Cloud Security in Multi-Cloud Environments: Closing the Visibility Gap [2025]
Cloud adoption has stopped being a strategic choice. It's now table stakes. Your business runs on it. Your data lives in it. Your AI initiatives depend on it.
But here's the uncomfortable truth: the same move to the cloud that's supercharged your operations has also fundamentally broken how you defend them.
The problem isn't that cloud security is hard. It's that it's become chaotic. You're not defending one perimeter anymore. You're managing multiple cloud providers, each with their own security models, their own compliance frameworks, their own dashboards. Your team is stitching together half a dozen tools—some that barely talk to each other—trying to maintain visibility across an attack surface that's grown exponentially.
And the pressure is relentless. 69% of organizations now cite tool sprawl and visibility gaps as the primary barrier to good cloud security. Even worse, 66% admit they're not confident in their ability to detect and respond to cloud threats in real-time. That's not a technical problem anymore. That's an existential one.
Why? Because while you've been adding more tools, the threats have gotten faster. Misconfigurations that expose sensitive data. Identity sprawl that creates phantom access points. Data exposure happening at cloud speeds—detected hours too late. These aren't hypothetical risks. They're happening right now, across thousands of organizations, at a scale we've never seen before.
This guide walks through the real state of cloud security in 2025. We'll cover what's broken, why it's broken, and—most importantly—how to fix it without ripping out your entire infrastructure. Because the good news is this: most organizations don't need a complete overhaul. They need clarity, consolidation, and automation.
Let's start with the actual numbers, because they're worth understanding.
TL; DR
- 88% of organizations use hybrid or multi-cloud: The complexity of managing multiple providers creates exponential security challenges
- 69% struggle with tool sprawl: Too many point solutions create visibility gaps and slow incident response
- 66% lack confidence in real-time threat detection: Most automation only alerts; true autonomous remediation remains rare (11%)
- 77% of organizations identify identity and access risks as the biggest threat: IAM complexity is the #1 attack vector in cloud environments
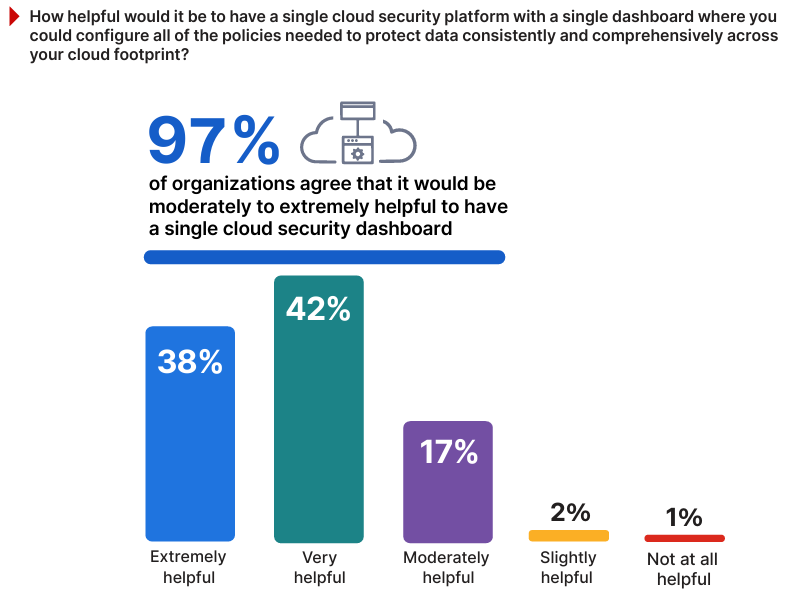
- Unified platforms are the answer: 64% of organizations prefer a consolidated security approach over stitched-together tools
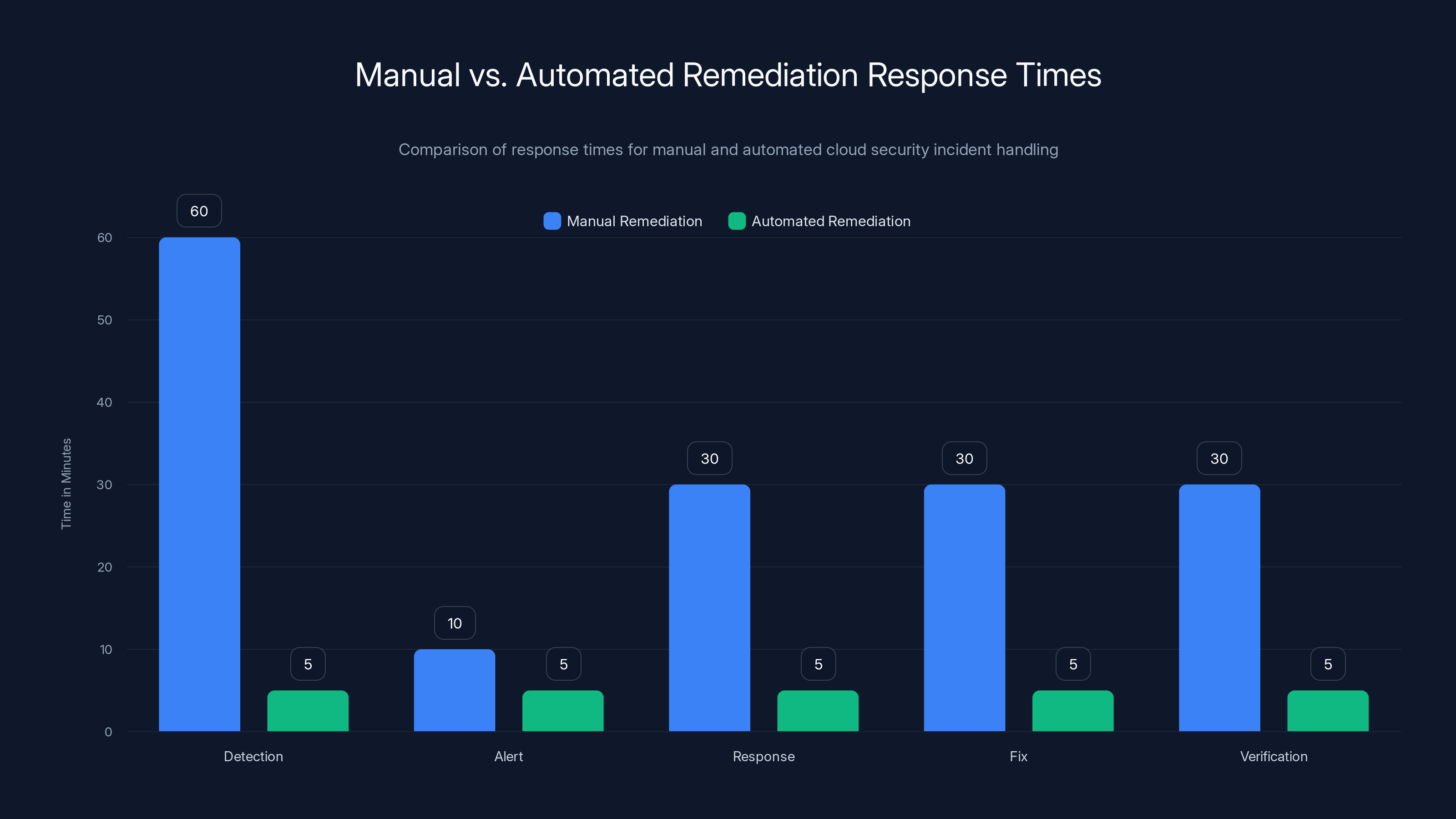
Automated remediation significantly reduces response times from up to 2 hours to just minutes, enhancing cloud security incident handling efficiency. Estimated data.
The Multi-Cloud Reality: Bigger Isn't Always Better
The shift to multi-cloud wasn't a deliberate security decision. It happened because the business demanded it.
One team needed AWS for machine learning workloads. Another needed Google Cloud for data warehousing. The enterprise standardized on Azure for its Microsoft ecosystem. Pretty soon, you've got three cloud providers, each with its own security controls, its own compliance posture, and its own blind spots.
The numbers tell the story: 88% of organizations now operate in hybrid or multi-cloud environments. And 81% use two or more providers simultaneously. That's not a niche scenario anymore. That's the new normal.
Here's what that means practically. Your data could live on AWS in the us-east-1 region. Your backups might be on Azure in Europe. Your Saa S applications are running on Google Cloud. Your on-premises data centers are still handling legacy workloads. Now, your security team is expected to maintain consistent security posture across all of it—using tools that were never designed to work together.
The theoretical benefit of multi-cloud is real: you reduce vendor lock-in, you can choose best-of-breed solutions for different workloads, and you distribute risk. But the practical overhead is brutal. Every additional cloud provider means additional compliance frameworks to understand, additional security controls to implement, and additional tools to manage.
The Attack Surface Has Exploded
Back when everything lived on-premises or in a single cloud account, you had a defined perimeter. You knew what needed defending. The security model was relatively straightforward: control the edges, monitor the core.
Multi-cloud obliterated that model.
Now you're defending:
- Multiple cloud accounts across multiple providers
- Dozens of data stores (S3 buckets, GCP Storage, Azure Blobs, databases, data lakes)
- Hundreds of workloads running across different availability zones and regions
- Thousands of APIs connecting cloud services together
- Millions of identity tokens issued and rotated constantly
- Exponential connectivity points between your clouds and your on-premises infrastructure
Each of these represents an attack surface. The aggregate creates an attack landscape that's fundamentally different from anything your security team has defended before.
Traditional cybersecurity tools were built for the era when the network perimeter was the primary defense. Firewalls, intrusion detection systems, network segmentation—all critical, but insufficient for cloud. Because cloud doesn't respect network boundaries. It exists at the application layer, the identity layer, the data layer. A misconfigured S3 bucket in AWS doesn't care about your firewall rules. Exposed credentials in a Git Hub repository don't care about your network segmentation.
Why Traditional Tools Fail at Cloud
Your legacy security tools were built assuming three things:
- Everything behind the firewall is trusted: Cloud blows this up. Your cloud instances live outside your firewall.
- Network isolation = security: Cloud doesn't isolate by network. It isolates by identity, by encryption, by policy.
- Static inventory: Your on-premises servers were relatively static. Cloud workloads spin up and down constantly. Your tools can't even see them all.
The result? A visibility gap.
More than two-thirds (69%) now blame tool sprawl and visibility gaps for creating cloud security barriers. This isn't a new problem discovered in 2025. This is a worsening problem that's been building for years. Organizations that stitched together five security tools in 2023 are now running ten. Each tool has its own API, its own dashboard, its own alert system, its own compliance reporting.
Your team is now spending 40% of their time just managing tools instead of defending systems.
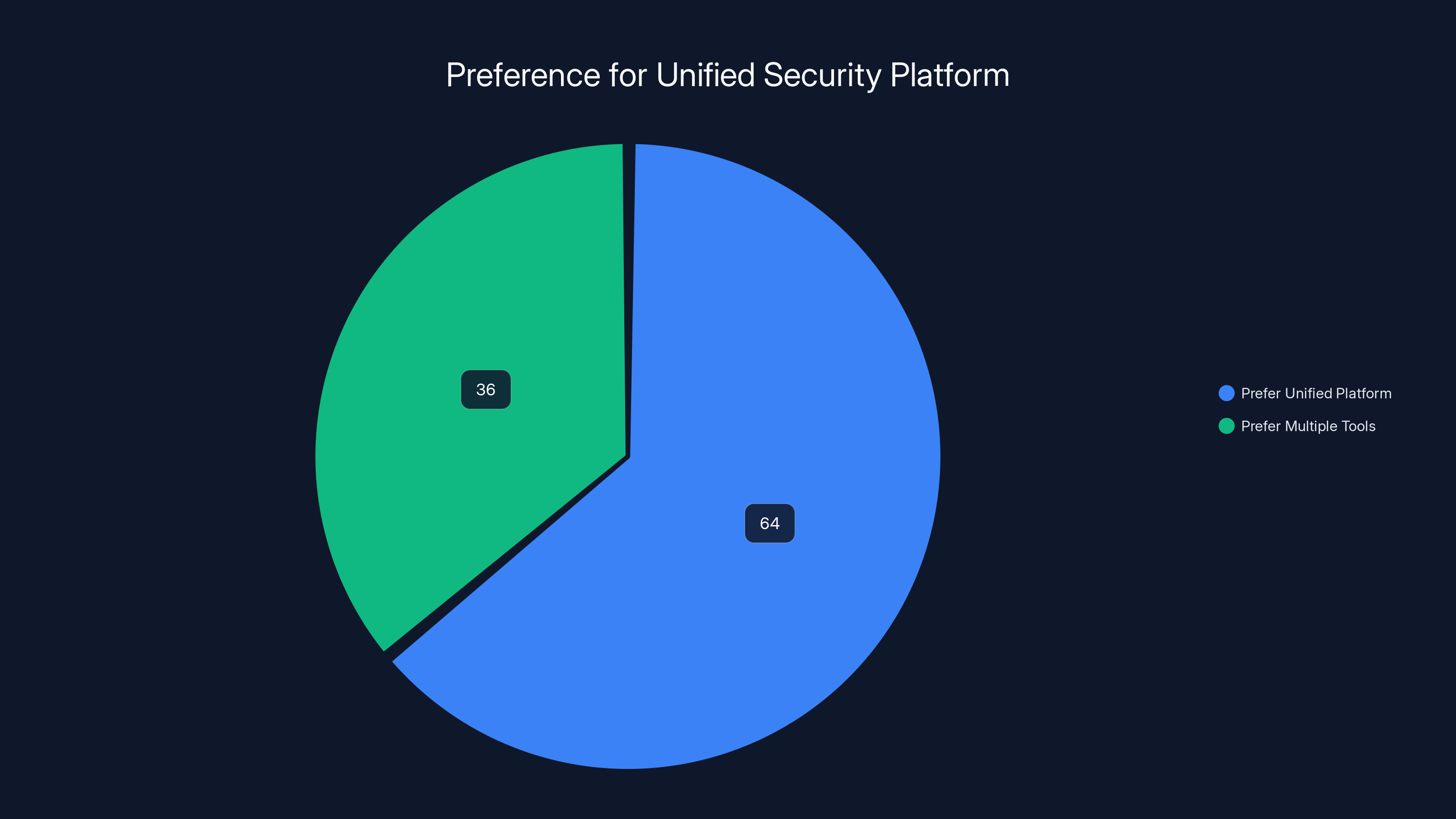
64% of organizations prefer a unified security platform over multiple tools, highlighting the challenge of tool sprawl. Estimated data for 'Prefer Multiple Tools' is calculated as the remainder.
Why Visibility Gaps Are the Gateway to Breaches
The most dangerous breaches aren't the ones that sneak past your defenses. They're the ones you don't know happened until weeks later.
Consider a real scenario: A junior developer creates an S3 bucket and, in a rush to deploy, sets it to public access. Inside that bucket: customer data, API keys, configuration files. The breach happens instantly. Your customers' data is exposed. But you don't find out until a researcher stumbles across it and reports it. Or worse, until a competitor buys the data.
How long did that bucket sit exposed? Days? Weeks? You don't know, because you couldn't see it.
This is the visibility gap in action.
Visibility gaps exist at three critical layers:
1. Asset Discovery Gaps
You don't know everything running in your cloud environment. I'm not being hyperbolic. Most organizations can't name all their cloud accounts, let alone all the resources inside them.
Why? Because cloud is cheap and fast. A developer spins up a test environment, then forgets about it. A pilot project gets launched in an isolated account that nobody documents. A contractor creates AWS resources during a project and doesn't clean them up. Before you know it, you've got dormant environments running in accounts you forgot you owned.
One financial services company discovered—during a security audit—that they had 47 AWS accounts they didn't know about. Forty-seven. Dormant projects, contractor-created accounts, environments spun up for proof-of-concepts. Some had been running for three years without anyone realizing they existed.
Each undocumented account is a potential blind spot. And blind spots are where attackers hide.
2. Configuration Visibility Gaps
Even when you know a resource exists, you often don't know if it's configured securely.
Take S3 buckets again. You might know you have 200 S3 buckets. But do you know which ones allow public access? Which ones have logging enabled? Which ones have versioning turned on? Which ones are replicated to another region? Which ones contain encrypted data?
Your team might think they've implemented security policies, but without continuous visibility into how those policies are actually configured, you're flying blind.
A typical large organization has hundreds of thousands of configuration combinations across their cloud environment. A security misconfiguration could be anywhere. Finding it manually? Impossible. Finding it without the right tools? Still pretty impossible.
3. Access and Permission Visibility Gaps
Identity and access management is where most breaches start. And it's where visibility gaps cause the most damage.
Here's why: cloud identity is deeply different from on-premises identity. In your data center, you have Active Directory, maybe some LDAP. You've got RBAC (role-based access control) that's been tuned over years. You understand the permission model.
Cloud identity is fragmented. You've got IAM roles in AWS, custom roles in Google Cloud, Azure AD assignments in Microsoft Azure. You've got service accounts, managed identities, federated identities, temporary credentials. You've got permissions scattered across resource-based policies, identity-based policies, and session policies.
Adding a single user's access to a multi-cloud environment might require touching twelve different systems. Removing that access when they leave your organization? Even trickier. Did you remember to revoke their access in the Azure account created six months ago? What about the temporary credentials issued to their service account?
The data confirms the problem: 77% of organizations identify identity and access as their biggest cloud security risk. That's not surprising. It's also the hardest problem to solve without proper visibility.
The Tool Sprawl Problem: Why More Tools Make You Less Secure
The natural response to visibility gaps is to buy another tool. Get better visibility? Buy a cloud security posture management (CSPM) tool. Detect threats better? Buy a cloud workload protection platform (CWPP). Need better access controls? Buy a cloud access security broker (CASB).
Now you have three new tools, each with its own console, its own API, its own alerts, its own reporting.
You've made the problem worse.
64% of organizations agree they would prefer a unified security platform rather than stitching together multiple tools. But only a small fraction have actually made that transition. Why? Because consolidating tools is hard. It requires ripping out existing integrations, training teams on new platforms, and migrating years of configuration.
So instead, organizations keep layering on new point solutions.
Here's what tool sprawl actually does to your security:
Alert Fatigue and False Positives
Tool #1 alerts on a potential security violation. Tool #2 disagrees—it says this behavior is normal. Tool #3 isn't even aware the event happened because it wasn't integrated. Your team gets three conflicting signals and spends two hours investigating something that was a false positive.
Multiply that by dozens of alerts per day, and you've got a team that's drowning in noise. Real threats get missed because your team is exhausted from chasing false positives.
Integration Nightmares
Your tools don't talk to each other. Tool #1 (CSPM) discovers a misconfiguration. Tool #2 (threat detection) identifies suspicious access. These are clearly related—someone found a gap and exploited it. But without integration, your team has to manually correlate the alerts.
Integrating security tools is a special kind of torture. APIs have rate limits. Data formats don't align. Latency between tools causes timing mismatches. You spend hundreds of engineering hours building Zapier workflows and custom scripts just to make your tools talk.
Inconsistent Policies
Your CSPM tool enforces one security policy. Your CWPP tool enforces another. They contradict in three places. Your cloud team implements Policy A because that's what CSPM recommends. Your security team expects Policy B because that's what they configured in CWPP. Nobody's happy, and nothing's consistent.
Inability to Respond at Cloud Speed
Cloud threats move fast. A misconfiguration exists for minutes before an attacker finds it. A compromised credential is used to exfiltrate data in seconds. Your response needs to be automated and instant.
But if your remediation workflow requires manual steps across three different tools, you're already too slow.
The Hidden Costs
Tool sprawl also has a financial cost that most organizations don't fully account for.
You're paying for Tool #1, Tool #2, and Tool #3. Overlap? Sure, there's overlap. You're essentially paying for redundant capabilities. But you can't eliminate the redundancy because each tool has unique strengths, and your team has spent time learning all three.
You're also paying in human capital. Your security team needs to maintain expertise across all three tools. You need to invest in training. You need to staff multiple on-call shifts because nobody understands all three systems well enough to be the sole expert.
A typical organization with five security tools is paying roughly 30-40% more for capabilities than they would with a consolidated platform. And they're getting less security out of it.
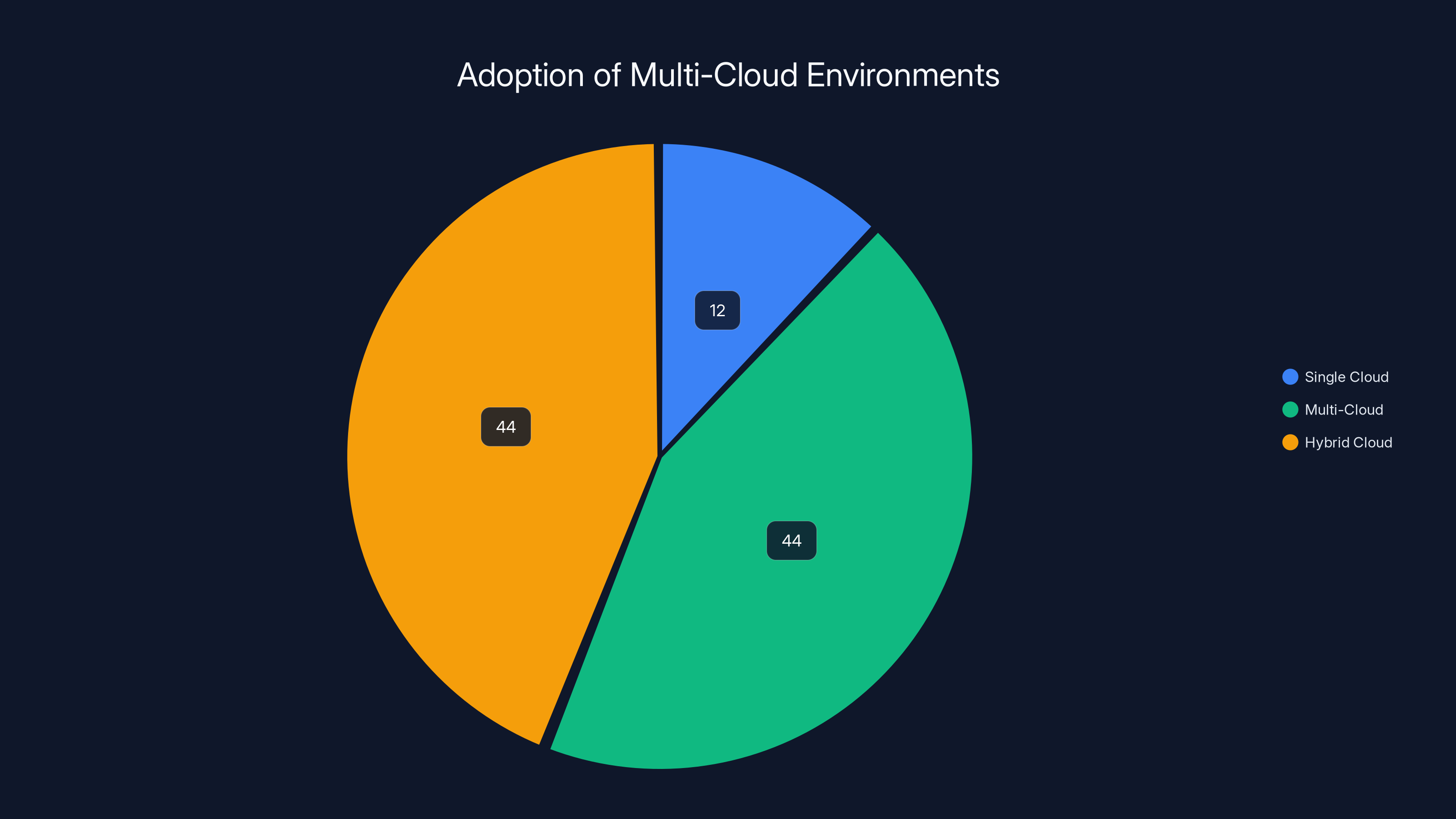
An estimated 88% of organizations operate in hybrid or multi-cloud environments, with 81% using two or more providers. Estimated data.
Misconfigurations: The Most Expensive Security Problem
Here's something that keeps CISOs up at night: the biggest breaches aren't from sophisticated zero-days. They're from basic misconfigurations.
70% of organizations identify misconfigurations as a critical risk in their cloud environment. And that's probably understating the problem. Most organizations don't actually know how many misconfigurations they have.
A misconfiguration isn't malicious. It's not even usually negligent. It's usually just... human. A developer needs to debug something, so they temporarily relax security permissions. They forget to re-tighten them. A team is moving fast to launch a feature, and they copy security settings from a non-production environment to production. Nobody tests the configuration before shipping.
These things happen every day.
Common Misconfigurations and Their Impact
Public S3 buckets: A bucket gets created, some data is uploaded, bucket policy is misconfigured, suddenly your customer data is accessible on the public internet. Security researcher finds it, reports it, you have a PR nightmare.
Overly permissive IAM roles: A developer creates an IAM role with broad permissions to speed up development. That role gets attached to a Lambda function. The Lambda gets compromised. Attacker now has broad permissions across your AWS account. Game over.
Disabled encryption: Encryption adds a tiny bit of latency. Developer disables it to squeeze out performance. Nobody catches it in code review. Now production data is sitting unencrypted in a database accessible to anyone with network access.
Missing security group rules: A security group is supposed to restrict traffic to a specific port. It gets accidentally opened to 0.0.0.0. Your database is now exposed to the internet. It gets scanned, attacked, and potentially breached.
Logging disabled: You disable Cloud Trail logging to save a few dollars on storage costs. Now when a breach happens, you have no audit trail. You can't determine what was accessed, when, by whom, or what was exfiltrated.
Each of these misconfigurations seems minor in isolation. Collectively, they represent your primary attack surface.
Why Misconfigurations Are Hard to Prevent
Misconfigurations happen because cloud is fundamentally permissive. By default, resources are created with broad permissions. You have to actively restrict them. It's the opposite of most legacy systems, where resources are locked down and you grant permissions as needed.
Cloud is also very fast. You can create a new database in 30 seconds. Configure security? That takes 15 minutes. In an organization moving at cloud speed, people take shortcuts.
Cloud is also complex. The number of configuration options for a single S3 bucket is staggering. Bucket policy, IAM policy, ACLs, block public access settings, versioning, logging, replication, encryption, CORS, website settings, lifecycle policies, tags... miss one setting and your bucket is misconfigured.
Cloud providers aren't doing developers any favors. AWS, Google Cloud, and Azure all want you to move fast. The most frictionless path is usually the least secure path.
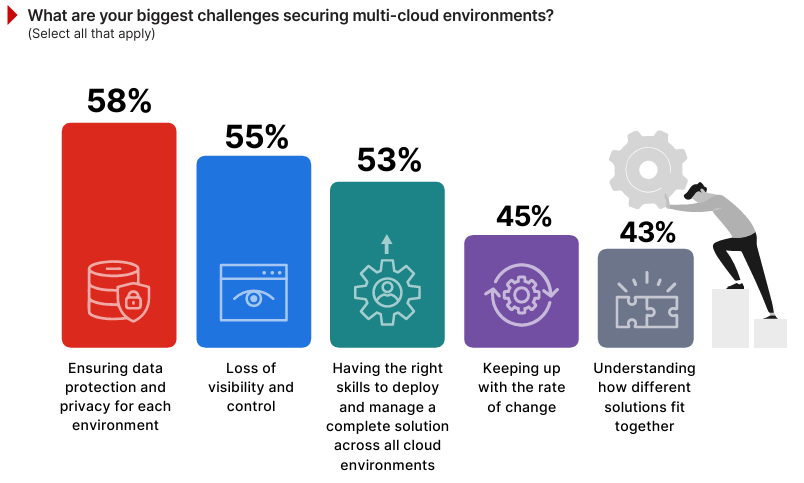
Identity and Access Management: The Weakest Link in Cloud Security
If misconfigurations are your most common problem, identity and access management is your most critical problem.
77% of organizations identify identity and access management as their biggest cloud security challenge. This isn't a technical vulnerability. It's an architectural problem with how cloud identity works.
Here's the core issue: cloud fundamentally changed how identity works.
In your data center, you had a relatively simple model. Users logged into computers. Computers authenticated against Active Directory. Active Directory determined what resources the user could access. When a user left the company, you removed them from AD, and they were locked out of everything.
Cloud broke this model.
The Identity Explosion
Now you have human identities, service identities, application identities, federated identities, and temporary identities. Let's break down each:
Human identities: Your employees. But in cloud, human identity is fragmented. You've got users in Azure AD, users in AWS IAM, users in Google Cloud, users in dozens of Saa S applications. When an employee changes departments, do you update their access in all of these places? Usually not.
Service identities: Applications need to authenticate as something. In cloud, this means service accounts. You might have dozens per application. Managing lifecycle (creation, rotation, revocation) is a nightmare.
Federated identities: You're probably federating identity from your corporate directory. But the federation is different for each cloud provider. Azure AD federation works one way. AWS federation (via SAML) works differently. Google Cloud federation works yet another way.
Temporary identities: Containers, serverless functions, Lambda functions, Cloud Run jobs—they all need short-lived credentials. Managing this at scale requires sophisticated tooling.
Machine identities: Your infrastructure as code tools, your CI/CD pipelines, your automation orchestration—they all need credentials. Managing machine identity lifecycle is complex and often overlooked.
Access Control Complexity
Once you've figured out who (or what) needs access, you need to determine what they can access.
In cloud, this means understanding:
- Identity-based policies: What can this user or service account do?
- Resource-based policies: Who can access this specific resource?
- Attribute-based access control (ABAC): What can users do if they have certain attributes (team, department, cost-center)?
- Session-based policies: What can this user do in this specific session?
- Condition-based policies: What can this user do from this IP address, at this time of day, from this device?
You might have a policy that says a user can read S3 buckets (identity-based). But a specific bucket has a policy that denies that user access (resource-based). Which one wins? The deny, in most cases. But if you don't understand that, you'll be confused.
Add multiple cloud providers into the mix, and the complexity becomes overwhelming. AWS IAM policies look different from Google Cloud IAM policies, which look different from Azure RBAC.
The Privilege Creep Problem
Here's a problem that most organizations completely miss: privilege creep.
Your employee joins the organization. They get assigned to Team A. Team A needs access to Resource X. So you grant them permission to Resource X.
Six months later, they move to Team B. Does someone remove their access from Resource X? Maybe. Often not.
A year later, they're now on Team C. They've accumulated access across five different teams. They have permissions to resources they haven't touched in a year. If their credentials get compromised, the attacker has access to systems they shouldn't.
Multiply this across an organization with high turnover, and you've got a permission model that's grown far beyond what's actually necessary.
Why MFA Isn't Enough
Every security team enforces multi-factor authentication. Good. But MFA addresses only one part of the problem: proving that you are who you claim to be.
It doesn't address:
- Whether you should have that access: An attacker with a compromised password AND a stolen MFA token is in. MFA just made it a little harder.
- What you're doing with that access: You can log into your AWS account. But are you doing something normal? Or are you about to exfiltrate your entire database? MFA doesn't know.
- Whether your access is still needed: You logged in six months ago. Do you still need access? MFA doesn't care.
- Whether you're the right person: You have valid credentials. But are you the actual employee? Or someone using stolen credentials? In a large organization, MFA can't distinguish.
MFA is essential. But it's not sufficient for cloud security.

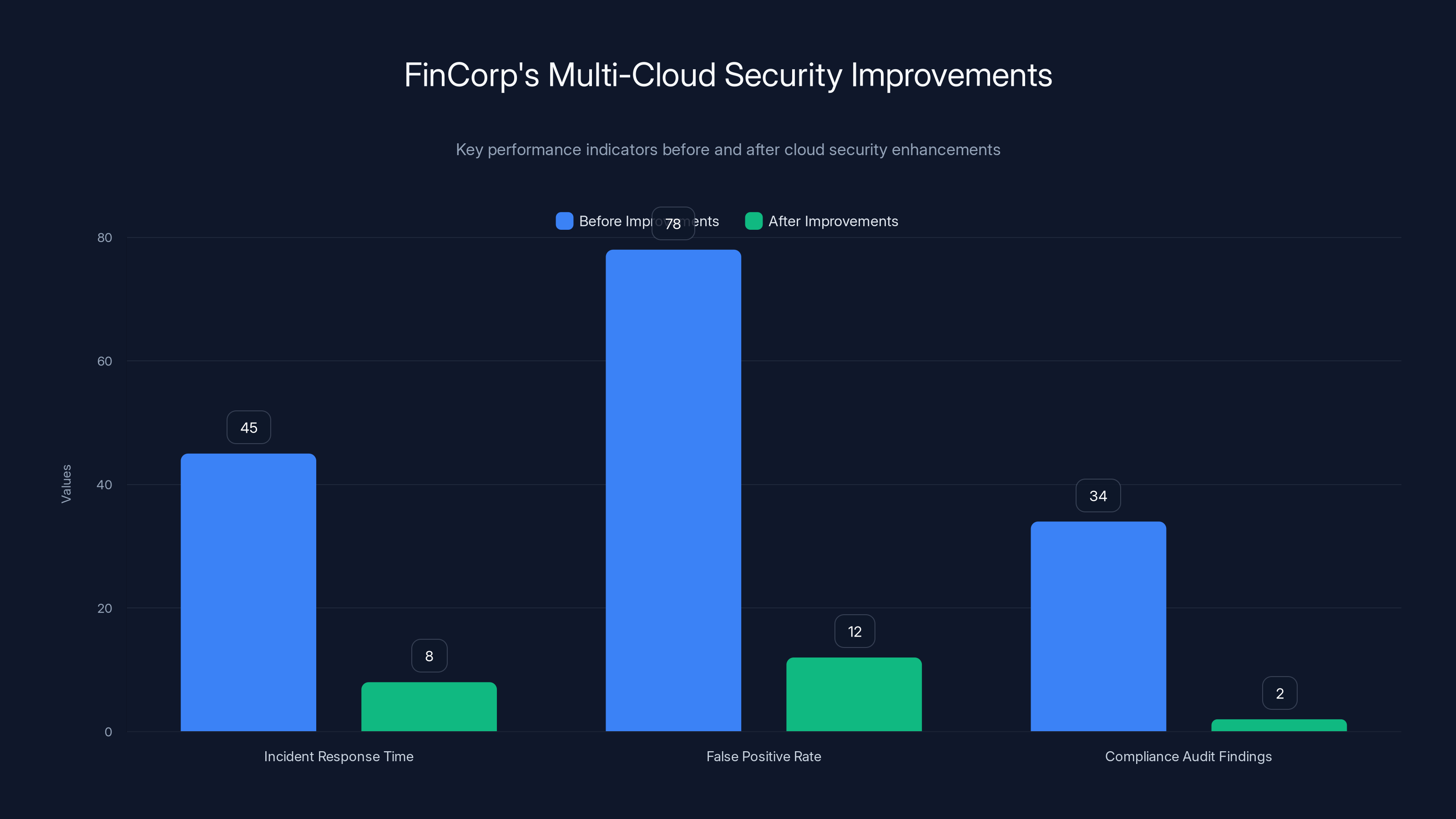
FinCorp significantly improved their cloud security posture, reducing incident response time from 45 to 8 minutes, false positive rate from 78% to 12%, and compliance audit findings from 34 to 2.
The Automation Gap: Alerting Without Action
Here's a brutal statistic: only 11% of organizations have autonomous remediation in their cloud security.
Meaning: 89% of organizations are still manually remediating security incidents.
This is the biggest operational failure in cloud security. Because cloud threats move at machine speed. Your team responds at human speed. And humans are always too slow.
Let's think about what happens when a security incident occurs:
- Attacker finds a misconfigured S3 bucket (minutes)
- Attacker begins exfiltrating data (seconds to minutes)
- Your monitoring detects unusual activity (minutes to hours, if it detects at all)
- Alert fires in your SIEM (seconds after detection)
- Your on-call engineer gets paged (seconds to minutes)
- Engineer wakes up / sees the notification (seconds to minutes)
- Engineer investigates (minutes)
- Engineer determines the appropriate response (minutes)
- Engineer makes the fix (minutes)
- Engineer verifies the fix is working (minutes)
Total time elapsed: 15 minutes to 2 hours. In a serious incident, the damage is already done.
Automated remediation collapses this timeline:
- Attacker finds a misconfigured S3 bucket (minutes)
- Attacker begins exfiltrating data (seconds to minutes)
- Your monitoring detects unusual activity (seconds to minutes)
- Alert fires and triggers automated remediation (seconds)
- Misconfiguration is automatically fixed (seconds)
- Attack is stopped (within seconds to minutes)
- Human team is notified to investigate what happened (minutes)
Total time elapsed: seconds to minutes. Drastically different outcome.
Why Automation is Hard
Automation isn't hard because the technology doesn't exist. It's hard because it's scary.
What if the automated remediation breaks something? What if it makes things worse? What if it takes action based on incomplete information?
These are legitimate concerns. An automated remediation system that aggressively removes permissions could lock out your team from critical systems. An automated remediation system that terminates instances could cause an outage.
So security teams stay conservative. They implement alerting without remediation. They page engineers at 3 AM to manually investigate and respond. The system works, but it doesn't scale.
Low-Risk, High-Volume Remediation
The path forward is to start with low-risk, high-volume remediation.
Examples:
- Unused access removal: If a user hasn't accessed a service in 90 days, automatically remove their permissions. Low risk (they can request re-access), high volume (thousands of access removal per month).
- Misconfiguration fix: If an S3 bucket is detected as publicly readable when it shouldn't be, automatically restrict the bucket policy. Low risk (blocking unintended access), high volume (hundreds per month across many organizations).
- Encryption enablement: If a database is detected without encryption, automatically enable encryption. Low risk (doesn't break application functionality), high volume (dozens per month).
- Logging enablement: If Cloud Trail or audit logging is disabled, automatically enable it. Low risk (just adds logs), high volume (dozens per month).
- Expired credential revocation: If a long-lived credential hasn't been rotated in 180 days, automatically revoke it and alert the owner. Low risk (prompts re-authentication), high volume (hundreds per month).
Start here. Build trust in automated remediation. Then gradually increase the risk/complexity of automated remediations.

Data Exposure: The Consequence of Visibility Gaps
Visibility gaps, misconfigurations, and weak access controls all lead to one outcome: data exposure.
66% of organizations identify data exposure as a critical risk in their cloud environment. And this is probably understating the actual risk.
Data exposure in cloud has a different character than data exposure in legacy systems. In your data center, data breach meant someone got past your perimeter and your network controls. In cloud, data exposure often means someone found publicly accessible data or exploited a permission misconfiguration. It's faster, easier, and—crucially—it's harder to detect.
Types of Cloud Data Exposure
Public cloud storage: S3 buckets, GCS buckets, Azure blobs that are readable by the internet. Most common, most avoidable, most frequently exploited.
Cloud databases without authentication: A Mongo DB instance deployed without authentication requirements. A Redis cache with no password. A Postgre SQL database with default credentials. Attackers use automated scanners that find thousands of these per day.
API keys and secrets in configuration files: Credentials hardcoded into source code, committed to Git Hub, exposed. Attackers scrape public repositories, find credentials, and have instant access to your cloud infrastructure.
Unencrypted backups: You backed up your database to S3. You forgot to encrypt the backup. Now your entire database is accessible to anyone with the right permissions or who stumbles across the backup.
Temporary credentials left behind: A developer got temporary AWS credentials for debugging. They left the credentials in their shell history, or in an environment variable, or on a USB drive. Attacker finds it. Has temporary access to your infrastructure.
Logs containing sensitive data: Your application logs contain customer PII. You ship those logs to Cloud Watch. Someone with Cloud Watch access can read customer data. You never intended to expose it, but you did.
The Speed of Data Exposure
Here's the scary part: data exposure happens fast.
Researchers have shown that a publicly accessible S3 bucket is discovered within minutes of creation. Automated scanners are continuously probing cloud infrastructure looking for exposed data. You create a bucket at 10:00 AM. By 10:03 AM, it's been scanned. If it's publicly readable, its contents are cataloged.
The attacker might not access your data immediately. They might just catalog it and move on. But the exposure window is measured in minutes, not hours or days.
Your incident response timeline needs to match that speed. If you detect the exposure at 10:15 AM, you're already 15 minutes in. If you need 30 minutes to investigate and respond, the attacker has already been gone for 15 minutes.
Data Classification and Governance
The first step in preventing data exposure is understanding what data you have and where it lives.
Most organizations have blind spots here. You know you have customer data, but do you know exactly where it lives? Is it in S3 buckets? In Dynamo DB tables? In RDS databases? In cached Redis instances? In logs? In backups? In all of the above?
You need:
- Data classification: What data do you have? Is it public? Internal? Confidential? Regulated? This needs to be standardized and documented.
- Data location mapping: Where does each classification of data live in your cloud environment? Which S3 buckets? Which databases? Which services?
- Data access policies: Who should be able to access each classification of data? What's the business justification for their access?
- Data exposure detection: Automated scanning that continuously checks whether classified data is exposed to unauthorized users.
Without this, you're relying on luck. You hope nobody finds your exposed data. You hope your developers don't accidentally commit credentials. You hope your security team catches misconfigurations before attackers do.
Replacing hope with automated detection is the only viable path.
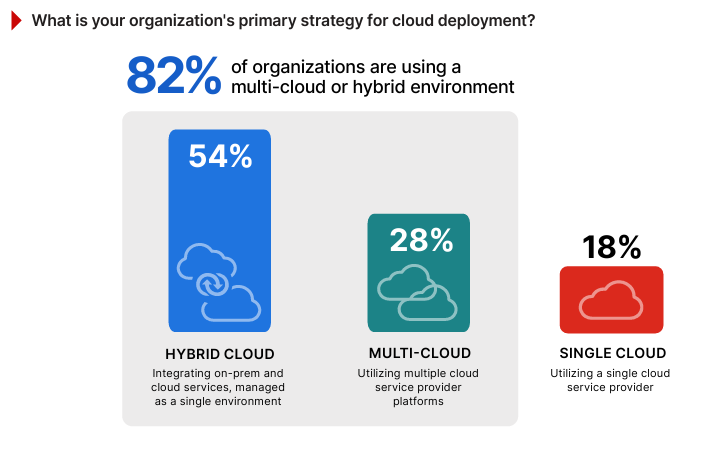
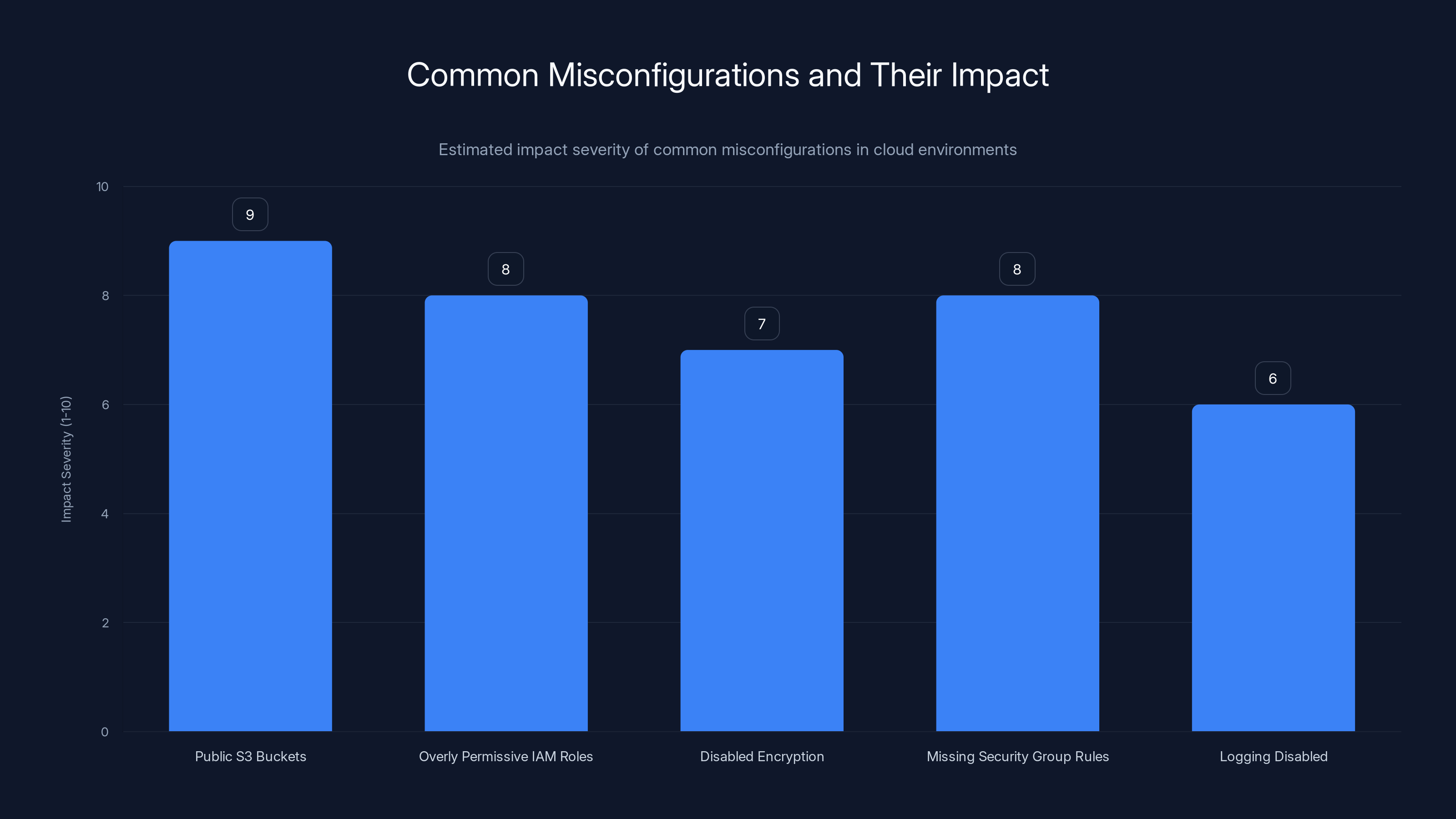
Public S3 buckets and overly permissive IAM roles are among the most severe misconfigurations, posing significant security risks. Estimated data.
Multi-Cloud Compliance: The Hidden Complexity
Compliance used to be simpler. You had one data center, probably in one country. You needed to comply with maybe three regulations. HIPAA if you handled health data. PCI-DSS if you processed credit cards. SOC 2 because vendors demanded it.
Now you've got data spread across three continents on four different cloud providers. And compliance requirements vary significantly by geography and data type.
Here's what makes multi-cloud compliance hard:
Divergent Compliance Models
AWS has one way of demonstrating compliance. Google Cloud has a slightly different way. Azure has yet another way.
You need to maintain SOC 2 certification. But SOC 2 audits require detailed evidence of your controls. The evidence looks different for each cloud provider. You need separate audits for each cloud, or you need to run a unified audit that somehow aggregates evidence across divergent platforms.
Data Residency Requirements
Some regulations require data to stay in specific countries. GDPR requires EU personal data to stay in the EU. Russia has local storage requirements. Australia has data residency rules. Brazil has LGPD compliance needs.
Now multiply that by multiple cloud providers. You might need to ensure your data in AWS eu-west-1 stays in Europe, while your Azure data stays in Australian regions. Different rules, different enforcement mechanisms, different audit trails.
Audit Trail Consistency
Compliance requires audit trails. Who accessed what data? When? Why? For how long?
But audit trails are formatted differently across providers. AWS Cloud Trail logs look different from Google Cloud audit logs, which look different from Azure Activity Log.
Consolidating these logs into a single searchable system is non-trivial.
Control Framework Misalignment
Your organization probably uses a control framework like NIST or CIS. You've mapped your controls to that framework. But different cloud providers have different ways of implementing equivalent controls.
How do you demonstrate that your controls are equivalent when they're implemented differently across providers? It's a compliance headache.
The Path Forward: Consolidation, Automation, and Visibility
So far, we've covered the problems. Now let's talk about solutions.
There are five core principles to improving multi-cloud security:
1. Establish Unified Visibility
You need to see everything. Every account, every resource, every configuration, every identity, every permission.
This means:
- Cloud asset management (CAM): A system that automatically discovers and inventories all your cloud resources across all providers
- Configuration management database (CMDB): Tracks the configuration state of every resource
- Identity and access governance: Tracks all identities, all permissions, and all access patterns
- Data discovery and classification: Finds sensitive data wherever it lives
Unified visibility is the foundation. Everything else builds on top of it.
2. Implement Tool Consolidation
Stop stitching together point solutions. Find platforms that can deliver broad capabilities across your multi-cloud environment.
Look for platforms that provide:
- Cloud security posture management (CSPM): Configuration assessment and compliance
- Cloud workload protection platform (CWPP): Runtime threat detection and response
- Identity and access management (IAM): Unified access control across clouds
- Data loss prevention (DLP): Data exposure detection and prevention
- Security information and event management (SIEM): Centralized logging and correlation
Consolidating to three or four platforms instead of ten is a massive operational improvement.
But beyond tools, consider whether Runable or similar automation platforms could help orchestrate your security responses across these tools. Being able to define automated workflows that trigger across multiple security tools is critical.
3. Connect Risk Domains
Stop treating identity risks, infrastructure risks, data risks, and application risks as separate problems.
A misconfigured S3 bucket (infrastructure risk) is only dangerous if someone with access (identity risk) exploits it to steal data (data risk). These risks are connected.
Your security platform needs to correlate across risk domains. When an identity-based alert fires at the same time as an infrastructure alert, the system should recognize that these might be related and escalate appropriately.
This requires data integration between systems. It's non-trivial. But it's the difference between a tool that generates noise and a tool that delivers signal.
4. Automate Low-Risk, High-Volume Remediation
Start small. Identify the most common, lowest-risk security issues in your environment. Automate responses to those issues.
Examples:
- Public bucket found? Automatically block public access. Alert the team to investigate.
- Unused credential found? Automatically revoke it. Ask the owner if they need it back.
- Encryption not enabled? Automatically enable it. Notify the team of the change.
- IAM permission never used in 180 days? Automatically remove it. Let the user request re-access if needed.
Build success with low-risk automation. Build trust in the system. Then gradually expand to more complex automations.
5. Extend Security Beyond Cloud
Your cloud environment doesn't exist in isolation. You've got:
- On-premises infrastructure and data centers
- Saa S applications that your team uses
- Endpoints (laptops, phones, tablets)
- Network infrastructure
- API gateways and proxies
Your security platform needs visibility and control across all of these. Cloud is important, but it's not the entirety of your infrastructure.
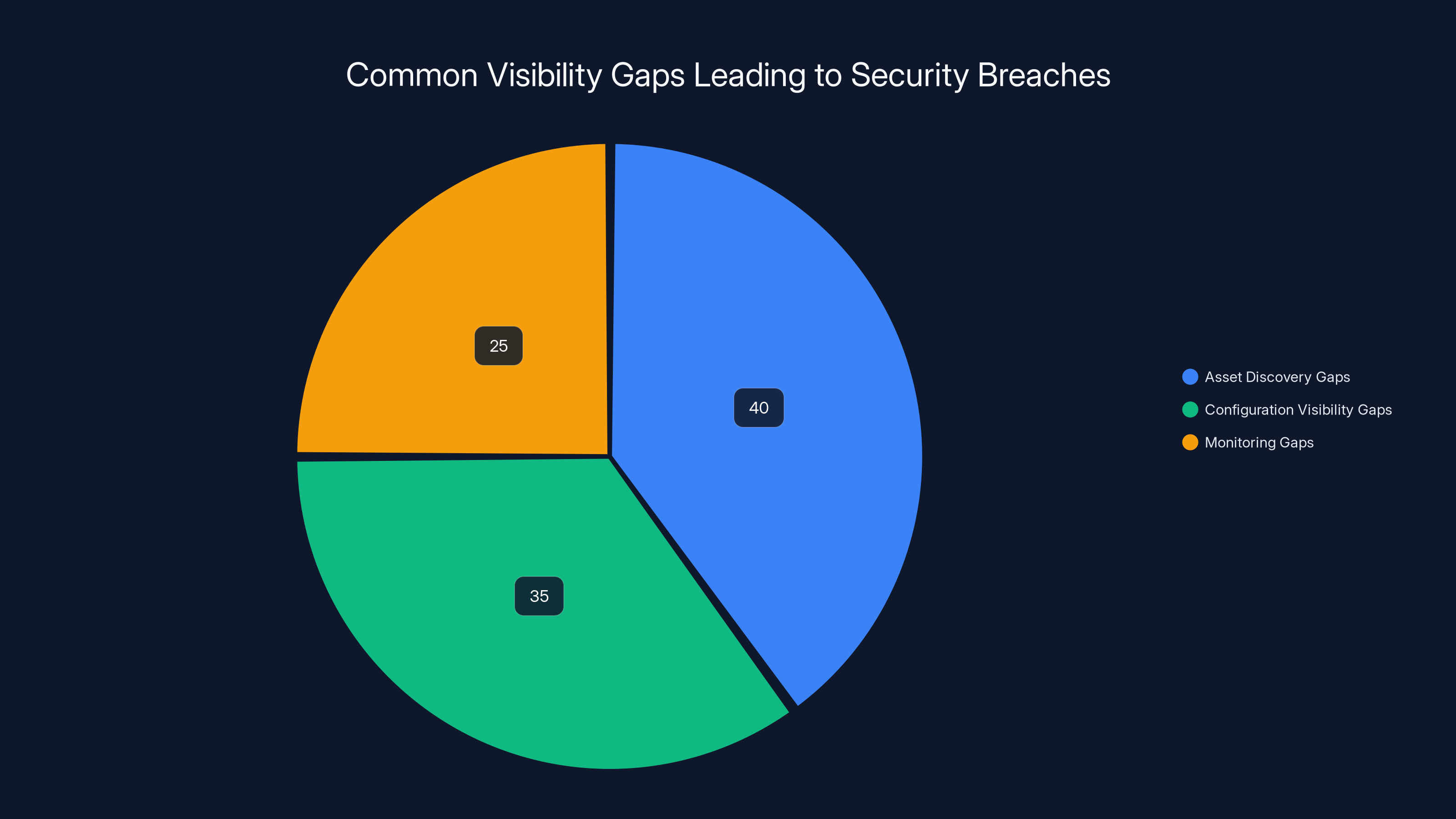
Asset discovery gaps account for the largest portion of visibility issues, estimated at 40%, highlighting the importance of comprehensive asset management in cloud environments.
Building Your Multi-Cloud Security Team
Tools are necessary but not sufficient. You also need people.
Multi-cloud security requires different skills than traditional security. Your team needs to understand:
- Cloud platforms: Deep knowledge of AWS, Google Cloud, and/or Azure
- Infrastructure as code: Terraform, Cloud Formation, Deployment Manager
- Cloud-native security: Kubernetes security, container security, serverless security
- Dev Ops practices: Continuous integration, continuous deployment, the development workflow
- Security automation: Python, shell scripting, CI/CD pipeline integration
Here's the hard truth: these skills are in short supply and high demand. You're competing with every other organization for the same talent.
How do you build this team?
Hire for Cloud-Native Mindset
You don't necessarily need someone who's spent ten years in cloud security. They might not exist at your salary level anyway.
Instead, hire people with strong fundamentals in security who are intellectually curious about cloud. Hire developers who have cloud experience but want to move into security. Hire people from cloud-first startups who've never worked in a traditional enterprise but understand how to scale systems.
Train them. Give them time to learn. Invest in cloud certifications (AWS certified, GCP certified, Azure certified, or all three).
Automate Away Manual Work
The best way to scale a small security team is to eliminate manual work. Automation doesn't replace security staff. It frees them up to do higher-value work.
Instead of having your team manually review cloud configurations every week, implement automated scanning that continuously checks configurations. Instead of having your team manually remove permissions when users leave, implement automated access removal workflows.
Your team should spend time designing security architectures and responding to novel threats. Not running reports and fixing the same recurring issues.
Partner with Platform Teams
Cloud infrastructure is usually managed by platform engineers or Dev Ops teams, not security. But security is everyone's responsibility.
Work closely with platform teams. Help them implement security in infrastructure as code. Automate security checks into CI/CD pipelines. Make security easy to do right and hard to do wrong.
If your platform team has to choose between shipping a feature fast (doing it wrong) and shipping it securely but slowly (doing it right), they'll ship it wrong. Fix the incentives. Make the secure path the fast path.
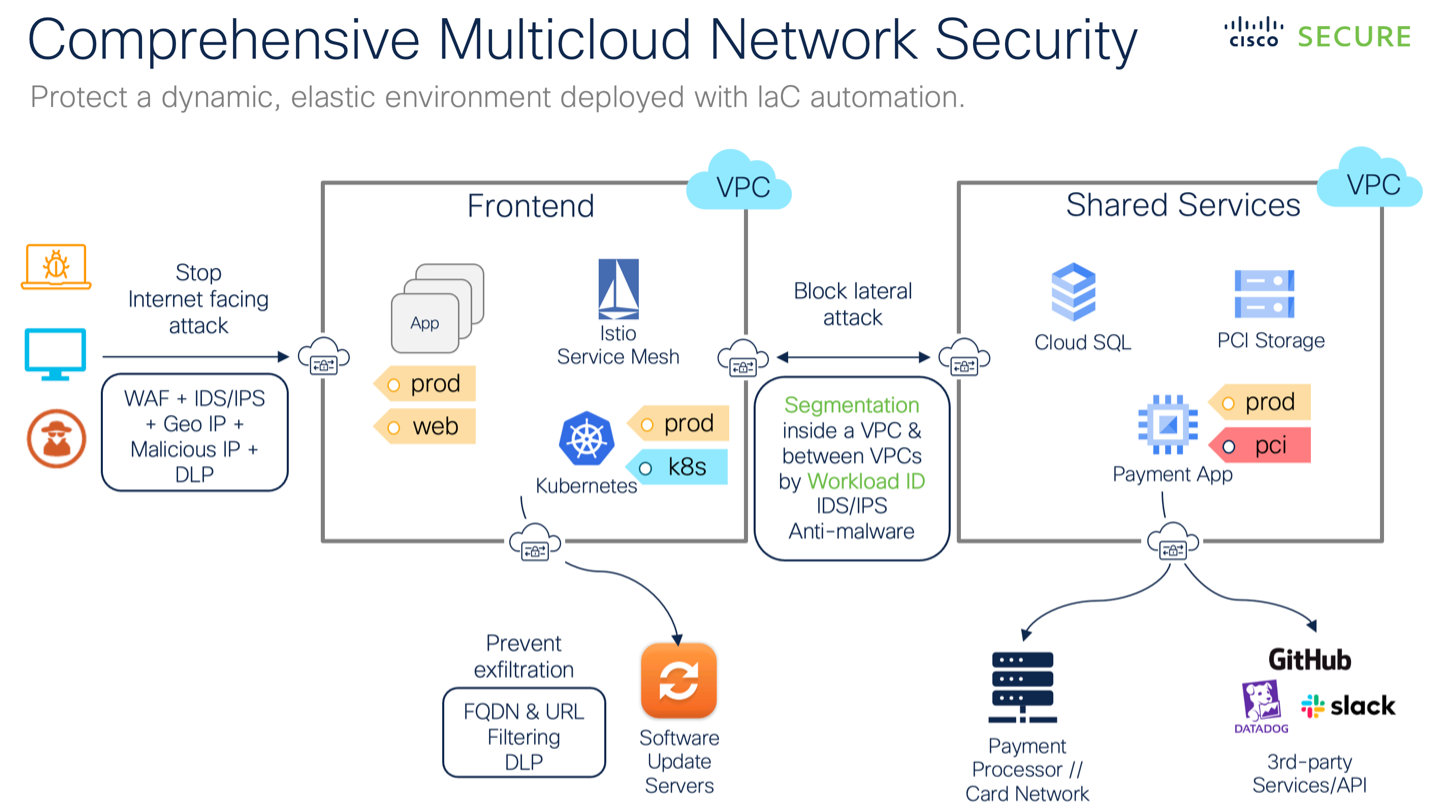
Real-World Case Study: A Financial Services Company's Multi-Cloud Journey
A mid-size financial services firm—let's call them Fin Corp—had grown to $200 million in annual revenue with 800 employees. They ran primarily on-premises but had started moving to cloud.
Here's what they faced:
The Problem: They were running workloads across AWS (primary), Azure (for Microsoft Dynamics), and Google Cloud (for specific data analytics) without a unified security strategy. They had four separate SIEM tools because different teams had implemented different solutions. Their security team of eight people was drowning in alerts.
What They Did:
-
Unified visibility first: Implemented a cloud security posture management (CSPM) tool that discovered 23 misconfigurations in their first scan, including two publicly accessible databases. They fixed those immediately.
-
Tool consolidation: Over six months, they consolidated four SIEM tools into one platform that natively supported all three cloud providers. This reduced alert volume by 65% through better deduplication and alert tuning.
-
Automated remediation for low-risk issues: They automated removal of unused IAM permissions, which they found had grown to 8x what was actually needed. This reduced their permission surface area significantly.
-
Identity governance: They implemented a unified identity platform that managed access across all three clouds from a single source of truth. Removed 92 ex-employee access profiles that were still active.
-
Compliance integration: Consolidated three separate compliance frameworks (SOC 2, HIPAA, PCI-DSS) into one unified attestation process.
Results After 12 Months:
- Incident response time: Improved from 45 minutes average to 8 minutes average
- False positive rate: Dropped from 78% to 12%
- Compliance audit findings: Reduced from 34 to 2 (both minor)
- Mean time to detect (MTTD): Dropped from 6 hours to 12 minutes
- Security team morale: Improved dramatically—they were solving problems instead of fighting tools
The entire project cost
ROI was clear within the first year.

Emerging Threats in Multi-Cloud Environments
As organizations have moved to cloud, so have attackers. New threat vectors have emerged that are specific to multi-cloud environments.
Cloud-Native Malware
Malware is evolving to exploit cloud-specific vulnerabilities. Cryptominers that target Kubernetes. Ransomware that spreads through container registries. Malware that exploits cloud-specific APIs.
AWS, Azure, and Google Cloud all publish threat intelligence. Stay updated on what's actively being exploited.
Supply Chain Attacks Through Cloud
Attackers are compromising cloud-hosted dependencies. A library in the Python Package Index gets compromised. Your CI/CD pipeline pulls it. Now you've pulled malicious code into your supply chain.
Or an attacker gains access to a cloud infrastructure vendor and modifies infrastructure as code templates. You deploy that template. You've now deployed compromised infrastructure.
These are hard to defend against without deep visibility into your supply chain.
Credential Theft at Scale
Cloud credentials are more valuable than traditional credentials. One set of cloud credentials might give access to thousands of resources. Attackers are specifically targeting credential theft.
Phishing campaigns that target cloud credentials. Credential scraping from Git Hub. Exploitation of poorly secured CI/CD pipelines. All of these are increasing in sophistication.
Lateral Movement in Cloud
Once an attacker gains initial access to your cloud environment, lateral movement is often trivial. Overly permissive IAM roles mean they can move from one resource to another easily. Lack of segmentation means they can access resources that should be isolated.
Traditional network-based lateral movement detection doesn't apply in cloud. You need cloud-specific detection mechanisms.

The Future of Cloud Security: Predictions for 2025-2026
Based on current trends, here's what we expect to see in cloud security over the next 12-24 months:
Autonomous Cloud Security Becomes Standard
More organizations will move beyond alerting to autonomous remediation. As organizations get more sophisticated and tools become more reliable, they'll trust automation with broader responsibilities.
Expect to see organizations automatically quarantining suspicious workloads, revoking anomalous permissions, and isolating compromised instances without human intervention.
AI-Driven Threat Detection Matures
Machine learning for threat detection is still in early stages in cloud. But it's improving rapidly. Expect AI-driven anomaly detection to become significantly better at distinguishing between legitimate unusual activity and actual attacks.
This will help solve the false positive problem that's plaguing security teams today.
Consolidation Accelerates
The era of best-of-breed point solutions is ending. Organizations are consolidating. This consolidation will continue as integrated platforms become more capable.
Expect to see some of the smaller security vendors acquired by larger platform vendors. Expect organizations to move from five-tool stacks to two or three integrated platforms.
Zero Trust Goes Cloud-Native
Zero trust principles (verify every access request, assume breach) are becoming mainstream. But traditional zero trust implementations are built for on-premises networks.
Cloud-native zero trust implementations are emerging. Expect these to become more standardized and easier to implement.
Compliance Automation Becomes Table Stakes
Manual compliance audits are expensive and error-prone. Continuous compliance verification is becoming possible. Expect compliance to shift from annual audits to continuous attestation.
Organizations that can demonstrate continuous compliance will have competitive advantages.

FAQ
What is multi-cloud security and why is it important?
Multi-cloud security refers to the strategies and tools used to protect data and infrastructure spread across multiple cloud providers like AWS, Azure, and Google Cloud. It's critical because 88% of organizations now operate in multi-cloud environments, and each additional cloud provider exponentially increases complexity and attack surface. Without proper multi-cloud security, organizations face visibility gaps, misconfigurations, and data exposure.
How do visibility gaps lead to security breaches?
Visibility gaps occur when organizations can't see all their cloud assets, configurations, and access controls. When you don't know what resources exist in your cloud environment, you can't protect them. Attackers exploit undocumented accounts, misconfigured resources, and overly permissive access that your team doesn't even know about. Research shows it takes an average of 43 days to discover a breach in cloud environments, primarily because visibility gaps prevent early detection.
What is tool sprawl and why is it a problem?
Tool sprawl happens when organizations accumulate many point-solution security tools instead of using integrated platforms. The problem is that these tools don't talk to each other, creating integration nightmares, alert fatigue, and inconsistent policies. 69% of organizations blame tool sprawl for creating security barriers. Instead of making you more secure, more tools often make you less secure by creating gaps, confusion, and false positives that overwhelm your team.
What are the most critical cloud security misconfigurations?
Common misconfigurations include public S3 buckets exposing data, overly permissive IAM roles granting excessive permissions, disabled encryption on sensitive data, security groups opened to the entire internet (0.0.0.0/0), and disabled logging on critical resources. 70% of organizations identify misconfigurations as a critical risk. These misconfigurations are often not malicious—they're usually the result of developers moving fast or debugging issues and forgetting to re-secure resources.
How can organizations implement automated remediation safely?
Start with low-risk, high-volume remediations like removing unused permissions, blocking public bucket access, enabling encryption, and activating logging. These have minimal downside if implemented incorrectly and high frequency of occurrence. Build trust in automated remediation with these low-risk scenarios, then gradually expand to more complex automations. Organizations should also implement strong approval workflows and maintain audit trails of all automated actions.
What's the difference between identity-based and resource-based cloud security policies?
Identity-based policies specify what permissions an identity (user, service account, role) has. Resource-based policies specify who can access a specific resource. In cloud environments, both matter. A user might have permission to read S3 buckets (identity-based), but a specific bucket might have a policy denying that user access (resource-based). The deny typically wins, but understanding which policy controls access is crucial for proper access management across multiple cloud providers.
How should organizations approach compliance in multi-cloud environments?
Multi-cloud compliance requires establishing consistent controls across different cloud providers while respecting provider-specific compliance models. Organizations should implement data classification systems to understand what data they have and where it lives, establish data residency policies for regulatory requirements, consolidate audit trails across providers, and use continuous compliance monitoring instead of annual audits. The goal is unified compliance posture despite using divergent cloud platforms.
What skills do cloud security teams need?
Cloud security professionals need deep knowledge of specific cloud platforms (AWS, Azure, Google Cloud), infrastructure as code tools (Terraform, Cloud Formation), cloud-native technologies (Kubernetes, containers, serverless), Dev Ops practices, and security automation scripting. These skills are in high demand and short supply. Organizations should hire people with strong security fundamentals and cloud curiosity, then invest in training and cloud certifications to build expertise.
How can organizations reduce incident response times in multi-cloud environments?
Incident response times improve through unified visibility (knowing what happened), consolidated tooling (reducing investigation complexity), automation (eliminating manual response steps), and cloud-native detection mechanisms (triggering on cloud-specific indicators). Organizations that move from manual remediation (45+ minutes) to automated remediation (under 10 minutes) typically see dramatic improvements in breach impact and faster threat containment.
What role does identity and access management (IAM) play in cloud security?
IAM is the primary attack vector in cloud environments, with 77% of organizations identifying identity and access as their biggest security risk. Proper IAM includes managing human identities, service identities, federated identities, and temporary credentials across multiple cloud providers. Organizations should implement identity governance to prevent privilege creep, automated access removal when employees leave, and continuous auditing of who has access to what resources.
Conclusion: The Multi-Cloud Security Path Forward
Cloud adoption isn't slowing down. If anything, it's accelerating. The businesses that are winning aren't those that resisted the cloud. They're those that figured out how to secure it.
Here's what we know for certain:
-
Tool sprawl is making you less secure, not more secure. You need consolidation. Not one monolithic tool (those don't exist yet), but fewer, better-integrated platforms.
-
Visibility gaps are your biggest vulnerability. You can't defend what you can't see. Unified asset discovery and continuous configuration monitoring are non-negotiable.
-
Automation is not optional. Cloud threats move at machine speed. Your response needs to as well. Start with low-risk automations and build from there.
-
Identity is the critical battleground. 77% of organizations identify IAM as their biggest risk. This is where attackers focus. This is where your security needs to focus.
-
Compliance needs to be continuous, not annual. The days of annual audits discovering problems that happened months ago are ending. Expect regulators to demand continuous compliance attestation.
The organizations that master these five areas will have fundamentally better security posture. They'll detect breaches faster. They'll respond to threats quicker. They'll have more confident boards and quieter CISOs.
The path to multi-cloud security is clear. It starts with visibility. It continues with consolidation. It succeeds through automation. And it's delivered by teams that understand that cloud security is not just a technology problem—it's an operational and organizational problem.
Start today. Pick one area. Build momentum. Scale from there. Your 2025 security posture will be dramatically better than your 2024 posture if you commit to these principles.
The future of cloud is here. Make sure your security is ready for it.

Key Takeaways
- 88% of organizations use multi-cloud, but 69% struggle with visibility gaps created by tool sprawl and fragmented security tooling
- Identity and access management is the #1 security risk, with 77% of organizations citing it as their biggest challenge in cloud
- Only 11% of organizations have automated remediation; most are still manually responding to security incidents, creating dangerous delays
- Misconfigurations affect 70% of organizations and are the most exploitable security problems, often taking minutes to discover after deployment
- Unified security platforms and consolidated tooling are essential; consolidating from 5+ tools to 2-3 integrated platforms improves security and reduces costs by 30-40%
Related Articles
- AWS CodeBuild Supply Chain Vulnerability: What You Need to Know [2025]
- N8n Ni8mare Vulnerability: What 60,000 Exposed Instances Need to Know [2025]
- CrowdStrike SGNL Acquisition: Identity Security for the AI Era [2025]
- Cyera's $9B Valuation: How Data Security Became Tech's Hottest Market [2025]
- Threat Hunting With Real Observability: Stop Breaches Before They Spread [2025]
- Enterprise AI Security: How WitnessAI Raised $58M [2025]
![Cloud Security in Multi-Cloud Environments: Closing the Visibility Gap [2025]](https://tryrunable.com/blog/cloud-security-in-multi-cloud-environments-closing-the-visib/image-1-1769089048107.jpg)



