Digital Squatting: How Hackers Target Brand Domains [2025]
Last month, someone tried to buy what they thought was a premium proxy service. The website looked legitimate, the SSL certificate was there, the copy was nearly identical to the real thing. They bought a plan, uploaded their credentials, and disappeared into what turned out to be a fake. The company they thought they were buying from? They had no idea the scam existed until the customer support inquiry came through.
This isn't an edge case anymore. It's becoming the standard playbook.
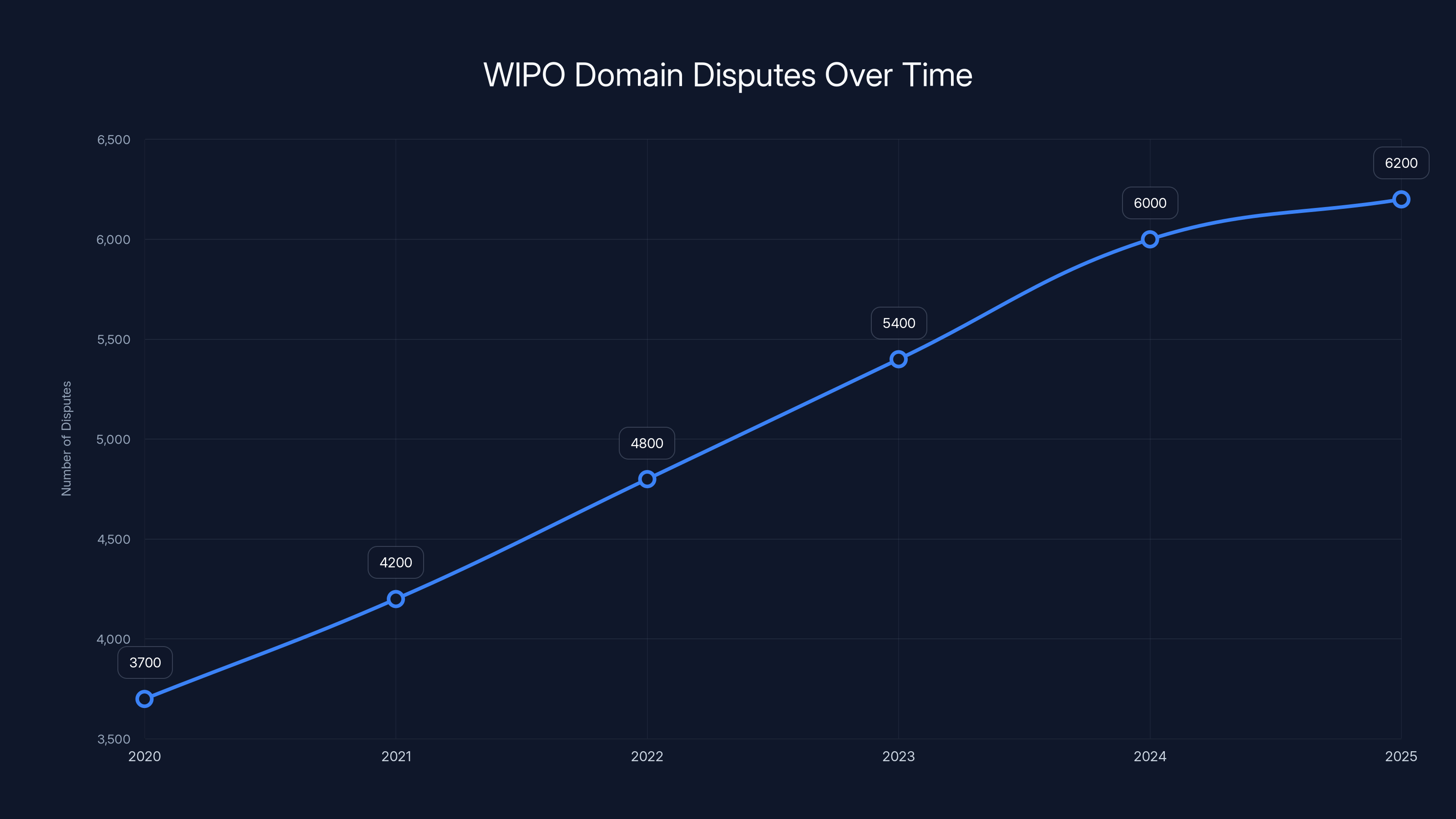
Digital squatting, the practice of registering domains that mimic legitimate brands to deceive users, has exploded into a full-blown crisis. According to recent data from the World Intellectual Property Organization (WIPO), there were 6,200 domain name disputes filed in 2025 alone, the highest number in the organization's history. That's a 68% increase since 2020. Real companies are getting impersonated at scale, customers are losing money, and the infrastructure supporting these scams is becoming more sophisticated by the week.
What's alarming isn't just the volume. It's the technique. Hackers aren't just slapping a hyphen in the wrong place anymore. They're using homograph attacks, combosquatting, international domain variations, and TLD (top-level domain) exploitation to create near-perfect replicas that fool both users and, sometimes, search engines.
This guide breaks down exactly what digital squatting is, how it works, why it's accelerating, and most importantly, what businesses can do to defend themselves. Because here's the reality: if you haven't registered the domain variations of your brand yet, someone else might be planning to.
TL; DR
- Digital squatting is exploding: 6,200 WIPO domain disputes in 2025, up 68% since 2020, with brands losing millions annually
- Tactics are evolving: Typosquatting, combosquatting, homograph attacks, and international TLD variations make impersonation harder to detect
- The impact is severe: Customers lose money, brands lose reputation, and trust becomes currency that's hard to rebuild
- Prevention beats remediation: Registering domain variations, monitoring DNS, and educating users is far cheaper than recovering from a breach
- Legal options exist but move slowly: WIPO dispute procedures work, but they take time and resources that most small companies don't have
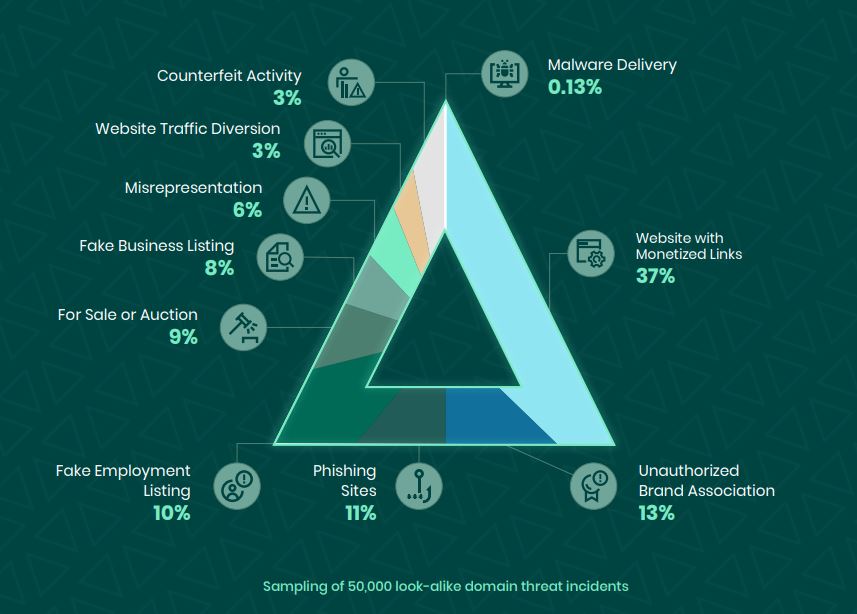
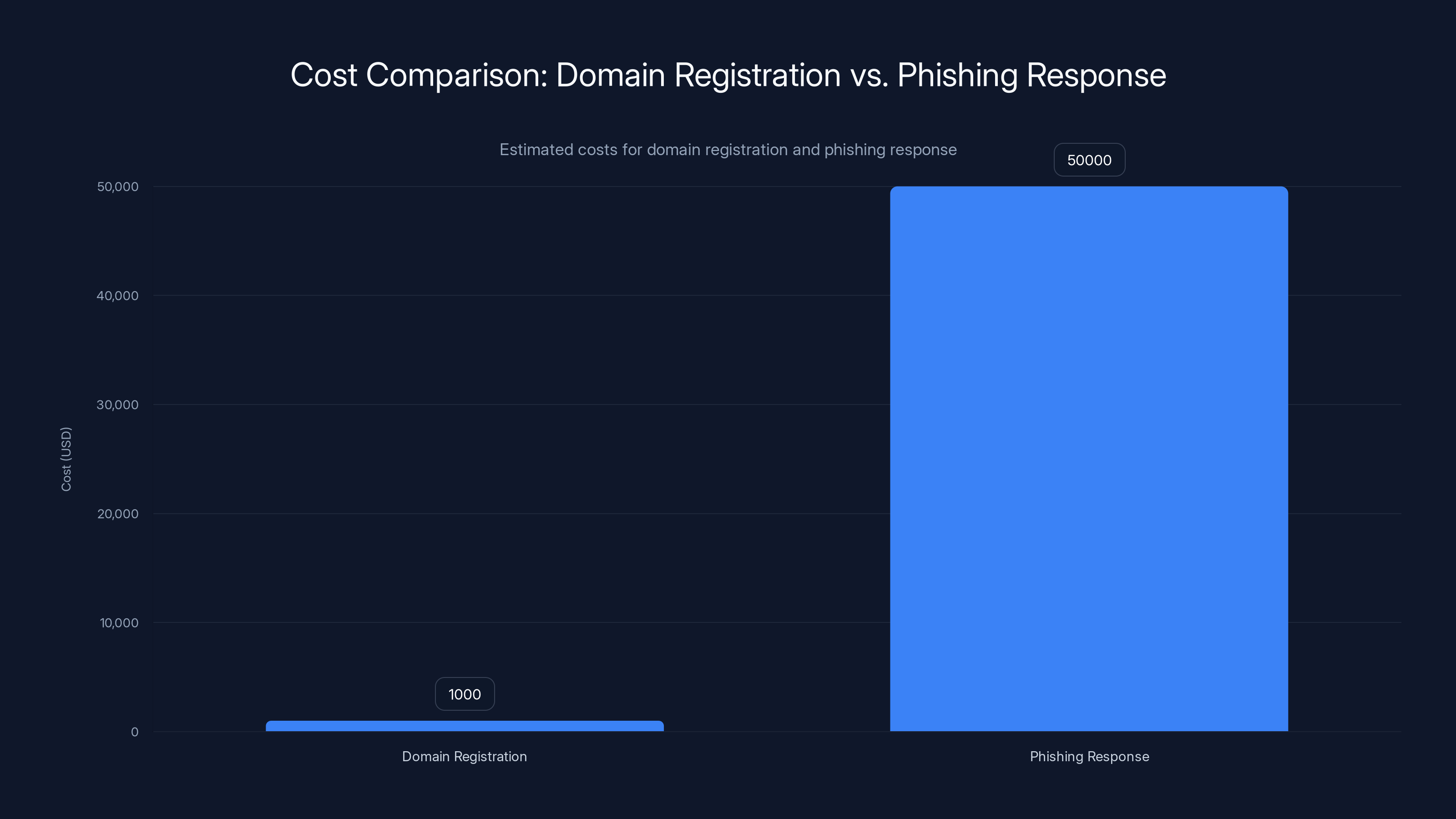
Registering domain variations is a cost-effective strategy, with prevention costs being significantly lower than the potential costs of responding to a phishing campaign. Estimated data.
What Is Digital Squatting and Why Does It Matter Now?
Digital squatting isn't new. The concept dates back to the early 2000s when domain registration exploded and became cheap enough for anyone to grab valuable web real estate. But calling it "squatting" undersells what's happening today. Squatting implies passive ownership. What we're seeing now is active, organized, profit-driven impersonation.
The practice has evolved from simple typosquatting (registering misspellings like "gooogle.com") into a sophisticated ecosystem. Hackers now use these domains to:
- Harvest login credentials through phishing pages
- Distribute malware or ransomware
- Sell fake services and collect payment
- Damage brand reputation through association with illegal content
- Generate ad revenue by ranking these domains in search results
- Redirect traffic to competitors or adult sites
What changed? Three things. First, the sophistication of tools available to attackers has skyrocketed. You can spin up a convincing fake website in under an hour using legitimate website builders. Second, the ROI on these attacks is genuinely attractive. A single successful phishing campaign against a company's customer base can net tens of thousands of dollars before anyone notices. Third, enforcement has lagged dramatically. WIPO can dispute domains, but the process takes months, and by then, the damage is already done.
The reason this matters now is volume and impact. When digital squatting was rare, companies could ignore it. Now? A mid-size Saa S company might have 15 or 20 fake domains registered against them at any given time. A large enterprise could have hundreds. The cumulative damage to brand trust, customer safety, and revenue is no longer theoretical.

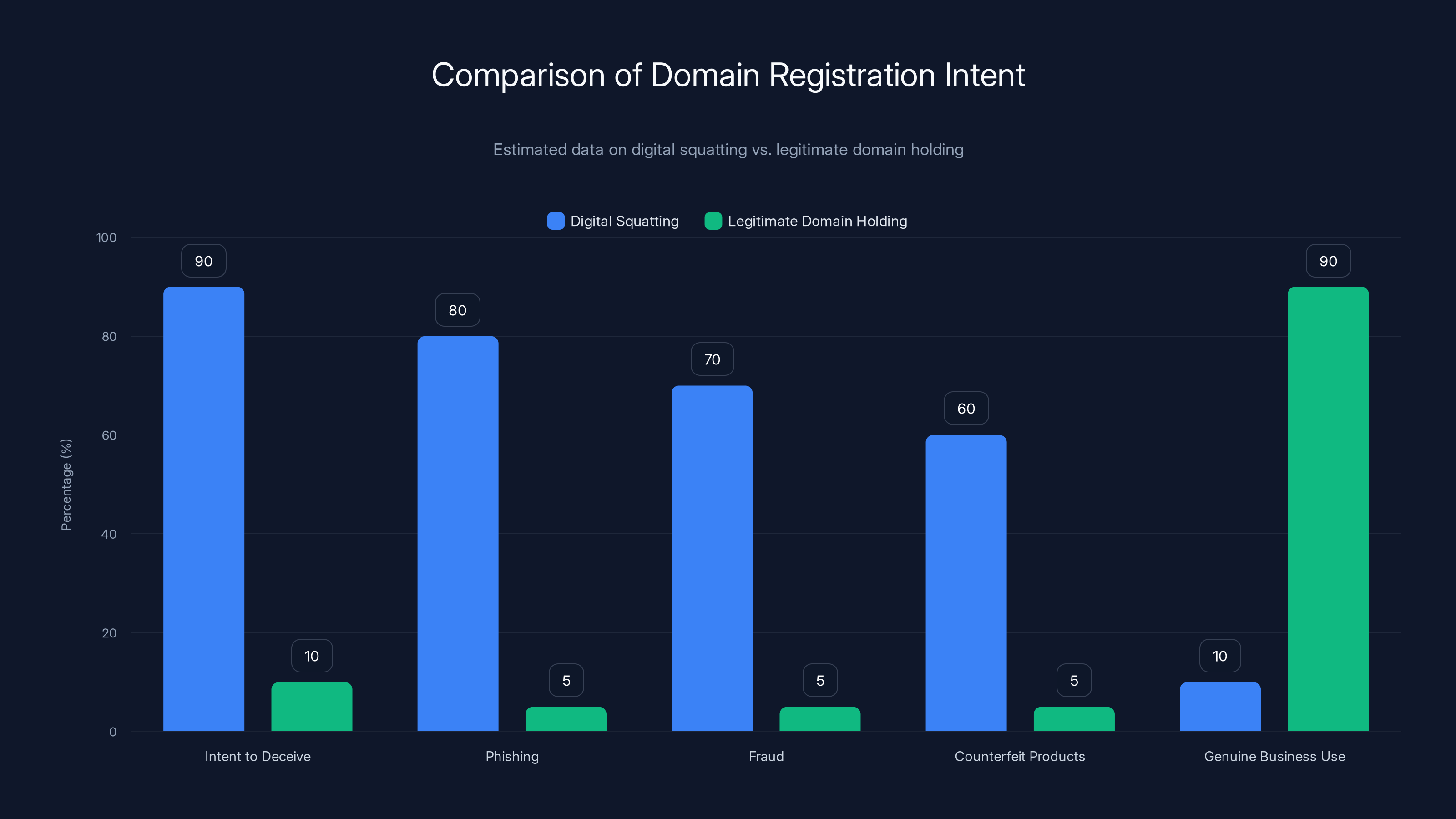
Digital squatting is primarily driven by malicious intents such as deception and fraud, whereas legitimate domain holding is focused on genuine business use. Estimated data.
The Rising Tide: Statistics and Trends
Let's talk numbers, because they tell the real story.
WIPO filed 6,200 domain disputes in 2025. That's not a small uptick. That's a fundamental shift in how frequently legitimate companies are being targeted. Five years ago, in 2020, that number was closer to 3,700. A 68% increase in five years means the problem is doubling faster than most cybersecurity challenges.
But WIPO disputes only capture the formal cases where companies actually go through the dispute process. The real number of impersonated domains is almost certainly 10 times higher. Most small companies never bother filing a dispute. They don't know about it, or they don't have the legal resources to pursue it.
Here's what we know from security researchers and brand protection firms:
- Crypto and fintech companies are hit hardest: These sectors lose the most money per incident because users are often transferring significant funds
- Saa S and productivity tools are second: These get targeted because they hold user credentials and payment information
- Retail and e-commerce follow: Black Friday and holiday seasons see massive spikes in fake storefronts
- Financial institutions: Banks and payment processors get impersonated constantly, though they have better detection systems
The sophistication has also increased. A decade ago, fake domains would use obviously different registrars or unencrypted connections. Now, attackers use legitimate SSL certificate providers, clean DNS configurations, and professional design templates. A user visiting a fake domain might spend 30 seconds there and genuinely believe it's the real thing.

The Main Tactics: How Digital Squatting Actually Works
Attackers use several distinct techniques. Understanding these is critical for defense.
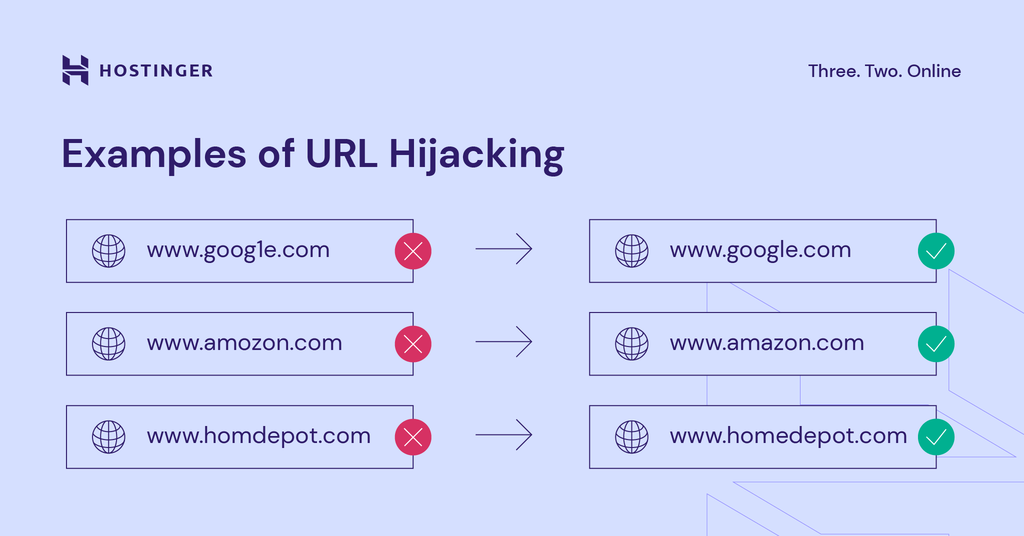
Typosquatting: The Classic Attack
Typosquatting is the oldest and still one of the most effective tactics. The attacker registers a domain that's a common misspelling of a legitimate brand.
Examples:
- Real: "spotify.com" | Fake: "spotifly.com"
- Real: "paypal.com" | Fake: "paypa 1.com" (zero vs. one, hard to see in small fonts)
- Real: "dropbox.com" | Fake: "dropbx.com"
Why does this work? Because humans type fast, and we often don't double-check URLs before hitting enter. Studies show that between 10-30% of traffic to typosquatted domains comes from accidental visitors. Of those, a percentage will interact with the page, enter credentials, or make a purchase before realizing the mistake.
The attacker then either harvests the credentials, installs malware, or redirects the user to a real site while logging their behavior for future exploit attempts.
Typosquatting is low-tech, but it's effective because it scales. An attacker can register 100 typo variations for under $1,000 and see a return within weeks.
Combosquatting: Adding Legitimacy
Combosquatting is more sophisticated. The attacker combines the legitimate brand name with other words to create a domain that looks official but isn't actually owned by the brand.
Examples:
- Real: "support.company.com" | Fake: "support-company.online"
- Real: "help.company.com" | Fake: "company-help.cloud"
- Real: "login.company.com" | Fake: "company-login.io"
What makes combosquatting dangerous is that it can fool automated security checks. The domain includes the legitimate brand name, so it might pass basic filters. A user might receive an email saying "Click here to reset your password" with a link to "company-password-reset.info" and believe it's legitimate because the brand name is right there in the URL.
Combosquatting often targets support pages, login systems, and billing pages because these are the areas where users expect to enter sensitive information.
Homograph Attacks: The Invisible Threat
Homograph attacks exploit the fact that different characters can look identical on screen. An attacker registers a domain using Unicode characters that are visually indistinguishable from standard Latin characters.
For example:
- The Cyrillic "а" (U+0430) looks identical to the Latin "a" but is a different character
- A domain registered as "g 00gle.com" (with a zero) looks like "google.com" at small sizes
When a user clicks a link or types the domain, their browser resolves it to the attacker's site, but the address bar might still show what looks like the legitimate domain. This technique is particularly effective in emails, where users don't carefully inspect links before clicking.
Homograph attacks are harder to defend against because they're technically different domains, but they appear identical. Browser vendors have added some protections, but these aren't universal.
TLD Squatting: Playing With Suffixes
TLD (top-level domain) squatting registers the brand name under a different top-level domain.
Examples:
- Real: "company.com" | Fake: "company.io", "company.cloud", "company.shop"
This works because:
- The brand might only own the .com version
- New TLDs (.cloud, .tech, .xyz, .online) are cheaper and less regulated
- Users might forget which TLD they're looking for and try alternatives
- International TLDs (.co.uk, .de, .fr) are often available even if the brand owns the primary domain
Attackers often use TLD squatting to create look-alike domains that rank in search results. A user searching for "company login" might see both the real site and a .io version and click the wrong one.
International Domain Variations: Global Reach
For global brands, attackers register variations in different countries and languages. This is particularly effective for brands that operate in multiple regions.
For instance, a company might own "company.com" but not "company.de", "company.fr", or "company.jp". An attacker can register these and create region-specific phishing pages in local languages.
These attacks are even more dangerous because they're harder for the brand to detect and monitor. A company might have automated alerts for their main domain but miss variations in other countries.
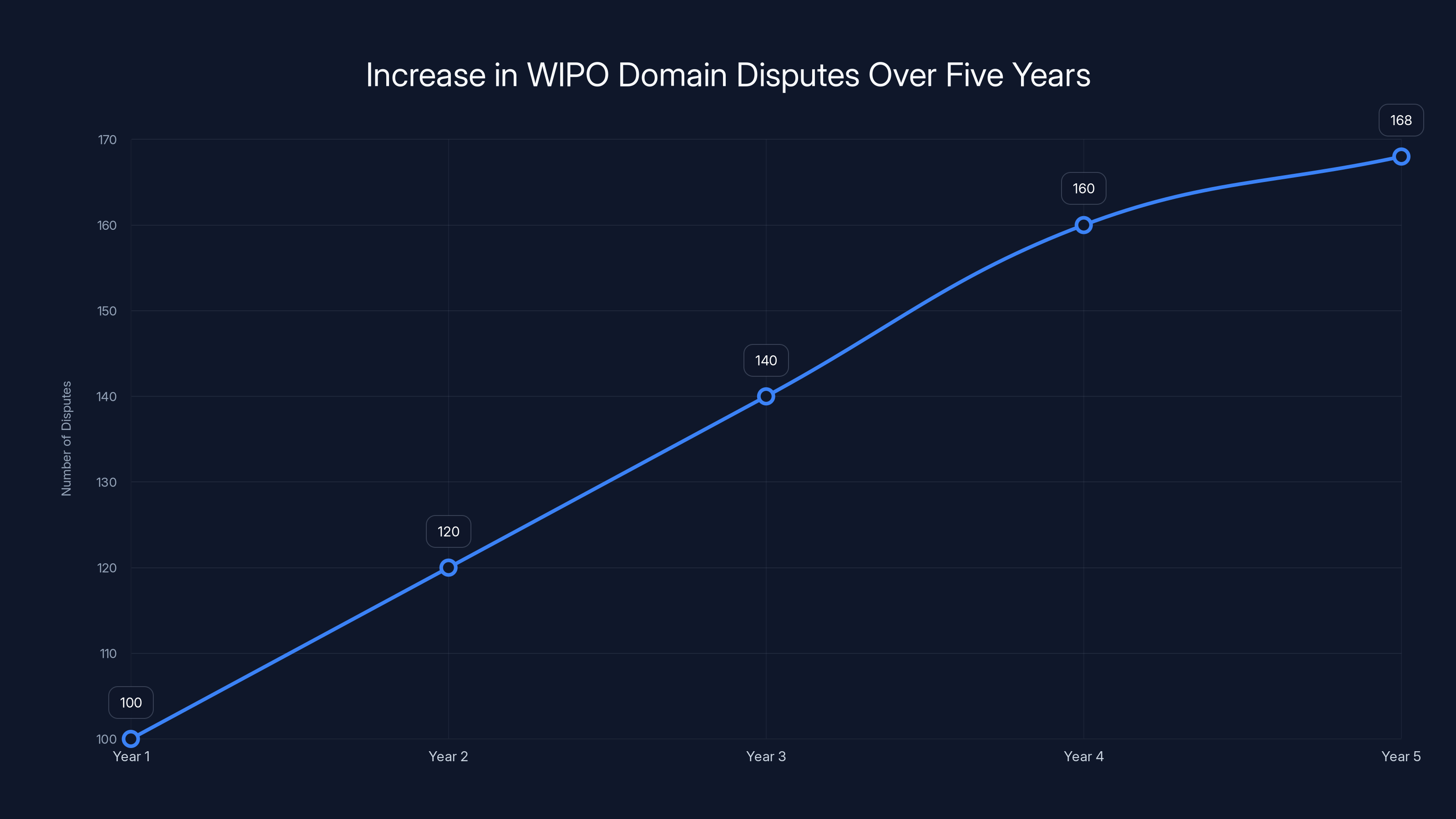
The line chart illustrates a 68% increase in WIPO domain disputes over five years, highlighting the growing threat of digital squatting. Estimated data based on reported increase.
Who Gets Hit and Why
Digital squatting doesn't affect all companies equally. Some industries and company sizes are dramatically more vulnerable.
High-Risk Industries
Cryptocurrency and blockchain: These companies face relentless squatting attacks. Why? Because users routinely transfer large sums of money, and a single successful phishing attack can result in permanent loss (blockchain transactions can't be reversed). A hacker can steal millions in a single incident.
Saa S and software platforms: These are targeted because they often hold:
- Login credentials (which can be reused on other platforms)
- Payment information and credit cards
- Sensitive data (for tools like password managers, note-taking apps, etc.)
- API keys and tokens that provide access to other systems
A single compromised account in a team productivity tool can give an attacker access to an entire organization's internal communications and files.
Financial services: Banks, payment processors, and investment platforms get hit constantly. But they generally have better security infrastructure and user education, so the attack success rate is lower than you'd expect.
E-commerce and retail: During peak shopping seasons, fake storefronts proliferate. These operate for weeks, harvest hundreds of customer payment cards, then disappear. The brand gets the chargebacks, the customers get fraud on their cards, and the attacker moves on.
Healthcare and pharmaceutical: These are targeted because they hold incredibly valuable personal health information. Fake patient portals, prescription refill sites, and pharmacy domains are common.
Company Size Vulnerability
Interestingly, small and mid-size companies are hit harder than large enterprises because:
- Large companies have dedicated brand protection teams and legal resources
- They automatically monitor domain registrations and trademark infringement
- They have relationships with domain registrars and can get domains removed quickly
- They have incident response procedures in place
Small companies often don't even know they're being impersonated. They lack the monitoring infrastructure and legal budget to fight back. A startup might lose thousands to a phishing campaign against its customers and only discover it weeks later.
The Business Impact: More Than Just Reputation
Companies often underestimate the true cost of digital squatting attacks. The damage extends far beyond immediate financial loss.
Direct Financial Impact
- Fraudulent purchases: Customers buy fake products or services and never receive them
- Credential theft: Stolen login information leads to account takeovers and follow-up attacks
- Payment fraud: Credit card information harvested from fake checkout pages
- Ransomware infections: Users who visit compromised domains and download malware
The average cost of a single credential theft incident for a company is estimated at
Reputational Damage
Customers who fall for a scam don't blame the attacker. They blame the brand. When someone buys a fake service from what they believed was your company and gets nothing, they:
- Leave negative reviews on your real company
- Post about the scam on social media, tagging your account
- File chargebacks with their credit card company
- Dispute the fraudulent charge, which damages your payment processor relationship
- Tell friends and family not to trust your brand
This ripple effect is hard to measure but easy to feel. A brand might spend years building trust, only to have it eroded by a handful of successful phishing campaigns.
Customer Trust Erosion
Trust is currency. Once a customer falls for a fake domain and loses money or information, they become skeptical of your actual domain too. They'll verify URLs more carefully, they'll be hesitant to click links in emails, and they might ultimately switch to a competitor they perceive as safer.
The cost of rebuilding trust after multiple squatting attacks far exceeds the cost of preventing the attacks in the first place.
The number of domain disputes filed with WIPO has increased by 68% from 2020 to 2025, indicating a growing challenge in domain impersonation. Estimated data.
Case Study: The Smartproxy Impersonation Campaign
Let's look at a real example: Smartproxy, a proxy service provider, became a target of a sophisticated digital squatting campaign.
Attackers registered multiple domains with slight variations:
- smartproxy.cloud (instead of smartproxy.com)
- smartprox-y.com (hyphenated)
- smartproxys.io (subtle plural variation)
They copied the entire website design, including product screenshots, pricing tables, and customer testimonials. They even created fake customer support email addresses that looked legitimate.
Customers would click on ads or search results, land on the fake site, and purchase proxy plans. They'd receive setup instructions and activation details, but when they tried to use the service, nothing worked. By then, they'd already paid.
Smartproxy's actual CEO, Vytautas Savickas, commented on the incident: "Impersonators don't just steal money. They deliver low-quality services that fall far short of what real companies provide. Every fake site makes it harder for honest businesses to earn trust and for customers to know who to rely on."
What made this campaign particularly effective:
- The fake sites ranked in search results for Smartproxy-related keywords
- The copy was nearly identical, including the same promise of reliable service
- The payment flow was smooth and professional
- Customers wouldn't realize they'd been scammed until they tried to use the service
Smartproxy had to:
- File domain disputes with WIPO for each fake domain
- Contact search engines to request deindexing
- Issue alerts to customers about the scam
- Set up monitoring for new fake domains
- Invest in customer communication to rebuild trust
The entire process took months and cost tens of thousands of dollars. And that was just one campaign. New fake domains kept appearing because the ROI on the initial fraud was clearly high.

Defensive Strategies: What Works and What Doesn't
So how do companies actually defend against this? Let's separate effective strategies from security theater.
Domain Registration and Monitoring
What works: Registering domain variations proactively is the single most effective defense.
This means:
- Buying the .com, .io, .co, and .net versions of your primary domain
- Registering country-code TLDs in markets where you operate
- Securing common typos and misspellings
- Monitoring new TLD registrations that match your brand
For a company with a global presence, this might mean owning 30-50 domain variations. The cost is roughly
Compare that to the cost of responding to a single phishing campaign: customer support, fraud investigation, legal consultation, and reputation management could easily exceed $50,000.
The prevention-to-remediation cost ratio is roughly 1:50. Prevention wins.
Monitoring: Use domain monitoring services that alert you when new domains are registered that match your brand name or contain your trademark. Services like Domain Tools, Brand Shield, and others track registrations across all TLDs in real-time.
WHOIS Privacy and Transparency
WHOIS privacy (registrant information hiding) is a double-edged sword.
Privacy protects legitimate businesses from harassment and spam. But it also hides who registered a domain, making it harder to identify and contact bad actors.
When you register domains for your company, consider:
- Using privacy protection for defensive registrations (domains you register but don't actively use)
- Being selective about privacy on primary domains (allowing some visibility to help customers verify you own it)
- Including WHOIS information that's legitimate and verifiable
For attacking a phishing domain, WHOIS records can sometimes help you identify the threat actor and report them to their registrar.
Search Engine and DNS Monitoring
Bad actors rank fake domains in search results and use DNS hijacking to redirect traffic. You can combat this through:
Search Engine Alerts:
- Set up Google Alerts for your brand name
- Use Google Search Console to monitor which domains appear for your brand
- Report fake domains to Google, Bing, and other search engines using their abuse reporting tools
DNS Monitoring:
- Monitor your DNS records for unauthorized changes
- Use DNSSEC (Domain Name System Security Extensions) to prevent DNS hijacking
- Set up alerts if someone registers your domain on a different registrar
- Use a DNS provider that offers protection against common attacks
Email Authentication and Verification
Many phishing attacks use email to direct people to fake domains. You can reduce the success of these attacks by:
SPF (Sender Policy Framework): Specifies which mail servers can send emails from your domain, preventing others from spoofing your address.
DKIM (Domain Keys Identified Mail): Digitally signs your emails so recipients can verify they actually came from you.
DMARC (Domain-based Message Authentication, Reporting and Conformance): Tells email providers what to do with emails that fail SPF or DKIM checks.
When properly configured, these technologies make it much harder for attackers to send convincing emails impersonating your company. Emails from fake domains will fail these checks and might be rejected or marked as spam.
User Education
Technical defenses help, but the weakest link is always the human.
Effective user education includes:
- Teaching customers to verify URLs before entering credentials
- Showing the difference between legitimate and suspicious domains
- Explaining how to check SSL certificates
- Encouraging the use of password managers (which automatically fill credentials only on legitimate sites)
- Regular security awareness training for employees
The challenge is that phishing websites are becoming better. Even technically savvy users can be fooled by a well-crafted fake site. But education still helps reduce the percentage of people who fall for attacks.
Legal and Regulatory Remediation
When preventive measures fail, you can pursue legal action. The most common avenue is WIPO domain dispute resolution.
WIPO Dispute Process:
- File a complaint with WIPO alleging the domain infringes your trademark
- The registrar presents the case to an independent arbitrator
- The arbitrator decides whether the domain should be canceled or transferred
- The whole process takes 60-120 days
WIPO disputes cost
Success rate: WIPO complainants win roughly 80% of cases, but only if they meet the criteria (trademark ownership, bad faith registration, no legitimate rights to the domain).
This is effective but reactive. It only works after the domain is already registered and operational.
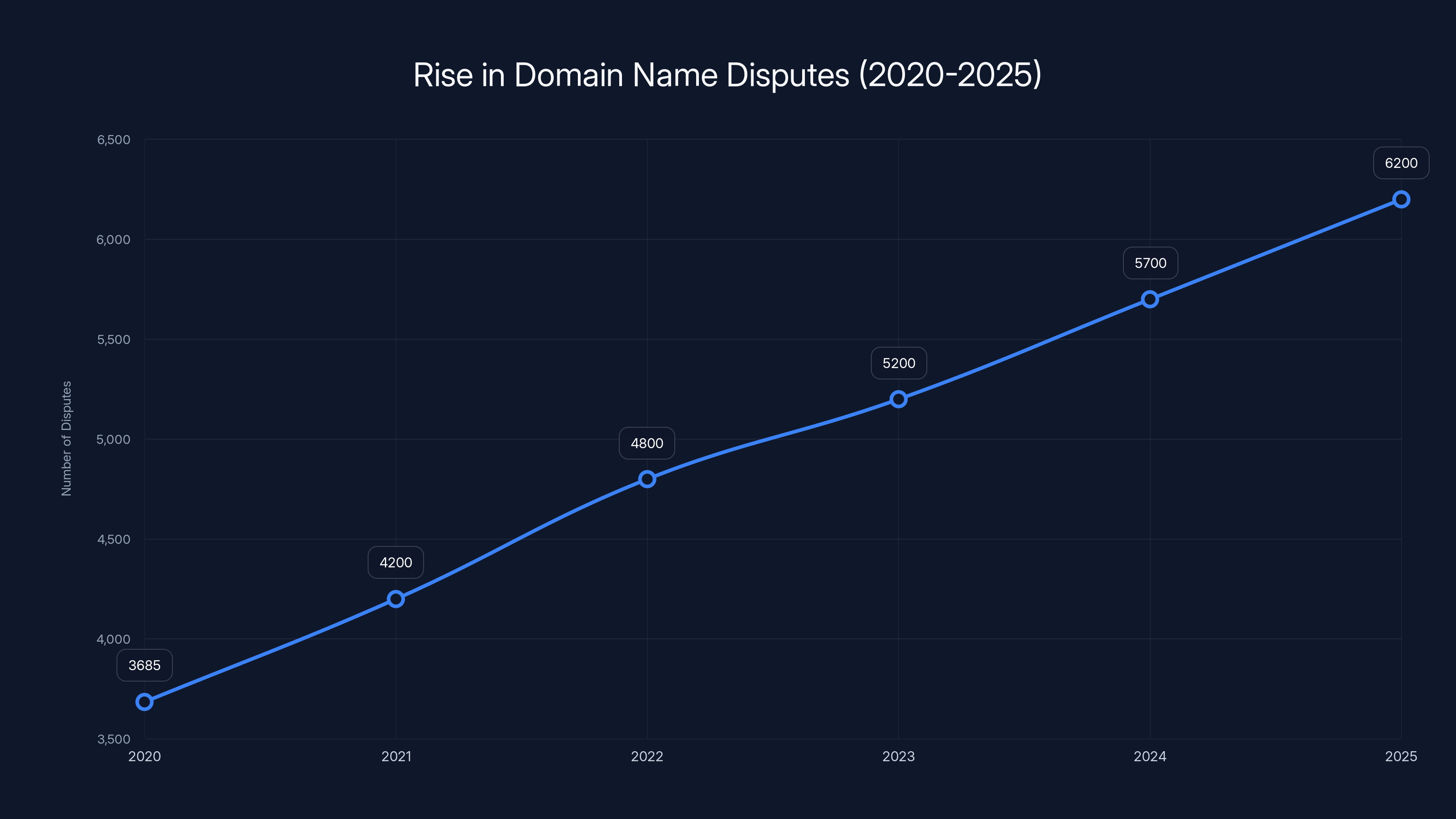
Domain name disputes have increased by 68% from 2020 to 2025, highlighting the growing issue of digital squatting. Estimated data based on trend projection.
The Gaps in Current Defense Systems
Despite all these tools, there are still significant gaps.
Search Engines Still Index Fake Domains
Google has improved its detection of phishing sites, but it's not perfect. Sophisticated fake domains can rank well for branded keywords before Google catches them. By then, they might have already harvested hundreds of credentials.
The challenge is scale. Google processes millions of new domains daily. Even with AI-powered detection, some slip through.
Registrars Have Limited Enforcement
Domain registrars can suspend or cancel domains that violate their terms of service, but many only do so when presented with a legal complaint or WIPO decision. Some registrars are known for being permissive with phishing domains, particularly those based in jurisdictions with weak enforcement.
Certificate Authorities Still Issue Certs to Phishing Domains
SSL certificates create the impression of legitimacy. Certificate authorities are supposed to validate domain ownership, but the process is often automated. An attacker can prove they control a domain (even if they registered it fraudulently) and get a legitimate SSL certificate within minutes.
The existence of an SSL certificate doesn't mean a site is trustworthy, but most users interpret the green lock icon that way.
International Variation Makes Monitoring Impossible
For global brands, registering every possible variation across every country and TLD is cost-prohibitive and impossible to monitor. Attackers exploit this by creating variations in different regions that the brand doesn't even know exist until damage is already done.

Future Trends and Emerging Threats
Digital squatting isn't standing still. The threats are evolving in predictable ways.
AI-Generated Content and Deep Fakes
Attackers are already using AI to generate highly convincing copy and images for fake sites. Within the next 1-2 years, we'll likely see:
- Fake product demos and customer testimonials generated entirely by AI
- Voice synthesis for customer support chat bots
- Deep fakes of company founders or executives used in phishing videos
This makes distinguishing legitimate content from fake increasingly difficult.
Subdomain Squatting
Attackers are registering subdomains under legitimate domains (or domains similar to legitimate ones) to create trusted-looking URLs.
Example: A fake domain "company-login.xyz" could create a subdomain "support.company-login.xyz", which further mimics the legitimate "support.company.com".
Machine Learning-Powered Detection Evasion
As security tools improve at detecting phishing sites using pattern recognition, attackers are using machine learning to generate variations that evade detection. This arms race will continue to accelerate.
Blockchain Domain Exploitation
Blockchain-based domain systems (like .eth domains on Ethereum) are becoming more common. These operate outside traditional ICANN governance, making them harder to monitor and remove. We'll likely see attackers exploiting this gap.

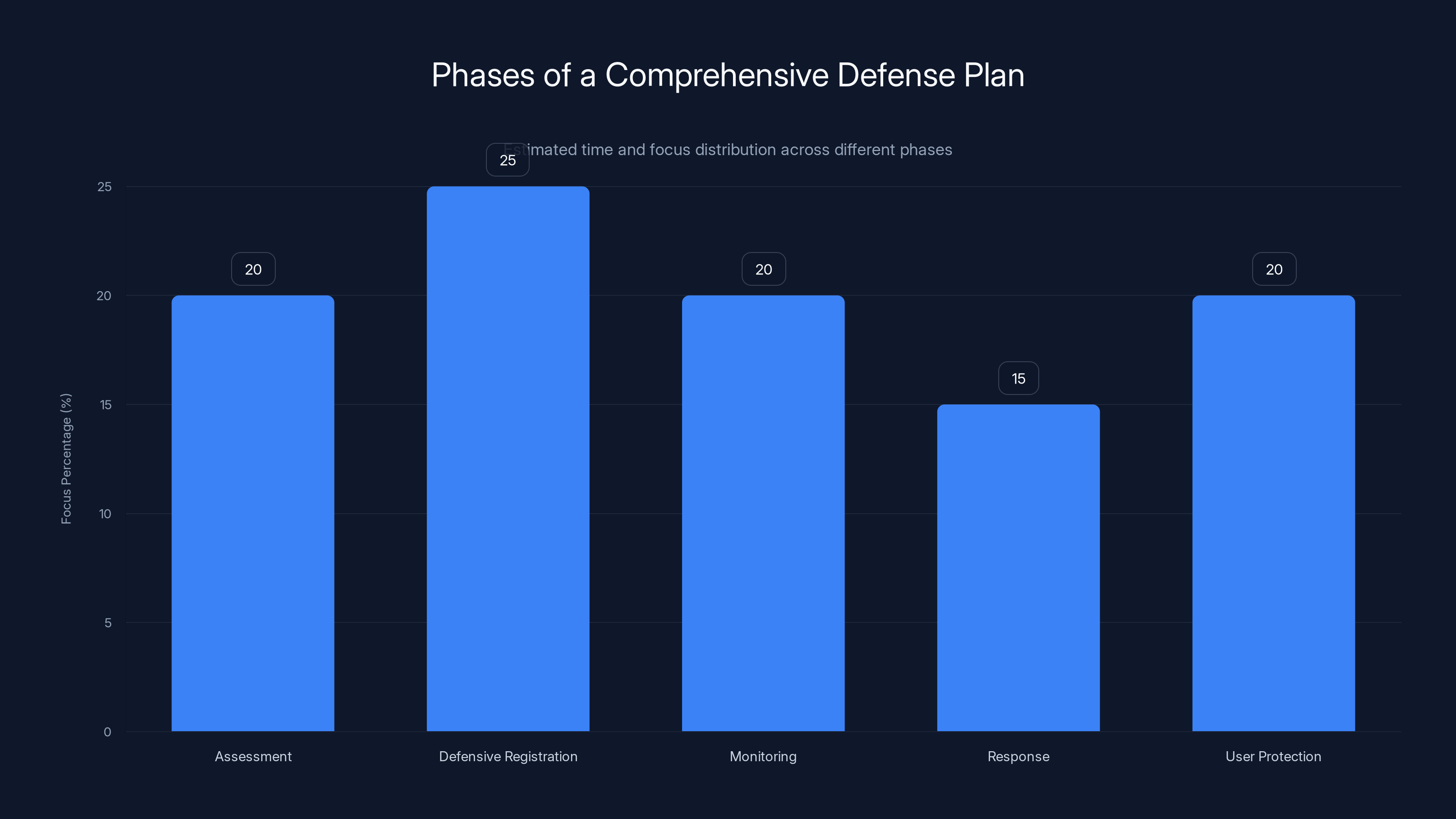
The defense plan is distributed across five key phases, with defensive registration receiving the highest focus. Estimated data based on typical strategic allocation.
Best Practices: A Comprehensive Defense Plan
Here's what a solid defense strategy actually looks like:
Phase 1: Assessment and Baseline (Month 1)
- Audit your current domain portfolio. Which domains do you own? Which variations are missing?
- Search for existing fake domains impersonating your company using brand monitoring tools
- Check if your trademarks are registered in key jurisdictions
- Evaluate your current monitoring and detection capabilities
Phase 2: Defensive Registration (Month 1-2)
- Register defensive domains for common typos, misspellings, and brand variations
- Register country-code domains in markets where you operate
- Register new TLDs that are commonly exploited (.cloud, .io, .shop, .online, etc.)
- Set up 301 redirects from defensive domains to your primary domain
- Implement HTTPS on all domains
Phase 3: Monitoring and Detection (Ongoing)
- Set up domain monitoring alerts for new registrations matching your brand
- Implement DNS monitoring and DNSSEC
- Use Google Alerts and search engine monitoring tools
- Set up email alerts from registrars when someone tries to modify your domains
- Monitor social media and online forums for reports of fake sites
Phase 4: Response Procedures (Ongoing)
- Document your WIPO dispute process and keep templates ready
- Establish contacts at major registrars and search engines
- Create a response playbook for when a new fake domain is discovered
- Brief your legal and customer support teams on the procedure
- Track response times and effectiveness of different approaches
Phase 5: User Protection (Ongoing)
- Educate your customers about phishing and fake domains
- Provide clear guidance on how to verify they're on your legitimate site
- Implement email authentication (SPF, DKIM, DMARC) on all company email
- Use branded links in emails with custom tracking or warnings
- Consider two-factor authentication to reduce the impact of stolen credentials

The Role of Industry and Regulation
While companies can take individual defensive measures, the broader problem requires industry-wide and regulatory action.
What Registrars Should Be Doing
Domain registrars are the gatekeepers. They could dramatically reduce digital squatting by:
-
Requiring verified identity: Many registrars offer privacy protection that hides the registrant's actual identity. This makes it impossible to identify bad actors. Registrars could require verified identity for any domain that matches known brands.
-
Pre-registration trademark checks: Registrars could automatically flag domains that match registered trademarks and require additional verification before allowing registration.
-
Faster suspension procedures: When a domain is reported as phishing, registrars could suspend it within hours rather than waiting for formal legal complaints.
-
Sharing threat intelligence: Registrars could share data about suspicious registrations and patterns with each other and with security researchers.
What Search Engines Can Do Better
Google and other search engines have made progress in detecting phishing sites, but there's more they could do:
-
Faster deindexing: When a domain is reported as phishing, it should be removed from search results within 24 hours, not weeks.
-
Branded domain verification: Search engines could display a verified check mark next to legitimate brand websites and warn users about unverified look-alikes.
-
Stricter ranking for new domains: New domains that rank for branded keywords should be scrutinized more carefully.
What Certificate Authorities Need to Address
SSL certificates lend legitimacy to fake sites. Certificate authorities could:
-
Require trademark verification: For domains matching known brands, CAs could require the applicant to prove they have the right to use the brand name.
-
Issue warnings for lookalike domains: CAs could flag certificates issued for domains that are suspiciously similar to legitimate ones.
Regulatory Considerations
Some jurisdictions are beginning to regulate this space. The European Union, for example, has requirements around digital service provider liability that could eventually push registrars and platforms to be more proactive.
However, regulation moves slowly, and the threat is moving fast. Most progress will continue to come from industry self-regulation and best practices rather than legal requirements.
Estimating Your Risk and Prioritizing Action
Not all companies face the same level of risk. Here's how to assess where you stand:
High-Risk Indicators
You should prioritize digital squatting defense immediately if:
- Your company operates in fintech, cryptocurrency, or handles payments
- Your brand name is short, simple, or has common typos
- You have a large customer base with sensitive data
- You operate in multiple countries
- You've already discovered fake domains impersonating you
- Your industry has seen recent phishing campaigns against competitors
- You have significant brand value and trademark registrations
Medium-Risk Indicators
You should implement defenses in the next quarter if:
- You're a growing Saa S company with an expanding customer base
- You handle customer payment information or credentials
- You operate in healthcare, legal, or other regulated industries
- You have a recognizable brand name
- You haven't yet registered domain variations
Lower-Risk Indicators
You can take a more measured approach if:
- Your company is very new or has minimal brand recognition
- Your brand name is unique and hard to misspell
- You handle minimal customer data
- You operate in a narrow niche
Even in lower-risk categories, implementing basic defenses (domain monitoring, email authentication, user education) takes minimal effort and costs almost nothing.

Tools and Services for Defense
While we won't recommend specific commercial solutions, the general categories of tools that help include:
Domain Monitoring Services: Alert you when new domains are registered matching your brand across all TLDs and registrars.
Brand Protection Platforms: Comprehensive tools that combine domain monitoring, search engine monitoring, social media monitoring, and take-down request automation.
DNS Security Services: Protect against DNS hijacking and provide DNSSEC implementation.
Email Authentication Services: Implement SPF, DKIM, and DMARC at scale, with monitoring and reporting.
Threat Intelligence: Feeds that provide information about newly registered domains, phishing campaigns, and emerging threats.
Trademark Management: Tools that help you track trademark registrations, renewal deadlines, and enforcement.
For small companies, starting with free tools (domain monitoring, Google Alerts, email authentication) and scaling to paid tools as you grow is a reasonable approach.
For mid-size and large companies, investing in a comprehensive brand protection platform is usually justified by the prevention of even a single successful phishing campaign.

FAQ
What is digital squatting and how does it differ from legitimate domain holding?
Digital squatting refers to registering a domain name with the deliberate intent to deceive users or cause harm to a brand, typically through phishing, fraud, or selling counterfeit products. Legitimate domain holding involves registering a domain you plan to develop or use for a genuine business purpose. The key difference is intent: squatters register domains to impersonate legitimate companies, while legitimate holders own domains they actually use or plan to use for their own purposes.
How do hackers find and register fake domains before legitimate companies can protect themselves?
Hackers use automated tools that monitor trademark registrations, watch for new company launches, and identify high-value brand names. They then quickly register variations across multiple TLDs and registrars before the legitimate company has time to register defensive variations. Many registrars make bulk registration easy, allowing someone to register hundreds of domains in minutes. Speed and scale are the attacker's advantages, which is why preventive registration is so important.
Why do typosquatted domains still rank in search results?
Search engines use complex algorithms to detect phishing sites, but the process isn't instantaneous. A newly registered typosquatted domain might rank temporarily for the correct brand keyword, especially if it copies content from the legitimate site. Additionally, some typosquatted domains rank for slightly different searches (like "company typo name") and might accidentally receive traffic from users. Once reported, search engines usually remove these domains from results within 24-72 hours, but that window is enough for attackers to harvest credentials.
Can WIPO dispute resolution actually prevent digital squatting, or is it just a cleanup tool?
WIPO disputes are primarily a remediation tool, not a prevention mechanism. By the time you file a dispute, the attacker has already had weeks or months to operate the fake domain and harvest user information. However, disputes are effective at removing domains after the fact and preventing future attacks using the same domain. The real prevention happens through proactive domain registration and monitoring before attackers register variations in the first place.
What should my company do if we discover a fake domain impersonating us right now?
Immediately: document the domain, take screenshots of the content, and preserve evidence. Then file reports with the registrar using their abuse reporting form, contact the relevant search engines (Google, Bing) to request deindexing, and notify your customers about the scam if it appears to be actively targeting them. If you have a trademark registration, file a WIPO dispute. In parallel, consider hiring a brand protection firm to handle the technical aspects and explore legal options. For critical incidents, also notify law enforcement if financial fraud or data theft has occurred.
Is registering hundreds of domain variations really cost-effective for my small company?
Yes. A domain costs
How effective is email authentication (SPF, DKIM, DMARC) at preventing phishing emails?
Very effective, but only if properly configured and if recipients' email providers enforce these standards. When properly set up, these technologies prevent attackers from sending emails that appear to come from your domain (spoofing). However, they don't prevent emails from similar-looking domains (like "company-support.com" instead of "company.com"). They're one layer of defense that works best in combination with other measures like user education and link verification.
What's the difference between domain hijacking and digital squatting?
Domain hijacking involves taking over a domain that someone else already owns, typically through hacking the registrar account or DNS provider. Digital squatting involves registering a new domain that mimics a legitimate brand but isn't actually controlled by that brand. Hijacking is a more serious attack that directly impacts the legitimate owner's ability to use their own domain. Squatting creates a competing look-alike domain. Both are harmful, but they require different defensive strategies.
Are blockchain domains (.eth, .crypto) immune to digital squatting?
No, they're actually more vulnerable in some ways because they operate outside traditional governance structures like ICANN and have less regulation. There's no central authority to dispute a blockchain domain registration or force removal of a phishing domain. However, blockchain domains are currently less well-known than traditional domains, so there's less active squatting of them. As blockchain domains become more popular, expect to see the same squatting problems replicate on decentralized domain systems.
How can I verify that a domain is actually legitimate before entering sensitive information?
Several steps can help: first, check the full URL in the address bar (don't rely on email links or search results). Verify it matches exactly what you expect, with no extra characters or typos. Check for a valid SSL certificate by clicking the lock icon (though certificates can be obtained fraudulently). Visit the company's official website directly by typing the domain yourself rather than following links. Call the company using a phone number from their main website to verify contact information. Be particularly careful with forms asking for passwords, credit cards, or personal information.
Conclusion: Building a Culture of Domain Defense
Digital squatting has evolved from a niche problem affecting a few high-profile companies into a widespread threat affecting businesses of all sizes. The 68% increase in WIPO domain disputes over five years isn't a blip in the data. It's a signal that this threat is becoming an expected part of operating a business online.
The good news? It's highly preventable. Unlike many cybersecurity challenges that require sophisticated technical expertise, defending against digital squatting is straightforward. It requires:
- Proactive domain registration: Own the variations of your domain before attackers do
- Continuous monitoring: Know when new domains matching your brand are registered
- Quick response: Have procedures in place to report and remove fake domains
- User education: Help your customers recognize and avoid phishing attempts
- Technical hardening: Implement email authentication, DNS security, and other baseline protections
The companies that get hit hardest by digital squatting aren't the ones that neglect defense entirely. They're the ones that think one or two preventive measures are enough. They register their main domain but miss the .io variation. They set up monitoring but don't act when an alert fires. They educate users but don't implement email authentication.
Defense against digital squatting works best as a system, with multiple overlapping layers. When one layer fails (and someday one will), the others catch the problem.
The cost of this comprehensive approach is minimal for most companies. The cost of not having it in place is potentially severe: lost customer revenue, damaged brand reputation, regulatory scrutiny, and the organizational disruption of responding to a successful attack.
Start with the obvious: audit your domain portfolio today. Register the variations you're missing. Set up monitoring. Brief your team on the threat. Then move through the other defenses methodically.
If you operate a global business, the ROI on these investments is even clearer. The potential impact of a successful digital squatting campaign against your international customer base could easily reach six or seven figures.
Digital squatting is a problem that's only going to accelerate as domains become cheaper, tools become more accessible, and attackers become more sophisticated. But it's also a problem that's entirely preventable with the right approach.
The question isn't whether you'll be targeted. If you have a recognizable brand and meaningful customer base, you almost certainly are being targeted right now. The question is whether you'll be ready.
Key Takeaways
- Digital squatting attacks have increased 68% over five years, with 6,200 WIPO disputes filed in 2025 alone
- Attackers use multiple sophisticated techniques including typosquatting, combosquatting, homograph attacks, and international domain variations
- The financial and reputational impact extends far beyond the initial fraud, affecting customer trust long-term
- Preventive domain registration is 50+ times more cost-effective than remediation after an attack occurs
- A comprehensive defense strategy combines proactive registration, monitoring, quick response, user education, and technical hardening
- No single tool or approach completely prevents digital squatting, effectiveness comes from layered defenses
- Companies of all sizes can implement these defenses without massive budgets, starting with free tools and scaling as needed

Key Takeaways
- Digital squatting has increased 68% over five years with 6,200 WIPO disputes in 2025, marking a systemic shift in how brands are attacked online
- Attackers use five primary techniques: typosquatting, combosquatting, homograph attacks, TLD squatting, and international domain variations, each with different detection challenges
- The real cost of digital squatting extends beyond immediate fraud to include customer trust erosion, reputational damage, and long-term revenue impact
- Preventive domain registration and monitoring costs under 50,000+, making prevention 50 times more cost-effective
- A layered defense combining domain registration, monitoring, email authentication, DNS security, and user education provides the most effective protection against evolving threats
Related Articles
- Quishing: The QR Code Phishing Scam Taking Over [2025]
- DNS Malware Detour Dog: How 30K+ Sites Harbor Hidden Threats [2025]
- Network Modernization for AI & Quantum Success [2025]
- dYdX Supply Chain Attack: How Malicious NPM Packages Emptied Wallets [2025]
- CISA End-of-Life Edge Device Replacement Guide [2025]
- Best VPNs for Super Bowl LIX: Complete Streaming Guide 2025
![Digital Squatting: How Hackers Target Brand Domains [2025]](https://tryrunable.com/blog/digital-squatting-how-hackers-target-brand-domains-2025/image-1-1770648014466.jpg)



