Introduction: The Silent Threat Hidden in Plain Sight
You're walking through a restaurant, and you see a QR code printed on the table. Scan it, and it supposedly takes you to the menu. Your phone buzzes with a prompt asking you to log into your account. You think it's normal. You do it. Two hours later, someone's draining your bank account from across the world.
Welcome to quishing.
Quishing is a new flavor of phishing attack that uses QR codes instead of suspicious links or emails. The term itself is straightforward: QR code plus phishing equals quishing. And it's becoming one of the fastest-growing security threats in 2024 and 2025. What makes it so dangerous? Most people don't think twice before scanning a QR code. Unlike clicking a link in an email, which raises immediate red flags, QR codes feel legitimate. They're everywhere now, from restaurant menus to parking meters to advertisements. That trust is exactly what scammers are exploiting.
The scale of this problem is staggering. According to reports from major VPN providers and cybersecurity firms, approximately 26 million individuals have already been exposed to quishing attacks. Some estimates suggest the number is far higher, but the actual exposure rate is hard to track because many victims don't realize they've been compromised. The attack vector is so effective that it's become a preferred method for sophisticated threat actors targeting both consumers and enterprises.
What's particularly insidious about quishing is that it bypasses many of the traditional defenses people use to protect themselves. Email security filters won't catch a malicious QR code because the attack doesn't come through email. Advanced users who know better than to click suspicious links still fall for QR codes because the interaction feels different, more benign. And for organizations, quishing presents a unique problem: you can't simply block QR codes because they've become essential for legitimate business operations.
In this guide, we'll break down exactly what quishing is, how attackers execute these campaigns, the real-world impact on victims, and most importantly, the concrete steps you can take right now to protect yourself and your organization. We'll cover the psychology behind why quishing works so well, the different types of quishing attacks you might encounter, and the advanced defensive strategies that actually work.
TL; DR
- Quishing is a phishing attack using QR codes instead of traditional links or email attachments to redirect users to malicious websites or credential harvesting pages
- 26 million people have already been exposed to quishing attacks, with the problem growing exponentially across all industries
- QR codes bypass traditional security defenses because they're perceived as safe and legitimate by most users, unlike suspicious email links
- The attack works in seconds with minimal friction: scan, redirect, credential theft, account compromise, or malware infection
- Prevention requires a multi-layered approach: education, URL preview tools, VPN usage, browser security features, and organizational policies

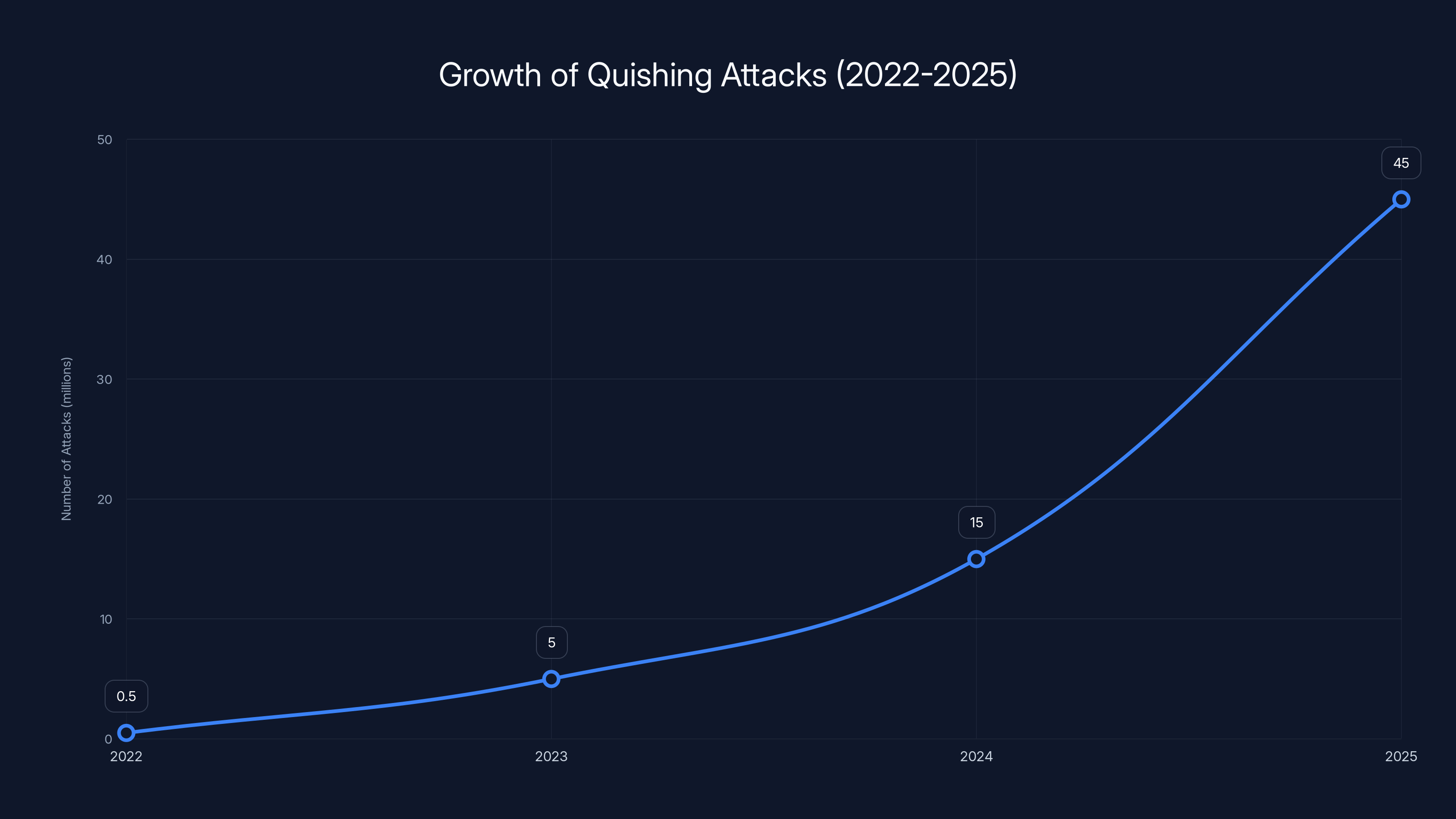
The number of quishing attacks has grown exponentially, from virtually none in 2022 to an estimated 45 million by 2025. Estimated data based on reported trends.
What Is Quishing? Understanding the Mechanics
Quishing is fundamentally a variation of phishing, but it weaponizes QR codes as the attack vector instead of traditional methods. To understand quishing, you need to know what makes it different from standard phishing.
Traditional phishing relies on sending emails with malicious links or attachments. Users are supposed to click the link or download the file, which either installs malware or redirects them to a fake login page designed to steal credentials. Phishing succeeds because attackers craft convincing messages that mimic legitimate organizations. However, email security tools have become increasingly sophisticated at detecting and filtering these attacks. Users also have some level of awareness now about not clicking random links in emails.
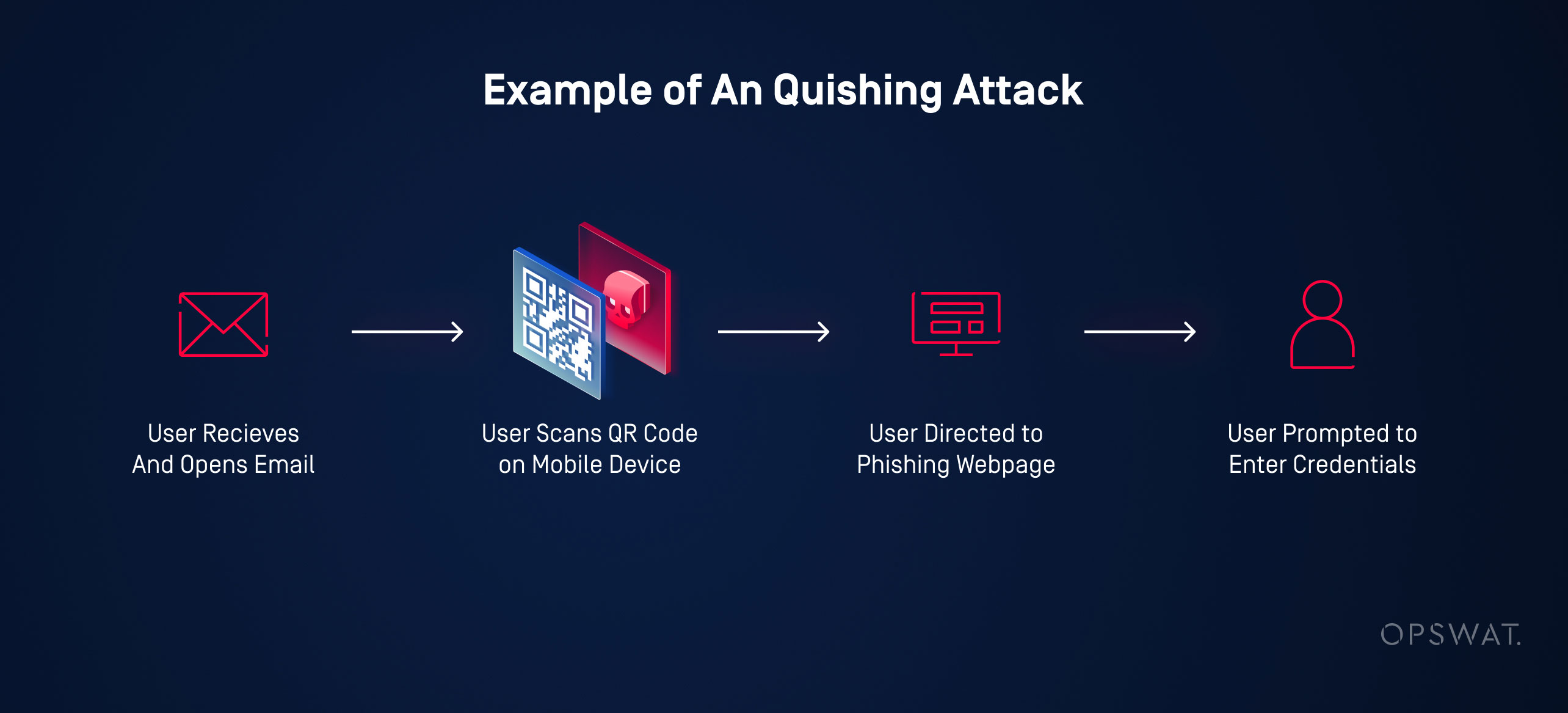
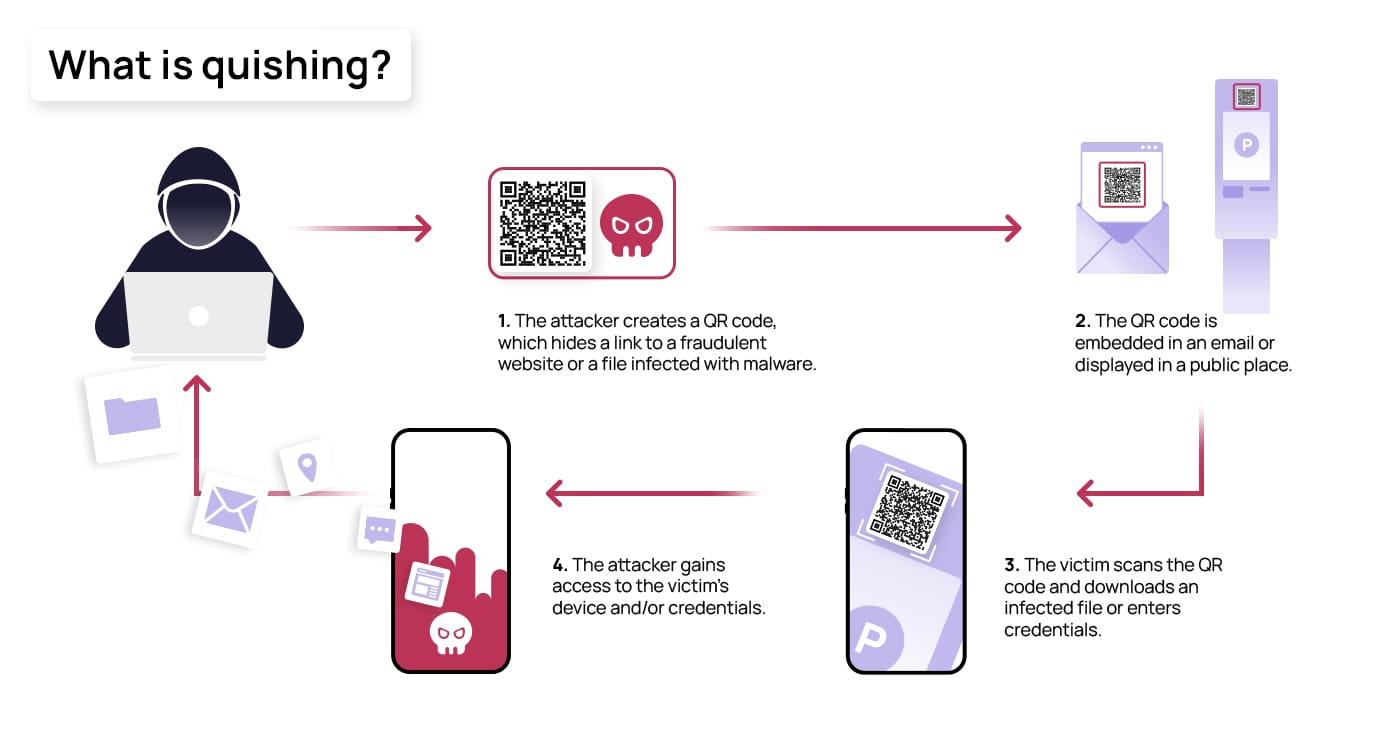
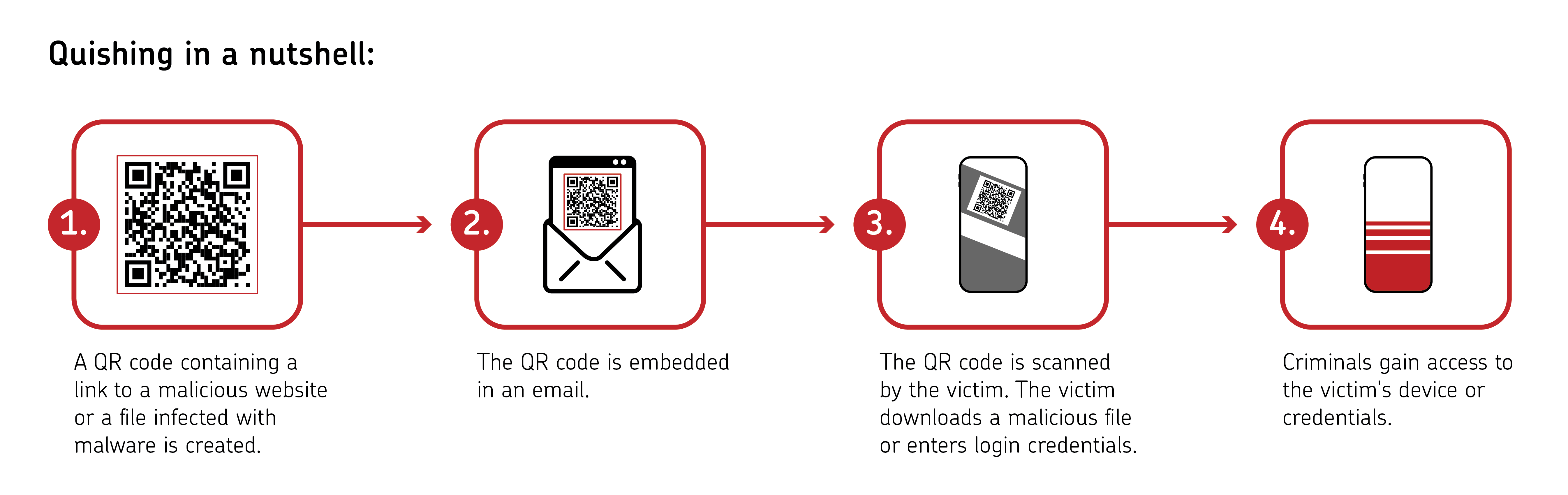
Quishing takes the same objective—stealing data or compromising accounts—but uses a completely different delivery mechanism. Instead of emailing you a link, attackers print or post a QR code in a location where you're likely to find it. The QR code looks innocent. You scan it with your phone, and your device immediately navigates to a URL without you ever seeing the actual web address. This is the critical vulnerability: you don't see the destination before you scan.
Here's how it technically works. A QR code is simply an encoded URL. When you scan it with your phone's camera or a QR code reader app, your device decodes the image and extracts the URL embedded within it. Your phone then opens that URL automatically in your browser. The entire process takes 2-3 seconds, and most users never think to question what happens next. The attacker has successfully redirected you to their malicious website without any additional steps from you.
Once you land on the attacker's page, several things can happen depending on what they're after. The most common scenario is credential theft. The fake website mimics a legitimate service—your bank, email provider, social media platform, or work login portal. You see a login form that looks identical to the real thing. You enter your username and password, thinking you're logging into a legitimate service. But you're not. The attacker's server captures your credentials and stores them. Your account is now compromised.
Less commonly, scanning a malicious QR code can directly execute actions on your device. If your phone is configured to handle certain URL schemes, scanning a QR code containing a specially crafted URL can trigger phone calls, send text messages, or initiate app installations without requiring additional user interaction. This is particularly dangerous with Android devices, which are more permissive with URL schemes than iOS.
The psychological component of quishing is where it becomes truly dangerous. QR codes feel modern and tech-savvy. They're everywhere in legitimate contexts: restaurants use them for menus, stores use them for product information, events use them for registration. This ubiquity has created an implicit trust. When you see a QR code, your brain doesn't immediately flag it as a potential threat the way it might with a random link in an email. You scan first, think later.
Attackers understand this psychology perfectly. They exploit the trust and legitimacy that QR codes have earned in our daily lives. By placing a malicious QR code in a location where users expect to see one—a restaurant, a parking lot, a retail store—attackers can harvest credentials or compromise devices with minimal suspicion.
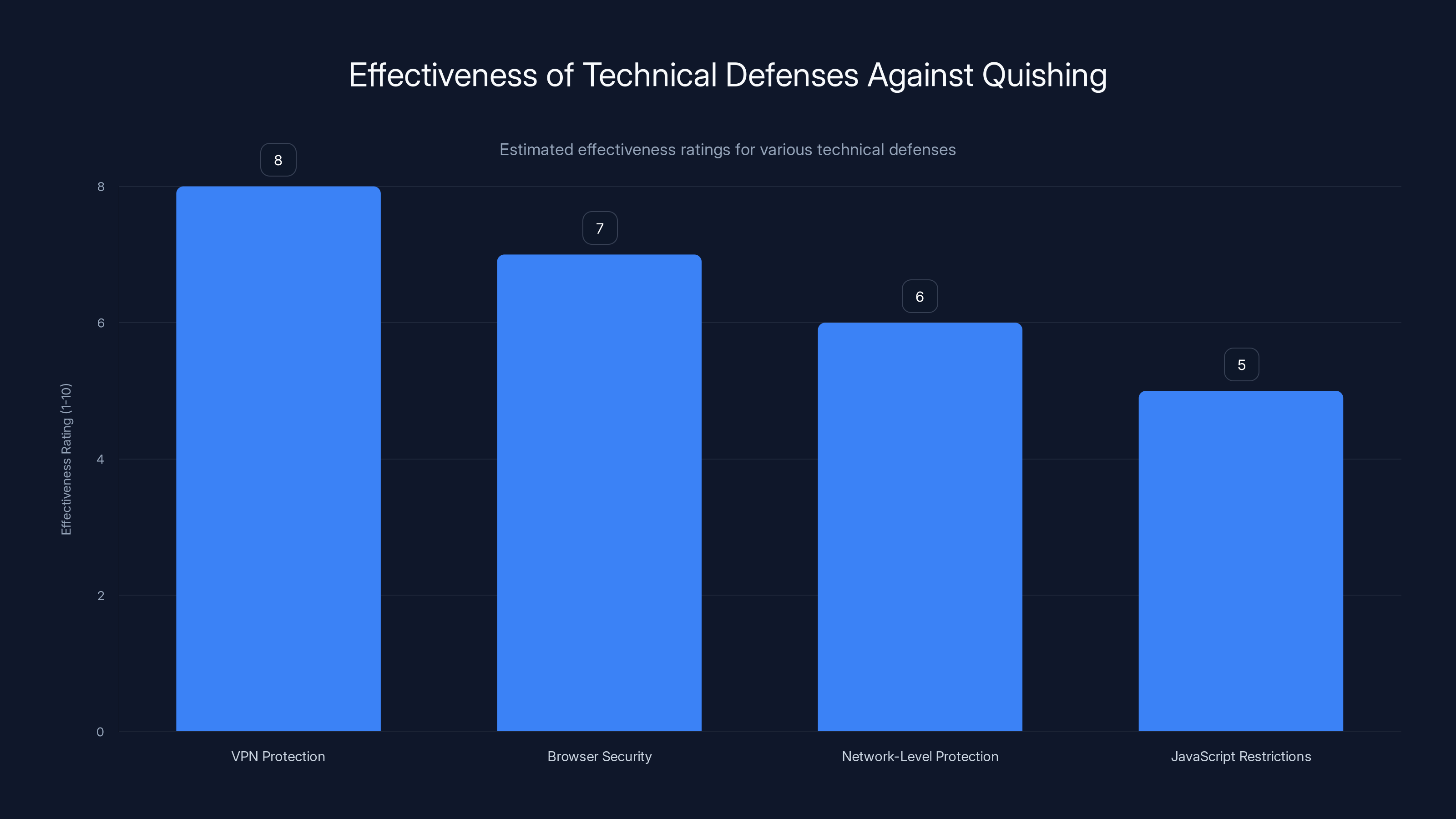
Estimated data shows VPN protection as the most effective technical defense against quishing attacks, followed by browser security features.
The Scale of the Problem: 26 Million Exposed and Growing
The statistics around quishing are genuinely alarming. The figure of 26 million individuals already exposed to quishing attacks comes from reports by major cybersecurity firms and VPN providers analyzing attack patterns throughout 2023 and 2024. But this number represents only the incidents that were detected and reported. The actual number of people affected is likely significantly higher because many users never realize they've been compromised.
Here's the reality: most victims of quishing attacks never know it happened. They scan a QR code, enter their password on a fake login page, and carry on with their day. The credentials are stolen in real-time. Within hours or days, attackers use those stolen credentials to access the victim's account, extract sensitive information, or pivot to other accounts. By the time the victim discovers something is wrong, significant damage may have already occurred.
The growth rate of quishing attacks is exponential. In 2022, quishing was virtually unknown. By 2023, reports of quishing attacks started appearing regularly. In 2024, the volume of quishing attacks roughly tripled compared to 2023. This growth trajectory suggests that 2025 could see quishing attacks become even more common than traditional phishing for certain demographic groups and use cases.
Why is the growth so rapid? Several factors contribute. First, quishing is remarkably effective. Success rates for quishing campaigns are significantly higher than for traditional phishing emails. While email phishing might have a 3-5% click-through rate, quishing can achieve 15-25% scan rates in some contexts. Second, the barrier to entry is low. An attacker doesn't need sophisticated infrastructure to generate QR codes—any free QR code generator will do. They can print the codes and post them in high-traffic locations with minimal cost.
Third, detection and attribution are difficult. Unlike email attacks, which leave trails in email logs, QR code attacks are harder to trace. If someone scans a malicious QR code posted in a public location, there's no direct link to the attacker until the user reports it to authorities or security researchers.
The industries most affected by quishing attacks include finance, healthcare, retail, and technology. Attackers specifically target these sectors because users in these industries are accustomed to scanning QR codes for legitimate purposes. A bank customer scanning a QR code at an ATM to check their balance is in the exact right mindset to enter credentials when prompted. A healthcare patient scanning a QR code to verify insurance information is primed to provide personal data.
The demographic distribution of quishing victims is also changing. Early quishing attacks primarily targeted tech-savvy users who were comfortable scanning QR codes. However, as QR codes have become ubiquitous and adoption has spread across all age groups, attackers are now successfully targeting older demographics who might be less suspicious of the attack vector.
How Quishing Attacks Are Executed: The Attack Chain
Understanding how attackers execute quishing campaigns gives you insight into where defenses can be most effective. The attack chain typically involves several distinct phases, each with different technical and social engineering elements.
Phase 1: Planning and Reconnaissance
Before an attacker ever creates a QR code, they spend time researching their target. For consumer-focused attacks, this might involve identifying high-traffic locations frequented by people with disposable income or access to sensitive accounts. Attackers might research parking lots, restaurants, retail stores, or public transit stations. They look for places where people are distracted and moving quickly—exactly the conditions that make people less likely to question a QR code.
For corporate attacks, attackers research the target organization's infrastructure, common workflows, and tools employees use regularly. They might study where employees park, where they eat lunch, or what conference rooms they frequent. The goal is to place a QR code somewhere that feels contextually appropriate and trusted.
Phase 2: Creating the Malicious Infrastructure
Once the target is selected, attackers set up the malicious infrastructure. This typically involves registering a domain name that's visually similar to a legitimate service—for example, "appleid-securelogin.com" instead of "appleid.apple.com." They then create a fake login page that's pixel-perfect identical to the legitimate service. This isn't difficult because legitimate login pages are publicly accessible. Attackers simply download the HTML and CSS, modify it to capture credentials, and host it on their server.
The QR code itself is then generated to point to this malicious page. Free QR code generators like QR Code Generator or similar services are used. The attacker specifies the URL they want encoded, and the tool generates the corresponding QR code image.
Phase 3: Deployment and Distribution
This is where the physical world meets the digital attack. The QR code is printed on stickers or labels and physically placed in locations where targets are likely to scan them. Attackers might use:
- Stickers placed over legitimate QR codes to replace them
- QR codes printed on business-like signage placed in parking lots or building lobbies
- Fake package delivery notices with QR codes left on car windshields
- QR codes in physical mail designed to look like official correspondence
- QR codes on product packaging in retail environments
- QR codes on parking meters or toll booths
The key is placement in a location where the target expects to see a QR code and has psychological permission to scan without thinking.
Phase 4: Credential Harvesting and Account Compromise
When a user scans the malicious QR code, they're redirected to the attacker's fake login page. If the attacker has done their homework, the page looks identical to the legitimate service. The user enters their username and password. The fake page captures these credentials and, in some cases, stores them in a database or sends them directly to the attacker's email.
At this point, the attacker has the victim's credentials. What happens next depends on the attacker's goals. They might:
- Immediately log into the victim's account to change the password and lock them out
- Extract sensitive personal information before the victim realizes anything is wrong
- Pivot to related accounts using the compromised email address
- Set up persistence mechanisms like forwarding rules or backup authentication methods
- Monitor the account for financial transactions to intercept money before the victim notices
Phase 5: Monetization and Data Exploitation
The final phase is where attackers convert their access into profit or intelligence. For financial crimes, they drain accounts or execute unauthorized transfers. For identity theft, they extract personal information like Social Security numbers, addresses, and phone numbers. For corporate espionage, they download proprietary information, customer data, or source code. For account takeover, they might hold the account for ransom or use it to launch further attacks against the victim's contacts.
Many attackers operate on a timeline. They know that once a victim realizes their account has been compromised, the account will likely be locked or the password changed. So they work quickly, extracting maximum value within a compressed timeframe.
The sophistication of these attacks varies widely. Some attackers are opportunistic individuals running small-scale campaigns. Others are part of organized crime networks with significant resources and technical expertise. The most advanced attacks, suspected to be state-sponsored or nation-backed, use quishing as a component of multi-stage campaigns targeting high-value individuals or organizations.
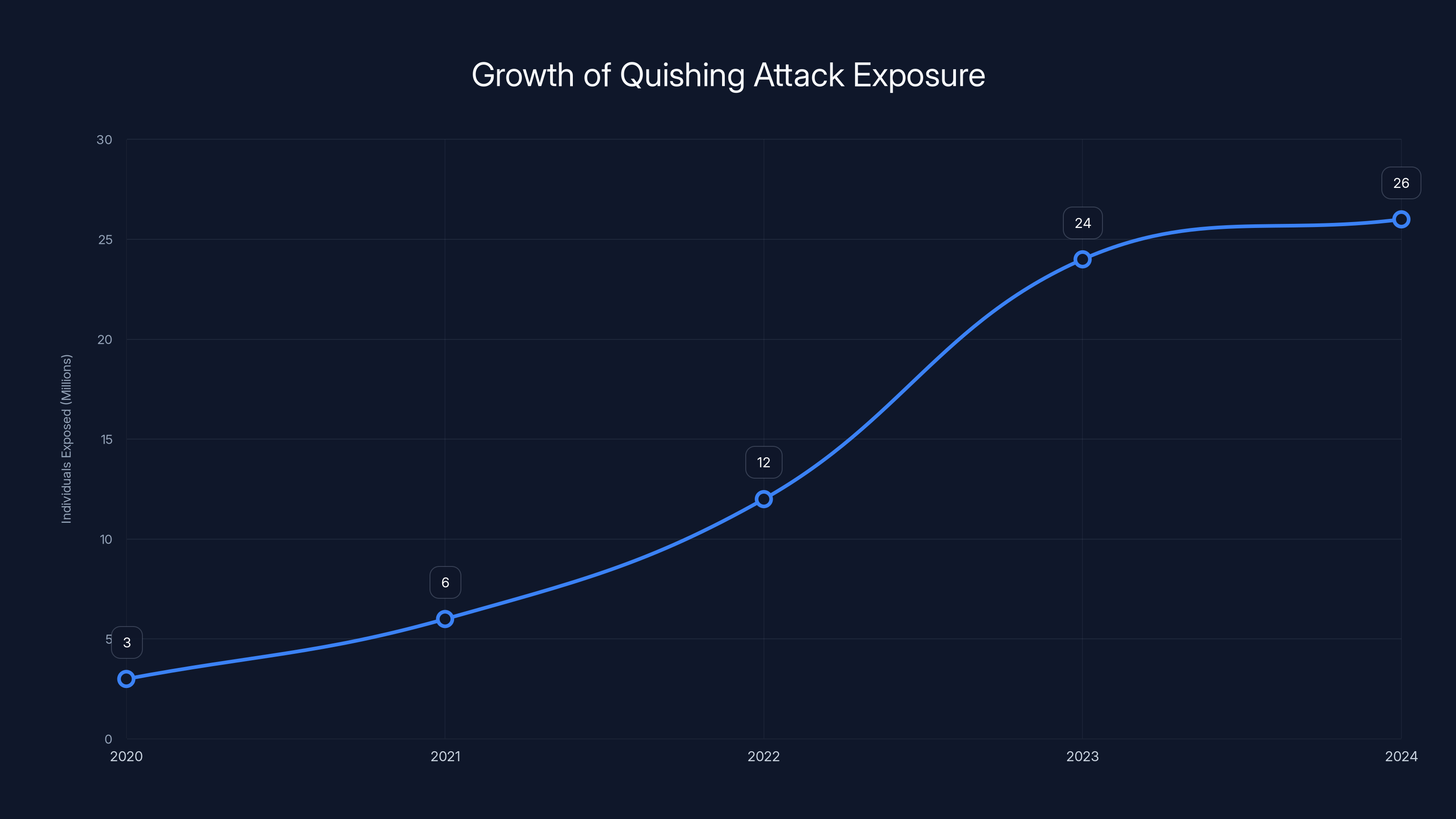
The number of individuals exposed to quishing attacks has grown rapidly, with estimates suggesting a doubling trend annually. Estimated data.
Why Quishing Is More Dangerous Than Traditional Phishing
While quishing and traditional phishing share the same ultimate objective—compromising user accounts—quishing presents unique dangers that make it more difficult to defend against.
First, visibility is non-existent. With traditional phishing email, at least the email itself provides some surface that can be analyzed. Email security tools can inspect the sender's address, check for authentication failures like SPF or DKIM violations, analyze the body text for common phishing patterns, and scan any attachments for malware. None of this is possible with a QR code. The QR code itself is just a visual representation of an encoded URL. Without scanning it, you have no way of knowing where it points.
Second, URL obfuscation is inherent. When you click a link in an email, you can hover over it and see the actual URL. Most email clients also show you the destination before you click. With a QR code, the URL is completely invisible. You scan the code and your device immediately navigates to the URL without giving you a chance to inspect it. For tech-savvy users who regularly check URLs before clicking, this is a significant loss of protection.
Third, trust transfer is automatic. The context in which a QR code appears transfers legitimacy to the code itself. If you see a QR code in a restaurant, you trust it because you trust the restaurant. If you see a QR code on a parking meter, you trust it because you trust the municipality. This trust is then transferred directly to whatever the QR code points to. An attacker can hijack this trust by placing a malicious code in a trusted context.
Fourth, friction is minimal. Traditional phishing requires multiple steps: the user needs to receive the email, read it, understand it, click the link, and then interact with the malicious page. Each of these steps introduces friction and opportunity for the user to question their actions. Quishing reduces friction dramatically. Scan, redirect, prompt for credentials. Three steps instead of six.
Fifth, demographic agnostic targeting is possible. Traditional phishing attacks often rely on social engineering and understanding cultural or demographic context. Not everyone falls for a Nigerian prince scam, and technical users immediately recognize the signs of a phishing email. But QR codes can be scanned by anyone, from teenagers to senior citizens. The attack vector itself doesn't require literacy or technical knowledge. You just point your camera at a code and tap a button.
Sixth, deniability for the attacker is higher. If someone posts a malicious QR code in a public place, it's nearly impossible to trace back to the attacker. Email addresses can be tracked, email servers can be identified, and email logs provide evidence. A printed QR code sticker? That's untraceable. This makes law enforcement response difficult and increases attacker confidence.

Real-World Quishing Attack Scenarios
Understanding how quishing attacks play out in real situations helps you recognize and avoid them. Here are several realistic scenarios that have actually occurred or are based on documented attack patterns.
Scenario 1: The Parking Lot Attack
You're at a shopping mall and park your car. You notice a printed notice on your car's windshield that looks like a parking violation notice. The notice has an official-looking logo and explains that your vehicle was flagged for a safety inspection. To complete the inspection virtually and avoid a fine, scan the QR code provided.
You scan the code and are taken to a page that looks like your state's Department of Motor Vehicles website. It asks you to enter your driver's license number and date of birth to "verify" your vehicle registration. You do. The attacker now has your driver's license number and date of birth, which combined with other publicly available information can be used for identity theft.
This attack is particularly effective because you're in a hurry, you're stressed about the supposed violation, and you're in a public place where you might feel awkward calling your DMV to verify. The attacker has correctly anticipated your emotional state and used it against you.
Scenario 2: The Restaurant Menu Attack
You're at a restaurant and see a QR code printed on a flyer at your table with text saying "Tap here for our full menu." You scan it and are taken to a page that looks like the restaurant's website. It says your session has expired and asks you to log into your account to view your order history.
Wait, you think. You've never used this restaurant's app. But the page looks legitimate, so you assume the restaurant's system is confused. You enter your email and create a password. The attacker now has your email address and a password (which you probably use elsewhere). They try that password on Gmail, Amazon, and other major services. They gain access to one of your accounts.
This attack works because it exploits the principle of false authority. The QR code is in a restaurant, so it must be legitimate. The page is asking you to log in, so it must be a legitimate login page. You don't question why a restaurant's menu needs you to log in.
Scenario 3: The Corporate Network Attack
You work at a mid-sized tech company. You receive an email from "IT Support" saying that the company is implementing a new two-factor authentication system and asking you to complete your enrollment immediately. The email includes a QR code with instructions to scan it and verify your identity.
You scan the QR code and are taken to a page that looks like your company's login portal. It asks for your employee ID, password, and a code from your authenticator app. You provide all three pieces of information, thinking you're enrolling in the new security system. The attacker now has your company credentials and, more critically, a valid code from your authenticator app that they can use immediately to log into company systems.
This attack targets the trust employees have in internal IT communications. A real IT team would likely use a different authentication method rather than asking employees to scan a QR code and re-enter their credentials.
Scenario 4: The Package Delivery Attack
You receive a notice on your door from a package delivery company saying that they couldn't deliver your package because the address was incomplete. To resubmit your address, scan the QR code or click the link provided.
You scan the QR code and are taken to a page for the delivery company. It asks you to enter your account username, password, and payment method to "verify" your identity before resubmitting the address. You do. The attacker now has your delivery account credentials and your payment method information.
This attack is effective because it exploits the expectation of a package delivery. Many people are expecting a delivery, making this message seem urgent and legitimate.

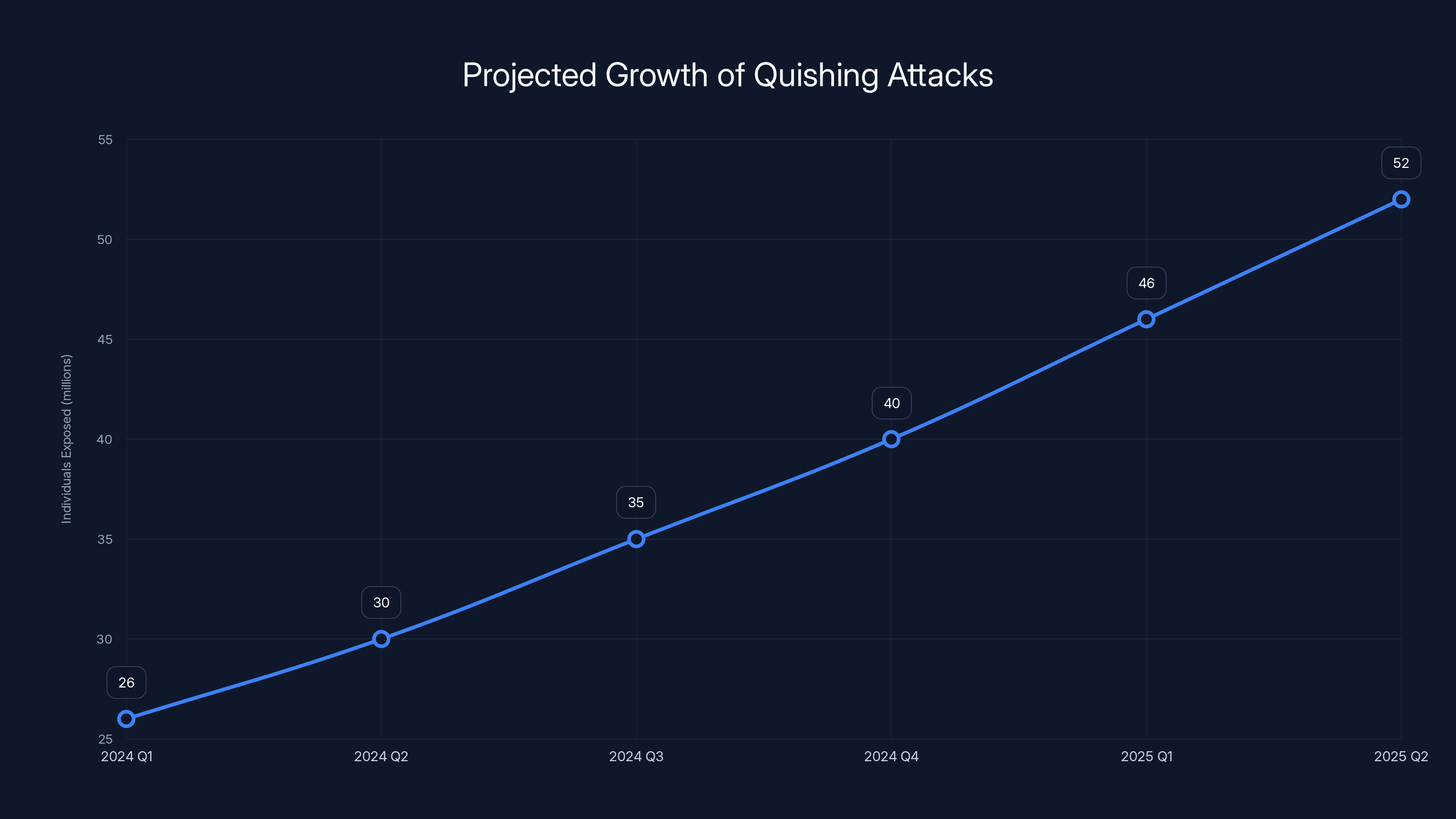
Quishing attacks are projected to expose an increasing number of individuals, reaching an estimated 52 million by mid-2025. Estimated data based on current trends.
The Psychology Behind Why Quishing Works
Quishing is fundamentally an exploitation of human psychology. Understanding why people fall for quishing attacks is crucial to protecting yourself from them.
Authority and Trust Transfer
When you see a QR code in a particular context, you transfer the authority and legitimacy of that context to the QR code itself. A QR code in a bank looks like it must lead to the bank's website. A QR code in a government building must lead to an official government service. This is a cognitive shortcut that normally serves us well—in most cases, QR codes in legitimate locations do go to legitimate destinations.
Attackers exploit this by placing malicious QR codes in contexts where legitimate QR codes are expected. By putting a malicious code on a parking meter, in a restaurant, or in a building lobby, they're borrowing the trust that users have in those locations.
Reduced Friction and Cognitive Load
When you click a suspicious link in an email, there's friction. You need to interpret the email, understand that the link might be malicious, potentially hover over it to see the destination, and then make a conscious decision to click. This friction gives you time to engage your critical thinking.
With a QR code, friction is minimal. You see a code, point your camera, and tap. The action is so quick and requires so little thought that you don't engage your skeptical mind. By the time you're on the malicious page, you've already completed the action that got you there. Your mind is playing catch-up.
Urgency and Social Proof
Many quishing attacks include language or context that creates a sense of urgency. "Your account will be locked if you don't verify immediately." "Complete this action to avoid a fine." "Claim your promotion before it expires." Urgency shuts down critical thinking. When you're under time pressure, you're less likely to question your actions.
Social proof also plays a role. You see other people scanning the QR code (or you assume they are because it's in a public place), so it must be safe. If it were dangerous, surely others would have warned about it by now. This is a false assumption, but it feels true in the moment.
Specificity and False Precision
Attackers often include specific details that make their attacks feel more legitimate. A fake parking violation might include your license plate number, your make and model of vehicle, and the exact time you parked. A fake delivery notice might include a specific package weight or carrier name. These details create a sense of specificity that makes the attack feel more real.
Your brain interprets specificity as authenticity. If someone knows your license plate number, they must be legitimate, right? But attackers can easily gather this information from publicly visible sources or through basic reconnaissance.
Fatigue and Automation
After years of using legitimate QR codes for menus, directions, and product information, your brain has automated the action of scanning. It doesn't feel like a decision anymore—it feels like a normal action that doesn't require consideration. This automation is precisely what attackers exploit.
When actions become automated, they bypass your conscious critical evaluation. You don't think before you scan a QR code for a menu because you've done it hundreds of times. That automation is the vulnerability.

How to Identify Suspicious QR Codes
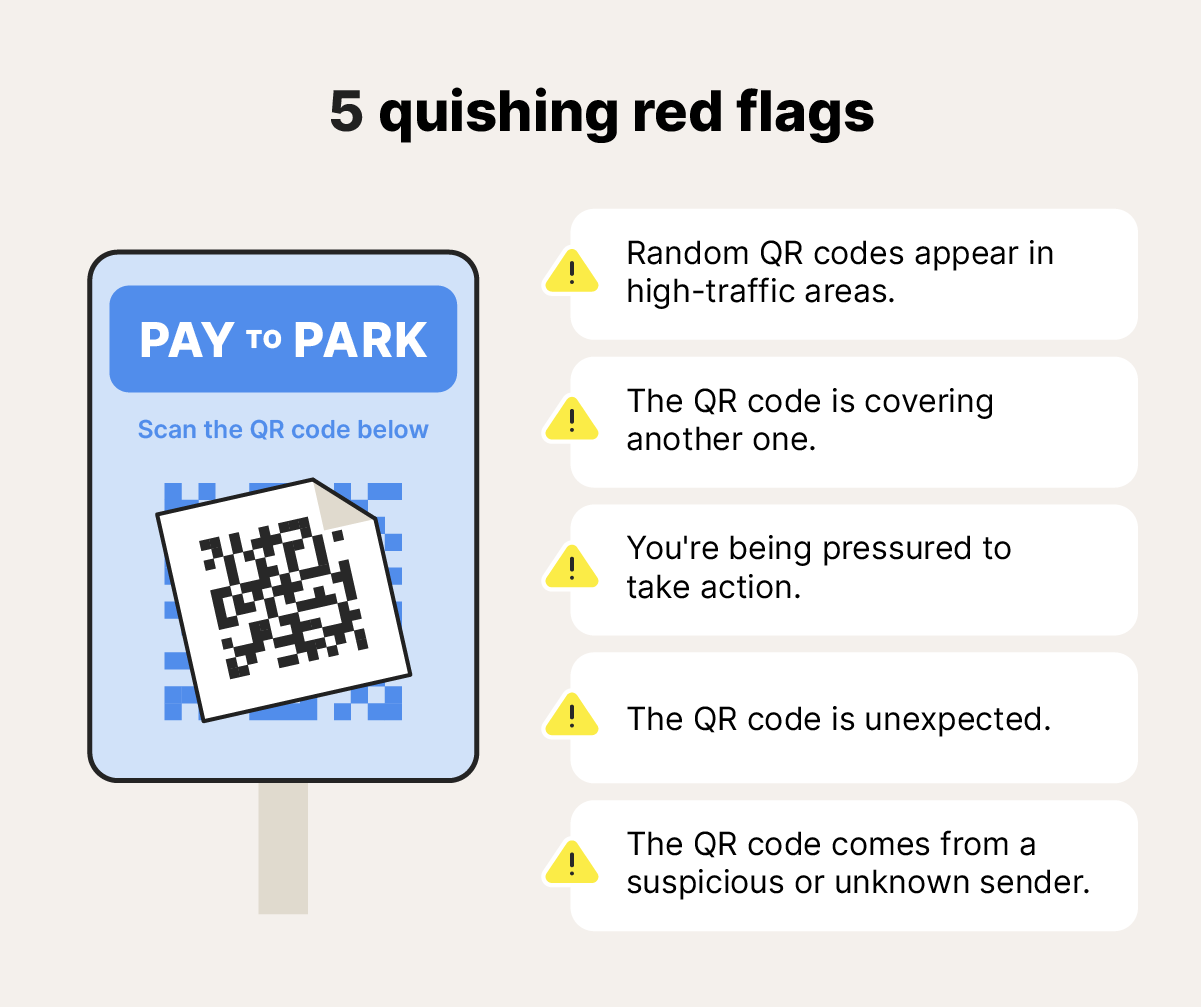
While no method is foolproof, there are several signs that should raise your suspicion and cause you to pause before scanning a QR code.
Visual Inspection Techniques
The first step is to look at the QR code itself before you scan it. Is the code printed clearly, or is it pixelated and difficult to read? Legitimate QR codes are usually printed with good quality. A damaged or pixelated code might indicate a hastily created malicious code.
Look at the context. Is the QR code in a place where you would expect to see one? If you see a QR code on a parking meter, that might be normal if you live in a city that uses digital parking systems. But if you see a QR code on a random sticker attached to a street sign, that's unusual.
Check for physical tampering. Is the QR code a sticker that appears to be pasted over another code? Are there edges around the code that suggest it was added later? Attackers often place their codes directly over legitimate ones. If you notice a QR code that looks like it's been added or modified, avoid it.
Contextual Red Flags
Consider the context of the QR code's placement. Is it in a location where it makes sense? A QR code for a restaurant menu in a restaurant makes sense. A QR code for a restaurant menu in a random parking lot does not.
Pay attention to any accompanying text. Legitimate QR codes often have explanatory text nearby: "Scan here for our menu" or "Learn more about our products." If a QR code has no explanation or the explanation seems vague or suspicious, be cautious.
Think about the request the QR code is making. Is it asking you to do something unusual? If a QR code promises something too good to be true—free money, instant prizes, exclusive offers—approach with extreme skepticism.
Verification Steps Before Scanning
If you're unsure about a QR code, verify through alternative means. If the code is supposed to take you to a restaurant's menu, go to the restaurant's website directly rather than scanning the code. If the code is supposed to provide information about a product, search for that product on the manufacturer's website.
Asking the organization directly is also effective. If you see a QR code in a store, ask a store associate where the code points to. If they can't tell you or seem unsure, that's a red flag.
Mobile Device Indicators
Some newer phones show a preview of the QR code destination before opening it. If your phone has this feature, use it. Look at the URL that the code points to before allowing your device to navigate there.
Note that some phones will also block QR codes that point to known malicious URLs. This protection isn't perfect, but if your phone warns you about a QR code, definitely don't scan it.
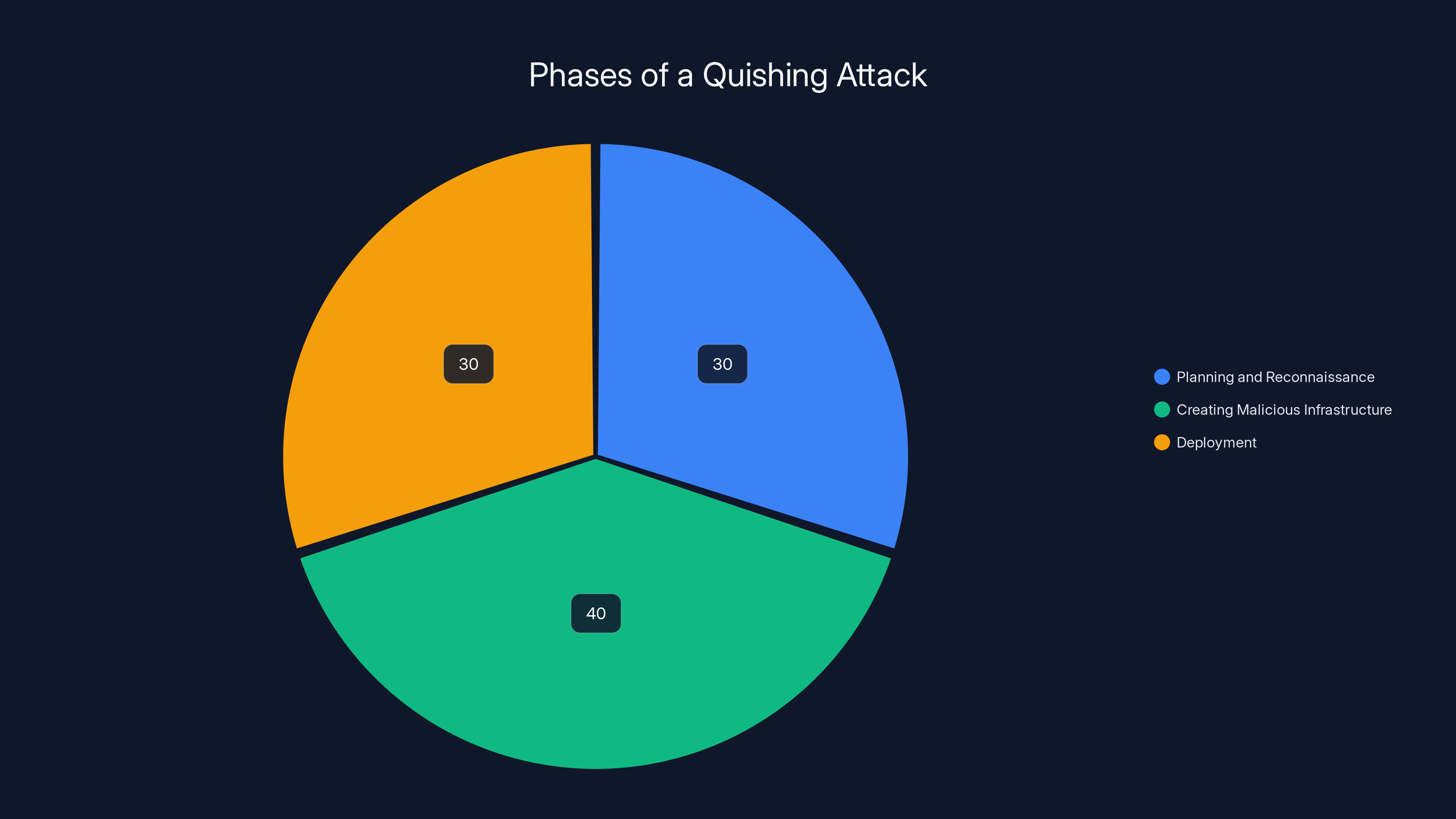
Estimated data shows that creating malicious infrastructure requires the most effort in a quishing attack, followed by planning and reconnaissance, and deployment.
Technical Defenses Against Quishing Attacks
While user awareness is critical, technical defenses provide multiple layers of protection. A combination of technical and behavioral strategies offers the best protection.
VPN and Network-Level Protection
Using a reputable VPN service adds a layer of protection against quishing in several ways. First, a VPN encrypts your connection, making it harder for attackers to monitor your traffic and extract data. Second, many VPNs include built-in malware and phishing protection that can block known malicious domains.
When you scan a malicious QR code while connected to a VPN, the VPN's security features might recognize the destination as malicious and warn you or block the connection entirely. This doesn't protect you from phishing attacks where you've already entered credentials, but it can prevent you from landing on the malicious page in the first place.
For corporate environments, organizations should require employees to use VPNs when scanning QR codes or connecting to public Wi-Fi. This is particularly important in organizations where employees regularly use QR codes to access internal systems.
Browser Security Features
Modern browsers like Chrome, Firefox, Safari, and Edge include built-in protection against phishing and malware. These browsers maintain lists of known malicious domains and will warn you or block you from visiting them.
When you scan a QR code and land on a malicious page, your browser might recognize it as a known phishing site and display a warning. These warnings aren't always foolproof—sophisticated attacks can evade browser protections—but they provide valuable protection against the majority of quishing attacks.
Enabling browser security features is essential. This includes:
- Safe browsing enabled (default in most browsers)
- Automatic updates to ensure you have the latest phishing definitions
- JavaScript restrictions if you're particularly security-conscious
- Extension blockers that prevent malicious extensions from being installed
Two-Factor Authentication (2FA) and Passwordless Authentication
Even if attackers steal your username and password through a quishing attack, two-factor authentication provides a critical second layer of defense. If your account has 2FA enabled, an attacker who has your credentials still cannot log in without the second factor (usually a code from your phone).
Passwordless authentication methods like Windows Hello, biometric authentication, or passkeys are even more secure because they don't rely on passwords that can be stolen through quishing. When you use biometric or device-based authentication, a quishing attack that tricks you into entering credentials is pointless because those credentials are never used for actual authentication.
All of your critical accounts—email, banking, social media, cloud storage—should have 2FA or passwordless authentication enabled. Yes, it adds an extra step to logging in, but that extra step can prevent complete account compromise.
QR Code Scanning Apps with Security Features
If you regularly scan QR codes, consider using a dedicated QR code scanning app that includes security features. Some QR code apps display the destination URL before opening the link, allowing you to verify the destination. Others include databases of known malicious QR codes.
Built-in camera apps on modern phones often have basic QR code scanning, but specialized apps might offer more security features. Research QR code apps that prioritize security and provide URL preview functionality.
Email Security and Employee Training
For organizations, email security tools should be configured to detect and warn about QR codes in emails. While this can't prevent employees from scanning physical QR codes they encounter in the real world, it can prevent attacks distributed through email.
Employee training is equally important. Teach employees what quishing is, show them examples of attacks, and explain the organizational policies around QR code scanning. Regular security awareness training should include modules on quishing attacks.
Device-Level Protections
Keep your device's operating system and all applications up to date. Security updates often patch vulnerabilities that could be exploited through malicious URLs or compromised landing pages.
Use a reputable mobile antivirus or security app. While these can't prevent you from scanning a malicious QR code, they can detect malware that might be installed through certain types of attacks.
Disable automatic installation of apps and restrict app permissions. If a malicious QR code tries to trigger an app installation, these restrictions will prevent it.
Organizational Defenses: Protecting Your Business from Quishing
For organizations, quishing presents a significant risk because it can compromise employee credentials, which then provide attackers with access to corporate systems. Organizations need comprehensive strategies to address this threat.
Policy Development and Implementation
Create clear policies around QR code scanning, especially for accessing sensitive systems. Policies might include:
- Employees should never scan QR codes to access corporate systems or enter credentials
- Only use official applications or web addresses provided by IT for accessing company systems
- If unsure about a QR code, contact IT support before scanning
- Report any suspicious QR codes immediately
These policies should be documented, communicated clearly to all employees, and reinforced through regular training.
Training and Awareness Programs
Develop comprehensive training programs that educate employees about quishing attacks. Training should include:
- Real examples of quishing attacks
- How to identify suspicious QR codes
- The types of attacks employees in your organization are likely to encounter
- Step-by-step procedures for what to do if they've scanned a suspicious QR code
- The importance of immediately reporting suspected attacks
Make the training interactive and engaging. Dry, boring security training is forgotten quickly. Use simulations, phishing tests, and scenario-based training to help employees truly internalize the threat.
Technical Controls for Employees
Implement technical controls that protect employees even if they fall for a quishing attack:
- Mandatory VPN usage for all employees, with particular emphasis on scanning QR codes outside the office
- Enhanced security policies that require additional verification before accessing sensitive systems
- Conditional access controls that require additional authentication if login occurs from an unusual location or device
- URL filtering that blocks known malicious domains at the network level
- Mandatory 2FA for all corporate accounts, especially email and VPN access
Monitoring and Response
Implement monitoring systems that detect suspicious activity that might indicate a quishing attack. This includes:
- Unusual login patterns from employee accounts (multiple login attempts from different locations, logins at unusual times, failed 2FA attempts)
- Data exfiltration from employee accounts
- Password changes initiated by users outside normal IT processes
- Mass email forwarding or rules that might indicate account compromise
When suspicious activity is detected, trigger an immediate response. This might include disabling the account, forcing a password reset, revoking active sessions, and contacting the employee to determine if they fell for an attack.
Third-Party and Partner Risk Management
If your organization works with external partners, contractors, or vendors, assess their quishing vulnerability. Partners who have access to your systems should also implement protection measures.
When communicating with partners through email or messaging, be cautious about including QR codes. If you need to share links, consider more secure methods like password-protected portals or encrypted channels.
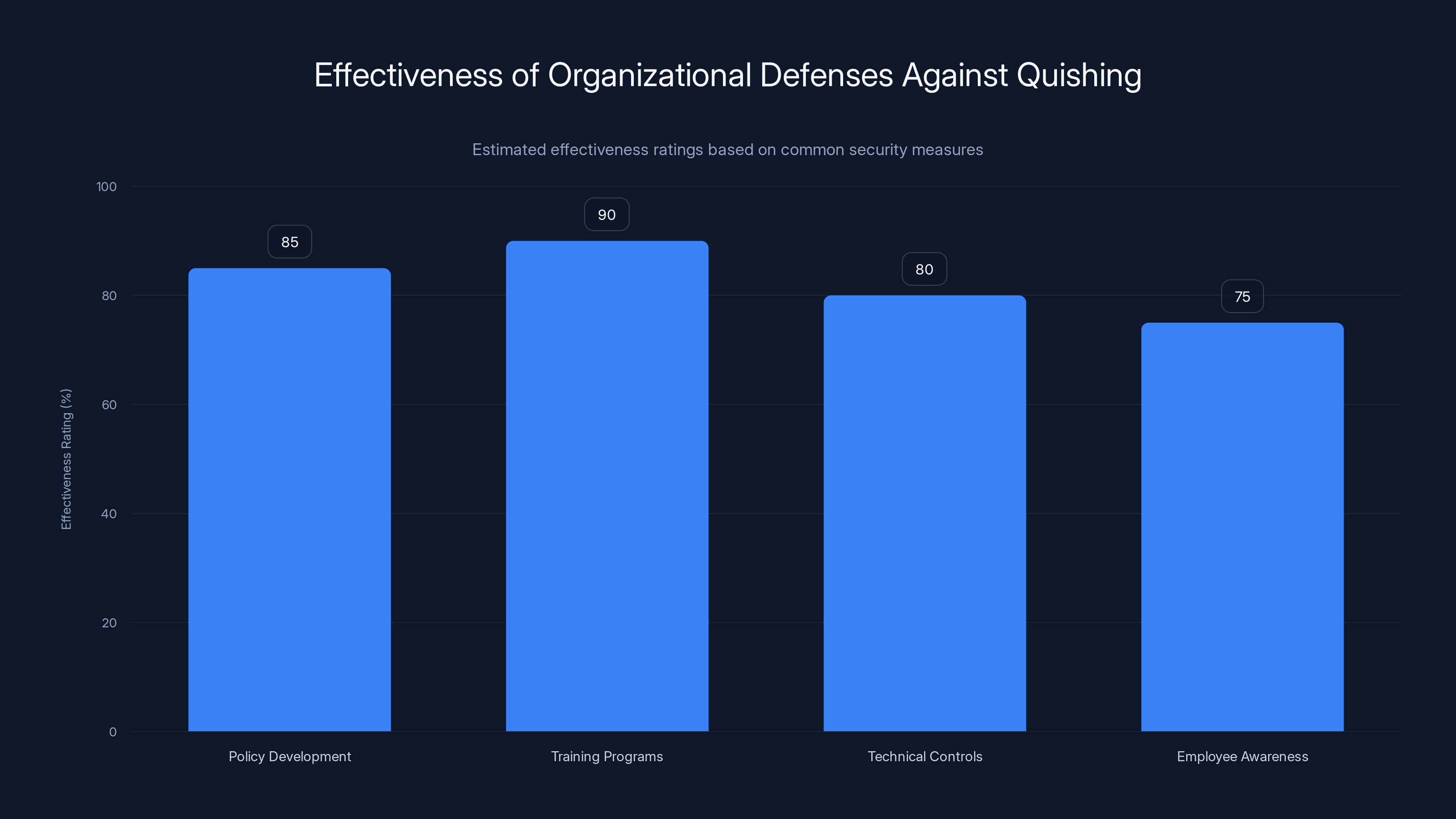
Training programs are estimated to be the most effective defense against quishing, with a 90% effectiveness rating, followed by policy development at 85%. Estimated data.
What to Do If You've Fallen for a Quishing Attack
If you suspect that you've scanned a malicious QR code or entered credentials on a phishing page, take immediate action. The faster you respond, the less damage can occur.
Immediate Actions
Step 1: Stop and Assess. If you've scanned a QR code and entered information, don't panic. Focus on determining exactly what information was compromised. Did you enter just an email address? A password? Payment information? The scope of what was compromised determines your next steps.
Step 2: Change Your Password. If you entered a password on a phishing page, change it immediately. Use a computer or device that you're confident is secure (not the device you used for the phishing attack). Go to the legitimate website of the service whose credentials you entered and change your password.
When changing your password, create a completely new password that's different from your previous one. Don't just make a small modification. Use a password manager to generate a strong, unique password.
Step 3: Check Account Activity. Log into your account (using the legitimate website, not any link from an email) and check for suspicious activity. Look for:
- Recent login attempts from unknown devices or locations
- Changed email address or recovery options
- Changes to notification settings or forwarding rules
- Unusual account activity or transactions
If you see suspicious activity, immediately take steps to secure your account further.
Step 4: Enable or Verify 2FA. If the compromised account doesn't have two-factor authentication enabled, enable it immediately. Even if it does have 2FA, verify that the phone number or email address associated with 2FA hasn't been changed by an attacker.
Step 5: Report the Phishing. Report the QR code and phishing page to the legitimate organization whose service was being impersonated. Most organizations have a security contact or phishing report email address where you can report attacks. This helps them warn other users and take down malicious pages.
Broader Account Security Audit
If you've fallen for a phishing attack, use it as an opportunity to audit your broader account security.
Check linked accounts and services. If attackers have your email password, they can potentially reset passwords for other services that use email recovery. Check your email recovery and security options. If your email has been compromised, review what other services use that email as their account email or recovery method.
Review permissions and integrations. Check if the compromised service has any third-party applications or integrations connected to it. Attackers often use compromised accounts to access connected services.
Consider a credit freeze or fraud alert. If payment information was compromised, consider placing a fraud alert with the three major credit reporting agencies (Equifax, Experian, TransUnion) or a credit freeze. This prevents attackers from opening new accounts in your name.
Monitor credit and financial accounts. Keep a close watch on your credit reports and financial accounts for the next several months. You can get free credit reports from Annual Credit Report.com. Sign up for fraud monitoring services if your information was compromised.
Recovering from Account Compromise
If attackers actually gained access to your account beyond just stealing credentials, recovery is more complex.
Contact the service provider directly. Call the customer support number from the official website (not any number provided by the attacker or in suspicious emails). Explain that your account has been compromised and ask what recovery steps they recommend.
Document everything. Keep detailed records of what happened, when you discovered it, and what actions you've taken. This documentation is important if you need to dispute fraudulent charges or if the service provider needs to investigate the attack.
Work with law enforcement if necessary. If significant financial fraud occurred, file a report with the FBI's Internet Crime Complaint Center (IC3). While they may not directly investigate your case, the reports help law enforcement identify patterns and large-scale criminal operations.
Follow the service provider's recovery process. Different services have different account recovery procedures. Follow their procedures precisely and maintain communication with their support team.
Best Practices for Safe QR Code Scanning
QR codes aren't inherently dangerous. They're a legitimate technology with many legitimate uses. The key is developing safe habits around scanning them.
Before You Scan
Make scanning QR codes a deliberate action rather than an automatic one. Before scanning, pause and ask yourself these questions:
- Do I expect to see a QR code in this location?
- Does the context make sense? Is there a legitimate reason for this code to be here?
- Can I verify the source? Can I check independently that this QR code belongs to the organization it purports to be from?
- What information will I be asked to provide if I scan this code?
- Is there an alternative way to access what this QR code supposedly points to without scanning it?
If you can't answer these questions satisfactorily, don't scan.
During Scanning
When you scan a QR code, take advantage of your phone's preview features if available. On newer iPhones, you can hold the camera on a QR code and a notification will appear showing what website it points to. Look at that URL before you tap to open it. Does it look legitimate? Is it a domain you recognize? Are there any typos or suspicious characters?
On Android phones, long-press on a QR code in your camera app (if your phone supports it) to see a preview before opening.
If you're using a dedicated QR code scanning app, use the preview feature if available.
When You Land on a Website
After scanning a QR code and landing on a website, look carefully at the URL in your address bar. Does it match what you expected? Are you on the legitimate website of the organization?
Before entering any information, verify you're on the correct website. Look for:
- The correct domain name (be careful of look-alike domains with extra characters)
- A valid SSL certificate (look for the padlock icon in the address bar)
- The correct branding and layout of the legitimate website
- No unusual prompts or requests for information you wouldn't normally provide
If anything feels off, don't enter information. Navigate away and access the service through a different means.
After Scanning
Even after you've scanned a code and accessed what seems to be a legitimate service, remain cautious if you're asked for sensitive information. Legitimate services rarely ask you to re-enter your credentials, especially without context or explanation.
If a website asks you to log in immediately after scanning a QR code, be suspicious. Legitimate services would display content first and only ask for login if you were trying to access personal account information.
Future of Quishing: Emerging Trends and Evolving Threats
Quishing is still a relatively new attack vector, and attackers are constantly evolving their techniques. Understanding emerging trends can help you stay ahead of the threat.
Advanced QR Code Techniques
Attackers are developing more sophisticated QR code techniques that make them harder to detect. Some of these include:
Animated QR codes: Instead of a static image, animated QR codes that change based on how long you look at them or from different angles. This makes it harder to detect that the code has been replaced or tampered with.
3D QR codes: Exploiting depth and perspective to make malicious codes blend in with legitimate ones in photographs or mixed reality environments.
Personalized QR codes: Using analytics to determine which codes are most effective against certain demographics or in certain locations, then deploying specifically targeted malicious codes.
Targeting Specific Industries
Attackers are increasingly targeting specific industries with tailored quishing attacks. Healthcare organizations are being targeted with codes that impersonate patient portals or insurance portals. Financial institutions are targeted with codes that appear to be from their banks. Retail organizations are targeted with codes on products or in stores.
As attackers learn which industries are most vulnerable, attacks in those industries will become more sophisticated and personalized.
Integration with Other Attack Vectors
Quishing is increasingly being combined with other attacks. For example:
Quishing plus malware: A malicious QR code redirects you to a page that not only harvests credentials but also attempts to install malware on your device.
Quishing plus social engineering: An attacker combines a quishing campaign with phone calls or other social engineering to make the attack more convincing.
Quishing plus data mining: An attacker uses credentials stolen through quishing to gain access to systems, then uses those systems to steal broader data or identify additional targets.
AI and Machine Learning in Quishing
Future quishing attacks might use AI to create more sophisticated phishing pages that adapt in real-time to the user. Machine learning could be used to:
- Automatically generate phishing pages that match any website with high fidelity
- Adapt the attack based on the user's actions and responses
- Identify the most effective messages and page designs for different demographics
- Evolve attacks automatically when they're detected as malicious
Defenses will need to evolve in parallel to detect and prevent these more sophisticated attacks.
FAQ
What is quishing and how is it different from traditional phishing?
Quishing is a phishing attack that uses QR codes instead of email links or attachments. The fundamental difference is the attack vector. Traditional phishing requires you to click a link or download an attachment, giving you a chance to see the destination. Quishing redirects you immediately upon scanning without showing the URL, making it harder to detect. The destination URL is completely hidden until after you've already scanned the code.
How many people have been exposed to quishing attacks?
According to multiple cybersecurity reports, approximately 26 million individuals have been exposed to quishing attacks as of 2024. However, this number likely underestimates the actual exposure because many victims never discover they've been compromised. The actual number could be significantly higher, with estimates from some security researchers suggesting the exposure rate is doubling annually.
Can I scan a QR code safely?
Yes, you can scan QR codes safely by following several precautions. Pause before scanning to verify that the code's location makes sense. Use your phone's preview feature to see the URL before opening it. Look carefully at the website after scanning to verify it's legitimate. Only enter credentials or sensitive information on pages you're confident are authentic. When in doubt, access the service directly through your browser rather than through a QR code.
What should I do if I accidentally scanned a malicious QR code?
First, assess what information was compromised. If you entered a password, change it immediately on the legitimate website. If you provided payment information, contact your bank or credit card company. Enable two-factor authentication if it's not already enabled. Monitor your accounts for suspicious activity. Report the malicious QR code to the legitimate organization being impersonated. Consider placing a fraud alert with credit bureaus if payment information was involved.
How can I tell if a QR code is malicious before scanning it?
While no method is completely foolproof, several signs should raise suspicion. Look for codes that are damaged, pixelated, or appear to be stickers pasted over other codes. Be suspicious of QR codes in unusual locations or with vague accompanying text. If the code promises something too good to be true, approach with skepticism. Use your phone's preview feature to see the URL before opening. When in doubt, verify the link by accessing the service directly rather than scanning the code.
Do I need to use a VPN to protect against quishing attacks?
While a VPN isn't a complete defense against quishing, it adds a valuable layer of protection. A VPN encrypts your connection and can block known malicious domains. If you regularly scan QR codes, especially in public places or untrusted environments, using a VPN significantly reduces your risk. However, a VPN won't prevent you from entering credentials on a phishing page, so user awareness remains critical.
What's the best way to report a suspicious QR code?
If you discover a malicious QR code, report it to the legitimate organization being impersonated. Most large organizations have a security contact or phishing report email address. Additionally, report it to your local law enforcement and the FBI's Internet Crime Complaint Center (IC3) at ic3.gov. If the code is in a public place, alert the organization that manages the location (a restaurant, parking lot, etc.) so they can remove the malicious code.
Can older phones get infected by scanning a malicious QR code?
Older phones might be at higher risk in certain scenarios. Older devices might not have the latest browser security features or the ability to preview QR code URLs. Additionally, some older phones might have vulnerabilities that could be exploited through specially crafted URLs. However, the most common quishing attacks rely on phishing rather than exploiting technical vulnerabilities, so older phones are at risk from the same attacks as newer devices.
Are there specific industries that are targeted more frequently by quishing attacks?
Yes, certain industries are targeted more frequently. Financial services are heavily targeted because of the high value of banking credentials. Healthcare is targeted because of valuable patient information and insurance data. Retail is targeted because of payment information and customer data. Technology companies are targeted because of the sensitive systems employees can access. Understanding your industry's particular risks helps you develop targeted defenses.
How does my organization implement quishing defenses at scale?
Organizational defenses should be multi-layered. First, develop clear policies around QR code scanning and credential entry. Provide regular employee training with real examples and scenarios. Implement technical controls like mandatory VPNs, enhanced authentication, and network-level URL filtering. Monitor for unusual account activity that might indicate a compromised credential. Establish an incident response process so that when employees suspect they've fallen for an attack, they can quickly report it and take corrective action. The most effective organizations combine policy, training, technology, and response processes.
Conclusion: Taking Control of Your Security
Quishing represents a genuine and growing threat in 2024 and beyond. Unlike traditional phishing, which relies on getting you to click a link, quishing leverages the implicit trust people have in QR codes to compromise accounts with minimal friction. The fact that 26 million individuals have already been exposed demonstrates how quickly this attack vector has matured.
But quishing is far from unstoppable. By understanding how these attacks work, recognizing the psychological tactics attackers use, and implementing concrete defenses, you can significantly reduce your risk. The key is moving from passive acceptance of QR codes to active skepticism paired with deliberate safety practices.
For individuals, this means developing new habits. Before you scan any QR code, pause. Verify the context. Use your phone's preview features. Think before you provide credentials. These small behavioral changes dramatically reduce your vulnerability to quishing attacks.
For organizations, the challenge is more complex but manageable. You need to balance security with usability, because organizations can't simply ban QR codes—they're too useful for legitimate purposes. Instead, you need comprehensive strategies that combine clear policies, employee training, technical controls, and rapid response capabilities.
The threat landscape will continue to evolve. Attackers will develop more sophisticated techniques. They'll use AI to create more convincing phishing pages. They'll target specific industries with tailored attacks. But if you stay informed, maintain healthy skepticism, and implement layered defenses, you can protect yourself and your organization from these attacks.
The future of security isn't about eliminating all threats—that's impossible. It's about understanding threats, implementing smart defenses, and maintaining the kind of critical thinking that our ancestors used to survive in a dangerous world. QR codes are safe when you approach them with the same level of skepticism you'd apply to any unfamiliar technology.
Start today. Check if your critical accounts have two-factor authentication enabled. Set aside time to educate yourself on quishing attacks. If you're responsible for an organization, begin developing an organizational quishing defense strategy. Share what you've learned with friends and family. The more people understand this threat, the less effective it becomes.
Your security is in your hands. Use it wisely.

Key Takeaways
- Quishing is a phishing attack using QR codes that bypasses traditional email security defenses and exploits user trust in QR code technology.
- 26 million individuals have been exposed to quishing attacks, with the threat growing exponentially as attackers refine their techniques.
- QR codes are particularly dangerous because users don't see the destination URL before scanning, and the attack requires minimal friction or user skepticism.
- Multi-layered defense combining behavioral practices (pausing before scanning, verifying URLs) with technical controls (VPNs, 2FA, browser security) significantly reduces quishing risk.
- Organizations must develop comprehensive quishing strategies including clear policies, employee training, technical controls, monitoring systems, and incident response procedures.
Related Articles
- CISA End-of-Life Edge Device Replacement Guide [2025]
- DNS Malware Detour Dog: How 30K+ Sites Harbor Hidden Threats [2025]
- Best VPNs for Super Bowl LIX: Complete Streaming Guide 2025
- NordVPN Complete Plan 70% Off: Full Breakdown [2025]
- Network Modernization for AI & Quantum Success [2025]
- dYdX Supply Chain Attack: How Malicious NPM Packages Emptied Wallets [2025]
![Quishing: The QR Code Phishing Scam Taking Over [2025]](https://tryrunable.com/blog/quishing-the-qr-code-phishing-scam-taking-over-2025/image-1-1770637036047.jpg)



