Introduction: When Your Intimate Purchase History Becomes Public
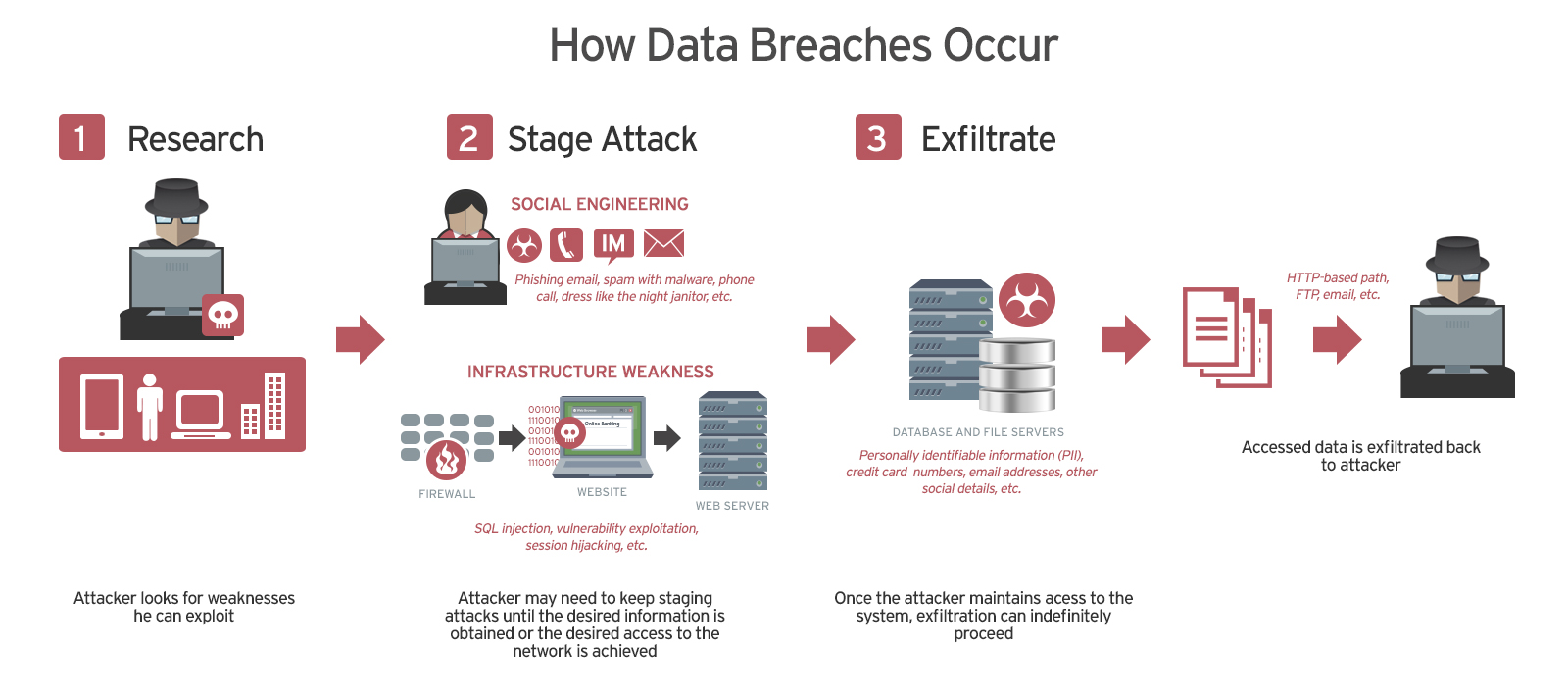
Imagine opening your email to find out that someone, somewhere, now has your complete purchase history for a specific category of products. That's what happened to thousands of Tenga customers in early 2026 when the Japanese adult product manufacturer disclosed a significant data breach. But here's the thing: this wasn't a sophisticated zero-day exploit or a complex ransomware attack. It was something far more mundane. A hacker gained access to a single employee's email account, and that single point of failure exposed customer information that most people would rather keep private.
This incident matters far beyond the sex toy industry. It's a stark reminder that some of the most damaging breaches don't come from nation-state actors or elaborate cybercriminal syndicates. They come from basic security failures. The kind of failures that should've been prevented with standard security practices that most enterprises implemented years ago.
Tenga is no small operation. The company has shipped over 162 million products worldwide and maintains a significant customer base across multiple countries. Yet despite this scale, a single compromised employee email account became the gateway for attackers to access sensitive customer data. This included names, email addresses, order histories, and customer service correspondence—all information that carries significant privacy implications for customers of intimate products.
What's particularly striking about this breach isn't just what happened, but what it reveals about security practices at companies of various sizes. Even well-established businesses sometimes lack fundamental security controls. The irony is that the technology to prevent this breach has existed for over a decade. Multi-factor authentication, email security monitoring, and access controls could have stopped this attack cold.
In this article, we'll break down exactly what happened during the Tenga breach, why it matters for privacy-conscious consumers, what it reveals about broader cybersecurity practices in e-commerce, and most importantly, what you should do if you're affected. We'll also explore the larger pattern of breaches targeting adult product retailers and what that tells us about security priorities across different industries.
TL; DR
- The Breach: A hacker accessed a single Tenga employee's email account, gaining access to customer names, email addresses, and order history
- What Was Exposed: Customer correspondence including order details and customer service inquiries, plus the hacker sent spam to that employee's contacts
- Scale: Tenga has shipped 162 million products worldwide, though the company didn't disclose exact numbers of affected customers
- Response: Tenga reset the compromised account credentials and enabled multi-factor authentication company-wide
- Pattern: This breach is part of a larger trend affecting adult product retailers, including similar incidents at other companies in the industry
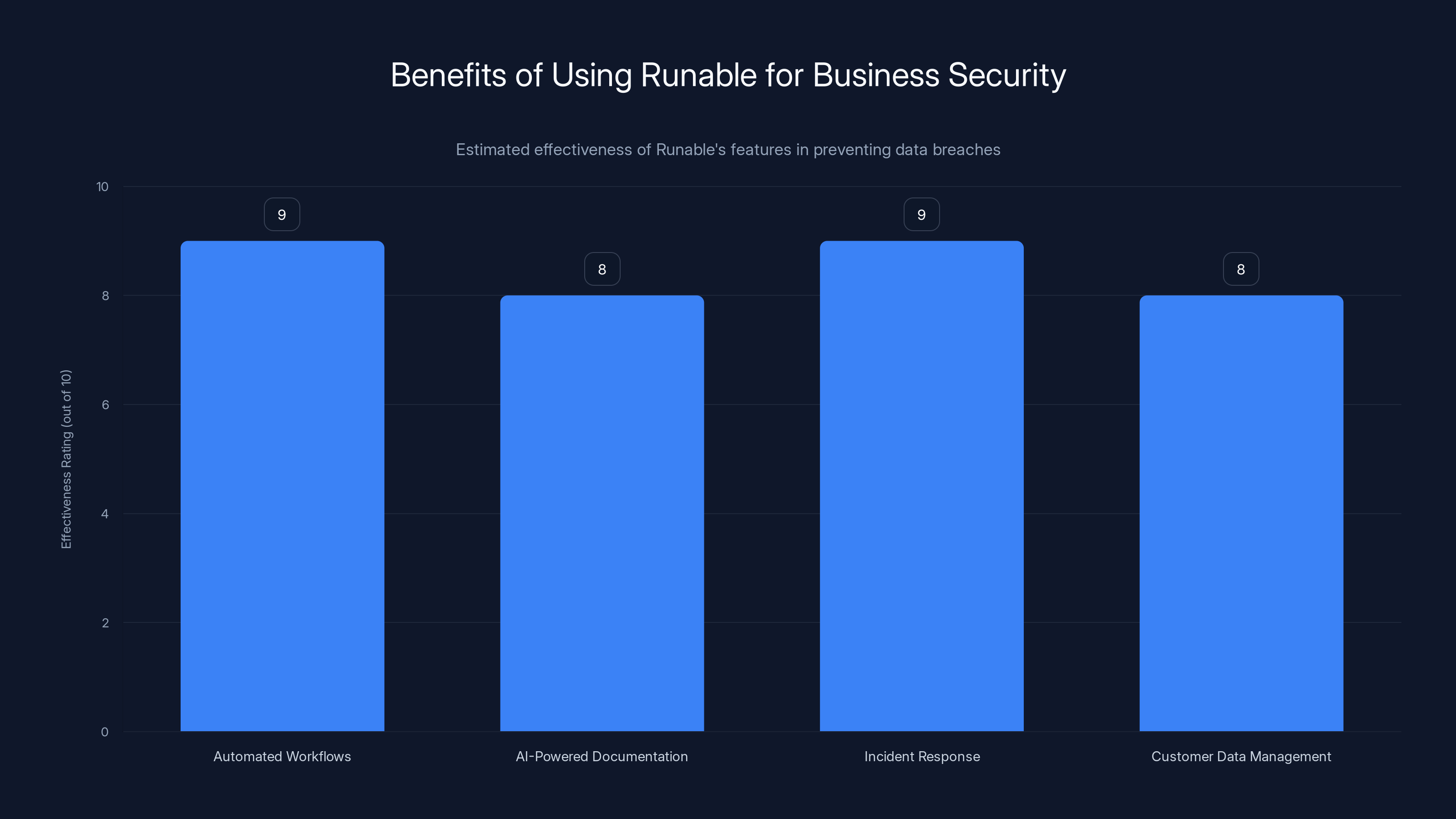
Runable's features are highly effective in securing business operations, with automated workflows and incident response rated highest. Estimated data.
The Attack: How One Email Account Became a Data Goldmine
Security breaches follow predictable patterns, and the Tenga incident hits several familiar notes. Everything started with someone's compromised credentials. We don't know exactly how the attacker obtained the employee's login information. It could have been phishing, credential stuffing, password reuse across multiple services, or exploitation of a vulnerability in a web service that employee used. The method matters less than the result: the attacker got in.
Once inside, the attacker discovered something that shouldn't have surprised anyone but apparently did surprise Tenga's security team. The email account contained extensive customer data. Not in an encrypted database behind multiple security layers. Not in a restricted data warehouse with access controls. Just sitting there in an email inbox, visible to anyone with valid credentials.
This is where most breaches reveal their mundane reality. Companies often assume that email is "just email." It's seen as a communication tool, not a data repository. But in practice, email inboxes become de facto databases. Customer service teams discuss orders via email. Customers share sensitive information in support tickets. Order confirmations sit in inboxes for months or years. Passwords occasionally get reset via email links. Suddenly, a single email account contains an embarrassing amount of sensitive information.
Why Email Became the Weak Point
Email remains one of the most targeted vectors in cybersecurity, yet many organizations treat it like infrastructure rather than a security perimeter. The Tenga breach demonstrates this perfectly. An employee's email inbox had access to:
- Customer names and email addresses
- Complete order histories
- Customer service correspondence and inquiries
- Communication about returns and complaints
- Potentially sensitive information about customer preferences
None of this needed to be in that email account. Modern customer relationship management systems, ticketing platforms, and order management systems exist precisely to organize this information securely. But if they're not being used, or if email is being used as a backup communication channel, the risk skyrockets.
The problem is compounded when you consider that the email account belonged to an employee. Employees are in a different trust category than external systems. They're often given broader access to company systems. Their accounts are less scrutinized. Their activity is often less monitored. This makes employee accounts particularly attractive to attackers.
The Spam Campaign That Proved Access
Here's the part that actually helped Tenga discover the breach: the attacker sent spam emails to the compromised employee's contacts. This wasn't subtle. The attacker used the legitimate company account to send messages, which would have appeared to come from Tenga's official domain. Some of those recipients were customers.
This kind of activity is how breaches get discovered. Someone notices something off. They report it. The company investigates. In this case, it probably worked something like this: customers received suspicious emails appearing to come from Tenga staff. They report it as spam. Tenga's support team notices a pattern. They investigate and discover that the emails came from an internal account. They realize they've been breached.
The irony is that many breaches remain undetected for months or years. The Tenga breach was likely discovered relatively quickly because of this noisy activity. A more sophisticated attacker might have accessed the email, stolen everything, and disappeared without triggering any alerts.
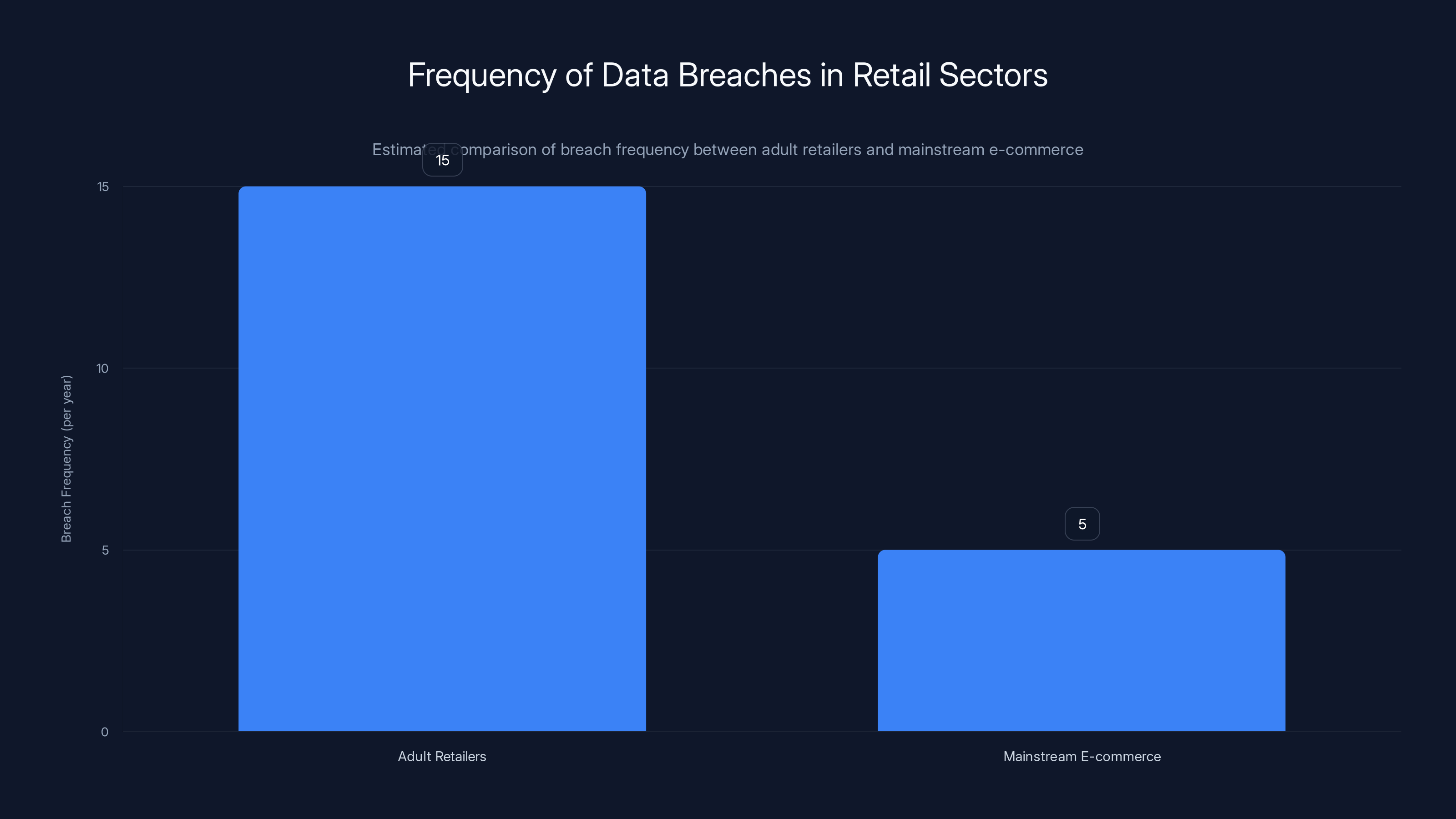
Adult retailers experience an estimated three times more data breaches annually compared to mainstream e-commerce, highlighting a significant security challenge. (Estimated data)
What Information Was Actually Compromised
Let's get specific about what the attacker could access. According to Tenga's notification, the breach potentially exposed customer names, email addresses, and "historical email correspondence, which may include order details or customer service inquiries."
That phrase "may include" is doing a lot of work. It's actually saying "we don't know exactly what was accessed, but it could include any of this." For a company that shipped 162 million products, that's a pretty wide net.
The Specific Risk Categories
Purchase History and Product Information: Customers of adult product companies often have privacy concerns about their purchases. An order history for Tenga products contains information that, if publicly disclosed, could cause embarrassment or real harm. In some jurisdictions, this information could even pose safety risks. Someone's boss, family member, or social circle learning about their intimate product purchases can have real consequences.
Email Addresses: By themselves, email addresses might seem innocuous. But combined with the fact that these are customers of an adult product retailer, they become valuable. Attackers can use these email addresses for targeted phishing campaigns. They can sell them to spammers. They can use them to fuel blackmail schemes. Phishing campaigns targeted at adults who shop online for intimate products might have particularly high success rates.
Customer Service Inquiries: This is where things get really sensitive. Customer service correspondence about products designed for intimate use often contains deeply personal information. Someone might ask about product functionality, sizing, health concerns related to use, or customization options. This information is even more sensitive than just knowing someone made a purchase.
Order Details: The specifics matter here. Did orders include shipping addresses? Did they include payment information like the last four digits of credit cards? The company's statement is vague, which actually makes the situation worse from a customer perspective. When a company doesn't disclose exactly what was compromised, you have to assume the worst.
The Privacy Implications
Here's where this breach differs from a typical e-commerce breach. When your Amazon purchase history gets exposed, that's bad. People know you buy books and kitchen equipment. When your sex toy purchase history gets exposed, that's categorically different. The stigma around adult products means the privacy violation feels more acute.
This isn't just about embarrassment, though that's certainly part of it. In some jurisdictions, this information could be used for extortion or blackmail. In others, it could affect employment, housing, or relationships. The sensitivity of intimate product purchases means the potential harm from this breach extends beyond typical data theft consequences.
Tenga's Response: Too Late and Too Basic
Once Tenga discovered the breach, they took several steps. Let's evaluate what they did and what they should have done earlier.
What Tenga Actually Did
The company reset the compromised employee's credentials. This is basic stuff. Immediately terminate access through the compromised password. Generate a new password. Force the employee to change it. This prevents the attacker from using the old credentials to access the account again. But it's also the bare minimum.
Second, Tenga enabled multi-factor authentication across their systems. This is where it gets interesting. The company didn't explicitly state whether multi-factor authentication was enabled on the breached email account before the attack. When asked by journalists whether MFA was active prior to the breach, the company didn't respond. That silence is pretty telling.
Multi-factor authentication has been available for over fifteen years. Google, Microsoft, and Amazon have been pushing MFA for over a decade. By 2026, any company handling customer data should have MFA enabled on email accounts. The fact that Tenga apparently didn't have this basic security control enabled suggests some troubling gaps in their security posture.
What They Should Have Done Earlier
Let's talk about what basic security practices would have prevented this breach:
Mandatory Multi-Factor Authentication: MFA should have been mandatory for all employee email accounts. This would have stopped the attack even if the attacker had obtained the employee's password. You need both something you know (password) and something you have (phone, authenticator app) to access the account.
Email Security Monitoring: Enterprise email systems can monitor for suspicious activity. Unusual login locations, logins at strange times, bulk downloads of attachments, large forwarding rule changes. These behavioral signals can trigger alerts or require additional verification.
Data Minimization: Employee inboxes shouldn't contain customer order information in the first place. This data should be in specialized systems with proper access controls, encryption, and audit trails.
Email Encryption: Customer correspondence should be encrypted either in transit or at rest, or preferably both. This wouldn't have prevented the breach, but it would have made the stolen information useless without the encryption keys.
Access Logging: Every access to sensitive customer information should be logged and periodically reviewed. An employee account suddenly downloading years of customer data should trigger an alert.
The Silence Around Incident Response
One thing that's notable is how little Tenga has disclosed. The company hasn't said how many customers were affected. It hasn't provided a detailed timeline of when the breach occurred and when it was discovered. It hasn't explained whether there were any other compromised accounts. It hasn't disclosed whether it conducted a full forensic investigation.
This silence creates a trust problem. Customers affected by a breach deserve transparency. When a company is vague about what happened, customers have to assume the worst.
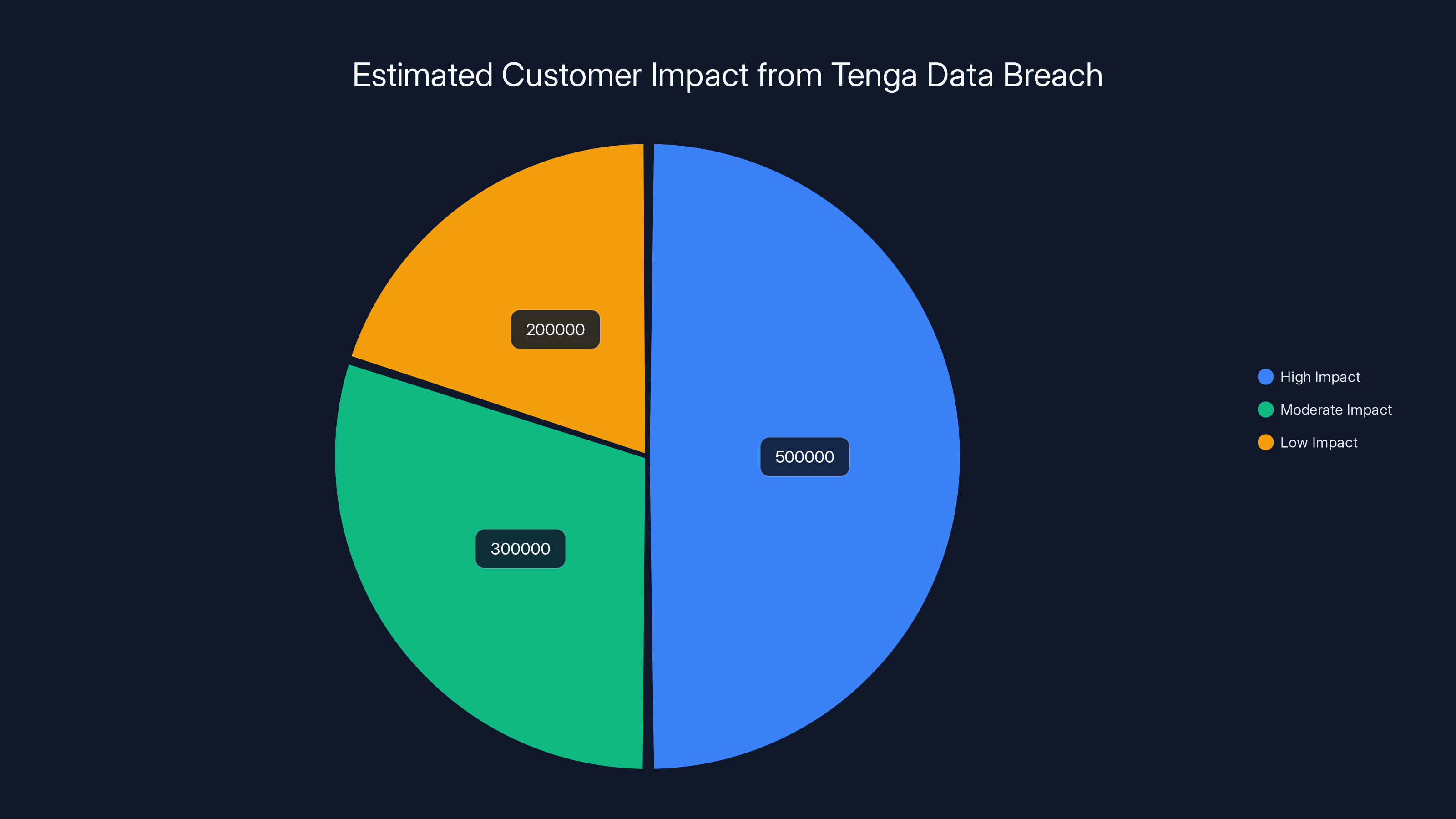
Estimated data suggests a potential impact on 1 million customers, with varying degrees of exposure. 'High Impact' represents the most affected group.
Understanding the Scope: How Many Customers Were Really Affected
Tenga didn't disclose the number of customers impacted. That's frustrating. The company would presumably know how many customers exchanged emails with the breached employee account. Even if every email in the account couldn't be recovered or wasn't fully accessed, the company should have a good sense of the exposure.
So why the silence? A few possibilities:
It's a large number: If the breach affected a significant portion of Tenga's customer base, the company might be reluctant to disclose that. The PR damage from saying "we've exposed 500,000 customers' intimate shopping history" is substantial.
They genuinely don't know: This is also possible. If the investigation was incomplete or didn't thoroughly determine what the attacker accessed, the company might not have accurate numbers. This would be concerning from a security incident response perspective.
Regulatory considerations: Different jurisdictions have different data breach notification requirements. In some cases, companies might calculate exposure numbers differently based on local regulations.
Regardless of the reason, the lack of specificity undermines confidence in Tenga's handling of the situation.
Projecting the Scale
Let's think about this analytically. Tenga has shipped over 162 million products worldwide. That suggests a customer base in the millions. If the company has been operating since 2005 and maintains email correspondence with customers, years of emails could be in that compromised inbox.
A single customer service representative might handle hundreds of customer inquiries per year. Over a career at the company, a single employee's email account could contain tens of thousands of customer conversations. If this employee worked in customer service, support, or management, the number could be even higher.
Without specific numbers, we're left guessing. And guessing is exactly what customers are trying not to do with their intimate shopping information.

Why Sex Toy Makers Are Attractive Targets
The Tenga breach isn't an isolated incident. Other adult product retailers have suffered similar breaches. Lovesense reported a breach in 2025. Adult content sites including Pornhub and Sex Panther have experienced data theft. Why are these companies disproportionately targeted?
The Sensitivity Premium
Hackers understand what we discussed earlier: intimate product purchase history is more sensitive than most other personal data. This sensitivity creates value. The data can be sold on the dark web for higher prices. It can be used for extortion. It can be used for targeted phishing campaigns.
A list of email addresses for people who shop at mainstream retailers might sell for a few cents per address. A list of email addresses from customers of adult product companies might sell for dollars per address. That multiplies the financial incentive significantly.
The Extortion Angle
Some attackers don't bother selling data on dark web markets. Instead, they use it directly for extortion. They contact targets claiming they'll expose their purchase history publicly unless they pay a ransom. The shame and privacy concerns around intimate product purchases make this extortion particularly effective. People might be reluctant to report it to authorities because it means admitting they received such an email.
This extortion angle makes adult product retailer breaches especially damaging. It's not just about data exposure. It's about psychological manipulation based on that exposure.
Industry-Wide Security Gaps
Here's an uncomfortable truth: the adult products industry has historically lagged behind mainstream e-commerce when it comes to security practices. This isn't about judgment. It's just reality. Many adult product companies started as smaller operations without enterprise-level security infrastructure. Some remain relatively lean.
This creates a gap. The industry deals with more sensitive data than most e-commerce sectors. Customers have especially legitimate privacy concerns. Yet the security practices sometimes don't match the sensitivity level. This gap between sensitivity and security creates attractive targets for attackers.
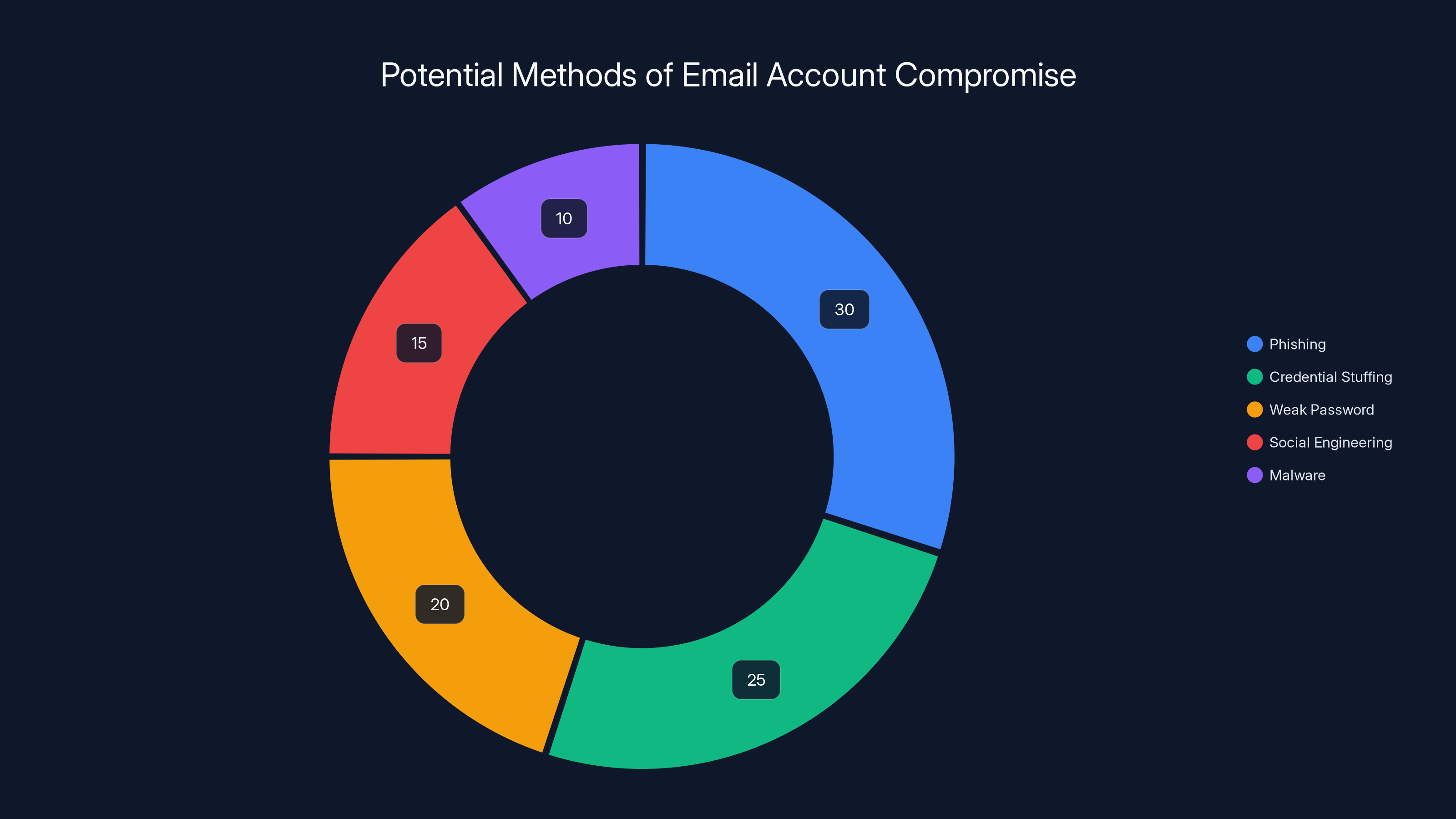
Phishing is estimated to be the most likely method used to compromise the Tenga employee's email account, followed by credential stuffing and weak password selection. Estimated data based on common hacking techniques.
The Email Account Attack: A Pattern That Keeps Working
The Tenga breach follows a well-established attack pattern. Get credentials. Access email. Extract data. The reason attackers keep using this pattern is that it works. Email remains one of the most valuable targets in cybersecurity because email accounts contain so much sensitive information.
How Attackers Get Initial Access
Attackers typically don't stumble into email accounts. They have to gain access through one of several vectors:
Phishing: The attacker sends a fake email that looks like it's from a legitimate company (Apple, Microsoft, Google). The target clicks a link and enters their credentials on a fake login page. The attacker now has the password.
Credential Reuse: The target uses the same password on multiple services. Their password gets exposed in a breach at some unrelated company. The attacker tries that password on the company's email system. It works.
Weak Passwords: The employee uses a weak password like "Password 123" or "Spring 2026!" An attacker using password-guessing tools or a dictionary attack cracks it.
Social Engineering: The attacker calls the employee pretending to be from IT, claiming there's a security issue, and convinces them to reset their password through a fake portal. The attacker captures the new password.
Malware: The employee's personal computer gets infected with malware that captures passwords or browser credentials.
We don't know which of these methods the attacker used against Tenga's employee. Any of them could have worked if basic security controls weren't in place.
Why Email Is the Prize
Once inside an email account, attackers have legitimate treasure. Email contains:
- Password reset links for other services
- Receipts and order confirmations
- Sensitive documents and attachments
- Conversation history revealing customer relationships
- Access to email forwarding rules, which can hide the attacker's presence
An attacker in someone's email account can reset passwords on other services, access other systems, and remain undetected by forwarding incoming emails to an external address while deleting the originals.

Multi-Factor Authentication: The Control That Should Have Stopped This
Let's focus on the most glaring security gap here: the apparent lack of multi-factor authentication on the compromised email account.
How MFA Works
Multi-factor authentication requires two or more verification methods. The most common approach:
- Enter username and password (something you know)
- Verify through a second factor (something you have or are)
The second factor might be:
- Time-based code: An authenticator app (Google Authenticator, Authy, Microsoft Authenticator) generates a code that changes every 30 seconds
- Push notification: The user gets a notification on their phone asking them to approve the login
- SMS code: A text message sends a one-time code to the user's phone
- Hardware key: A physical device that authenticates the login
- Biometric: Fingerprint or facial recognition on the second device
With MFA enabled, an attacker needs both the password AND access to that second factor. If they only have the password, they can't get in.
Why MFA Is So Effective
MFA stops the vast majority of common attacks. A password alone isn't enough. Here's what that means:
- Phishing attacks fail: Even if the attacker tricks the user into revealing their password, they can't access the account without the second factor
- Credential stuffing fails: Even if the attacker has passwords from other breaches, they can't use them without the second factor
- Malware becomes less effective: Even if malware captures the password, it needs the second factor too
- Social engineering fails: Even if the attacker convinces someone to share their password, they need the second factor
MFA is so effective that it's become the security control that makes the biggest difference. Every major security organization recommends it. The adoption rate among secure organizations is extremely high.
Yet apparently Tenga didn't have it enabled on the employee email account that contained customer data. This is exactly the kind of basic security failure that makes security professionals grimace.
MFA Adoption Across Industries
We're now at a point where MFA should be universal for any account containing sensitive data. The technology is mature, easy to implement, and user-friendly. Yet adoption varies significantly across organizations.
Large enterprises managing sensitive data typically mandate MFA for all employees. Government agencies require it. Financial institutions require it. But smaller organizations and less security-focused companies sometimes still see MFA as optional or an inconvenience.
This creates a two-tiered security environment. Well-resourced organizations have MFA. Smaller or less sophisticated organizations don't. Attackers know this and target accordingly.
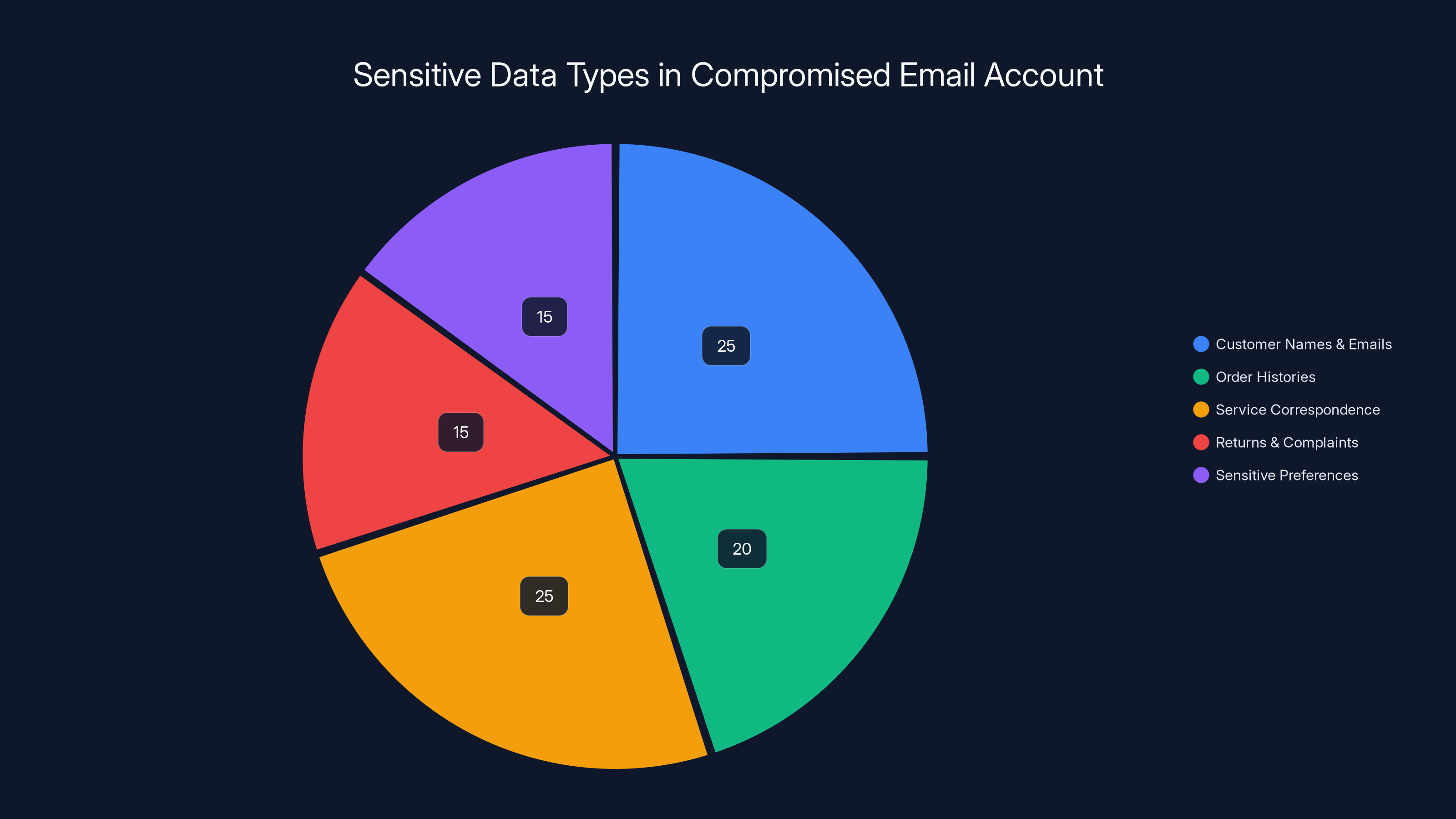
The compromised email account contained various types of sensitive data, with customer names and emails, and service correspondence each making up 25% of the data. Estimated data.
Customer Actions: What Affected Customers Should Do
If you're a Tenga customer concerned about the breach, here's what you should actually do (not just what the company recommends).
Immediate Actions
Change your password: Tenga recommended this in their notification. Even though the company said customer passwords weren't compromised, changing your password is sensible. If you used the same password on your Tenga account as you use on other services, change it everywhere. This prevents the attacker from using it to access other accounts.
Review your email for suspicious activity: Attackers sometimes establish persistence by setting up email forwarding rules or creating backup email addresses. Log into your email account on the device where you normally check it (not a public computer or someone else's device). Look for settings changes. Check if any new recovery email addresses were added. Look for forwarding rules sending copies of emails to external addresses.
Monitor your payment methods: Order history was potentially exposed. If you used a credit card or debit card for the purchase, consider monitoring that card for suspicious charges. Most payment cards have fraud protection, but it's good to be vigilant. Consider ordering a copy of your credit reports from the major bureaus.
Longer-Term Monitoring
Watch for phishing emails: Attackers often use stolen email lists for targeted phishing campaigns. If you get an email claiming to be from Tenga or another company, asking you to verify your account or update payment information, be suspicious. Phishing emails might reference the breach in attempts to seem legitimate.
Be cautious about unexpected communications: If someone contacts you claiming to have information about your intimate product purchases and threatening to expose it unless you pay, that's extortion. Don't pay. Report it to law enforcement. This isn't a legitimate threat; it's a crime.
Consider using privacy-focused alternatives: Some vendors offer discretion when it comes to packaging and billing. Some use non-descript company names on credit card statements. If privacy is a major concern, seek out vendors who prioritize it.
Enable multi-factor authentication on your own accounts: When you sign up for services or reset passwords, enable MFA if available. This protects your personal accounts from the same kind of attack that hit Tenga's employee.

The Broader Industry Pattern: Recurring Breaches at Adult Retailers
The Tenga breach fits into a larger pattern. Adult product retailers and adult content sites seem to suffer breaches more frequently than mainstream e-commerce. Why is that?
The Targeting Hypothesis
One explanation is that attackers deliberately target these companies because they know the data is more valuable and more effective for extortion. A list of people who bought adult products is more valuable to an attacker than a list of people who bought office supplies.
This would explain the pattern. If attackers are strategically targeting adult retailers, we'd expect to see more breaches there than at similar-sized mainstream retailers.
The Security Maturity Hypothesis
Another explanation is that adult product retailers, as an industry category, are less mature when it comes to security practices. Some companies in this space started small and have maintained relatively lean operations. Enterprise security practices might not be as embedded in the organizational culture.
This doesn't mean the companies are negligent. It just means that security practices might not have evolved as quickly as they have at older, larger retail companies that have been managing security for decades.
The Resource Allocation Hypothesis
Adult retailers face unique challenges. Payment processors sometimes restrict them. Banking relationships can be difficult. Advertising channels are limited. These restrictions mean less revenue flowing to the company, which can mean fewer resources for security infrastructure.
If a company is fighting payment processing battles, they might have fewer resources to dedicate to security. This isn't an excuse for poor security practices, but it's a factor worth acknowledging.
The Real-World Consequence
Regardless of why the pattern exists, the result is clear: customers of adult product retailers face higher breach risks. Their intimate shopping information is more likely to be exposed. This creates a difficult situation. Customers want privacy and discretion. But buying from a company that gets breached puts their privacy at risk.
This is where market forces could drive change. Customers could preferentially buy from adult retailers that are transparent about security practices, maintain third-party security certifications, and publicly report on security investments.
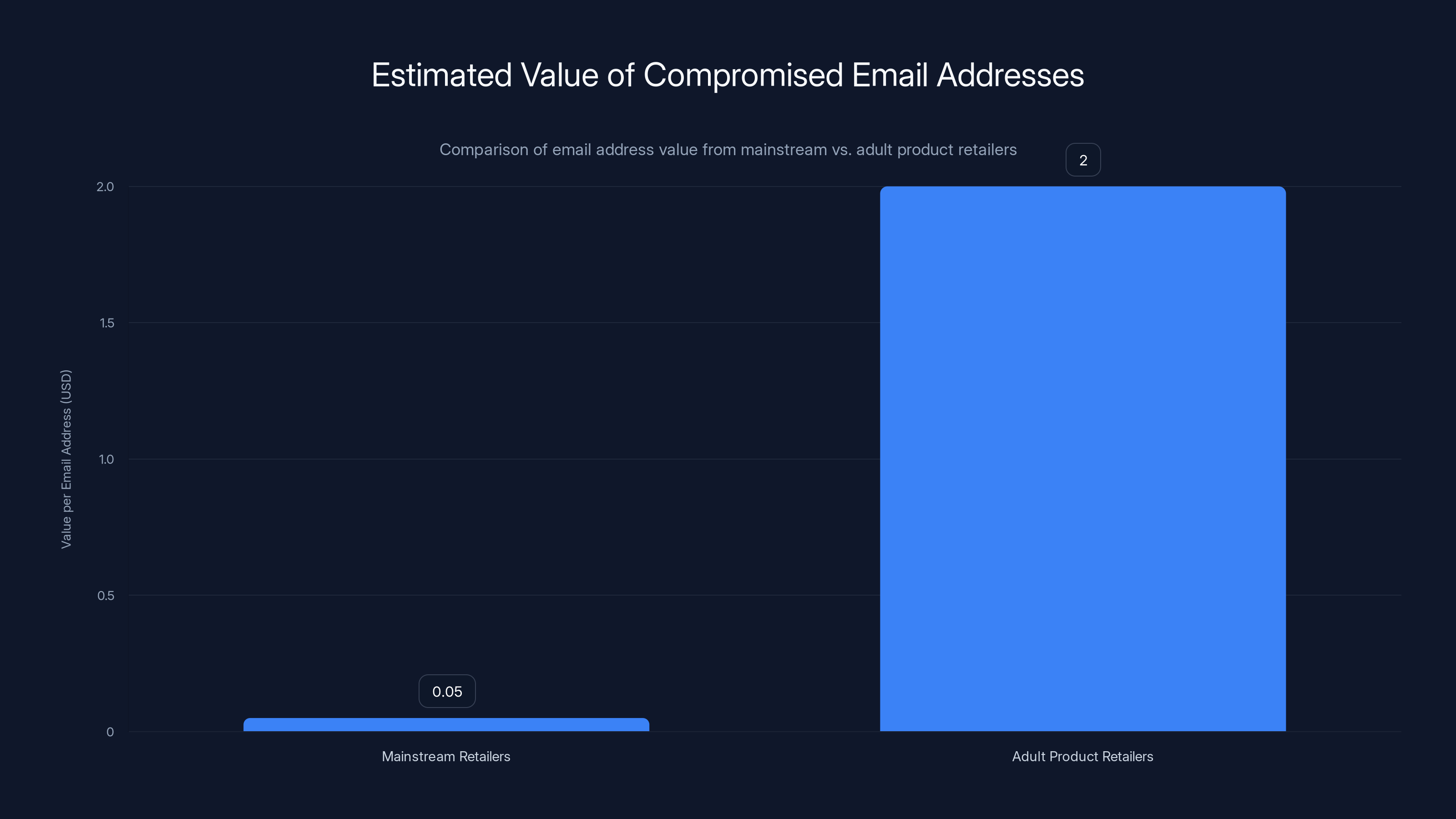
Email addresses from adult product retailers can be worth up to 40 times more than those from mainstream retailers due to their sensitivity. (Estimated data)
Learning from Tenga: What This Breach Teaches About Security
The Tenga incident is educational because it reveals common failures that appear at organizations across industries. Here's what we can learn:
Email Is Not a Secure Data Store
Organizations persist in using email as a de facto database for customer information. Email inboxes aren't designed for secure information storage. They lack encryption at rest. They don't have granular access controls. They're not typically backed up with the same rigor as databases. Yet companies keep putting sensitive information there.
The solution is organizational discipline. Customer service tools should handle customer data. Customer relationship management systems should store customer information. Email should be for communication, not data storage.
Basic Security Controls Still Matter
MFA has been available for years. It's not cutting-edge. It's not expensive. It's not difficult to implement. Yet apparently Tenga didn't have it enabled on critical accounts. This suggests that basic security hygiene is still a problem across the industry.
For companies reading about this breach, the lesson is clear: don't skip the basics. Multi-factor authentication on critical accounts. Password managers to generate and store strong passwords. Regular security updates. Email security scanning. These aren't sophisticated. They're not advanced. But they prevent the vast majority of attacks.
Assume a Breach Is Inevitable
No organization is immune to breaches. The question isn't whether a breach will happen, but when. The organizational response should be focused on minimizing damage when the inevitable breach occurs.
This means:
- Encrypt sensitive data so that even if it's stolen, it's worthless without the key
- Keep detailed logs so breaches can be detected quickly
- Have incident response plans ready
- Know who to notify and what to disclose
- Have customer communication templates ready
Tenga's breach was likely discovered relatively quickly because of the spam emails. If the attacker had been more subtle, the breach might have gone undetected for months. Organizations should assume that subtlety and plan accordingly.
What Regulation Might Come From This
Data breaches at companies handling intimate information sometimes trigger regulatory attention. Lawmakers in various jurisdictions might look at the Tenga breach and consider new requirements for adult-oriented companies.
Existing Regulatory Frameworks
The EU's GDPR already applies to companies handling personal data of EU residents. Tenga is a global company, so GDPR likely applies to some of their customers. GDPR requires companies to implement appropriate technical and organizational measures to protect personal data. It requires notification of breaches without undue delay.
The CCPA and similar US state laws apply to companies handling California and other state residents' data. These laws require reasonable security measures and mandate breach notification.
But these existing laws were written with mainstream commerce in mind. They don't specifically address the unique concerns around intimate product purchases.
Potential New Requirements
Legislators might consider specific requirements for companies handling sensitive personal data:
- Mandatory multi-factor authentication on all accounts with access to customer data
- Mandatory encryption of stored customer data
- Mandatory regular security audits and penetration testing
- Mandatory incident response plans with specific timelines
- Specific notification requirements for breaches involving intimate product purchases
- Required privacy impact assessments
Whether any of these actually get implemented into law varies by jurisdiction. But the Tenga breach certainly gives lawmakers material to consider.
Restoring Trust: What Tenga Should Do Now
Tenga has a trust problem. Customers whose intimate shopping history was potentially compromised now question whether the company takes their privacy seriously. Rebuilding that trust requires more than just resetting passwords and enabling MFA.
Transparency and Disclosure
Tenga should fully disclose what happened. How many customers were affected? What information was accessed? When was the breach discovered? How long was the attacker in the system? When was access terminated? These details matter for customers trying to assess their personal risk.
The company should also explain what went wrong. Why wasn't MFA enabled? Why was customer information in an email account? What's the company's actual security posture? These answers help customers understand whether this was a rare lapse or symptomatic of broader problems.
Third-Party Validation
Tenga should hire an independent security firm to conduct a full forensic investigation of the breach. The report should be shared with affected customers. This provides third-party validation that the company understands what happened.
The company should also conduct a comprehensive security audit. Not just of email security, but of the entire infrastructure. The audit report should be made public (with sensitive details redacted). This shows customers that the company takes security seriously.
Proactive Monitoring
Tenga should offer free credit monitoring and identity theft protection services to affected customers. This isn't just PR. It's a practical way to help customers protect themselves.
The company should also monitor dark web and other underground forums for their customer data. If the data appears on criminal marketplaces, they should work with law enforcement.
Concrete Security Improvements
Beyond investigation, Tenga should implement concrete security improvements:
- Mandatory MFA for all employees
- Complete removal of customer data from email systems
- Implementation of data loss prevention tools
- Regular security training for employees
- Annual third-party penetration testing
- Public security roadmap showing planned improvements
These improvements cost money. But they're an investment in customer trust. In an industry where privacy is paramount, security investments are worth their weight in gold.
The Privacy Paradox: Why People Don't Act Even When They Know
Here's an interesting psychological fact about data breaches: many affected customers don't actually change their behavior. They get a breach notification. They know their data is compromised. But they don't change passwords. They don't enable MFA on their accounts. They don't monitor their credit.
Researchers call this the privacy paradox. People claim to care about privacy. But when it comes to actually taking protective actions, many don't follow through.
This happens for a few reasons:
Inconvenience: Changing passwords is annoying. Setting up MFA takes time. Customers often decide that the inconvenience outweighs the risk.
Psychological Distance: A breach feels abstract. The risk seems distant. Identity theft happens to "other people." This psychological distance reduces motivation to act.
Mistrust of Institutions: Many people assume their bank or credit card company will catch fraud. They think "if something happens, it's not my problem." This fatalism reduces protective action.
Normalized Breaches: We've had so many data breaches that they've become normalized. One more breach in the news barely registers. The emotional response that would drive action has been dampened by repeated incidents.
From Tenga's perspective, understanding this psychology is useful. Yes, the company should offer credit monitoring. But the company should also make protective actions as easy as possible. One-click MFA setup. Pre-filled password change forms. These reduce friction and increase the likelihood that customers will actually take protective action.
Comparing the Response: How Tenga's Handling Stacks Up
Let's evaluate Tenga's breach response against best practices and against how other companies have handled similar incidents.
The Best-Case Scenario
When a company handles a breach exceptionally well, they:
- Discover the breach quickly
- Investigate thoroughly and quickly
- Disclose comprehensively and transparently
- Offer concrete remediation (monitoring, credit protection)
- Implement visible security improvements
- Maintain ongoing communication with customers
Companies that handle breaches well actually build trust through transparency. Customers see that the company takes the incident seriously and is responsive.
The Tenga Response
Tenga's response is middling. The company discovered the breach relatively quickly (the spam emails helped). But disclosure was minimal. The company didn't disclose the number of affected customers. It didn't provide detailed information about what was accessed. There's no indication that Tenga is offering credit monitoring or other remediation to affected customers.
The company did mention enabling MFA company-wide, which is good. But beyond that, there's limited evidence of a comprehensive response.
The Worst-Case Scenario
When companies handle breaches poorly, they:
- Take weeks or months to discover the breach
- Conduct minimal investigation
- Disclose only what law requires
- Offer no remediation
- Make minimal security improvements
- Go silent once the immediate news cycle passes
Tenga isn't at the worst end of the spectrum. But they're not at the best end either. They're in that unsatisfying middle where customers are left wondering if the company really understands what happened or takes security seriously.
The Future of Breach Notification: Should Standards Change
Current breach notification laws typically focus on data category (personal info, health data, financial data). They often don't distinguish between different types of personal information based on sensitivity.
But not all data breaches are equally problematic. A breach of home addresses and phone numbers is less sensitive than a breach of intimate product purchases. Should notification requirements be different?
The Case for Sensitivity-Based Requirements
One argument is that breaches involving particularly sensitive data should trigger enhanced notification requirements. More detailed disclosure. Mandatory remediation. Longer remediation periods. This would create pressure on companies to better protect sensitive information.
For intimate product purchases specifically, notification could be required to include:
- Exact number of affected customers
- Specific products affected
- Exact data elements exposed
- Recommended monitoring period
- Mandatory credit protection offering
The Implementation Challenge
The challenge is defining "sensitive." Is medical information sensitive? Yes. Is financial information sensitive? Yes. Is intimate product purchase information sensitive? Yes. But so is location data, political affiliation data, and other categories.
As you create more specific categories, you create more complexity and more opportunities for companies to argue their data is less sensitive than it actually is.
The Market Approach
Alternatively, markets could drive change. Customers could avoid companies with poor breach handling and poor security practices. Companies that handle breaches well and invest in security could become preferred vendors.
This would require customers to actually care about security practices when making purchasing decisions. In practice, most customers choose based on price, selection, and convenience. Security practices are an afterthought.
Conclusion: A Preventable Breach Reveals Preventable Problems
The Tenga breach is notable not because it was particularly sophisticated or unexpected. It's notable because it was preventable using basic security controls that have existed for over a decade.
A company with multi-factor authentication enabled on employee email accounts would have stopped this breach. A company using a proper customer relationship management system instead of email for customer data storage would have limited exposure. A company monitoring for suspicious email activity would have detected it faster.
Yet despite these basic controls being available and widely recommended, Tenga apparently didn't have them. This is the real lesson here.
For organizations reading about this breach, the message is clear: don't skip the fundamentals. Security isn't about having the fanciest tools or the most advanced detection systems. It's about executing the basics consistently and thoroughly.
For customers, especially those in industries where privacy matters more than most, the message is also clear: ask companies about their security practices before giving them your data. Prefer companies that are transparent about security investments. Enable MFA on your personal accounts. Assume that you'll eventually be breached and plan accordingly.
The Tenga incident, while uncomfortable for the company and concerning for affected customers, is an opportunity. An opportunity for the adult products industry to collectively raise security standards. An opportunity for regulators to consider whether existing breach notification frameworks adequately protect sensitive personal data. An opportunity for other organizations to learn from Tenga's failures and avoid making the same mistakes.
Data breaches will continue to happen. The question is whether we'll learn from incidents like this one and raise our collective security practices, or whether we'll see the same preventable failures repeated again and again.
FAQ
What exactly happened in the Tenga data breach?
A hacker gained access to an employee's email account at Tenga, a Japanese adult product manufacturer. Through this single compromised email account, the attacker could access customer names, email addresses, order histories, and customer service correspondence. The attacker also sent spam emails to the compromised employee's contacts to spread the attack further.
How did the hacker get access to the employee's email account?
Tenga didn't disclose the exact method used to compromise the employee's credentials. Possible methods include phishing emails, credential stuffing using passwords from other breaches, weak password selection, social engineering, or malware on the employee's device. Without multi-factor authentication enabled, any of these methods could have succeeded.
How many Tenga customers were affected by the breach?
Tenga did not disclose the specific number of affected customers. The company has shipped over 162 million products worldwide and has been operating since 2005, suggesting a large customer base. The lack of specific numbers makes it impossible for affected customers to accurately assess their risk.
What information was exposed in the breach?
The compromised data included customer names, email addresses, order details, and customer service inquiries. The company used vague language like "may include," suggesting uncertainty about exactly what data was accessed. For an intimate product retailer, this exposed information is particularly sensitive and could be misused for extortion or phishing campaigns.
What should affected customers do if they think their data was exposed?
Affected customers should change their Tenga password immediately and enable multi-factor authentication if available. They should monitor their email and payment methods for suspicious activity and watch for phishing emails or extortion attempts. Consider checking your credit reports through official channels and remaining vigilant about unexpected communications claiming to have information about your purchases.
Why is multi-factor authentication so important for security?
Multi-factor authentication requires two or more verification methods to access an account, such as a password plus a code from an authenticator app or a push notification to your phone. Even if an attacker obtains your password, they cannot access your account without the second factor. MFA would have prevented the Tenga breach if it had been enabled on the compromised employee account.
Is this breach part of a larger pattern in the adult products industry?
Yes. Other adult product retailers and adult content sites have experienced similar breaches, including Lovesense, Pornhub, and Sex Panther. This pattern suggests that adult retailers face either higher targeting by attackers who value sensitive data for extortion purposes, or have less mature security practices relative to mainstream e-commerce companies.
What should other companies learn from the Tenga breach?
The Tenga incident demonstrates that basic security fundamentals matter. Companies should mandate multi-factor authentication on all employee accounts, especially those with access to customer data. They should not store sensitive customer information in email accounts but rather in proper database systems with access controls. They should invest in email security monitoring, implement data loss prevention tools, and conduct regular security training for employees.
Could this breach have been prevented?
Absolutely. The breach was preventable through basic security controls that have existed for over a decade. Multi-factor authentication alone would have blocked this attack even if the attacker had obtained the employee's password. The incident reveals gaps in security practices rather than sophisticated attack techniques.
What is Tenga doing to prevent future breaches?
Tenga stated that they reset the compromised employee's credentials and enabled multi-factor authentication company-wide. However, the company has not disclosed a comprehensive security improvement plan, the results of an independent security audit, or whether they're offering credit monitoring and identity protection to affected customers as part of their response.
How Runable Can Help Protect Your Business From Similar Incidents
While the Tenga breach highlights the importance of security practices, it also underscores a broader truth: most companies struggle with managing sensitive customer data securely across multiple systems and communications channels.
This is where comprehensive automation and workflow management becomes critical. Runable enables organizations to build automated workflows that keep sensitive data out of email inboxes and in properly secured, logged systems. Instead of customer service teams exchanging sensitive information through email, teams can use Runable's AI-powered automation to handle data management, documentation, and communication in controlled environments.
Think about it: when customer service teams need to document customer interactions, generate reports on customer inquiries, or create records of transactions, they can do this through automated workflows rather than forwarding sensitive information via email. Runable's AI agents can generate documentation, create reports, and maintain audit trails automatically.
For incident response specifically: Rather than relying on manual notification processes when a breach is discovered, teams can use automated workflows to quickly generate breach notifications, compile affected customer lists, and organize customer communications. What might take hours of manual work and email exchanges becomes a streamlined automated process.
For customer data management: Runable helps organizations document data handling policies and implement them through automation. Customer information flows through proper channels rather than ending up scattered across email inboxes.
Starting at just $9 per month, organizations can implement automation workflows that significantly reduce the attack surface that incidents like the Tenga breach exploit.
Use Case: Automate your customer data workflows to keep sensitive information out of employee inboxes and into secure, auditable systems.
Try Runable For Free
Key Takeaways
- Tenga's breach resulted from a single compromised employee email account containing customer names, emails, order histories, and customer service inquiries for over 162 million shipped products
- Multi-factor authentication was apparently not enabled on the breached account, a basic security control that would have prevented the attack entirely
- Adult product retailers face disproportionate targeting by attackers due to the sensitivity of purchase history data, which is valuable for extortion and phishing campaigns
- Email should not be used as a customer data repository; proper database systems with access controls and encryption provide significantly better security
- Customers affected should change passwords, enable multi-factor authentication on personal accounts, and monitor for suspicious activity and extortion attempts
Related Articles
- Fake Chrome AI Extensions: How 300K+ Users Got Compromised [2025]
- Odido Telco Breach Exposes 6.2M Users: Complete Analysis [2025]
- iRobot's Chinese Acquisition: How Roomba Data Stays in the US [2025]
- Odido Data Breach: 6.2M Customers Exposed [2025]
- WPvivid Plugin Security Flaw: Nearly 1M WordPress Sites at Risk [2025]
- Testing OpenClaw Safely: A Sandbox Approach [2025]
![Tenga Data Breach: What Happened and What Customers Need to Know [2026]](https://tryrunable.com/blog/tenga-data-breach-what-happened-and-what-customers-need-to-k/image-1-1771015002070.jpg)



