The N8n Security Crisis: How 60,000 Instances Got Exposed to Ni 8mare
It was early January 2026 when researchers at Shadowserver Foundation took inventory of the internet's n8n problem. The numbers were staggering: 59,559 internet-connected n8n instances sitting vulnerable to a maximum-severity flaw. This wasn't a theoretical risk or a "maybe someday" scenario. This was an active, exploitable vulnerability affecting real teams running real workflows.
N8n is everywhere now. If you're automating data pipelines, building AI agent workflows, or connecting disparate systems without writing custom code, odds are you're running n8n. It's become the backbone of countless automation stacks because it solves a real problem: you shouldn't need a team of engineers just to move data between tools.
But that popularity came with a hidden cost. The flaw they called Ni 8mare (CVE-2026-21858) turned n8n's flexibility into a liability. For versions 1.65.0 through 1.120.x, attackers didn't need credentials, didn't need to be invited to the system, didn't need anything except a connection to the internet. They could remotely take complete control of the underlying server.
Here's what made this worse: most organizations didn't know they were exposed. Security patches aren't automatic. Teams get busy. Priorities shift. And suddenly you're sitting on a server that's effectively open to anyone on the internet who knows what to look for.
We're going to walk through exactly what happened, why it matters, and most importantly, what you need to do right now if you're running n8n. This isn't theoretical security theater. This is about protecting the automated workflows that probably run some critical part of your business.
TL; DR
- Nearly 60,000 n8n instances remain exposed to CVE-2026-21858 (Ni 8mare), a maximum-severity vulnerability allowing unauthenticated remote server takeover
- The flaw affects versions 1.65.0 to 1.120.x, with the fix available in version 1.121.0 and later
- Geographic spread is wide: 28,087 vulnerable instances in the US, 21,268 in Europe, 7,553 in Asia as of January 11, 2026
- No workarounds exist, meaning upgrading is your only real defense
- Discovered by Cyera in November 2025, the vulnerability stems from improper input validation in webhook and form endpoints
- Immediate action required: If you're running n8n, verify your version and upgrade or implement temporary restrictions on public endpoints

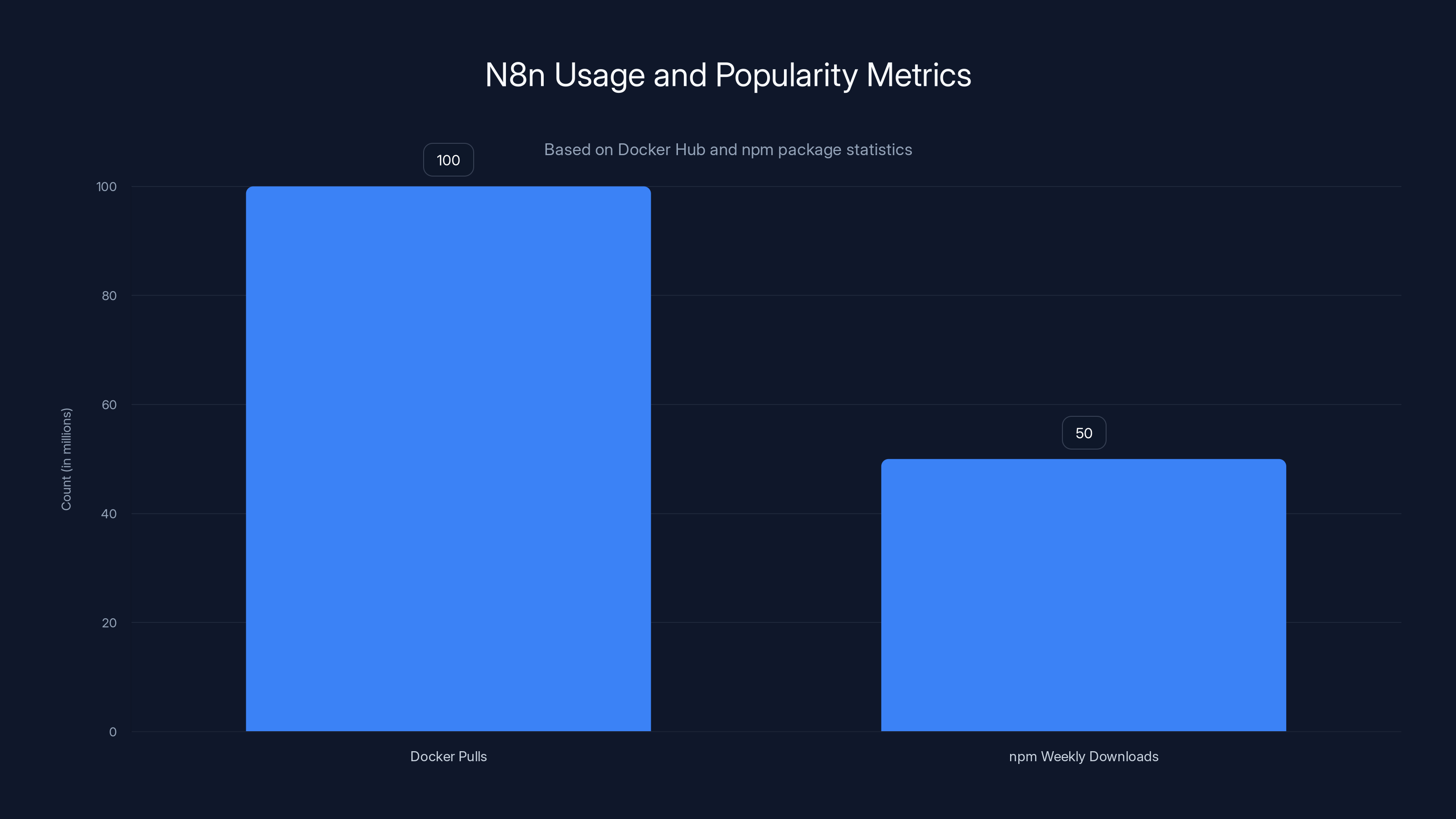
N8n has been pulled over 100 million times from Docker Hub and receives more than 50,000 weekly downloads on npm, highlighting its widespread adoption and utility.
Understanding N8n: The Workflow Platform Under Attack
N8n isn't just another automation tool. It's fundamentally changed how teams think about connecting systems without writing massive amounts of integration code.
The platform lets you build visual workflows that move data between tools, trigger actions, and run custom logic. You're essentially composing APIs together. Need to grab data from a HubSpot contact, transform it, and write it to a Postgres database? That's a few clicks and no Python required. Need to build an AI agent that ingests documents, processes them, and stores results? Same story.
That's the magic. But magic in distributed systems often comes with hidden complexity.
N8n has exploded in popularity because it's genuinely useful. According to Docker Hub metrics, it's pulled over 100 million times. The npm package gets more than 50,000 weekly downloads. The growth has been especially dramatic in the AI era, where teams suddenly need to wire together language models, data sources, and execution environments.
But with explosive growth comes security responsibility. N8n is open source, which is both a strength and a challenge. Strength because the code is auditable and the community catches issues. Challenge because not every organization maintains the same security posture.
When n8n instances are deployed, they often run with internet-facing webhooks and form endpoints. These are critical features. Webhooks let external systems trigger workflows when events happen. Forms let you collect data from users. But they're also the attack surface.
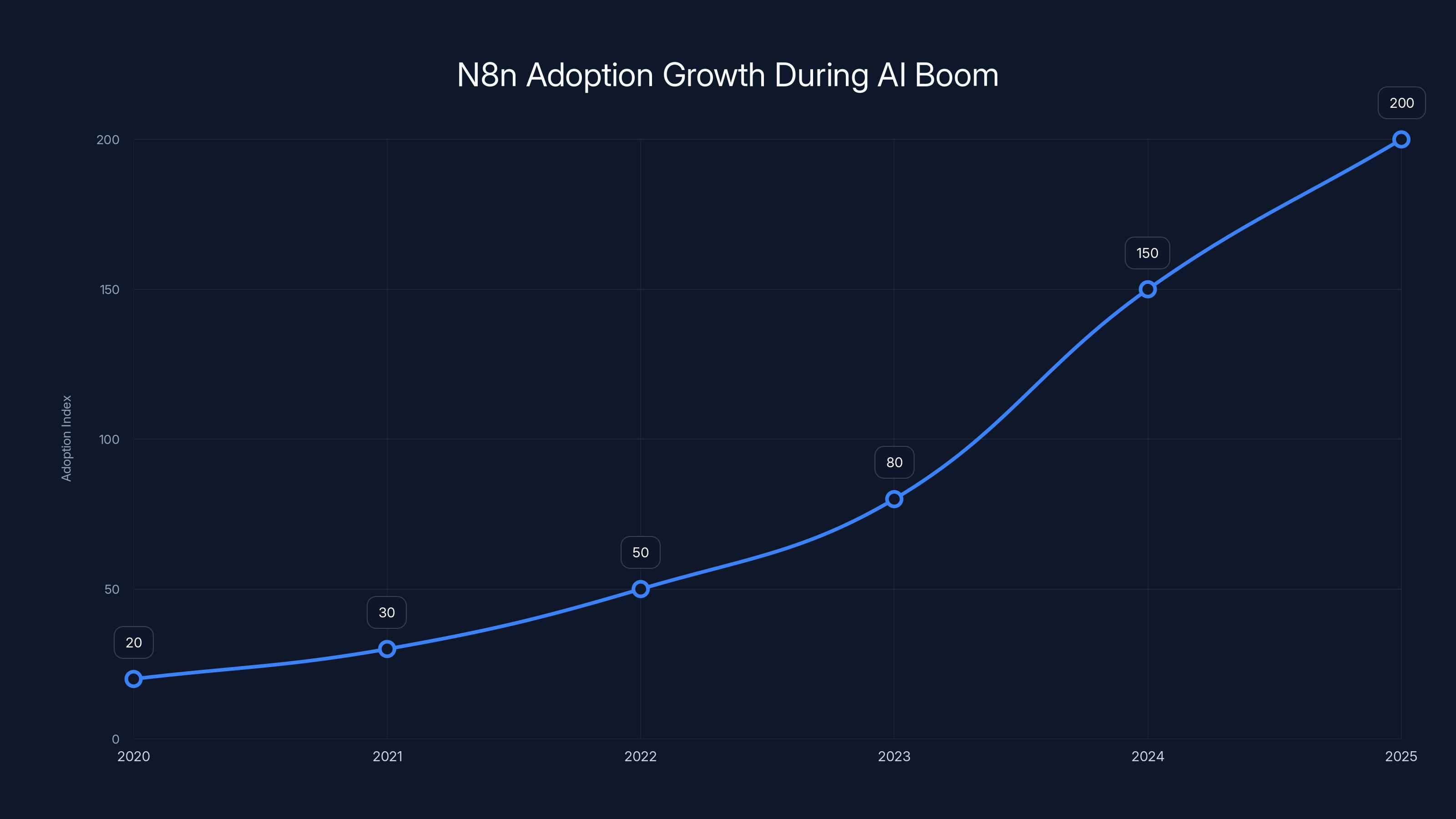
N8n's adoption spiked significantly during 2024-2025, coinciding with the AI boom, making it critical infrastructure for AI automation workflows. (Estimated data)
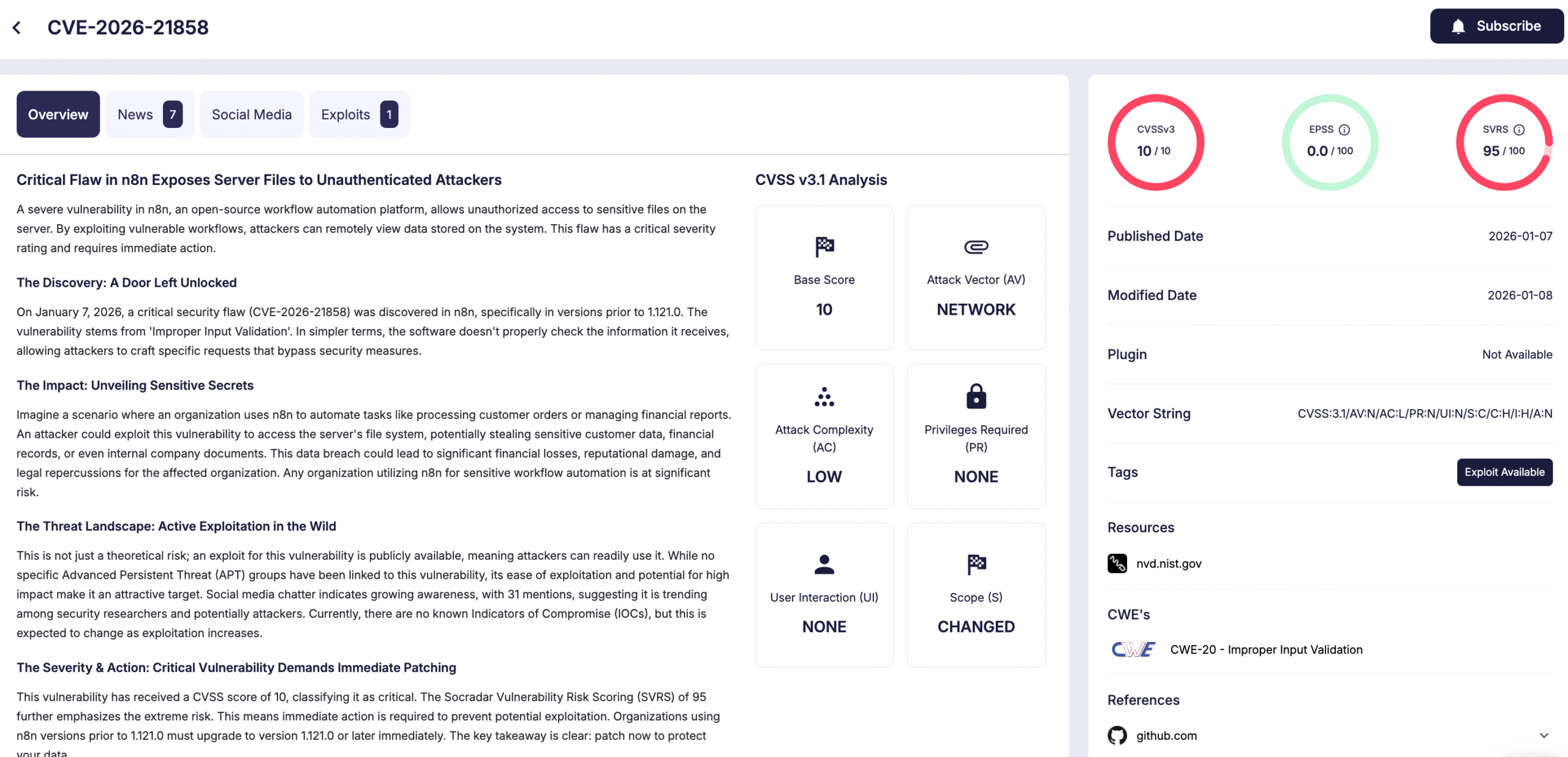
What Is CVE-2026-21858? The Ni 8mare Explained
The vulnerability researchers at Cyera discovered is almost textbook perfect in its severity. It's a case study in how a single input validation mistake can cascade into complete system compromise.
CVE-2026-21858 stems from improper input validation in how n8n handles certain webhook and form endpoint requests. Essentially, the application wasn't properly checking or sanitizing certain parameters before passing them to system functions.
Here's the critical part: unauthenticated attackers can exploit this. You don't need to be logged in. You don't need special credentials. You don't need an invite or an account at all. If you know an n8n instance exists and what version it's running, you can send a malicious request and take control.
The CVSS score of 10.0 (maximum severity) reflects the reality: this vulnerability allows remote code execution on the underlying server without authentication. That's the worst-case scenario in security. You've gone from "unauthorized access" to "complete compromise."
The attack works roughly like this:
- An attacker discovers an exposed n8n instance (easier than you'd think, given how many are internet-facing)
- They craft a specially formed request to a webhook or form endpoint
- The request contains malicious input that exploits the validation flaw
- Instead of rejecting the request, n8n processes it
- The attacker gains remote code execution on the server
- From there, they can access your data, your credentials, your connected systems, everything
What's particularly dangerous is that n8n often doesn't run in isolation. It's typically deployed as the orchestration layer for an entire automation ecosystem. It connects to databases, APIs, cloud services, and AI models. If an attacker compromises n8n, they're not just breaking into one tool. They're breaking into your entire integration stack.
The Scope: 60,000 Exposed Instances and Growing
The Shadowserver Foundation, a nonprofit organization that specializes in tracking threats and gathering security intelligence, conducted a scan on January 11, 2026. What they found was sobering.
59,559 internet-connected n8n instances were vulnerable to the flaw. Let that number sink in for a moment. Not hundreds. Not thousands in the hundreds. Nearly sixty thousand.
The geographic distribution tells you how widely n8n has been adopted:
- 28,087 instances in the United States (approximately 47% of total)
- 21,268 instances in Europe (approximately 36% of total)
- 7,553 instances in Asia (approximately 13% of total)
- Smaller concentrations scattered across other regions
The fact that Shadowserver could find and catalog these instances reveals something important: many of them are discoverable. They're not hidden behind private networks or properly secured. They're just out there on the internet, accessible to anyone with basic reconnaissance tools.
Now here's the crucial distinction: being discoverable doesn't mean all 60,000 were being actively exploited. But the window for exploitation was wide open. The vulnerability was discovered and publicly disclosed. Attackers had multiple months where the flaw existed in the wild before patches were available and deployed.
Nobody knows exactly how many of those 60,000 instances were actually compromised. Security researchers rarely get perfect visibility into breach incidents. But the potential impact was enormous. Think about what kind of data flows through n8n workflows: customer information, API keys, database credentials, financial records, AI model outputs.
If an attacker compromised even a small fraction of those instances, they'd have access to sensitive data and credentials across hundreds or thousands of organizations.

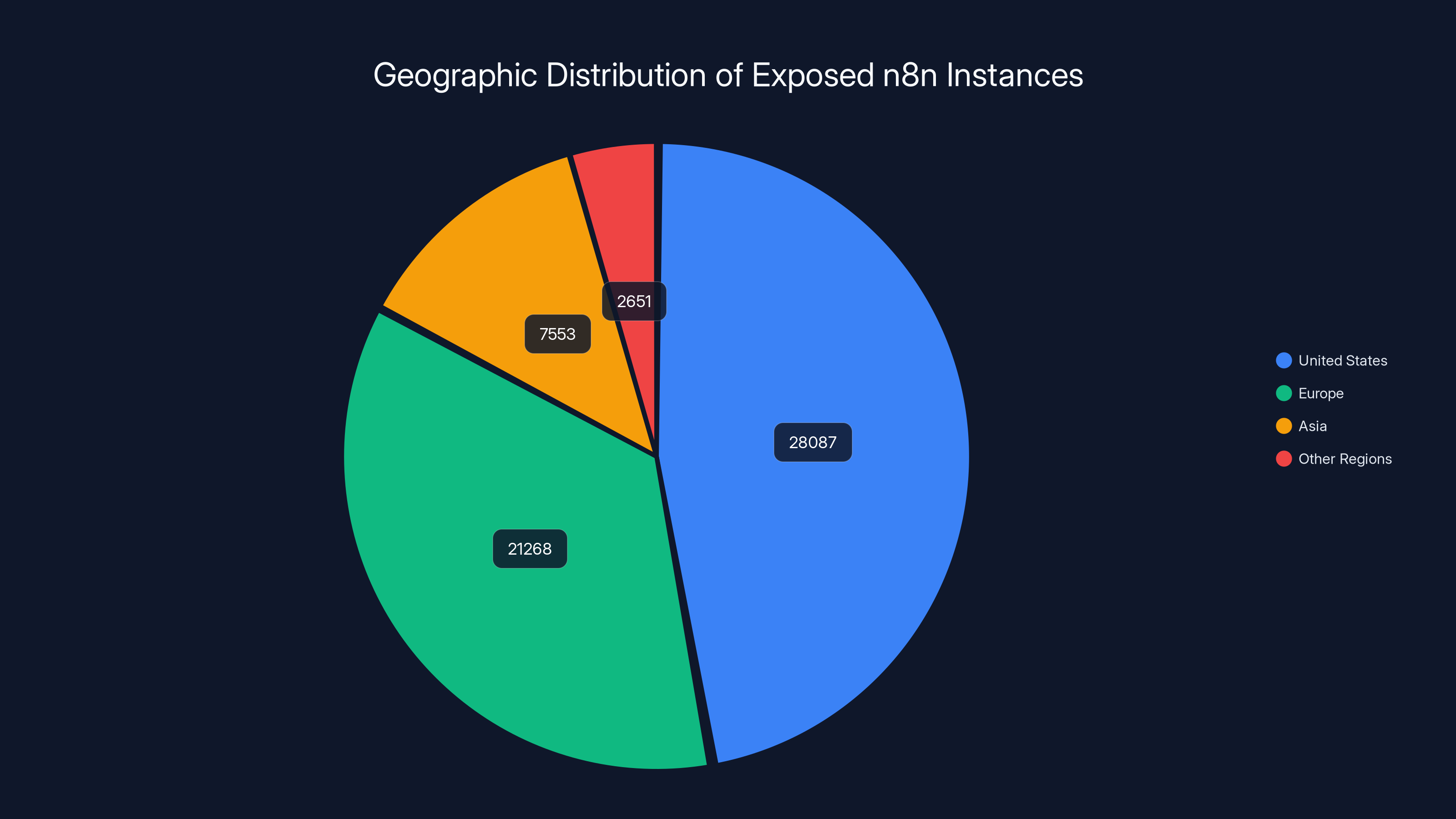
The United States accounts for the largest share of exposed n8n instances at 47%, followed by Europe at 36% and Asia at 13%. Estimated data for smaller concentrations in other regions.
The Discovery Timeline: How Ni 8mare Was Found
The story of how vulnerabilities get discovered is usually less dramatic than the story of the vulnerability itself, but the timeline matters.
Cyera, a cybersecurity research firm, identified the flaw in early November 2025. They responsibly disclosed it to the n8n team, giving them time to develop a patch before public disclosure. This is the responsible disclosure process that's supposed to work.
The n8n team released version 1.121.0 in response, which included the fix. The patch became available relatively quickly, but here's the reality of software security: "available" doesn't mean "deployed."
Organizations move at different speeds. Some have automated update processes. Others manually review patches before deploying. Some simply don't have monitoring in place and don't know an update is even available.
The vulnerability sat in the wild for months. If this sounds like a damning critique of the patching process, it is. But it's also just reality. Security patches are like fire drills: everyone agrees they're important, but actually executing them consistently across an organization is harder than it sounds.
By January 2026, when Shadowserver did their scan, fixes had been available for weeks. But nearly 60,000 instances still hadn't deployed them. Some organizations didn't know about the vulnerability. Others were in testing cycles. Some had processes that required approval from multiple stakeholders.
The point is: the vulnerability didn't just exist for a few days. It existed in production systems for months. That's a long window for opportunistic attackers.
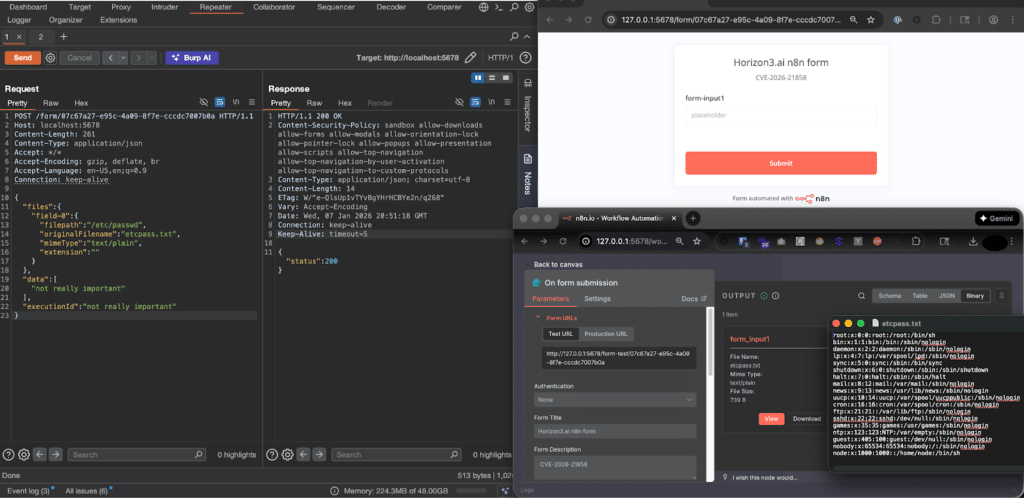
Why Webhooks and Forms Are the Problem
To understand why this vulnerability is so critical, you need to understand why n8n exposed these endpoints in the first place.
Webhooks are how modern systems talk to each other asynchronously. When something happens in System A, it sends a message to System B. That message typically goes to an HTTP endpoint. N8n's webhook feature lets you define what happens when that message arrives.
Forms are similar. They're how you let non-technical users input data that triggers a workflow. Someone fills out a form, submits it, and it starts an automated process.
Both of these features are intentionally public. You want external systems to access them. You want users to be able to submit forms from the internet. That's the whole point.
But "intentionally public" doesn't mean "intentionally unsecured." The problem with Ni 8mare is that these public endpoints weren't properly validating input before processing it.
Think of it like a restaurant's front door. You want customers to walk in. But you still install locks, hire security, and don't let people just wander into the kitchen and start handling food. The front door being public doesn't mean security doesn't matter.
N8n's webhook and form validation was equivalent to leaving the kitchen door propped open. Attackers could walk right in.

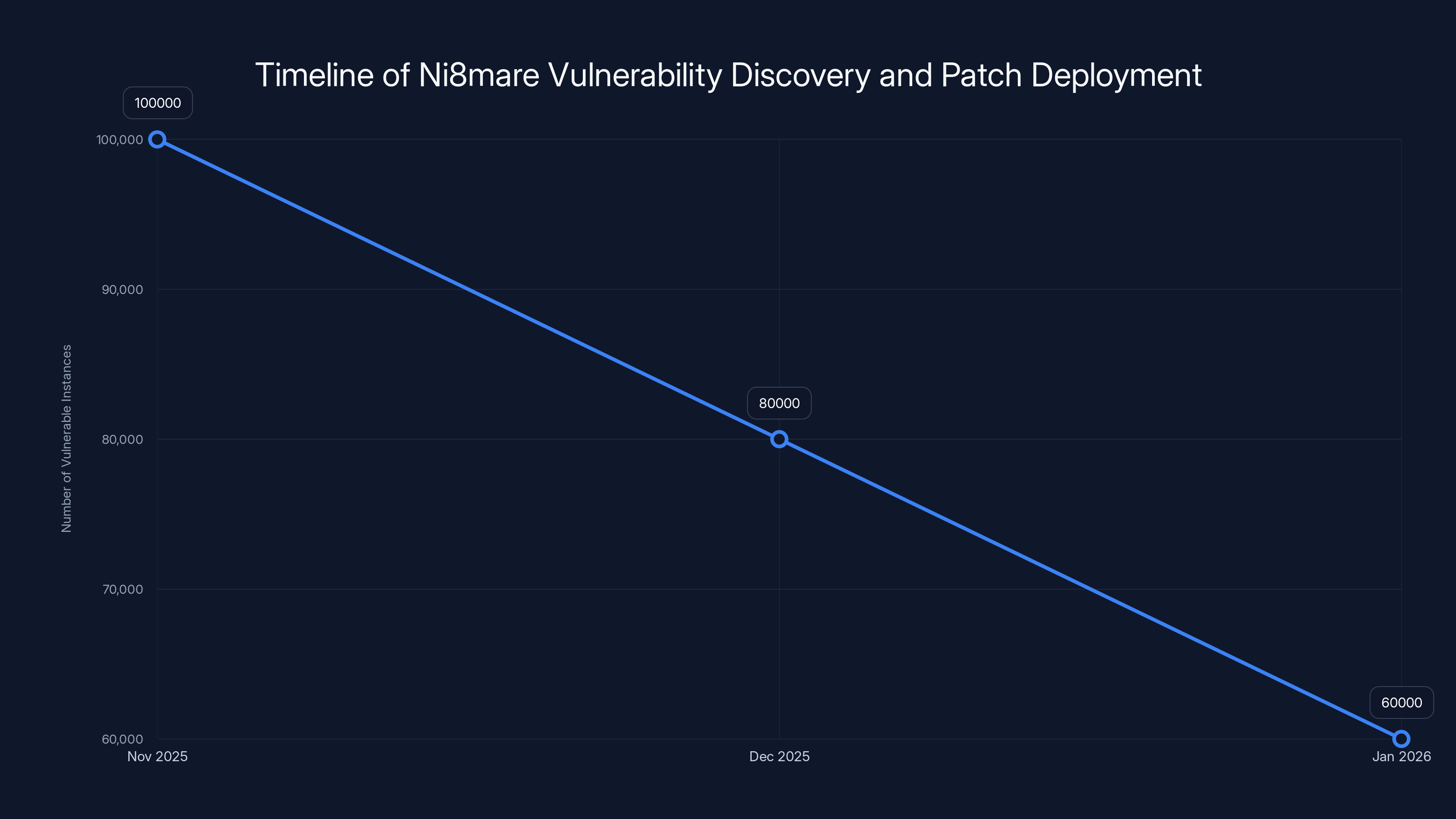
The Ni8mare vulnerability was discovered in November 2025, with patches available shortly after. However, by January 2026, 60,000 instances remained unpatched, highlighting the slow adoption of security updates. (Estimated data)
Temporary Mitigations: If You Can't Patch Yet
The n8n team acknowledged that not every organization can upgrade immediately. They provided guidance on temporary mitigations while you work on a full upgrade.
The primary temporary mitigation is restricting or disabling publicly accessible webhook and form endpoints. This means:
- Identify which n8n workflows have public webhooks or forms
- Determine if they need to be publicly accessible right now
- If possible, temporarily restrict access by IP range, authentication requirement, or disabling the endpoints entirely
- Document which workflows you've restricted and why
- Establish a timeline for upgrading to a patched version
- Re-enable the endpoints only after you've upgraded
This isn't a perfect solution. If your business depends on public webhooks and forms, you're choosing between security vulnerability and operational disruption. Neither is ideal.
But it's better than sitting completely exposed while you work on a full upgrade. It's a temporary trade-off that buys you time.
The n8n team understood that upgrading isn't always instant. Infrastructure changes require testing, validation, potential downtime planning, and stakeholder coordination. Providing temporary workarounds acknowledges this reality.
But temporary isn't permanent. You're operating on borrowed time. The longer you wait to upgrade, the longer your system remains at risk. Even with temporary mitigations, you're assuming that attackers aren't finding other ways in. That's not a bet most security teams should be comfortable with.
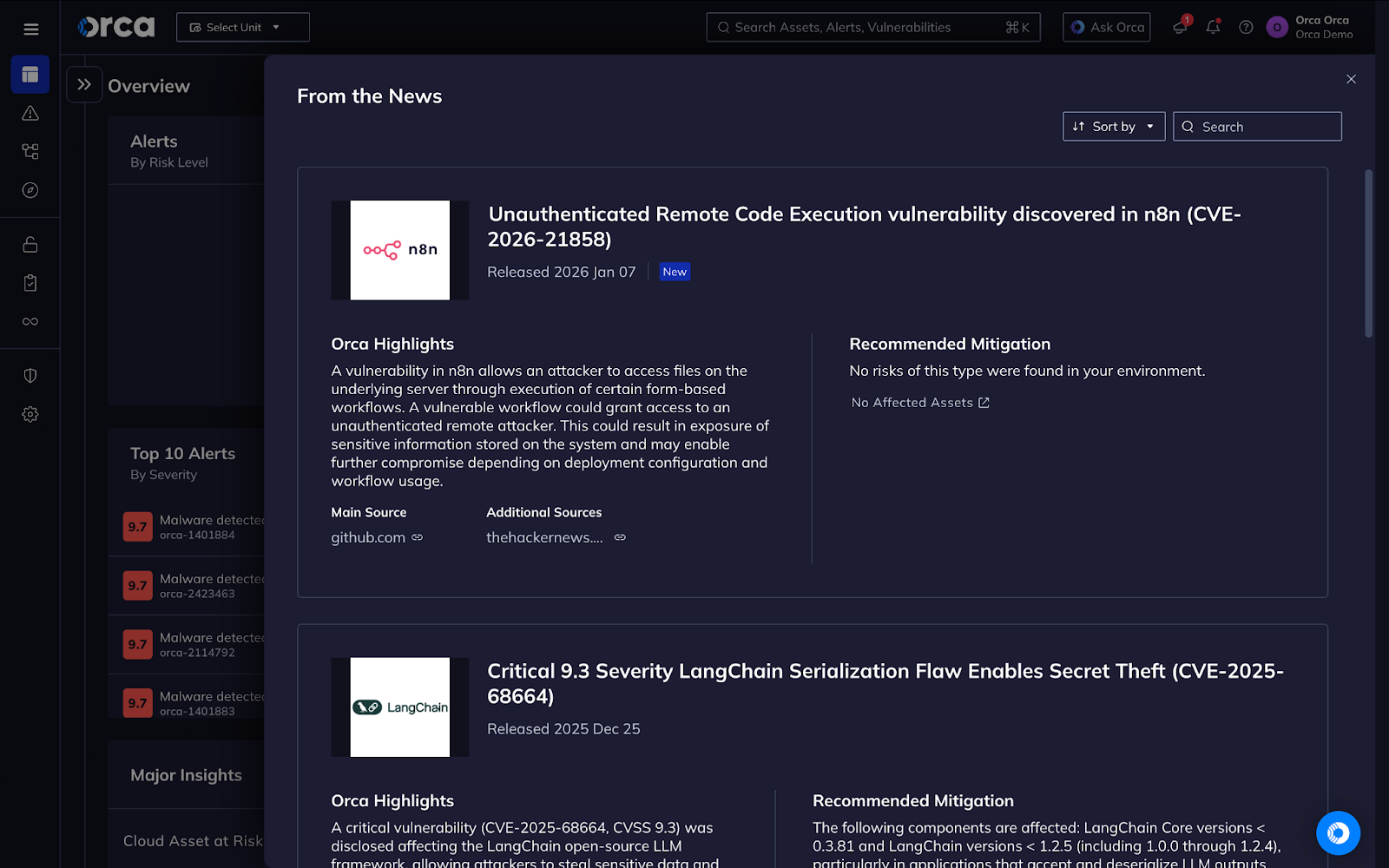
The Real Problem: Unpatched Systems at Scale
Here's something that keeps security teams awake at night: if Shadowserver found 60,000 vulnerable instances in January, how many were vulnerable in November, December, and early January? The number was probably higher. And how many vulnerable instances aren't internet-facing and therefore not discoverable to automated scanning?
The vulnerability represents a fundamental challenge in distributed systems security: patch lag.
Patch lag is the time between when a vulnerability is disclosed and when a patch is deployed. During that window, systems are at risk. The industry has gotten better at reducing this window, but it still exists.
There are good reasons for patch lag. You need time to:
- Test patches in staging environments to make sure they don't break anything
- Schedule deployments during maintenance windows
- Coordinate across teams (operations, security, development)
- Communicate changes to stakeholders
- Monitor for any issues after deployment
- Document the change for compliance purposes
But from an attacker's perspective, patch lag is an opportunity window. They know when vulnerabilities are disclosed. They can watch repositories, watch release notes, and immediately start looking for unpatched systems.
The fact that nearly 60,000 n8n instances were still vulnerable weeks after a patch was available is partly about the patch lag problem. It's partly about visibility (many organizations don't know what versions of what software they're running). It's partly about process (not every team has automated patch management). And it's partly about competing priorities (security updates compete with feature work and bug fixes for attention).

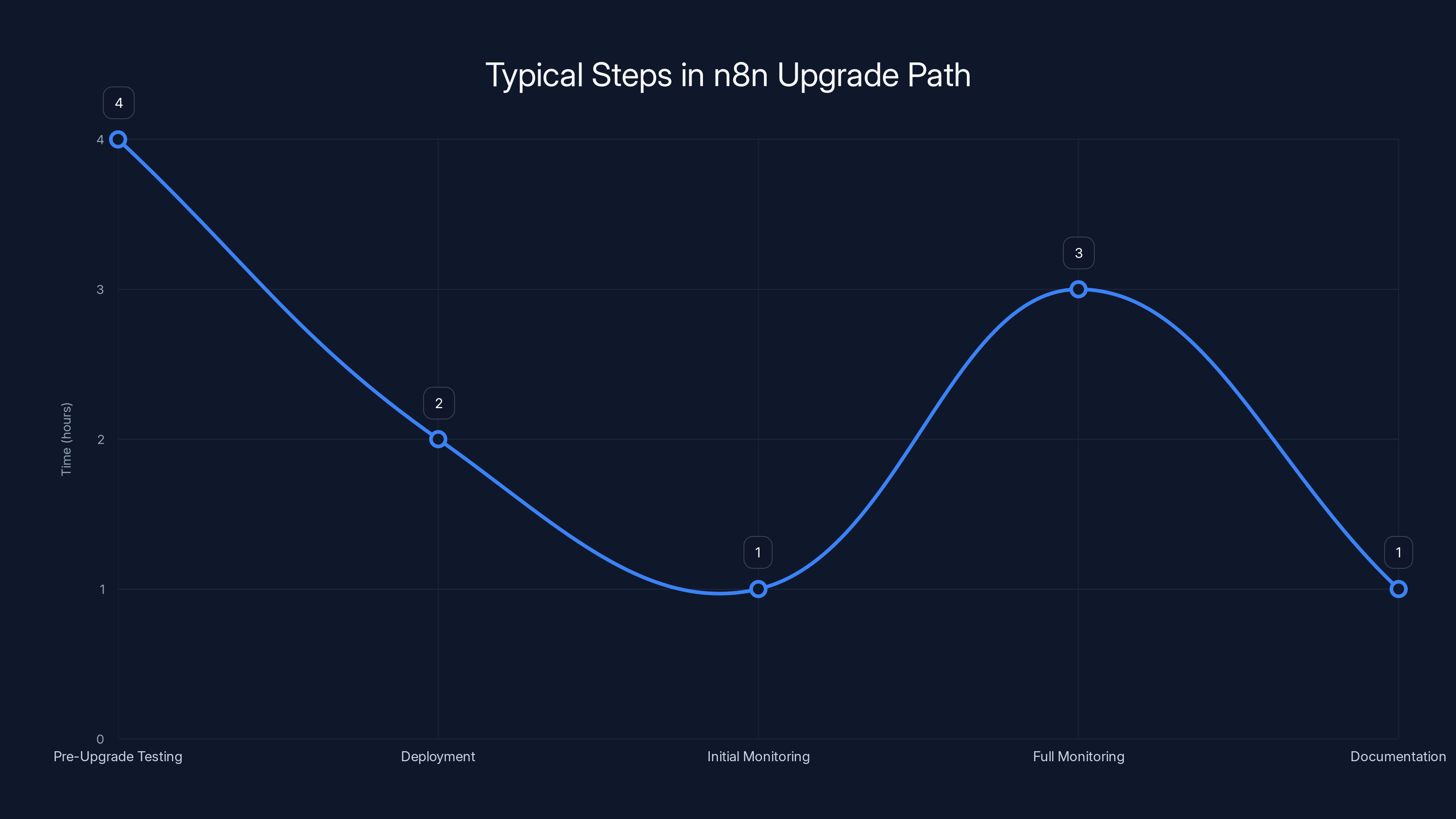
Estimated data suggests that a complete upgrade path for n8n to version 1.121.0, including testing and monitoring, might take around 11 hours.
Why N8n Matters: The AI Automation Connection
Understanding why this vulnerability is critical requires understanding why n8n has become so important in the first place.
N8n's growth accelerated dramatically during the AI boom. Teams suddenly needed to orchestrate complex workflows involving language models, data sources, and execution environments. You can't do that with hardcoded integrations. You need a flexible, visual workflow platform.
N8n fits that need perfectly. It lets developers and non-developers build AI agents by connecting models to APIs and data sources. It handles the orchestration, error handling, and data flow. It's become infrastructure for teams building AI-powered automation.
That means a compromise of an n8n instance isn't just an operational issue. It's a potential compromise of your AI agents, your data pipelines, and your model integrations.
An attacker with control of n8n could:
- Redirect data flows to their own systems
- Poison data being fed to AI models
- Steal API keys and credentials for your other systems
- Modify workflow logic to do things you didn't intend
- Extract results of model inferences
- Access the databases and APIs your workflows interact with
In an AI context, that's particularly dangerous. If your AI agents are compromised, they might operate normally from a user perspective while silently exfiltrating data or learning patterns they shouldn't.
This is why the severity of Ni 8mare isn't theoretical. It's not a vulnerability in a niche tool. It's a vulnerability in infrastructure that's fundamental to how teams are building AI systems.
Assessment: Checking Your Exposure
If you're running n8n, how do you know if you're vulnerable?
First, check your version number. Log into your n8n instance, go to settings, and look for the version information. You need to be running 1.121.0 or later. If you're on anything earlier, you're vulnerable.
Second, assess your exposure level. Ask yourself:
- Is this instance internet-facing? Can someone from outside your network access it?
- Do you have webhooks or forms that are publicly accessible?
- Are those webhooks and forms critical to your operations?
- Would an attacker compromising this instance give them access to sensitive data or other systems?
- Do you have security monitoring in place that would detect compromise?
- What's your incident response plan if this system were compromised?
Third, inventory your n8n deployments. You might have more than one instance running. Some might be in production, some in development, some in testing. You need to know all of them.
Fourth, check your logs. If you have access to server logs, look for suspicious activity between early November 2025 and when you patched. Look for unusual webhook requests, errors in the logs, or authentication failures. This is forensic analysis that can help you understand if you were compromised before you patched.
If you don't know your version, if you're unsure about your exposure, or if you suspect you might have been compromised, that's worth escalating internally. Talk to your security team. Document your concerns. Get approval to upgrade or implement mitigations.

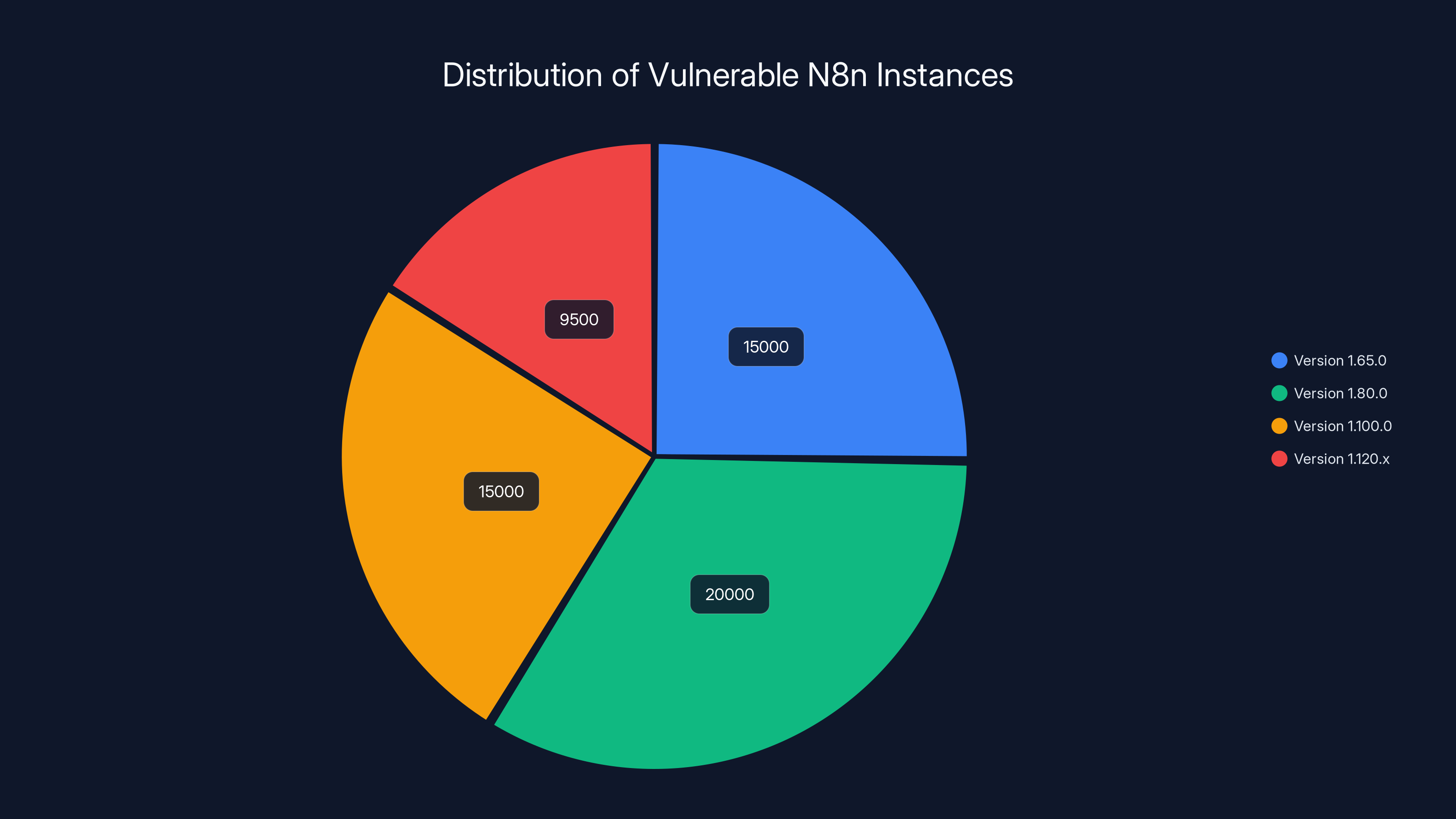
Estimated data shows that the majority of vulnerable instances are running on versions 1.80.0 and 1.100.0, highlighting the widespread impact of the Ni8mare flaw.
The Upgrade Path: Getting to 1.121.0
Upgrading n8n is straightforward in theory but requires planning in practice.
Before you upgrade, test in a staging environment. Deploy the new version in a non-production setting and run your critical workflows. Make sure nothing breaks. Some workflows might depend on specific behavior that changed between versions.
N8n publishes detailed release notes for each version. Read them. They'll tell you about breaking changes, new features, and bug fixes. If you're jumping multiple versions (which you might be if you're several versions behind), read all the release notes in between.
Use a blue-green deployment strategy if you can. Keep your current version running (blue), deploy the new version alongside it (green), test the green environment, and then switch traffic to it. If something goes wrong, you can quickly switch back to blue. This minimizes downtime.
If you can't do blue-green, schedule a maintenance window. Notify users that n8n will be unavailable for a specific period. Plan for enough time to: deploy the new version, run basic smoke tests, monitor for errors, and roll back if needed.
After the upgrade, monitor closely. Watch logs for errors. Check that workflows are executing as expected. Have your on-call team available for the first few hours. Sometimes issues only show up under production load.
Document the upgrade. Record the date, the version, any issues encountered, and how you resolved them. This matters for compliance and for troubleshooting if issues come up later.
Detection and Response: Did You Get Compromised?
If you were running a vulnerable version during the vulnerability window, you should assume there's some chance you were compromised. That's a difficult thing to acknowledge, but it's the realistic approach.
Here's how to assess compromise:
Check logs for exploitation attempts. Look for POST requests to webhook endpoints with suspicious parameters or payloads. Look for unusual request sizes, encoding schemes, or patterns. Look for requests from IPs you don't recognize.
Monitor for lateral movement. If an attacker compromised n8n, they probably didn't stop there. Look for:
- Unusual database queries or access patterns
- Unexpected API calls to external services
- New credentials being created or used
- Modified workflow logic in your n8n instances
- Data exfiltration to unusual destinations
Check file integrity. If you have filesystem access, look for modified n8n installation files or new files in unexpected places. Attackers often leave backdoors or tools they can use for future access.
Review credential usage. If n8n has access to API keys, database passwords, or other credentials, check if those credentials have been used for unauthorized actions. If you store credentials in n8n's vault, verify they haven't been accessed or changed.
Examine workflow modifications. Review your workflows for changes you didn't make. Attackers sometimes modify workflows to exfiltrate data or perform unauthorized actions while keeping the workflow operational so you don't immediately notice.
If you find evidence of compromise, activate your incident response plan:
- Isolate affected systems from the network
- Preserve evidence (logs, memory dumps, file copies)
- Notify your security team and leadership
- Scan for malware or backdoors
- Reset all credentials that the compromised system had access to
- Notify affected users and customers as appropriate
- Work with forensic specialists if needed
- Document everything for post-incident analysis
Compromise is serious. But knowing you're compromised and responding quickly is better than being compromised and not knowing it.
Long-Term Security: Beyond Ni 8mare
Ni 8mare is one vulnerability. But the lessons from it apply to any distributed system you're running.
First, implement vulnerability management processes. You need to:
- Monitor for security advisories from vendors you depend on
- Track which versions you're running across all systems
- Test patches before deploying them
- Deploy patches within a defined SLA (usually 30-90 days, faster for critical vulnerabilities)
- Document the patching process for compliance
Second, segment your network. Even if n8n is internet-facing, it shouldn't have direct access to your entire infrastructure. Use network segmentation to limit the damage if one system is compromised. N8n should only be able to access the systems it actually needs to reach.
Third, use authentication and authorization properly. Even though Ni 8mare didn't require authentication, most attack vectors do. Make sure:
- Weak passwords are prevented
- Multi-factor authentication is enabled for sensitive systems
- Role-based access control limits what each user can do
- Service accounts have minimal required permissions
Fourth, monitor actively. You can't respond to incidents you don't know about. Implement:
- Log aggregation and analysis
- Alerting for suspicious patterns
- Regular security assessments
- Penetration testing to find vulnerabilities before attackers do
Fifth, plan for incidents. Even with perfect security (which doesn't exist), assume you'll eventually be compromised. Have an incident response plan that includes:
- Clear notification procedures
- Technical response steps
- Communication templates
- Forensics and analysis processes
- Post-incident reviews
Industry Context: Why This Matters Now
Ni 8mare exists in a broader context of automation platforms becoming critical infrastructure.
Organizations increasingly depend on workflow automation for core business processes. Data pipelines, AI agent orchestration, system integration, user onboarding, customer communication flows. These aren't nice-to-haves. They're how business happens.
When those automation platforms are compromised, business doesn't just stop. Worse, business continues but in corrupted ways. Data flows silently to the wrong place. User communications go to attackers. AI agents make decisions based on compromised data.
That's why a vulnerability in n8n affects so many organizations so severely. It's not just a tool. It's infrastructure.
The n8n team responded reasonably quickly with a patch. But the fact that 60,000 instances were still vulnerable weeks later reveals the patching problem at scale. We've built this distributed ecosystem of tools and services, and we haven't solved the problem of keeping all of them secure.
This is why automation platform security matters. These are not edge-case tools. They're central infrastructure. And they need to be treated with the security rigor we apply to databases and web servers.
The Path Forward: Practical Steps
If you're running n8n, here's what you need to do, in order:
This week:
- Check your version number
- If you're vulnerable, apply a temporary mitigation (restrict public access to webhooks/forms)
- Plan your upgrade (test environment, maintenance window, rollback plan)
- Communicate the situation to stakeholders
Next week:
- Deploy the patch to your staging environment
- Test your critical workflows
- Schedule a maintenance window for production
Within 30 days:
- Deploy the patch to production
- Monitor closely for issues
- Verify the upgrade was successful
- Document the change
- If you suspect compromise, start forensic analysis
Ongoing:
- Subscribe to n8n security advisories
- Implement patch management process
- Review logs regularly
- Assess your vulnerability exposure quarterly
- Plan security improvements for your n8n deployments
This isn't optional. This is basic security hygiene. Your n8n instances are trusted with data, credentials, and workflow logic. They need to be secure.

Looking Ahead: The Future of Automation Security
Ni 8mare won't be the last vulnerability in n8n or similar platforms. It's a useful reminder that as we build more complex, distributed, automated systems, security becomes harder and more important simultaneously.
The future probably includes:
- Better automated patching processes (hopefully towards zero-day windows)
- More sophisticated supply chain security (knowing what you're running and what it depends on)
- Better isolation and segmentation (limiting blast radius when compromise happens)
- More aggressive security by default (not leaving public endpoints exposed without authentication)
- Better incident response tooling and frameworks
But those are long-term improvements. Right now, the responsibility is on organizations running these systems to be diligent about security.
N8n is a powerful tool. That power comes with responsibility. Taking security seriously isn't optional when you're running mission-critical infrastructure.

FAQ
What exactly is CVE-2026-21858, and why is it called Ni 8mare?
CVE-2026-21858 is a maximum-severity vulnerability in n8n workflow automation platform affecting versions 1.65.0 through 1.120.x. It stems from improper input validation in webhook and form endpoints, allowing unauthenticated attackers to achieve remote code execution on the underlying server. The nickname "Ni 8mare" is a playful reference to n8n itself, using the numeral 8 to replace letters in the pronunciation of the platform name.
How many n8n instances are currently vulnerable to Ni 8mare?
As of January 11, 2026, Shadowserver Foundation identified approximately 59,559 internet-connected n8n instances vulnerable to CVE-2026-21858. The geographic distribution shows 28,087 instances in the United States, 21,268 in Europe, and 7,553 in Asia. This count represents only publicly accessible instances discovered through internet scanning; the actual total of vulnerable systems could be higher when including instances behind firewalls or private networks.
What versions of n8n are vulnerable to Ni 8mare?
Versions 1.65.0 through 1.120.x are vulnerable to CVE-2026-21858. The vulnerability was patched in version 1.121.0 and later. If you're running n8n, you must verify your installed version. You can check this in your instance settings under the About section. Any version below 1.121.0 is at risk and requires immediate upgrading or temporary mitigation.
Can I use a temporary workaround instead of upgrading immediately?
Yes, but it's a short-term solution only. The n8n team provided a temporary mitigation: you can restrict or completely disable publicly accessible webhook and form endpoints while you plan your upgrade. This reduces your attack surface but doesn't fully protect you. The only permanent defense is upgrading to version 1.121.0 or later. Temporary mitigations should be treated as a bridge to upgrading, not a replacement for it.
When was Ni 8mare discovered, and how long has it been exploitable?
The vulnerability was discovered by cybersecurity researchers at Cyera in early November 2025. The n8n team released patch version 1.121.0 shortly after responsible disclosure. This means the flaw was potentially exploitable in production systems for several months before patches were available and deployed. The vulnerability window extended from November 2025 through January 2026 for many organizations, giving attackers months to discover and exploit unpatched instances.
What can an attacker do if they exploit Ni 8mare?
An attacker exploiting CVE-2026-21858 gains complete remote code execution on the underlying server hosting n8n. This allows them to: access all data flowing through your workflows, steal API keys and database credentials stored in n8n, modify workflows to perform unauthorized actions, compromise any external systems your n8n workflows connect to (databases, APIs, AI models), and establish persistent backdoors for future access. Essentially, a compromise means complete loss of confidentiality, integrity, and availability of your automation infrastructure.
How do I check if my n8n instance has been compromised?
Check for compromise by examining: server logs for suspicious webhook requests with unusual parameters between November 2025 and your patch date, any modifications to workflows you didn't authorize, unexpected usage of credentials stored in n8n, file integrity of your n8n installation for unauthorized modifications, and unusual database queries or API calls made by your workflows. If you find evidence of compromise, isolate the system, preserve logs for forensic analysis, and reset any credentials the system had access to.
Should I upgrade immediately or test first?
Both. Deploy the patch to a staging environment first to test your critical workflows and verify nothing breaks between versions. Then schedule a production maintenance window to upgrade. This approach balances security (getting the patch deployed) with operational stability (testing before production). Typically this can be accomplished within 1-2 weeks while maintaining reasonable security posture with temporary mitigations in place.
What's the difference between this vulnerability and typical web application vulnerabilities?
This vulnerability is particularly dangerous because n8n isn't just a web application—it's automation infrastructure with access to your systems, data, and credentials. A compromise doesn't just mean an attacker can see your data; it means they can modify your automated workflows, redirect data, poison AI models, and compromise everything downstream. The blast radius is much larger than a typical application vulnerability because n8n is often the orchestration layer connecting everything else in your infrastructure.
Why do so many n8n instances remain vulnerable if patches are available?
Multiple factors contribute to patch lag: many organizations lack visibility into what versions they're running, patching requires testing in staging environments before production deployment, organizations must schedule maintenance windows to deploy updates, coordination across teams (security, operations, development) takes time, and patching sometimes competes with feature development and bug fixes for attention. This is why Shadowserver found 60,000 vulnerable instances even though patches were available for weeks—deploying patches at scale across diverse infrastructure is operationally complex.

Key Takeaways
- Nearly 60,000 internet-connected n8n instances remain vulnerable to CVE-2026-21858 (Ni8mare), a maximum-severity remote code execution flaw affecting versions before 1.121.0
- The vulnerability stems from improper input validation in webhook and form endpoints, allowing unauthenticated attackers to completely compromise underlying servers and access all connected systems
- Vulnerable instances are concentrated in the United States (47%), Europe (36%), and Asia (13%), with geographic distribution revealing how widely n8n has been adopted globally
- No technical workarounds exist; upgrading to version 1.121.0 or later is the only permanent defense, though temporary mitigation involves restricting public webhook and form access
- Patch lag from November 2025 discovery through January 2026 demonstrates the ongoing challenge of security management at scale, with many organizations lacking visibility into their software versions
Related Articles
- Gogs CVE-2025-8110 RCE Vulnerability: What Federal Agencies Must Know [2025]
- Hackers Targeting LLM Services Through Misconfigured Proxies [2025]
- CrowdStrike SGNL Acquisition: Identity Security for the AI Era [2025]
- Target Data Breach 2025: 860GB Source Code Leak Explained [2025]
- DDoS Attacks in 2025: How Threats Scale Faster Than Defenses [2025]
- Geopatriation & Cloud Sovereignty: What 2026 Means for Enterprise Data [2026]
![N8n Ni8mare Vulnerability: What 60,000 Exposed Instances Need to Know [2025]](https://tryrunable.com/blog/n8n-ni8mare-vulnerability-what-60-000-exposed-instances-need/image-1-1768325869957.jpg)



