Crowd Strike's $740 Million SGNL Acquisition: Reshaping Identity Security for AI-Powered Threats
When Crowd Strike announced it would acquire SGNL for approximately $740 million in early 2025, the cybersecurity community took notice. But this wasn't just another corporate consolidation. It represented something more fundamental: a public acknowledgment that modern identity security frameworks are broken, as reported by CyberScoop.
Here's the reality. Most enterprises still rely on privilege management systems built in the early 2000s. You get access to a resource. That access stays there. Static. Permanent. Maybe you rotate a password every 90 days. Maybe you don't. The system assumes that if you're authenticated once, you're trusted for the entire session.
Then came AI agents.
Now your organization has non-human identities operating at superhuman speed. They're requesting access, executing tasks, modifying systems, and moving laterally through your infrastructure faster than any human ever could. Your old privilege management system? It doesn't even see them as a threat because they're "trusted" identities.
This is the problem Crowd Strike is solving with SGNL. And it's not just a product play. It's an admission that the entire premise of how we think about access control needs to fundamentally change, as noted by SecurityWeek.
The Identity Management Gap: Why This Acquisition Matters Now
The cybersecurity industry has spent two decades perfecting perimeter defense. Firewalls. Intrusion detection. Network segmentation. But the actual attack surface has shifted dramatically.
Attacks don't come from the outside anymore. They come from inside, using legitimate credentials. A compromised employee account. A stolen API key. A service account that was never supposed to be privileged but nobody downgraded it. These are the vectors that actually compromise organizations now, as highlighted by American Banker.
Identity has become the new perimeter. And it's fractured.
Consider what's happening in real enterprises right now. You've got humans with traditional usernames and passwords. You've got service accounts running applications. You've got API keys managing integrations. You've got cloud functions with IAM roles. And now, increasingly, you've got AI agents with their own identities performing autonomous operations.
Your identity governance system tries to manage all of this through static rule sets. "This user can access this database between 9 AM and 5 PM." "This service account can write to this S3 bucket." "This API key has read-only access." These rules assume that risk is constant. They assume that if something was safe yesterday, it's safe today.
But that's not how real compromise works. A user's behavior changes. An API key's usage pattern shifts. An agent starts requesting resources it never touched before. These signals matter. They're the early warning signs of an intrusion, as explained by InfoSecurity Magazine.
SGNL's core technology addresses exactly this gap. Instead of managing access through static permissions, SGNL continuously evaluates whether an identity should have access right now, based on current risk signals and behavioral patterns.
Who SGNL Is and What They Actually Do
SGNL wasn't some unknown startup when Crowd Strike acquired them. They'd been operating in stealth mode for years, building something genuinely innovative in the identity space.
The company focused on a single problem: continuous identity verification. Not identity management as the industry had traditionally understood it, but something more dynamic.
Here's how it works in practice. An employee logs in from their usual location at their usual time using their usual device. Access granted instantly. Zero friction. But that same employee logs in from a different country at 2 AM using a new device and requests access to sensitive data they've never touched before? The system flags it. Not as an absolute "deny," but as a signal that warrants additional verification, as detailed by Identity Week.
Now scale that logic to non-human identities. An AI agent runs routine tasks every day at the same time, accessing the same resources. It's generating reports, updating databases, moving data between systems. All normal. But one day, the agent starts requesting elevated privileges it never needed before. It's trying to access systems outside its normal scope. It's making unusual API calls.
Traditional identity systems see this as: "The credentials are valid. The service account has permissions. Allow it." SGNL's approach sees this as a potential security incident and flags it for investigation or automatic remediation.
The company was founded on the principle that static access controls are fundamentally insufficient in a world of dynamic threats. They built technology that treats identity verification as a continuous process, not a one-time gate you pass through.
Crowd Strike's Strategic Pivot: From Endpoint to Identity
Crowd Strike built its reputation on endpoint detection and response (EDR). The Falcon platform became the gold standard for stopping threats on laptops, servers, and workstations. When their agent processes executed a kernel-level exploit that crashed Windows systems in 2024, it shook the industry. But the company recovered. Their share price is higher now than before the incident.
But EDR, for all its sophistication, solves only part of the security problem. You can detect malicious behavior on endpoints. You can block unauthorized process execution. You can identify lateral movement. But if an attacker has valid credentials, your endpoint security is largely irrelevant.
This is why Crowd Strike is aggressively moving into identity security. It's not a distraction from their core business. It's a natural expansion that completes their security stack.
Think about the attack chain. An adversary needs to compromise credentials or steal them. They use those credentials to move through your environment. They escalate privileges to reach more valuable resources. At each stage of this chain, identity is the control point.
Crowd Strike's CEO George Kurtz was explicit about this in the acquisition announcement. He talked about "disrupting the premise of modern privilege and access." This isn't marketing speak. This is describing a fundamental rethinking of how privilege management should work, as noted by SecurityWeek.
For every identity, human or machine. That phrase is crucial. Because the industry has been managing humans and machines separately. Different solutions. Different governance models. Different teams. Crowd Strike is betting that consolidating this under a single "continuous identity" framework, powered by SGNL's technology, is the future.
The AI Agent Problem: Why Traditional Identity Frameworks Are Obsolete
Let's be direct about why this acquisition happened now and not five years ago. The AI agent explosion changed the threat landscape completely.
When you have a human user, there are natural constraints on what they can do. They're awake eight hours a day. They work from a few locations. They use a few devices. Their actions leave audit trails. If they do something abnormal, their manager might notice.
An AI agent operates with none of these constraints. It can run 24/7. It can execute thousands of API calls per second. It can iterate through millions of permission combinations. It can compromise itself, get caught, and keep trying.
Worse, the agent looks legitimate the entire time. It's using valid credentials. It's hitting authorized endpoints. It's executing permitted operations. Traditional access controls see nothing wrong, as explained by Analytics Insight.
Consider a concrete example. A company deploys an AI agent to analyze customer data and generate insights. The agent has read access to the customer database. It's supposed to run once per day and generate a report. But an attacker compromises the agent's code. Now the agent is exfiltrating data. It's querying customer information at rates that would be impossible for a human. But the logs show legitimate access using the agent's legitimate credentials.
Your traditional IAM system says: "The service account has permissions. All requests are authenticated. Everything looks normal."
SGNL's system would flag this immediately. "That service account never made API calls at this frequency before. The request pattern doesn't match its normal behavior. Access denied pending verification."
This behavioral analysis at scale is what organizations need now. And it's what Crowd Strike is acquiring with SGNL.
The Market Opportunity: Why $740 Million Makes Sense
Some analysts questioned whether Crowd Strike overpaid for SGNL. At $740 million for a startup that hadn't yet achieved significant public market penetration, the price seemed aggressive.
But contextualizing this makes the valuation logical. The identity and access management market itself is massive. Every organization with more than a few hundred employees needs IAM. The category includes legacy players like Okta, Ping Identity, and Forge Rock. But none of these companies have truly solved the continuous identity problem.
Moreover, Crowd Strike isn't buying SGNL in isolation. They're buying a technology that unlocks access to millions of enterprise customers already running Falcon. Every organization using Crowd Strike for endpoint security becomes a potential customer for identity solutions.
The TAM (total addressable market) for continuous identity management is essentially unlimited right now because nobody's really doing it at scale. SGNL had a technology wedge into this market. Crowd Strike has the distribution, brand trust, and financial resources to scale it.
Historically, platform companies have acquired specialized security firms to fill product gaps. Microsoft acquired security companies. Palo Alto Networks acquired multiple identity and threat prevention firms. Cisco acquired security startups. Crowd Strike is following the same playbook.
The question isn't whether $740 million is expensive. The question is whether continuous identity management becomes table stakes for enterprise security. If it does, SGNL's technology could enable billions in future revenue.
How Continuous Identity Management Actually Works
Understanding SGNL's technology requires understanding how it fundamentally differs from traditional IAM.
Traditional access control follows a simple model: authentication followed by authorization. You log in (authentication proves you are who you claim to be). The system checks your permissions (authorization confirms you're allowed to do what you're asking). You get access.
This model is binary. You're either authorized or you're not. The system checks this once, at the point of access request. After that, it assumes the access is safe for the entire session.
Continuous identity management replaces this with a probabilistic model. Instead of asking "Is this person authorized to do this?" the system asks "What is the current risk profile for this identity and request?"
The system continuously collects signals. Location data. Device information. Network context. Time of day. Historical behavior patterns. Requested resource type. Request frequency. Unusual parameter values. Everything becomes a data point.
These signals feed into a risk model. The model is constantly re-evaluating. Not just at login, but continuously throughout the session. If risk rises above a threshold, the system can automatically revoke access, force re-authentication, or escalate for human review.
For AI agents specifically, this becomes even more powerful. The system can monitor:
- Request rates: Is this agent making requests at its normal frequency or has something changed?
- Resource access patterns: Is it touching resources in its normal scope or branching into new areas?
- API parameters: Are the specific parameters in requests consistent with normal operations?
- Data volumes: Is the agent moving data at expected volumes or are there anomalies?
- Temporal patterns: Is the agent running at expected times or has the schedule changed?
- Cross-system correlations: Are related systems showing unusual activity that correlates with this agent's behavior?
When anomalies are detected, the system has options. It can deny the request. It can require additional verification (MFA, hardware token confirmation, manager approval). It can log the suspicious activity for investigation. It can automatically rollback changes. It can revoke the identity's privileges temporarily.
The key word is continuous. Traditional systems check permissions once. Continuous systems are always checking, always evaluating, always adapting.
SGNL's Technology Architecture and Approach
While SGNL operated mostly in stealth mode before the acquisition, their technical approach became clear through patents, research, and industry conversations.
The core architecture centers on behavioral baselining and anomaly detection. When an identity first becomes active in the system, SGNL builds a behavioral profile. It's not a simple statistical average. It's a multi-dimensional model of normal behavior.
For a human employee, this includes:
- Geographic locations where they typically access systems
- Times of day when they're active
- Devices they typically use
- Systems and applications they interact with
- Data volumes they typically access
- Request patterns and frequencies
- Peer group behavior (what do similar employees do?)
For service accounts and AI agents, this includes:
- Expected operating times and durations
- Normal API endpoints being called
- Typical data flow volumes and directions
- Database tables or resources typically accessed
- Computational resource requirements
- Integration patterns with other systems
Once baselines are established, any deviation triggers investigation. But not all deviations are equally important. SGNL's system uses sophisticated weighting to distinguish between minor variations that are probably fine and major anomalies that suggest a real problem.
The system integrates with standard enterprise tools. It consumes logs from cloud providers, on-premises systems, SaaS applications, and network infrastructure. It correlates signals across systems. It understands context.
A user logging in from a new country isn't automatically blocked. But that new location combined with requests for high-value resources combined with unusual file downloads combined with access outside normal business hours? That's a concerning pattern.
Integration with Crowd Strike's Falcon Platform
Where SGNL becomes truly powerful is integrated with Crowd Strike's existing Falcon platform.
Falcon runs at the kernel level on endpoints. It has deep visibility into process execution, network connections, file access, and system behavior. This visibility is granular and real-time.
When SGNL's identity assessment combines with Falcon's endpoint visibility, something interesting emerges. The system can connect the identity making a request with the actual system behavior on the endpoint.
Example: An API key makes a request to access sensitive data. SGNL evaluates whether that access is consistent with the identity's baseline. But simultaneously, Falcon could be showing that the process making that API call is unusual. The process was spawned by an unexpected parent process. It's trying to access files it shouldn't. It's making network connections to suspicious destinations.
Neither signal alone might be conclusive. But together, they create a much stronger case for intervention.
This convergence of identity-based and endpoint-based security is where Crowd Strike's acquisition strategy makes sense. They're not just buying a point solution. They're buying a component that integrates with their existing platform to create a more complete picture of threats.
The Regulatory and Compliance Angle
There's a second reason this acquisition matters: regulatory compliance.
SOC 2, ISO 27001, HIPAA, PCI-DSS, and other compliance frameworks all have requirements around access control. The basic requirement is consistent: ensure that only authorized individuals access sensitive data.
For years, companies could satisfy this requirement through static controls. Document who should have access. Implement that access through role-based access control (RBAC) or attribute-based access control (ABAC). Audit access logs periodically.
But regulatory bodies are increasingly questioning this approach. A single compromised credential can expose vast amounts of sensitive data. Even if access logs show the compromise eventually, the damage is done.
Auditors and regulators are starting to expect more. They're asking: "Did you detect this compromise? How quickly? What did you do to prevent unauthorized access?"
Continuous identity monitoring directly addresses these questions. If your system is continuously evaluating access risk, you can detect compromises faster. You can prevent unauthorized access automatically. You have evidence of proactive defense, not just reactive detection.
This becomes especially important in regulated industries: financial services, healthcare, government. These sectors have the most stringent requirements and the highest compliance costs. Continuous identity management that improves compliance posture is valuable.
Security Implications: What Changes with This Acquisition
For organizations already using Crowd Strike, the SGNL acquisition creates new possibilities.
Their current security posture probably includes:
- Endpoint detection and response (EDR) through Falcon
- Maybe cloud workload protection
- Possibly some threat intelligence integration
But identity-specific threats have been under-addressed. If an attacker steals credentials but never executes suspicious code on endpoints, Falcon isn't going to catch them.
SGNL fills that gap. Now Crowd Strike customers can add continuous identity verification to their security stack. Not as a separate product requiring a different team and different processes, but integrated with their existing deployment.
This matters operationally. Security teams are already overloaded. Adding another product means adding another console, another team, another set of alerts. Integrating continuous identity into Falcon means one platform, one set of APIs, one unified view of threats.
For organizations not using Crowd Strike, this acquisition is a signal about where the industry is moving. If Crowd Strike is investing $740 million in continuous identity management, and if their customers need it (enough that they're willing to integrate it into their core security platform), then identity security has become core.
That means budget dollars will follow. Organizations will invest in identity. Competing solutions will emerge. The market will consolidate around products that best solve the continuous identity problem.
The Timeline and Regulatory Path
Crowd Strike announced the acquisition was expected to close by the end of April 2026, pending standard regulatory approvals.
For a $740 million all-cash deal, regulatory approval is typically straightforward. The deal doesn't raise antitrust concerns (SGNL is small, the identity management market is large, and lots of competitors exist). It doesn't involve critical infrastructure or national security technology (though this is borderline for security software, approval is likely).
The main regulatory work is probably administrative: filing with relevant authorities, disclosure obligations for a public acquirer, maybe some state-level regulatory notifications. Nothing that typically derails such deals.
So expect SGNL to become part of Crowd Strike sometime in the second quarter of 2026. This timing is important because it gives Crowd Strike time to plan integration. Acquiring companies always overestimate how quickly they can integrate. Real integration takes time.
Expect to see:
- Early 2026: Antitrust filing and regulatory process
- Mid-2026: Deal closure, SGNL formally becomes a Crowd Strike subsidiary
- Late 2026/Early 2027: First integrated product releases combining SGNL tech with Falcon
- 2027: Full integration into Falcon platform roadmap
- 2028+: Fully integrated, mature continuous identity capabilities available to all customers
This is a multi-year integration, not a quick acquisition.
What About SGNL's Existing Customers?
One concern for organizations that had already purchased or were evaluating SGNL: what happens to their existing deployments?
Crowd Strike's official statement: SGNL will be retained as a team. There will be no layoffs. The company will continue to operate (at least initially) as a relatively independent entity within Crowd Strike.
This suggests that existing SGNL customers will continue to be supported. Their existing deployments probably won't be immediately discontinued or migrated.
Over time, expect gradual integration. SGNL's functionality will likely be packaged into the broader Falcon platform. Customers will have migration paths. Eventually, continuous identity management becomes just another module in Falcon.
For organizations relying on SGNL: this acquisition is probably good news. It means better funded development, faster innovation, broader distribution, and integration with the most capable endpoint security platform in the market.
For organizations deciding whether to bet on SGNL or choose a competitor: the acquisition should increase confidence in SGNL's roadmap and viability.
Competitive Implications: How This Affects the Market
The SGNL acquisition sends a clear message to the identity and access management market.
Okta has historically owned the identity market. They went public, built an empire on the strength of their access management platform, and became somewhat dominant. But Okta struggles with several things: complexity, implementation time, customer satisfaction scores. The SGNL acquisition suggests that even Okta's dominance is being challenged by more specialized, more focused solutions.
Now, with Crowd Strike entering with continuous identity capabilities, the market gets more fragmented. Organizations will have choices:
Option 1: Best-of-breed approach. Use Okta for traditional access management. Use Crowd Strike Falcon for endpoints. Use SGNL (within Crowd Strike) for continuous identity. This requires integration work but lets you optimize each component.
Option 2: Platform consolidation. Move everything to Crowd Strike if they can deliver competitive identity capabilities. Simpler operationally. One vendor. One invoice. One support team.
Option 3: Stay with legacy. Continue using Okta, Ping Identity, Forge Rock, and traditional IAM. This works fine if you don't care about continuous identity monitoring or AI agent security.
Most enterprises will probably choose option 2 or 3, depending on their current architecture. But the threat is clear to incumbent players. If Crowd Strike can deliver continuous identity capabilities that are even 80% as good as pure-play identity solutions, but integrated with the world's best endpoint security platform, many customers will consolidate.
This puts pressure on Okta, Ping, and Forge Rock to accelerate their continuous identity roadmaps or acquire capabilities in that space.
For smaller identity startups, the SGNL acquisition is a mixed signal. Good news: if your technology is good, you might get acquired at a high price. Bad news: the barrier to entry is now higher. You're not just competing against Okta. You're competing against Crowd Strike's resources and distribution.
Technical Integration Challenges Ahead
While Crowd Strike's acquisition is strategically sound, the technical integration will be complex.
SGNL's technology was probably built to be cloud-native and independent. It has its own APIs, its own database architecture, its own logging and monitoring systems. Integrating this with Falcon without duplicating functionality and without creating performance issues is non-trivial.
Specific challenges:
API consistency: Falcon has its own API design patterns. SGNL probably has different patterns. Making them coherent for customers is an integration effort.
Data model alignment: How does SGNL's concept of an "identity" map to Falcon's existing data models? How do you represent continuous identity signals in Falcon's existing schema?
Performance at scale: Falcon runs on millions of endpoints. Adding continuous identity evaluation for every endpoint means adding massive data collection and processing requirements. The architecture has to handle that.
Backwards compatibility: Existing Falcon customers need to keep working without changes. But adding continuous identity features means adding new code paths, new decision points, new data flows. That increases complexity and risk.
Customer migration: How do you move customers from SGNL as a standalone product to SGNL as a Falcon component without disrupting their operations?
These challenges are solvable, but they're not trivial. Expect integration to take 12-18 months to reach mature status.
The Broader Trend: Security Consolidation
The SGNL acquisition fits into a broader industry trend: security consolidation.
Twenty years ago, enterprises would cobble together 15-20 different security tools. A firewall from one vendor. Antivirus from another. IDS/IPS from a third. SIEM from a fourth. It was a nightmare to manage.
Slowly, the industry moved toward platform consolidation. Palo Alto acquired companies to build a more complete platform. Cisco bought security startups. Microsoft built security into Windows and Office.
Today, the trend is accelerating. Organizations want fewer vendors, more integration, simpler operations. They want one platform that covers endpoints, cloud, identity, threat intelligence, and incident response.
Crowd Strike was already moving in this direction with their cloud security and threat intelligence acquisitions. Adding SGNL's identity capabilities completes more of the platform picture.
Expect this trend to continue. Every security vendor will face pressure to consolidate. Standalone point solutions become less valuable. Integrated platforms become more valuable.
For customers, this is a double-edged sword. Consolidation brings operational benefits (fewer tools, simpler integration, unified logging). But it also creates vendor lock-in and reduces flexibility.
Preparing Your Organization for Continuous Identity Management
If your organization is considering whether to adopt continuous identity management, here's what you should think about now.
First, get your identity inventory in order. You probably don't have a complete picture of all the identities in your environment. Humans have identities. Service accounts have identities. API keys are identities. Managed credentials in vaults are identities. AI agents have identities. If you're not tracking all of these in one place, start now.
Second, understand your current baseline. Normal behavior looks different for different identities. Understanding what's normal for your environment is prerequisite to detecting what's abnormal. Start collecting behavioral data now. You'll need 30-90 days of baseline to build accurate models.
Third, audit your privilege levels. Most organizations have massive privilege creep. Someone gets access for a specific project. The project ends but the access remains. After a few years, people have way more access than they actually need. Start revoking unnecessary privileges now, before deploying continuous verification. Otherwise you'll get false positives on legitimate (but infrequently used) access.
Fourth, plan for integration. Continuous identity management requires data from multiple systems. Your cloud provider. Your on-premises systems. Your SaaS applications. Your network. Make sure these systems can export the necessary data and that your security operations center can ingest and correlate it.
Fifth, design your response procedures. When continuous identity monitoring flags a suspicious request, what happens? Does it automatically deny access? Does it force MFA? Does it escalate for human review? Design this workflow now, before you deploy the technology. Otherwise you'll have alerts but no clear process for responding.
Cost-Benefit Analysis: Is Continuous Identity Worth It?
Let's talk about the practical economics.
Continuous identity management systems cost money. Either as part of a platform like Crowd Strike Falcon, or as a standalone product like SGNL was. Typical costs run from thousands to tens of thousands of dollars per year depending on deployment scope.
But what do you get?
Faster breach detection. Traditional methods for detecting compromised credentials rely on external intelligence or customer complaints. It might take weeks to discover a credential compromise. Continuous identity monitoring can detect it in minutes. Faster detection means less time for attackers to move laterally or exfiltrate data. Reduced dwell time.
Reduced blast radius. Even if a credential is compromised, continuous identity monitoring limits what the attacker can do with it. Unusual requests are blocked. Lateral movement is detected immediately. The damage is contained.
Compliance improvement. Auditors see continuous monitoring as evidence of strong controls. This improves compliance assessments and might reduce audit scope or audit costs.
Reduced incident response costs. When a security incident occurs (and they will), having continuous identity data accelerates investigation. You know exactly when the compromise started. You know which resources were accessed. You know what was changed or exfiltrated. This reduces incident response time and costs.
Prevention of insider threats. Not all threats are external. Continuous identity monitoring detects inappropriate access patterns regardless of whether they originate from external attacks or internal misconduct.
A rough ROI calculation:
Average cost of a data breach:
Now, assume continuous identity monitoring reduces your dwell time from 215 days to 15 days (a reasonable expectation). That faster detection and containment prevents escalation. It reduces overall breach impact by maybe 40%.
That's $1.8 million in prevented costs per incident. If your organization faces a material breach once every 2-3 years (which is increasingly common), continuous identity monitoring pays for itself many times over.
Of course, this assumes you actually detect the breach faster and respond to alerts appropriately. If you deploy continuous identity monitoring but ignore the alerts, you get no benefit. So organizational commitment matters.
Industry Adoption and Future Outlook
Where is continuous identity management heading?
Right now, it's still relatively early. Most organizations are just beginning to think about this. But adoption is accelerating due to three factors:
AI and automation: As more organizations deploy AI agents, the need for continuous identity management increases. You can't manage AI agent risk with static access controls.
Regulatory pressure: Regulators are increasingly expecting continuous monitoring. They're not satisfied with static controls and after-the-fact breach forensics.
Vendor consolidation: As major vendors like Crowd Strike invest in continuous identity, it becomes a competitive expectation. Other vendors have to offer it too.
In 3-5 years, expect continuous identity monitoring to be table stakes. Not a differentiator. Just a baseline capability that all serious security platforms have.
The question then becomes: who does it best? Who has the most accurate behavioral models? Who has the best integration with other security tools? Who causes the least operational friction?
That's where the real competition happens.
TL; DR
- Crowd Strike acquired SGNL for $740 million to add continuous identity management to their Falcon platform, addressing gaps in traditional static access control
- AI agents create new identity risks that legacy IAM systems can't detect because agents operate at superhuman speed and agents look like legitimate identities using valid credentials
- The identity market is growing fast: expected to reach 29 billion in 2025), driven primarily by demand for continuous behavioral monitoring and AI-aware identity solutions
- Continuous identity verification constantly evaluates access risk instead of granting static permissions, using behavioral baselines and anomaly detection to catch compromises in minutes rather than weeks
- This acquisition signals a major shift: platform consolidation around core security vendors, pressure on traditional IAM players to innovate, and the emergence of identity security as a critical enterprise priority

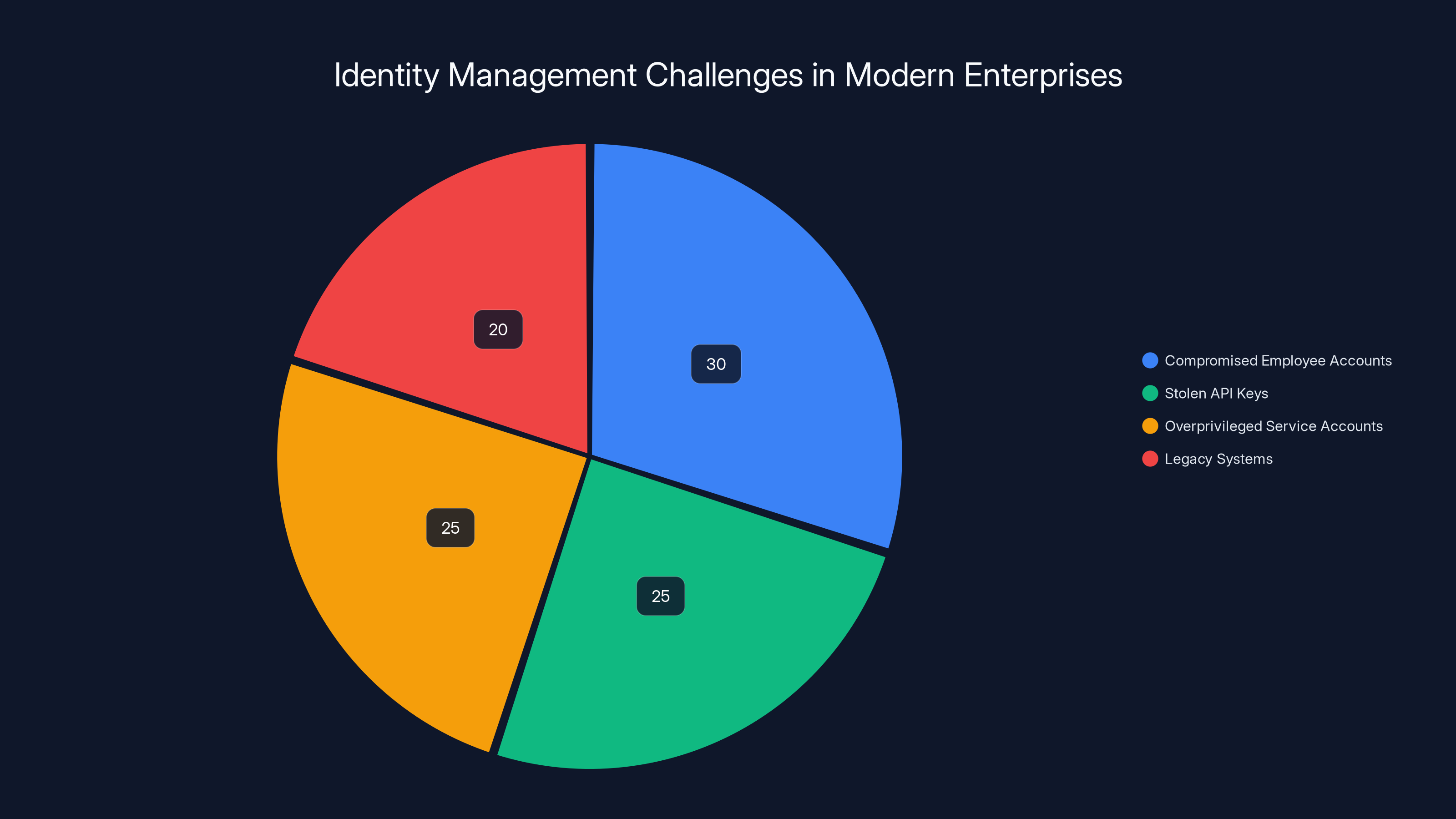
Estimated data shows that compromised employee accounts and stolen API keys are leading identity security challenges, highlighting the need for advanced solutions like those from CrowdStrike's acquisition of SGNL.
Comparing Identity Management Approaches
| Approach | Detection Speed | AI Agent Support | Integration | Cost |
|---|---|---|---|---|
| Static Access Control (legacy) | Weeks to months | Poor | Fragmented | Low |
| Traditional IAM with SIEM | Hours to days | Moderate | Complex multi-vendor | Moderate |
| Continuous Identity Monitoring | Minutes | Excellent | Integrated platform | Higher upfront, lower incident costs |
| Crowd Strike + SGNL (post-acquisition) | Minutes | Excellent | Single platform | Moderate to high |
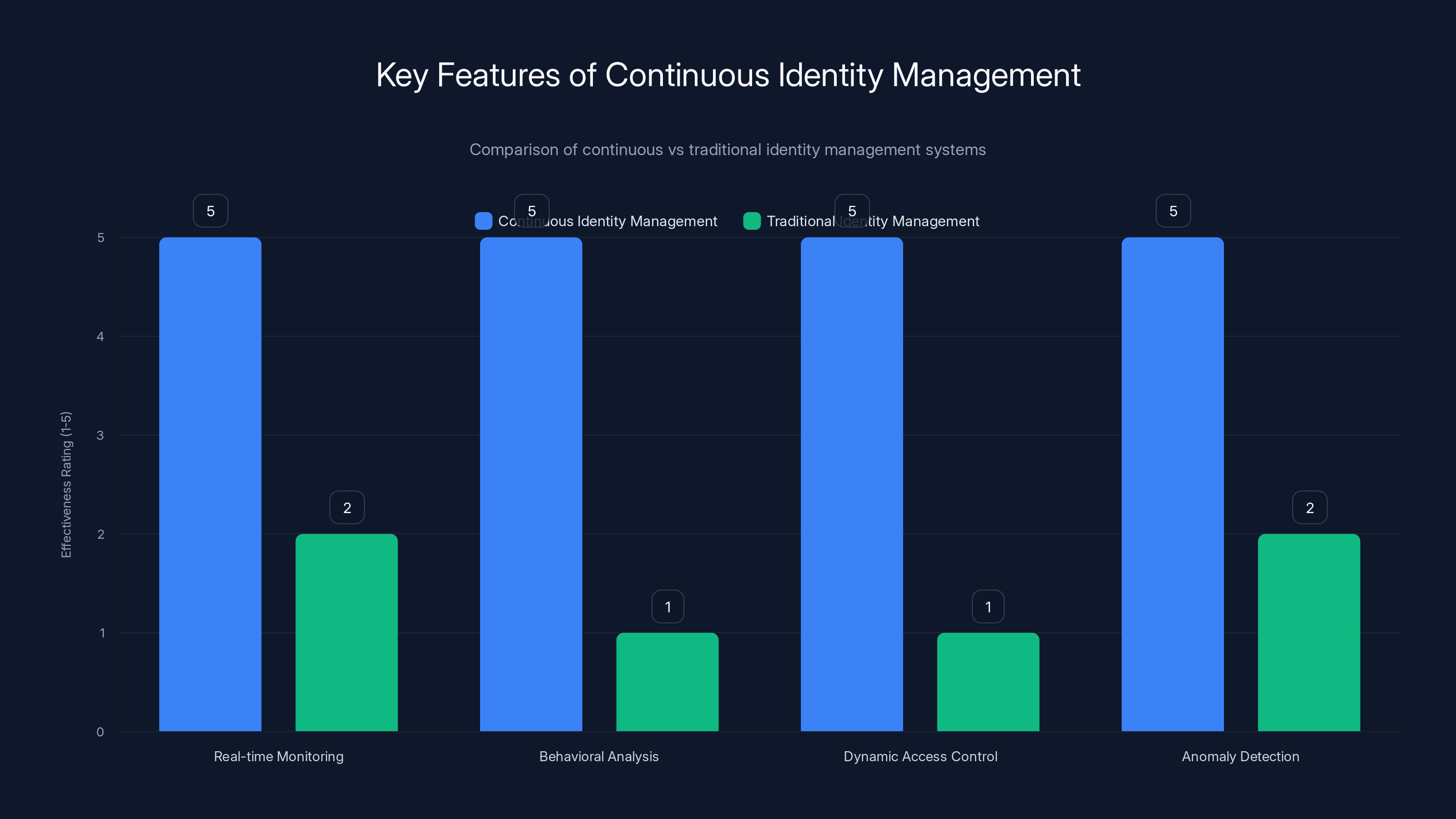
Continuous identity management excels in real-time monitoring, behavioral analysis, dynamic access control, and anomaly detection compared to traditional systems. Estimated data.
FAQ
What exactly is continuous identity management?
Continuous identity management is an approach to access control that constantly evaluates whether an identity should retain access based on real-time behavioral signals, risk assessment, and contextual factors. Rather than granting access once and assuming the holder is trustworthy for the entire session, continuous systems monitor behavior continuously and adjust access policies dynamically based on detected anomalies.
How does continuous identity monitoring detect AI agent compromises?
Continuous systems establish behavioral baselines for each identity, including normal access patterns, request frequencies, resource usage, and timing. When an AI agent's behavior deviates from its baseline, the system flags the anomaly. For example, if an agent suddenly requests resources it never touched before, makes requests at unusual frequencies, or accesses high-value systems outside its normal scope, the system detects and flags it immediately rather than waiting for human discovery.
Why can't traditional identity management systems handle AI agents?
Traditional IAM systems use static rule-based access control. They authenticate an identity once and check if it has permissions for the requested resource. If both check pass, access is granted. This approach treats all requests from the same identity equally, regardless of context. AI agents operating at superhuman speed with complex behavioral patterns don't fit this simple binary model, and their legitimate fast-moving activity can mask malicious activity using the same credentials.
What is the main risk Crowd Strike is addressing with the SGNL acquisition?
The primary risk is compromised credentials going undetected for extended periods. Today, attackers can steal a valid API key or service account credential and move laterally through systems for months using legitimate access. Continuous identity monitoring shrinks this "dwell time" from weeks or months to minutes by detecting suspicious behavioral patterns immediately.
How does SGNL's technology actually integrate with Crowd Strike Falcon?
SGNL's continuous identity evaluation runs alongside Falcon's endpoint monitoring. While Falcon watches what's happening on the endpoint level (processes, network connections, file access), SGNL watches what's happening at the identity and access level (who's accessing what, when, and whether it's consistent with their baseline). Together, they create a more complete picture. A suspicious API call combined with unusual process behavior on the endpoint creates stronger evidence of a compromise than either signal alone.
Will existing SGNL customers be forced to migrate to Crowd Strike?
No, at least not immediately. Crowd Strike has stated that SGNL will continue operating as a team with no layoffs, and existing customers will continue to be supported. However, over time, SGNL's technology will be integrated into the broader Falcon platform, and customers will have migration paths available. The timeline is likely 1-2 years for full integration.
What does this acquisition mean for Okta and other traditional IAM vendors?
It represents competitive pressure on traditional IAM vendors to accelerate their continuous identity and behavioral monitoring capabilities. If Crowd Strike can deliver continuous identity management that's even moderately competitive with pure-play identity solutions but integrated with the world's best endpoint security, many customers will consolidate around Crowd Strike rather than maintaining multiple vendors. Okta, Ping Identity, and Forge Rock now face either innovating faster or potentially losing market share.
Is continuous identity monitoring expensive to implement?
Initial implementation costs can be significant because it requires understanding your baseline identity behavior and configuring policies. However, the ROI is typically strong for larger organizations. If continuous monitoring prevents even one material data breach (which can cost $4.5+ million), it pays for itself many times over. Smaller organizations should evaluate carefully based on their breach risk profile and available security budgets.
What's the timeline for the SGNL acquisition to close and be integrated?
The deal was expected to close by the end of Q2 2026, pending regulatory approval (which is expected to be straightforward for a $740 million security software acquisition). Full integration with Falcon will likely take 12-18 months after closure, with initial integrated products arriving in late 2026 or early 2027 and mature integrated capabilities available throughout 2027.
How should organizations prepare for continuous identity management?
Start by getting a complete inventory of all identities in your environment (humans, service accounts, API keys, AI agents, etc.). Build 30-90 days of baseline behavior data. Audit and remove unnecessary elevated privileges. Ensure your systems can export necessary behavioral data. Design incident response procedures for when continuous monitoring flags suspicious activity. These steps before deployment will dramatically improve the effectiveness of continuous identity monitoring when you do deploy it.

The Future of Identity Security
This acquisition marks a turning point. Identity security, long treated as a separate concern from other cybersecurity domains, is becoming central.
Crowd Strike's move says something clear: if you want to build a competitive security platform in 2025 and beyond, continuous identity management isn't optional. It's foundational.
Over the next 3-5 years, expect:
Adoption acceleration. Organizations will move from optional monitoring to mandatory continuous identity verification. It becomes part of your baseline security posture.
Regulatory mandates. Regulators will start explicitly requiring continuous identity monitoring for high-value data and critical systems. It'll move from best practice to compliance requirement.
Vendor consolidation. The players who have end-to-end solutions will win. Standalone identity vendors without strong endpoint or threat intelligence capabilities will struggle.
Automation advancement. Today's continuous identity systems mostly flag suspicious activity for human review. Future systems will automatically remediate many threats without human intervention.
AI integration. The systems that detect AI agent threats will themselves use AI for behavioral analysis. The sophistication of both offense and defense will increase exponentially.
The SGNL acquisition is Crowd Strike positioning for this future. Whether they execute on the integration is the open question. But the strategy is clear: platform consolidation around continuous identity is where the market is heading.
If you're making security decisions today, assume continuous identity management is coming to your environment. Start preparing now.
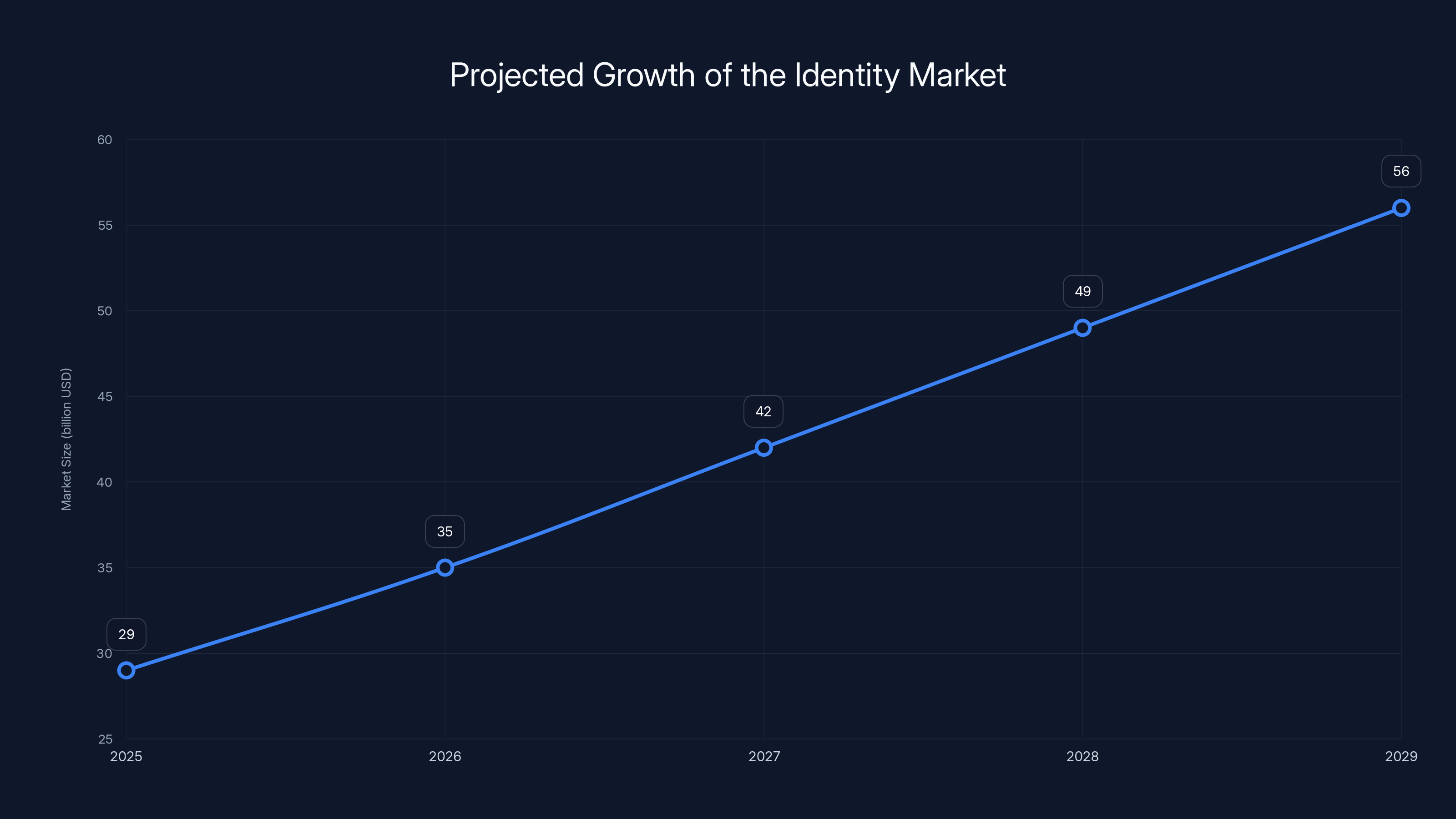
The identity market is projected to grow from
Key Takeaways
- CrowdStrike's $740M acquisition of SGNL reflects a strategic bet that continuous identity management is the future of enterprise security
- AI agents operating at superhuman speed expose critical gaps in legacy static access control systems that grant permanent privileges
- The identity and access management market is growing 13.7% annually and expected to nearly double from 56B by 2029
- Continuous behavioral monitoring can reduce breach detection dwell time from 215 days to 15 days, preventing escalation and reducing incident costs by 40%
- Platform consolidation around integrated security solutions threatens traditional IAM vendors like Okta, creating competitive pressure to innovate faster
Related Articles
- IBM Bob AI Security Vulnerabilities: Prompt Injection & Malware Risks [2025]
- Cyera's $9B Valuation: How Data Security Became Tech's Hottest Market [2025]
- AI-Generated Non-Consensual Nudity: The Global Regulatory Crisis [2025]
- Illinois Data Breach Exposes 700,000: How Government Failed [2025]
- NSO's Transparency Claims Under Fire: Inside the Spyware Maker's US Market Push [2025]
- Iran's Internet Collapse: What Happened and Why It Matters [2025]
![CrowdStrike SGNL Acquisition: Identity Security for the AI Era [2025]](https://tryrunable.com/blog/crowdstrike-sgnl-acquisition-identity-security-for-the-ai-er/image-1-1767978675594.jpg)



