Whisper Pair Bluetooth Hack: The Complete Security Guide to Fast Pair Vulnerabilities
Your wireless headphones might be listening to you, and not in the way you'd expect. A new security vulnerability called Whisper Pair has exposed a fundamental weakness in how millions of Bluetooth devices handle pairing requests. Researchers from KU Leuven University in Belgium discovered that attackers can hijack Fast Pair-enabled accessories in as little as 10 seconds, gaining access to your microphone, location data, and audio stream from up to 14 meters away.
The scary part? Google's own earbuds are vulnerable. So are devices from Sony, JBL, One Plus, Nothing, and at least six other major manufacturers. Even worse, there's no easy way to disable Fast Pair, leaving you dependent on firmware updates that companies might take weeks or months to release.
This isn't theoretical hacking. Whisper Pair is a practical, reproducible attack that requires nothing more than basic Bluetooth hardware and a little patience. The attack exploits a fundamental design flaw in how Bluetooth devices handle the Fast Pair protocol, specifically in the pairing mode verification process.
In this guide, we'll break down exactly what Whisper Pair is, how it works, which devices are at risk, and what you can actually do about it. Whether you're a tech enthusiast worried about your own security or someone responsible for organizational device security, understanding this vulnerability is critical.
TL; DR
- Whisper Pair exploits Fast Pair weakness: Attackers can hijack Bluetooth devices by forcing them to accept pairing requests outside of pairing mode
- Attack takes just 10 seconds: Median hijacking time is only 10 seconds at ranges up to 14 meters, far enough that victims won't notice
- Affects 10+ manufacturers: Sony, JBL, One Plus, Nothing, Google, and others have vulnerable devices on the market right now
- Enables microphone and location access: Once hijacked, attackers can spy on conversations, track location, and interrupt audio
- No easy protection exists: You can't disable Fast Pair, and firmware updates are slow in coming from manufacturers
- Factory reset is your only real option: If you suspect compromise, factory reset your device and wait for patches
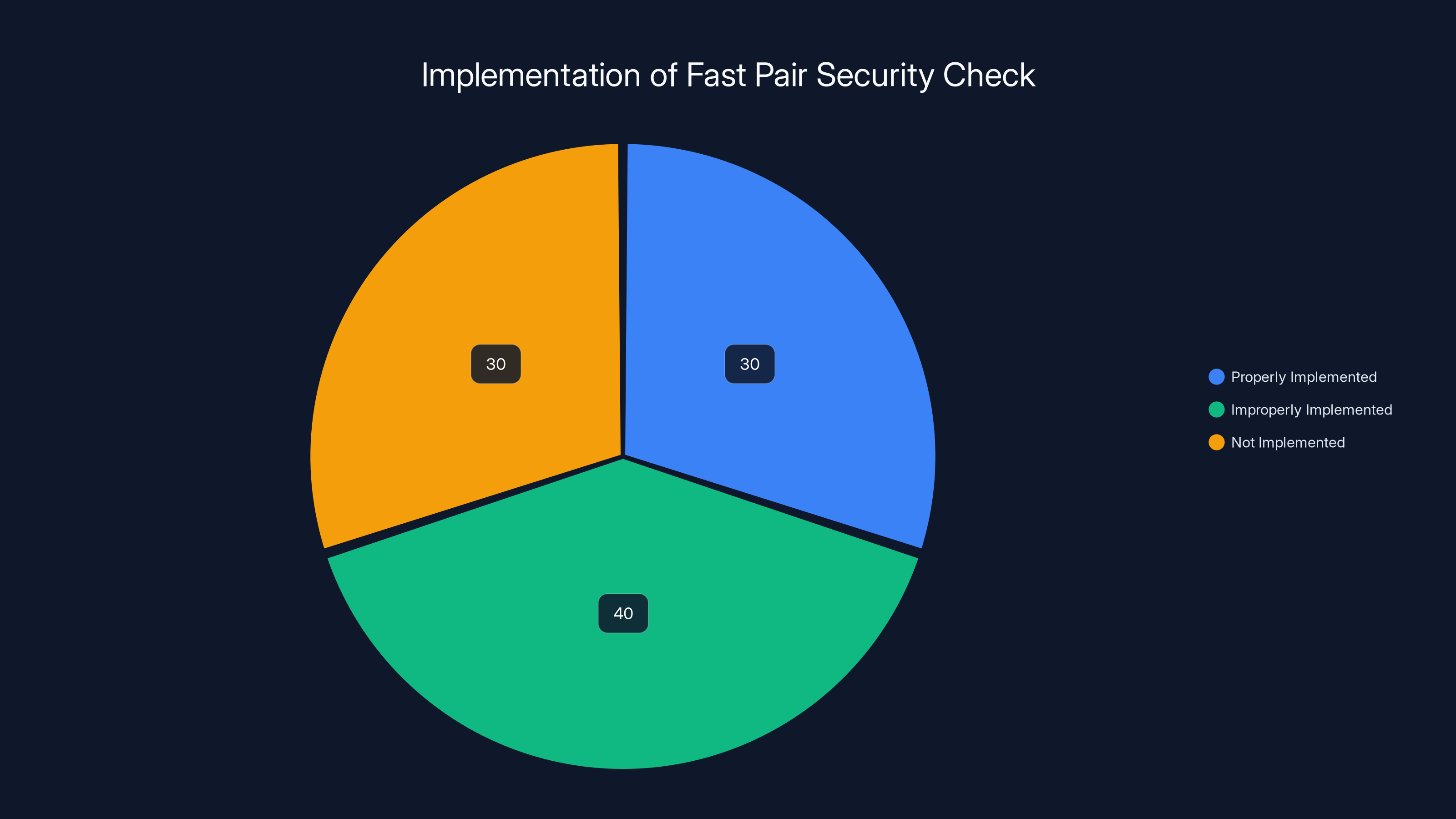
Estimated data shows that a significant portion of manufacturers either improperly implement or do not implement the necessary security checks in the Fast Pair protocol, leading to vulnerabilities like WhisperPair.
Understanding Google Fast Pair: Why It Exists and What It Does
Bluetooth pairing used to be a nightmare. I remember the days of hunting through menus, entering PIN codes, and watching devices fail to connect for no apparent reason. Google Fast Pair was designed to solve this problem by automating the pairing process almost entirely.
Instead of manual configuration, Fast Pair lets your phone recognize nearby compatible Bluetooth devices and prompt you to connect with a single tap. If you've ever gotten a notification on your Android phone suggesting you pair your newly purchased headphones, that's Fast Pair at work. It's seamless, it's intuitive, and it just works.
The system works through a backend database that Google maintains. When a Bluetooth device comes in range, your phone queries Google's servers to identify the device model and fetch the appropriate pairing information. This means your phone immediately knows what device you're trying to connect to, what permissions it needs, and how to configure it properly. No hunting through settings. No fumbling with cryptic device names like "JBL_Headphones_AF2B".
Fast Pair has become remarkably popular because it genuinely improves the user experience. Google has licensed it to a huge array of manufacturers. The protocol is now used in devices from over 100 brands, ranging from cheap basic earbuds to premium audio equipment. Billions of people use Fast Pair daily without thinking about it.
But here's the thing: convenience and security are always in tension. Fast Pair was built to be convenient. The security implications were clearly not the primary design focus.
What Is Whisper Pair? The Vulnerability Explained
Whisper Pair isn't a software bug in the traditional sense. It's not a coding error that developers made. Instead, it's a fundamental design flaw in how the Fast Pair protocol is implemented across the ecosystem.
The protocol itself has a security requirement: Bluetooth accessories should only accept Fast Pair connection requests when they're in pairing mode. This makes sense as a security principle. If your headphones accept pairing requests from any random device at any time, then anyone nearby could pair with them and potentially access sensitive functionality.
So the protocol specification says: "Before pairing, the device must check whether it's in pairing mode. Only if it is should it accept the connection."
Many manufacturers, however, either didn't implement this check properly or didn't implement it at all. Their devices accept pairing requests regardless of whether pairing mode is actually enabled. This creates an opening for attackers.
Whisper Pair exploits this gap by forcing a standard Bluetooth pairing connection with a device that fails to properly verify whether it should accept the request. The attack forces the pairing through the regular Bluetooth protocol, which is robust and well-established. The device, lacking the proper gating mechanism, accepts the pairing request even though it shouldn't.
Once paired, the attacker becomes a trusted accessory. And here's where it gets bad: trusted accessories have access to sensitive functionality like the microphone and location services. They can't do absolutely anything (the device still has permission boundaries), but they can do enough to cause real harm.
The research team from KU Leuven created a practical demonstration of the attack. They showed that a nearby attacker with basic Bluetooth hardware could hijack vulnerable devices in about 10 seconds on average. The attack works from up to 14 meters away, which is near the technical limit of Bluetooth range. This means an attacker could be far enough from their target that the target wouldn't even see them lurking nearby.
This is not a theoretical vulnerability. The researchers didn't just identify a mathematical weakness or a logical flaw in the protocol. They built the attack, tested it against real devices, and demonstrated that it works consistently. They created videos showing the attack in action, dramatizing scenarios where someone's headphones are hijacked without their knowledge.
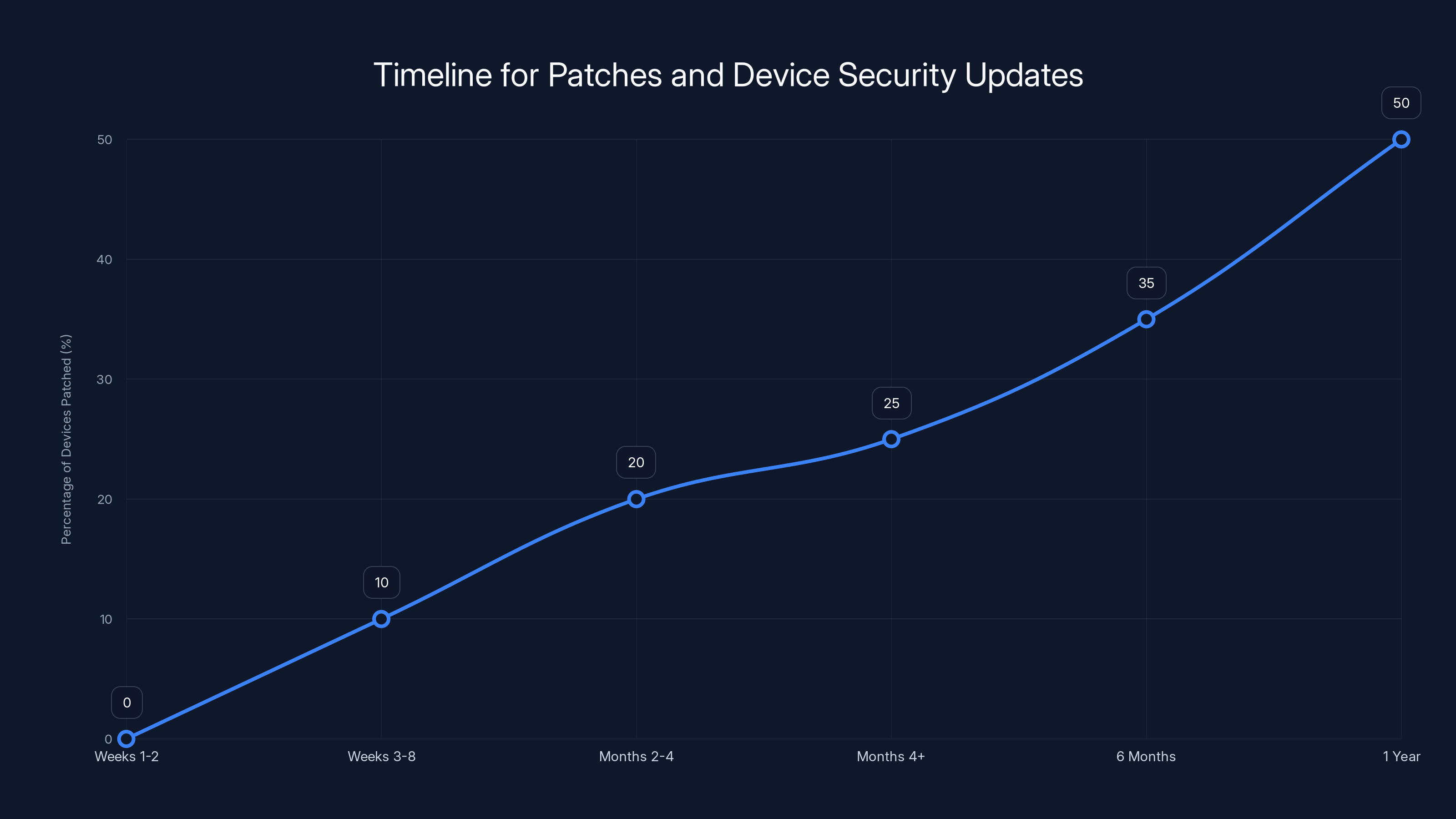
Estimated data shows that within a year, about 50% of affected devices are patched, highlighting a slow adoption rate for security updates.
How the Whisper Pair Attack Actually Works: Step by Step
Let's break down exactly what happens during a Whisper Pair attack. Understanding the mechanics helps explain why it's so dangerous and why it's been difficult for manufacturers to patch.
Step 1: Attacker Detection and Proximity
The attacker is in range of a target device. They don't need to know anything about the target device beforehand. They just need to have a Bluetooth-enabled computer or specialized hardware that can scan for nearby Bluetooth devices. Once they detect a vulnerable Fast Pair device, the attack can begin.
Step 2: Pairing Mode Spoofing
Here's where the actual exploit begins. The attacker sends a specially crafted Bluetooth pairing request to the target device. Normal Bluetooth pairing is usually initiated by the device itself (the headphones announce they're in pairing mode) or requires explicit user action (holding a pairing button).
But the attacker doesn't wait for that. They force the pairing request directly. The vulnerable device should reject this because it's not actually in pairing mode. But many devices don't perform that check, or perform it incorrectly.
Step 3: Connection Establishment
Because the device fails to properly verify whether it's in pairing mode, it accepts the pairing request. From the device's perspective, it's just received a normal Bluetooth pairing request, and it should accept it. The connection gets established normally, following standard Bluetooth protocols.
Step 4: Trust Assignment
Once paired, the attacker's device is now trusted. In the Bluetooth security model, once a device is paired, it gets elevated privileges. It can access functionality that unpaired devices cannot. This includes audio permissions, potentially location services, and other sensitive capabilities depending on the device implementation.
Step 5: Exploitation
Now the attacker can perform various actions. The baseline attack allows them to interrupt the audio stream or inject their own audio. More seriously, they can access the microphone to eavesdrop on conversations. They can track the device's location. They can manipulate what the user hears or sees through the device.
The attack is particularly effective because the user has no idea it happened. They didn't approve anything. They didn't see a pairing prompt. The device simply accepted a connection request that it should have rejected.
Which Devices Are Actually Vulnerable?
Researchers confirmed vulnerabilities across devices from at least 10 different manufacturers. The confirmed list includes some of the most popular audio brands on the market.
Google's Vulnerabilities
Google Pixel Buds Pro and Google Pixel Buds Pro 2 are both vulnerable. These are Google's flagship audio products, and the company that created Fast Pair has devices that fall victim to Whisper Pair. Google has released patches for these devices, but researchers discovered that even the patched versions could be defeated with minor workarounds.
Sony's Audio Products
Multiple Sony wireless earbuds and headphone models are vulnerable, including their premium WF and WH series products. Sony has been notified and is working on patches, but the company has not released them for all affected models.
Nothing Ear and CMF Products
Nothing, the consumer electronics brand founded by former One Plus co-founder Carl Pei, has vulnerable devices. Their Ear buds and CMF audio products all need updates.
JBL Vulnerability Across the Product Line
JBL, owned by Harman (itself owned by Samsung), has numerous vulnerable products. Their popular true wireless and over-ear models need patching.
One Plus Buds
One Plus, known for their Android phones, also sells wireless earbuds that are vulnerable to Whisper Pair.
Additional Manufacturers
Researchers also confirmed vulnerabilities in products from Soundcore, Edifier, Anker, and others. The full list continues to grow as testing expands.
The researchers have published a comprehensive list on their project website, and it's worth checking if your specific device model is listed. Not all products from these manufacturers are vulnerable. Usually it's specific product lines or generations, but you should verify.
The Technical Root Cause: Why This Happened
Understanding why manufacturers implemented Fast Pair incorrectly requires understanding the pressures and constraints they face.
First, the Fast Pair specification is complex. Google published documentation for manufacturers, but implementing it correctly requires careful attention to security details. Many smaller manufacturers have limited security expertise on their teams. They're not professional software companies with large security teams. They're hardware companies that added Bluetooth as a feature.
Second, there's pressure to get products to market quickly. Security features can feel like obstacles when you're trying to launch a product line. If the pairing mode check adds complexity or latency, it's tempting to skip it. "We can always patch it later," the logic goes.
Third, the Fast Pair protocol sits on top of standard Bluetooth, and there's an assumption that the underlying Bluetooth layer handles security. Manufacturers might have assumed that the Bluetooth layer validates pairing properly, not realizing they needed to add their own validation on top.
Finally, testing this properly would require security review and attack simulation. That costs money and time. If a manufacturer doesn't have a security team, they might not have tested the pairing mode validation at all until Whisper Pair was discovered.
The result is a systematic vulnerability across the ecosystem. It's not one manufacturer's mistake. It's a pattern that emerged because many companies implemented the same protocol incorrectly in similar ways.
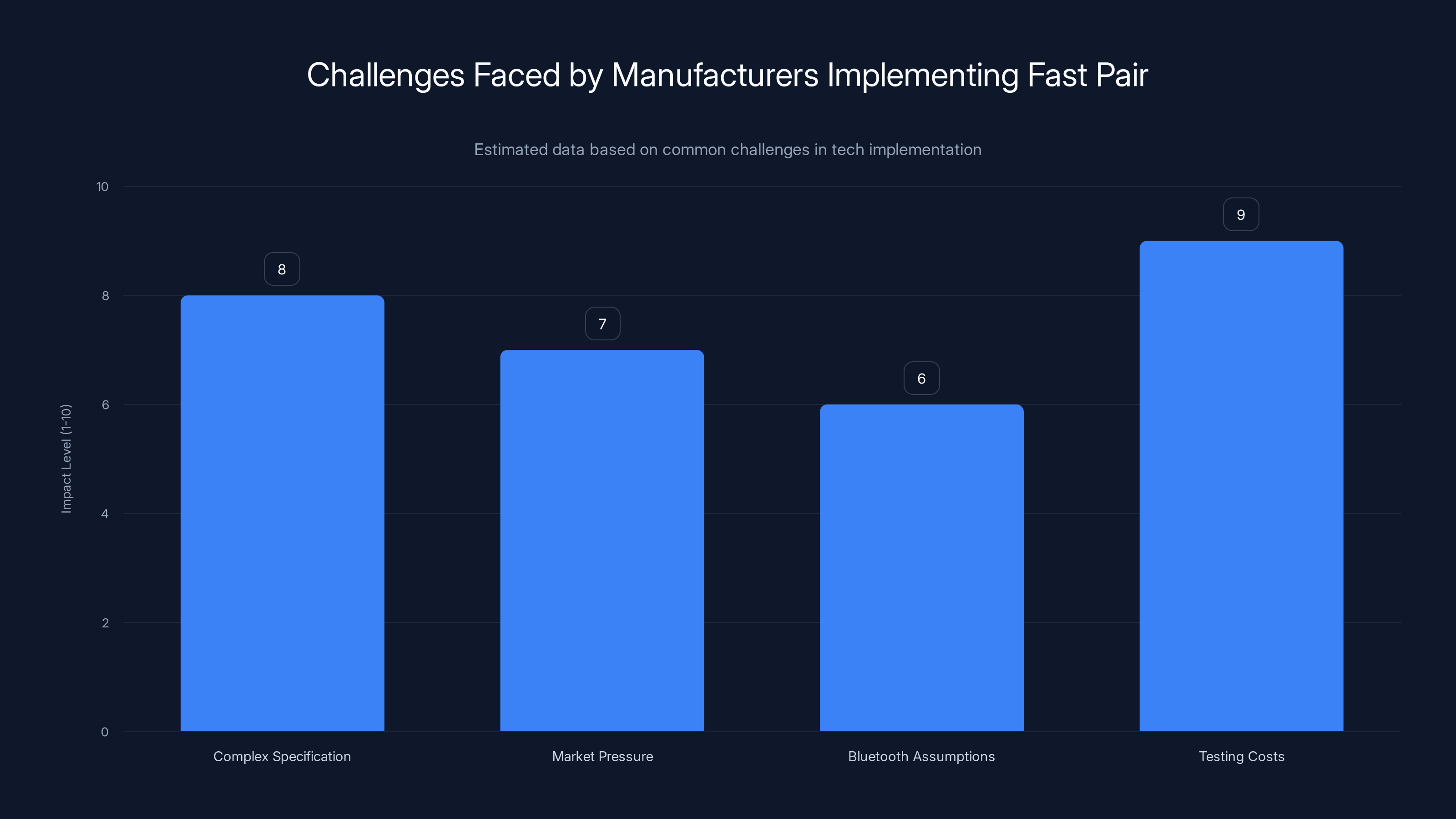
Complex specifications and high testing costs are major challenges for manufacturers implementing Fast Pair. Estimated data shows these factors have the highest impact.
What Attackers Can Actually Do With a Hijacked Device
Let's be specific about the attack capabilities, because there's a spectrum from "annoying" to "seriously dangerous."
Audio Stream Interruption
Once paired, an attacker can interrupt your audio playback. Your music stops. Your podcast cuts out. An attacker could do this repeatedly just to mess with you, or they could use it to create an opportunity to inject different audio. It's the least harmful attack, but it's still a violation of your device.
Audio Injection
The attacker can play audio through your headphones. They can play a sound, a voice message, or any audio content they choose. In the dramatization video, researchers showed an attacker injecting a voice message pretending to be from your bank, asking you to verify account information. This is social engineering with direct access to your ear.
Microphone Eavesdropping
This is the really dangerous capability. Once paired, the attacker can access the microphone. They can listen to conversations happening near your headphones. If you're in a private meeting, they hear it. If you're having a sensitive phone call, they hear that too. If you're discussing passwords, financial information, or anything confidential, they're listening.
Location Tracking
Many audio devices with Bluetooth support location services. An attacker who has hijacked your headphones can access location data. They know where you are, where you go, and where you spend your time. This is particularly concerning for personal safety and privacy.
Permission Escalation
In some device implementations, trusted accessories might have elevated permissions that allow them to perform additional actions. This depends on how the device manufacturer implemented their permission system, but the potential exists for more serious compromises.
What's particularly insidious is that the victim has no way to know any of this is happening. There's no notification that a new device paired. There's no audio click or popup. The headphones just silently accept a pairing request that they should have rejected.

Why Patching Is So Difficult
When you find a vulnerability in Windows, Apple releases a security update automatically. Your computer updates itself, and the vulnerability is closed. Even Android security patches, while slower than many would prefer, reach most devices through regular system updates.
Accessories are different. They're not computers. They don't have automatic update mechanisms built in. They have firmware, sure, but that firmware is typically updated through companion mobile apps if anything.
The Firmware Update Problem
Many Bluetooth accessories don't have any firmware update capability built in at all. They ship with firmware burned into ROM, and there's no way to change it. For these devices, there's no fix. They remain vulnerable forever. Manufacturers can only address the vulnerability by releasing new hardware versions.
Even devices that do support firmware updates often do so inconsistently. Some update through a mobile app. Some require a computer application. Some have never had an update released for them and might not have update infrastructure ready.
The User Adoption Problem
To apply a firmware update, users need to take action. They need to download and install a companion app, connect the device, and run the update. Many people never do this. They buy headphones, connect them to their phone once, and never think about that headphones again until they break.
Google has pushed updates to their own Pixel Buds, but other manufacturers have far less control. They can release patches, but actually getting users to install them is a separate challenge entirely.
The Fragmentation Problem
With 10+ manufacturers affected and dozens of different device models, there's no coordinated response. Google can't force everyone to patch at once. Each manufacturer is responsible for their own devices. Some will move quickly. Some will take months. Some might never release patches at all for older models.
This is the reality of the accessories market. There's no automatic update infrastructure like there is for phones and computers. Manufacturers have little incentive to support old products with firmware updates. Users have minimal awareness of the need to update. Patches trickle out slowly.
Google's Attempted Patch and Its Limitations
Google moved relatively quickly once Whisper Pair was disclosed. The company released updates for its own Pixel Buds devices. But here's the problem: researchers discovered that the patch itself could be bypassed.
This isn't necessarily Google's fault. The fundamental issue is that you can't really prevent pairing mode spoofing at the accessory level if the protocol itself doesn't have robust defenses. A patch might make the attack slightly harder or slower, but determined attackers might find workarounds.
Google also has the advantage of being the company that created Fast Pair in the first place. They understand the protocol deeply and have the resources to develop proper fixes. But even with those advantages, the patch needed by other manufacturers requires them to reimplement parts of the Fast Pair protocol, understand the security implications, and test thoroughly.
This is why the researchers emphasize that a comprehensive fix requires changes to how Fast Pair itself is implemented across the entire ecosystem. Individual device patches help, but they're not a complete solution.
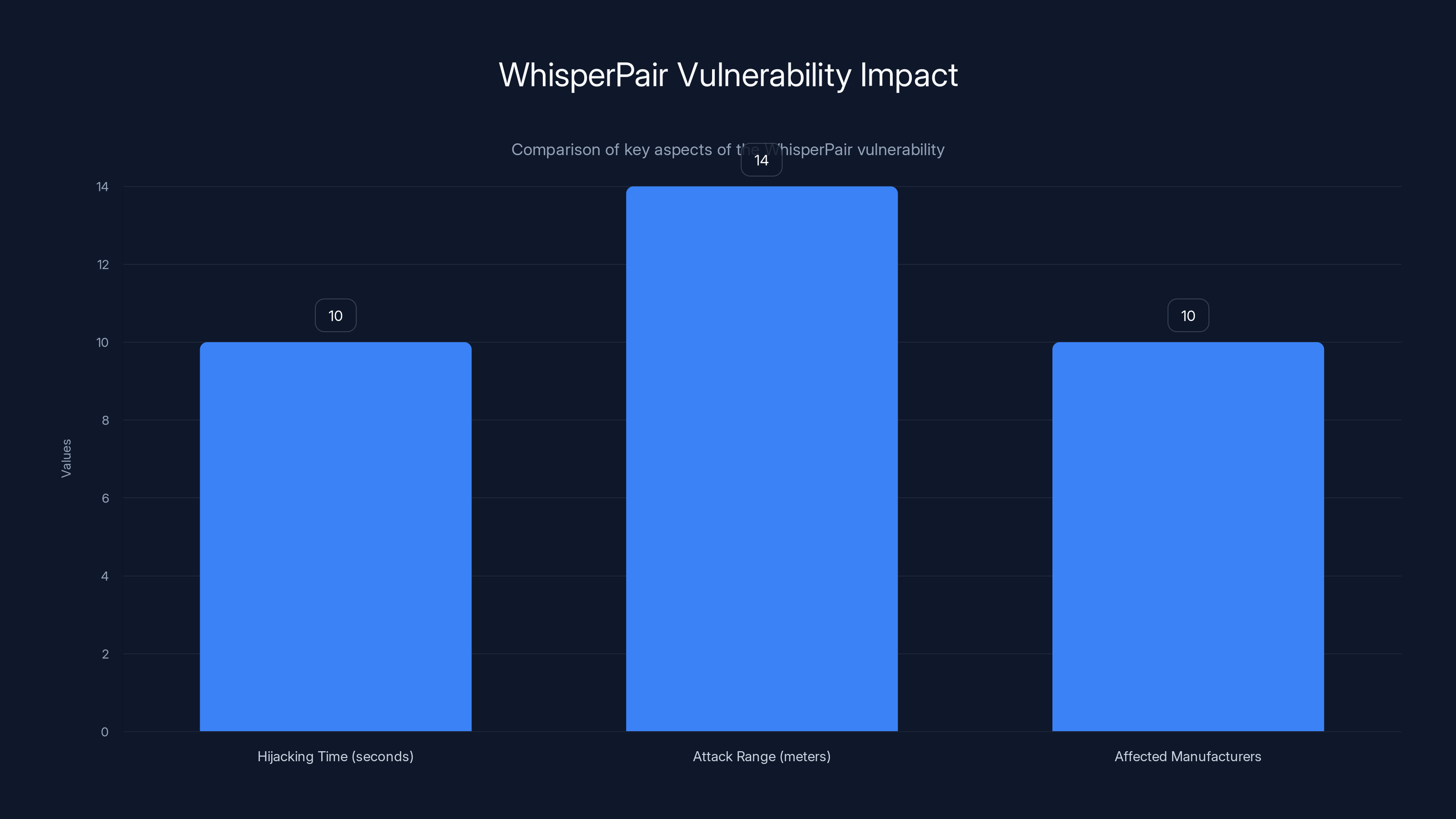
WhisperPair can hijack devices in a median time of 10 seconds from up to 14 meters away, affecting at least 10 manufacturers. Estimated data based on typical vulnerability reports.
Can You Actually Disable Fast Pair?
One obvious question: can you just turn off Fast Pair and avoid the vulnerability altogether?
Not really. There's no user-facing setting to disable Fast Pair functionality on devices. It's built into the Bluetooth stack on supported devices, and there's no way to toggle it off in settings. You can't opt out.
Google's reasoning is probably that Fast Pair is a convenience feature that most users want. Adding a setting to disable it would clutter the interface and confuse people. But it also means users don't have the option to choose security over convenience.
The only real way to avoid the vulnerability would be to not use devices that support Fast Pair. Buy older Bluetooth headphones that lack Fast Pair support. But as the protocol becomes more common, that becomes increasingly impractical.
Some devices do have companion apps that might offer more granular control, but this varies by manufacturer. Theoretically, if a manufacturer implemented proper security controls in their app, they could prevent pairing outside of pairing mode through the app. But most haven't done this.
Current Wild Exploitation: Is This Being Exploited Now?
When Whisper Pair was first disclosed, Google stated they were not aware of any active exploitation in the wild. This is actually credible. The attack requires specialized knowledge, Bluetooth hardware, and you need to target someone specific and be in range of them.
Wildlife exploitation is possible but would likely target specific high-value victims rather than random people. A nation-state actor or sophisticated criminal could definitely use this. But opportunistic widespread exploitation is less likely.
However, the situation changes now that the vulnerability is public. Security researchers have published demonstrations showing how to execute the attack. The technical barrier to entry is much lower once someone shows you exactly how.
This is the classic security researcher dilemma: you've found a real vulnerability, so you report it responsibly. But once it's public, bad actors have a clear roadmap. The expectation is that manufacturers will patch quickly, but we've established that's difficult in the accessories market.
What we'll probably see is a period where the vulnerability exists in millions of devices, patches slowly roll out over months, and security-aware users start looking for alternatives or disabling their accessories.

The Microphone Access Implications: Eavesdropping Risks
The ability to access a device's microphone is perhaps the most concerning aspect of Whisper Pair. Let's think through what this means in practice.
Your headphones have a microphone for calls and voice commands. Once an attacker pairs with your headphones, they can theoretically access that microphone. But importantly, they can only do this if the headphone firmware explicitly allows it. Not all headphones grant microphone access to paired devices.
However, many do. Wireless headphones are designed to handle calls. They're designed to respond to voice commands. For these features to work, the microphone needs to be accessible to paired devices. An attacker who gains trusted device status can potentially leverage this.
The scenario is not that your headphones are always recording. It's that an attacker can access the microphone when they want to, potentially without your knowledge. This could be during a call, during a voice command, or during a period when the microphone is otherwise active.
The ramifications for privacy are severe. If someone eavesdrops on your private conversations, medical consultations, or sensitive business meetings, the damage is real and irreversible. You wouldn't know it happened. You wouldn't see evidence of a breach.
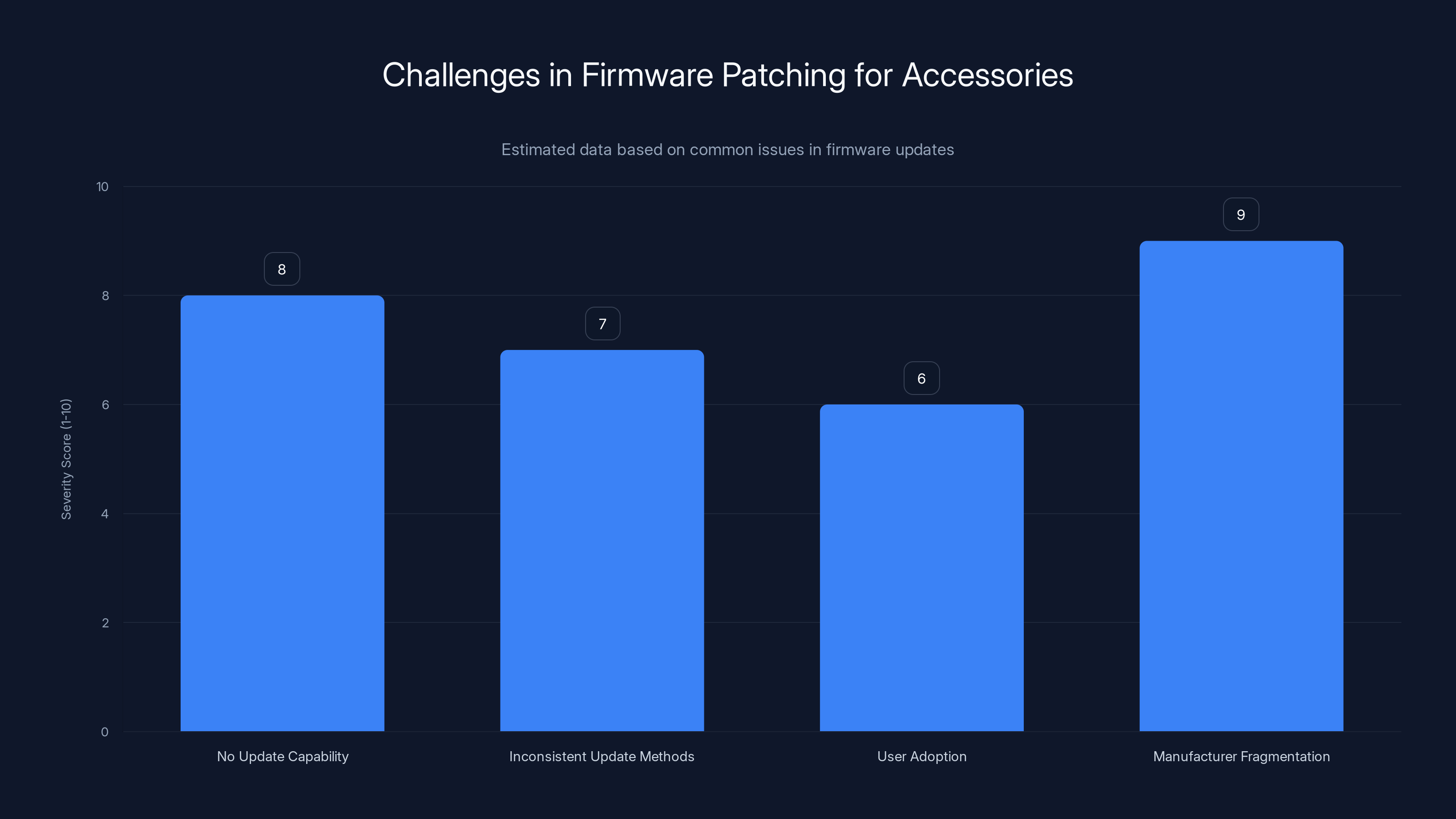
The most severe challenge in firmware patching is manufacturer fragmentation, with a score of 9, indicating significant difficulty in coordinating updates across multiple manufacturers. Estimated data.
Location Tracking Capabilities and Safety Concerns
Many wireless headphones now include location features. Some track the headphones themselves so you can find lost ones. Some integrate with location services for fitness tracking. Some use location for geofencing features.
Once an attacker has hijacked your headphones through Whisper Pair, they can potentially access location data. If your headphones can determine location through GPS, Bluetooth, or Wi-Fi triangulation, an attacker could track you.
This is particularly concerning for vulnerable populations. A victim of stalking or domestic abuse who needs to maintain their location privacy could be tracked through their headphones. Someone using headphones to maintain privacy in an abusive situation could be located.
For personal safety, the implications are serious. Headphones are often on your person. They're often connected to your phone. Tracking the headphones is effectively tracking the user.
Furthermore, an attacker who knows your location, your audio environment (through the microphone), and can inject audio could engage in personalized attacks. They could spoof location-specific alerts or notifications.

Real-World Scenarios: How Whisper Pair Attacks Could Manifest
Let's think through realistic attack scenarios to understand the practical implications.
Scenario 1: Social Engineering Through Audio Injection
An attacker is in a coffee shop where you're working. They detect your headphones using Fast Pair. Within 10 seconds, they've hijacked the connection. They inject audio that sounds like a notification from your bank: "Suspicious activity detected on your account. Please call customer service immediately at [number]." You hear this "notification" and call the number, which is the attacker's line. They convince you to verify your credentials or attempt to trick you into revealing sensitive information.
Scenario 2: Meeting Eavesdropping
You're in a business meeting wearing your wireless headphones. You're not using them to listen to anything at the moment, but they're connected to your phone. Someone in the building has hijacked your headphones and is recording the meeting through the microphone. They're a competitor, a disgruntled employee, or a corporate spy. They capture confidential information about upcoming products, pricing, or business strategy.
Scenario 3: Relationship Privacy Violation
Someone in an unhealthy relationship is using headphones. Their partner suspiciously hijacks the headphones to listen in on private conversations. They can eavesdrop on therapy sessions, conversations with friends about the relationship, or calls to support services. They use this information to maintain control and manipulate their partner.
Scenario 4: Location Stalking
Someone leaves an abusive relationship and moves to a new location. They're still in danger but trying to rebuild their life. An attacker hijacks their headphones and tracks their location through them. The victim doesn't know they're being followed. Their location is compromised despite taking precautions.
Scenario 5: Hotel Room Eavesdropping
You're traveling on business and leave your headphones in your hotel room while you're at meetings. A hotel employee or someone with access to the room hijacks the headphones. They can listen to phone calls you make in the room, conversations with colleagues, or anything else that happens within microphone range.
These scenarios aren't theoretical. Whisper Pair makes them possible. They might not happen frequently, but the vulnerability creates the opportunity.
Device Factory Reset as a Temporary Mitigation
If you suspect your headphones have been hijacked, the only real action you can take right now is to factory reset them. This removes all pairings, essentially wiping the slate clean.
Factory reset usually involves holding a specific button combination for several seconds. The process varies by manufacturer, so you'll need to check your device's manual or website for specific instructions.
After factory reset, the attacker is no longer paired and loses access. But they could potentially pair again if they're still in range and if the device is still vulnerable (it will be, unless a patch has been released and installed).
Factory reset is an inconvenience because you'll need to re-pair your headphones with your phone and any other devices. But if you believe you've been compromised, it's the safest action.
The challenge is knowing whether you've been compromised. There's no way for users to check whether their headphones have extra paired devices. You don't get notifications. There's no log of pairing attempts.
Some people might factory reset regularly out of paranoia. Others won't do it at all and hope they were never targeted.

Estimated data shows exploitation incidents may rise initially as awareness spreads, but decrease as patches are applied over time.
The Importance of Firmware Update Apps: Why They Matter Now
Unfortunately, your best defense right now is boring but important: install the companion app for your headphones and check for updates regularly.
If you have Sony WH-1000XM series headphones, download the Sony Headphones Connect app. If you have JBL headphones, get the JBL Headphones app. If you have One Plus Buds, grab the One Plus Buds app. These apps are usually designed for things like customizing audio profiles or checking battery life, but they're also the mechanism through which firmware updates get delivered.
When a manufacturer releases a Whisper Pair patch, it will come through these apps. Without the app installed, you won't get the patch. Your device will remain vulnerable.
Check for updates weekly if possible. Some apps notify you when updates are available, but notifications aren't always reliable. Proactively opening the app and looking for an "Update" or "Firmware" section is more reliable.
This is inconvenient, and it shouldn't be necessary. Devices should update themselves automatically. But we don't live in that world with accessories. You need to be the one responsible for keeping your headphones patched.
Broader Security Implications: What Whisper Pair Reveals About Io T Security
Whisper Pair isn't just about headphones. It's a symptom of a much larger problem in the Internet of Things ecosystem.
Most Io T devices, from smart home gadgets to wearables to audio accessories, have minimal security infrastructure. Many were designed before security became a priority in consumer devices. Many are built by companies with no history of software security.
Furthermore, Io T devices often persist for years without updates. Unlike phones and computers, which users expect to update regularly, people keep the same headphones, smart home devices, and wearables for years. They rarely think about patches.
This creates a situation where vulnerabilities can persist indefinitely. Whisper Pair might be fixed for new devices, but millions of older devices will remain vulnerable for years because there's no practical way to patch them.
Manufacturers have little incentive to maintain support. Once a device is sold, the manufacturer has earned their revenue. Continuing to develop patches and support infrastructure is ongoing cost with no new revenue.
Users rarely know what to do with updates even if they're offered. They don't know that their device needs security attention. They think it just works and don't question it.
The result is an ecosystem where security is often an afterthought and persistent vulnerabilities are the norm.

Comparing Whisper Pair to Other Bluetooth Vulnerabilities
Whisper Pair isn't the first serious Bluetooth vulnerability, and it won't be the last. Understanding how it compares to previous issues provides context.
KNOB (Key Negotiation of Bluetooth)
In 2019, researchers discovered KNOB, a vulnerability that allowed attackers to downgrade Bluetooth encryption to weak 1-byte keys. This affected essentially all Bluetooth devices made up to that point. Like Whisper Pair, it was a protocol-level issue rather than a bug in a specific implementation.
BLURtooth
Researchers discovered that Bluetooth connection reestablishment could be exploited to inject data into connections without the user's knowledge. This proved that established Bluetooth connections weren't as secure as people assumed.
Sweyntooth
In 2020, researchers found 13 different vulnerabilities affecting Bluetooth Low Energy implementations across multiple vendors. Some of these vulnerabilities caused crashes or could be exploited for denial of service.
What's consistent across these vulnerabilities is that they're protocol-level or implementation-level issues that affect broad categories of devices. Patches are slow. Older devices often never get patched. And users have minimal visibility into whether they're affected.
Whisper Pair follows the same pattern.
How Manufacturers Should Really Implement Fast Pair Securely
From an ideal security perspective, here's how the protocol should work:
First, devices should have a robust pairing mode check. When a pairing request arrives, the device should verify whether it's actually in pairing mode before accepting. This check should be separate from the Bluetooth layer and explicitly implemented.
Second, devices should have a timeout. Pairing mode should automatically disable after 60 seconds or so. If the user hasn't paired something by then, the window closes and you have to manually enable pairing mode again.
Third, there should be user feedback. When entering pairing mode, the device should give some indication (an LED, a sound, a voice announcement). When pairing occurs, there should be notification. Users should know that their device is in a state where it will accept new connections.
Fourth, some kind of out-of-band verification would be helpful. For example, a confirmation step on the phone where the user explicitly taps to approve the pairing.
Finally, security headers and advanced Bluetooth features could be leveraged to make forced pairing more difficult.
The reality is that manufacturers didn't do most of these things. They implemented a minimal version of Fast Pair that prioritized convenience and quick implementation over security.
Moving forward, manufacturers need to understand that security isn't optional. When you're handling user data and access, security must be built in from the start, not added later.
What Happens Next: Timeline for Patches and Long-Term Impact
Here's what we expect to happen in the coming months:
Weeks 1-2: Researchers publish details. Media coverage explodes. Users become aware of the vulnerability. Manufacturers acknowledge the issue. Some companies promise patches "coming soon."
Weeks 3-8: Some manufacturers release patches for their more popular products. Google has already done this for Pixel Buds. Sony, JBL, and others follow gradually.
Months 2-4: Patches for older or less popular products trickle out. Some manufacturers decide certain products are too old and won't receive patches. Some products might be abandoned entirely.
Months 4+: Some percentage of users have updated. A large percentage haven't. Devices that don't have firmware update capability remain vulnerable indefinitely.
In six months, maybe 30-40% of affected devices have been patched. In a year, maybe 50%. But devices without patching capability remain vulnerable forever.
Long-term, this vulnerability reveals the need for better security practices in the accessories market. It might prompt some manufacturers to take security more seriously. It might prompt users to research device security before buying. But it won't fundamentally change how the industry operates unless there's regulatory pressure or market incentives to do so.
Practical Security Best Practices for Wireless Headphone Users
If you use wireless headphones, here are concrete steps to reduce your risk:
Install the Companion App
Find the official app from your headphone manufacturer (Sony, JBL, One Plus, etc.) and install it. Check for firmware updates weekly. Set a calendar reminder if necessary.
Check Your Device Against the Vulnerability List
Go to the KU Leuven research project website and verify whether your specific device model is listed as vulnerable. If it is, prioritize getting updates.
Use Strong Phone Security
Whisper Pair requires pairing with the headphones. If your phone is compromised, an attacker could pair devices remotely. Keep your phone's OS updated and use a strong password.
Be Aware of Your Pairing State
Do you know which devices are paired to your headphones? Could you name them? If you can't, you might have paired devices you don't remember. Periodically check your headphones' paired devices list (access varies by model) and delete any you don't recognize.
Consider Wired Alternatives for Sensitive Situations
If you're in a meeting where you're discussing highly sensitive information, consider wired headphones or no headphones at all. Wired doesn't have these wireless vulnerabilities.
Factory Reset if Suspicious
If you believe you might have been targeted (noticed strange behavior, unexpected sounds, etc.), factory reset your headphones. Re-pair them and monitor for unusual behavior.
Stay Informed
Follow tech security news. If a new vulnerability is discovered affecting your device, you'll know about it before it becomes a widespread problem.
Don't Assume Patches Will Come
If you have older headphones, the manufacturer might not release patches. Know which of your devices likely won't be fixed so you can decide whether to keep using them.

The Bigger Picture: Security Theater vs. Real Protection
One frustration with Whisper Pair is that there's a limit to what users can actually do to protect themselves right now. You can't disable Fast Pair. You can't encrypt headphone communications on your own. You can't prevent pairing hijacking through user behavior.
You're dependent on manufacturers to patch. You're dependent on them to release patches. You're dependent on them to do it quickly. And most importantly, you're dependent on you remembering to install the patches when they come out.
This is a situation where individual responsibility meets systemic failure. The system (accessories manufacturer security) has failed. Users are told they need to protect themselves. But most of the protection requires action from the manufacturers, not the users.
What users need is manufacturers that ship secure devices and provide timely patches automatically. What users have instead is a patchwork of different companies with different security practices and different update mechanisms.
Until there's regulatory pressure or market incentive for better security practices, we'll keep seeing vulnerabilities like Whisper Pair emerge.
Looking Forward: Standards and Regulations
One possible future response to Whisper Pair and similar vulnerabilities is stronger regulations around Io T device security.
The EU has started developing regulations requiring Io T device manufacturers to implement security practices and provide patches for a certain period. The US might follow with similar requirements. Security requirements could eventually be enshrined in law rather than left to manufacturers' discretion.
Alternatively, industry standards organizations might develop stricter certification requirements for devices using Fast Pair or similar protocols. Before a device can use Fast Pair, it would need to pass security review.
Or consumers might vote with their wallets, choosing brands known for security over brands that have been lax. This could incentivize manufacturers to take security more seriously.
More likely, we'll see a combination of all three approaches. Some regulatory pressure, some industry self-regulation, and some consumer preference shift toward security-conscious companies.
But in the short term, individuals need to be aware of Whisper Pair, take steps to protect themselves, and hope manufacturers patch quickly.
FAQ
What is Whisper Pair and how does it differ from other Bluetooth vulnerabilities?
Whisper Pair is a vulnerability in how many manufacturers implement Google's Fast Pair protocol that allows attackers to hijack Bluetooth accessories like headphones. Unlike some other Bluetooth vulnerabilities that target the underlying Bluetooth protocol itself, Whisper Pair specifically exploits incomplete implementations of Fast Pair's pairing mode verification mechanism. The vulnerability allows attackers to force a pairing connection with devices that should reject the request but fail to perform proper validation.
How long does it take for an attacker to hijack my headphones using Whisper Pair?
Researchers demonstrated that Whisper Pair can hijack vulnerable devices in a median time of just 10 seconds. The attack works from distances up to 14 meters, which is near the maximum range of Bluetooth. This means an attacker could be far enough away that you wouldn't see them while they're exploiting your headphones. The speed and range make it a practical attack that could target someone without their knowledge or consent.
Which specific devices are vulnerable to Whisper Pair?
Whisper Pair affects devices from at least 10 manufacturers including Google (Pixel Buds Pro and Pro 2), Sony (WF and WH series), JBL, One Plus Buds, Nothing Ear, Soundcore, Edifier, Anker, and others. Not all devices from these manufacturers are vulnerable, typically only specific product lines or generations. The research team has published a comprehensive list of affected models on their project website, and you should check if your specific model is listed before assuming your device is safe.
What can attackers do once they've hijacked my headphones through Whisper Pair?
Once successfully paired through Whisper Pair, attackers can interrupt your audio playback, inject audio of their choice, access your headphone's microphone to eavesdrop on conversations, and track your location if your device supports location services. They cannot perform every action (permission boundaries still exist), but these capabilities are serious enough to enable eavesdropping on private conversations, location-based tracking, and social engineering through injected audio.
Can I disable Google Fast Pair to prevent Whisper Pair attacks?
Unfortunately, there is no user-facing setting to disable Fast Pair on supported devices. Fast Pair is built directly into the Bluetooth implementation and cannot be toggled off in device settings. Your only real option is to either wait for manufacturers to release security patches through firmware updates or to not use devices that support Fast Pair—though as the protocol becomes more common, avoiding it entirely becomes increasingly impractical.
What should I do if I think my headphones have been hijacked?
If you suspect your headphones have been compromised, the best immediate action is to perform a factory reset. This removes all pairings and disconnects any attackers. After resetting, you'll need to re-pair your headphones with your devices, but this breaks the attacker's connection. However, if your device remains unpatched and the attacker is still in range, they could attempt to hijack again. The long-term solution is to ensure your device receives and installs the security patches from your manufacturer.
When will manufacturers release patches for Whisper Pair?
Google has already released patches for its own Pixel Buds devices, though researchers have found workarounds for even these patches. Other manufacturers are in various stages of developing fixes. Some companies move quickly and will have patches available within weeks. Others may take months. Some older devices or smaller manufacturers might not release patches at all due to development costs and limited support for older products. The timeline varies significantly by manufacturer and product, so check your device's official support page for update availability.
How do I make sure my headphones get security updates?
Most headphone manufacturers deliver firmware updates through official mobile apps (Sony Headphones Connect, JBL Headphones, etc.). Install the app for your specific headphone model and check for updates weekly. Most apps have an update or settings section where you can check and install new firmware. Without the app installed, you likely won't receive patches automatically. Set a calendar reminder if needed to regularly check for updates until your device receives the Whisper Pair patch.
Is Whisper Pair currently being exploited in the wild?
Google stated they were not aware of active Whisper Pair exploitation in the wild at the time of disclosure. However, now that technical details are public and demonstrations are available, the barrier to entry for attacks has lowered significantly. Exploitation is more likely to target specific high-value individuals rather than random victims, as the attack requires an attacker to be in proximity to their target. The vulnerability could be used by sophisticated actors for targeted surveillance or eavesdropping.
What are the privacy implications of Whisper Pair's microphone access?
Whisper Pair allows attackers to potentially access your headphones' microphone, enabling them to eavesdrop on private conversations without your knowledge. This is particularly concerning for sensitive contexts like private meetings, medical consultations, therapy sessions, confidential business discussions, or personal phone calls. An attacker could listen to conversations happening near your headphones while you're completely unaware they've hijacked the device, representing a serious privacy violation.
Moving Forward: Your Action Plan
Whisper Pair is a reminder that convenience and security often exist in tension. Google Fast Pair makes Bluetooth pairing dramatically easier, which is valuable. But that convenience came with security tradeoffs that manufacturers didn't implement correctly.
Right now, you're in a period of vulnerability. Manufacturers are slowly releasing patches. Some devices will never be patched. Users like you are trying to figure out what to do.
Here's what I recommend: First, check if your device is vulnerable by looking up your specific model on the research team's list. Second, download and install the official app from your headphone manufacturer if you haven't already. Third, check for firmware updates in that app weekly. Fourth, if updates are available, install them immediately.
Beyond that, stay aware. If you're in a situation where you're discussing highly sensitive information, consider whether wireless headphones with all their connected features make sense. Sometimes a wired option might be more appropriate.
Long-term, manufacturers need to build security into devices from the start, not add it as an afterthought. Users need access to timely updates. Regulators might need to enforce security requirements. But those changes take time.
In the meantime, understand the risk, take reasonable precautions, and advocate for better security practices from manufacturers. That's the realistic path forward.
The silver lining, if there is one, is that Whisper Pair being disclosed publicly creates pressure for real change. Manufacturers face reputational damage. Users become aware of the risks. Industry practices evolve. Sometimes vulnerabilities are the catalyst for meaningful improvement.
But that improvement has to come from action. Stay informed. Apply patches. Demand better from manufacturers. That's how we make the accessories ecosystem more secure.
Key Takeaways
- WhisperPair allows attackers to hijack Bluetooth Fast Pair devices in just 10 seconds from up to 14 meters away
- Over 10 major manufacturers have vulnerable devices including Google, Sony, JBL, OnePlus, and Nothing
- Once hijacked, attackers can access microphones for eavesdropping and location data for tracking without user awareness
- You cannot disable Fast Pair, and patches are rolling out slowly with some devices never receiving security updates
- Install manufacturer apps and check for firmware updates weekly as your best defense while waiting for patches
Related Articles
- Fast Pair Bluetooth Vulnerability: Why 300M Devices Need Patching [2025]
- Microsoft Copilot Prompt Injection Attack: What You Need to Know [2025]
- NordVPN vs Proton VPN 2025: Complete Comparison Guide
- Jen Easterly Leads RSA Conference Into AI Security Era [2025]
- 45 Million French Records Leaked: What Happened & How to Protect Yourself [2025]
- Tea App's Comeback: Privacy, AI, and Dating Safety [2025]
![WhisperPair Bluetooth Hack: Complete Security Guide [2025]](https://tryrunable.com/blog/whisperpair-bluetooth-hack-complete-security-guide-2025/image-1-1768500439017.jpg)



