Why Startups Are Prime Targets for Hackers in 2025: A Reality Check for Founders
You've probably heard the startup mentality before: move fast, break things, ask forgiveness later. It's catchy. It's worked for some companies. But there's one thing you shouldn't break in the name of speed, and that's your security.
Here's what keeps me up at night: A five-person startup in Germany just had 10.5 million customer records exposed. A tracking app in the US leaked 1.4 million records. These weren't massive Fortune 500 companies with legacy systems and thousands of employees. These were small, nimble teams building the future. And they got hit hard.
According to recent data from the Swiss privacy firm Proton, 794 major breaches occurred in 2025 alone, exposing over 306 million records. The kicker? 71% of those breaches affected small- and medium-sized businesses. Not small percentages either—the vast majority of cyberattacks target companies like yours.
I get why founders think they're safe. You're not a bank. You don't have customer credit cards on file (hopefully). You're working out of a shared office space or someone's garage. Why would hackers care about your data?
That's exactly the wrong way to think about it.
Cybercriminals don't discriminate based on company size. They follow opportunity. And startups represent some of the juiciest targets going: valuable intellectual property, customer data, minimal security infrastructure, underpaid (or non-existent) security teams, and founders too busy shipping features to worry about access controls.
This guide walks through why startups have become ground zero for cyber attacks, what's actually at risk, and what you can realistically do about it without hiring a security officer and derailing your product roadmap.
TL; DR
- 306+ million records exposed in 2025: With 71% of breaches targeting small and medium-sized businesses, the "too small to hack" myth is officially dead
- Startups have the perfect storm of vulnerabilities: Valuable IP, minimal security infrastructure, and founders prioritizing speed over security create an irresistible target
- The "build in private" approach works: Embedding privacy and security from day one—not bolting it on after a breach—prevents catastrophic data loss
- Three critical controls matter most: Gate your access, encrypt everything, and centralize your security infrastructure before you scale
- The cost of inaction is brutal: GDPR fines, total loss of customer trust, and potential business collapse make security a survival issue, not a nice-to-have
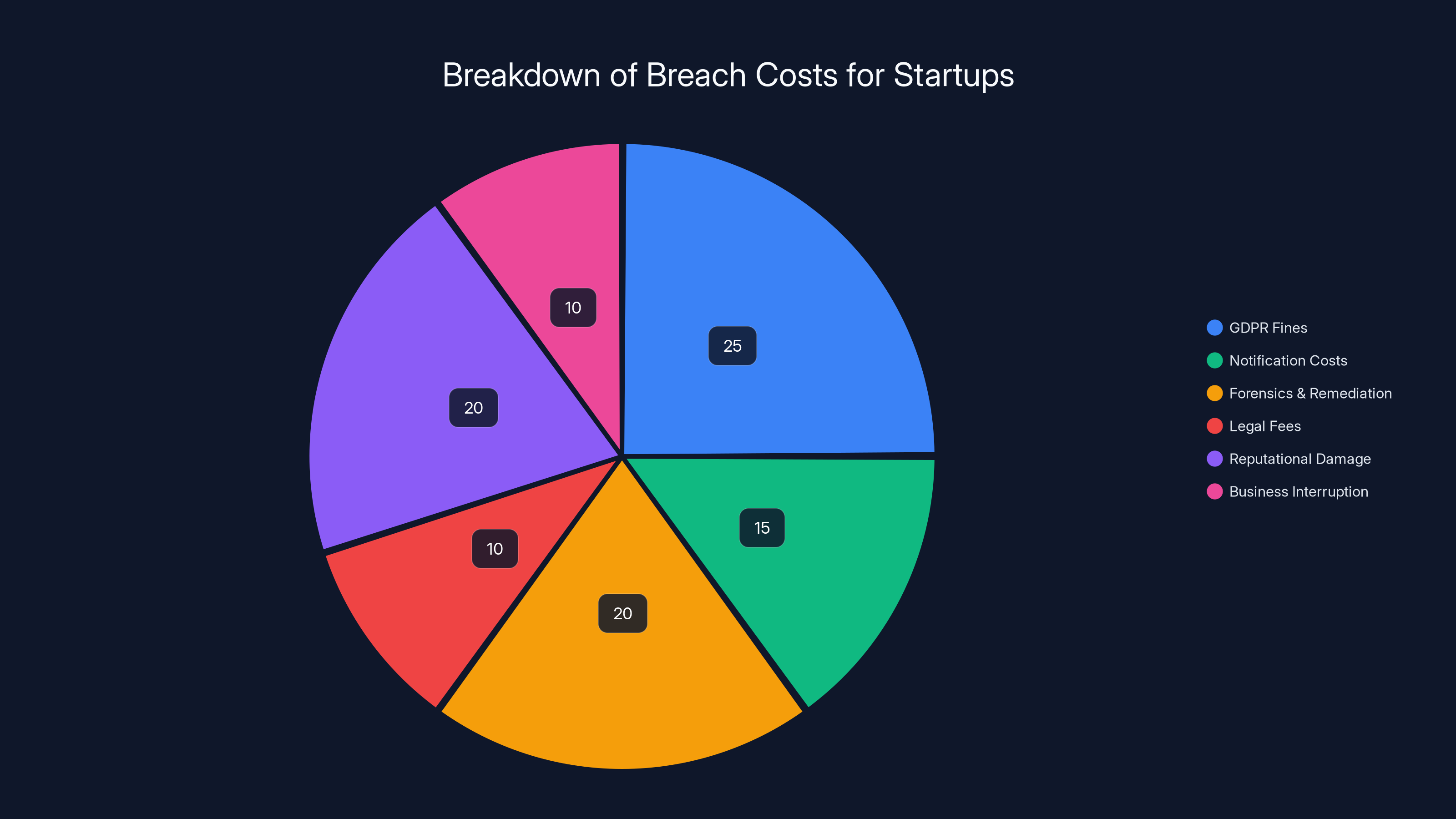
Estimated data shows that GDPR fines and forensics/remediation are major cost drivers in a breach scenario, each accounting for 20-25% of total costs.
The Numbers Don't Lie: Small Businesses Are Now the Primary Target
Let's start with the raw data, because it's shocking enough to warrant immediate action.
In 2025, Proton's Data Breach Observatory recorded 794 significant breaches. That's more than two breaches per day, every single day, all year long. But the scale of exposure matters more than the frequency. Those 794 breaches exposed 306.1 million records.
Take a moment to sit with that number. 306 million. That's roughly the entire population of the United States, all of whom had their personal information compromised through various security failures.
What's more alarming is the distribution. When you hear about data breaches on the news, the coverage often focuses on mega-corporations: Facebook, Equifax, Target, Amazon. These are the breaches that make headlines because the companies are household names. But according to the data, that's not where the actual damage is happening.
Proton found that 71% of breaches affected small- and medium-sized businesses. Not 30%. Not 50%. Seventy-one percent. That means for every major corporation breach you hear about, there are multiple startup breaches happening in the shadows, affecting millions of people whose personal data got exposed to criminals.
Why? Because SMBs are vulnerable in ways that large corporations aren't. They don't have dedicated security teams. They don't have legacy systems that have been hardened over decades. They don't have compliance frameworks already in place. Instead, they have founders saying "we'll fix security later" and engineers shipping features as fast as possible.
It's a recipe for disaster.
The really scary part? Most breaches affecting startups don't make the news. They get handled quietly. The company patches the vulnerability. They notify affected users. They pay the fines. And life goes on. Nobody knows about it except the customers whose data was compromised and the founder losing sleep at night.
But the data is there. And it shows that if you're running a startup, the odds are increasingly in favor of you getting hacked. Not might get hacked. Will get hacked. The question is just whether you'll survive it.
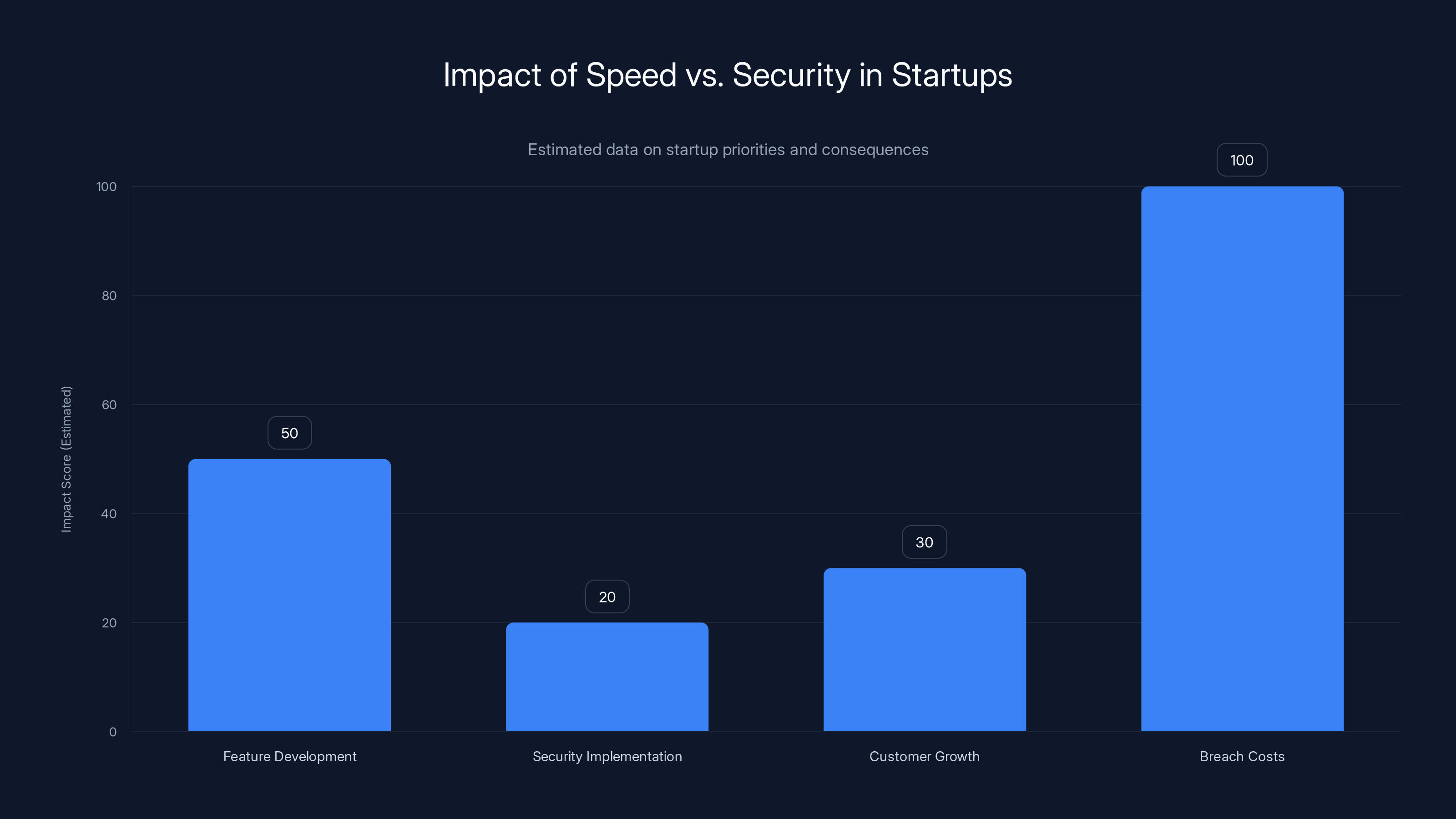
Startups often prioritize feature development over security, leading to significant breach costs. Estimated data shows the disproportionate impact of breaches.
The "Too Small to Hack" Myth Is Officially Dead
There's a dangerous misconception floating around in startup circles, and it needs to die.
The myth goes like this: "We're too small. Nobody cares about our data. Hackers target big companies with big payoffs. We're not worth the effort."
This logic is fundamentally flawed, and it's getting startups breached every single day.
Cybercriminals aren't sophisticated hackers with Ph Ds in cryptography sitting in dark rooms plotting to take down major corporations. That happens sometimes, sure. But the reality is far more mundane and far more dangerous: most attacks follow the path of least resistance.
A startup with 10,000 customer records and virtually no security infrastructure is infinitely easier to breach than a Fortune 500 company with armies of security engineers, penetration testers, and incident response teams.
Think of it like a bank heist metaphor. A heavily guarded bank with vaults and security cameras is hard to rob. But a corner shop with a single lock on the back door? That's low-hanging fruit. Cybercriminals are the same way. They're not out to prove some political point or take down a big institution. They want money, data, or leverage, and they want it with minimal effort.
Startups offer exactly that.
First, startups often hold extremely valuable intellectual property. You've built something novel. Your algorithms, your codebase, your product strategy—these represent years of work and are worth real money. A competitor might pay hundreds of thousands for your trade secrets. A criminal might hold it for ransom.
Second, startups hold customer data. If you're building a B2C product—a fitness app, a finance tool, a dating platform—you're collecting personal information from users. Email addresses, phone numbers, location data, health information, financial information. Criminals can sell this data on the dark web or use it for identity theft, phishing attacks, or fraud.
Third, and most importantly, startups are security-naive in ways that large companies aren't. A CISO (Chief Information Security Officer) at Google has spent their entire career thinking about security. They've probably attended dozens of conferences, read hundreds of papers, and managed teams of security professionals. A startup founder has spent the last 18 months living in Google Drive and Slack, shipping code and talking to customers.
Security? It's on the roadmap. Somewhere down there. After Series A funding. After we hit 100K users. After we prove product-market fit.
For many startups, security never makes it onto the roadmap. Or if it does, it's deprioritized when a customer yells about a missing feature.
Proton's report cites real examples that hammer this home. Phone Mondo, a five-person team in Germany, had over 10.5 million records exposed. Five people. Tracelo, a US-based tracking app, leaked 1.4 million records. These weren't massive corporations with complex systems. They were small teams building products, and their products became liabilities.
The thing that shocks most people is how large the exposure was relative to company size. These teams probably had a few thousand users, maybe tens of thousands. Yet somehow they were exposed to millions of records. How?
Bad database configuration. Unencrypted backups. Overly permissive access controls. Hardcoded credentials. Dependencies with known vulnerabilities. All of the security failures that a startup with zero security infrastructure might make.
The myth dies the moment you realize that hackers don't target companies—they target opportunities. And startups are full of opportunities.

Why Startups Fall Victim: The Speed vs. Security Trade-Off
There's a cultural tension in the startup world that nobody talks about enough.
The dominant narrative in startup culture is "move fast and break things." It's the ethos that built Facebook, Uber, Airbnb, and a thousand other disruptive companies. Speed is competitive advantage. Your competitor isn't better than you—they're just slower. If you can ship twice as fast, you win.
This mentality works great for product development. It fails catastrophically for security.
Here's what happens: A founder realizes they need to ship a feature. They need it done by Friday so they can demo it to investors. They look at their security checklist. It says things like "implement API rate limiting" and "add request signing" and "rotate credentials monthly." That's two extra weeks of work. So they ship without it. They ship fast. They iterate. They fix security issues later.
Except "later" never comes. Because next week there's another feature. And an investor meeting. And a customer complaint. And a new competitive threat. Security keeps getting bumped to the bottom of the queue because it doesn't move the needle on growth metrics.
Patricia Egger, Head of Security at Proton, put it perfectly: "In startup circles, 'speed wins,' and security can be seen as a hindrance to that speed. This can result in missing crucial steps when securing a business."
It's not malice. It's not negligence in the traditional sense. It's a reasonable tradeoff that goes catastrophically wrong when you account for the tail risk of a major breach.
Consider the math: Let's say implementing proper security infrastructure takes 20% of your engineering capacity for 3 months. That delays your feature roadmap by 3 months. It might cost you some customers or slower growth. That's a real cost.
But getting breached costs you everything. It costs you your entire customer database. It costs you millions in GDPR fines (€10-20M per incident is typical). It costs you investor trust. It costs you your reputation. Companies have folded after major breaches. The probability might be 20%, and the impact is 100% loss, which means the expected value calculation should definitely include security.
But human brains don't work that way. We discount tail risks and focus on immediate pressures. So founders optimize for speed and deprioritize security.
This happens across the entire startup ecosystem:
Early stage (pre-seed to Series A): You're bootstrapped or operating on minimal funding. You have 2-3 engineers. Every person-day costs money. Security feels like a luxury for bigger companies.
Growth stage (Series A-B): You're hiring rapidly. New engineers onboard weekly. You don't have processes or documentation. Everybody has access to everything. You're adding integrations with third-party services, most of which are adding their own security gaps to your infrastructure.
Late stage (Series C+): You've scaled to hundreds of engineers across multiple services. You have a sprawling technology stack held together with duct tape and prayers. You finally hire a security team, but they're fighting decades of bad decisions baked into the codebase.
Each stage has different vulnerabilities, but they all stem from the same root cause: speed prioritized over security.
Raphael Auphan, COO of Proton, commented on this tension: "I cannot stress enough to founders and business owners the importance of pausing to make the conscious choice to 'build in private.' While consumers understand privacy, it can be harder to convey to founders of startups when widely adopted big tech tools prioritize speed."
Translation: The tools you're using (Google Workspace, Slack, AWS, etc.) don't make you secure by default. They make you productive. You have to consciously choose to build securely, and that choice is easier to make before you're moving at full speed than after.
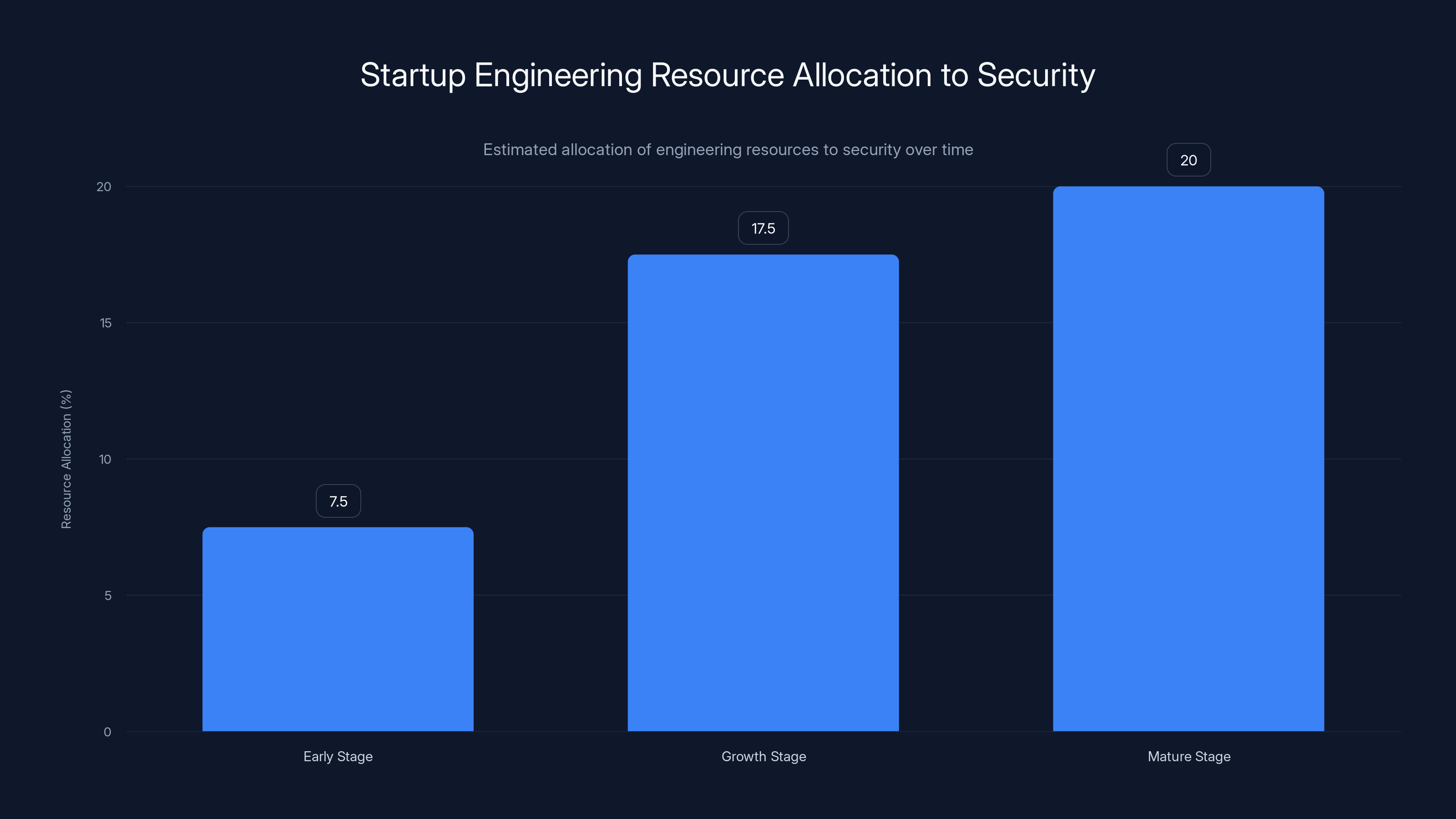
Startups should allocate 5-10% of engineering resources to security in early stages, increasing to 15-20% as they scale. Estimated data.
The "Build in Private" Framework: Security From Day One
So how do you escape the speed vs. security trap?
Proton's recommendation is to adopt what they call a "build in private" mentality. Rather than bolting security onto your product after it's mature, you embed security into your culture, processes, and infrastructure from day one.
This doesn't mean hiring a CISO on day one. It doesn't mean months of security audits before shipping your MVP. It means making conscious decisions about privacy and security at each stage of your growth, starting with the very beginning.
Think of it like technical debt, except in reverse. If you incur security debt (shipping fast without security considerations), you're creating obligations that compound over time. Every unencrypted connection, every overly permissive access control, every unpatched dependency adds to that debt.
With interest. Because now hackers have a larger surface area to exploit.
Building in private means you're investing in security proactively, not reactively. You're saying: "We're going to be secure by default. Security isn't optional. It's how we operate."
What does that look like in practice?
Day one: You're a founder and a contractor or freelancer. You're building an MVP in your garage. Even then, you make conscious choices about data handling. You don't store customer passwords in plaintext. You don't commit API keys to Git Hub. You don't use free Wi Fi to access production systems. You're building with the assumption that you might scale, and you don't want to rebuild everything.
Series A: You hire your first full engineering team. They onboard fast. Instead of "here's the codebase, go ship," you give them a security onboarding. You establish policies: VPN for remote work, two-factor authentication (2FA) for all company accounts, encryption for data at rest and in transit. You choose infrastructure providers that offer strong defaults (not necessarily the cheapest option).
Series B: You've scaled to 50+ employees. You have multiple product teams working on different services. You establish a security review process. Not every change needs security approval, but major architectural decisions do. You implement automated security scanning in your CI/CD pipeline. You run quarterly penetration tests. You have an incident response plan.
Series C+: You hire a dedicated security team. You've built security into your DNA. New hires understand that security is non-negotiable. You're thinking about security implications of every new feature, every new integration, every new market you enter.
At each stage, security investment is proportional to your growth and risk. You're not spending the same budget on security as a 2-person team as a 200-person company. But you're making consistent, deliberate choices about how to operate securely.
The key insight is that building in private is cheaper than cleaning up after a breach. A few hours of security consideration during design costs hundreds of hours of incident response, forensics, notification, legal, and remediation after a breach.
The practical question is: where do you start? What's the minimum viable security for a startup?
Three Critical Controls Every Startup Needs
Proton's report identifies three fundamental controls that can dramatically reduce your breach risk. They're not revolutionary. They won't require massive engineering investment. But they address the most common attack vectors that compromise startups.
Control One: Gate Your Access
Imagine your startup's data as a house. Who has keys to every room? Probably everyone. Your designer needs access to the production database to test something. Your sales person needs root access to the billing system to check a customer's account. Your intern gets the same credentials as your VP of Engineering because onboarding is too complicated to bother with granular permissions.
This is an absolute nightmare from a security perspective.
Gating your access means implementing a simple principle: people only get access to what they need to do their job. Your designer doesn't need production database access. Your accountant doesn't need backend code repositories. Your customer service team doesn't need to SSH into servers.
This seems obvious when you say it out loud. But in practice, it's surprisingly rare. Most startups operate under a "everybody gets access to everything" model because the overhead of managing granular permissions feels annoying.
Here's why it matters: If a designer's laptop gets compromised, a hacker has everything. All your databases, all your code, all your infrastructure. If access had been gated, they'd only have access to design assets and maybe staging environments.
Implementing gated access doesn't require fancy enterprise software. Start with basic practices:
Use a VPN for remote access. A business VPN creates a private gateway that all employees connect through. Instead of exposing your infrastructure to the open internet, you only expose it to people connected to the VPN. If someone's laptop is compromised, the hacker still has to be connected to the VPN to access anything.
Tools like Wire Guard or commercial VPN solutions offer this. The cost is minimal. The security benefit is substantial.
Implement role-based access control (RBAC). In your infrastructure, database, and application layer, define different roles and assign permissions accordingly. A junior engineer doesn't need root access. An intern doesn't need to manage billing. A contractor doesn't need to see customer data.
Cloud providers like AWS, Google Cloud, and Azure all offer built-in RBAC systems. They're not hard to use. They just require thinking about permissions upfront.
Rotate credentials regularly. Database passwords, API keys, SSH keys—these should change periodically. If a credential gets leaked, you've minimized the window of exposure. If an employee leaves, their access disappears immediately.
Audit access logs. Who accessed what? When? Why? You should have basic logging that shows access patterns. If someone suddenly starts accessing systems they've never touched before, that's a red flag.
The deeper principle here is: assume one device will get compromised. It might be an employee's laptop. It might be a contractor's equipment. It might be a Saa S tool they use that has a vulnerability. When it happens, you've minimized the blast radius by limiting what that compromised device can access.
Control Two: Encrypt Everything
Encryption doesn't prevent attacks. A skilled attacker will still find ways in. But encryption makes stolen data worthless.
Imagine a hacker breaches your database. They get access to your customer table. If the data is encrypted, they have a database full of gibberish. It's useless to them. They can't sell it on the dark web. They can't use it for identity theft or fraud. They've wasted their effort.
But if the data is plaintext, they've hit the jackpot. Email, password hashes, phone numbers, addresses, billing information—all valuable, all sellable.
Encryption is a force multiplier for your security. It doesn't replace good access controls or secure infrastructure. But it means that even if someone gets access to your data stores, they can't do anything with the information.
Here's what to encrypt:
Email. Use encrypted email services or ensure your email provider supports TLS (Transport Layer Security) for transmission. This prevents intercepted emails from being readable.
Cloud storage. If you're using Dropbox, Google Drive, or One Drive, ensure that sensitive files are encrypted before upload. Some tools offer client-side encryption where you control the encryption keys and the cloud provider can't read your data even if they wanted to.
Databases. Use encrypted databases or add an encryption layer in your application code. Many databases support encryption at rest (data encrypted when stored) and encryption in transit (data encrypted when transmitted).
Backups. If you have database backups, they should be encrypted too. A backup sitting on an S3 bucket is a goldmine for hackers. An encrypted backup is useless.
API credentials and secrets. Any sensitive configuration (database passwords, API keys, private encryption keys) should be encrypted and stored in a secrets management system. Tools like Vault or AWS Secrets Manager make this straightforward.
The key phrase here is "end-to-end encryption." This means the data is encrypted on your device before it leaves, transmitted encrypted, and decrypted only when it reaches the intended recipient. Only you hold the keys. The service provider can't read your data. A hacker who intercepts transmission can't decrypt it.
Control Three: Centralize and Monitor Your Security Infrastructure
The last control is about visibility and centralization.
As you scale, your infrastructure becomes complex. You have databases, servers, APIs, third-party services, cloud storage, development environments, staging environments, production environments. Data flows everywhere. It's easy to lose track of where everything is and who has access.
Centralizing your security infrastructure means creating a single pane of glass where you can see:
- Who has access to what
- What's being accessed
- When access patterns change
- When systems behave abnormally
This is usually handled by a combination of tools:
Identity and Access Management (IAM). A system that controls who gets access to what across your entire infrastructure. You have a single source of truth for user credentials and permissions.
Security Information and Event Management (SIEM). Tools like Splunk or Elastic aggregate logs from all your systems and look for suspicious activity. Abnormal access patterns, failed login attempts, unusual data transfers—the system flags these.
Intrusion Detection Systems (IDS). Tools that monitor network traffic for signs of attack or compromise.
For a startup, you probably don't need all of this immediately. But you can implement simplified versions:
- Use your cloud provider's built-in logging and monitoring
- Set up alerts for unusual activities
- Review access logs weekly
- Keep a simple spreadsheet of who has access to what
The principle is: if something goes wrong, you want to know about it fast. The average breach goes undetected for 206 days. That's six months of hackers having free access to your systems. Faster detection cuts that window dramatically.
Centralization also helps with offboarding. When someone leaves your company, their access should disappear everywhere, instantly. If access is scattered across different systems (this person's laptop, that service, this API key), something will inevitably slip through.

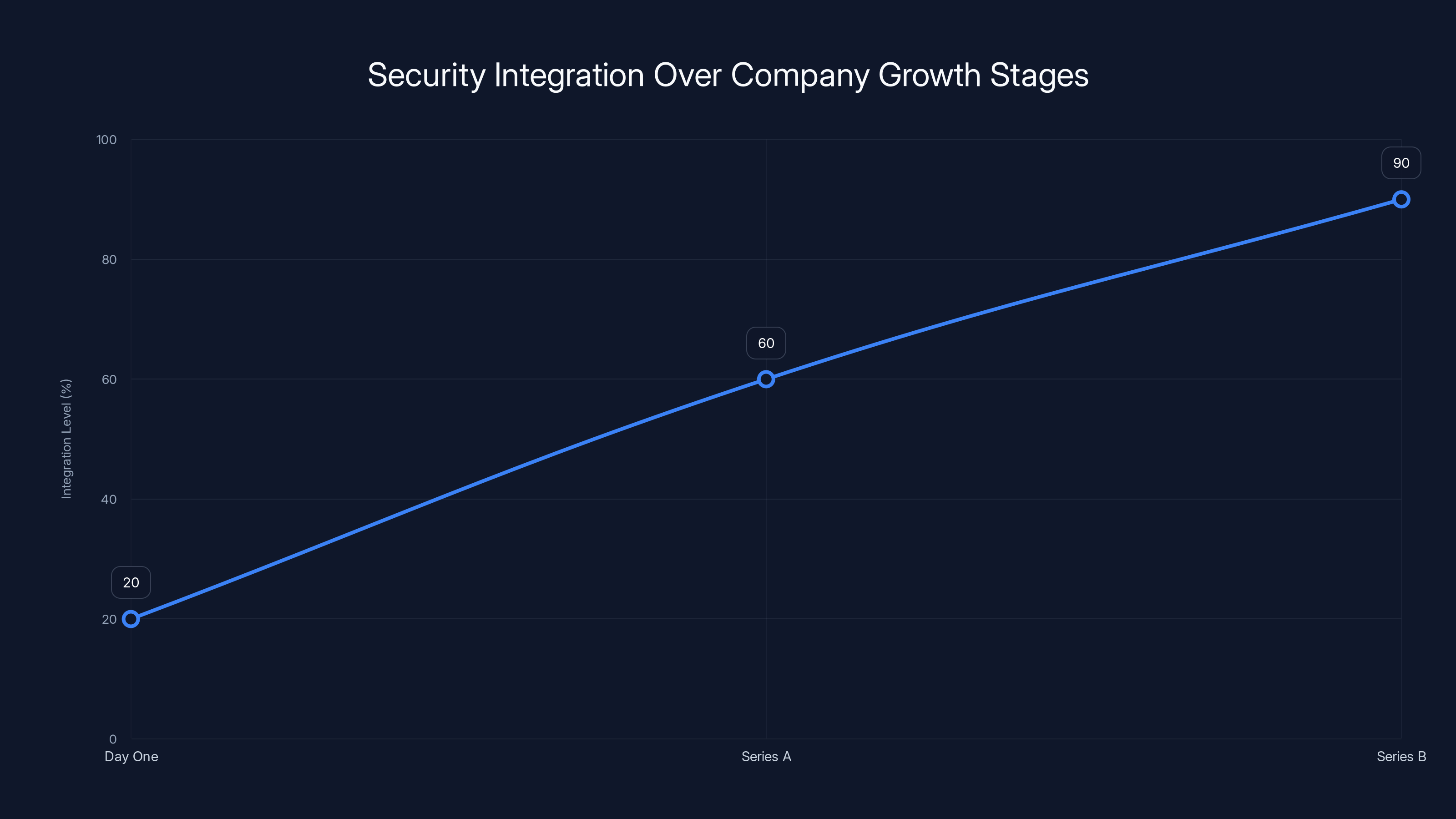
Estimated data shows increasing integration of security practices as companies grow from MVP to Series B, emphasizing proactive security measures.
The Cost of Inaction: What a Breach Actually Costs
Let's talk about why this matters beyond the abstract. What does a breach actually cost?
The direct financial costs are just the beginning:
GDPR fines. If you're in Europe or serving European customers, the General Data Protection Regulation applies. Fines go up to €10 million or 2% of global revenue—whichever is higher. A startup with 10 million exposed records could face fines in the millions, even if you're a small company.
Notification costs. You have to notify everyone whose data was compromised. Depending on scope, you might need to set up credit monitoring services. Costs run into the hundreds of thousands.
Forensics and remediation. You need to hire forensic experts to figure out what happened, secure your infrastructure, patch vulnerabilities, rebuild systems if necessary. This is expensive and time-consuming.
Legal fees. You'll probably face lawsuits from affected customers. Legal fees add up quickly.
Reputational damage. This is harder to quantify, but it's real. Customers lose trust. Press coverage is negative. You struggle to acquire new customers. Your valuation tanks.
Business interruption. While you're dealing with a breach, you're not shipping features. You're not talking to customers. You're not building the product. Growth stalls.
For small startups, this can be fatal. A company with
Some startups have folded after breaches. Not because the technical recovery was impossible, but because they couldn't survive the financial and reputational damage.
There's also a human cost. Breaches are stressful. They keep founders and engineers up at night. They strain relationships with investors and customers. They're just brutal to experience.
The mathematics should be obvious: spending a few thousand dollars on security infrastructure is vastly cheaper than dealing with a breach. Yet most startups don't make that investment until it's too late.

Real-World Examples: How Startups Actually Get Breached
Let's look at the specific examples Proton cited, because understanding how these breaches happened is more instructive than just knowing they happened.
Phone Mondo (Germany, 5 employees, 10.5 million records exposed):
Phone Mondo was a small telecom service provider. Five people. Probably operating lean, shipping features fast. Somehow, they exposed 10.5 million customer records. How?
Most likely culprits based on similar breaches: misconfigured database (a Mongo DB or Elasticsearch instance exposed on the public internet with no authentication), unencrypted backups, or overly permissive access controls.
With a five-person team, there's probably not a dedicated database administrator. There's probably one engineer who spun up the database and everyone got credentials. Configuration was "secure by default" or maybe someone found a template online and used it. Security hardening felt like it could wait.
A hacker probably found it through automated scanning (there are tools that scan the internet looking for exposed databases) or through basic reconnaissance.
Once they found it, they had access to everything. All customer names, all phone numbers, all billing information. Exposed.
Tracelo (US, tracking app, 1.4 million records exposed):
Tracelo was a location tracking application. Users were logging their locations. That's valuable data if it gets exposed.
The breach likely happened through one of several vectors: a third-party API integration that had insecure endpoints, a web interface with inadequate authentication, cloud storage misconfiguration, or a compromised employee account.
With a typical startup in the location/tracking space, they probably integrate with services like Google Maps, Twilio, or other third-party APIs. They probably have a web dashboard where users log in. They probably store data in a cloud database like Firebase or Dynamo DB.
Any of these could be the weak link. An API endpoint that returns data without proper authentication checks. A login system vulnerable to password stuffing attacks. A database with predictable naming and default credentials.
Once exposed, 1.4 million location records represent a major privacy violation. Location data is extremely sensitive. Knowing where someone lives, where they work, where they go on weekends—that's intimate data that exposes them to stalking, theft, harassment.
Both of these breaches share a common pattern: small teams building valuable products, moving fast, and not implementing basic security controls until it was too late.
Neither of these companies was hacked by sophisticated state-actors or zero-day exploits. They were breached through basic security failures that could have been prevented with standard practices.

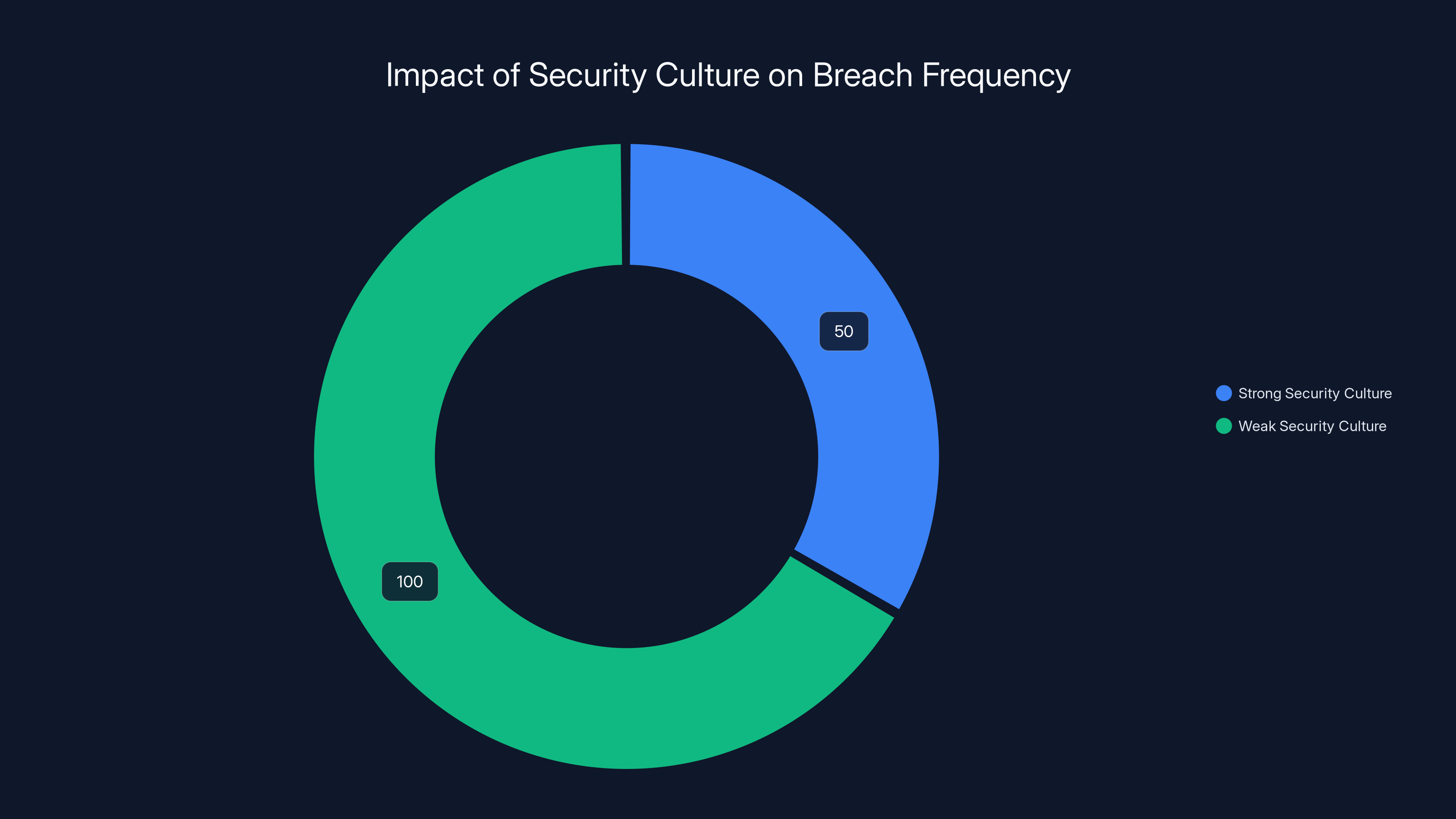
Companies with strong security cultures experience 50% fewer breaches on average compared to those with weak security practices. Estimated data based on industry insights.
Building Security Into Your Processes: Practical Steps
So you've bought into the idea that security matters. You want to build in private. What do you actually do?
Here's a practical roadmap for startups at different stages:
For Pre-MVP/Idea Stage
You probably don't have customers yet. You're building the product. Even so, establish security baselines:
-
Version control discipline: Use Git. Don't commit secrets (API keys, database passwords, private keys). Use a
.gitignorefile to exclude these. Never commit to a public repository without carefully reviewing what you're exposing. -
Database security: If you're using a hosted database (AWS RDS, Google Cloud SQL, Firebase), enable all security options: encryption at rest, encryption in transit, regular backups, automated patching.
-
Access control: Even with two people, establish who has access to what. Use different credentials for different services. Use unique, strong passwords. Enable two-factor authentication (2FA) everywhere.
-
Dependency management: Track your software dependencies. Use tools like Dependabot or Snyk to monitor for security vulnerabilities. Update regularly.
For MVP/First Customers
You have users. You have real data. Security becomes critical:
-
Implement VPN: If anyone works remotely, require VPN access to company infrastructure. Wire Guard is free and easy to set up.
-
Encryption: Encrypt data in transit (use HTTPS everywhere). Encrypt data at rest in your databases. Use HTTPS for all API communication.
-
Access control: Implement role-based access (read, write, admin). Junior engineers don't need database password. Interns don't need production access. Create an offboarding checklist: when someone leaves, disable all their access.
-
Monitoring: Set up basic alerts. Get notified if there are unusual access patterns or failed login attempts. Use your cloud provider's built-in monitoring.
-
Incident response plan: Have a simple document that explains what to do if a security incident happens. Who do you contact? What's your first move? How do you communicate with customers? It doesn't need to be elaborate, but it should exist.
For Growth Stage (Series A-B)
You're hiring. You have multiple teams. Security gets more complex:
-
Security onboarding: New engineers get security training. You explain the architecture, the threats, the security controls. You don't assume everyone knows what you know.
-
Code review process: Security should be part of code review. Someone looks at changes and thinks about security implications. Is this exposing data? Is this creating an access control bypass? Could this be exploited?
-
Secrets management: Move credentials into a secrets management system. Developers shouldn't have database passwords lying around. They request access through a system that logs who accessed what.
-
Automated security scanning: Use tools like Semgrep or Sonar Qube to automatically scan code for security vulnerabilities. Integrate into your CI/CD pipeline.
-
Third-party risk management: As you add integrations and services, think about what data they have access to. Do you really need to give them access to your entire customer database? Can you restrict them to what's necessary?
-
Regular security reviews: Schedule quarterly reviews. Look at access logs. Check for unusual activity. Review recent infrastructure changes. Identify gaps.
For Late Stage (Series C+)
You're at scale. You need a formal security program:
-
Dedicated security team: Hire a security engineer or security leader. You need someone whose job is explicitly security.
-
Penetration testing: Hire external security firms to attempt to break into your infrastructure. Learn from the attempts. Fix the gaps they find.
-
Security policies and standards: Document your security practices. Create policies for handling sensitive data, password management, encryption, access control. Make it official.
-
Vendor security management: Audit your vendors. Are they secure? What data do they have access to? Do you have contracts in place that require certain security practices?
-
Incident response team: Establish a dedicated incident response team. They have training and processes for dealing with security incidents. They know how to investigate, contain, and remediate.
-
Compliance frameworks: Depending on your customers and regulations, you might need to certify to compliance frameworks like SOC 2, ISO 27001, or HIPAA. Build these into your processes.
Each stage adds complexity and cost, but the cost is proportional to your size and risk. A 2-person company shouldn't be running penetration testing. A 200-person company should be.

Common Security Mistakes Startups Make
Let me highlight the mistakes I see again and again:
Mistake #1: Hardcoded Credentials
Developers hardcode database passwords, API keys, or other secrets directly into code. Then they commit this code to Git Hub (or another repository). Now the secret is in git history, visible to anyone who can see the repository.
Hackers use tools that scan Git Hub for secrets. They find your database password. They connect to your database. They own you.
Solution: Use environment variables or a secrets management system. Credentials should never be in code.
Mistake #2: Default Credentials
You spin up a database or service and forget to change the default username and password. The default is probably widely known (the entire internet knows the default Postgres password).
A hacker finds your database, tries the defaults, and gets in.
Solution: Change all defaults. Use unique, strong credentials. Use 2FA where available.
Mistake #3: Overly Permissive Access
Everyone gets access to everything. Your designer has database admin. Your intern has production server access. Your contractor has code repository permissions.
When any of them leave or get compromised, the entire infrastructure is exposed.
Solution: Implement role-based access. Give people only what they need.
Mistake #4: No Encryption
Data is stored and transmitted in plaintext. If someone gets access to your data stores or intercepts your communications, they can read everything.
Solution: Encrypt data at rest and in transit. Use HTTPS for everything.
Mistake #5: No Monitoring
Something bad happens, and you don't find out for months. A hacker accesses data for weeks before anyone notices. A malicious insider steals intellectual property and you never know who.
Solution: Set up basic logging and monitoring. Alert on unusual access patterns.
Mistake #6: Ignoring Vulnerabilities
You use open-source libraries with known vulnerabilities. You know about the vulnerability but don't prioritize fixing it.
A hacker exploits the vulnerability. You get breached.
Solution: Use dependency scanning tools. Monitor for vulnerabilities. Update dependencies regularly.
Mistake #7: No Offboarding Process
An employee leaves. Nobody remembers to disable their database access. Nobody revokes their SSH keys. They still have access to everything months later.
Solution: Create a checklist. When someone leaves, you go through the checklist and revoke all access.
Mistake #8: Trusting Third Parties Blindly
You integrate a third-party service and give them unlimited access to your data. You don't think about what could go wrong.
The service gets hacked. Your data leaks.
Solution: Audit third-party access. Use least privilege. Limit what they can access. Have contracts in place.

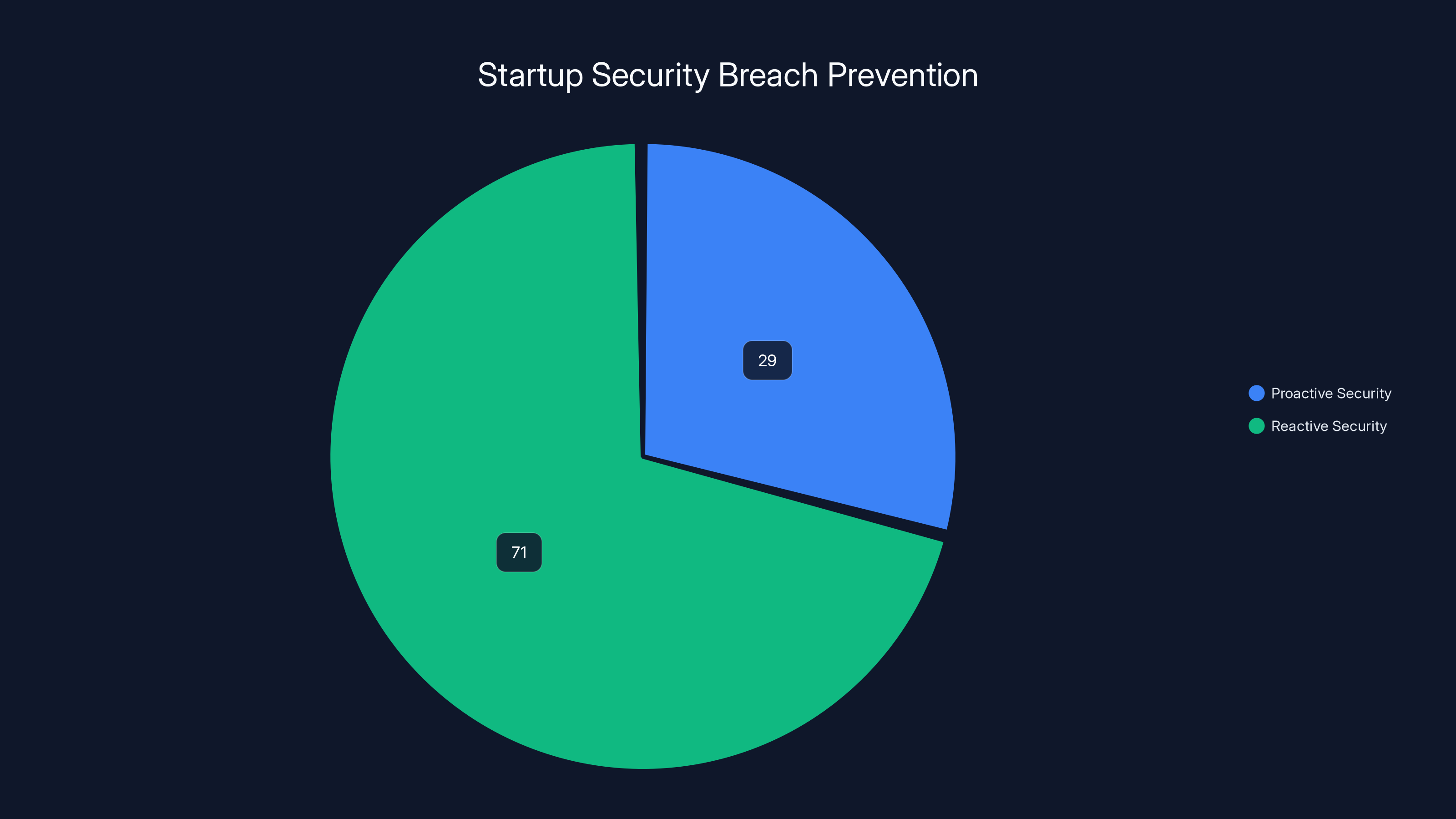
Estimated data suggests that 71% of startups operate reactively and are at risk of breaches, while 29% adopt proactive security measures and are better protected.
The Future of Startup Security: Threats on the Horizon
The threat landscape is evolving. New attack vectors emerge constantly. Here's what to watch:
AI-powered attacks: Hackers are using AI to automate and scale attacks. Automated vulnerability scanning. Automated phishing. Automated credential stuffing. Security tools need to keep pace.
Supply chain attacks: Instead of attacking you directly, attackers compromise your dependencies or vendors. They inject malicious code into libraries you use. Your customers get compromised through you.
Ransomware: Ransomware attacks are becoming more sophisticated. Attackers encrypt your data and demand payment to decrypt it. They often also exfiltrate data and threaten to publish it.
Insider threats: Disgruntled employees stealing data. Contractors with access selling information. The threats come from inside your organization, not just outside.
Cloud misconfiguration: As more startups use cloud services, misconfigurations become attack vectors. Exposed S3 buckets, overly permissive IAM roles, unencrypted data.
The common thread: as systems get more complex, the surface area for attacks grows. Startups need to stay vigilant.

Building a Security-Conscious Culture
Ultimately, security isn't a technical problem. It's a cultural problem.
You can implement all the technical controls in the world, but if your engineers don't think about security, they'll find ways around them. If your founders don't prioritize security, it won't get resources.
Building a security-conscious culture means:
-
Making security everyone's job. It's not just the security team's responsibility. It's every engineer's responsibility. Product managers think about security implications of features. Designers think about secure user flows. Everyone considers security.
-
Celebrating security wins. When someone catches a vulnerability before it reaches production, celebrate it. When an engineer implements a security improvement, recognize them. Make security visible and valued.
-
Learning from incidents. When something goes wrong, treat it as a learning opportunity, not a reason to blame someone. Conduct a blameless postmortem. Figure out what happened and how to prevent it next time.
-
Investing in education. Security is complex. Keep your team educated. Send them to conferences. Provide training. Help them stay current.
-
Allocating resources. Security isn't free. Budget for it. Allocate engineering time. Pay for tools. Show through your resource allocation that security matters.
When security is embedded in your culture, people think about it naturally. They ask questions: "Is this exposing data? Are we encrypting this? Does this person really need this access?"
It becomes automatic. It becomes how you operate.

Runable: Automating Security and Compliance Workflows
As you scale your security practices, managing documentation, reports, and compliance workflows becomes complex. This is where automation helps.
Platforms like Runable can help startups automate the non-technical aspects of security management. You can generate security reports, compliance documentation, and incident response procedures without manual creation.
Runable enables you to create automated workflows for security tasks: generating monthly access review reports, creating incident response templates, producing compliance documentation. This frees your team to focus on actually implementing security controls rather than documenting them.
Use Case: Automatically generate monthly security access reports and compliance documentation, saving your team 5-10 hours per month on administrative work.
Try Runable For FreeStartups that use automation for security documentation can allocate more resources to actual security implementation. You're not trading off security for convenience; you're using automation to make security more efficient.
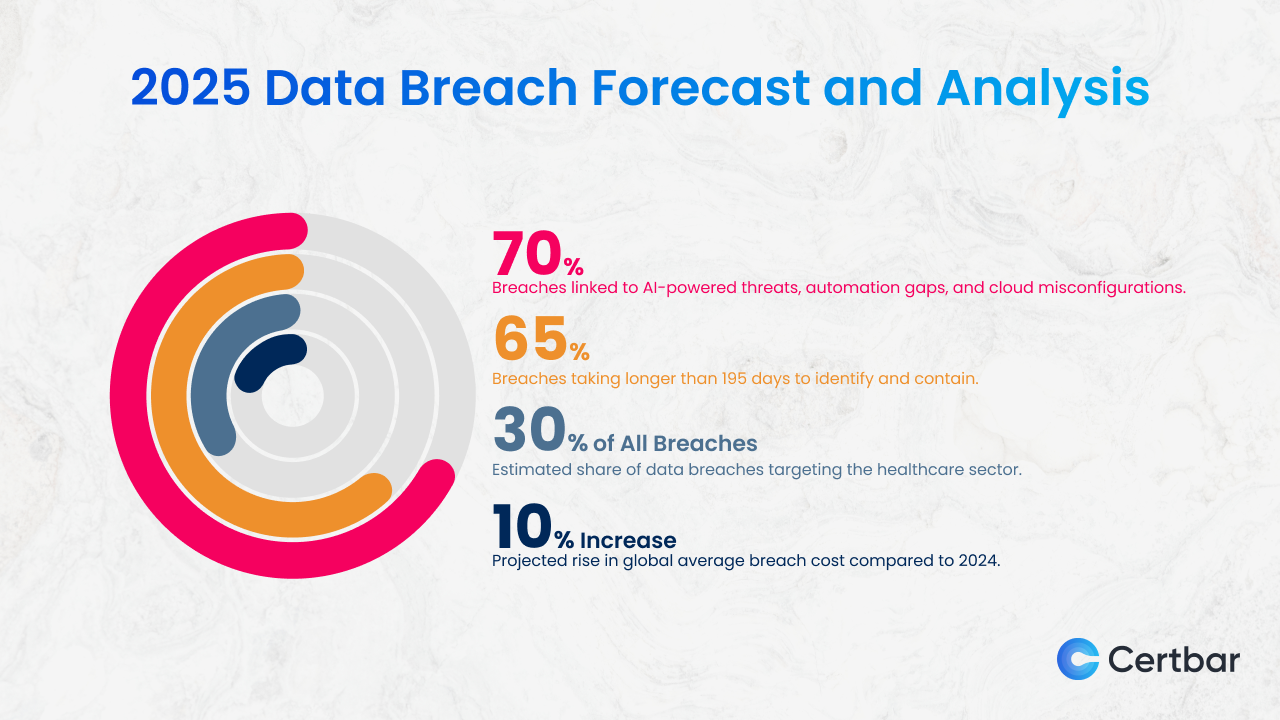
The Path Forward: From Reactive to Proactive
Most startups operate reactively. Something bad happens. You respond. You fix it. Then you move on.
The companies that survive—that thrive—operate proactively. They anticipate threats. They implement controls before something happens. They invest in security when things are going well, not after things go wrong.
This is the shift from "too small to hack" thinking to "building in private" thinking.
It's not complicated. It's not exotic. It's basic, fundamental security practices applied consistently from day one.
Gate your access. Encrypt everything. Monitor and centralize your infrastructure.
These three things will prevent the vast majority of attacks.
Add proper offboarding, dependency scanning, and monitoring, and you're in the 90th percentile of startup security.
The 306 million records exposed in 2025 breaches? Most could have been prevented with these basics.
The question is: will your startup be part of the 71% that get breached, or will you be the exception? Will you spend a few thousand dollars on security now, or millions dealing with a breach later?
The choice is yours. But choose consciously. Because the "too small to hack" myth just cost 306 million people their data.

FAQ
Why are startups specifically targeted by hackers?
Startups are targeted because they represent the perfect balance of opportunity and vulnerability. They hold valuable intellectual property and customer data, yet they typically lack the security infrastructure and dedicated security teams that larger organizations have. Hackers follow the path of least resistance, and startups provide both valuable targets and minimal security barriers.
How much of a startup's engineering resources should go to security?
There's no one-size-fits-all answer, but a useful rule of thumb is to allocate 5-10% of engineering time to security considerations in early stages, growing to 15-20% as you scale. This includes implementing controls, code reviews, dependency scanning, and monitoring. The exact amount depends on your risk profile and regulatory requirements.
Can a startup really implement encryption and access controls without a security team?
Absolutely. Basic encryption and access controls use standard tools and practices that any competent engineer can implement. You don't need a security expert to enable HTTPS, use a secrets management system, or implement role-based access control. What you need is the discipline to prioritize these practices.
What's the most important first step for a startup concerned about security?
Start by implementing the three critical controls: gate your access (use VPN, role-based access), encrypt everything (data at rest and in transit), and centralize your security infrastructure (basic logging and monitoring). These three practices will prevent the vast majority of attacks and can be implemented with minimal engineering effort and budget.
How long does it typically take to recover from a major data breach?
Recovery typically involves multiple phases spanning weeks to months: initial response and containment (24-48 hours), investigation and forensics (1-2 weeks), remediation and patching (1-3 weeks), notification to affected users (required by law), followed by ongoing legal, compliance, and reputation management issues that can extend for months or years. The total cost and impact depend on breach scope and your existing incident response processes.
Should startups invest in security tools immediately or focus on cultural practices first?
Focus on cultural practices and free or inexpensive open-source tools first. Tools like Wire Guard for VPN, Vault for secrets management, and your cloud provider's built-in security features cost little or nothing. The bigger investment is in mindset and discipline. Only move to premium tools when you've outgrown open-source options.
How can startups balance speed with security without sacrificing either?
Building security in from day one is actually faster than bolting it on later. Basic security practices like using a VPN, role-based access, and encryption integrate naturally into your development workflow. The key is to embed security thinking into your development process rather than treating it as a separate phase. Well-integrated security practices add minimal overhead while preventing catastrophic failures.
What's the relationship between startups' compliance requirements and security practices?
Compliance frameworks (GDPR, HIPAA, SOC 2) essentially codify good security practices. If you're building securely, you're already most of the way to compliance. The difference is documentation and formal processes. Compliance requirements actually provide a helpful structure for implementing security at scale.
How should a startup handle third-party security risks from vendors and integrations?
Treat third-party risk as part of your security architecture. Vet vendors before integrating their services. Understand what data they access and limit access to what's necessary. Review security practices and certifications. Include security requirements in contracts. Regularly audit third-party access. Avoid giving vendors blanket access to sensitive systems or data.
What's the biggest misconception founders have about startup security?
The biggest misconception is that security is a feature, not a requirement. Founders think "we'll add security after Series A" or "we'll hire a security team when we scale." But security debt compounds like technical debt, and unlike technical debt, security failures can be catastrophic and irrecoverable. Security is a foundational requirement, not an optional feature.
The bottom line: The 306 million records exposed in 2025 breaches represent real people whose privacy was violated. Many of those breaches happened at startups that thought they were too small to hack. Don't let your startup be next. Start with security basics today. Build in private from day one. The investment is minimal compared to the cost of cleaning up after a breach.

Key Takeaways
- 71% of data breaches now target small and medium-sized businesses, destroying the myth that startups are too small to hack
- 306+ million records were exposed in 2025 breaches, many at companies like PhoneMondo (5 employees, 10.5M exposed) and Tracelo (1.4M leaked)
- The startup culture prioritizing speed over security creates perfect conditions for breach: valuable IP, minimal security infrastructure, no dedicated security teams
- Three core controls prevent most breaches: gate your access (VPN, role-based access), encrypt everything (data at rest and transit), centralize monitoring (detect attacks early)
- Breaches cost an average of $4.45M and often represent 20-30% of startup revenue, making proactive security investment vastly cheaper than reactive remediation
- Building in private from day one is faster than bolting security on later; basic practices integrate naturally into development workflows
Related Articles
- Substack Data Breach: What Happened & How to Protect Yourself [2025]
- Substack Data Breach [2025]: What Happened & How to Protect Yourself
- ExpressKeys Password Manager: Complete Guide & Alternatives [2025]
- ExpressAI: The Privacy-First AI Platform Keeping Your Data Completely Safe [2025]
- European Governments Ditching Microsoft: Why Cloud Sovereignty Matters [2025]
- Harvard and UPenn Data Breaches: What You Need to Know [2025]




