Microsoft Handed Over Bit Locker Keys to the FBI: Here's Why This Matters [2025]
It's one of those stories that sounds like fiction until you realize it's completely real. In January 2026, reports surfaced that Microsoft provided the FBI with recovery keys that unlocked encrypted hard drives belonging to suspects in a Pandemic Unemployment Assistance fraud case in Guam. Three laptops. Three sets of encryption keys. All handed over through what the company describes as a routine legal process.
But here's the problem: most people don't realize their encrypted data isn't actually encrypted against the people they should be most worried about.
This incident exposes something fundamental about how modern encryption works in the real world versus how we imagine it works in our heads. When you enable Bit Locker on a Windows machine, you get the sense that your data is locked down tight. Military-grade encryption. Unbreakable without your password. That's technically true—except Microsoft also gets a copy of the master key, and when law enforcement shows up with a warrant, Microsoft hands it over without much resistance.
The question isn't whether Microsoft did something illegal. They almost certainly didn't. They followed a warrant. The real question is whether storing encryption recovery keys in a centralized location controlled by a single corporation is a security architecture we should accept in 2025.
This article breaks down what actually happened, how Bit Locker encryption works, why Microsoft maintains these keys, what the security implications are, and what you should know about protecting your data in an era of cloud-based encryption management.
TL; DR
- Microsoft stores Bit Locker recovery keys by default in its cloud infrastructure, allowing the company to comply with law enforcement requests
- The FBI received 20+ Bit Locker keys per year from Microsoft on average, according to company disclosures
- Encryption backdoors aren't theoretical: This Guam case shows they're actively used in criminal investigations
- Your Bit Locker encryption protects against theft, not law enforcement with a valid warrant
- Security experts warn that centralized key storage creates systemic risk if Microsoft's infrastructure is compromised by hackers
Estimated data shows that regular users would constitute the majority of affected individuals in a BitLocker key breach, highlighting the widespread impact beyond high-profile targets.
What Actually Happened: The Guam Pandemic Unemployment Assistance Case
In late 2025, the FBI was investigating suspected fraud related to the Pandemic Unemployment Assistance program in Guam. The program distributed federal unemployment benefits during the pandemic, and like many federal relief programs, it became a target for fraudsters who filed false claims or manufactured fake documentation.
The investigation identified three suspects and seized their laptops as evidence. All three devices were encrypted with Bit Locker, which is now enabled by default on Windows machines with certain system configurations. Rather than spend months cracking the encryption, the FBI did something simpler: they got a warrant and served it on Microsoft.
Microsoft complied. Within weeks, the company provided the FBI with the Bit Locker recovery keys needed to decrypt all three hard drives. The investigation could proceed. Evidence was accessible. Nobody broke any laws.
On the surface, it's a straightforward law enforcement success story. But the mechanics underneath reveal something much more complicated about how encryption actually works when corporations control the keys.
The case wasn't unique. Pacific Daily News and Kandit News, local Guam news outlets, reported that this wasn't an isolated incident. Law enforcement had pursued similar warrants before. And Microsoft later confirmed to Forbes that it receives approximately 20 Bit Locker recovery key requests per year on average from law enforcement agencies.
Twenty per year. That's about once every two weeks somewhere in the United States (or potentially international jurisdictions). Each request represents a warrant served on Microsoft and a copy of someone's encryption key handed over to law enforcement.
Most people don't know this is happening. Most people don't know it's even possible.

Estimated data shows that fraud in the Pandemic Unemployment Assistance program could account for 36% to 95% of all payments, highlighting significant vulnerabilities.
How Bit Locker Encryption Works: The Architecture Behind the Controversy
Bit Locker is Microsoft's full-disk encryption technology, and it's been built into Windows since 2007. The name is straightforward: it locks your bits. Encrypt the entire drive, and nothing is readable without the decryption key.
When you enable Bit Locker on a Windows machine, several things happen in sequence. The operating system generates an encryption key, typically a 256-bit AES key (that's advanced encryption standard, the same encryption standard used by the U. S. government for classified information). This key is then used to encrypt every single file, every single piece of data on the drive.
Without this key, a stolen laptop is essentially worthless. The hard drive might be physically intact, but the data on it is unreadable gibberish. You could plug that drive into any other computer, and you'd see encrypted sectors. No files. No folders. No access to anything.
That's where recovery keys come in. A recovery key is essentially a backup copy of the master encryption key. If something goes wrong, if you forget your password, if the drive gets corrupted, you can use the recovery key to regain access. It's a safety mechanism designed to prevent you from being locked out of your own data.
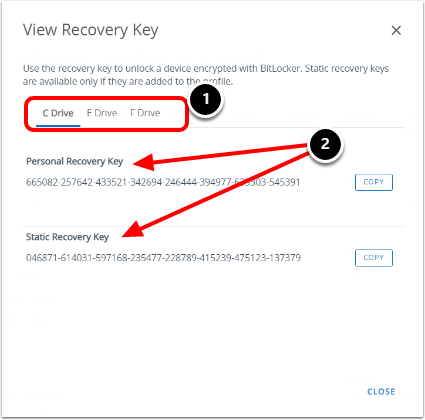
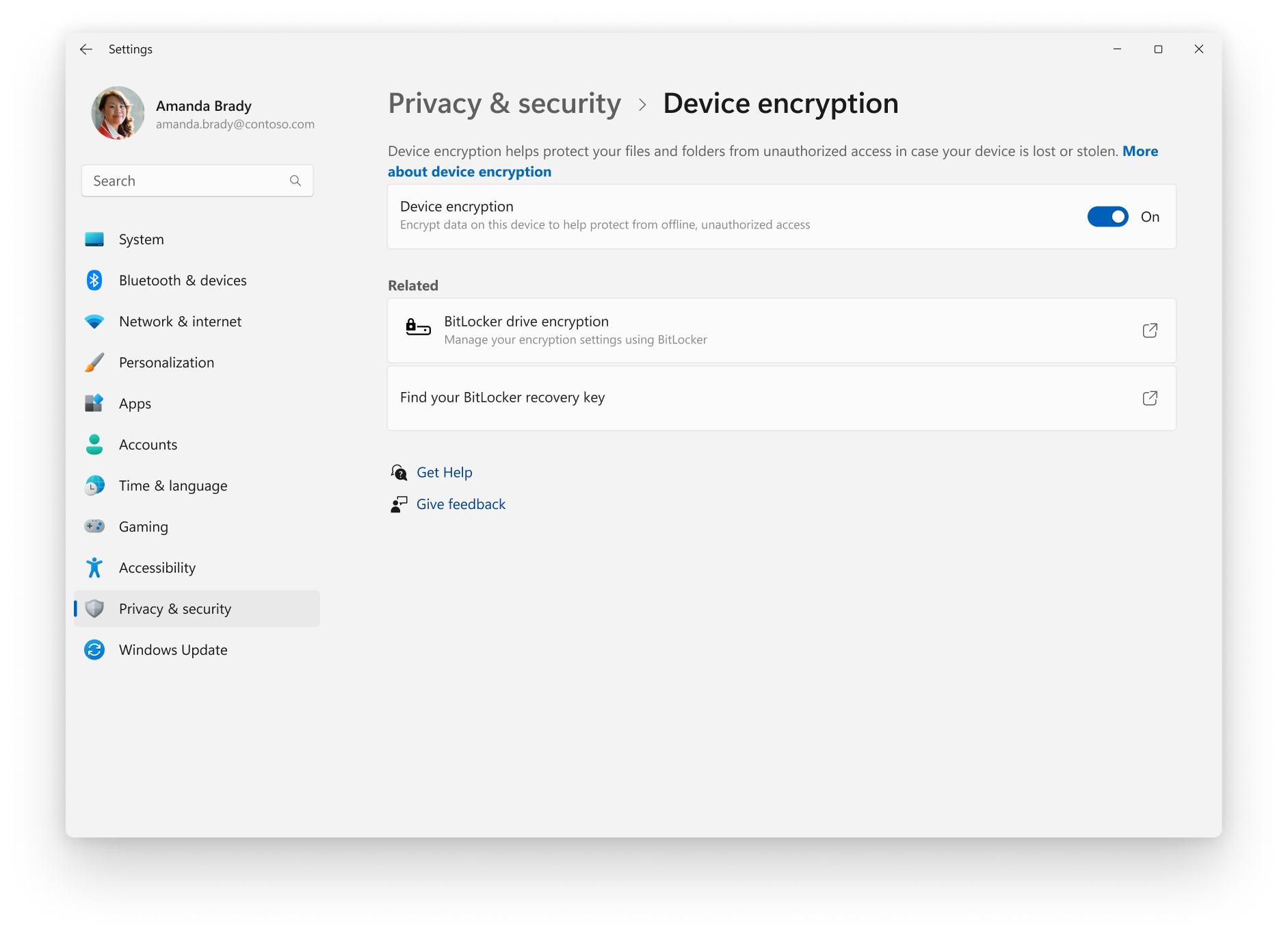
Microsoft's design choice was to store these recovery keys in the cloud. Specifically, they're stored on Microsoft's servers, associated with your Microsoft account. When you enable Bit Locker on a modern Windows machine with a Microsoft account, the recovery key gets automatically uploaded. You can manually back it up to a USB drive or print it, but by default, Microsoft has a copy.
The reasoning was straightforward: if you lose your password and lose the physical recovery key, at least Microsoft can help you get back into your own data. It's a customer service feature.
But it's also a master key in the hands of a corporation, accessible to anyone who can legally compel Microsoft to provide it.
The encryption itself is strong. 256-bit AES is not breakable through brute force. The U. S. government uses it for classified information. But the encryption is only as strong as the key management. If the key is stored somewhere accessible to law enforcement, the encryption becomes more of a deterrent against casual data theft than a barrier against determined legal processes.
There's a critical distinction here. Bit Locker protects your data in several scenarios: against someone stealing your laptop and trying to boot it up. Against someone pulling the hard drive out and plugging it into another computer. Against thieves, hackers, data brokers, and criminals.
It does not protect your data against the U. S. government with a warrant. The encryption becomes theoretically perfect but practically irrelevant when Microsoft has the key and law enforcement has legal authority to request it.

Why Microsoft Stores Recovery Keys: The Business and Legal Architecture
Understanding Microsoft's decision to store recovery keys requires understanding the balance between security, customer service, and legal obligations.
First, the customer service angle. If you're a regular consumer using Windows, you're probably not a cryptography expert. You might enable Bit Locker because it sounds like a good security practice (and it is), but then six months later, you forget your password. Or your drive gets corrupted. Or you're locked out for some other reason. Without a recovery mechanism, you've got a brick. A computer that won't boot. Data that's inaccessible.
Microsoft's approach was to be the recovery mechanism. They store the key. If you ever need it, you log into your Microsoft account, and you can access the recovery key. It's convenient. It's customer-friendly. And statistically, most of that stored data will never need to be accessed except by the user who created it.
Second, the liability angle. If Microsoft didn't store recovery keys and someone lost access to critical data, lawsuits would follow. That's the reality of consumer software. Microsoft found that storing keys—with appropriate security measures—was better than the alternative of never being able to help customers recover from encryption lockouts.
Third, and most relevant to this discussion, the legal framework. Microsoft is a U. S. corporation. When the FBI or any law enforcement agency serves a warrant, Microsoft has legal obligations to comply. The company can't simply refuse because it's inconvenient or because it affects privacy. If they have the keys and there's a valid warrant, they have to hand them over.
Microsoft hasn't hidden this. In fact, the company publishes transparency reports detailing the number of government requests it receives. For Bit Locker recovery keys specifically, Microsoft told Forbes that it averages about 20 requests per year. That number has been stable for several years.
But here's where it gets interesting. Different jurisdictions have different standards for what constitutes a valid warrant. The U. S. requires a warrant based on probable cause. European countries often have different standards. And overseas, the situation becomes murkier. If Microsoft is storing encryption keys for customers around the world, those keys are accessible to whatever legal process applies in that jurisdiction.
The company has also made a calculation about risk. The probability that law enforcement will request your specific Bit Locker key is low. The probability that you'll need customer service recovery is higher. And the probability that hackers will breach Microsoft specifically to steal Bit Locker keys is lower than the probability that you'll forget your password.
From a purely mathematical standpoint, centralized key storage makes sense. It optimizes for the most common scenario (customer service) at the expense of rare scenarios (law enforcement requests) and very rare scenarios (sophisticated hacks targeting Microsoft's infrastructure specifically).
But security experts argue that the math is incomplete. It assumes Microsoft's infrastructure is secure. It assumes law enforcement only requests keys in legitimate cases. And it assumes that corporate control of encryption keys won't expand in scope.
Microsoft receives approximately 20 government requests for BitLocker recovery keys annually, demonstrating a stable trend over recent years.
The Technical Reality: Encryption Keys, Cloud Infrastructure, and Warrant Compliance
When Microsoft stores your Bit Locker recovery key, it's not like the company is writing it down on paper and filing it in a cabinet. It's stored in encrypted form in Microsoft's Azure infrastructure—specifically, their cloud storage systems that power One Drive, Outlook, and other Microsoft services.
The keys themselves are encrypted. Microsoft doesn't store the Bit Locker key in plain text sitting in a database somewhere. Instead, it's encrypted with another layer of encryption, protected by additional keys stored in Hardware Security Modules (HSMs). This is actually quite sophisticated from a security architecture perspective.
But when law enforcement serves a warrant, it doesn't matter how encrypted the key is. Microsoft has the means to decrypt it, and they're legally obligated to do so. The warrant compels the company to produce the key in a format readable by law enforcement.
Here's how the process typically works:
- Law enforcement obtains a warrant from a federal judge based on probable cause that a crime has been committed
- The warrant is served on Microsoft, requesting the Bit Locker recovery key for a specific device, identified by some combination of device ID, user account, serial number, or device identifier
- Microsoft receives the warrant through its legal department and verifies it's valid
- The appropriate team at Microsoft accesses the encrypted key storage, decrypts the key using authorized access, and provides it to law enforcement
- Law enforcement uses the key to decrypt the suspect's hard drive
- The evidence becomes accessible and can be analyzed
The entire process is legal, documented, and defensible. Microsoft isn't breaking any laws. Law enforcement isn't breaking any laws. But the technical architecture creates a situation where encryption—which is supposed to protect your data—becomes transparent when the government wants to look.
Microsoft's encryption key management does include internal safeguards. Access is logged. Multiple people typically need to approve key releases. The company maintains detailed records of who accessed what and when. But these are process controls, not technical controls. They prevent accidental disclosure but not intentional, lawful disclosure.
The company has also implemented rate limiting and pattern detection on key requests. If someone tries to request thousands of Bit Locker keys, it gets flagged. If requests come from unusual IP addresses or patterns, they trigger additional verification steps. But a properly issued warrant will pass through all these checks.

The Security Expert Perspective: Why Matthew Green and Cryptography Researchers Are Concerned
Matthew Green is a cryptography professor at Johns Hopkins University and one of the most respected voices in computer security research. When the Bit Locker warrant story broke, Green made a pointed observation on Bluesky: "It's 2026 and these concerns have been known for years. Microsoft's inability to secure critical customer keys is starting to make it an outlier from the rest of the industry."
That's worth unpacking, because it highlights the core security concern: Microsoft isn't just creating a backdoor for law enforcement (which is their choice and, arguably, legally necessary). They're also creating a potential backdoor for anyone who can compromise Microsoft's infrastructure.
Why is this a concern in 2026? Because Microsoft has been hacked before. In 2023, a researcher discovered that Chinese state-sponsored hackers had accessed Microsoft's servers and stolen source code. In 2024, hackers compromised Microsoft Exchange servers through a zero-day vulnerability. And in 2022, the company discovered that a contractor's credentials had been stolen, potentially giving bad actors access to internal systems.
None of these breaches specifically exposed Bit Locker recovery keys—at least not publicly. But they demonstrated that Microsoft's infrastructure, despite being well-defended, is not impenetrable. There are always gaps. There are always ways in.
From a threat model perspective, if you're a sophisticated attacker (nation-state, criminal organization, well-funded hackers), you have two paths to accessing someone's Bit Locker key:
- Break into Microsoft's infrastructure and steal the key directly
- Compromise law enforcement records after they've received the key from Microsoft
Both are theoretically possible. Both are better defended than trying to break the encryption algorithm itself. And both are more practical than physically stealing the laptop and trying to brute-force the password.
Green's criticism is that Microsoft should be moving toward a model where the company doesn't have copies of recovery keys at all. Instead, recovery keys could be:
- Stored only on the user's device, with backup only to encrypted form on the user's own cloud storage (that Microsoft can't decrypt)
- Managed through hardware security modules that the user controls
- Backed up to services like Apple's i Cloud Keychain, which have different security models
- Never centrally stored by Microsoft at all
Apple, for comparison, uses a different approach with File Vault encryption on mac OS. Recovery keys can be stored on i Cloud, but Apple doesn't maintain a centralized database of all recovery keys. The keys are tied to the user's i Cloud account encryption, which has a different security model. This makes it somewhat harder (but not impossible) for law enforcement to request specific keys.
The broader point that Green and other security researchers are making is that there's a difference between building products that comply with lawful requests and building products where the architecture assumes law enforcement access is normal. Microsoft's Bit Locker design leans toward the latter.
This isn't about whether Microsoft should comply with warrants. Of course they should. This is about whether the architecture should centralize recovery keys in the first place. From a pure security perspective, distributed key management—where keys are only stored where the user controls them—is more robust.
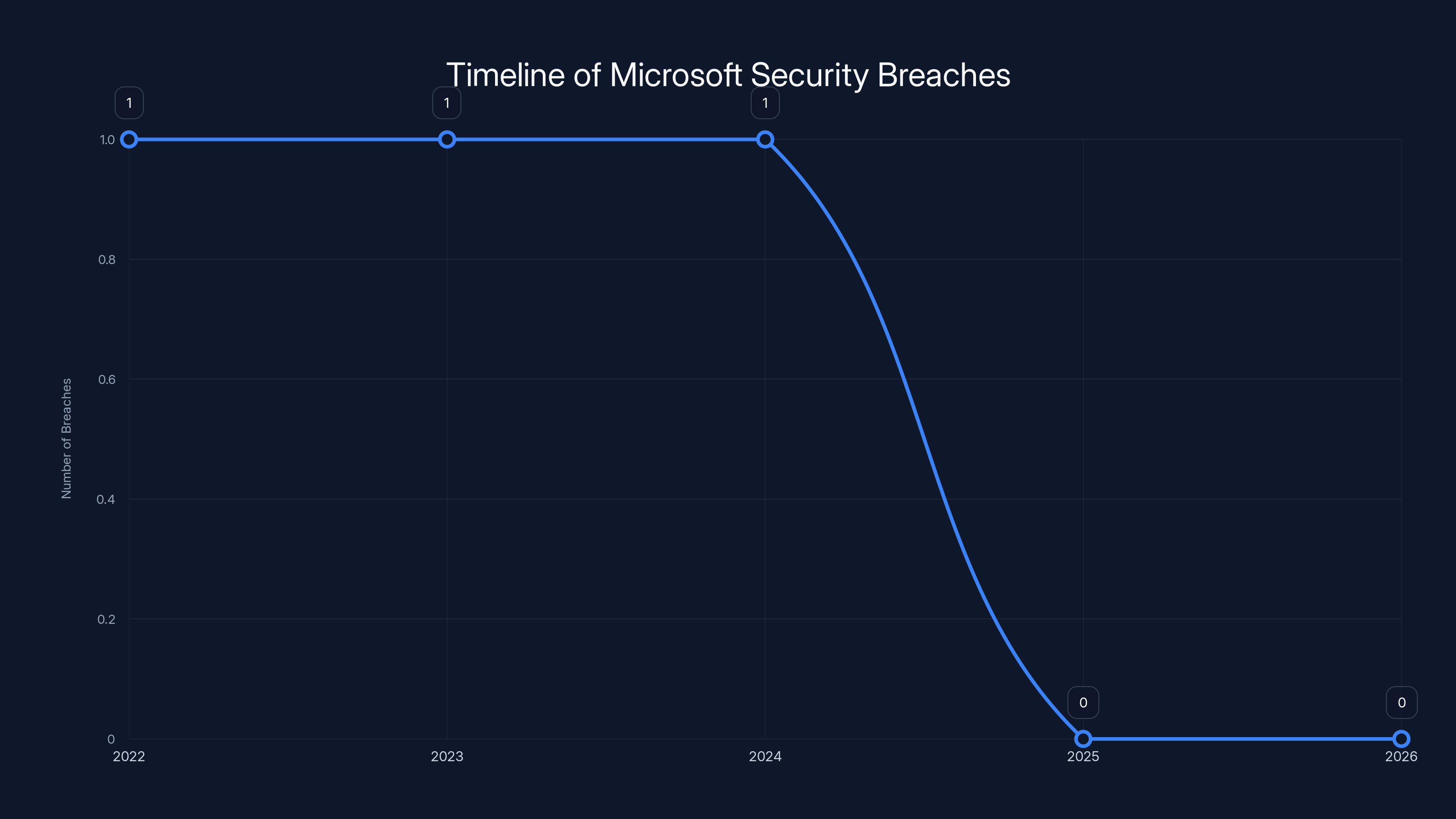
Microsoft faced significant security breaches in 2022, 2023, and 2024, highlighting ongoing vulnerabilities. Estimated data.
Comparing Bit Locker to Other Encryption Solutions: How Does the Key Management Stack Up?
Bit Locker isn't the only full-disk encryption option available on Windows. There are third-party solutions, open-source alternatives, and different architectural approaches. Understanding how Bit Locker compares to these alternatives illustrates why the key storage issue matters.
Vera Crypt is one of the most popular alternatives to Bit Locker, and it's open-source and free. Vera Crypt does not have any online key storage. There's no cloud backup. You generate a key, you store it locally, and Vera Crypt uses it to encrypt your drive. If you lose the key, you're out of luck—but nobody else has it either.
The trade-off is obvious. Vera Crypt is less convenient. If you forget your password, there's no recovery mechanism. If you want to access encrypted data from another device, you need to manage the key transfer manually. But from a security perspective, you have absolute control.
LUKS (Linux Unified Key Setup) is the standard encryption framework on Linux distributions. Like Vera Crypt, LUKS stores keys locally on the device. There's no centralized key storage. And like Vera Crypt, this means recovery requires physical access and key management.
Windows Encrypted File System (EFS) is an older Microsoft encryption technology, predating Bit Locker. EFS works at the file level rather than the disk level, and keys are stored locally on the device. It's less commonly used now, but it demonstrates that Microsoft knows how to design encryption where the user controls the keys.
File Vault on mac OS is Apple's equivalent to Bit Locker. File Vault also allows recovery keys to be stored on i Cloud, but the architecture is different. Apple's recovery keys are tied to the user's i Cloud Keychain security model, which uses end-to-end encryption. Apple claims it cannot access user keys even if served with a warrant (though this claim is disputed by security researchers).
The comparison reveals something important: Bit Locker isn't inherently flawed because it's centralized. Centralized key storage can be secure if properly managed. The issue is that centralization creates a single point of failure. If Microsoft's infrastructure is breached, every key is potentially compromised. If a legal process becomes abusive, access is theoretically unlimited.
The alternative to centralized key management is distributed key management, where each user controls their own keys. This is more complex, less convenient, and creates recovery challenges. But it's also more secure against the specific threats that matter to people concerned about privacy.
Microsoft could, theoretically, redesign Bit Locker to offer options. Some users might opt for convenience (cloud recovery key backup). Others might opt for security (local-only key management). This is how many modern security-conscious services work—they let users choose their own threat model.
But Bit Locker's current design assumes everyone wants the same thing: convenience with Microsoft as the safety net.
The Legal Framework: What Warrants Actually Require, and When Microsoft Must Comply
The Bit Locker situation exists within a specific legal framework that's worth understanding, especially if you live in the United States or any country with similar law enforcement structures.
In the United States, law enforcement must obtain a warrant before accessing encrypted data on a device. The warrant is issued by a judge and is based on probable cause that a crime has been committed. This is the Fourth Amendment in action, though the Fourth Amendment's protections for digital data are still being actively litigated and redefined.
When the FBI wanted to access the three laptops in the Guam case, they likely followed this process:
- Agents identified the three suspects and the specific devices
- Agents presented evidence to a federal judge of probable cause that those devices contained evidence of a crime
- The judge issued a warrant specifically authorizing the seizure and search of those devices
- The warrant was served on Microsoft (or Microsoft was notified that the devices belonged to certain accounts)
- Microsoft's legal team reviewed the warrant and verified it was legitimate
- Microsoft provided the recovery keys
- Law enforcement decrypted the drives
This is legal and constitutional. In fact, law enforcement would argue it's necessary and proper. Without the ability to access encrypted devices, criminal investigations become much harder. Would the U. S. allow Microsoft to refuse cooperation? Almost certainly not.
But here's where the legal landscape gets fuzzy: different jurisdictions have different standards.
In the European Union, the GDPR and other privacy regulations create different frameworks. Serving a warrant on Microsoft for data about European citizens is theoretically possible, but it's more complicated because European privacy law is stronger than U. S. law. There are more procedural protections. There are more requirements for narrowness and specificity.
In countries like China or Russia, the situation is entirely different. These countries don't necessarily require warrants. Governments can demand access to encryption keys as a matter of national security or law enforcement, with minimal oversight or judicial process.
From Microsoft's perspective, the company has to serve all these different jurisdictions. The technical infrastructure that stores Bit Locker recovery keys is the same whether a request comes from the U. S. FBI or the Chinese government. The legal standards are different, but the access mechanism is similar.
This creates a potential problem: if Microsoft stores keys in a way that complies with U. S. warrants, is the company also implicitly allowing access to those keys under different legal standards from other countries? This is an unresolved question in tech law.
Microsoft has also had to navigate the thorny issue of government overreach. The company publishes transparency reports detailing how many government requests it receives, how many it complies with, and how many it challenges. For Bit Locker keys specifically, the company claims to evaluate each request carefully.
But there's limited public visibility into what that evaluation process looks like. Microsoft says it refuses requests that don't include proper legal process, but the number of refused Bit Locker key requests is essentially zero. Either every request is perfectly valid (possible, but statistically unlikely), or the company's evaluation process isn't very stringent (more plausible), or refused requests are simply never reported (also plausible).
The legal framework protects law enforcement but not necessarily the people whose data is being accessed. A warrant based on probable cause is a relatively low standard, and once issued, it doesn't expire. If someone's Bit Locker key is accessed, they're typically not notified unless the data is used in prosecution.
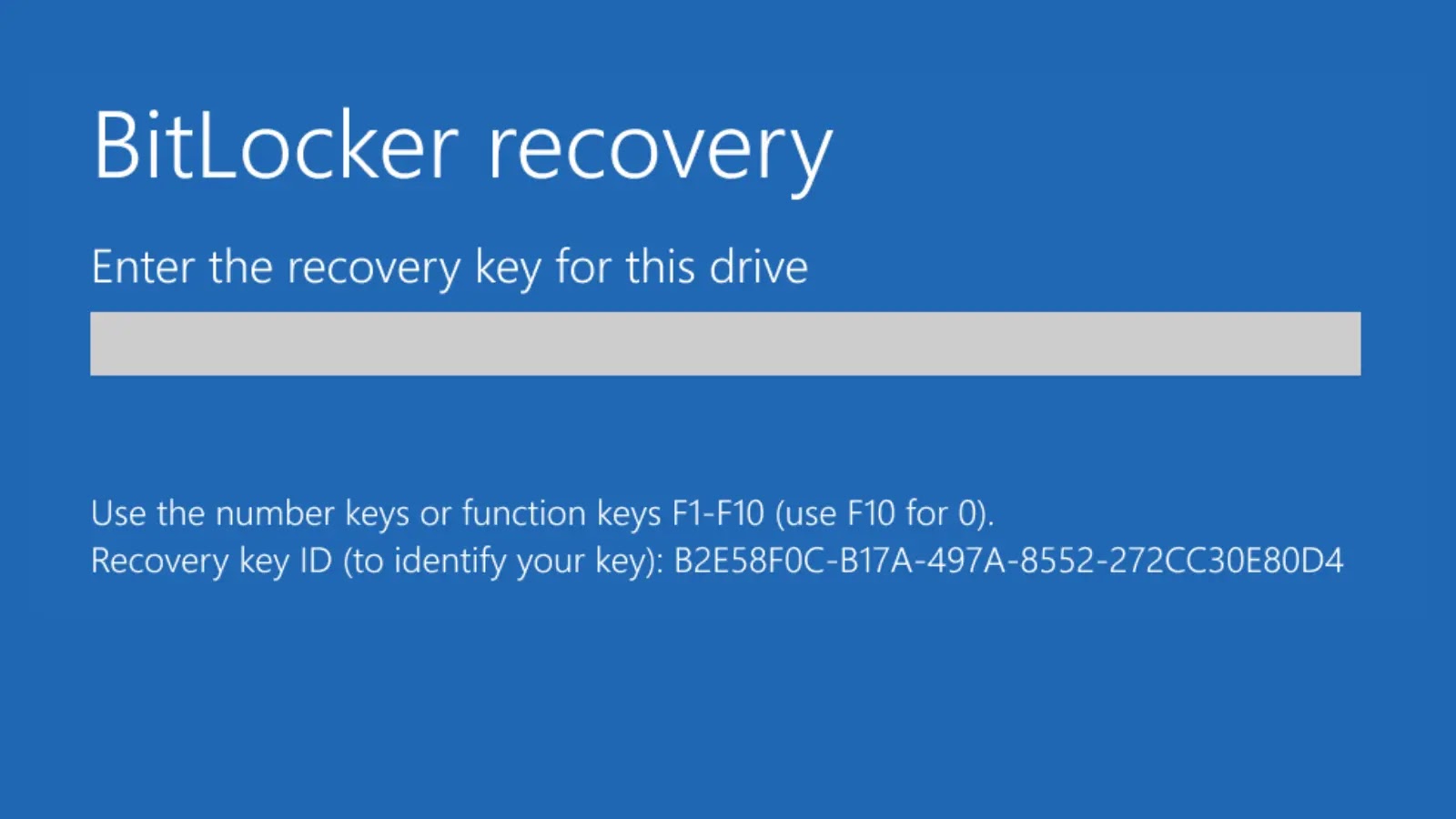
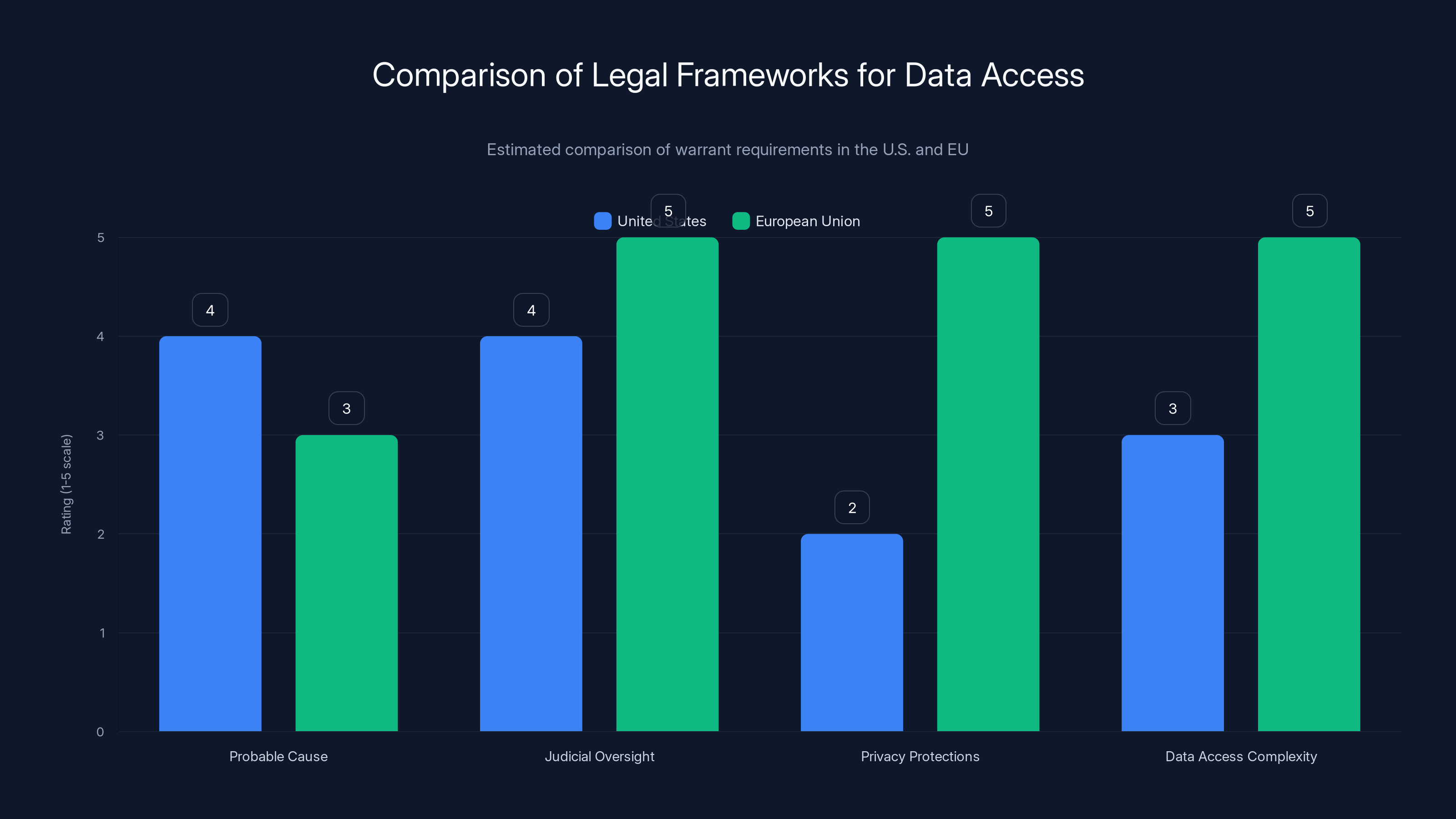
The EU generally has stronger privacy protections and more complex data access procedures compared to the U.S., which emphasizes probable cause and judicial oversight. Estimated data.
What Happens to Your Data After Law Enforcement Gets Access: The Chain of Custody Problem
Once the FBI obtained the Bit Locker recovery keys and decrypted the three laptops in the Guam case, what happened next? That's actually an important question that often gets overlooked.
The data on those laptops became evidence in a criminal investigation. Law enforcement followed chain of custody procedures, documented what they found, and presumably built a case against the suspects. The data they found was admissible in court because they obtained it through proper legal process (the warrant).
But here's what's less clear: what happens to that decrypted data after the investigation? Is it stored? Is it archived? Can it be accessed later by other law enforcement agencies? Can it be shared as part of inter-agency intelligence sharing?
Once encryption is bypassed, the data is vulnerable. It's no longer protected by the encryption that the suspect relied on. It's now in the hands of the government, subject to government data management standards, which are sometimes less rigorous than we'd hope.
There have been documented cases of law enforcement mishandling sensitive data. Data breaches from law enforcement agencies. Unauthorized access by officers. The data that's protected by encryption on your device might be less protected once it's copied to government servers.
This is actually one of the lesser-discussed but important consequences of encryption backdoors. It's not just about law enforcement having access. It's about what happens to the data after they have it.
The Broader Encryption Debate: Backdoors, Lawful Access, and the Technical Impossibility Problem
The Bit Locker recovery key story is actually part of a much larger, ongoing debate in technology and policy about encryption backdoors.
Governments worldwide want the ability to access encrypted communications and data in criminal and national security investigations. That's a reasonable law enforcement goal. Crime and terrorism are real problems, and encryption makes investigating those problems harder.
Technology companies and security researchers argue that building intentional backdoors in encryption systems makes everyone less secure. This is the technical position that Matthew Green articulated. If you design encryption with a backdoor specifically for law enforcement, you've created a vulnerability that might also be exploitable by criminals, hackers, or hostile governments.
The FBI has repeatedly pushed for "lawful access" solutions. After the San Bernardino shooting in 2015, the FBI asked Apple to build a backdoor into i Phone encryption so law enforcement could access the shooter's phone. Apple refused. The FBI eventually hired a private security firm to breach the phone without Apple's help.
The incident highlighted the core tension: law enforcement wants guaranteed access. Technologists argue that guaranteed access doesn't exist in a secure system.
Microsoft's approach with Bit Locker is actually a pragmatic middle ground. Instead of building backdoors into the encryption algorithm itself (which would weaken encryption for everyone), Microsoft created a backdoor in the key management system. The encryption stays strong. The keys are strong. But the keys are stored somewhere accessible to law enforcement.
This satisfies law enforcement's immediate needs while maintaining encryption strength. But it creates a security problem: if the key storage system is compromised, encryption becomes meaningless.
From a policy perspective, there's an ongoing argument about whether law enforcement access to encryption keys should be required by law. Some politicians and law enforcement officials argue that companies should be legally required to provide plaintext access or keys when served with a warrant. Others argue that this creates security risks that are unacceptable.
The debate has been ongoing since the 1990s and shows no signs of resolution. Countries have reached different conclusions. China requires encryption backdoors. The EU's current position is unclear and evolving. The U. S. hasn't mandated backdoors but expects voluntary cooperation from companies.
Microsoft's position is to comply with legal requests while maintaining the security of its products and services. That's a reasonable corporate position. But it does mean that users who rely on Bit Locker should understand that their encryption is not protection against law enforcement with proper legal authority.
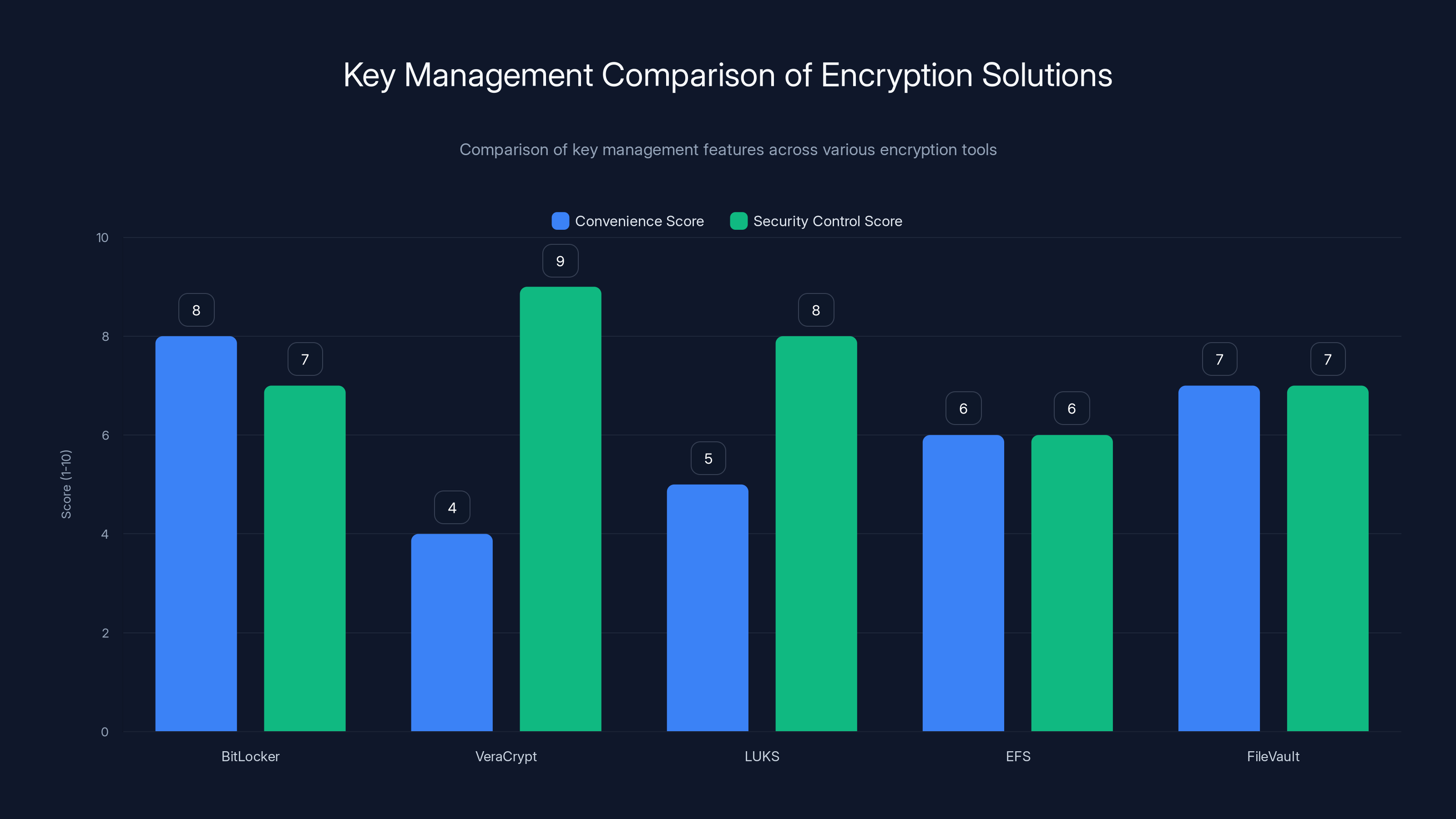
BitLocker offers a balanced approach with good convenience and security control. VeraCrypt excels in security control but lacks convenience. FileVault provides a good balance with its iCloud integration. (Estimated data)
The Data Security Risk: What If Microsoft's Infrastructure Gets Breached?
Here's the scenario that keeps security experts awake at night: What if attackers compromise Microsoft's key storage infrastructure? Not to steal data from millions of users, but specifically to get Bit Locker recovery keys.
This isn't hypothetical. We know sophisticated attackers target technology companies specifically to access sensitive data or systems. Nation-states have done it. Criminal organizations have done it. In 2023, Microsoft disclosed that a Chinese state-sponsored group called Storm-0558 had accessed internal Microsoft systems, including source code repositories.
That breach didn't specifically target Bit Locker keys (as far as we know), but it demonstrated that determined attackers with nation-state resources can get into Microsoft's infrastructure.
If an attacker obtained a copy of Bit Locker recovery keys, they'd have access to encrypted hard drives belonging to:
- Corporate executives
- Government officials
- Activists and journalists
- Regular people just using Windows with Bit Locker
The attacker wouldn't need to know which specific keys were valuable. They'd have them all. They could decrypted any Bit Locker drive from any affected user.
This is the "concentrated risk" problem. By storing all recovery keys in one place, Microsoft created a single point of failure. If that point fails, the impact is massive.
Microsoft does have security measures in place. Keys are encrypted at rest. Access is logged and monitored. Multiple people need to authorize access. But these are defenses in depth. They increase the difficulty of a breach but don't eliminate the possibility.
And here's the problem: even if Microsoft's defenses are 99.9% effective, that's still not enough when the potential impact is so large. If there's a 0.1% annual risk of a successful breach, and millions of users are affected, the expected value of that risk is very high.
From a risk management perspective, the question becomes: Is the convenience of cloud recovery key backup worth the concentration of risk? Most security professionals would say no, at least not for sensitive devices or high-value targets.
This is why organizations handling sensitive information often disable cloud key backup for Bit Locker and manage keys locally or through hardware security modules they control.
Real-World Implications: What This Means for Different User Groups
The Bit Locker recovery key access story has different implications depending on who you are and what you're using your device for.
For regular consumers: The practical impact is minimal. You're probably not under criminal investigation. The probability that law enforcement will serve a warrant for your specific Bit Locker key is very low. Bit Locker still provides excellent protection against device theft, lost computers, and unauthorized physical access. For most people, the convenience of cloud recovery outweighs the theoretical risk of law enforcement access.
For business users: Organizations should have a clear policy on Bit Locker key management. Is cloud backup enabled? Where are recovery keys stored? Who has access to them? Depending on the company's industry and sensitivity of data, the right answer might be local key management or dedicated hardware security modules.
For activists, journalists, and people in high-risk situations: Cloud-backed Bit Locker keys are not a reliable security mechanism. If you're at serious risk of government surveillance or law enforcement action, you need encryption that you control completely. That might mean using Vera Crypt instead of Bit Locker, or using operating systems with different encryption models.
For people in countries with authoritarian governments: This is the highest-risk scenario. If you're in a country where government surveillance is aggressive and legal protections are weak, storing encryption keys with any U. S. company might be dangerous. The keys could be accessed through legal processes that aren't as protective as U. S. warrants.
For law enforcement and government agencies: The ability to access encrypted devices through legal process is valuable, and the existence of centralized key management makes that process easier.
Each group has different threat models and different risk tolerance. The issue with Bit Locker is that Microsoft has designed a system that works well for some groups but creates risks for others.

Alternative Approaches: How Could Encryption and Law Enforcement Access Be Balanced?
If Microsoft wanted to redesign Bit Locker to balance security and law enforcement access differently, what alternatives exist?
Option 1: Local Key Management Only Store recovery keys only on the user's device or on physical media the user controls. This provides maximum security but eliminates law enforcement convenience. Microsoft would need to explain to users that if they lose their password and lose the recovery key, their data is permanently inaccessible.
Option 2: Multi-Party Recovery Require multiple parties to approve recovery key access. For example, a Bit Locker key might be split between Microsoft and the user, with both parties needing to approve recovery. This reduces the risk of a single bad actor having unilateral access. But it increases complexity significantly.
Option 3: Time-Limited Access Recovery keys could be stored, but access could be limited to a specific time window. A warrant is valid for a specific case, so the key access could expire after the investigation concludes. This would require more sophisticated infrastructure but would reduce the window of vulnerability.
Option 4: Hardware Token Management Recovery keys could be issued to users on hardware tokens (USB devices or similar) that only the user possesses. Law enforcement wanting to access encrypted data would still need the physical token. This requires users to manage the physical hardware but provides strong security.
Option 5: Zero-Knowledge Recovery Microsoft could implement recovery key mechanisms that don't require the company to have access to plaintext keys. This is technically complex (it involves cryptographic commitments and zero-knowledge proofs) but is possible. Recovery would work, but Microsoft wouldn't actually have the key.
Microsoft has chosen the current approach because it balances competing priorities: security, convenience, customer service, and legal compliance. Other companies have chosen differently. Apple's File Vault uses a different model. Linux distributions often use local-only keys. Different choices reflect different values.
The Future: Are Encryption Key Escrow Requirements Coming to Windows?
As of 2025, Microsoft's Bit Locker key storage and law enforcement access are voluntary and based on legal warrants. But will that always be the case?
There's ongoing political pressure in many countries for technology companies to build encryption backdoors or key escrow mechanisms as a matter of law. The European Union has been debating this. The United Kingdom passed laws suggesting it could require tech companies to provide access to encrypted data. China has already mandated encryption backdoors.
If such requirements were imposed on Microsoft in the United States or other major markets, the company would face a choice: comply with the law or stop operating in that country. There's little doubt they'd comply.
This could mean:
- Mandatory escrow of all Bit Locker recovery keys in a government-controlled database
- More frequent law enforcement access without the same legal protections (warrants becoming less necessary)
- International complications where keys stored to comply with U. S. law are also accessible to other governments
The debate is far from settled. Technology companies, civil liberties groups, and security researchers continue to argue against encryption backdoors. Law enforcement and government agencies argue for them. Each new crime or terrorist attack reignites the debate.
For now, Bit Locker remains a product where Microsoft has chosen to store keys in a way that complies with law enforcement but isn't mandated by law. That could change if legislation changes.

Practical Steps: How to Protect Your Data from Bit Locker Key Access
If you want to reduce the risk that law enforcement could access your Bit Locker-encrypted drives through Microsoft-held recovery keys, here are practical steps:
Step 1: Disable Cloud Key Backup During Bit Locker setup, choose not to back up the recovery key to your Microsoft account. Instead, manually save the key to a USB drive or print it and store it physically.
Step 2: Use a Passphrase Enable Bit Locker with a strong passphrase. The passphrase is separate from the recovery key. Even if someone has the recovery key, they'd need to know the passphrase or have the TPM device to boot the system.
Step 3: Store Recovery Keys Securely If you have a recovery key, treat it like a password. Store it somewhere secure. Don't write it down in an easily discoverable place. Consider using a password manager to store it.
Step 4: Consider Alternative Encryption For highly sensitive data, consider using Vera Crypt or other encryption tools that don't involve cloud key storage. These have less convenience but more control.
Step 5: Use Strong Windows Passwords Bit Locker is only as strong as your logon password. Use a strong, unique password. Biometric authentication (fingerprint, face recognition) is convenient but not as secure as a strong password.
Step 6: Enable TPM and BIOS Passwords Bit Locker works with TPM (Trusted Platform Module) chips. You can also set a BIOS password to prevent someone from booting from alternative media or accessing the system at a low level.
Step 7: Monitor Your Microsoft Account If your recovery key is backed up to Microsoft, monitor your account security. Use two-factor authentication. Check your Microsoft account activity for unauthorized access.
Step 8: Document Your Setup If you're disabling cloud backup and managing keys locally, document exactly what you did and where you stored the key so you can access it later if needed.

Institutional Response: What Companies and Organizations Are Doing
Large organizations with sensitive data have largely moved beyond relying on individual Bit Locker cloud backup. Instead, they've implemented centralized key management systems.
Microsoft Active Directory Key Management: Organizations using Active Directory can implement Group Policy settings that control how Bit Locker keys are managed. Keys can be stored in Active Directory instead of the cloud, giving the organization control.
Hardware Security Modules (HSMs): Sensitive organizations often use dedicated HSMs to manage encryption keys. These are hardened devices designed specifically for key security. Keys never leave the HSM in plaintext form.
Third-Party Key Management Solutions: Companies like Thales, Gemalto, and others offer enterprise key management platforms that integrate with Bit Locker and provide auditing, access control, and regulatory compliance features.
Volume Shadow Copy Monitoring: Some organizations disable the ability to take volume shadow copies or system restore points on encrypted drives, reducing opportunities for anyone to access key material through backup mechanisms.
Multi-Factor Bit Locker: Using Bit Locker with smart cards or hardware tokens in addition to passwords provides additional security layers.
For organizations in regulated industries (healthcare, finance, government), these kinds of key management implementations are often required by compliance frameworks like HIPAA, PCI-DSS, or NIST standards.
The Transparency Question: Should Microsoft Publish More Information About Bit Locker Key Requests?
Microsoft does publish a transparency report detailing government requests for customer data and information. The report includes categories like:
- Law enforcement requests
- National security letters
- Government preservation requests
- Total accounts affected
- Requests Microsoft declined
But the report doesn't specifically break down Bit Locker recovery key requests. It's lumped into broader categories of legal requests.
Security advocates argue Microsoft should publish more detailed information:
- How many Bit Locker recovery key requests does Microsoft receive per year, broken down by country?
- How many requests does Microsoft decline?
- What percentage of Bit Locker users have cloud backup enabled versus local-only backup?
- What's the average time between request and compliance?
More detailed transparency would help researchers understand the scale of the issue and help users make informed decisions about whether to use cloud key backup.
Microsoft's position is probably that such detailed reporting could compromise law enforcement operations or individual investigations. Publishing that the FBI requested Bit Locker keys for devices in a specific geographic area could tip off suspects that they're under investigation.
But there's a middle ground. Microsoft could publish aggregate numbers without details tied to specific investigations.
FAQ
What is Bit Locker and how does it protect my data?
Bit Locker is Microsoft's full-disk encryption technology that encrypts all data on a Windows drive using 256-bit AES encryption. This means if your laptop is stolen or powered off, the data is unreadable without the encryption key or password. Bit Locker protects against physical theft and unauthorized access, making stolen devices functionally worthless to attackers who can't access the user's password or recovery key.
Why does Microsoft store Bit Locker recovery keys in the cloud?
Microsoft stores recovery keys in the cloud to help users who forget their password or lose access to their device. If you enable Bit Locker and then forget your password, Microsoft can help you recover access to your own data through your Microsoft account. This is a customer service feature designed to prevent users from being permanently locked out of their own encrypted drives.
Can law enforcement access my encrypted drive through Bit Locker recovery keys?
Yes, when law enforcement serves a proper warrant on Microsoft, the company is legally obligated to provide the Bit Locker recovery key associated with a user's device. This means law enforcement can decrypt the drive without needing to break the encryption algorithm. The warrant requires probable cause that a crime has been committed, but once issued, law enforcement can access your Bit Locker-encrypted data.
How can I prevent Microsoft from storing my Bit Locker recovery key?
During Bit Locker setup on Windows, you can choose not to back up the recovery key to your Microsoft account. Instead, you can save it to a USB drive, print it, or store it elsewhere. If you disable cloud backup, Microsoft won't have a copy of your recovery key, though this means you won't be able to use Microsoft's recovery service if you forget your password.
Is Bit Locker encryption still secure if Microsoft has the recovery key?
Bit Locker encryption itself is secure—256-bit AES is mathematically sound and not breakable. However, encryption only protects against unauthorized access. Law enforcement with a valid warrant is authorized access. So while your Bit Locker encryption protects against theft and unauthorized access, it doesn't protect against law enforcement with proper legal authority.
What's the difference between Bit Locker and other encryption options like Vera Crypt?
Bit Locker is integrated into Windows and uses cloud-based recovery key management by default. Vera Crypt is free, open-source software that stores encryption keys locally only—no cloud backup, no recovery service. Vera Crypt provides stronger privacy but less convenience if you lose your password. Both use strong encryption algorithms, but the key management approaches are very different.
Could hackers steal Bit Locker recovery keys from Microsoft's servers?
It's theoretically possible but unlikely. Microsoft encrypts recovery keys at rest and implements access controls. However, if Microsoft's infrastructure was breached by sophisticated attackers, recovery keys could potentially be compromised. This is why security experts argue against centralized key storage—it creates a single point of failure affecting all users.
How many times has the FBI requested Bit Locker recovery keys?
Microsoft stated it receives an average of 20 Bit Locker recovery key requests per year from law enforcement. The company doesn't publicly disclose how many of these requests it approves versus denies, making it difficult to assess how frequently keys are actually handed over in practice.
Should organizations use Bit Locker for sensitive data?
For general business use, Bit Locker is secure and appropriate. For organizations handling highly sensitive data, security experts recommend implementing enterprise key management solutions where the organization controls the recovery keys rather than relying on Microsoft's cloud storage. This provides more control and security for sensitive information.
What will happen to Bit Locker encryption in the future?
As of 2025, Bit Locker remains unchanged, but there's ongoing policy debate in many countries about whether encryption backdoors or key escrow should be required by law. If such laws pass, Microsoft would likely be required to build different key management mechanisms. For now, the current system remains based on legal requests rather than mandatory access.
The Bottom Line: Security Versus Convenience in a Warrant-Accessible World
The story of Microsoft providing Bit Locker recovery keys to the FBI isn't surprising, scandalous, or illegal. It's actually straightforward and predictable. Microsoft stores recovery keys in accessible form, law enforcement gets a warrant, and the company complies.
But understanding how this works is important because it reveals something fundamental about encryption in the real world. Encryption is only as strong as the key management system supporting it. And key management in the cloud, controlled by corporations, is always accessible to law enforcement with proper legal authority.
This doesn't mean you shouldn't use Bit Locker. For most people, for most purposes, Bit Locker provides excellent security against the threats that matter: device theft, lost computers, casual data theft. It's significantly better than no encryption.
But if you're in a situation where law enforcement access is a genuine concern—if you're an activist, a journalist, someone at serious risk of government surveillance—then you need to understand the architectural limits of Bit Locker. You need to either manage your own recovery keys, use encryption that doesn't involve cloud key storage, or accept that your encryption may not protect you against legal processes.
For organizations handling sensitive data, the lesson is similar. Don't rely on default cloud key management. Implement enterprise solutions that give your organization control over encryption keys. Document your key management procedures. Audit access regularly.
The reality of 2025 is that encryption backdoors exist, not as mathematical vulnerabilities, but as architectural choices about where keys are stored and who has access to them. Microsoft's choice to store Bit Locker recovery keys in the cloud is a pragmatic one that balances multiple priorities. But it's a choice with trade-offs, and understanding those trade-offs is essential for anyone relying on encryption.
Security is always about trade-offs: convenience versus control, service versus privacy, accessibility versus secrecy. Bit Locker represents one particular balance point. There are others available if you need them.

Key Takeaways
- Microsoft stores BitLocker recovery keys in cloud infrastructure, making them accessible to law enforcement with proper warrants
- Law enforcement receives approximately 20 BitLocker recovery key requests per year from Microsoft on average
- BitLocker encryption protects against device theft and unauthorized access, but not against law enforcement with legal authority
- Centralized key storage creates security risks: if Microsoft's infrastructure is breached, all recovery keys could be compromised
- Organizations handling sensitive data should implement enterprise key management solutions instead of relying on cloud backup
- Users concerned about law enforcement access can disable cloud key backup and manage recovery keys locally or on physical media
- Different encryption solutions (VeraCrypt, FileVault, LUKS) use different key management architectures with different security trade-offs
- The broader encryption backdoor debate continues worldwide, with potential policy changes that could expand government access requirements
Related Articles
- Freecash App: How Misleading Marketing Dupes Users [2025]
- EU GDPR Fines Hit €1.2bn in 2025: What You Need to Know [2025]
- TikTok's US Deal Finalized: What the ByteDance Divestment Means [2025]
- ICE Agents Doxing Themselves on LinkedIn: Privacy Crisis [2025]
- Under Armour Cyberattack 2025: What 7M Users Need to Know [Guide]
- UK VPN Ban Explained: Government's Online Safety Plan [2025]
![Microsoft BitLocker Encryption Keys FBI Access [2025]](https://tryrunable.com/blog/microsoft-bitlocker-encryption-keys-fbi-access-2025/image-1-1769184542838.jpg)



