Authentication Is Evolving Faster Than You'd Expect
MFA felt revolutionary ten years ago. Two factors instead of one? Game changer. But here's what nobody talks about openly: attackers stopped caring about your second factor around 2022. They're not trying to crack your password anymore. They're not brute-forcing your authenticator app. Instead, they're calling your IT support desk, impersonating you, and asking for a password reset. The human element isn't a vulnerability they exploit—it's the primary attack surface now.
I watched this play out with three different organizations last year. Same pattern every time. The attacker doesn't need to be technical. They just need to be convincing. A social engineering call to your help desk beats your two-factor authentication every single time because MFA doesn't protect the recovery process. This shift represents the defining challenge of 2026. Your organization probably has solid MFA adoption—about 70% of enterprises do now. But that statistic masks something critical: 30% of users remain completely unprotected. More importantly, the attacks that matter aren't hitting your MFA at all. They're hitting everything around it.
The good news? The solution isn't some futuristic technology. Organizations are already moving toward phishing-resistant authentication methods like FIDO2 keys, Web Authn, and hardware authenticators. These aren't experimental anymore. They're mainstream. But the transition requires understanding what you're moving away from and why.
TL; DR
- MFA adoption hit 70% in enterprises, but social engineering attacks bypass it entirely by targeting password recovery processes
- Phishing-resistant methods grew 63% year-over-year, with SMS usage dropping from 17.5% to 15.3% as organizations recognize the vulnerability
- 84% of security breaches involve phishing attacks, making credential-stealing the #1 attack vector in enterprise environments
- Passwordless authentication is now achievable at scale, with 7% of enterprise users signing in without passwords as of January 2025
- Implementation requires strategic planning, but the cost of delay is higher than the cost of migration across legacy systems
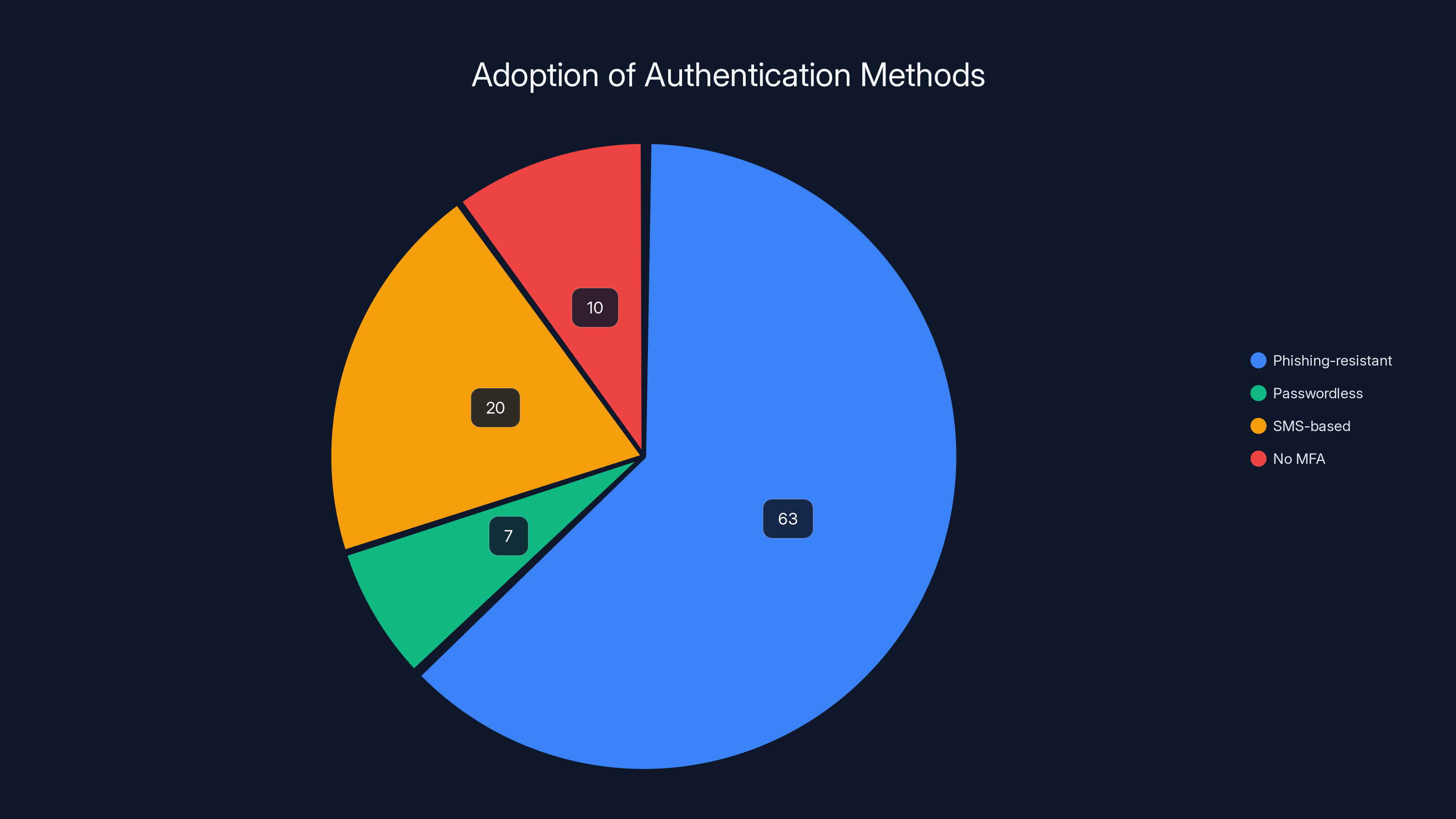
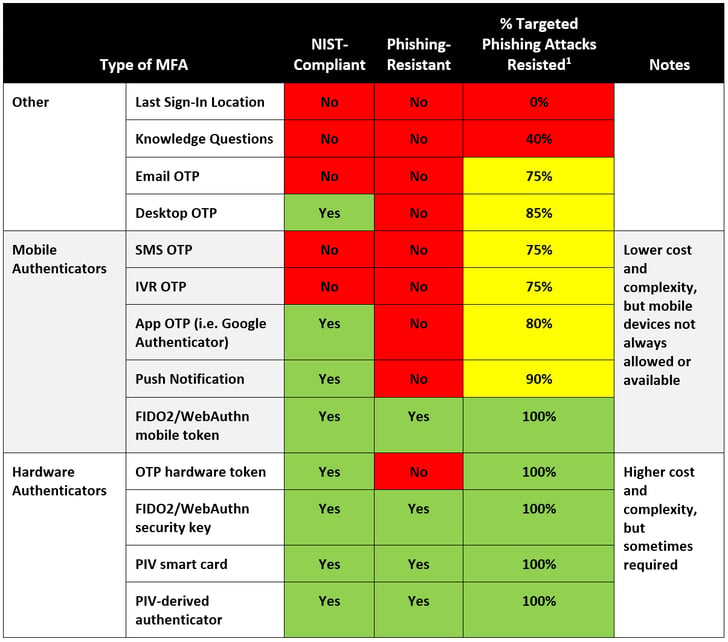
Phishing-resistant authentication methods have seen a 63% adoption rate, highlighting a shift towards more secure authentication strategies. Estimated data.
Why MFA Succeeded—And Why It Can't Protect You Now
Multi-factor authentication fundamentally changed enterprise security. Before MFA became standard, attackers could steal a password and walk straight into your systems. That era is gone. When you require something you know (password) plus something you have (phone) or something you are (biometric), the attack gets harder.
The statistics back this up. Organizations with MFA implemented see measurably fewer successful breaches from credential theft. Password spraying attacks largely stopped working. Brute force attempts became economically unviable. MFA did exactly what it was designed to do: make stolen credentials significantly less valuable.
But here's the problem nobody wants to admit: attackers adapted. They didn't try harder to break MFA. They found paths around it. Think about how password recovery actually works at most organizations. You forget your password. You call support. They verify your identity using information they can pull from a system (your employee ID, start date, manager's name). Once verified, they reset your password. You get back in. This process bypasses MFA entirely because MFA wasn't protecting the entry point—only the normal login path.
Attackers realized this. They studied how support teams verify identity. They learned what information an employee might not resist sharing if asked in the right way by someone claiming authority. A sophisticated social engineer can convince a support representative they're the CTO needing emergency access. The support team resets credentials. No MFA stops that.
Last year, multiple organizations reported this exact pattern. It wasn't isolated incidents. It was coordinated, repeatable, scalable. Attackers had identified the human touchpoint in the recovery process and weaponized it. There's another vulnerability MFA doesn't address: supply chain attacks. If an attacker compromises the system delivering your MFA codes (your SMS provider, for example), they get the code and the password. SMS in particular has fundamental cryptographic weaknesses—it uses unencrypted, unauthenticated channels. Attackers can intercept SMS-based codes through SIM swapping or by compromising telecom infrastructure.
MFA also doesn't protect against malware-based attacks. If your device is compromised, sophisticated malware can observe every input you make, including your MFA code. It can also intercept authentication traffic directly. The protection MFA provides assumes the endpoint you're using is clean. Once that assumption breaks, MFA's value diminishes.
Organizations aren't abandoning MFA—they're layering it with something stronger. But recognizing MFA's limitations is the first step toward building security that actually matches 2026's threat landscape.
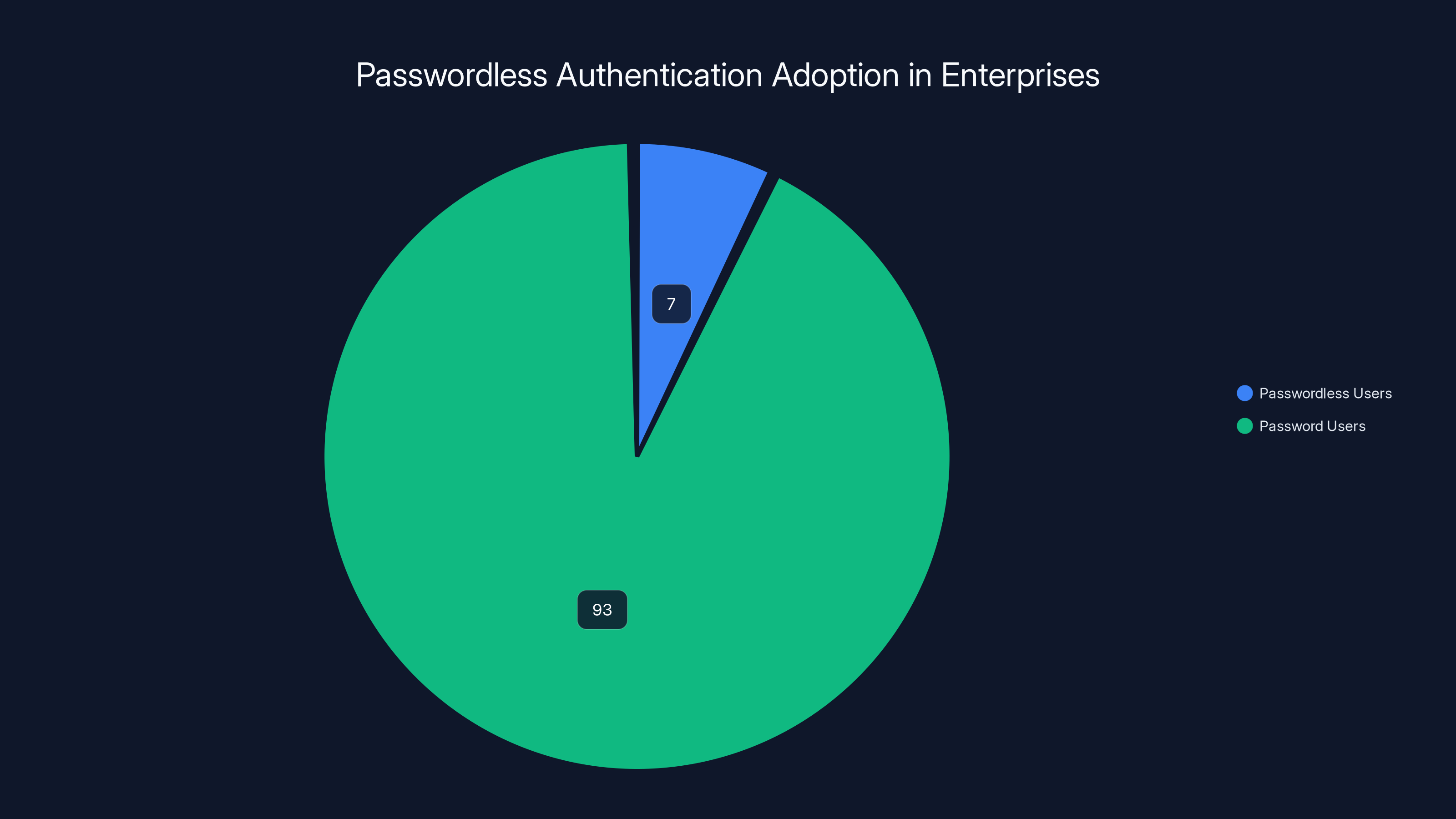
As of January 2025, 7% of enterprise users are using passwordless authentication, indicating a growing trend towards eliminating passwords in complex environments. Estimated data.
The Phishing Attacks That Are Actually Happening
Phishing gets mentioned so often it's lost impact. It sounds like something that happens to people who don't know better. But the data tells a different story. The UK government reports that 84% of security breaches trace back to phishing attacks. That's not a small percentage. That's the dominant attack category. In 2024 alone, organizations detected over 7.5 million phishing attacks. But that number represents only attacks that made it past detection. Many more succeed silently.
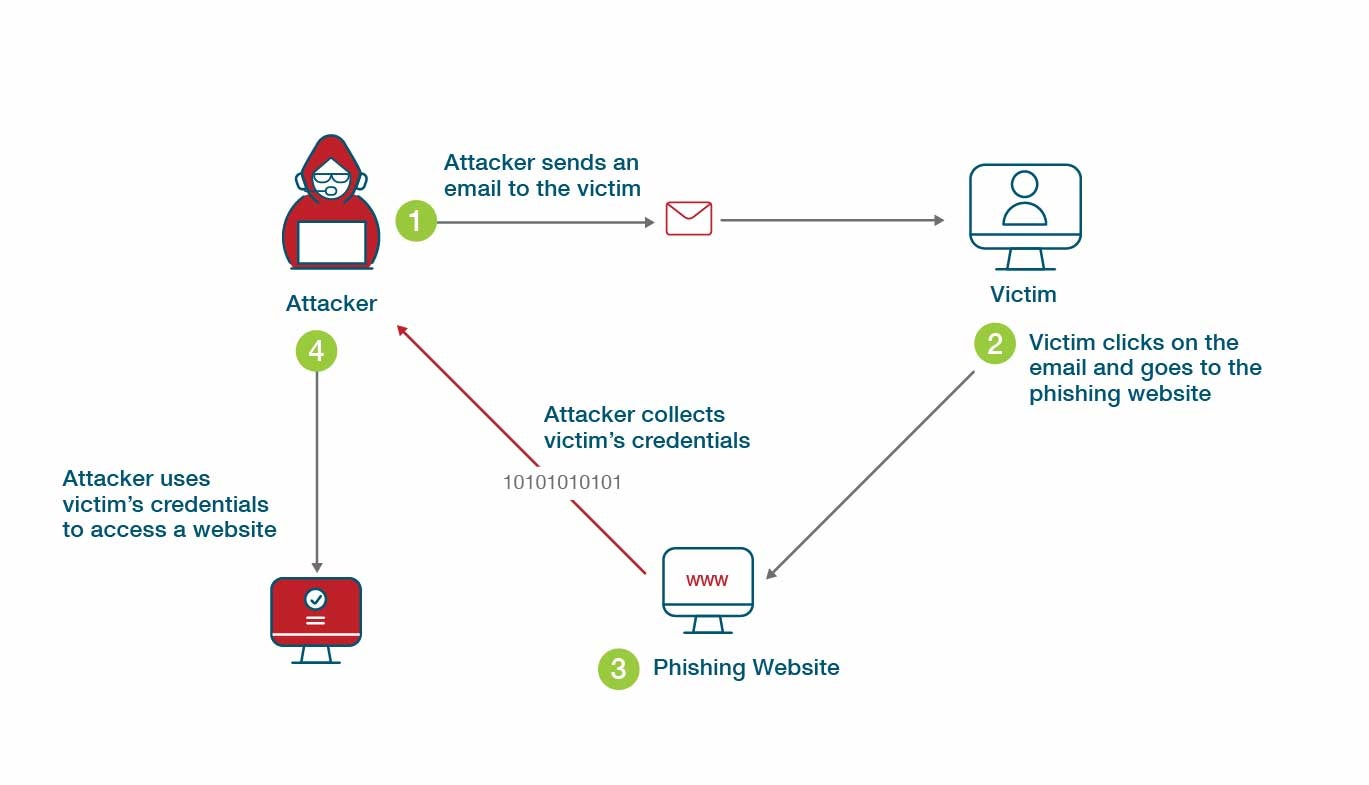
Phishing has evolved dramatically. It's not the obvious "Nigerian prince" emails anymore. Modern phishing campaigns are personalized, targeted, and technically sophisticated. I've seen phishing emails that perfectly mimic internal communications from your actual IT department. The sender address looks correct because it's spoofed. The content includes specific details about your role and recent projects. The request seems reasonable: update your authentication method, verify your account for compliance, or confirm your identity for a security refresh.
When you click, you don't get a fake login page that looks "almost" like the real one. You get redirected to something that's pixel-perfect. Your credentials get captured. The attacker now has your username and password. At this point, your MFA becomes their problem to solve. But solving it is easier than most people realize. If they have your credentials, they can try logging in repeatedly from different IP addresses until they either trigger password reset functionality or convince a support representative there's an account compromise (which there now is).
Some phishing campaigns use more sophisticated tactics. They send you to a page that captures your username and password, then immediately redirects you to the real authentication page with legitimate credentials. You log in successfully and never know your credentials were stolen. The attacker waits days or weeks before using them, letting the credential theft fall out of your short-term security monitoring window.
Other campaigns use context-aware phishing. They study your organization, identify your executives, and send emails specifically crafted to those individuals. A CFO gets an urgent message from the CEO about a deal closing. A security director gets contacted about a potential vulnerability. The phishing success rate on these targeted campaigns runs 30-40%.
The fundamental problem is this: phishing targets the human, not the system. Your password security, your MFA, your encryption—none of it matters if you voluntarily give your credentials to someone pretending to be someone else. That's not a technical failure. It's a social engineering win. Organizations spending millions on MFA while remaining vulnerable to phishing are optimizing the wrong threat. They're defending the front door while the attacker has already walked through the side door using a key they got by calling and asking nicely.
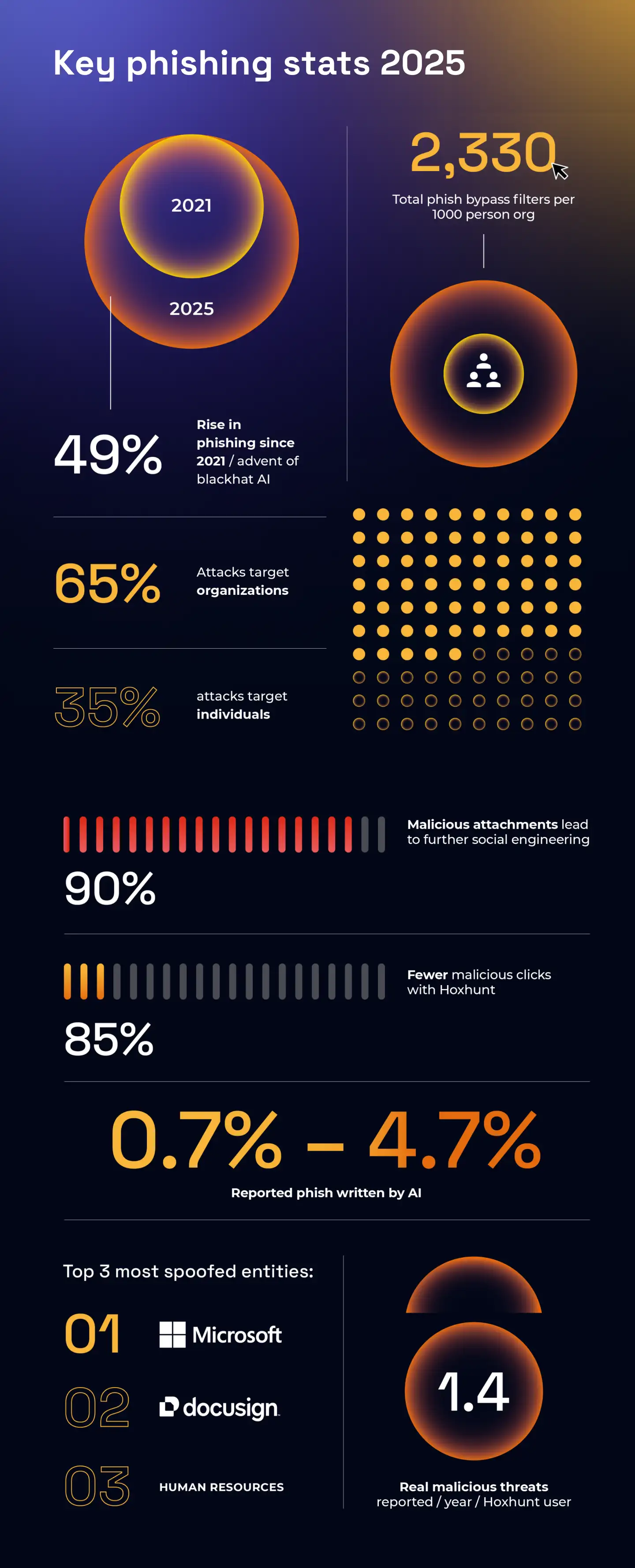
What Makes Phishing-Resistant Authentication Actually Different
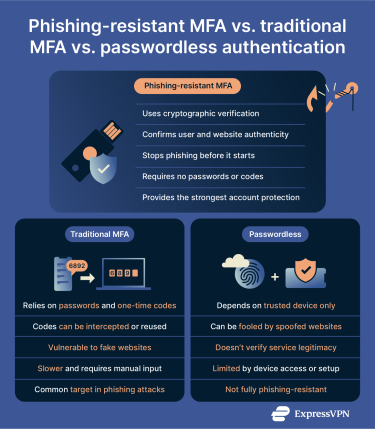
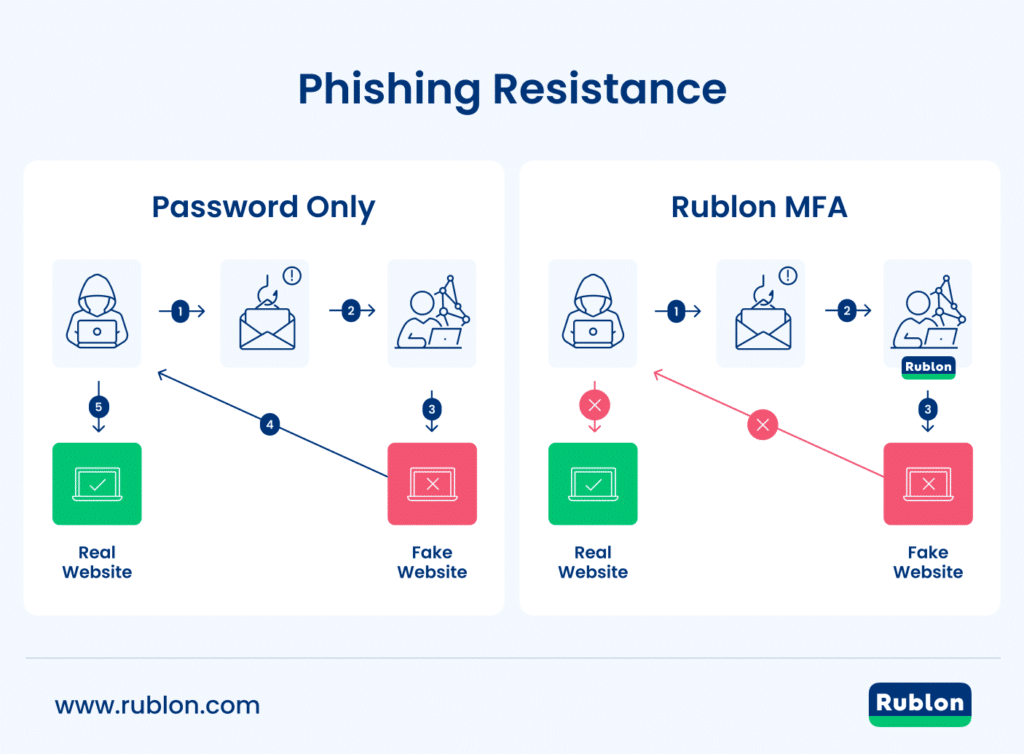
Phishing-resistant authentication works on a fundamentally different principle than everything that came before. With passwords and codes, you're giving something you know to a system you trust it belongs to. But here's the trust problem: you have to verify that trust visually or through social signals. An email looks legitimate. A phone number seems right. A website displays correctly. All of these can be spoofed.
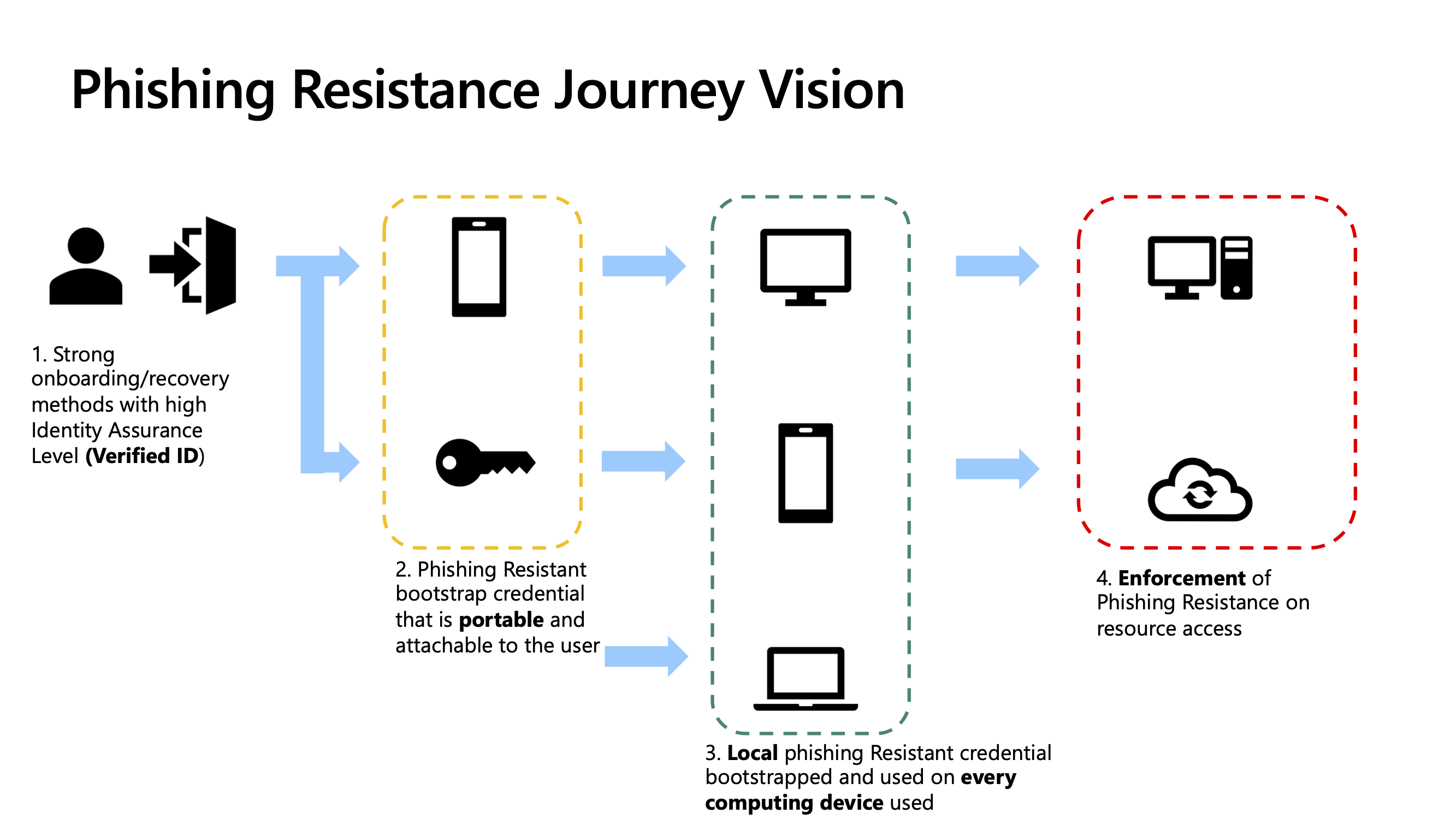
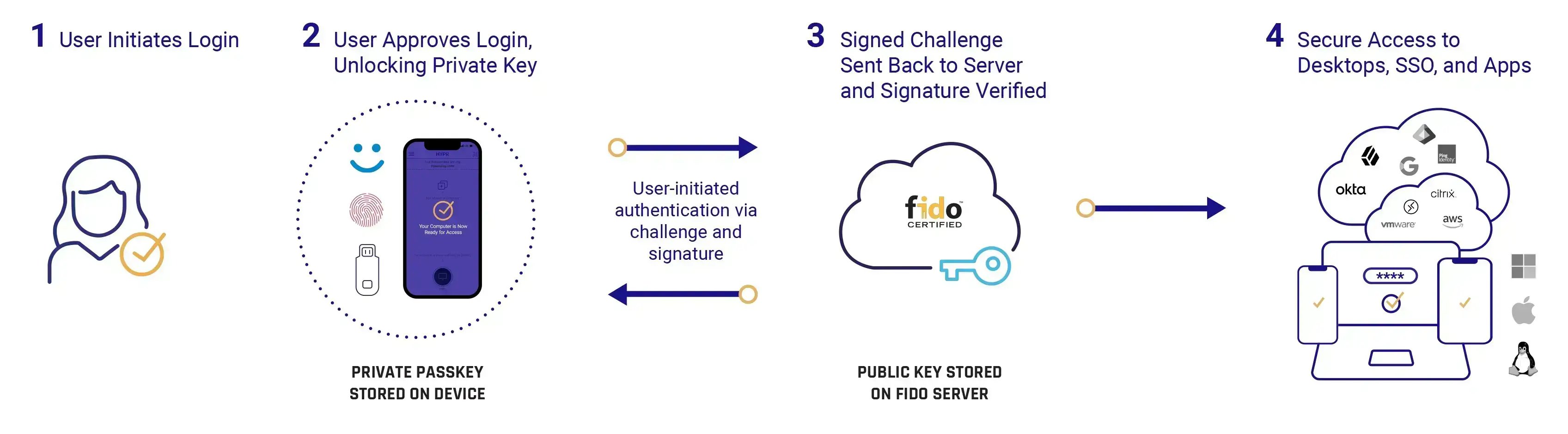
Phishing-resistant authenticators work differently. Instead of sending a secret, they prove something cryptographically. When you use FIDO2 with a hardware key or platform authenticator, here's what actually happens: Your device generates a unique cryptographic keypair. The private key never leaves your device—it stays locked in secure hardware or encrypted storage. The public key gets registered with the service.
When you authenticate, your device doesn't send that private key. It receives a cryptographic challenge from the service. Your device signs that challenge using the private key. The service verifies the signature using the public key. If verification succeeds, you're authenticated.
The crucial part: if an attacker tricks you into authenticating to their fake website, their website won't be able to verify the signature. Your device creates a signature that's mathematically valid only for the legitimate service's domain. An attacker can't reuse that signature anywhere else. Even if they steal it, it's worthless.
This is what cryptographic binding means. Your authenticator binds the authentication response to the specific service you're accessing. A phishing site can't intercept it, replay it, or reuse it because the math doesn't work.
Hardware keys make this even more explicit. A FIDO2 key is a small USB device that generates and stores cryptographic keys. It never sends your private key to anything. It only signs challenges. The key itself is immune to malware because it's a separate physical device with no internet connection.
Biometric authenticators on modern phones work similarly. Your fingerprint or face unlock never gets transmitted as data. Your phone's secure enclave stores the biometric template and performs the matching locally. When authentication happens, your biometric unlocks the signing process, but the biometric data itself stays isolated on your device.
The implications are significant. You can be socially engineered into entering your password. You can be tricked into using your second factor. But you cannot be tricked into signing a challenge for a phishing site. Your device verifies it's talking to the legitimate service first. If it's not, the entire operation fails. Organizations tracking adoption metrics found that phishing-resistant authenticator usage grew 63% in a single year. That's not gradual migration. That's rapid realization that the security model actually works.
Meanwhile, SMS-based authentication—vulnerable to SIM swapping, interception, and carrier compromise—fell from 17.5% to 15.3% of authentication methods. Organizations are literally voting against less secure methods by adopting more secure ones.

Phishing-resistant authentication significantly reduces credential theft and enhances security, while also improving user experience and reducing support costs. (Estimated data)
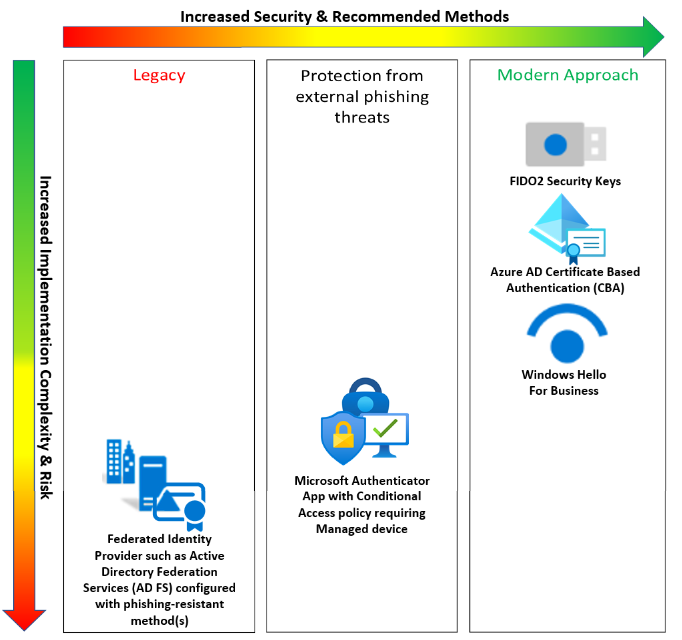
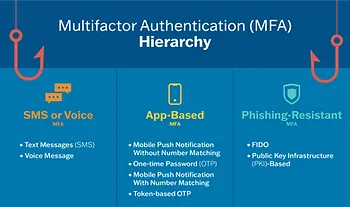
FIDO2, Web Authn, and the New Authentication Standards
FIDO2 is the protocol. Web Authn is the web standard. Together, they represent the most significant advance in authentication security in two decades. FIDO stands for Fast Identity Online. The FIDO Alliance—a consortium including Microsoft, Google, Apple, and major security companies—developed it to replace passwords with cryptographically stronger alternatives.
FIDO2 defines how authentication should work. It specifies that your private key never gets shared. It specifies that services must verify you're communicating with the legitimate service, not an attacker's fake. It specifies that authentication should be resistant to phishing, credential theft, and replay attacks.
Web Authn is the web implementation of FIDO2. It's a Java Script API that web browsers support. When a website uses Web Authn, it can request authentication without ever handling your credentials. Your browser talks to your authenticator (a hardware key, your phone, your laptop's built-in biometric), and the authenticator handles the cryptographic operations.
Here's what using Web Authn actually feels like: You go to your bank's website. You click "Sign In." The system asks for your username. You provide it. Then it asks you to authenticate. You either insert your hardware key and press the button, or you use your phone's face recognition. That's it. No codes. No second factor that arrives separately. Just a single, fast authentication step that's simultaneously more secure and simpler.
Microsoft's Fast Pass represents their implementation of passwordless authentication at scale. Google's Passkey implementation on Android and i OS brings authentication tied to your biometric. Apple's platform uses their Secure Enclave to store cryptographic keys. These aren't competing standards—they're implementations of the same underlying FIDO2 protocol, all compatible with Web Authn.
Yubikeys are hardware authenticators that implement FIDO2. You plug them in or tap them to your phone. Teleport is identity infrastructure that builds on FIDO2. Okta's implementation integrates FIDO2 into their identity platform. These are real, shipping products that organizations deploy today.
The advantage of hardware keys is explicit: they're a separate device. Malware on your computer doesn't compromise them. A phishing email doesn't matter because your key won't authenticate to a phishing site. Someone stealing your computer doesn't get your keys—they're in your pocket.
The advantage of platform authenticators (using your phone or laptop's biometric) is convenience. You don't need to carry another device. Your existing phone or laptop becomes your authenticator. When you sign in, you use your fingerprint, face, or PIN. These are generally equivalent in security to hardware keys because they use secure hardware (the device's processor) and never expose private keys.
Platform authenticators are what moved enterprise adoption to scale. When every employee already has a phone with Face ID or Touch ID, deploying passwordless authentication becomes feasible. You don't need to buy and distribute hardware keys to thousands of users.
The real shift in thinking is this: authentication should be something only you can do, not something someone could trick you into revealing. FIDO2 and Web Authn deliver that principle in practice.

The Practical Reality of Implementation at Scale
Deploying phishing-resistant authentication across a large organization is genuinely hard. Not impossible. Not even particularly expensive at scale. But hard in the ways that matter for real businesses.
First, you're dealing with legacy systems. Your company probably has applications built five years ago that don't support FIDO2. Your SSO platform might support it, but your internal tools might not. Your enterprise software vendors—the ones you pay significant licensing fees to—might still be months away from adding support.
Second, you have organizational complexity. Authentication changes affect everyone. If you require FIDO2 for all users immediately, you break access for people with older devices or unsupported configurations. You need a migration path that lets people authenticate either way while you transition systems.
Third, hardware costs add up when you're talking about millions of users. If you decide to distribute hardware keys, you're buying physical devices, managing inventory, handling lost or broken keys, and supporting users who can't find their authenticator. Platform authenticators avoid this cost—the device already exists—but limit you to organizations where most users have modern phones or laptops.
Fourth, you're dealing with change management. Users are used to passwords and codes. Moving to biometric or hardware-based authentication requires explaining why, showing that it works, and supporting them through the transition. Some users will resist. Some will find it strange. Some will have legitimate technical concerns.
Fifth, you have to maintain backward compatibility during the transition. Contractors, vendors, partners, and edge-case users might not be able to use your new authentication method. You need fallback options that provide security while being accessible to everyone who needs legitimate access.
Here's what actually works: a staged rollout with executive sponsorship. Start with your most security-critical users—your IT and security teams. Let them pioneer the technology and work out rough edges before you expand. Simultaneously, prepare your support team for questions. Create documentation. Test with real employees from different technical skill levels.
Phase two targets sensitive groups—finance, legal, executive leadership—where phishing attacks have historically been most successful. These users typically have more control over their environment and are easier to migrate.
Phase three expands to everyone else, using a combination of push (requirements) and pull (making the new method so obviously better that people want to switch). By this point, your systems support it, your users understand it, and your support team has handled the problems.
Organizations following this path report successful migrations in 6-12 months for mid-sized companies, 12-18 months for large enterprises. The timeline isn't about the technology. It's about organizational change management.
The financial math is straightforward: deploying phishing-resistant authentication costs money upfront through software licensing, hardware (if needed), and migration effort. But the cost per breach from phishing attacks far exceeds the implementation cost. An enterprise paying millions in ransomware, incident response, regulatory fines, and customer notification after a breach wishes they'd spent hundreds of thousands on authentication security years earlier.
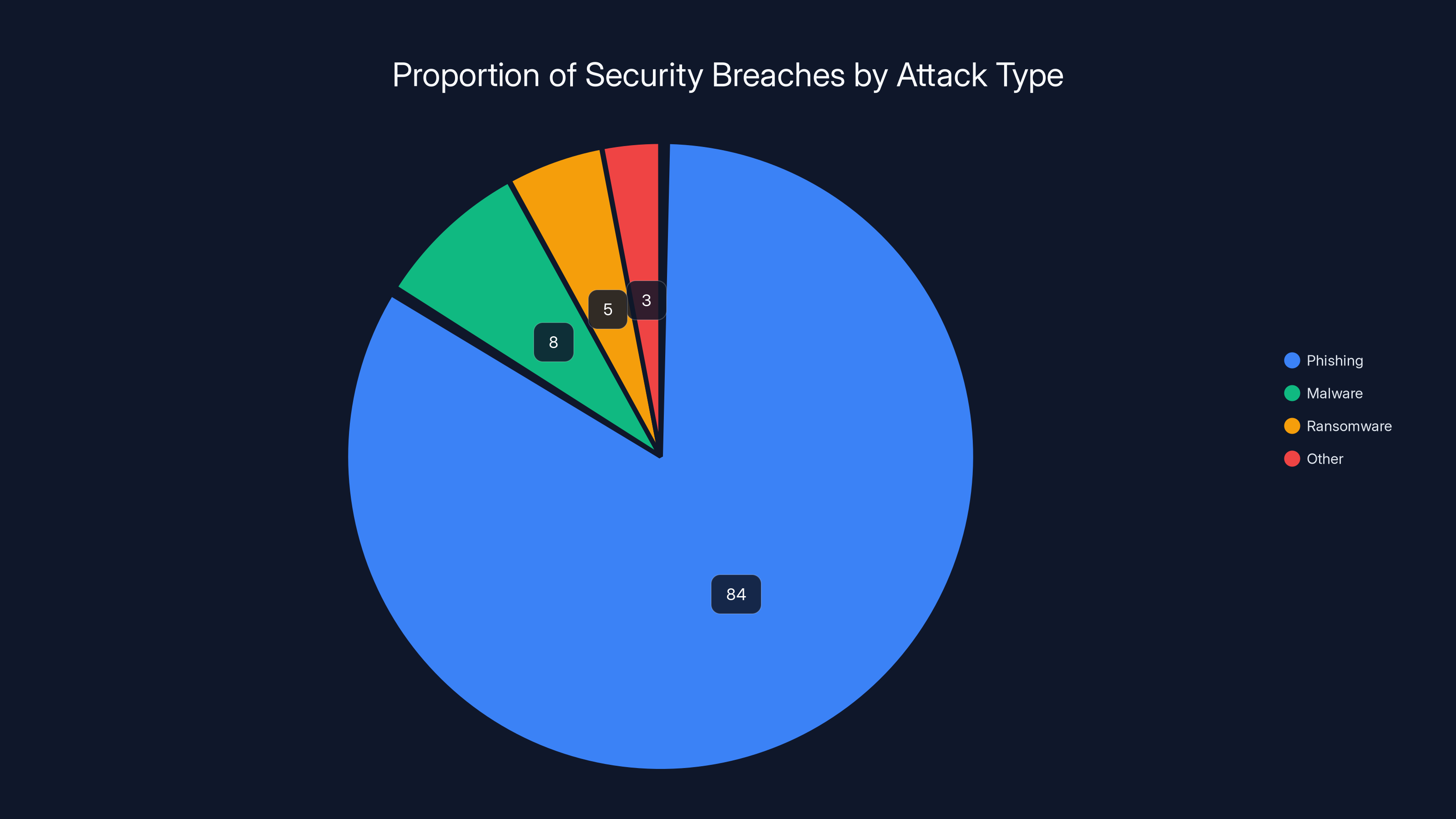
Phishing attacks account for 84% of security breaches, making it the dominant attack type. Estimated data for other categories.
How Biometric Authentication Fits Into Your Security Strategy
Biometrics often get discussed as if they're a new thing. They're not. But they're finally moving into enterprise security in practical ways. Biometric authentication works by confirming that you are who you claim to be. Your fingerprint is unique to you. Your face is unique to you. These characteristics are difficult to forge and impossible to change.
The security question with biometrics isn't whether they work—fingerprint and facial recognition technology is genuinely accurate now. The question is whether biometric data itself can be stolen or misused.
Here's the important distinction: modern biometric implementations on phones and laptops store biometric data locally. Your fingerprint data doesn't travel across the network. It doesn't get sent to a server. It stays encrypted on your device, in a secure hardware area called a Secure Enclave (Apple), Trusted Execution Environment (Android), or Hardware Security Module.
When you authenticate with your biometric, your device verifies your fingerprint locally, then uses that to unlock the private key stored in the secure area. The private key signs the authentication challenge. The signed challenge gets sent to the service. Your biometric data never leaves your device.
This design is fundamentally more secure than passwords because even if the service gets compromised, your biometric data isn't exposed. The compromise reveals the signed authentication responses, not the biometric itself.
Enterprise adoption of biometric authentication faces some real questions. What happens when someone loses their phone? What if an employee gets injured and can't use their fingerprint? What if someone is uncomfortable with facial recognition?
These aren't imaginary problems. They're operational considerations. The solution is layering. Biometric authenticates to unlock a hardware key or derive a cryptographic key. If you lose your phone, your hardware key still works. If biometric fails, you have a PIN fallback. If someone's uncomfortable, they use hardware keys instead.
The practical advantage of biometric authentication is dramatic friction reduction. Signing in with your fingerprint is faster and more convenient than SMS codes, authenticator apps, or hardware keys. Users actually prefer it. When users prefer the secure method, adoption increases naturally.
Organizations moving to biometric-backed authentication are seeing measurable productivity increases. Fewer login failures. Fewer password reset requests. Fewer "I forgot my MFA app" support tickets. The security improvement comes with a usability improvement, not at its expense.

Passwordless Authentication at Enterprise Scale (It's Already Happening)
Passwordless sounds theoretical. It sounds like something companies will do in five years. The data suggests otherwise. As of January 2025, 7% of enterprise users are signing in without passwords at all. That's not a pilot program. That's real production usage across complex enterprise environments with thousands of employees and legacy systems.
Seven percent doesn't sound significant until you do the math. For a 10,000-person company, that's 700 employees operating entirely without passwords. They're not using passwords as a fallback. They're not using passwords for certain applications. They're completely passwordless.
How is that possible? Because enterprises are implementing passwordless authentication in stages. Your email might be passwordless while your legacy database access still requires a password. Your Saa S applications might be entirely passwordless while your on-premises systems use passwords. The transition happens application by application, system by system, until one day you realize you haven't changed your password in months.
Implementing passwordless authentication across an organization requires infrastructure. You need an identity provider that supports passwordless authentication. Microsoft Entra ID (formerly Azure AD), Okta, Google Workspace, and others have added passwordless capabilities to their platforms.
You need your applications to support passwordless authentication. Cloud-based Saa S applications added support relatively quickly because their vendors could push updates rapidly. On-premises applications require more work. Legacy systems might require API changes or additional middleware to support passwordless authentication.
You need your users to have authenticators. This is where platform authenticators become critical. When passwordless authentication works with your phone's biometric or your laptop's camera, adoption becomes feasible. Users don't need to carry additional devices. They use technology they already have.
The mechanics are straightforward. For a Saa S application, your identity provider handles authentication. When you try to access the application, the identity provider prompts you for authentication. You authenticate using your biometric or hardware key. The identity provider issues you a token. You access the application.
For on-premises applications, you might use a protocol like FIDO2 directly, or your identity provider might handle the authentication and issue credentials for the on-premises system.
The practical shift is profound. Passwords are stateless by design—they work on any device, any network, anywhere. Phishing-resistant authenticators are device-centric. Your authentication is tied to your specific device. This changes security dynamics.
If someone steals your password, they can use it from anywhere. If someone steals access to your phone, they still can't authenticate unless they also have your biometric. The security model is fundamentally more robust.
The user experience is simultaneously simpler and more secure. You don't memorize passwords. You don't reset forgotten passwords. You authenticate using something you already have and something you already do (using your biometric).
Organizations successfully implementing passwordless authentication at scale report measurable improvements: fewer security incidents, lower IT support costs, faster user onboarding, and simpler offboarding. When you don't need to manage passwords, entire classes of IT operations become simpler.
The remaining 93% of enterprise users using passwords—and the 7% using passwords for legacy systems—represents the transition period. But the direction is clear. The question isn't whether passwordless authentication will become standard. It's how quickly organizations will get there and what they'll do during the migration.
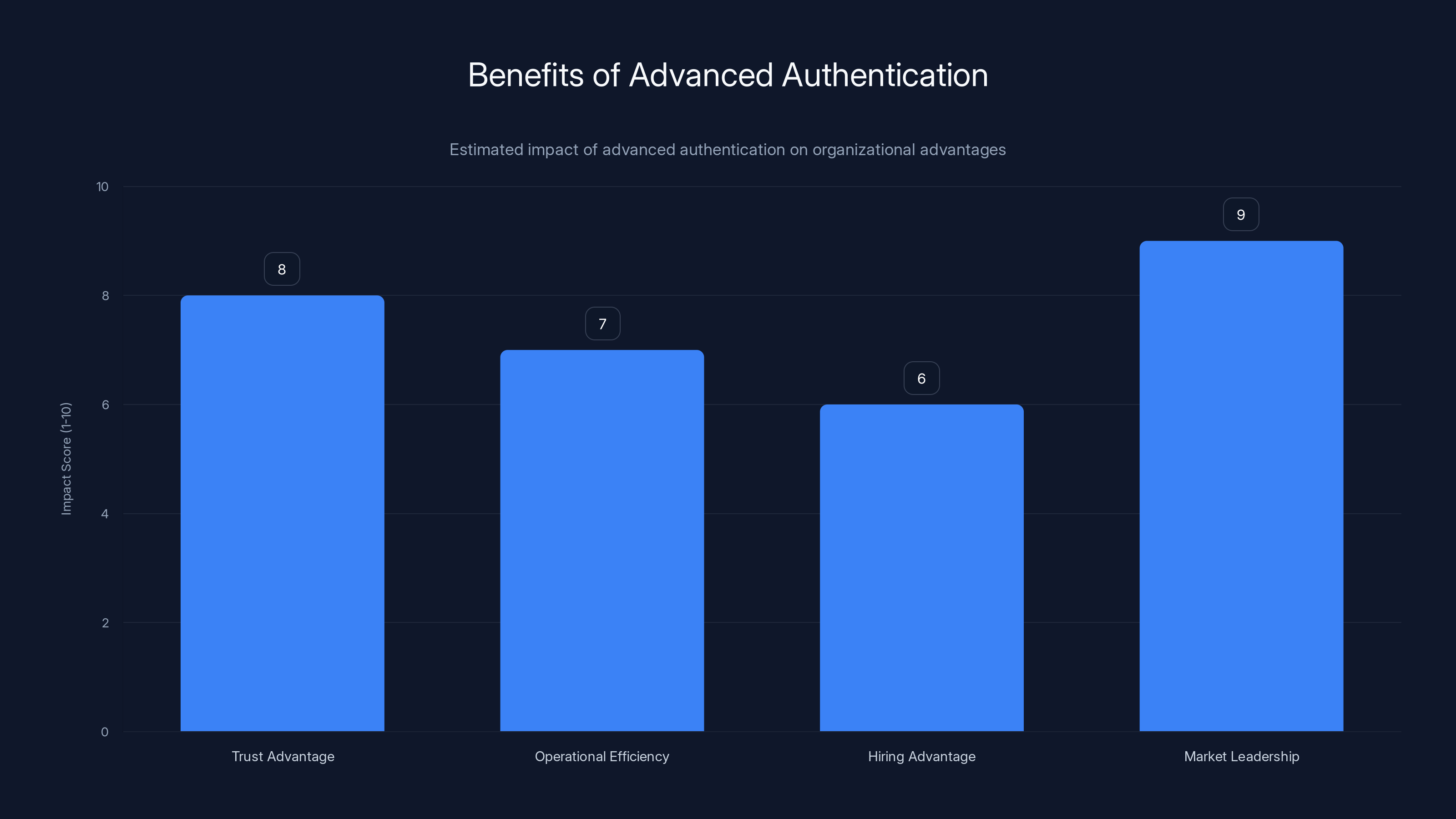
Advanced authentication provides significant competitive advantages, with market leadership and trust being the most impacted areas. (Estimated data)
Beyond Authentication: The Broader Zero Trust Architecture
Phishing-resistant authentication is powerful, but it's not a complete security solution by itself. It's part of something larger: zero trust security architecture.
Zero trust starts from a different assumption than traditional security. Traditional security assumes that if you're inside the corporate network, you're trusted. Zero trust assumes that trust must be earned—continuously—regardless of location or network.
Authentication is the first step in zero trust: verifying that you are who you claim to be. But it's just the first step.
After authentication comes authorization: determining what you should be allowed to do. Just because you've proven your identity doesn't mean you should have access to everything. Authorization limits access based on your role, the context of your access request, and your current risk posture.
Context includes things like: Are you accessing from your company-issued device or a personal device? Are you on the corporate network or accessing from home? Is your device up-to-date with security patches? Have you been authenticating normally, or is there unusual activity on your account?
Risk assessment combines all these factors. A user authenticating from their company laptop on the corporate network on a Tuesday afternoon at 2 PM has very different risk than a user authenticating from a new location on a weekend using a device that's never accessed the company network before.
Zero trust systems adjust access requirements based on risk. Low-risk situations require simpler authentication. High-risk situations require stronger authentication, additional verification, or might be denied entirely.
This isn't just paranoia. Organizations tracking access patterns have identified that risk-based access control catches attempts that other security systems miss. An attacker stealing legitimate credentials might be able to pass your authentication check, but they'll fail your zero trust evaluation because they're accessing from an unfamiliar location or device.
Phishing-resistant authentication fits into zero trust by making the authentication step harder to compromise. Combined with context-based access control, device security requirements, and behavioral analysis, it creates a security model that's genuinely difficult for attackers to navigate.
Implementing full zero trust is complex. It requires changes to your network architecture, application architecture, and security operations. But organizations implementing zero trust frameworks report significant security improvements. The combination of strong authentication, context-aware access control, and continuous verification reduces successful breach attempts substantially.
For most organizations in 2026, the path forward is staged: strengthen authentication first with phishing-resistant methods, then add context-based access control, then implement network segmentation and device security as part of a broader zero trust strategy.
The Role of Hardware Security Modules and Secure Enclaves
When you're implementing phishing-resistant authentication, you need somewhere secure to store the private keys that make everything work.
Hardware Security Modules—HSMs—are specialized devices designed for exactly this purpose. They're essentially secure computers that do nothing but cryptography. You load them with private keys. They perform cryptographic operations when requested. The private keys never leave the module.
For enterprise deployments managing authentication for thousands or millions of users, HSMs provide a secure root. Your identity provider stores all the public keys in normal systems. The corresponding private keys live in the HSM. When authentication happens, the HSM performs the cryptographic signing. Even if someone compromises your identity provider system, they don't get the private keys.
HSMs are expensive to buy and complex to operate. They require specialized knowledge. But for organizations where security is critical, the cost is justified. Financial institutions, government agencies, and large enterprises managing sensitive data often rely on HSMs.
Secure Enclaves are the modern evolution. These are specialized hardware areas built into processors—especially in phones and modern laptops. They're essentially tiny HSMs built into your device.
When you use biometric authentication on your phone, your biometric template is stored in the Secure Enclave. Your private keys for FIDO2 authentication are stored there. The Secure Enclave is isolated from the main processor. Malware running on your phone can't access it. If someone physically disassembles your phone, accessing the Secure Enclave requires specialized hardware.
Secure Enclaves are why biometric authentication on modern devices is genuinely secure. Your biometric never leaves the Secure Enclave. Your private keys never leave the Secure Enclave. Compromising the rest of your phone doesn't compromise your authentication.
The distribution of cryptographic trust through HSMs and Secure Enclaves creates a security model where even significant compromises don't necessarily compromise authentication. An attacker getting your password doesn't get your keys. An attacker compromising your identity provider doesn't get your private keys. An attacker getting your phone doesn't get your biometric data.
This is what defense in depth means in practice: multiple layers of security such that compromising one layer doesn't compromise the others.

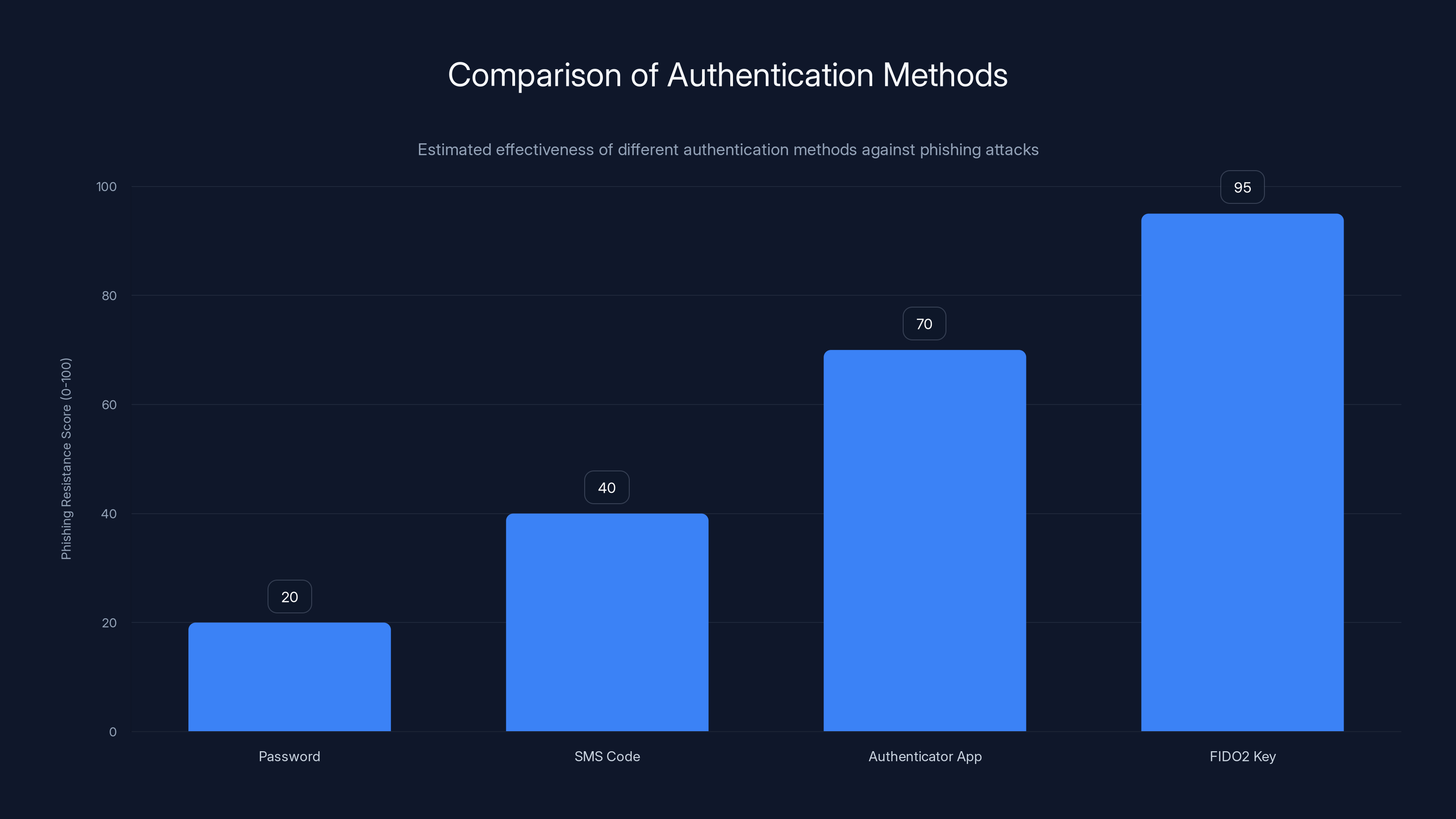
FIDO2 keys provide the highest resistance to phishing attacks due to cryptographic binding, significantly outperforming traditional methods like passwords and SMS codes. (Estimated data)
Overcoming Skepticism: User Experience With Phishing-Resistant Methods
When organizations first announce passwordless authentication or hardware key requirements, they typically face skepticism. Users worry it will be complicated. IT leaders worry about support costs. Executives worry about adoption.
The actual data contradicts these concerns. Phishing-resistant methods are both more secure and more usable than traditional authentication. Users aren't fumbling with SMS codes that never arrive. They're not trying to remember which MFA app they're using. They're using biometrics or hardware keys that work intuitively.
Authentication with your fingerprint takes seconds. Hardware keys require a single button press. These operations are faster than typing a password and waiting for an SMS code.
The operational impact is measurable. Organizations tracking help desk metrics report significant reductions in password reset requests when they implement passwordless authentication. Fewer reset requests means lower IT support costs.
The user adoption is actually faster than organizations expect. When users experience authentication that's both faster and more secure, adoption accelerates. You don't need to force people to switch. They actively want to.
There are edge cases. Users with disabilities might have difficulty using biometric authentication. Some older devices don't support the necessary hardware. Some contractors or external partners might not have compatible authenticators.
The solution is layering with fallbacks. Biometric is the primary method, but a PIN works if biometric fails. A hardware key works if the device doesn't support biometric. A browser extension might work if the hardware doesn't support direct FIDO2 integration.
Organizations successfully implementing these systems create authentication hierarchies: primary method (biometric), secondary method (hardware key), tertiary method (backup codes), and support-assisted recovery for edge cases. Most users use the primary method. Some use the secondary. Very few need tertiary. Almost none need support assistance.
The user experience improves because you're removing friction (no more typing passwords or waiting for codes) while increasing security (phishing can't compromise biometric-backed authentication). Simultaneously improving security and usability is rare. That's why adoption accelerates.
Real-World Challenges: Supply Chain, Third Parties, and Legacy Systems
Theory is clean. Reality is messy. Your organization probably doesn't control the entire authentication stack. You use Saa S applications from vendors. You integrate with partners. You have legacy systems that won't be updated for years.
This creates real implementation challenges that don't show up in case studies or marketing materials.
Third-party Saa S applications vary in their authentication support. Some have native FIDO2 support. Some support it through your identity provider but not directly. Some don't support it at all. You might require FIDO2 across your organization, but your accounting software—which processes millions of dollars annually—only supports passwords and SMS MFA.
Partner integrations get complicated. You need to authenticate your users to partner systems. But your partners might not support your phishing-resistant authentication method. They might require you to send credentials through APIs. They might only support basic password authentication.
Legacy systems are the biggest challenge. Systems built ten years ago often have authentication baked in at the kernel level. Updating them to support modern authentication standards requires deep infrastructure work or expensive migrations.
Real organizations solve this through layering and mapping. Your identity provider acts as a intermediary. Users authenticate to your identity provider using FIDO2. Your identity provider handles the authentication and issues credentials to systems that only support passwords. The user never enters a password. The identity provider generates passwords behind the scenes.
This isn't perfect—you're still generating passwords that could theoretically be intercepted—but it's significantly more secure than users handling passwords directly. More importantly, it lets you implement phishing-resistant authentication in the user experience while maintaining backward compatibility with legacy systems.
Supply chain risks in authentication are real. If your identity provider gets compromised, that affects everything. If the Saa S applications you rely on get compromised, that affects your security. If your hardware key manufacturer ships devices with vulnerabilities, that affects everyone using those keys.
These aren't hypothetical risks. They've happened. The solution is defense in depth: don't rely on any single component. Combine strong authentication with network segmentation, access control, monitoring, and incident response capabilities. No authentication system is unbreakable. But combining strong authentication with multiple layers of defense makes breakthrough attacks significantly harder.
The Path Forward: Starting Your Migration in 2026
If your organization hasn't started moving toward phishing-resistant authentication, 2026 is the year to begin.
The first step is assessment. Audit your current authentication methods. How many users are using passwords only? How many are using SMS-based MFA? How many are using authenticator apps? How many are using hardware keys or platform authenticators?
Identify your high-risk users. Who has access to critical systems? Who authenticates from multiple locations? Who interacts with sensitive data? These are your priority users for phishing-resistant authentication.
Assess your infrastructure. Does your identity provider support FIDO2 or Web Authn? Does your primary business-critical application support it? What about your Saa S applications? Your on-premises systems? This assessment reveals the gaps in your infrastructure.
The second step is pilot. Pick a small group—ideally your security team—and deploy phishing-resistant authentication. Use hardware keys or platform authenticators. Let them work through the rough edges. Have them document problems. Use their feedback to improve your rollout plan.
The third step is infrastructure preparation. Update your identity provider if needed. Configure your critical applications to support FIDO2 or Web Authn. Set up hardware key distribution processes if you're using hardware keys. Create backup and recovery processes for edge cases.
The fourth step is phased rollout. Start with security and IT teams. Then move to high-risk users. Then expand to everyone else. Each phase should last several weeks, not days. You want time to work through support issues and build confidence.
The fifth step is legacy system handling. Decide how you'll maintain backward compatibility with systems that don't support phishing-resistant authentication. Will you use identity provider-mediated credential management? Will you maintain separate passwords for legacy systems? Will you plan system replacements?
The sixth step is ongoing security. Phishing-resistant authentication is a significant security improvement, but it's not the endpoint. Continue monitoring. Continue updating systems. Continue training users. Continue assessing risks.
Throughout all of this, you're fighting inertia. Change is hard. Passwords are familiar. Users will resist. Some leaders will question whether it's worth the effort.
The answer is in the data. 84% of breaches involve phishing. That's your answer. You can spend effort on phishing-resistant authentication now, or you can handle a breach later. The only variable is whether you prepare proactively or reactively.

The Competitive Advantage of Advanced Authentication
Secure authentication isn't just about defense. It's about competitive advantage. Organizations with strong authentication security gain trust advantages. Customers trust you more. Partners trust you more. Investors look more favorably at your security practices.
You also gain operational advantages. Fewer breaches means fewer incident response costs. Fewer password resets means lower IT costs. Faster onboarding and offboarding processes mean better employee experience and lower administrative overhead.
You gain hiring advantages. Security-conscious professionals want to work for organizations that take security seriously. Demonstrating that you're implementing modern, phishing-resistant authentication methods makes you more attractive to top talent.
Organizations that move first on authentication security get to define the standards. They learn what works and what doesn't. They build the processes and infrastructure. By the time it becomes industry standard, they're years ahead.
The organizations that wait until it's mandatory—either because of regulations or because breaches force their hand—pay the price of compressed timelines. They make rushed decisions. They implement systems quickly without proper planning. They face user adoption resistance because they're mandating change without adequate preparation.
Moving to phishing-resistant authentication in 2026 positions you ahead of the market. It's not too early—the technology is proven and available. It's not too late—you still have time for deliberate planning. It's exactly the right moment.
Regulatory Trends and Compliance Requirements
Authentication standards are increasingly becoming regulatory requirements. The National Institute of Standards and Technology (NIST) has updated its authentication guidance. NIST Special Publication 800-63 now recommends phishing-resistant authentication for sensitive systems. NIST no longer recommends SMS-based authentication due to its vulnerabilities.
These aren't mandatory requirements in most jurisdictions, but they're influential. When NIST recommends something, regulatory bodies eventually follow. Frameworks like SOC 2 increasingly ask about authentication methods. Frameworks like ISO 27001 ask about multi-factor authentication and phishing resistance.
For financial services, SEC regulations increasingly require strong authentication. For healthcare, HIPAA security rules emphasize authentication controls. For government contractors, CMMC requirements include authentication standards.
Organizations in regulated industries are moving to phishing-resistant authentication partly because it's the right thing to do for security, and partly because regulations are moving in that direction.
Even if your industry doesn't have explicit authentication requirements yet, building phishing-resistant authentication into your systems makes you future-proof. When regulations do change, you're already compliant.
The regulatory momentum is clear. Passwords are becoming less acceptable as a standalone authentication method. SMS-based MFA is becoming questionable. Phishing-resistant methods are becoming expected for sensitive data and critical systems.
FAQ
What is phishing-resistant authentication?
Phishing-resistant authentication uses cryptographic methods where your authenticator device or biometric verifies it's communicating with the legitimate service before completing authentication. This means you cannot be tricked into providing credentials to an attacker because the cryptographic binding to the legitimate service prevents authentication from working on phishing sites. Methods like FIDO2, Web Authn, and hardware keys implement this by using public-key cryptography where only the legitimate service can verify authentication responses.
How does FIDO2 authentication work?
FIDO2 uses asymmetric cryptography where your device or authenticator generates a keypair: a private key that never leaves your device and a public key registered with the service. When you authenticate, the service sends a cryptographic challenge. Your device signs this challenge with the private key and sends the signature back. The service verifies the signature using your public key. Because the signature is mathematically bound to both the challenge and the service domain, an attacker cannot reuse or forge it, making phishing ineffective.
What are the main benefits of phishing-resistant authentication?
Phishing-resistant authentication eliminates credential theft as an attack vector, making social engineering and phishing attacks significantly less effective. It also improves user experience because signing in with biometrics or hardware keys is faster than entering passwords and waiting for SMS codes. Organizations report measurable reductions in help desk support costs, fewer password reset requests, and faster user onboarding. Additionally, these methods are inherently more secure against breaches since your authenticator ensures authentication only works with the legitimate service.
Do I need to buy hardware keys for all employees?
Not necessarily. Platform authenticators built into modern phones (Face ID, Touch ID) and laptops provide equivalent security without requiring separate devices. Hardware keys offer advantages for high-security environments or users accessing systems from shared devices, but for most organizations, platform authenticators on employee-owned devices provide sufficient security with greater convenience. Your implementation strategy can use platform authenticators as the primary method with hardware keys as optional secondary authenticators.
How can I implement phishing-resistant authentication if my legacy systems don't support it?
Your identity provider can act as an intermediary. Users authenticate to your identity provider using FIDO2 or Web Authn. Your identity provider then handles authentication to legacy systems that only support passwords or traditional MFA. This approach gives users a phishing-resistant authentication experience while maintaining backward compatibility with legacy infrastructure. Planning system replacements for legacy applications should be part of your long-term migration strategy.
What happens if someone loses their hardware key or can't use their biometric?
Most implementations use layered authentication where biometric is the primary method but a PIN or password works as a backup. Hardware keys serve as secondary authenticators if the primary device doesn't support biometric. For edge cases, backup codes generated during setup allow account recovery. Supporting users through these scenarios requires documented processes and help desk training, but these are manageable with proper planning.
Is passwordless authentication really achievable at enterprise scale?
Yes, and it's already happening. As of January 2025, 7% of enterprise users authenticate entirely without passwords. Most organizations implement passwordless authentication gradually through staged rollouts rather than immediate migration. This phased approach allows time for infrastructure updates, user training, and support team preparation. The timeline varies by organization size and system complexity, typically ranging from 6 to 18 months for complete migration.
How does phishing-resistant authentication fit into zero trust security?
Phishing-resistant authentication is the foundational authentication layer in zero trust architecture. While zero trust goes beyond authentication to include context-aware access control, device security requirements, and behavioral analysis, phishing-resistant authentication makes the authentication step itself resistant to compromise. Combining strong authentication with zero trust principles creates defense in depth where attackers must overcome multiple security layers even if they steal credentials.
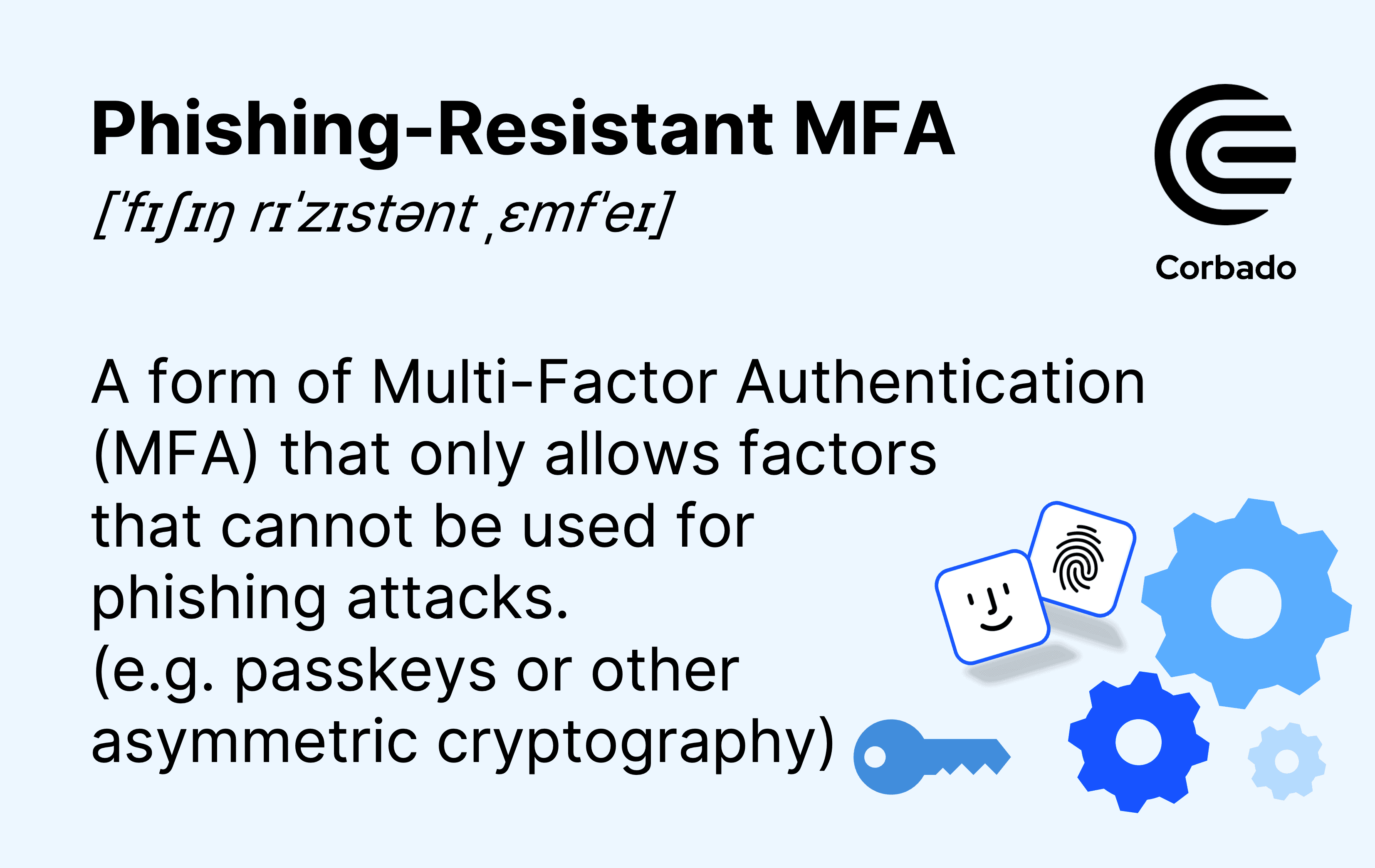
Conclusion: Your Authentication Strategy for the New Threat Landscape
Multi-factor authentication served enterprise security well. It raised the bar from passwords alone and stopped many brute-force attacks. But the threat landscape changed while many organizations kept their authentication strategy the same.
Phishing isn't a technical problem your infrastructure can solve alone. It's a human problem where attackers exploit trust, create urgency, and convince people to voluntarily share credentials. MFA doesn't stop that because MFA doesn't protect the recovery process where most successful social engineering attacks happen.
Phishing-resistant authentication fundamentally changes the game. You can't be socially engineered into providing a valid FIDO2 signature for a phishing site. Your device won't authenticate because the cryptographic math doesn't work. SMS-based codes can be stolen. Biometric data stays on your device. Hardware keys stay in your pocket.
This isn't theoretical. The data is clear: 84% of breaches involve phishing. Phishing-resistant authentication adoption grew 63% in a single year. 7% of enterprise users are authenticating entirely without passwords. SMS usage is declining as organizations recognize its vulnerabilities. The market is voting for phishing-resistant methods.
The migration isn't painless. You'll face legacy systems that don't support these methods. You'll need new infrastructure. You'll need to manage change with your organization. You'll need to build processes for edge cases and support scenarios.
But the cost of not migrating is higher. Every month you delay is another month where 30% of your users have no MFA at all, where social engineers are testing your support desk, where phishing emails are sitting in mailboxes.
The competitive advantage goes to organizations that move first. You'll have operational advantages from fewer password resets and fewer breaches. You'll have security advantages from authentication that actually resists the attacks happening today. You'll have talent advantages from demonstrating that you take security seriously.
Start your assessment now. Identify your critical systems and high-risk users. Plan your pilot. Prepare your infrastructure. Build your roadmap. The organizations that move decisively in 2026 toward phishing-resistant authentication will spend the rest of the decade ahead of those that delay.
Your password era is ending. Your phishing-resistant era is beginning. The question isn't if you'll make the transition. It's when.
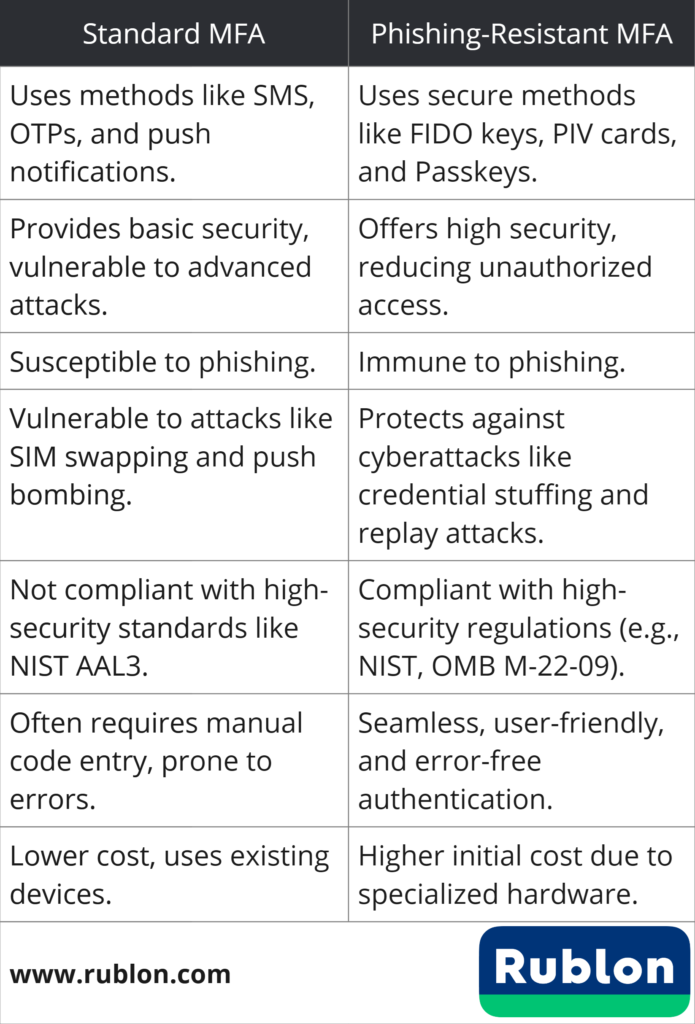
Key Takeaways
- MFA adoption reached 70% enterprise-wide, but 30% of users remain unprotected, and social engineering attacks now bypass MFA by targeting password recovery processes
- Phishing-resistant authentication using FIDO2, WebAuthn, and hardware keys grew 63% year-over-year as organizations recognize that cryptographic binding prevents phishing attacks fundamentally
- 84% of security breaches involve phishing attacks, making credential theft the dominant attack vector that traditional authentication methods cannot adequately defend against
- Passwordless authentication is already operational at enterprise scale with 7% of enterprise users authenticating without passwords as of January 2025 through staged implementations
- Implementing phishing-resistant authentication requires infrastructure updates and organizational change management, but measurably reduces help desk costs, support tickets, and successful breach attempts
Related Articles
- CISA End-of-Life Edge Device Replacement Guide [2025]
- ExpressKeys Password Manager: Complete Guide & Alternatives [2025]
- Password Security Guide: Why Strong Credentials Matter in 2025
- Android Privacy Tips: Protect Your Device From Prying Eyes [2025]
- Microsoft's Security Leadership Shift: What Gallot's Return Means [2025]
- AI Agents & Access Control: Why Traditional Security Fails [2025]
![Authentication Beyond MFA in 2026: Phishing-Resistant Methods [2025]](https://tryrunable.com/blog/authentication-beyond-mfa-in-2026-phishing-resistant-methods/image-1-1770739903287.jpg)



