Device Protection Beyond Hardware: Securing Your Digital Identity [2025]
Your phone isn't just a device anymore. It's your wallet, your identity, your memories, and your connection to the world. But traditional device protection? It's stuck in 2015, obsessed with cracked screens while your most valuable assets sit completely exposed.
Here's the problem: In London alone, a phone is stolen every six minutes. Last year, 1.4 million devices vanished in the US. But here's what actually keeps security experts up at night—the criminals don't care about the hardware. They're after what's inside.
One London victim learned this the hard way. Criminals stole his phone on the Underground, and within hours, they'd drained over £21,000 from his accounts, including taking out a £7,000 loan in his name. The physical device? Worth maybe £800. The damage? Life-altering.
Yet 72% of Brits don't even carry device insurance, convinced that breaches and scams happen to "other people." That optimism is a luxury we literally cannot afford anymore. The gap between the threats we actually face and the protection we've actually got is widening every single day, and it's time we talked about why device protection has completely failed to evolve.
TL; DR
- The Real Threat Isn't Hardware: Modern device theft targets digital assets—banking apps, crypto wallets, identity documents—not the physical handset itself
- Protection Hasn't Evolved: Traditional device insurance covers cracked screens and water damage, but ignores the digital threats that cause catastrophic financial and identity damage
- The Coverage Gap Is Massive: 43% of UK consumers find insurance policies confusing, and 59% can't find appropriate coverage for digital risks
- AI Changes Everything: Next-generation protection uses AI to flag malicious behavior before fraud occurs, lock stolen devices automatically, and provide instant recovery
- Integration Is Essential: 94% of British consumers want bundled protection integrated into services they already use, not fragmented across multiple providers
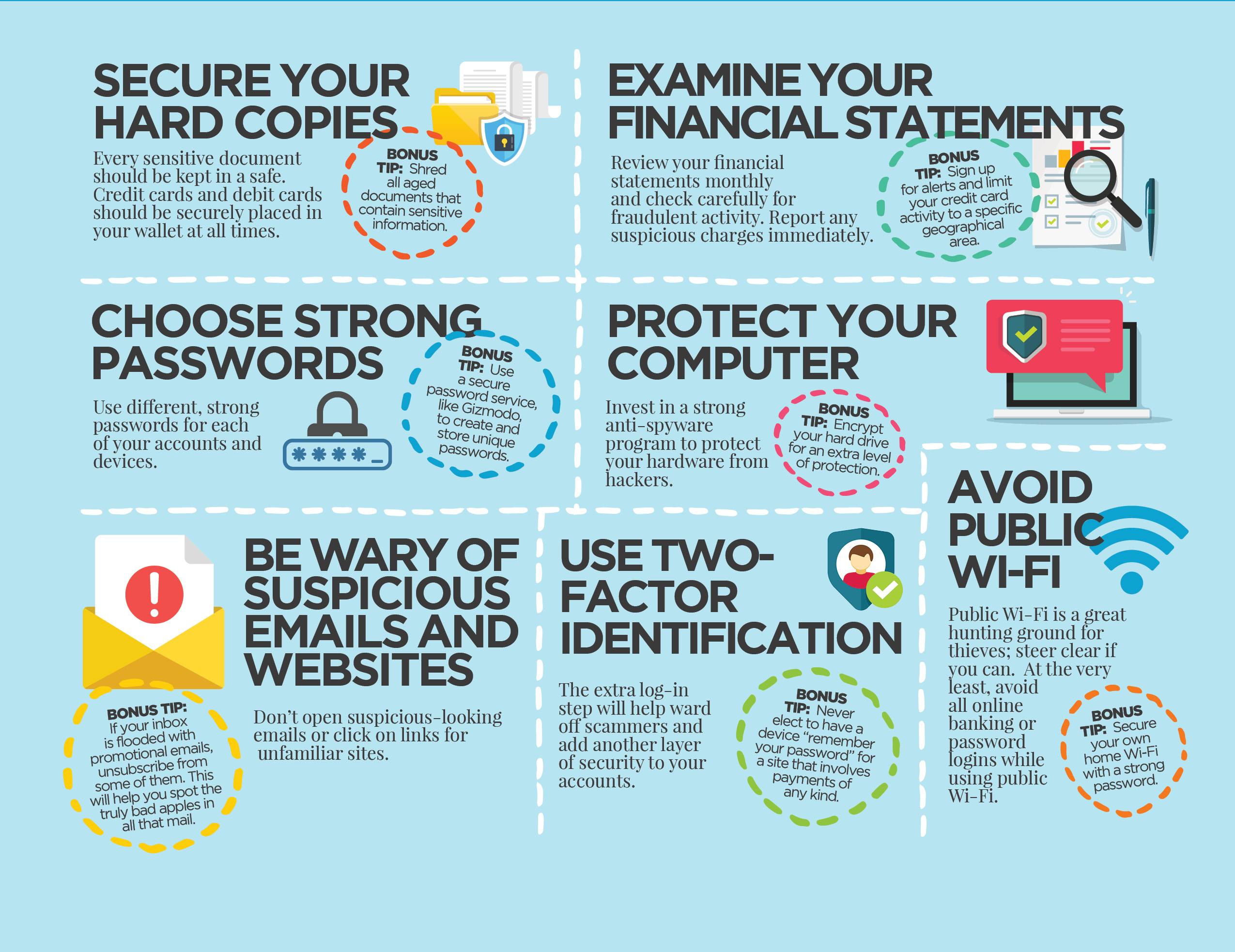
Unified coverage and speed of response are rated highest in importance for next-gen device protection, highlighting the need for comprehensive and rapid solutions. Estimated data.
The Shift From Physical Loss to Digital Catastrophe
Let's be honest about what's changed. A decade ago, losing your phone meant losing a communication tool. You'd call your carrier, get a replacement in a few days, restore your contacts from backup, and move on. The insurance conversation was pretty straightforward: "Does it cover accidental damage? Does it cover theft? How much is the deductible?"
That world is completely gone.
Your phone today is a financial gateway. It holds your banking apps, investment portfolios, cryptocurrency wallets, and payment systems. One compromised device can drain your accounts faster than you can react. Your phone is also an identity key—it stores authentication codes, biometric data, government IDs, passport information, and documents that criminals can use to open accounts in your name.
The physical device is almost irrelevant.
When a criminal steals your phone today, they're not celebrating because they got a £1,000 handset. They're celebrating because they just gained immediate access to financial systems that would normally require multiple layers of verification. They have your face for biometric authentication. They have your backup codes. They have the trust that your device itself represents in the digital ecosystem.
Traditional device insurance completely misses this. Your policy might promise to replace a stolen phone within 5 business days. Fantastic—except your accounts were drained in 5 minutes.
The insurance companies haven't ignored this by accident. They've ignored it because the problem is genuinely complex. Covering physical damage is simple—the damage is visible, quantifiable, and happens to a defined object. Covering digital fraud involves fighting sophisticated criminals who operate across jurisdictions, constantly evolving attack methods, and the messy reality that sometimes the victim's own behavior contributed to the compromise.
But here's the thing: complexity isn't an excuse. It's an opportunity for innovation.

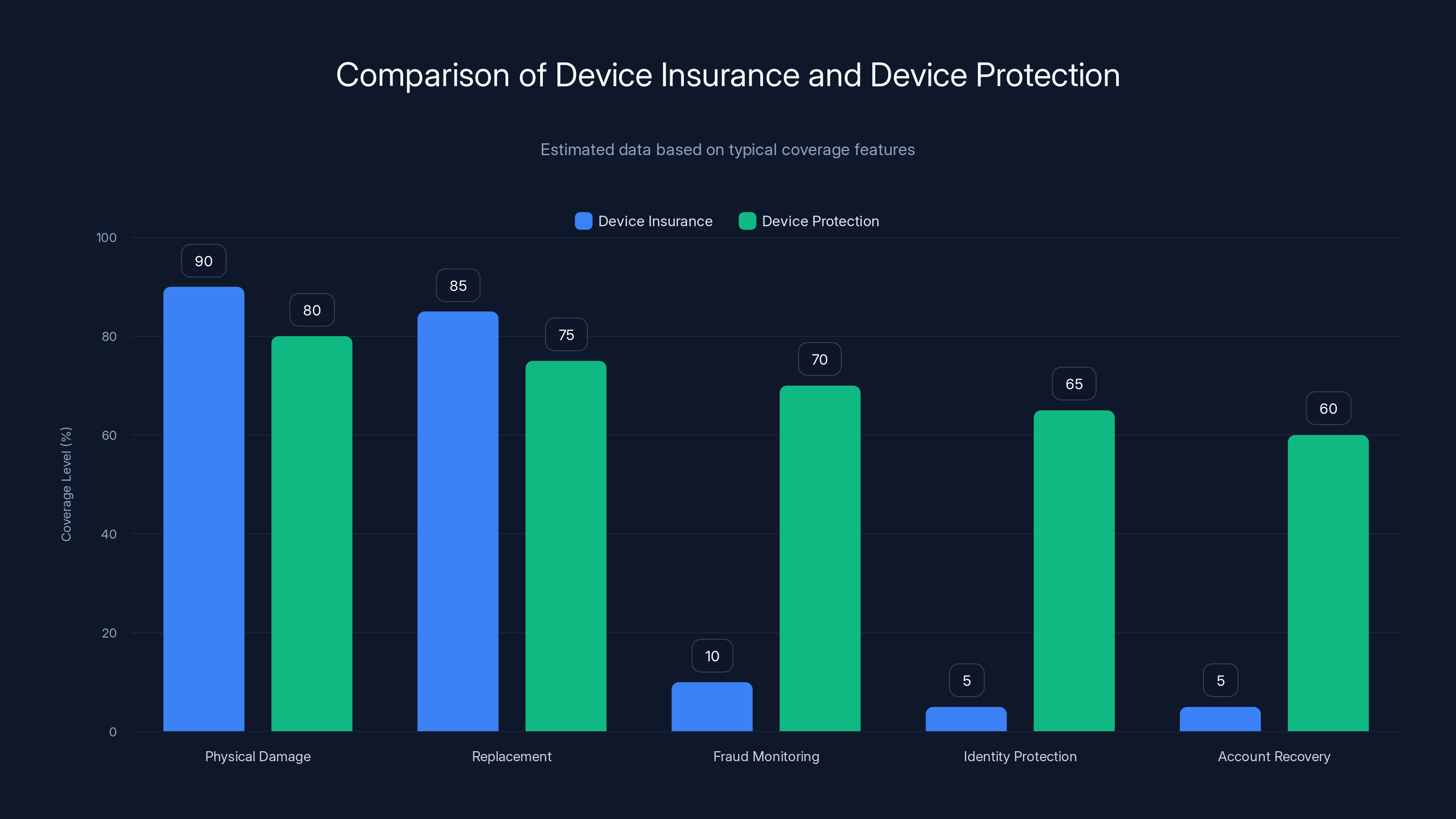
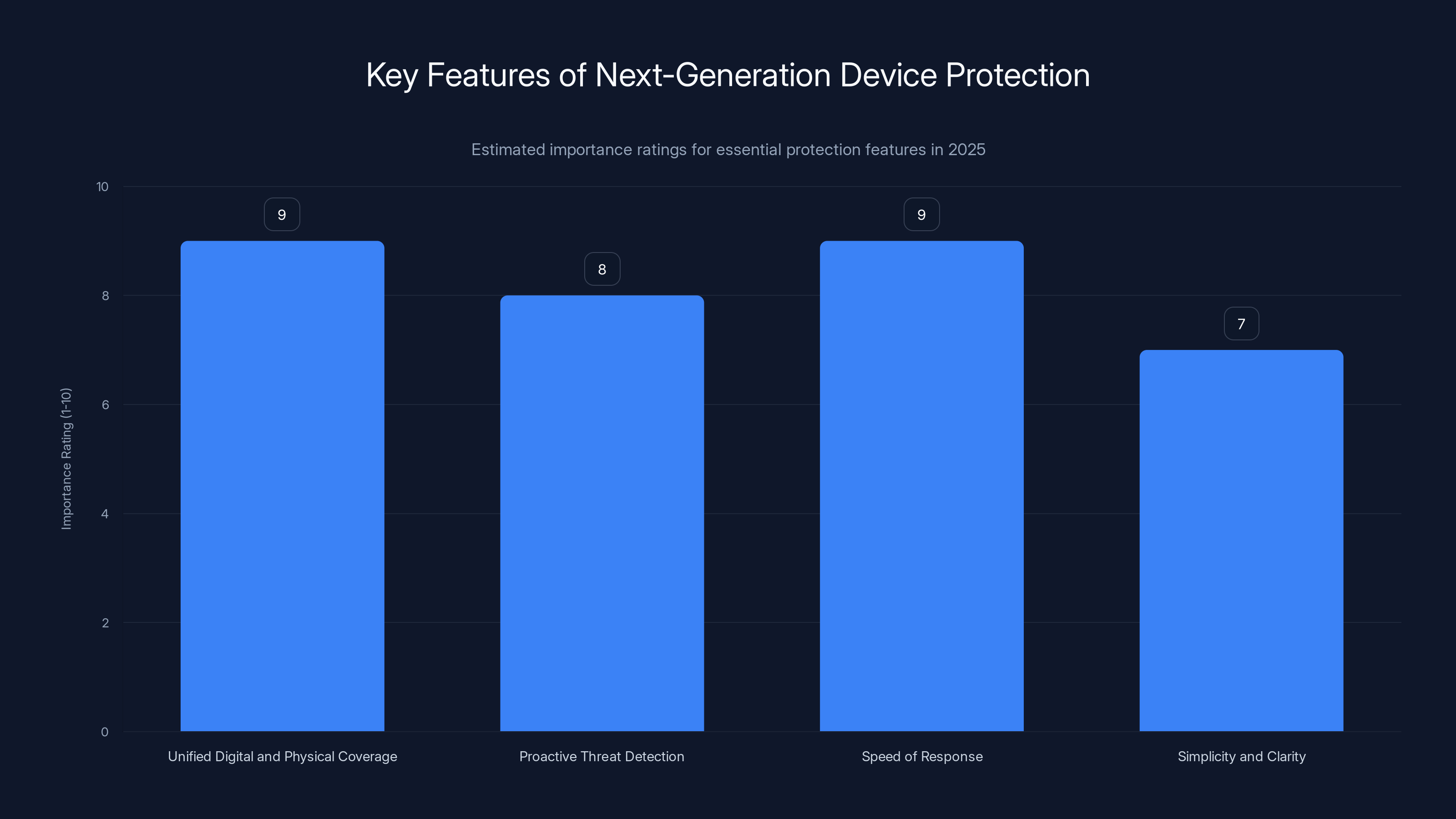
Device protection offers broader coverage, including digital security services, compared to traditional device insurance. (Estimated data)
Why Current Device Insurance Is Fundamentally Broken
Let's dig into what makes traditional device protection so inadequate for the modern threat landscape.
The Fragmentation Problem
When something goes wrong today, the responsibility gets scattered across multiple companies with no coordination. Your phone gets stolen, and suddenly you're managing claims across three or four different institutions:
- Your device insurer replaces the phone
- Your bank handles fraudulent transactions
- Your email provider manages account recovery
- Your identity monitoring service flags suspicious new accounts
- Your phone carrier deals with SIM swaps
Each one operates independently. They don't share information. They don't coordinate response. You end up explaining the same situation multiple times, waiting for each company to process claims separately, and filling out forms that ask for information you've already provided to other companies.
Meanwhile, the damage compounds. Criminals are actively using your identity while you're on hold with your bank.
Research shows that 43% of UK consumers find insurance policies confusing. That's not because people are stupid—it's because the industry has built genuinely confusing systems. Coverage is scattered. Terms overlap in some areas and leave massive gaps in others. Nobody knows who's responsible for what.
The Reactive vs. Proactive Failure
Even when device insurance covers something, it's always reactive. Something bad happens, you file a claim, and then protection kicks in. By that point, the damage is already done.
Imagine if fire insurance worked like this: your house burns down, you file a claim, and then fire protection activates to prevent future fires. That would be ridiculous. But that's exactly how device insurance operates in the digital realm.
We have the technology to be proactive. We can monitor devices for suspicious behavior patterns. We can flag unusual access attempts. We can automatically lock down accounts when theft is detected. We can trigger additional verification steps when a phone moves to a new location. We can do all of this in real time.
Instead, most device protection still operates on a "cover the damage after it happens" model.
The Coverage Gap
Survey data reveals something fascinating and terrifying: 59% of consumers struggle to find appropriate coverage for the risks they actually care about. They want their digital assets protected, but they can't figure out what covers what.
Some risks fall completely through the cracks:
- Account takeover: What happens when someone gains access to your email or social media? Some policies might cover the device replacement, but not the fraudulent charges or identity restoration.
- Credential compromise: If your passwords get stolen, does your insurance cover the resulting fraud? Usually not—but your identity could be compromised.
- SIM swapping: A criminal convinces your carrier to move your phone number to a new SIM card in their possession. This isn't covered by device insurance, but it's one of the most devastating attacks imaginable.
- Deepfake fraud: Criminals create synthetic videos of you committing fraud to open accounts or access resources. Device insurance doesn't cover this, but identity insurance might not either.
- Financial app compromise: Your banking app gets malware. Your funds disappear. Device insurance replaces the phone, but doesn't restore the funds or investigate the compromise.
Consumers look at this landscape and either buy insurance that doesn't cover their real risks, or they buy nothing and hope for the best.

The Digital Identity Crisis: What's Actually at Risk
When we talk about device protection, we need to be specific about what we're protecting. It's not the hardware—it's the digital identity stored within it.
Your phone contains multiple layers of your identity:
Financial Identity
This is the most obvious one. Your banking apps, payment systems, investment accounts, and cryptocurrency wallets are all accessible from your unlocked phone. More importantly, many of these systems trust your phone as a verification device.
Two-factor authentication usually works like this: you log in with your password, and then the system sends a confirmation code to your phone via SMS or an authenticator app. The problem is, if someone has your physical phone, they have both factors of authentication. They have your password (possibly captured via keylogger or phishing), and they have your device (which receives the confirmation code).
For the criminal, it's like having the key and the security code already.
Biometric Identity
Modern phones store encrypted biometric data—your fingerprints, face recognition data, and increasingly, iris scans. This isn't just for phone security. Many payment systems, banking apps, and identity services now use biometric verification.
If a criminal has your phone unlocked, they potentially have access to biometric data that was previously thought to be uniquely secure. Face recognition has become sophisticated enough that presentation attacks (spoofing with photos) are sometimes possible, though modern systems have largely defeated this. But the underlying data itself is valuable to criminals.
Government and Legal Identity
This is where it gets genuinely dangerous. Modern phones increasingly store:
- Digital driver licenses
- Passport information
- Government ID documents
- Birth certificates
- Social security details
These documents can be used to open accounts, apply for loans, or commit identity fraud that can take months or years to unwind. Unlike financial fraud, which often appears on a statement and can be disputed, identity fraud can silently compound for years before you discover it.
Digital Access Keys
Your phone increasingly serves as a key to other digital systems. It might be:
- Your authentication method for email (and therefore the reset mechanism for every account that uses that email)
- Your 2FA for bank and investment accounts
- Your access to your cloud storage
- Your backup for your cryptocurrency wallets
- Your connection to your smart home security system
Compromise your phone, and you've compromised the master key to your entire digital life.
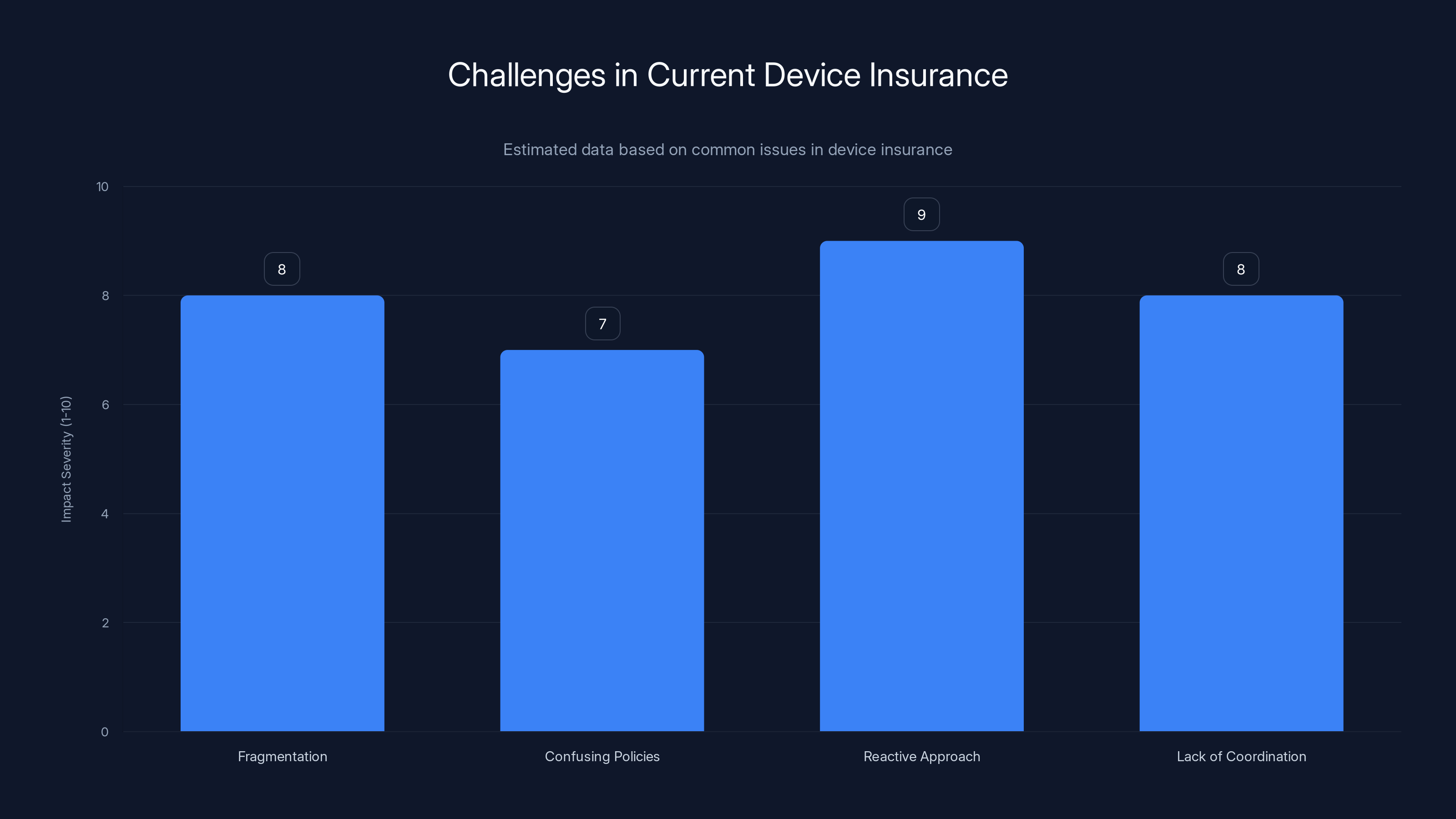
Fragmentation and a reactive approach are major issues in device insurance, with high impact severity. Estimated data.
How Modern Threats Have Evolved Beyond Traditional Hacking
The threat landscape has become radically more sophisticated, and traditional device protection hasn't even acknowledged this change.
AI-Enabled Scams and Deepfakes
Phishing used to be easy to spot. You'd get an email from someone claiming to be your bank, but the grammar was terrible and the logo was pixelated. Easy reject.
AI has changed that completely.
Now criminals can generate perfectly grammatical, personalized messages targeting you specifically. They can analyze your social media to understand your language patterns, your interests, and your vulnerabilities. They can create deepfake videos of people you know, asking for urgent help. They can synthesize voice messages that sound exactly like your manager requesting an urgent transfer.
These aren't generic phishing attempts anymore. They're personalized, they're sophisticated, and they're increasingly successful because they exploit psychological vulnerabilities, not just technical ones.
Device insurance doesn't protect against this. In fact, traditional insurance wouldn't even recognize this as a claim-worthy event until after the damage is done.
Smishing and Voice Phishing Evolution
Smishing (SMS phishing) has evolved from obvious scams to sophisticated social engineering. Criminals send text messages that appear to come from your bank, your carrier, or your delivery service. They include urgent language that triggers an immediate response.
Voice phishing (vishing) is even more effective because it exploits the trust we place in voice communication. A criminal calls claiming to be from your bank's security department, speaks with authority and knowledge about your account, and convinces you to provide sensitive information or approve a transfer.
These attacks work because they're not targeting your device—they're targeting your judgment in the moment. You're stressed, the message feels urgent, and you react without thinking. By the time you realize it was a scam, the damage is done.
SIM Swapping and Account Takeover
SIM swapping is beautifully simple and devastatingly effective. A criminal calls your phone carrier, claims to be you, and requests that your phone number be transferred to a SIM card in their possession. This takes minutes.
Now they have your phone number. They receive your SMS-based two-factor authentication codes. They receive password reset emails. They have the keys to your digital kingdom, and your legitimate phone is suddenly useless.
Account takeover through SIM swapping has resulted in crypto losses exceeding millions of dollars. Victims have lost life savings because their email recovery mechanism (the SMS code to their phone number) was compromised.
Once again, traditional device insurance doesn't address this. The compromise never touches your device—it happens at the carrier level.
The Psychology of Risk: Why People Underestimate Digital Threats
Here's something that genuinely puzzles security researchers: people understand that their phones are valuable. They spend £1,000 on the hardware. They back up their data. They use passwords and biometric authentication.
But when you ask them about insurance and protection, suddenly they're convinced they don't need it.
This disconnect exists for several psychological reasons:
Optimism Bias
Humans are fundamentally optimistic about negative events. We know bad things happen to people, but we're convinced they're less likely to happen to us specifically. This is called optimism bias, and it's one of the most consistent findings in behavioral psychology.
You know that phones get stolen. You've probably known someone whose phone was stolen. But you're convinced your phone, specifically, won't get stolen. You're more careful. You're more aware. You're different.
Statistically, you're not.
The same bias applies to fraud. You know that people get scammed. You're not falling for obvious phishing emails. You don't click suspicious links. Therefore, fraud won't happen to you.
Except the fraudsters are specifically targeting people who think they won't get scammed. Those are the people whose defenses are lower.
Invisibility Bias
Physical damage is immediately visible. You drop your phone, the screen cracks, you see the damage. Your brain registers the problem and accepts that you need protection.
Digital fraud is invisible until it's catastrophic. You get hacked on Tuesday, but nobody notices until Friday when someone applies for a credit card in your name. By then, the damage is done, and your brain is still operating under the assumption that everything was fine on Tuesday.
Because you can't see the threat, you underestimate its likelihood.
The Illusion of Technical Competence
Most people think they understand technology better than they actually do. You use your phone every day, so you must understand its security, right?
In reality, modern security is incredibly complex. You might think your authentication is secure because you use a fingerprint. You might think your data is private because you turned on encryption. You might think you're protected because your bank uses two-factor authentication.
You might all be wrong.
This illusion of competence means people don't seek out protection they actually need, because they don't recognize the gaps in their own understanding.
The Victim Blame Problem
Society has a terrible habit of blaming victims of fraud. If you get scammed, people's first question is usually: "Why did you fall for that?" This creates shame and prevents people from discussing security issues openly.
This shame also affects insurance adoption. Admitting that you need device and identity protection feels like admitting that you're vulnerable or that you might make mistakes. Many people would rather risk the actual problem than admit that they need help.

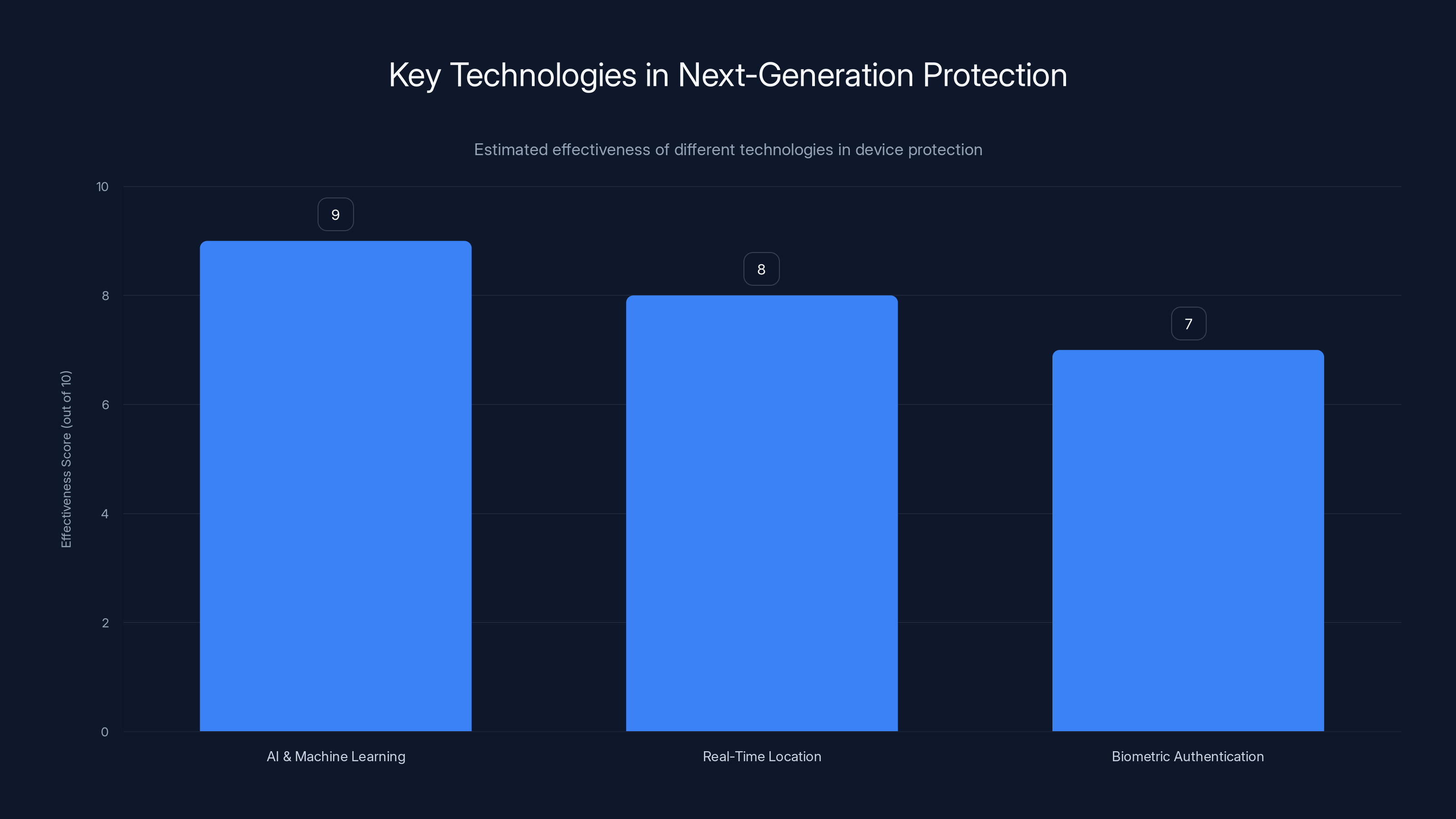
AI & Machine Learning is estimated to be the most effective technology in next-generation protection, followed by real-time location tracking and biometric authentication. Estimated data.
Current Solutions: Partial Measures and Coverage Gaps
The market has started to recognize these problems, and several innovations have emerged. But none of them solve the complete picture yet.
Banks and Financial Institutions
Many banks now offer fraud protection and account monitoring. They monitor for unusual spending patterns and suspicious login attempts. They send alerts when transactions occur outside your normal geographic area.
This is genuinely useful. Banks have powerful tools because they have access to transaction data and spending patterns. They can identify fraud better than anyone else.
But banks only protect financial accounts. They don't protect your email, your social media, your identity documents, or your device itself.
Cybersecurity Companies
Traditional cybersecurity firms offer antivirus software, password managers, VPN services, and identity monitoring. These tools are essential and genuinely valuable.
But they're focused on prevention and after-the-fact recovery. They prevent malware from infecting your device. They monitor if your identity appears on the dark web. They help you manage passwords securely.
They don't address what happens when your physical device is stolen and immediately used by a criminal who has physical access to an already-unlocked phone.
Device Manufacturers
Apple, Google, and Samsung have invested heavily in device security. They've built in biometric authentication, encrypted storage, remote locate and wipe capabilities, and security updates that patch vulnerabilities regularly.
These are genuinely important. A stolen phone running modern security software is far less useful to a criminal than an older device.
But device security doesn't prevent account takeover. It doesn't protect against SIM swaps. It doesn't stop criminals who have already compromised your email. It's a layer of defense, but not a complete solution.
Device Insurance Companies
Companies like Apple Care+, Samsung Protection, and third-party insurers have started adding security features to their offerings. Some now include identity monitoring, fraud alerts, and account recovery assistance.
This is movement in the right direction. At least the conversation has shifted from "just replace the device" to "also help with the digital consequences."
But coverage remains fragmented and unclear. Different plans cover different things. The claims process is still mostly reactive. Response times are measured in days, not minutes.
Revolut's Street Mode: A Glimpse at the Future
One innovative example is worth discussing specifically: Revolut's Street Mode feature. This represents exactly the kind of thinking that device protection needs.
Street Mode is location-aware. It recognizes when your phone leaves your trusted areas. When triggered, it automatically delays bank transfers and requires additional biometric verification before any transactions can be completed.
Why is this brilliant?
First, it's proactive rather than reactive. The protection activates before fraud occurs, not after.
Second, it recognizes the specific vulnerability: if your phone is stolen while you're traveling or in an unfamiliar area, there's a critical window where the criminal can access your financial accounts while you might not immediately notice.
Third, it adds friction at the exact moment it's needed. The additional biometric verification step doesn't affect normal usage, but it creates a crucial delay if someone else is trying to drain your account.
This is the kind of adaptive, intelligent protection that the broader device insurance industry needs to learn from. Not replacing the device after it's stolen, but preventing fraud in the moment of vulnerability.

The Technology Enabling Next-Generation Protection
The good news is that the technical capability to create comprehensive device protection already exists. We have the tools. We're just not using them together yet.
Artificial Intelligence and Machine Learning
AI enables pattern recognition at scale. Modern systems can analyze millions of transactions, login attempts, and user behaviors to identify what "normal" looks like for each individual.
When something deviates from normal, the system can flag it. Is this person usually in London at 9 AM on a Wednesday? No? Then maybe we should add verification before allowing a bank transfer.
Does this person usually access their email from an iPhone in their home? Then suddenly accessing it from an Android in Russia deserves extra scrutiny.
AI can also identify phishing attempts and fraud patterns that humans would miss. It can spot deepfakes and synthetic voices that sound convincing to human ears.
The key limitation is that AI works best with lots of data. The more transactions, logins, and behaviors it can analyze, the better it gets at identifying anomalies.
Real-Time Device Location and Identity
Modern phones can report their location in real time with remarkable accuracy. This data could be used to:
- Verify that you're actually attempting to access your accounts from the location you claim
- Detect when your device suddenly appears in a different country (indicating theft or SIM swap)
- Automatically trigger additional verification steps when you're in high-risk environments
- Correlate your device location with account access to identify stolen credentials being used remotely
Privacy concerns exist, obviously. But with proper consent and control, location data could be the most powerful anti-fraud tool available.
Biometric Continuous Authentication
Instead of authenticating once when you unlock your phone, continuous authentication verifies your identity throughout your session. If someone grabs your phone, the continuous authentication system detects that the biometric profile doesn't match and immediately locks down sensitive functions.
This is already technically feasible on modern devices. It just hasn't been broadly implemented because it requires coordination between device manufacturers, app developers, and security services.
Blockchain and Cryptographic Verification
For high-value transactions like cryptocurrency transfers or identity verification, cryptographic systems could require multiple devices or physical locations to verify before the transaction completes.
Instead of a simple SMS verification code, imagine a system that requires:
- Biometric authentication on your phone
- A verification code sent to a separate device (like your smartwatch or a hardware key)
- A final approval from a trusted contact or security service
This creates a verification process that's nearly impossible for a thief to complete, even with both your phone and knowledge of your passwords.
Automated Device Isolation and Recovery
When theft is detected, the system can:
- Immediately lock down all financial functions
- Disable biometric access to sensitive apps
- Begin account recovery procedures
- Alert your financial institutions
- Preserve forensic evidence for investigation
All of this can happen automatically and instantly, before the criminal has time to drain your accounts.

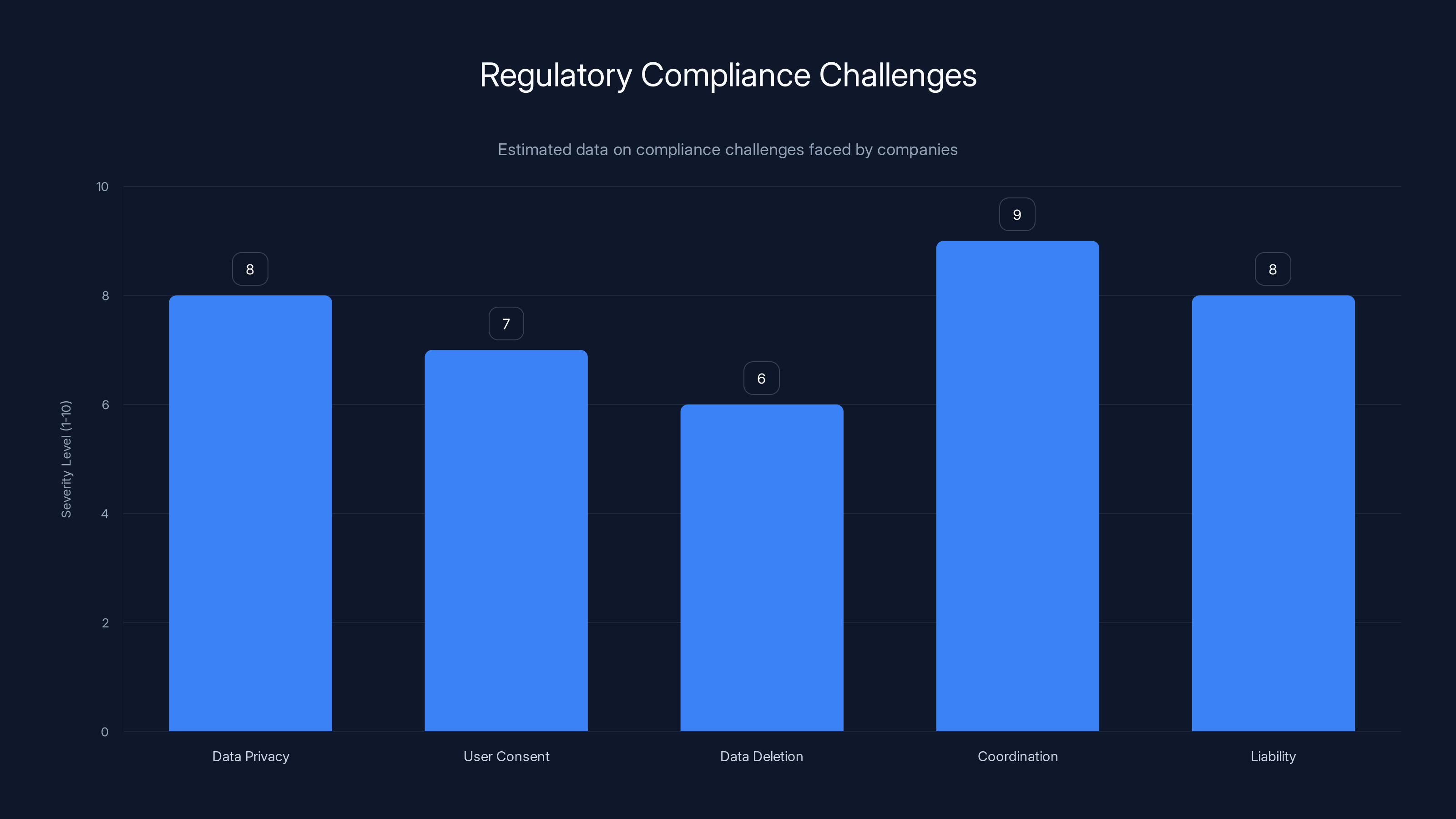
Coordination between companies and liability issues are the most severe challenges, with estimated severity ratings of 9 and 8 respectively. Estimated data.
What Next-Generation Device Protection Must Include
Based on everything we've discussed, comprehensive device protection in 2025 and beyond needs to address specific gaps in current offerings.
Unified Digital and Physical Coverage
The first requirement is straightforward: protection needs to cover both the device and the digital assets within it. This means:
- Replacement or repair costs for hardware damage
- Recovery costs for compromised financial accounts
- Identity restoration and fraud investigation
- Account recovery and security services
- Legal support if needed
All of this under one policy with one claims process. No more shuffling between different companies trying to figure out who covers what.
Proactive Threat Detection and Prevention
Protection needs to shift from reactive to proactive. This means:
- Continuous monitoring for unusual account activity
- Real-time detection of phishing attempts and malware
- Behavioral analysis to identify suspicious patterns
- Immediate alerting and remediation when threats are detected
- Gradual account lockdown rather than catastrophic compromise
The goal is to catch threats before they cause damage, not after.
Speed of Response
When something goes wrong, response needs to happen in minutes, not days. This means:
- Automated device locking when theft is detected
- Instant account freeze capabilities
- Immediate fraud investigation
- Same-day claims resolution
- 24/7 customer support
The first 60 minutes after a compromise are critical. If protection can contain the damage during that window, the consequences become manageable instead of catastrophic.
Simplicity and Clarity
Coverage needs to be simple enough that ordinary people understand what's protected without reading 47 pages of fine print. This means:
- Clear categories of protection
- Honest explanation of what is and isn't covered
- Straightforward claims process
- Transparent pricing
- No gotchas or hidden exclusions
The reason 43% of consumers find insurance confusing isn't because consumers are dumb. It's because insurance is deliberately complex. Fixing this requires intentional simplification.
Integration Into Services You Already Use
The survey data was clear: 94% of British consumers prefer protection bundled into services they already use. This makes sense from a practical perspective.
Instead of buying separate insurance, you get device and identity protection built into:
- Your bank's app (integrated with their fraud detection)
- Your phone manufacturer's ecosystem (integrated with their security)
- Your primary payment service (integrated with their monitoring)
- Your email provider (integrated with their account recovery)
Integration eliminates friction and coordination problems. When your bank detects suspicious activity, it can immediately coordinate with your device security service. When your device detects theft, it can instantly alert your financial providers.

Implementation Challenges and Regulatory Hurdles
Here's where the reality gets complicated. Creating comprehensive device protection sounds straightforward, but it runs into massive practical and regulatory challenges.
Data Privacy and Regulatory Compliance
Proactive threat detection requires analyzing user behavior, tracking location, and monitoring transaction patterns. This triggers data protection regulations like GDPR in Europe, CCPA in California, and similar laws worldwide.
Providers need explicit user consent. They need to explain what data they're collecting and how it's being used. They need to allow users to opt out. They need to delete data when users request it.
These requirements are important for protecting individual privacy, but they also create friction in implementing comprehensive protection.
The solution isn't to ignore privacy—it's to design protection that maximizes effectiveness while minimizing data collection. Only collect data that's strictly necessary. Delete data as soon as it's no longer needed. Give users granular control over what's collected and analyzed.
Coordination Between Companies
Device protection requires coordination between device manufacturers, banks, payment processors, email providers, and insurance companies. These are large organizations with different incentives and different security approaches.
Getting them to share data, coordinate response, and integrate systems isn't a technical problem—it's an organizational one. It requires industry standards, technical agreements, and agreement on responsibility.
Some progress is happening. The Financial Conduct Authority, European regulators, and similar bodies are pushing for stronger coordination on fraud prevention. But true integration is still years away.
Liability and Responsibility
When something goes wrong, who's responsible? If:
- Your bank's fraud detection fails to catch a $10,000 unauthorized transfer
- Your device security service doesn't detect malware
- Your insurance company takes too long to freeze your accounts
- Your device manufacturer's security update introduces a vulnerability
Each of these involves different parties, and it's genuinely unclear where liability falls.
Creating comprehensive protection requires clarifying this. Clear responsibility prevents both under-protection (companies claiming it's not their problem) and creates incentives for each party to do their part well.
Cost and Scalability
Comprehensive protection is expensive to provide. It requires 24/7 monitoring, AI systems, human support teams, and rapid response capabilities.
Making this affordable to ordinary consumers (not just wealthy individuals who can pay for premium services) requires scale. You need millions of customers to spread the cost.
But getting millions of customers requires clear value, which requires integration and effectiveness. It's a chicken-and-egg problem that requires someone to take the first step and build at scale before profitability is proven.

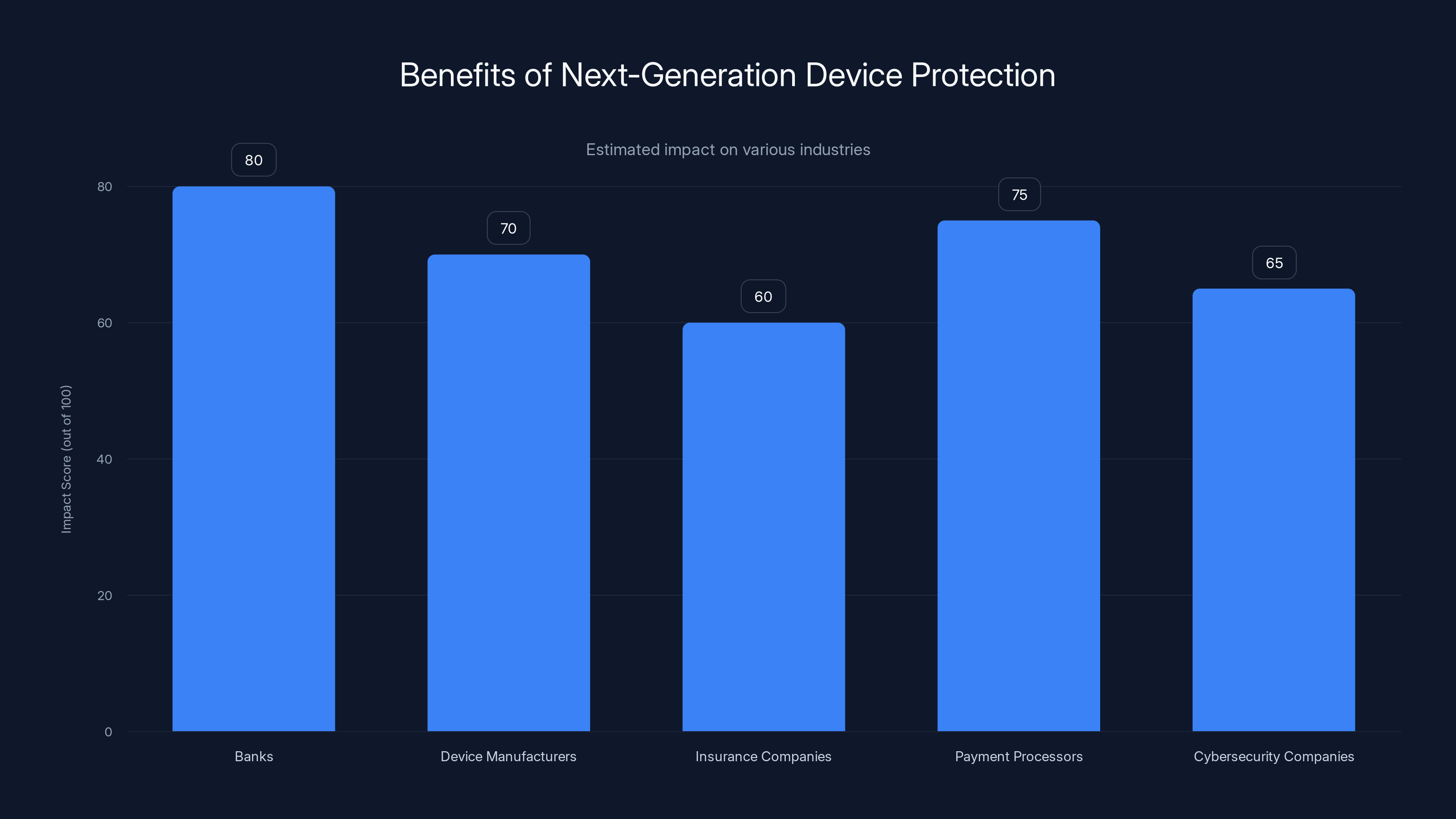
Next-generation device protection significantly impacts fraud reduction across industries, with banks and payment processors seeing the highest estimated benefits. Estimated data.
The Role of AI in Modern Device Protection
Artificial intelligence will be central to next-generation device protection. Not because it's trendy to say "AI-powered," but because specific AI capabilities solve specific problems that human experts cannot solve at scale.
Behavioral Analysis at Scale
A human fraud analyst can examine a few transactions per day and identify patterns. An AI system can examine millions of transactions simultaneously and identify patterns that humans would never spot.
This matters because fraudsters are getting better at mimicking legitimate behavior. They're not just flooding your account with suspicious transactions—they're carefully conducting a few legitimate-looking transactions mixed with fraudulent ones.
AI can spot the difference.
Real-Time Threat Response
When a threat is detected, human analysts can't respond to every incident simultaneously. With millions of potential fraud cases happening globally at any moment, even a large team of humans is helpless.
AI responds instantly to detected threats. When a compromised account is identified, the system can immediately freeze transactions, lock down access, and alert the user, all happening in seconds.
Personalized Protection Rules
Every person uses their phone differently. Your "normal" behavior is completely different from someone else's normal behavior.
AI learns your patterns specifically. It knows when you usually access your email. Where you normally make purchases. What payment amounts you typically approve. Who normally calls you.
Using this personalized baseline, AI can detect when something deviates from your actual normal behavior, rather than applying generic rules that might be too strict (blocking legitimate transactions) or too loose (allowing fraud).
Phishing and Fraud Detection
Phishing attempts are getting incredibly sophisticated. They use real logos, correct grammar, personal details about you, and urgent language designed to bypass your defenses.
Humans struggle with this. We're social creatures trained to trust communications that look legitimate and use urgent language.
AI can analyze phishing at scale, identifying patterns in fraudulent emails and messages that humans would miss. It can flag suspicious messages before they reach your inbox.
The key limitation is that phishing is constantly evolving. Fraudsters are using machine learning to make their attacks better. This creates an arms race where AI fraud detection must continuously improve to stay ahead of AI fraud creation.
Deepfake Detection
As deepfake technology improves, criminals will increasingly use synthetic videos and audio to commit fraud. Someone will call your company claiming to be the CEO, but the voice will be synthesized from audio samples they've collected.
Detecting this requires analyzing video and audio for artifacts of synthetic creation—subtle imperfections that indicate the content is artificial rather than genuine.
AI is getting better at both creating deepfakes and detecting them. The race is on, and detection needs to stay ahead.

What Users Need to Do Right Now
While the industry works on next-generation solutions, you need to protect yourself with tools that exist today.
Use Authenticator Apps Instead of SMS
SMS-based two-factor authentication is vulnerable to SIM swapping. Authenticator apps (Google Authenticator, Microsoft Authenticator, Authy) store the authentication code on your device instead of relying on your phone number.
This isn't perfect—if your device is compromised, the codes are compromised too. But it's far better than SMS.
Setting this up takes maybe 10 minutes per account. Do it.
Enable Biometric Locks on Financial Apps
Banking apps and payment services should be protected with biometric authentication (fingerprint or face recognition). This creates friction for criminals who steal your phone.
Use a Password Manager
Password managers store your passwords in encrypted form and auto-fill them securely. This makes it possible to use unique, strong passwords for every account without trying to memorize them.
When one service gets breached, your password for that service is compromised, but your passwords for other services remain secure.
Monitor Your Accounts Regularly
Check your bank, credit card, and email accounts regularly for suspicious activity. Set up alerts for any transactions. Check your credit report at least annually.
Early detection of fraud can significantly reduce damage.
Enable Location-Based Authentication Where Available
If your bank or financial service offers location-based verification (like Revolut's Street Mode), enable it. This creates an extra verification step when your account is accessed from unusual locations.
Consider Device Insurance
While current device insurance doesn't cover everything you need, it's better than nothing. Look for policies that include:
- Hardware replacement or repair
- Identity monitoring
- Fraud protection
- Account recovery assistance
Check the specific coverage, claims process, and response times before buying.
Use a VPN When Connecting to Public Wi Fi
Public Wi Fi networks are notoriously insecure. A VPN (Virtual Private Network) encrypts your traffic, preventing someone on the same network from intercepting your data.
This matters because if you're checking your email or accessing financial apps on public Wi Fi without a VPN, someone could potentially capture your credentials.

The Future of Device Protection: 2025 and Beyond
Based on current trends, device protection will evolve in specific directions over the next few years.
Convergence of Services
We'll see increasing integration between device manufacturers, banks, payment providers, and insurance companies. These services will share threat intelligence, coordinate response, and create unified protection that's currently fragmented.
Apple's recent moves into financial services (Apple Card, Apple Pay), Google's expansion of its financial ecosystem (Google Wallet, Google Pay), and Samsung's Pay Master initiative all suggest that device manufacturers see device protection as inseparable from financial services.
AI-Driven Predictive Protection
Instead of detecting fraud after it occurs, future protection will predict and prevent it. AI systems will identify when you're likely vulnerable (traveling to an unusual location, accessing your phone from new networks, visiting unfamiliar apps) and proactively increase verification requirements.
This shifts the entire model from reactive claims processing to proactive threat prevention.
Decentralized Identity Verification
Current systems rely on centralized identity verification (banks verify you through your phone number, email, or biometric data stored with them). Future systems might use decentralized identity verification where you control your identity credentials directly.
This would reduce the catastrophic impact of any single company's breach.
Standardized Threat Response
Industry standards for threat response are emerging. When fraud is detected, the system will immediately:
- Freeze compromised accounts
- Alert relevant financial institutions
- Notify the customer
- Begin investigation
- Start recovery procedures
All of this according to agreed standards, so response is consistent and reliable.
Quantum-Resistant Cryptography
As quantum computing matures, current encryption methods will become obsolete. Future device protection will incorporate quantum-resistant cryptography, ensuring that data encrypted today remains secure even when quantum computers become available.
This is important because criminals are currently collecting encrypted data, betting that they'll be able to decrypt it once quantum computers are available. Quantum-resistant cryptography prevents this "harvest now, decrypt later" attack.
Regulation and Standardization
Regulators around the world are increasingly focused on fraud prevention and device security. We'll see:
- Mandatory fraud prevention standards
- Clear responsibility for different parties
- Minimum response time requirements
- Data privacy protections for protective monitoring
- Consumer education requirements
This regulatory pressure will actually drive innovation by clarifying what's required and who's responsible.

The Business Case for Next-Generation Protection
From a purely business perspective, comprehensive device protection makes sense for everyone involved.
For Banks and Financial Institutions
Fraud costs the banking industry billions annually. Comprehensive device protection reduces fraud losses dramatically. It also improves customer satisfaction and reduces the support burden created by fraud victims.
Banks that offer superior protection will attract and retain customers, creating a competitive advantage.
For Device Manufacturers
Apple, Google, and Samsung have already invested billions in device security. Extending that security to financial and identity protection creates a more valuable ecosystem.
Customers with comprehensive protection will be more likely to use their device for financial transactions (which benefits the manufacturer through volume and data) and more likely to remain loyal to the platform (reducing churn).
For Insurance Companies
Traditional device insurance is dying. Phones are getting more durable. Consumers are keeping devices longer. The margin on replacing broken screens is compressing.
Comprehensive digital protection is a growth market. The TAM (total addressable market) is massive—anyone with a smartphone needs it. The margins are better because the service is based on monitoring and prevention rather than hardware replacement.
For Payment Processors
Payment processors are liable for fraud. They have powerful incentive to reduce fraud. Integrated device protection works with their fraud systems to identify and prevent fraudulent transactions.
This reduces their fraud losses, their compliance risk, and their support costs. It's a win across the board.
For Cybersecurity Companies
Cybersecurity companies have built incredible threat detection and response capabilities. Device protection is a natural extension of their existing business.
By partnering with banks, manufacturers, and insurers, cybersecurity companies can take their capabilities to market at scale.

Implementing Your Own Digital Safety Plan
While waiting for the industry to evolve, you need a personal digital safety plan.
Step 1: Inventory Your Digital Assets
Make a comprehensive list of everything stored on or accessible from your phone:
- Financial accounts (bank, investment, crypto)
- Email accounts
- Social media accounts
- Identity documents
- Health information
- Sensitive personal data
Next to each, note: what would happen if this was compromised?
Step 2: Identify Your Vulnerabilities
For each asset, identify the specific ways it could be compromised:
- Device theft
- Account takeover
- Phishing/social engineering
- Malware
- Data breach
- SIM swapping
Not every asset is vulnerable to every attack. A thoughtful inventory helps you focus protection where it's actually needed.
Step 3: Implement Protection Layers
For each vulnerability, implement protection:
- Device-level: strong password/biometric, encryption, location tracking enabled
- Account-level: unique passwords, authenticator apps, recovery codes saved securely
- Network-level: VPN for public Wi Fi, secure home network
- Financial-level: fraud monitoring, account limits, geographic restrictions
- Identity-level: identity monitoring service, credit freeze if appropriate
Step 4: Create a Incident Response Plan
When (not if) something goes wrong, you need to know what to do:
- How quickly can you detect compromised accounts?
- Who do you call first? (Your bank? Your carrier? Your police department?)
- What information do you need to provide to recover accounts?
- Do you have backup authentication methods if your primary method is compromised?
- Where are your backup recovery codes stored?
Create a document and keep it secure (not on your phone).
Step 5: Test Your Plan
Don't wait for an actual emergency to discover gaps in your protection. Test your recovery procedures:
- Can you recover your email account without your phone?
- Can you access recovery codes for your important accounts?
- Can you verify your identity with your bank through alternate methods?
This testing reveals gaps before something actually goes wrong.

Industry Initiatives and Standards Development
Across the industry, various organizations are working on establishing standards and best practices for device protection.
Open Standards and Frameworks
The FIDO Alliance is developing authentication standards that reduce reliance on passwords and SMS verification. FIDO2 creates standards for biometric and hardware-based authentication.
The Financial Industry Regulatory Authority (FINRA) is developing standards for financial device security.
These standards help ensure that different companies' systems can work together and that protection is consistent across providers.
Information Sharing and Threat Intelligence
The Financial Services Information Sharing and Analysis Center (FS-ISAC) helps financial institutions share threat intelligence about emerging fraud patterns.
Similar organizations exist for other industries. By sharing information about new threats, organizations can collectively improve their defenses faster than any single organization could develop them alone.
Regulatory Guidance
Regulators are increasingly issuing guidance on expected fraud prevention and device security standards. This creates pressure on organizations to innovate while providing clarity on what's required.
The UK Financial Conduct Authority, European Banking Authority, and Federal Reserve all issue regular guidance on fraud prevention expectations.
Conclusion: The Next Chapter in Device Protection
Device protection has been stuck in the past for far too long. We've created an incredible technology ecosystem where our phones handle nearly everything in our lives, but we're protecting them with insurance models designed for broken screens.
The gap is unsustainable.
Over the next few years, we'll see protection evolve from reactive (something goes wrong, you file a claim) to proactive (threats are detected and prevented before damage occurs). We'll see protection extend from hardware to digital assets. We'll see fragmented services consolidate into unified solutions.
Most importantly, we'll see protection that actually matches the threats we face in 2025 and beyond.
For now, this requires vigilance on your part. The tools and best practices exist. Protection is available. You just have to actually implement it instead of hoping nothing bad happens.
Because here's the reality: something bad probably will happen. The question is whether you'll be ready.
The criminal stealing a phone every six minutes in London isn't stopping. The attacks are getting more sophisticated. The stakes are getting higher.
Your protection can get better too. It just requires taking it seriously, implementing the tools available today, and staying informed as the industry evolves.
Start with that inventory of your digital assets. Take it seriously. Then build protection around what actually matters.
Your digital life is worth protecting. Treat it that way.

FAQ
What is the difference between device insurance and device protection?
Device insurance traditionally covers physical damage (cracked screens, water damage) and device replacement. Device protection is a broader concept that includes hardware coverage plus digital security services like fraud monitoring, identity protection, and account recovery assistance. True comprehensive protection addresses both the physical device and the digital assets stored within it, responding to threats proactively rather than just replacing hardware after damage occurs.
How can I protect my phone from being stolen in the first place?
While complete prevention is impossible, you can reduce the risk by keeping your phone in secure pockets rather than bags, avoiding using your phone in ways that make it an obvious target (like holding it up while taking photos in busy areas), keeping your phone out of sight when traveling, using apps with location tracking enabled so you can locate it if stolen, and backing up your data regularly so theft doesn't result in data loss. More importantly, focus on protecting what's inside the phone rather than the phone itself, since the real danger lies in criminals accessing your financial and identity data.
What should I do immediately if my phone is stolen?
First, stay calm and contact your phone carrier's fraud department immediately to prevent SIM swapping. Then log into your email from another device and change your password, since email is the master key to most other accounts. Contact your banks and financial institutions to lock your accounts and monitor for fraudulent transactions. Report the theft to police for the official record. Finally, contact your device manufacturer to locate and remotely wipe your phone if necessary. The first 60 minutes are critical—criminals work fast, so speed matters far more than perfection.
Why is two-factor authentication more secure than just a password?
Two-factor authentication (2FA) requires something you know (your password) plus something you have (your phone or authenticator app) or something you are (your biometric). This means even if someone obtains your password through phishing or a data breach, they still can't access your account without your phone. Authenticator apps are more secure than SMS because they're harder to intercept—criminals would need your physical device rather than just access to your phone number through a SIM swap.
How can AI help prevent fraud on my device?
AI analyzes your normal behavior patterns—where you usually access accounts, what amounts you typically spend, when you normally use your phone—then flags deviations from these patterns as potential fraud. AI can also identify phishing attempts by analyzing email language and structure for patterns associated with fraud, detect deepfake videos and synthetic voices, monitor for malware by analyzing app behavior, and respond instantly to threats by freezing accounts or locking down access. The key advantage is that AI can process millions of transactions simultaneously and adapt as fraud methods evolve, something human analysts cannot do at scale.
What is SIM swapping and why is it dangerous?
SIM swapping occurs when a criminal calls your phone carrier, claims to be you, and convinces them to activate your phone number on a SIM card the criminal controls. This gives the criminal access to SMS verification codes and password reset emails sent to your phone number. It's dangerous because two-factor authentication based on SMS becomes useless, account recovery mechanisms fail, and cryptocurrency wallets and financial accounts using phone-based verification become accessible. Prevention requires setting a PIN with your carrier that must be provided before any SIM changes, and using authenticator apps instead of SMS for 2FA wherever possible.
Is it safe to store sensitive documents on my phone?
Modern phones have encryption and security features that can protect sensitive documents as long as you enable them. Enable biometric locks on apps containing sensitive information, use encrypted storage where available, keep your phone's software updated to patch security vulnerabilities, and avoid storing documents in plain-text or unencrypted folders. However, storing sensitive information on any device carries some risk. If the phone is stolen, the device is compromised, or malware is installed, sensitive documents could be accessed. Consider using secure document storage services that require additional authentication rather than storing documents directly on your phone.
What recovery codes are and why should I save them?
Recovery codes are backup authentication codes generated when you enable two-factor authentication for an account. If you lose access to your phone or authenticator app, recovery codes allow you to regain access to your account without your primary authentication method. You should save recovery codes in a secure location separate from your phone, such as a password manager with strong encryption or a physical document stored securely. Store them in multiple locations so a single point of failure (like your password manager being compromised) doesn't result in complete lockout from all your accounts.
How often should I monitor my accounts for fraud?
Check your bank and credit card accounts at least weekly for unauthorized transactions, review your email account's login history monthly for unauthorized access attempts, check your credit report at least annually through a free service like Annual Credit Report.com, and set up alerts on all your important accounts so you're notified immediately of suspicious activity. Most fraud is easier to stop if caught within hours of occurrence, so the more frequently you monitor, the better. Setting up automatic alerts means you don't have to remember to check—you'll be notified if something suspicious happens.
What is the most important device protection step I can take right now?
Enabling two-factor authentication (preferably using an authenticator app rather than SMS) on your most important accounts is the single most impactful protection step. This prevents most common account takeover attacks even if your password is compromised. After enabling 2FA, set up fraudulent transaction alerts with your banks, keep your phone's software updated to patch security vulnerabilities, and save recovery codes for your most important accounts in a secure location. These three steps address the highest-probability, highest-impact threats and take less than an hour to implement.

Key Takeaways
- Traditional device insurance covers hardware damage (broken screens, water damage) but completely ignores digital threats (account takeover, identity fraud, financial compromise), leaving users catastrophically exposed
- The real danger of device theft is not the £800 phone—it's access to banking apps, crypto wallets, biometric data, and government IDs that criminals can weaponize within minutes of theft
- 72% of British consumers carry zero device insurance despite 64% saying they'd feel disconnected from their lives without their phones, demonstrating a dangerous protection gap
- Next-generation protection must be proactive (detecting and preventing fraud before it occurs) rather than reactive (processing claims after damage), using AI to analyze behavior patterns and flag threats instantly
- 94% of consumers prefer device protection bundled into services they already use rather than fragmented across separate policies—integration is essential for effective protection
Related Articles
- I Tested a VPN for 24 Hours. Here's What Actually Happened [2025]
- SMS Sign-In Security Flaws: The Hidden Risk Exposing Millions [2025]
- Google's War on Residential Proxies: How IPIDEA's Network Collapsed [2025]
- Are VPNs Really Safe? Security Factors to Consider [2025]
- Why Brits Fear Online Privacy But Trust the Wrong Apps [2025]
- Iran's Digital Isolation: Why VPNs May Not Survive This Crackdown [2025]
![Device Protection Beyond Hardware: Securing Your Digital Identity [2025]](https://tryrunable.com/blog/device-protection-beyond-hardware-securing-your-digital-iden/image-1-1769701304362.jpg)



