Minecraft Server Security Guide: Keep Your Server Safe [2025]
Running your own Minecraft server sounds amazing in theory. You get unlimited creative control, no subscription fees, and the satisfaction of building something from scratch. Then reality hits.
Your server gets DDoS attacked. A player finds a vulnerability in your plugin and exploits it. You realize you forgot to back up your world, and someone deleted it. Your electricity bill triples because your PC runs 24/7.
Here's the thing: hosting a Minecraft server isn't inherently dangerous, but it requires thinking like a sysadmin, not just a gamer. Most server problems aren't caused by sophisticated hackers. They're caused by overlooked configurations, weak passwords, outdated software, and untrusted plugins.
This guide walks you through every security consideration you need to know before hosting a Minecraft server. Whether you're planning to self-host on your PC or exploring dedicated hosting options, you'll understand the real risks involved and exactly how to mitigate them.
I've tested both self-hosted and managed server setups, interviewed server administrators who've dealt with security incidents, and researched the most common attack vectors targeting Minecraft infrastructure. What you'll find here isn't marketing fluff. It's the actual security practices that experienced server admins use.
TL; DR
- Self-hosting works but requires careful configuration, regular updates, and strong security practices
- Strong passwords and 2FA are your first line of defense against unauthorized access
- Firewall configuration and port management eliminate most attack surface area
- Plugin vetting is critical—malicious mods can compromise your entire server
- Dedicated hosting costs less than you think and handles infrastructure security for you
- Regular backups prevent catastrophic data loss from attacks or accidents
- RCON disabled by default is good, but verify it's actually disabled
- Whitelist your server to prevent unwanted players from ever connecting
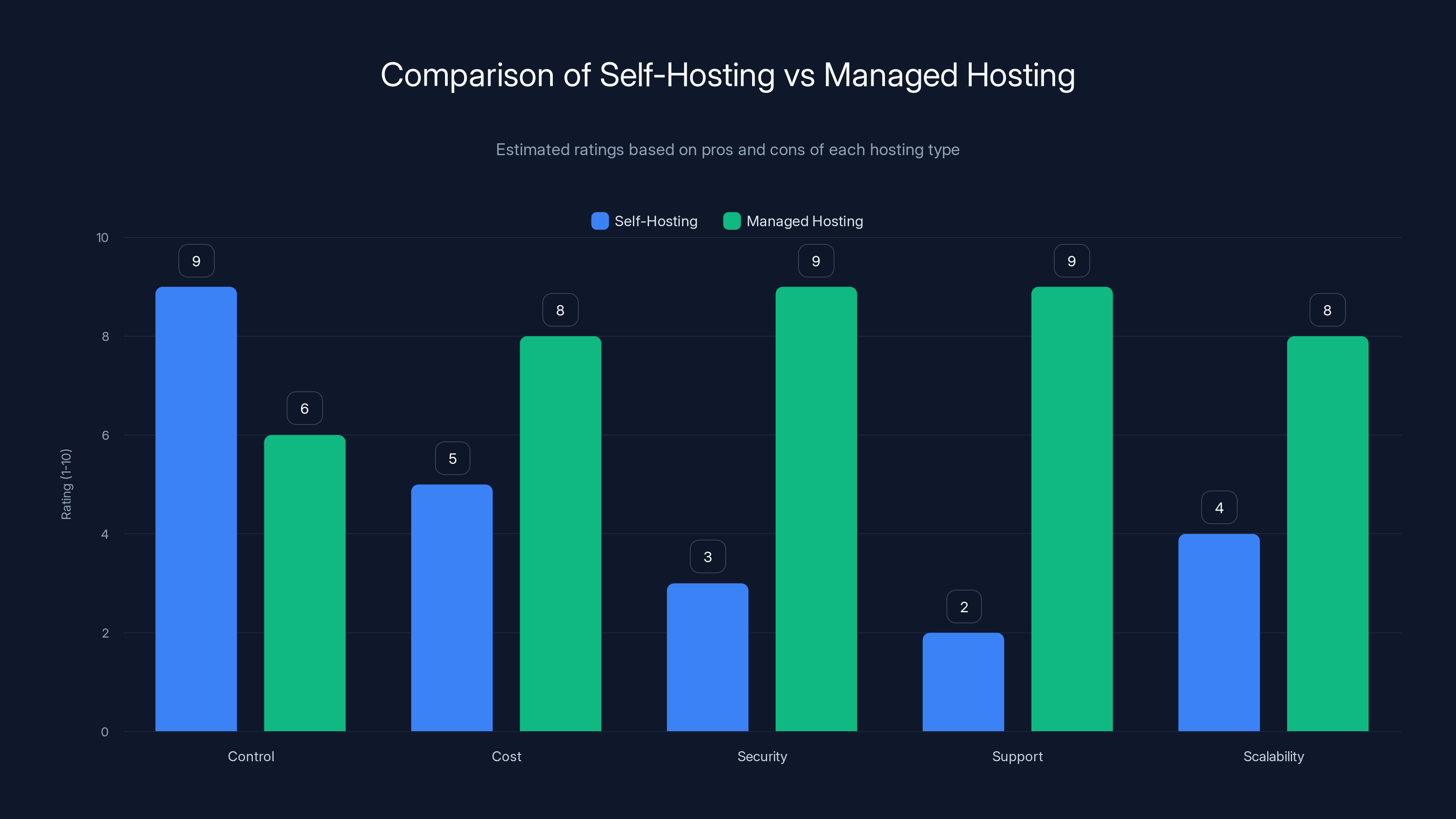
Self-hosting offers maximum control but lacks in security and support, while managed hosting excels in security, support, and scalability. Estimated data based on typical hosting experiences.
Understanding Minecraft Server Vulnerabilities
Before jumping into solutions, you need to understand what you're actually protecting against. Minecraft servers face several distinct threat categories, each requiring different defenses.
First, there's unauthorized access. Someone figures out your admin password or finds an unpatched vulnerability in your server software. Once inside, they can execute commands, modify world data, or crash the server entirely. This is the most common attack vector, and it's almost always preventable.
Second is denial of service (DoS) attacks. An attacker floods your server with traffic, making it unresponsive to legitimate players. If your server runs on your home connection, a basic DDoS can saturate your bandwidth completely. You'll get the blame even though you're the victim.
Third is plugin exploits. A popular plugin has a vulnerability. An attacker exploits it to escalate privileges, execute arbitrary code, or steal player data. The catch: you might not know the vulnerability exists until it's already been exploited.
Fourth is social engineering. Someone tricks a trusted admin into giving them access. Or a player social engineers an admin into installing a malicious plugin "recommended by the community."
Fifth is hardware compromise. You're running the server on shared hardware with other services. An attacker compromises another service, then pivots to your Minecraft server. Or someone physically accesses your PC and copies the server files containing player data and world information.
Fifth is data exposure. Your server contains player IPs, usernames, potentially player accounts linked to the server. If compromised, this data can be used for harassment, stalking, or identity theft.
Understanding these threat categories helps you prioritize defenses. You're not trying to achieve perfect security (impossible). You're trying to eliminate the easy wins that attackers exploit first.
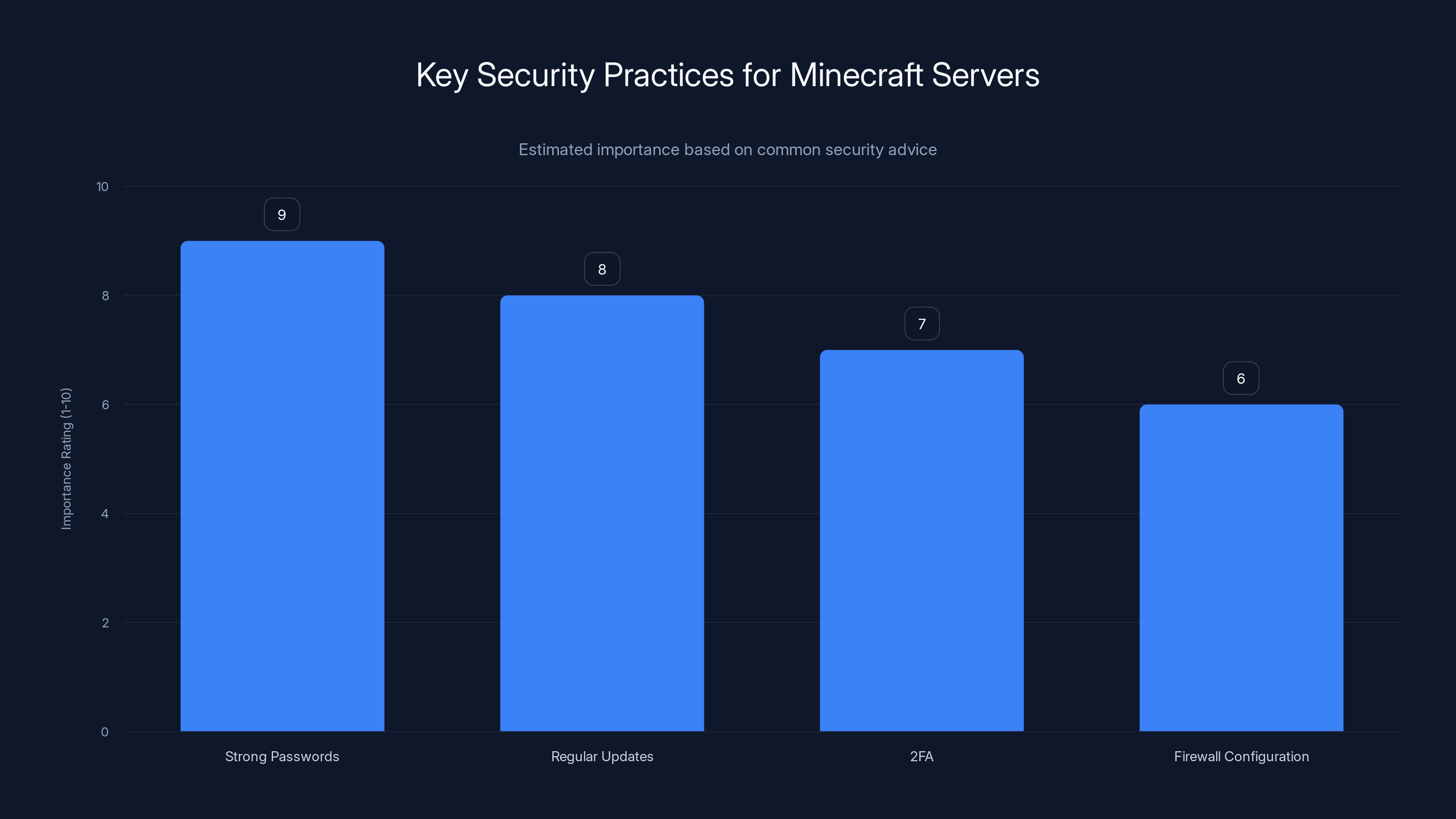
Strong passwords and regular updates are the most critical security practices for Minecraft servers. Estimated data.
The Basics of Server Hardening
Server hardening means closing every unnecessary door and locking the ones that remain. Most of this is straightforward configuration, not rocket science.
Update Your Server Immediately and Regularly
Every Minecraft server update includes security patches. Mojang (now part of Microsoft) actively maintains the Java Edition server software, releasing updates regularly. When you skip updates, you're leaving known vulnerabilities open.
But here's what most people miss: it's not just the Minecraft server software. Your Java runtime needs updates. Your operating system needs updates. Your router firmware needs updates. These aren't directly related to Minecraft, but they're part of the system running your server.
Set a schedule. Update your server weekly, ideally during low-traffic times. If you're using a managed host, they handle this automatically. If you're self-hosting, make it a habit.
The real risk isn't that you forget to update occasionally. It's that you forget for months. Then a critical vulnerability gets exploited, and you realize your server is running software from 2023.
Implement Strong Password Security
Your admin password is the master key to everything. A weak password gets cracked in minutes. A strong password makes brute-force attacks impractical.
Strong means at least 16 characters mixing uppercase, lowercase, numbers, and symbols. "My Server 123!" is weak. "Tr 0p!cal$unset#2024*Blue" is strong. The difference? One can be cracked in hours, the other in years.
Better yet, use a passphrase. "blue-elephant-running-backward-23" is 34 characters, easy to remember, and cryptographically stronger than most passwords. It's harder to brute-force because the character set is larger, and length matters more than complexity.
Store your password in a password manager like Bitwarden or 1Password. Never save it in a text file on your desktop. Never email it to yourself. Never use the same password across multiple servers.
If someone asks for your admin password (even someone claiming to be from Mojang or your host), the answer is no. Legitimate administrators never ask for passwords. Ever.
Enable Two-Factor Authentication (2FA)
If your hosting provider offers 2FA for the control panel, enable it immediately. This adds a second requirement beyond your password. Even if someone steals your password, they can't access your account without your phone or authenticator app.
Use an authenticator app like Authy or Google Authenticator, not SMS-based 2FA if possible. SMS is vulnerable to SIM swapping attacks. Authenticator apps are resistant to this attack.
Backup your 2FA recovery codes. If you lose access to your authenticator app and don't have recovery codes, you could get locked out of your own server.
Minimize Admin Access
This is where people often fail. You give admin access to your friend "temporarily." They give it to someone else. Suddenly you've got five people with admin access and you can't remember who has what.
Better approach: only you have admin access. If someone needs to manage something specific, use role-based permissions instead. Most server software supports moderators with limited permissions (can kick players, reset claims, etc.) without full admin access.
If you absolutely must give admin access to someone else, change your own password afterward. This invalidates any cached credentials they might have.
Don't share passwords via Discord, email, or messaging apps. These leave traces. If access is truly necessary, use a password manager with permission delegation, or use SSH keys instead of passwords for technical access.
Disable RCON (Remote Console)
RCON is a feature that lets you execute server commands remotely. Sounds useful, but it's a massive security risk. If RCON is enabled and someone gets the password, they can crash your server, execute arbitrary commands, and modify world data.
The good news: RCON is disabled by default in modern Minecraft server software. Verify this by checking your server properties file. Look for the line enable-rcon=false. If it says true, change it immediately and restart your server.
If you actually need remote command execution (rare for casual servers), use SSH to connect to your server directly instead of relying on RCON. SSH is far more secure and gives you better control.
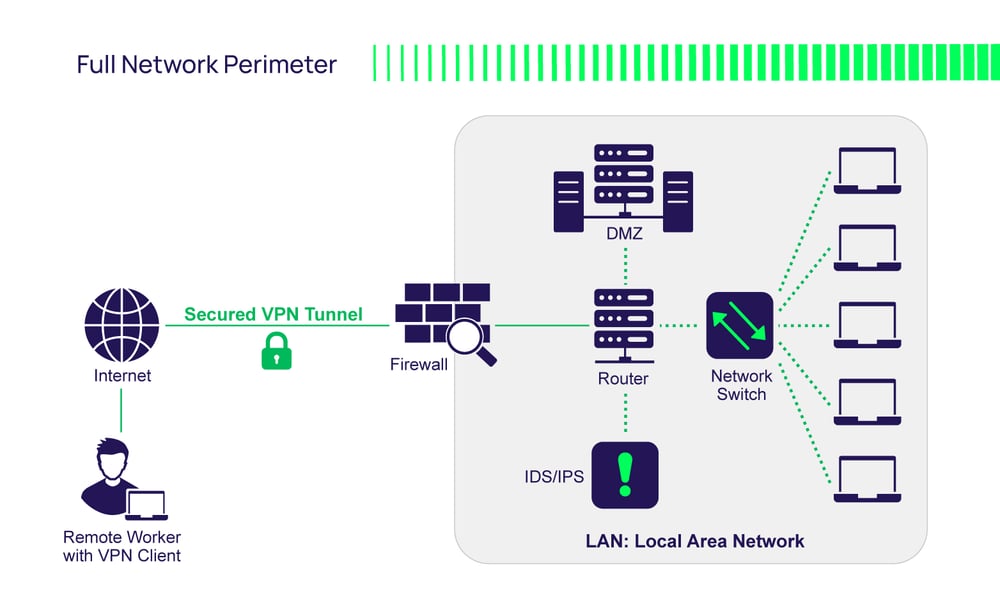
Network and Firewall Configuration
Your firewall is the bouncer at the door. Its job is to let legitimate players in and keep attackers out.
Understanding Ports and Port Management
Minecraft servers run on a specific port (default is 25565). Your firewall needs to allow traffic on that port. But here's the crucial part: it should allow traffic only on that port.
This is where many self-hosters mess up. They disable their firewall entirely "for convenience." Or they open all ports. This is like leaving your front door wide open.
Configure your firewall (Windows Defender Firewall on Windows, UFW on Linux, or your router's firewall) to allow inbound traffic only on port 25565 (or whatever port you're using). Everything else gets blocked.
If you're using a VPS or dedicated hosting, the host provides firewall management. Use it. Close all ports except the one your Minecraft server actually uses.
Binding to the Correct Network Interface
When you start a server, it binds to a network interface. The default is usually all interfaces, which means it's accessible from anywhere. For a casual server, you might want to restrict it.
If you're only playing with local friends, bind your server to localhost (127.0.0.1). This makes it accessible only from your computer. Friends can't connect remotely, but neither can attackers.
If friends are joining remotely, you need to bind to your public IP address. But understand that this exposes your server to the internet. Anyone can try to connect.
Whitelisting Players
Whitelisting is your most effective defense against unwanted players accessing your server. When enabled, only players on your whitelist can connect.
This prevents:
- Griefers finding your server and destroying builds
- Hackers testing exploits against your server
- Malicious players introducing infected mods or malware
- Resource consumption from random players
To enable whitelisting, set white-list=true in your server.properties file. Then add player names to the whitelist.json file in your server directory.
The downside: whitelisting is inconvenient if you want to run a public server. You need to manually add each player. But for a small server with friends, it's invaluable.
Consider your use case. Running a server just for close friends? Whitelist is a no-brainer. Running a public server? Whitelisting defeats the purpose, so you need other defenses (better moderation, anti-cheat plugins, etc.).

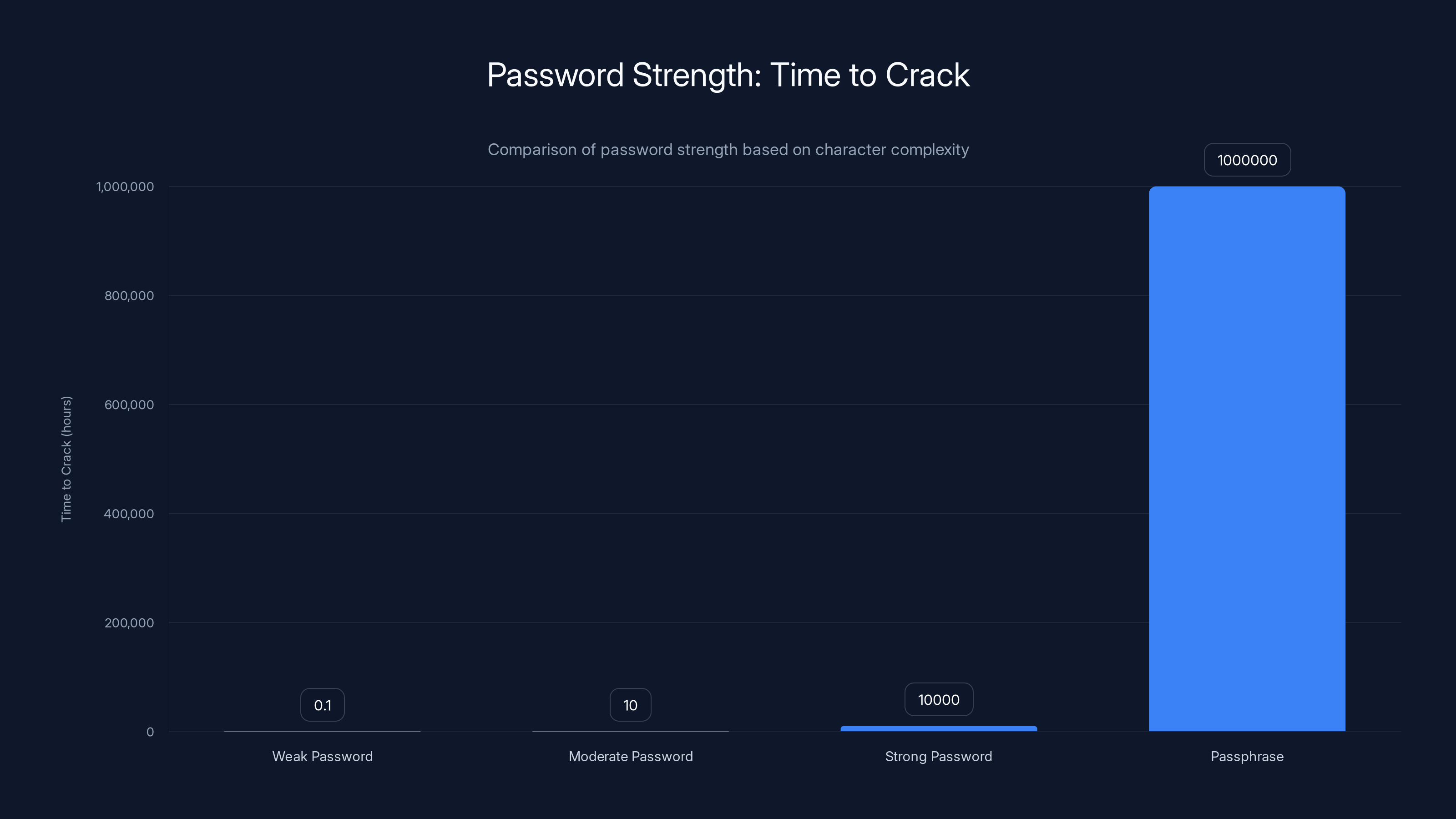
A weak password can be cracked in minutes, while a strong password or passphrase can take years, highlighting the importance of password complexity.
Plugin and Mod Security
Plugins extend your server's functionality. They're also your server's greatest security vulnerability.
Evaluating Plugin Trustworthiness
Not all plugins are created equal. Some are maintained by experienced developers. Some are abandoned and vulnerable. Some are intentionally malicious.
Before installing any plugin, research it thoroughly:
- Check the source: Is it hosted on an official repository like SpigotMC, PaperMC, or Bukkit? Or is it a random JAR file from Discord?
- Review the developer: How many plugins has this developer released? How long have they been active? Do they respond to bug reports?
- Check for recent updates: If a plugin hasn't been updated in years and your server is on the latest version, there's risk. Actively maintained plugins stay compatible.
- Read reviews and reports: Search the plugin name + "malware" or "exploit." Check plugin forums for reported issues.
- Examine the source code: If the plugin is open source, review the code. Look for suspicious permissions requests or data collection.
- Test on a staging server: Before installing a plugin on your main server, test it on a copy of your world. This catches crashes and compatibility issues without risking your players' data.
Permission Systems and Plugin Isolation
Even legitimate plugins can be exploited if they have excessive permissions. Modern Minecraft server software (Paper, Spigot) uses permission systems that let you control what each plugin can do.
Never give a plugin permissions it doesn't need. If a cosmetics plugin requests administrative access, that's suspicious. Cosmetics don't need admin permissions.
Use your server software's permission system to isolate plugins. A World Edit plugin shouldn't be able to delete player accounts. A chat plugin shouldn't be able to execute console commands.
This is advanced configuration, but it's worth learning if you're running a serious server.
Managing Dangerous Mods
Some mods are inherently risky:
- Remote Access mods: Mods that allow external control of your server
- Data collection mods: Mods that transmit player data to external servers
- Privilege escalation mods: Mods that bypass permission systems
- Unverified mods: Mods from unknown developers with no community presence
Stick with the best-known Minecraft mods from trusted developers. Essential mods like EssentialsX, WorldEdit, and LuckPerms are well-maintained and widely reviewed.
If you find a plugin that does exactly what you need but it's from an unknown developer, consider alternatives first. It's not worth the risk.

Backup and Disaster Recovery
Backups aren't just about security. They're about protecting against any data loss: corruption, accidents, server crashes, or actual attacks.
Automated Backup Strategies
Your server world data is irreplaceable. Players have spent hundreds of hours building. If you lose it, they're gone. Set up automated backups that run regularly.
For self-hosted servers, use a backup tool like Duplicati, Restic, or your OS's built-in backup system. Configure it to back up your server directory every 6-12 hours to an external drive or cloud storage.
For managed hosting, your host usually provides automated backups. Verify they're actually running. Ask: how often are backups created? How many versions are retained? Can you restore to a specific point in time?
Backup Testing
Here's what catches people: they set up backups, never test them, and when they need to restore, the backups don't work. The files were corrupted. The restore process failed. They never actually restored a backup.
Monthly, restore a backup to a test environment. Verify that the world loads, chunks are intact, and player data is uncorrupted. This only takes 15 minutes but saves you from catastrophic failure.
Off-Site Backup Storage
If your server is compromised and an attacker deletes your backups, you're worse off than before. Store backups off-site in cloud storage (AWS S3, Google Drive, OneDrive) that the attacker can't access from your server.
Encrypt your backups before uploading. Use a strong encryption key that's stored separately from the backups themselves.

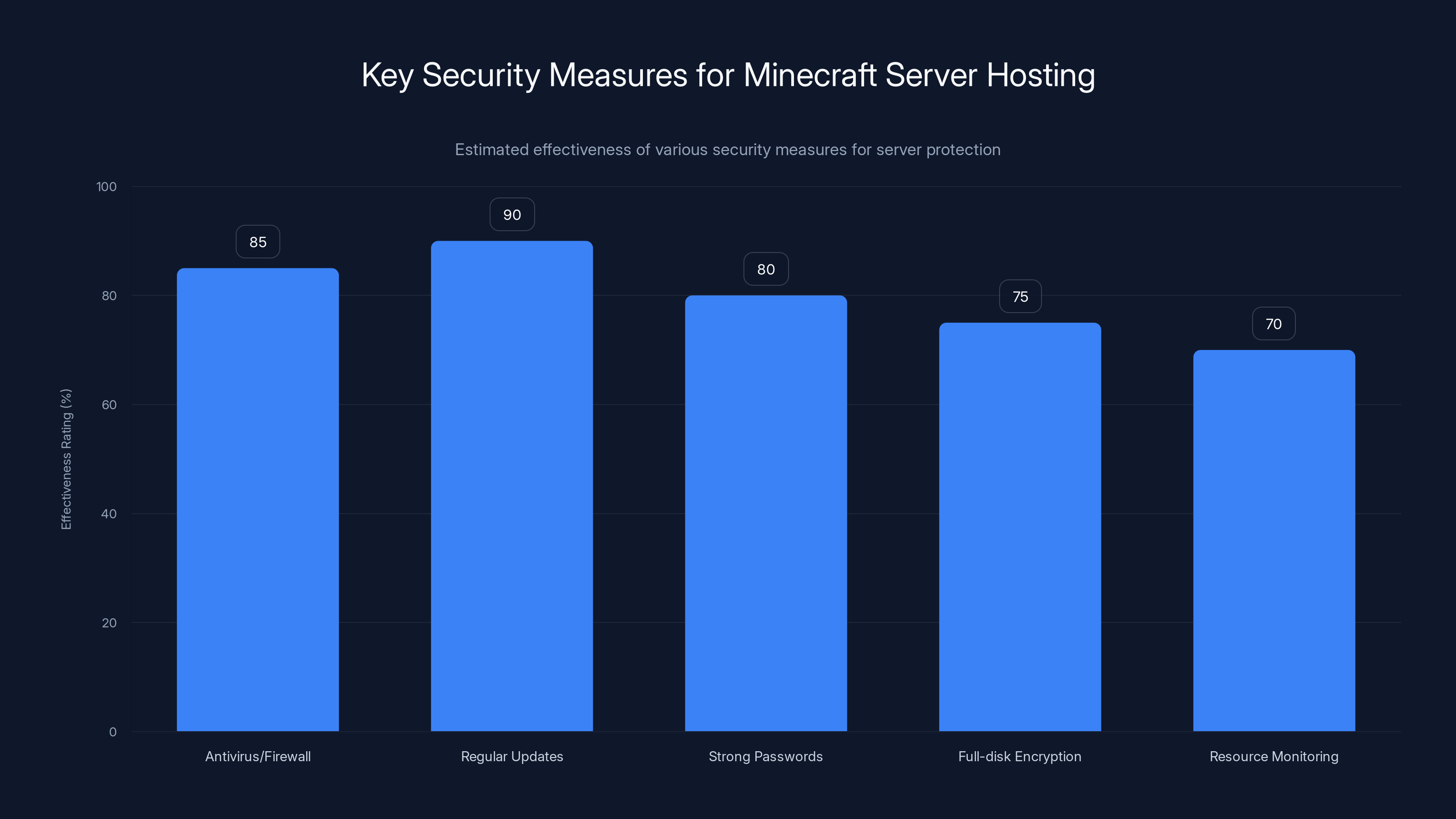
Estimated data shows that regular updates and antivirus/firewall usage are among the most effective security measures for protecting a Minecraft server. Full-disk encryption and resource monitoring also play significant roles.
Operating System and Hardware Security
Your Minecraft server is only as secure as the computer running it.
Secure Your Host Machine
If you're self-hosting, your Minecraft server runs on your PC. If someone compromises your PC, they compromise your server.
Harden your operating system:
- Enable Windows Defender or your preferred antivirus
- Enable Windows Firewall (assuming Windows OS)
- Run Windows Update regularly
- Disable unnecessary services that might introduce vulnerabilities
- Use strong passwords for your system accounts
- Enable Windows Defender for malware and virus protection
For Linux, the process is similar but more technical. Keep your system packages updated, disable unnecessary network services, use iptables or UFW for the firewall.
Physical Security
If your Minecraft server runs on a PC in your house, anyone with physical access to that PC can steal your hard drive, access your files, or modify the system.
If this concerns you (small risk for most people, but higher risk in shared living situations), consider:
- Full-disk encryption using BitLocker or LUKS
- A lock on your equipment
- Keeping your server in a secure location
- Using a VPS or dedicated hosting instead
Most casual server admins don't worry about physical security. But if your server contains sensitive player data or valuable builds, it's worth considering.
Resource Monitoring
Some attacks don't crash your server. They just consume all resources (CPU, RAM, disk space) until the server becomes unresponsive.
Monitor your server's resource usage. Set up alerts if CPU usage exceeds 80% consistently, or if disk space drops below 20% free.
Tools like Grafana with Prometheus can monitor your server and alert you to anomalies. For most small servers, the built-in Windows Task Manager or Linux top command is sufficient.

Handling Attacks and Incidents
Despite your best efforts, your server might still face an attack or security incident. Here's how to respond.
Detecting Attacks
Some attacks are obvious: your server is unresponsive, or you get complaints from players that they can't connect.
Others are subtle. Look for:
- Unauthorized world changes (terrain modified, builds deleted)
- New players appearing that you never whitelisted (if your whitelist is enabled)
- Unusual server logs with repetitive error messages
- Players reporting that their items disappeared or permissions changed
- Sudden increase in server lag despite normal player count
Check your server logs regularly. If you see repeated failed login attempts, that's a brute-force attack. If you see plugin errors, investigate.
Immediate Response
If you detect an active attack:
- Take the server offline immediately
- Don't make changes while the attack is ongoing
- Review your backup to understand what was changed
- Restore from your latest pre-attack backup
- Reset all admin passwords
- Review and update your security configuration
- Bring the server back online
Post-Incident Investigation
After containing the attack, investigate what happened:
- How did they get in? (Weak password? Unpatched plugin? Open RCON?)
- What damage did they cause? (Griefing? Data theft? Installed malicious plugins?)
- Were any other systems compromised?
- Did they exfiltrate any player data?
This investigation helps you prevent the same attack from happening again.
Communication with Players
If your server suffers a security incident, your players want to know. Be transparent:
- Explain what happened in simple terms
- Explain what you're doing to fix it
- Estimate when the server will be back online
- If any player data was compromised, tell them immediately
- Provide them with clear action steps (change their password, etc.)
Player trust is earned through transparency, not silence.

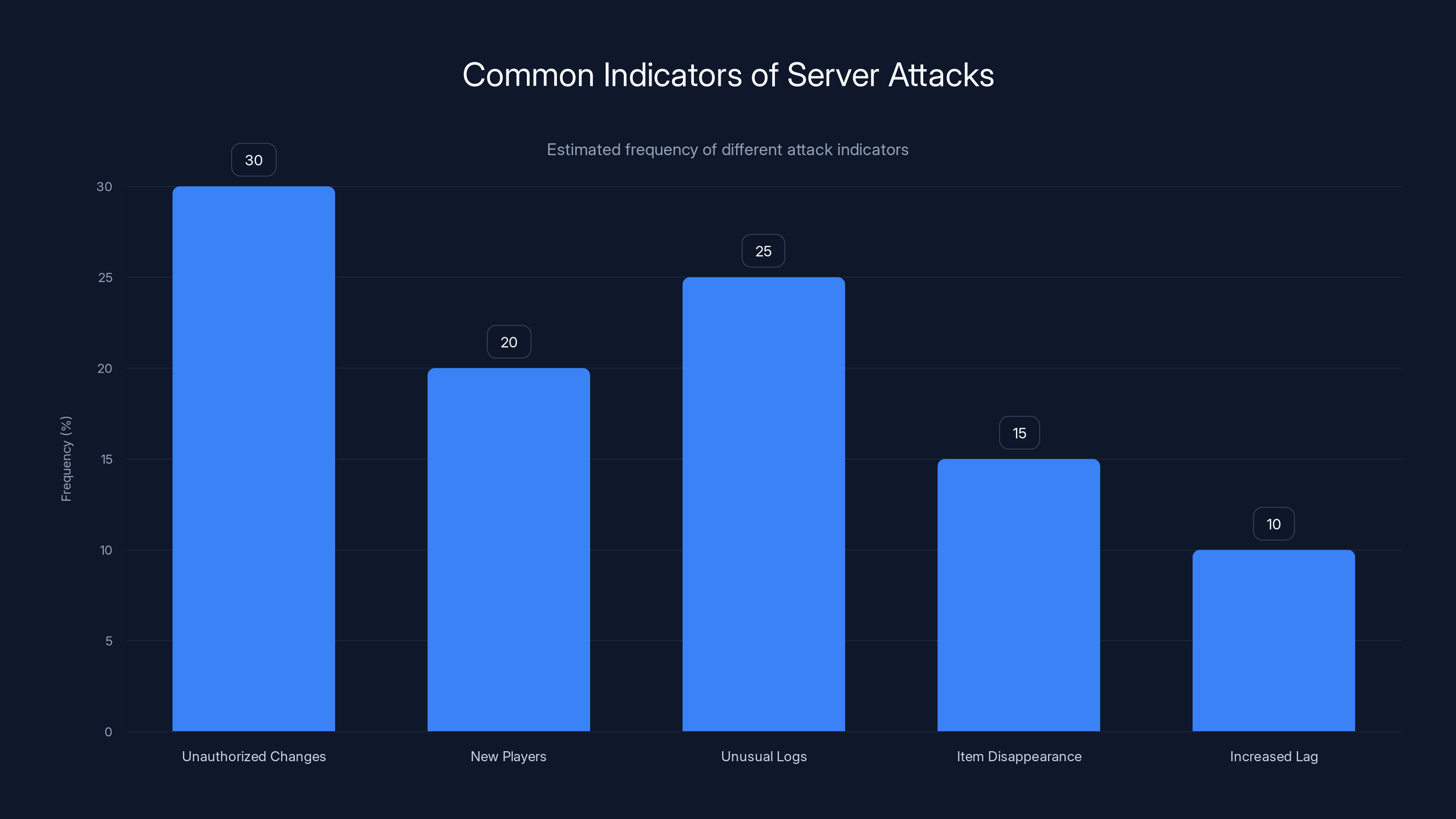
Unauthorized world changes and unusual server logs are the most common indicators of server attacks. Estimated data based on typical server incidents.
Choosing Between Self-Hosting and Managed Hosting
You've learned how to secure a self-hosted server. But is self-hosting the right choice for you?
Self-Hosting Pros and Cons
Pros:
- Maximum control over configuration
- No monthly fees
- No middleman between you and your data
- Good learning experience for sysadmin skills
Cons:
- You handle all security updates and patches
- You're responsible for DDoS protection (challenging on residential internet)
- Your home network is exposed to the internet
- You pay for electricity 24/7
- If something breaks, you fix it (no support team)
- Limited uptime guarantees compared to managed hosts
Self-hosting works great for small, trusted friend groups. It's not ideal if you want to run a large public server.
Managed Hosting Benefits
Managed Minecraft hosting providers (like Nitrado, Aternos, or Minehut) handle infrastructure, backups, security updates, and DDoS protection for you.
Benefits:
- Automatic security updates and patches
- Professional-grade DDoS protection
- Automated backups
- 24/7 server uptime
- Technical support
- Scalable resources
Tradeoffs:
- Monthly cost (typically $3-15 for small servers, scaling with size)
- Less control over some configurations
- You're trusting the host with your data
- Potential host restrictions on mods or plugins
The cost is actually lower than most people think. A small managed server hosting 5-10 players might cost $5/month. That's cheaper than the electricity to self-host. Larger servers scale up, but you're paying for actual infrastructure costs.
VPS Hosting as Middle Ground
A VPS (Virtual Private Server) is a middle ground between self-hosting and managed hosting. You get a virtual server hosted in a data center. You have root access and full control. The host provides infrastructure, DDoS protection, and backups.
VPS hosting costs more than managed Minecraft hosting ($5-15/month for a basic VPS) but gives you more flexibility. You're not limited to Minecraft software. You can run whatever you want.
VPS hosting requires more technical knowledge than managed hosting. You need to manage the operating system, firewall configuration, and backups. But you get more control.
For someone technical and wanting flexibility, VPS is excellent. For someone who just wants a Minecraft server, managed hosting is simpler.

Best Practices and Ongoing Security
Security isn't a one-time setup. It's an ongoing process.
Create a Security Checklist
Create a simple checklist of security tasks. Review it monthly:
- Check for server software updates
- Check for Java updates
- Check for OS updates
- Verify RCON is disabled
- Review admin access (confirm only trusted people have it)
- Test a backup restoration
- Review server logs for suspicious activity
- Check firewall configuration
- Review installed plugins for updates
- Verify 2FA is enabled on hosting accounts
Monthly reviews take 30 minutes but catch most problems.
Security Audits
Quarterly, do a deeper security audit:
- Scan your server with antivirus software
- Review all plugins and mods for outdated versions
- Check your passwords haven't been compromised (use haveibeenpwned.com)
- Verify backup restoration still works
- Review your firewall rules
- Check for any suspicious user accounts
Stay Informed
Follow Minecraft security news. Subscribe to security bulletins from your hosting provider. Join server administrator communities where people share security tips.
Security threats evolve. A vulnerability that didn't exist last year might be common today. Staying informed helps you adapt.

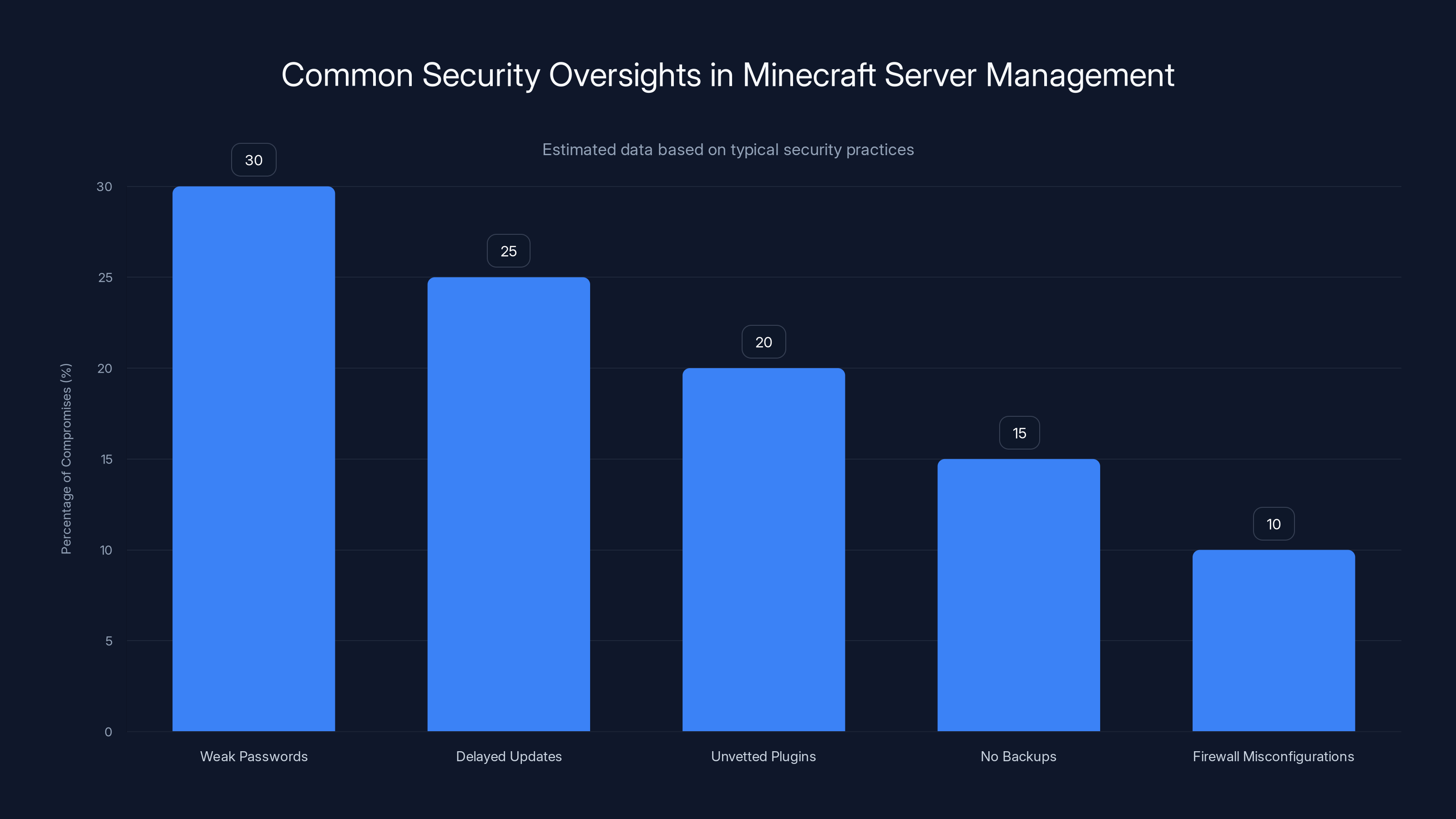
Estimated data suggests that weak passwords and delayed updates are the most common oversights leading to server compromises. Addressing these can significantly enhance server security.
Common Mistakes to Avoid
After discussing what to do, let's talk about what not to do.
Mistake 1: Skipping Updates
This is the most common mistake. "If it's working, don't touch it." But unpatched software is vulnerable software. Update immediately when new versions are released.
Mistake 2: Using Weak Passwords
Password managers exist for a reason. Use them. There's no excuse for weak passwords in 2025.
Mistake 3: Disabling Firewalls "For Performance"
Firewall overhead is negligible. Disabling it exposes your entire system. Keep it enabled.
Mistake 4: Trusting Unknown Plugins
That plugin that does exactly what you need? If it's from an unknown developer with no track record, don't install it. Use well-known alternatives instead.
Mistake 5: Not Testing Backups
Backups that have never been tested don't actually work. Test them monthly.
Mistake 6: Sharing Admin Passwords
Never. Use permission systems instead. If access is necessary, use role-based permissions.
Mistake 7: Ignoring Server Logs
Server logs tell you everything. Take 5 minutes daily to skim them. Watch for patterns that indicate problems.
Mistake 8: Running a Public Server Without Moderation
If you run a public server, you need moderators and clear rules. Without them, griefers take over and ruin the experience.

The Future of Minecraft Server Security
Minecraft server security is evolving. Here's what's changing:
Microsoft's Security Improvements
Microsoft owns Minecraft now. They're slowly improving server security infrastructure. Newer authentication mechanisms and permission systems are more robust than older versions.
Keep your server updated to benefit from these improvements. Old server versions have worse security.
Community-Driven Solutions
The Minecraft server community has created excellent security tools. Anti Cheat plugins, vulnerability scanners, and permission management systems have gotten more sophisticated.
Take advantage of these tools. They're usually free and maintained by passionate developers.
Rising Threat Complexity
As more servers come online, targeted attacks become more sophisticated. It's not just automated brute-force attempts anymore. Some attacks are specifically designed to exploit configuration mistakes.
This doesn't mean panic. It means you need to stay vigilant. Keep learning. Stay informed. Adapt your security as threats evolve.

Conclusion: Security as Ongoing Responsibility
Securing a Minecraft server isn't complicated, but it requires attention. It's not about implementing one perfect solution. It's about eliminating the easy wins: strong passwords, regular updates, careful plugin selection, proper backups, and basic firewall configuration.
Most server compromises happen because someone skipped a basic step. They used a weak password. They didn't update for six months. They installed a suspicious plugin without vetting it. They never tested their backups.
You don't need to be a security expert to run a safe server. You just need to be intentional about it.
Start with the basics: strong password, 2FA if available, firewall configured correctly, whitelist enabled if appropriate, and automated backups. That covers 95% of security concerns.
Then work on the rest. Update regularly. Monitor your server. Review your plugins. Test your backups.
If you find self-hosting overwhelming, consider managed hosting. It costs less than you think, handles security for you, and lets you focus on actually playing instead of managing infrastructure. There's no shame in delegating infrastructure to professionals.
Whichever path you choose, remember: your players are trusting you with their time, builds, and potentially personal information. Take that responsibility seriously. Implement reasonable security measures. Respond to incidents quickly and transparently. Your server will thrive.

FAQ
What is the biggest security risk for Minecraft servers?
Weaknesses in authentication are the largest security risk. Weak admin passwords and unpatched software account for the majority of server compromises. An attacker with admin access can do nearly anything: delete the world, install malicious plugins, steal player data, or crash the server permanently. This is why strong passwords, 2FA, and regular updates are your first priorities.
How often should I update my Minecraft server?
Update your Minecraft server immediately when new versions are released. Mojang patches security vulnerabilities regularly, and running old versions leaves known exploits open. At minimum, update monthly. For critical security patches, update within 24 hours. Also update your Java runtime regularly, as Java vulnerabilities can be exploited through Minecraft.
Is self-hosting a Minecraft server safe?
Self-hosting can be safe if you implement proper security practices: strong passwords, firewall configuration, regular updates, and careful plugin selection. However, it requires more attention than managed hosting. If your players' data is important to you, or if you're running a large public server, managed hosting is safer because professionals handle the infrastructure security.
What should I do if my server gets hacked?
If you detect a security breach, immediately take your server offline to prevent further damage. Restore from your most recent pre-attack backup. Reset all admin passwords. Review how the attacker gained access (usually weak password, unpatched plugin, or malicious mod) and fix that vulnerability. Update your security configuration and bring the server back online. Finally, communicate transparently with your players about what happened and what measures you're taking to prevent it.
Do I need to enable RCON on my server?
No. RCON (Remote Console) is disabled by default and should stay disabled. Enabling it creates a severe security risk. If an attacker gets your RCON password, they can execute arbitrary commands and take full control of your server. If you need remote access to your server, use SSH instead of RCON. SSH is far more secure and gives you better control.
How much does Minecraft server hosting cost?
Managed Minecraft hosting typically costs
Can I run a Minecraft server 24/7 on my home computer?
Technically yes, but it has downsides. Your electricity bill will increase by $10-30 per month depending on your hardware. Your home network is exposed to the internet. If your internet connection drops, your server goes offline. You're responsible for all security updates and maintenance. Most people find managed hosting more convenient despite the monthly cost.
What plugins are safe to install?
Stick with plugins from established developers on official repositories like SpigotMC, PaperMC, or Bukkit. Check when they were last updated. Look for community reviews and reports of problems. Read the source code if it's available on GitHub. Never install plugins from unknown sources or random Discord servers. Test new plugins on a backup of your world first, not on your live server.
Should I whitelist my server?
If you're running a private server for friends, yes. Whitelisting prevents random players from joining, discovering vulnerabilities, or griefing. If you're running a public server that welcomes new players, whitelisting isn't practical. Instead, use moderation, clear rules, and anti-grief plugins.
How do I backup my Minecraft server?
Set up automated backups that run every 6-12 hours. For self-hosted servers, use backup software like Duplicati or Restic to back up your server directory to an external drive and cloud storage. For managed hosting, verify your host provides automated backups and understand their backup retention policy. Critically, test your backup restoration process monthly. Untested backups are worthless if they don't actually restore correctly.
What's the difference between Java Edition and Bedrock servers?
Java Edition is the original Minecraft version for PC. It's open to mods and customization. Bedrock Edition is the newer cross-platform version (Windows 10/11, mobile, console). Java Edition servers are more customizable but require more security attention. Bedrock servers are more locked down by default. For maximum security with customization, Java Edition with careful plugin vetting is standard. For simplicity and less customization, Bedrock can be easier to secure.
How This Relates to Your Server's Success
Running a secure Minecraft server isn't just about preventing attacks. It's about building trust with your players. When players know their world is safe, their items won't disappear, and their work won't be griefed, they invest more time and energy.
A secure server with strong moderation and clear rules becomes a community. Players want to be there. They recruit their friends. The server grows organically.
An insecure server fails for different reasons. Maybe someone gets hacked and resets the world. Maybe malicious plugins corrupt player data. Maybe griefers destroy everything because moderation is absent. Players leave. The server dies.
Your choice of whether to self-host or use managed hosting, your commitment to updates and backups, your careful selection of plugins—these aren't just technical decisions. They determine whether your server thrives or fails.
Choose wisely. Stay vigilant. Your players will thank you.
Key Takeaways
- Strong admin passwords and 2FA are your first line of defense against unauthorized access
- Regular updates eliminate vulnerabilities; unpatched servers are easily compromised
- Firewall configuration and port management prevent most external attacks
- Plugin security requires vetting from trusted sources; malicious mods compromise entire servers
- Automated backups with monthly restoration testing prevent catastrophic data loss
- Managed hosting often costs less than self-hosting when factoring in electricity and administration time
- RCON disabled and whitelisting restrict access to known, trusted players
- Incident response procedures and player communication build trust when breaches occur
Related Articles
- Best Password Managers: Why Keeper Leads in 2025 [Complete Guide]
- NordVPN No-Logs Audit 2025: What Independent Verification Really Means
- Viral AI Prompts: The Next Major Security Threat [2025]
- Malwarebytes and ChatGPT: The AI Scam Detection Game-Changer [2025]
- Notepad++ Supply Chain Attack: Chinese Hackers Hijack Updates [2025]
- Canada Computers Data Breach 2025: Timeline, Impact, Protection [2025]
![Minecraft Server Security Guide: Keep Your Server Safe [2025]](https://tryrunable.com/blog/minecraft-server-security-guide-keep-your-server-safe-2025/image-1-1770138538607.jpg)



