The Volvo Conduent Data Breach: What Happened and Why It Matters
In January 2025, Conduent discovered something every company dreads: hackers had been quietly sitting inside their network for roughly two and a half months, stealing sensitive data. By the time the intrusion was detected, the damage was already done. Tens of millions of people across North America found themselves in the blast radius of what security researchers now consider one of the largest breaches of its kind according to The Register.
Volvo Group North America—one of Conduent's major clients—notified roughly 17,000 of its employees, customers, and staff members that their personal information had been compromised. Names, Social Security numbers, medical records, and health insurance details were all part of what the attackers exfiltrated as reported by Bleeping Computer. But here's the thing: this breach didn't happen in a vacuum. Conduent processes data for hundreds of government agencies, transportation organizations, and major corporations. The actual scope of this incident reaches far beyond Volvo as noted by TechCrunch.
In Texas alone, over 15.4 million people were affected—roughly half the state's entire population. In Oregon, more than 10 million residents had their data compromised. Hundreds of thousands more in Delaware, Massachusetts, New Hampshire, and other states received notification letters. A ransomware group calling itself Safe Pay claimed responsibility, stating they'd stolen 8.5 terabytes of sensitive information according to the New York Post.
What makes this breach particularly alarming isn't just the sheer volume of data stolen. It's the sensitivity of what was taken. Medical records combined with Social Security numbers create a perfect storm for identity theft and fraud. And because Conduent works across healthcare, transportation, and government sectors, the fallout continues to ripple outward months after the initial discovery as detailed by HIPAA Journal.
This article digs into everything you need to know about the Volvo-Conduent breach: what actually happened, who's affected, what data was stolen, and most importantly, what you should do to protect yourself right now.
TL; DR
- 17,000 Volvo employees and customers had their personal data exposed in the Conduent breach affecting tens of millions nationwide as reported by The Register.
- Stolen data includes names, Social Security numbers, medical records, and health insurance information making victims vulnerable to identity theft and fraud according to HIPAA Journal.
- Safe Pay ransomware group claimed responsibility and exfiltrated 8.5 TB of sensitive information from Conduent's network as noted by the New York Post.
- Hackers had network access for 2.5 months before being detected, giving them extensive time to steal data as detailed by HIPAA Journal.
- Texas affected most severely with 15.4 million victims, followed by Oregon with 10+ million affected according to the New York Post.
- Free monitoring services offered by Conduent, but victims should remain vigilant for years as advised by HIPAA Journal.

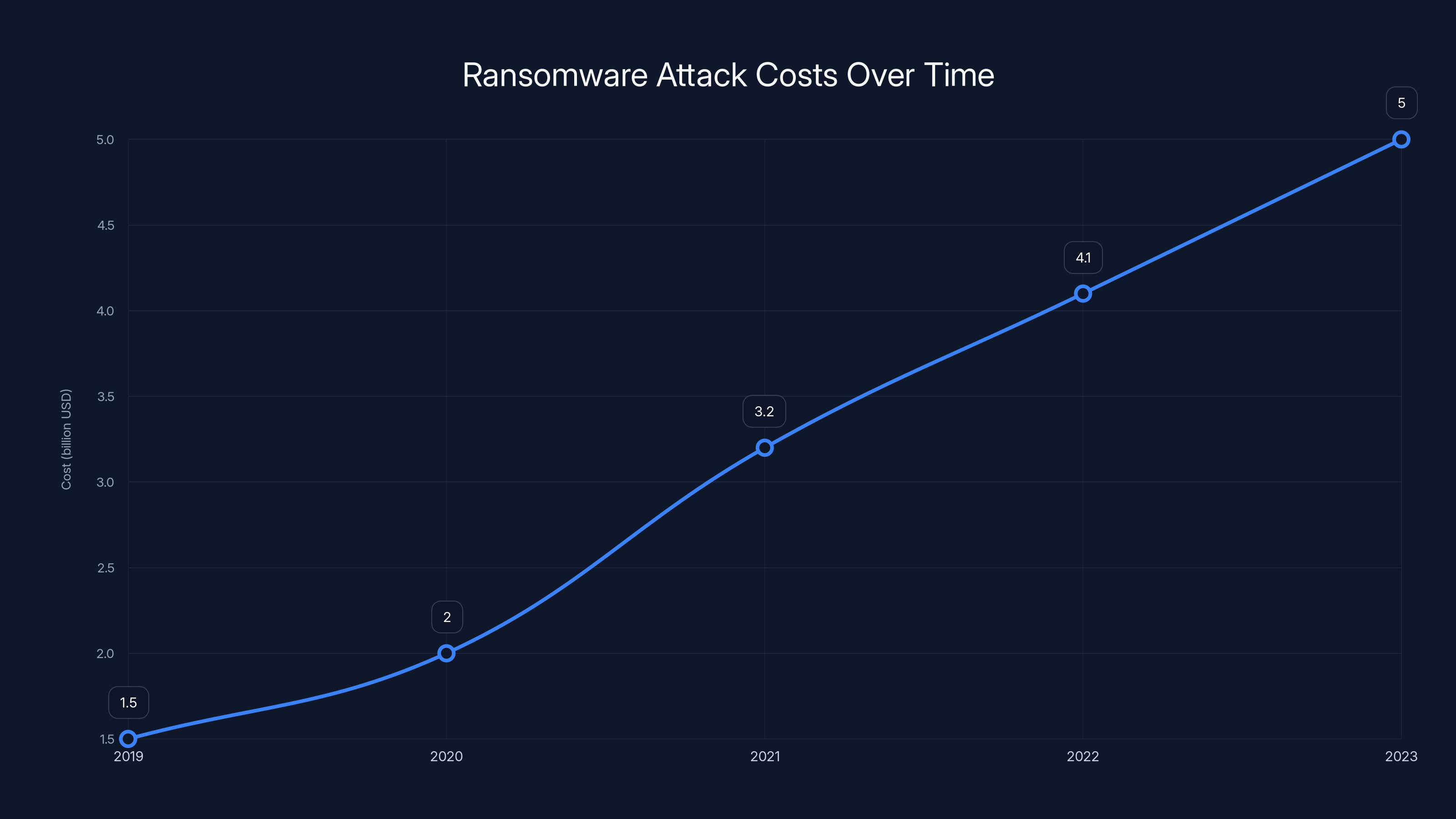
Ransomware attacks have increased in cost from
Understanding Conduent: Why This Company's Breach Matters So Much
Most people have never heard of Conduent. That's by design. The company operates behind the scenes, processing sensitive transactions and managing critical data for some of the most important institutions in America. Understanding what Conduent does is crucial to understanding why this breach is so serious.
Conduent Incorporated is an American business process outsourcing company that provides transaction processing, automation, and analytics services across healthcare, transportation, government, and other sectors. Think of them as the invisible infrastructure holding up critical services you depend on every day as noted by Business Wire.
Their client roster reads like a who's who of important institutions. The US Secret Service uses Conduent's services. District of Columbia Medicaid relies on their systems. State transportation departments, healthcare providers, and government agencies across the country depend on Conduent to process everything from benefit payments to licensing applications to medical claims according to HIPAA Journal.
In total, Conduent serves hundreds of government and transportation organizations. They process millions of transactions annually, touching the lives of tens of millions of Americans without most people even knowing the company exists as reported by The Register.
This is precisely why the breach is so devastating. Conduent doesn't just handle data for one company or one industry. They're a central hub connecting multiple critical sectors. When hackers breach a company like this, they gain access to data flowing through multiple channels simultaneously. A single security failure at Conduent cascades across healthcare systems, government agencies, and private companies like Volvo as noted by TechCrunch.
How Conduent Became a Target
Large business process outsourcing companies like Conduent are attractive targets for ransomware groups. Here's why: they're valuable precisely because of their position in the supply chain. Breach Conduent, and you've compromised dozens of other organizations simultaneously. The leverage for ransom demands is enormous according to HIPAA Journal.
These companies also manage massive volumes of data, which means they're either incredibly well-defended or—as this case demonstrates—potentially vulnerable if security investments lag behind their growth. Conduent is a publicly traded company with revenues in the billions, but that doesn't automatically translate to best-in-class cybersecurity across all systems as reported by The Register.
The Discovery Timeline
Conduent discovered the breach in January 2025. But here's the critical detail: the hackers had already been inside the network for approximately 2.5 months by that point. That means the actual intrusion likely began around October or November 2024. The attackers had roughly 75 days to explore the network, identify valuable data, and exfiltrate it before anyone noticed according to the New York Post.
In cybersecurity, this is called "dwell time," and it's one of the most important metrics for understanding breach severity. The longer attackers stay in a network undetected, the more damage they can do. A 2.5-month dwell time is substantial. It suggests the attackers had time to locate the most sensitive information and extract it systematically as detailed by HIPAA Journal.

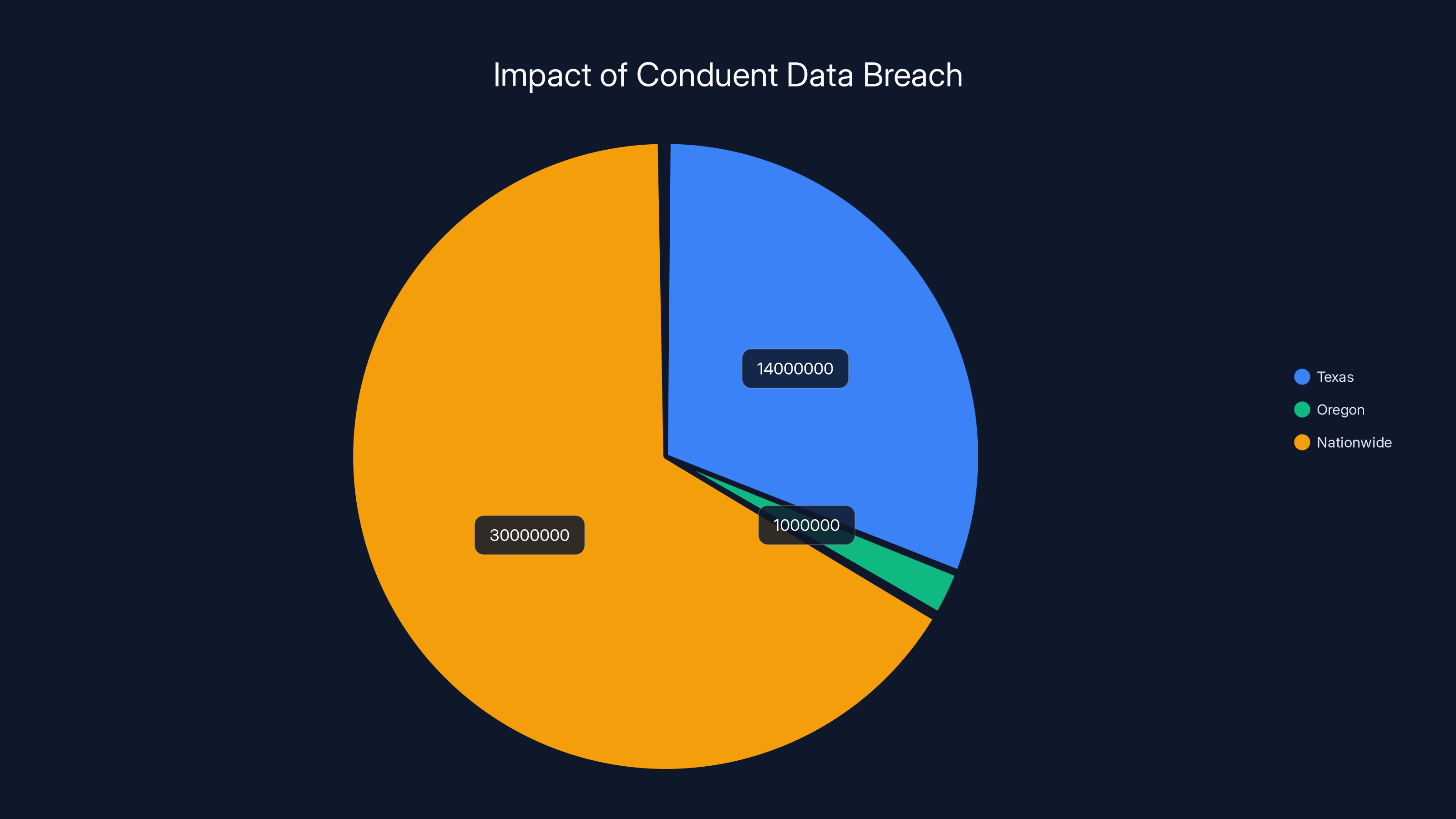
Estimated data shows that the Conduent breach affected approximately 14 million in Texas, 1 million in Oregon, and 30 million nationwide, highlighting the extensive impact of the breach.
What Data Was Stolen: The Specifics
Conduent's breach notification letter to Volvo and its affected individuals was surprisingly vague. The company stated that names were definitely compromised. But earlier security reports painted a much clearer picture of what was actually stolen according to HIPAA Journal.
Based on available security research and reports, the data exfiltrated from Conduent's systems included:
Personal Identifiers:
- Full names
- Social Security numbers
- Date of birth
- Driver's license numbers and state identification numbers
- Passport information (in some cases)
Medical and Health Information:
- Medical diagnosis codes
- Healthcare provider information
- Medical history details
- Prescription information
- Health insurance plan details and policy numbers
- Insurance company names and member IDs
Financial and Employment Data:
- Employment history
- Employer information
- Salary details (in some cases)
- Banking information (limited scope)
Why This Combination Is Dangerous
If hackers steal just your name and email, that's unfortunate but manageable. If they get just your Social Security number without additional context, identity thieves face barriers. But when you combine multiple data points—name plus SSN plus medical history plus health insurance details—you've created a blueprint for comprehensive identity theft as noted by HIPAA Journal.
A criminal with this complete profile can:
Open fraudulent credit accounts in your name with sufficient identity information to pass verification checks. They'll max out the cards and leave you holding the debt.
File fake insurance claims using your health insurance details, causing your policy to show fraudulent treatments and potentially causing your actual claims to be denied.
Access healthcare services under your identity, creating medical records under your name for conditions you never had, which could affect your insurance rates and medical treatment.
Apply for government benefits using your Social Security number and personal information, creating legal complications that take years to unravel.
Target you for advanced phishing and social engineering attacks that use personal details to seem credible and gain your trust.
Scale of the Data Loss
Safe Pay claimed they exfiltrated 8.5 terabytes of data from Conduent's systems. To put that in perspective: 8.5 TB equals roughly 2.1 million four-page documents. That's an enormous volume of information according to the New York Post.
Conduent claimed there was no evidence the data was being abused in the wild at the time of notification, but that statement came with an implicit caveat: just because abuse hasn't been detected yet doesn't mean it won't happen. The data is out there. What criminals do with it in the coming months and years remains to be seen as detailed by HIPAA Journal.
The Geographic Impact: Who's Actually Affected
While Volvo reported 17,000 affected individuals, the actual scope of the Conduent breach is orders of magnitude larger. The geographic distribution reveals just how far this breach's reach extends as reported by The Register.
Texas: The Hardest Hit State
Texas reported approximately 15.4 million affected individuals. To contextualize this: Texas's current population is roughly 30 million. This breach affected about half of Texas's entire population. Think about that. One in two Texans has data exposed in this breach according to the New York Post.
Why so many people in Texas specifically? Conduent handles significant portions of Texas's Medicaid administration, transportation services, and government benefit processing. When you breach Conduent's Texas systems, you hit multiple state agencies simultaneously as detailed by HIPAA Journal.
Oregon and the Pacific Northwest
Oregon reported more than 10 million affected individuals in the state. That represents roughly one-quarter of Oregon's entire population. Other Pacific Northwest states also saw significant impact from the breach as reported by The Register.
Oregon's Attorney General's office was actively notifying residents and providing resources, suggesting this state's systems were among those compromised according to HIPAA Journal.
Multistate Notification Wave
Conduent reached out to "hundreds of thousands" of people in Delaware, Massachusetts, New Hampshire, and additional states. The breach notification process was staggered, with different states learning about impacts on different timelines as reported by The Register.
This staggered notification actually created secondary problems. Victims in the last states to be notified had no warning or time to begin monitoring their accounts while the earliest notifications had already alerted consumers to watch for fraud as detailed by HIPAA Journal.
Why Geographic Variation Matters
Different states have different regulatory requirements for breach notification. States like Massachusetts and California have stringent data protection laws requiring notification within specific timeframes. Other states have looser requirements, which is why Conduent's notification process took time to roll out nationwide according to HIPAA Journal.
The International Dimension
Volvo is an international company. While the Volvo Group North America subsidiary was directly affected, Volvo's global operations suggest that similar Volvo entities in Europe and other regions might also have been impacted. Conduent's systems serve international clients, and the breach might extend beyond the North American footprint initially reported as reported by The Register.

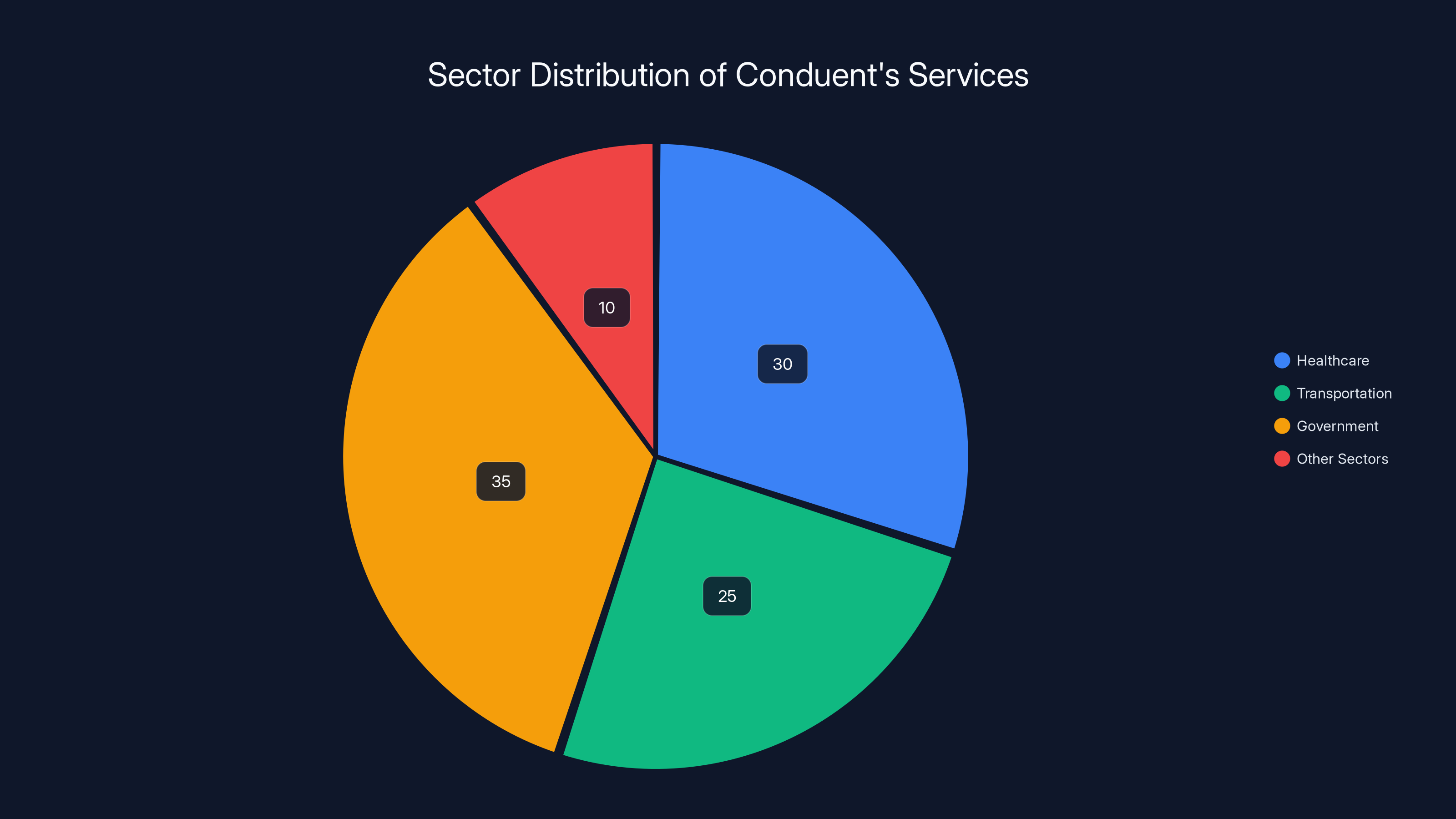
Conduent's services are heavily involved in government and healthcare sectors, making breaches potentially impactful across multiple critical areas. Estimated data.
Safe Pay Ransomware: The Actors Behind the Breach
Safe Pay is a relatively newer player in the ransomware ecosystem, but don't let that fool you into thinking they're unsophisticated. The group demonstrated significant capability in executing this attack against a Fortune 500-adjacent target as noted by HIPAA Journal.
Who Is Safe Pay?
Safe Pay emerged in 2024 as an aggressive ransomware operation. Unlike the most prominent ransomware groups like Lock Bit or Ransom Hub, which have years of operational history, Safe Pay is newer and still building its reputation. But they're making a name for themselves through high-profile targets according to HIPAA Journal.
Their attack on Ingram Micro, one of the world's largest IT distributors, demonstrated their capability to target major companies. The Conduent breach shows they're willing to go after critical infrastructure-adjacent targets with massive reach as detailed by HIPAA Journal.
Their Modus Operandi
Safe Pay typically operates using the "double extortion" model that's become standard in modern ransomware attacks. Here's how it works:
Stage 1: Initial Access - The group gains entry to a target network through vulnerable systems, phishing attacks, or compromised credentials. In Conduent's case, the attack method hasn't been publicly disclosed, but common vectors include VPN vulnerabilities, unpatched systems, or compromised employee credentials according to HIPAA Journal.
Stage 2: Network Reconnaissance - Once inside, the attackers spend weeks exploring the network, identifying valuable data repositories, understanding system architecture, and locating backup systems. This is the dangerous dwell time where maximum damage potential is assessed as detailed by HIPAA Journal.
Stage 3: Data Exfiltration - Before encrypting anything, the attackers copy massive volumes of sensitive data to their own servers. They know that encryption alone might not convince victims to pay. But threatening to release sensitive data creates pressure from regulators, competitors, and customers according to HIPAA Journal.
Stage 4: Encryption and Ransom Note - The attackers then encrypt the victim's systems, typically making them inaccessible. A ransom note appears demanding payment in cryptocurrency to provide a decryption key as noted by HIPAA Journal.
Stage 5: Public Disclosure Threat - If the victim doesn't pay, Safe Pay threatens to release the stolen data publicly. They may publish samples to prove they have it as detailed by HIPAA Journal.
Safe Pay's Track Record
While not as prolific as Lock Bit, Safe Pay has demonstrated capability against notable targets. The fact that they successfully exfiltrated 8.5 TB from Conduent suggests their technical capabilities are solid. They have the infrastructure to handle massive data volumes and the operational security to maintain it according to HIPAA Journal.
Security researchers tracking Safe Pay suggest the group likely operates from Eastern Europe or potentially China, based on operational patterns and timestamps. Their infrastructure uses standard bulletproof hosting providers and cryptocurrency mixing services to hide ransom payments as detailed by HIPAA Journal.

How the Breach Likely Happened: Attack Vectors and Vulnerabilities
Conduent hasn't publicly disclosed exactly how Safe Pay gained initial access to their network. But based on what we know about similar attacks against large companies and infrastructure providers, the most likely scenarios are clear according to HIPAA Journal.
Likely Attack Vectors
VPN and Remote Access Vulnerabilities - Large companies like Conduent need remote access capabilities for their distributed workforce. If VPN systems weren't fully patched or used weak authentication, they're prime entry points. Safe Pay could have used known exploits against VPN infrastructure to bypass perimeter security as detailed by HIPAA Journal.
Credential Compromise - A Conduent employee's credentials, leaked in a previous breach or purchased on the dark web, could have given attackers access. Many companies struggle with credential hygiene, reusing passwords across systems. One weak password could have been the entry point according to HIPAA Journal.
Phishing and Social Engineering - A convincing phishing email targeting Conduent employees, impersonating executives or IT departments, could have tricked someone into revealing credentials or installing malware. This is still the most common initial access vector for enterprise breaches as noted by HIPAA Journal.
Unpatched Systems - Despite security patches being available, large organizations often have legacy systems running unpatched versions. If Conduent had systems vulnerable to known exploits, Safe Pay could have leveraged that immediately as detailed by HIPAA Journal.
Supply Chain Attack - A third-party software vendor or service provider used by Conduent could have been compromised first, giving attackers a foothold to pivot into Conduent's network. This is becoming increasingly common according to HIPAA Journal.
The 2.5-Month Undetected Period
Once inside, the attackers operated for roughly 75 days without detection. How does that happen at a company as large as Conduent? Several factors:
Insufficient Monitoring - Conduent may not have had robust logging and monitoring across all systems. If they weren't actively monitoring network traffic and user behavior, attackers could operate openly as detailed by HIPAA Journal.
Alert Fatigue - Large networks generate thousands of alerts daily. If security teams face constant false positives, real intrusions get buried in the noise according to HIPAA Journal.
Lack of Threat Hunting - Detection requires actively looking for suspicious activity, not just waiting for alerts. Many companies only react to alerts rather than proactively hunting for threats as noted by HIPAA Journal.
Compromised Credentials Used Legitimate Access - If attackers used stolen credentials, they'd appear as legitimate users in logs. This makes detection much harder because they're not triggering obvious intrusion indicators as detailed by HIPAA Journal.

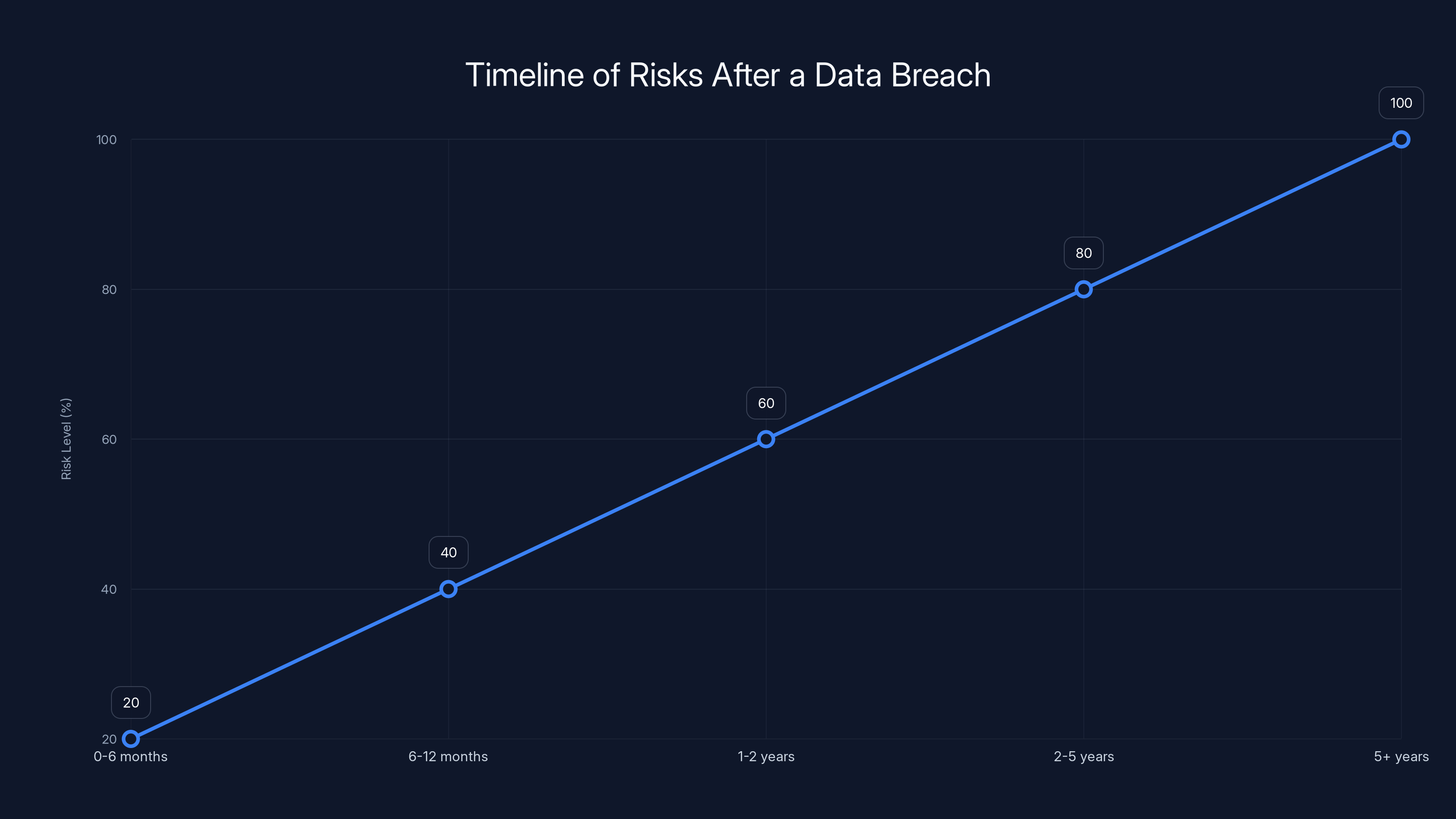
Estimated data shows that the risk of identity theft and fraud increases over time after a data breach, peaking several years later. Continuous monitoring is crucial.
The Impact on Volvo and Its Customers
For Volvo specifically, this breach created multiple problems beyond the immediate data exposure according to HIPAA Journal.
Reputational Damage
Consumer trust in Volvo's ability to protect customer data has been damaged. When customers learn their Social Security numbers, medical information, and health insurance details were stolen through a Volvo service provider, confidence erodes. Volvo didn't cause the breach, but they were the vector through which customers' data was exposed as noted by HIPAA Journal.
Regulatory Scrutiny
State attorneys general offices are investigating Conduent's security practices. This will likely lead to regulatory pressure on Volvo to implement stronger vendor security requirements and due diligence processes as detailed by HIPAA Journal.
Notification and Legal Costs
Volvo had to notify 17,000 individuals, provide free credit monitoring services, and potentially deal with lawsuits from affected parties. These costs, while manageable for a company of Volvo's size, are still significant according to HIPAA Journal.
Supply Chain Implications
For other companies using Conduent's services, this breach raises urgent questions about vendor security. Organizations need to reassess their reliance on third-party service providers who handle sensitive data as noted by HIPAA Journal.
The Monitoring Services Offered
Conduent offered free identity theft and credit monitoring services to affected individuals. These typically include:
- Credit report monitoring and alerts for changes
- Credit freeze assistance
- Identity theft insurance
- Dark web monitoring for exposed credentials
- Fraud resolution support
While these services help, they're not a complete solution. They address reactive measures but don't prevent all possible fraud as detailed by HIPAA Journal.

Broader Industry Context: Why Data Breaches Keep Happening
The Conduent breach isn't an isolated incident. It's part of a larger pattern of massive breaches affecting critical infrastructure companies according to HIPAA Journal.
The Ransomware Epidemic
Ransomware attacks have exploded in frequency and scale over the past five years. The reason is simple: they work. Companies often pay ransoms because the cost of remediation exceeds the ransom demand. The FBI estimates ransomware cost American victims over $5 billion in 2023 alone according to the New York Post.
When attacks are profitable, more criminals attempt them. It's basic economics. Safe Pay likely calculated that Conduent's value as a target—with access to millions of records and critical government services—made it worth the effort as noted by HIPAA Journal.
The Vulnerability of Large Service Providers
Companies like Conduent, while large, are under constant pressure to cut costs and maximize efficiency. Security sometimes takes a backseat to operational efficiency. A breach that costs millions to remediate is often cheaper, in the eyes of some executives, than implementing comprehensive security improvements that cost millions annually as detailed by HIPAA Journal.
This is a market failure. Companies don't bear the full cost of breaches they cause—victims do. Until regulatory frameworks force companies to fully internalize breach costs, the incentive structure encourages inadequate security investment according to HIPAA Journal.
The State of Infrastructure Security
Conduent processes data for government agencies. This means critical government services are dependent on private companies' security practices. If Conduent's infrastructure is breached, government services are degraded. Yet government agencies have limited control over those vendors' security decisions as noted by HIPAA Journal.
This creates systemic risk. The breach of one key vendor cascades through government services, healthcare systems, and transportation networks. The infrastructure security problem is deeper than any single breach as detailed by HIPAA Journal.
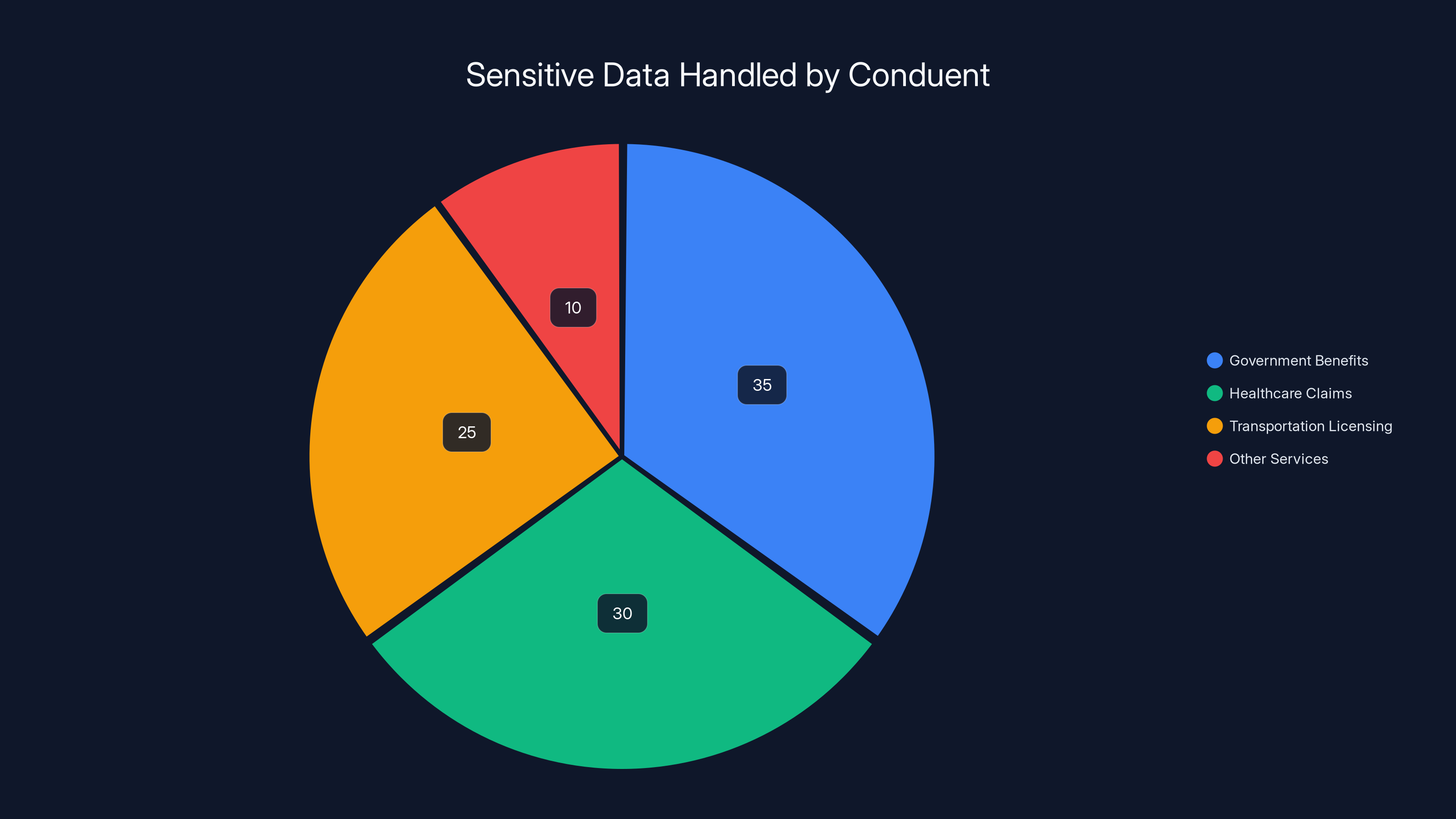
Estimated distribution of data types shows government benefits and healthcare claims as major components, highlighting why Conduent is a target for data breaches.
What You Should Do: Immediate Actions for Affected Individuals
If you might be affected by this breach—and given the scale, many people are—here are concrete steps you should take immediately.
Step 1: Verify You're Affected
Conduent set up notification letters to affected individuals. If you received a letter from Conduent or Volvo notifying you of exposure, you're definitely affected. Check the Conduent website (conduent.com) for their official breach notification page as noted by HIPAA Journal.
You can also check if your data appeared in this breach using Have I Been Pwned (haveibeenpwned.com), a database of breached records maintained by security researcher Troy Hunt. Enter your email address to see if it appears in any known breaches according to HIPAA Journal.
Step 2: Enroll in Provided Monitoring Services
Conduent is offering free identity theft and credit monitoring services to affected individuals. You should enroll immediately. The notification letter should include enrollment instructions and a unique ID code as detailed by HIPAA Journal.
These services typically monitor your credit reports for suspicious activity and alert you to changes. They're free and useful, though not foolproof according to HIPAA Journal.
Step 3: Place a Fraud Alert on Your Credit Reports
Contact the three major credit bureaus (Equifax, Experian, Trans Union) and request a fraud alert. This adds a note to your credit report requiring creditors to verify your identity before opening new accounts as noted by HIPAA Journal.
A fraud alert lasts one year but can be renewed. The credit bureaus:
Equifax: 1-888-378-4329 or equifax.com/personal/credit-report-services Experian: 1-888-397-3742 or experian.com Trans Union: 1-800-680-7289 or transunion.com
Step 4: Consider a Credit Freeze
A credit freeze is more powerful than a fraud alert. It restricts access to your credit file, making it nearly impossible for criminals to open new accounts in your name without your explicit permission according to HIPAA Journal.
Credit freezes are free in all 50 states. You can place one through the same credit bureaus listed above. The process takes about 15 minutes as detailed by HIPAA Journal.
The downside: if you apply for credit yourself, you'll need to temporarily lift the freeze. But for most people, the security benefit outweighs this minor inconvenience as noted by HIPAA Journal.
Step 5: Monitor Your Financial Accounts Closely
Even with monitoring services, you should manually check your accounts regularly:
Bank and credit card accounts - Review statements weekly for unauthorized charges. Set up account alerts for large transactions according to HIPAA Journal.
Credit reports - Request your free annual credit reports from annualcreditreport.com. Review them carefully for accounts you don't recognize as detailed by HIPAA Journal.
Medical accounts - Check explanation of benefits (EOBs) from your insurance company for claims you didn't incur as noted by HIPAA Journal.
Government benefits - If you receive any government benefits, verify that payouts are correct and no fraudulent claims have been filed according to HIPAA Journal.
Step 6: Watch for Phishing and Social Engineering
Now that criminals have your personal information, they may use it to craft convincing phishing emails or social engineering attacks. They'll reference real details about you to appear credible as detailed by HIPAA Journal.
Be skeptical of unsolicited emails, calls, or texts claiming to be from financial institutions, the IRS, or other agencies. Never click links in unexpected emails or provide personal information to callers—call the organization back using a number you find independently as noted by HIPAA Journal.
Step 7: Consider Identity Theft Protection Services
Beyond Conduent's free services, you might consider paid identity theft protection services like Identity Guard or Lifelock (now part of Norton). These provide more comprehensive monitoring, but many experts argue that diligent personal monitoring plus credit freezes is sufficient for most people according to HIPAA Journal.
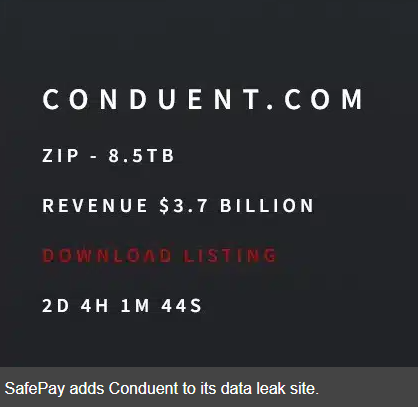
Long-Term Risks: What Happens After a Massive Breach
You might think that once you've taken these protective steps, the risk diminishes. Unfortunately, that's not how data breaches work. The data is now in criminal hands, and the risks persist for years as noted by HIPAA Journal.
The Extended Timeline of Risk
Identity theft and fraud from data breaches don't typically happen overnight. Criminals are patient. They may:
Hold the data for months or years while monitoring your credit for better opportunities. If you have good credit now, they'll wait for financial stress or life events that might make you vulnerable according to HIPAA Journal.
Sell it to other criminals on dark web marketplaces. Your data might change hands multiple times, each buyer potentially attempting different fraud schemes as detailed by HIPAA Journal.
Use it for targeted attacks - combining it with information from other breaches to construct detailed profiles for sophisticated fraud or hacking attempts as noted by HIPAA Journal.
Activate dormant accounts years later when you've let your guard down and stopped monitoring closely according to HIPAA Journal.
Security researchers recommend treating a major data breach with your personal information as a decades-long security incident, not a one-time event as detailed by HIPAA Journal.
Medical Identity Theft Specific Concerns
Because medical information was stolen, there's a particular risk of medical identity theft. A criminal could:
Use your health insurance to obtain prescriptions or medical services, running up fraudulent claims as noted by HIPAA Journal.
Create a false medical history under your name that could affect your insurance rates or medical treatment decisions according to HIPAA Journal.
Obtain medical devices or durable medical equipment in your name through insurance fraud as detailed by HIPAA Journal.
Monitoring your medical accounts and checking Explanations of Benefits (EOBs) regularly is crucial. If you see medical claims you didn't authorize, report them immediately to your insurance company and healthcare providers as noted by HIPAA Journal.
Dark Web Monitoring
Many monitoring services include dark web monitoring, which searches hacker forums and marketplaces for your personal information. This is helpful for detecting if your data is actively being traded among criminals according to HIPAA Journal.
But remember: the absence of detection doesn't mean your data isn't being used. Criminals may use your information privately without putting it on public dark web marketplaces as detailed by HIPAA Journal.

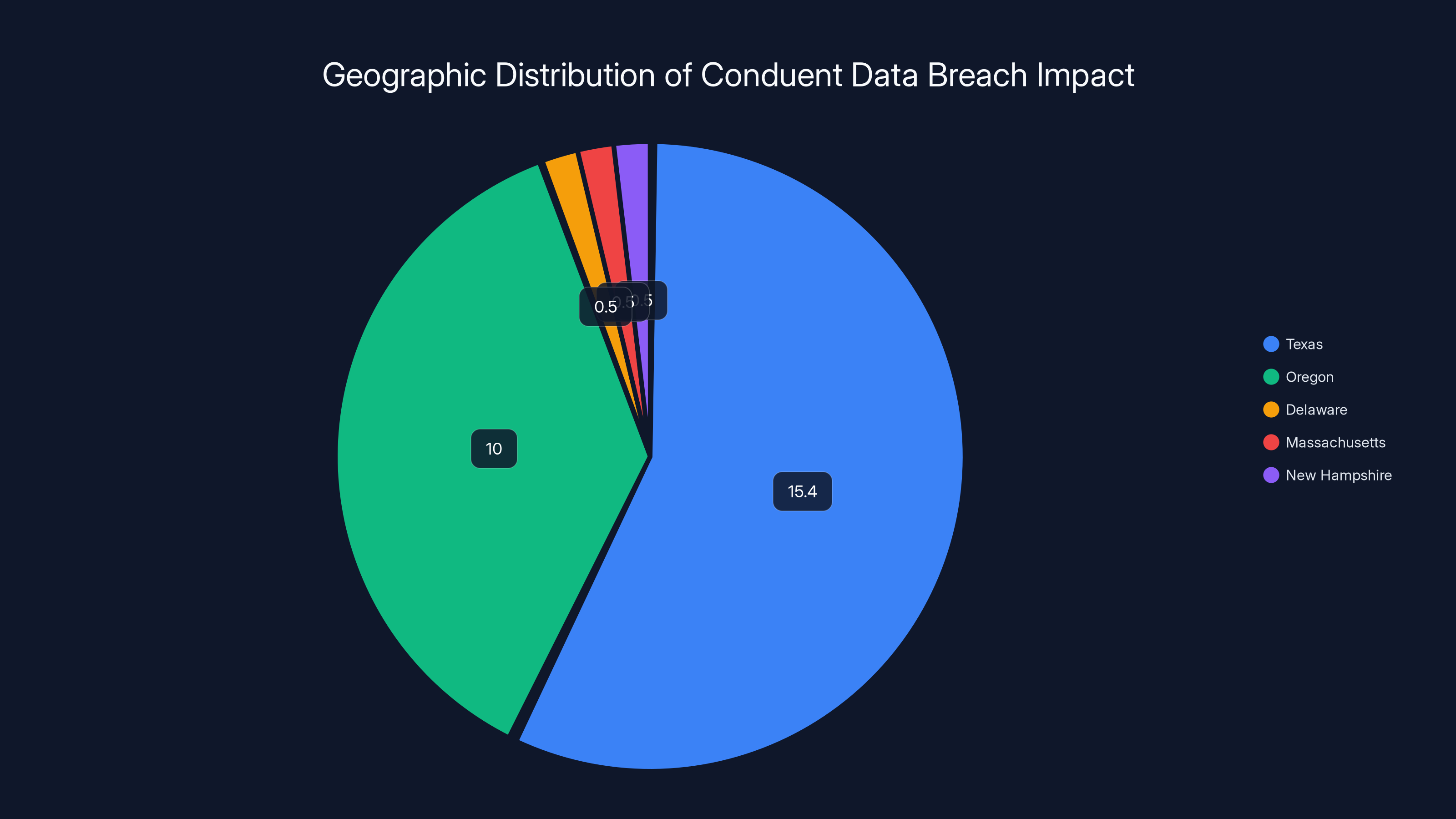
Texas and Oregon are the most affected by the Conduent breach, with Texas alone accounting for approximately half of its population. Estimated data for other states shows significant impacts, highlighting the breach's extensive reach.
The Legal and Regulatory Aftermath
Beyond individual victims' concerns, the Conduent breach has significant legal and regulatory implications according to HIPAA Journal.
State Regulatory Investigations
State attorneys general offices, particularly in heavily affected states like Texas and Oregon, are likely investigating Conduent's security practices. These investigations can result in:
Fines and penalties for inadequate security measures or violations of state data protection laws as noted by HIPAA Journal.
Mandatory security improvements that Conduent must implement going forward as detailed by HIPAA Journal.
Restitution to affected individuals, though this is relatively rare unless fraud is proven according to HIPAA Journal.
Potential Class Action Lawsuits
Affected individuals and advocacy groups may file class action lawsuits against Conduent, Volvo, and potentially the insurers and vendors involved. These lawsuits typically seek:
Damages for exposed personal information and associated risks as noted by HIPAA Journal.
Free credit monitoring and other protective services as detailed by HIPAA Journal.
Punitive damages if negligence can be proven according to HIPAA Journal.
Class action settlements in data breaches rarely result in large individual payouts because the damages are spread across millions of claimants. But they can force companies to change security practices going forward as noted by HIPAA Journal.
Regulatory Framework Changes
Large breaches like this often prompt regulatory attention and potential new laws. Given that Conduent's breach compromised government services, Congress might pressure federal agencies to implement stricter vendor security requirements as detailed by HIPAA Journal.
State-level data protection laws, like the California Consumer Privacy Act (CCPA) and similar laws in other states, may be strengthened with faster notification requirements, higher penalties, or more prescriptive security standards according to HIPAA Journal.
The Role of Cyber Insurance
Conduent likely carries cyber liability insurance that covers breach response costs, notification expenses, and legal liability. Cyber insurance is becoming more important and more expensive following major breaches as noted by HIPAA Journal.

How to Assess Your Own Vendor Security Risk
If you're a business that uses third-party vendors handling sensitive data, the Conduent breach raises urgent questions about your vendor security practices according to HIPAA Journal.
Conducting Vendor Security Assessments
Request documentation of your vendor's security practices, certifications, and incident response plans. Reputable vendors should have SOC 2 Type II certifications or equivalent security audits as detailed by HIPAA Journal.
Ask about specific security controls including network segmentation, encryption standards, access controls, and monitoring capabilities as noted by HIPAA Journal.
Understand their breach notification timeline - How quickly will they notify you if a breach occurs? Within 24 hours? A week? according to HIPAA Journal.
Review their insurance coverage - Do they carry cyber liability insurance? Are you named as an additional insured? as detailed by HIPAA Journal.
Conduct penetration testing - Work with security firms to test your vendor's network security if they handle particularly sensitive data as noted by HIPAA Journal.
The Due Diligence Checklist
Pre-contract vendor security review:
- Security certifications (SOC 2, ISO 27001)
- Incident response plan documentation
- Data encryption standards (in transit and at rest)
- Access control and authentication mechanisms
- Regular security audit history
- Cyber liability insurance coverage
- Data retention and deletion policies
- Compliance with relevant regulations (HIPAA, PCI-DSS, GDPR, etc.)
Ongoing vendor management:
- Annual security reassessment
- Regular breach notification protocol testing
- Monitoring of vendor security incidents and advisories
- Contract clauses allowing for on-site security audits
- Defined security incident escalation procedures

The Bigger Picture: Infrastructure Security in America
The Conduent breach reveals systemic vulnerabilities in how America's critical services are secured according to HIPAA Journal.
Outsourcing and Systemic Risk
Government agencies contract with companies like Conduent to reduce costs and increase efficiency. But this outsourcing creates systemic risk. When a private vendor is breached, government services degrade, affecting millions of citizens who never chose to trust that vendor as noted by HIPAA Journal.
This creates a market failure where vendors don't fully bear the cost of their security failures. The government and citizens bear the cost. Without realigning incentives, there's insufficient pressure to improve security at the vendor level as detailed by HIPAA Journal.
The Skills Gap in Cybersecurity
Qualified cybersecurity professionals are in short supply. Good security requires experienced talent, and talent is expensive. Some companies cut corners on security staffing to maintain profit margins according to HIPAA Journal.
Conduent, a profitable public company, could afford top-tier security. Whether they chose to invest in it adequately is unclear. But many smaller vendors genuinely lack the resources for enterprise-grade security as noted by HIPAA Journal.
Legacy Systems and Technical Debt
Large companies supporting critical services often maintain legacy systems that are difficult or expensive to modernize. These systems may not support modern security features like multi-factor authentication or encryption as detailed by HIPAA Journal.
Modernizing legacy infrastructure is expensive and disruptive. Many organizations delay it until a breach forces action. By then, it's too late according to HIPAA Journal.
The Need for Systemic Regulation
Some security experts argue that critical infrastructure security should be more heavily regulated by government. If services are truly critical to national interests, the government should have authority to mandate minimum security standards as noted by HIPAA Journal.
Others counter that regulation stifles innovation and that market competition creates better security than government mandates. This debate continues as breaches become larger and more consequential as detailed by HIPAA Journal.
Future Outlook: What Comes Next
The Conduent breach will have ripple effects for years. Here's what to expect according to HIPAA Journal.
Immediate Aftermath (Next 3-6 Months)
Expect increasing numbers of fraud reports from affected individuals as criminals attempt to exploit the exposed data. State attorneys general will complete initial investigations and likely announce enforcement actions. Litigation will accelerate with class actions being certified as noted by HIPAA Journal.
Conduent will announce security improvements and may bring in external security firms to assess and remediate vulnerabilities as detailed by HIPAA Journal.
Medium Term (6 Months to 2 Years)
Some regulatory changes may emerge, particularly around vendor security requirements for companies handling government data. Cyber insurance costs may increase for business process outsourcing companies according to HIPAA Journal.
Settlements from class action lawsuits will begin paying affected individuals, typically modest amounts per person as noted by HIPAA Journal.
Conduent's reputation will recover partially, but customer trust will remain damaged. Some government agencies may move portions of business to competitors as detailed by HIPAA Journal.
Long Term (2+ Years)
The incident becomes a case study for vendor security management. Business schools include it in curriculum. Security conference speakers reference it as a cautionary tale according to HIPAA Journal.
But history suggests that despite lessons learned, similar breaches will continue. The incentive structure hasn't changed. Vendors will continue making security decisions based on cost-benefit analysis, not absolute protection as noted by HIPAA Journal.

Key Takeaways and Practical Recommendations
Here's what you need to remember about the Conduent-Volvo breach and how to protect yourself according to HIPAA Journal.
For Affected Individuals
Act immediately - Enroll in free monitoring services, place credit freezes, and monitor your accounts. Don't wait for fraud to occur as noted by HIPAA Journal.
Assume persistent risk - Treat this as a long-term security incident affecting your credit for years. Stay vigilant indefinitely as detailed by HIPAA Journal.
Use free tools - Credit freezes are free. Credit monitoring from annualcreditreport.com is free. You don't need to pay for expensive identity theft protection unless you prefer the extra features according to HIPAA Journal.
Document everything - Keep records of all accounts you freeze, monitoring enrollments, and fraud alerts. You may need this documentation if fraud does occur as noted by HIPAA Journal.
For Businesses Using Vendors
Audit your vendors immediately - If you use third-party service providers handling sensitive data, assess their security practices now as detailed by HIPAA Journal.
Strengthen contracts - Add security requirements, audit rights, and incident notification timelines to vendor contracts according to HIPAA Journal.
Diversify providers - Reduce concentration risk by using multiple vendors for critical services. Don't put all sensitive data with one provider as noted by HIPAA Journal.
Invest in security internally - Don't assume vendors are protecting you. Implement your own layers of monitoring and controls as detailed by HIPAA Journal.
For Government Agencies
Mandate security standards - Require vendors handling government data to meet specific security baselines before contracts are awarded according to HIPAA Journal.
Conduct regular audits - Don't trust vendors' self-reporting. Conduct independent security audits of critical vendors as noted by HIPAA Journal.
Diversify critical services - No single vendor should be a single point of failure for critical government services as detailed by HIPAA Journal.

FAQ
What exactly is Conduent and why do they handle so much sensitive data?
Conduent is an American business process outsourcing company that provides transaction processing, automation, and analytics services to hundreds of government agencies, healthcare providers, transportation departments, and other organizations. They handle massive volumes of sensitive data because they process government benefits, healthcare claims, transportation licensing, and similar critical services. This makes them an attractive target for hackers seeking to compromise multiple organizations simultaneously according to HIPAA Journal.
How did Safe Pay get into Conduent's network and stay undetected for 2.5 months?
Conduent hasn't disclosed the specific attack vector, but common methods include compromised credentials, VPN vulnerabilities, or phishing attacks that gave hackers initial access. Once inside, they likely operated using stolen legitimate credentials, making them appear as regular users in system logs. With inadequate threat monitoring and hunting, the attackers could explore the network, identify valuable data, and exfiltrate it over 75 days without detection. Large enterprises often struggle with alert fatigue and insufficient logging across all systems as detailed by HIPAA Journal.
What should I do immediately if I think I'm affected by this breach?
Enroll in the free monitoring services Conduent is offering, place credit freezes with all three credit bureaus (Equifax, Experian, Trans Union), and monitor your credit reports, bank accounts, and medical accounts for unauthorized activity. These steps take just a few hours but protect you against most common identity theft scenarios. Don't wait for fraud to occur—act now while the breach is fresh according to HIPAA Journal.
How long should I worry about fraud from this breach?
Treat this as a lifetime security concern, though risk diminishes over time. Criminals may hold stolen data for months or years before attempting fraud. Keep monitoring your credit for at least seven years—the standard period for credit report accuracy. Your Social Security number is compromised permanently, but the active risk window is longest in the first year or two as noted by HIPAA Journal.
Will Conduent face legal consequences for this breach?
Likely yes, in multiple forms. State attorneys general are investigating and will likely announce fines or penalties. Class action lawsuits will be filed seeking damages and restitution. Settlements, if reached, will require Conduent to improve security and may provide limited compensation to affected individuals. Beyond legal liability, Conduent faces reputational damage and potential loss of government contracts as agencies reassess vendor security according to HIPAA Journal.
How can I tell if my data is specifically at risk in this breach?
Check for notifications from Conduent or Volvo sent to your address on file. The notification letter should specify if your data was exposed. You can also check Have I Been Pwned (haveibeenpwned.com) or use Conduent's official breach notification website. Given the scale of the breach affecting millions in affected states, if you received government benefits or used Volvo services through an affected state agency, you were likely exposed as detailed by HIPAA Journal.

Conclusion: From Crisis to Vigilance
The Conduent breach affecting 17,000 Volvo customers and millions more nationwide represents one of the largest data compromises in recent years. But more importantly, it illustrates systemic vulnerabilities in how America secures critical infrastructure and personal data according to HIPAA Journal.
Safe Pay got in, stayed undetected for months, and stole 8.5 terabytes of sensitive information. Medical records combined with Social Security numbers create a perfect storm for sophisticated identity theft. The geographic scope—affecting roughly half of Texas's population, a quarter of Oregon's, and millions nationwide—demonstrates just how central Conduent is to critical services as noted by HIPAA Journal.
But here's the crucial point: while you can't control whether vendors secure their networks, you can control your response. Placing a credit freeze takes 15 minutes and prevents most identity theft scenarios. Monitoring your accounts takes modest effort but catches fraud early. These aren't perfect solutions, but they're powerful and free as detailed by HIPAA Journal.
The Conduent breach also serves as a wake-up call for organizations relying on third-party vendors with sensitive data. The due diligence you conduct on vendors today might prevent a breach tomorrow. The security investments you make now might save you from becoming another cautionary tale according to HIPAA Journal.
Final thought: data breaches at this scale will continue happening. Companies will assess security investments through a cost-benefit lens. Hackers will keep targeting high-value vendors with critical reach. The only way to break this cycle is for individuals to protect themselves actively, for organizations to demand more from vendors, and for regulators to realign incentives so that security failures carry their full cost. Until then, vigilance is your best defense as noted by HIPAA Journal.
Consider using Runable for securing your organization's sensitive data workflows. Runable provides AI-powered automation for creating secure documentation, reports, and presentations without exposing data to third-party integrations. For teams managing sensitive information, Runable's platform enables secure document generation and workflow automation starting at $9/month, reducing reliance on external vendors for critical processes.

Related Articles
- SmarterTools Ransomware Breach: How One Unpatched VM Compromised Everything [2025]
- Wikipedia vs Archive.today: The DDoS Controversy Explained [2025]
- Google's New Tools to Remove Your ID From Search Results [2025]
- Google's Enhanced Safety Tools Remove More Personal Data [2025]
- Vega Security Raises $120M Series B: Rethinking Enterprise Threat Detection [2025]
- Google's Tool for Removing Non-Consensual Images from Search [2025]
![Volvo Conduent Data Breach: 17,000 Customers Exposed [2025]](https://tryrunable.com/blog/volvo-conduent-data-breach-17-000-customers-exposed-2025/image-1-1770817184252.jpg)



