The Leadership Transition That Could Reshape Cybersecurity's Future
Jen Easterly's appointment as CEO of RSA Conference represents far more than a typical executive leadership change. It's a signal moment for an industry grappling with existential questions: How do we secure artificial intelligence? How do we rebuild trust between government and the private sector? And what does cybersecurity leadership look like when the political landscape shifts beneath our feet?
Easterly isn't new to high-stakes transitions. She spent more than three years leading the Cybersecurity and Infrastructure Security Agency (CISA), where she oversaw some of the most contentious security initiatives in recent American history. Before CISA, she spent five years as Morgan Stanley's global chief information security officer, modernizing security operations at one of the world's largest financial institutions. She's also held roles at the National Security Agency and helped establish the US Cyber Command at the Department of Defense.
What makes this moment particularly interesting isn't just her resume. It's the timing. Cybersecurity is at an inflection point. AI tools are simultaneously making attackers more dangerous and defenders more capable. Election security remains politically fraught. Supply chain attacks are becoming more sophisticated. And a new administration in Washington is signaling significant changes to how the federal government approaches cybersecurity partnerships.
For decades, RSA Conference has positioned itself as the industry's neutral ground. When thousands of security professionals, researchers, policymakers, and vendors gather each spring in San Francisco, they're supposed to set aside politics and focus on shared technical challenges. Easterly's hiring suggests the organization is doubling down on that mission—even as the external political environment makes that neutrality harder to maintain.
Understanding CISA's Role and Why It Matters
To understand why Easterly's move matters, you need to understand what CISA does and why it became controversial.
CISA was established in 2018 as a division of the Department of Homeland Security. Its mission: protect civilian federal infrastructure and critical infrastructure from cyberattacks. That's a broad mandate. It includes everything from helping water utilities secure their systems to advising hospitals about ransomware defense to protecting the electoral infrastructure that runs American elections.
Under Easterly's leadership from 2021 to 2024, CISA became more visible and more active. The agency released advisories within hours of new vulnerabilities. It launched programs to help small businesses improve security. It coordinated with election officials to protect voting systems and infrastructure. It worked with software companies to address supply chain risks.
That last part—election security—is where Easterly found herself caught between technical necessity and political controversy. After the 2020 election, CISA helped coordinate security improvements across state and local election systems. This work was universally praised by election security experts as essential. But it became politically polarized. The Trump administration and its allies criticized CISA's election security work, with Trump calling it the "most secure election in American history"—meant as sarcasm, not praise.
When Easterly took office at CISA in 2021 under the Biden administration, she inherited significant relationships with state election officials and vendors. She expanded CISA's capabilities and visibility. She also made clear that CISA viewed election security as critical infrastructure protection, not politics.
But when the Trump administration took office again in January 2025, it didn't ask Easterly to stay. In fact, in July 2024, the Army rescinded a job offer that would have made Easterly a distinguished chair at West Point, after media reports and criticism from Trump allies. The message was clear: Easterly's previous work, particularly on election security, was being viewed through a partisan lens.
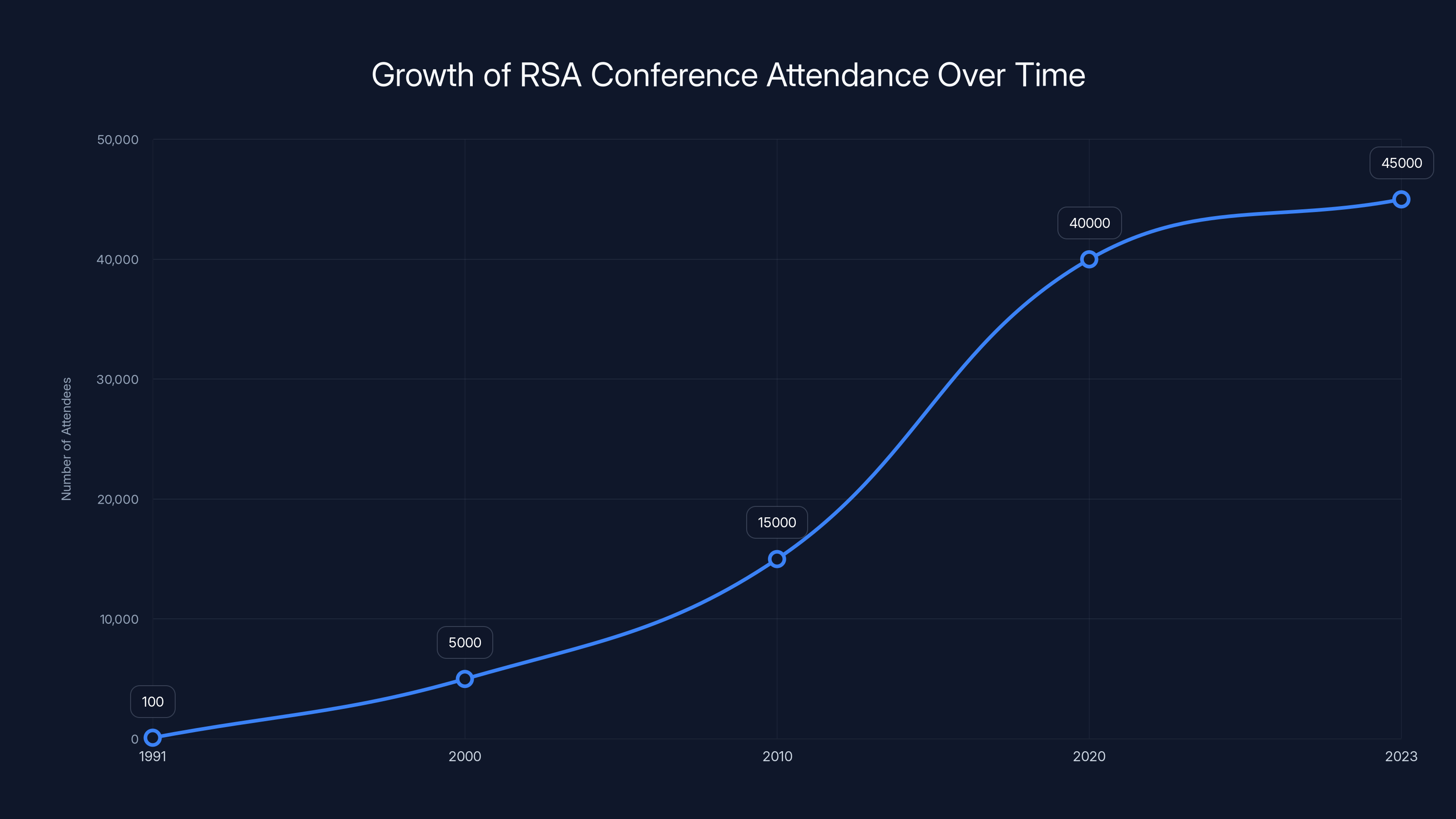
The RSA Conference has grown from a small gathering in 1991 to attracting tens of thousands of attendees by 2023, reflecting its increasing influence in the cybersecurity industry. Estimated data based on historical trends.
The Controversy Surrounding Election Security Leadership
The pushback against Easterly and CISA's election security work deserves deeper examination, because it illustrates a broader challenge facing cybersecurity professionals: how to do technical work when it becomes politicized.
Election security is genuinely technical. Voting systems use outdated software, often running on Windows 7 or earlier. Poll books that register voters use different systems across different states, creating integration challenges. Election officials face severe budget constraints. And foreign adversaries have repeatedly attempted to intrude into election-related systems.
CISA's work to secure these systems involved installing better monitoring, helping states implement voter registration database security, advising on supply chain risks when purchasing voting equipment, and coordinating information sharing about threats.
None of this is controversial from a security standpoint. Election officials across the political spectrum wanted this help. But the optics became toxic. When Trump claimed the 2020 election was stolen, and when CISA actively contradicted that claim (calling it "the most secure election in American history"), the agency became seen as taking a political position rather than a technical one.
This is the core tension that Easterly must navigate at RSA Conference. How do you bring together security professionals and policymakers from a Trump administration that's hostile to your predecessor's work, while maintaining the fiction that cybersecurity is apolitical?
Easterly's statement on this is worth parsing carefully. She emphasized that she approaches her new role "not through the lens of fear and speculation" but with "relentless optimism and belief in the power of community." She noted that cybersecurity "crosses all administrations and borders." She committed to welcoming government officials "of all governments" to contribute to RSAC's forums.
In other words, she's signaling that RSA Conference will remain a neutral venue. She's also signaling that she's not going to fight her predecessor's battles or defend the previous administration's policies. She's moving forward.
Whether that's possible without pretending the previous controversies didn't exist remains to be seen.
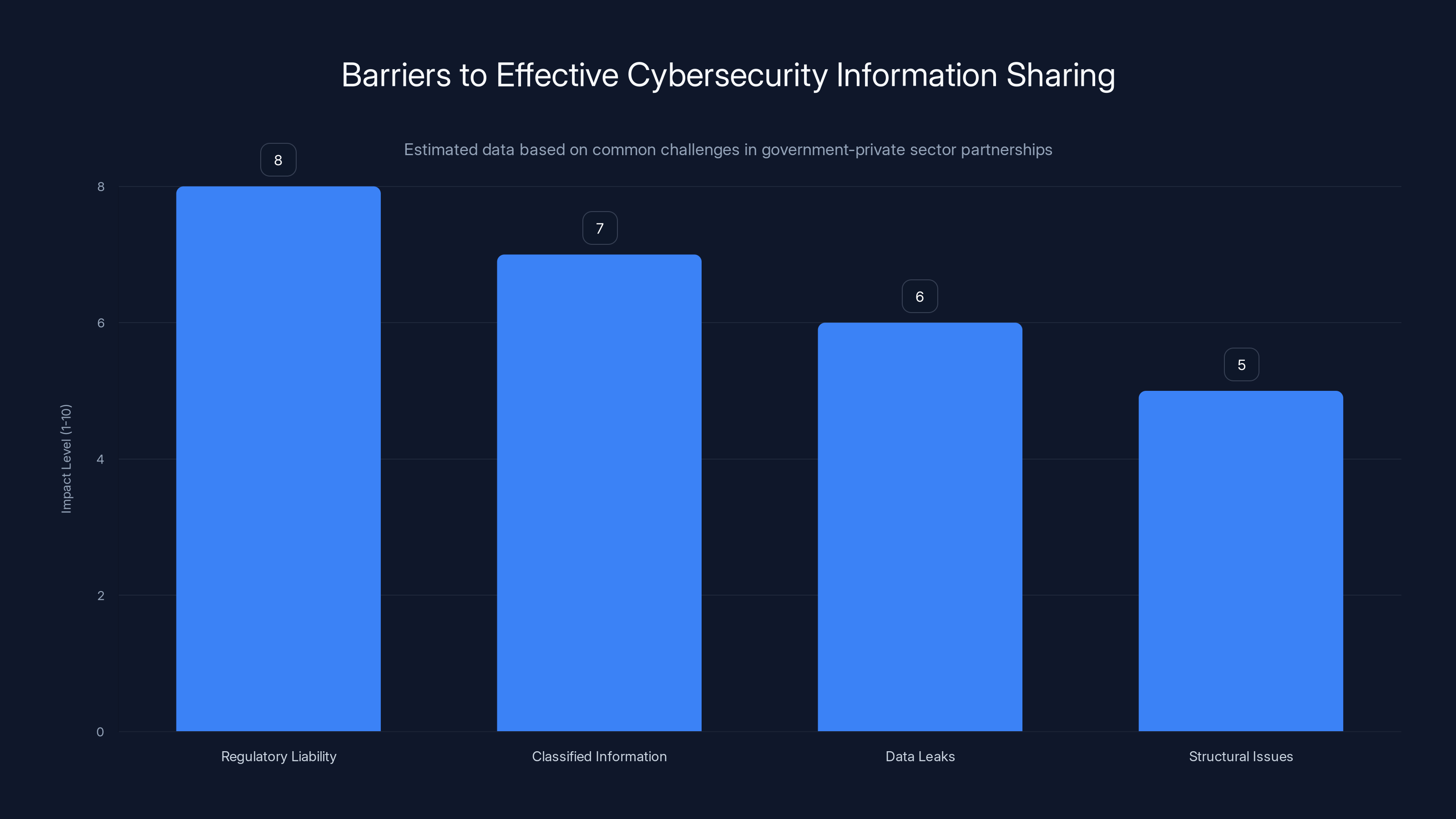
The chart highlights key barriers to effective information sharing between government and private sectors in cybersecurity, with regulatory liability being the most significant. Estimated data.
RSA Conference: History, Scale, and Influence
To understand the importance of Easterly's appointment, you need to understand RSA Conference itself and why it matters to the cybersecurity industry.
RSA Conference started in 1991 as a small gathering of cryptographers. It was hosted by RSA Laboratories, the research division of RSA Security Inc., and focused on advances in cryptography. Back then, public discussion of encryption algorithms was genuinely cutting-edge. The field was small enough that you could fit everyone interested in mathematical cryptography into a single room.
The internet changed that. As the web exploded in the 1990s, cybersecurity became critical to commerce, government, and infrastructure. RSA Conference grew. By the 2000s, it had become the major annual gathering of the cybersecurity industry. Vendors displayed products. Researchers presented findings. Government officials spoke about policy. Vendors pitched solutions. Job seekers networked with employers.
Today, RSA Conference in San Francisco draws tens of thousands of attendees each spring. That's tens of thousands of security engineers, information security leaders, researchers, vendors, policymakers, and journalists. The main conference runs for several days. The expo floor features hundreds of vendors. Hundreds of sessions cover everything from cloud security to AI to supply chain risk management to elections.
This scale gives RSA Conference outsized influence in cybersecurity. When a researcher presents a new vulnerability, other security professionals learn about it. When government officials speak, they're often broadcasting policy priorities. When vendors showcase products, the market responds. When security leaders give keynote speeches, the industry pays attention.
RSA Conference is also specifically positioned as a neutral venue. Unlike some industry conferences that are explicitly vendor-focused or government-focused, RSAC includes everyone. It's a rare place where security professionals from competing vendors, from government agencies, from academia, and from the financial sector all gather.
That neutrality is what makes Easterly's hiring significant. The organization is essentially saying: we want leadership that can bridge divides, maintain credibility across the political spectrum, and uphold the principle that cybersecurity is fundamentally technical, not political.

The AI Security Challenge That Defined Her Timing
Easterly's appointment arrives precisely when the cybersecurity industry is grappling with AI security—perhaps the most significant technical challenge since cloud computing.
The challenge is dual-sided. On one hand, AI tools are making attackers more dangerous. Large language models can help threat actors write more convincing phishing emails, identify vulnerable infrastructure, and automate reconnaissance. Generative AI could accelerate the development of malware. An attacker armed with AI tools can accomplish in hours what used to take weeks.
On the other hand, AI is also making defenders more capable. Machine learning models can identify anomalous network traffic faster than human analysts. AI-powered security information and event management (SIEM) systems can correlate events across massive datasets. Automated threat response can execute defensive actions in milliseconds. The most sophisticated security operations centers are already integrating AI to augment human analysts.
But there's a meta-challenge: the systems being protected include the AI systems themselves. How do you secure an AI model against poisoning attacks where an attacker influences training data? How do you prevent an AI system from producing biased security decisions? How do you audit an AI system's decision-making when it's essentially a black box? How do you guarantee that an AI system won't be manipulated by adversaries who understand its vulnerabilities?
These aren't merely technical questions. They have policy implications. If a bank's loan-approval AI makes biased decisions, that's both a security issue and a regulatory issue. If a government's AI system for detecting critical infrastructure threats can be fooled, that's both a technical problem and a national security problem.
Easterly's background makes her particularly suited to bridging these domains. She's spent her career at the intersection of technical security and policy. At CISA, she saw how security technical decisions become policy issues. At Morgan Stanley, she saw how security decisions affect business decisions and regulatory compliance.
RSA Conference will inevitably become a primary venue for discussing AI security. With Easterly leading, there's reason to believe those discussions will be sophisticated, balanced, and bridge the gap between technical practitioners and policymakers.
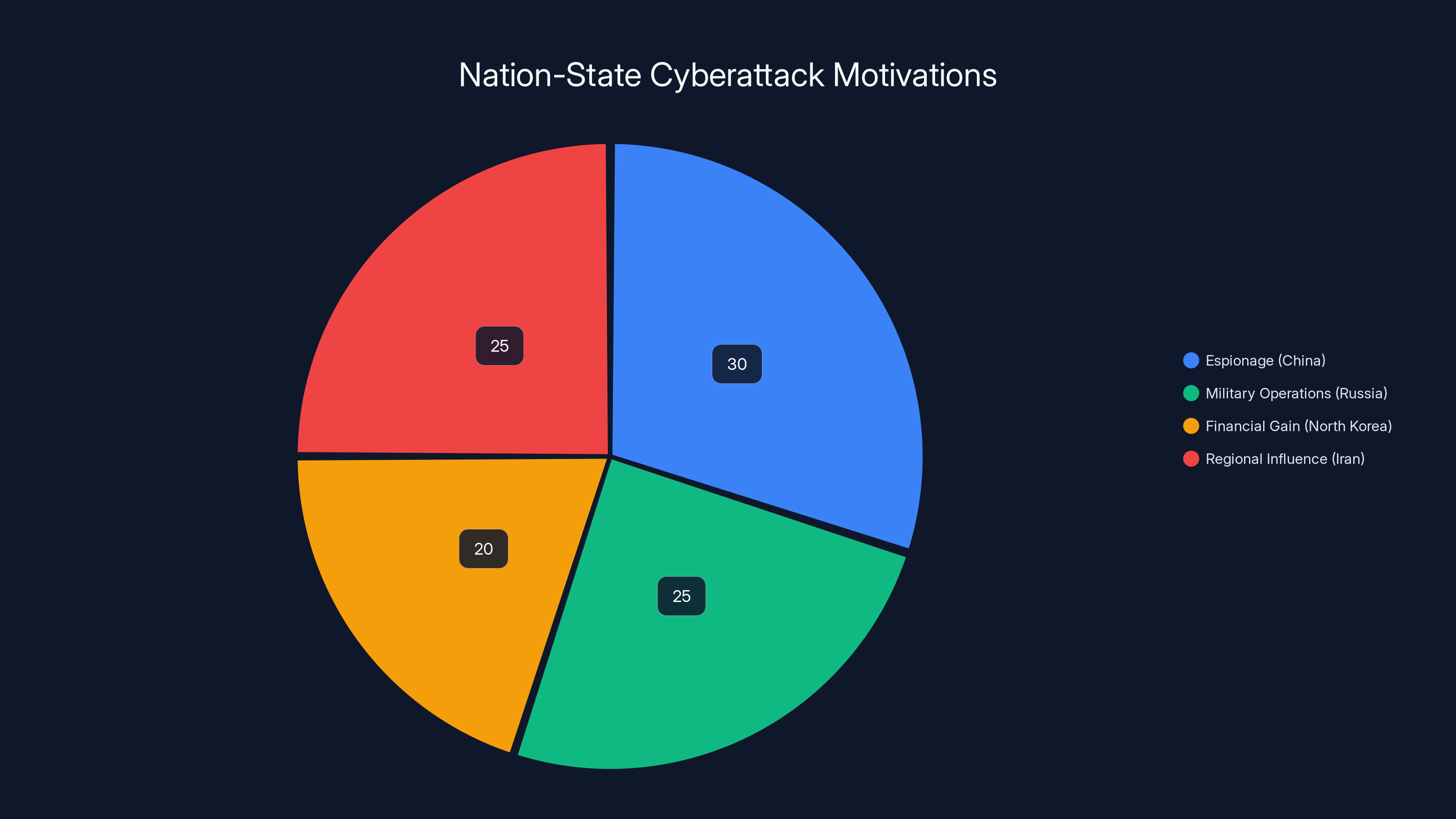
Estimated data shows varied motivations for cyberattacks by nation-states, with espionage and military operations being prominent. Estimated data.
Supply Chain Security: A Decade-Long Challenge
Another defining theme of Easterly's career—and likely a focus area under her leadership at RSAC—is supply chain security. This is one of the most intractable problems in cybersecurity, and it's gotten worse over the past decade.
Supply chain attacks happen when an attacker compromises a vendor or supplier, then uses that access to compromise the vendor's customers. A famous example: in 2020, attackers compromised SolarWinds, a widely-used network management software company. SolarWinds' software was used by thousands of organizations, including U.S. government agencies. Attackers inserted malicious code into a legitimate SolarWinds software update. When organizations installed the update, they installed malware.
The scale of the SolarWinds breach was extraordinary. Hackers gained access to U.S. Treasury Department systems, U.S. Commerce Department systems, multiple federal agencies, and countless private companies. The assessment took months. The cleanup took years.
Since SolarWinds, the software industry has gotten significantly better at security. But the problem hasn't gone away, it's evolved. Now we see attacks through vulnerable open-source libraries that are embedded in millions of applications. We see attacks through hardware supply chains. We see attacks where adversaries compromise the build systems that developers use to compile code.
Easterly saw this challenge firsthand at Morgan Stanley. Large financial institutions depend on thousands of software vendors. Every vendor is a potential attack vector. The largest banks now have entire teams dedicated to vendor risk management, evaluating vendors' security practices, monitoring for breaches, and designing contracts that push security responsibility downstream.
At CISA, Easterly pushed the federal government to implement similar vendor risk management. She emphasized the importance of "secure software development practices" and pushed vendors to implement security-first coding, automated testing, and rigorous code review.
Under her leadership at RSAC, you can expect supply chain security to remain a central theme. RSAC's forums will likely feature discussions about industry standards for vendor security assessments, best practices for software bill of materials (SBOM), and how organizations can reduce their supply chain risk.
This is practical, unglamorous work, but it's the kind of thing that actually prevents breaches.
The Role of Government Partnerships in Cybersecurity
One of the most contentious issues facing cybersecurity is the relationship between government agencies and the private sector. This relationship is crucial for national security but complicated by misaligned incentives, classified information, and competing priorities.
Historically, government and private-sector cybersecurity have operated in separate domains. Government agencies had their own networks, their own security practices, and their own classified threat intelligence. Private companies had their own security operations and their own threat intelligence.
But infrastructure interdependence broke down this separation. When a hospital's computer system is hacked and patients can't access records, that's a national security issue (hospitals are critical infrastructure). When a power grid is compromised, that affects everyone. When telecommunications systems are disrupted, that's a national crisis.
So government and private sector must coordinate. Information sharing is essential—government agencies have visibility into nation-state threats that private companies don't, while private companies have visibility into techniques and tools that criminals and nation-states are using that government doesn't.
But information sharing is complicated. Private companies worry about regulatory liability. Government agencies worry about classified information. Both worry about the other side leaking sensitive information. There are also structural issues: if you report a breach to government, will that trigger regulatory investigations?
CISA worked to address these issues by creating information-sharing mechanisms that protect companies from liability. The Cybersecurity Information Sharing Act (CISA) of 2015 was one attempt. CISA created "automatic exemptions" from liability for companies that shared cyber threat indicators with the government.
But information sharing has been inadequate. Many companies still don't report breaches quickly to government. Many government agencies don't have the capacity to receive and act on threat intelligence from the private sector.
Easterly's task at RSAC is to revitalize these partnerships without pretending that the previous administration's skepticism about government partnerships didn't exist. Some in the Trump administration view government-private-sector partnerships suspiciously, seeing them as either corporate welfare or government overreach.
Easterly's approach will likely emphasize mutual benefit: private companies benefit from government threat intelligence, and government benefits from understanding private-sector threats. She's likely to de-emphasize the aspects of partnership that sound like government mandates or restrictions.

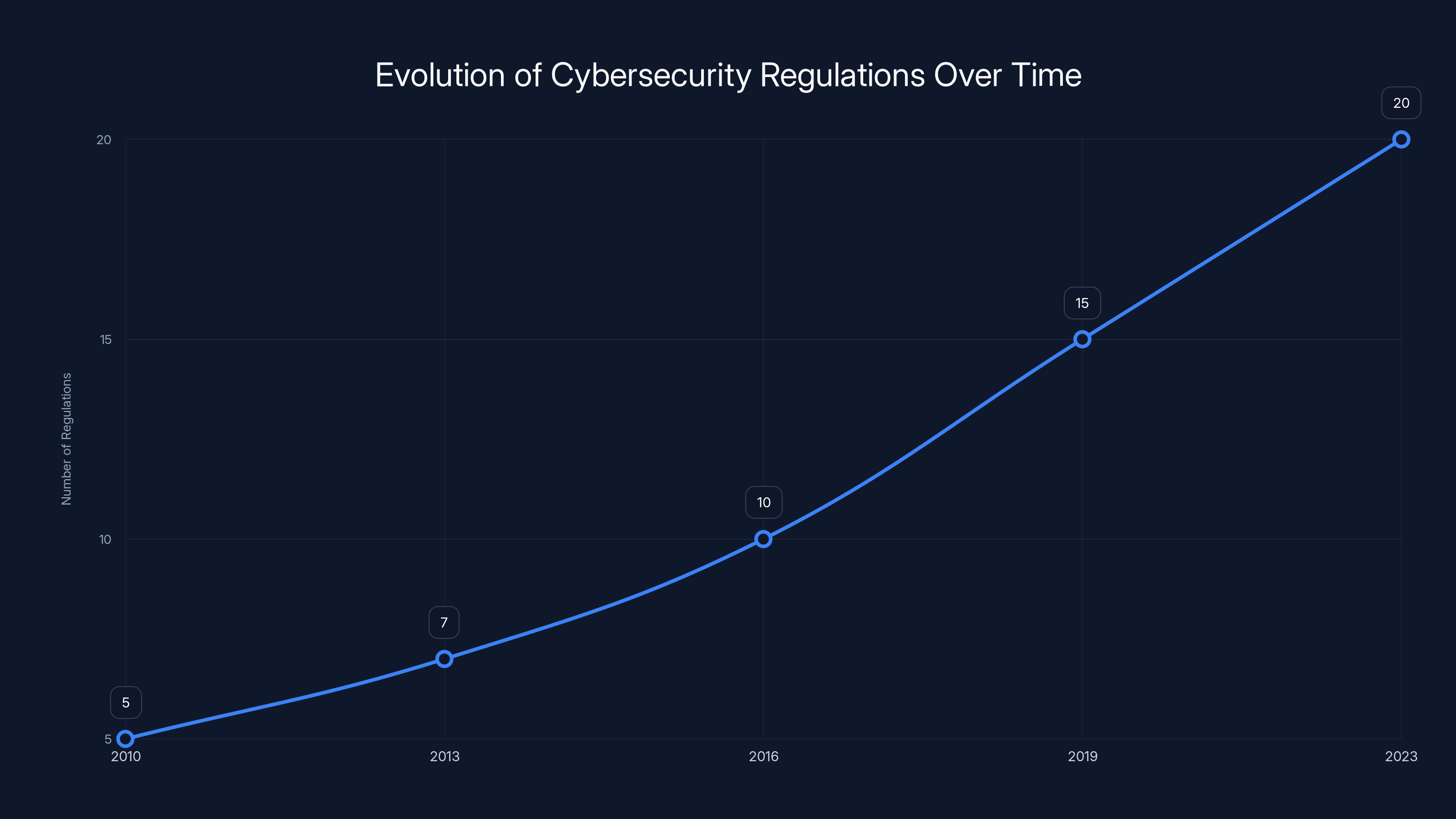
The number of major cybersecurity regulations has steadily increased over the past decade, reflecting a growing emphasis on comprehensive security measures. (Estimated data)
Rebuilding Trust in Cybersecurity Leadership
One of the most important challenges Easterly faces is rebuilding trust. Trust in cybersecurity has been eroded over the past few years for several reasons.
First, there's distrust from the security community toward government. Cybersecurity professionals have watched government agencies struggle with basic security hygiene. The Office of Personnel Management breach exposed security clearances and background investigation data for millions of people. The Twitter/X compromise showed how easily government accounts can be breached. There's a perception that government lags private sector in security sophistication, which makes government mandates about security seem like they're coming from a less sophisticated actor.
Second, there's distrust from government toward the security industry. Government officials have watched security vendors overhype threats, oversell solutions, and fail to deliver on promises. The security industry has a well-earned reputation for fear-mongering. Vendors warn about catastrophic threats, then their solutions don't fully address the threats.
Third, there's distrust from the public toward government cybersecurity. The Edward Snowden revelations showed the scale of government surveillance. The election security controversies showed how partisan concerns can color government security priorities. There's skepticism about whether government is actually trying to protect citizens or surveille them.
Easterly's reputation as a trust-builder is relevant here. At Morgan Stanley, she was known for straight talk about risks and realistic expectations about what security can and can't do. At CISA, she emphasized transparency—CISA publishes its advisories publicly, shares threat intelligence publicly, and doesn't hide behind classification.
At RSAC, Easterly will likely emphasize that trust is built through transparency, consistency, and honesty. She's likely to acknowledge past failures and disagreements rather than pretend they didn't happen. She's likely to position RSAC not as a government mouthpiece but as a forum where tough conversations about government policy, private-sector responsibility, and technical best practices can happen.

The Shift From Breach Response to Prevention
Another significant theme in cybersecurity over the past decade has been a shift from breach response to breach prevention.
Historically, cybersecurity operated on a reactive model: companies would get breached, would discover the breach after some period, would respond to the breach, and would learn lessons. Security investments focused on detection and incident response—how do you find attackers after they've penetrated your network, and how do you remove them?
But the economics of this model are backwards. A major breach costs millions or tens of millions of dollars. Prevention investments are orders of magnitude cheaper. If you can prevent a breach for
Over the past decade, the security industry has shifted toward prevention models: secure development practices to prevent vulnerabilities from being introduced, vulnerability management to find and fix vulnerabilities before they're exploited, threat hunting to proactively search for adversaries before they cause damage, and continuous security testing to maintain security posture.
Easterly's background reflects this shift. At Morgan Stanley, she implemented continuous security testing and vulnerability management programs that reduced the attack surface significantly. At CISA, she promoted secure coding practices and vulnerability management for federal agencies.
Under Easterly's leadership, RSAC will likely emphasize prevention-focused approaches. You can expect sessions on secure development practices, supply chain security, vulnerability management, and threat hunting. The industry is moving in this direction anyway, but leadership signals matter. When the head of RSA Conference emphasizes prevention over response, vendors adjust their messages, and practitioners adjust their priorities.

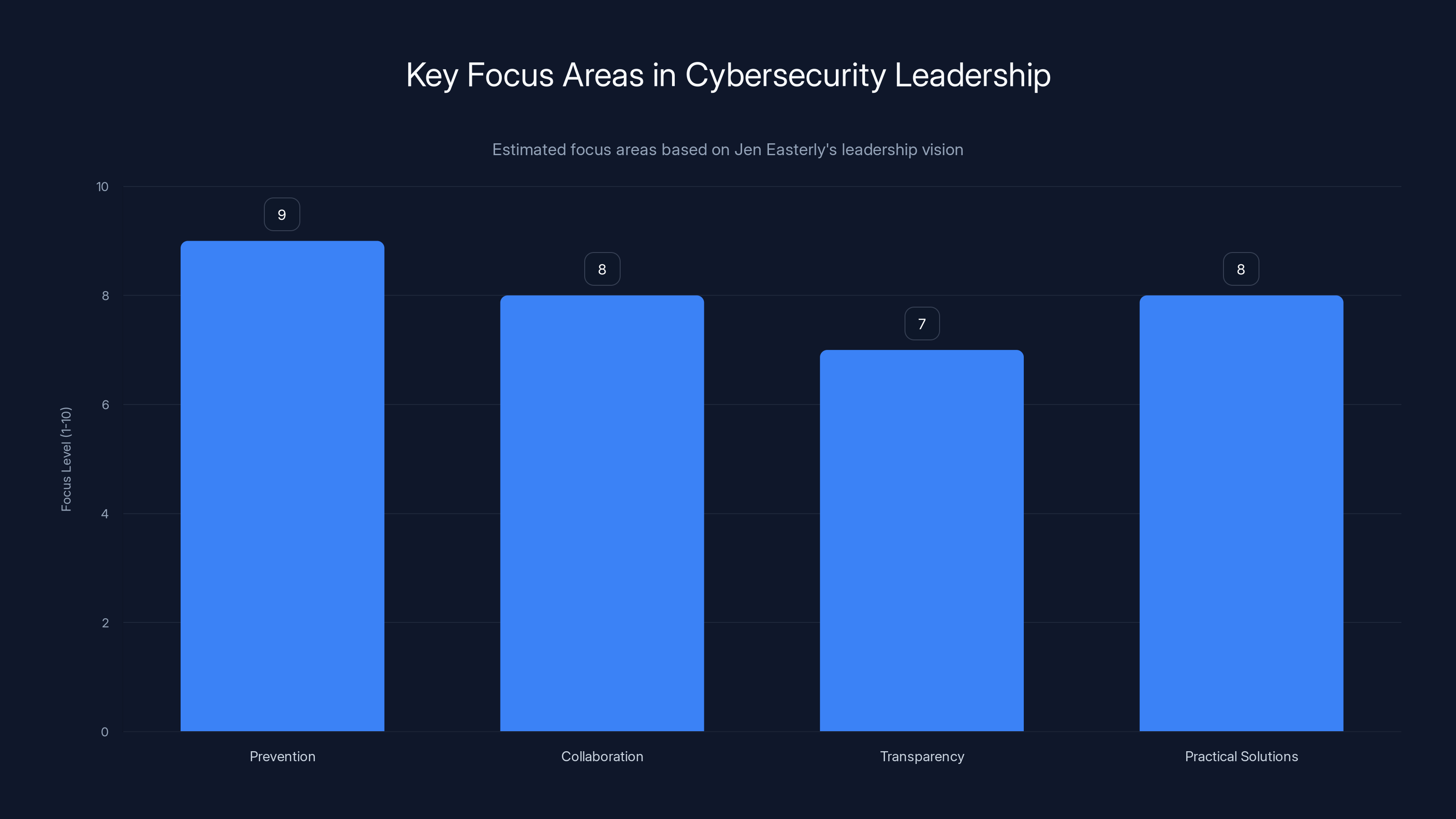
Jen Easterly's leadership emphasizes prevention, collaboration, transparency, and practical solutions in cybersecurity. Estimated data based on her career focus.
The Geopolitical Dimension of Cybersecurity
One aspect of Easterly's work that often gets overlooked is the geopolitical dimension. Cybersecurity isn't just about defending networks; it's also about international relations, espionage, and power dynamics between nations.
Cyberattacks by nation-states are routine. China's Ministry of State Security conducts continuous espionage against U.S. companies and government agencies. Russia uses cyberattacks as part of its military operations. North Korea uses cyberattacks to finance its government. Iran uses cyberattacks to target adversaries in the Middle East.
Understanding these nation-state threats requires geopolitical context. When CISA warns about a particular threat, it's often because a particular nation-state is conducting that attack. When the agency recommends certain defensive measures, it's often because those measures are effective against particular nations' tools and tactics.
But discussing nation-state cyber activity is inherently political. The Trump administration has taken a different approach to geopolitical challenges than the Biden administration. It's skeptical of alliances, more confrontational toward China, and more accommodating toward Russia. These differences affect how government approaches cybersecurity against nation-states.
Easterly will need to navigate this carefully at RSAC. The conference can discuss technical details of nation-state attacks without endorsing particular foreign policies. But the geopolitical context always lurks underneath.
One approach: focus on defensive measures that are effective regardless of which nation-state is attacking. RSAC can host technical discussions about counter-intelligence, defensive technologies, and resilience-building that don't require political consensus.

Emerging Threats: Ransomware, Extortion, and Evolving Tactics
One of the most pressing cybersecurity challenges facing organizations today is ransomware. This has been a growing threat for over a decade, but the scale and sophistication have evolved dramatically.
Ransomware is malware that encrypts an organization's data and demands payment for a decryption key. Originally, ransomware targeted individuals—criminals would encrypt someone's photos and demand a small payment. But over time, it evolved to target organizations, particularly hospitals, municipalities, and businesses where downtime is extremely expensive.
The economics of ransomware are perverse. If a hospital's systems are encrypted and patients can't access records, the hospital faces pressure to pay the ransom. A municipality facing ransomware might pay rather than rebuild systems. A business might pay rather than face extended downtime.
With those economics in place, ransomware became a lucrative criminal business. Organized crime groups emerged that specialized in ransomware. Some operate like legitimate businesses, with customer support, negotiations, and payment processing. Some have even published rules of conduct (don't attack hospitals, don't attack critical infrastructure).
But the threat has evolved further. Now ransomware operators don't just encrypt data, they exfiltrate it. They steal sensitive data and then threaten to release it publicly unless the organization pays. This "double extortion" approach works even against organizations with good backups (you can restore from backup to recover from encryption, but you can't recover stolen data).
CISA tracked these trends closely. Under Easterly's leadership, CISA published advisories about ransomware threats, coordinated responses to major ransomware attacks, and worked with law enforcement to disrupt ransomware operations.
At RSAC, ransomware will certainly be a major theme. Easterly is likely to emphasize: the importance of backups, the need to segment networks so ransomware doesn't spread, the value of threat intelligence about ransomware operators, and the critical importance of law enforcement collaboration to disrupt ransomware as a business.
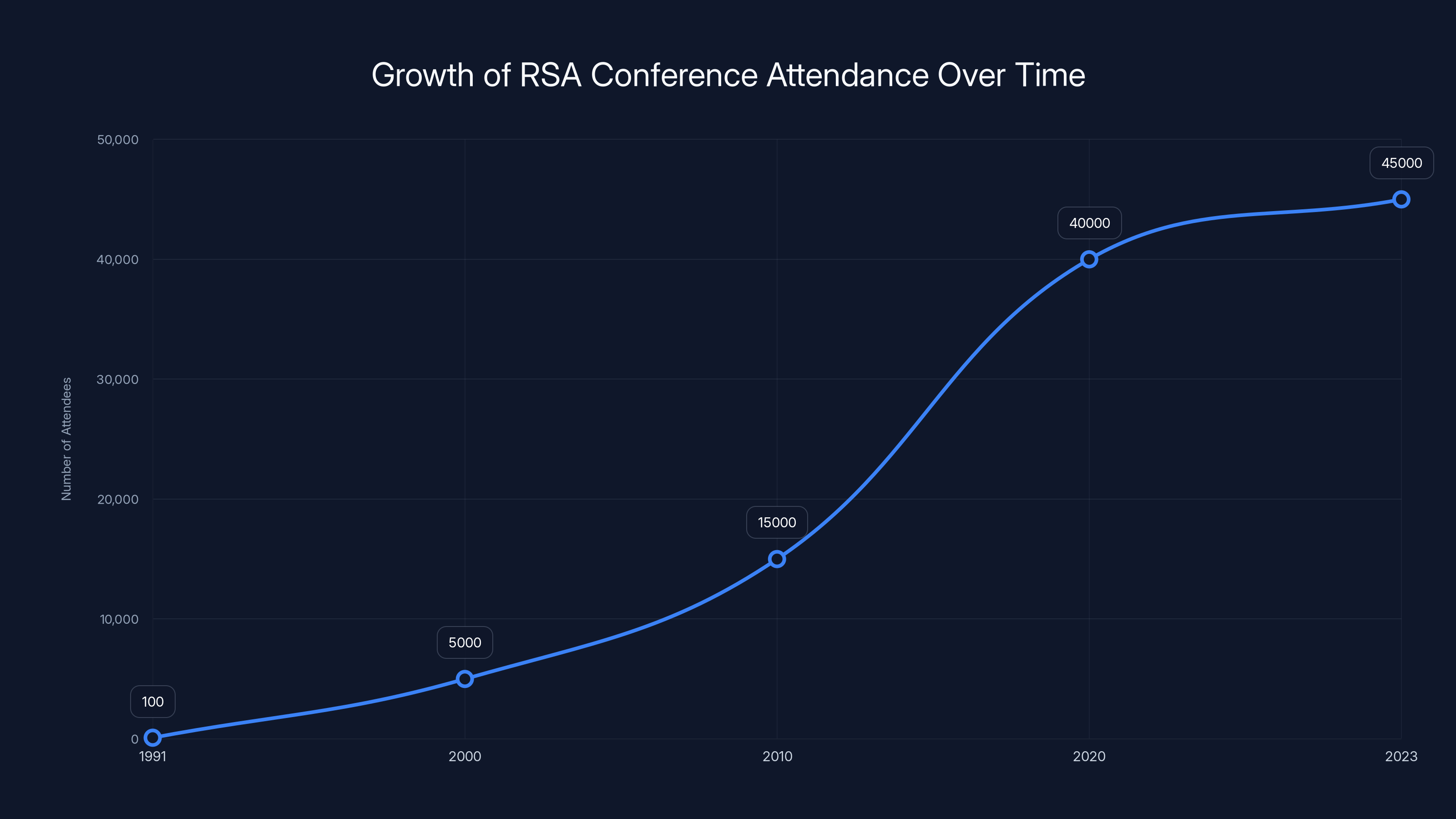
The RSA Conference has seen significant growth since its inception in 1991, evolving from a small cryptography event to a major cybersecurity forum with tens of thousands of attendees. (Estimated data)
Organizational Security: Building Resilient Security Cultures
Beyond the technical and geopolitical dimensions, there's the organizational dimension: how do you build security cultures within organizations that make security everyone's responsibility, not just the security team's?
This is perhaps the most underrated aspect of cybersecurity. You can have the best technology in the world, but if employees click on phishing emails, fall for social engineering, or leave sensitive data exposed, technology won't protect you.
Easterly has thought deeply about this throughout her career. At Morgan Stanley, she worked on making security a part of the organizational culture, not something imposed from outside. At CISA, she emphasized the importance of public-private partnerships and working with organizations rather than imposing mandates.
Building security cultures involves several components: clear policies that employees understand and can follow, training that's relevant and engaging rather than checkbox-completion, recognition and rewards for security-conscious behavior, and leadership that models security-consciousness.
It also involves managing the tension between security and usability. If you make security too difficult, people will find workarounds. If you make it too easy, you'll miss threats. The goal is to find the balance where security is easy enough that people follow policies willingly.
Under Easterly's leadership, RSAC will likely host many discussions about organizational security culture, change management, and how to build security that scales across enterprises. This is practical, relevant work that helps organizations improve their security posture.

The Skills Gap and The Future of Cybersecurity Workforce
One challenge facing the cybersecurity industry is the skills gap. There aren't enough qualified cybersecurity professionals, and the ones that exist are in high demand and command high salaries.
This creates several problems. Organizations struggle to hire security professionals. The ones they do hire are often overworked. Junior security professionals don't get good mentorship because senior ones are too busy. Organizations fall behind on security improvements because they lack the people to implement them.
Easterly has been thoughtful about this challenge. At CISA, she worked on promoting cybersecurity education and training. She emphasized the importance of building the next generation of security professionals. She supported initiatives to bring non-traditional backgrounds into cybersecurity (many great security people don't have formal computer science education).
At RSAC, building the security workforce will likely be a major theme. The conference can provide mentorship opportunities, career guidance, and networking for people entering the field. It can showcase career paths and highlight organizations doing good work to develop talent.
One approach Easterly might emphasize: the importance of hiring people from diverse backgrounds into security. Some of the best security people come from non-traditional paths: network administrators who became security engineers, developers who discovered a passion for security, operators who identified critical security gaps.
Building the workforce is a long-term challenge that requires investment from government, from educational institutions, and from the private sector. RSAC is well-positioned to promote these conversations.

Regulatory Evolution and Compliance in the New Era
The regulatory landscape for cybersecurity is in constant flux, and Easterly will need to navigate this carefully at RSAC.
Historically, cybersecurity regulation was fragmented. Different industries had different requirements: HIPAA for healthcare, PCI-DSS for payment processors, GLBA for financial institutions, and so on. This patchwork approach meant that organizations operating across multiple industries had to comply with multiple standards, often with conflicting requirements.
Over the past few years, there's been a push toward broader cybersecurity requirements. The SEC proposed rules requiring public companies to disclose cyber incidents. The EU's NIS2 directive imposes cybersecurity requirements across Europe. Various countries are implementing data protection and privacy regulations that have security implications.
Within the U.S., the Biden administration issued an executive order on cybersecurity that pushed agencies and contractors to implement specific security practices. There's ongoing discussion about potential legislation requiring certain companies to meet cybersecurity standards.
But the Trump administration will likely take a different approach. It's likely to be skeptical of new regulations and more focused on industry self-regulation. This creates uncertainty for organizations trying to plan their compliance strategies.
Easterly's task at RSAC is to help the industry navigate this uncertainty. RSAC can host discussions about what good cybersecurity practices look like independent of specific regulations. It can help organizations understand the rationale behind regulations so they can continue to implement effective security even if specific regulations change. It can facilitate conversations between industry and government about what regulations make sense.
This is important work. Companies need to invest in security regardless of regulations, but regulations provide a floor for what security should look like. Getting this balance right is crucial.

Strategic Vision: What Easterly Could Accomplish at RSAC
Looking forward, what might Easterly accomplish as CEO of RSA Conference?
First, she could deepen the connection between technical security professionals and policymakers. RSAC has always had both groups, but the conversations between them are often surface-level. Easterly could facilitate deeper engagement: policymakers understanding technical constraints, technologists understanding policy drivers.
Second, she could make RSAC the primary venue for establishing industry standards and best practices. When RSAC reaches consensus on something—like secure development practices or supplier security requirements—that has real impact on the industry.
Third, she could position RSAC as the forum for discussing geopolitical and policy implications of cybersecurity. This is the space where government, industry, academia, and civil society can have honest conversations about how to balance security, privacy, innovation, and freedom.
Fourth, she could use RSAC to showcase the human dimension of cybersecurity: the people building security, the challenges they face, the careers available, and the importance of diversity and inclusion.
Fifth, she could drive RSAC's agenda toward practical problems and solutions rather than hype and marketing. The security industry has a well-earned reputation for fear-mongering and overselling solutions. Easterly could use her credibility to shift the conversation toward realistic assessment of threats, honest evaluation of solutions, and pragmatic approaches to improving security.
These are ambitious goals, but Easterly has a track record of achieving ambitious things. And she's taking the helm at a moment when the industry needs leadership that can bridge divides and maintain focus on what actually matters.

The Broader Context: Industry Inflection Points
Easterly's appointment arrives at a moment when the cybersecurity industry faces multiple inflection points simultaneously.
First, the AI inflection point: AI is fundamentally changing both attack and defense. The industry is still figuring out what this means practically.
Second, the geopolitical inflection point: U.S. foreign policy is shifting. The implications for cybersecurity strategy are still unclear.
Third, the regulatory inflection point: the regulatory environment is uncertain. Different administrations will take different approaches to regulation.
Fourth, the workforce inflection point: the skills gap is becoming critical. The industry needs to figure out how to attract, develop, and retain talent.
Fifth, the technology inflection point: the architecture of the internet is becoming more complex and distributed. Cloud, edge computing, AI, and other technologies are creating new security challenges.
When an industry faces multiple simultaneous inflection points, the quality of leadership becomes critical. Easterly is the kind of leader who can navigate complexity, bridge divides, and make hard choices about priorities.
Her appointment signals that RSAC is taking its role seriously: not as a vendor showcase or a government propaganda venue, but as a neutral forum where the industry's toughest problems get thoughtful analysis and discussion.

Key Insights on Cybersecurity Leadership Transitions
Easterly's move from government to the private sector—specifically to industry leadership—offers several insights about cybersecurity leadership more broadly.
First, credibility matters more than ideology. Easterly brings credibility from her time in government and the private sector. That credibility allows her to engage with people who might disagree with her politically or professionally.
Second, technical expertise is essential for security leadership. Easterly isn't just a manager; she's a security professional who understands the technical challenges the industry faces. That gives her perspective that's valuable in conversations about policy, regulation, and strategy.
Third, the ability to bridge communities is increasingly valuable. Cybersecurity leaders increasingly need to work across government, industry, academia, and civil society. Easterly's experience in all of these contexts makes her valuable in this role.
Fourth, humility about uncertainty is important. The cybersecurity industry faces many challenges where the answers aren't obvious. Leaders who acknowledge uncertainty and invite input are more likely to find good solutions than leaders who pretend to have all the answers.
Fifth, commitment to transparency and honesty is crucial. Easterly's reputation is built on telling the truth even when it's inconvenient. In a field where fear-mongering is common, that kind of honesty is valuable.

Implications for Organizations and Security Teams
What does Easterly's appointment mean for organizations and security teams?
First, it suggests that the cybersecurity industry is maturing. RSAC's decision to hire someone with deep government experience and a track record of bridging communities suggests that the industry recognizes it needs more sophisticated leadership.
Second, it suggests that industry will continue to emphasize the importance of government partnerships, supply chain security, and workforce development. These are areas where Easterly has been focused throughout her career.
Third, it suggests that neutrality is valued in industry forums. RSAC is positioning itself as a place where people from competing organizations, competing ideologies, and competing nations can gather to discuss shared technical challenges.
For security teams, this means: pay attention to RSAC 2025 and beyond. The themes Easterly emphasizes, the speakers she invites, and the conversations she facilitates will shape industry conversation. RSAC will likely be a source of industry leadership and vision for the next several years.

Conclusion: A Moment of Significance
Jen Easterly's appointment as CEO of RSA Conference is significant because it represents a moment of maturity and continuity in the cybersecurity industry.
It's maturity because RSAC recognized that it needed leadership that could bridge divides, navigate complexity, and maintain focus on technical excellence even amid political turbulence.
It's continuity because Easterly brings a consistent vision about what cybersecurity should focus on: prevention over response, collaboration over isolation, transparency over fear-mongering, and practical solutions over hype.
The timing is important too. As AI becomes central to both attack and defense, as the regulatory environment becomes uncertain, as workforce challenges intensify, and as geopolitical tensions affect cybersecurity strategy, the industry needs leadership that can help navigate these challenges thoughtfully.
Easterly has demonstrated that ability throughout her career. At CISA, she managed incredibly complex political and technical challenges, maintained focus on what actually mattered, and built relationships across divides. At Morgan Stanley, she modernized security operations in a large, complex organization. At the National Security Agency and US Cyber Command, she worked on strategic challenges at the highest levels.
Her appointment signals that RSA Conference intends to remain the industry's neutral forum for discussing technical challenges, policy implications, and strategic direction. It signals that the industry values experienced, credible leadership that can bridge communities. And it signals that cybersecurity, despite its political complexities, is ultimately about technical excellence and practical solutions.
That's a hopeful message for an industry that sometimes feels overwhelmed by fear, hype, and partisan division. Easterly's leadership suggests that it's possible to maintain focus on what matters: building secure systems, developing talent, collaborating across borders, and solving the technical problems that affect everyone.

FAQ
Who is Jen Easterly and what are her qualifications?
Jen Easterly is a cybersecurity professional with over two decades of experience across government and the private sector. She served as director of the Cybersecurity and Infrastructure Security Agency (CISA) from 2021 to 2024, where she oversaw protection of critical infrastructure and federal systems. Before CISA, she spent five years as global chief information security officer at Morgan Stanley, modernizing security operations for the financial services company. She's also held roles at the National Security Agency and helped establish the U.S. Cyber Command. Her combination of government experience, private-sector leadership, and technical expertise makes her well-qualified to lead RSA Conference during a critical period for cybersecurity.
What is RSA Conference and why does it matter?
RSA Conference (RSAC) is the largest annual gathering of cybersecurity professionals, researchers, vendors, policymakers, and academics, held each spring in San Francisco with tens of thousands of attendees from over 130 countries. It started in 1991 as a small cryptography event but has evolved into the industry's primary forum for discussing threats, technologies, standards, and policy. The conference matters because it shapes industry conversation, influences standards adoption, brings together competing perspectives, and creates space for government and industry to collaborate on shared security challenges. For many security professionals, RSAC is the most important annual conference for understanding industry direction and connecting with peers.
What was Easterly's role at CISA and why did it become controversial?
As CISA director, Easterly oversaw the agency's mission to protect federal civilian infrastructure and critical infrastructure from cyberattacks. She made CISA more visible and active, releasing faster advisories, launching programs for small business security, and coordinating protection of election infrastructure. The controversy centered on election security work. After the 2020 election, CISA coordinated improvements to election security and issued statements that the election was secure. When the Trump administration took office, it criticized this work, viewing it as political. The Trump administration did not ask Easterly to remain at CISA, and the Army rescinded a post-transition job offer. This illustrates how even technical security work can become politically polarized when high-stakes issues are involved.
Why is Easterly's appointment at RSA Conference significant given the political context?
Easterly's appointment is significant because it positions RSAC as committed to maintaining neutrality despite political tensions surrounding cybersecurity. By hiring someone whose previous work became controversial under the Trump administration, RSAC is signaling that it will include diverse perspectives and remain a forum for discussing technical challenges across political lines. Easterly's expertise in bridging government and industry, her track record of maintaining credibility with different administrations, and her focus on technical excellence over political positioning make her well-suited to maintain RSAC's role as a neutral venue. This is particularly important at a moment when cybersecurity is becoming increasingly politicized.
What are the main cybersecurity challenges Easterly will address at RSAC?
Easterly will likely focus on several major challenges: AI security (securing AI systems and defending against AI-enabled attacks), supply chain security (managing risk from software vendors and suppliers), government-private sector partnerships (rebuilding trust and information sharing), election security and critical infrastructure protection, ransomware and extortion threats, cybersecurity workforce development (addressing the skills gap), regulatory evolution (helping industry navigate uncertain regulatory landscape), and nation-state cyber threats. These challenges require collaboration across government, industry, academia, and civil society—exactly the kind of forum RSAC provides.
How might Easterly's leadership change the direction of RSA Conference?
Easterly is likely to emphasize practical solutions over fear-mongering, increase focus on prevention-focused approaches, deepen engagement between technologists and policymakers, promote industry standards and best practices, showcase the human dimension of cybersecurity, and facilitate honest conversation about geopolitical and policy implications. Her credibility and bridge-building ability should help RSAC function better as a neutral forum. She's likely to make the conference more focused on solving actual industry problems and less focused on vendor marketing and hype. Her emphasis on transparency and integrity is likely to elevate the quality of conversations at RSAC.
What does Easterly's move from government to the private sector signal about the cybersecurity industry?
It signals that the industry recognizes it needs mature, experienced leadership that can navigate complexity and bridge communities. It suggests that cybersecurity is becoming more integrated into broader business and policy strategy, not just a technical domain. It indicates that the industry values people with both government and private-sector experience, recognizing that cybersecurity challenges increasingly require collaboration across both sectors. It also suggests that neutrality and credibility are increasingly valuable in industry leadership, particularly as cybersecurity becomes more politicized.
How will Easterly address the politicization of cybersecurity at RSAC?
Easterly has stated that cybersecurity is not political and that RSAC is committed to welcoming government officials from all administrations. Her approach will likely be to focus on technical and policy challenges that transcend politics, facilitate conversations that bring together different perspectives, maintain transparency and honesty about disagreements, emphasize shared interests (all organizations want secure systems), and avoid positioning RSAC as aligned with any particular administration or political perspective. By maintaining focus on practical problems and technical excellence, RSAC can continue to serve as a neutral forum even amid political tensions.
What should security professionals expect from RSAC under Easterly's leadership?
Security professionals should expect deeper engagement between technical practitioners and policymakers, more focus on practical problems and proven solutions, continued emphasis on supply chain security and secure development practices, substantial coverage of AI security as it evolves, conversations about workforce development and career paths in cybersecurity, and a commitment to maintaining RSAC as a neutral venue where diverse perspectives can engage respectfully. Expect less marketing hype and vendor focus than some industry conferences, and more emphasis on solving actual industry challenges. RSAC should become an even more valuable resource for understanding where the industry is heading and connecting with peers facing similar challenges.
How does Easterly's background in election security affect her leadership role?
Her election security work at CISA is simultaneously a credential and a liability. It demonstrates her ability to handle politically sensitive, high-stakes security challenges. It shows her commitment to technical excellence even when work becomes controversial. But it also means that some in the current administration may be skeptical of her. Easterly's approach will likely be to not defend or promote the previous administration's policies, but to emphasize that election security is critical infrastructure protection, not politics. She'll likely position RSAC as committed to security challenges that affect all citizens regardless of political affiliation, including election security, critical infrastructure protection, and protection of civic institutions.
What are the long-term implications of Easterly's appointment for cybersecurity governance?
Easterly's appointment suggests that the cybersecurity industry is moving toward more sophisticated governance that bridges government, industry, academia, and civil society. It indicates that industry recognizes the importance of neutral forums where diverse perspectives can engage. It suggests that cybersecurity professionals with deep government experience will increasingly move into industry leadership roles as the field matures. It also implies that government-private partnerships will remain important despite political tensions, and that maintaining those partnerships requires leaders with credibility across divides. Long-term, we should expect RSAC to play a more central role in shaping cybersecurity standards, best practices, and industry direction.

Key Takeaways
- Jen Easterly's appointment as RSA Conference CEO signals industry commitment to maintaining neutrality despite political tensions in cybersecurity
- Her background bridging government, military, and private sector positions her to guide industry through multiple simultaneous inflection points
- AI security, supply chain protection, and government-private partnerships will likely be primary focus areas under her leadership
- RSAC's selection of Easterly reflects cybersecurity industry's maturation and recognition that experienced leadership capable of navigating complexity is essential
- Election security controversies from her CISA role illustrate broader challenge of keeping technical security work separate from political polarization
Related Articles
- CISA Retires 10 Emergency Directives: What Changed for Federal Cybersecurity [2025]
- 45 Million French Records Leaked: What Happened & How to Protect Yourself [2025]
- Tea App's Comeback: Privacy, AI, and Dating Safety [2025]
- Pax8 Data Breach: 1,800 MSPs Exposed in Email Mistake [2025]
- RedDVS Phishing Platform Takedown: How Microsoft Stopped a $40M Cybercrime Operation [2025]
- ExpressVPN 78% Discount Deal: Complete Savings & Comparison Guide [2025]
![Jen Easterly Leads RSA Conference Into AI Security Era [2025]](https://tryrunable.com/blog/jen-easterly-leads-rsa-conference-into-ai-security-era-2025/image-1-1768484707314.jpg)



