Substack Data Breach [2025]: What Happened & How to Protect Yourself
It happened quietly. Five months between the initial breach and public disclosure. By the time Substack's CEO Chris Best sent that apology email in early February 2026, bad actors had already spent months with access to millions of email addresses and phone numbers. This wasn't a minor incident you could shrug off. This was a fundamental violation of trust for a platform that had grown to 50 million active subscriptions.
The Substack data breach is a wake-up call for content creators, newsletters, and readers who thought they were safe on one of the internet's most popular publishing platforms. It's also a window into how security incidents unfold in 2025, what companies do wrong, and what you should do right now to protect yourself.
Let's break down what actually happened, why detection took so long, and what specific steps you need to take today.
TL; DR
- What Happened: Attackers accessed Substack's systems in October 2025, stealing email addresses and phone numbers from an unknown number of users
- Critical Timeline: The breach occurred in October, but wasn't discovered until February 2026—a five-month gap that raises serious questions about monitoring
- Data Exposed: Email addresses and phone numbers confirmed compromised; financial data (credit cards, passwords) reportedly NOT accessed
- Company Response: Substack CEO apologized, said the vulnerability was fixed, but provided minimal details about scope or investigation findings
- Your Action: Change passwords immediately, enable two-factor authentication, watch for phishing attempts, and consider monitoring credit reports
- Bigger Issue: A five-month detection window suggests Substack lacked real-time security monitoring, a critical failure for a platform handling millions of user accounts

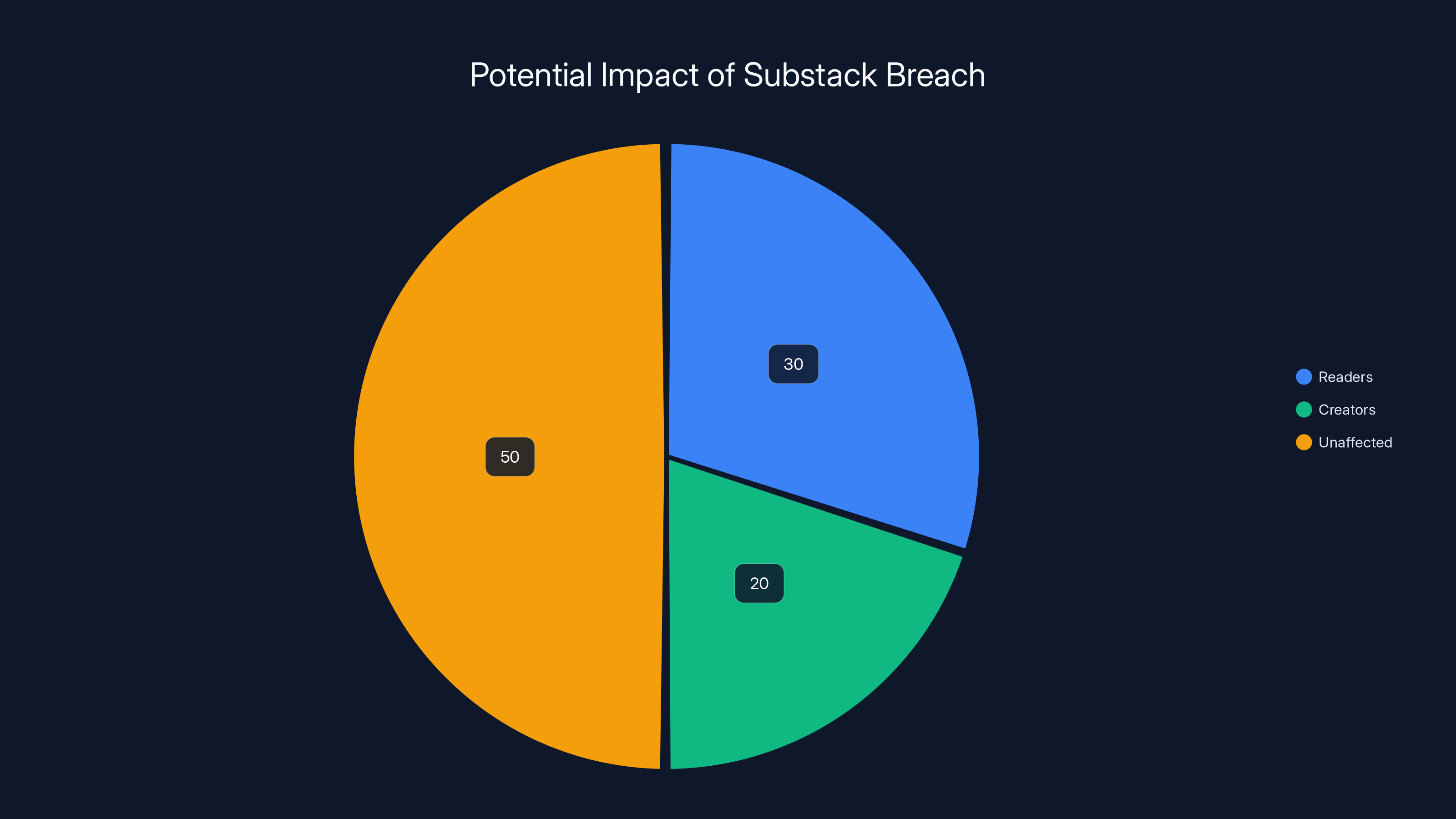
Estimated data suggests that readers and creators could be affected differently, with a significant portion potentially unaffected. Estimated data.
What Exactly Got Breached: The Data You Need to Know About
Here's what Substack actually confirmed: email addresses and phone numbers from user accounts were accessed without permission. That's the floor of the damage. But what does that really mean for your digital life?
Email addresses are your digital identity. They're the key to resetting passwords on any platform. They're what attackers use for credential stuffing attacks (trying your email with common passwords on other sites). They're also incredibly valuable on the dark web, where lists of stolen emails get packaged and sold for anywhere from a few cents to dollars per record, depending on how fresh they are.
Phone numbers are arguably worse. With your phone number in hand, attackers can attempt SIM swapping (convincing your carrier to transfer your number to a new phone they control), which gives them access to two-factor authentication codes. They can use your number for SMS-based phishing attacks. They can target you with social engineering. A phone number is a skeleton key to your digital accounts.
The silver lining: Substack says credit card numbers, passwords, and other financial data weren't compromised. If that's true (and it's a big if), you dodged the worst of it. No one's going to drain your bank account. But the information that was stolen is still dangerous. It's the kind of data that enables secondary attacks.
What we don't know—and what should infuriate you—is the scope. Substack never disclosed how many users were affected. Were it 1 million? 10 million? All 50 million active subscriptions? The company refused to say. That's not transparent. That's evasive.
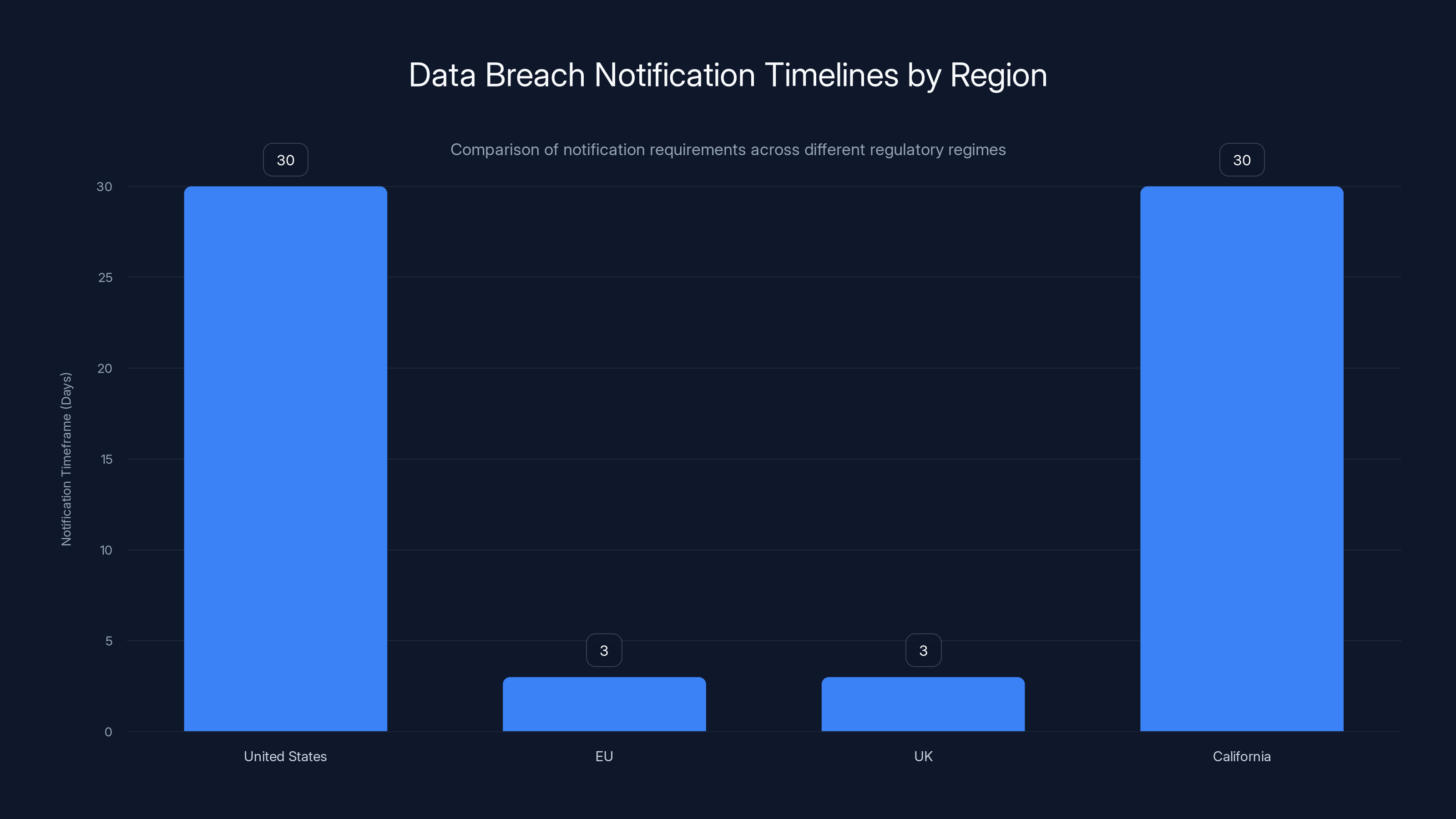
The EU and UK require notification within 3 days, while the US and California generally allow up to 30 days. Estimated data based on typical regulatory requirements.
The Detection Failure: Why Five Months Is Unacceptable
Let's talk about the elephant in the room. The breach happened in October 2025. Substack discovered it in February 2026. That's a five-month gap. Think about what that means.
For five months, attackers had an open door to Substack's systems. For five months, they could have accessed more data, exfiltrated additional information, or deepened their access for future attacks. For five months, Substack had no idea their customers' information was being stolen.
This isn't a minor timeline detail. This is the most damning part of the entire incident.
A company with 50 million active users should have security monitoring in place that detects unauthorized system access in hours, not months. Modern infrastructure includes security information and event management (SIEM) tools that alert teams to suspicious activity in real time. Cloud providers offer automated intrusion detection. There's no excuse for a five-month detection window.
The most likely explanation? Substack either didn't have adequate monitoring in place, or the monitoring existed but nobody was actively watching the alerts. Both scenarios are failures of operational security. Both suggest the company treated security as a checkbox, not a continuous responsibility.
Worse, Substack hasn't explained why detection took so long. Was there an alert they missed? Did a security team member spot it but the message got lost in communication? Was monitoring not configured correctly? The company's silence here is deafening. Until we know what went wrong, we have to assume they're not willing to acknowledge the real problem.
Timeline of the Breach: What We Know and What's Missing
Let's reconstruct the known timeline, because the gaps are as important as the facts.
October 2025: Someone gains unauthorized access to Substack's systems. We don't know how. It could have been a phishing attack against an employee, an unpatched vulnerability in a public-facing service, compromised credentials purchased from a dark web marketplace, or insider access. Substack hasn't said.
October 2025 to Early February 2026: The attacker (or attackers) has access for five months. They exfiltrate email addresses and phone numbers. Substack's security team is oblivious. Maybe no one's monitoring the logs. Maybe alerts are disabled. Maybe the logs themselves aren't being checked.
Early February 2026: Something finally triggers detection. We don't know what. Did a security researcher contact Substack about seeing their data for sale on the dark web? Did someone notice suspicious activity by accident? Did a threat intelligence feed pick it up? Substack hasn't said.
Early February 2026: Substack launches an investigation. How thorough is this investigation? Days? Weeks? We don't know. Typically, incident response takes days to determine scope, attribute the attack, and understand what was accessed. But we're never told the investigation timeline.
Early February 2026: CEO Chris Best sends an email to affected users. The email is apologetic but short on details. Best says the company "fixed the problem" and is investigating, but provides no technical specifics about what the vulnerability was, how it was introduced, or how it was resolved.
The gaps in this timeline are where the real story lives. Every gap represents a question Substack won't answer.
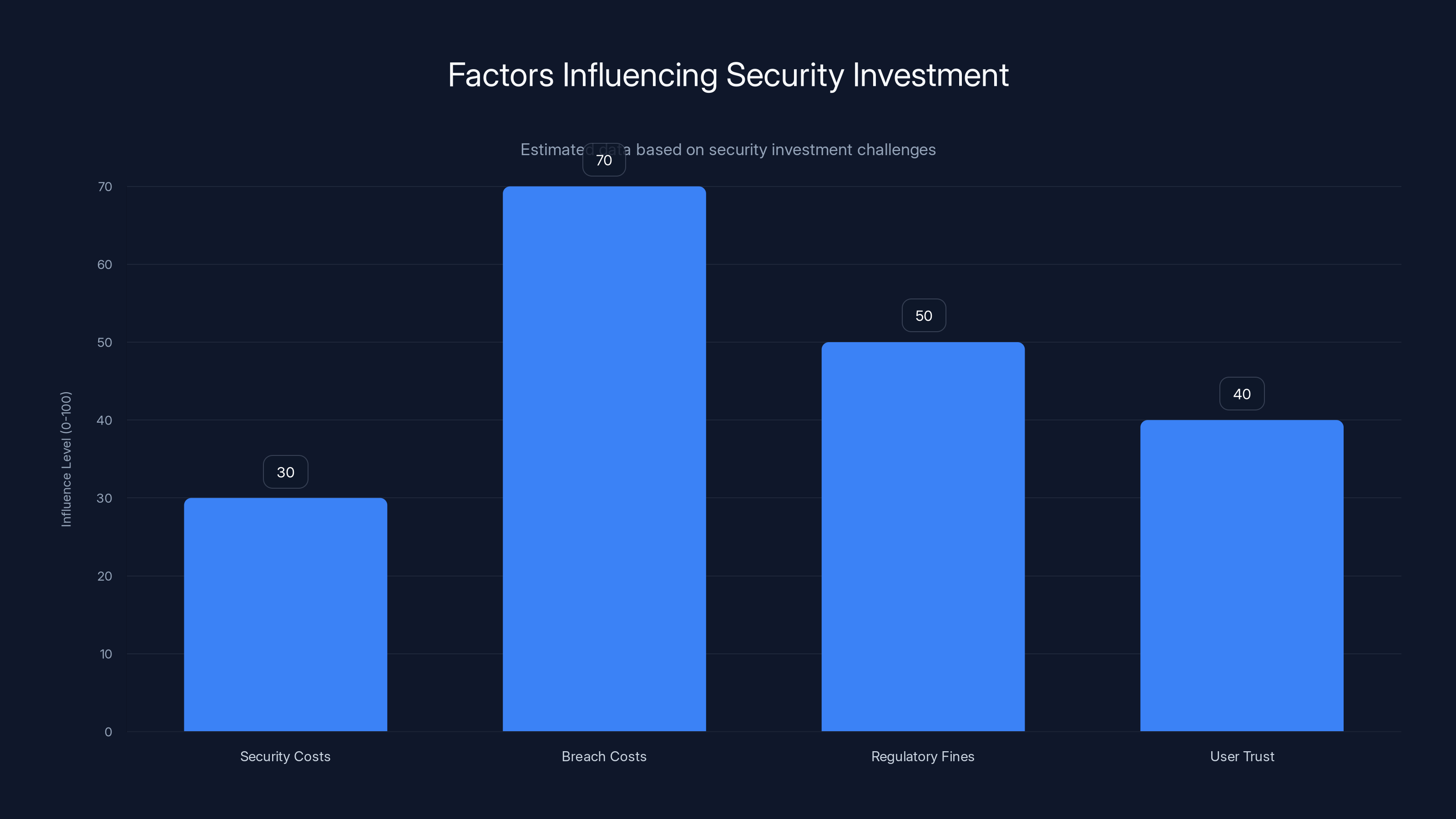
Security investment is heavily influenced by breach costs and regulatory fines. Estimated data shows that while security costs are a factor, the potential costs of breaches and fines are more significant motivators.
Why Detection Took So Long: The Structural Problems
The five-month detection window didn't happen by accident. It's the result of specific failures in how Substack manages security operations.
First failure: Inadequate monitoring. If a company actually had SIEM tools and intrusion detection systems in place, a five-month breach would be nearly impossible. These tools generate alerts for suspicious database access, unusual data exfiltration patterns, and credential compromise. The fact that Substack didn't catch this suggests they either didn't have these tools, or had them but didn't use them effectively.
Second failure: No alert fatigue management. Security teams often struggle with alert fatigue, where so many notifications come in that important alerts get buried. Did Substack have so many alerts that the real intrusion went unnoticed? Possibly. That's still a failure, just a specific kind.
Third failure: Lack of threat intelligence integration. Some companies subscribe to threat intelligence services that monitor dark web marketplaces and track where stolen data appears. If Substack had integrated this intelligence into their operations, they might have heard that their user data was being sold, which could have triggered investigation. They didn't, or didn't act on it.
Fourth failure: No assumption of breach mentality. Security experts talk about "zero trust" and "assume breach" frameworks. The idea is that you assume attackers are already in your systems, so you monitor aggressively for lateral movement, data exfiltration, and persistence mechanisms. Substack's five-month window suggests they weren't operating with this mindset.
Fifth failure: Probably inadequate incident response planning. When you do discover a breach, how quickly can you act? Do you know which systems to check first? Do you have the right people on call? Can you forensically preserve evidence without contaminating it? If Substack's incident response wasn't planned, the weeks or months after discovery could have been chaotic, leading to further delays in understanding scope.
Each of these failures is fixable. Each is also inexcusable at Substack's scale.
The Attack Vector: How Did Attackers Get In?
Substack never explained the attack vector. That's another critical gap in transparency. But based on common attack patterns against Saa S platforms, the likely scenarios are:
Phishing and credential compromise is the most common attack vector against enterprise systems. An employee receives a convincing email pretending to be from IT, clicks a link, enters credentials on a fake login page, and boom—attacker has an employee account. From there, they can explore internal systems, look for admin accounts, and escalate privileges. Substack employees use the same tools as thousands of other companies, so there's nothing unique about their security awareness training that would make them immune.
Unpatched vulnerabilities in public-facing applications are the second most common. If Substack was running outdated software with known vulnerabilities, attackers could exploit those vulnerabilities remotely, gaining initial access without any credentials at all. Once inside, lateral movement to systems holding user data is relatively straightforward for someone with technical skills.
Compromised third-party access is a growing risk. If Substack integrated with third-party vendors or service providers, attackers might compromise one of those vendors first, then use that access to infiltrate Substack. This is harder to defend against because you're trusting your partners' security posture.
Insider threat is always possible but statistically less likely. An employee or contractor with existing access steals data. No external break-in required. But Substack hasn't suggested this is what happened, so it's probably not the culprit here.
Social engineering targeting multiple employees could have revealed credentials or sensitive information that helped attackers gain access. If the attackers were particularly determined, they might have called Substack employees pretending to be IT support, asking questions that gradually revealed information about the architecture and security systems.
The fact that Substack won't say which vector was exploited is frustrating. It prevents the broader tech community from learning what went wrong and how to avoid similar attacks. It also makes it harder for users to assess the level of negligence involved.

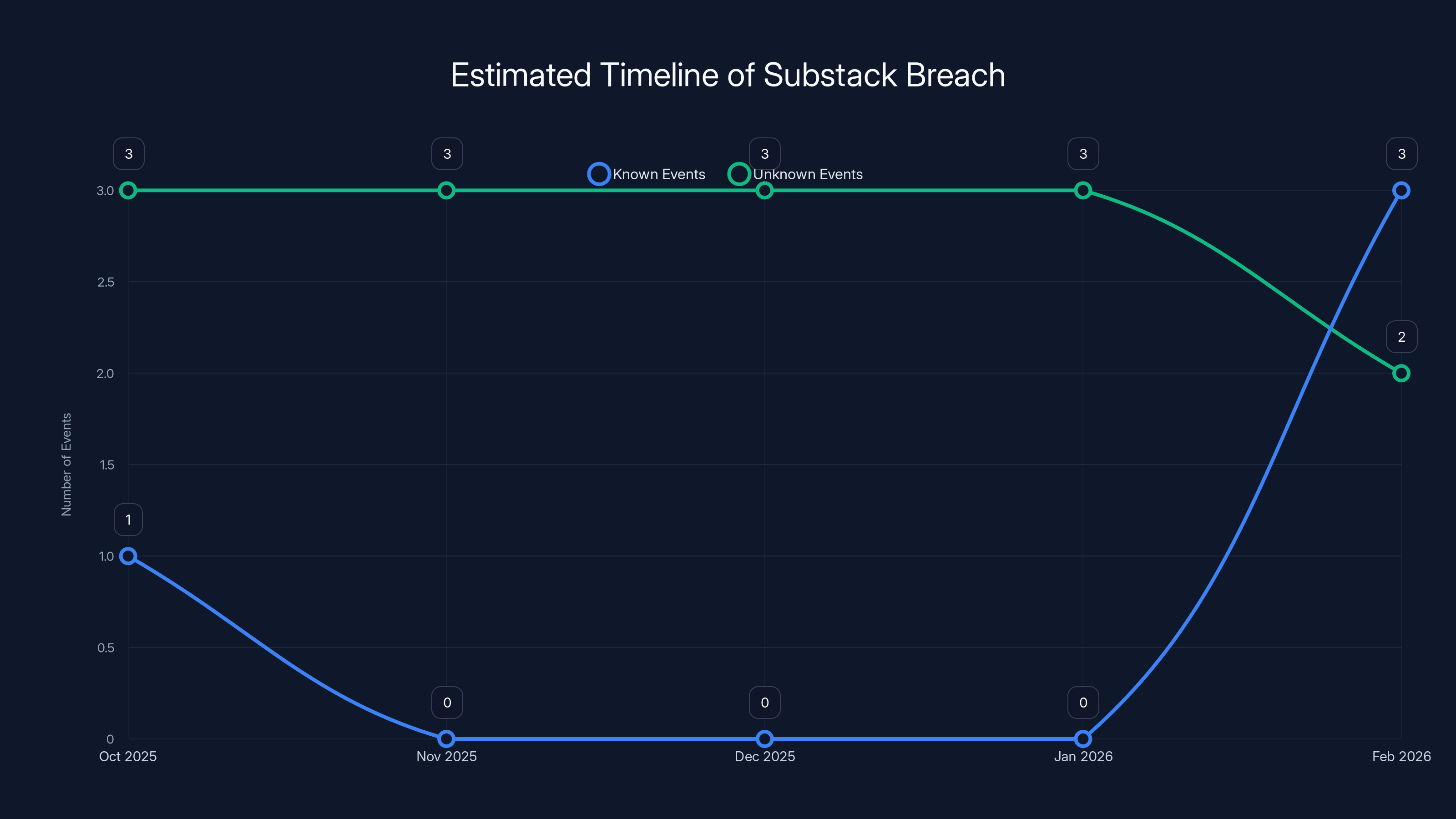
The timeline highlights the significant gaps in the known events of the Substack breach, with more unknown events than known ones. Estimated data.
What Data Is Most Valuable to Attackers
Your email address and phone number might seem mundane, but on the dark web, they're incredibly valuable when sold together.
Email + phone number combos are used for:
- Account takeover attacks: Attackers use your email to request password resets on your financial accounts. They use your phone number to intercept SMS codes. Boom, they're in.
- SIM swapping: Call your phone carrier pretending to be you, say your SIM card is damaged, and request a transfer to a new phone they control. Now they intercept all SMS messages, including two-factor codes.
- Phishing campaigns: Highly targeted phishing emails are more convincing and more likely to work than mass campaigns. Knowing your email gives attackers a vector. Knowing you're a Substack user (from the platform info) helps them craft convincing emails.
- Identity theft: Attackers use email and phone to reset passwords on other platforms, gradually building access to more and more accounts.
- Dark web resale: Some attackers simply harvest data and sell it to criminal syndicates who use it for all of the above.
The value of this data depends on several factors. If your email hasn't been previously breached, it's worth more. If you're a high-profile creator or user, it's worth more. If your email is associated with financial accounts, it's worth more. None of this is reassuring.

Substack's Response: What the Company Said (and Didn't)
CEO Chris Best's email to users was brief and somewhat evasive. Let's break down what he said and what he conspicuously didn't say.
What Best said:
- A security incident resulted in email addresses and phone numbers being shared without permission
- He's "incredibly sorry this happened"
- The company takes responsibility seriously but "came up short"
- Credit cards, passwords, and financial data were not affected
- The company identified the issue in February
- The company fixed the problem
- An investigation is underway
What Best didn't say:
- When exactly the breach was discovered ("early February" is vague)
- How many users were affected
- What the vulnerability was
- How attackers gained initial access
- Whether customer data was actually sold or is being sold
- What specific steps Substack took to prevent this in the future
- Whether law enforcement was involved
- Whether the company was contacted by attackers demanding ransom
- What the investigation timeline is
- Whether customers should expect any compensation or credit monitoring
The email is a masterclass in saying just enough to sound apologetic without actually committing to transparency. It hits the required emotional beats ("I'm incredibly sorry") without providing the information users need to actually assess the damage and take action.
Tech Crunch (the original source of this story) asked Substack for more details. As of the time of the original reporting, Substack hadn't provided additional information. That's not surprising. Companies often maintain silence beyond the initial notification because further disclosure might expose them to litigation or regulatory action.
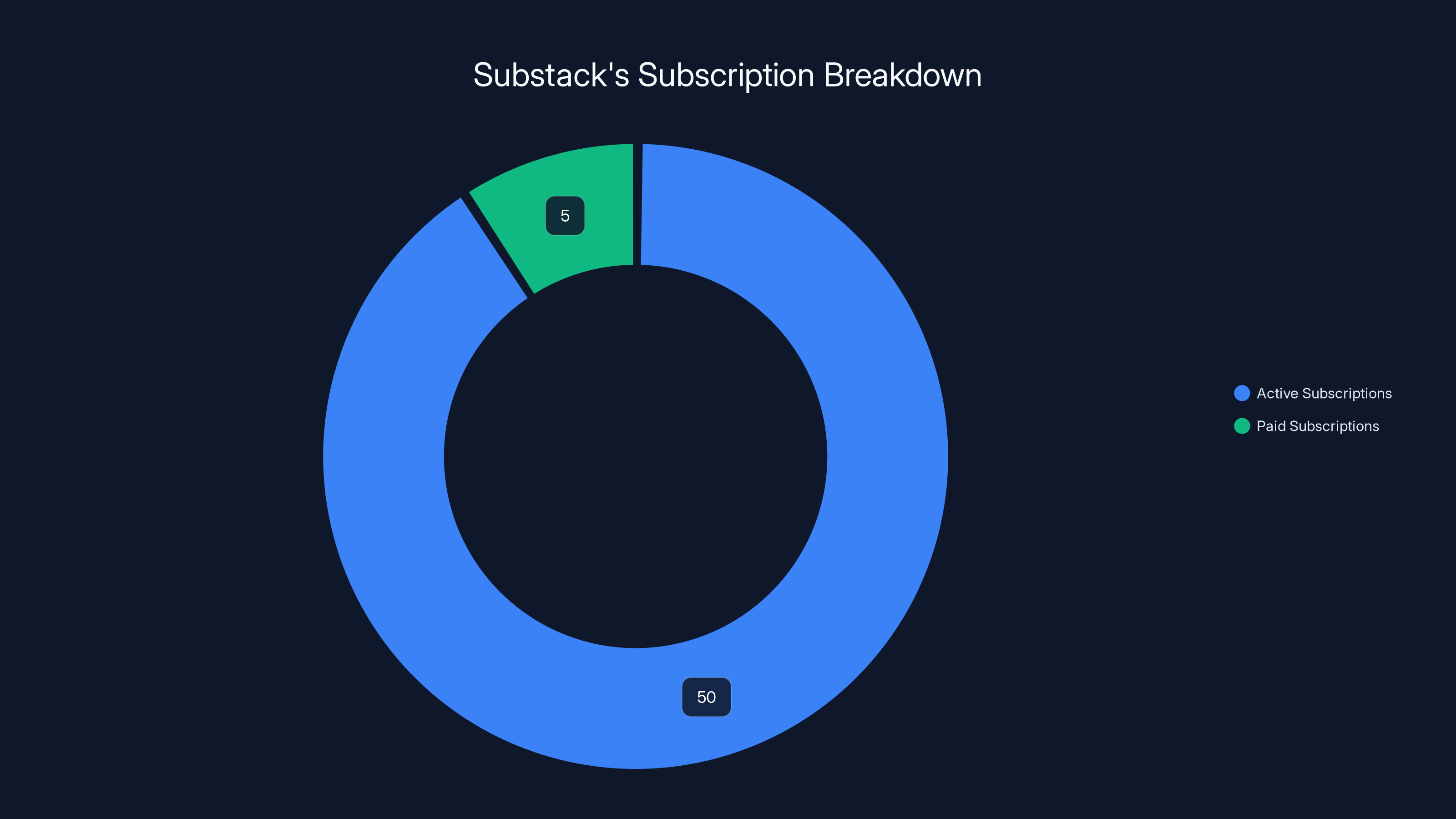
Substack has a total of 50 million active subscriptions, with 5 million being paid. This highlights the platform's significant role in independent media.
The Regulatory Angle: What Laws Apply Here
Substack operates globally, which means multiple regulatory regimes apply to this breach.
In the United States, individual states have data breach notification laws. Most require companies to notify affected residents if unencrypted personal information is exposed. The definition of "personal information" varies by state but generally includes names, email addresses, and phone numbers. Substack's notification to users satisfied most state requirements, though some states require notification within specific timeframes (often 30 days of discovery, or the time the breach was publicly disclosed, whichever is earlier). The five-month gap between breach and discovery works in Substack's favor here; the clock starts when they discovered it, not when it happened.
The FTC (Federal Trade Commission) can investigate whether Substack's practices violated the FTC Act, which prohibits unfair or deceptive practices. If Substack claimed to have strong security but demonstrably didn't, that could be deceptive. The five-month detection window might be evidence that the company failed to implement reasonable security measures.
In the EU, the GDPR (General Data Protection Regulation) is far stricter. The regulation requires companies to implement appropriate technical and organizational measures to protect personal data. The GDPR also requires notification to the relevant supervisory authority within 72 hours of becoming aware of a personal data breach. Given that Substack discovered the breach in February 2026, they should have notified the relevant EU authorities within 72 hours. Any delay beyond that could result in fines up to 10 million euros or 2% of annual revenue, whichever is higher.
In the UK, following Brexit, GDPR still applies due to the UK's own data protection laws being largely equivalent. Similar notification timelines and fines apply.
In California, CCPA (California Consumer Privacy Act) gives users the right to know what personal information companies have collected, to delete it, and to opt out of sale. Substack's breach involved data that residents couldn't prevent being collected, so CCPA remedies are limited here. But if Substack experiences further breaches due to inadequate security practices, CCPA could be relevant for future incidents.
The regulatory consequences might actually be more significant than the direct damage to users. If the FTC or EU authorities investigate and determine that Substack failed to implement reasonable security measures, the company could face substantial fines, forced operational changes, or both.
What You Should Do Right Now: Immediate Actions
You've been notified that your data was breached. What do you actually do? Here's a prioritized list of immediate actions.
Step 1: Change your Substack password immediately. Not tomorrow. Not after you finish reading this. Right now. Make it a strong, unique password that you don't use anywhere else. Use a password manager if you have one. If you reused your Substack password on other sites (which you shouldn't have, but you probably did), you have a bigger problem. See Step 3.
Step 2: Enable two-factor authentication on Substack. If you haven't already, set this up today. Use an authenticator app (Google Authenticator, Authy, Microsoft Authenticator) rather than SMS if possible. SMS-based 2FA is better than nothing, but it's vulnerable to SIM swapping. An app-based authenticator is significantly more secure. If Substack doesn't offer app-based 2FA, use SMS and then contact Substack to request they add stronger 2FA options.
Step 3: Check for password reuse. Log in to haveibeenpwned.com and enter your email address. This will tell you if your email appears in any known data breaches. For each breach where you appear, check what password you used at that time. If you reused that password on Substack or other important accounts, change those passwords immediately. This is a tedious process, but it's critical. If you used the same password on multiple sites, attackers can log in to all of them.
Step 4: Monitor your credit reports. Go to annualcreditreport.com (the official site authorized by the FTC) and pull your credit reports from Equifax, Experian, and Trans Union. Look for accounts you don't recognize. Check for hard inquiries (requests for new credit) that you didn't authorize. If your phone number was compromised, attackers might attempt to open accounts using that number. Catching this early gives you the best chance of preventing identity theft. You can pull one free report every 12 months, so stagger them (one in February, one in May, one in August) for continuous monitoring.
Step 5: Consider a credit freeze. If you're particularly concerned about identity theft, you can freeze your credit with the three major bureaus. This prevents anyone (including you) from opening new accounts in your name without unfreezing first. It's an inconvenience, but it's strong protection. You can freeze for free, though you'll need to unfreeze if you want to apply for credit yourself.
Step 6: Watch for phishing. Attackers often follow up a data breach with targeted phishing. Since they know your email came from Substack, they'll craft convincing emails pretending to be from Substack (asking you to verify your account, reset your password, confirm payment information, etc.). Be suspicious of any emails asking you to click links or enter information. When in doubt, go directly to Substack.com in your browser rather than clicking links in emails.
Step 7: Check for SIM swapping attempts. Call your phone carrier and ask if anyone has attempted to transfer your phone number to a different account. If so, strengthen your phone account security (longer PIN, additional security questions, etc.). Some carriers let you add a special note to your account requesting human verification before any SIM swaps are allowed.
Step 8: Use a phone number monitoring service. Services like Truecaller and similar apps can notify you if your phone number is used in suspicious ways. This is optional but adds another layer of visibility.
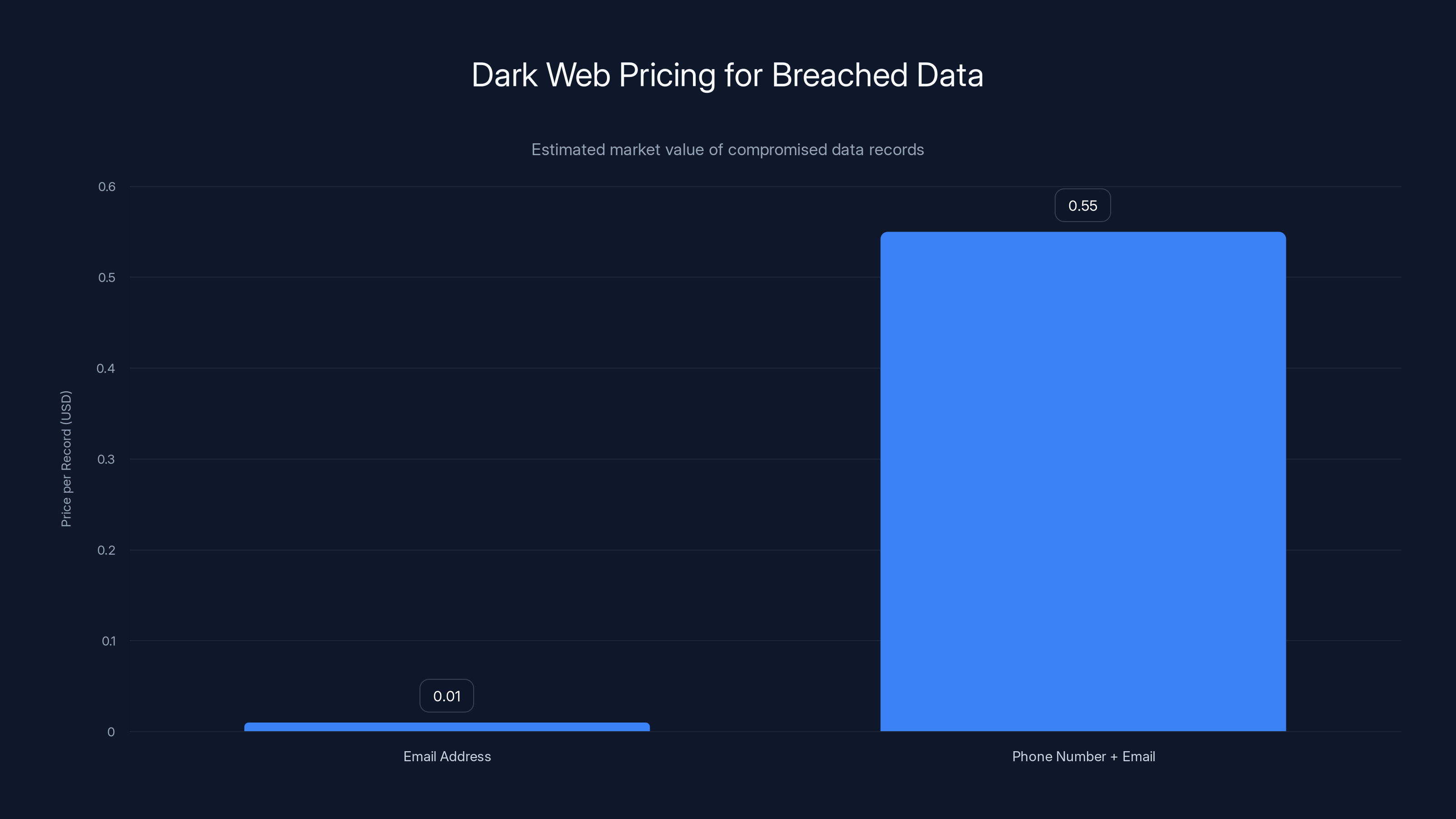
Email addresses from breaches can sell for as little as
Substack's Context: Why This Matters Beyond Creators
Substack isn't just another Saa S platform. It's become central infrastructure for independent media. As of the latest data, Substack has over 50 million active subscriptions, with 5 million paid subscriptions. That's not just hobbyist newsletters. Major journalists, political commentators, scientists, and thought leaders use Substack as their primary publishing platform. Some of them make six or seven figures annually from Substack.
When Substack's security fails, it's not just a privacy issue for readers. It's a business threat for creators. If attackers get their email and phone number, they can attempt to take over their accounts, steal their subscriber lists, or impersonate them. For creators making significant income from Substack, account takeover could be catastrophic.
The breach also reflects on Substack's credibility as a platform. Creators considering whether to build their business on Substack now have evidence that the platform may not take security seriously. In early 2025, Substack had been raising substantial capital (a $100 million Series C in July 2025). A major security breach is exactly the kind of thing that makes investors nervous about a platform's long-term viability.
Substack's larger context also matters for understanding the broader Saa S landscape. If a platform with 50 million users and $100 million in recent funding can take five months to detect a breach, what about smaller platforms? What about startups with skeleton engineering teams? If Substack—a well-funded, well-regarded platform—failed this badly at security, the implication is that security failures are endemic across the entire industry.
Lessons for Other Companies: What Not to Do
Every company can learn from Substack's failures. Here's what other companies must do differently.
Implement continuous security monitoring: Use SIEM tools, intrusion detection systems, and automated alerts. Configure these tools to detect unusual database access, large data exports, and suspicious user activity. Monitor these alerts actively. If you're getting too many alerts to monitor effectively, adjust your thresholds or add filtering. The goal is to detect breaches in hours, not months.
Integrate threat intelligence: Subscribe to threat intelligence feeds that monitor dark web marketplaces, paste sites, and other locations where stolen data appears. If your data shows up for sale, you'll know within days, not months.
Implement zero trust architecture: Don't assume employees or internal systems are trustworthy. Require authentication for every access, monitor all data movement, and assume that attackers are already inside your network. This changes how you architect your systems, but it's the foundation of modern security.
Plan for incident response: Before a breach happens, create a detailed incident response plan. Who's on the incident response team? What tools do you use to investigate? How do you preserve evidence without contaminating it? What's your notification process? How do you communicate with customers? Planning ahead means you respond in days rather than weeks.
Be transparent in your disclosure: When you do disclose a breach, tell customers exactly what happened, when it happened, when you discovered it, what data was affected, how many people were affected, and what you're doing to prevent it from happening again. Transparency builds trust. Evasiveness destroys it.
Invest in security engineering: Security isn't an afterthought. It's a core engineering discipline. Hire security engineers early, involve them in architecture decisions, and fund security infrastructure as a first-class concern, not a second-class afterthought.
The Broader Security Landscape: Why This Keeps Happening
Substack's breach is part of a pattern. In 2025, major breaches were constantly in the news. Attackers are getting better. Infrastructure is getting more complex. Security is getting harder. But companies aren't getting more serious about it.
The fundamental problem is that security costs money and resources, while the benefits are invisible until a breach happens. As long as a company can operate without a major incident, the economic incentive is to underfund security. Only after a breach happens—and the company has to spend millions on incident response, notification, remediation, and legal fees—does security suddenly become a priority.
This is a structural problem in tech economics. It won't change until regulators start imposing fines large enough to make security investment economically rational. The GDPR is beginning to do this in Europe (with fines up to 2% of annual revenue). The FTC is beginning to do this in the US (with enforcement actions and mandatory remediation). But until these regulatory consequences become consistent and large, companies will continue to treat security as optional.
For users, this means you have to assume every major platform will experience a breach eventually. You have to operate with that assumption. You have to use strong, unique passwords everywhere. You have to enable two-factor authentication everywhere. You have to monitor your financial accounts regularly. You can't rely on companies to keep your data safe. You have to take that responsibility on yourself.
What Substack Should Have Done: A Roadmap for Remediation
If Substack wanted to genuinely earn back customer trust after this breach, here's what the company should do.
First, provide complete transparency: Tell customers exactly what happened. What was the vulnerability? How did attackers get in? When was access first gained? When was it detected? How was it discovered? What data was actually accessed? How many customers does that affect? If you don't know the answers to all these questions, you haven't finished your investigation.
Second, offer concrete compensation: Free credit monitoring for affected users for at least two years. Affected users didn't choose to be part of this breach; the company forced them into it. Offering credit monitoring is the bare minimum. Some companies offer identity theft insurance or account credit. Substack has offered nothing publicly.
Third, undergo third-party security audit: Hire a reputable external security firm to audit Substack's entire security posture. Where are the gaps? What's missing? Publish a remediation roadmap and timeline. Then actually follow it. This transparency proves you're serious about fixing the underlying problems.
Fourth, implement bug bounty program: Let the broader security community help find vulnerabilities before attackers do. Offer meaningful rewards (not $50 per bug, but thousands for serious issues). Publish how many bugs have been found and fixed.
Fifth, hire a Chief Information Security Officer: Get someone in a leadership role who is accountable for security outcomes. Not a CTO who has security as one of five responsibilities. Someone whose sole job is to make sure breaches don't happen.
Sixth, commit to continuous monitoring: Implement the monitoring systems that should have been in place years ago. Share metrics about detection times. Publish information about your threat detection program. Show that the gap between breach and discovery will never be five months again.
None of this will undo the breach. But it would demonstrate that the company is serious about remediation rather than just trying to make the problem go away.
FAQ
What exactly happened in the Substack breach?
Attackers gained unauthorized access to Substack's systems in October 2025 and exfiltrated email addresses and phone numbers from user accounts. The breach went undetected for five months until Substack discovered it in early February 2026. Credit card numbers, passwords, and financial information were not compromised according to the company's statement.
How many Substack users were affected by the breach?
Substack has not disclosed the number of affected users. The company's platform has over 50 million active subscriptions, but the breach could affect anywhere from a subset of that to the entire user base. The lack of disclosure makes it impossible to assess the true scope of the incident.
Why did it take five months to detect the breach?
Substack has not provided a detailed explanation for the five-month detection gap. The most likely explanation is that the company lacked adequate security monitoring systems (SIEM tools, intrusion detection, etc.) or failed to actively monitor the alerts they did have in place. This represents a significant failure in operational security practices.
Should I delete my Substack account?
Whether to delete your account depends on your risk tolerance. If you use Substack as a reader, the risk is relatively low (you're mostly concerned about email/phone compromise). If you're a creator with significant income, you might consider whether the security risk affects your decision to continue using the platform. Substack has not provided enough information to make this decision with confidence.
What should I do if I have a Substack account?
Immediate actions include changing your password, enabling two-factor authentication, checking haveibeenpwned.com for other breaches involving your email, monitoring credit reports for suspicious activity, and watching for phishing emails. These steps protect you from the most likely secondary attacks following the breach.
Could my identity be stolen because of this breach?
Identity theft is possible but not inevitable. Attackers need more than just email and phone to steal your identity (they typically need SSN, date of birth, etc.). However, your email and phone can be used to reset passwords, intercept two-factor codes, and gain access to other accounts. The risk is real and should be taken seriously, which is why active monitoring is essential.
Will Substack offer compensation or free credit monitoring?
As of the original reporting, Substack has not publicly offered compensation or free credit monitoring. The company offered only an apology and assurance that the problem was fixed. Given similar breaches at other companies, Substack may face pressure to offer credit monitoring, but nothing has been announced.
Is Substack shutting down because of the breach?
No, Substack remains operational and is not shutting down. The breach is a serious security failure, but it's not an existential threat to the company unless it leads to massive exodus of creators or regulatory action. The platform continues to function normally for readers and creators.
How does this compare to other major data breaches?
The Substack breach is significant in scope (50 million potential users) and in the detection timeline (five months). Most major breaches are detected within weeks due to modern monitoring practices. The five-month window suggests more fundamental security failures than typical breaches, making it more concerning from an operational perspective.
What regulatory consequences could Substack face?
Substack could face investigations from the FTC for allegedly failing to implement reasonable security measures. If the company operates in EU countries, it could face GDPR investigations and potential fines up to 10 million euros or 2% of annual revenue. State-level investigations in California and other states are also possible. The regulatory consequences could be more significant than the direct customer impact.

Conclusion: The Aftermath and Future
The Substack data breach is a watershed moment for the platform, its users, and the broader Saa S ecosystem. It's not the scale of the breach that makes this incident significant (50 million potential users is huge but not unprecedented in our post-2013 world). It's the five-month detection window that reveals something more troubling: a company with substantial funding and resources failed to implement basic security practices that have been industry standard for over a decade.
For Substack users and creators, the immediate task is clear. You can't rely on the platform to protect your data. You have to protect yourself through strong passwords, two-factor authentication, and active monitoring. The breach has already happened. The data is already exposed. The only question now is whether you'll take the steps to prevent secondary attacks.
For other companies, Substack serves as a cautionary tale. A five-month detection window isn't a hypothetical risk. It's not a theoretical concern. It actually happened. If it happened to Substack, it can happen to any company that doesn't invest seriously in continuous security monitoring, threat intelligence integration, and incident response planning.
For regulators, this breach should be a trigger for investigation. The FTC should examine whether Substack's security practices met the "reasonable security" standard required by law. The EU authorities should investigate whether the company met GDPR notification timelines (which we won't know for certain until more details emerge). These investigations matter because they set precedent for what companies must do to protect user data.
The worst outcome would be if this breach becomes one more forgotten incident in an endless parade of data breaches. The slightly better outcome would be if Substack takes genuine remediation seriously, becomes a leader in transparency about security practices, and demonstrates that even after a major breach, a company can rebuild customer trust. The best outcome would be if this breach becomes a catalyst for the entire industry to take security seriously as a core engineering discipline, not a checkbox on a compliance list.
For now, assume Substack's data is in circulation. Assume that email and phone will be used for attacks. Assume you need to actively defend yourself. And assume that no company—no matter how well-funded or well-regarded—will protect your data better than you will protect it yourself.
Change your password. Enable 2FA. Monitor your accounts. Because the next breach is coming, and you need to be ready.
Key Takeaways
- Substack's data breach exposed email addresses and phone numbers from an unknown number of users in October 2025, with detection delayed until February 2026—a five-month gap that indicates inadequate security monitoring
- The combination of email and phone number enables secondary attacks like SIM swapping, password resets, and phishing, making this breach more dangerous than it initially appears
- Immediate actions include changing your Substack password, enabling two-factor authentication, checking haveibeenpwned.com, and monitoring credit reports for fraud
- Substack's minimal disclosure (no user count, no technical details about the vulnerability, no compensation offered) raises questions about the company's transparency and accountability to users
- The five-month detection window suggests fundamental failures in security infrastructure that Substack must remediate through investment in SIEM monitoring, threat intelligence integration, and incident response planning
Related Articles
- ExpressKeys Password Manager: Complete Guide & Alternatives [2025]
- Harvard and UPenn Data Breaches: What You Need to Know [2025]
- Password Security Guide: Why Strong Credentials Matter in 2025
- 8.7 Billion Records Exposed: Inside the Massive Chinese Data Breach [2025]
- European Governments Ditching Microsoft: Why Cloud Sovereignty Matters [2025]
- Substack Data Breach Exposed Millions: What You Need to Know [2025]
![Substack Data Breach [2025]: What Happened & How to Protect Yourself](https://tryrunable.com/blog/substack-data-breach-2025-what-happened-how-to-protect-yours/image-1-1770303986528.jpg)



