Introduction: When Blockchain Companies Aren't Immune to Breaches
Figure Technology, a fintech lending platform built on blockchain infrastructure, did what most companies dread: confirm a significant data breach. The announcement came quietly at first, but the details that followed painted a concerning picture of how sophisticated social engineering attacks can compromise even technology-forward companies.
On a Friday afternoon in February 2026, Figure's spokesperson confirmed the breach originated through a classic attack vector that has plagued enterprises for years. A single employee fell victim to social engineering tactics, granting hackers access to the company's systems. This single compromised account opened doors to internal data that should have been protected by multiple layers of security.
What makes this breach particularly noteworthy isn't just the compromise itself, but what it reveals about the fintech industry's actual security posture. While blockchain companies market themselves as secure by design, decentralized, and technologically superior, the Figure breach demonstrates a harsh reality: technology is only as strong as the human behaviors that use it.
The hacking group Shiny Hunters didn't just claim responsibility. They published 2.5 gigabytes of allegedly stolen data on their dark web leak site, claiming Figure refused to negotiate a ransom. This information included customer full names, home addresses, dates of birth, and phone numbers. For customers whose financial data was exposed, the implications extend far beyond embarrassment.
This article dives deep into what happened at Figure, why social engineering remains the most effective attack vector in 2025, and what both businesses and individuals can do to protect themselves in an increasingly hostile threat landscape. We'll examine the breach mechanics, the attackers behind it, the regulatory implications, and practical steps to mitigate your personal risk.
TL; DR
- Figure Technology confirmed a major data breach affecting an undisclosed number of customers through a social engineering attack on a single employee
- 2.5 gigabytes of sensitive data was stolen, including customer names, addresses, birthdates, and phone numbers
- Shiny Hunters, a known hacking group, claimed responsibility and published the data after Figure refused to pay ransom
- The breach wasn't through blockchain infrastructure but through traditional employee account compromise, highlighting a critical vulnerability
- Okta SSO was implicated in the broader campaign that affected Figure, Harvard University, and University of Pennsylvania
Fintech companies are prime targets due to handling sensitive data, varying security maturity, and being attractive to organized crime. Estimated data highlights key vulnerabilities.
What Exactly Is Figure Technology?
Before understanding the breach, you need context on what Figure actually does and why it matters that their systems were compromised.
Figure Technology positions itself as a blockchain-based lending platform. The company uses distributed ledger technology to enable faster loan origination, underwriting, and settlement. In theory, blockchain should eliminate intermediaries, reduce fraud, and increase transparency. Figure's pitch to the financial services industry has been compelling enough to attract serious institutional interest.
The company operates in the fintech lending space, competing with both traditional banks and newer digital lending platforms. Their customers include borrowers seeking loans and potentially institutional partners looking for lending infrastructure. The variety of customer types means the data breach affects multiple constituencies with different risk profiles.
What's critical to understand is that Figure is a fintech company, not a cryptocurrency exchange. They're managing sensitive financial data, personal information, and loan histories. This isn't speculative crypto trading data, but real credit information tied to real people's financial lives. When a company like this gets breached, the downstream effects ripple through the entire financial ecosystem.
Figure raised significant venture capital, positioning themselves as an innovator in the blockchain-based finance space. This combination of growth-stage startup and sensitive financial data created an attractive target for sophisticated threat actors. The company was well-funded enough to presumably have valuable data, but potentially still operating with startup-level security practices.

The breach exposed full names, home addresses, dates of birth, and phone numbers equally. No credit card or Social Security numbers were compromised. Estimated data.
The Social Engineering Attack: How One Employee Compromised Everything
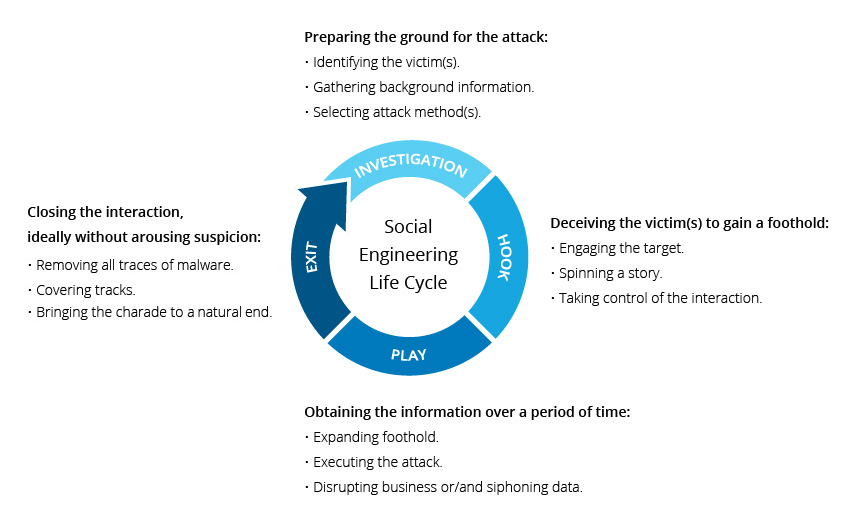
Social engineering isn't new, but it remains devastatingly effective. The Figure breach followed a playbook that's worked countless times before: identify a target employee, build trust, extract credentials or authorization, then pivot into the network.
According to Figure's statement, hackers used social engineering to trick an employee. The statement was deliberately vague about specifics, which is typical for companies in breach response mode. But we can infer the likely attack pattern from what we know about modern social engineering campaigns.
The attacker probably started with reconnaissance. LinkedIn and company websites reveal who works at Figure, their job titles, and potentially their professional interests. The attacker might have created a fake identity, perhaps posing as an IT support person, a vendor, or even someone from another team at Figure.
The social engineering likely came through email, phone, or possibly through a platform like LinkedIn or Slack. The goal wasn't subtle technical hacking, but rather psychological manipulation. Get the employee to click a malicious link, enter credentials into a fake login page, or provide sensitive information willingly.
Once the attacker had valid credentials or access, they had a foothold inside Figure's network. From there, they could explore the environment, escalate privileges, and hunt for valuable data. The company said hackers downloaded "a limited number of files," which could mean anything from a few megabytes to multiple gigabytes. Shiny Hunters later published 2.5 gigabytes, suggesting the attackers were quite thorough.
What's troubling about this attack vector is how scalable it is. The attacker didn't need to find zero-day vulnerabilities or break encryption. They needed to understand human psychology and exploit the trust that organizations build into their workplace culture. Most companies encourage employees to be helpful, responsive, and accommodating. Attackers weaponize these qualities.
Shiny Hunters: The Hacking Group Behind the Breach
Shiny Hunters isn't an unknown quantity in the cybersecurity landscape. They're a known threat actor group that has operated publicly and relatively brazenly for years. Understanding who they are provides context for how serious this breach actually is.
Shiny Hunters operates on the dark web, maintaining a presence on leak sites where they publish data allegedly stolen from victims who refuse to pay ransom demands. They announce their operations publicly, claiming credit for breaches, and using these announcements as leverage to pressure targets into negotiating.
The group's existence is known to security researchers, law enforcement, and enterprise security teams. They don't hide their identity in the traditional sense, but they do maintain operational security that keeps them largely ahead of law enforcement. They've claimed responsibility for breaches affecting various industries, from retail to healthcare to finance.
What's notable about Shiny Hunters claiming the Figure breach is the apparent connection to a broader campaign. According to reporting, Figure was among victims targeted in a campaign that exploited a vulnerability or misconfiguration in Okta, a widely-used single sign-on provider. Okta is the authentication layer that many enterprises use to manage employee access across multiple applications.
If Okta was compromised or misconfigured, the attacker could potentially access not just Figure, but any other organization using Okta for authentication. This is why Shiny Hunters mentioned other victims like Harvard University and the University of Pennsylvania in connection with the same campaign. One underlying security issue created multiple breach opportunities.
Shiny Hunters' method is straightforward: find data, extract it, demand ransom, then publish to maintain credibility and pressure. When Figure refused to pay, Shiny Hunters followed through on the threat, publishing the data publicly. This isn't sophisticated extortion in the traditional sense, but it's highly effective.
Figure Technology holds an estimated 15% market share in the fintech lending space, competing with traditional banks and digital lending platforms. Estimated data.
The Okta Connection: A Systemic Vulnerability
The Okta angle is where this breach becomes bigger than just Figure. If Okta was the underlying vulnerability, the potential impact extends to thousands of organizations using Okta for employee authentication.
Okta provides identity and access management services to hundreds of thousands of organizations worldwide. The platform handles employee authentication, manages access permissions, and serves as the central authentication layer for enterprise software. When Okta has a vulnerability or security issue, it can impact every organization that depends on it.
The reporting that Shiny Hunters targeted Okta customers suggests this wasn't a random attack but a coordinated campaign against a specific infrastructure weakness. The victims mentioned, including Harvard University and University of Pennsylvania, all potentially used Okta for employee authentication.
This is a critical security distinction. It means that Figure's breach might not have been caused by a flaw in Figure's own security practices, but rather by a compromise or misconfiguration in a third-party service they depend on. This actually makes the situation more systemic and more concerning. Companies can't fully control the security of services they depend on, yet their data is at risk if those services are compromised.
For organizations using Okta, the breach should trigger a thorough audit. Security teams need to review authentication logs, check for suspicious activity, and verify that access controls were properly configured. The incident reinforces a critical security principle: you're only as secure as your most vulnerable dependency.
The Okta angle also explains why Figure might have been relatively unprepared. If the vulnerability was in Okta and not in Figure's own systems, Figure might not have discovered the breach through their own monitoring. They might have only learned about it when Shiny Hunters announced it or when security researchers notified them.
What Customer Data Was Actually Exposed?
Shiny Hunters published information about what was taken. Security researchers and journalists who examined the leaked data confirmed its contents. Understanding exactly what was exposed helps assess personal risk.
The leaked data included customer full names, home addresses, dates of birth, and phone numbers. This is classic personal information that forms the foundation for identity theft. With a name, address, and birthdate, an attacker can attempt to reset passwords on various accounts, open new accounts, or sell the information to other criminals.
The data didn't include credit card numbers or Social Security numbers from what was publicly reported, which is somewhat fortunate. Those would have presented more acute financial risk. However, the personal information exposed is still valuable and dangerous.
Figure's statement said that a "limited number of files" were downloaded, which creates ambiguity about the total scope. Did the hackers access a sample of customer records, or a significant percentage of the entire customer database? The company hasn't disclosed the exact number of affected customers, which is frustrating for those trying to assess personal risk.
The company is offering free credit monitoring to customers who receive breach notification notices. This is standard practice, though it's more of a gesture than comprehensive protection. Credit monitoring helps identify if someone opens accounts in your name, but it doesn't prevent identity theft itself.

International cooperation and forensic investigation are key to successful cybercrime prosecutions, while jurisdictional challenges remain a significant hurdle. Estimated data.
The Timeline: When Figure Discovered the Breach
Public breaches often have a significant lag between when the breach occurs and when organizations discover it. The Figure breach timeline illustrates this gap.
Figure didn't discover the breach immediately. The company became aware after Shiny Hunters announced it publicly or after some other notification occurred. This gap is crucial because it means hackers had time to explore the network, exfiltrate data, and establish persistence before Figure knew anything was wrong.
The exact timeline isn't entirely clear from Figure's statements, which provided minimal detail. The company confirmed the breach on Friday and indicated they're working with partners and law enforcement, suggesting investigation was already underway. But how long had the breach been active before discovery? Days? Weeks? Months?
This is a persistent problem in cybersecurity. The average time to detect a breach is measured in months. Hackers typically operate with more time than defenders realize. They can move slowly, avoiding detection, and create multiple persistence mechanisms to maintain access even if the initial entry point is closed.
Figure's rapid public disclosure is actually positive from a customer communication standpoint. However, the delay between the actual breach and discovery represents a critical window where customer data could have been copied, exfiltrated, and potentially already sold or published elsewhere.

Regulatory and Legal Implications for Figure
Data breaches trigger extensive regulatory obligations, and Figure faces several layers of regulatory scrutiny depending on which jurisdictions their customers reside in.
If Figure has customers in California, they must comply with the California Consumer Privacy Act and California's breach notification laws. These laws require notification within a specific timeframe, free credit monitoring, and specific disclosures about the nature of the breach. Failure to comply can result in significant fines and class action litigation.
If Figure operates in other states or internationally, they must comply with various state and international data protection laws. The General Data Protection Regulation in Europe imposes strict requirements on any company processing data of EU residents. Other states like New York, Massachusetts, and Virginia have increasingly stringent data protection laws.
Figure's breach notification letters to customers will need to provide specific information: what data was exposed, what happened, what customers should do, and contact information for more details. The company's notification letters are likely still being prepared and sent as of the time of this breach.
The financial implications are substantial. Legal fees for breach response can reach millions of dollars. Class action lawsuits are likely, though the success of such suits varies. Settlement amounts for breaches like this typically range from a few million to tens of millions of dollars, depending on the number of affected customers and the sensitivity of the exposed data.
Figure also faces potential regulatory investigation from state attorneys general and federal agencies if any customer complaints are filed. The company's response to the breach, including their communication with customers and their security practices, will be scrutinized.
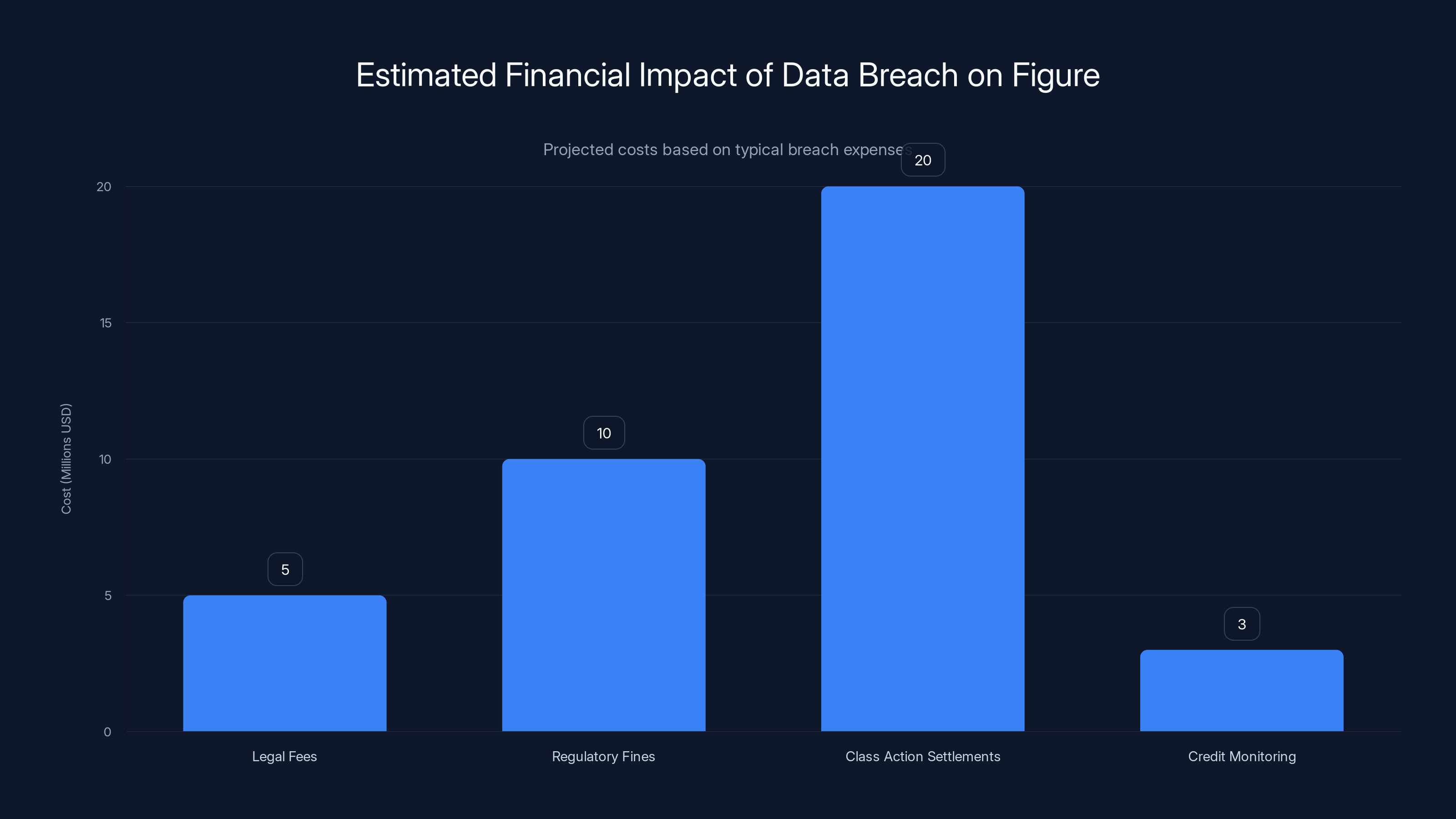
Estimated data shows legal fees, fines, settlements, and credit monitoring could cost Figure tens of millions. Estimated data.
Industry Context: Why Fintech Companies Are Prime Targets
Figure isn't the first fintech company to suffer a major breach, and unfortunately won't be the last. Understanding why fintech is such an attractive target helps contextualize this incident.
Fintech companies handle sensitive financial information and personal data. Unlike traditional banks that have been fortified with security practices for decades, many fintech startups are newer, leaner, and sometimes less mature in their security practices. This creates an asymmetry: valuable data with potentially weaker protections.
Fintech companies also operate in a competitive race to market. The pressure to launch features and grow rapidly sometimes conflicts with the deliberate process of building robust security. Security infrastructure can slow down development, so some fintech companies optimize for speed at the expense of security depth.
The fintech industry has also been a target for organized crime and nation-state actors because of the financial value. A breach affecting financial data creates opportunities for fraud, unauthorized transactions, identity theft, and other crimes that generate revenue for attackers.
Figure's position in blockchain lending also created unique considerations. Blockchain companies often position themselves as more secure than traditional systems, which can create overconfidence in security practices. The reality is that blockchain infrastructure security and organizational security are different things. Being blockchain-based doesn't protect against social engineering attacks targeting employees.
The industry trend suggests that fintech companies need to treat security as a core product feature, not an afterthought. Companies that have invested heavily in security infrastructure, employee training, and incident response planning are more likely to detect breaches early and respond effectively.

Social Engineering as the Weakest Link
The Figure breach illustrates a fundamental security principle: technology is only as secure as the people using it. Social engineering remains one of the most effective attack vectors because it exploits human psychology rather than technical systems.
Phishing emails, pretexting, baiting, tailgating, and other social engineering techniques succeed because they work on proven psychological principles. People want to be helpful, they trust authority figures, and they often follow routine patterns. Attackers exploit these patterns.
Employee security training helps, but it's not a silver bullet. Even well-trained employees can be fooled by sophisticated social engineering attacks. The best defense is a combination of technical controls and cultural practices that make social engineering harder.
Technical controls include multi-factor authentication, which prevents an attacker from using stolen credentials alone. They also include endpoint detection and response, which can identify suspicious behavior after an initial compromise. And they include network segmentation, which limits how far an attacker can move through systems after gaining initial access.
Cultural practices include encouraging employees to question unusual requests, verifying identities through secondary channels, and creating a security-conscious environment where people feel comfortable saying no to requests that seem suspicious.
Figure presumably had some security practices in place. The question is whether these practices were sufficient to prevent the attack or whether the attackers were simply more sophisticated than the defenses. Social engineering at the right target can defeat even strong technical controls.
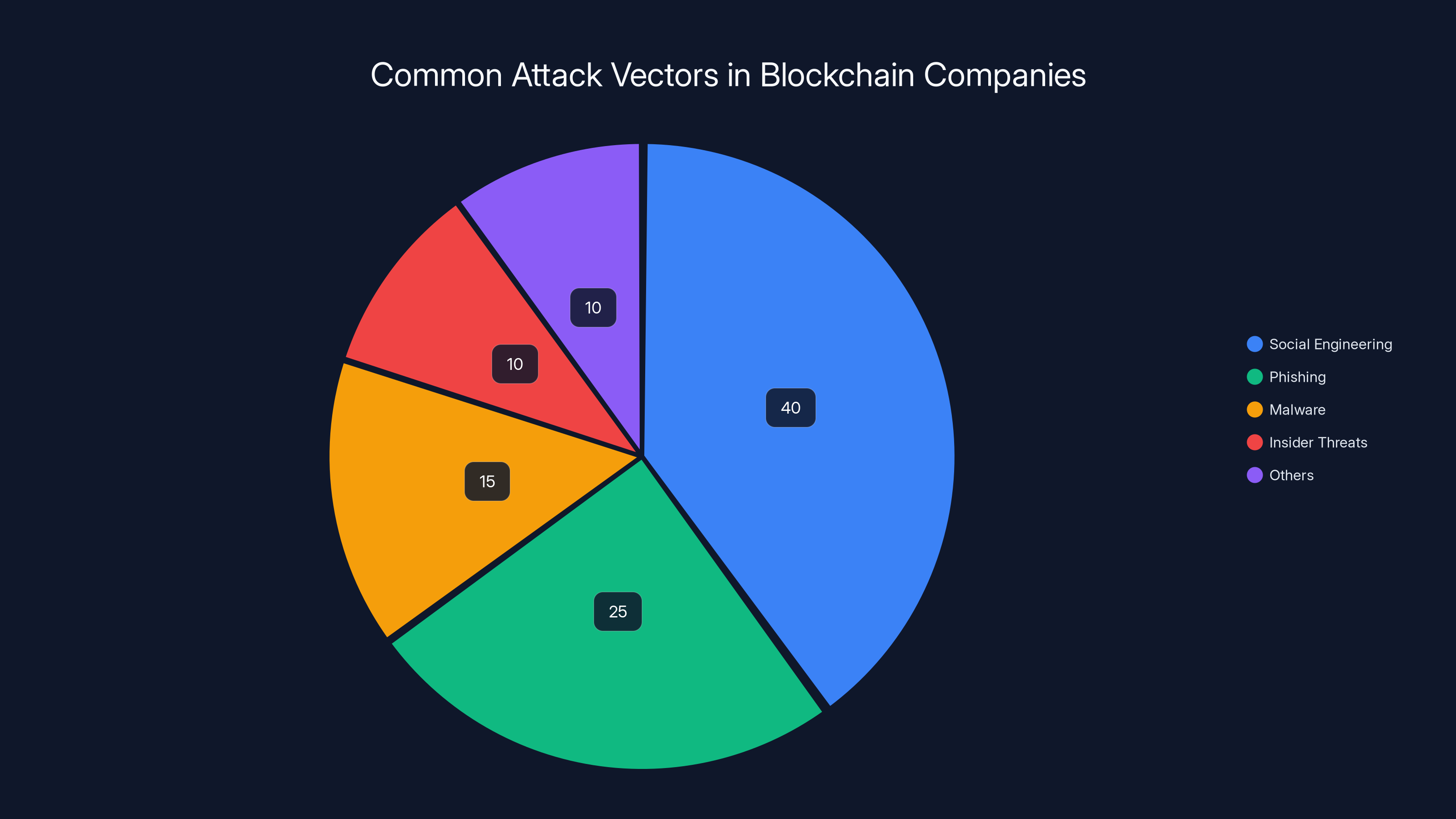
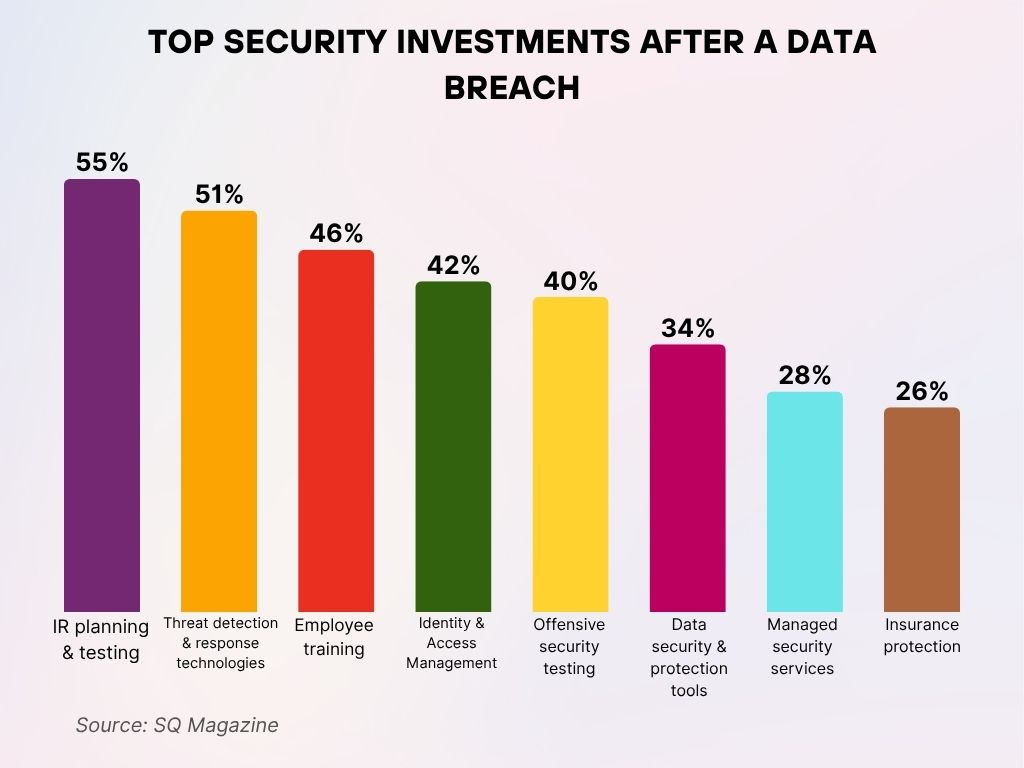
Social engineering remains the most effective attack vector, responsible for 40% of breaches in blockchain companies. Estimated data reflects typical threat distribution in 2025.
What Customers Should Do Now
If you're a Figure Technology customer or someone whose data was exposed in this breach, specific steps can help protect you from downstream harm.
First, monitor your credit. Check your credit reports from all three bureaus at annualcreditreport.com, which provides free annual reports. Look for accounts you don't recognize, inquiries you didn't authorize, or other suspicious activity. The free credit monitoring that Figure is offering helps, but active monitoring by you is also important.
Second, consider placing a credit freeze. A credit freeze prevents credit bureaus from releasing your credit report to potential creditors without your permission. This effectively blocks new account openings in your name. It's not inconvenience-free, as you'll need to temporarily lift the freeze if you want to apply for credit yourself, but it's a powerful defense against fraud.
Third, change your passwords, especially for any accounts where you used similar passwords or reused credentials. If you used the same password for Figure as other services, change those too. This prevents attackers from using compromised credentials to access other accounts.
Fourth, be cautious of communications claiming to be from Figure or financial institutions. Phishing attacks often follow major breaches, with attackers impersonating the breached company or other financial institutions to trick people into revealing information or clicking malicious links.
Fifth, consider whether you have answers to common security questions on file. If your birthdate and full name were exposed, attackers might be able to answer common security questions like "What city were you born in?" or "What's your mother's maiden name?" Check accounts that might have security questions and update them if possible.

Broader Security Lessons from the Figure Breach
Beyond the specific incident, the Figure breach offers lessons that apply across the entire business world.
First, the breach demonstrates that social engineering remains the most effective attack vector. Companies spending billions on sophisticated technical security can be compromised by an attacker manipulating a single employee. This suggests that employee training, security culture, and psychological resilience need to be core security investments.
Second, the breach highlights the risk of third-party dependencies. Figure's breach might have originated through an Okta vulnerability, meaning Figure's own security practices might have been exemplary but still insufficient to protect customer data. This suggests that due diligence on vendors and dependencies needs to be rigorous, and monitoring for vulnerabilities in critical infrastructure needs to be continuous.
Third, the breach illustrates the value of transparency in security. Shiny Hunters announced the breach publicly, which is better for customers than if it remained hidden, despite the embarrassment for Figure. Companies need systems to detect breaches quickly, not rely on attackers to inform them.
Fourth, the breach demonstrates that rapid response and communication matter. Figure disclosed the breach, offered credit monitoring, and worked with authorities. While these actions don't undo the breach, they show commitment to managing the fallout responsibly.
Fifth, the breach suggests that security maturity should scale with data sensitivity and company growth. Startups handling sensitive financial data need to invest in security proportionally to the value of that data and the potential harm from compromise.

The Rise of Ransomware and Data Extortion
The Figure breach followed a specific pattern: breach, exfiltrate data, demand ransom, publish data if ransom isn't paid. This pattern has become increasingly common across all industries.
This approach, sometimes called "double extortion," is more effective than traditional ransomware where attackers just encrypt files and demand payment for decryption. With data exfiltration and publication threats, organizations face pressure even if they have backups and can restore systems without paying.
The threat of public data release affects not just operational recovery but reputation and customer trust. For companies with customer relationships dependent on trust and confidentiality, the threat of data publication is compelling.
Figure's decision not to pay ransom is actually notable. Some companies decide that paying is cheaper than dealing with the legal, regulatory, and reputational fallout. However, there's no guarantee that paying prevents data publication, and paying funds criminal enterprises and encourages more attacks.
The rise of data extortion has led to insurance products specifically covering these risks, and to investment in better breach detection and incident response capabilities. Organizations increasingly recognize that breach response needs to be as important as breach prevention.

Lessons for Other Organizations
Companies across industries can learn from the Figure breach. The lessons apply broadly because the attack vector, social engineering, is universal.
Organizations need to invest in security awareness training that goes beyond annual checkbox compliance. Training should be regular, relevant, and should include simulated social engineering attacks to test employee responses. Employees should understand not just what they shouldn't do, but why security matters.
Organizations need to implement multi-factor authentication universally. This is non-negotiable for any company handling sensitive data. Single-factor authentication, even with strong passwords, is insufficient in 2025.
Organizations need to monitor for suspicious access patterns. If someone accesses the network from an unusual location, at an unusual time, or with unusual access patterns, that should trigger alerts. Behavioral analytics can help identify compromised accounts before significant damage is done.
Organizations need to segment networks so that a compromise of one system doesn't automatically compromise everything. Critical data should be isolated in ways that require additional authentication even for administrators.
Organizations need to maintain incident response plans and practice them regularly. When a breach happens, the first 24-48 hours are critical. Having a pre-planned response, with identified decision-makers and communication protocols, can dramatically improve outcomes.

Future of Fintech Security
The fintech industry will likely experience more breaches and more regulatory pressure as a result. This will drive maturation of security practices, but also potentially slower innovation as security becomes a more critical consideration.
We'll likely see increased consolidation in fintech, as smaller companies without sufficient security resources are acquired or shut down. Regulators will likely mandate specific security controls, making compliance more explicit and uniform across the industry.
Investors will increasingly scrutinize security practices during due diligence, understanding that breaches create existential risk for companies. This might slow fundraising for security-light startups and accelerate funding for companies with mature security practices.
The Okta angle will likely drive increased attention to identity and access management security. Companies will realize that they can't adequately secure their data if their authentication layer is compromised. This might lead to adoption of more advanced authentication methods, including passwordless authentication and continuous verification.
Artificial intelligence and machine learning will increasingly be used for threat detection, helping organizations identify suspicious behavior patterns that humans might miss. However, AI-powered attacks will also become more sophisticated, creating an ongoing arms race between defenders and attackers.
The Role of Law Enforcement and Attribution
Law enforcement agencies, including the FBI and international partners, are involved in investigating the Figure breach and tracking Shiny Hunters. Attribution and prosecution of cybercriminals remains challenging but not impossible.
Shiny Hunters' relatively public approach, publishing data on dark web leak sites under their name, makes attribution easier. Law enforcement can track the digital breadcrumbs of these publications, sometimes leading to real-world identities. However, jurisdictional challenges complicate prosecution, as the attackers might be operating in countries with limited extradition treaties.
There have been successful prosecutions of significant cybercriminals in recent years, though these are still relatively rare given the scale of cybercrime. High-profile cases have involved international cooperation, cryptocurrency tracking, and extensive forensic investigation.
The threat of prosecution might deter some opportunistic attackers but likely won't stop determined criminal organizations or nation-state actors. However, every successful prosecution increases the risk and cost for criminals, potentially shifting risk calculations.
Law enforcement is also increasingly cooperating internationally, recognizing that cybercriminals operate globally. Organizations like Europol and Interpol coordinate investigations across borders, making international attribution and prosecution more feasible.
Looking Ahead: What This Means for Data Security
The Figure breach is one incident among thousands that occur annually, yet it's representative of broader trends in cybersecurity. Organizations are increasingly targeted, attackers are increasingly sophisticated, and the data at risk includes sensitive personal and financial information for millions of people.
Individuals need to understand that data breaches are now a regular occurrence, not a once-in-a-lifetime event. Taking proactive steps to protect yourself, including monitoring your credit, using strong passwords, enabling multi-factor authentication, and being cautious of phishing attempts, is now essential.
Organizations need to treat security as a core business function, not an compliance checkbox. The companies that will thrive in this environment are those that invest in security proportionally to the value and sensitivity of their data, and that build security-conscious cultures where employees understand their role in protecting customer data.
The Figure breach specifically and fintech industry broadly will likely face increased regulatory scrutiny. This might slow innovation in the short term but should ultimately lead to more secure and trustworthy fintech services.
The underlying principles driving this breach, and driving most breaches, are unchanged: attackers will exploit the weakest link, which is often human psychology rather than technological defenses. Until organizations address the human element of security with the same rigor they apply to technology, breaches like Figure's will continue to occur.
FAQ
What is Figure Technology and what does the company do?
Figure Technology is a blockchain-based fintech lending company that uses distributed ledger technology to streamline loan origination, underwriting, and settlement. The company operates in the lending space, competing with traditional banks and digital lending platforms, serving both individual borrowers and institutional partners.
How did the hackers initially compromise Figure's systems?
The hackers used social engineering to trick an employee into compromising their account credentials or authorization. Once the attackers had valid credentials, they accessed Figure's network, explored the environment, and exfiltrated sensitive customer data. The attack likely didn't target technical vulnerabilities but rather exploited human psychology and trust.
What specific customer information was exposed in the Figure breach?
The exposed data included customer full names, home addresses, dates of birth, and phone numbers. While this is serious personal information that can enable identity theft, the breach did not include credit card numbers or Social Security numbers, according to public reporting. The company stated that a "limited number of files" were downloaded, though the exact scope of affected customers was not disclosed.
Who is Shiny Hunters and why are they significant?
Shiny Hunters is a known threat actor group that operates on the dark web, publishing data allegedly stolen from victims who refuse ransom demands. They announced responsibility for the Figure breach and claimed the company refused to negotiate, leading them to publish 2.5 gigabytes of stolen data. They also targeted other organizations, including Harvard University and University of Pennsylvania, potentially through the same Okta vulnerability.
What is the connection between the Figure breach and Okta?
Reporting suggests Shiny Hunters targeted Okta, a single sign-on provider, as part of a broader campaign. Figure was among the victims of this campaign, meaning the breach might have originated from a vulnerability or misconfiguration in Okta rather than a flaw in Figure's own systems. This indicates the breach was likely part of a coordinated campaign against multiple organizations using Okta for authentication.
What should I do if I'm a Figure customer and my data was exposed?
Monitor your credit reports through annualcreditreport.com, consider placing a credit freeze with the three major credit bureaus (Equifax, Experian, Trans Union), change your passwords especially for accounts using similar credentials, and be cautious of phishing communications claiming to be from Figure. Use the free credit monitoring service Figure is offering and keep copies of important financial documents for reference.
What are the regulatory implications for Figure?
Figure faces obligations under state and international data protection laws, including notification requirements, free credit monitoring, and specific breach disclosures. The company will likely face class action lawsuits and potential investigation by state attorneys general and federal regulators. The financial impact could include substantial legal fees, potential settlements, and regulatory fines depending on the extent of non-compliance.
Why are fintech companies particularly vulnerable to breaches?
Fintech companies handle sensitive financial information and personal data while often being younger and potentially less mature in security practices than traditional banks. The competitive pressure to launch features quickly sometimes conflicts with deliberate security building. Additionally, fintech companies are attractive targets because of the financial value of their data and the opportunities for fraud or identity theft that breaches create.
How can organizations prevent social engineering attacks like the one that affected Figure?
Organizations should implement multi-factor authentication universally, provide regular security awareness training including simulated phishing attacks, monitor for suspicious access patterns, segment networks to limit the impact of compromised accounts, and develop incident response plans practiced regularly. Creating a security-conscious culture where employees understand their role in protecting data is essential.
What does the Figure breach suggest about the future of fintech security?
The breach likely signals increased regulatory scrutiny, more stringent security requirements for fintech companies, and potential consolidation as smaller companies without sufficient security resources struggle to compete. Organizations will increasingly scrutinize security practices during due diligence, and investors will factor breach risk into funding decisions. Advanced authentication methods and AI-powered threat detection will become more prevalent in the industry.
Conclusion: Moving Forward in a Breach-Prone World
The Figure Technology breach confirms what security professionals have known for years: data breaches are becoming more frequent, attackers are becoming more sophisticated, and the financial and personal consequences are becoming more severe. This isn't a story about a single company's failure, but rather a reflection of systemic challenges in how organizations handle security and how individuals protect their personal information.
Figure's breach, originating from a compromised employee account and potentially rooted in a third-party vendor vulnerability, exemplifies the complexity of modern cybersecurity. The company couldn't fully control the security of services they depend on, yet their customers' data was at risk. This creates a paradox: organizations need to secure their systems, but they're also vulnerable to breaches originating outside their direct control.
For individuals whose data was exposed, the breach is concerning but manageable with proactive steps. Monitor your credit, place a freeze if necessary, change passwords, and remain cautious of phishing attempts. The financial information exposed is valuable to attackers, but your awareness and quick response significantly reduce the damage.
For organizations across industries, the Figure breach offers urgent lessons. Social engineering remains the most effective attack vector, and no amount of technical security can fully compensate for human psychology. Multi-factor authentication, behavioral monitoring, network segmentation, and strong incident response capabilities need to be non-negotiable for any organization handling sensitive data.
For the fintech industry specifically, the breach marks a potential inflection point. As regulatory scrutiny increases and investors demand stronger security practices, fintech companies will need to integrate security as a core business function from day one. The companies that recognize this and invest accordingly will thrive; those that treat security as an afterthought will face existential risk.
The broader security landscape in 2025 is characterized by an asymmetry: attackers can find thousands of targets and only need one to succeed, while defenders must protect everything. This asymmetry is unlikely to change, which means organizations must accept that breaches might happen and focus on detection and response in addition to prevention.
The Figure breach will likely fade from headlines within weeks, replaced by the next breach, the next extortion attempt, the next leak. But the lessons from this incident remain relevant. Invest in security, train employees, monitor for threats, respond quickly, and communicate transparently. For individuals, understand that your data is likely already exposed somewhere, and focus on the behaviors that minimize the damage from that exposure.
Cybersecurity is ultimately a game of risk management, not risk elimination. Figure Technology faced risks that they couldn't completely eliminate, and those risks materialized. The response now is to learn, improve, and help others avoid the same fate. That's the only path forward in a world where breaches are increasingly common and increasingly consequential.

Key Takeaways
- Figure Technology confirmed a data breach originating from a social engineering attack targeting a single employee account
- ShinyHunters published 2.5GB of stolen customer data including full names, addresses, birthdates, and phone numbers after Figure refused to pay ransom
- The breach was likely part of a broader campaign exploiting Okta SSO vulnerability that also affected Harvard University and University of Pennsylvania
- Fintech companies remain attractive targets for attackers because they handle valuable financial and personal data often with startup-level security maturity
- Customers should monitor credit reports, place credit freezes, change passwords, and remain vigilant for phishing attempts following the breach
Related Articles
- Tenga Data Breach: What Happened and What Customers Need to Know [2026]
- 6.8 Billion Email Addresses Leaked: What You Need to Know [2025]
- Social Security Data Handover to ICE: A Dangerous Precedent [2025]
- iRobot's Chinese Acquisition: How Roomba Data Stays in the US [2025]
- Odido Data Breach: 6.2M Customers Exposed [2025]
- Government Censorship of ICE Critics: How Tech Platforms Enable Suppression [2025]



