Grubhub Data Breach 2025: What Happened and How to Protect Yourself
When you hear "Grubhub data breach," your first instinct might be panic. You're not alone. Millions of people use Grubhub to order food regularly, which means this incident touches a massive chunk of the US population.
But here's what you actually need to know right now: Grubhub confirmed that hackers accessed certain company systems and stole data. However, the company says sensitive information like financial details and order history weren't compromised. That's the good news. The less good news? We don't yet know exactly what was taken or how many people are affected.
This breach is part of a much larger, interconnected attack that's affecting dozens of major companies. It started with a vulnerability in Salesloft and Drift, two customer relationship management platforms. Attackers exploited that weakness to break into customer systems, stealing data from companies ranging from Cloudflare to Palo Alto Networks.
The group behind this mess is Shiny Hunters, a notorious cybercriminal crew known for data theft and extortion. They're not your typical hackers trying to encrypt everything and demand ransom. Instead, they steal data, then demand payment to keep it off the dark web. It's pure extortion.
TL; DR
- Grubhub confirmed unauthorized access to certain company systems, with attackers downloading data
- Financial and order data appear safe according to Grubhub's statement, but full scope of theft remains unclear
- Shiny Hunters is behind the attack, demanding bitcoin payments to prevent data leaks
- At least 31 organizations compromised since August 2025 through the Salesloft/Drift breach chain
- Your best move now: Monitor credit reports, set up account alerts, and consider a password manager for unique logins

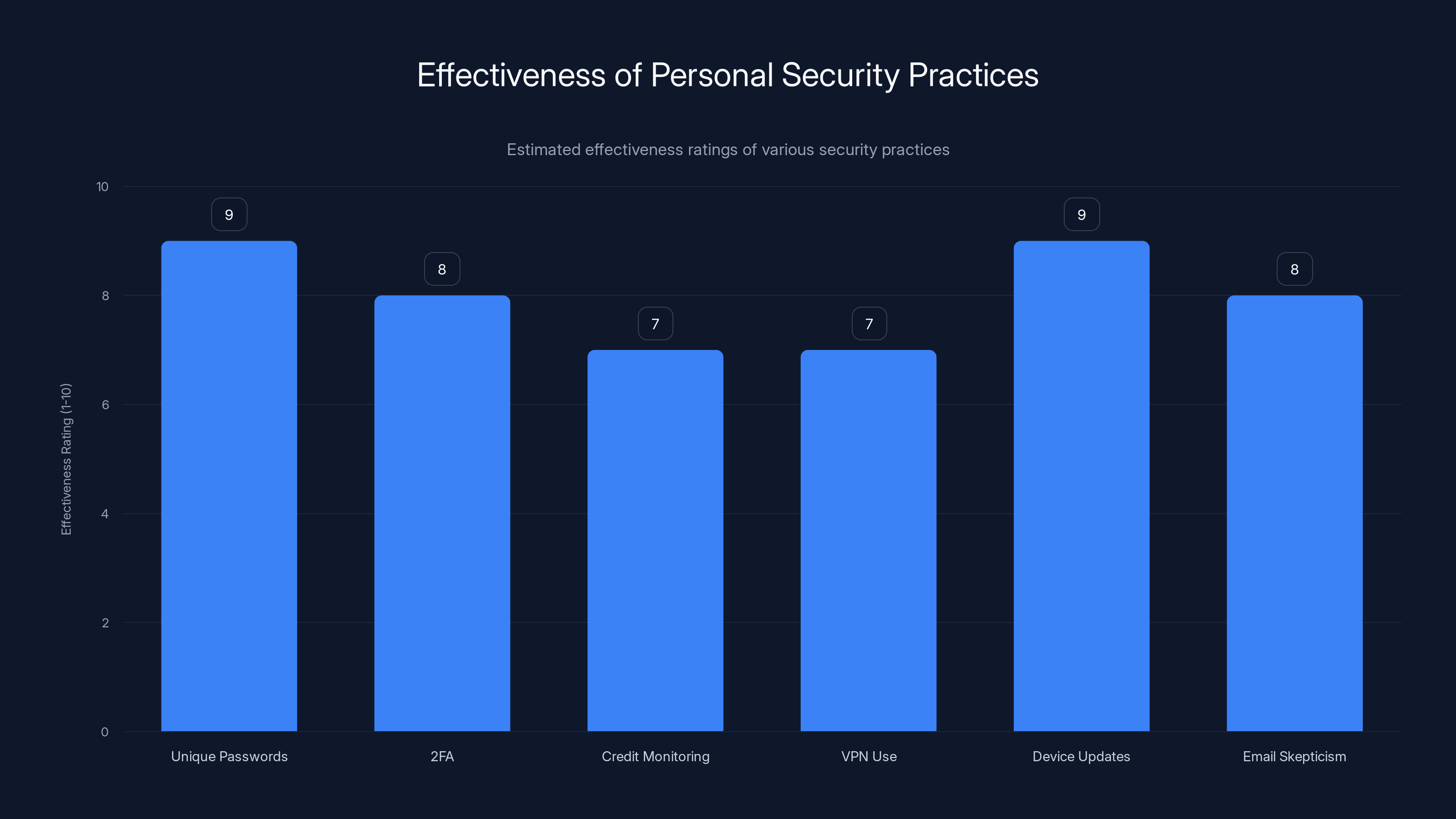
Using unique passwords and keeping devices updated are among the most effective personal security practices. Estimated data based on typical security advice.
What Actually Happened: The Timeline
The Grubhub breach didn't start at Grubhub. It started somewhere else, and that's crucial to understand because it explains how a massive company got breached.
Back in August 2025, security researchers discovered a vulnerability in Salesloft's infrastructure. Drift, a popular chatbot platform owned by Salesforce, had similar issues. These weren't zero-days discovered by white-hat hackers—they were exploitable vulnerabilities that existed for a while.
Shiny Hunters found them. They exploited them. And then they had a massive window into customer systems for both platforms.
Here's where it gets interesting: Salesloft and Drift aren't just random tools. Thousands of companies use them for customer communication and sales automation. When Shiny Hunters broke into Salesloft and Drift's infrastructure, they didn't just access those two companies' data. They got access to customer data stored on those platforms.
That's how Grubhub got compromised. Grubhub uses Salesloft or Drift (or both) for their customer-facing communication. When Shiny Hunters breached Salesloft and Drift, they could see whatever data those tools had about Grubhub.
This is called a "supply chain attack," and it's become one of the most effective hacking strategies because it exploits trust. Companies trust their vendors. Vendors have access to sensitive data. When vendors get breached, everything downstream gets compromised too.
The timeline looks like this:
- August 2025: Vulnerability discovered in Salesloft/Drift infrastructure
- August-September 2025: Shiny Hunters begins exploiting the vulnerability and accessing customer data
- September 2025: External researchers and the companies themselves start discovering the breach
- Late September/Early October 2025: Grubhub publicly announces it was affected
- October 2025: Shiny Hunters begins extortion campaigns, demanding bitcoin to prevent data leaks
The exact entry point is still being investigated, but what we know is that attackers got in through a software vulnerability and then had sustained access to Grubhub's systems for weeks.
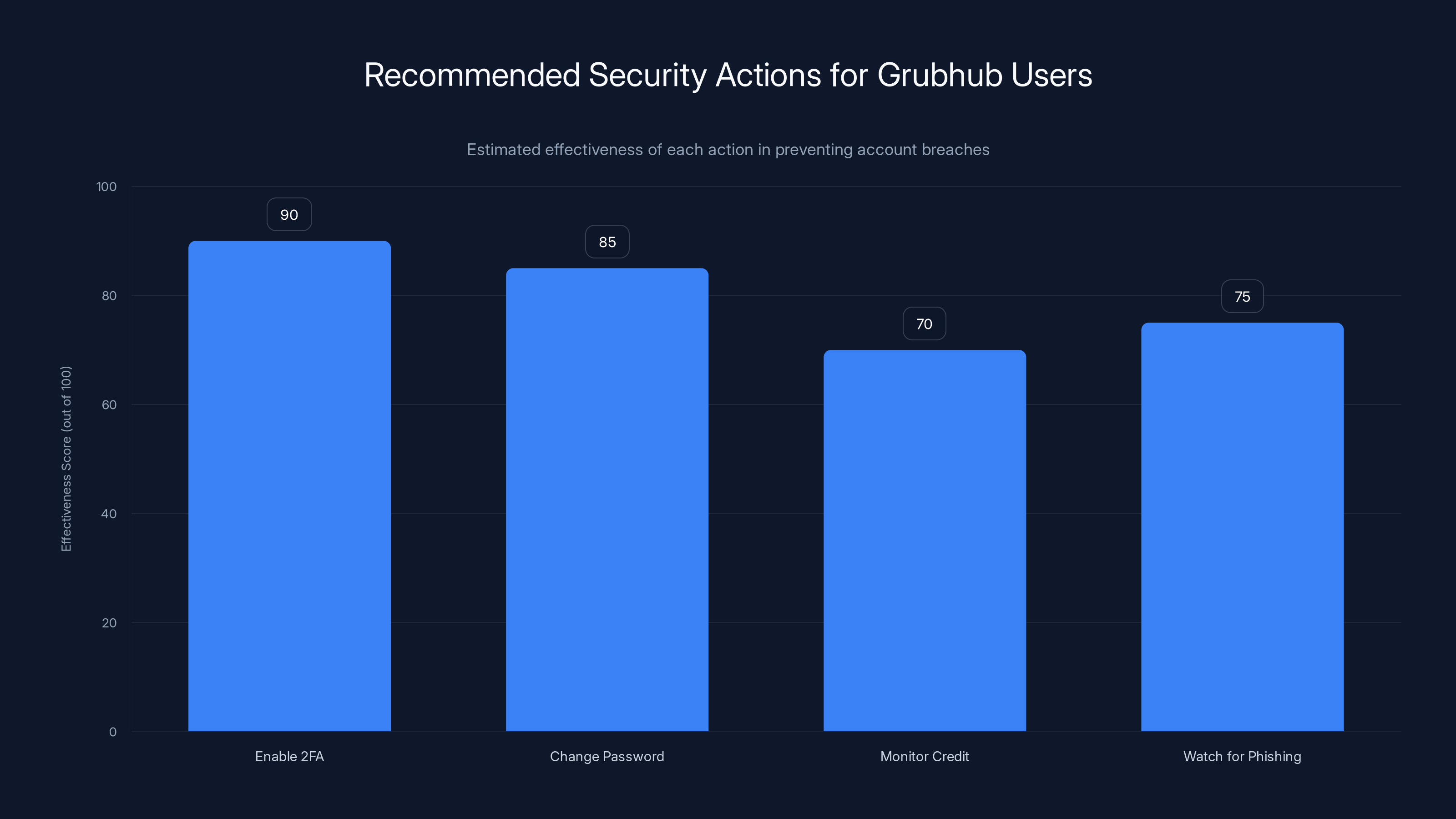
Enabling two-factor authentication is the most effective immediate action Grubhub users can take to secure their accounts, followed closely by changing passwords. (Estimated data)
Understanding the Shiny Hunters Connection
You've probably heard about ransomware—hackers encrypt your data, then demand money to unlock it. Shiny Hunters operates differently, which actually makes them more dangerous in some ways.
Shiny Hunters is what's called a "data exfiltration" group. They still practice extortion, but instead of locking you out of your data, they steal it and threaten to publish it publicly if you don't pay. It's like theft followed by blackmail.
This approach has advantages for the criminals:
-
It works even if you have backups. You can't restore encrypted data if your backups are current, but you can't "restore" stolen data being sold on the dark web.
-
It's harder to defend against. You can monitor your network for strange encryption activity. Detecting data exfiltration is much harder—it looks like normal data movement.
-
The leverage is different. With ransomware, there's a clear technical solution: pay the ransom, get the decryption key. With data theft, paying just makes the criminals disappear—you never know if they actually deleted your data.
Shiny Hunters has been active since at least 2020, stealing data from hundreds of organizations. They've targeted healthcare companies, banks, retail chains, and tech companies. In this particular incident, they claimed responsibility for stealing Salesforce and Zendesk data, along with whatever they got from Salesloft and Drift.
The group operates like a business. They have processes, they honor agreements (mostly), and they maintain reputation on dark web forums. This makes them predictable in some ways—they need to follow through on threats, or they lose credibility for future extortion attempts.
What Data Was Actually Stolen from Grubhub?
This is where things get frustrating. Grubhub hasn't released a detailed inventory of what was stolen. They've only said what wasn't stolen:
- Financial information (credit cards, bank accounts)
- Order history
- Password hashes
What that leaves is a big gray area. The attackers accessed "certain Grubhub systems," but which systems? Here are some possibilities:
Personnel data: Employee names, email addresses, phone numbers, and possibly job titles. This is valuable because it lets hackers target specific employees with phishing attacks.
Customer contact information: Names, addresses, phone numbers, email addresses. This is typically less sensitive than financial data, but it's still worth protecting.
Internal communications: Messages, chat logs, emails. Sometimes these contain embarrassing or proprietary information.
Business information: Details about partner restaurants, contracts, or expansion plans.
System architecture details: Information about how Grubhub's infrastructure is set up, which could help with future attacks.
Based on what Shiny Hunters has claimed and typical data theft practices, the stolen data most likely includes customer contact information and possibly internal documentation. That's enough to cause problems for individuals (spam, phishing, identity theft attempts) but not catastrophic like credit card theft would be.
The honest truth: Nobody outside Grubhub and the investigators knows exactly what was stolen. The company has incentives to downplay the scope. Shiny Hunters has incentives to exaggerate what they got to increase the extortion value. Somewhere in the middle is probably the truth.

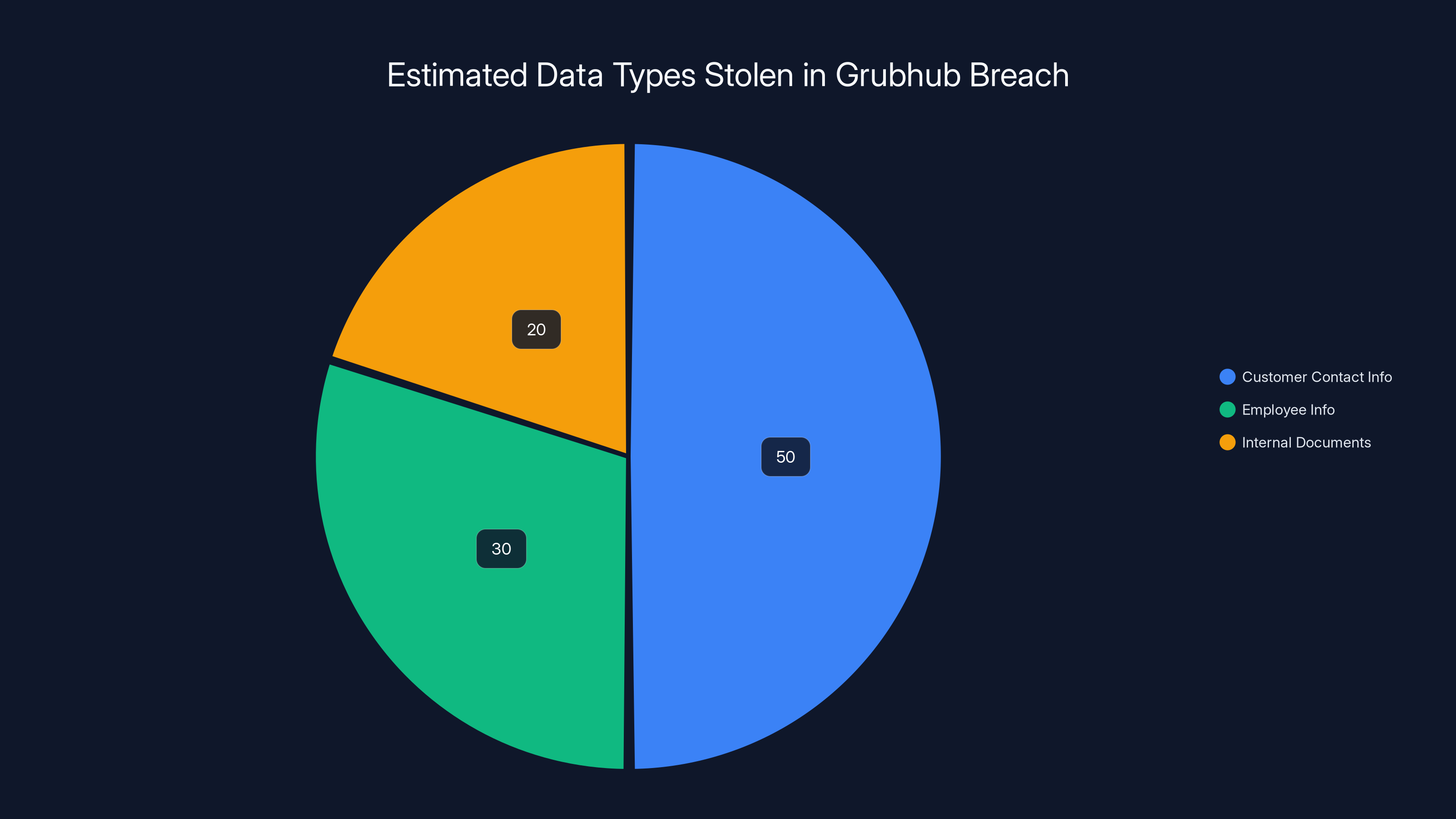
Estimated data shows customer contact information as the most likely stolen data type, followed by employee info and internal documents. Estimated data.
The Bigger Picture: 31+ Organizations Compromised
Grubhub isn't an isolated incident. It's part of a cascading breach affecting at least 31 confirmed organizations. Here are some of the major companies caught up in this:
Technology companies: Cloudflare, Palo Alto Networks, Dynatrace
Software vendors: SAP, multiple Saa S companies
Enterprise software: Various companies using Salesforce, Zendesk, or other cloud platforms
Financial and insurance companies: Banks and insurers relying on Salesloft/Drift for customer communication
The common thread: all these organizations either used Salesloft, Drift, or customer data was accessible through those platforms.
This creates a vulnerability multiplication effect. When a company with thousands of customers gets breached, each of those customers gets exposed. It's like dominoes falling. One bad security vulnerability becomes a cascade of compromises.
The full list of affected organizations keeps growing as researchers discover new victims. Bleeping Computer and other security outlets are maintaining running lists of confirmed breaches.

How Supply Chain Attacks Work (And Why They're So Effective)
To understand how Grubhub got breached despite presumably having decent security, you need to understand supply chain attacks.
Traditional security thinking focuses on defending your own network. You patch systems, install firewalls, train employees. But supply chain attacks ignore your defenses and attack through your suppliers instead.
Here's how it works in practice:
Step 1: Identify a trusted vendor. Salesloft and Drift are trusted vendors that thousands of companies rely on. They have access to sensitive customer data.
Step 2: Find a vulnerability. It could be a zero-day (previously unknown) vulnerability, a misconfiguration, or an unpatched system. In this case, it was apparently vulnerabilities in how Salesloft and Drift handled authentication and data access.
Step 3: Exploit and gain persistence. The attackers get in and create backdoors so they can maintain access even if the initial vulnerability is patched. They move slowly to avoid detection.
Step 4: Exfiltrate data. Once established, they have access to whatever data their victim companies have stored on the vendor platform. If Grubhub stores customer data, employee information, or business documents in Salesloft or Drift, Shiny Hunters can access it.
Step 5: Monetize. They steal the data and either sell it or extort the companies for payment to keep it secret.
The reason this works so well is that companies trust their vendors more than they trust the internet in general. You put strong authentication between you and the public internet, but you might have weaker controls between you and your trusted vendors. You assume vendors have good security, so you don't monitor their access as closely.
Shiny Hunters exploited exactly this—they got into a trusted vendor's systems, then accessed downstream customer data.

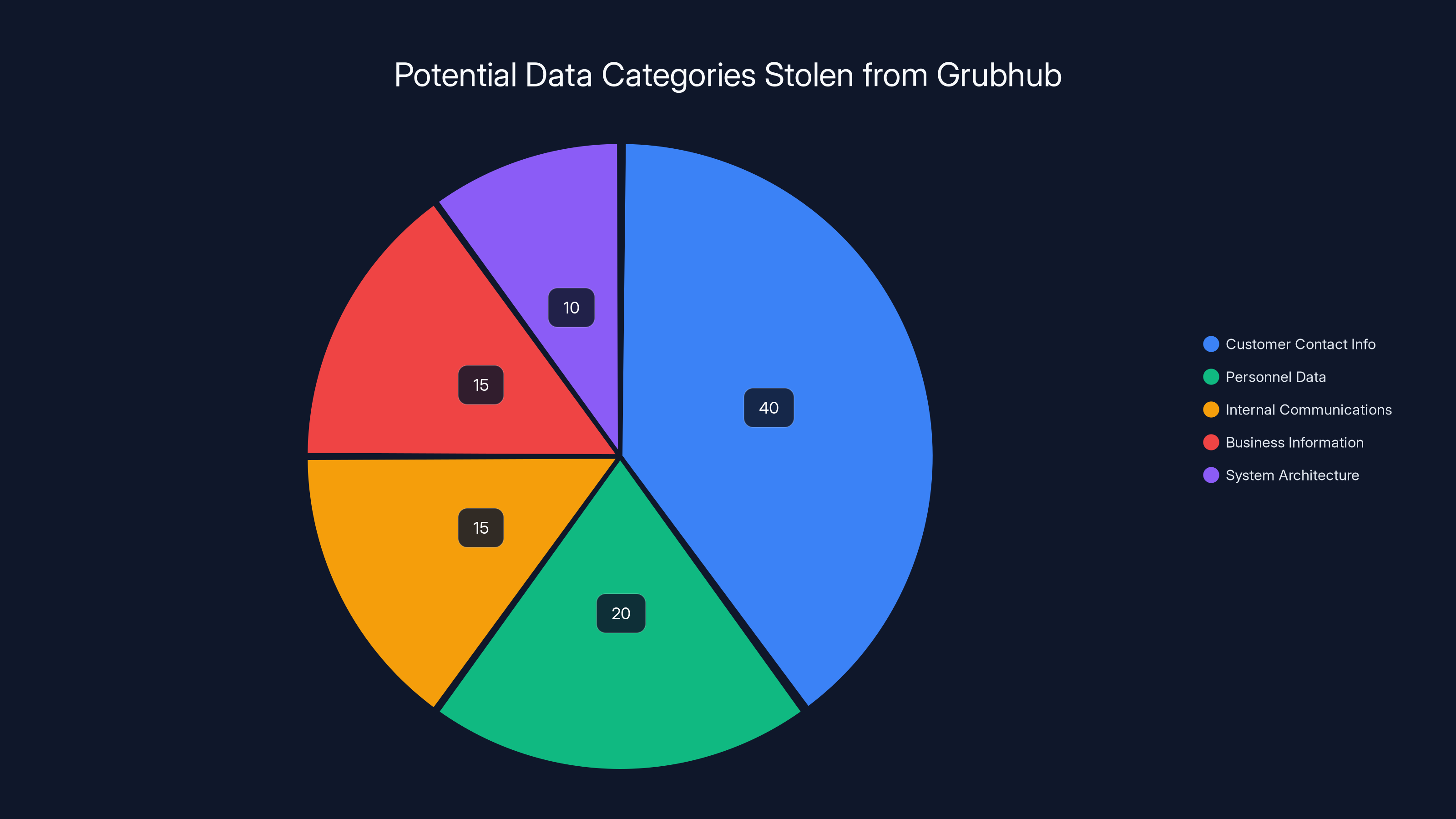
Estimated data suggests customer contact information is most likely to be stolen, followed by personnel data and internal communications. Estimated data.
Immediate Actions: What Grubhub Users Should Do
Okay, so your data might have been stolen. What actually matters right now? Here's what security experts recommend:
1. Enable two-factor authentication on your Grubhub account.
If your email address and password were in the stolen data, two-factor authentication prevents hackers from accessing your account even with your credentials. Go to your Grubhub account settings, find security options, and enable 2FA. Most accounts can use either SMS or an authenticator app—authenticator apps are more secure.
2. Change your Grubhub password, especially if you reuse it elsewhere.
If your password was stolen and you use the same password on other sites, attackers can access those accounts too. Create a unique, complex password for Grubhub. Better yet, use a password manager like 1 Password or Bitwarden to generate and store unique passwords.
3. Monitor your credit reports and set up fraud alerts.
While Grubhub says financial data wasn't stolen, the safest move is to check your credit reports anyway. You can get free annual reports from Annual Credit Report.com. Look for accounts you didn't open or inquiries you didn't authorize. If you see suspicious activity, contact the credit bureau immediately and consider placing a fraud alert.
4. Watch for phishing emails and calls.
Scammers will use the stolen data to send fake emails pretending to be from Grubhub, banks, or other legitimate companies. They'll try to get you to click links or provide information. If you get an unexpected email about your account, don't click links in the email. Instead, go directly to the company's website by typing the URL yourself.
5. Check Have I Been Pwned.
Visit Have I Been Pwned and search for your email address. This site tracks known data breaches and can tell you if your information has been exposed. You can even sign up for notifications if your email appears in future breaches.
6. Consider identity theft protection.
Services like Life Lock, Norton Life Lock, or Aura monitor your identity across the internet and alert you to suspicious activity. They're not essential for everyone, but they can be worth it if you're concerned about identity theft.

Businesses Affected: What Enterprise Customers Need to Know
If your company uses Salesloft, Drift, Salesforce, or Zendesk, you need a different response than individual users.
First, assume your data was accessed. Don't wait for official confirmation. Work with your security team to identify what data you had on these platforms and who it might impact.
Second, audit your own security. If an attacker got into your vendor's systems and could access your data, what does that tell you about your data protection? Do you have adequate encryption, access controls, and monitoring?
Third, communicate with your customers. If your customer data was potentially exposed, you might have legal obligations to notify them. Check your privacy policies and consult with legal. Transparency is better than being caught hiding a breach.
Fourth, review your vendor agreements. Most Saa S vendors have security clauses that specify what happens if they get breached. You might have grounds for compensation or service credits.
Fifth, implement data minimization. Going forward, don't store more data in third-party platforms than absolutely necessary. If a vendor doesn't need a particular data field, don't give it to them.

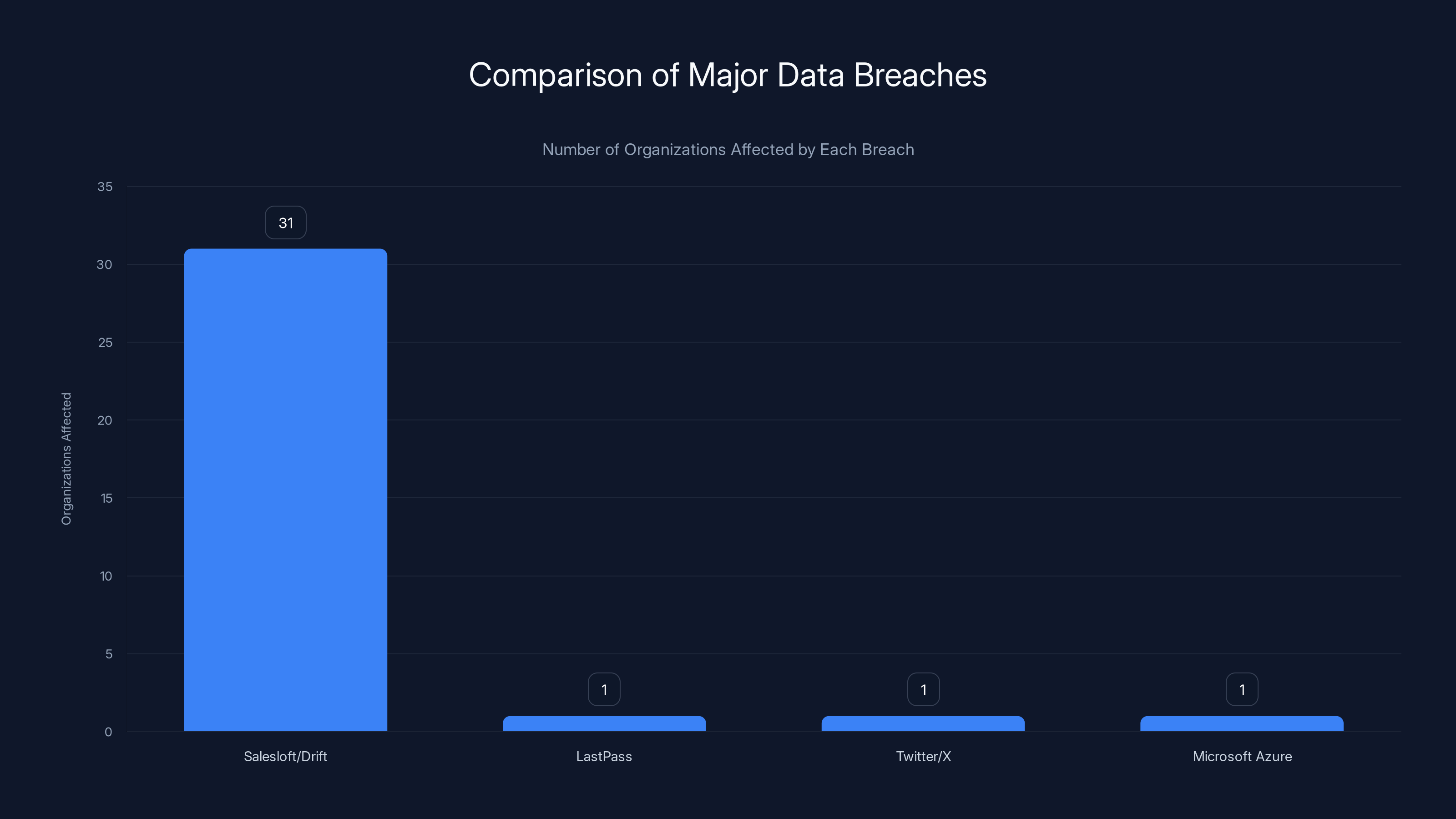
The Salesloft/Drift breach had a significant impact, affecting over 31 organizations, unlike other breaches that were contained to a single company.
How to Prevent This: Technical Defenses
From a company perspective, how do you prevent supply chain attacks? The honest answer is: partially. You can't guarantee it won't happen, but you can reduce risk significantly.
Implement zero-trust architecture.
Traditional security assumes that if you're inside the network, you're trusted. Zero-trust assumes everyone is untrustworthy until proven otherwise, even vendors. Every data access is logged and verified. This sounds paranoid, but it's increasingly how companies need to operate.
Encrypt data at rest.
If your data is encrypted and the attacker steals it, it's useless without the encryption keys. This doesn't prevent theft, but it reduces the damage.
Use VPNs for all vendor access.
Vendors shouldn't have direct internet access to your systems. They should connect through a VPN or dedicated network link that can be monitored and restricted.
Segment your network.
Not all systems should talk to all other systems. If a vendor only needs access to your CRM system, they shouldn't be able to see your financial systems or employee data.
Monitor for data exfiltration.
Most companies focus on preventing intrusions but don't monitor for data leaving their systems. Deploy network monitoring tools that watch for large data transfers, especially to external locations.
Keep systems patched.
This is the most basic security measure, but it's often neglected. The Salesloft/Drift vulnerabilities probably could have been prevented with timely patches.

The Extortion Game: Why Shiny Hunters Demanded Bitcoin
Understanding why Shiny Hunters demanded bitcoin in this situation explains a lot about how modern cybercrime operates.
Bitcoin is pseudonymous but traceable on the blockchain. That seems counterintuitive for criminals, but it's actually useful:
1. Proving payment. When a company pays ransom or extortion demands, they want to verify that the criminals received it. Bitcoin provides an immutable record.
2. Reputation. Criminal groups need reputation to operate. If they promise to delete data after payment, the blockchain proves they received payment. They need to follow through to maintain credibility.
3. Regulatory arbitrage. Bitcoin transactions are faster than international bank transfers. Criminals can move money across borders quickly.
4. Plausible deniability for buyers. From a company's perspective, paying a bitcoin address is easier to hide than a wire transfer. It's not that it's truly hidden, but it's one layer of separation.
Shiny Hunters has demanded payment in previous incidents and has sometimes been paid. In some cases, they've actually deleted the stolen data after payment. In other cases, they've sold the data anyway. This unpredictability is part of the extortion threat—you never know if you're wasting money.
Most experts recommend that companies don't pay extortion demands. It rewards criminal behavior and funds future attacks. But we don't know what Grubhub decided to do in this situation.

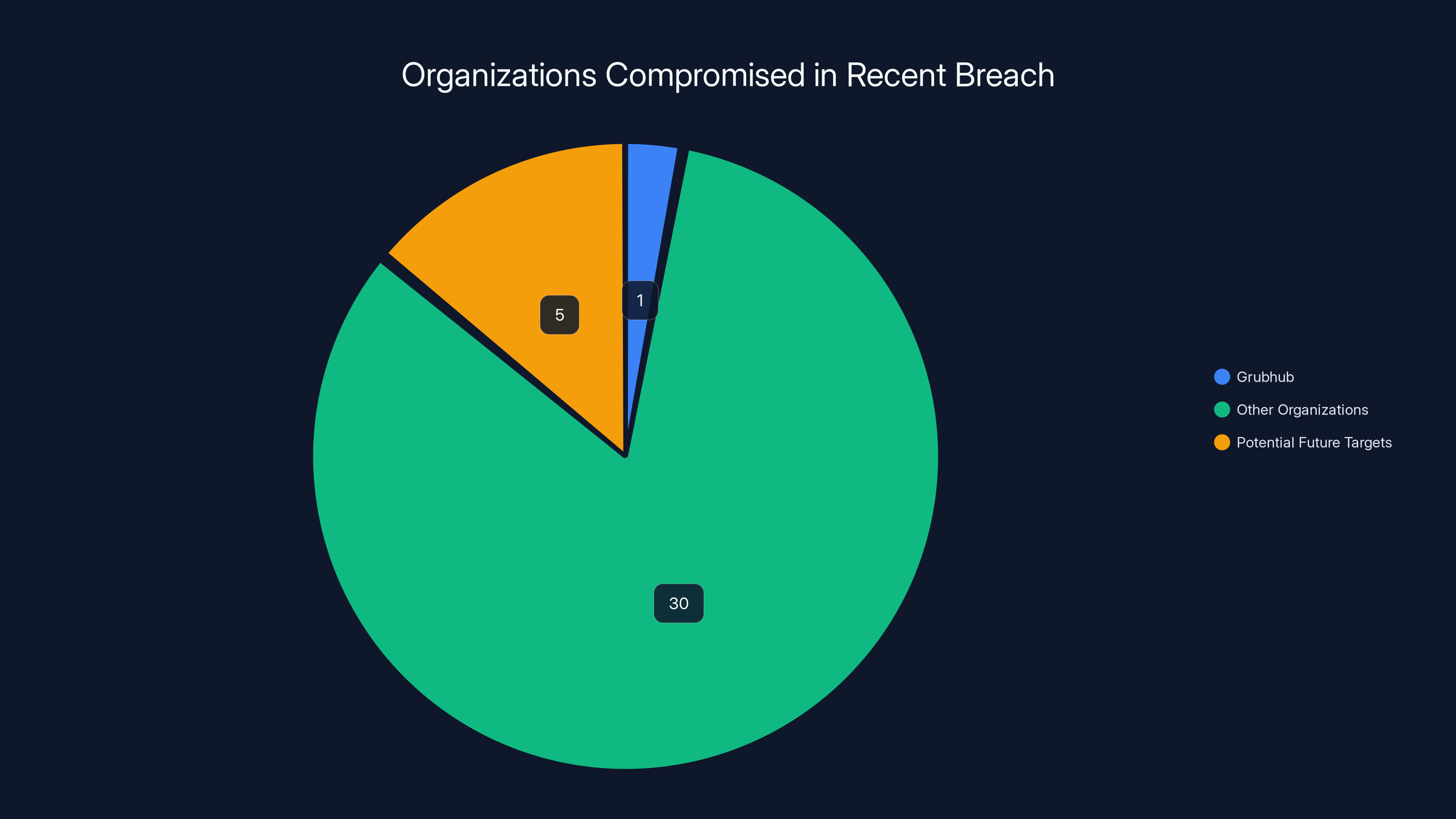
Grubhub is one of at least 31 organizations compromised in a recent breach, with potential for more targets. Estimated data.
Legal and Regulatory Fallout
This breach will have legal consequences for multiple organizations.
For Grubhub: They'll likely face lawsuits from affected users and possibly regulatory fines. The FTC has been increasingly aggressive about data breaches, and fining companies for inadequate security.
For Salesloft and Drift: As the platforms where the breach originated, they face similar liability. Companies using their platforms could sue them for damages. Their insurance policies might cover some of this, but the costs could be substantial.
For affected individuals: In some states, data breaches trigger mandatory notification requirements. You should receive notification emails from affected companies. In the future, you might be eligible for class action settlements.
Regulatory responses: The incident will probably lead to regulatory investigations and possibly new data protection requirements. GDPR in Europe and various US state privacy laws have data breach notification requirements.

What About Your Passwords and Security Questions?
Grubhub specifically said passwords weren't affected. That's worth understanding in detail.
Modern companies shouldn't store passwords in plaintext. Instead, they store password hashes—one-way mathematical functions of passwords. When you enter your password, the system hashes it and compares it to the stored hash. If they match, you're logged in.
If hackers get password hashes, they can't directly use them because hashes are supposed to be one-way. However, hackers can attempt to crack them through brute force—trying millions of password combinations and seeing which ones hash to match.
Grubhub saying "password hashes were not affected" suggests either:
- The attackers didn't access the database containing password hashes
- Grubhub uses such strong hashing with salt and stretching that cracking them would take thousands of years
Either way, it means your Grubhub password is relatively safe even if your email and name were stolen.
Security questions are different. If attackers have your name, email, address, and phone number, and they try to reset your password, they might be able to answer security questions like "What's your mother's maiden name?" (because it's searchable on genealogy websites) or "What's your pet's name?" (because people share this on social media).
That's why two-factor authentication is crucial—it prevents account reset attacks even if someone knows your password and security questions.

How This Compares to Other Major Breaches
To put the Grubhub breach in perspective, let's compare it to other recent major incidents:
Magnitude comparison:
| Breach | Year | Organizations Affected | Data Type | Extortion Used |
|---|---|---|---|---|
| Salesloft/Drift Supply Chain | 2025 | 31+ | Customer contact, business data | Yes |
| Last Pass Breach | 2022 | 1 | Password vaults, encryption keys | No |
| Twitter/X Hack | 2023 | 1 | Tweet data, user IDs | No |
| Microsoft Azure | 2020 | 1 | Cloud infrastructure logs | No |
What's notable about the Salesloft/Drift breach is the multiplier effect. One vulnerability affected dozens of organizations simultaneously. Most breaches are contained to a single company.

The Future: Is This Type of Attack Preventable?
Honestly? No. Supply chain attacks are here to stay, and they'll probably get worse.
The reason is asymmetry. Attackers only need to find one vulnerability. Defenders need to prevent every possible vulnerability. As software becomes more complex, the attack surface grows. Cloud computing makes this worse because you're now responsible for security you can't fully control.
What will probably change:
Mandatory vulnerability disclosures: Governments will likely require companies to disclose and patch vulnerabilities faster. The EU is already moving in this direction with regulations.
Vendor security certifications: Companies will demand that vendors meet security standards before granting access to data. Certifications like SOC 2 might become mandatory.
Insurance requirements: As cyber insurance becomes more expensive, insurance companies might require certain security practices.
Architectural changes: Companies will move toward more decentralized systems that don't store as much data in central locations.
Ai-based threat detection: As attacks become more sophisticated, AI-powered security systems will become necessary to detect sophisticated attacks in real time.
But fundamentally, the vulnerability game will continue. Attackers will find new exploits. Defenders will patch them. It's an endless cycle.

Protecting Yourself Long-Term
While we can't prevent breaches, we can minimize their impact with good personal security practices.
Use unique passwords everywhere. This is the single most important thing. If your password is reused across websites and one site gets breached, attackers can access all your accounts. A password manager like Bitwarden (free), 1 Password, or Dashlane solves this by generating and remembering unique passwords.
Enable 2FA on important accounts. Accounts with financial data, email access, or personal information should have two-factor authentication. It's not perfect, but it prevents password-only attacks.
Monitor your credit. Sign up for free credit monitoring from Annual Credit Report.com. Check your reports a few times per year.
Use a VPN for public Wi Fi. When you connect to public Wi Fi (coffee shops, airports), attackers on the same network can see your traffic. A VPN encrypts it. Services like Express VPN or Mullvad provide this protection.
Keep devices updated. Security patches fix vulnerabilities. If you delay updates, you stay vulnerable. Enable automatic updates on your phone, computer, and other devices.
Be skeptical of unexpected emails. Phishing is how most breaches start. Attackers send you emails pretending to be legitimate companies, hoping you'll click a malicious link or enter your password.

What Companies Should Demand from Vendors
If you work at a company that's evaluating a vendor relationship, here's what you should require:
Security audit results. Ask for SOC 2 Type II reports, penetration test results, or independent security audits. If they won't provide these, that's a red flag.
Encryption specifications. How do they encrypt data at rest and in transit? What encryption standards do they use?
Data retention policies. How long do they keep your data? Can you delete it on demand? What happens to your data if the company goes out of business?
Incident response plan. If they get breached, what's their process for notifying you? How quickly? What information will they provide?
Insurance coverage. Do they carry cyber liability insurance? How much? What does it cover?
Vendor security agreements. Get a security addendum to your contract that specifies security requirements and remedies if they breach security.
Regular security updates. Require that they patch vulnerabilities within a specified timeframe (e.g., critical vulnerabilities within 30 days).
Most vendors will balk at detailed security requirements. That's actually useful information—if they won't meet basic security standards, do you really want to trust them with your data?

The Role of Security Researchers and Ethical Disclosure
One interesting aspect of this breach is how it was discovered and disclosed. Security researchers at companies and independent researchers typically find breaches before the companies do.
When researchers find a vulnerability, they face an ethical dilemma: tell the company privately (ethical disclosure) or tell the public immediately (public disclosure). Private disclosure gives the company time to patch before attackers know about it. Public disclosure alerts the company quickly but also alerts attackers.
Most researchers follow the responsible disclosure model: notify the company privately, give them time to patch (usually 90 days), then publicly disclose.
In the case of Salesloft and Drift, researchers apparently discovered the breach and reported it responsibly. However, attackers were already exploiting the same vulnerabilities, so the damage was already done.
This is why "disclosure" matters for security. Public knowledge of a vulnerability incentivizes patches. Companies that know about a vulnerability they haven't patched yet get pressure to act faster.

FAQ
What is the Grubhub data breach?
The Grubhub data breach refers to an incident in 2025 where hackers accessed Grubhub's systems and stole company data. The breach occurred because attackers first compromised Salesloft and Drift, two customer communication platforms that Grubhub used. Through this supply chain attack, the hackers gained access to Grubhub systems. Security researchers determined that the Shiny Hunters cybercriminal group was responsible.
Was my credit card information stolen in the Grubhub breach?
According to Grubhub's official statement, financial information and order history were not compromised in this breach. However, the company acknowledged that some data was stolen, though they didn't specify exactly what. It's prudent to monitor your accounts regardless, but credit card data appears safe based on available information.
What data was actually stolen in the Grubhub breach?
Grubhub hasn't disclosed the complete inventory of stolen data, but based on what was accessed through the Salesloft and Drift platforms, it likely includes customer contact information (names, email addresses, phone numbers), employee information, and possibly internal business documentation. The exact scope depends on what data Grubhub had stored on these third-party platforms.
Should I change my Grubhub password?
Yes, you should change your password, especially if you use the same password on other websites. Grubhub stated that password hashes were not compromised, but changing your password is still a good practice. Use a unique password different from what you use elsewhere, and consider using a password manager like Bitwarden or 1 Password to generate and store complex passwords.
How many people were affected by the Grubhub breach?
Grubhub hasn't released a specific number of affected users. The breach is part of a larger incident affecting at least 31 organizations through the Salesloft and Drift vulnerability. Since millions of people use Grubhub, the potential number of people affected is substantial, though not all users' data may have been stolen.
Is Grubhub still safe to use?
While Grubhub was compromised in this incident, the company has stated that financial and order history information weren't affected. You can continue using Grubhub, but take precautions: enable two-factor authentication, use a unique password, monitor your account for suspicious activity, and consider using payment methods that offer fraud protection like credit cards. The breach doesn't mean Grubhub is fundamentally unsafe—it means a vulnerability in their vendors exposed their systems, which is a risk all companies face.
What is Shiny Hunters?
Shiny Hunters is a cybercriminal group known for data theft and extortion. Rather than encrypting data and demanding ransom like traditional ransomware groups, Shiny Hunters steals data and threatens to sell it on the dark web unless the victim pays. They've been active since at least 2020 and have targeted hundreds of organizations across various industries.
What should I do if I was affected by the Grubhub breach?
First, enable two-factor authentication on your Grubhub account. Second, change your password to something unique. Third, monitor your credit reports through Annual Credit Report.com for any suspicious activity. Fourth, check Have I Been Pwned to see if your email appears in other breaches. Fifth, watch for phishing emails and never click links from unexpected emails—go directly to company websites instead. You can also consider identity theft protection services if you're concerned.
How did the hackers access Grubhub if they didn't break into Grubhub directly?
This is a "supply chain attack." Grubhub uses Salesloft and/or Drift for customer communication and sales automation. When hackers exploited vulnerabilities in these platforms, they could access the data of all companies using those platforms. It's like breaking into a post office to get access to mail destined for thousands of homes. The hackers didn't target Grubhub specifically—they got it as a side effect of breaching a vendor.

Conclusion: Learning from the Breach
The Grubhub data breach is frustrating but not surprising. It's one of dozens of breaches happening constantly, affecting millions of people. What makes this one notable is the scale and the supply chain angle—it shows how interconnected our digital infrastructure is and how one vulnerability can cascade through an entire ecosystem.
For individuals, the breach is manageable. If you use Grubhub, the key steps are straightforward: unique password, two-factor authentication, credit monitoring. Those three things address the vast majority of risk.
For companies, the lessons are more complex. You can't fully prevent supply chain attacks, but you can:
- Minimize the data you store in third-party systems
- Implement strong access controls and monitoring
- Demand security certifications from vendors
- Have incident response plans ready
- Monitor for data exfiltration, not just intrusions
For society, the breach highlights why cybersecurity regulation is needed. The FTC is starting to crack down on companies with inadequate security practices. GDPR in Europe imposes heavy fines for breaches. More countries will likely follow with similar regulations.
The uncomfortable truth is that perfect security is impossible. Attackers only need to find one way in. Defenders need to prevent every possible attack. As software becomes more complex and interconnected, this asymmetry gets worse.
But "impossible" doesn't mean "hopeless." Better practices, stronger regulation, investment in security, and individual vigilance can reduce breaches' frequency and impact. The Grubhub breach is a wake-up call. The question is whether we'll respond by implementing the defensive measures that work, or whether we'll wait for the next breach and repeat this cycle again.
For now, enable that two-factor authentication. Change that password. Check your credit. You'll be fine.

Key Takeaways
- Grubhub confirmed unauthorized data access through third-party vendor vulnerability in Salesloft/Drift platforms, affecting financial data protection
- ShinyHunters cybercriminal group used supply chain attack to access 31+ organizations, demanding bitcoin extortion payments
- Users should enable two-factor authentication, change passwords, and monitor credit reports as immediate breach response steps
- Supply chain attacks cascade through trusted vendor relationships, making single vulnerabilities affect dozens of downstream companies simultaneously
- Long-term personal security requires unique passwords, credit monitoring, VPN use on public WiFi, and skepticism toward phishing emails
Related Articles
- Instagram Password Reset Incident: What Really Happened [2025]
- Brightspeed Data Breach Investigation: What Happened & What's Next [2025]
- Microsoft Copilot Prompt Injection Attack: What You Need to Know [2025]
- LinkedIn Comment Phishing: How to Spot and Stop Malware Scams [2025]
- Major Shipping Platform Exposed Customer Data, Passwords: What Happened [2025]
- Target Data Breach 2025: 860GB Source Code Leak Explained [2025]
![Grubhub Data Breach 2025: What Happened and How to Protect Yourself [2025]](https://tryrunable.com/blog/grubhub-data-breach-2025-what-happened-and-how-to-protect-yo/image-1-1768574540666.jpg)



