CIRO Data Breach Exposes 750,000 Investors: What Happened and What to Do [2025]
It started like most breaches do: quietly. In mid-August 2025, the Canadian Investment Regulatory Organization (CIRO) discovered something nobody wants to find. Hackers had infiltrated their systems and stolen sensitive data on roughly 750,000 Canadian investors. This wasn't some obscure fintech startup either. CIRO is Canada's national self-regulatory body that oversees investment dealers, trading activity, and the whole machinery that keeps Canadian markets honest.
When CIRO went public with this in mid-August, they painted a picture of immediate action: forensic investigators spending over 9,000 hours digging through systems, identifying exactly what was taken, and confirming the stolen data hadn't hit the dark web. They offered two years of free credit monitoring and identity theft protection to affected investors. Sounds reassuring, right? But here's where it gets complex.
Data breaches at this scale hit different when they target financial institutions. You're not dealing with compromised email addresses or leaked usernames. We're talking about dates of birth, social insurance numbers, investment account details, annual income figures, and government-issued ID numbers. These aren't randomly assembled details. They're the exact building blocks that identity thieves use to drain accounts, open fraudulent credit lines, and ruin financial lives.
What makes this breach particularly significant is the trust relationship involved. Investors went to CIRO-regulated dealers assuming their most sensitive financial information was locked down tight. They were wrong. That breach of trust isn't something two years of credit monitoring fully repairs.
This article walks you through everything you need to know about the CIRO breach: what was actually stolen, how extensive the damage really is, whether you're affected, and exactly what protective steps work best right now. We're not going to sugarcoat it or hide behind corporate doublespeak. You're getting the straight analysis.
TL; DR
- The Breach: CIRO, Canada's investment regulator, suffered a cyberattack in August 2025 exposing data on approximately 750,000 Canadian investors
- Data Stolen: Names, dates of birth, social insurance numbers, investment account numbers, account statements, annual income, phone numbers, and government-issued ID numbers were compromised (passwords and PINs were not stolen)
- The Response: CIRO confirmed the data has not been leaked on the dark web or misused, and is offering two years of free credit monitoring and identity theft protection
- Key Action: Check CIRO's official notifications or contact your investment dealer directly to verify if your information was among the exposed records
- Bottom Line: This is serious because personal identifiers were stolen, but immediate protective action can substantially reduce your fraud risk
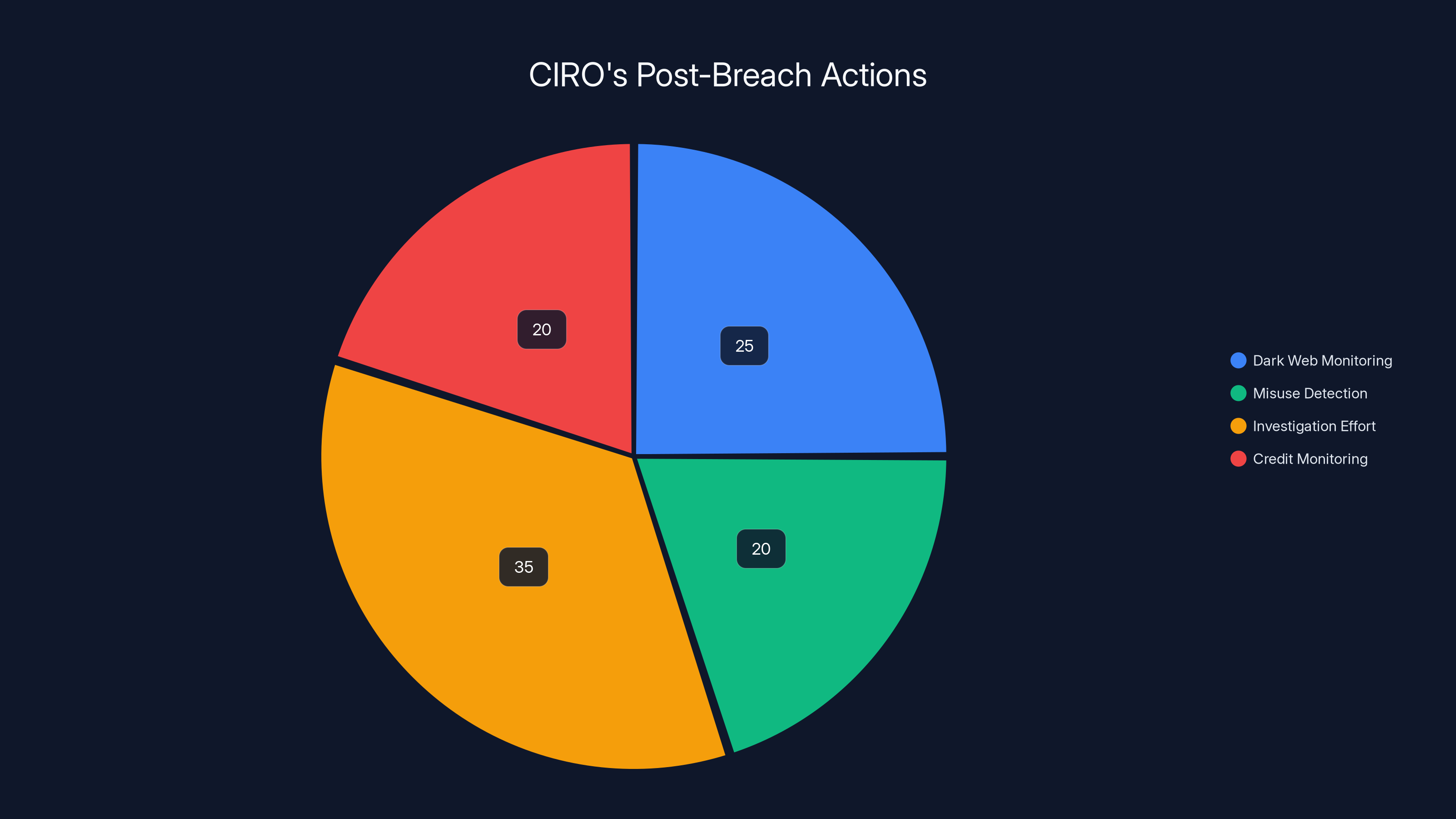
Estimated distribution shows significant focus on investigation effort (35%) and dark web monitoring (25%), reflecting CIRO's emphasis on thorough forensic work and data security. Estimated data.
Understanding CIRO and Why This Breach Matters
Before we dive into the specifics of what happened, it helps to understand exactly who CIRO is and why a breach at this organization carries significant weight in Canada's financial ecosystem.
CIRO stands for the Canadian Investment Regulatory Organization. Despite the relatively recent founding in 2023, CIRO consolidated Canada's investment industry oversight by merging the IIROC (Investment Industry Regulatory Organization of Canada) and the MFDA (Mutual Fund Dealers Association). Think of them as Canada's financial watchdog for investment dealers and trading activities.
Here's what matters: if you invest through any major Canadian bank or independent investment dealer, there's a solid chance your account is regulated by CIRO. They oversee roughly 170 dealer firms across Canada and ensure these firms meet regulatory standards. They handle complaints, conduct audits, and set the rules that protect investors from fraud and misconduct.
When a breach happens at this level, it's not just a customer service problem. It's a systemic vulnerability that affects hundreds of thousands of people simultaneously. The breach exposed data that most consumers would consider their most closely guarded financial secrets.
What makes CIRO particularly critical to understand is their role in market integrity. They monitor trading activity to catch market manipulation, insider trading, and other forms of fraud. They're supposed to be bulletproof. A breach here signals that even Canada's institutional safeguards have gaps.
The timing also matters. Data breaches have become so routine that people have started tuning them out. But investor data is different from a compromised email list. When someone has your social insurance number and investment account details, they don't need to crack passwords. They can call your bank, impersonate you, and potentially liquidate positions or redirect funds.
CIRO's response was to launch what they called a "robust" forensic investigation. Over 9,000 hours of investigative work went into understanding the scope and nature of the breach. That's roughly the equivalent of four investigators working full-time for a year. For transparency, CIRO released findings that the data hadn't been sold on dark web forums or misused by the attackers. But here's the uncomfortable truth: we have no way to independently verify that claim.
What Data Was Actually Stolen in the Breach
Let's get specific about what the hackers walked away with. CIRO's disclosure identified the following compromised data categories:
Personal Identifiers: Full names, dates of birth, phone numbers, and email addresses. These are the basic building blocks used in identity theft and social engineering.
Financial Identifiers: Social insurance numbers (SINs), investment account numbers, and financial account statements. A SIN alone is potentially catastrophic because it's used to open credit lines, get loans, and file taxes. Combine it with other data points, and a criminal has everything needed to impersonate someone financially.
Income and Government Documentation: Annual income figures and government-issued ID numbers. This data is valuable for synthetic identity fraud schemes where criminals create new identities using stolen real information combined with fake details.
Account History: Full investment account statements showing transaction history, account values, and holdings. This reveals investment patterns, wealth levels, and potentially predictable behaviors.
What Was NOT Stolen: Passwords, PIN codes, and security question answers. This is one genuine silver lining. The hackers didn't compromise the actual access credentials needed to log into accounts and move money.
Here's what this combination of stolen data means practically: A criminal with this information can:
- Apply for credit cards and lines of credit in the victim's name
- Open new investment accounts or attempt to take over existing ones
- Commit tax fraud by filing false returns
- Sell the data to other criminals for use in various fraud schemes
- Use personal details for targeted phishing and social engineering attacks
- Apply for loans or mortgages
- Set up utility accounts or other services
The fact that passwords weren't stolen is meaningful but not game-changing. A sophisticated attacker with a complete personal profile doesn't need your password. They call your bank's customer service, answer security questions using information they just acquired, and reset access themselves.
CIRO's investigators confirmed that the stolen data hadn't been dumped on dark web marketplaces or discovered in the hands of other criminal organizations. But this doesn't mean the data is safe. It means the initial hackers either haven't sold it yet, are holding it for leverage, or plan to use it themselves in a coordinated campaign.
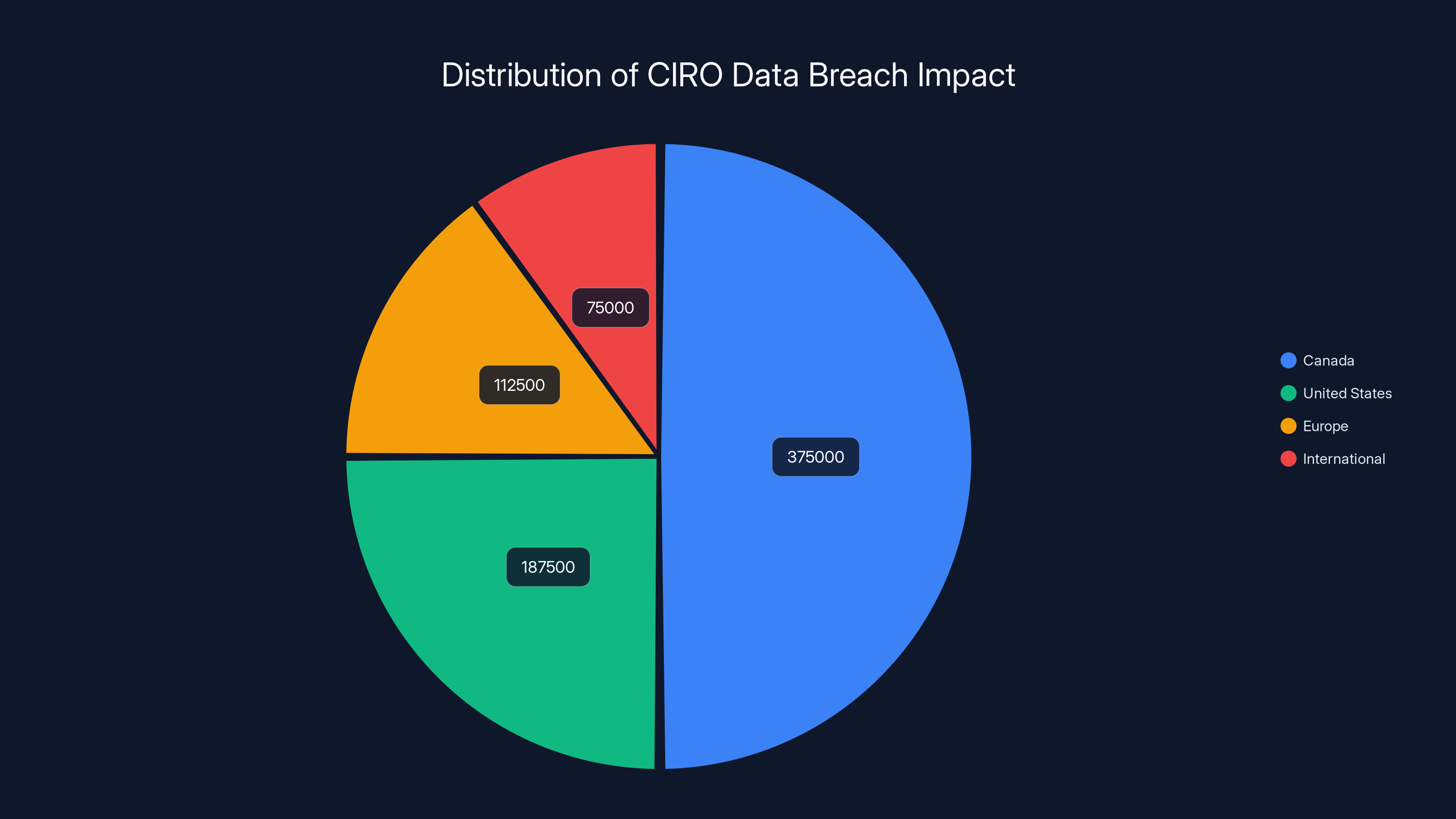
Estimated data shows that 50% of the affected individuals are in Canada, with significant numbers also in the US and Europe, highlighting the international reach of the breach.
The Timeline: How the Breach Unfolded
Understanding when and how the breach occurred helps explain both what happened and what might happen next. The timeline here matters because it tells us something about the attackers' sophistication and planning.
Mid-August 2025 is when CIRO publicly disclosed the breach. But the actual intrusion and data theft likely happened before that. Data breaches typically have a discovery lag of weeks or even months. The time between compromise and detection is when hackers extract data, cover their tracks, and disappear before anyone notices.
CIRO's disclosure statement noted that upon discovery, they "immediately" shut down portions of their infrastructure and launched the forensic investigation. This shutdown phase is critical because it stops the bleeding. It prevents further data exfiltration and contains the damage.
The investigation phase took time. Over 9,000 investigative hours means this wasn't a quick analysis. Forensic investigators had to trace the initial breach point, map the attacker's lateral movement through networks, identify every system accessed, catalog the data touched, and determine what was actually exfiltrated versus what was merely accessed.
What we don't know: The exact point of compromise. Was this a phishing email to an employee that escalated to system access? A vulnerability in an internet-facing application? Compromised credentials purchased on the dark web? Insider involvement? CIRO hasn't disclosed the initial attack vector, which is fairly standard practice for regulatory organizations trying to avoid giving other hackers a roadmap.
The sophistication level is significant. This wasn't script kiddies running automated scanning tools. Someone with planning and technical expertise targeted CIRO specifically, likely because they knew the value of the data held there. Investment data on 750,000 people is worth real money on criminal marketplaces.
The timeline suggests one more critical point: If you had investment accounts at CIRO-regulated dealers during the breach window, your data was potentially compromised. CIRO hasn't specified when the intrusion occurred, but announced it in mid-August 2025.
Scope and Scale: 750,000 Affected Individuals
When you hear "750,000 people," it's easy to numb out. That number is so large it almost becomes meaningless. Let's put it in perspective.
Canada's adult population is roughly 30 million people. The Canadian stock market has approximately 15 million registered investors. CIRO's breach affected roughly 5% of Canada's entire population and nearly half of all Canadian investors. That's not a data breach. That's a breach of a major segment of Canada's investing population.
To frame it another way: If you're Canadian and invest through banks or registered dealers, there's roughly a 1-in-4 chance your data was in this breach. Not certain, but statistically significant.
The breach affects people across geographic regions where CIRO-regulated dealers operate:
United States: Large numbers of Canadian-American investors and dual citizens holding Canadian investment accounts
European Countries: Canadian expats and international investors using Canadian dealers
International: Investors across multiple time zones using CIRO-regulated platforms
What's important about the scope is understanding that it's not evenly distributed across all demographics. This breach skews toward people with investment accounts, which correlates with higher age, higher income, and higher net worth. These are exactly the people most vulnerable to coordinated identity theft and fraud attacks.
The 750,000 figure also raises questions about CIRO's own data practices. Why were so many individuals' records on easily accessible systems? Shouldn't investor data be compartmentalized and encrypted in ways that make bulk extraction much more difficult? The breach's scale suggests data was either centralized (poor practice) or the attackers had unusually broad access (even worse).

What CIRO Says Happened After the Breach
Let's examine CIRO's response and what it tells us. After discovering the breach, CIRO made several public commitments:
No Dark Web Leakage: CIRO's investigators confirmed that as of their investigation's conclusion, the compromised data had not appeared on dark web forums, data marketplaces, or criminal channels. This is worth taking seriously but with appropriate skepticism. Dark web monitoring is imperfect, and data can be held privately before being sold or used.
No Misuse Detected: CIRO reported that they found no evidence of misuse of the stolen data at the time of their investigation. This is somewhat reassuring but comes with a major caveat: the absence of detected misuse doesn't mean future misuse won't occur. It just means hackers haven't leveraged the data yet in ways CIRO could observe.
9,000+ Investigation Hours: The depth of investigation is legitimate and suggests professional forensic work. But the public rarely gets to see the actual forensic reports. CIRO's conclusion is filtered through their communications team.
Two Years of Credit Monitoring: CIRO is providing affected individuals with two years of complimentary credit monitoring and identity theft protection. We'll talk about what this actually covers in the next section.
What's notably absent from CIRO's public statement:
- The specific date the breach occurred
- How long data was accessible before discovery
- The initial attack vector or vulnerability
- Exactly how many of the 750,000 had complete data sets versus partial exposure
- Whether any employees or contractors were involved
- Specific details about the forensic findings
This is fairly standard corporate response protocol, but it's worth noting that we're getting the sanitized version. What CIRO is comfortable disclosing publicly isn't necessarily everything investigators found.
The "robust" investigation claim deserves scrutiny too. Nine thousand hours sounds substantial until you consider what that team size means. If a forensic firm sent five people for three months at 50-hour weeks, that's about 7,500 hours. Add a few more people, extend the timeline, and you're there. It's thorough but not impossibly so for a breach of this magnitude.
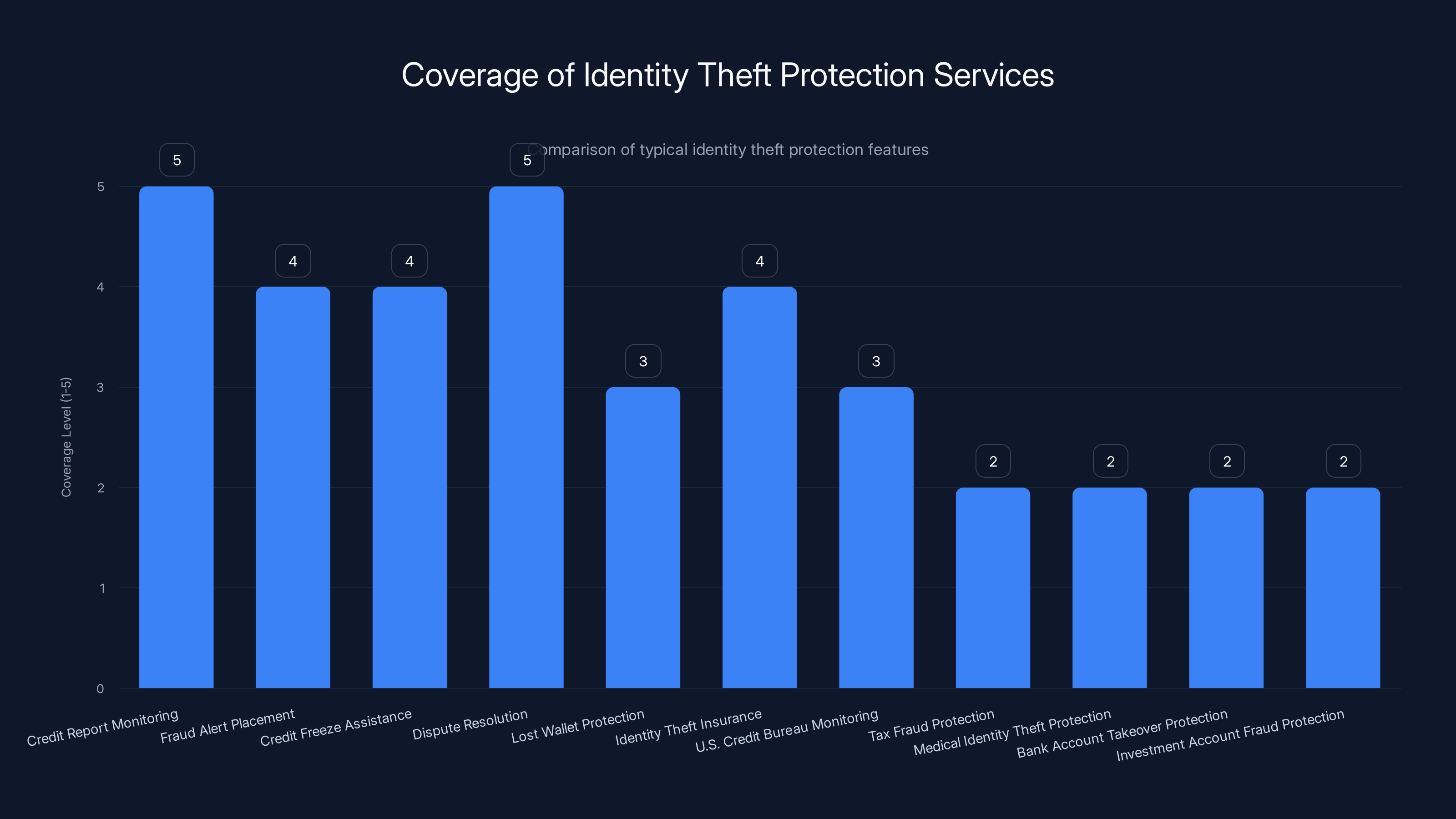
Identity theft protection services provide strong coverage for credit monitoring and dispute resolution but often lack in areas like tax fraud and investment account protection. Estimated data.
Credit Monitoring and Identity Theft Protection: What It Actually Covers
CIRO is offering two years of free credit monitoring and identity theft protection. This sounds good on the surface. But here's what you actually get and what you don't.
Credit Monitoring Basics:
Credit monitoring services track your credit reports from Canada's two major credit bureaus: Equifax and Trans Union. They alert you when new credit inquiries hit your file, when accounts are opened, when loans are applied for, or when your credit score changes significantly. This is valuable because it catches fraud attempts before they fully develop.
BUT: Credit monitoring is reactive, not preventive. It tells you after someone has already tried to open a credit card in your name. By that point, damage has been done. You've got to dispute the fraudulent account, prove you didn't apply for it, and wait for the bureaus to investigate.
Identity Theft Protection Components:
Identity theft protection services typically include:
- Credit report monitoring (mentioned above)
- Fraud alert placement on credit files
- Credit freeze setup assistance
- Dispute resolution support
- Lost wallet protection
- Identity theft insurance (usually covers costs of cleaning up identity theft)
- U. S. credit bureau monitoring (important for cross-border investors)
Critical Gaps in Typical Coverage:
Here's what even good identity theft protection doesn't cover well:
- Tax Fraud: Someone filing a tax return in your name. The CRA (Canada Revenue Agency) has improved their verification, but this is still an issue.
- Medical Identity Theft: Using your health information to access medical services or prescription drugs.
- Bank Account Takeovers: Direct access to existing bank accounts (though some insurance policies cover losses).
- Investment Account Fraud: This is particularly relevant to CIRO breach victims. Using your investment account information to liquidate positions or redirect funds.
- Utility and Service Fraud: Setting up utilities, cell phone accounts, or subscriptions in your name.
Two years of coverage is also a concern. Identity theft doesn't have a statute of limitations. Someone using your stolen information could commit fraud years later. After the coverage expires, you're on your own.
How to Actually Use the Credit Monitoring:
- Enroll immediately: Don't wait. Sign up for the monitoring service CIRO provides and set it to the highest alert sensitivity.
- Check your credit reports: Review your full credit reports from both Equifax and Trans Union within the first month. Look for any accounts you don't recognize.
- Place a fraud alert: Ask CIRO's monitoring service or contact the bureaus directly to place a fraud alert on your file. This requires creditors to verify your identity before opening new credit.
- Consider a credit freeze: A credit freeze is more restrictive than a fraud alert. It prevents any new credit inquiries unless you temporarily lift the freeze. Most monitoring services can help set this up.
How to Check If You're Affected by the CIRO Breach
This is the practical question everyone asking: Am I in this breach? How do I know for sure?
Direct Contact from CIRO: If your data was compromised, CIRO is required to notify affected individuals. They're likely doing this through multiple channels: mailed letters, email notifications, and possibly phone calls. Check your mail carefully over the coming weeks. These notifications typically contain:
- Confirmation that your data was affected
- Specific details about what was exposed
- Instructions for enrolling in the credit monitoring service
- Reference numbers for tracking
- Contact information for the monitoring service provider
Contacting Your Investment Dealer Directly: If you invest through a Canadian bank or independent dealer, contact them directly and ask if your account data was included in the CIRO breach. They likely have their own notification system and can confirm your status.
CIRO's Official Website: CIRO maintains a dedicated breach response page where they list affected entities and provide resources. Check CIRO's official website periodically for updates, though specific individual affected lists are typically only disclosed via direct notification (privacy concerns prevent public posting of affected names).
Red Flags That Suggest You're at Risk:
Even if you haven't received direct notification yet:
- You held investment accounts with CIRO-regulated dealers during mid-2025
- Your personal information recently changed on investment statements without your action
- You've received strange credit inquiries or account opening attempts
- Banks or creditors contact you about accounts you don't recognize
What to Do If You Can't Confirm Your Status:
If weeks pass and you haven't heard from CIRO or your dealer, don't assume you're safe. Take these proactive steps:
- Call your investment dealer's fraud line directly
- Request they confirm whether your account was involved
- Ask them to place fraud alerts on your accounts
- Request they note your file with heightened verification requirements
- Manually check your credit reports at equifax.ca and transunion.ca (you're entitled to free reports)
Passwords and PINs: Why They Weren't Stolen Matters (But Only Partly)
One detail worth unpacking: The breach exposed vast amounts of sensitive data but did NOT include passwords or PIN codes. On its surface, this is genuinely good news. It means the attackers can't just log into your investment accounts and drain them.
But here's the nuance that matters.
Why Passwords Weren't Stolen: Either the passwords were stored separately from the main database (good security practice), encrypted with standards the attackers couldn't crack (also good), or the attackers didn't reach the systems where passwords were stored (they had targeted access to specific data stores).
Any of these explanations suggests CIRO had at least some defensive security layers in place. That's worth acknowledging.
Why Passwords Not Being Stolen Doesn't Eliminate Risk:
Without your password, a criminal with your full personal profile can still:
- Use the "Forgot Password" feature: Most investment platforms have account recovery processes that verify identity using personal information. With your name, SIN, DOB, and address, someone can often reset your password.
- Call customer service: Banks train customer service reps to verify identity using security questions and personal information. With a complete stolen profile, someone can potentially pass this verification.
- Use your information for other purposes: They don't need your investment account password. They can use your SIN to file taxes, open new credit accounts, or commit other fraud.
- Sell the data to someone else: Criminal networks will pay for complete personal profiles even without passwords, because they can execute fraud without needing direct account access.
The absence of passwords is a meaningful reduction in immediate account takeover risk. But it's not a get-out-of-jail-free card for identity protection.

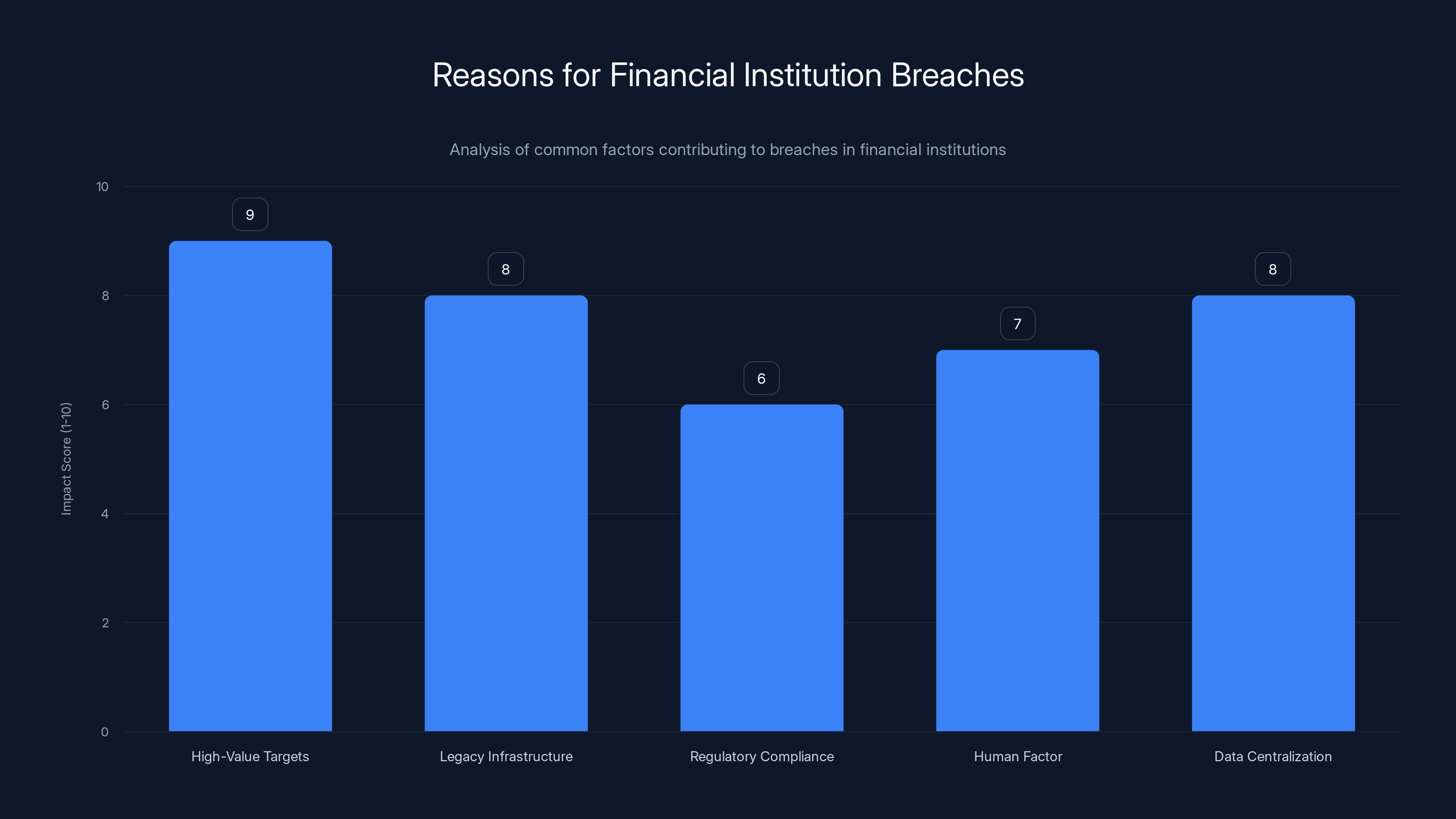
The chart highlights the key reasons financial institutions are frequently breached, with 'High-Value Targets' and 'Legacy Infrastructure' being the most impactful. Estimated data based on common industry insights.
Comparing CIRO to Other Major Canadian Data Breaches
To understand the scale and significance of CIRO's breach, it helps to see how it compares to other major Canadian incidents.
The Equifax Breach (2017):
Equifax Canada was hit with a breach affecting approximately 19,000 Canadian residents, though the overall Equifax breach affected 147 million people globally. Unlike CIRO, Equifax was hit because of known vulnerabilities in their systems that weren't patched. The breach was discovered months after it occurred.
Similarity to CIRO: Both involved massive troves of personal financial data. Difference: The Equifax breach was caused by poor patching practices, while CIRO's cause remains unclear.
The Air Bn B Breach Affecting Canadians (2016):
Airbnb disclosed a breach affecting a much smaller number of Canadian users. The breach was discovered relatively quickly, and Airbnb offered credit monitoring.
Unlike CIRO: Airbnb's breach was smaller in scope and involved different data types.
The Rogers Wireless Breach (2022):
Rogers suffered a breach affecting approximately 9.9 million Canadians, making it one of Canada's largest breaches. The breach exposed email addresses, phone numbers, names, dates of birth, and Social Insurance Numbers of Rogers customers.
Direct Comparison:
CIRO's 750,000 affected individuals makes it smaller than Rogers (9.9 million) but more targeted because it's concentrated on investors specifically. The data types are similar across Rogers and CIRO: personal identifiers, SINs, dates of birth. The key difference is the victim demographic. CIRO breach victims tend to be wealthier and more investment-savvy, making them potentially higher-value targets for fraud.
What Other Breaches Tell Us About CIRO's Response:
Looking at how Rogers and others handled similar breaches:
- Rogers: Offered 3 years of complimentary credit monitoring (more generous than CIRO's 2 years)
- Equifax: Offered 3 years plus identity theft protection
- Industry standard: 2-3 years of monitoring
CIRO's 2-year offering is on the lower end of what we've seen from comparable breaches. This isn't necessarily indication of mismanagement, just baseline reality.
Immediate Actions to Take Right Now
If you're concerned you might be affected, here's a practical action checklist. Some of these apply whether or not your data was actually compromised, because they're just good security hygiene.
Within 48 Hours:
- Verify Your Account Status: Contact your investment dealer and ask directly whether your account was included in the CIRO breach. Get this in writing if possible.
- Check Investment Accounts: Log into your investment accounts (using YOUR normal login, not any links in emails) and review recent transactions, account ownership details, and contact information.
- Review Credit Card Statements: Check your last 3 months of credit card statements for charges you don't recognize.
Within 1 Week:
- Enroll in Credit Monitoring: If CIRO has sent you notification and monitoring details, enroll immediately. Don't put this off.
- Order Your Credit Reports: Get your full credit reports from Equifax and Trans Union. This is free in Canada and shows you everything any creditor has seen.
- Place a Fraud Alert: Contact both credit bureaus and request a fraud alert on your file. This costs nothing and makes new credit applications harder for fraudsters.
- Update Security Questions: Where possible, change security questions on financial accounts. If a fraudster has your personal information, they might be able to answer the default questions.
Within 1 Month:
- Consider a Credit Freeze: If you're genuinely worried, place a credit freeze on your accounts. This is stronger protection than a fraud alert. It prevents almost all new credit applications.
- Document Everything: Keep records of all CIRO breach notifications, credit monitoring enrollment confirmations, credit reports, and any communications with financial institutions.
- Set Calendar Reminders: Mark your calendar 3 months from now to check your credit reports again, and every quarter for at least a year. Watch for fraud patterns.
- Monitor for Tax Fraud: When tax season comes (spring 2026 for 2025 taxes), file your taxes early before a fraudster can file in your name. The CRA now has improved verification.
Ongoing Protection:
- Review Statements Monthly: Never skip this. Make it a monthly habit to check investment and bank statements.
- Use Unique Passwords: If you don't already, make all your financial account passwords unique and strong. Use a password manager.
- Enable Multi-Factor Authentication: Where available, turn on 2FA or MFA for financial accounts. This prevents account takeovers even if passwords are compromised.
- Monitor Credit Reports: Even after 2 years of monitoring ends, you can still pull free credit reports once per year from both bureaus.

How Identity Thieves Use Stolen Investor Data
Understanding the actual attack patterns helps you spot them early. This isn't abstract. Here's how stolen investor data gets weaponized.
Attack Pattern 1: Synthetic Identity Fraud
A criminal takes your real SIN and personal identifiers and combines them with fake information (a different name, address, or phone number). They create a new "synthetic" identity that passes initial credit checks because the SIN portion is real. They open credit lines, max them out, and disappear. You don't notice for months because accounts are opened in a different name.
How to Spot It: Unexpected credit inquiries that don't match any accounts you recognize.
Attack Pattern 2: Account Takeover Through Customer Service
A fraudster calls your bank or investment dealer. They provide your full name, SIN, DOB, address, and investment account number. They claim they lost access to their account and need to reset the password. With a complete profile, they often get transferred to the account recovery team and successfully change the password. By the time you notice, they've liquidated positions and transferred funds.
How to Spot It: Unexpected password reset emails, login notifications from locations you weren't at, or missing account access.
Attack Pattern 3: Tax Fraud
A fraudster files a tax return in your name claiming various tax credits they're not entitled to. The CRA eventually notices discrepancies when you file, but the fraud can take months to unwind. You might get refund checks sent to addresses you don't recognize.
How to Spot It: Unexpected tax refunds, letters from CRA about discrepancies, or denials of refunds you expected.
Attack Pattern 4: New Account Fraud
Using your personal information, a fraudster applies for new credit cards, loans, or lines of credit. Because your credit hasn't been damaged yet, new applications sometimes get approved. You discover this when bills start arriving.
How to Spot It: Unexpected credit card offers, bills for accounts you didn't open, or calls from debt collectors about accounts you don't recognize.
Attack Pattern 5: Data Brokering
Your stolen information (along with thousands of others) gets sold on dark web criminal marketplaces. Someone else buys it and uses it for fraud. You never know it happened until fraud actually occurs.
How to Spot It: This one you can't spot early. Prevention and rapid fraud detection are your only defenses.
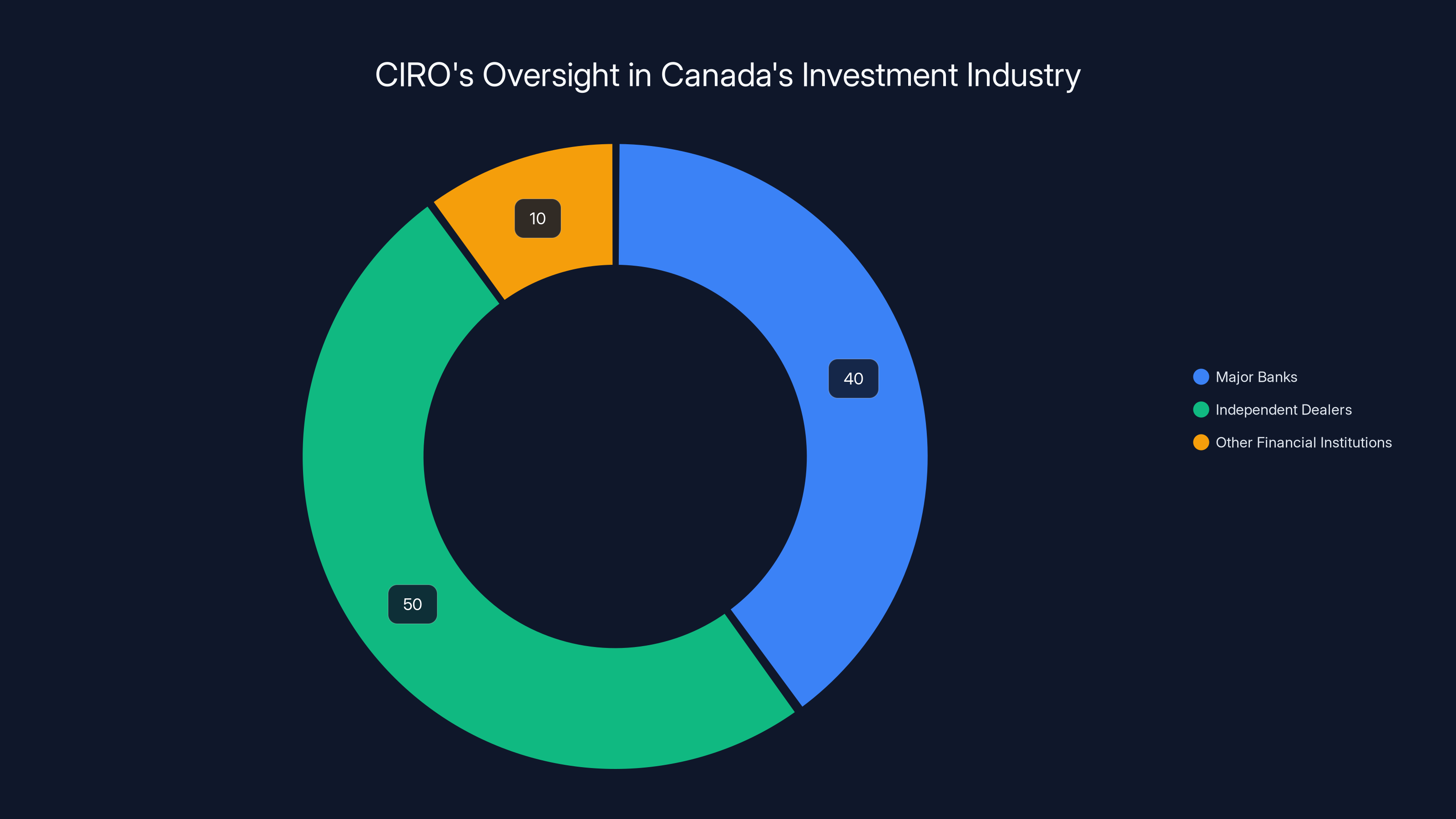
CIRO oversees approximately 170 dealer firms, with an estimated 40% being major banks, 50% independent dealers, and 10% other financial institutions. (Estimated data)
The Broader Context: Why Financial Institutions Keep Getting Breached
CIRO's breach isn't an anomaly. It's part of a pattern. Why do financial institutions keep suffering breaches?
Reason 1: High-Value Targets
Investor data is currency. A complete profile on a Canadian investor (name, SIN, DOB, income, investment account details) sells for real money on criminal marketplaces. A sophisticated attacker targeting CIRO knew exactly what they'd get and that it was valuable.
Reason 2: Legacy Infrastructure
CIRO is an organization consolidated from multiple legacy systems in 2023. Legacy organizations often run older infrastructure that hasn't been fully modernized. Older systems have more bugs, more unknown vulnerabilities, and less sophisticated security. Integrating two organizations' databases and systems is complex and creates temporary gaps in security.
Reason 3: Regulatory Compliance Doesn't Equal Security
CIRO is subject to Canadian regulatory requirements around data protection and security. But regulatory compliance is a baseline, not a ceiling. It's the minimum required. Sophisticated attackers look for and exploit gaps between "regulatory compliant" and "actually secure."
Reason 4: Human Factor
Most breaches begin with phishing emails or compromised credentials, not sophisticated zero-day exploits. Someone at CIRO clicked a link, opened an attachment, or reused a password on multiple sites. That's how the initial access began. No amount of firewall sophistication prevents that.
Reason 5: Data Centralization
CIRO holds data on 750,000 people. That's a massive single point of failure. If systems aren't heavily compartmentalized (and they often aren't due to operational complexity), a breach of one area can compromise everything.

What Experts Are Saying About This Breach
Beyond CIRO's official statements, security researchers and industry analysts have had things to say about this breach.
The Pattern Recognition Angle:
Security analysts note that targeting regulatory bodies is increasingly common. These organizations hold critical data on entire industries or user populations. Compromising them is high-value intelligence gathering.
The Data Types Angle:
Expert opinion suggests that investment and financial data is more valuable to criminals than general personal data. It enables more sophisticated fraud targeting higher net-worth victims who are less likely to catch fraud immediately because transactions blend in with their normal market activity.
The Scale Angle:
The 750,000 number is significant enough to indicate systematic access, not opportunistic breach. Small breaches are usually random (attacker stumbles into data). Breaches of this scale mean someone specifically targeted CIRO with knowledge of what they'd find.
The Response Angle:
CIRO's handling has been viewed as competent but not exceptional. The two-year monitoring is on the lower end of industry standards. The transparency about the breach scope is good, but lack of detail about the initial attack vector is standard (and frustrating for security practitioners).
Long-Term Impact: What Happens After the Headlines Fade
Right now, CIRO breach is major news. But breaches follow a predictable cycle. The news fades, the monitoring service runs its course, and victims are left managing the fallout.
Months 1-6 After Breach: High alert. Victims watch accounts carefully, fraud attempts increase as criminals test the data, monitoring services are actively deployed. This is the riskiest period.
Months 6-12: Vigilance decreases. Some victims stop checking accounts as carefully. Fraudsters who waited to avoid detection now start using data. Some fraud attempts happen months after the breach when people have lowered their guard.
Year 2 and Beyond: Monitoring expires. This is when real risk begins. The data is still valuable, still being used. People who relied on monitoring as their sole protection now have no eyes on their credit anymore.
Years 5-10+: Delayed fraud emerges. Someone who bought your data in year 2 uses it in year 5. You're no longer protected by any monitoring service.
The implication: The two years of monitoring CIRO provides is valuable, but it's not your complete defense. You need ongoing vigilance beyond the monitoring period.

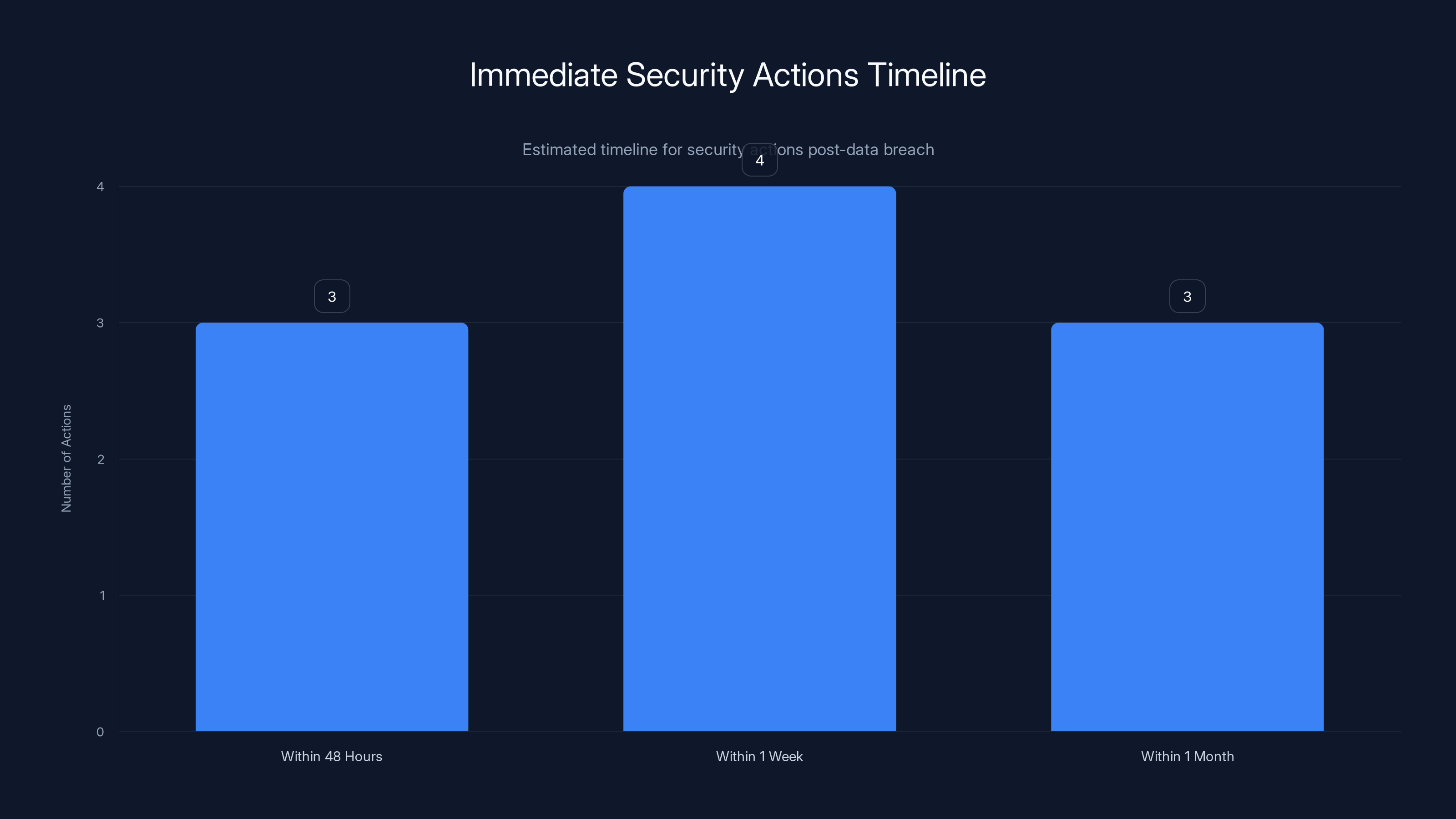
The chart outlines a timeline for immediate actions to take following a data breach, emphasizing the urgency and number of tasks within each timeframe. Estimated data based on typical security recommendations.
Specific Steps for Different Investment Account Types
The impact of this breach varies depending on what type of investment account you hold. Here's how to respond based on your specific situation.
RRSP Accounts:
If you hold an RRSP (Registered Retirement Savings Plan), the breach exposed your contribution history and account balance. A fraudster could use this information to attempt account takeover. Immediate actions: Contact your bank or dealer, confirm who has authority to make changes to your RRSP, and ask them to add enhanced verification requirements before allowing changes.
TFSA Accounts:
TFSAs (Tax-Free Savings Accounts) are lower-security targets than RRSPs because they're not registered with the government. But they still can be compromised. Same response: Contact your provider and add verification requirements.
Taxable Brokerage Accounts:
These are prime targets for account takeover because they're easy to liquidate. Someone taking over your brokerage account can sell all positions and request wire transfers. Response: This is where credit monitoring is most important. Set up alerts for any account activity. Consider placing transactions on hold with your provider.
Managed Accounts and Discretionary Accounts:
If you have an account where a licensed adviser has authority to make trades on your behalf, verify exactly what they have authorization for. Confirm that new authorization forms can only be signed if you're personally verified.
FHSA Accounts:
For First Home Savings Accounts, the breach exposed details about your home savings plans. Less of an immediate account takeover risk, but a fraudster knowing your savings goals could use this for targeted fraud.
GICs and Fixed-Income Investments:
If your investments are in locked-in GICs or bonds, they're less vulnerable to quick liquidation. But their maturity dates and values could be used for fraudulent new account applications.
Red Flags: How to Spot Fraud Attempts Early
The earlier you catch fraud, the easier it is to stop. Here are the specific warning signs to watch for.
Credit Monitoring Red Flags:
- Unexpected hard inquiries from lenders you never applied to
- New accounts appearing on your credit report
- Your credit score dropping suddenly without explanation
- Collections notices for accounts you don't recognize
- Credit card statements showing inquiries in different provinces or countries
Investment Account Red Flags:
- Unexpected login notifications from locations you weren't
- Password reset emails you didn't request
- Trades or transactions you didn't authorize
- Changes to account contact information or beneficiary designations
- Account statements with unfamiliar activities
- Calls from your bank asking to verify activities
Personal/Financial Red Flags:
- Bills or invoices arriving for services you didn't use
- Calls from creditors about accounts you don't recognize
- Unexpected tax refund checks or CRA notices
- New loan or credit card offers from banks you've never used
- Calls from collection agencies about debts you don't owe
- Unexpected utility bills or account statements
What to Do if You Spot Red Flags:
- Act immediately: Don't wait. Call your financial institutions immediately.
- Document everything: Write down dates, times, who you spoke with, what was discussed.
- File a report: Report suspected fraud to your local police. You'll need a police file number for credit disputes.
- Dispute fraudulent accounts: Contact credit bureaus and dispute fraudulent accounts in writing. Provide your police report number.
- Freeze affected accounts: Ask your bank or investment firm to freeze accounts pending investigation.
- Place a fraud alert: If you haven't already, contact credit bureaus and place fraud alerts on your file.

Additional Free Tools and Resources You Should Know About
Beyond CIRO's provided monitoring, Canada has resources available to help you protect yourself.
Government Resources:
Equifax Canada and Trans Union: You're entitled to free credit reports once per year from both bureaus. You can also place fraud alerts and credit freezes for free.
Canada Revenue Agency (CRA): The CRA maintains resources about identity theft and tax fraud. You can file taxes early to prevent someone else from doing it in your name.
Competition Bureau: The Canadian Competition Bureau has resources about fraud prevention and what to do if you've been defrauded.
Private Sector Resources:
Credit Bureau Monitoring: Beyond CIRO's provided service, you can set up additional monitoring directly with Equifax or Trans Union.
Password Managers: Services like Bitwarden, 1 Password, or Dashlane help you maintain unique passwords. Some are free or low-cost.
Antivirus and Security Software: Comprehensive security software helps prevent malware that could compromise credentials.
Looking Forward: Systemic Changes This Breach Might Trigger
Will CIRO's breach force systemic changes to how Canadian financial data is protected? Historically, yes. Major breaches lead to regulatory reviews, compliance updates, and industry shifts.
Likely Regulatory Response:
Canadian regulators (particularly the Office of the Superintendent of Financial Institutions and provincial securities commissions) will likely conduct reviews of CIRO's security practices. CIRO may be required to implement enhanced security measures, more frequent security audits, and better data compartmentalization.
Industry-Wide Changes:
Other regulated financial institutions will likely accelerate their own security upgrades, conduct independent penetration testing, and update incident response procedures. Regulatory bodies share information about breaches to help the broader industry avoid similar incidents.
Legislative Possibilities:
Depending on political will, Canada might strengthen its privacy and data protection laws. The Personal Information Protection and Electronic Documents Act (PIPEDA) governs how organizations handle personal data, but it's relatively old. Stronger requirements around encryption, data minimization, and incident reporting could emerge.
Consumer Protection:
CIRO's breach, combined with Rogers and other major breaches, may prompt discussions about mandatory credit freeze offers or stronger identity theft protections.

Prevention Going Forward: Building Personal Resilience
Beyond responding to CIRO's breach, you should build personal security practices that protect you against all breaches, not just this one.
Layered Password Security:
Don't use the same password twice. A breach at one company shouldn't compromise all your accounts. Use a password manager to generate and store unique passwords. This removes the weak link of human memory.
Multi-Factor Authentication Everywhere:
Enable MFA on email, investment accounts, banks, and any financial accounts. Even if someone has your password, they can't access your account without the second factor. This is the single most effective consumer security practice.
Minimal Data Sharing:
Question every company that asks for your SIN, date of birth, or government ID number. Do they really need it? Can they use something else? The less data you provide to companies, the less data exists to be breached.
Regular Account Audits:
Every three months, check all your financial accounts. Log in, verify account details, review transaction history. This isn't paranoia. It's maintenance.
Email Security:
Your email is the master key to your digital life. If someone compromises your email, they can reset passwords on everything else. Protect your email account like your life depends on it. Use a strong, unique password and enable MFA.
Credit Report Monitoring:
Beyond specific breaches, monitoring your credit reports regularly catches fraud early. Set yourself a quarterly reminder to check at least one of your three free reports (you can pull one from Equifax, then wait four months and pull from Trans Union, staying updated constantly).
FAQ
What exactly was exposed in the CIRO data breach?
The CIRO breach exposed sensitive personal and financial information on approximately 750,000 Canadian investors. Compromised data includes full names, dates of birth, phone numbers, email addresses, social insurance numbers, investment account numbers, account statements, annual income figures, and government-issued ID numbers. Notably, passwords and PIN codes were not compromised, which prevents direct account takeovers but doesn't significantly reduce identity theft risks.
How can I find out if my information was included in the CIRO breach?
CIRO is notifying affected individuals directly through mailed letters, email communications, and potentially phone calls. Check your mail carefully and monitor your email for official CIRO notifications. You can also contact your investment dealer directly and ask whether your account data was included in the breach. For questions about the breach or to verify your status, you can visit CIRO's official website or contact their breach response team through official channels listed on their website.
What should I do immediately if I think I'm affected by this breach?
If you believe you're affected, take these immediate steps: first, verify your account status by contacting your investment dealer directly; second, enroll in the free credit monitoring and identity theft protection service CIRO provides; third, review your investment and bank accounts for unauthorized activities; and fourth, order your free credit reports from both Equifax and Trans Union to check for fraudulent accounts already opened in your name. Don't delay these steps, as early action significantly reduces fraud risk.
Does CIRO's free credit monitoring cover all the protection I need?
CIRO's two-year credit monitoring and identity theft protection service is valuable but not comprehensive. It monitors credit inquiries and alerts you to new accounts opened in your name, which catches many fraud attempts. However, it doesn't prevent fraud, only alert you after fraud attempts occur. It also doesn't cover all forms of identity theft, such as tax fraud, medical identity theft, or direct investment account takeovers. You should layer additional protections like credit freezes, regular account audits, and multi-factor authentication on all financial accounts.
What's the difference between a fraud alert and a credit freeze, and which should I use?
A fraud alert notifies creditors that they should verify your identity more carefully before extending credit. It's easier to lift than a freeze and doesn't prevent you from accessing credit yourself. A credit freeze prevents new credit inquiries entirely, requiring you to temporarily lift the freeze when you actually want to apply for credit. For CIRO breach victims, starting with a fraud alert is reasonable, but if you don't plan to apply for credit soon, a full freeze provides stronger protection against fraudulent applications.
How long should I monitor my accounts and credit for fraud related to this breach?
While CIRO provides two years of monitoring, fraud can occur beyond this period. Identity theft doesn't expire. Someone could purchase your stolen data and use it years later. Plan to continue monitoring your credit reports quarterly indefinitely by pulling free reports from Equifax and Trans Union. Set up permanent alerts on investment and bank accounts. The two-year monitoring is a starting point, not a complete solution.
Can someone take over my investment account if they have my personal information but not my password?
Yes, even without your password, someone with complete personal information can potentially reset your account access through customer service verification or account recovery processes. They can claim they lost access and provide personal details that match your account. This is why account takeover remains a serious risk even though passwords weren't compromised. Contact your investment dealer and ask them to place additional verification requirements on your account, requiring phone calls or in-person verification before any changes are made.
What are the warning signs that someone is using my stolen information for fraud?
Key warning signs include unexpected credit inquiries on your credit report, new credit card accounts you don't recognize, bills or invoices arriving for services you didn't use, calls from collection agencies about debts you don't owe, unexpected tax-related communications from CRA, unauthorized trades in investment accounts, or password reset emails you didn't request. Act immediately if you notice any of these signs by contacting affected institutions and filing a police report for fraud documentation.
Should I be worried about tax fraud with my SIN being stolen?
Yes, tax fraud is a specific concern when SINs are exposed. However, the CRA has implemented improved verification processes. The best protection is filing your own taxes early in tax season, before fraudsters can file returns in your name. Once your legitimate return is filed and processed, the CRA can catch any fraudulent returns filed later. You might also contact CRA directly to notify them that your SIN was compromised in the CIRO breach.
How does the CIRO breach compare to other major Canadian data breaches in terms of seriousness?
The CIRO breach affecting 750,000 Canadians is significant but smaller in scope than the Rogers breach affecting 9.9 million people in 2022. However, the data types are similarly sensitive (SINs, personal identifiers, financial information). The key difference is that CIRO's breach targets a more concentrated demographic of investors, making victims potentially higher-value targets for fraud. The response (two years of free monitoring) is on the lower end of what other major institutions offered.
What specific steps should I take with different investment account types like RRSPs and TFSAs?
For RRSP accounts, which are government-registered, contact your provider and confirm who has authority to make changes, asking them to add enhanced verification before allowing any changes. For TFSAs, follow similar procedures since they can also be compromised. For taxable brokerage accounts, enable alerts for any trades or withdrawals and consider putting transaction holds in place. For all account types, verify that new authorization forms require your personal verification and not just paperwork that could be fraudulently submitted.
Is the fact that passwords weren't stolen actually reassuring?
The fact that passwords weren't compromised is somewhat reassuring because it prevents simple account takeovers where someone just logs in with stolen credentials. However, it's not as reassuring as it initially seems. Fraudsters with complete personal information can use account recovery procedures, social engineer customer service representatives, or use the data for other fraud purposes that don't require account access. Passwords are just one security layer, and their absence doesn't eliminate identity theft risk.
Conclusion: Staying Safe After CIRO
The CIRO breach is a reminder that even Canada's regulated financial institutions can fall victim to sophisticated cyberattacks. With 750,000 investors affected and sensitive data including social insurance numbers and account information compromised, this is a serious incident that demands immediate action from affected individuals.
Here's what we know for certain: your data might have been stolen. CIRO confirms it hasn't appeared on dark web marketplaces yet, but that doesn't mean it's safe. Criminals could be sitting on this data, planning coordinated fraud attacks for months from now. Or they could sell it to others. The uncertainty itself is part of what makes breaches so disruptive.
What you control right now is your response. Enroll in CIRO's credit monitoring service immediately. Don't wait. Order your free credit reports and review them carefully. Place a fraud alert on your file. Set up multi-factor authentication on all financial accounts. Change any security questions on accounts. Review your investment and bank accounts for unauthorized activity. These aren't optional steps you do if you feel like it. They're your best defense against turning a data breach into actual financial loss.
Beyond the immediate response, commit to ongoing security practices. Credit monitoring expires after two years, but your responsibility for protecting yourself doesn't. Establish quarterly habits of reviewing account statements and credit reports. Use unique passwords with a password manager. Keep two-factor authentication enabled on every financial account. These practices protect you not just against CIRO-related fraud, but against all breaches, phishing attempts, and account compromise attempts.
The uncomfortable reality is that data breaches will continue happening. Companies will keep getting hacked. Your personal information will keep being stolen. You can't control that. What you can control is how quickly you detect fraud attempts, how effectively you respond, and how many layers of protection you have in place. That's where your energy should go.
If you're affected by the CIRO breach, you're in good company. Hundreds of thousands of Canadians are in the exact same situation. The silver lining, if there is one, is that this incident will likely force CIRO and other financial institutions to take data security even more seriously. Regulatory scrutiny will increase. Security standards will improve. The next breach might be smaller or slower to occur because of lessons learned here.
For now, treat this seriously, act quickly, and stay vigilant. Your financial security depends on it.
Key Takeaways
- CIRO data breach in August 2025 exposed names, SINs, investment account numbers, and personal details for 750,000 Canadian investors; passwords and PINs were not compromised
- Compromised data includes social insurance numbers, dates of birth, annual income, investment account statements, and government-issued ID numbers making victims vulnerable to identity theft and fraud
- CIRO confirmed stolen data has not appeared on dark web marketplaces but offers two years of free credit monitoring and identity theft protection to affected individuals
- Immediate actions include verifying your status through your investment dealer, enrolling in CIRO's free monitoring service, ordering credit reports, and placing fraud alerts on your accounts
- Criminals use stolen investor data for synthetic identity fraud, account takeovers through social engineering, tax fraud, and new fraudulent account openings months or years after the breach
Related Articles
- Most Spoofed Brands in Phishing Scams [2025]
- Proton VPN Kills Legacy OpenVPN: What You Need to Know [2025]
- Best VPN Service 2026: Complete Guide & Alternatives
- Supreme Court Hacker Posted Stolen Data on Instagram [2025]
- Grubhub Data Breach 2025: What Happened and How to Protect Yourself [2025]
- WhisperPair Bluetooth Hack: Complete Security Guide [2025]
![CIRO Data Breach Exposes 750,000 Investors: What Happened and What to Do [2025]](https://tryrunable.com/blog/ciro-data-breach-exposes-750-000-investors-what-happened-and/image-1-1768851439869.jpg)



