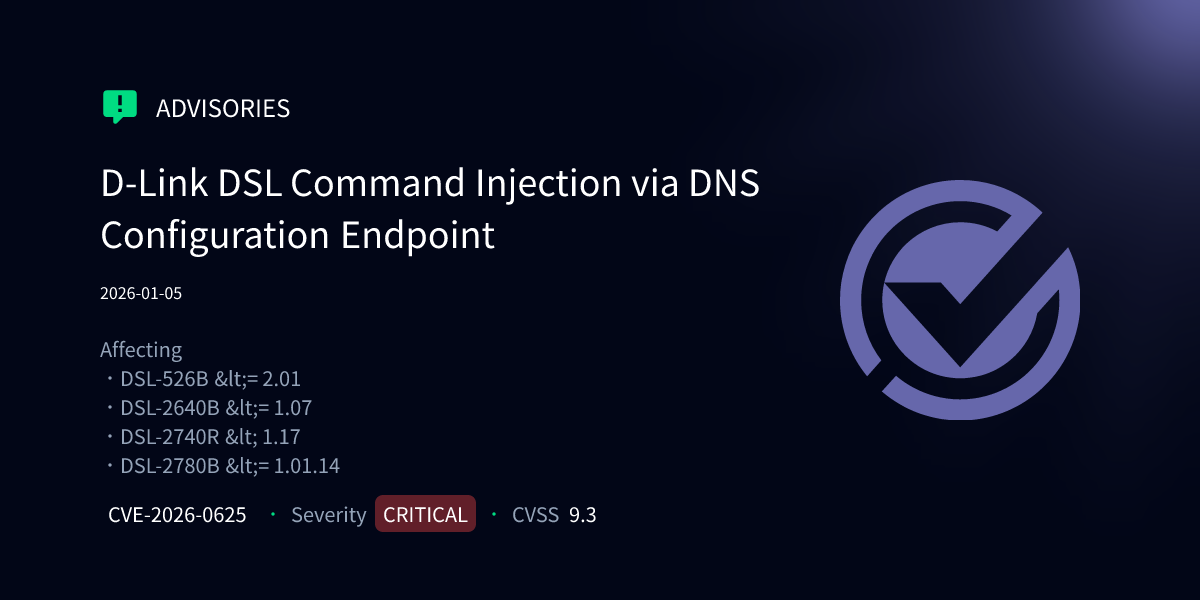
D-Link DSL Gateway Vulnerability: Understanding CVE-2026-0625 and the Critical RCE Risk
Your router sits at the edge of your network, quietly managing every packet of data flowing in and out. Most people never think about it until something breaks. But what if that quiet device became an active threat?
That's exactly what's happening right now with thousands of D-Link DSL gateway routers worldwide. A critical vulnerability identified as CVE-2026-0625 has been actively exploited since late November 2025, allowing attackers to execute arbitrary commands on affected devices without authentication. We're not talking about minor inconvenience here. We're talking about complete network compromise.
The vulnerability carries a severity score of 9.3 out of 10. To put that in perspective, that's borderline critical. The attack requires no special knowledge, no phishing, no social engineering. An attacker simply needs to know your router's IP address and can inject malicious commands directly through the DNS configuration interface.
Researchers at Vuln Check discovered active exploitation targeting specific D-Link models, including the DSL-2740R, DSL-2640B, DSL-2780B, and DSL-526B. These aren't new routers. Most reached end-of-life status between 2016 and 2019. But here's the thing: thousands of small businesses, remote offices, and home networks still use them. They work fine. They're invisible. So they stay.
That's the dangerous assumption we're examining in this guide.
TL; DR
- Critical Vulnerability: CVE-2026-0625 scores 9.3/10 severity, enables unauthenticated remote code execution on D-Link DSL routers
- Affected Models: DSL-2740R, DSL-2640B, DSL-2780B, DSL-526B with active exploitation since November 27, 2025
- Root Cause: Improper sanitization of DNS configuration parameters allows command injection attacks
- Business Impact: Compromised routers enable credential theft, ransomware deployment, botnet activity, and complete network infiltration
- Recommended Action: Immediately replace unsupported devices with current hardware; implement firewalls, strong authentication, and MFA
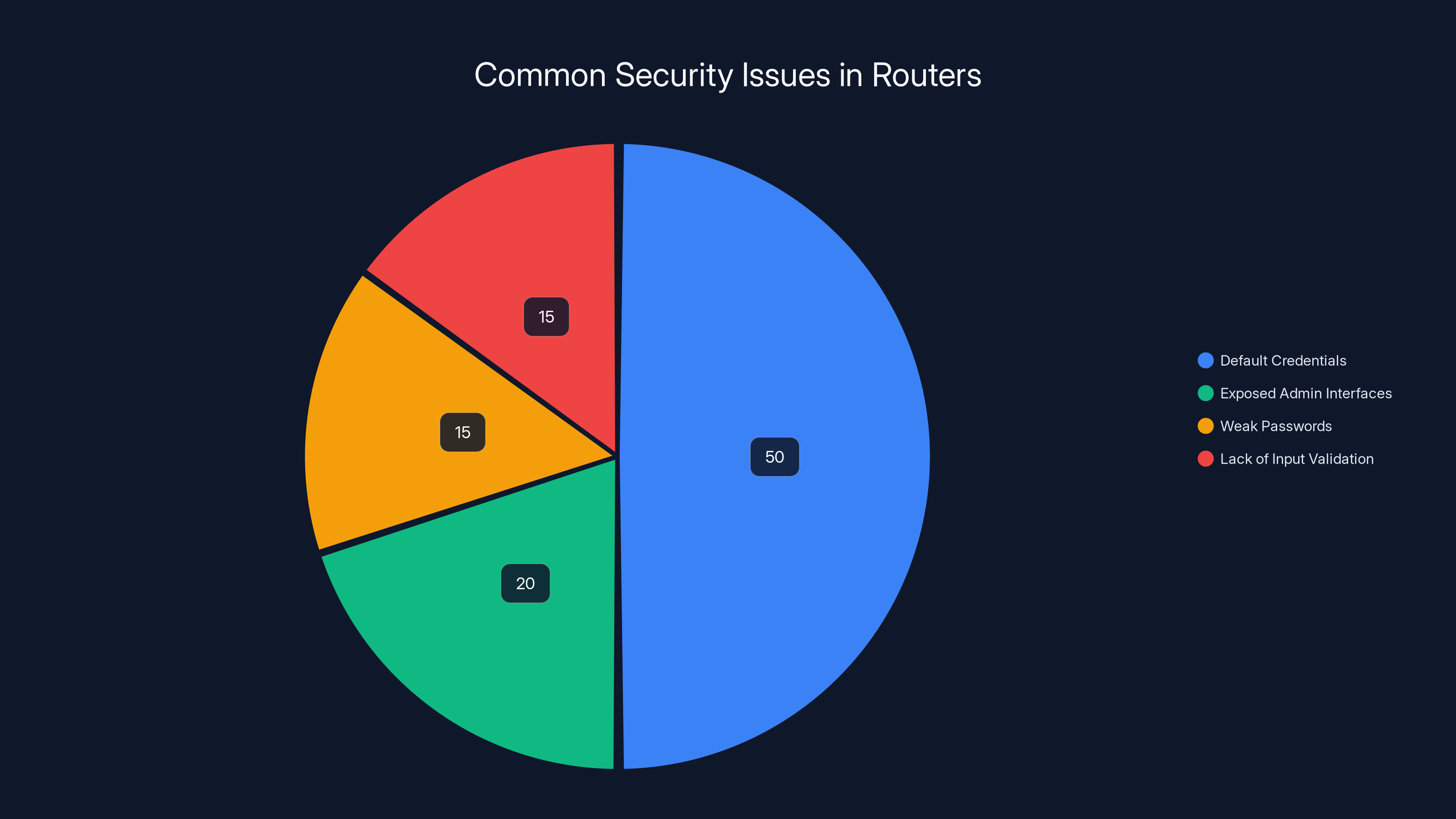
Estimated data shows that 50% of routers use default credentials, making them vulnerable to attacks. Other common issues include exposed admin interfaces and weak passwords.
What Exactly Is CVE-2026-0625?
Let's break down what we're dealing with. CVE-2026-0625 is a command injection vulnerability. That phrase might sound technical, but the concept is straightforward: an attacker tricks the router into executing commands it shouldn't.
The vulnerability exists in the router's DNS configuration endpoint. DNS (Domain Name System) is the internet's address book. It translates human-readable website names into IP addresses. Your router handles DNS requests constantly. Most users never interact with the DNS settings directly.
But the router's administrative interface allows DNS configuration. That's where the problem lives. The code that processes DNS changes doesn't properly validate what gets submitted. It accepts user input without checking whether that input contains malicious commands.
Here's how it works in practice: An attacker crafts a specially formatted request with embedded shell commands. Instead of just containing valid DNS data, the request includes characters or syntax that, when processed, execute additional instructions. The router interprets these instructions as legitimate commands and runs them with full administrative privileges.
The attack requires no authentication. You don't need a username or password. You don't need to be connected to the internal network. Anyone who can reach the router's IP address can attempt this attack. In many cases, routers are accessible from the internet itself if not properly configured.
Researchers traced the vulnerability back to improper sanitization of user-supplied DNS configuration parameters. Sanitization is the process of cleaning input data by removing or escaping potentially dangerous characters. The D-Link firmware simply wasn't doing this.
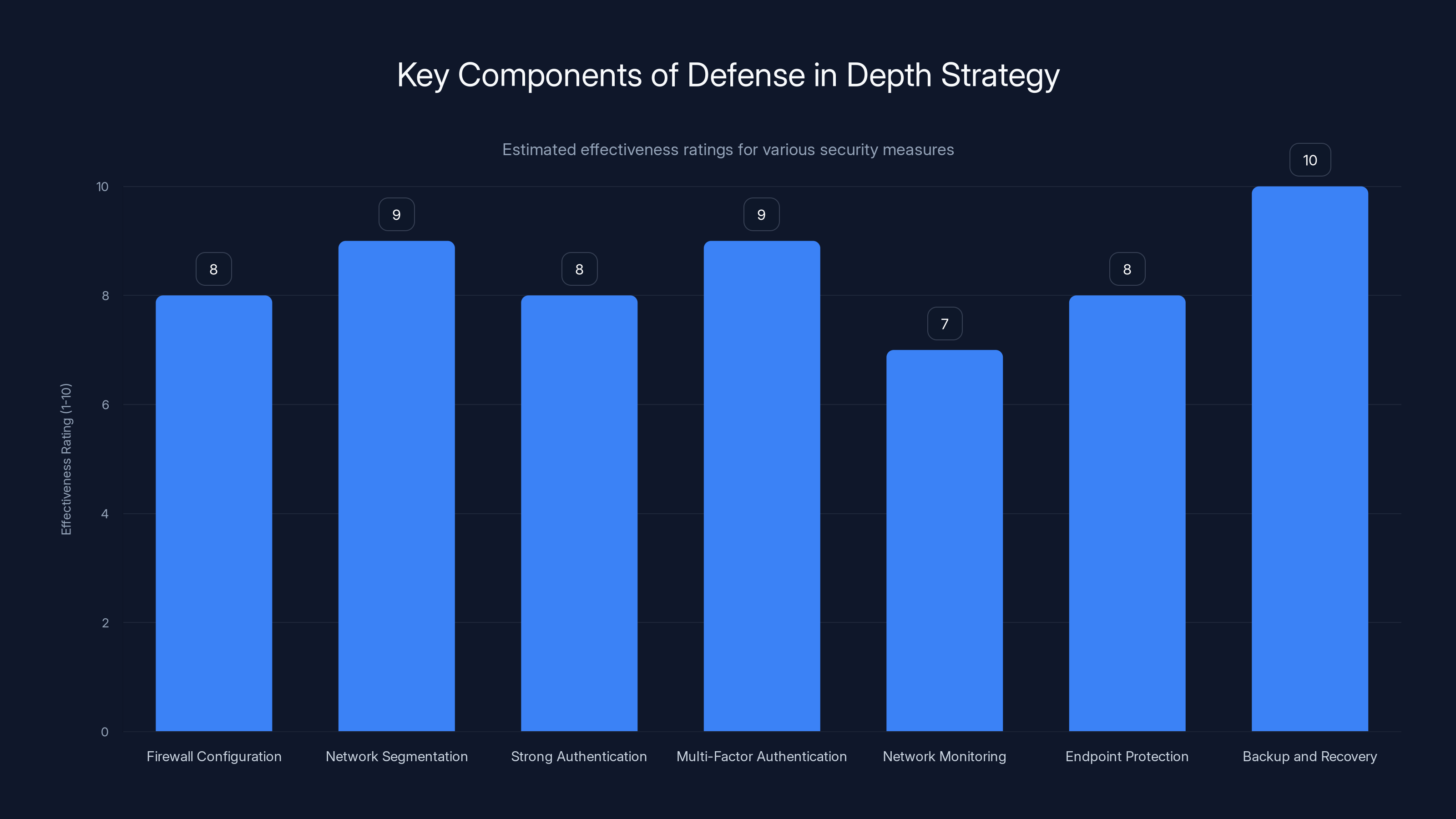
Network segmentation and multi-factor authentication are highly effective in a defense in depth strategy, with backup and recovery being crucial for data protection. Estimated data.
The Timeline: When Did Attacks Actually Begin?
Vulnerability disclosure follows a specific pattern. First, someone discovers the flaw. Then researchers analyze it. Eventually, it becomes public. But real-world attacks often start before any of that happens.
In this case, the Shadow Server Foundation detected actual exploitation attempts dating back to November 27, 2025. That's important. That means threat actors had found and weaponized this vulnerability weeks before public disclosure. That's weeks of undetected attacks against live networks.
We don't yet have a complete picture of how many routers were compromised during that window. D-Link stated they're still investigating the full scope of affected models. The company admitted that determining all impacted devices is difficult because "firmware is implemented across product generations." Translation: even D-Link doesn't have a complete inventory.
What we do know is that attacks were active and ongoing. That means somewhere right now, someone's router might be compromised. They have no idea.
This vulnerability appears to be linked to DNSChanger activity that D-Link has documented before. DNSChanger attacks redirect DNS requests to attacker-controlled servers. Instead of visiting the website you intended, your browser gets redirected to a fake site. Credentials get stolen. Malware gets installed. Ransomware gets deployed.
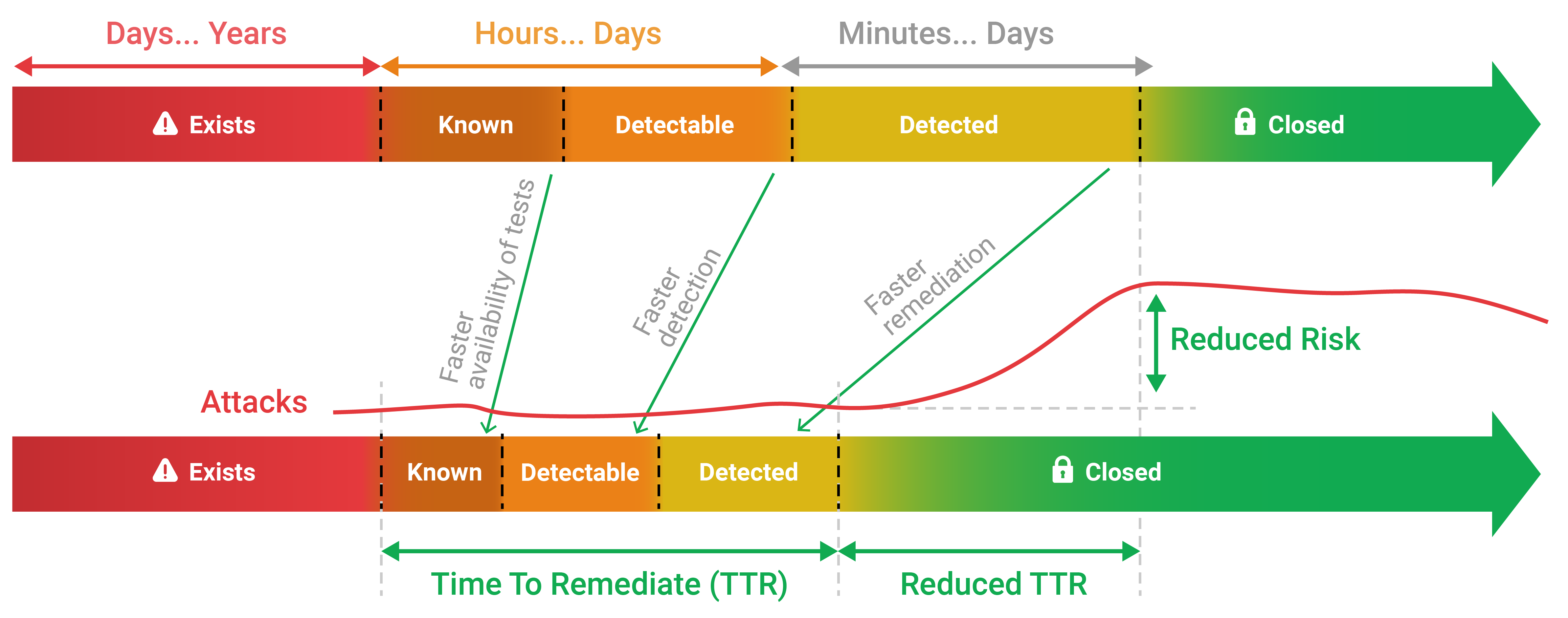
The Vulnerable D-Link Models: Which Devices Are at Risk?
D-Link has confirmed exploitation affecting these specific models:
- DSL-2740R (DSL ADSL2+/ADSL Modem Router)
- DSL-2640B (DSL Modem Router)
- DSL-2780B (DSL ADSL2+/ADSL Modem Router)
- DSL-526B (DSL Modem)
These firmware versions appear particularly vulnerable, with active attacks documented on 2016 through 2019 firmware variants. If your device has a firmware version from that period with no updates available, assume it's vulnerable.
But here's where it gets complicated. D-Link stated that determining all affected models beyond this initial list is difficult. The company said "current analysis shows no reliable model number detection method beyond direct firmware inspection." That's corporate language for: we're still figuring out the scope.
This means other D-Link DSL models might be vulnerable too. The company is actively validating firmware builds across legacy and supported platforms. A complete list of affected models should be released eventually, but for now, if you own an end-of-life D-Link DSL router, treat it as potentially compromised.
D-Link did not provide a patched firmware version for these models at the time of public disclosure. That's a significant point. There's no fix you can download. Patching isn't an option. Replacement is the only mitigation available for affected users.

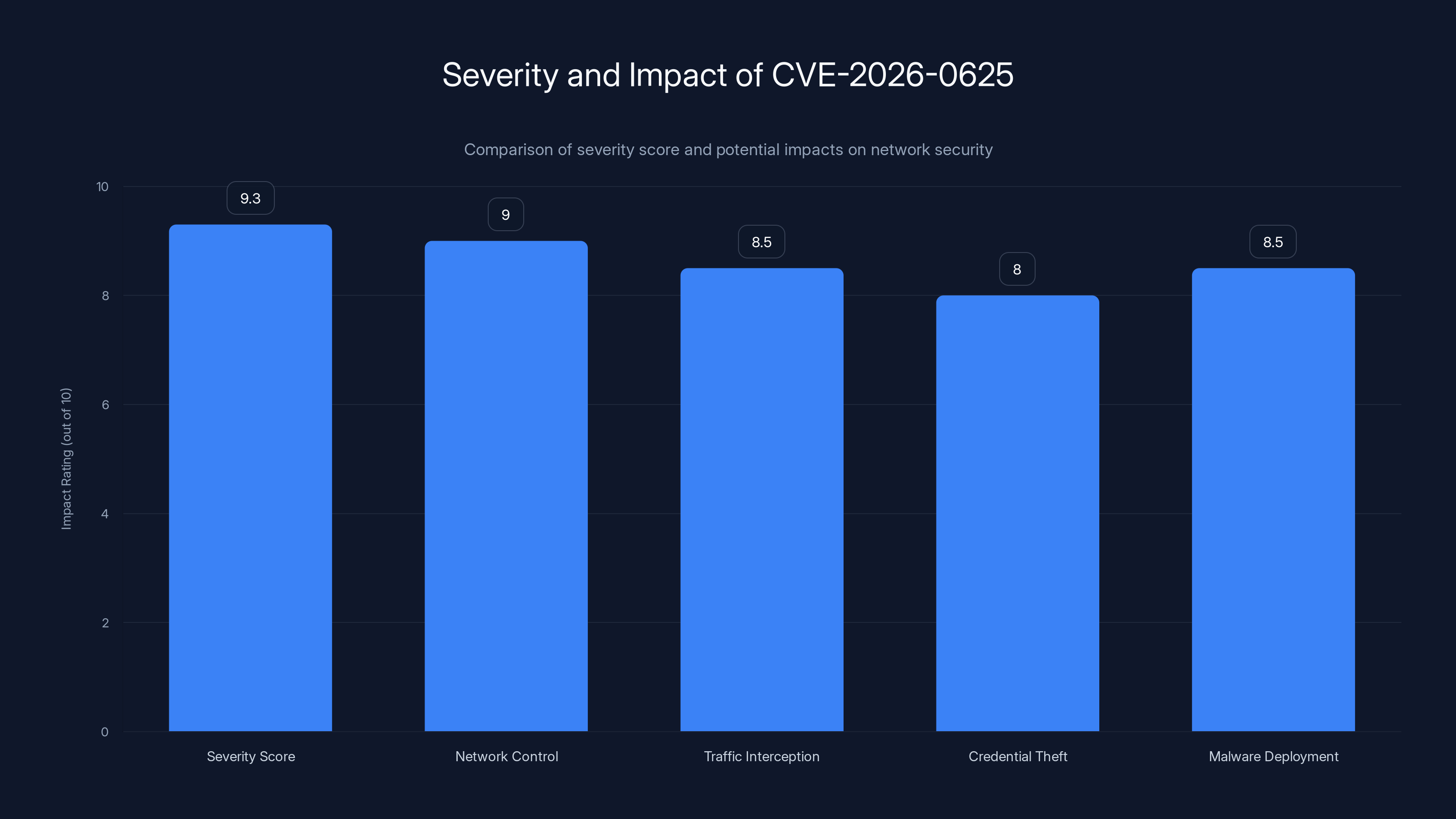
The CVE-2026-0625 vulnerability has a high severity score of 9.3, indicating significant risks such as network control and credential theft. Estimated data for impact ratings.
How Remote Code Execution Works: What Can Attackers Actually Do?
Remote code execution sounds scary in abstract terms. Let's make it concrete.
When an attacker achieves RCE on a router, they gain the ability to run any command the router's operating system supports. Think of it like having full administrator access to that device. They can:
Read sensitive data - Configuration files, stored credentials, historical logs, and cached information. Routers sometimes store usernames, passwords, and network configuration details in memory or storage.
Modify network behavior - Redirect traffic, intercept data, modify DNS responses, implement man-in-the-middle attacks. Every device on your network routes through this router. Compromising it means compromising everything connected to it.
Deploy malware - Install backdoors, rootkits, or persistent agents that survive reboots. These could continue operating indefinitely, collecting data and launching attacks.
Establish reverse shells - Create persistent connections that let attackers access the router remotely whenever they want, even if the vulnerability is eventually patched.
Participate in botnets - Use the router as a node in a distributed attack network. Your device could be participating in DDoS attacks, cryptocurrency mining, or spam distribution without your knowledge.
Pivot to internal networks - From the router, attackers scan for vulnerable systems on your internal network. They probe for unpatched servers, weak passwords, and exploitable services.
For small business routers, the impact scales dramatically. A compromised gateway router is a foothold into the entire network. Attackers can:
- Intercept all network traffic
- Steal customer data, financial records, and intellectual property
- Deploy ransomware to critical systems
- Establish persistent backdoors for ongoing access
- Spy on internal communications
- Compromise security systems and monitoring tools
The router's position makes it uniquely dangerous. It's not just another network device. It's the border device between your internal network and the internet. Control it, and you control the boundary.
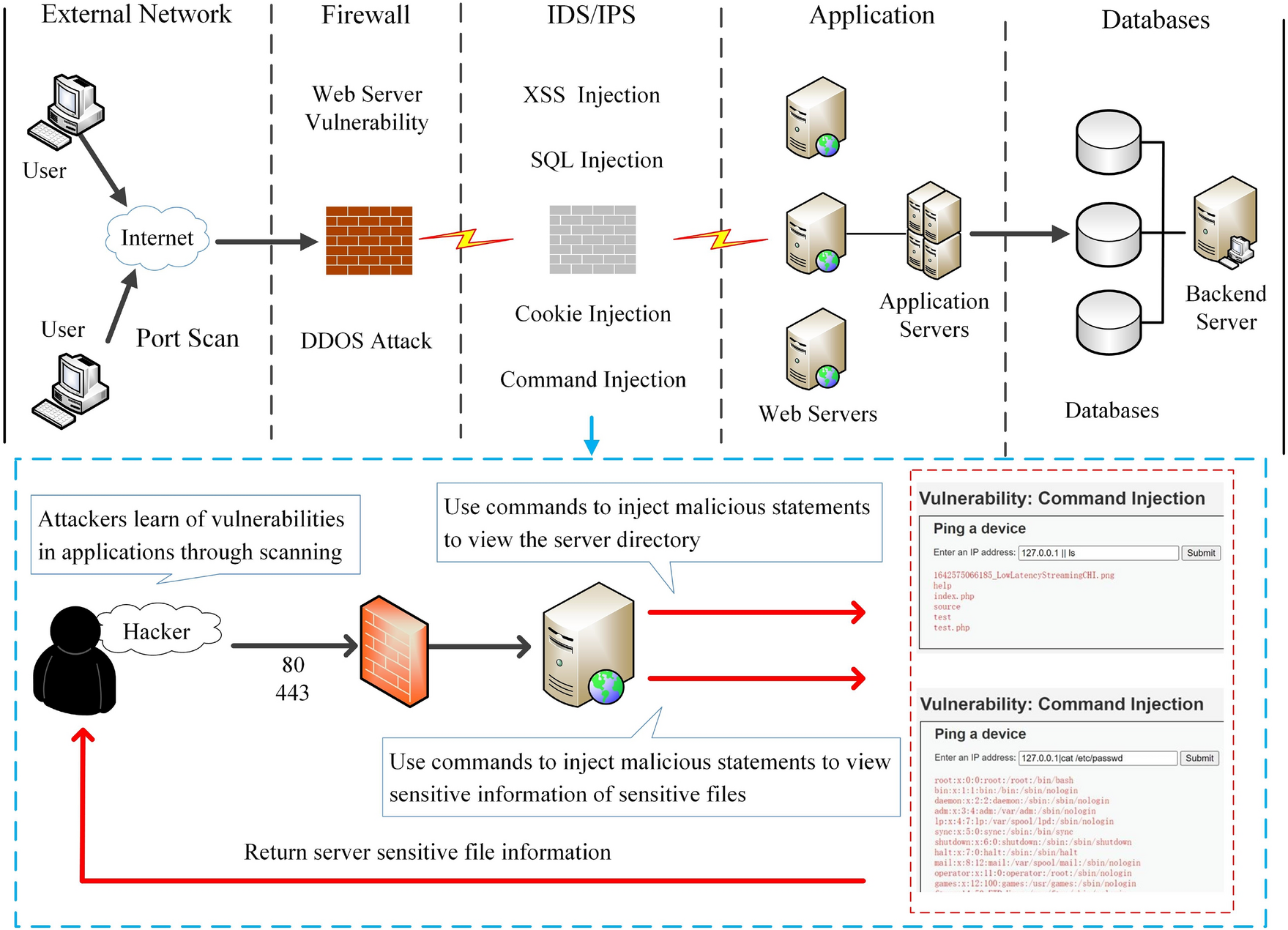
The Attack Vector: How Exploitation Actually Happens
We need to understand exactly how attackers exploit this vulnerability in practical terms.
The D-Link DSL routers in question expose a web-based administrative interface. This interface lets network administrators change settings like DNS servers, DHCP configuration, and other network parameters. The DNS configuration endpoint is the attack vector.
An attacker would craft an HTTP request targeting that endpoint. Instead of providing valid DNS server IP addresses, they would inject shell metacharacters and commands. The vulnerable code would accept this input without validation.
For example, instead of submitting:
DNS1=8.8.8.8&DNS2=8.8.4.4
An attacker might submit:
DNS1=8.8.8.8; cat%20/etc/passwd; DNS2=8.8.4.4
The semicolon acts as a command separator in shell environments. The vulnerable code doesn't sanitize this input, so the router attempts to execute:
bashset_dns 8.8.8.8; cat /etc/passwd;8.8.4.4
The legitimate DNS command executes, then the attacker's injected command (cat /etc/passwd) executes with router privileges, dumping system files that might contain credentials or configuration information.
More sophisticated attacks would use this initial foothold to deploy additional payloads. A practical exploitation sequence might look like:
- Reconnaissance - Scan the target network for D-Link routers
- Initial Access - Inject commands to create a backdoor user account
- Persistence - Install a rootkit or firmware modification that survives reboots
- Privilege Escalation - Ensure the attacker maintains full administrative access
- Internal Scanning - Use the router to scan the internal network for vulnerable systems
- Lateral Movement - Attack internal systems from the compromised router
- Data Exfiltration - Steal sensitive data through the router's connection
What makes this particularly insidious is that the attack is unauthenticated. Most administrative interfaces require login credentials. This vulnerability doesn't. If the router is accessible from the internet (which many are due to misconfiguration), anyone can attempt exploitation.
Even if the router isn't directly accessible from the internet, an attacker on the internal network could exploit it. Or an attacker could combine this with social engineering to trick someone into clicking a malicious link that targets the router's DNS endpoint.
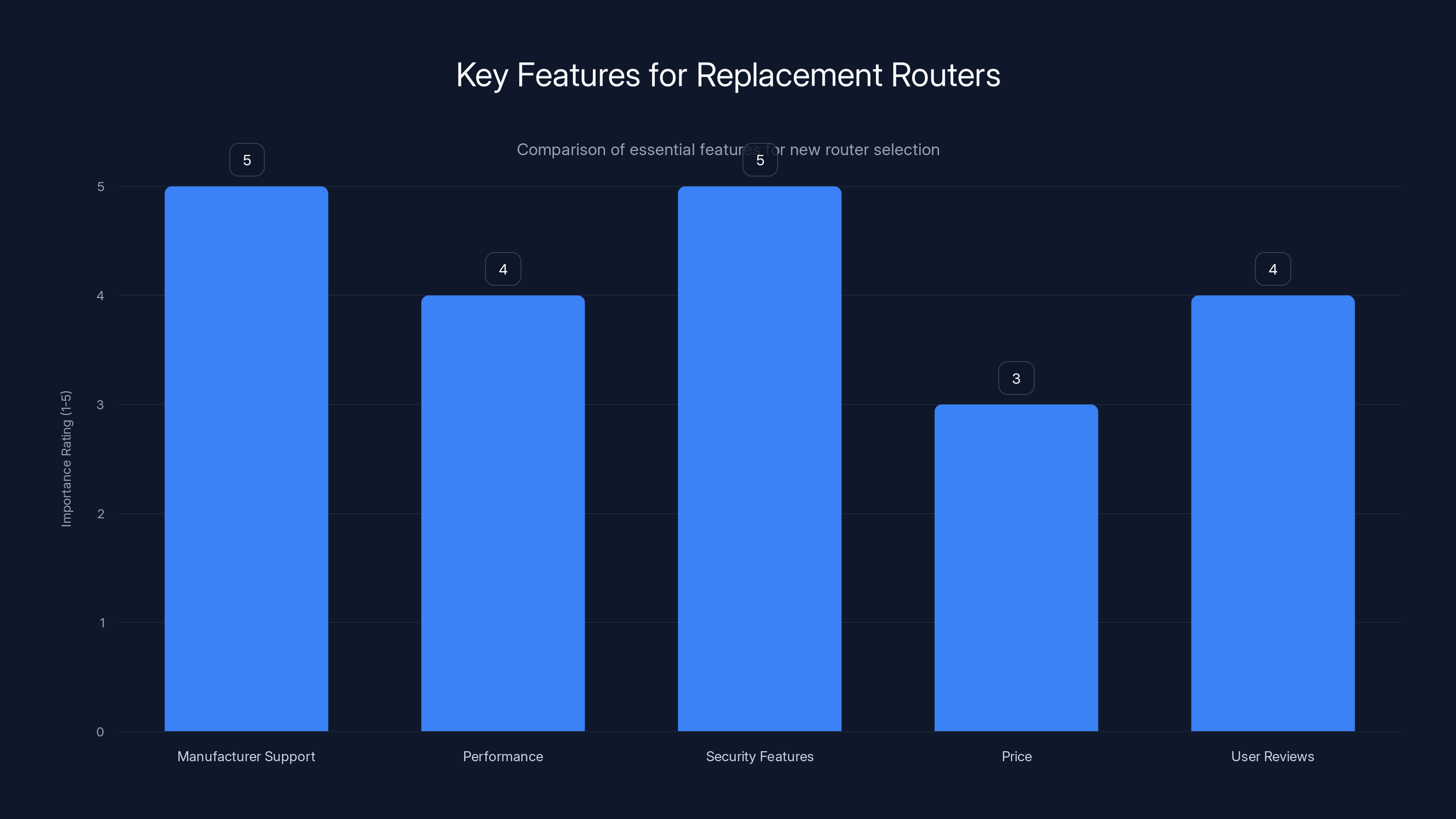
Security features and manufacturer support are the most critical factors when selecting a replacement router, followed by performance and user reviews. Estimated data based on typical consumer priorities.
Real-World Impact: What Happens to Compromised Networks?
Let's move from technical theory to business reality. What actually happens when a router gets compromised through this vulnerability?
For a small business with 20-50 employees:
An attacker gains control of the network gateway. Within hours, they establish persistent access mechanisms. They begin scanning internal systems for unpatched servers, weak passwords, and exploitable services. They identify and compromise a file server containing customer records and financial data. They install ransomware on critical workstations. The business wakes up to encrypted files and a ransom demand.
But that's just the visible damage. In the background, the attacker has exfiltrated months of emails, customer data, and proprietary information. Even after paying the ransom or recovering from backups, the data breach remains undetected for weeks or months. Customer notification requirements, regulatory fines, legal liability, and reputational damage follow.
A single compromised router becomes an existential threat to small businesses that depend on reliable operations and customer trust.
For a residential user:
A compromised router could be redirecting DNS queries to attacker-controlled servers. When the user visits their bank's website, they're actually visiting a fake site that looks identical but runs by the attacker. Credentials are captured. The account is drained. The user has no idea the attack originated from their router, not from a phishing email or malware on their computer.
The router might also participate in botnet activities. Thousands of routers become part of a distributed attack infrastructure. That bandwidth is used for DDoS attacks against websites or organizations. Law enforcement traces the attack back to your IP address. Now you're dealing with investigations and potential liability.
For critical infrastructure:
D-Link routers are used in various industrial and critical infrastructure settings. A compromised router in a hospital might disrupt patient care systems. A compromised router at a utility could affect service delivery. The attack surface expands dramatically.
The common thread across all scenarios: the router is trusted infrastructure. Nobody expects it to be the attack vector. It sits in a corner, does its job, stays off everyone's radar. That invisibility is exactly what makes it so valuable to attackers.
Why These Devices Remain Vulnerable: The End-of-Life Problem
Understanding why this vulnerability persists in 2025 requires looking at how we treat network hardware.
Most people buy a router and use it until it stops working. It doesn't require active management like a computer or phone. It doesn't prompt for updates constantly. It just sits there, doing the same job year after year. From a user perspective, a functional router from 2016 is indistinguishable from a current one.
But software doesn't age well. Security threats evolve. New attack techniques emerge. A router that was perfectly secure in 2016 is ancient by 2025 standards. The underlying operating system might have design flaws. The code might contain buffer overflows, injection vulnerabilities, or logic errors that nobody knew about when the device shipped.
D-Link stopped supporting these models years ago. No security updates arrive. No firmware patches fix emerging vulnerabilities. The company moved on to newer product lines. The routers continue operating in the field, undefended against threats that didn't exist when they were manufactured.
This creates what cybersecurity professionals call a "legacy vulnerability problem." Thousands or millions of devices remain in use past their intended lifecycle. Each represents a potential attack vector. Collectively, they form a persistent threat landscape.
The vulnerability discovery process compounds this issue. When researchers find flaws in old hardware:
- Vendors must decide whether to allocate resources to legacy products
- Supporting end-of-life hardware is expensive and low-priority
- No revenue incentive exists to patch old devices
- Many vendors simply don't
D-Link's response reflected this reality. The company acknowledged the vulnerability in legacy products but didn't release patches. The only mitigation recommended was replacement.
This leaves users with an unappealing choice: continue using unsupported hardware and accept the risk, or spend money replacing devices that still function. Most choose the former.

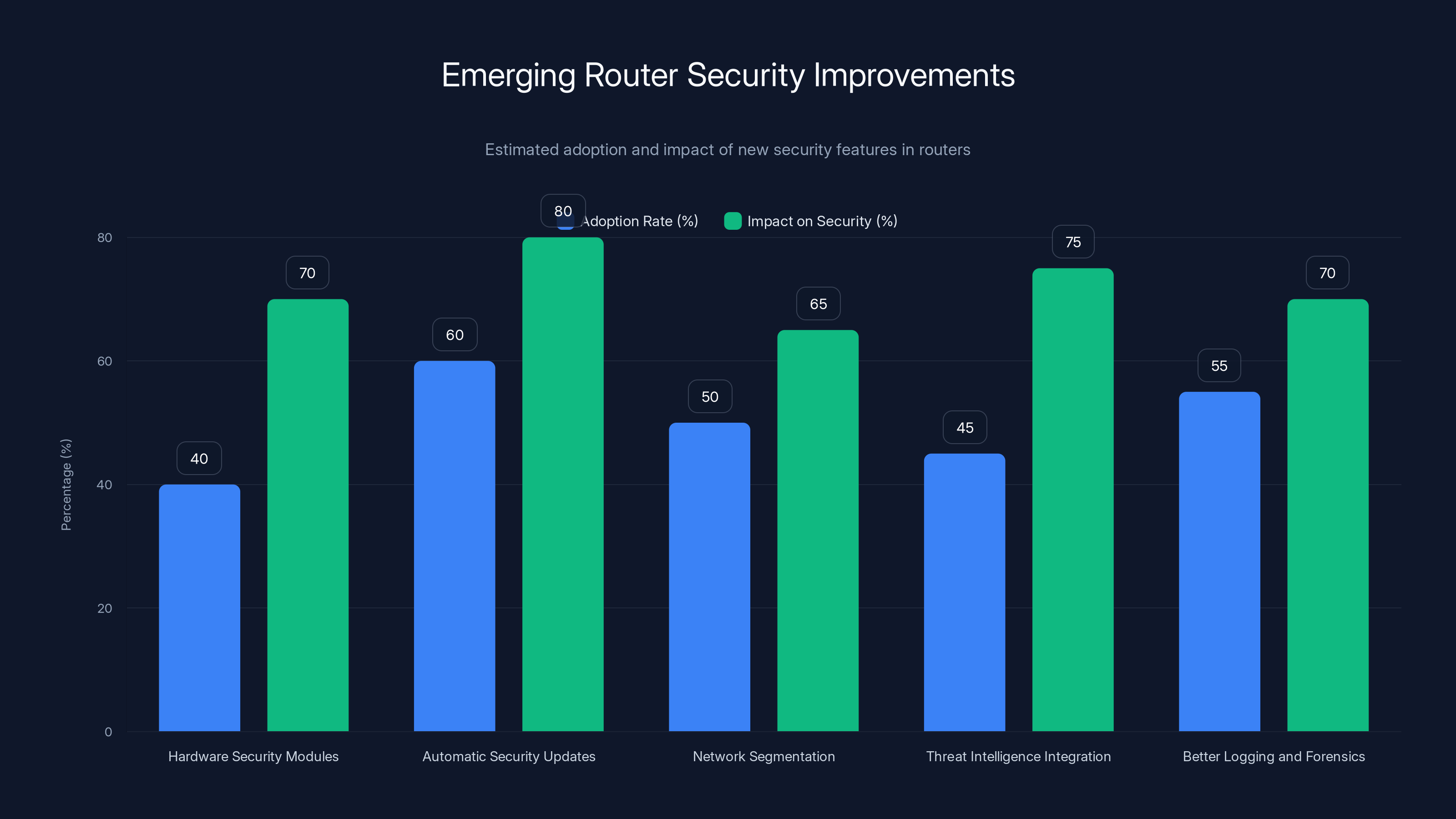
Estimated data shows that automatic security updates have the highest adoption and impact on router security, while hardware security modules, although less adopted, significantly enhance security. Estimated data.
The Broader Context: Why Routers Remain Weak Links
The D-Link vulnerability isn't an isolated incident. It's part of a broader pattern affecting router security across the industry.
Routers are constrained devices. They have limited processing power, limited memory, and limited storage. Every development decision involves trade-offs. Adding robust input validation costs processing cycles and memory. Implementing secure coding practices requires skilled engineers. Maintaining long-term security requires ongoing investment.
Many vendors optimize for cost and speed-to-market rather than security. The router industry is competitive and margin-thin. Security improvements that consumers don't see and don't demand often get deprioritized.
Routers also operate in what's called the "security perimeter blind spot." Users invest in firewalls to protect their networks. They invest in endpoint protection to secure their computers. But the router itself? It's often treated as trusted infrastructure that doesn't require protection.
This assumption is dangerous. The router is the most powerful device on many networks. It has the broadest system access. It can see all traffic. A compromised router is more valuable to attackers than a compromised endpoint.
Furthermore, routers are frequently poorly configured by default. Many ship with default credentials. Many expose administration interfaces to the internet. Many don't require strong passwords. These are preventable mistakes, but they persist across the industry.
The D-Link situation reflects these systemic issues. The company produced devices that were vulnerable to a fundamental attack type (command injection). They didn't adequately validate input. They didn't patch the vulnerability when it was discovered. And now, thousands of networks remain exposed.

Detecting Compromise: How to Tell If Your Router Is Already Infected
By the time this article is published, some D-Link routers are already compromised. Their owners have no idea.
Detecting router compromise is difficult because routers are invisible to most users. The device sits between the user and the internet. It processes all traffic but shows no obvious symptoms of compromise unless the attacker wants it to.
However, there are signs worth investigating:
DNS behavior changes - If websites suddenly redirect unexpectedly, or if you end up on strange sites when typing URLs, DNS hijacking might be occurring. Your router might be redirecting legitimate domain lookups to attacker-controlled servers.
Unexpected DNS servers - Access your router's administrative interface and check the DNS configuration. If the DNS servers don't match what you configured, or if you see unfamiliar IP addresses listed, someone modified your settings.
Unusual traffic patterns - If your internet connection seems slower than normal, or if bandwidth usage spikes without explanation, your router might be involved in botnet activity or data exfiltration.
Administrative changes - Check the router's login history if available. Look for access from IP addresses you don't recognize. If the router has logged administrative changes you didn't make, someone accessed it.
Firmware version inconsistencies - If your router suddenly has a different firmware version than you remember, or if the version number is unusual, the device might have been modified.
Network device anomalies - Use a network scanning tool to see what devices are connected to your router. Unknown devices or unexplained connections might indicate an attacker established a persistent presence.
The problem is that sophisticated attackers cover their tracks. They modify logs to hide their activity. They disable administrative notifications. The absence of evidence isn't evidence of absence.
For end-of-life devices like the vulnerable D-Link models, the most practical approach is assuming compromise. Even if no active compromise is detected, the device is vulnerable to exploitation at any moment. Rather than spend time and resources investigating, replace the device.
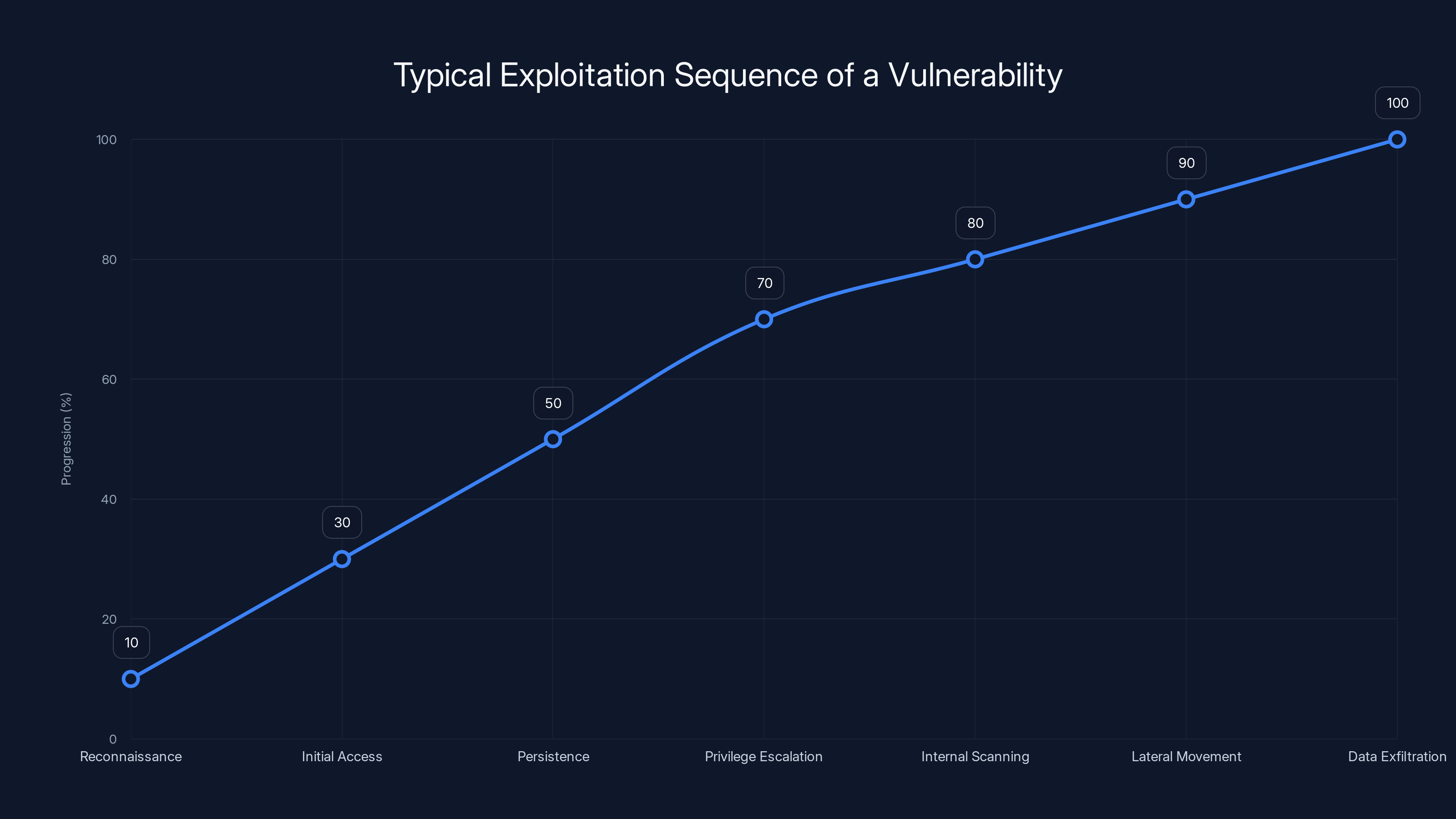
This line chart illustrates the typical progression of an exploitation sequence, from initial reconnaissance to data exfiltration. Estimated data shows how each stage builds upon the previous.
Step-by-Step: Replacing Your Vulnerable D-Link Router
If you own one of the affected D-Link models, here's how to approach replacement responsibly.
Step 1: Document Current Configuration
Before you remove the old router, write down or screenshot the following:
- Current Wi Fi SSID and password
- DNS servers configured
- Port forwarding rules if any
- Static IP configurations
- Any custom settings specific to your setup
This information helps you configure the replacement device identically, minimizing disruption.
Step 2: Identify Suitable Replacement Hardware
The replacement router should have:
- Current manufacturer support and regular security updates
- Adequate performance for your network size and usage
- Modern security features (WPA3 Wi Fi encryption, firewall capabilities)
- Reasonable price point
- Positive reviews regarding security updates and vendor responsiveness
Step 3: Prepare the New Router
Unbox and inspect the replacement device. Check the firmware version. If a newer version is available from the manufacturer's website, download it before connecting the router to your network.
Step 4: Disable the Old Router
Power down the D-Link router but don't discard it yet. Keep it available for several days while you verify the new router operates correctly.
Step 5: Install and Configure the New Router
Connect the new router following the manufacturer's instructions. Apply the configuration settings you documented from the old device. Test all critical functions.
Step 6: Update Firmware Immediately
Once the new router is operational and connected to the internet, check for firmware updates immediately. Install any available updates before using the router for sensitive operations.
Step 7: Secure the New Router
- Change default administrator credentials to a strong, unique password
- Enable WPA3 Wi Fi encryption (or WPA2 if WPA3 isn't available)
- Disable remote administration access
- Enable the firewall
- Disable UPn P unless you have a specific need for it
- Consider enabling automatic firmware updates if available
Step 8: Verify Proper Operation
After configuration, verify:
- Wi Fi connectivity works for all devices
- Internet access functions normally
- Port forwarding (if needed) operates correctly
- No unexpected devices appear on the network
Step 9: Safely Dispose of the Old Router
Once you've confirmed the new router works reliably for at least a week, safely dispose of the old device. Consider:
- Donating it to an electronics recycling facility
- Checking if the manufacturer accepts old devices for proper disposal
- Never throwing networking equipment in regular trash, as it contains hazardous materials
Step 10: Monitor and Maintain
Set a calendar reminder to check for firmware updates on your new router monthly. Subscribe to the manufacturer's security notifications. Stay informed about vulnerabilities affecting your device.

Broader Protection Strategies: Defense in Depth
Replacing the router is the primary mitigation, but it's part of a larger security picture.
Firewall Configuration
Even with a new router, restrict what comes in from the internet. Configure the firewall to:
- Block inbound access to internal resources
- Allow only necessary outbound traffic
- Monitor for suspicious connection patterns
- Log attempted intrusions
For businesses, consider hardware firewalls separate from the router itself.
Network Segmentation
Divide your network into zones based on security requirements. Critical systems (financial records, healthcare data, intellectual property) should be on isolated networks with additional access controls. This limits the impact if a compromise occurs.
Strong Authentication
Implement strong passwords everywhere:
- Router admin accounts (minimum 16 characters, complexity)
- Wi Fi access (strong WPA3 passphrase)
- Administrative systems (no default credentials ever)
Password managers help manage complexity without forcing users to remember weak passwords.
Multi-Factor Authentication
For any administrative or remote access, require MFA. This adds a second verification factor, making compromised credentials significantly less useful to attackers.
Network Monitoring
Deploy tools that monitor network traffic for anomalies:
- Unexpected DNS changes
- Unusual outbound connections
- Traffic spikes to unfamiliar destinations
- Failed authentication attempts
Even if compromise occurs, monitoring provides early detection.
Endpoint Protection
Despite router-level protections, endpoints (computers, phones, servers) should have independent security:
- Antivirus/antimalware software
- Host-based firewalls
- EDR (Endpoint Detection and Response) tools for critical systems
Endpoint protection catches what perimeter defenses miss.
Backup and Recovery
Maintain offline backups of critical data. If ransomware executes despite other protections, you can recover without paying attackers. Backups should be:
- Automated and frequent
- Stored offline (not accessible to attackers)
- Regularly tested for successful recovery
- Geographically distributed
Incident Response Plan
Develop a documented plan for responding to security incidents:
- Who gets notified and when
- Escalation procedures
- Evidence preservation steps
- Communication with affected parties
- Recovery procedures
Having a plan in place means faster response when something goes wrong.

Industry Response and Vendor Accountability
The D-Link situation raises important questions about vendor responsibility for legacy devices.
Current Industry Practice:
Most vendors follow a lifecycle model:
- Active Support: 2-3 years of security updates and patches
- Extended Support: Optional paid support extending lifecycle
- End-of-Life: No further updates or support
Once a device reaches EOL, vendors allocate no resources to it. Vulnerabilities discovered afterward go unpatched. Users must replace hardware to receive security updates.
This model makes business sense for vendors. Continuing to support old hardware incurs costs that don't generate revenue. The economic incentive to move customers to newer products is strong.
But it creates security problems. End-of-life devices accumulate in networks for years after support ends. They become undefended against threats discovered long after manufacture. When vulnerabilities affect hundreds of thousands of legacy devices, the aggregate impact becomes significant.
Proposed Solutions:
Security researchers and policy advocates have suggested alternatives:
-
Extended Support Requirements - Regulations could mandate minimum support periods (e.g., 7-10 years) for network infrastructure devices.
-
Responsible Disclosure Timelines - Vendors could be required to provide critical patches for legacy devices even after EOL, with reasonable timeframes for remediation.
-
Security-by-Design Standards - Certification standards could require routers to implement secure coding practices, input validation, and other fundamental protections.
-
Customer Notification - Clear communication to customers about EOL status and security implications, rather than silent abandonment.
-
Standardized Firmware Updates - Building modularity into router designs so security updates are easier to deploy across hardware variations.
Whether industry adopts these approaches remains to be seen. Regulatory pressure continues increasing, particularly in regions emphasizing critical infrastructure protection.
D-Link's Specific Response:
Regarding this vulnerability, D-Link stated it's investigating the scope of affected models and validating firmware builds. The company hasn't released patches for vulnerable devices but acknowledged the security risk.
D-Link also committed to improving vulnerability disclosure processes and coordination with security researchers going forward. Whether these commitments translate to meaningful changes in how the company supports legacy hardware will become clear in coming months.
The Bigger Picture: Why Router Security Matters More Than Most People Realize
Routers represent a unique security challenge in the networking ecosystem.
Most people focus security efforts on endpoints: computers, phones, servers. These devices are visible. They run applications. Users interact with them directly. Their security feels obvious and important.
Routers lack this visibility. They're infrastructure. They work in the background. From a user's perspective, a secure router is one that doesn't cause problems. That invisibility creates a dangerous blind spot.
But routers occupy the most strategic position in any network:
Network Border Control - All traffic passes through the router. It's the boundary between your network and the internet. Compromise at this level means compromise of everything beyond it.
Trust Anchor - Most network security assumes the router is trustworthy. Firewalls, VPNs, and security policies all depend on the router functioning honestly. If that assumption breaks, everything built on it breaks too.
Persistent Access - A compromised router remains accessible indefinitely. Unlike endpoint malware that might be detected and cleaned, router compromise can persist through multiple system rebuilds.
Stealth Operations - Sophisticated attackers use compromised routers for persistent access while keeping their activities invisible to endpoint monitoring tools.
The D-Link vulnerability illustrates these principles perfectly. A simple flaw in input validation on a network device becomes a gateway to entire networks. The attack vector isn't sophisticated. The flaw isn't rare. It's a fundamental security practice (input validation) that's been well-understood for decades.
Yet the vulnerability persisted undetected and unpatched. It got exploited in the wild. It affected thousands of networks. This happens because routers aren't treated with the same security rigor as other critical infrastructure.
Changing this requires treating routers as the critical security devices they actually are:
- Organizations should maintain router inventories with firmware version tracking
- Security teams should monitor for router-specific vulnerability disclosures
- Firmware updates should be applied with the same urgency as OS patches
- Router configurations should be documented and audited regularly
- Network monitoring should specifically look for router compromise indicators
For vendors, it requires longer support lifecycles, more rigorous security testing, and commitment to patching vulnerabilities even in legacy products. It requires treating security as a core responsibility, not an afterthought.

What Happens Next: Future Vulnerabilities and Improved Defenses
CVE-2026-0625 won't be the last router vulnerability. It won't even be the last critical one this year.
Security researchers continue finding flaws in routers. The attack surface keeps expanding as routers gain more features (threat detection, content filtering, advanced analytics). Each new feature introduces potential vulnerabilities.
What changes is our ability to detect and respond to these threats. Better monitoring tools emerge. More sophisticated intrusion detection happens. Vendors improve their security processes.
Emerging Router Security Improvements:
-
Hardware Security Modules - TPM (Trusted Platform Module) chips in routers authenticate firmware and detect unauthorized modifications.
-
Automatic Security Updates - More routers now support automatic, transparent firmware updates that don't disrupt connectivity.
-
Network Segmentation Features - Consumer and SMB routers are adding more granular control over network policies and traffic routing.
-
Threat Intelligence Integration - Routers increasingly leverage threat feeds to detect and block known malicious destinations.
-
Better Logging and Forensics - Improved logging capabilities help identify compromise and reconstruct attack timelines.
These improvements help, but they're not magic. The fundamental requirement remains unchanged: users and organizations must actively manage their network security. They must replace old hardware. They must apply updates. They must configure devices securely.
The good news: doing these things is straightforward. It doesn't require technical expertise. The bad news: most people and organizations don't do them consistently.

Immediate Action Items: What You Should Do Today
If you read nothing else in this article, read this section.
If you own an affected D-Link model (DSL-2740R, DSL-2640B, DSL-2780B, DSL-526B):
- Power down the router immediately
- Order a replacement from a reputable vendor with good security track record
- Don't wait for it to be actively exploited
- Assume it's already compromised
- Replace it before using for sensitive activities
If you own any D-Link DSL router from 2019 or earlier:
- Check the exact model number (usually on the back or bottom)
- Visit D-Link's website to check support status
- If EOL, replace it
- If still supported, check for and install any available firmware updates
- Change the default Wi Fi password immediately
- Change the admin panel password to something strong and unique
For all other routers:
- Check your router's current firmware version
- Visit the manufacturer's website to see if newer versions are available
- If yes, download and install updates
- Enable automatic updates if available
- Change default credentials
- Document your current configuration
- Add firmware update checks to your calendar (quarterly minimum)
For small businesses and organizations:
- Inventory all networking hardware including routers
- Determine the age and support status of each device
- Develop a replacement schedule for devices approaching or past EOL
- Establish a firmware update process
- Monitor security advisories for hardware you operate
- Implement network monitoring to detect router compromise
- Segment your network so a router compromise doesn't compromise entire infrastructure
For everyone:
- Remember that routers are critical security devices, not just internet connectivity tools
- Treat them with appropriate attention
- Don't assume old hardware is safe just because it still works
- Replace hardware before it fails
- Stay informed about vulnerabilities affecting devices you use

FAQ
What is CVE-2026-0625 exactly?
CVE-2026-0625 is a command injection vulnerability found in D-Link DSL gateway routers. It allows unauthenticated attackers to execute arbitrary commands on affected devices by injecting shell metacharacters into the DNS configuration endpoint. The vulnerability scores 9.3 out of 10 in severity and has been actively exploited since November 2025.
Which D-Link routers are affected by this vulnerability?
The confirmed affected models are DSL-2740R, DSL-2640B, DSL-2780B, and DSL-526B, with firmware versions from 2016 through 2019. However, D-Link stated that other legacy DSL models might be vulnerable as well. The company is currently investigating the full scope of affected devices. If you own a D-Link DSL router from 2019 or earlier that no longer receives support, assume it's potentially vulnerable.
How do attackers actually exploit this vulnerability?
Attackers craft specially formatted HTTP requests targeting the router's DNS configuration endpoint. Instead of submitting valid DNS server addresses, they include shell commands using metacharacters like semicolons that cause the vulnerable firmware to execute arbitrary instructions. No authentication is required, so anyone who can reach the router's IP address can attempt exploitation. The attack happens over the network and requires no physical access.
What damage can occur if my router is compromised?
A compromised gateway router provides attackers with complete control over your network's internet connection. They can intercept and redirect traffic, steal credentials, deploy malware, establish backdoors, spy on communications, redirect DNS queries, participate in botnets, and access internal systems. For businesses, this means potential data breaches, ransomware deployment, and complete network compromise. For individuals, it means credential theft, identity fraud, and participation in illegal activities without their knowledge.
Should I try to patch my vulnerable router or should I replace it?
You should replace it. D-Link hasn't released patches for affected models because they're end-of-life products. The company's official guidance is that users should replace unsupported devices. Attempting to patch the device yourself or hoping for a future patch isn't a reliable security strategy. Replacement ensures you have a device with active vendor support and regular security updates.
How do I know if my router is already compromised?
Compromised routers are often invisible to their owners. However, watch for these signs: unexpected DNS redirects, strange DNS configurations in the router settings, unusual bandwidth usage, login activity from unfamiliar IP addresses, and unexplained changes to administrative settings. If you suspect compromise, assume the router is affected and replace it immediately. Don't attempt to clean it or investigate extensively, as sophisticated attackers hide their tracks.
What's the difference between a vulnerable router and a compromised router?
A vulnerable router has a security flaw that could be exploited, but hasn't been exploited yet. A compromised router has actually been attacked and now contains malicious code or configurations controlled by an attacker. All affected D-Link models are vulnerable, but not all are necessarily compromised. However, if your router is vulnerable and publicly accessible, assume it's likely already been compromised by someone.
Can I just keep using my old D-Link router if I'm careful with my password?
No. A strong password on the admin panel doesn't protect against this vulnerability because CVE-2026-0625 requires no authentication. Attackers don't need to log in to exploit it. They can target the vulnerability directly regardless of password strength. The only effective mitigation is hardware replacement.
What should I look for in a replacement router?
Prioritize modern routers from vendors with a track record of regular security updates and long-term support (at least 5-7 years). Check that the device supports WPA3 Wi Fi encryption, has a hardware firewall, and includes features like automatic firmware updates. Read reviews specifically about the vendor's security update history, not just performance. Avoid extremely cheap routers from vendors with poor security reputations.
How often should I update my new router's firmware?
Check for firmware updates at least monthly. Many modern routers support automatic updates that install securely without disrupting your internet connection. Enable this feature if available. Subscribe to security notifications from your router's manufacturer so you're immediately aware of critical updates. Don't wait for problems to appear before checking for updates.

Key Takeaways
The D-Link DSL gateway vulnerability represents a critical but solvable security problem. The vulnerability itself—command injection through unsanitized input—is a fundamental security flaw that should never reach production. Its presence in widely deployed hardware that reached end-of-life years ago creates the perfect condition for widespread exploitation.
But the solution is straightforward: replace affected devices with modern hardware and establish practices that treat routers as the critical security infrastructure they actually are.
Router security often gets overlooked because routers are invisible. They work so well that we forget they're there. But that invisibility masks their strategic importance. Compromise at the router level means compromise of everything beyond it.
If you own an affected D-Link model, act immediately. Don't wait. Don't assume your specific device isn't targeted. The active exploitation window is open. The longer your vulnerable device remains online, the higher the risk.
For everyone else, this situation should be a reminder: old hardware isn't safe hardware just because it still works. Security isn't a one-time purchase. It's an ongoing practice. Apply updates. Monitor advisories. Replace devices appropriately. These practices cost far less than dealing with the aftermath of a network compromise.
The routers we rely on deserve the same attention we give to other critical infrastructure. CVE-2026-0625 proves what happens when they don't get it.

Related Articles
- Scattered Lapsus$ Hunters Caught in Honeypot: Inside the Bust [2025]
- NordVPN in 2025: Post-Quantum Encryption, Scam Protection, and What's Next [2026]
- Should You Use a VPN Browser? Complete Guide [2025]
- Essential Cybersecurity Habits for 2026: Expert Guide [2025]
- Most Dangerous People on the Internet [2025]
- Prompt Injection Attacks: Enterprise Defense Guide [2025]
![D-Link DSL Gateway CVE-2026-0625 Critical Flaw: RCE Risk [2025]](https://tryrunable.com/blog/d-link-dsl-gateway-cve-2026-0625-critical-flaw-rce-risk-2025/image-1-1767800418228.jpg)



