How 1Password's New Phishing Prevention Feature Changes Your Cybersecurity
Phishing attacks have become one of the most dangerous threats to both individual and business security. The statistics are genuinely alarming. According to recent industry research, a successful phishing attack costs businesses an average of $4.8 million. That's not just money lost to fraud, either. It's the investigation time, the credential reset cascade, the potential breach of sensitive data, the regulatory fines, and the damage to reputation.
For individuals, the stakes feel different but are equally real. One wrong click on a fake login page, and suddenly someone's got access to your email, your bank account, or your work accounts. The attackers are getting better at disguising these attacks too. A domain that's one letter off from the real thing? A website that looks pixel-perfect identical to the legitimate service? These tricks work because humans aren't great at spotting tiny URL differences when they're in a hurry.
That's why password managers have become critical tools in the modern security toolkit. And that's why 1Password's new phishing prevention feature is such a big deal.
The company just rolled out an intelligent detection system designed to catch phishing attempts before they succeed. It's not a magic bullet, but it's a meaningful step forward in the arms race between security and social engineering. Let's dig into what this feature actually does, how it works, and why you should care about it whether you're protecting a Fortune 500 company or just your personal Netflix account.
TL; DR
- New Detection Technology: 1Password's phishing prevention feature detects suspicious websites by analyzing URL patterns, SSL certificate information, and domain registration age
- Real-time Warnings: Users get alerts before entering credentials into potentially fraudulent sites, giving them a chance to stop and think
- Gradual Rollout: The feature began rolling out in early 2025 but may take weeks to reach all users across different subscription tiers
- Automatic vs. Manual: Individual and family plan users have it enabled by default, but business admins must manually enable it for their teams
- Not Foolproof: The system can't stop determined users from manually copying and pasting credentials into fake sites, but it significantly raises the bar for attackers
- Free Tier Included: This protection is available across all 1Password plans, not locked behind premium pricing

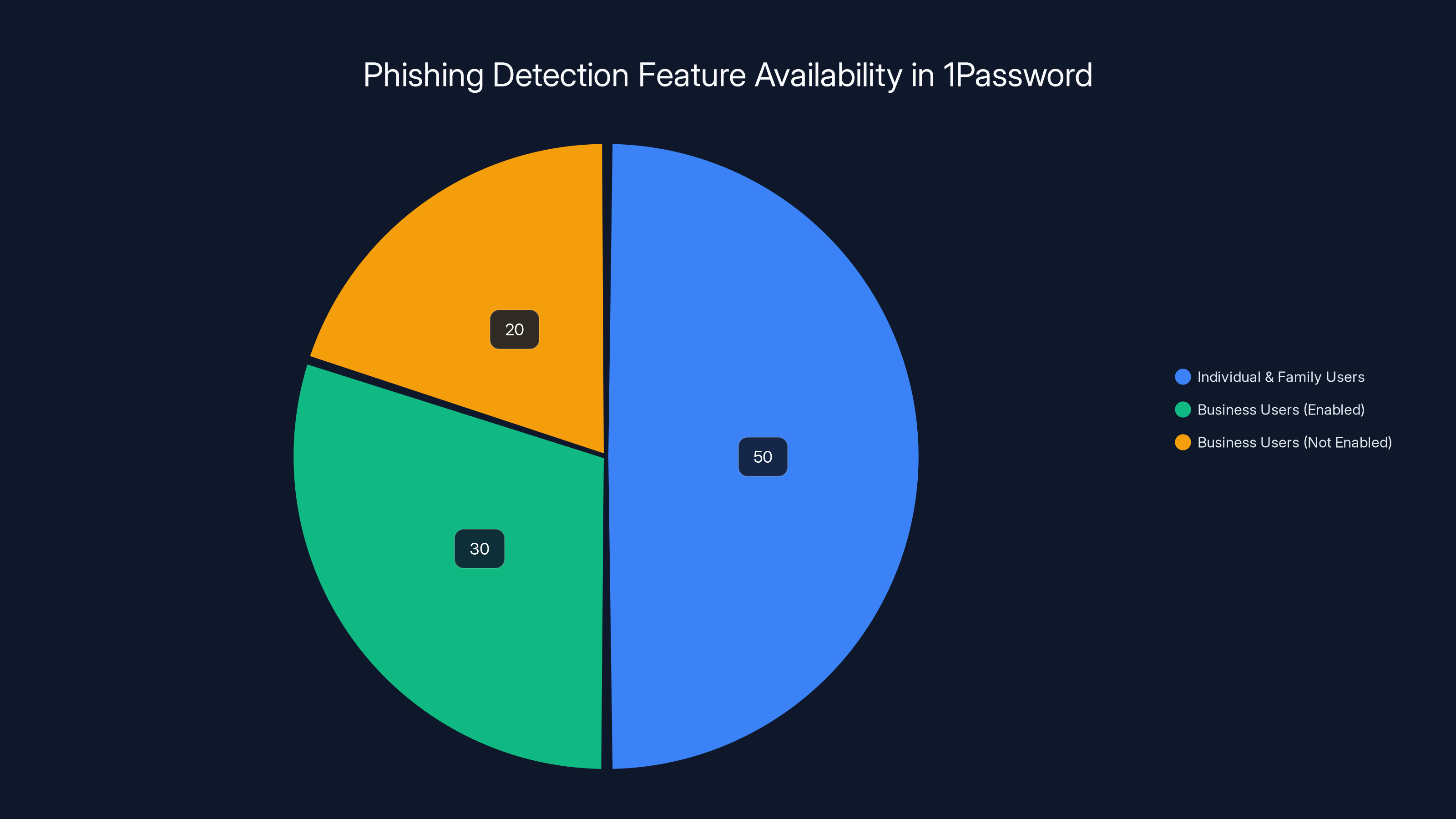
Estimated data shows that 50% of individual and family users have the phishing detection feature enabled by default, while 30% of business users have it enabled, and 20% have not enabled it yet.
Understanding the Phishing Threat Landscape
Phishing isn't new. It's been around since the early days of email, and for decades it seemed like a relatively simple problem. Scammers send out emails pretending to be from legitimate companies, users click malicious links, and bad things happen.
But the sophistication has evolved dramatically. Modern phishing attacks are surgical. They target specific individuals with insider knowledge about their work, their habits, and their relationships. They use publicly available information from LinkedIn, company websites, and social media to build convincing narratives. They'll craft an email that appears to come from your CEO during a high-stress moment, asking you to wire money or verify login credentials immediately.
The shift from spray-and-pray mass phishing to targeted spear phishing has changed the calculus. These attacks work because they exploit trust and urgency, not just user ignorance. A security-conscious employee might still fall for a well-executed spear phishing attack because it appears to come from someone they know and because it's asking them to do something that makes business sense in context.
Password managers have traditionally addressed this by storing your credentials and automatically filling them in only on legitimate sites. But here's the vulnerability that's always existed: if a phishing site looks convincing enough and is on a different domain, the password manager won't automatically fill in your credentials. At that point, you're relying on human vigilance.
That's a terrible place to be. Humans are terrible at vigilance, especially when they're under time pressure or stress. We scan URLs. We miss character substitutions. We assume that if something looks right and feels right, it probably is right.
The new 1Password phishing prevention feature is designed to handle the task that humans keep failing at: detecting when a website isn't what it claims to be.
How the Detection System Actually Works
Understanding the mechanics of the phishing detection system helps explain why it's effective and where its limitations are.
The system operates at the browser extension level, which means it's checking every website you visit while 1Password is active. When you land on a site that asks for login credentials, the extension analyzes several factors in real time.
First, it checks the domain name itself. Legitimate companies own multiple variations of their domain to protect themselves, but there are patterns in how real companies register domains. A fraudulent site might try to register something like "amazon-login.com" or "paypa1.com" (with a number instead of a letter). The system can detect these subtle variations by comparing against known legitimate domain patterns.
Second, it examines the SSL certificate. Real websites have SSL certificates issued by recognized certificate authorities. Those certificates contain information about the site's ownership. The system can verify whether the certificate matches the domain and whether the certificate authority is legitimate. This is harder to fake than it sounds because certificate authorities maintain strict validation processes.
Third, it looks at the domain registration history. A brand new domain registered yesterday that's asking you to log into your Amazon account? That's a massive red flag. Legitimate sites have been registered for years. The system can check domain age and registration information through public records.
Fourth, it analyzes the page content and structure. Many phishing sites copy legitimate sites by stealing their HTML and CSS. The detection system can identify when a site's code structure matches a phishing template rather than the legitimate site's actual structure.
When these factors add up to a high probability of phishing, the system shows you a warning directly in your browser. The warning is pretty hard to miss, and it appears before you've entered any information. That's the critical moment. You're forced to pause and think about what you're doing.
The beauty of this approach is that it's happening behind the scenes. You don't have to do anything special to enable it for most users. You just browse normally, and the system quietly monitors everything.

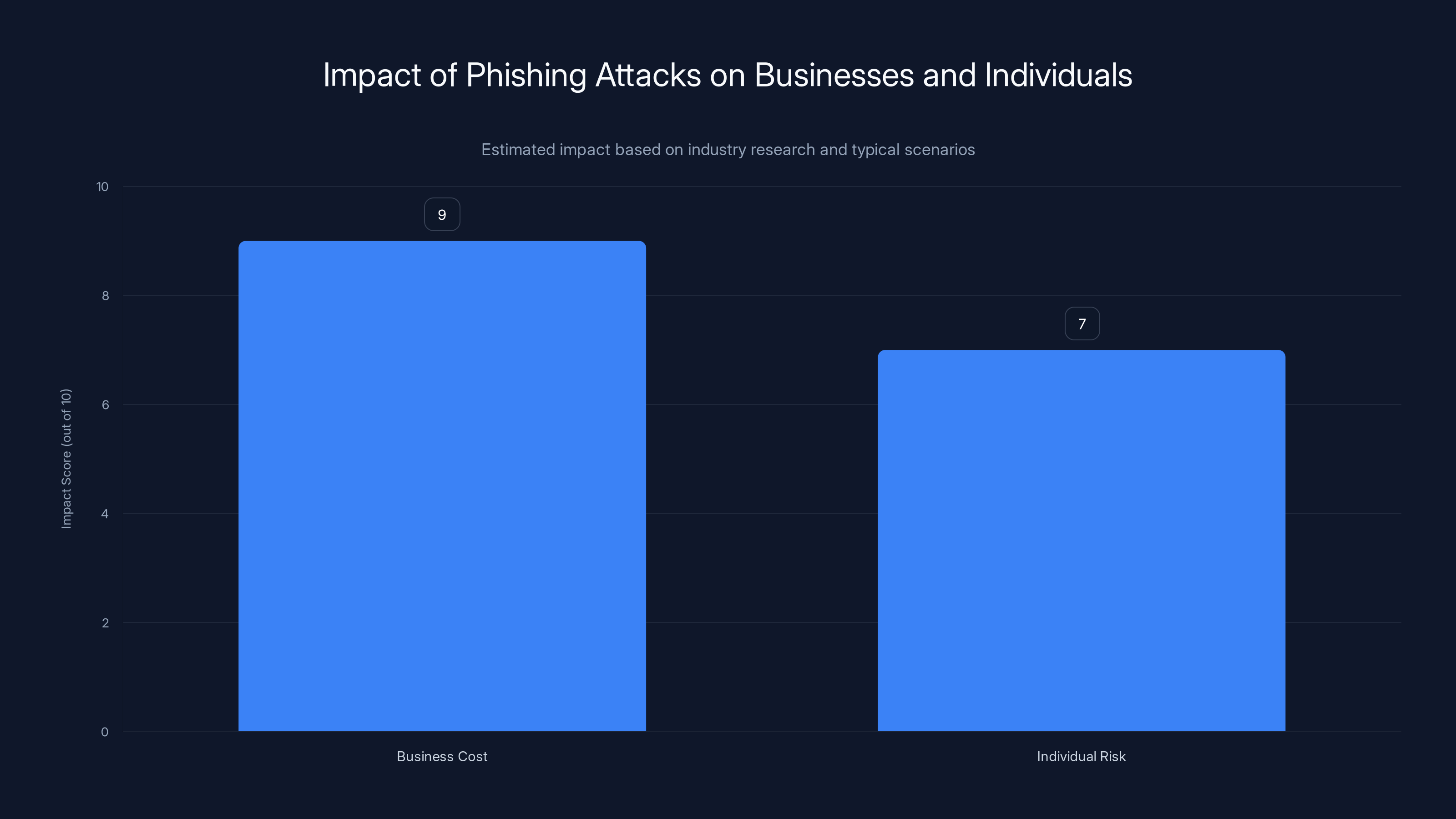
Phishing attacks have a severe impact on businesses, costing an average of $4.8 million, and pose significant risks to individuals. Estimated data.
Why URL Analysis Alone Isn't Enough
You might think that checking the URL would be sufficient to catch phishing attacks. It seems simple enough: compare the URL to the legitimate site's URL, and if there's a mismatch, warn the user.
The problem is that URL analysis is easier to defeat than you'd think, and relying on it alone would create a false sense of security while still letting many attacks through.
Consider internationalized domain names, which use non-Latin characters. A sophisticated attacker can register domains that use Cyrillic characters that look visually identical to Latin letters when rendered in certain fonts. You can't reliably spot these differences by looking, even if you're trained to do so. The system needs to analyze the actual Unicode composition of the domain, not just how it looks to human eyes.
Consider also the problem of legitimate subdomains. Many companies use subdomains for different services. Amazon might use a subdomain for its AWS login, for example. An attacker could register "amazon-login.fake-domain.com" and if the system is just looking for "amazon" in the domain, it might miss this. The actual legitimate domain structure needs to be understood to distinguish between real subdomains and fake ones.
There's also the issue of typosquatting on a massive scale. Attackers register thousands of variations of popular domains. Some are obvious ("amaz0n.com" with a zero), but others are incredibly subtle. The system can't rely on a blocklist of known phishing domains because new ones are created constantly. Instead, it needs to detect the characteristics that make a domain suspicious.
This is why the 1Password detection system combines URL analysis with SSL certificate verification, domain age checking, and content analysis. Each of these signals is weaker on its own, but together they create a detection system that's much harder to trick.
The Role of Machine Learning in Phishing Detection
While the basic detection methods rely on well-established security principles, modern phishing detection also uses machine learning to spot patterns that humans might not easily recognize.
Machine learning models trained on massive datasets of known phishing and legitimate sites can identify subtle patterns in site structure, CSS styling, form layout, and content arrangement that correlate with phishing attempts. The model might notice, for example, that phishing sites tend to use certain patterns of form fields or buttons that legitimate companies don't use.
These models need constant updating because attackers adapt. Once an attacker discovers that their particular site structure is being detected, they'll modify it. The machine learning system needs to detect these new patterns without creating false positives that frustrate legitimate users.
The challenge with machine learning in security is that false positives are annoying but false negatives are dangerous. If the system warns you about a legitimate site, you've lost some trust in the system but you haven't actually been compromised. If the system fails to warn you about a phishing site, you might get compromised. This asymmetry means that phishing detection systems tend to err on the side of warning too much rather than warning too little.
1Password's team would have had to carefully tune their detection threshold. Set it too high, and you get false positives that make users ignore the warnings. Set it too low, and phishing attacks slip through. The fact that they're starting with a gradual rollout suggests they're being careful about this tuning process and gathering real-world feedback.
Comparing Phishing Detection Approaches Across Password Managers
The security industry has been working on phishing detection for years. Different password managers have taken different approaches, and understanding these differences helps explain what makes 1Password's approach distinctive.
Some password managers rely primarily on integration with third-party threat intelligence services. They outsource the detection to companies like Zscaler or Cloudflare that maintain global threat databases. This approach is relatively simple to implement and updates happen automatically as the third-party service updates their threat data. The downside is that you're dependent on another company's detection accuracy and you're potentially revealing which sites you're visiting to that service.
Other password managers build their own detection systems from scratch, analyzing every site locally in your browser. This keeps your browsing data private, but it requires significant security engineering resources and ongoing model training. The advantage is full control over your detection logic and the ability to tune it for your user base.
Bitwarden, another popular password manager, implemented a phishing detection feature that warns users when they're about to enter credentials into unrecognized sites. Their approach is relatively conservative, focusing on sites that are completely unknown to the Bitwarden servers rather than trying to identify phishing specifically. This creates fewer false positives but might miss sophisticated attacks on recognized domains.
Dashlane, meanwhile, has been integrating security features more broadly into their platform, including breach monitoring and identity theft protection. Their phishing detection is part of a larger security suite rather than a standalone feature.
1Password's approach seems to fall somewhere in the middle. They're building local detection that preserves privacy while also likely incorporating threat intelligence. The gradual rollout suggests they're being careful about false positives, and the fact that it's available across all plans suggests they're betting on this being a core security feature rather than a premium add-on.
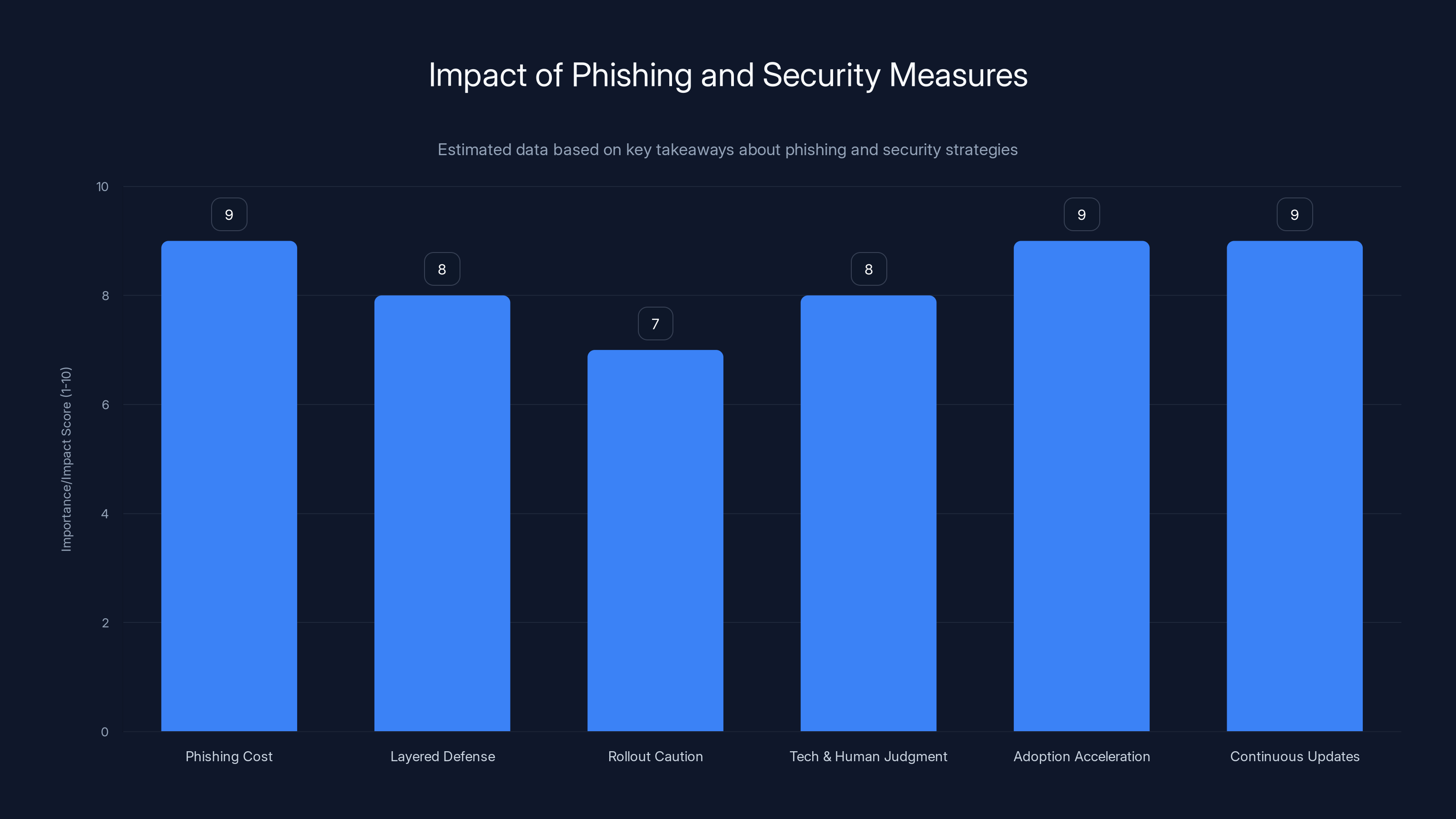
Phishing attacks are costly, with an average impact score of 9, highlighting the importance of layered defenses and continuous updates. Estimated data.
Real-World Phishing Attack Scenarios
Let's walk through some realistic phishing attack scenarios and see how 1Password's detection would actually help.
Scenario 1: The Credential Harvesting Email
You receive an email that appears to be from your company's IT department. The email says your password will expire in 24 hours and you need to update it immediately by clicking the link in the email. The link looks legitimate. It goes to something like "secure-password-update.yourcompany.com-services.com" (note the subtle extra domain component).
You click the link, and you're taken to a page that looks almost identical to your company's password reset page. You're about to enter your current password and new password when 1Password's phishing detection kicks in. The extension notices that the domain doesn't match 1Password's stored record of your company's legitimate login site. It also notices that the SSL certificate doesn't match. A warning appears: "This site may be impersonating your organization."
You pause. You read the warning. You close the tab and navigate directly to your company's website by typing the address into the address bar. You discover that you never actually needed to change your password, and IT never sent that email.
In this scenario, the phishing detection prevented a complete account compromise.
Scenario 2: The Brand Impersonation Attack
You're shopping online and you add some items to your cart. When you go to check out, you're redirected to a payment page. The page looks like it's from the retailer, but it's actually on a different domain that the attackers registered to look similar to the legitimate checkout domain.
You're about to enter your credit card information when 1Password's detection system notices that the domain is new (registered just days ago) and that the SSL certificate is from a different issuer than the legitimate site uses. It displays a warning.
You stop and look more carefully at the URL. You notice the subtle difference. You go back to the retailer's actual website and complete your purchase through the legitimate checkout.
In this scenario, you avoided entering your payment information into a fraudulent site.
Scenario 3: The Advanced Attack That Still Gets Through
This is where we need to be honest about limitations. A sufficiently sophisticated attacker might compromise the legitimate retailer's website or the DNS system that routes traffic to it. In this case, you'd be taken to a legitimate-looking site that's actually serving phishing content from a compromised server.
Or an attacker might use a man-in-the-middle attack to intercept your connection and replace the content with phishing content. These advanced attacks are outside the scope of what phishing detection can address.
Or, as the original 1Password blog acknowledges, a user might simply choose to manually copy and paste their credentials into a phishing site they don't trust, overriding the system entirely.
No phishing detection system can protect against a determined attacker who completely compromises the underlying infrastructure or against users who deliberately ignore warnings. The goal isn't perfection. The goal is to raise the barrier to entry enough that many attacks fail and that casual attackers move on to easier targets.
The Rollout Strategy and What It Means
1Password announced that the phishing prevention feature would be rolled out starting in early 2025, but acknowledged that it could take several weeks for everyone to receive it. This gradual rollout is actually revealing about how the company approaches security features.
Why not just flip a switch and enable it for everyone simultaneously? Several reasons.
First, a gradual rollout allows 1Password to monitor real-world performance. They can see how many false positives are occurring, whether legitimate sites are being incorrectly flagged, and whether the detection is actually preventing phishing attacks. If there are systemic issues, they can be caught and fixed before the feature reaches millions of users.
Second, it allows time for customer support to prepare. There will be users who encounter false positives and who need help understanding what the warnings mean. A gradual rollout lets support teams get up to speed and develop help documentation.
Third, it signals something important about 1Password's confidence level. If they were absolutely certain this feature was perfect, they could just enable it globally. The fact that they're rolling it out gradually suggests they're still tuning it and expecting to learn from real-world usage.
The different rollout strategy for individual users versus business users is also worth noting. Individual and family plan users get the feature enabled by default. Business users need admins to manually enable it. This suggests that 1Password wants to be cautious about enterprise environments where users might have different expectations about the tools they're using.
In an enterprise context, IT admins have generally whitelisted certain sites and configured password manager behavior to fit specific security policies. Introducing a new warning system without explicit opt-in could disrupt workflows. By requiring manual enablement for business, 1Password ensures that IT admins understand the feature and decide if it aligns with their security policies.
False Positives and User Trust
One of the biggest challenges with any warning system is maintaining user trust when false positives occur. A false positive is when the system warns about a legitimate site.
Imagine you're trying to access a legitimate site that 1Password incorrectly flags as phishing. You're now annoyed. You might blame the password manager rather than understanding that the warning is overly cautious. Worse, after a few false positives, you might stop taking the warnings seriously and click through even when there's a real phishing threat.
This is known as alert fatigue, and it's a well-documented problem in security. When users get too many false alarms, they tune them out. The system that's supposed to protect them becomes essentially invisible.
1Password needs to balance the false positive rate against the miss rate (attacks that aren't detected). Setting the threshold too high catches more attacks but creates more false positives. Setting it too low creates fewer false positives but misses some attacks.
The machine learning model that powers the detection is being trained to optimize this tradeoff. The company probably has internal metrics about what false positive rate is acceptable. Industry standards suggest that users will tolerate a false positive rate of around 1-2% if the system is detecting real threats effectively.
One way 1Password might handle this is by creating a whitelist system. If you override a warning and add a site to your whitelist, 1Password stops warning you about that site in the future. This serves two purposes: it respects your judgment and reduces future annoyance, and it gives 1Password data about which sites are generating false positives.

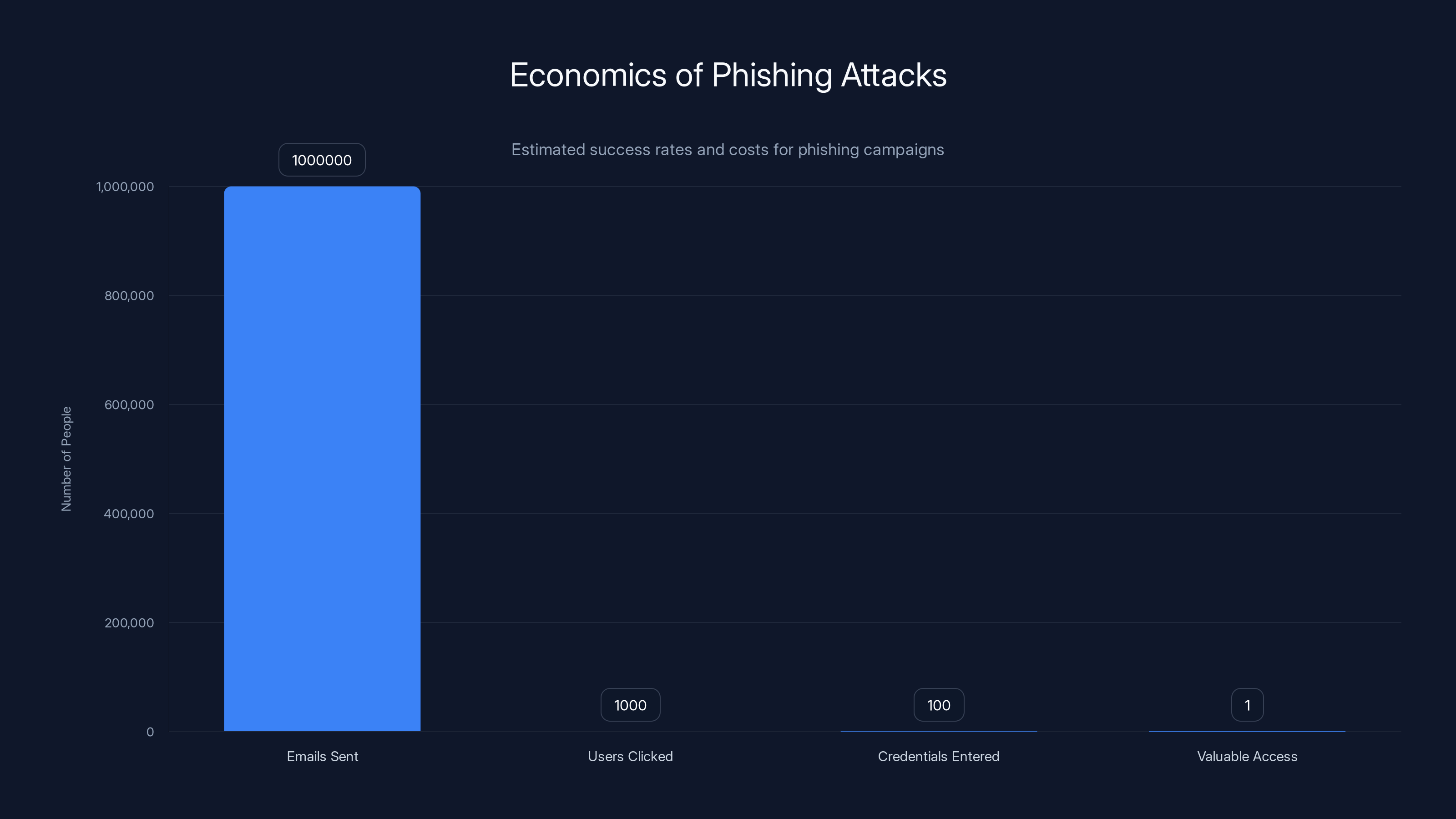
Estimated data shows that out of 1 million phishing emails sent, even a single valuable credential can make the attack worthwhile for attackers.
Privacy Implications of Phishing Detection
When a password manager analyzes every website you visit to check for phishing, there are privacy implications worth considering.
In the best case, all of this analysis happens locally in your browser extension. 1Password sends no information about the sites you're visiting to any external server. The detection is entirely based on local rules and local models.
But if 1Password uses any threat intelligence data or cloud-based machine learning models, they might need to send some information about the sites you're visiting to their servers. This is where privacy gets complicated.
Most password managers are transparent about this. When they use cloud-based threat intelligence, they'll typically hash the domain you're visiting before sending it anywhere. A hash is a one-way mathematical function that converts the domain name into a unique fingerprint. Even if 1Password sends the hash to their servers, the company on the receiving end sees a hash, not the actual domain name.
But this isn't perfect privacy. A company that maintains a list of popular domains could theoretically hash all of them and compare against the hashes they receive to figure out which sites users are visiting. It's not trivial, but it's not impossible either.
For sensitive use cases, local-only detection is more private. For most users, the privacy tradeoff of using threat intelligence is acceptable if it means better phishing detection.
The important thing is transparency. 1Password should clearly document what data is being sent, to where, and how it's being used. Users deserve to make informed decisions about the privacy tradeoff.
Integration With Existing Security Practices
Phishing detection in a password manager is just one layer of a comprehensive security strategy. Understanding how it fits into the broader picture helps explain why it matters.
For individuals, the layers of phishing defense typically look like this:
First, there's email security. Most email providers now use machine learning to detect phishing emails before they reach your inbox. Gmail, Outlook, and Apple Mail all have built-in phishing detection. These systems are quite effective at filtering obvious phishing emails. The 1Password detection catches the ones that slip through.
Second, there's browser-based security. Most modern browsers will warn you if you're visiting a known malicious site or if you're visiting a site with a suspicious SSL certificate. This is a baseline of protection that applies to all extensions and all sites.
Third, there's the password manager's phishing detection. 1Password's new feature adds an extra layer specifically focused on credential theft.
Fourth, there's user training and awareness. Even with all these technical defenses, user awareness is still critical. If you understand what phishing looks like and you know to pause and verify before entering credentials, you're much less likely to fall for an attack.
For businesses, the picture is more complex. Companies typically layer:
Mail gateway filtering to catch phishing emails before they reach users. Email authentication protocols like DMARC and SPF to prevent email spoofing. Multi-factor authentication to ensure that stolen credentials alone aren't sufficient to compromise an account. Single sign-on systems that reduce the number of places users enter credentials. Browser isolation technology that runs websites in sandboxed environments. Security awareness training that teaches employees how to recognize and report phishing attempts.
When 1Password's phishing detection is added to this stack, it becomes another layer in a defense-in-depth strategy. It's not replacing any of these other defenses. It's complementing them.
The ideal approach is that if a phishing email slips past the mail gateway, and a user clicks the link, and they're taken to a phishing site, 1Password's detection will catch it before they enter their credentials. That's a meaningful reduction in risk.
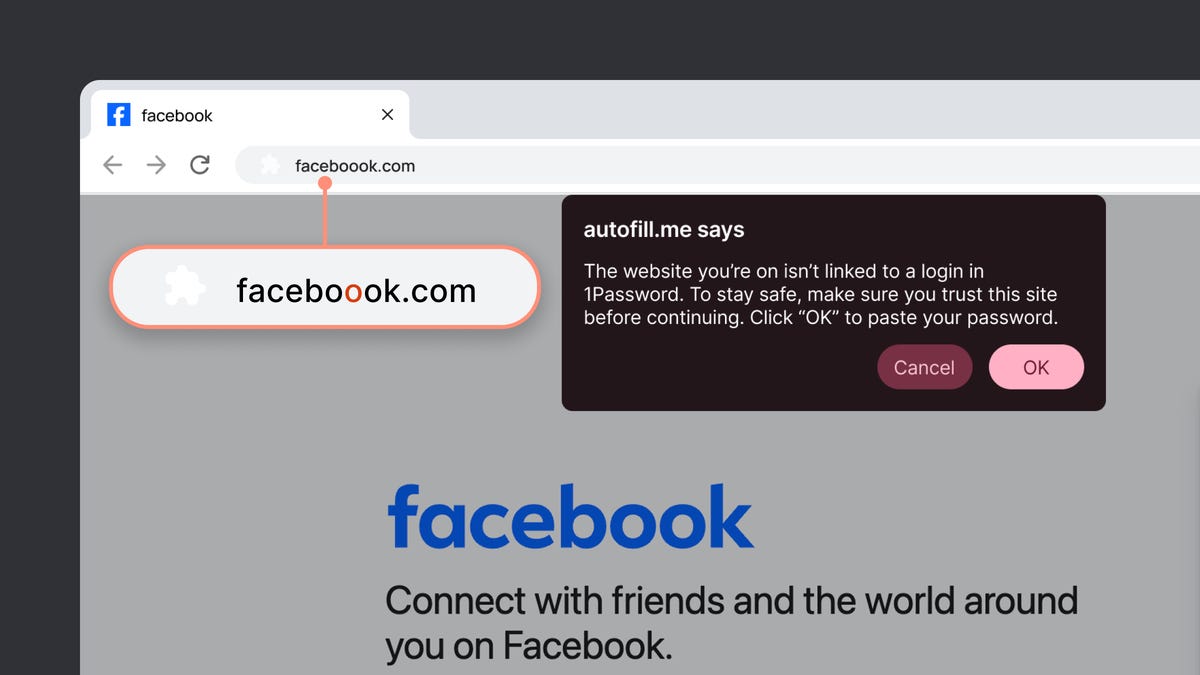
The Competitive Landscape of Password Manager Security
Phishing prevention isn't unique to 1Password anymore. It's becoming an expected feature across the password manager category. Understanding where different products stand helps explain what's driving this innovation.
Microsoft is integrating phishing detection directly into their Edge browser, which gives them an advantage in identifying phishing sites across the web, not just within their password manager.
Apple has implemented phishing detection in iCloud Keychain, though it's limited to Safari and other Apple browsers.
The competition in this space is driving innovation. Each company is trying to offer better security while maintaining usability. 1Password's approach of combining local analysis with threat intelligence and machine learning seems to be a reasonable middle ground that balances security and privacy.
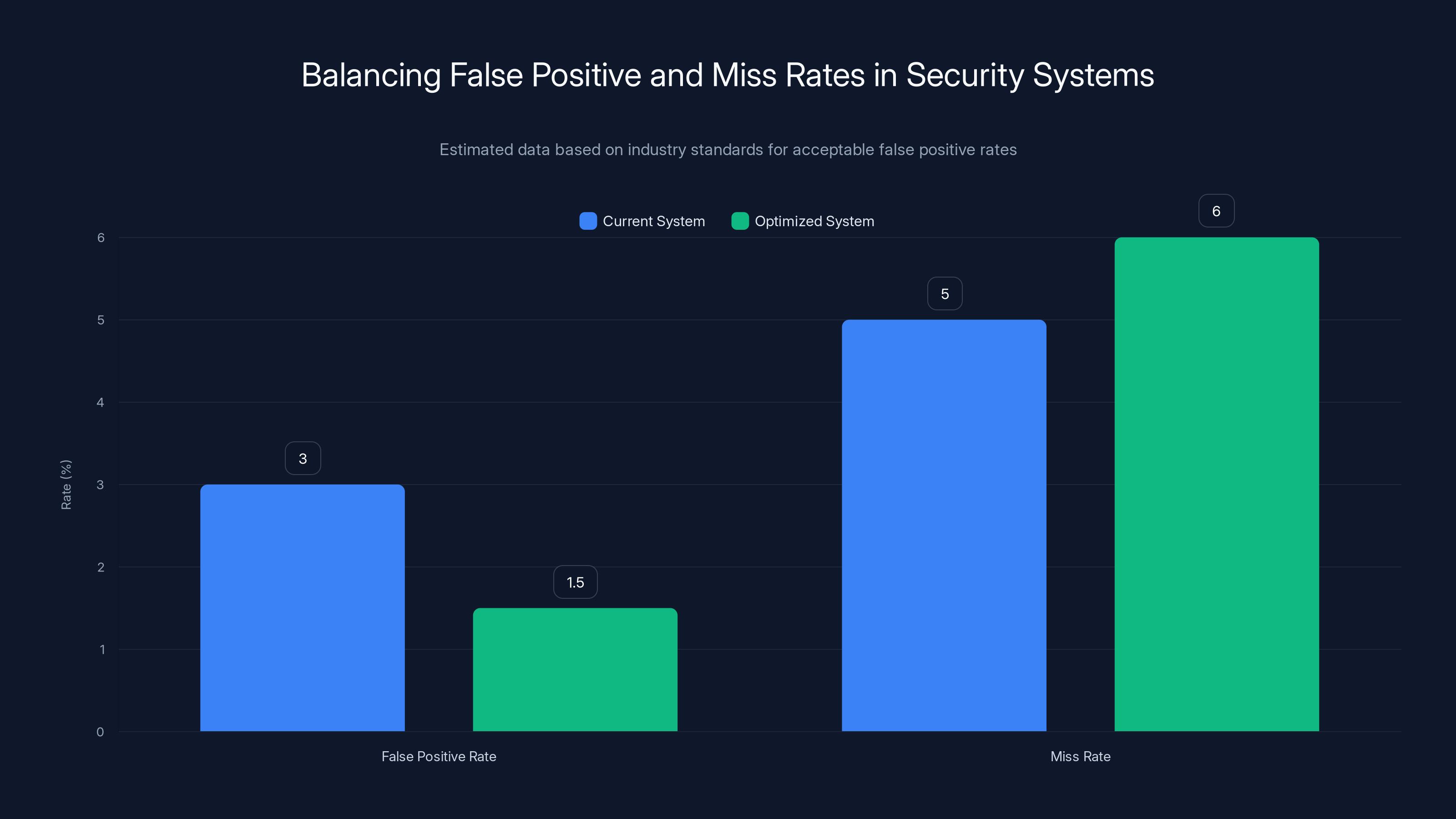
Balancing false positive and miss rates is crucial for maintaining user trust. An optimized system aims for a 1.5% false positive rate while slightly increasing the miss rate to 6% to ensure effective threat detection. Estimated data.
Understanding the Technical Architecture
For those interested in how this actually works under the hood, the architecture of phishing detection in a browser extension is worth exploring.
The 1Password browser extension runs in your browser with direct access to the page content and the request/response cycle. When you navigate to a website, the extension can see the URL, inspect the page content, and examine the SSL certificate information.
The extension doesn't need to contact a server for every website you visit, though it might contact servers periodically to update its threat database or machine learning models. The key analysis can happen locally.
When the extension detects a suspicious site, it can inject warnings directly into the page or display them in the extension popup. These warnings are part of the extension's user interface and can't be easily bypassed by the website itself.
The detection logic itself is probably written in JavaScript, the language that powers browser extensions. This language is flexible and well-suited to pattern matching and analysis of web content. The machine learning models might be written in Python or another language and then compiled to run in JavaScript.
One interesting architectural decision is how to handle performance. Analyzing every website for phishing characteristics takes processing power. The extension can't use so much CPU that it slows down your browsing. The architecture probably includes optimizations like only running deep analysis on sites that request login credentials and using cached results for sites you visit frequently.

How Users Should Respond to Phishing Warnings
The existence of a warning system only matters if users actually respond appropriately to the warnings. Here's what users should do when they see a 1Password phishing warning.
First, stop and read the warning carefully. Don't just dismiss it reflexively. Take a moment to understand what the warning is saying and why the system thinks there's a problem.
Second, verify the site independently. Check the URL in your browser's address bar carefully. If you're trying to access a banking or shopping site, try typing the website address directly into your browser rather than clicking any links.
Third, think about context. Did you expect to be on this site? Did you navigate to it intentionally or were you redirected from a link in an email or another website? Phishing sites are often reached through unexpected redirects or suspicious links.
Fourth, if you're still unsure, don't proceed. The cost of being wrong is much higher for phishing than for false positives. Even if there's a small chance it's a false alarm, it's better to be cautious.
Fifth, report the phishing site if possible. Most companies have a process for reporting suspected phishing attempts. Reporting helps the company improve their defenses and helps law enforcement track attackers.
What users should NOT do is ignore phishing warnings consistently. If you're getting frequent false positives, that's worth reporting to 1Password so they can improve the detection. But you shouldn't train yourself to ignore the warnings.
The Economics of Phishing Attacks
Understanding why phishing is so prevalent helps explain why so many companies are investing in detection.
Phishing is economically attractive to attackers because of the low cost to conduct attacks and the high potential payoff. Sending a phishing email costs essentially nothing. If even 0.1% of recipients fall for it, the attack is profitable.
Consider the numbers. An attacker sends a phishing email to 1 million people. It costs them essentially nothing. 0.1% of people (1,000 people) fall for it and visit the phishing site. Of those, maybe 10% enter their credentials (100 people). If even one of those credentials gives the attacker access to something valuable, the attack succeeded.
Now multiply this. Attackers send thousands of phishing campaigns per day. They're constantly iterating on techniques to improve success rates. The economics are completely in the attacker's favor.
From the defender's perspective, preventing phishing is expensive. It requires investment in detection technology, security training, and ongoing updates as attackers adapt. But the cost of a successful phishing attack (both the direct financial cost and the intangible cost of breached trust) justifies the investment.
This economic reality is why phishing detection is becoming a standard feature. Companies like 1Password can absorb the cost of developing and maintaining these systems across millions of users, making the per-user cost negligible. For individual users, phishing detection is essentially a free security upgrade.
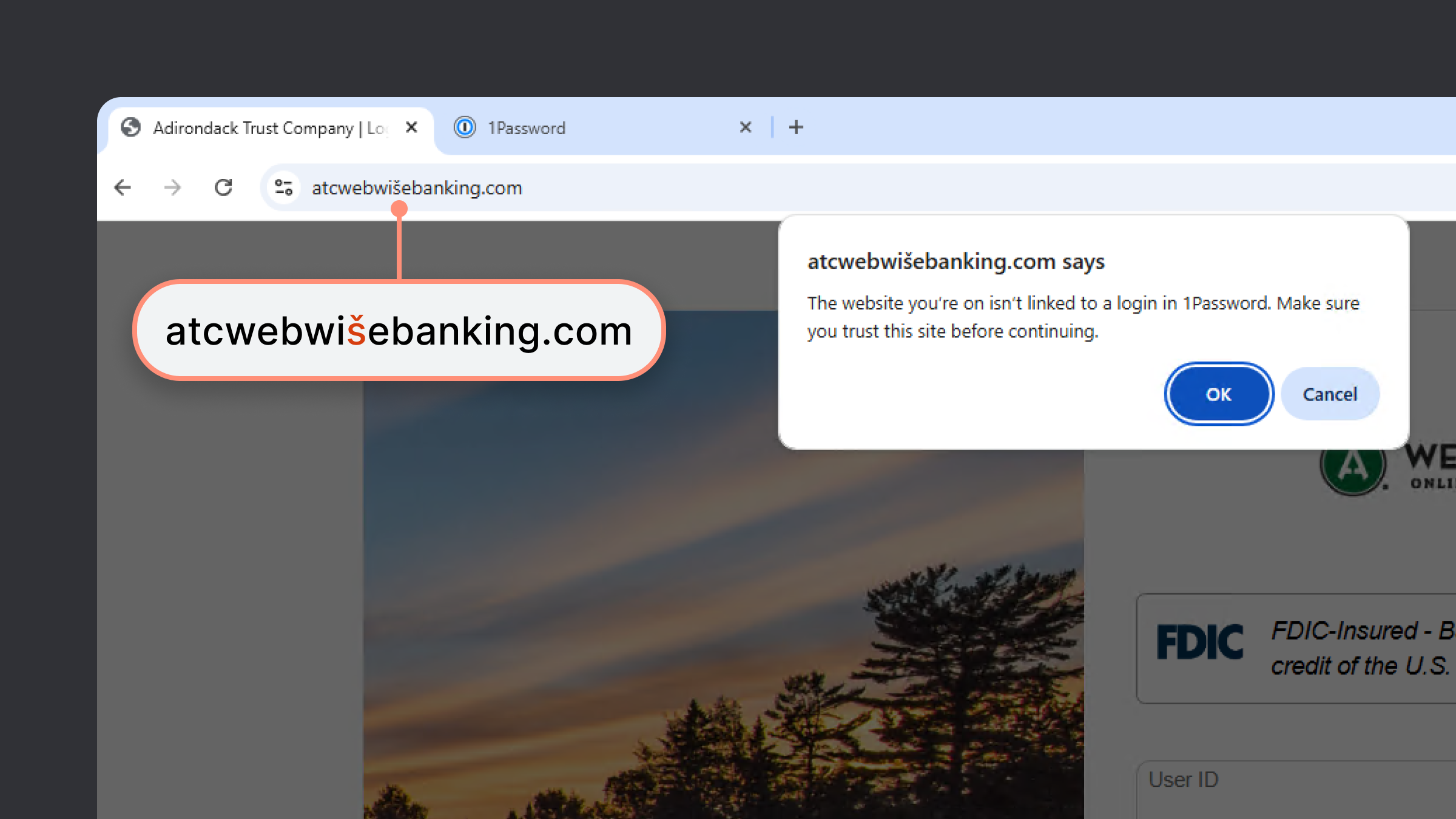
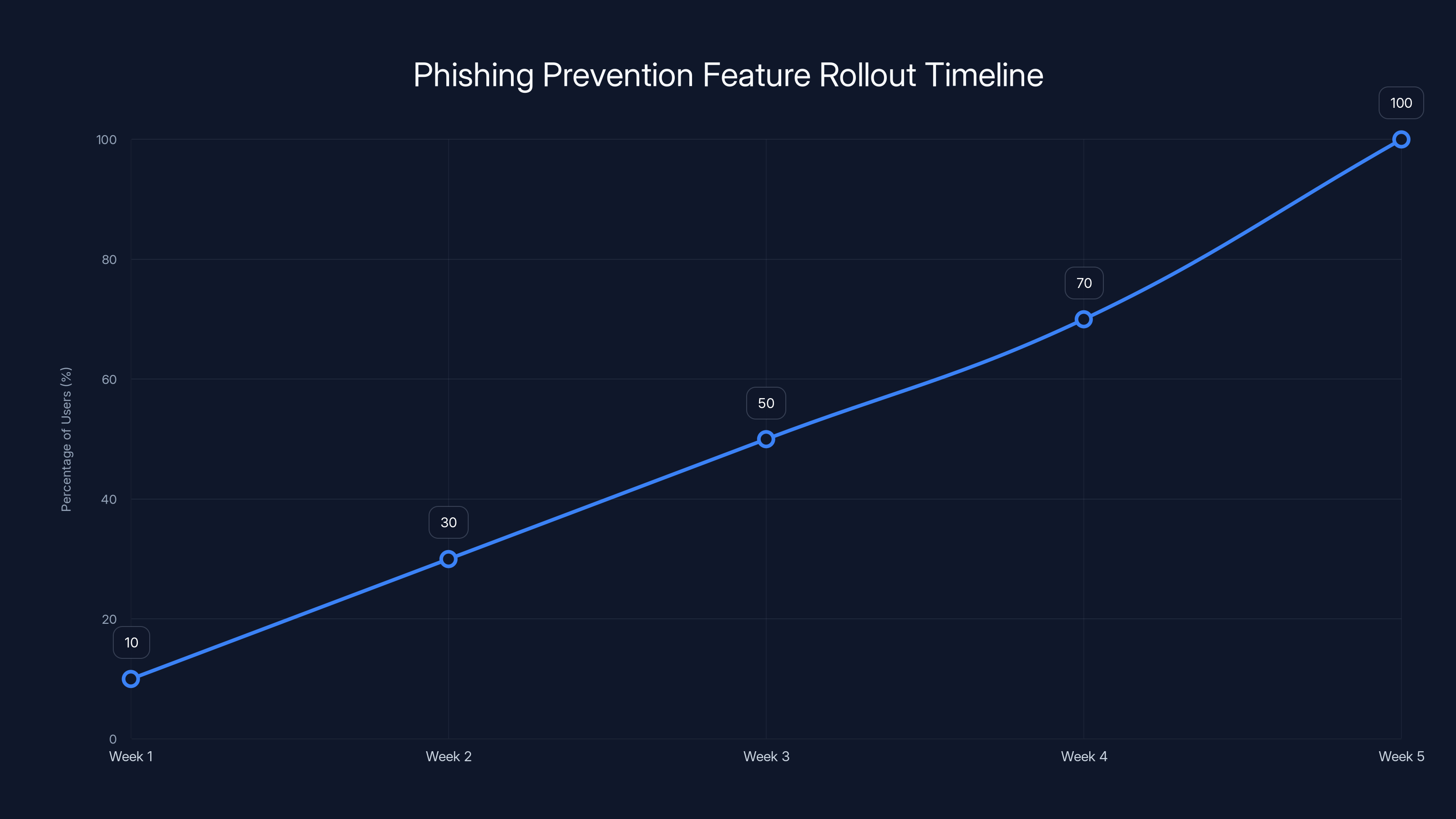
The gradual rollout of 1Password's phishing prevention feature is estimated to reach all users over a 5-week period, allowing for monitoring and adjustments. Estimated data.
Future Directions in Phishing Detection
Where is phishing detection heading in the future? Several trends seem likely.
First, we'll probably see phishing detection become even more deeply integrated into browsers and operating systems. Rather than relying on individual extensions, the browser itself will have built-in phishing detection that applies across all sites and all extensions.
Second, phishing detection will become more sophisticated as machine learning models improve. Future systems will probably detect phishing attempts that are harder to distinguish from legitimate sites, using more subtle signals about page structure, user behavior patterns, and content semantics.
Third, we might see phishing detection integrated with incident response. Rather than just warning users, systems might automatically gather forensic information about the phishing attempt for later analysis and prosecution.
Fourth, phishing detection will probably become more personalized. Machine learning models could learn about your specific habits and alert you when something doesn't match your normal behavior. If you never access your banking app from certain countries, for example, you could get alerted if a login attempt happens from there.
Fifth, there's likely to be development of anti-phishing that goes on the attacker's end. Frameworks and standards that make it harder to impersonate legitimate sites through better cryptographic verification, better domain security, and harder authentication mechanisms.
The cat-and-mouse game between attackers and defenders will continue to evolve, but the trend is clearly toward better detection and stronger defenses.
Limitations You Need to Understand
It's important to be clear about what 1Password's phishing detection can't do, because overconfidence in a security tool is actually more dangerous than underconfidence.
First, the system can't protect you if you manually override it. If you see a warning and you decide to proceed anyway and manually type in your credentials, the system has done everything it can. You've made a deliberate choice to ignore the warning.
Second, the system can't protect against advanced attacks that compromise the legitimate infrastructure. If an attacker has breached the company's website or DNS system, you'll be taken to what appears to be a legitimate site but is actually serving phishing content. The warning system can't detect this because from a technical perspective, it looks legitimate.
Third, the system has a learning curve. New phishing techniques might not be detected immediately. Attackers are actively trying to figure out ways to evade detection, and there's always a window where new techniques work before the detection system is updated.
Fourth, the system can create false positives. You might encounter legitimate sites that have characteristics that the detection system finds suspicious. This is frustrating but unavoidable when you're trying to balance security with usability.
Fifth, the system can't replace other security practices. Using a phishing detection system but not using multifactor authentication is like locking your door but leaving your windows open. You need defense in depth.
Finally, the system relies on active maintenance. 1Password needs to continuously update their detection rules and machine learning models as attackers develop new techniques. If they stop maintaining the system, it will become increasingly ineffective.

Implementation Best Practices for Businesses
If you're implementing 1Password with phishing detection in a business environment, here are practices that maximize the security benefits.
First, enable the feature thoughtfully. As noted, 1Password requires business admins to manually enable it. Take time to understand how it works before rolling it out to your organization.
Second, test it on internal sites before enabling it broadly. Create a test group and see if the feature correctly identifies your internal sites as legitimate. You don't want legitimate internal traffic blocked by overly aggressive detection.
Third, communicate with your users about what the feature is and why it matters. A security feature only works if users understand and trust it. Send out a brief explanation and show users an example of what a phishing warning looks like.
Fourth, monitor the feedback. As users start experiencing the system, they'll report false positives and issues. Listen to this feedback and report it to 1Password. Help the company improve the system.
Fifth, combine it with other defenses. Phishing detection in the password manager is one layer. You should also have email security, browser isolation, multifactor authentication, and security awareness training.
Sixth, use the warning events as learning opportunities. If users are encountering phishing attempts, even ones that are caught by the detection system, investigate them. Understand where the phishing attacks are coming from and whether there are internal vulnerabilities that are making your organization a target.
The Bigger Picture: Why This Matters Now
The timing of 1Password's phishing detection rollout is worth noting because it reflects broader changes in the cybersecurity landscape.
Phishing attacks have been increasing in sophistication and frequency. AI and language models are making it easier for attackers to generate convincing phishing content at scale. Deepfakes and AI-generated voice calls are making impersonation attacks more effective. The threat is real and growing.
At the same time, people are increasingly relying on password managers as a core part of their security infrastructure. Unlike browsers or operating systems, password managers update frequently and are actively maintained. They've become the natural place to add security features that protect users at the authentication boundary.
Companies are also dealing with the reality that users are tired of security warnings and security friction. Multi-factor authentication has become normalized because it provides clear value. Phishing detection in a password manager is positioned similarly: it adds a layer of security without requiring users to change their behavior significantly.
The introduction of this feature by 1Password signals that the password manager industry sees phishing detection as a table-stakes feature moving forward. Other companies will likely follow with similar capabilities if they haven't already.
For users, this is good news. You're getting better security without having to do anything different. For attackers, this is bad news. The bar to successfully execute a phishing attack just got higher.
Conclusion: Taking Action
Phishing attacks remain one of the most effective ways for criminals and sophisticated attackers to compromise individuals and organizations. The human element of these attacks makes them inherently difficult to defend against, which is why automation and detection systems matter so much.
1Password's new phishing prevention feature represents a meaningful step forward in this arms race. By automatically detecting and warning about suspicious websites, the system removes the burden from users to manually verify every site they visit. That's a significant improvement in security posture.
But this feature isn't a complete solution. It's one layer in a comprehensive security strategy that should also include multifactor authentication, email security, browser security, and user awareness. The system has limitations and isn't foolproof. It can create false positives that might frustrate users, and it can't stop determined users from overriding warnings.
For individuals using 1Password, the feature will be automatically enabled once it rolls out to your account. You don't need to do anything, but you should understand what the warnings mean when you see them and take them seriously.
For businesses, the feature requires manual enablement. Take time to understand how it works, test it in your environment, and communicate it clearly to your users. Use it as part of a layered defense strategy rather than relying on it alone.
For everyone, the broader lesson is that security is increasingly being built into the tools we use every day. That's a positive trend. The password managers and browsers and operating systems we rely on are getting smarter about protecting us. That doesn't mean we can be passive about security, but it does mean we have better tools at our disposal.
Stay vigilant. Take phishing warnings seriously. Use multifactor authentication. Don't reuse passwords. And appreciate the work that goes into detecting threats automatically so you don't have to do it manually.
FAQ
What exactly is 1Password's phishing prevention feature?
1Password's phishing prevention feature is a security system built into the password manager's browser extension that automatically detects and warns users when they land on websites that show suspicious characteristics of phishing attempts. The system analyzes factors like domain names, SSL certificates, domain registration age, and page content to identify potential fake sites before you enter any credentials.
How does 1Password detect phishing sites?
The detection system works by analyzing multiple factors simultaneously. It examines the website's domain name to spot variations that might indicate spoofing, verifies the SSL certificate against recognized certificate authorities, checks the domain registration age (newly registered domains are more suspicious), and analyzes the page content and structure to identify copied or fraudulent layouts. When these factors add up to suspicious activity, the system displays a warning directly in your browser.
Is the phishing detection enabled by default?
For individual and family plan users, yes, the phishing prevention feature is enabled automatically once it rolls out to your account. For business users, the feature must be manually enabled by 1Password administrators. The gradual rollout means it could take several weeks before everyone receives it, and 1Password is monitoring real-world performance before making it universally available.
Can the phishing detection prevent all phishing attacks?
No, no phishing detection system can prevent all attacks. The feature protects against many common phishing methods but can't stop attacks that compromise legitimate infrastructure, and it can't prevent users who deliberately ignore warnings from entering credentials manually. It's designed to raise the barrier to entry for attackers and catch common phishing techniques, not to provide absolute protection.
What should I do when I see a phishing warning from 1Password?
When you see a phishing warning, pause and read it carefully. Don't dismiss it reflexively. Verify the website address in your browser's address bar, and consider typing the correct address directly rather than clicking any links. If you're unsure whether the site is legitimate, don't proceed. The cost of being cautious is much lower than the cost of being compromised by a phishing attack.
Does phishing detection slow down my browser?
The system is designed to minimize performance impact. Analysis happens locally in the browser extension and is optimized to use minimal CPU. Most users shouldn't notice any slowdown, though the extension will use some additional memory. If you notice significant slowdown, report it to 1Password support.
How does this compare to other password managers' phishing protection?
Different password managers take different approaches. Bitwarden's phishing detection is simpler, focusing mainly on alerting users to unrecognized sites. Microsoft Edge has phishing detection built directly into the browser. 1Password's approach combines local analysis with machine learning and threat intelligence, aiming for a balance between security and privacy. The key difference is 1Password's attempt to specifically identify phishing characteristics rather than just alerting on unknown sites.
Is there any privacy concern with phishing detection?
The analysis happens locally in your browser extension, which maintains privacy. However, if 1Password uses cloud-based threat intelligence or machine learning models, some information about the sites you visit might be sent to their servers. Typically, this information is hashed or anonymized before sending. 1Password should provide clear documentation about what data is collected and how it's used.
What if I encounter a false positive from phishing detection?
If you encounter a website that you're certain is legitimate but 1Password flags it as phishing, you can report it to 1Password. The company uses this feedback to improve their detection and reduce false positives. You may be able to add the site to a whitelist so you don't get warnings about it in the future, though you'll need to verify the correct domain first.
Should I turn off phishing detection if it's causing too many false positives?
If you're experiencing frequent false positives, report them to 1Password first rather than disabling the feature entirely. Help the company improve the detection by providing feedback about which sites are generating false alarms. However, if you find the feature truly interferes with your workflow, you can disable it in your 1Password settings. Just be aware that you're reducing your security posture by doing so.

Key Takeaways
- Phishing is expensive: Successful phishing attacks cost businesses an average of $4.8 million, making detection a worthwhile investment
- Layered defense works: Phishing detection in 1Password is one component of a comprehensive security strategy that should also include MFA, email security, and user awareness
- Gradual rollout signals caution: The fact that 1Password is rolling out the feature gradually suggests they're being careful about false positives and real-world performance
- Technology complements human judgment: Even with automatic detection, users still need to understand phishing threats and take warnings seriously
- Adoption is accelerating: Multiple password managers and browsers are now implementing phishing detection, making it an expected baseline feature
- The arms race continues: Attackers adapt quickly to new defenses, so these systems require continuous maintenance and updating to remain effective
Related Articles
- LastPass Phishing Scam: How to Spot Fake Support Messages [2025]
- Most Spoofed Brands in Phishing Scams [2025]
- How to Disable Chrome's On-Device AI Scam Detection [2025]
- UK VPN Ban Explained: Government's Online Safety Plan [2025]
- PcComponentes Data Breach Denial: What Really Happened [2025]
- SMS Sign-In Links: A Critical Security Vulnerability Affecting Millions [2025]
![1Password's New Phishing Prevention Feature [2025]](https://tryrunable.com/blog/1password-s-new-phishing-prevention-feature-2025/image-1-1769090844106.jpg)



