Introduction: The Unguarded Gateway to Your Enterprise Data
Your security operations center has probably approved a dozen customer experience platforms like Salesforce, Qualtrics, Drift, and Salesloft. They're marked low-risk in your asset inventory because they're just "survey tools." That classification is killing you.
These platforms aren't collecting feedback anymore. They're ingesting billions of unstructured interactions every single year: survey responses, chat transcripts, social media reviews, call center notes, email threads. Then they're feeding that raw data into AI engines that automatically trigger workflows touching your payroll systems, CRM, payment processors, and cloud infrastructure. No DLP rule can see inside that flow. No SIEM alert catches what the AI is doing with it. And attackers have figured that out.
The breach pattern is getting worse. In August 2025, attackers compromised Salesloft's GitHub repository and stole Drift chatbot OAuth tokens. From there, they accessed Salesforce environments across 700 organizations including Cloudflare, Palo Alto Networks, and Zscaler. They weren't dropping malware. They weren't using zero-days. They were just walking through approved API connections that nobody was actually monitoring, exporting terabytes of data that DLP policies couldn't see because it looked like unstructured text. And security teams saw nothing because the traffic came through legitimate authentication channels that were already signed off.
The statistics are brutal. Ninety-eight percent of organizations claim to have a data loss prevention program. Only six percent actually dedicate resources to it. Eighty-one percent of cloud intrusions now use legitimate access instead of malware. Cloud attacks themselves surged 136 percent in just the first half of 2025.
Yet most security teams still haven't touched CX platform security. The gap isn't theoretical anymore. It's actively being exploited right now. And it exists because there's a fundamental mismatch between how security teams classify these platforms and what they've actually become. Qualtrics alone processes 3.5 billion interactions annually—double what they were handling in 2023. That's not a survey tool. That's a data processing engine sitting between your workforce and your infrastructure, and it's operating almost entirely outside your security framework.
This article breaks down exactly what's happening, why it's happening, and what you need to do to close each gap. These are six control failures that showed up in every conversation with security leaders trying to fix this problem. Some solutions exist today. Some don't. But understanding them is the first step toward actually securing this layer.
The Scale of the Problem: Why CX Platforms Became Attack Vectors
Customer experience platforms started simple. Surveys. Net Promoter Score collection. Basic feedback loops. The security team looked at them, shrugged, and filed them under "low risk" in the same category as project management apps.
That's the moment the calculus broke. Because over the last three years, CX platforms exploded in scope and connectivity. They're not just collecting sentiment anymore. They're connecting directly to HRIS systems to correlate employee feedback with compensation data. They're integrating with CRM platforms to track customer satisfaction alongside revenue. They're pulling data from Slack, email archives, social media feeds, call recordings. And they're feeding all of that—every piece of unstructured text, every audio transcription, every sentiment score—into machine learning models that make recommendations and trigger automated workflows.
Those workflows touch real systems. An HR platform might receive a recommendation from a CX engine analyzing employee survey responses and automatically flag someone for attrition risk. A payment processing system might integrate with a CX platform to refund dissatisfied customers automatically. A Salesforce instance might trigger lead scoring based on sentiment data the CX platform just processed.
Each of those connections is an API token. Each token is a relationship between systems that your security team approved based on assumptions that don't hold anymore. When that token gets compromised—which they do, constantly—an attacker has a direct path through an already-approved connection into multiple critical systems.
The Salesloft breach crystallized exactly this vulnerability. The attackers didn't need to exploit a zero-day or bypass a firewall. They got OAuth tokens. Those tokens had scopes that connected to Salesforce, which connected to downstream systems across 700 organizations. The lateral movement path was already built into the approved integration. The security team had signed off on it.
What made it worse is that nobody was watching. Not because the tools don't exist—they do, in fragments. But because the category "CX platform security posture management" doesn't really exist as a mature market yet. You can buy tools to monitor Salesforce user activity, permissions, and API usage. You can buy tools to monitor Service Now configurations. But the combination of tools that would let you see what data a CX platform is ingesting, how the AI is processing it, what workflows it's triggering downstream, and whether API tokens are still valid—that doesn't come as a package.
So security teams are flying blind. They see an approved integration in their SaaS management tool. They might have a SIEM alert if something breaks. But they have almost no visibility into the day-to-day operation of the platform, what data is flowing through it, who has admin access, and whether any of the connections are being abused.
Attackers have noticed. And the scale of CX platform deployment means the payoff is huge. If you hit one CX platform with a thousand customers, you've potentially compromised data across a thousand organizations. The breach surface is enormous. The detection probability is nearly zero. And the approved connection means you don't need to hide.
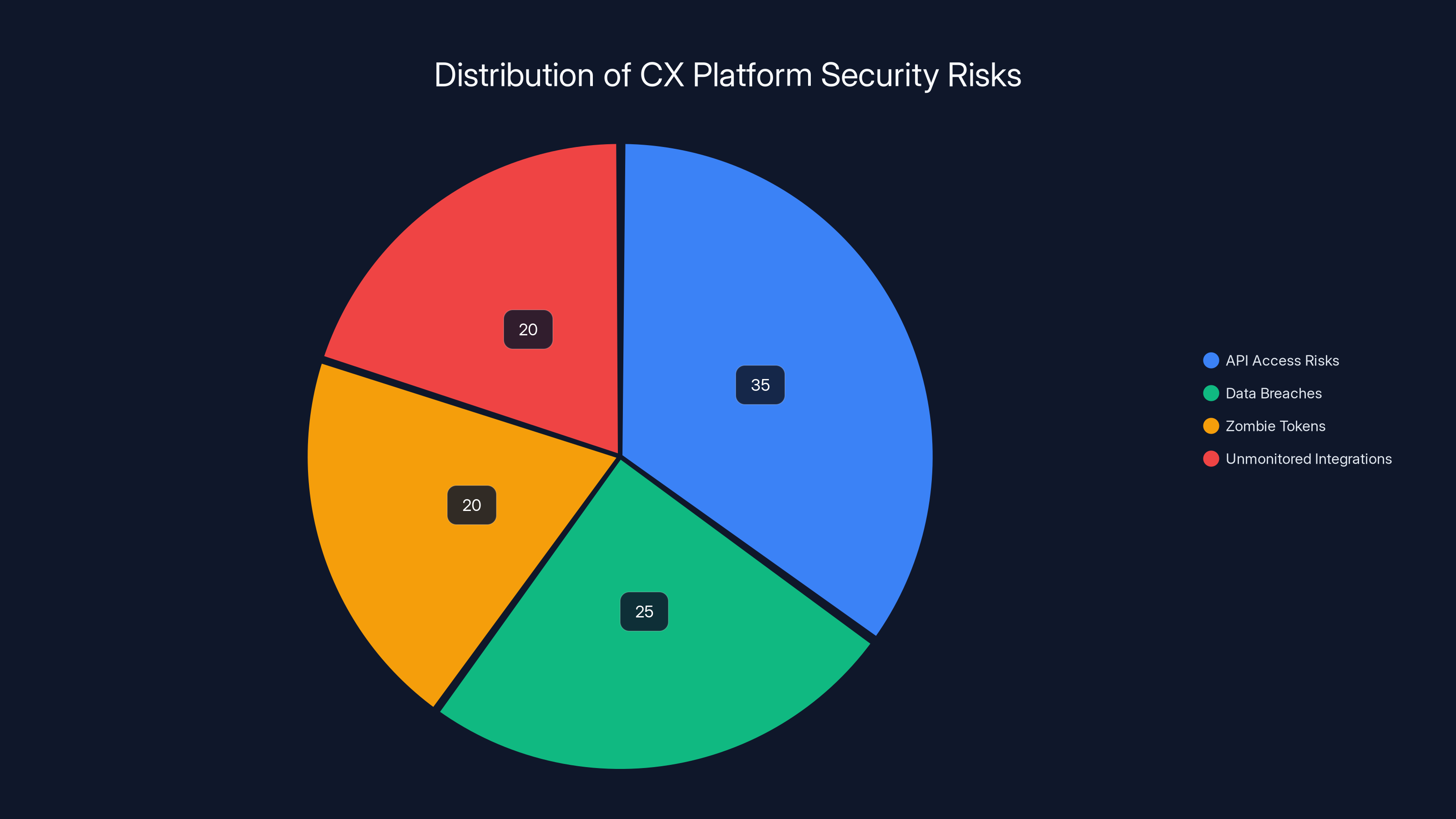
API access risks represent the largest security threat in CX platforms, followed by data breaches and zombie tokens. Estimated data.
Blind Spot #1: DLP Tools Can't See Sentiment Data Leaving Through API Calls
Your data loss prevention team spent months tuning rules. They know what a credit card number looks like. They know the format of Social Security numbers, health record identifiers, AWS key patterns. They've built detections around structured PII that flows through email, cloud storage, and API calls.
Then unstructured data happens. An employee survey response that reads: "My manager is handling this horribly and I'm looking for a new job. My salary is 140K which is below market and I have been doing this role for four years." That's multiple categories of sensitive information. It's explicit about salary. It's admitting to job searching. It's a management criticism that could affect someone's career. But it doesn't match any standard PII regex pattern. It's free text.
When that survey response gets pulled by a third-party CX analytics platform through an API call, the DLP system sees exactly what's happening: an API call exporting data. But it can't see the content because the DLP policy is looking for structured patterns, not sentiment in prose. The call goes through. Nobody fires an alert.
Customer feedback is exactly the same problem. A Trustpilot review might include account numbers, details about disputes, information about payment methods. But it arrives at the CX platform as unstructured text. If the CX platform re-exports that data to a vendor for analysis—for example, a third-party AI service that does sentiment scoring—the export looks like a routine API call to any DLP system. The data is sensitive. The transit is monitored. But the monitoring can't see what's actually being transmitted because it's wrapped in prose instead of structured fields.
The real kicker is that this isn't a hypothetical problem. During the Salesloft breach, attackers exported customer data that included exactly this kind of unstructured PII. They got email addresses, account details, and sensitive information embedded in notes and transcripts. The DLP should have caught it. But because it came through a legitimate API connection and the content was unstructured, the policies didn't trigger.
Some organizations are trying to solve this by deploying semantic DLP tools that actually read the content of data in transit, not just pattern-match on field formats. Those tools are more expensive and more resource-intensive, but they can actually see what "My salary is 140K" means even when it's embedded in a longer sentence. The problem is that semantic DLP typically runs on network perimeter. When data is exported through a legitimate API that your security team already approved, the semantic DLP sees it as expected traffic and doesn't flag it as anomalous.
The real solution requires understanding not just that data is leaving, but whether it should be leaving. That's where you hit the next blind spot: nobody's actually tracking what data the CX platform should be holding onto versus what should be exported. The business case for the platform says "analyze customer feedback for insights." But the actual data flow has evolved to include everything from salary information to health disclosures to information about security practices and infrastructure. The approved use case doesn't match the actual use case anymore.
One approach that's starting to work is adding another layer: tagging data at the point of ingestion in the CX platform itself. When an employee survey response containing salary information arrives, the CX platform should tag it as "contains_compensation_data." When a customer review mentions an AWS configuration, it should be tagged as "contains_infrastructure_info." Then API calls that export data with those tags can be flagged as anomalous, regardless of whether the DLP system can parse the semantic content. It's not perfect, but it's significantly better than hoping DLP pattern matching will catch everything.
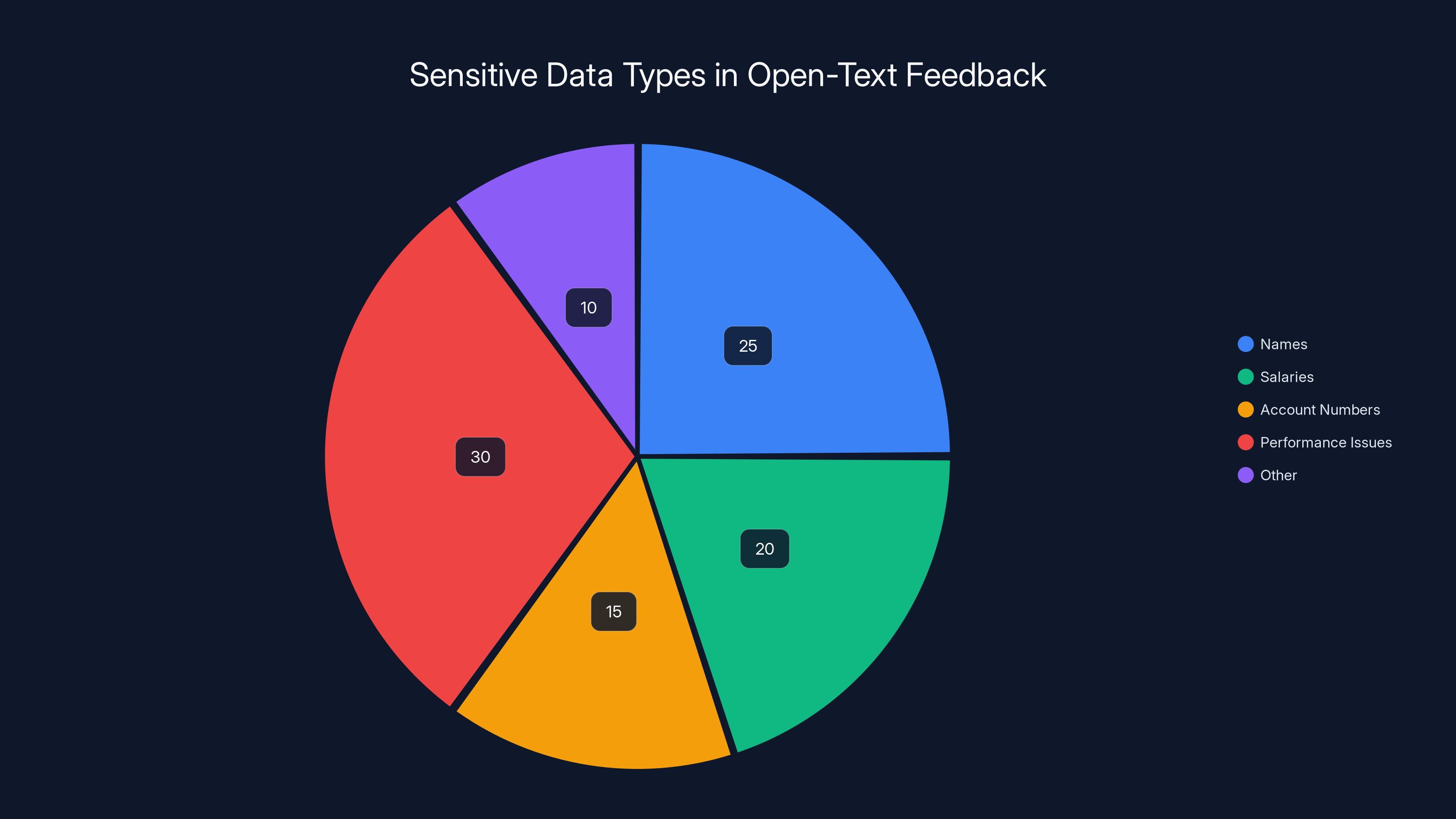
Estimated data shows that performance issues and names are the most common sensitive data types in open-text feedback, highlighting the need for effective masking strategies.
Blind Spot #2: Zombie API Tokens Create Forgotten Lateral Movement Paths
Six months ago, your marketing team ran a customer experience campaign. They integrated the CX platform with your HRIS system to correlate employee engagement scores with performance data. It was a time-limited project. It had a clear end date. Then the campaign ended and everyone moved on.
But the OAuth token connecting those two systems is still valid. Nobody revoked it. It's still there, in the CX platform's integration configuration, with the same scopes it had when the campaign was active. Those scopes still allow reads and writes to your HRIS system. And if that CX platform gets compromised, that token becomes a direct lateral movement path.
This isn't paranoia. JPMorgan Chase's CISO flagged this exact vulnerability in April 2025. The problem is fundamental to how SaaS integrations work. When system A wants to access system B, you grant it explicit permission through a token. That token includes scopes: what data it can read, what data it can write, how long it's valid. Then you stop using the integration. But most organizations have no systematic process for revoking tokens that are no longer needed.
The threat is compounded because CX platforms tend to be owned by business teams, not security teams. Marketing sets up the integration because they need speed and don't want to wait for security approval processes. Then when the campaign ends, marketing moves on to the next project. Six months later, nobody even remembers the integration existed. The token is still sitting there.
If a CX platform later gets compromised—through malware, through a supply chain attack, through developer access being stolen—an attacker with access to the platform's integration configuration can find those zombie tokens and use them immediately. They don't need to crack anything. They don't need to know the credentials. The token is already there, already authenticated, already with the right scopes.
From the HRIS system's perspective, the traffic is completely legitimate. The authentication succeeds. The token was granted by the CX platform, which is an approved partner. The access is within the token's scopes. The SIEM system sees successful authentication and maybe doesn't even alert because this is expected behavior for an approved integration.
But the usage pattern is wrong. Normally the CX platform pulls employee engagement data once a month for analytics. Now it's exporting the entire HRIS database at 3 AM on a Saturday. That's anomalous, but a SIEM system has to know the normal pattern first. And most organizations don't have that baseline for CX platforms because they don't think of them as security-relevant.
The solution requires systematic token lifecycle management. Every CX platform integration needs documentation: what it connects to, what scopes it has, when it was created, when it's supposed to expire. Then you need a quarterly review process where business owners verify that each integration is still active and still needed. If it's not, the token gets revoked immediately.
Some organizations are using a "token expiration by default" approach where every integration token has a maximum lifetime—maybe six months—and then it expires automatically unless someone explicitly renews it. That forces a review cycle and prevents zombie tokens from lingering indefinitely. But it requires discipline and tooling that most organizations haven't built yet.
The tougher problem is visibility. If you don't have an inventory of every CX platform your organization is using, and every integration that CX platform has, you can't possibly know which tokens need to be revoked. And most organizations don't have that inventory. A CX platform gets approved once for the marketing team. Then HR discovers it and sets up their own instance. Then customer success sets up another one. Now you have three separate CX platforms from the same vendor running in your organization, and security has no idea.
Blind Spot #3: Public Input Channels Have No Bot Mitigation Before Data Hits the AI Engine
Your CX platform is probably ingesting data from multiple sources. Internal surveys, sure. But also public reviews: Trustpilot ratings, Google Maps reviews, social media mentions, review sites. The idea is to get a complete picture of customer sentiment from every channel where customers are talking about you.
The problem is that none of those public channels are protected by your WAF, your bot mitigation, or your perimeter controls. A web application firewall inspects HTTP payloads for your web application. But it doesn't inspect a Trustpilot review that your CX platform is ingesting. It doesn't see a bot that's flooding Google Maps with negative reviews. It doesn't catch an attacker who's crafted a malicious customer feedback submission designed to trigger a specific workflow in your CX platform.
Let's say your CX platform is connected to your payment system. When customer sentiment hits a certain threshold—too many refund requests, too many complaints about billing—the system automatically issues refunds or provides credits. An attacker could flood your feedback channels with fake reviews saying "billing error, charged twice, no response to support ticket." They could use a botnet to generate hundreds of reviews. The bot mitigation on your web properties would catch some of it. But the Trustpilot reviews? The Google Maps reviews? Those go directly into your CX platform without any integrity checking.
Now your CX platform is ingesting fraudulent data. The AI engine trains on it. The sentiment analysis sees "billing error" repeated hundreds of times. A workflow gets triggered that issues automatic refunds or credits. An attacker has just turned your CX platform into a fraud engine without ever touching your infrastructure directly.
This is fundamentally a category gap. When you ask security vendors whether anyone provides "input channel integrity monitoring for public-facing CX data sources," the answer is: that category doesn't really exist yet. You can get bot mitigation for your web properties. You can get DLP for structured data flows. But there's no standard tool that says "before a CX platform ingests data from external sources, verify that the data is legitimate and not bot-generated."
Some organizations are bolting together solutions. They're using bot detection APIs before data gets to the CX platform. They're running sanity checks on incoming data to flag unusual patterns: too many reviews from the same IP address, reviews with identical phrasing, reviews that hit suspicious keywords. They're adding CAPTCHA challenges to public feedback submission forms. But it's all manual integration and there's no standard framework.
The challenge is that you can't just block all bot traffic from your feedback channels. Legitimate customers might be submitting feedback through VPNs or proxies. International customers might have IP addresses in unexpected locations. The bot detection has to be nuanced enough to catch attacks without blocking legitimate users.
One approach that's gaining traction is adding a verification layer: when your CX platform ingests external data, it tags it as "unverified" until it can be validated. Maybe that means checking whether the reviewer has a legitimate account and history on Trustpilot. Maybe it means correlating Google Maps reviews with actual customer purchase history. Maybe it means adding a human review step for high-impact feedback that would trigger expensive workflows like automatic refunds. The idea is to add friction to the data flow just enough to prevent automated attacks, while keeping the system fast for legitimate customers.
Another angle is post-ingestion verification. Your CX platform takes in all the data, but then applies content checks before feeding it to the AI engine. It could use semantic analysis to detect if review text is suspiciously generic or repetitive. It could flag reviews that reference infrastructure or internal details that external customers shouldn't know. It could watch for sudden spikes in feedback volume that suggest a coordinated attack. None of this is revolutionary—it's all fairly standard security hygiene applied to a new context. But it's not being done systematically right now.

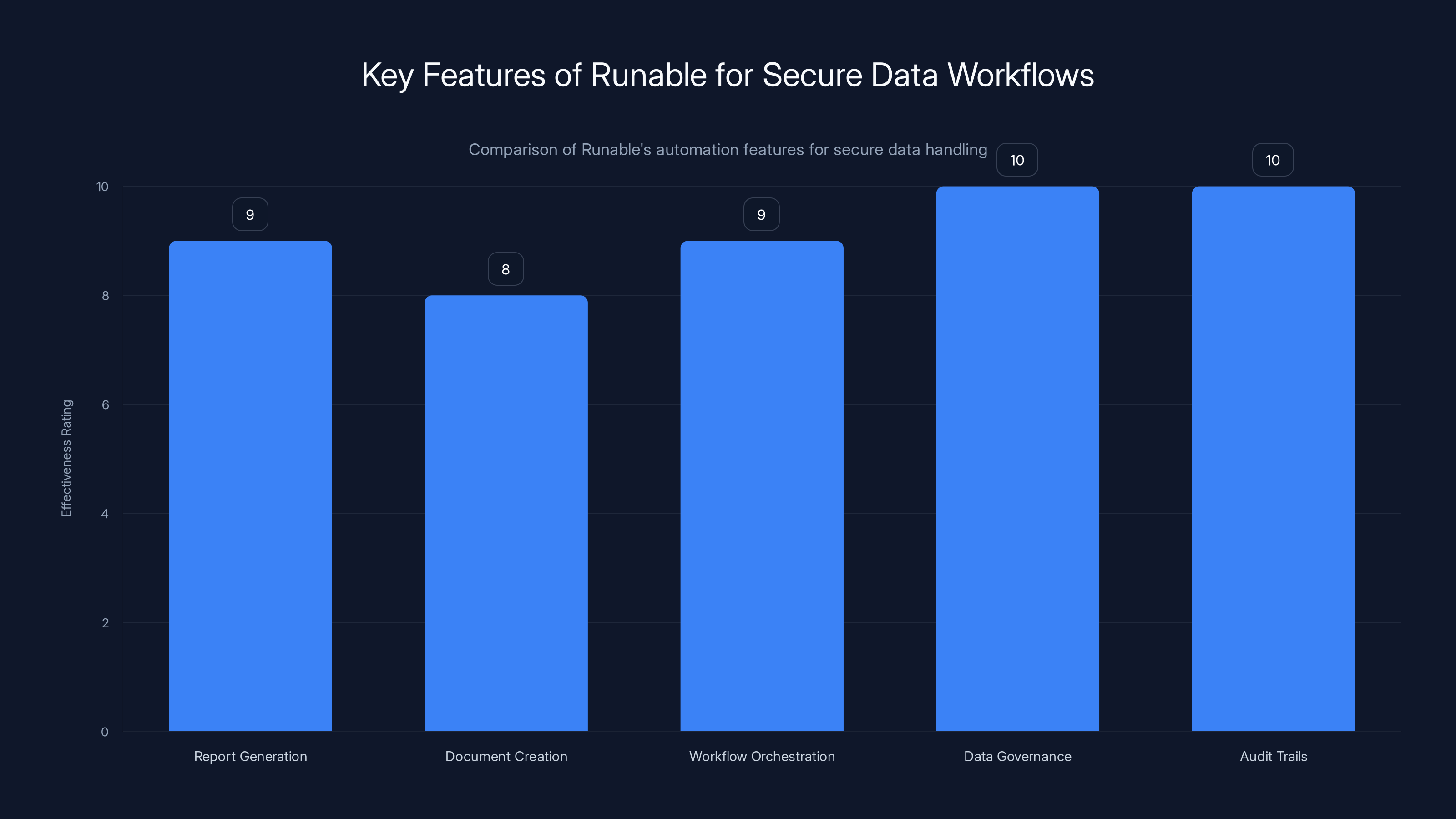
Runable excels in providing secure, automated workflows with high effectiveness in data governance and audit trails, making it a robust solution for managing CX platform outputs.
Blind Spot #4: Lateral Movement Through Approved API Calls Has No Behavioral Detection
Your SIEM sees that the CX platform authenticated successfully to your Salesforce instance. That's expected. The authentication attempt succeeds. The SIEM logs it and moves on.
Then the CX platform exports two terabytes of Salesforce data. The timestamp is 3 AM on a Sunday. The export includes customer PII, payment information, sales pipeline data, and email archives. But from the SIEM's perspective, nothing is wrong. The authentication token was valid. The export API calls all used the correct authentication headers. The data went to an IP address that the CX platform has accessed before. There's nothing technically anomalous about any individual API call.
But the behavior is wildly anomalous. The CX platform normally exports a few gigabytes of data once a month for reporting purposes. Now it's exporting terabytes. The CX platform normally accesses Salesforce between 9 AM and 5 PM on business days. Now it's running at 3 AM. The CX platform normally reads from specific data objects (campaigns, accounts, contacts). Now it's reading everything.
Your SIEM probably can't catch this because it doesn't have a baseline for CX platform behavior. Even if it did, the detection would require running behavioral analysis on every API call from every approved integration, which most SIEM deployments aren't configured to do.
This is where software posture management comes in. The concept is similar to user behavior analytics, but applied to SaaS applications instead of individual users. The idea is that you establish a baseline for what normal CX platform behavior looks like: how much data it usually exports, when it usually exports it, which systems it usually connects to, how long API calls usually take. Then you alert when behavior deviates significantly from that baseline.
The problem is that most organizations haven't built that visibility. They have API logs somewhere—maybe in their cloud provider, maybe in the CX platform itself. But they're not sending those logs to a centralized system where they can be analyzed for anomalies. Even if they are, they probably don't have the baseline because they've never actually looked at what the CX platform normally does.
One approach is to add an API gateway between your CX platform and the systems it connects to. The gateway sits in the middle of every connection and can enforce policies. It can rate-limit API calls: if the CX platform suddenly tries to export way more data than it usually does, the gateway can block it or alert security. It can enforce time-based policies: if the CX platform tries to make API calls outside of business hours, the gateway can challenge it or require additional authentication. It can enforce scope policies: if the CX platform tries to access data objects it doesn't normally access, the gateway can block it.
The gateway can also do something that's basically impossible without it: correlate behavior across multiple API calls. A single request to export data is normal. But 500 requests in a row to export data, all to the same endpoint, all to external IPs? That's suspicious. The gateway can see the pattern and block it. A SIEM looking at individual API logs would probably miss it.
Another approach is to add a detection layer specifically for CX platforms. There are a few startups building tooling in this space, though the market is still early. The idea is that you connect the detection tool to your CX platform's audit logs, and it automatically flags anomalous behavior based on patterns it's learned. It doesn't require you to specify exactly what normal looks like—it learns it over time.
But the fundamental issue is that this all requires treating CX platforms as security-relevant. Right now, most security teams don't. They approve the integration, add it to the SaaS management tool, and move on. If you're going to catch lateral movement through CX platforms, you need to start monitoring them the same way you'd monitor a Salesforce instance or a Service Now deployment.
Blind Spot #5: Non-Technical Business Users Have Admin Privileges Nobody Reviews
Marketing needs to set up a new customer experience campaign. They don't want to wait three weeks for security approval. So they set up the CX platform themselves, configure the integrations themselves, maybe even grant themselves admin access so they can make changes as the campaign evolves. It's fast. It works. Security never finds out about it.
This is shadow admin exposure, and it exists in almost every organization. Not because people are malicious, but because the approval process is too slow and the business need is real. Telling a marketing team "we can't approve that integration for three weeks" doesn't work when the campaign starts next week. So they bypass the process.
The problem is that when they set up the integration, they're making security decisions without security input. Maybe they grant the CX platform read-and-write access to your HRIS system when it only needs read access. Maybe they don't set up any MFA on the admin account they created. Maybe they reuse credentials across multiple platforms. Maybe they don't document the integration anywhere, so nobody knows it exists.
Then the campaign ends. The marketing person who set it up gets promoted or moves to a new team. Six months later, the integration is still there, still configured with overly permissive scopes, still with the admin account that nobody monitors. And if the CX platform gets compromised, the attacker has a direct path through an undocumented integration that security wasn't even aware of.
One CX vendor told us that when they conduct security audits for new customers, they typically find that 40-60 percent of the integrations the CX platform has are completely unknown to the security team. The business teams set them up, the integrations work, everyone's happy. Security has no idea they exist.
The solution, according to security leaders we interviewed, requires making security an enabler, not a blocker. That means having a fast-track approval process for CX platform integrations—maybe 24 hours instead of three weeks. It means having templates and best practices that marketing can follow to set up integrations securely without needing security's hands-on involvement. It means having documentation requirements: when you set up an integration, you document what it connects to, what scopes it needs, how long it's supposed to run. And it means having regular audits where security actually goes through the CX platform's integration list and verifies that everything is still needed and still configured correctly.
Some organizations are deploying "governance by defaults" approaches. Instead of requiring approval for every new integration, they allow integrations by default but with restrictive scopes. The CX platform can only read data by default, not write. The integration only works between 9 AM and 5 PM by default. The admin account requires MFA by default. If the business team needs broader permissions, they have to submit a request that goes through a lightweight approval process. But the default safe configuration means that even if they set up an integration wrong, the damage is limited.
Another angle is to build the approval process into the CX platform itself. Some CX vendors are adding features where integrations can be set up by business users but need security sign-off before they go live. The business team configures everything, then security gets a notification to review it. Security can either approve it or ask for changes. It's faster than a separate approval process, and it means security is actually seeing what integrations are being set up.
But the underlying issue is visibility. You can't approve something you don't know about. Most security teams have no idea how many CX platforms their organization is running, or what integrations those platforms have. Building that inventory is step one.

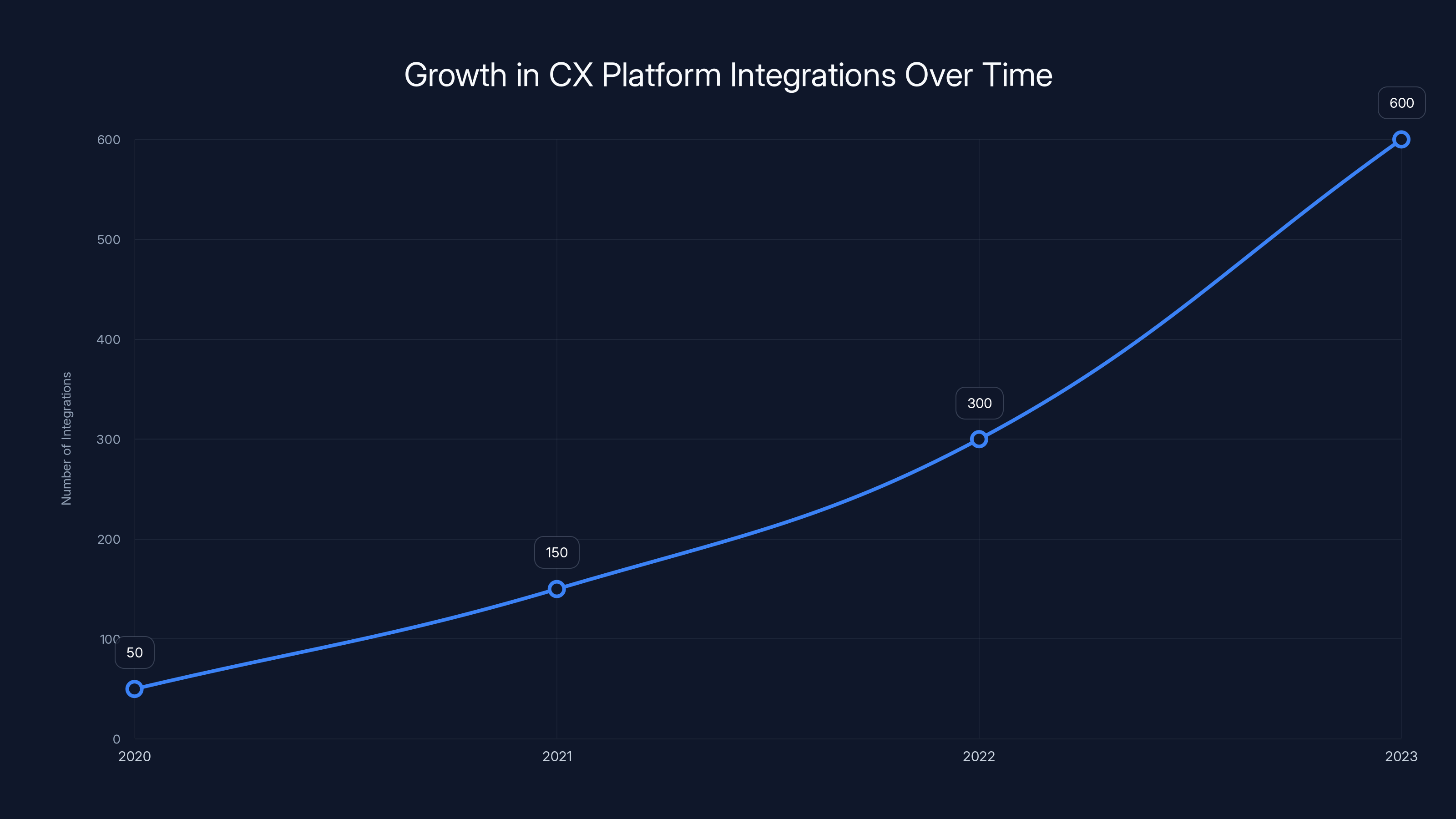
Estimated data shows a rapid increase in CX platform integrations, highlighting the growing complexity and potential security risks over the past three years.
Blind Spot #6: Open-Text Feedback Gets Stored Unmasked Before PII Classification Happens
Your employees are complaining in a survey. One response says: "My manager Susan is terrible. She criticized me in front of the team last month and I haven't gotten a raise since 2023. I make 95K and my coworker in the same role makes 110K. I'm looking to leave." That's multiple sensitive data points embedded in prose: a manager's name, salary information, information about performance management, signal about attrition.
Your CX platform ingests that response. Maybe it's supposed to be processed through a PII classifier that masks names and salary information. But the classifier is supposed to run after the data hits the database. So first the raw, unmasked response gets stored. Then the classifier runs. If a breach happens in between—and breaches can be hours or days before discovery—the attacker gets unmasked personal information.
Even worse, if the PII classifier is the only thing protecting that data, and a breach exposes the database, an attacker gets the raw text with every piece of sensitive information intact. The classifier didn't mask the underlying data, it just marked it with tags or flags. The data itself is still there.
Customer feedback has the same issue. A review that mentions "my account number is X" or "I received invoice Y" or "I had issues with your Salesforce integration" just gets stored as-is. The PII classifier sees account number and flags it. But the underlying data is still there, still available to anyone with database access.
This is especially problematic because CX platforms tend to have permissive access controls. The theory is that customer success, HR, and marketing teams need to access the feedback to do their jobs. So the access control is usually pretty loose. That means a compromised account, or even an employee with access who's exfiltrating data, can access the unmasked information.
The solution requires reversing the order: mask data at ingestion time, not after. When a survey response arrives, it immediately runs through a PII classifier that identifies sensitive information. Instead of storing the raw text, it stores masked text: "My manager [PERSON_1] is terrible. She criticized me in front of the team last month and I haven't gotten a raise since 2023. I make [AMOUNT_1] and my coworker in the same role makes [AMOUNT_2]. I'm looking to leave."
If an attacker breaches the database, they get the masked version. They know there's a salary difference, but they don't know the actual numbers. They know there's a manager involved, but they don't know the name. The semantic meaning of the feedback is preserved for analysis, but the sensitive data is protected.
The challenge is that masking can reduce the value of the feedback for some use cases. If you're trying to identify which managers have attrition problems, you need to know the manager's name. If you're trying to correlate salary information with performance reviews, you need the actual salary. So sometimes the business team wants access to unmasked data.
The solution there is granular access control: different users can see different levels of detail. The executive dashboard showing aggregate attrition trends by department shows masked data. The HR manager who needs to investigate a specific department can request access to unmasked data, which gets logged and audited. The data gets masked by default, and access to unmasked data is treated as a security-relevant decision that requires review.
Another approach is to use tokenization instead of masking. Instead of replacing the sensitive data with [AMOUNT_1], you store a token that's meaningless to an attacker but can be resolved by an authorized system. The actual salary data lives in a separate, highly protected database with much stricter access controls. The CX platform stores only the token. That way the CX platform can still be analyzed for insights, but the sensitive data itself is protected in a different system.
The Root Cause: CX Platforms Never Got the Security Treatment
Underlying all six of these blind spots is a single root cause: CX platforms have matured as a category, but their security posture management hasn't matured at the same pace.
Five years ago, companies like Gartner, Forrester, and the cloud security vendors all focused on SaaS security posture management for the big platforms: Salesforce, Service Now, Microsoft 365, Slack. That effort paid off. Today, there are mature tools for monitoring Salesforce user activity, permissions, and API usage. There are well-established best practices for securing Service Now instances. There's a clear framework for understanding what normal access patterns look like in each of these platforms.
But CX platforms never got the same treatment. From a market perspective, they're still seen as fringe tools. They're not as ubiquitous as Salesforce. They're not as high-profile as Service Now. They're owned by business teams instead of IT teams, which means they don't get the same security attention. And they're relatively new in their current form—it's only in the last three years that CX platforms have really expanded their data processing scope and AI capabilities.
So the security industry never built tooling for them. There are no mature CX platform SSPM tools. There are no CX platform-specific SIEMs or behavioral analytics tools. There are no frameworks for thinking about CX platform security. The security team looks at a CX platform and doesn't have a playbook for how to secure it.
Meanwhile, the business is moving forward. Marketing is using CX platforms. HR is using CX platforms. Customer success is using CX platforms. Each one is setting up integrations to downstream systems. The business value is real. And security can't block everything, because then the business would just route around security and hide what they're doing.
So we're in a gap: CX platforms have become critical infrastructure, but security tooling and frameworks haven't caught up. The six blind spots we've covered are manifestations of this gap. They're not unsolvable problems, but they require security teams to take an active stance on CX platform security instead of just approving it once and moving on.

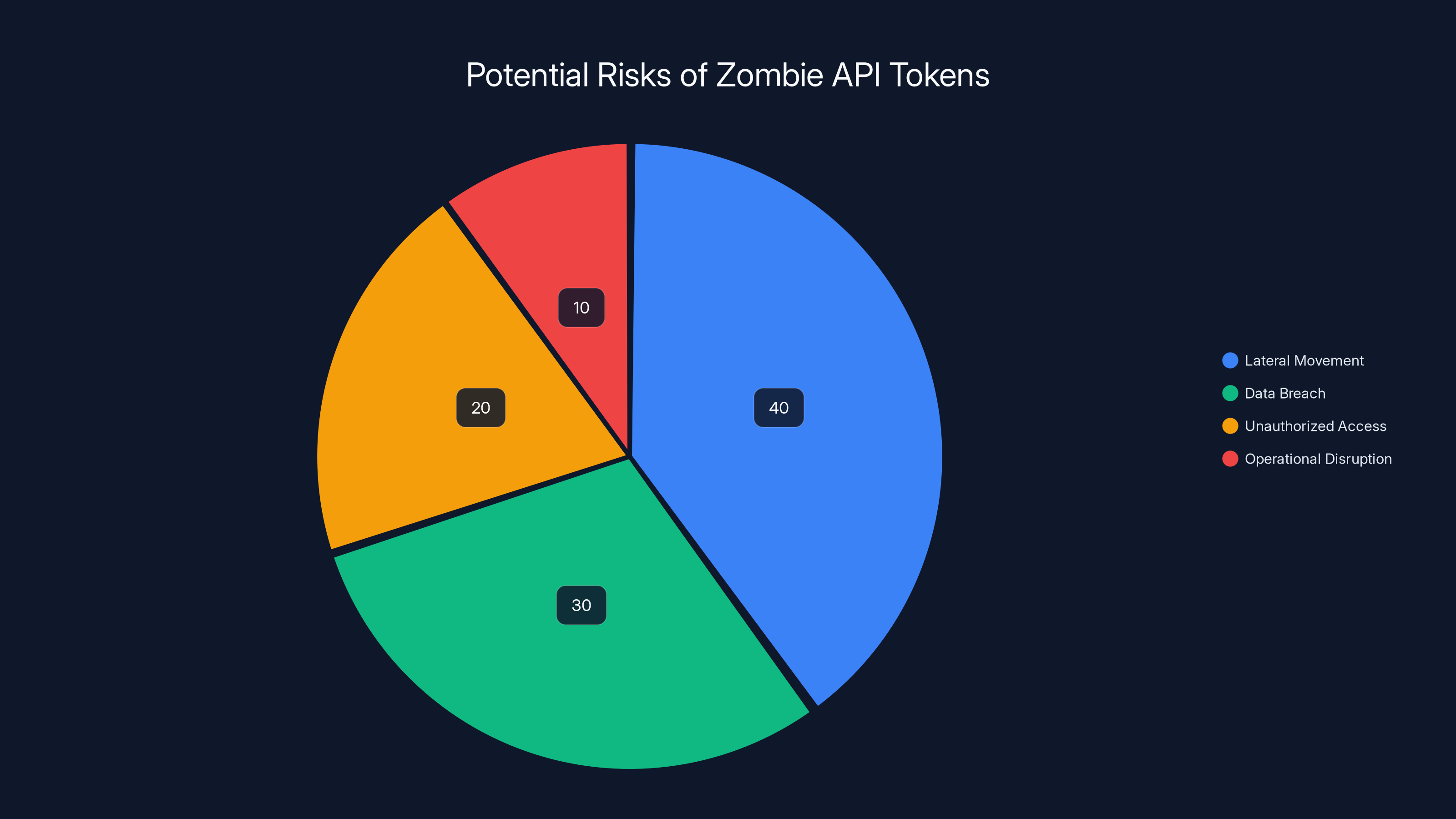
Estimated data shows that lateral movement poses the highest risk from zombie API tokens, followed by data breaches and unauthorized access. (Estimated data)
How Organizations Are Starting to Close the Gaps
Security teams that have made progress on this problem tend to be doing one or more of three things:
First, they're extending existing SSPM tools to cover CX platforms. The SSPM they already bought for Salesforce or Okta can probably be extended to monitor CX platform user activity, permissions, and configurations. It won't catch everything—CX platforms have unique data flows and AI processing that other platforms don't have. But it's a starting point. It gives you visibility into who has admin access, what integrations are configured, and whether things have changed.
Second, they're deploying API security gateways between CX platforms and the systems they connect to. The gateway lets you enforce policies on API calls: rate limiting, time-based restrictions, scope validation, behavioral anomaly detection. It's not CX-specific, but it's effective at catching lateral movement and preventing zombie tokens from being abused.
Third, they're building CX-specific security programs. That means documenting every CX platform the organization is using, every integration it has, every business use case it supports. It means establishing baseline behavior for each CX platform and monitoring for deviations. It means requiring that data be masked at ingestion time instead of after storage. It means implementing a lightweight approval process for new integrations that's fast enough that business teams will actually use it instead of bypassing it.
No single approach solves all six problems. But organizations that are doing at least some of these things are dramatically reducing their exposure.

Detection Strategies: How to Find If You're Already Compromised
The uncomfortable truth is that your CX platform might already be compromised. If you haven't been monitoring it, you might not know.
Here are some detection strategies security teams are using:
Anomalous data exports: Enable full API logging on your CX platform and aggregate those logs in a SIEM or data warehouse. Look for exports that are larger than usual, happening outside of business hours, or going to unexpected destinations. Volume baselines are key—you need to know what normal looks like before you can spot abnormal.
Token usage patterns: Audit every API token that your CX platform has access to. For each token, look at when it's being used, what data it's accessing, and whether the usage pattern has changed. A token that suddenly starts accessing new data objects or requesting much larger datasets than it used to is suspicious.
Failed authentication attempts: If an attacker is trying to compromise a CX platform, you might see unusual authentication patterns first: multiple failed login attempts, login attempts from unusual locations, attempts to access accounts that don't normally use the system. Those can be early warning signs.
Changes to integrations: Set up alerts for any changes to CX platform integrations. New integrations, modifications to existing integrations, revoked integrations, or changes to integration scopes should all trigger a review. Most organizations don't have this instrumentation, but it's relatively easy to add.
Unusual API calls: If your CX platform starts making API calls that it doesn't normally make—like accessing your payment system when it never did before, or accessing your AWS account—that's a strong signal. You need baseline behavior data to detect this.
Data appearing in unexpected places: If data from your CX platform starts showing up in unusual locations—exfiltrated to cloud storage, copied to web shells, sold on dark web forums—that's the discovery phase of a breach. Threat intelligence services and data breach notification services can help with this.
The challenge with all of these detection approaches is that they require visibility you probably don't have right now. If you haven't been logging CX platform activity, you can't go back and check for historical anomalies. The time to start monitoring is now, even if it means you can't detect past compromise.

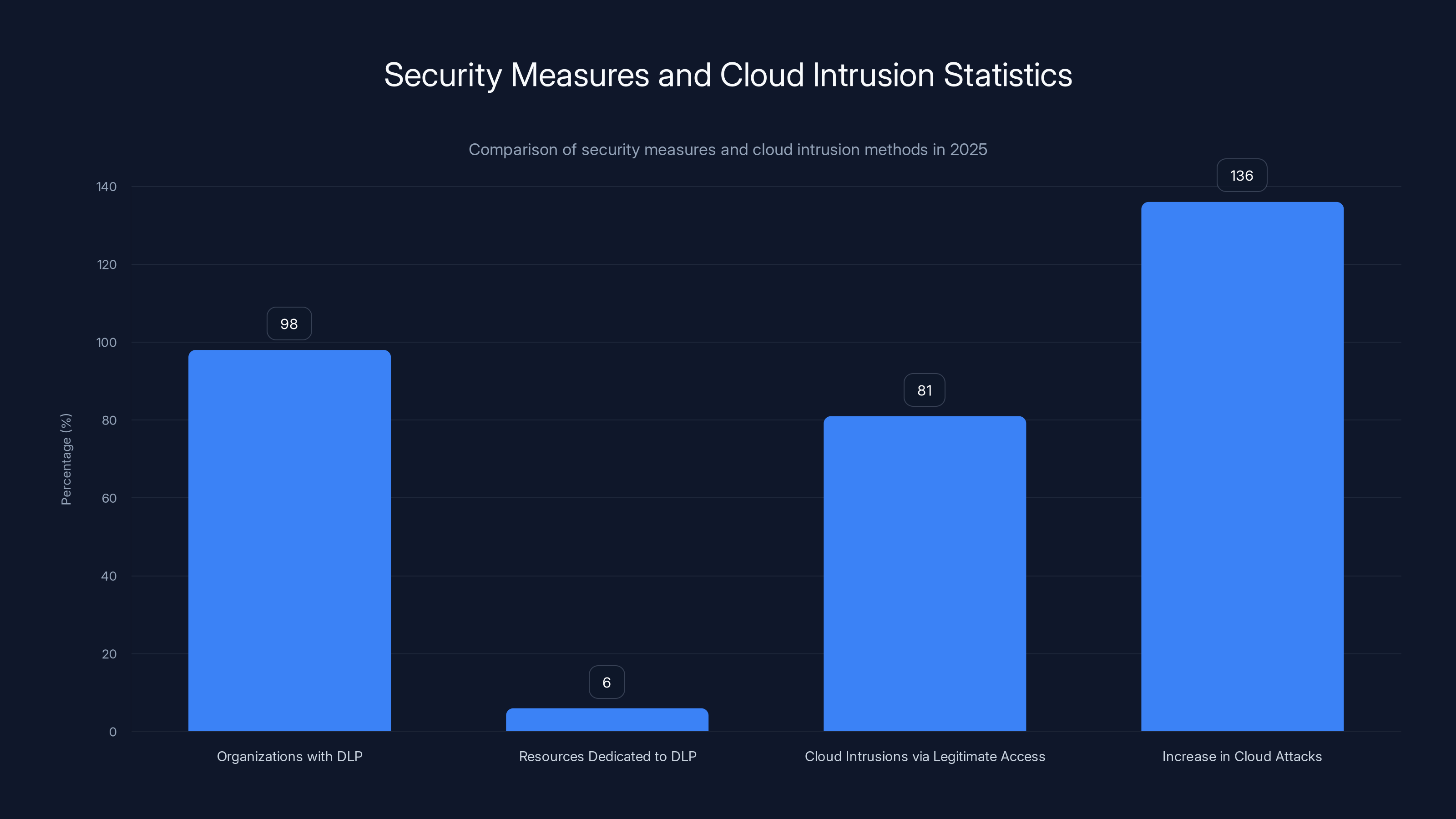
Despite 98% of organizations claiming to have a DLP program, only 6% dedicate resources to it. Meanwhile, 81% of cloud intrusions exploit legitimate access, with cloud attacks surging by 136% in early 2025.
Building a CX Platform Security Program: Step by Step
If you want to start closing these gaps, here's a practical roadmap:
Step 1: Inventory your CX platforms: Find out how many CX platforms your organization is running. Check with marketing, HR, customer success, and product teams. Look in your SaaS management tool. Check your cloud provider's API logs for common CX platform domain names. Once you have the list, document it: vendor, deployment date, owner, business use case, data it processes.
Step 2: Document all integrations: For each CX platform, list every system it connects to. Include the OAuth token, the scopes it has, the data it can access, when the integration was created, and whether it's still active. This is tedious but essential. You can't secure what you don't know about.
Step 3: Establish baseline behavior: For at least your most critical CX platforms, enable full API logging and export the logs to a SIEM or data warehouse. Run a full month of logging, then analyze the results: how much data does the platform normally export? When does it normally export? Which systems does it normally connect to? Document the baseline so you can detect deviations.
Step 4: Mask data at ingestion: Work with your CX platform administrators to enable data masking for any PII that enters the platform. PII should be masked at ingestion time, before it gets stored. If business teams need access to unmasked data, implement granular access controls and audit all access.
Step 5: Revoke zombie tokens: Go through every integration and verify that it's still active. For any integration that's ended, immediately revoke the token. Document the business justification for keeping any integration that's not actively used.
Step 6: Add bot mitigation to public input channels: If your CX platform is ingesting data from public sources (reviews, social media, etc.), add bot detection before the data reaches the AI engine. Verify that the input is legitimate before processing it.
Step 7: Set up monitoring: Enable continuous monitoring of CX platform activity. Use an API gateway if possible, or use log analysis if not. Establish alerting for anomalous behavior: unusual data exports, access outside business hours, token usage that deviates from baseline.
Step 8: Approve future integrations thoughtfully: Implement a lightweight approval process for new CX platform integrations. The process should be fast enough that business teams will use it. But it should require documenting the business use case, the data that will be accessed, the access controls, and the expected duration.
This isn't a one-week project. For a large organization with dozens of CX platforms and hundreds of integrations, this could take months. But it's necessary. The alternative is accepting that you have a large blind spot in your security posture.
What CX Vendors Are Doing to Improve Security
The leading CX vendors are starting to take this seriously. Some are building security features directly into their platforms:
Better data masking: Some vendors are enabling PII masking at ingestion time, so sensitive data never gets stored unmasked. That's a good step.
Integration approval workflows: Some are adding approval steps when business users try to create new integrations, so security can see and approve new connections before they go live.
Audit logging: Better audit logs let security teams see what's happening inside the platform. Some vendors are making those audit logs easier to export and analyze.
Role-based access control: More granular RBAC means you don't have to grant admin access to everyone who needs to make configuration changes. A user might be able to configure campaigns without being able to modify integrations.
API rate limiting and time-based restrictions: Some vendors are adding built-in API rate limiting and the ability to restrict API access to specific time windows, which makes it harder for attackers to export data quickly.
But the reality is that vendor features can only take you so far. The real security burden is on the organization deploying the platform. You need to own the inventory, the monitoring, the access control, and the incident response. The vendor can make that easier, but the responsibility is on you.
Future Trends: How This Is Going to Change
The CX platform security market is immature right now, but it's going to mature. Here's what's probably coming:
Purpose-built CX security tools: Startups are going to build tools specifically designed to monitor and secure CX platforms. These will likely focus on API security, behavioral anomaly detection, and PII protection.
CX platforms as critical infrastructure: As breaches continue to prove the severity of this gap, organizations are going to start classifying CX platforms as critical infrastructure. That means they'll get the same security treatment as ERP systems and payment platforms.
Regulatory pressure: Data protection regulations like GDPR, CCPA, and upcoming regulations are going to force companies to take CX platform security seriously. If a breach exposes personal data, the company's going to be liable.
Vendor consolidation: Some of the CX vendors that don't take security seriously are going to lose customers to competitors that do. Over time, this will force the entire category to raise their security standards.
Integration of AI safety: As CX platforms become more AI-driven, there's going to be more focus on AI safety—making sure the AI engines aren't being poisoned with malicious input, aren't making harmful decisions, and aren't leaking sensitive data.
Runable: Automating Secure Data Workflows
While closing CX platform security gaps is critical, there's another layer to consider: how you're managing the output of these platforms and the workflows they trigger. Runable offers an AI-powered automation platform that can help teams securely process and respond to data from CX platforms without manually touching sensitive information.
Instead of having humans manually review and act on CX platform outputs (which introduces its own security risks), you can use Runable to automate report generation, document creation, and workflow orchestration. The platform helps teams create AI-driven workflows that can ingest data from multiple sources—including CX platforms—and generate secure outputs like reports, presentations, and automated responses, all while maintaining data governance and audit trails.
The advantage is that you have centralized, auditable automation instead of scattered manual processes. Plus, at $9/month, it's affordable enough for teams to implement comprehensive automation without breaking the budget.
Use Case: Automate the generation of customer sentiment reports from CX platforms while masking PII and maintaining audit trails.
Try Runable For Free
Conclusion: This Is a Problem You Can Solve, But You Have to Start Now
The six blind spots in CX platform security are real, and attackers are actively exploiting them. But they're not unsolvable. Organizations that take this seriously and implement the controls we've covered can dramatically reduce their risk.
The key is recognizing that CX platforms have evolved. They're not survey tools anymore. They're data processing engines that connect to your most critical systems and process sensitive information about your customers and employees. They deserve the same security rigor that you apply to your ERP systems and payment platforms.
That means:
Own the inventory: Know exactly what CX platforms you have, what data they process, and what systems they connect to. This is table stakes.
Mask data early: Stop storing unmasked PII in your CX platforms. Mask it at ingestion time. If business teams need access to unmasked data, make that an explicit decision that gets audited.
Monitor behavior: Establish baselines for normal CX platform activity and alert on deviations. This is how you catch compromises early.
Revoke zombie tokens: Do a complete audit of every API token your CX platforms have. If an integration is no longer active, revoke the token. Then institute a regular review process to make sure unused tokens don't accumulate.
Add bot mitigation: If your CX platform is ingesting data from public sources, verify that the data is legitimate before processing it. This prevents attackers from poisoning your data sources.
Move fast on approval: Make it easy for business teams to get security sign-off for new CX platform integrations. If the process is too slow, they'll route around it and hide what they're doing.
These are not expensive fixes. Most of them are organizational changes, not technology purchases. But they're necessary. The Salesloft breach showed that attackers know about these blind spots and they're exploiting them. If you don't close these gaps, you're accepting risk that you don't have to accept.
Start with the inventory. That's always the hardest part, but it's also the most essential. Once you know what you have, the rest becomes possible.
FAQ
What are CX platforms and why are they security-critical?
Customer experience platforms like Salesforce, Qualtrics, Drift, and Salesloft collect and process billions of unstructured interactions annually—survey responses, chat transcripts, social media mentions, call recordings. They've evolved from simple feedback collection tools to AI-driven data processing engines that connect directly to HR systems, CRM platforms, payment processors, and cloud infrastructure. They're security-critical because they process sensitive data and have API access to your most important systems, yet they're often still classified as low-risk survey tools by security teams.
How did the Salesloft breach happen and what can we learn from it?
Attackers compromised Salesloft's GitHub environment and stole Drift chatbot OAuth tokens, which gave them legitimate API access to Salesforce instances across 700+ organizations including major security vendors like Palo Alto Networks and Zscaler. The breach succeeded because: the compromised tokens were valid, the access was pre-approved by security teams, and the lateral movement through approved API channels wasn't detected. The key lesson is that legitimate API access can be as dangerous as a malware infection if the access isn't properly monitored.
What is a zombie API token and why is it dangerous?
A zombie token is an OAuth token that was created for a time-limited integration that has since ended, but the token was never revoked. For example, a CX platform might have been granted access to your HRIS system for a three-month campaign. The campaign ends, but the token remains valid and stored in the CX platform's configuration. If the CX platform is later compromised, the attacker has immediate access through that zombie token, which the CX platform's authentication system recognizes as valid. The attacker doesn't need to crack anything or find new credentials—the path is already open.
How can DLP tools miss sensitive data leaving through CX platforms?
DLP tools are designed to detect and block structured PII: credit card numbers, SSNs, AWS keys. But CX platforms process unstructured data: employee survey responses containing salary complaints, customer reviews mentioning account details, transcripts of sensitive conversations. When that unstructured data is exported through a legitimate API call that your DLP team already approved, the DLP system sees expected traffic and doesn't flag it. The sensitive information is embedded in prose rather than structured fields, so standard PII pattern matching doesn't catch it. The solution requires either semantic DLP that reads prose content, or data tagging at ingestion time so the system knows unstructured data contains sensitive information.
What is software posture management for CX platforms and do such tools exist?
Software posture management (SPM) for CX platforms would involve monitoring user activity, permissions, configurations, and API usage patterns to establish what normal behavior looks like, then alerting when behavior deviates. SPM tools mature for platforms like Salesforce and Service Now track these metrics routinely. For CX platforms, the category barely exists. Some organizations are extending existing SSPM tools to cover CX platforms, while others are using API gateways or building custom monitoring using SIEM log analysis, but there's no mature, purpose-built market for CX platform security monitoring yet.
How can we detect if our CX platform is being abused?
Detection strategies include: monitoring API logs for unusual export patterns (larger volumes, unusual times, unexpected destinations), tracking API token usage to spot tokens accessing data they normally don't, setting up alerts for integration changes, looking for access to the CX platform from unusual locations or failed login attempts, and checking if CX platform data is appearing in threat intelligence feeds (indicating a breach may have occurred). The challenge is that most organizations lack baseline behavior data, so establishing normal patterns first is essential before anomaly detection can work.
What's the difference between masking and tokenization for protecting PII in CX platforms?
Masking replaces sensitive data with generic placeholders: a salary of "$140,000" becomes "[AMOUNT_1]" in stored records. This protects the sensitive value itself, but the semantic meaning remains—you can still see there's salary information. Tokenization goes further: it replaces the sensitive data with a meaningless token like "T7a 2b" that points to the actual data stored separately in a highly protected system. Tokenization is more secure for highly sensitive data because even someone with database access can't recover the original values, but masking is often sufficient for most use cases and is easier to implement.
How often should we audit CX platform integrations?
At minimum, quarterly reviews of all CX platform integrations. This review should verify that each integration is still active, still necessary, still has the correct scopes and permissions, and is still in use. For integrations that aren't actively used, the OAuth token should be revoked immediately. Some organizations are implementing auto-expiring tokens that require explicit renewal, which forces a review cycle automatically. The frequency should be higher if you've experienced a security incident or if your CX platforms have significantly increased their data processing scope.
What should we do if we discover a zombie token still has valid access?
Immediate actions: (1) Revoke the token immediately in the CX platform's integration configuration, (2) Verify the token hasn't been abused by checking API logs for unusual access from that token in the past 30-90 days, (3) Revoke any sessions or credentials the compromised integration might have used to authenticate to downstream systems, (4) Check access logs on downstream systems (HRIS, CRM, payment systems) for suspicious activity during the period the token was active. Then conduct a broader review to find other zombie tokens and implement a process to prevent new ones from accumulating.
How can we prevent bot attacks against public feedback channels feeding our CX platforms?
Implement bot detection on review sites and feedback submission channels before data reaches your CX platform: use bot detection APIs on public feedback forms, enable CAPTCHA on feedback submission, correlate review data with verified customer accounts (don't accept reviews from accounts without purchase history), flag reviews that match suspicious patterns (multiple reviews from same IP, identical phrasing), add a human review step for feedback that would trigger expensive automated actions like refunds. Post-ingestion, use semantic analysis to detect generic or suspicious content, and monitor for sudden spikes in feedback volume that suggest coordinated attacks.
What's the relationship between CX platform security and data privacy regulations?
Data privacy regulations like GDPR and CCPA hold organizations accountable for breaches of personal data, regardless of whether the breach happened in your own systems or a third-party vendor's systems. If a CX platform breach exposes customer or employee PII, your organization is liable for notification, fines, and potential lawsuits. Regulations are increasingly requiring that organizations implement data protection measures (encryption, access controls, audit trails) throughout their data processing pipelines, which includes CX platforms. This regulatory pressure is one reason why CX platform security is becoming a compliance issue, not just a best practice.

Key Takeaways
- CX platforms process 3.5+ billion interactions annually but are often classified as low-risk survey tools despite connecting directly to HRIS, CRM, and payment systems
- The Salesloft breach proved attackers can compromise 700+ organizations through CX platform OAuth tokens without deploying malware or using zero-days
- DLP tools can't see sensitive information in unstructured feedback, zombie tokens from ended campaigns create persistent lateral movement paths, and public input channels lack bot mitigation before AI ingestion
- 98% of organizations claim DLP programs but only 6% dedicate resources; 81% of cloud intrusions now use legitimate access instead of malware
- Closing the gap requires inventory of all CX platforms and integrations, baseline behavior monitoring, data masking at ingestion, token revocation processes, and lightweight security approval workflows
Related Articles
- AI Governance & Data Privacy: Why Operational Discipline Matters [2025]
- OpenClaw AI Ban: Why Tech Giants Fear This Agentic Tool [2025]
- Password Manager Vulnerabilities Explained [2025]
- Claude Desktop Extension Security Flaw: Zero-Click Prompt Injection Risk [2025]
- AI Security Breaches: How AI Agents Exposed Real Data [2025]
- N8N Critical Vulnerabilities Explained: CVE-2025-68613 & CVE-2026-25049 [2025]
![CX Platform Security Gaps: 6 AI Stack Blind Spots Attackers Exploit [2025]](https://tryrunable.com/blog/cx-platform-security-gaps-6-ai-stack-blind-spots-attackers-e/image-1-1771533428154.jpg)



