Vishing Kits Targeting SSO Accounts: What Companies Need to Know Right Now
You wake up to a phone call. The voice on the other end sounds professional, authoritative. They claim to be from your IT support team. Your MFA is acting up, they say. They need you to verify your credentials on a quick form. You click the link. You enter your password. By the time you hang up, your accounts have been compromised.
This isn't a hypothetical scenario anymore.
Over the past eighteen months, security researchers have been tracking a disturbing trend: highly sophisticated, customizable phishing kits designed specifically to complement voice-based social engineering attacks, commonly known as vishing. These aren't the clumsy phishing attempts of years past. These are polished, professional-grade tools that adapt in real time as attackers manipulate victims on the phone.
The scope is staggering. Threat actors are actively targeting employees at organizations using Google Workspace, Microsoft 365, Okta, and even cryptocurrency exchanges. The kits work by creating a synchronized attack where the attacker controls both the conversation and what appears on the victim's screen, making it nearly impossible to detect the deception without specialized defenses.
What makes this threat particularly dangerous is the erosion of traditional security assumptions. For years, organizations have relied on multi-factor authentication (MFA) as a safety net. But these new vishing kits don't try to crack MFA. Instead, they work around it entirely by deceiving the user into providing access willingly, in real time, while guided by an attacker's voice.
In this comprehensive guide, you'll learn exactly how these attacks work, why they're so effective, which organizations are being targeted, and most importantly, what practical defensive measures actually stop them.
TL; DR
- Customized vishing kits are now being weaponized at scale against SSO providers like Google, Microsoft, and Okta, combining voice-based social engineering with real-time phishing site adaptation
- The attack bypasses traditional MFA by manipulating users into authenticating themselves on spoofed pages while the attacker controls the call flow and timing
- Victim profiling is a critical first step, with attackers researching targets' apps, support numbers, and organizational structure before initiating contact
- Phishing-resistant authentication (passkeys, FIDO2) is the only proven defense that blocks these attacks at the protocol level, unlike SMS or push-based MFA
- Network controls and tenant access management add significant friction, forcing attackers to use less reliable anonymization services that risk detection
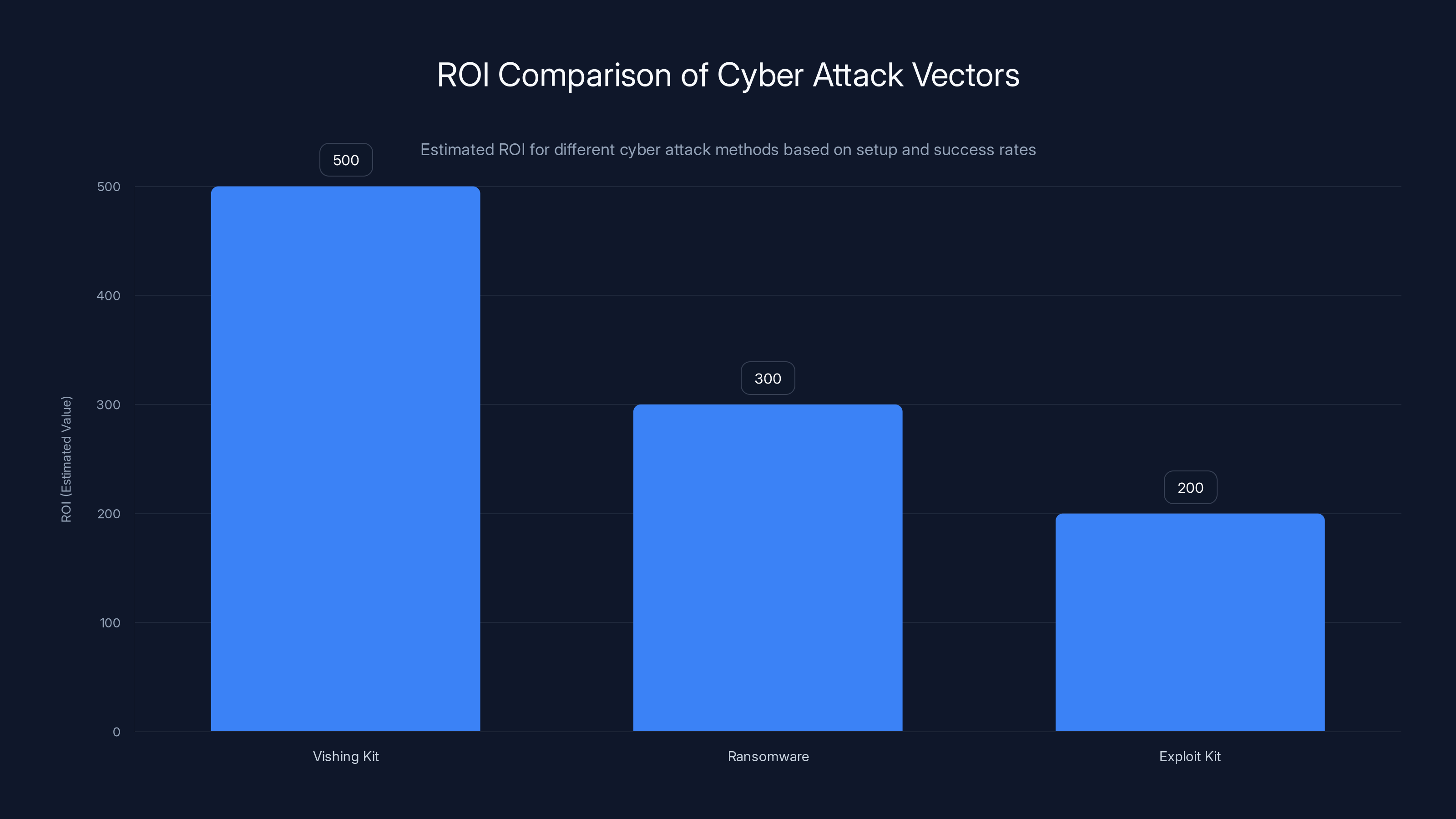
Vishing kit attacks offer the highest ROI due to low setup costs and relatively high success rates, compared to ransomware and exploit kits. Estimated data based on typical attack scenarios.
Understanding the Vishing Kit Threat Landscape
Vishing, the voice equivalent of phishing, isn't new. Attackers have been cold-calling employees for decades, pretending to be IT support or vendors. What's changed is the sophistication and scale.
Traditional vishing relied on the attacker's ability to convincingly impersonate someone and hope the victim complied. The success rate depended entirely on social engineering skill. But these new customizable kits have transformed vishing from an art into an engineered process.
Think of a vishing kit as a complete attack platform. It includes phishing site templates that can be rapidly customized, backend infrastructure to serve different pages to different users, real-time communication interfaces, and logging systems to track what worked and what didn't. The attacker doesn't need to be a social engineering expert. They need to follow a script and manage a system.
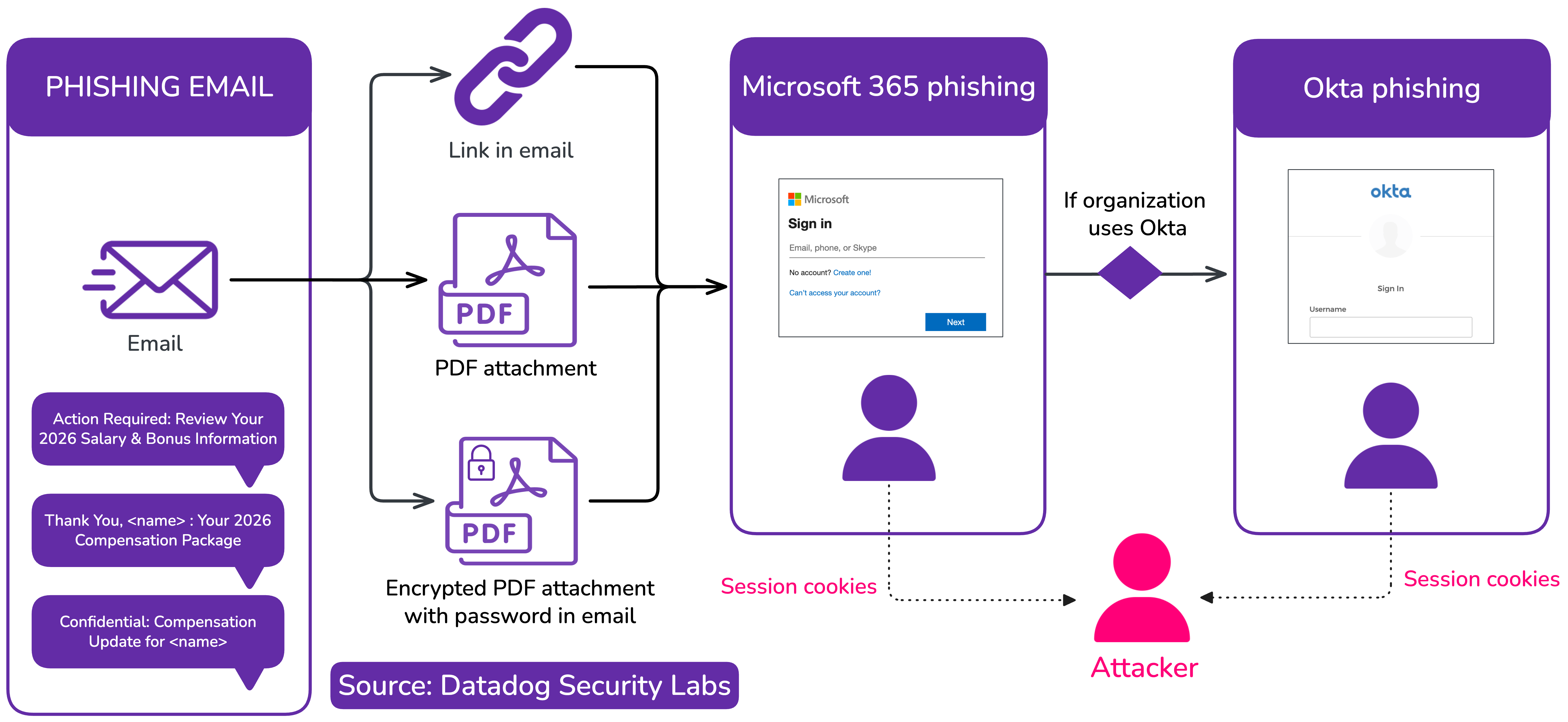
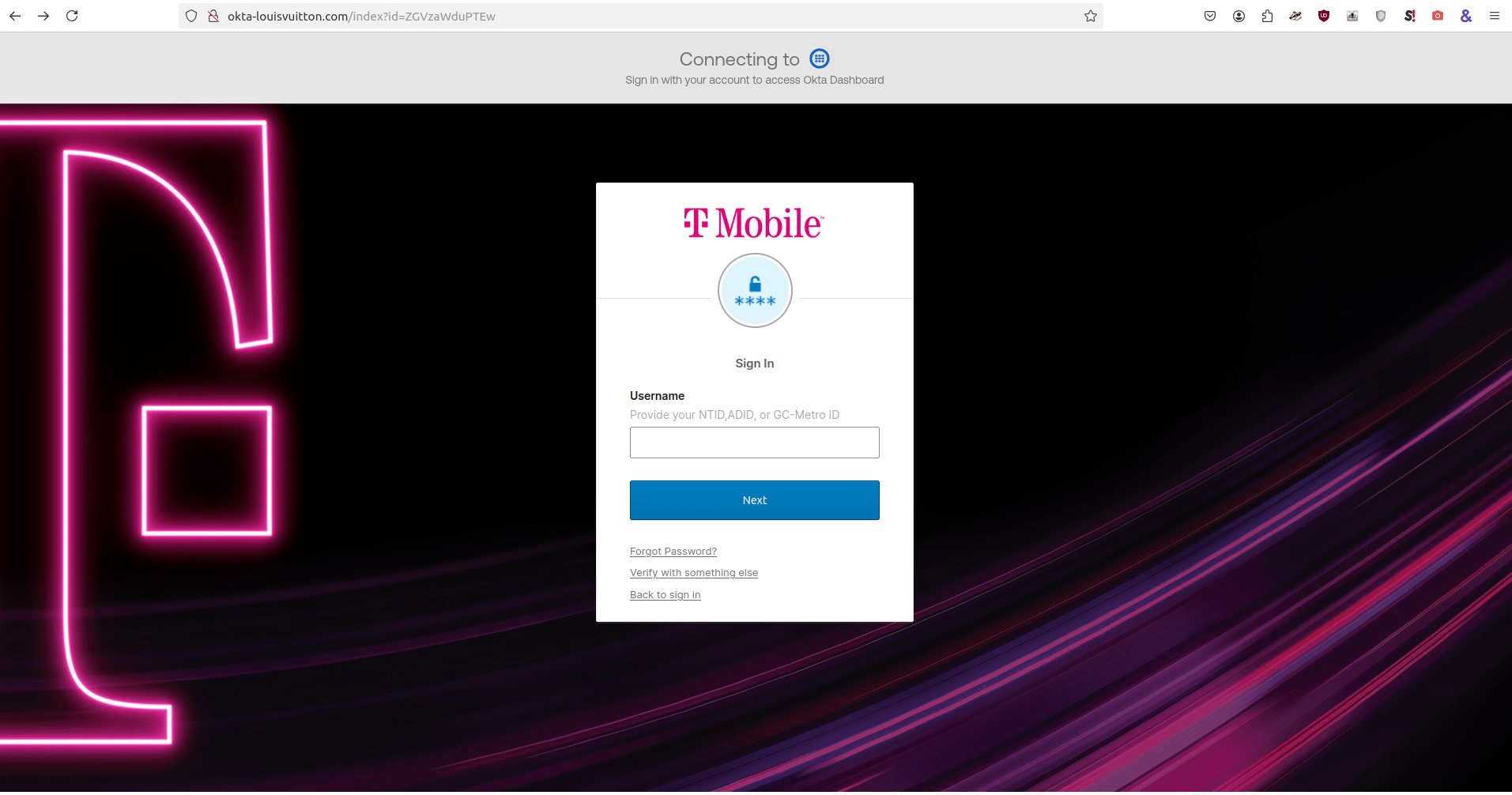
The kits themselves are modular and adaptable. An attacker can create a phishing page that looks like Google's login screen in minutes. They can clone Microsoft's authentication UI. They can replicate Okta's branded appearance with such fidelity that even security-conscious employees hesitate when they see it.
What's particularly insidious is that these kits are increasingly sold as services. Threat actors don't need to build custom infrastructure anymore. They can purchase or rent access to pre-built platforms, dramatically lowering the barrier to entry for conducting these attacks.
The result? A significant increase in vishing volume. When attackers can launch campaigns efficiently and at scale, they naturally increase their attack frequency. Security researchers have documented a measurable surge in voice-based attacks over the past two years, correlating directly with the availability and improvement of these commercial kits.
The threat is further amplified by specialization. Some kits target specific platforms (like Okta or Azure AD). Others are designed for particular industries. Financial services, healthcare, and technology companies are seeing the highest attack volumes, but manufacturing, energy, and government organizations are increasingly targeted as well.

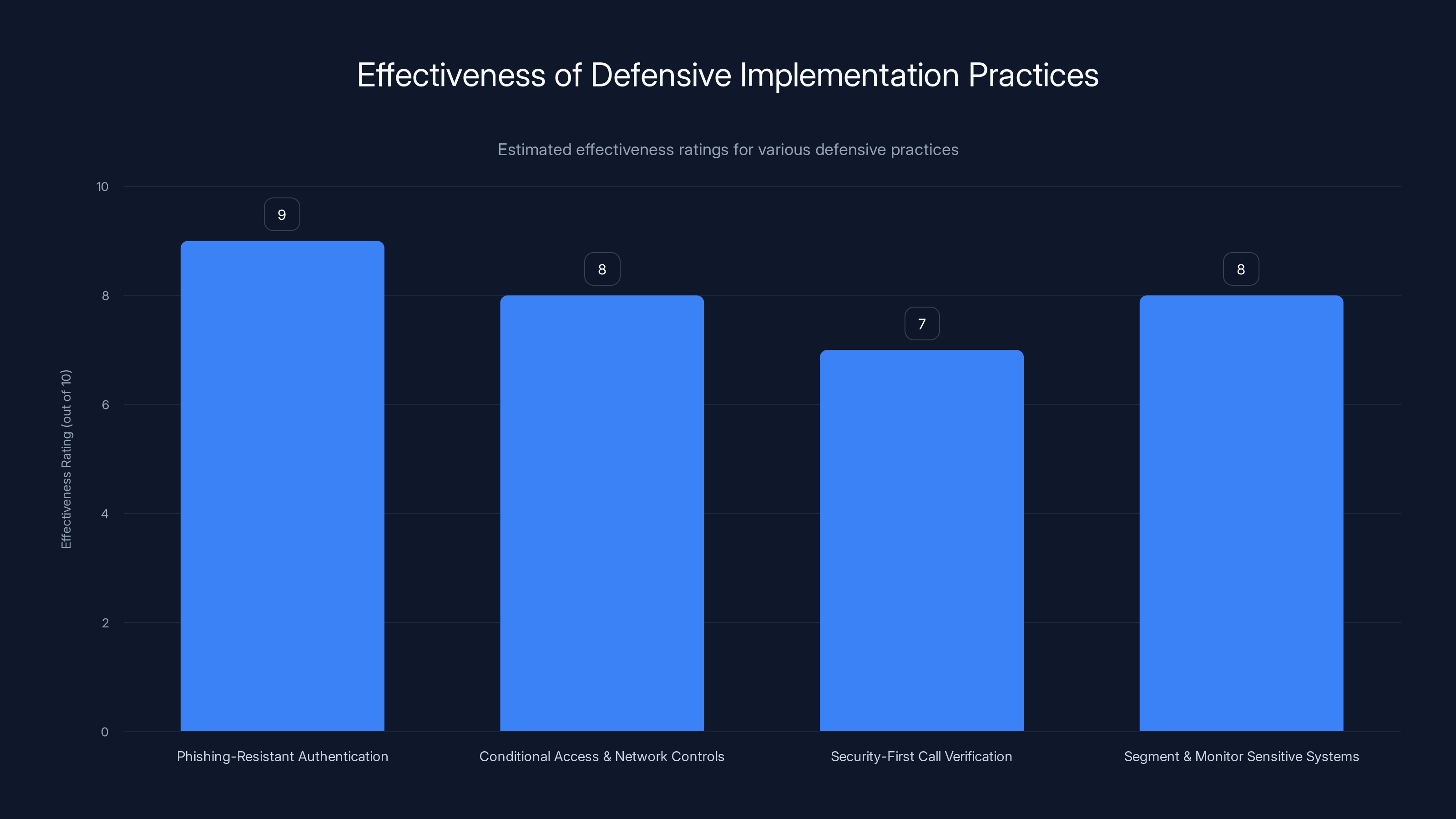
Phishing-resistant authentication is rated as the most effective defensive practice with a score of 9 out of 10. Estimated data based on typical security assessments.
How Vishing Kits Work: The Attack Flow
Understanding the mechanics of these attacks is crucial for defense. The attack follows a predictable sequence, each step building on the last.
Phase 1: Intelligence Gathering and Victim Profiling
Before the first phone call is made, attackers invest time in research. This is where the attack succeeds or fails.
Threat actors use publicly available information to identify targets. They might browse LinkedIn to find employees at a specific company, noting their job titles and departments. They search for IT support numbers, organizational hierarchies, and common applications used at the target company. They may purchase leaked employee lists from dark web markets.
The goal is to create a convincing pretext. If they're targeting a Google Workspace customer, they'll study how Google support communications typically work. They'll note common IT support phone numbers (either real numbers or spoofed ones that sound legitimate). They'll identify which employees have which apps enabled in their workspace.
Some attackers even monitor social media or browse company websites to understand organizational structure. They might find that a certain company uses specific VPN solutions or have particular security implementations, allowing them to tailor their narrative accordingly.
This profiling phase typically takes hours to days per target, depending on available information. The more information gathered, the more convincing the attack becomes.
Phase 2: Initial Contact and Trust Building
The attacker calls the target, typically using VOIP services that can spoof caller ID to display a legitimate company number or internal extension.
The conversation starts with a credible pretext. The attacker might say, "Hi, this is [Name] from IT support. We're experiencing an authentication service issue on your account and need to verify your credentials to re-provision your access. This will only take a minute." The specificity matters. They mention real services the victim uses. They reference recent incidents that actually happened. They create urgency.
Professional attackers sound calm and authoritative. They know IT support terminology. They're patient when victims express skepticism. Some even stay on the line while walking the victim through the "verification" process, making it feel like a legitimate support call.
This is where social engineering meets technical attack. The attacker is building trust while simultaneously preparing the technical component of the assault.
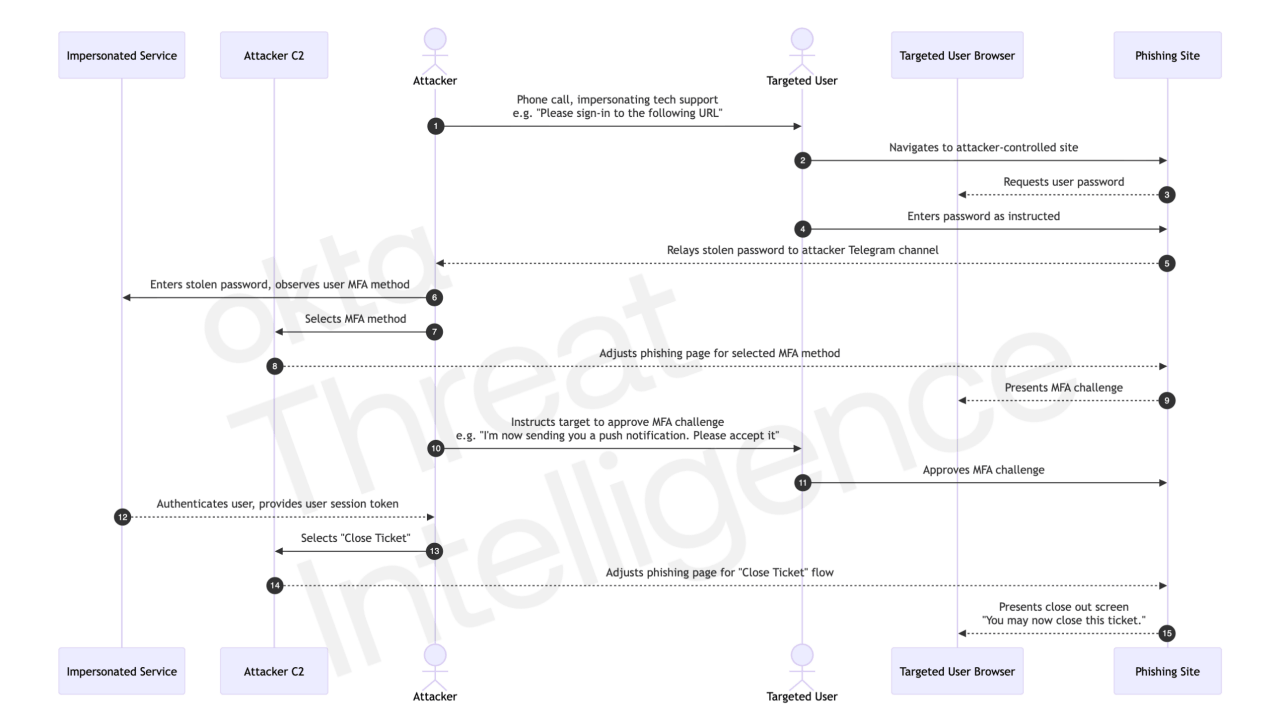
Phase 3: Technical Synchronization and Phishing
Now the synchronized attack begins. The attacker tells the victim to open a browser and navigate to a specific URL or click a link provided via email. This is where the vishing kit's real power emerges.
The victim lands on a phishing page. It looks authentic. It has the company's branding, correct fonts, proper colors, security badges. The victim is asked to enter their username and password, or their email and password, or some variation depending on the kit's configuration.
But here's the critical part: the attacker is watching in real time. The kit logs every keystroke. Every page load. The attacker sees what the victim typed. The attacker sees which MFA method is being triggered.
The attacker then coaches the victim through the next step. "Now you should see a push notification on your phone from Microsoft Authenticator. Just approve it, and we'll have you re-provisioned." The victim, still on the phone with someone who sounds legitimate, approves the push notification. The attacker captures the session token.
Or, if the organization uses SMS-based MFA, the attacker asks the victim to read the code aloud. "What's the code you're seeing?" "It's 847629." The attacker enters it. Account compromised.
Some advanced kits even inject phishing pages that appear to be MFA completion screens, asking the user to enter the code themselves, which the kit captures directly.
The entire process takes five to ten minutes.
Phase 4: Post-Compromise Access and Lateral Movement
Once the attacker has valid credentials and has bypassed MFA, they have legitimate account access. They log in from their own infrastructure, often through anonymizing services or compromised proxies to avoid detection.
At this point, they typically perform reconnaissance on what's available in the account. They check for stored authentication tokens. They look for information that helps them move laterally to other accounts or systems. They search for sensitive data.
Some attackers immediately establish persistence by adding recovery email addresses, backup phone numbers, or security keys they control. Others exfiltrate data and move on to the next victim.
The entire attack, from initial research to account compromise, might be completed in a single day per victim. Attackers who run campaigns manage dozens of targets simultaneously, with different team members handling different phases.

The Customization Advantage: Why These Kits Are So Effective
The adaptability of modern vishing kits represents a fundamental shift in attack capability. Traditional phishing kits were static. They worked the same way for every victim. Modern kits are dynamic.
Imagine an attacker running a campaign against employees at ten different companies. Each company uses different SSO providers, different MFA methods, and different authentication flows. A static kit wouldn't work efficiently across all targets. But customizable kits can be configured for each organization in minutes.
The kit might have pre-built templates for Google Workspace, Microsoft 365, and Okta. The attacker simply selects the template, customizes the company name, uploads the company logo, and deploys. The backend knows how to handle Google's authentication flow differently than Microsoft's. It captures codes appropriately for different MFA methods.
This customization extends to the script and pretext as well. The same kit infrastructure supports different narratives. One campaign might target Office 365 users with a "license renewal" pretext. Another might target Google Workspace users with a "security audit" pretext. The underlying technology is identical, but the social engineering is tailored.
Some advanced kits even include A/B testing capabilities. Attackers can test which phishing page design gets the highest completion rate. Which pretext language works better. Which time of day produces higher success rates. They can optimize their attack in real time based on live data.
This is where the attacker's capabilities start to rival legitimate organizations' user experience optimization practices. Except they're optimizing for deception instead of usability.
The speed of adaptation is crucial. If a vishing kit fails against a specific organization (maybe because users are trained, or security monitoring caught the phishing domain), the attacker can quickly redeploy against a different organization. No significant technical change needed.
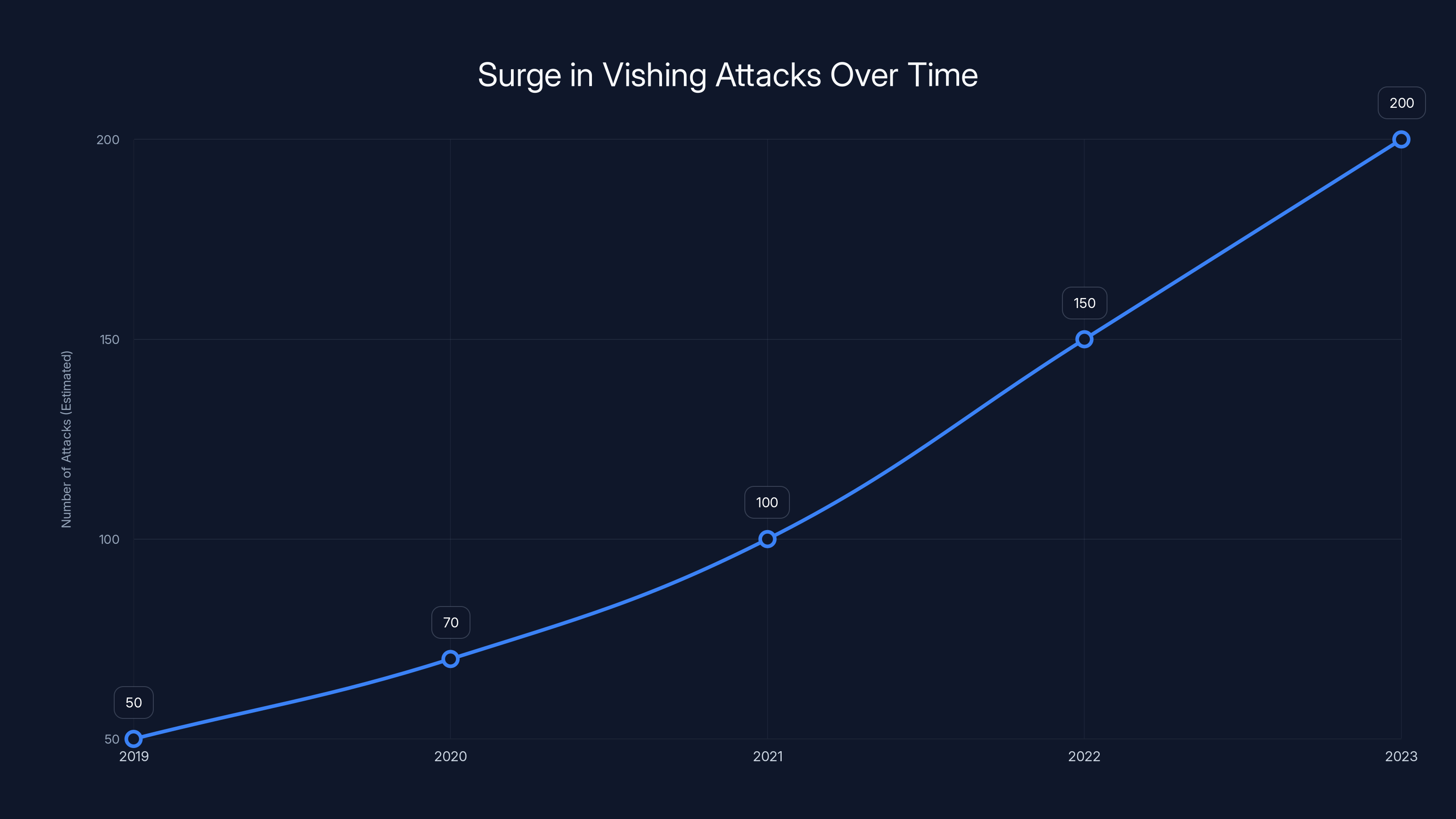
The availability of vishing kits has led to a significant increase in attack frequency, with an estimated fourfold rise from 2019 to 2023. Estimated data based on observed trends.
Target Selection: Who Are These Attacks Hitting?
These vishing kit attacks aren't random. Threat actors have specific targets in mind, and understanding the pattern reveals important insights about attacker motivations.
Enterprise SSO Providers as Primary Targets
Google Workspace, Microsoft 365, and Okta are heavily targeted because they're identity gateways. Compromising an SSO account doesn't just give access to the SSO provider itself—it potentially unlocks access to dozens of integrated applications.
This is what attackers call the "golden ticket" approach. Instead of compromising individual applications, they compromise the authentication layer. Then, every application connected to that identity provider becomes accessible.
A single Microsoft 365 account might unlock access to:
- Email (obviously the most valuable)
- One Drive and Share Point (often containing sensitive documents)
- Microsoft Teams (internal communications, project details)
- Power BI (business analytics and reporting)
- Azure (cloud infrastructure)
- Connected third-party applications (CRM systems, collaboration tools, business applications)
The attacker gets exponential value from a single successful vishing attack.
Okta is particularly attractive because many organizations use it as a bridge between on-premises systems and cloud applications. Compromising an Okta account sometimes provides access to systems that aren't cloud-native, expanding the attack surface further.
Cryptocurrency and Financial Services Targets
Security researchers have documented vishing kit campaigns specifically targeting cryptocurrency exchange employees. The pretext is usually internal access claims or suspicious account activity.
The goal here is often not general account access but rather administrative access or access to cryptocurrency wallets. A single compromised admin account at a crypto exchange can lead to theft of significant assets.
Traditional financial institutions (banks, investment firms, payment processors) are also heavily targeted. The narrative often revolves around regulatory compliance, fraud investigation, or emergency access provisioning.
High-Value Targets in Healthcare and Energy
Healthcare organizations operate with regulatory pressure around identity management. They're likely to have robust email security but sometimes weaker security awareness around phone-based requests.
Energy companies, especially those in critical infrastructure, are valuable because of potential downstream impacts. Compromising an energy company's IT systems could potentially enable further attacks on the power grid itself.
Why Traditional MFA Fails Against These Attacks
This is the critical point that organizations often misunderstand. Traditional MFA doesn't prevent vishing kit attacks. In many cases, it actually makes them easier.
Push Notification MFA: The Illusion of Security
Push-based MFA (like Microsoft Authenticator, Duo, or Google Authenticator push notifications) creates a false sense of security.
When a victim is on the phone with an attacker pretending to be IT support, and they receive a push notification, what do they think? They think the notification is legitimate. They think it's part of the normal authentication process. The attacker is standing by, saying, "Just approve that notification, and we'll have you re-provisioned."
The victim approves. The attacker captures the session. Account compromised.
The MFA didn't fail—it worked exactly as designed. But the user was manipulated into using it incorrectly.
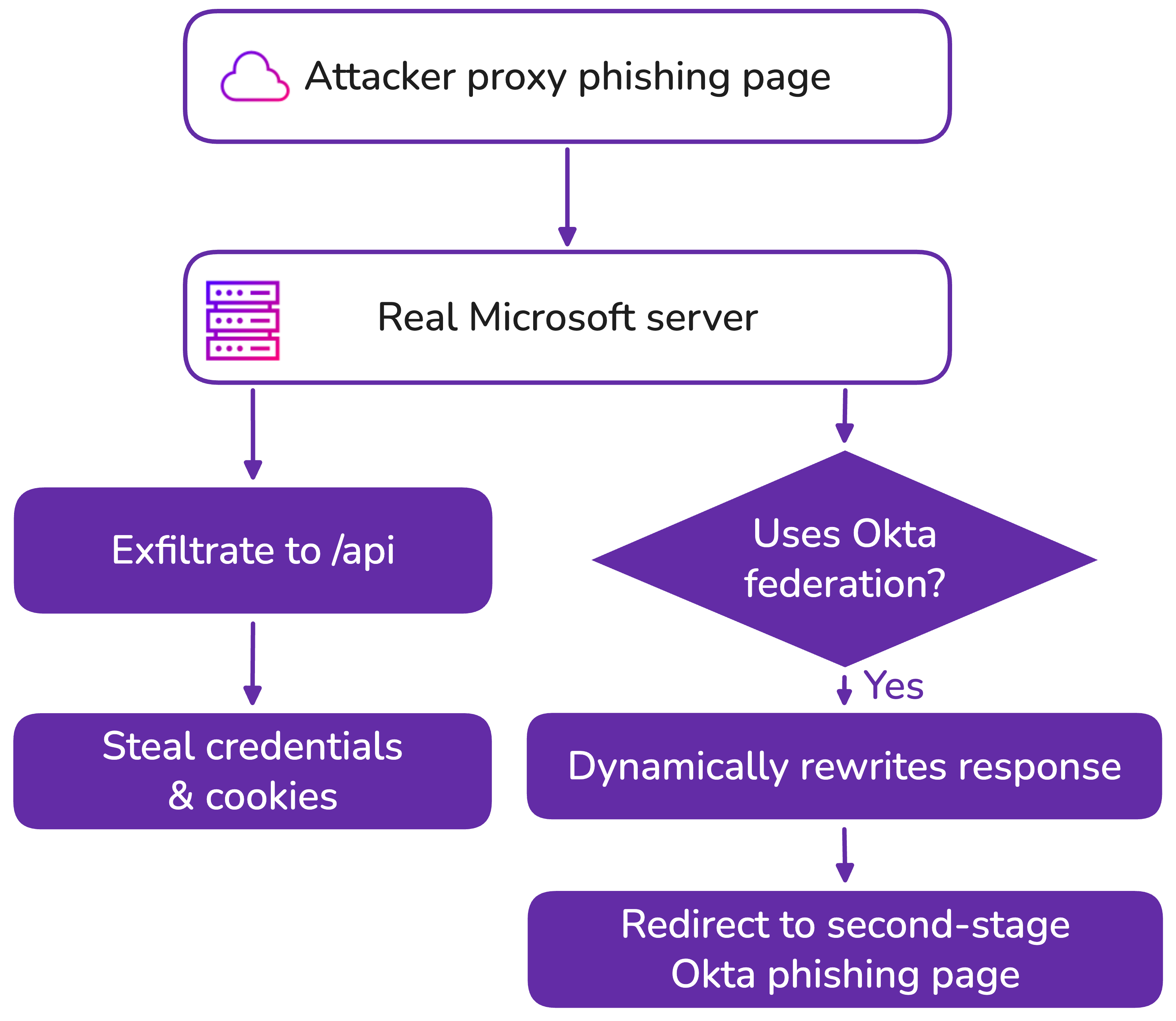
Some sophisticated kits even bypass this step entirely by hijacking the MFA flow themselves. They present a fake "authentication pending" screen that proxies the real authentication attempt. When the real push notification comes through, they relay it back to the victim's phone. Some kits can even intercept the notification entirely in certain network configurations.
SMS-Based MFA: Trivially Exploitable
SMS-based MFA is even worse. The attacker simply asks the victim to read the code aloud over the phone. "What's the six-digit code you're seeing?" "347892." Done.
Some organizations try to mitigate this by telling users "never share SMS codes." But when someone claiming to be IT support asks for the code, the pressure is enormous. The attacker creates urgency. "We need to re-provision your access immediately, or your account will be locked." Users comply.
Time-Based OTP: Slightly Better, But Still Vulnerable
Time-based one-time password (TOTP) apps like Google Authenticator are somewhat more difficult to exploit over the phone because the code expires in thirty seconds. But it's not impossible. An attacker can ask the victim to open their authenticator app and read the code immediately. It works.
Some advanced kits have even integrated screen-sharing capabilities (disguised as legitimate support tools) to see the authenticator directly without requiring the user to read the code.
The Fundamental Problem
All of these MFA methods share a critical weakness: they authenticate the user, not the application or service the user is interacting with. They prove that you are you, but they don't prove that the service asking for authentication is legitimate.
When an attacker controls both the communication channel (the phone call) and the application the user is interacting with (the phishing page), they can create a complete illusion of legitimacy that bypasses all user-centric MFA methods.
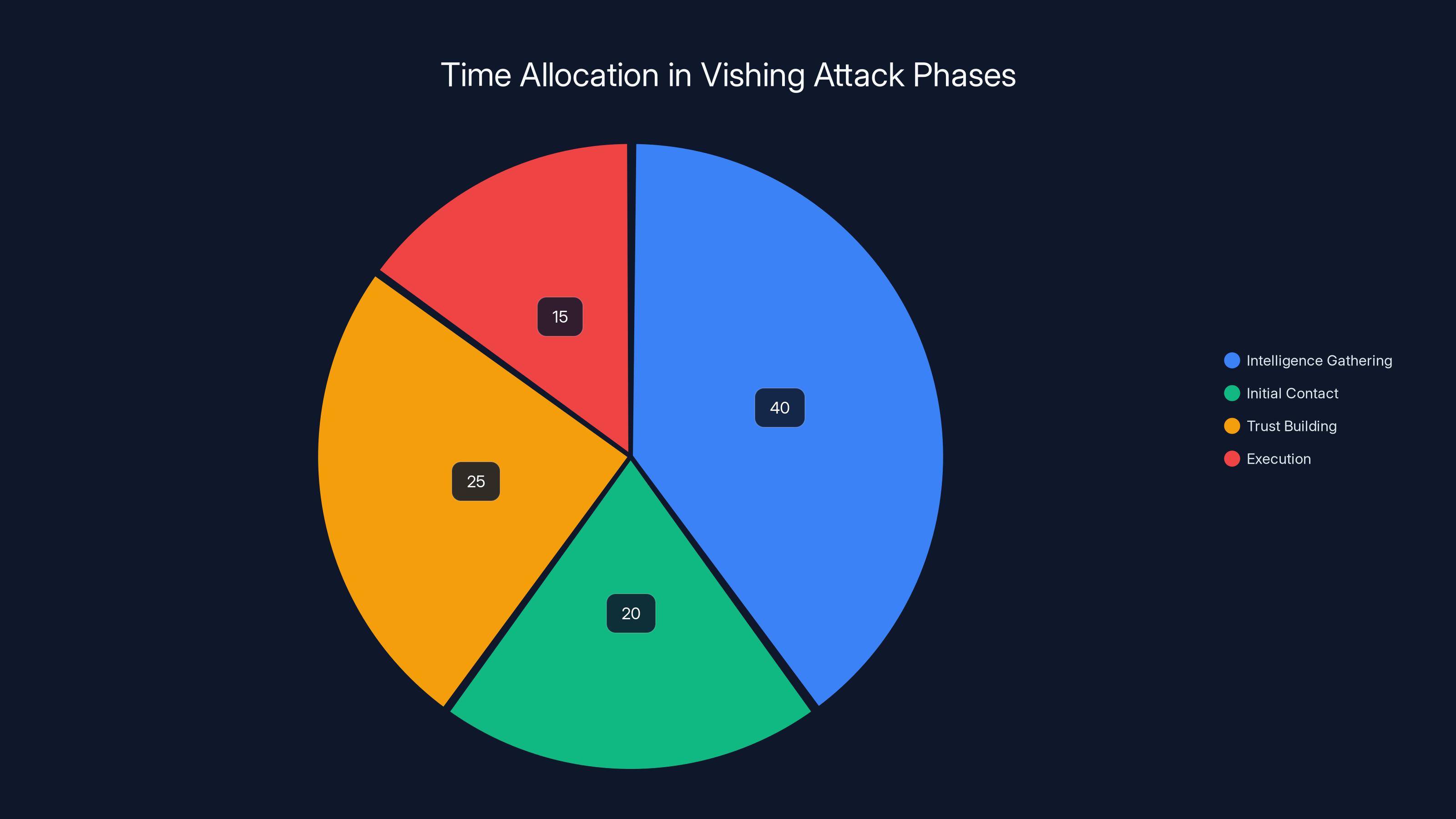
Estimated data shows that intelligence gathering is the most time-consuming phase, taking up 40% of the total time in a vishing attack.
Phishing-Resistant Authentication: The Only Real Defense
If traditional MFA can be defeated, what actually stops these attacks? The answer is phishing-resistant authentication, specifically FIDO2 (Fast Identity Online 2) and passkeys.
How FIDO2 and Passkeys Work
FIDO2 is a cryptographic protocol that makes impersonation impossible. Instead of asking users to prove they are who they claim to be, FIDO2 makes the service prove it's legitimate.
Here's the technical difference. When you use a password or even push notification MFA, you're sending proof of your identity (or approving authentication) regardless of what service is asking. If a phishing page that looks identical to the real service asks for this proof, you provide it.
With FIDO2, you're doing something fundamentally different. Your device generates a challenge specific to the legitimate service you're trying to access. Your authenticator (which might be your computer, phone, or a security key) cryptographically signs that challenge with a key that's specific to that service. You can only authenticate to the real service. A phishing page that's identical in every visual way will fail because it's not the legitimate service.
Passkeys are a user-friendly implementation of FIDO2. They're stored on your device (or synced to your device if your provider supports syncing). When you need to authenticate, your device automatically signs the challenge. No codes to enter. No notifications to approve. Just biometric authentication or PIN entry, and you're done.
The critical security property: an attacker on the phone with a victim, even if they're showing a perfect visual replica of the login page, cannot trick the victim into authenticating to the attacker's fake service.
Why This Stops Vishing Kits Cold
Consider the attack from the attacker's perspective. They call the victim, guide them through the process. The victim goes to the phishing page. But instead of seeing a password field or a push notification prompt, they see "Authenticate with passkey."
On a modern device, this means the victim would use their fingerprint or face to authenticate. The device checks: "Is this the real Google domain?" If it's not (which it isn't, because it's a phishing page), the device silently refuses. No authentication happens.
The attacker can't fake this. The entire attack falls apart.
Some attackers might try to work around this by asking the victim to use a traditional password instead, if the service supports both. But if the organization has disabled password-based authentication in favor of passkeys-only, there's no fallback.
This is why FIDO2 adoption is considered the gold standard for phishing-resistant authentication.
Network Controls: Making Attacker Infrastructure Visible
Phishing-resistant authentication stops the attack at the user level. But there's another defense layer: making it harder for attackers to operate the vishing kit infrastructure in the first place.
Tenant Access Control Lists (TACLs)
Modern identity providers like Okta, Azure AD, and Google Workspace support tenant access control lists. These are policies that restrict where authentication traffic can originate from.
Instead of allowing authentication from anywhere on the internet, organizations can specify that authentication is only allowed from corporate networks, or from VPN connections, or from specific geographic regions.
From the attacker's perspective, this is a major problem. They want to connect from their compromised infrastructure, not from a corporate network. If the TACL prevents authentication from external sources, the entire attack fails.
Attackers have workarounds. They can try to compromise legitimate corporate networks to authenticate through them. They can rent access to corporate VPN infrastructure. But these workarounds require additional steps, additional infrastructure, and increase the risk of detection.
Security researchers have noted that when organizations implement TACLs, attackers become "frustrated," in the words of threat intelligence researchers. The attacks become harder to execute and less profitable.
Network Zone Configuration
Similarly, configuring network zones that restrict which locations can authenticate helps. If an organization's employees are primarily in the US, but authentication attempts suddenly come from Vietnam, it's suspicious.
These controls don't stop determined attackers with sophisticated infrastructure, but they add friction. They force attackers to use anonymization services that are easier to detect or to compromise additional infrastructure to make their traffic appear legitimate.
The cumulative effect of these controls is significant. Attackers operating vishing campaigns want high volume and low detection risk. Controls that add friction reduce the attacks' viability.
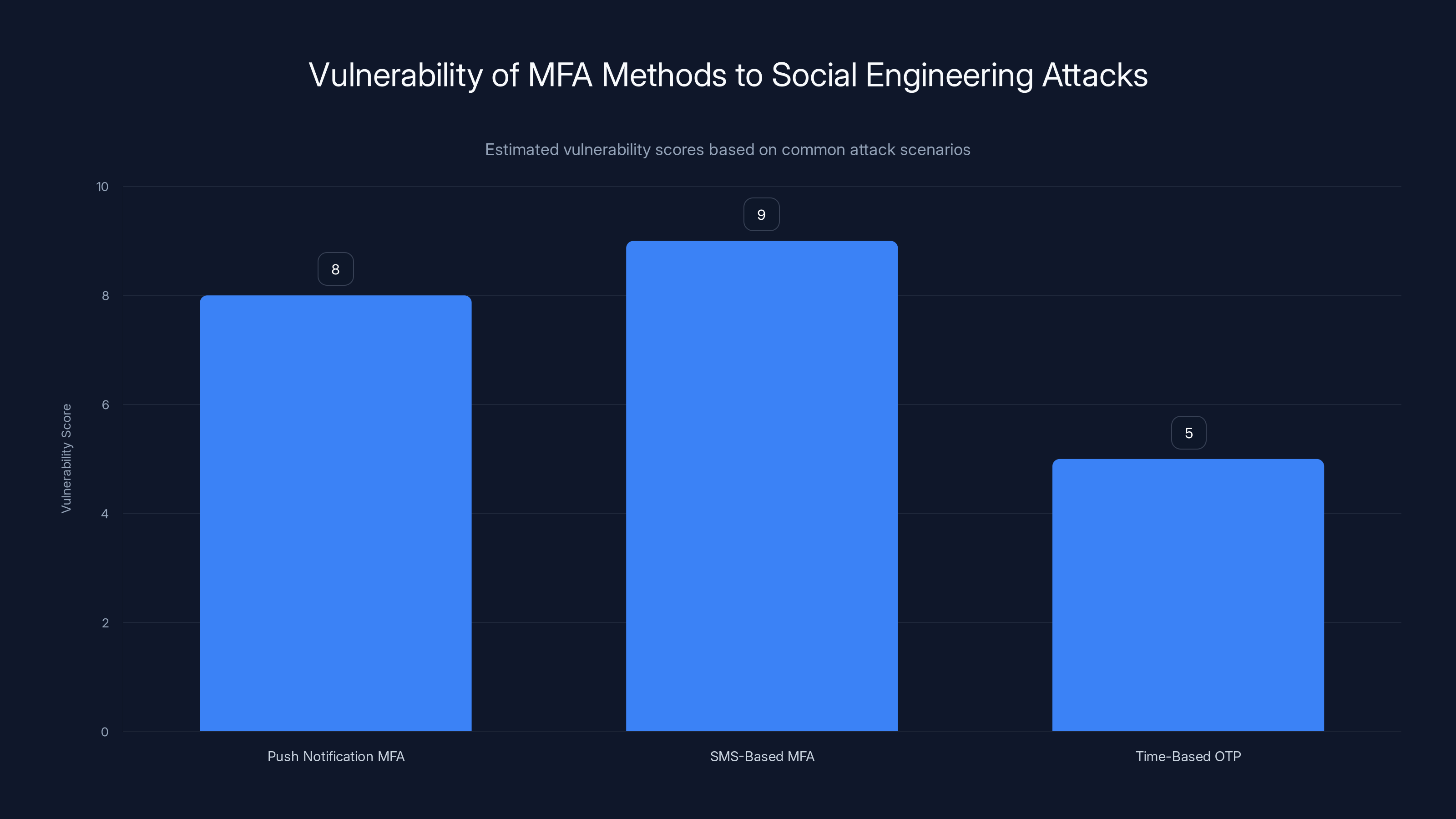
Push Notification and SMS-Based MFA methods are highly vulnerable to social engineering attacks, with estimated scores of 8 and 9 out of 10, respectively. Time-Based OTP is slightly more secure with a score of 5. (Estimated data)
Organizational Response: What Companies Are Doing
Organizations that have been targeted by these vishing kit campaigns, or are concerned about them, are implementing a multi-layered defensive approach.
Security Awareness Training: The Reality Check
Most organizations are updating their security awareness training to specifically address vishing attacks. The old training message "never share your password" isn't sufficient anymore.
Effective training now includes:
- Caller verification techniques: Legitimate IT support will agree to hang up and let you call back on the official company number
- Urgency as a red flag: If the request is urgent, it's probably a social engineering attempt
- Procedure documentation: Real IT support follows documented procedures that employees can verify
- Permission to question: Creating a culture where it's normal to verify requests, even if they seem legitimate
Some organizations even conduct internal red team exercises, actually calling employees pretending to be IT support to see who falls for it. The data from these exercises helps identify high-risk individuals and areas where training needs improvement.
But there's a reality check here: no amount of training eliminates the risk entirely. Attackers are sophisticated. Some employees are trusting. A few percentage point improvement in user compliance rates still translates to successful attacks when you're targeting thousands of employees across multiple organizations.
Technical Controls: Layered Defense
Organizations are deploying multiple technical controls to reduce risk:
Email Domain Authentication
- SPF, DKIM, and DMARC prevent domain spoofing in emails
- Attackers can't send emails from legitimate company addresses
- Forces them to use similar-looking spoofed addresses, which training might catch
Phishing Detection and Prevention
- Email security gateways scan emails for phishing links
- Some can even sandbox links to see if they lead to phishing pages
- Blocks many phishing pages before users ever see them
Device Security
- Endpoint detection and response (EDR) tools monitor for suspicious activity
- If a device is used to access a phishing site, security tools might detect unusual behavior
- Mobile device management (MDM) restricts which apps can handle authentication
Identity Provider Security
- Real-time anomaly detection flags suspicious authentication attempts
- Machine learning models identify unusual locations, devices, or patterns
- Impossible travel detection (authentication from two locations that couldn't physically be traveled between in the time available) blocks obviously compromised accounts
These controls don't stop vishing attacks from happening, but they can detect compromised accounts faster and limit the damage.
The Economics of Vishing Kit Attacks
Understanding why these attacks are increasing requires looking at the economics from the attacker's perspective.
Return on Investment for Attackers
A vishing kit attack, when successful, provides extremely high ROI. Consider the typical numbers:
- Setup cost: Purchasing or renting access to a vishing kit might cost 1000
- Time cost: An attacker might spend 8 hours researching targets, making calls, and managing the attack
- Success rate: Against unprepared targets, success rates run 10–30% depending on the pretext and target industry
- Value per account: A compromised email account in a technology company might allow access to intellectual property worth millions. Cryptocurrency exchange access might compromise six-figure amounts.
Even with a 10% success rate and only moderate value per account, the ROI is exceptional.
Compare this to other attack vectors. Ransomware requires more setup, more technical skill, and has higher detection risk. Exploit kit attacks require 0-day vulnerability discovery. Vishing kit attacks are relatively simple, require minimal technical skill, and provide immediate access.
Why Kits Are Proliferating
Successful attacks lead to commercialization. Once one threat actor develops an effective vishing kit, others want to use it. This creates a market.
Kits are sold on dark web marketplaces, rented as services, or shared within threat actor networks. The price is typically low enough that even small threat actor groups can afford access. Some kits are even offered free as part of larger attack platforms (like a botnet operator offering vishing capability to their existing customers).
This democratization of attack tools means that vishing attacks are no longer limited to sophisticated nation-state actors or established criminal organizations. Any reasonably motivated threat actor can now conduct campaigns.

Phishing-resistant methods like FIDO2 and Passkeys offer significantly higher protection against phishing attacks compared to traditional MFA and passwords. Estimated data.
Industry-Specific Vulnerability Patterns
While vishing attacks can target any organization, certain industries show higher vulnerability.
Technology Companies
Technology company employees are often familiar with technical social engineering but complacent about voice-based attacks. They assume their colleagues wouldn't make mistakes. The attacker's technical credibility (using correct terminology, understanding the company's systems) combined with the phone's relative anonymity creates a gap.
Additionally, technology companies often have employees distributed across multiple time zones and offices. Employees are accustomed to getting support from unfamiliar faces and voices, making impersonation easier.
Financial Services
Financial services have high-value targets. Compromised accounts might provide access to transaction systems, customer data, or wire transfer capabilities. The perceived urgency in financial institutions (regulatory audits, fraud investigations, account freezes) makes the vishing pretext credible.
Healthcare
Healthcare organizations deal with regulatory requirements around identity and access management. Attackers leverage this by creating pretexts around compliance audits or access provisioning. Healthcare workers are also trained to respond to urgent requests (because lives are at stake), which makes them more compliant with phone requests.
Measuring Attack Impact and Attribution
Determining the full scope of vishing kit attacks is challenging. Not all successful attacks are detected. Not all detected attacks are reported. Attribution is difficult because attackers use anonymization services and compromised infrastructure.
Detection Challenges
A vishing attack that successfully compromises an account might go undetected for weeks. Organizations only notice when:
- The compromised account performs unusual actions (accessing files it never accessed before, forwarding emails)
- A victim notices account activity they didn't authorize
- Threat intelligence tools flag the compromised account
- A downstream victim (like a partner organization) notifies them
Some organizations have better detection capability than others. Large enterprises with dedicated security operations centers (SOCs) catch compromises faster. Smaller organizations might never detect them.
Reporting Gaps
Many compromised accounts are never reported to authorities or security vendors. Organizations might remediate internally without disclosing the incident. Victims might not understand that they were attacked via vishing.
This creates significant underestimation of the attack volume.
Attribution Difficulty
Attackers use VOIP services that don't require identity verification. They route calls through international providers. They use voice cloning technology and hire call centers in multiple countries. They connect through compromised infrastructure and VPNs.
Attributing a specific vishing attack to a specific threat actor is nearly impossible without insider information or law enforcement cooperation.
Future Evolution of Vishing Kit Threats
These attacks are evolving. Understanding the trajectory helps with long-term defensive planning.
AI-Powered Social Engineering
The next evolution is AI-powered voice cloning and script generation. Attackers are already testing synthetic voice technology to create convincing automated calls. Combined with AI-generated personalized scripts based on victim profiling, the human element becomes optional.
This would enable enormous scale. Instead of hiring call centers or making calls themselves, attackers could deploy AI agents making thousands of calls simultaneously, each customized for the target.
Deepfake Video Integration
Some advanced attackers are experimenting with deepfake video combined with vishing. The call isn't just voice—it's video of someone claiming to be IT support. The video is convincing enough that the victim never suspects they're talking to an AI.
Ecosystem Integration
Vishing kit operators are integrating with other attack infrastructure. A successful vishing attack feeds data into ransomware operators, data brokers, and lateral movement tools. The vishing kit becomes part of a larger attack platform rather than a standalone tool.

Best Practices for Defensive Implementation
Based on what we know about these attacks, certain defensive practices are proven effective.
Prioritize Phishing-Resistant Authentication
This is non-negotiable. Organizations should:
- Evaluate FIDO2 or passkey solutions that fit their environment
- Pilot with high-value users first (executives, IT staff, finance)
- Expand to all users over time
- Eventually make it the primary or only authentication method for critical applications
The longer you delay, the more time attackers have to target your organization.
Implement Conditional Access and Network Controls
- Configure tenant access control lists to restrict authentication origins
- Set up network zones and geographic restrictions
- Deploy real-time anomaly detection
- Monitor for impossible travel and other suspicious patterns
Create a Security-First Call Verification Culture
- Train employees on how to verify caller identity independently
- Create a documented process for support requests that includes verification steps
- Make it normal and expected to verify requests, even if they seem legitimate
- Report attempted attacks to security so patterns can be identified
Segment and Monitor Sensitive Systems
- Identify which systems are most attractive to attackers (email, VPN, financial systems)
- Require additional authentication factors for accessing these systems
- Monitor access patterns and alert on anomalies
- Consider requiring separate devices for accessing sensitive systems

The Reality of Perfect Defense
Here's the uncomfortable truth: perfect defense against vishing kit attacks isn't realistically achievable. Attackers will adapt. They'll find new pretexts. They'll integrate new technologies.
What's achievable is defense-in-depth. You can't eliminate the risk, but you can:
- Make attacks significantly harder and less profitable
- Detect compromises faster
- Limit the damage from compromises that do occur
- Make your organization a less attractive target compared to competitors
The organizations winning against these attacks aren't the ones trying to be perfect. They're the ones with:
- Strong technical controls that work even when users make mistakes
- Rapid detection and response capability
- A culture of security awareness without creating security theater
- Willingness to accept that attacks will happen and planning accordingly
This shift in mindset from "preventing all attacks" to "managing unavoidable attacks" is where most organizations are heading.

Regulatory and Compliance Considerations
Vishing attacks have implications for regulatory compliance in multiple ways.
Security Breach Notification Laws
When a vishing attack results in a data breach, organizations must notify affected parties according to applicable laws (GDPR in Europe, CCPA in California, breach notification laws in other states). This creates legal obligation to detect and report vishing attacks.
Data Protection Regulations
GDPR and similar regulations require organizations to implement appropriate technical and organizational measures to protect personal data. This is often interpreted to include phishing-resistant authentication for systems handling personal data.
Industry-Specific Requirements
- Healthcare: HIPAA requires administrative safeguards including access controls
- Financial services: PCI DSS, SOX, and other regulations mandate strong authentication
- Government: Fed RAMP, FISMA, and contractor requirements increasingly mandate FIDO2
Compliance isn't the main reason to defend against vishing attacks, but it's a compelling secondary motivation that can justify investment to stakeholders.
Conclusion: Moving Forward in a Vishing Kit World
Vishing kit attacks represent a mature threat that's unlikely to disappear. The attack vector is simple, effective, and economically viable. Organizations can't wish this problem away through training alone.
What's changed is that we now have proven defenses. Phishing-resistant authentication, network controls, and real-time detection aren't theoretical concepts. They're deployed and working in organizations today. The only question is whether your organization will adopt them before becoming a victim or after.
The timeline matters. Threat actors are improving their tools. Deployment of vishing kits is expanding to new threat actor groups. Victims span multiple industries and geographies. The attack trend is clearly upward.
Organizations that move quickly to implement phishing-resistant authentication, tenant access controls, and improved detection will dramatically reduce their risk. Those that delay, betting on user training alone or traditional MFA, are increasing their exposure.
The cost of implementation is declining as FIDO2 and passkey technology becomes mainstream. Major identity providers (Google, Microsoft, Okta) all support it. Device manufacturers are building it in. There's no longer an excuse of "it's too new" or "we don't have vendors who support it."
The question isn't whether your organization should defend against vishing kit attacks. The question is how quickly you'll implement defenses. The answer to that question may determine whether you're reading about being compromised in a security blog next year.
FAQ
What exactly is a vishing kit and how does it differ from traditional phishing?
A vishing kit is a customizable software platform that enables attackers to launch voice-based social engineering attacks (vishing) at scale. Unlike traditional phishing, which relies solely on email, vishing kits combine voice calls with real-time phishing pages that can be adapted during the attack. The attacker controls both the conversation and what the victim sees on screen simultaneously, creating synchronized deception that's much more difficult to detect than email-based attacks.
How do attackers use vishing kits to bypass multi-factor authentication?
Vishing kits bypass traditional MFA by manipulating users into providing authentication willingly while guided by the attacker's voice. When a victim receives a push notification, they're told to approve it as part of normal IT support procedures. When faced with SMS codes, they're asked to read them aloud. The attacker captures the session credentials in real time. The MFA functions exactly as designed—it's the user who's being manipulated into using it incorrectly.
Why is phishing-resistant authentication effective against vishing attacks?
Phishing-resistant authentication like FIDO2 and passkeys work cryptographically by binding authentication to the legitimate domain of the service. The victim's device verifies that they're authenticating to the real service (like google.com or microsoft.com) rather than a phishing replica. If the domain isn't legitimate, authentication silently fails. An attacker showing a perfect visual replica of the login page cannot trick the victim's device into authenticating to the fake domain.
What should I do if I receive a suspicious call claiming to be from IT support?
Legitimate IT support will understand your skepticism and cooperate with verification. Hang up the call and contact your IT department directly using a phone number from your company directory or official website. Ask about the issue the caller mentioned. If it's legitimate, they'll have a record of the request. If it's not, you've stopped the attack. Real IT support will never ask you to enter credentials immediately or request codes over the phone.
What organizations are being targeted by vishing kit attacks?
Primarily organizations using cloud identity providers like Google Workspace, Microsoft 365, and Okta. But attacks also target cryptocurrency exchanges, financial institutions, healthcare organizations, and energy companies. Any organization with valuable data or access is a potential target. The choice of target depends on attacker motivation and perceived value.
How can organizations detect if they've been compromised via a vishing kit attack?
Detection involves monitoring for unusual authentication patterns: logins from unexpected locations or devices, authentication from anonymization services or VPNs, impossible travel scenarios (authentication from two locations that can't be physically reached in the time available), and account activity inconsistent with normal user behavior (accessing files never accessed before, forwarding emails, etc.). Implementing real-time anomaly detection on your identity provider helps catch these patterns automatically.
Key Takeaways
- Vishing kits are sophisticated attack platforms that combine voice social engineering with real-time customizable phishing pages, enabling attackers to operate at scale with minimal technical skill
- Traditional MFA is not protection against vishing because it authenticates users, not applications—users can be manipulated into authenticating to fake services that look identical to real ones
- Phishing-resistant authentication (FIDO2/passkeys) is the only proven defense that stops vishing attacks at the protocol level, making impersonation impossible
- Victim profiling precedes attacks, with threat actors researching targets' applications, IT support numbers, and organizational structure before initiating contact
- Network controls and conditional access add significant friction by restricting where authentication can originate, forcing attackers to use more detectable infrastructure
- Detection and rapid response matter as much as prevention because some attacks will succeed despite defenses—focus on identifying compromises quickly and limiting damage
- The attack trend is clearly upward as kits become more available and organizations remain vulnerable—delay in deployment of defenses increases risk exposure
Related Articles
- LastPass Phishing Scam: How to Spot Fake Support Messages [2025]
- Most Spoofed Brands in Phishing Scams [2025]
- Password Security for UK Businesses: Beyond Weak Passwords [2025]
- Microsoft BitLocker Encryption Keys FBI Access [2025]
- The Human Paradox in Cyber Resilience: Why People Are Your Best Defense [2025]
- EU GDPR Fines Hit €1.2bn in 2025: What You Need to Know [2025]
![Vishing Kits Targeting SSO: Google, Microsoft, Okta at Risk [2025]](https://tryrunable.com/blog/vishing-kits-targeting-sso-google-microsoft-okta-at-risk-202/image-1-1769186257025.jpg)



