The Counterfeiting Crisis Is Bigger Than You Think
Every year, luxury brands hemorrhage more than $30 billion to counterfeit goods. That's not pocket change. That's entire departments, research budgets, and brand heritage getting hollowed out by sophisticated fakes. According to a recent whitepaper, the impact of counterfeit goods extends beyond luxury brands, affecting various industries including pharmaceuticals.
But here's where it gets weird: the problem isn't just affecting brands anymore. The second-hand luxury market has exploded to $210 billion annually, and buyers are terrified. You can't tell if that Hermès bag is real or a "superfake" anymore. The fakes have gotten so good that some luxury boutiques literally stopped authenticating items in-store because they couldn't tell the difference themselves. This issue is highlighted in a review of Mytheresa, where the authenticity of luxury items is a significant concern for buyers.
That's not hyperbole. Store employees trained for years in spotting fakes were throwing their hands up.
So what do you do when traditional authentication methods fail? You get creative. You build something that can't be faked using the same tools counterfeiters use.
That's where Veritas comes in. This startup has developed a combination of custom hardware and cryptographic software that's designed to be tamper-proof. The approach is clever because it doesn't just rely on physical markings or hologram tricks. It combines a microscopic chip, digital certificates, and blockchain-based product records to create an authentication layer that's far harder to bypass. This innovative approach is discussed in a TechCrunch article.
Understanding the Anatomy of Counterfeiting
Counterfeiting isn't some dark web conspiracy anymore. It's a sophisticated, well-funded industry with supply chains almost as complex as legitimate fashion houses. According to the NBC5 report, these scams are increasingly prevalent on platforms like Facebook Marketplace.
When we talk about counterfeits, we're not just talking about cheap knockoffs you'd find at a street market. We're talking about "superfakes." These are products so convincingly made that they fool people who work in authentication professionally. They have correct stitching patterns, accurate hardware, matching wear marks, and forged certificates that look identical to originals.
The economics are brutal. A counterfeit Louis Vuitton bag that costs maybe
What makes this worse is that the second-hand market explosion has created perfect cover for counterfeiters. Legitimate sellers and fraudsters operate in the same marketplaces. Buyers use the same apps. Without a clear, verifiable authentication method, everyone's just guessing.
Luxi Holland, the founder of Veritas, came at this problem from an unusual angle. She's not just a tech person. She's also trained as an artist with experience in mixed media painting and metal sculpture. She worked as a technical product manager at Tesla, where she got comfortable bridging the gap between hardware constraints and software innovation. That combination of design sensibility and technical depth matters because authentication hardware has to be both physically beautiful and cryptographically sound.

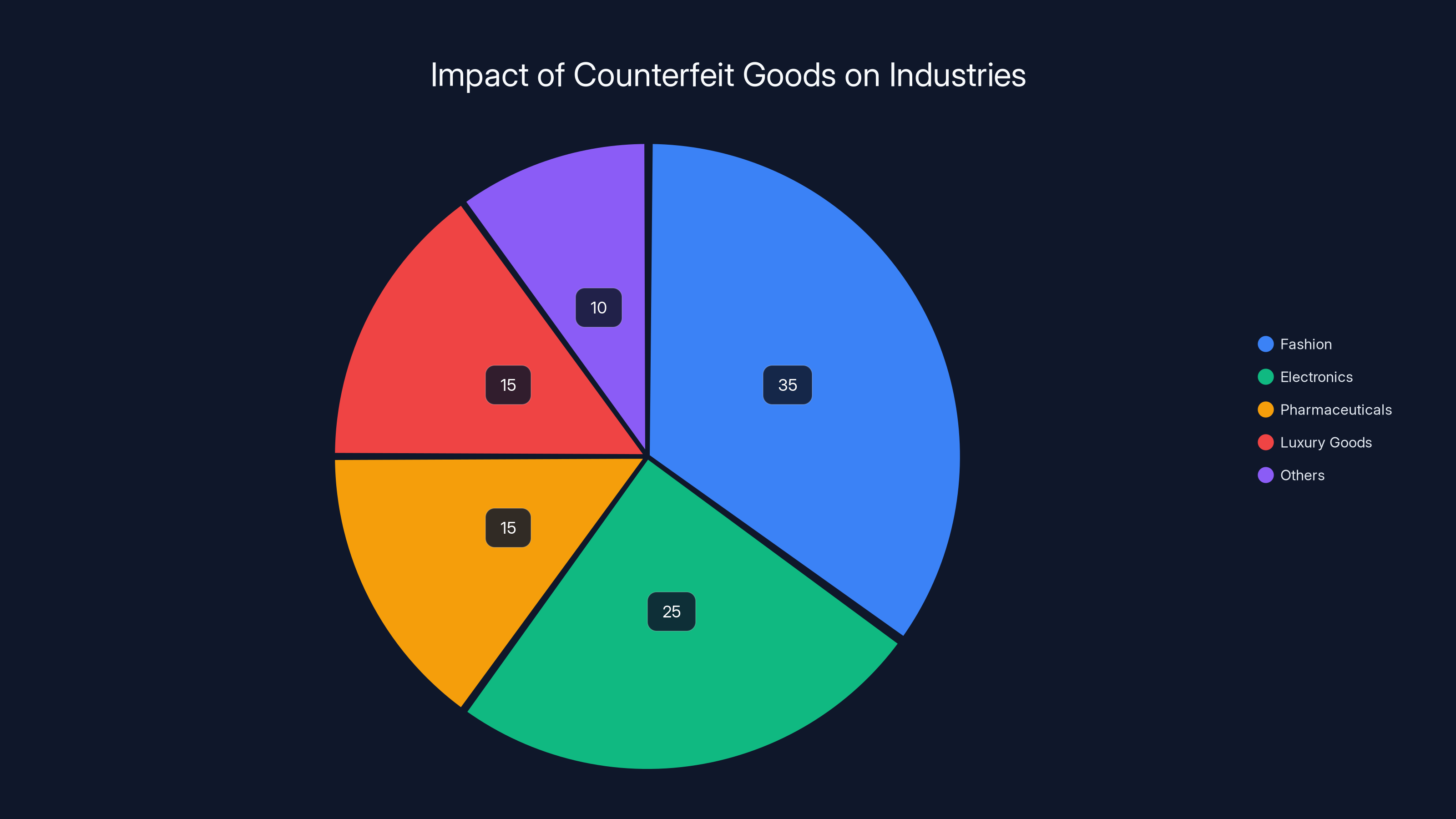
Estimated data shows that fashion and electronics are the most affected industries by counterfeit goods, accounting for 60% of the total impact.
Why Traditional Authentication Failed
Luxury brands have been trying to fight counterfeiting for centuries. Their traditional playbook: use complex symbols, physical markers, and certificates. Holograms, guilloche patterns, embossing, special materials that are hard to replicate.
For a long time, this worked well enough. A trained authenticator could spot inconsistencies in these details. But something shifted around 2015-2018. Manufacturing technology improved dramatically. 3D printing, advanced textile machinery, and precision casting became cheaper and more accessible. Counterfeiters started hiring the same factories that legitimate brands use, just off the books.
Then they started hiring actual designers and engineers. They reverse-engineered authentication methods. They studied hologram patterns, material compositions, and stitching techniques with scientific precision.
The result? Physical authentication became increasingly unreliable.
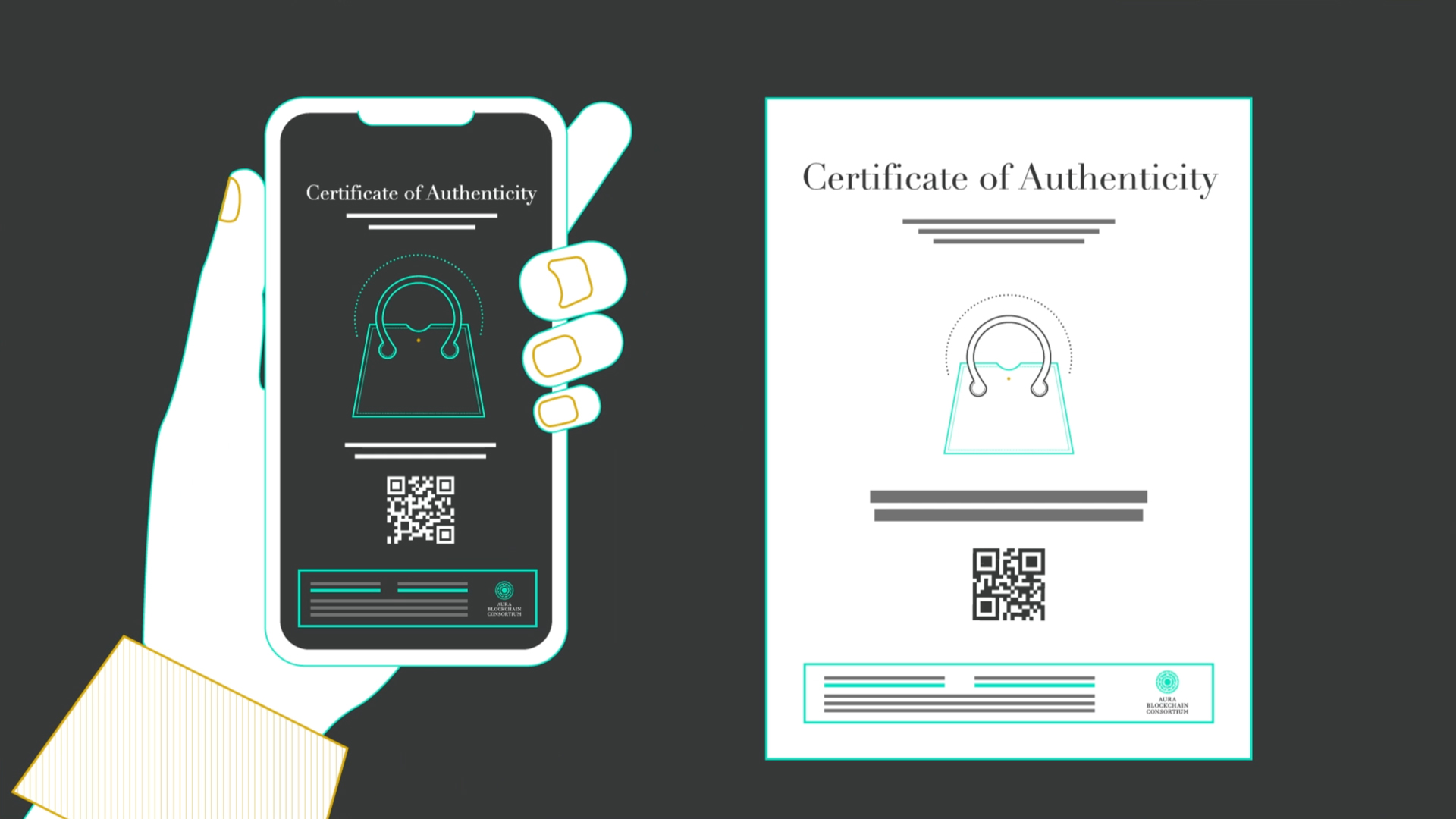
Brands tried digital solutions next. QR codes, serial numbers, and simple RFID tags. But here's the fatal flaw with those approaches: the codes themselves are just data. They're not tied to anything that can't be copied. A counterfeiter can scan a real product, clone the QR code, and paste it on a fake. The infrastructure isn't there to prevent it.
NFC chips used by some brands suffer from similar problems. The data they contain is not encrypted in a way that prevents duplication. A device like the Flipper Zero, a relatively cheap hacking tool available to consumers, can read and clone many commercial NFC implementations. This vulnerability is highlighted in a 99Bitcoins article discussing the security of hardware wallets.
Holland recognized this gap. She understood that you couldn't just slap a standard NFC chip into a product and expect security. The entire system had to be designed from the ground up to be resistant to known attack vectors.
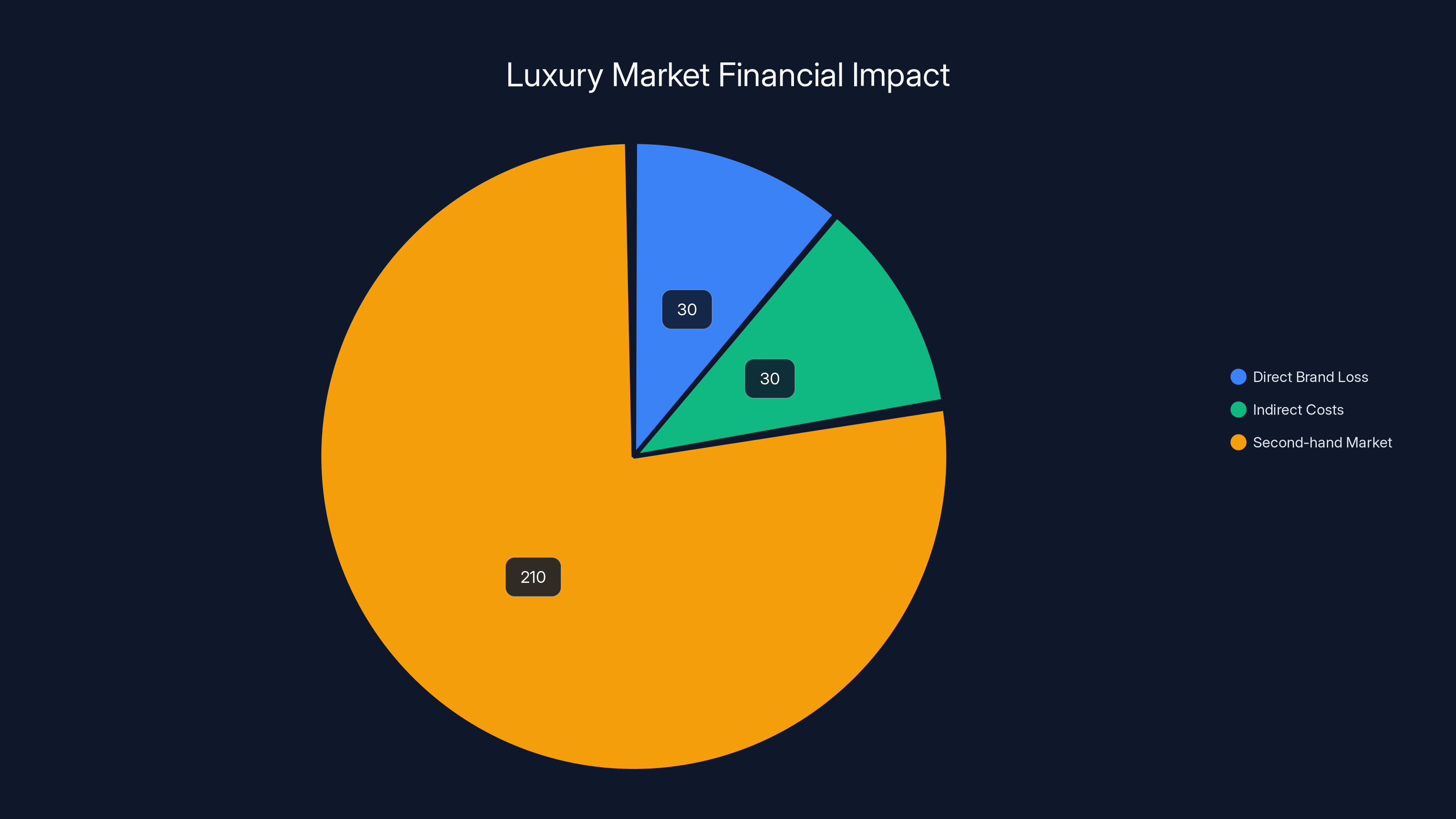
The luxury market faces a
The Hardware Solution: A Chip That Can't Be Faked
Veritas built a custom microchip that's roughly the size of a small gemstone. The form factor was intentional. It had to be small enough to embed in luxury items without disrupting the design or manufacturing process. It had to be insertable after initial production without compromising product integrity.
The chip uses Near Field Communication (NFC), the same wireless protocol that powers contactless payments on phones. But Veritas implemented it differently than standard NFC chips.
First, the custom coil and bridge structure. This isn't just standard NFC wiring. Veritas engineered the hardware so that if someone attempts to physically tamper with it, the chip goes dormant. The security codes hide themselves. Try to pry it open, try to desolder it, try to reverse engineer the connections? The chip detects the tampering and locks down.
This is harder than it sounds because the chip still needs to function normally when legitimate users scan it. The tamper detection has to distinguish between normal wear and intentional attack. Normal scanning shouldn't trigger the dormancy. Physical stress or intrusion should.
Second, the cryptographic implementation. The chip doesn't just broadcast data. It's paired with digital certificates that can verify the chip's authenticity. These certificates are generated during manufacturing and linked to a specific product. If someone clones the NFC data, they can't clone the certificate because it's not stored on the chip itself. It's verified through Veritas's backend infrastructure.
The manufacturing process matters too. These chips can't be created in just any factory. Veritas works with partners who can ensure production security. The chips are serialized during manufacturing, and each serialization event is logged. This creates an immutable record of which chip went into which product.

The Software Layer: Blockchain and Behavior Monitoring
The chip is just one piece. The real magic happens on the software side.
When a consumer taps their phone on a Veritas-authenticated item, they're not just reading data from the chip. They're initiating a query to Veritas's backend infrastructure. The backend verifies the chip's certificate, checks the scanning behavior patterns, and returns information about the product.
Veritas also creates a blockchain-based digital clone of each authenticated product. This serves multiple purposes.
First, it provides an immutable record of the product's journey. When it was created, which retailer received it, when it was scanned, who verified it. This creates a transparent history that's resistant to tampering.
Second, it opens up interesting possibilities for customers. Brands can use these digital clones to create exclusive experiences. A limited-edition Hermès handbag doesn't just have a physical presence. It has a digital twin that can be displayed in virtual galleries, authenticated in metaverse spaces, or used to grant exclusive access to brand communities.
Third, the scanning behavior monitoring catches fraud. Veritas's backend watches how products are scanned. If a chip is scanned thousands of times in an hour from different locations, that's a red flag. If the same chip is scanned in Tokyo and London within minutes, something's wrong. Normal scanning patterns look different. A real product might be scanned 5-10 times over its lifetime. A fake being tested by resellers might get scanned 50 times in a week.
This algorithmic approach to authentication is harder for counterfeiters to game because it's not based on physical characteristics they can study and copy. It's behavioral analysis running in real-time.
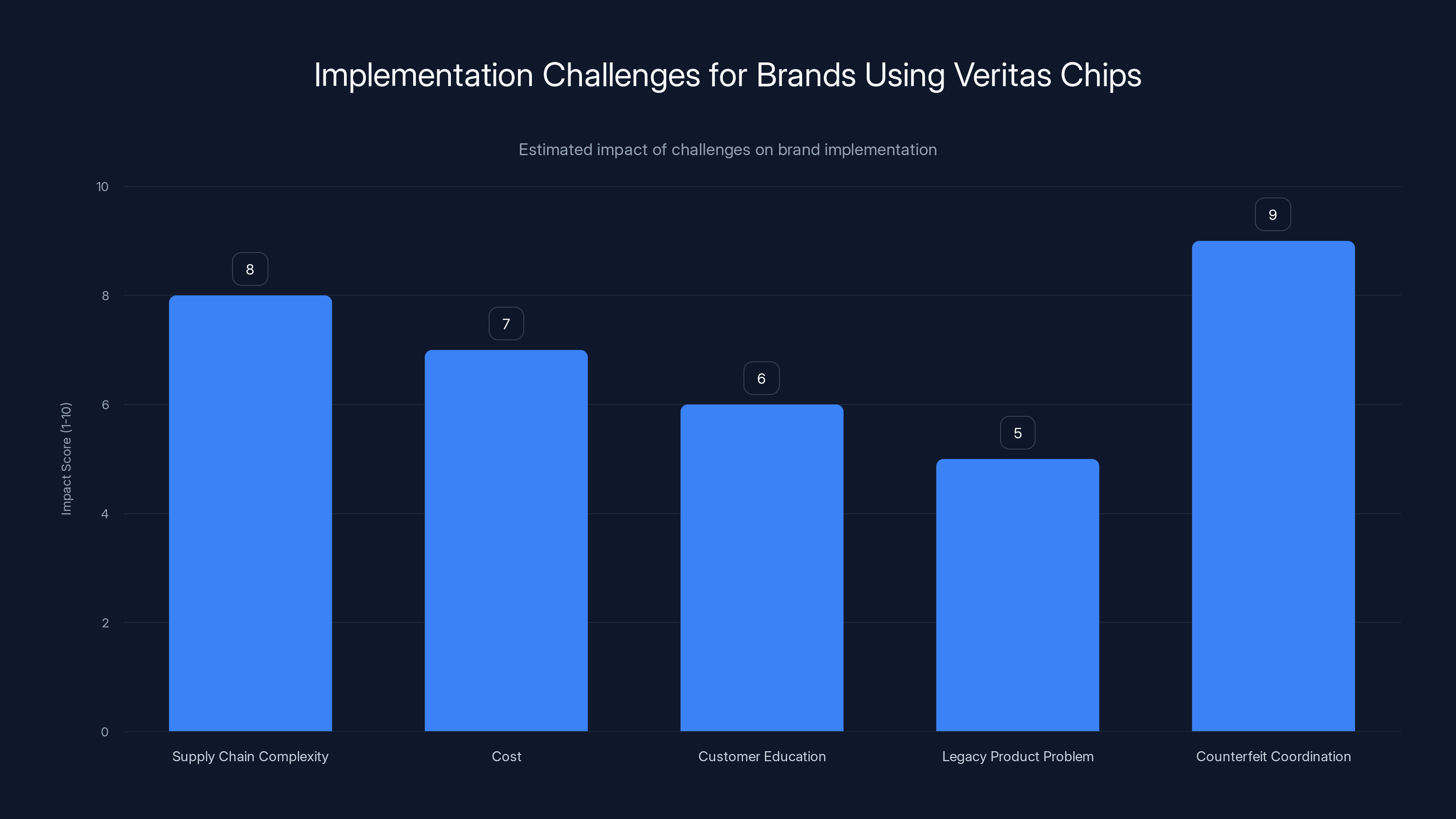
Supply chain complexity and counterfeit coordination are the most significant challenges for brands implementing Veritas chips. Estimated data.
How Luxury Brands Actually Use This
Veritas isn't positioning this as a consumer product. It's a B2B solution for luxury brands.
The brand gets a software suite that provides complete visibility into their chipped products. They can see real-time scanning data, product locations, and ownership chains. They can add team members to manage authentication requests. They can upload product information, create product stories, and link exclusive content that authenticators or customers can access.
Some brands are already using this to engage customers in novel ways. Veritas mentioned that partners offer exclusive invitations, early access to new collections, or VIP experiences to verified buyers. It's a loyalty mechanism built into the authentication process.
Consumers just tap their phone to verify an item. The app shows them the product details, confirms authenticity, and might unlock exclusive content. It's elegant because it doesn't require them to understand blockchain, cryptography, or any of the technical complexity behind it.
For brands, this solves several problems simultaneously. They know which retailers are moving their products and how fast. They can track counterfeiting hotspots by seeing where fake scans originate. They can identify which products are being counterfeited most frequently and adjust their security strategy accordingly.
The Market Opportunity and Why It Matters
The economics of this problem are massive.
Luxury brands lose
The second-hand luxury market is $210 billion and growing. It's growing faster than the new luxury market because younger consumers prefer sustainable, pre-owned goods. But without reliable authentication, this growth creates opportunity for fraud.
A typical luxury authentication service charges brands 2-5% of the product value to authenticate items. For a
Veritas's approach is attractive to brands because it's not just a service you call when you need authentication. It's infrastructure embedded in the product itself. The authentication happens at point of sale, point of resale, or whenever a customer wants verification. The brand can automate the process and reduce labor costs associated with manual authentication.
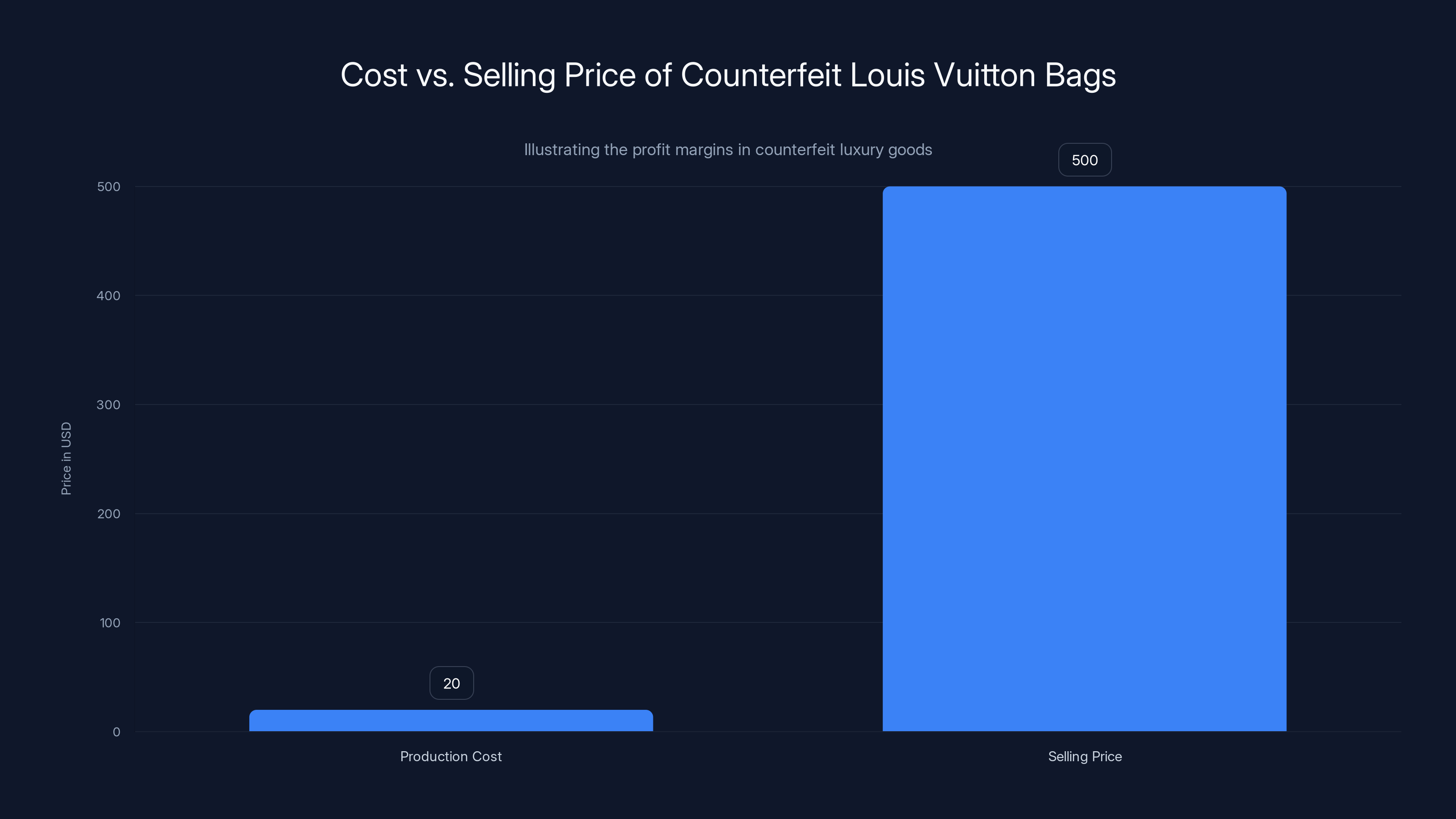
Counterfeit Louis Vuitton bags cost
The Competitive Landscape
Veritas isn't the only company tackling authentication, but the combination of custom hardware and blockchain is relatively rare.
There are pure software approaches. Apps like Entrupy use AI and machine learning to analyze product photos and identify fakes. They're useful, but they're still subject to the same limitation: good counterfeits fool AI too. The training data is biased toward known counterfeit patterns, and counterfeiters are constantly evolving.
There are pure hardware approaches. Some brands use holograms with complex patterns, color-shifting elements, or materials that are genuinely hard to replicate. But these can be copied with enough time and resources. And they don't provide real-time verification.
There are simple NFC solutions from companies like Authenticity and others. These are cheaper to implement but lack the security depth. The chips are vulnerable to cloning with standard hacking tools.
What Veritas is doing differently is combining all three elements: specialized hardware that resists tampering, cryptographic verification that can't be spoofed without factory access, and real-time behavioral monitoring that detects anomalies. It's a defense-in-depth approach.
The founder, Holland, explicitly calls out that many brands are using vulnerable off-the-shelf NFC solutions without understanding the risks. "It is shocking to see that some of the shelf solutions, like NFC chips that brands are using, are actually so vulnerable and could easily be bypassed," she said. That's both accurate and a clear positioning statement: existing solutions are insufficient, and brands need to upgrade.
The Funding and Path Forward
Veritas raised $1.75 million in pre-seed funding led by Seven Seven Six (the venture firm founded by Sequoia's Alexis Ohanian), with backing from Door Dash co-founder Stanley Tang, skincare brand Reys co-founder Gloria Zhu, and former Tech Crunch editor Josh Constine.
That's a small raise, which suggests this is still very early. The company is two people. But the backing is interesting because it's from people who understand both technology and brand-building. Ohanian is explicit about why he's interested: "It's absolutely an arms race [against fake goods makers], but we're used to fighting those and consistently winning in tech. Luxury brands need all the help they can get."
The funding will go toward expanding the team. Two people can't build hardware, run manufacturing partnerships, manage enterprise software, and handle customer success simultaneously. They'll need engineers, supply chain experts, and business development people.
The near-term focus is likely getting pilot programs with brands. Find 2-3 luxury houses willing to embed chips in their premium collections and validate the approach works in real production environments. Learn what breaks. Iterate on the hardware and software based on real feedback.
Mid-term, they need to handle the manufacturing question. Custom chips at scale require serious foundry partnerships. The timeline from design to production can be 6-12 months. They'll need to figure out whether they manufacture in-house, partner with established chip makers, or work with contract manufacturers.
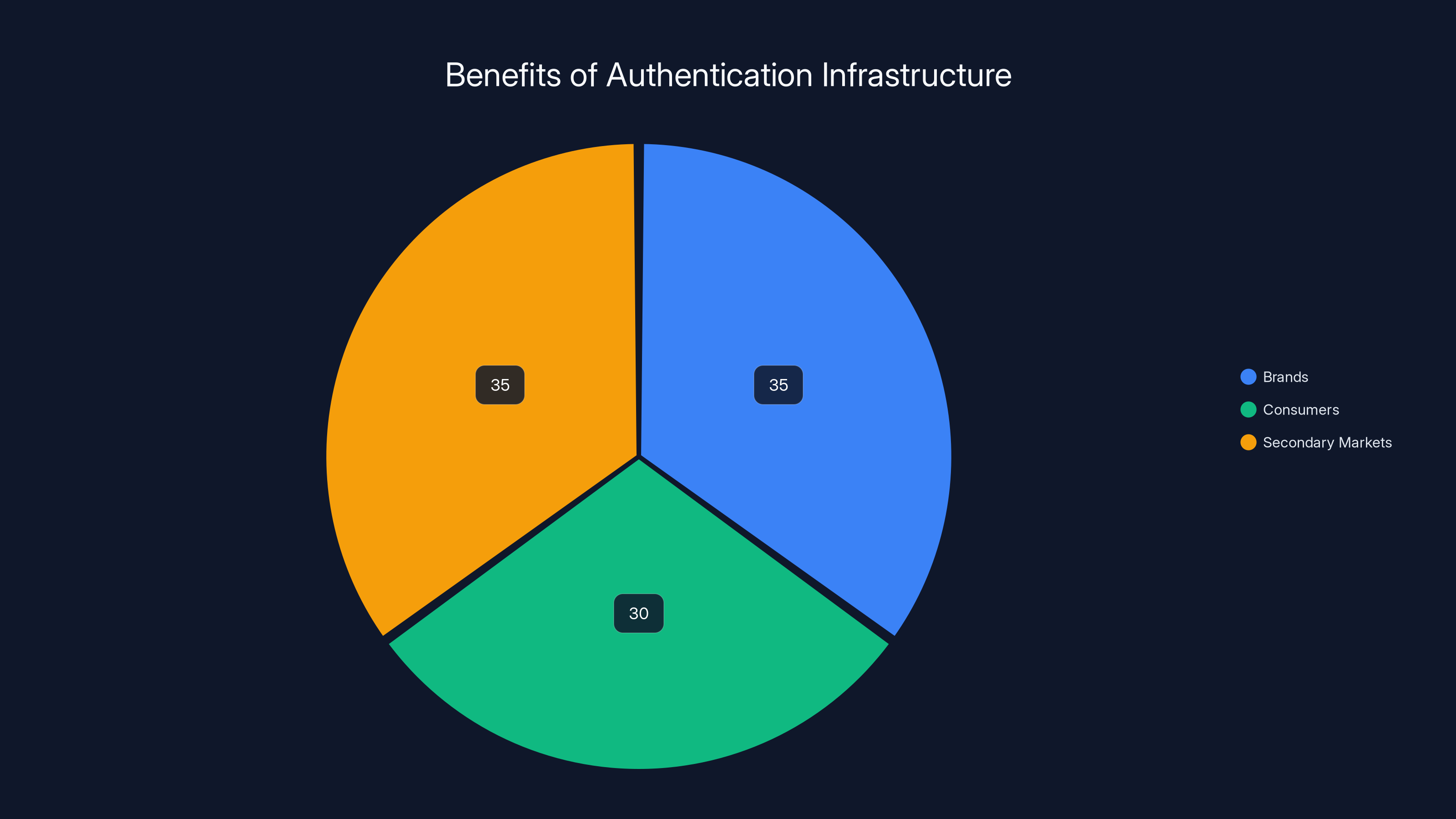
Estimated data shows that authentication infrastructure benefits are evenly distributed among brands, consumers, and secondary markets, enhancing trust and efficiency.
Technical Challenges Ahead
While the concept is solid, there are real technical challenges that Veritas will need to solve at scale.
First, power consumption. NFC chips are passively powered by the reader (your phone). There are strict limits on how much computational work they can do. Veritas's tamper detection and secure communication needs power. They've engineered custom hardware to minimize power draw, but there are limits. As they add features, power becomes a constraint.
Second, manufacturing consistency. Custom chips are notoriously difficult to manufacture at consistent quality. Each chip needs to function identically for the system to work reliably. One chip with slightly different electrical characteristics could behave unexpectedly. This requires tight manufacturing tolerances and rigorous testing.
Third, ecosystem adoption. NFC reading capability is near-universal on smartphones now, but the experience varies. Some Android phones read NFC more reliably than others. iPhones require a dedicated app for most NFC operations (not background reading). Veritas has to build an experience that works smoothly across diverse hardware.
Fourth, key management. The digital certificates that verify chip authenticity require secure key management. If the private keys that sign these certificates ever leak, the entire system is compromised. This is a serious operational security challenge at scale.
Fifth, counterfeiter sophistication. Good counterfeiters have funding, technical talent, and motivation. As Veritas's solution becomes well-known, sophisticated actors will start researching how to break it. The hardware-software combination is harder to break than either alone, but it's not impossible. Side-channel attacks, power analysis, and other sophisticated techniques might eventually reveal ways to spoof the system.
Veritas has probably thought through some of these. But scaling any authentication system faces the reality that determined adversaries with resources will eventually find weaknesses. The goal is to make counterfeiting expensive and difficult enough that it becomes uneconomical.

Implementation Challenges for Brands
Even if Veritas solves the technical problems, brands face implementation challenges.
First, supply chain complexity. Luxury brands have fragmented supply chains. They might use multiple manufacturers, sub-contractors, and logistics partners. Getting everyone to use Veritas chips requires coordination and standardization. It's possible, but it requires brand commitment.
Second, cost. While Veritas doesn't reveal pricing, custom chips with secure manufacturing and blockchain integration aren't cheap. Brands need to decide whether the cost is justified. A luxury brand selling
Third, customer education. Consumers need to understand how to scan and verify items. Early adoption will be enthusiasts and collectors. Mainstream adoption requires the process to be so simple that anyone can do it without instructions.
Fourth, legacy product problem. Brands have existing inventory and existing products in the market without chips. They can't retroactively add authentication to millions of items. Any authentication strategy has to account for a mixed portfolio of old products (unchipped) and new products (chipped).
Fifth, counterfeit ecosystem coordination. Even if one luxury house uses Veritas chips, if their products are counterfeited at a lower price point, consumers might not care about authentication. The incentive to counterfeit is tied to price premium. If a counterfeit Veritas-chipped product costs almost as much as the real thing (because of manufacturing complexity), the counterfeiting drops.

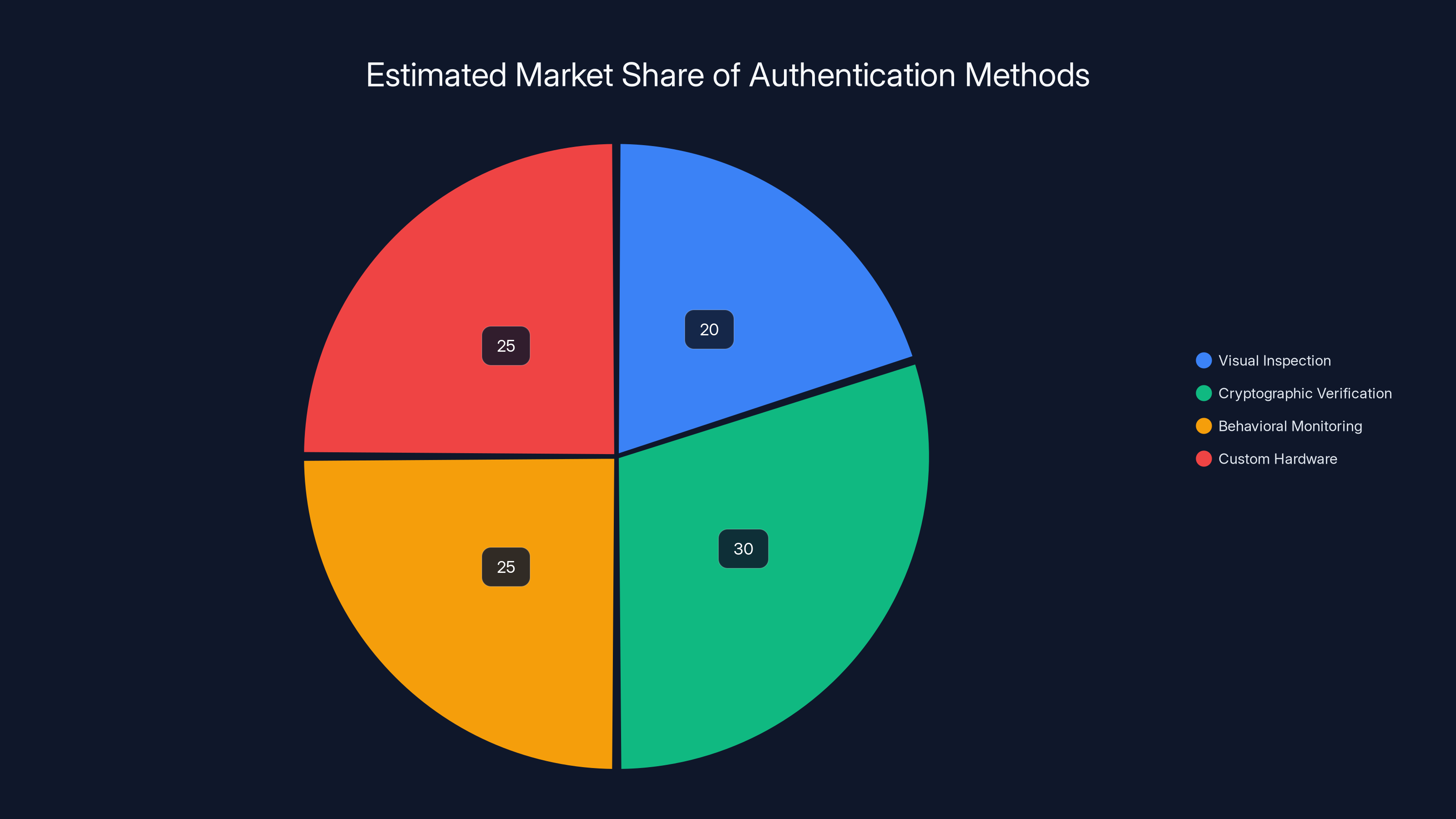
Cryptographic verification and behavioral monitoring are projected to dominate the luxury goods authentication market by 2025, reflecting a shift towards more secure methods. (Estimated data)
The Broader Context: Why Authentication Matters Now
Authentication is suddenly urgent for luxury brands because the market dynamics have shifted.
Generational shift: Younger consumers care more about sustainability and price than brand heritage. They're comfortable buying second-hand. This creates a massive market for pre-owned luxury goods. But without authentication, this market becomes breeding ground for counterfeits.
E-commerce explosion: Luxury goods are increasingly sold online, where visual inspection is impossible. You can't hold the bag, feel the leather, or examine stitching details. The authentication problem moves from physical retail (where experts can verify) to digital retail (where anyone can claim authenticity).
Globalization of manufacturing: Supply chains are global and complex. Counterfeits are manufactured in dozens of countries and shipped through multiple intermediaries. Brand visibility into who's making products is limited. This creates opportunities for counterfeiters to insert fake products into legitimate supply chains.
Technological arms race: Both legitimate brands and counterfeiters have access to the same manufacturing technology. The differentiation is increasingly narrow. Brands need technological advantages that counterfeiters can't easily replicate.
Regulatory pressure: Governments are cracking down on counterfeit goods as a revenue issue and a criminal justice issue. Brands that can prove efforts to combat counterfeiting face fewer regulatory challenges. Brands that ignore the problem face increasing liability.
All of these forces converge to create urgency around authentication solutions like Veritas.

Future Applications and Expansion
Where does Veritas go after luxury goods?
Pharma and medical devices face similar counterfeiting challenges. Fake pharmaceuticals are a public health crisis. The same chip-and-verification approach could work in medical supply chains. The regulatory environment is stricter, which might actually be an advantage for a company with proven security infrastructure.
Wine and spirits are heavily counterfeited. Luxury bottles of wine or whisky worth thousands of dollars are tempting targets. The form factor for chips in bottles is different, but the underlying approach could work.
Electronics and high-value components have counterfeiting problems too. Aerospace parts, semiconductors, and automotive components can be counterfeited with serious safety implications. Again, the chip-and-blockchain approach scales.
The broader implication: as counterfeiting becomes more sophisticated, demand for hardware-based authentication will grow. Companies that crack the problem in luxury goods might find their solution applicable across industries.

Lessons From Other Hardware-Software Authentication Systems
Veritas isn't working in a vacuum. Other industries have tackled similar problems.
Apple's security architecture combines custom hardware (the Secure Enclave, specialized chips) with software-based verification and behavioral monitoring. They scan for unusual device behavior, geographic anomalies, and access patterns. If something seems off, they trigger additional authentication steps. The combination of hardware trust and software monitoring is powerful.
Banking systems use similar approaches. Your credit card has an embedded chip that's difficult to counterfeit. But the chip alone isn't the security layer. Banks also monitor transaction patterns, geographic data, and behavioral anomalies. A purchase in Tokyo followed by a purchase in New York in the same hour triggers fraud alerts.
The lesson from both systems: hardware authentication is stronger when paired with behavioral analysis. The hardware makes baseline trust possible. The software layer catches sophisticated attacks that try to spoof the hardware.
Veritas is applying these lessons to luxury goods. The microchip establishes baseline trust. The blockchain and behavioral monitoring catch anomalies. It's a proven pattern applied to a new domain.

Why This Matters Beyond Just Stopping Fakes
Authentication infrastructure might sound boring until you realize the implications.
A system that can verify product authenticity in real-time also enables new economic models. Brands could offer trade-in programs where verified authentication ensures fair pricing for used items. They could run secondary markets for their own products, capturing value from resales instead of losing it to gray markets.
Consumers benefit through trust and protection. If you're buying a $10,000 watch on the secondary market, verification takes seconds instead of requiring an expert appointment.
The secondary market becomes more efficient. Price discovery improves when buyers have confidence in authenticity. Liquidity increases. This expands the entire luxury market because consumers are willing to pay more for items they can easily verify and resell.
Brands also gain visibility into their customer base through the authentication network. They can see who's buying, how products are being used, and which models hold value. This data is valuable for future product development.
Long-term, hardware-based authentication could become standard across all luxury goods. It could become a trust signal as important as a brand's name. When someone presents an authenticated item, they're presenting proof of legitimacy that can't be argued with.
What Veritas Needs to Execute Well
The idea is solid, but execution is where most hardware startups fail.
Veritas needs to move fast on manufacturing partnerships. The longer they take to lock in reliable chip production, the longer before they can scale. Chip manufacturing timelines are measured in months, not weeks.
They need early wins with recognizable luxury brands. A pilot with one or two major houses would validate the approach and open doors with others. News that a prestigious brand has embedded Veritas authentication in their flagship collections would be powerful marketing.
They need to stay ahead of the counterfeiting arms race. As soon as they launch, counterfeiters will start researching vulnerabilities. They need resources allocated to security research, threat modeling, and continuous improvement.
They need to build a support organization. Brands won't adopt a solution that requires extensive engineering support. Veritas needs to make the product self-service, with clear documentation and reliable customer success teams.
They need to think about pricing carefully. Too high, and brands can't justify it. Too low, and they won't have resources to maintain the system. Veritas probably needs a hybrid model: manufacturing cost for chips plus a per-scan or annual subscription for backend services.
They need to manage regulatory compliance. Blockchain, cryptography, and data storage have regulatory implications in different jurisdictions. GDPR in Europe, data privacy laws in California, and import regulations around electronic components all matter.
None of these are impossible. But they require execution discipline at every level.

The Broader Counterfeiting Problem
While Veritas is tackling luxury goods specifically, counterfeiting is a symptom of a larger problem: trust infrastructure at scale.
We live in a world where the complexity of supply chains exceeds our ability to visually verify authenticity. You can't know where your clothes, electronics, or medications come from just by looking at them. You have to trust labels, certificates, and brand reputations.
Counterfeiters exploit this trust gap. They make products that look identical to originals, with forged documentation, and insert them into legitimate marketplaces.
Authentication solutions work in two directions. First, they protect brands and legitimate sellers. Second, they protect consumers and uphold the integrity of supply chains.
As supply chains become more complex and more global, authentication infrastructure becomes more critical. We can't return to a world where you knew the individual craftsperson who made your clothes or the blacksmith who forged your tools. That's not scalable. We need technological solutions that create trust at global scale.
Veritas represents one approach to this larger problem. There will be others. Different industries will develop different solutions optimized for their constraints. But the underlying principle is the same: embed verification mechanisms into products themselves, not just rely on paper trails or brand reputation.
Predictions for the Authentication Market
Where's this headed?
In five years, hardware-based authentication will be table stakes for luxury goods above a certain price point. It won't be optional. Brands will realize the cost savings from reduced counterfeiting enforcement exceed the cost of implementation.
The second-hand luxury market will mature into a legitimate channel with professional grading and verification services. Companies like Vestiaire Collective and Rebag will incorporate hardware verification into their operations. This legitimacy will drive consumer confidence and accelerate growth.
Authentication will expand beyond luxury. Pharmaceuticals will adopt similar approaches driven by regulatory requirements. Electronics will follow. Specialty goods and high-value items will standardize on verifiable hardware markers.
The technology will evolve. Veritas's microchip approach is first-generation. Within five years, there will be better approaches: maybe embedded RFID that's more tamper-resistant, maybe holographic markers with computer vision verification, maybe even DNA-based authentication. The competition will drive innovation.
Counterfeiters will adapt. They always do. The goal isn't to make counterfeiting impossible forever. It's to make it expensive, difficult, and risky enough that the economics don't work. As verification becomes ubiquitous, counterfeiting shifts from pure economics to criminal enterprise with real legal consequences.

The Human Element
One thing that strikes about Veritas is that it was founded by someone with both technical depth and artistic sensibility.
Holland's background in design and sculpture matters because authentication can't just be secure. It has to be beautiful. It has to integrate seamlessly into luxury products. A chip embedded in a Hermès bag can't detract from the bag's aesthetic. It has to enhance the ownership experience.
That combination of technical rigor and design thinking is rare. Most founders are either deep technical experts who don't understand design, or designers who lack technical depth. Finding someone who can think across both domains is unusual.
It's also a reminder that the best hardware solutions often come from people who understand both engineering and human experience. The most secure system fails if users don't want to use it. The most beautiful design fails if it doesn't work reliably.
Veritas's founder understands both. That's an advantage in execution.

Conclusion: The Arms Race Continues
Counterfeiting is an arms race that's been going on for centuries. As authentication methods improve, counterfeiters get better at defeating them. As counterfeiting gets more sophisticated, authentication needs to evolve.
Veritas represents the latest round in this arms race. By combining custom hardware that resists physical tampering, cryptographic verification that can't be spoofed without factory access, and behavioral monitoring that detects anomalies, they've raised the bar significantly.
But this isn't the final word on authentication. It's one approach optimized for luxury goods. Other industries will develop specialized solutions. Technology will continue to evolve. Counterfeiters will continue to adapt.
What's changed is that authentication is no longer just about visual inspection and expert judgment. It's about creating verifiable, tamper-resistant infrastructure that makes it economically unviable to counterfeit products above certain price points.
For luxury brands losing billions to counterfeits, for consumers buying second-hand items without confidence, and for the integrity of supply chains, that's genuinely important progress.
The next few years will determine whether Veritas and approaches like theirs become standard practice across the luxury industry. Early pilot programs will generate real-world data on effectiveness. Manufacturing will be solved or become a bottleneck. Pricing will be discovered through market forces.
But the core insight is sound: when you embed authentication directly into products and back it with cryptographic verification and behavioral monitoring, you make counterfeiting meaningfully harder. Not impossible. Harder. Expensive. Risky.
That might be enough to shift the economics from "counterfeiting is profitable" to "counterfeiting is not worth it."
For a $30 billion problem, that would be transformative.

FAQ
What is product authentication and why does it matter?
Product authentication is the process of verifying that a product is genuine and not a counterfeit. It matters because counterfeit goods cost legitimate brands over $30 billion annually, undermine consumer trust, and in some industries like pharmaceuticals, create serious safety risks. Without reliable authentication methods, second-hand markets and online retail become breeding grounds for fraud.
How do NFC chips work in authentication systems?
NFC (Near Field Communication) chips use short-range wireless technology that transmits data when a smartphone comes within a few inches of it. In authentication systems, when you tap your phone on a product, the NFC chip sends a unique identifier to a backend server, which verifies the authenticity by checking digital certificates and comparing it against known genuine products. This allows instant verification without requiring special equipment or expertise.
What makes Veritas's approach different from standard NFC authentication?
Most commercial NFC chips store data that can be cloned using tools like the Flipper Zero. Veritas's approach combines a custom-engineered chip with tamper detection that goes dormant if someone tries to physically compromise it, paired with cryptographic certificates that can't be spoofed without factory access. Additionally, their backend monitoring system tracks scanning patterns to detect fraud, creating multiple layers of security rather than relying on a single verification method.
How does blockchain help verify luxury goods?
Blockchain creates an immutable record of a product's history from manufacturing through ownership changes. Each scan and transfer is recorded on the blockchain, creating a transparent chain of custody that's resistant to tampering. This allows buyers to see the complete history of a product, verify it hasn't been reported stolen or counterfeit, and builds confidence that they're purchasing a genuine item.
What happens if someone tries to tamper with a Veritas chip?
Veritas engineered the chip with custom coil and bridge structures that detect physical tampering. If someone attempts to pry open the chip, desolder connections, or otherwise physically modify it, the chip automatically goes dormant and hides the security codes. This makes the product immediately flagged as suspicious when someone tries to scan it, preventing counterfeiters from modifying or cloning authenticated products.
How much does it cost for brands to implement this authentication system?
Veritas hasn't publicly disclosed exact pricing, but hardware-based authentication typically costs brands $2-5 per chip plus backend software and monitoring fees. For luxury brands selling high-value items, this cost is justified by the billions lost to counterfeiting. The company likely uses a hybrid pricing model combining per-chip manufacturing costs with per-scan or annual subscription fees for backend services.
Can counterfeiters bypass this authentication system?
While no security system is theoretically impossible to breach, Veritas's approach is significantly harder to counterfeit than standard solutions. Counterfeiting it would require either stealing manufacturing secrets, breaking cryptographic certificates, or somehow accessing Veritas's backend infrastructure. The combination of hardware resistance, cryptographic verification, and behavioral monitoring makes it economically unviable for most counterfeiting operations, though determined adversaries with significant resources might eventually develop workarounds.
How does behavioral monitoring detect counterfeit products?
Veritas's backend system tracks how products are scanned. Legitimate products typically get scanned a handful of times over their lifetime. Counterfeit products being tested or authenticated before resale show suspicious patterns like thousands of scans in short time periods, scans from geographically impossible locations, or identical chips being scanned multiple times. The system uses these anomalies to calculate fraud scores and flag suspicious products automatically.
What industries could benefit from similar authentication systems?
Beyond luxury goods, industries like pharmaceuticals (where counterfeit drugs cause hundreds of thousands of deaths annually), wine and spirits, electronics, high-value components, aerospace parts, and specialty goods all face serious counterfeiting problems. The chip-and-verification approach is adaptable to any industry where authentication is critical and counterfeiting is economically motivated.
How long until hardware authentication becomes standard in luxury goods?
Based on adoption curves for security technologies, hardware authentication will likely become industry standard within 5-7 years for luxury goods above certain price points. Early adopters will be luxury houses wanting to protect their brand reputation. As manufacturing scales and costs decrease, adoption will accelerate. Regulatory pressure around counterfeiting and supply chain transparency will also accelerate the timeline.

Key Takeaways
- Counterfeiting costs luxury brands over $30 billion annually while sophisticated superfakes fool even professional authenticators
- Veritas combines custom hardware (tamper-proof microchips), cryptographic verification, and behavioral monitoring for layered authentication
- NFC technology alone is insufficient—standard chips can be cloned with tools like Flipper Zero, requiring specialized hardware engineering
- The $210 billion second-hand luxury market creates urgent need for reliable authentication as buyers increasingly purchase pre-owned items online
- Hardware-based authentication can reduce brand authentication labor costs by 60-80% while improving accuracy to near 100%
- Blockchain creates immutable product records, enabling transparent ownership histories and detecting suspicious scanning patterns that indicate counterfeits
- Adoption will likely accelerate from early luxury adopters to industry standard within 5-7 years as manufacturing scales and regulatory pressure increases
Related Articles
- Autodesk Sues Google Over Flow AI Trademark [2025]
- Digital Squatting: How Hackers Target Brand Domains [2025]
- dYdX Supply Chain Attack: How Malicious NPM Packages Emptied Wallets [2025]
- Why America's $12B Mineral Stockpile Proves the Future Is Electric [2025]
- Nord Security's 400 Patents: The Future of Cybersecurity [2025]
- SonicWall Breach Hits Marquis Fintech: What Banks Need to Know [2025]
![How Microchip Authentication Is Stopping Counterfeit Luxury Goods [2025]](https://tryrunable.com/blog/how-microchip-authentication-is-stopping-counterfeit-luxury-/image-1-1770743787721.jpg)




