SMS Sign-In Security Flaws: The Hidden Risk Exposing Millions [2025]
You've probably clicked on one of those SMS login links a hundred times. You get a text, tap the link, and boom—you're logged in. No password to remember. No database breach to worry about. Sounds secure, right?
Wrong.
What if I told you that millions of people are using an authentication method that researchers just called out as fundamentally broken? That's not hyperbole. A major technical review examining over 33 million SMS messages discovered something deeply unsettling: the SMS login links that billions of people rely on are leaving personal data dangerously exposed, often for years.
Here's the kicker: most people have no idea this is happening. The flaws aren't always visible to users. Your bank, your email provider, your job site—they all look secure on the surface. But the underlying authentication logic is quietly hemorrhaging data.
This isn't a problem that one company created. It's systemic. It's architectural. And it affects the security infrastructure that protects your personal information across 177 different digital services that researchers managed to identify.
Let's talk about what's actually happening, why it matters, and what you can do about it right now.
TL; DR
- SMS login links are fundamentally flawed: Researchers found that 322,000+ unique URLs from 33 million SMS messages across 177 services contain critical security weaknesses
- Weak tokens = guessable links: Many services use low-entropy tokens, meaning attackers can guess valid login links by changing a few characters
- No secondary verification: Most services treat possession of an SMS link as 100% proof of identity, with no additional checks
- Long-term exposure: SMS messages can remain accessible for years after being sent, multiplying attack windows exponentially
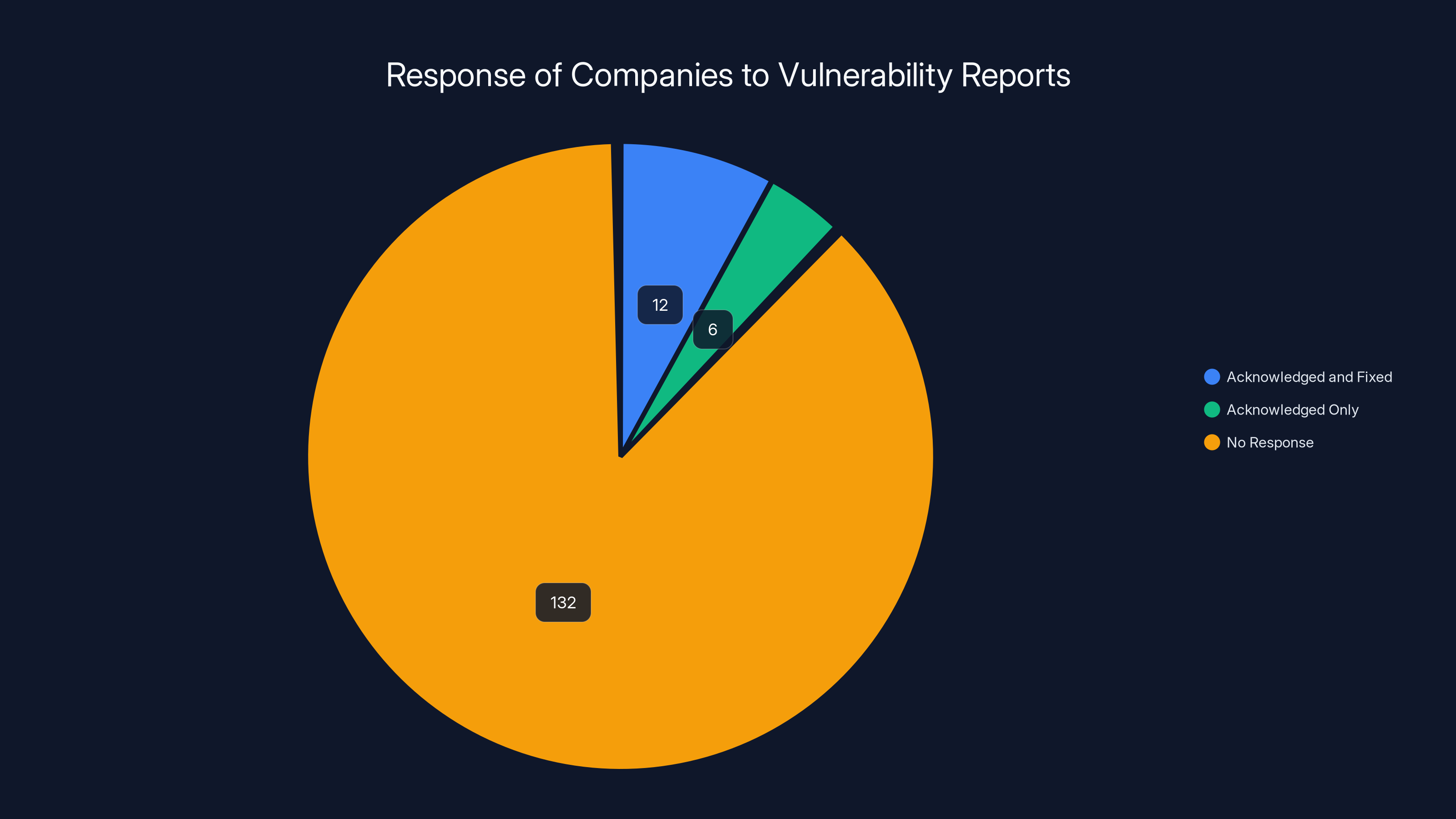
- Industry inaction: Of ~150 providers contacted, only 18 acknowledged weaknesses, and even fewer fixed them
- Your personal data is at risk: Exposed information includes dates of birth, banking details, credit records, and more

Estimated data shows an even distribution of exposed information across several categories, highlighting the comprehensive risk to personal security. Estimated data.
The Scale of the Problem: Numbers That Should Scare You
Let's start with the research itself, because the scope is enormous.
Security researchers didn't just test a handful of companies or observe a small sample of SMS messages. They analyzed 322,000 unique URLs extracted from 33 million SMS messages tied to 30,000+ phone numbers. These messages were collected from public SMS gateways—which means researchers had limited visibility into the actual scope of the problem.
Despite that limitation, they identified SMS login implementations at 177 different digital services. Some you've definitely heard of. Others you might use regularly without thinking twice. The categories included:
- Financial services and insurance platforms
- Employment and job listing websites
- Payment and transaction services
- Personal referral and networking sites
- E-commerce and retail platforms
- Ride-sharing and delivery applications
- Healthcare and medical providers
But here's what's important: that 177 figure is almost certainly a dramatic underestimate. Why? Because the researchers could only see SMS messages routed through public gateways. They had no visibility into SMS traffic from major carriers, private networks, or proprietary messaging systems.
The researchers took their findings and contacted roughly 150 providers. Only 18 of them acknowledged the vulnerabilities. Even fewer actually implemented fixes. Of those that did respond with improvements, the changes reportedly reduced exposure for tens of millions of users. But most services? Complete silence. No acknowledgment. No fixes. No public disclosure.
That's the baseline. Now let's dig into exactly what they found wrong.
The Core Vulnerability: Possession Equals Proof of Identity
Authentication systems are built on one core principle: proving you are who you claim to be. Different systems prove this in different ways.
A password system proves identity by verifying that you know a secret. A fingerprint scanner proves identity by verifying your biology. A private key system proves identity by demonstrating cryptographic possession.
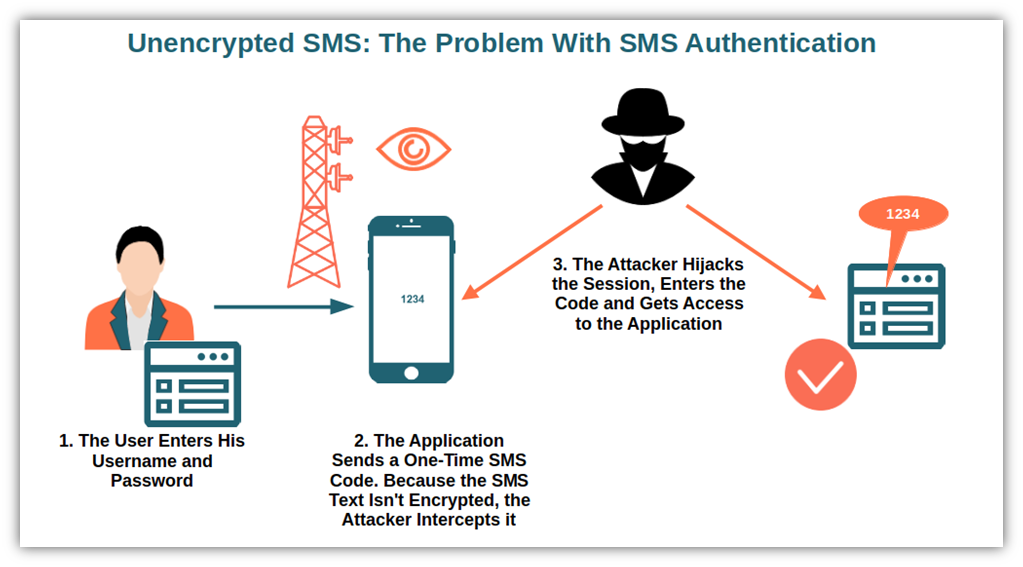
But SMS login links use a fundamentally broken model: possession of a link equals proof of identity.
Think about what that means in practice. Here's a typical flow:
- You visit a website and enter your email address
- The system sends you an SMS with a unique URL
- You click the URL
- You're logged in
The vulnerability is hiding in step 4. The system assumes that because you have the URL, you must be the legitimate account owner. But that assumption falls apart instantly once you realize:
- SMS is unencrypted: Your carrier, ISPs, network administrators—they can all see your text messages in plain text
- URLs get logged everywhere: Your phone logs it. Your carrier logs it. The receiving website logs it. Any admin with server access can see it
- URLs get shared: People forward authentication links to colleagues, save them in emails, store them in chat history, screenshot them
- URLs persist indefinitely: A link sent to you today might remain accessible for years
So here's the attack surface: If someone gets their hands on your SMS login link, they have complete account access. No follow-up verification needed. No secondary challenge. Nothing.
The researchers found something even worse.
Only 12% of companies acknowledged vulnerabilities, and even fewer fixed them. The majority provided no response, highlighting a significant issue in industry transparency and accountability.
The Guessing Problem: Low-Entropy Tokens
When you click an SMS login link, what you're actually clicking is a URL that contains a token. That token is supposed to be unique and unpredictable. It's the only thing protecting someone else from accessing your account.
The researchers analyzed the tokens embedded in 322,000 login URLs. What they discovered should have made security teams lose sleep:
125 services used tokens with low entropy.
What does that mean? It means the tokens weren't truly random. They were predictable. They followed patterns. And most critically: attackers could guess valid tokens by systematically trying variations.
Imagine a token that looks like this: auth-12345-abcd. An attacker doesn't need to know your exact token. They can script something like:
auth-12345-abca
auth-12345-abcb
auth-12345-abcc
auth-12345-abcd ← BINGO, this one works
With enough computing power, they can test thousands or millions of combinations per second. Some of those combinations will be valid. Some will grant access to other users' accounts.
This is a numbers game, and the attackers have computational advantage. The more weak tokens in circulation, the easier the guessing becomes. The longer tokens remain valid, the longer the attack window stays open.
Researchers demonstrated this wasn't theoretical. They showed it was actually happening.
The scariest part? This isn't a sophisticated attack. It doesn't require zero-day exploits or insider access. It just requires:
- A list of valid URLs (scraped from email, forwarded messages, etc.)
- Basic pattern recognition
- Automated request tools
- A connection to the internet
Any moderately skilled person could execute this attack. Any motivated script kiddie could automate it. And any competent security team at a service provider should have caught it in basic security testing.
Yet 125 services didn't.
Information Overfetching: The Accidental Data Exposure
Here's a vulnerability that's almost comical in how obvious it is, yet how widespread.
When you click a login link and get authenticated, the system needs to load your account information. But what data should it actually retrieve?
Only the minimum necessary. That's security 101.
But the researchers found massive mismatches between what the visible interface showed and what the backend was actually pulling.
Example: You click your SMS login link and arrive at a page that shows your name and email. But behind the scenes, the system is also retrieving:
- Your date of birth
- Your linked bank account details
- Your credit history references
- Your stored payment methods
- Your previous login locations
- Your full address history
Why? Often because:
- Lazy API design: The backend doesn't have fine-grained data controls. It retrieves entire user objects instead of specific fields
- Over-engineered systems: Developers pull everything "just in case" other pages might need it later
- No data minimization reviews: Nobody actually audits what data flows from backend to frontend
- Caching layers: API responses get cached and served to multiple endpoints without filtering
The consequence: If anyone intercepts your login request, views your network traffic, or accesses the service's logs, they don't just see "user logged in." They see your full profile data.
This violates a core principle called principle of least privilege. You should only get access to the minimum data necessary to accomplish your task. Anything else is unnecessary exposure.

The Unencrypted Foundation: SMS as a Security Protocol
Let's be brutally honest: SMS was never designed for security.
The Short Message Service protocol was created in 1992 as a way to send text messages over GSM networks. It was built when internet security wasn't even a concept. The protocol has zero encryption. Zero authentication. Zero integrity checks.
It's the technological equivalent of sending your passwords on a postcard through the mail. Except worse, because everyone at the post office can photocopy it.
Here's what happens to your SMS login link:
At the sending point: Your carrier's system generates the SMS and prepares to send it. Every person at that carrier who works with billing systems, infrastructure teams, or support staff can technically access it.
In transit: The message travels across radio waves and network infrastructure. Network sniffers (especially on non-encrypted Wi-Fi) can capture it. Advanced attackers with cellular infrastructure knowledge can intercept it.
At the receiving point: Your phone receives it unencrypted. Anyone who gains access to your phone can see it. Malware can exfiltrate it. If you're using an older phone without full storage encryption, it's stored in plain text.
In storage: SMS messages remain on your phone indefinitely. Your carrier stores backups. Cloud backups might include SMS. If your phone is lost, stolen, or seized, every login link you ever received is accessible.
Historical access: Unlike digital credentials that expire, SMS messages can be retrieved months or years later. A backup restored from an old cloud account. A phone kept in a drawer that still contains years of messages. A carrier's legacy system still holding old data.
Security researcher Bruce Schneier famously said: "Never trust anything that has a name in the title." If SMS authentication was called what it actually is—"sending secrets in plaintext over cellular networks"—would anyone use it?
The fact that billions of accounts rely on this is a massive, systemic failure of the technology industry.

Authentication apps and push notifications offer higher security compared to SMS login. Estimated data based on typical security assessments.
The Time Factor: Why Old Links Are a Persistent Threat
Most secure authentication tokens have expiration times. You log in today, your token is valid for 30 minutes, then it self-destructs. This limits the damage if the token gets compromised.
But the researchers found something alarming: many SMS login links never expire. Or they expire so slowly that they remain valid for months or years.
Why is this catastrophic?
Let's say a researcher captured an SMS login link in January 2024. According to their findings, there's a decent chance that same link still works in January 2025. Maybe even January 2026.
Now think about all the ways a link could be exposed:
- Email forwarding: Someone forwards you a link, and it lands in email backups
- Screenshots: Someone takes a screenshot and saves it to cloud storage
- Chat history: You paste it in Slack, Discord, or Teams, and it's in the permanent chat log
- Browser history: Your browser keeps a searchable cache of every URL you've visited
- Cloud sync: If you use a password manager or browser sync, that link gets stored in cloud backups
- Device sharing: A family member borrows your phone and can see old SMS messages
- Data breaches: Your phone manufacturer's cloud backup gets breached
Each of these scenarios creates a copy of your login link. And if that link is valid for a year, each copy remains a potential access vector for 365 days.
The math is brutal: if someone has 100 captured links and each has a 50% chance of still being valid after 6 months, they have 50 active access vectors. If each service takes 6 months to notice suspicious access, the attacker has already compromised thousands of accounts before remediation happens.
This is called extended attack surface expansion, and it's one of the reasons cryptographic tokens are supposed to expire. But SMS login implementations often skip this entirely.
Real-World Attack Scenarios: How This Breaks in Practice
Theory is interesting, but what does actual exploitation look like?
Scenario 1: The Shared Device
Your spouse uses your phone to check something while you're in the shower. They scroll through SMS messages and accidentally see an active login link from your banking app. Now they have temporary access to your financial accounts. Even if they don't use it maliciously, they know how easy it would have been. And if your phone gets stolen later, that same link (if still valid) could grant a criminal access to your bank account.
Scenario 2: The Recovered Phone
You buy a used smartphone from a refurbishment program. The previous owner didn't wipe it properly. You recover the phone's old SMS messages. In those messages are login links to various services. You're curious—you click one. It works. You just gained access to someone else's account.
This isn't theoretical. People have admitted to accidentally accessing previous owners' accounts through exactly this vulnerability.
Scenario 3: The Workplace Breach
A company offers SMS login to employees for their benefits portal. An insider (or a hacker who compromised the company's systems) pulls SMS messages from backup logs. They now have valid login links to hundreds of employee accounts. These links remain valid for 90 days. The attacker can slowly access employee personal information—addresses, dependent names, Social Security Numbers—for weeks before anyone notices.
Scenario 4: The Malware Exfiltration
You download what you think is a legitimate app. It's actually malware. The malware's primary job: read all SMS messages on your phone and send them to a command server. Every login link you receive gets exfiltrated. The attacker now has a collection of valid links. They use them to mass access accounts across multiple services.
Scenario 5: The Cloud Backup Breach
You use Samsung Cloud, Google One, or i Cloud backup on your phone. Your backup credentials get compromised (or you used a weak password). An attacker can restore your entire phone backup, including all SMS messages, all login links, everything. They now have months of authentication vectors.
Each of these scenarios is uncomfortably plausible. None require sophisticated hacking. None require zero-day exploits.
Why Companies Keep Using SMS Despite the Risks
Here's the frustrating part: security teams at these companies almost certainly know about these vulnerabilities.
So why do 177+ services continue using SMS-based authentication?
Reason 1: User Experience Wins
Password-based login is annoying. You have to remember your password. You have to type it. You have to manage password reset flows. SMS login is faster. One tap and you're in.
Companies optimize for user experience because users abandon services that are difficult to use. Friction kills engagement. So even though SMS is less secure, it gets adopted because it feels better.
Reason 2: Database Breach Prevention
When you don't store passwords, you can't have a password database breach. Every major company has been breached. So companies reasoned: "Let's not store passwords at all." SMS became the solution.
But they traded one risk (password database breach) for another (SMS interception and reuse). It's not clear they made the better choice.
Reason 3: Regulatory Checkbox Thinking
Companies in regulated industries (finance, healthcare) face requirements for "strong authentication." Many regulations specifically call out SMS as a valid strong authentication method (even though it's not particularly strong).
So companies implement SMS because it satisfies regulatory requirements, regardless of actual security.
Reason 4: Cost Efficiency
Implementing proper authentication (OAuth, SAML, cryptographic tokens) requires expertise and infrastructure investment. SMS is cheap. You pay per message. You integrate a basic SMS gateway. Done.
Most companies would rather pay SMS gateway costs than invest in security architecture.
Reason 5: Legacy Systems
Once a company deploys SMS authentication to millions of users, switching costs become enormous. Users expect SMS login. Changing it means migrating users, handling legacy sessions, managing backward compatibility.
So instead of fixing the underlying issue, companies just leave it in place. Maybe they add SMS as a second factor (somewhat better). But they rarely remove it entirely.
The result: A security vulnerability becomes entrenched infrastructure that nobody wants to change, even though everyone knows it's broken.

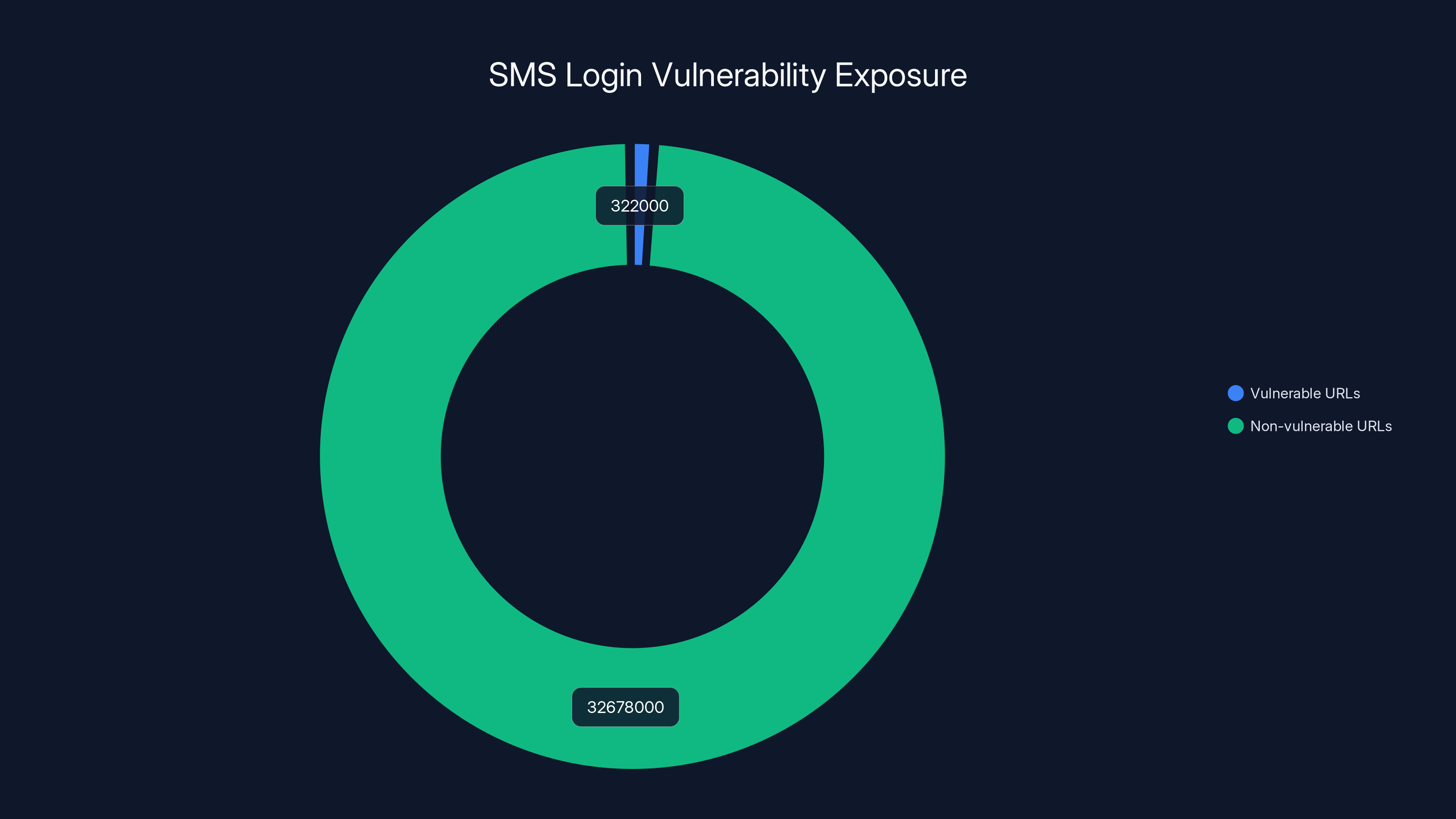
Research found 322,000 unique URLs with vulnerabilities out of 33 million SMS messages, highlighting significant exposure risk. Estimated data.
The Research Methodology: How They Found This
Understanding how researchers discovered this helps clarify why it's actually a bigger problem than it appears.
The study involved:
Phase 1: SMS Collection Researchers set up monitoring on public SMS gateways. These are services that forward SMS messages. By monitoring what passes through, they collected 33 million SMS messages without identifying users (privacy-preserving data collection).
From those 33 million messages, they extracted 322,000 unique URLs that appeared to be authentication links.
Phase 2: URL Analysis They analyzed the structure of these URLs, looking for patterns:
- Token entropy (how random the authentication codes were)
- Token length and complexity
- URL structure and consistency
- Reusability patterns
- Service identification
Phase 3: Testing For a subset of URLs, they tested whether the authentication links still worked days, weeks, or months after being sent. They didn't misuse access—they just verified that long-expired links were still functional.
Phase 4: Scope Mapping They identified which services were behind the URLs and categorized them by industry and sensitivity level.
Phase 5: Responsible Disclosure They contacted 150+ service providers with findings. They documented which ones responded, which ones acknowledged vulnerabilities, and which ones fixed issues.
The key limitation: This is all passive observation through public SMS gateways. The actual scope is much larger. Private carriers and proprietary messaging systems have far more SMS traffic. The vulnerabilities are worse than what this study could measure.
It's like measuring crime by only looking at reports from one neighborhood. The actual problem is bigger everywhere.
Data Exposed: What Information Was at Risk
When researchers accessed accounts using weak SMS login links, what personal information was vulnerable?
The findings were comprehensive and disturbing:
Financial & Banking Data:
- Bank account numbers
- Routing information
- Transaction history
- Credit card details
- Loan information
Personal Identification:
- Full legal names
- Dates of birth
- Social Security Numbers (in some cases)
- Driver's license information
- Passport details
Address & Location:
- Current residential address
- Previous address history (5-10 years)
- Workplace addresses
- GPS location history (in some cases)
Financial History:
- Credit scores
- Credit reports
- Bankruptcy records
- Debt information
- Payment history
Employment Data:
- Current and previous employers
- Job titles
- Salary ranges
- Employment history
Family & Relationships:
- Spouse/partner information
- Children's names and birthdates
- Dependent information
- Emergency contact details
This isn't just "your email was exposed." This is the type of information that enables identity theft, financial fraud, and targeted social engineering.
Once someone has this information, they can:
- Open fraudulent accounts in your name
- Access your existing accounts and change credentials
- Social engineer other services using your personal details
- Sell your information to other criminals
- Commit long-term identity theft
- Use your information for blackmail

Why Traditional Defenses Don't Work
You might think: "Okay, I'll just use strong passwords and firewall protection and I'll be fine."
Nope. This is exactly where SMS vulnerabilities are insidious.
Firewalls Can't Help
Your firewall blocks suspicious traffic. But once you click an SMS login link from your phone, you've explicitly authenticated. The traffic looks legitimate. Your firewall has no reason to block it.
Antivirus Can't Help
Your antivirus prevents malware. But clicking a valid login link isn't malware. The service intentionally wants you to click it. Antivirus can't distinguish between a legitimate link and one that was intercepted.
Password Managers Can't Help
Your password manager stores strong, unique passwords. But SMS login doesn't use passwords. It bypasses password managers entirely. Password managers are irrelevant.
2FA Can't Help
You might think: "I'll add two-factor authentication." But if the service uses SMS for authentication, and then you also use SMS for 2FA (which many companies do), you've just doubled down on the same broken technology.
Identity Theft Protection Can't Help
Services like Life Lock monitor your credit for fraudulent activity. But they typically only alert you after fraud has started. And their entire model assumes you'll know your credentials were stolen.
With SMS login vulnerabilities, you might not know. Your account could be accessed for months without triggering any alerts—depending on what the attacker does.
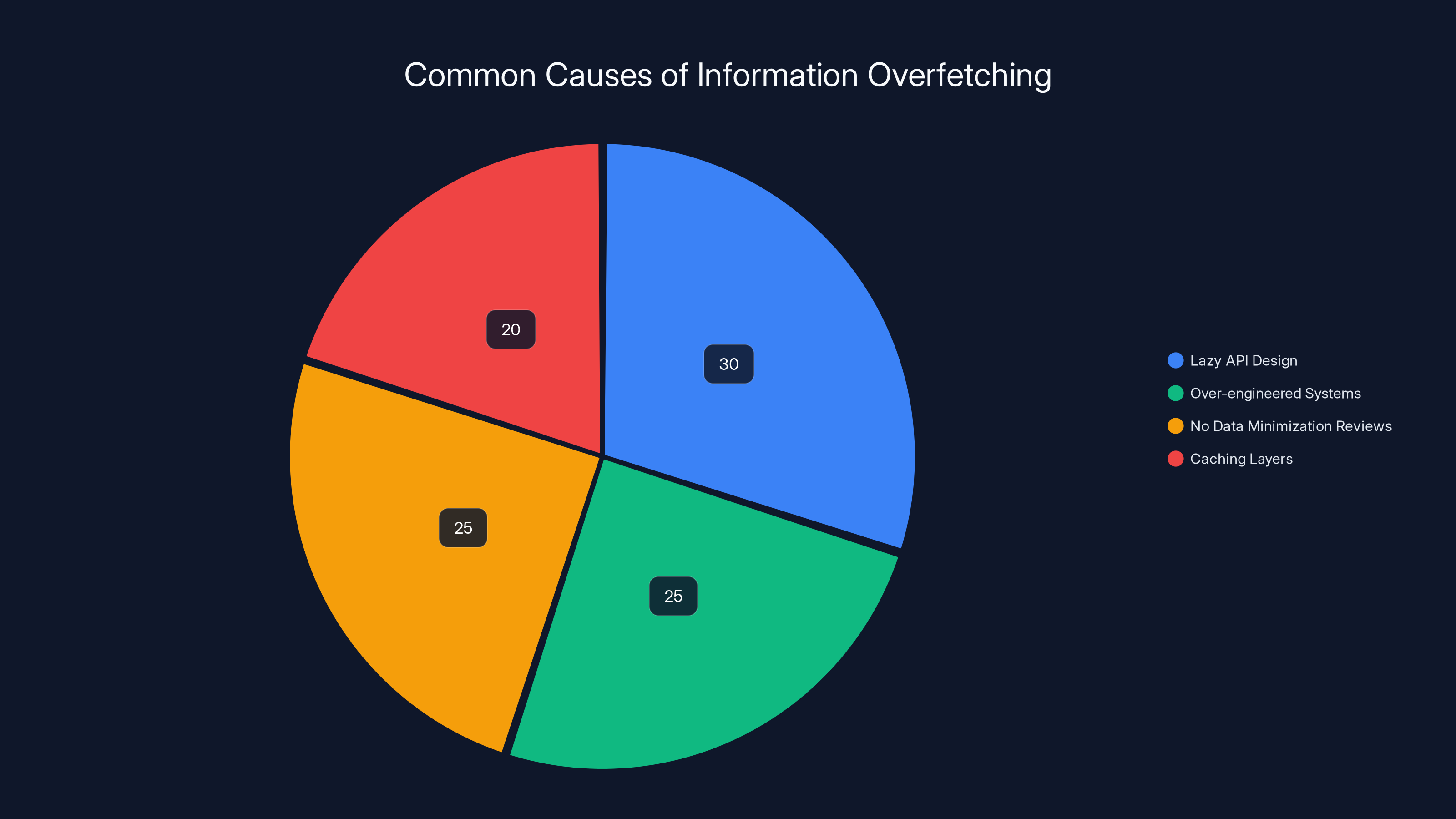
Lazy API design is the most common cause of information overfetching, accounting for 30% of cases. Estimated data.
The Industry Response: Inaction and Silence
Here's what should have happened:
- Researchers discovered vulnerabilities
- Researchers notified affected companies with details
- Companies implemented fixes within 90 days
- Vulnerabilities were patched
- Industry learned lessons and improved practices
Here's what actually happened:
Researchers contacted approximately 150 service providers with their findings. The contact explained the vulnerability, provided proof of concept, and offered recommendations for fixing it.
Out of 150 companies:
- 18 acknowledged the vulnerability (12% response rate)
- Fewer than 18 actually fixed it
- Most provided no response whatsoever
For the companies that did respond and fix issues, the fixes supposedly reduced exposure for tens of millions of users. But there's no public disclosure. No transparency. No explanation of what was fixed or how.
This is the norm in the tech industry: vulnerability researchers discover problems, contact companies, get mostly silence, and then publish findings hoping shame will drive action.
It doesn't always work.
Why does the industry respond so poorly?
Reason 1: Security Isn't Visible
When something breaks visibly (site crashes, data is obviously lost), companies scramble to fix it. Security vulnerabilities are invisible to users. You don't notice your account is at risk. So companies treat the vulnerability as low priority.
Reason 2: Liability Concerns
When a company acknowledges a vulnerability, it creates liability. Admitting you had a security flaw means users might sue. So companies prefer silence. The vulnerability is never acknowledged. Therefore, no lawsuit.
Reason 3: No Regulatory Pressure
There's no law saying "you must respond to security researchers within 90 days." There's no fine for ignoring vulnerability reports. Without legal consequences, companies deprioritize fixing issues.
Reason 4: Resource Constraints
Maybe it's true—maybe some companies genuinely can't spare engineering resources to fix SMS vulnerabilities. But usually it's a prioritization decision, not a resource issue.

What Users Can Actually Do
Let's be realistic: you can't force companies to fix their authentication infrastructure. But you're not helpless either.
1. Choose Password Login When Available
If a service offers both SMS login and password login, use the password option. Even though it's less convenient, it's more secure. You're not transmitting your credentials in plaintext.
Yes, password databases can be breached. But at least your credentials aren't broadcast across unencrypted cellular networks.
2. Use Authentication Apps Instead of SMS
If a service offers SMS as a second factor (2FA), see if they also support authentication apps like Google Authenticator, Authy, or Microsoft Authenticator.
Authentication apps are vastly more secure because:
- They use cryptography (not plaintext)
- They're time-based (tokens expire after 30 seconds)
- They're not vulnerable to SMS interception
- They're not stored in SMS message history
3. Enable Push Notifications If Available
Some services offer push-based authentication: a notification appears on your device asking "Is this you trying to log in?" You approve or deny.
This is better than SMS because:
- It's device-bound (only works on your registered device)
- It's not stored anywhere
- It can't be forwarded or screenshotted
- It's impossible to replay
4. Check Browser Auto-Fill
If you receive an SMS login link and click it, check whether your browser auto-fills any personal information. If it does, that's unnecessary information exposure.
Clear cached data regularly.
5. Use a Privacy-Focused Phone Number
For services that absolutely require SMS login, consider using a virtual phone number service instead of your personal number.
Services like Google Voice, Twilio, or others provide disposable numbers that aren't tied to your primary identity. If those numbers get compromised, the damage is limited.
6. Delete Old SMS Login Links
Regularly delete old SMS messages from services that use SMS login. Don't keep them in your message history. Don't screenshot them. Don't forward them.
The longer you keep them, the longer they remain as potential access vectors.
7. Monitor Account Activity
For sensitive services (banking, email, financial accounts), regularly check your login activity history. Most services show you recent logins with timestamps and locations.
If you see logins you didn't make, that's immediate evidence of account compromise. Respond fast.
8. Use Unique Usernames/Emails
If you have to use SMS login, at least use unique email addresses or usernames for each service.
This limits the damage if one service's SMS infrastructure is compromised. An attacker can't use the same username across 10 services.
9. Report Vulnerabilities
If you discover that a service has an SMS vulnerability (reusable links, never-expiring tokens, data overfetching), report it to their security team.
Most companies have a security.txt or responsible disclosure policy. Use it. The more companies get pressure to fix these issues, the faster they'll fix them.
10. Vote With Your Wallet
If you have a choice between two services, and one uses SMS login while the other uses authentication apps, choose the one with better security.
Over time, if customers reward secure companies and punish insecure ones, the market incentives shift.
The Bigger Picture: SMS Authentication vs. Modern Alternatives
SMS is clearly broken as an authentication method. So what should companies use instead?
Passkeys (The Future)
Passkeys are cryptographic key pairs stored on your device. When you need to authenticate, your device uses the private key to sign a challenge. The server verifies using the public key.
Advantages:
- Cryptographically secure
- Phishing-resistant
- No secrets transmitted
- Device-bound
- Can't be intercepted
- Can't be reused
Disadvantages:
- Requires device support
- Device loss means key loss
- Older devices don't support it
Passkeys are becoming mainstream. Google, Microsoft, Apple, and industry standards bodies all support them now.
Authentication Apps (Time-Based OTP)
Google Authenticator, Authy, and similar apps generate time-based one-time passwords.
Advantages:
- Cryptographically secure
- Device-bound
- 30-second token lifespan
- Works on any device with an app
- Can't be intercepted over networks
Disadvantages:
- User has to manually enter code (friction)
- Requires backup codes if device is lost
- Vulnerable to malware on the device itself
Biometric Authentication
Fingerprint, face recognition, or other biometric factors.
Advantages:
- User-friendly
- Device-bound
- Hard to fake
- No transmissible credentials
Disadvantages:
- Varies by device capability
- Can be spoofed with sufficient effort
- Privacy concerns
Hardware Security Keys
Physical keys (like Yubi Key) that use cryptographic protocols.
Advantages:
- Extremely secure
- Phishing-resistant
- Can't be hacked remotely
- Industry standard for high-security applications
Disadvantages:
- Requires physical key (can be lost)
- User has to carry it
- Higher cost
- Not practical for billions of users
OAuth/OIDC (Federated Identity)
Using your existing Google, Apple, or Microsoft account to authenticate to other services.
Advantages:
- Single sign-on
- Cryptographically secure
- Leverages platforms with strong security
- No repeated credentials
Disadvantages:
- Depends on identity provider's security
- Privacy concerns with data sharing
- Requires third-party accounts
The consensus among security experts: passkeys are the future, authentication apps are the present-day standard, SMS is the unsafe legacy.
Companies that still rely primarily on SMS authentication are literally using security architecture from decades ago.
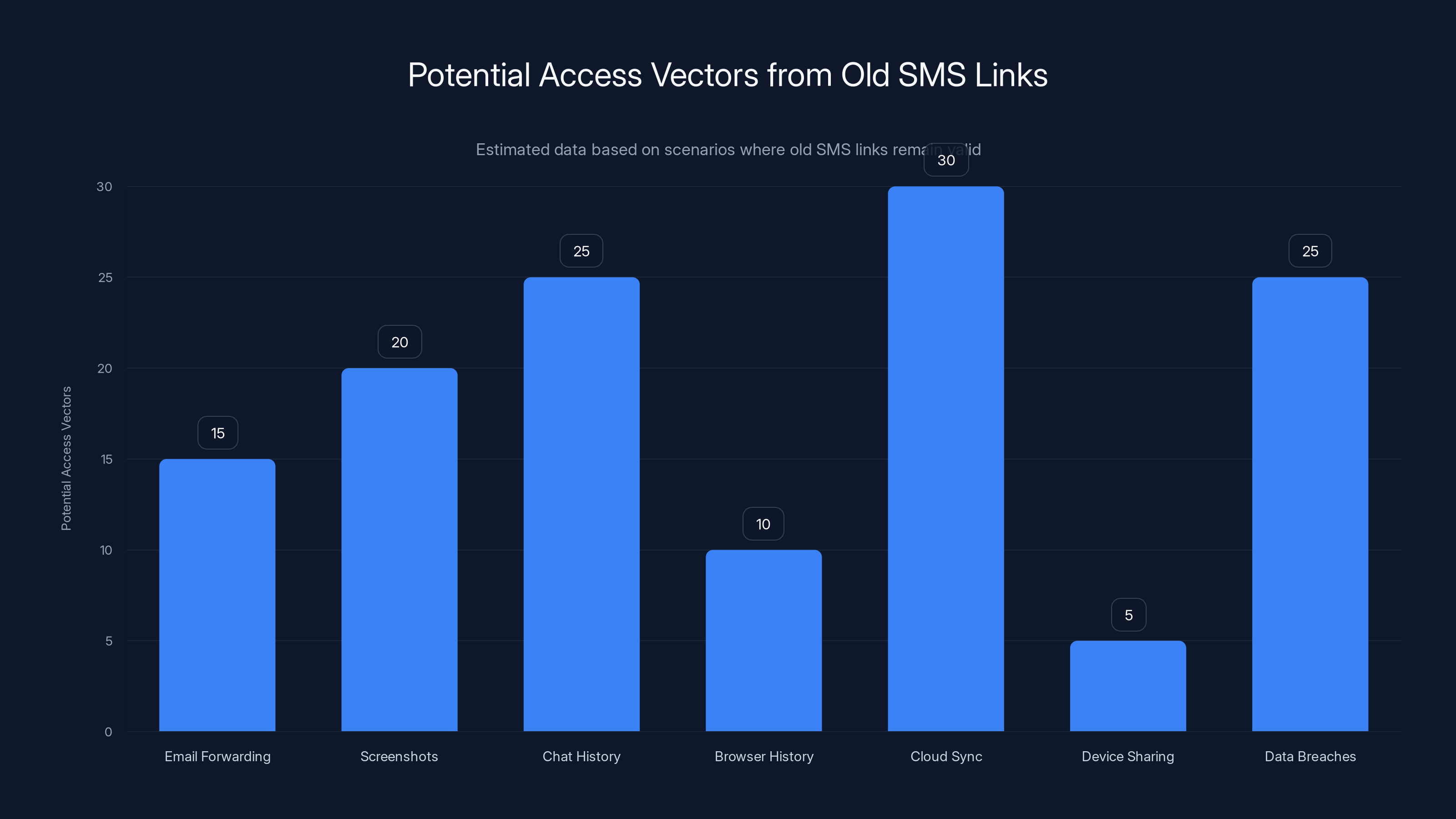
Estimated data shows that cloud sync and chat history are major contributors to potential access vectors from old SMS links, highlighting the importance of timely expiration.
Timeline: How Long Has This Been Known?
Here's what might surprise you: SMS authentication vulnerabilities aren't new. They're not even recent.
2011: Researchers first documented widespread SMS interception vulnerabilities, particularly through cellular network attacks.
2016: NIST (National Institute of Standards and Technology) officially downgraded SMS as a second factor to the lowest security tier in their authentication guidelines.
2018: Multiple security conferences published papers on SMS-based authentication weaknesses, including token predictability and message reuse.
2020: Cybersecurity agencies began warning enterprises about SMS vulnerabilities in their official guidance.
2023-2024: The recent major research study examined 33 million SMS messages and found that vulnerabilities persist at scale, with little improvement in the intervening years.
So we're not talking about a new discovery. We're talking about vulnerabilities that have been publicly documented for over a decade, yet persist at massive scale.
That's not a technical problem anymore. That's an institutional failure.
Regulatory Pressure: Are Things Changing?
Governments and regulators are slowly waking up to the problem.
NIST Updates (US)
The National Institute of Standards and Technology, which sets authentication standards for US federal agencies and influences private sector practice, has: n- Downgraded SMS OTP to the lowest security tier
- Recommended phasing out SMS for authentication
- Promoted passkeys and biometrics
But these are recommendations, not requirements. And federal agencies move slowly.
PSD2 (European Union)
The Payment Services Directive 2 requires "strong customer authentication" for financial transactions in Europe. Some implementations interpreted this as SMS being acceptable.
But regulators are now clarifying that SMS alone is insufficient. Regulations are tightening.
GDPR (European Union)
The General Data Protection Regulation doesn't specifically ban SMS authentication, but it does require companies to implement "security appropriate to the risk."
Increasing data breaches and known SMS vulnerabilities are raising the bar for what's "appropriate."
China's Personal Information Protection Law
Similar to GDPR, it requires appropriate security measures. Regulators are likely to challenge SMS-only authentication.
California Consumer Privacy Act (CCPA)
While not specifically addressing authentication, it holds companies liable for inadequate security. Continued reliance on SMS despite known vulnerabilities could be seen as negligence.
The regulatory trend is clear: SMS authentication is increasingly becoming seen as inadequate.
But regulatory change is slow. Enforcement is slower. And companies often respond by making minimal changes just enough to satisfy current regulations, rather than actually improving security.

What Companies Are (Slowly) Changing
Some companies have responded to pressure and begun shifting away from SMS authentication.
Google In 2024, Google announced they're pushing users away from SMS-based 2FA toward:
- Google Authenticator app
- Hardware security keys
- Biometric authentication
- Passkeys
Their reasoning: SMS is easier for users but less secure for accounts at risk.
Microsoft Microsoft has made push notifications their preferred 2FA method (over SMS) and has been promoting passkey adoption aggressively.
Apple Apple's focus on device-based authentication and biometrics means they've de-emphasized SMS in their ecosystem.
Financial Institutions Some banks have begun moving away from SMS-only authentication toward:
- App-based authentication
- Biometric verification
- Hardware tokens
But this varies dramatically by institution. Community banks and credit unions often still rely on SMS.
The key pattern: Large, sophisticated companies with strong security practices are moving away from SMS. Smaller and less-resourced companies stay with SMS because it's cheap and requires less development.
This creates a troubling security landscape where less-secure companies serve less-protected populations.
The Psychology: Why We Click Without Thinking
Ultimately, SMS login succeeds because of user psychology more than technology.
When you receive an SMS login link, you're in a particular mental state:
- You initiated the login: You know you asked for access, so the link feels legitimate
- You trust SMS: SMS has been around for 30 years. It feels safe and official
- You're in a hurry: You want to log in quickly. You don't stop to think about security implications
- There's no obvious warning: The link just looks like a normal text. Nothing screams "danger"
- You're not the target: Your brain assumes companies wouldn't expose security vulnerabilities. You trust that engineers thought about this
Second factor: confirmation bias. You've successfully logged in via SMS hundreds of times. Every time it worked, your brain confirmed: "SMS login works fine." You now expect it to be secure.
Third factor: invisibility. You never see the vulnerability. You never discover that your token was weak. You never find out that your personal data was overfetched. So the vulnerability remains abstract—something you intellectually know about but don't emotionally grasp.
This is why education matters. This is why articles like this exist. When users understand that SMS authentication is fundamentally broken, they might start demanding better options.

Future Outlook: Is SMS Authentication Doomed?
Predicting the future is hard, but trends suggest:
Short Term (1-2 Years): SMS authentication persists but with increasing pressure. Regulatory announcements mount. Some companies move away. Most stay put.
Medium Term (3-5 Years): Passkeys become mainstream with significant user adoption. Authentication apps remain the standard second factor. SMS gradually becomes seen as legacy.
Companies still using SMS-only authentication face customer pressure and regulatory scrutiny.
Long Term (5-10 Years): Passwordless authentication (passkeys + biometrics) becomes the norm. SMS authentication largely disappears except in legacy systems.
Regulatory requirements effectively ban SMS as a primary authentication method.
Historically, bad security practices don't die because security improves. They die because:
- Regulatory requirements change
- Customer expectations change
- Alternatives become convenient enough
- Liability pressure increases
All four are happening with SMS authentication.
Key Takeaways and Recommendations
Here's what matters:
The Threat Is Real SMS login vulnerabilities aren't theoretical. Researchers found evidence affecting 177 services and over 30,000 phone numbers. The actual scope is probably 10-100x larger.
The Exposure Is Comprehensive If someone accesses your account via a compromised SMS link, they get full visibility into your personal data: addresses, dates of birth, banking details, credit information, family relationships, employment history.
The Industry Response Is Inadequate Most companies won't fix these vulnerabilities unless forced by regulation or customer pressure.
You're Not Helpless You can:
- Prefer authentication apps over SMS
- Use password login when available
- Monitor account activity regularly
- Delete old SMS login links
- Report vulnerabilities
- Support companies with better security practices
The Future Is Passkeys Passwordless, cryptographically-secure passkeys are becoming mainstream. They solve most of the problems SMS creates.

FAQ
What exactly is an SMS sign-in vulnerability?
SMS sign-in vulnerabilities occur when authentication systems treat possession of an SMS login link as complete proof of identity, with no additional verification. These links often use weak tokens that can be guessed, remain valid for years, and contain overfetched personal data. If someone obtains your SMS login link, they have immediate access to your account and all linked personal information, making SMS-based authentication fundamentally insecure compared to modern alternatives.
How can I tell if a service I use is vulnerable?
You can't easily tell just by using a service, which is part of the problem—the vulnerability is largely invisible to users. However, you can check whether a service offers better authentication options like authentication apps, hardware keys, or biometric login. If they only offer SMS, that's a red flag. You can also check the service's security documentation or contact their security team directly if you're concerned.
Is my data already exposed if I use SMS login?
Possibly, but not necessarily. It depends on whether an attacker obtained your specific SMS login link. The research found that 322,000 unique URLs from 33 million SMS messages contained vulnerabilities, so the scope is large but not universal. However, you should assume your data is at risk if you've received multiple SMS login links from services and stored them anywhere (in cloud backups, chat history, email forwards, or phone memory).
Why do companies still use SMS if it's insecure?
Companies use SMS authentication because it's convenient for users, cheap to implement, and satisfies some regulatory requirements (even though those requirements are now outdated). Changing authentication methods at scale requires engineering resources, user migration, and backward compatibility handling. Most companies prefer to leave SMS in place rather than invest in replacement systems, even though experts have known about SMS vulnerabilities for over a decade.
What's the difference between SMS for login vs. SMS for two-factor authentication?
SMS for login means SMS is your primary authentication method—click the link and you're automatically logged in. SMS for 2FA (two-factor authentication) means you provide one factor (password or biometric) and SMS provides the second factor. SMS for 2FA is somewhat better because it requires the attacker to have both factors, but it's still vulnerable to SMS interception. The best 2FA uses authentication apps or hardware keys instead of SMS.
What should I do if I suspect my account was compromised through SMS?
If you believe your account was accessed without your permission: 1) Immediately change your password to something new and unique, 2) Enable additional authentication factors (app-based 2FA, hardware key), 3) Review recent account activity for suspicious logins or data changes, 4) Contact the service's support team and report the security breach, 5) Monitor your financial accounts and credit reports for fraudulent activity, 6) Change passwords on any other accounts that share the same credentials or email.
Are authentication apps completely secure?
Authentication apps like Google Authenticator or Authy are significantly more secure than SMS because they use cryptography, expire tokens after 30 seconds, and can't be transmitted over networks. However, they're not perfect. If your phone is compromised by malware, tokens could potentially be stolen. If you lose your phone without backup codes, you could be locked out. But for the vast majority of users, authentication apps represent a dramatic security improvement over SMS.
When will SMS login finally disappear?
Based on current trends, SMS will likely persist for another 3-5 years as companies migrate to passkeys and authentication apps, but regulatory pressure and customer expectations are accelerating the transition. Large tech companies are already pushing users away from SMS. Financial institutions are beginning to follow. By 2030, SMS-only authentication will probably be relegated to legacy systems and companies that haven't invested in security. However, complete elimination will take longer due to the massive number of deployed systems and the challenges of user migration.
Can I use SMS safely if I'm careful?
No. "Being careful" doesn't protect you from vulnerabilities built into the system itself. Even if you never share your SMS link, secure it carefully, and never forward it, you're still exposed to risks you can't control: carrier interception, cloud backup breaches, device compromise, server-side data overfetching, and token guessing attacks. The only way to be safe is to not use SMS authentication when other options are available.
What's the one thing I should do right now?
Go through your regularly-used accounts and check if they offer authentication app setup. Enable it. This single change improves your security dramatically without adding significant friction. Then delete old SMS login links from your phone. These two actions address the most acute risks from SMS-based vulnerabilities and take less than 20 minutes total.
Conclusion: The Silent Risk Under Your Nose
Here's what keeps me up about this research: it reveals a security problem that's been known for over a decade, affects hundreds of millions of people, and persists almost entirely because of institutional inertia rather than technical limitation.
We know SMS authentication is broken. Researchers published findings in 2011. NIST downgraded it in 2016. Academic papers emerged regularly. Security conferences discussed it constantly.
Yet 177+ identified services still use it. The real number is probably 10 times higher.
This isn't a problem that needs a breakthrough invention. We have better solutions today: authentication apps, hardware keys, passkeys, biometric authentication. Every major platform supports them.
The problem is purely organizational. Companies benefit from inertia. Users are resigned to SMS login. Regulatory pressure is minimal (though increasing). So nothing changes.
Meanwhile, your personal data sits in systems that treat SMS link possession as complete proof of identity. Your address, your date of birth, your banking details, your family information. All protected by a system that's fundamentally broken.
The security risk isn't invisible because of complexity. It's invisible because people haven't been educated that it exists.
Now you know it exists.
You can demand better. When you sign up for a service, ask if they offer authentication apps. When you contact support, suggest they implement passkeys. When you have a choice between two services, choose the one with better security.
Over time, if enough users demand better authentication, companies will build it.
But until that pressure arrives, SMS authentication persists. Visible only to security researchers. Silent. Dangerous. And affecting billions of accounts.
Don't be one of the people caught by surprise when your SMS-secured account gets compromised. The risk is real. The solution is straightforward. The time to act is now.

Related Articles
- EU GDPR Fines Hit €1.2bn in 2025: What You Need to Know [2025]
- Under Armour Cyberattack 2025: What 7M Users Need to Know [Guide]
- Okta SSO Under Attack: Scattered LAPSUS$ Hunters Target 100+ Firms [2025]
- WhatsApp's Strict Account Settings: What They Mean for Your Privacy [2025]
- Browser-Based Attacks Hit 95% of Enterprises [2025]
- VSCode Malicious Extensions: How 1.5M Developers Got Compromised [2025]
![SMS Sign-In Security Flaws: The Hidden Risk Exposing Millions [2025]](https://tryrunable.com/blog/sms-sign-in-security-flaws-the-hidden-risk-exposing-millions/image-1-1769555238472.jpg)



