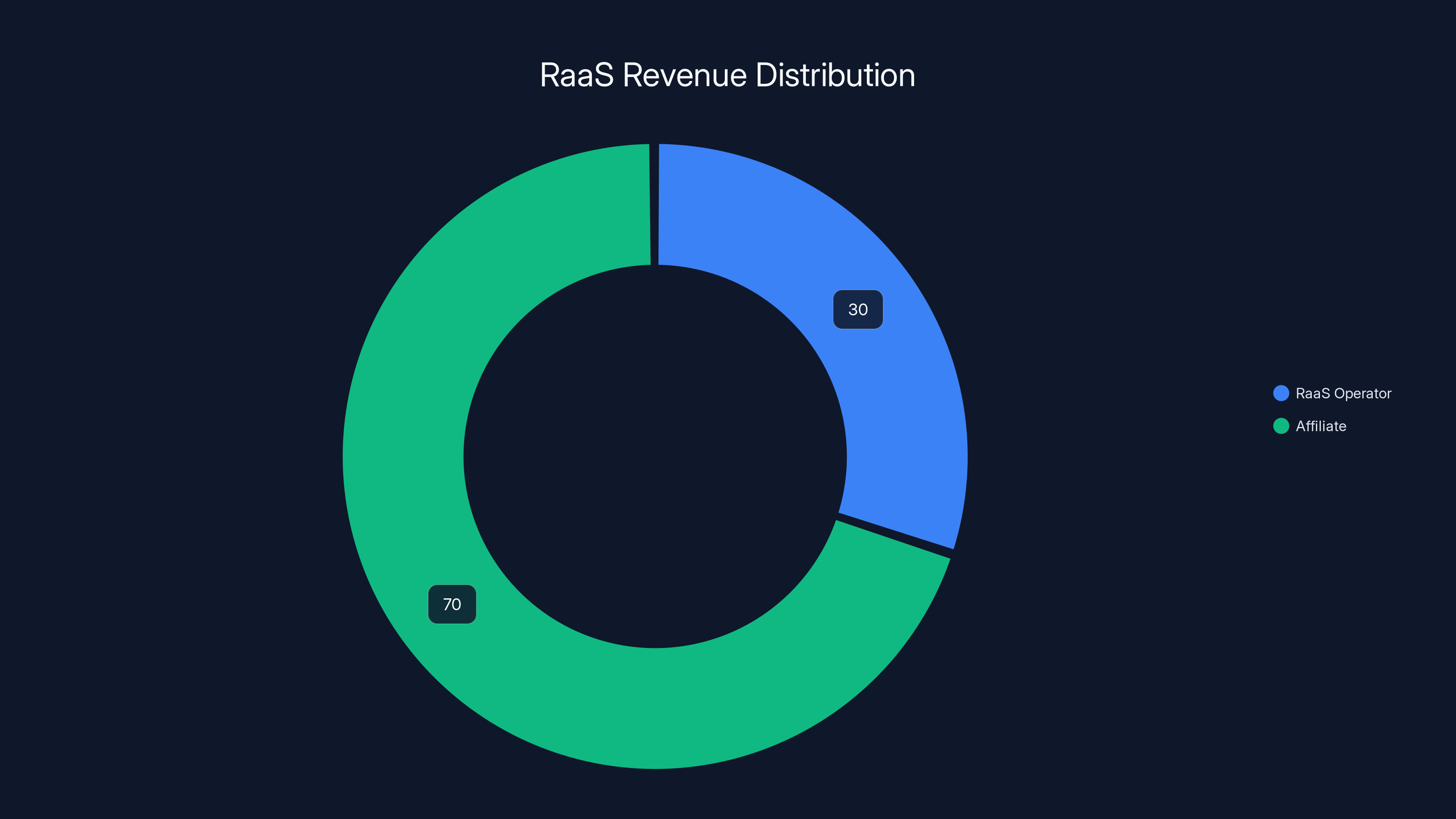
RaaS operators typically retain 20-40% of ransom payments, with affiliates receiving the remaining 60-80%. Estimated data based on typical RaaS models.
Case Study: The M&S Attack and What It Reveals
The Marks & Spencer breach in April illustrates the current state of youth-led cyberattacks with remarkable clarity.
The attack disrupted M&S's online services and ATM networks across the UK for several days, creating chaos for customers and staff. The retailer faced millions in direct losses from transaction failures, plus operational disruption and reputation damage.
What's remarkable isn't that the attack succeeded. It's who executed it: teenagers. The operational sophistication displayed—coordinating across multiple systems, evading detection, managing ransom negotiations—came from young people who shouldn't have possessed that capability according to traditional threat models.
The investigation revealed that the attackers used standard techniques: social engineering for initial access, legitimate administrative tools for lateral movement, and a professional Raa S platform for the actual encryption and ransom infrastructure.
Nothing in the attack was technically novel. Everything in the attack followed documented patterns that appear in thousands of incidents annually. Yet it succeeded against one of the UK's largest retailers because:
- Initial access was obtained through social engineering that was extraordinarily difficult for M&S to prevent
- The attackers executed with sufficient speed and sophistication to complete the attack before detection
- The Raa S platform handled technical complexity, allowing young attackers to focus on execution rather than infrastructure
- M&S's detection and response capabilities were inadequate to stop the attack in progress
From a defensive perspective, the M&S attack demonstrates that sophisticated attacks no longer require sophisticated attackers. It demonstrates that accessibility of professional-grade attack infrastructure has compressed the timeline from reconnaissance to impact dramatically.
It also demonstrates the operational professionalism young attackers can achieve. The ransom negotiation was professional. The threat of data publication was credible. The execution timeline was aggressive but realistic.

The Gaming Connection: How Fun Becomes Criminality
One of the most important (and least discussed) factors connecting youth to cybercrime is online gaming.
Fergus Hay's observation that gaming communities serve as incubators for hacking skills deserves deep examination. This isn't metaphorical. Gaming culture and hacking culture are merging in ways that have serious implications.
Modding as Gateway
In online games, "modding" (modifying game code to change behavior) is a fundamental skill. Players write custom code to create mods that add features, change mechanics, or enhance experiences. This is encouraged, celebrated, and an essential part of gaming culture.
Modding develops genuine programming and reverse engineering skills. Young players learn about code execution, memory management, system APIs, and security bypass techniques while modifying games. They learn to think systematically about how systems work and how to subvert intended behavior.
These skills transfer directly to real hacking. The methodologies are identical. The only difference is the target system.
Aimbots and Cheating Tools
Creating aimbots (tools that automatically aim and shoot in multiplayer games) is another common activity in gaming communities. Aimbots require understanding game code, intercepting player input, injecting commands, and evading detection systems. They require the same skills as malware development and command injection attacks.
Gaming culture celebrates aimbots and treats them as indicators of skill. Communities form around cheating tools. Creators of sophisticated aimbots achieve status and recognition.
Again, the skills transfer directly. The person who created a sophisticated aimbot for a popular multiplayer game has demonstrated the capability to create command injection tools, evade anti-cheat systems, and inject malicious code—the exact same skills needed for real cyberattacks.
Community and Status
What gaming communities provide is the same psychological reward structure that makes cybercrime appealing: status, community, recognition, and achievement. Young players who excel at hacking games receive praise, followers, sponsorships, and notoriety.
When these same individuals transition from modifying games to modifying real systems, they're already psychologically comfortable with the activity. The line between game hacking and real hacking has become blurred.

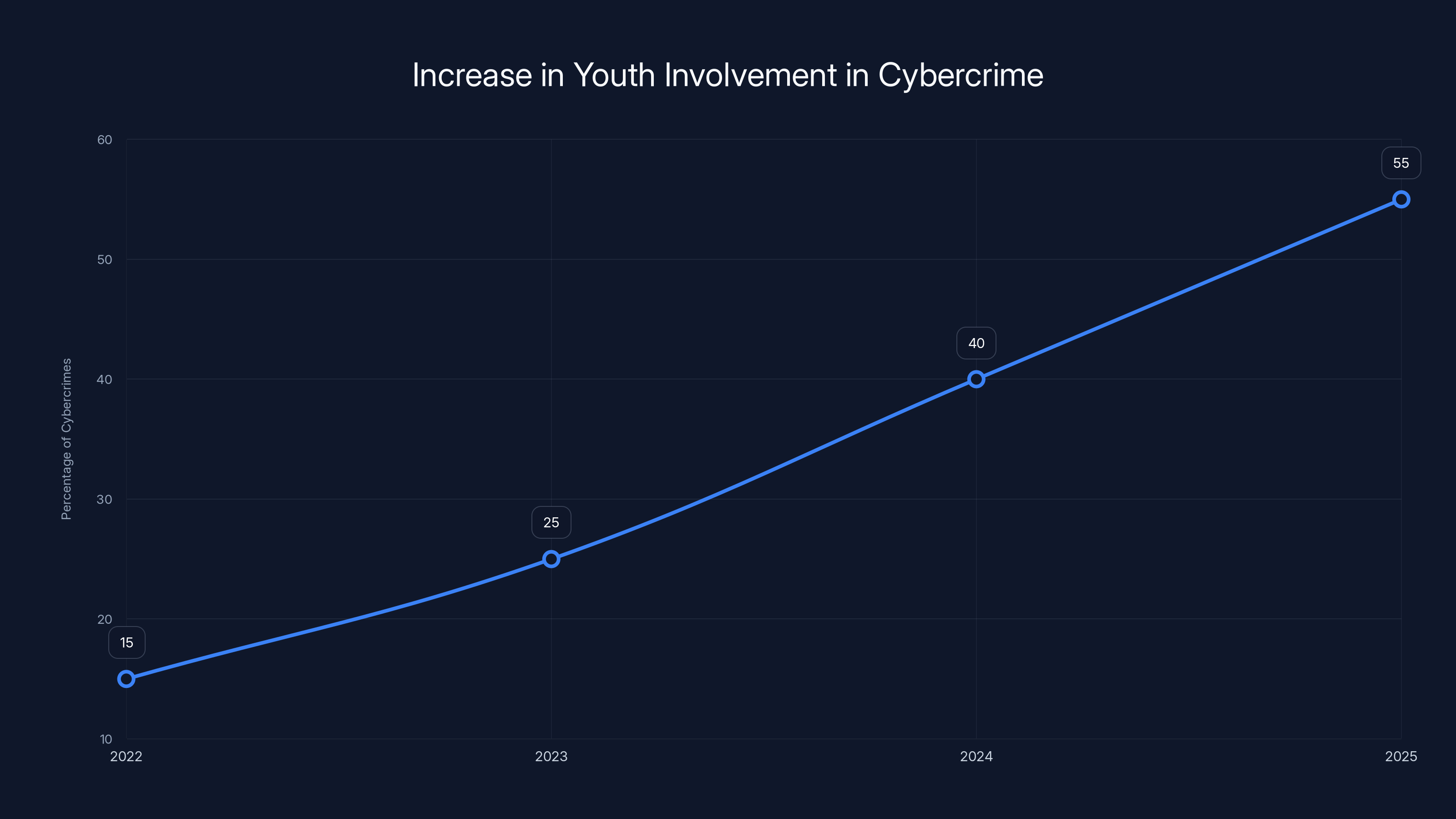
Estimated data shows a significant increase in youth involvement in cybercrime from 2022 to 2025, highlighting a shift in the demographic of cybercriminals.
Defending Against Youth Cybercriminals: The Strategic Approach
Traditional cybersecurity focused on building stronger perimeters: better firewalls, more sophisticated endpoint detection, better network segmentation.
These defenses have limited effectiveness against youth-led attacks because:
- Initial access bypasses technical controls: Social engineering works because it exploits human psychology, not technical vulnerabilities
- Lateral movement uses legitimate tools: Attacks that use legitimate administrative functionality evade signature-based detection
- The attacker's infrastructure is distributed: Raa S platforms are designed to be resilient against infrastructure-based defense
Defending against youth cybercriminals requires a completely different approach.
The Human Defense Layer
Since most attacks begin with social engineering, the human layer becomes the primary defense.
This doesn't mean "make employees paranoid about phishing emails." Everyone knows phishing attacks exist. The problem is that sophisticated social engineering is extraordinarily difficult to defend against, especially for young employees who haven't developed robust skepticism about authority figures and trusted-sounding requests.
Effective defenses require:
Authentication that doesn't rely on human judgment: Implement multi-factor authentication (MFA) that requires something the attacker doesn't have—a physical key, a biometric, or a device-bound token. If social engineering provides credentials, MFA prevents those credentials from being useful without additional factors.
Verification processes that bypass human perception: When someone requests system access or sensitive data, require verification through channels other than email or chat. Physical verification, out-of-band calls to known numbers, or institutional directories that can't be social engineered.
Rapid response to suspicious behavior: Social engineered access will eventually do something suspicious—accessing files outside normal job duties, modifying security settings, attempting privilege escalation. Detect these behaviors and respond immediately.
The Detection Problem
Most organizations detect attacks through endpoint detection and response (EDR) tools that flag suspicious behavior. But sophisticated attackers—including young ones using Raa S platforms—deliberately avoid triggering these alerts.
They use legitimate tools. They move slowly. They research normal behavior patterns before executing suspicious activities. They mimic the access patterns of legitimate users.
Detecting attacks that intentionally avoid looking malicious requires behavioral analysis. What access patterns does this user normally have? What files do they normally access? What systems do they normally connect to? When behavior deviates from the baseline, that's suspicious even if the behavior itself looks legitimate.
The challenge: Behavioral analysis requires substantial historical data and sophisticated analytics. For many organizations, this is beyond current capabilities.
Response and Recovery
When attacks succeed—and they will—the question becomes how quickly you can detect, respond, and recover.
Ransomware attacks that encrypt systems can cause catastrophic damage if you don't have recent, verified backups. The most critical defense after an attack succeeds is rapid recovery from clean backups.
This requires:
- Immutable backups: Backups that can't be modified or deleted even if attackers compromise administrative accounts
- Regular backup testing: Backups that haven't been tested can't be relied upon for recovery
- Air-gapped backup infrastructure: Backups stored offline, disconnected from network access
- Decryption preparation: Having documented processes for recovery (which systems matter most, recovery timeline, etc.)

The Recruitment Problem: Reversing the Trend
Ultimately, defending against youth cybercrime requires solving the recruitment problem. Organizations need to compete for talent that's currently being recruited into cybercrime.
This is radically different from traditional security approaches. It's not about technology. It's about making legitimate security careers more appealing than cybercrime.
Rethinking Hiring Requirements
The first step is abandoning formal credential requirements that exclude the most talented potential employees.
Instead of requiring degrees or certifications, evaluate demonstrated skills. Create apprenticeship programs for self-taught individuals. Partner with organizations like The Hacking Games that teach young people security skills in contexts they find engaging.
Hiring processes should assess actual security knowledge and capability, not credentials that correlate imperfectly with those qualities.
Building Inclusive Career Paths
Security careers need to be accessible to neurodiverse individuals. This requires:
- Flexible work arrangements: Accommodating different work patterns and preferences
- Clear documentation and expectations: Making implicit career progression and role expectations explicit
- Mentor support: Assigning mentors who understand neurodiverse work styles
- Neurodiversity hiring: Actively recruiting from organizations supporting neurodiverse professionals
Creating Immediate Impact Opportunities
Young people are attracted to cybercrime partly because they can have immediate impact. Traditional security careers require years of progression before handling meaningful work.
Organizations should create opportunities for talented junior staff to work on meaningful projects quickly. This might be security research, vulnerability analysis, or incident response work on actual breaches.
Status and Recognition
Cybersecurity organizations need to build cultures where security achievements are celebrated and recognized. This might involve:
- Public recognition: Sharing success stories and acknowledging individual contributions (with appropriate privacy)
- Speaking opportunities: Enabling team members to speak at conferences
- Publication opportunities: Encouraging security researchers to publish findings
- Career narrative: Making it clear how security achievements contribute to professional reputation and career progression
Community and Belonging
Final, but crucial, is creating community and belonging within legitimate security organizations.
Young people seek community. Cybercrime provides it. Legitimate security work should too. This might involve:
- Team cohesion activities: Building genuine friendships within security teams
- Collaborative projects: Work that requires creative teamwork
- Mentoring relationships: Connecting junior staff with experienced security professionals
- Internal communities: Slack channels, discussion forums, or informal groups around security topics
Community can be built, and it's a powerful recruitment and retention tool.

The Role of Law Enforcement and Geopolitics
Law enforcement has made significant efforts to prosecute youth cybercriminals. The M&S and Co-op attack arrests demonstrate that investigative capability exists.
But prosecution is playing defense. By the time law enforcement arrests attackers, the damage is done. The attack succeeded. The ransom was paid. The stolen data exists on attacker-controlled servers.
Moreover, prosecution creates martyrs. Arrested young hackers become legends within the hacking community. Their stories inspire others. Their operational techniques become documented and studied. The network effects work against law enforcement.
Geopolitically, the challenge is even more complex. Many Raa S platforms operate from Russia and Eastern Europe where law enforcement cooperation is weak. Some research suggests connection between Raa S platforms and Russian intelligence agencies.
Sanctions and international law enforcement cooperation have limited impact on this. The most effective response remains the strategic approach outlined above: make legitimate security careers more appealing than cybercrime.
The Future: What 2025-2026 Likely Holds
Based on current trends, several predictions about youth cybercrime in the coming years are reasonable:
Continued Increase in Participation
As Raa S platforms mature and become more accessible, more young people will be recruited into cybercrime. The barriers to entry continue to drop. The financial incentives remain substantial.
The age of perpetrators will likely drop further. Attacks executed by people in their late teens (ages 17-20) today will be standard within 2-3 years. By 2026-2027, expect attacks executed by people in their mid-teens (ages 14-17).
Increased Sophistication in Attack Planning
While technical sophistication may not increase dramatically (because young attackers already have access to professional infrastructure), planning sophistication will improve.
Young attackers will learn which targets are most vulnerable, which industries have highest ransom payment rates, which negotiation strategies work. Attack campaigns will become more targeted and efficient.
Greater Coordination and Organization
Informal networks of young attackers will increasingly organize into formal criminal syndicates. Hierarchy, specialization, and operational discipline within youth-led groups will increase.
You'll see emergence of young attack specialist roles: reconnaissance specialists, initial access specialists, lateral movement specialists, ransom negotiation specialists. As the field professionalizes, specialization increases.
Law Enforcement Responses
Governments will continue to pursue prosecution, with some high-profile arrests. These responses will have limited deterrent effect because the fundamental problem (accessibility of professional attack infrastructure and insufficient legitimate career alternatives) remains unaddressed.
Governments may pursue sanctions against Raa S platforms and countries harboring them. These will have moderate impact, potentially disrupting some platforms but not fundamentally changing the landscape.
Industry Responses
Organizations will invest in better detection, response, and recovery capabilities. There will be increased focus on incident response retainer services and cyber insurance.
Investment in backup and recovery infrastructure will increase. Organizations will realize that preventing attacks is insufficient; they must prepare for the likelihood they'll be successfully attacked.

Actionable Strategies: What Organizations Must Do Now
Given the threat landscape evolving as described above, organizations should prioritize these actions:
Immediate Priorities (Next 30 Days)
- Audit multi-factor authentication: Verify that MFA is enabled for all critical systems, especially administrative access points
- Test backup recovery: Conduct a full backup restoration test to confirm recovery capability
- Establish incident response procedures: Document how the organization will respond when attacked, who's involved, and decision authority
- Conduct social engineering assessment: Run controlled social engineering tests to identify personnel who are vulnerable to manipulation
Medium-Term Initiatives (30-90 Days)
- Implement behavioral analytics: Deploy tools that monitor for unusual access patterns and deviations from baseline behavior
- Segment network access: Ensure that systems are segmented so that compromise of one system doesn't automatically grant access to all systems
- Establish immutable backups: Implement backup infrastructure that can't be modified or deleted by attackers
- Develop security culture: Begin training programs focused on threat awareness and appropriate skepticism about requests for access
Long-Term Strategic Changes (90+ Days)
- Rethink hiring practices: Begin recruiting security talent without credential requirements; focus on demonstrated skill
- Build inclusive teams: Create career paths and working environments that support neurodiverse professionals
- Establish reputation: Make security achievements visible and celebrated within the organization
- Create community: Build teams with strong cohesion and shared mission
The Broader Context: Why This Matters Beyond Security
The rise of youth cybercrime represents a failure not just of the security industry but of broader society in channeling talented young people toward productive pursuits.
When a teenager with exceptional talent sees that legitimate pathways are blocked or unappealingly slow, while criminal pathways offer immediate rewards and recognition, that's a societal failure.
The solution isn't more law enforcement or better firewalls. It's creating legitimate pathways that compete with the illicit ones. It's building communities and career structures where talented young people feel they belong and can achieve recognition.
This is true for cybercrime but applies more broadly. Gangs, drug dealing, and other criminal enterprises often provide something legitimate society doesn't: immediate status, quick money, clear community, and rapid advancement.
Addressing youth cybercrime means addressing these underlying factors. It means creating legitimate alternatives that genuinely compete on these dimensions.
For the cybersecurity industry specifically, this is an opportunity disguised as a crisis. The most talented young people in the world are learning hacking skills. The opportunity is to recruit that talent into legitimate security work before it's too late.
The question isn't whether there's sufficient talent in the world to fill cybersecurity roles. There's more than sufficient talent. The question is whether the industry will build career paths and opportunities that are competitive with the alternatives.
Right now, it's failing that test. Until the industry changes how it recruits, develops, and values young security talent, expect youth participation in cybercrime to continue accelerating.

FAQ
What is Ransomware-as-a-Service (Raa S)?
Ransomware-as-a-Service is a business model where criminal organizations provide the infrastructure, tools, and support needed to execute ransomware attacks in exchange for a percentage of ransom payments. Raa S platforms handle the technical complexity of attack infrastructure, command-and-control systems, and data hosting, allowing affiliates to focus on reconnaissance and execution. This dramatically lowers the barrier to entry for conducting enterprise-grade attacks, which is why teenagers can now execute attacks that historically required advanced technical expertise.
Why are young people being recruited into cybercrime instead of legitimate security careers?
Young people are attracted to cybercrime due to four primary factors ("the four Fs"): fame (notoriety and recognition in hacking communities), frustration (outlet for dissatisfaction with conventional systems), finances (substantial income from ransom payments compared to entry-level legitimate work), and friends (community and belonging in hacking networks). Meanwhile, legitimate cybersecurity careers are perceived as dull and technical, involve years of progression before meaningful work, and have hiring practices that exclude self-taught and neurodiverse individuals who represent the most talented potential workforce. From a young person's perspective, cybercrime offers immediate rewards and recognition while legitimate careers offer neither.
How do teenagers execute sophisticated attacks if they don't have advanced technical skills?
Modern attacks rarely require advanced technical innovation. They rely on executing documented attack techniques (social engineering for initial access, legitimate administrative tools for lateral movement, professional Raa S platforms for encryption). Young attackers can access professional-grade attack infrastructure through Raa S platforms, which handle the technical complexity while attackers focus on reconnaissance and execution. Additionally, many young people learn hacking skills through gaming communities where modifying games and creating tools is encouraged and celebrated, developing genuine technical capability before transitioning to real attacks.
What's the connection between gaming communities and cybercrime?
Online gaming communities serve as incubators for hacking skills and hacking culture. Activities like game modding, creating aimbots, and bypassing anti-cheat systems develop the same technical skills needed for real cyberattacks. More importantly, gaming culture rewards these activities with status and recognition, normalizing rule-breaking and technical experimentation. When skilled players transition from gaming communities to cybercrime networks, the psychological framework is already in place: they're accustomed to being recognized for hacking, they understand the collaborative problem-solving aspects, and they've normalized operating in communities that celebrate breaking rules. Gaming is often where young people get their "first taste of hacking" in a culturally accepted context.
How can organizations defend against youth cyberattacks?
Defending against youth cybercriminals requires a multi-layered approach: implement multi-factor authentication to prevent social-engineered credentials from being useful, deploy behavioral analytics to detect unusual access patterns, maintain immutable offline backups for rapid recovery, and establish incident response procedures. However, preventing all attacks is unrealistic; organizations must focus equally on rapid detection and recovery capabilities. Beyond technology, organizations should invest in building strong security cultures and responding quickly to suspicious activities. Law enforcement approaches have limited deterrent effect because the fundamental problem—accessibility of professional attack infrastructure and insufficient legitimate career alternatives—remains unaddressed.
What should the cybersecurity industry do to compete for talent?
The industry needs to fundamentally rethink recruitment and career development. First, abandon credential-based hiring that excludes self-taught and neurodiverse individuals—evaluate demonstrated skill instead. Second, create career paths where talented technologists can achieve impact and recognition without managing people. Third, build inclusive working environments that accommodate different work styles. Fourth, create opportunities for junior staff to work on meaningful projects quickly rather than requiring years of progression. Finally, build community within security teams and provide public recognition of individual achievements. Until the industry creates legitimate career paths that compete with cybercrime on status, income, and belonging, expect youth participation in attacks to continue accelerating.
What's driving the age decrease of cybercriminals?
Three primary factors explain why attackers are getting younger: the democratization of attack infrastructure through Raa S platforms (removing the technical skill barrier), the gaming community's normalization of hacking skills (creating a pipeline of young talent), and the legitimate security industry's failure to create appealing career alternatives. Additionally, neurodiverse teenagers with exceptional hacking skills often find traditional career paths inaccessible due to hiring practices that require formal credentials, making them prime targets for recruitment by criminal organizations that value skills over credentials. As these factors intensify, expect the age of perpetrators to continue decreasing.
How does cryptocurrency enable youth cybercrime?
Cryptocurrency (primarily Bitcoin and Monero) enables cybercrime by providing anonymous payment channels that can't be seized by law enforcement and are difficult to trace back to perpetrators. When organizations pay ransoms in cryptocurrency, the funds move directly to criminal organizations without going through traditional financial systems that would flag suspicious activity. Cryptocurrency also allows young attackers to receive their portion of ransom payments without needing traditional banking relationships, which would be impossible for minors in many jurisdictions. The ability to quickly convert cryptocurrency to local currency (through peer-to-peer exchanges and localized trading) completes the anonymity chain, allowing young attackers to quickly access proceeds from attacks.
What role do gaming communities play in recruitment into cybercrime?
Gaming communities don't directly recruit people into cybercrime, but they serve as pre-recruitment environments where young people develop hacking skills, learn about exploit techniques, and develop identity as a "hacker." Gaming communities also establish the psychological framework where breaking rules for technical achievement is celebrated and rewarded with status. When criminal organizations recruit from these communities, they're recruiting people who already self-identify as hackers, have developed relevant technical skills, and are psychologically comfortable with the cultural values of the hacking community. The transition from gaming community hacking to actual cybercrime is often gradual, with young people initially participating in gray-area activities (game hacking, mod creation) before transitioning to actual criminal enterprises. This pipeline effect explains why criminals effectively target gaming communities for recruitment.

Conclusion: The Critical Years Ahead
The cybersecurity landscape is being fundamentally reshaped by youth participation in attacks. The suspects arrested in the M&S, Co-op, and Jaguar Land Rover breaches aren't anomalies. They represent the leading edge of a generational shift in cybercrime.
This shift isn't inevitable. It's the result of specific systemic failures: the democratization of attack infrastructure, the gaming community's normalization of hacking skills, and the security industry's complete failure to compete for young talent.
Organizations must respond on two levels. First, immediately, they must improve their defensive posture: implement multi-factor authentication, deploy behavioral analytics, establish immutable backups, and develop incident response procedures. These tactical measures buy time and reduce damage when attacks succeed.
But tactical measures alone are insufficient. At the strategic level, the security industry must fundamentally rethink how it recruits, develops, and retains young talent. Credential-based hiring that excludes self-taught individuals and neurodiverse people must end. Career paths that require years of progression before meaningful work must change. The perception of security work as dull and technical must shift.
This is genuinely difficult. It requires questioning hiring practices developed over decades. It requires building inclusive teams and work environments. It requires celebrating security achievements publicly. It requires accepting that talented individuals might not follow traditional career paths.
But the alternative—allowing the most talented young people to be recruited into cybercrime—is worse.
The next 24 months will determine the trajectory of youth cybercrime for a decade. If the industry acts now to build competitive legitimate pathways, it can stem the flow of talent into cybercrime. If it continues with business as usual, expect youth participation in attacks to accelerate exponentially.
The technology of cybersecurity is well-understood. The human problems—recruitment, retention, career development, team culture—are solvable. The question is whether the industry will prioritize solving them.
The clock is ticking.
If you're building incident response processes or managing security teams competing for talent in the current landscape, you face real challenges. Consider how tools designed for team collaboration and workflow automation—like Runable—can help your team operate more efficiently. When security teams are stretched responding to constant threats, automation of documentation, reporting, and process management becomes critical. Runable's AI-powered platform helps teams automate incident reports, security documentation, and operational processes starting at $9/month—letting your team focus on actual security rather than busywork.
Key Takeaways
- Youth participation in major cyberattacks (M&S, Co-op, Jaguar Land Rover) demonstrates that teenagers now execute enterprise-level breaches that previously required state-sponsored actors
- Ransomware-as-a-Service platforms democratized attack infrastructure, removing technical barriers and allowing 17-20 year olds to launch sophisticated attacks without advanced expertise
- The Four Fs (Fame, Frustration, Finances, Friends) explain why young people are attracted to cybercrime: immediate notoriety, community belonging, rapid income, and outlet for dissatisfaction
- Gaming communities serve as incubation environments where teenagers develop hacking skills through modding, aimbots, and cheating tools that translate directly to real cyberattacks
- The cybersecurity industry's failure to create appealing career alternatives is pushing talented young people toward crime; legitimate security work is perceived as dull, requires years of progression, and excludes self-taught and neurodiverse individuals
- Traditional defense approaches (perimeter security, signature-based detection) have limited effectiveness against youth attackers who use social engineering for access and legitimate tools for lateral movement
- Organizations must improve immediate defenses (MFA, behavioral analytics, immutable backups) while fundamentally rethinking recruitment to compete with cybercrime for young talent
Related Articles
- Cybersecurity Insiders Plead Guilty to ALPHV Ransomware Attacks [2025]
- Cyera's $9B Valuation: How Data Security Became Tech's Hottest Market [2025]
- Internal Message Spoofing Phishing Campaign: How to Stop It [2025]
- Scattered Lapsus$ Hunters Caught in Honeypot: Inside the Bust [2025]
- Blue Screen of Death Malware: How ClickFix Attacks Work [2025]
- Covenant Health Breach Exposes 500K Patients: What Happened [2025]
![Why Cybercriminals Are Getting Younger: The Crisis of 2025 [2025]](https://tryrunable.com/blog/why-cybercriminals-are-getting-younger-the-crisis-of-2025-20/image-1-1767973092739.jpg)



