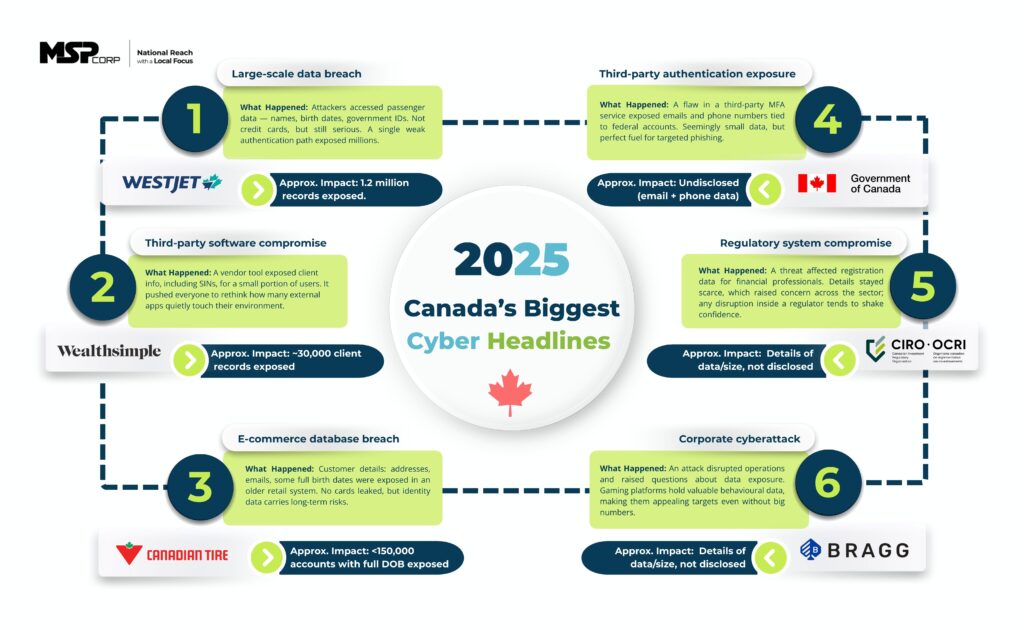
Canada Computers Data Breach 2025: Complete Guide to What Happened, Who's Affected, and How to Protect Yourself
A major Canadian retailer just got hacked. If you've bought anything online from Canada Computers in the last month, you need to pay attention.
On January 22, 2025, Canada Computers & Electronics discovered attackers inside their systems. The breach exposed customer data, including credit card information, from people who checked out as guests during the holiday shopping season. The company didn't immediately announce how many customers were impacted or provide specifics about the attack method, which naturally sparked concerns across the Canadian tech community.
This isn't some obscure incident. Canada Computers operates around 30 physical locations across Ontario, Quebec, and British Columbia, making it a significant player in Canadian consumer electronics retail. Thousands of people shop there every month, buying everything from gaming PCs to laptop components to home electronics. The breach window was narrow but critical: December 29, 2025 through January 22, 2025, the peak post-holiday period when online shopping volume spikes.
What makes this breach particularly interesting is its selective impact. Guest checkout customers got hit. Member account holders who logged in before purchasing? They're fine. In-store transactions? Untouched. This suggests a targeted vulnerability in a specific system rather than a complete infrastructure compromise.
Let's break down what actually happened, what data got exposed, who needs to worry, and what steps you should take right now if you're affected.
TL; DR
- Breach Timeline: Attackers accessed Canada Computers systems starting January 22, 2025, affecting guest checkout transactions between December 29, 2025 and January 22, 2025
- Data Exposed: Personal information and credit card details were stolen from guest checkout customers
- Who's Affected: Only customers who checked out as guests with payment information; member account holders and in-store purchases unaffected
- Free Protection: Canada Computers offering 2 years of free credit monitoring and identity theft protection to victims
- Action Required: Monitor your bank accounts, change passwords, and watch for fraudulent charges; consider a credit freeze if concerned
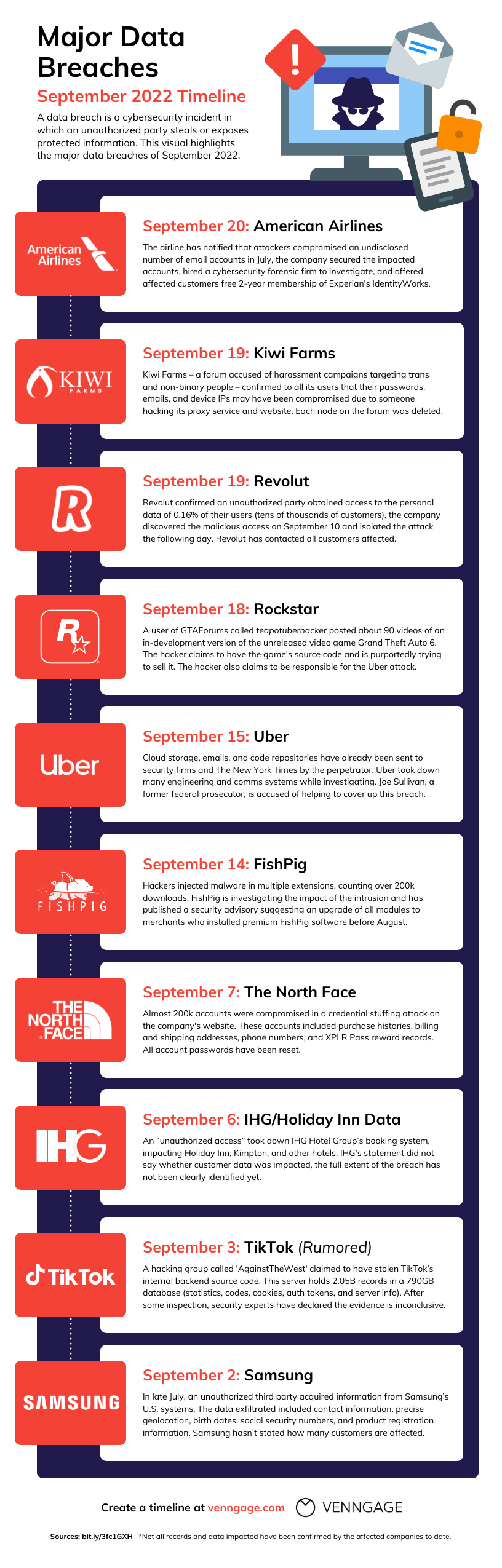
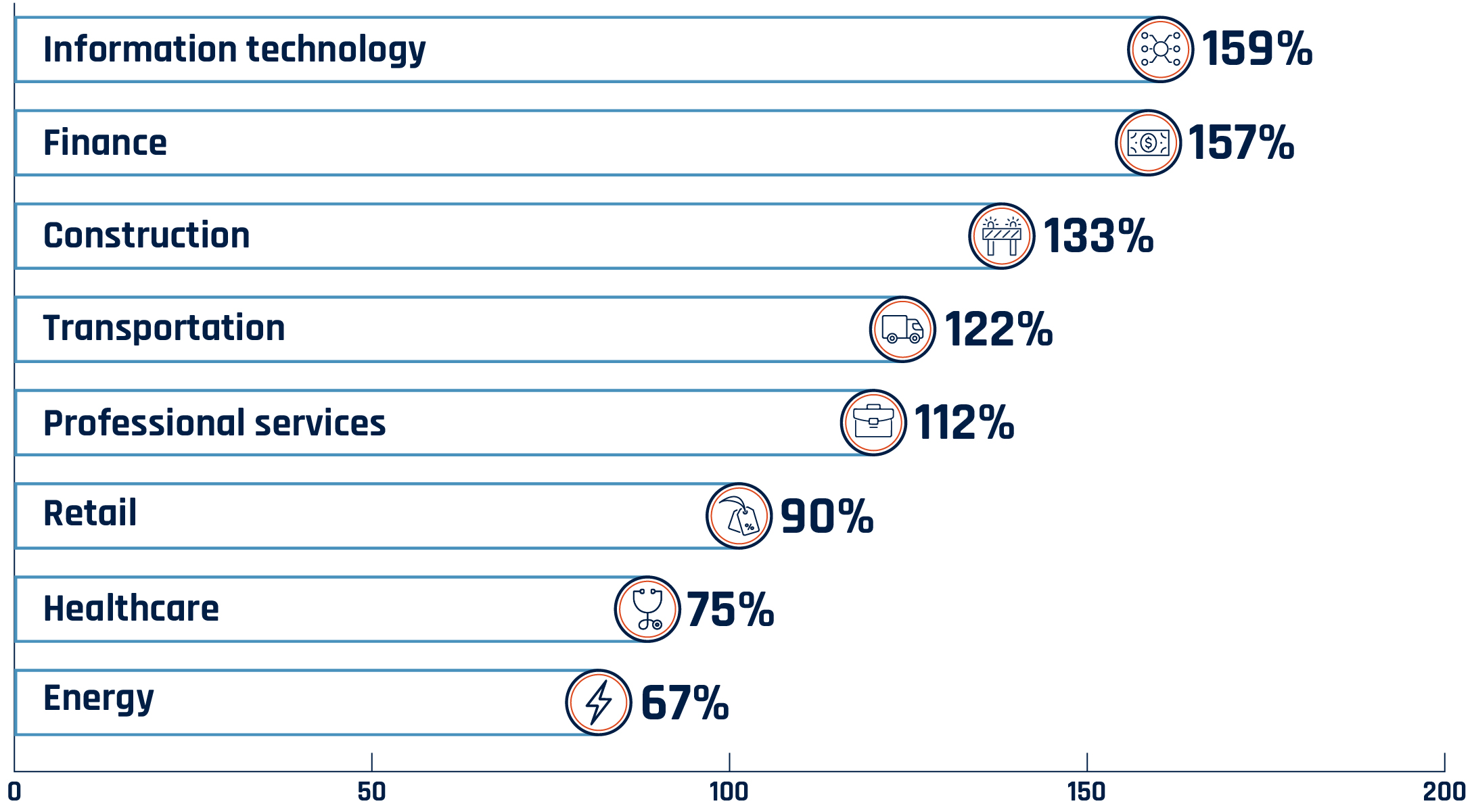
Hacking is estimated to account for 40% of data breaches, followed by misconfigured databases and employee negligence. (Estimated data)
What Exactly Happened: The Breach Timeline and Discovery
Let's establish the facts first. Canada Computers detected unauthorized access on January 22, 2025. Three days later, the company notified affected customers. The breach window itself was roughly a month: December 29, 2025 through the detection date.
This timeline matters because December 29 falls right after Christmas, when online shopping reaches absolute peak volume. People were buying last-minute gifts, New Year gaming setups, and replacement electronics. The attackers clearly timed this well, possibly knowing that holiday volume makes detection harder and gives them more cover in data logs.
The company's response was measured but not immediate. They discovered the breach, investigated internally, then contacted affected customers. By January 25, they had lawyers and forensic security firms involved. Law enforcement was already working with them. This is actually standard incident response protocol, though notification timing varies by province and situation.
Here's what's unclear: the actual attack vector. Canada Computers hasn't disclosed whether this was a vulnerability in their web checkout system, a phishing attack on employees, credential stuffing, or something else entirely. They've only confirmed the attackers "broke into a system that supports the retail website." That's vague. It could mean anything from a vulnerable API endpoint to weak database access controls.
The forensic investigation is ongoing, which is code for "we don't have all the answers yet." Independent security firms are still combing through the systems. This investigation matters because understanding how the breach happened determines what systemic changes Canada Computers needs to implement.
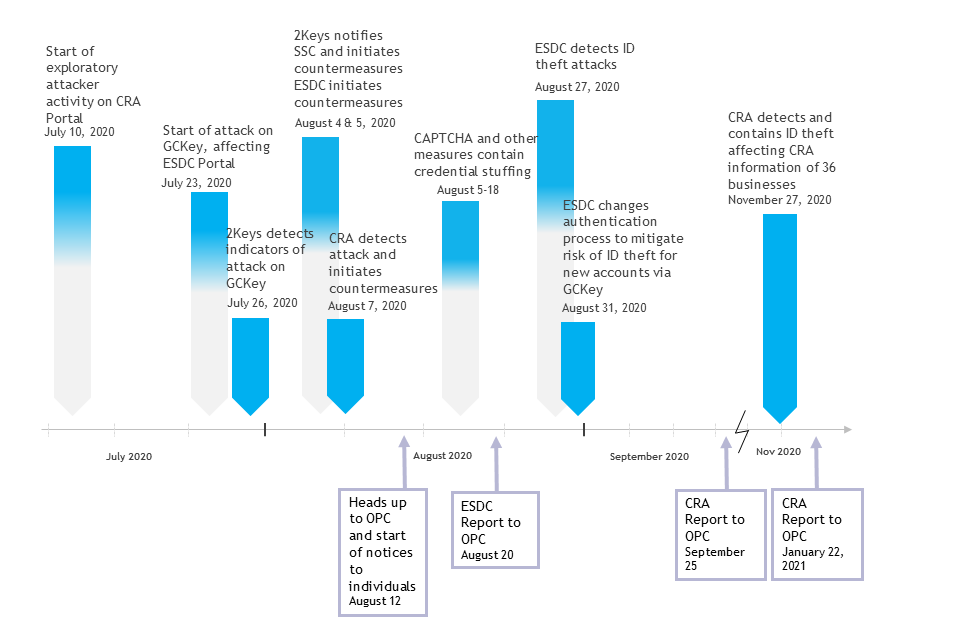
Canada Computers offers 24 months of credit monitoring, exceeding the typical 12-18 months provided by most companies after a data breach. Estimated data based on industry standards.
Scope and Scale: How Many Customers Are We Talking About?
Here's where it gets frustrating. Canada Computers hasn't revealed the exact number of affected customers. They've only confirmed that guest checkout customers who entered personal information during the window were impacted. That could be thousands or tens of thousands.
For context, Black Friday and Boxing Day (December 26) drive massive online traffic to Canadian retailers. Add in New Year's Week shopping, and you're looking at a significant customer volume. Without exact numbers, we can't assess the scale of this breach relative to other major Canadian incidents.
The selective impact is important to understand though. Guest checkout customers were hit. Registered account holders were not. This tells us the vulnerability was likely specific to the guest checkout flow, not the entire database infrastructure. If registered accounts were compromised, you'd expect the company to warn member account holders too, which they didn't.
In-store purchases using physical cards, whether credit or debit, weren't affected. This limits the damage profile significantly. The breach was digital and guest-specific.

What Data Was Actually Stolen
Let's be specific about what the attackers got. According to Canada Computers' official statement, the exposed data includes:
- Personal information (names, email addresses, likely phone numbers)
- Billing addresses
- Credit card information (this is the big one)
- Shipping addresses
They didn't explicitly say whether card security codes (CVV/CVC numbers) were stolen, though that's often included in guest checkout breaches. The presence of billing addresses and credit card numbers means attackers could potentially attempt fraud immediately.
What wasn't compromised: passwords for registered member accounts, encrypted payment tokens, or data from in-store purchases. This is actually fortunate. If password hashes were leaked, attackers could attempt to crack them. If registered account data was stolen, they could impersonate account holders.
The credit card data is the urgent problem. With full card numbers, expiration dates, and names, fraudsters can either:
- Make immediate online purchases with the cards
- Sell the card data on dark web marketplaces (typically $20-50 per card)
- Attempt card-not-present (CNP) fraud on other retail sites
- Clone the cards if they somehow obtained the CVV
Most financial institutions have fraud detection systems that flag unusual transactions, especially large or geographically distant purchases. But it takes time, and in the meantime, your credit limits might get maxed out.
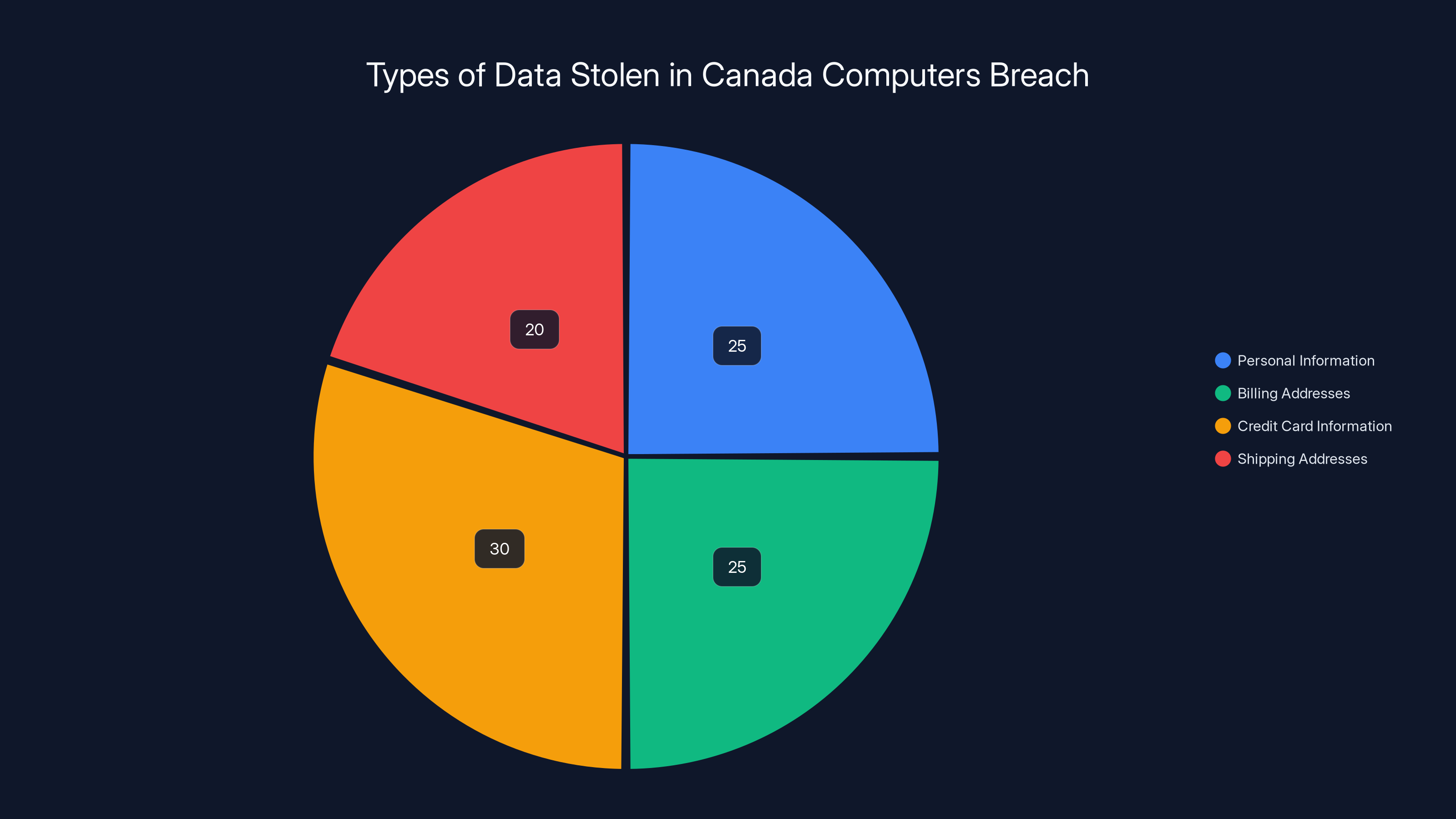
Credit card information is the most critical data stolen, posing immediate fraud risks. Estimated data distribution based on typical breach scenarios.
Impacted Customers: Who Needs to Take Action
Canada Computers defined the impact clearly: customers who checked out as guests and entered personal information. That's the operative term.
Registered member account holders? You're safe. Your account uses encrypted passwords and tokenized payment systems. The vulnerability wasn't in the member system.
In-store shoppers? Your in-person transactions aren't affected. If you paid with a physical card in-store, that transaction data wasn't compromised.
But here's the issue: if you made a guest checkout purchase between December 29, 2025 and January 22, 2025, your information is likely in the breach. Canada Computers should send notification directly to your email on file. If you don't receive communication within two weeks of the initial announcement, you might want to contact them directly to confirm.
Geographically, the breach could affect anyone with internet access, but Canada Computers' customer base is primarily Canadian. However, the company has shipped to international addresses before, so the impact might extend beyond Canada depending on their payment processing setup.
The Credit Card Exposure: Real Risk Assessment
Credit card breaches are common, but that doesn't make them harmless. Let's talk about the actual risk you face if your card was exposed.
Immediate risk (first 24-48 hours): Fraudsters attempting small test purchases to see if the card works. These are often $1-3 charges at gas stations or online retailers. If your card is active, these go through, confirming the card is valid. Your bank's fraud system might flag these.
Medium-term risk (days 1-14): Larger fraudulent purchases, potentially hitting your credit limit. If a fraudster maxes out your $5,000 limit, you'll discover it when your bank notifies you or when a legitimate transaction gets declined.
Longer-term risk (weeks to months): Your card data could be sold on dark web marketplaces. It might be used weeks later at retailers with looser verification systems. It might be used for subscription fraud (signing up for services, canceling after free trial).
Here's the mitigating factor: you're protected by chargeback laws in Canada. If fraudulent charges appear on your card, you can dispute them with your bank. Visa and Mastercard have zero-liability policies for fraudulent transactions. You'll likely get your money back, though it might take 30-45 days for the investigation.
But those 30-45 days of uncertainty? That's stressful. You might not be able to use that card. If it's your primary card, your purchasing power is reduced.
Credit card fraud is also used to validate cards for resale. A fraudster might make a small purchase to confirm your card works, then sell it on a dark web marketplace where it's bundled with thousands of others. The actual fraudulent use might come from a completely different person months later.

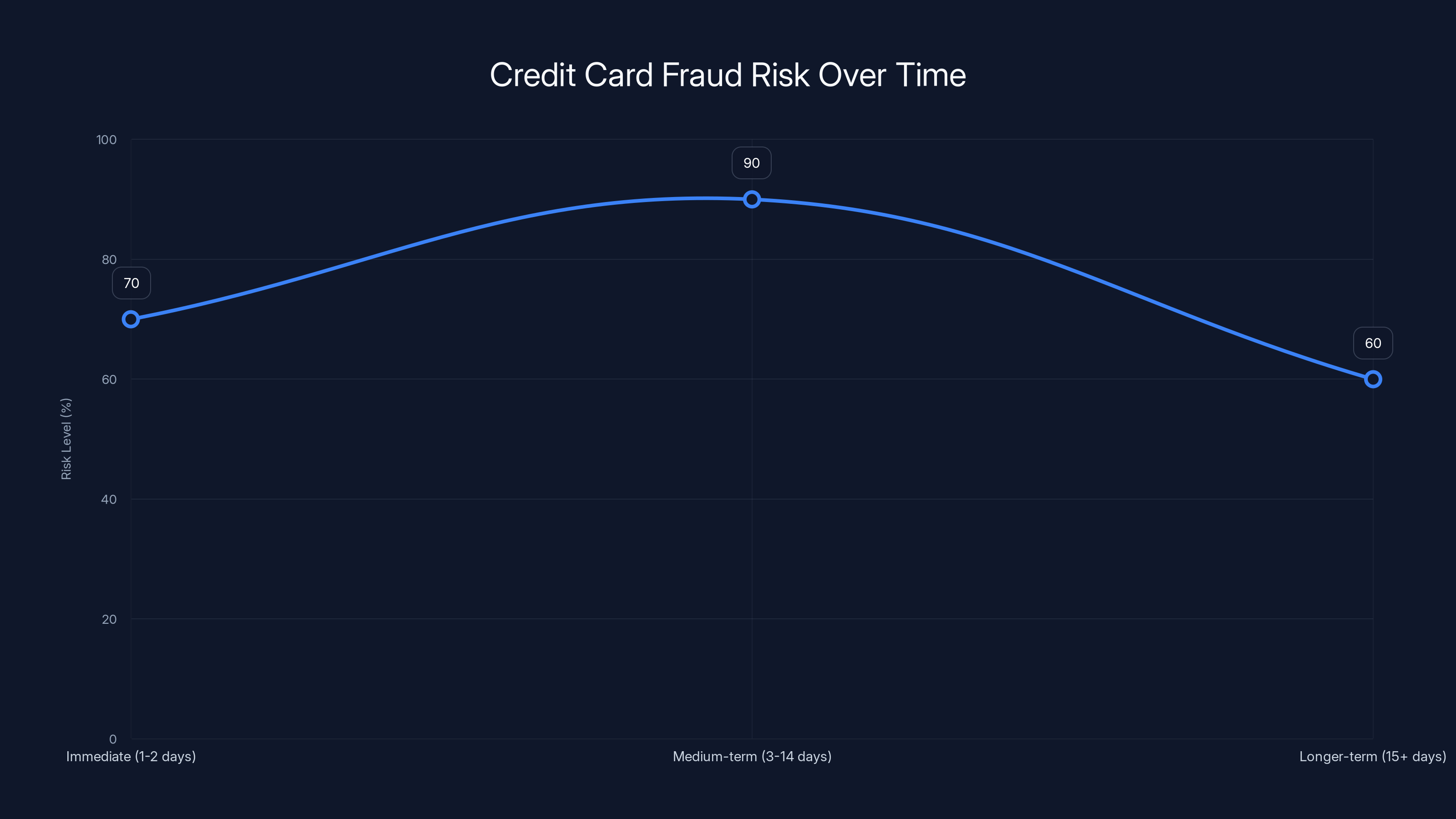
Estimated data shows that the risk of credit card fraud peaks in the medium-term (3-14 days) after exposure, with a significant risk still present in the immediate aftermath.
Credit Monitoring and Identity Theft Protection: What Canada Computers Is Offering
Canada Computers is offering two years of free credit monitoring and identity theft protection to affected customers. This is standard practice after breaches involving credit card data.
Here's what that typically includes:
Credit Monitoring: Regular checks on your credit report for unauthorized inquiries, new accounts, or changes. If someone tries to open a credit card, personal loan, or mortgage in your name, the monitoring service alerts you.
Identity Theft Protection: Monitoring for unauthorized use of your personal information. Some services include identity restoration support, meaning they help you recover if you actually become a victim.
Fraud Alerts: Automatic placement of fraud alerts on your credit file, making it harder for fraudsters to open new accounts in your name.
Two years is substantial. Most data breaches offer 12-18 months. The fact that Canada Computers is going with two years suggests they're taking this seriously.
The details are being mailed to victims directly, not just posted online. This is appropriate because it means each affected customer gets personalized information with their specific monitoring account credentials.
Take advantage of this offer immediately. Sign up for the monitoring as soon as you receive your notification. These services have enrollment deadlines, typically 30-60 days after the breach notification.

Steps to Take If You Were a Guest Checkout Customer
If you made a purchase from Canada Computers' website as a guest between December 29 and January 22, here's what you should do immediately.
Step 1: Check Your Bank Statements
Log into your bank's website or app right now. Check the last 30 days of transactions. Look for:
- Unauthorized charges (obviously)
- Small test charges under $10
- Charges from unfamiliar merchants or geographies
- Multiple small charges in rapid succession
If you spot anything suspicious, contact your bank immediately. Don't wait for your statement to arrive by mail. Fraud detection teams work faster when you report it proactively.
Step 2: Contact Your Credit Card Company Proactively
Call the number on the back of your card. Tell them your card information was compromised in a data breach. Ask them to:
- Flag your account for enhanced monitoring
- Consider issuing a replacement card with a new number
- Place a fraud alert on your account
Most credit card companies will issue a replacement card for free within 5-7 business days. Yes, it's an inconvenience, but it reduces your risk significantly. Any fraudster with your old card number can't use the new one.
Step 3: Monitor Your Credit Report
You're entitled to a free credit report from Canada's credit reporting agencies: Equifax and Trans Union. Get them. Check for:
- Unauthorized accounts or inquiries
- Hard inquiries you didn't authorize
- Changes to your credit limit
- New addresses
You can request free reports at equifax.ca or transunion.ca. This is different from credit monitoring services. You're just checking the report itself.
Step 4: Set Up a Credit Freeze (Optional But Recommended)
A credit freeze prevents creditors from accessing your credit report without your explicit permission. This blocks fraudsters from opening accounts in your name because lenders can't pull your credit report.
It's not complete protection (doesn't prevent fraud on existing accounts), but it prevents one major category of identity theft.
Canadian credit freezes are administered by Equifax and Trans Union. It costs $12-15 per agency to set up but takes 10 minutes online. Some provinces offer free freezes. It's worth the investment given that you're already in a breach.
Step 5: Enroll in the Credit Monitoring Program
When Canada Computers sends you the notification with enrollment details, sign up immediately. Don't procrastinate. Set a calendar reminder to activate your account.
The monitoring service will watch your credit file for suspicious activity and alert you. This gives you early warning if someone tries to open accounts using your information.
Step 6: Change Passwords on Related Accounts
If you use the same password on multiple sites (you shouldn't, but many people do), change them. Start with your email account. Your email is the master key to your digital identity. If compromised, someone can reset passwords on banking sites, payment apps, and social media.
Create a unique, strong password for each account. Use a password manager to store them securely.
Step 7: Watch for Phishing and Social Engineering
After breaches, fraudsters sometimes use stolen information to craft convincing phishing emails or calls. Someone might call claiming to be from Canada Computers or your bank, asking you to "verify" information or click a link.
Rules:
- Legitimate companies never ask for passwords via email or phone
- Never click links in unsolicited emails
- Always call companies back using numbers on their official website or your statement
- Verify email addresses carefully (scammers use lookalike addresses)
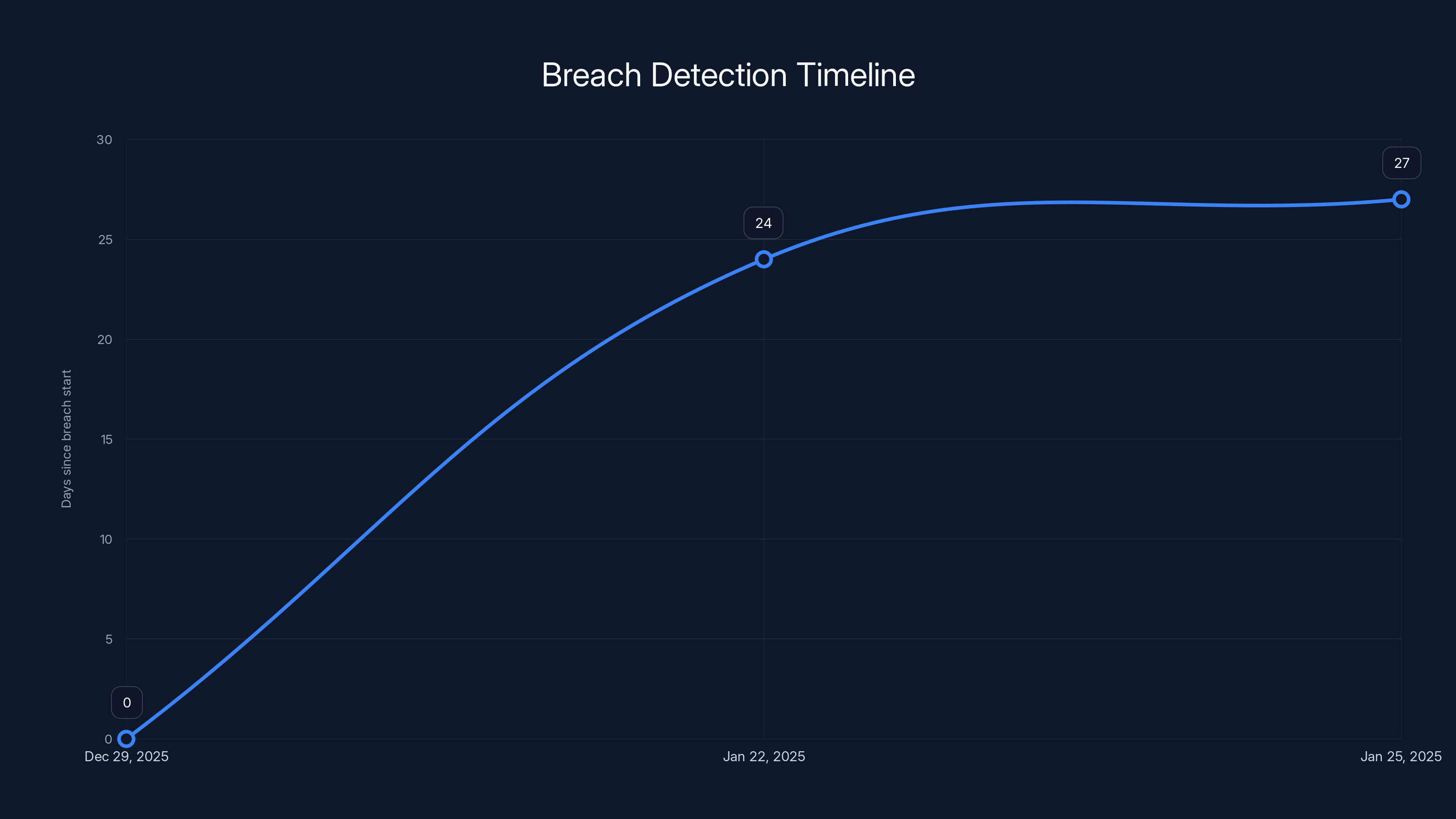
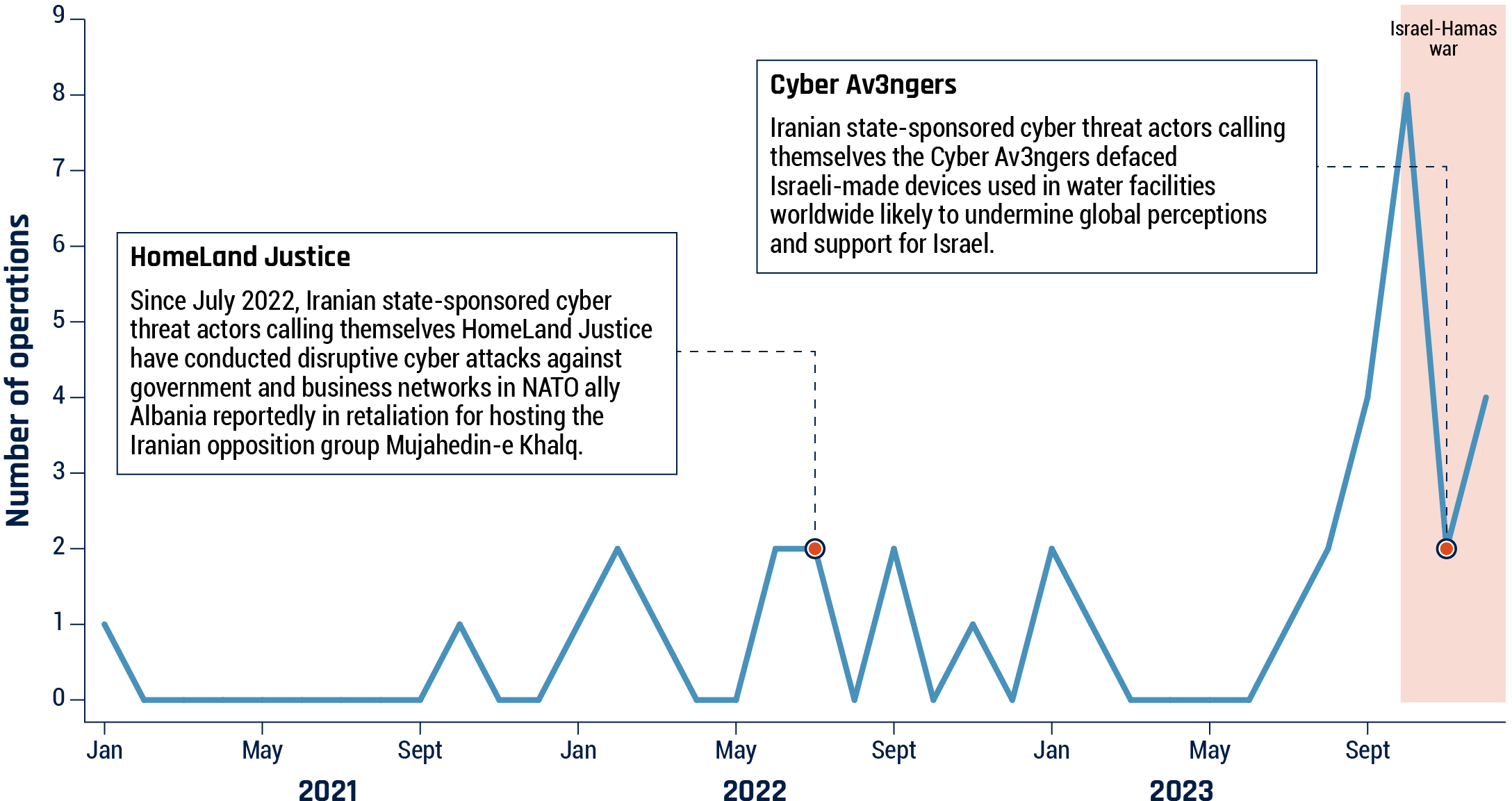
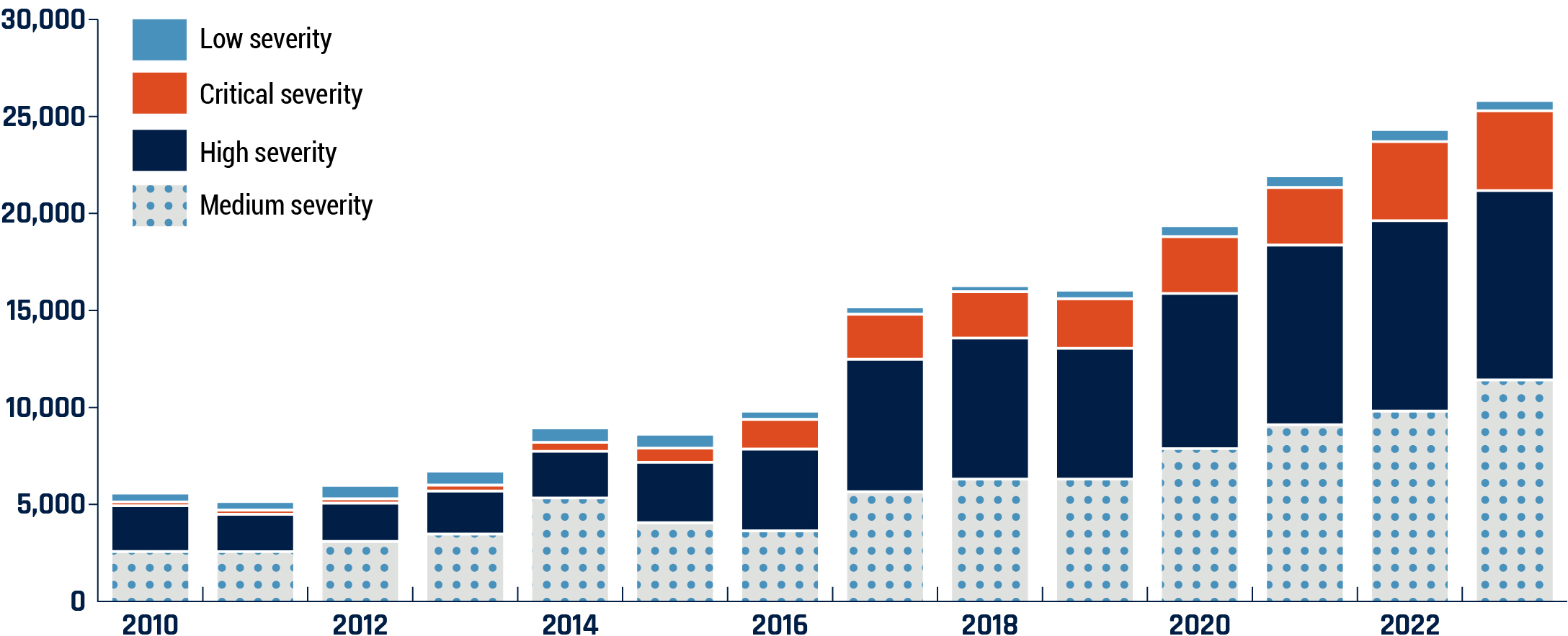
Canada Computers detected the breach in 24 days, significantly faster than the industry average of 207 days (Estimated data).
Understanding Data Breaches: Why Canada Computers' Response Matters
Canada Computers handled this breach reasonably well, but there are important questions unanswered.
First, they detected the breach relatively quickly. Many companies take months or longer to realize they've been compromised. Quick detection limits the damage window.
Second, they're offering appropriate compensation (free credit monitoring for two years). This is industry-standard for credit card breaches.
Third, they're conducting a proper investigation with independent forensic firms and law enforcement involvement.
But here's what's missing: transparency about the actual vulnerability. How did attackers get in? Was it a known vulnerability in their web framework? Poor database access controls? An employee's compromised credentials?
Without understanding the root cause, you can't assess whether Canada Computers will actually prevent this from happening again.
The company states the investigation is ongoing, so details might emerge later. But customers deserve to know whether this was a preventable mistake or an extremely sophisticated attack they couldn't have stopped.
Similar Breaches and Industry Context
Canada Computers isn't the first Canadian retailer to suffer a breach, and won't be the last.
Recent major Canadian breaches include Freedom Mobile's hack affecting 4.7 million customers, and various incidents at major financial institutions. The pattern is consistent: attackers target payment systems, guest checkout flows, and employee credentials.
Retailer websites are particularly attractive because they process thousands of payment transactions daily. One vulnerability in the payment flow means exposure to potentially millions of transaction records.
The fact that Canada Computers' guest checkout was compromised but member accounts weren't suggests that registered account systems with tokenized payments are more secure than guest checkout systems. This is a common pattern. Guest flows often have lighter security controls because they're optimized for speed and convenience, not maximum security.
What Changes We'd Expect to See
After this breach, reasonable security improvements would include:
Payment Processing Upgrades: Moving to point-to-point encryption or tokenization for all payment data. Tokens replace actual card numbers in the system, so even if a system is breached, the data is useless.
Web Application Firewall: Implementing WAF rules to block common attacks like SQL injection, cross-site scripting, and credential stuffing attempts.
Improved Access Controls: Limiting employee access to sensitive systems. Implementing multi-factor authentication for all admin accounts.
Regular Security Audits: Quarterly penetration testing and vulnerability scanning to find issues before attackers do.
Incident Response Plan: A documented procedure for detecting, investigating, and responding to breaches. This should include notification timelines, forensic investigation procedures, and communication protocols.
Whether Canada Computers actually implements these depends on their post-breach budget allocation and executive commitment to security.
Broader Lessons: What This Breach Reveals About E-Commerce Security
The Canada Computers breach is a snapshot of a broader problem in retail e-commerce: balancing security with user experience.
Guest checkout systems exist because forcing registration creates friction. Some customers abandon carts rather than create accounts. So retailers offer guest checkout as a conversion optimization feature.
But guest checkouts often cut corners on security because they're built for speed. Minimal verification, simplified payment processing, reduced monitoring.
This is inherently risky when processing payment data. The Canada Computers breach is partially a cautionary tale about this trade-off.
Smarter companies implement guest checkout that's fast AND secure:
- Immediate payment tokenization (no storage of actual card numbers)
- Real-time fraud detection with behavioral analysis
- 3D Secure verification for higher-risk transactions
- Immediate password prompts post-purchase (converting guests to accounts)
These aren't expensive or slow. They're about making security decisions explicit rather than treating it as an afterthought.
How to Protect Yourself Going Forward
Beyond the immediate steps, here are strategies to reduce your risk in future breaches (because there will be more).
Use Virtual Card Numbers
Some financial institutions offer virtual card numbers for online shopping. You get a unique card number that's linked to your real account but has limits (amount, merchant category, expiration date). If the merchant is breached, fraudsters get a useless virtual number, not your real card.
Shop with Payment Services
PayPal, Apple Pay, Google Pay, and similar services don't share your actual card number with merchants. They tokenize the payment. If the merchant is breached, your card number was never at risk.
Monitor Your Accounts Actively
Don't wait for your bank to notify you of fraud. Check accounts weekly. Most banks offer alerts for large purchases, but you need to set thresholds. Lower them to $100 or less for maximum visibility.
Use Strong, Unique Passwords
Password reuse is epidemic. If Canada Computers' systems stored passwords poorly and a hacker got them, they'd immediately try those credentials on banking sites, email, PayPal, etc. A unique password for each site limits this damage.
Consider Business Credit Monitoring
If you're self-employed and use your personal information for business accounts, fraudsters could open business accounts in your name. Business credit monitoring is less common but worth considering if you have business accounts.
Ask Retailers About Their Security
Before shopping, you can check a website's SSL certificate (green lock icon), but that's table stakes. What you really want to know:
- Do they tokenize payments?
- Do they use PCI-compliant payment processors?
- Do they conduct regular penetration testing?
- What's their incident response plan?
Most retailers won't have detailed answers, but asking signals that security matters to customers.
The Legal and Regulatory Side
Canada has privacy laws governing data breaches. Most provinces require notification "without unreasonable delay" when breaches involve personal information.
Canada Computers appears to be complying. They notified affected customers and relevant authorities. The company could face regulatory investigation, but compliance with notification requirements is the baseline.
Private liability is possible if affected customers pursue class action lawsuits. Some lawsuits succeed in securing settlement funds for affected users. Others fail. It depends on evidence of negligence and the damages users can prove.
From a regulatory standpoint, expect the provincial privacy commissioner and the federal Office of the Privacy Commissioner to investigate. The investigation might reveal systemic security failures that trigger enforcement action or compliance orders.
Timeline of Events: Quick Reference
December 29, 2025: Guest checkout vulnerability window opens
January 22, 2025: Canada Computers detects breach; investigators begin work
January 25, 2025: Company notifies affected customers; press release issued
January 26+: Investigation ongoing; forensic firms and law enforcement involved
Future: Notification letters mailed with credit monitoring enrollment details; investigation results may be released

FAQ
What is a data breach and how is it different from a hack?
A data breach occurs when unauthorized parties access sensitive information. A hack is the method used to create the breach. Not all breaches are from hacks—some result from misconfigured databases left publicly accessible or employee negligence. Canada Computers experienced a breach caused by a hack (unauthorized access to a system).
How did attackers get into Canada Computers' systems?
Canada Computers hasn't disclosed the specific attack vector. The company only confirmed that attackers broke into a system supporting their retail website. The actual method could be a web application vulnerability, phishing attack targeting employees, credential stuffing, or supply chain compromise. The forensic investigation is ongoing, so details may emerge later.
If I checked out as a guest but my card wasn't declined, does that mean my data wasn't stolen?
Not necessarily. Canada Computers' statement says the breach affected customers who checked out as guests and entered personal information. If you completed a guest checkout during the window and received an order confirmation, assume your information may be compromised. The breach's existence isn't determined by whether your card worked—it's determined by whether attackers accessed the system during that timeframe.
What should I do if I find fraudulent charges on my card?
Contact your bank immediately. Report the fraudulent charges and request a chargeback. In Canada, you're protected by zero-liability policies from Visa and Mastercard. You shouldn't be responsible for fraudulent charges, though the investigation can take 30-45 days. Request a replacement card with a new number while the investigation proceeds.
Is the credit monitoring Canada Computers offering actually useful?
Yes, for two years. Credit monitoring watches your credit report for unauthorized inquiries or accounts opened in your name. If someone tries to fraudulently open a credit card or take out a loan using your information, the monitoring service alerts you. This early warning allows you to contact credit bureaus and freeze your credit before significant damage occurs. The two-year duration is substantial and gives meaningful protection during the highest-risk period after the breach.
Can I get a credit freeze if I'm not an affected customer?
Yes. Credit freezes are available to anyone and are free in some provinces. If you're concerned about your information being compromised (from any source), a freeze is a powerful protection that prevents fraudsters from opening new accounts in your name. It takes about 10 minutes to set up through Equifax or Trans Union.
What's the difference between a credit freeze and credit monitoring?
A credit freeze prevents creditors from accessing your credit report without your express permission. This blocks fraudsters from opening new accounts in your name. Credit monitoring watches your credit report for unauthorized activity and alerts you if something suspicious happens. They're complementary. A freeze is more protective but requires manual unfreezing when you apply for credit. Monitoring is passive but catches fraud quickly.
How long do I need to monitor my credit after a breach like this?
Canada Computers is offering two years of monitoring. That's a reasonable timeframe because fraudsters often sell stolen data in batches, and it can take weeks or months for your information to be used. Two years covers the highest-risk period. After that, monitor your accounts yourself through annual credit report checks and regular bank statement reviews.
Could this breach affect my in-store purchases from Canada Computers?
No. Canada Computers explicitly stated that in-store purchases were not affected. Only guest checkout customers during the specific window (December 29 - January 22, 2025) are at risk. If you shopped in-store or used a registered member account, your data wasn't compromised in this breach.
What are the chances my card will be used fraudulently?
Statistically, the probability varies. Not every stolen card number is used fraudulently. Some are sold in bulk on dark markets but never used. Others are used weeks or months later when the data is old. Your bank's fraud detection systems actively monitor for unauthorized activity. Most fraudulent charges are caught and blocked within minutes. The real risk isn't complete card takeover—it's unauthorized charges that require dispute resolution. That's frustrating but recoverable.
Should I close my bank account after a breach like this?
Not necessarily. Closing accounts doesn't erase the fraudster's access to your information. A better strategy is to keep the account active so you monitor it, request a replacement card with a new number, and watch for fraudulent activity. The account number itself is less valuable to fraudsters than the card number and name. If you do close an account, open a new one (possibly at a different bank) to maintain banking access while the compromised account is investigated.

Conclusion: Moving Forward After the Canada Computers Breach
Data breaches are increasingly common in retail, and Canada Computers' incident is a stark reminder that even established retailers can be compromised. The good news: if you were affected, you have clear steps to take and protections available.
Canada Computers handled the response reasonably well by quickly detecting the breach, notifying customers promptly, and offering two years of credit monitoring. That doesn't erase the security failure, but it demonstrates appropriate post-breach responsibility.
If you made a guest checkout purchase during the breach window, treat this seriously. Check your bank statements, monitor your credit, and enroll in the free credit monitoring when notification arrives. These steps take a few hours total but provide meaningful protection.
Looking forward, this breach illustrates why payment tokenization, multi-factor authentication, and regular security audits are non-negotiable for online retailers. Companies processing payment data need to invest in security as a core business function, not an afterthought.
For consumers, the lesson is clear: use guest checkout when absolutely necessary, but when possible, create registered accounts with strong, unique passwords. Consider virtual card numbers or payment services like PayPal that tokenize your actual payment data. Monitor your accounts actively rather than waiting for banks to detect fraud.
Breach notifications are becoming routine. Your response shouldn't be panic—it should be methodical protection of your financial and personal information. Canada Computers has given you the tools. Now use them.
Stay vigilant, and don't hesitate to contact your bank at the first sign of suspicious activity. That proactive step often prevents fraud from escalating beyond a few fraudulent charges.

Key Takeaways
- Canada Computers detected a breach on January 22, 2025, affecting guest checkout customers from December 29 - January 22, 2025, with payment card data exposed
- Guest checkout customers were impacted, but registered member accounts and in-store purchases were completely unaffected by the breach
- Canada Computers is offering two years of free credit monitoring and identity theft protection to affected customers, detected faster than industry average
- Immediate actions include checking bank statements, contacting your credit card issuer, monitoring credit reports, and potentially implementing a credit freeze
- Credit card fraud risk increases over time from test charges to larger fraud to dark web resale; proactive monitoring and unique passwords reduce future breach impact
Related Articles
- TriZetto Provider Solutions Breach: 700K+ Affected [2025]
- Major Cybersecurity Threats & Digital Crime This Week [2025]
- Bumble & Match Cyberattack: What Happened & How to Protect Your Data [2025]
- Device Protection Beyond Hardware: Securing Your Digital Identity [2025]
- Qilin Ransomware Gang Hits Tulsa Airport: What You Need to Know [2025]
- IPVanish Threat Protection Pro: Malware Defense Guide & Alternatives 2025
![Canada Computers Data Breach 2025: Timeline, Impact, Protection [2025]](https://tryrunable.com/blog/canada-computers-data-breach-2025-timeline-impact-protection/image-1-1770053769500.jpg)



