Flickr Data Breach 2025: What Was Stolen & How to Protect Yourself
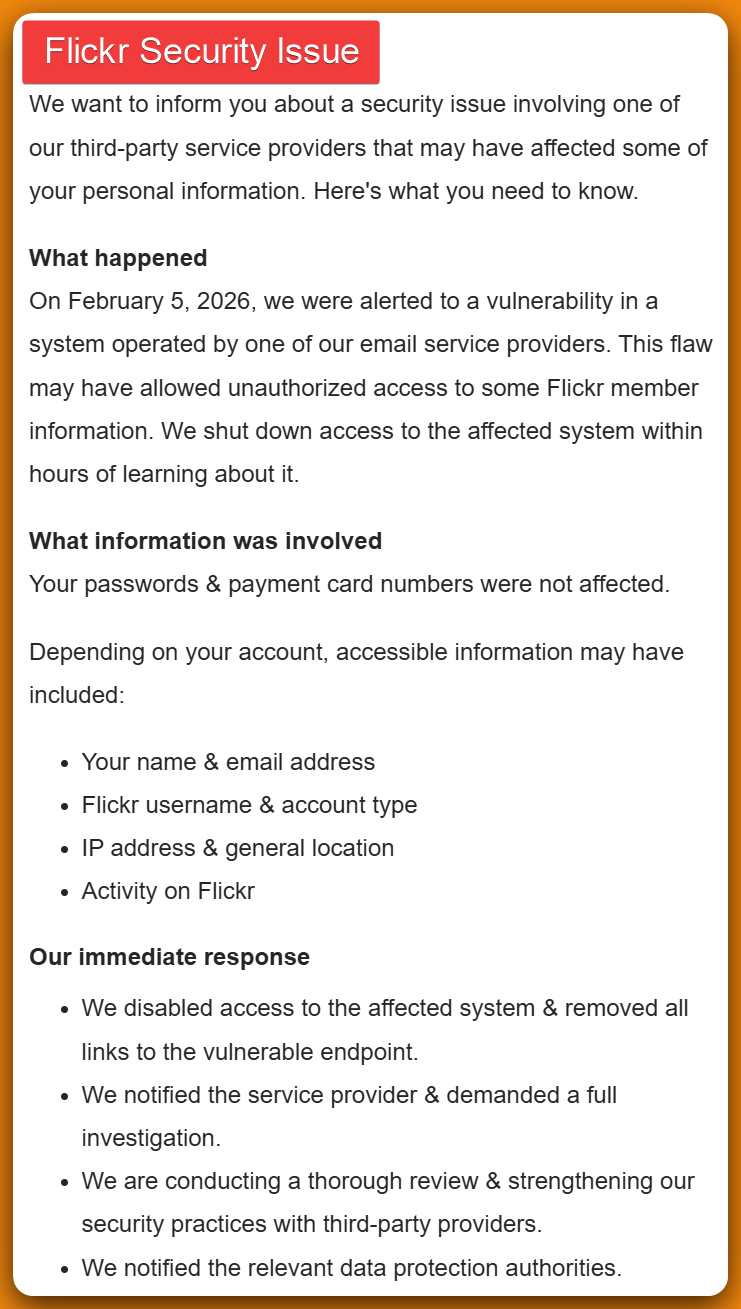
Flickr, the photo-sharing platform trusted by millions of photographers and casual users alike, confirmed in February 2025 that it suffered a significant data breach. The incident exposed sensitive personal information for an undisclosed number of users, though the company was quick to clarify what hackers did NOT access. This wasn't your typical ransomware attack or internal security lapse. Instead, the breach traced back to a third-party email service provider that Flickr uses to send notifications and communications to its user base.
The timing matters here. The breach occurred on February 5, 2025, but Flickr's security team detected it within hours. That rapid response likely prevented even more extensive data theft. Still, the incident raises serious questions about how major platforms handle their third-party vendor relationships, whether your photos are truly safe in the cloud, and what you should do right now if you're a Flickr user.
This article breaks down everything we know about the Flickr breach, what data was compromised, the real risks you face, and concrete steps to protect yourself going forward. We'll also explore why third-party vendors represent a growing security blind spot that even billion-dollar tech companies struggle to manage.
TL; DR
- Breach confirmed: Flickr suffered a third-party data breach on February 5, 2025, affecting customer personal information
- Data stolen: Names, email addresses, usernames, account types, IP addresses, and general location data were exposed
- Data protected: Passwords and financial information were NOT compromised in the attack
- Scope: Affects Flickr's 35 million monthly active users across 190 countries
- Action required: Change your password, enable two-factor authentication, and watch for phishing emails
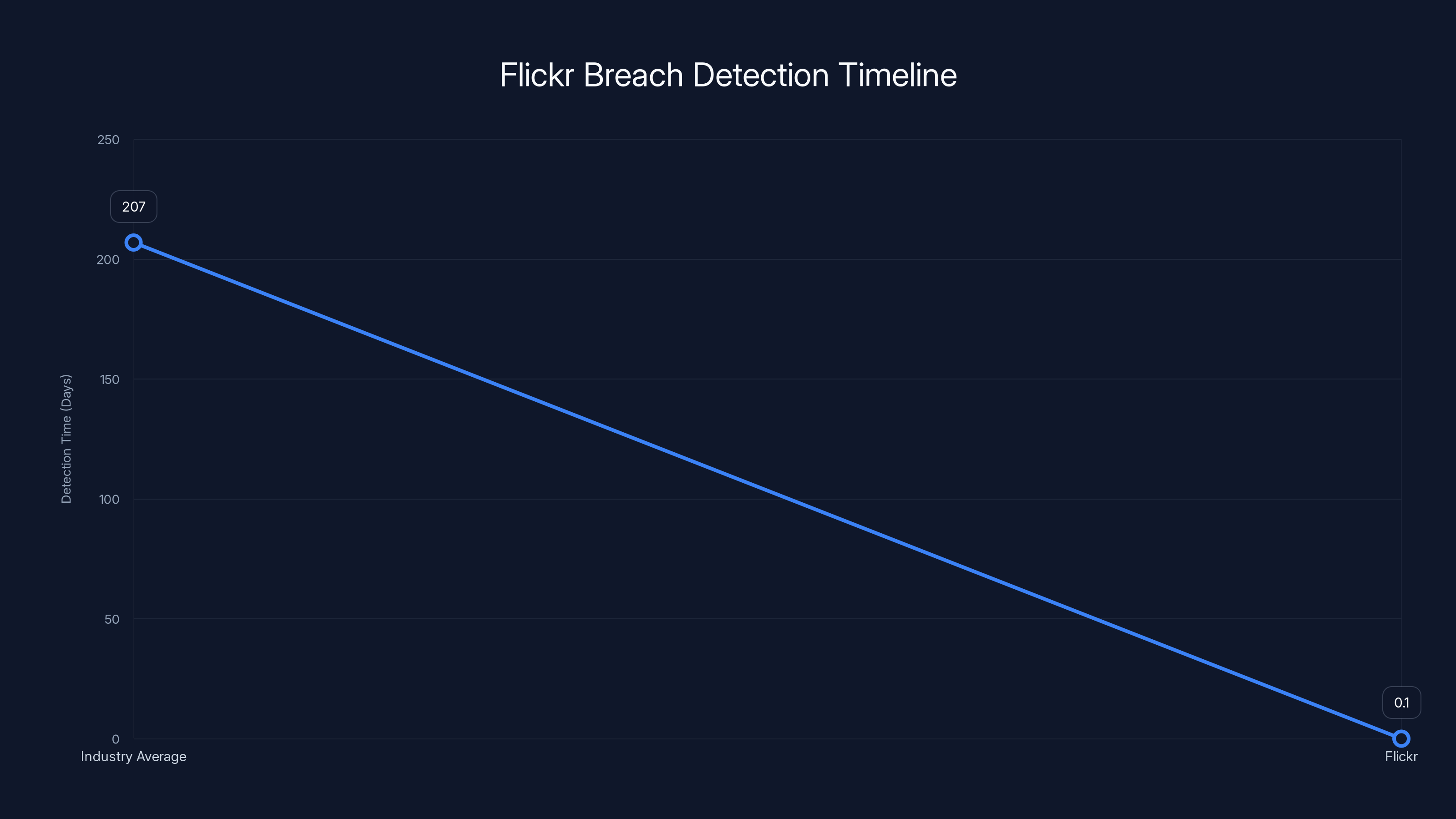
Flickr detected the breach within hours, significantly outperforming the industry average detection time of 207 days. Estimated data based on IBM's 2024 report.
What Actually Happened: The Flickr Breach Timeline
Understanding the breach requires looking at how it unfolded, because the sequence of events actually matters for assessing the damage.
On February 5, 2025, an attacker gained unauthorized access to a third-party email service provider that Flickr uses to manage customer communications. This wasn't Flickr's internal systems that got hit—it was an external vendor. Flickr relies on specialized email service providers to handle the massive volume of notifications that go out to 35 million monthly users. That outsourcing is normal, but it creates a vulnerability chain where the vendor's security becomes your security.
Flickr's security team detected the unauthorized access within hours of the attack occurring. That's actually a positive sign. Many breaches go undetected for months or even years before organizations discover them. The fact that Flickr spotted this intrusion so quickly suggests they maintain reasonable monitoring practices, though that doesn't erase the fact that the breach happened in the first place.
Once detected, Flickr moved to isolate the vulnerable endpoint, shut down the attacker's access, and notify all relevant parties. They contacted law enforcement, data protection authorities across Europe and the United States, and their affected customers directly.
What makes this breach particularly interesting is what wasn't stolen. Flickr explicitly stated that passwords and financial information were not accessed. That's because the breach targeted the email service provider's systems, not Flickr's core database where passwords and payment details are stored. The attacker got what the email provider had access to: user contact information and account metadata.
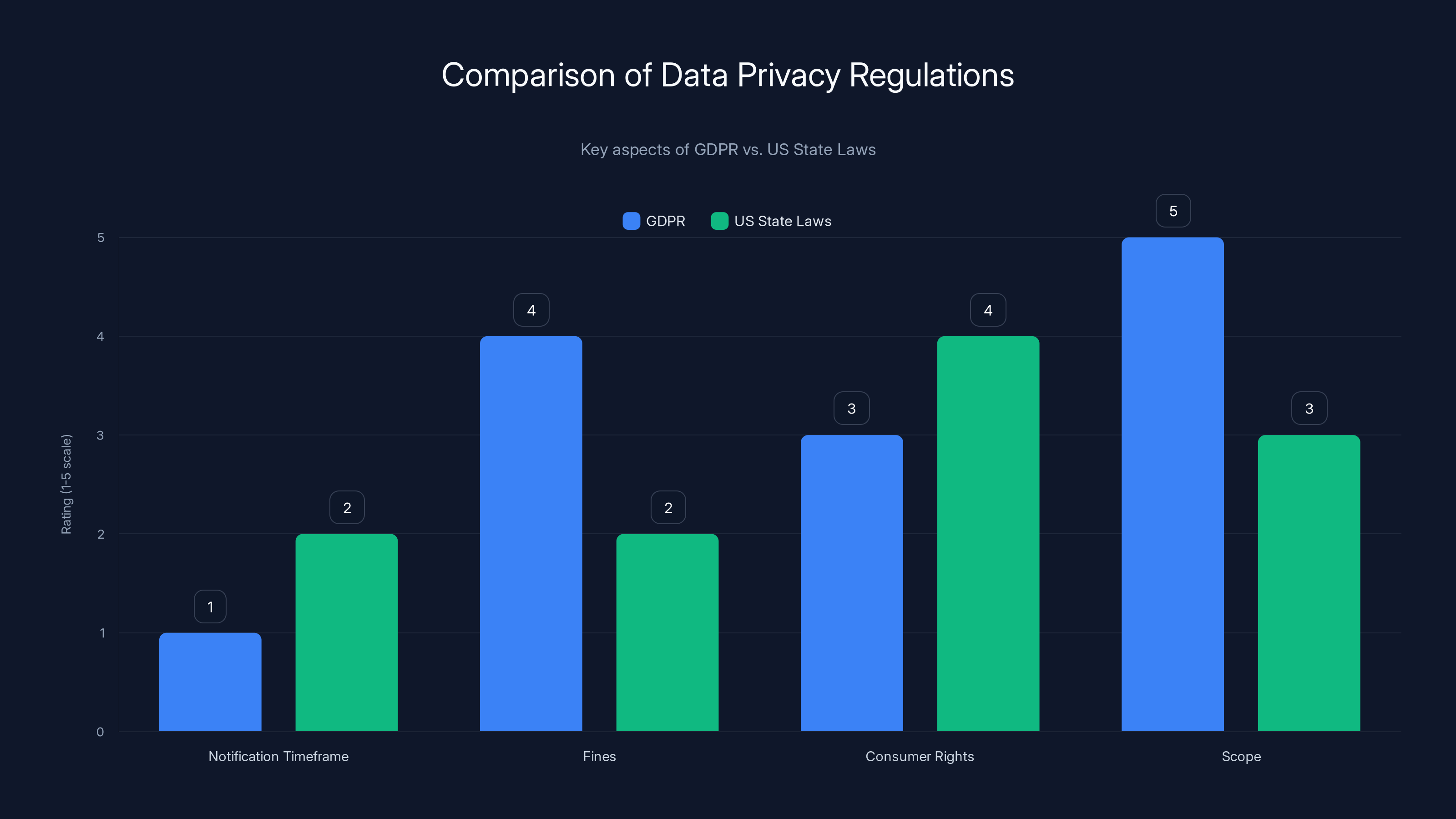
GDPR generally imposes stricter fines and broader scope compared to US state laws, but US laws often provide stronger consumer rights. Estimated data based on typical regulatory comparisons.
The Data Exposed: What Hackers Really Got
Let's be specific about what was compromised, because there's a huge difference between having someone's email address and having their password or credit card number.
The data stolen in the Flickr breach includes:
- Names: Your full name or display name as registered with Flickr
- Email addresses: The primary email address associated with your account
- Usernames: Your Flickr username (the handle you use to log in)
- Account types: Whether you have a free account or Flickr Pro subscription
- IP addresses: The internet address from which you accessed Flickr
- General location data: Approximate geographic location, not precise GPS coordinates
Flickr noted that the exact combination of data varies by user. Some accounts may have had all of these fields exposed, while others may have had only partial information. That's probably because not all users fill in every optional field, and the email provider's database may have included different data snapshots for different accounts.
What was NOT compromised:
- Passwords: Your Flickr password remains secure and was not exposed
- Financial information: Credit card numbers, billing addresses, and payment methods were not accessed
- Photo content: Your actual photos and private albums were not affected
- Private messages: Direct messages between users were not stolen
This distinction matters because it changes the severity assessment. A breach exposing passwords would be catastrophic—attackers could immediately log into accounts and cause havoc. A breach of names and emails is serious but manageable if you take the right precautions.
Why Third-Party Vendors Are the New Security Nightmare
The Flickr breach highlights a critical but often overlooked problem in modern cybersecurity: your security is only as strong as the weakest link in your vendor chain.
Flickr doesn't send emails directly from its own infrastructure. Like most large platforms, they outsource email delivery to specialized providers. These vendors handle massive scale (think billions of emails per day) and maintain the complex infrastructure needed for reliable delivery. It makes business sense. But it also means Flickr trusts that vendor with direct access to customer data.
This creates what security experts call a "supply chain attack" opportunity. Instead of attacking the big target (Flickr), attackers look for softer targets upstream (the email provider). The email vendor probably has fewer security resources, less sophisticated monitoring, and a broader attack surface because they work with hundreds of clients.
Flickr actually isn't alone here. In recent years, we've seen major breaches trace back to third-party vendors:
- MOVEit Transfer vulnerabilities (2023) affected thousands of organizations because enterprises use this file transfer software from Progress Software
- Solar Winds compromise (2020) exposed hundreds of major companies because attackers infiltrated the software update process
- 3CX breach (2023) targeted a communications platform used by enterprises worldwide
The common pattern: the vendor isn't the final target. The vendor is the entry point.
Flickr's response acknowledged this vulnerability. In their notification to customers, they stated: "We are conducting a thorough review and strengthening our security practices with third-party providers." Translation: they're auditing their entire vendor ecosystem and probably implementing stricter security requirements for anyone handling customer data.
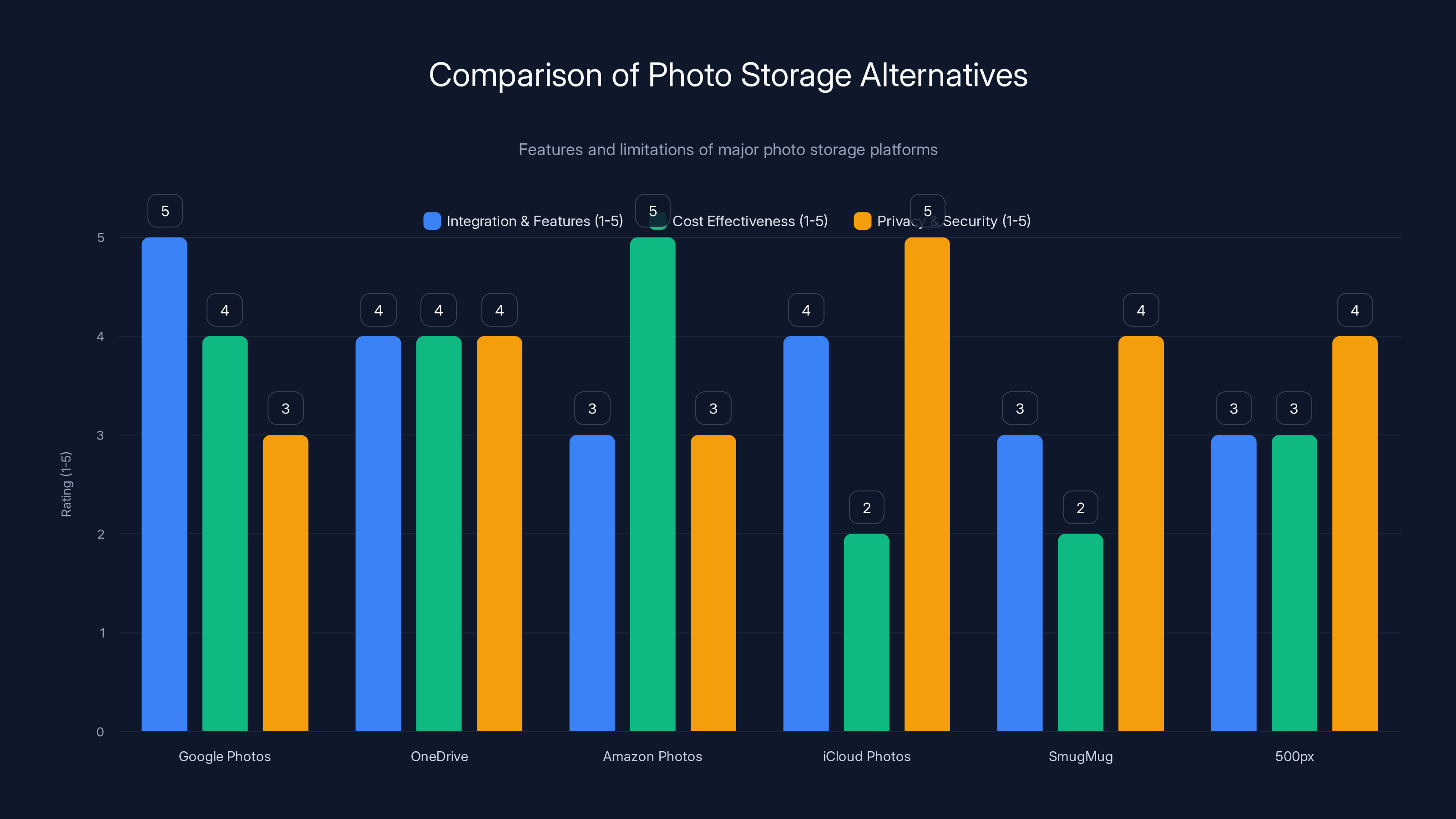
Google Photos offers the best integration, but privacy concerns exist. iCloud Photos excels in security, while Amazon Photos is cost-effective for Prime members. Estimated data based on typical features.
The Phishing Risk: Why This Breach Is Dangerous Right Now
Here's where the real danger sits: armed with your name, email, and the fact that you use Flickr, attackers can now launch sophisticated phishing campaigns.
Phishing isn't just random spam anymore. It's targeted, personalized, and increasingly effective. An attacker with your name and email address can craft messages that appear to come from Flickr, reference details they know about your account, and request sensitive information.
Common phishing scenarios you might see:
Account suspension threat: "Your Flickr account has been flagged for unusual activity. Click here to verify your identity and prevent suspension." The link goes to a fake login page that harvests your credentials.
Payment verification: "We need you to confirm your payment method to keep your Pro subscription active. Enter your credit card details here." You enter your card info into a fake form, and it goes straight to the attacker.
Security alert: "We detected a login from an unfamiliar location. Confirm this was you by entering your password." You think you're protecting your account. You're actually giving away the keys.
Password reset scam: "Click here to reset your password after our recent security incident." The page captures whatever password you enter.
What makes these attacks work is context. The attacker knows you're a Flickr user. They probably know your email address and username. They might know your location (from the IP data). This information lets them craft messages that feel legitimate.
Flickr warned customers about incoming phishing emails in their breach notification. They also provided links to data protection authorities (which is interesting—it suggests the breach may affect EU residents under GDPR, US residents under various state laws, and others under different regulations).
Assessing Your Personal Risk: Who Should Be Most Concerned
Not everyone faces the same level of risk from this breach. Let's break down the risk tiers.
High risk: If you fit any of these categories, you should take immediate action:
- You registered with Flickr using your primary email address
- You use the same password across multiple websites (including Flickr)
- You haven't enabled two-factor authentication on your Flickr account
- You've uploaded sensitive photos to Flickr (financial documents, travel itineraries, location patterns)
- You've provided detailed location information in your Flickr profile
- You've connected Flickr to other services via APIs or integrations
Medium risk: You should still protect yourself, but your immediate danger is lower:
- You use a secondary email address for Flickr that's not linked to important accounts
- You have a unique password for Flickr that differs from your other passwords
- You haven't uploaded sensitive content
- Your Flickr profile contains minimal personal information
Lower risk: Your baseline protections are probably sufficient:
- You registered with a pseudonym or alias
- You used a dedicated email address for Flickr
- You maintain different passwords across services
- You enable two-factor authentication on all accounts
- You regularly monitor your accounts for suspicious activity
The interesting angle here is that photographers who use Flickr professionally might face additional risks. If your photos contain location metadata (called EXIF data), attackers could potentially infer where you live, work, or frequently travel. Professional photographers should particularly review their privacy settings and consider stripping metadata from uploaded images.
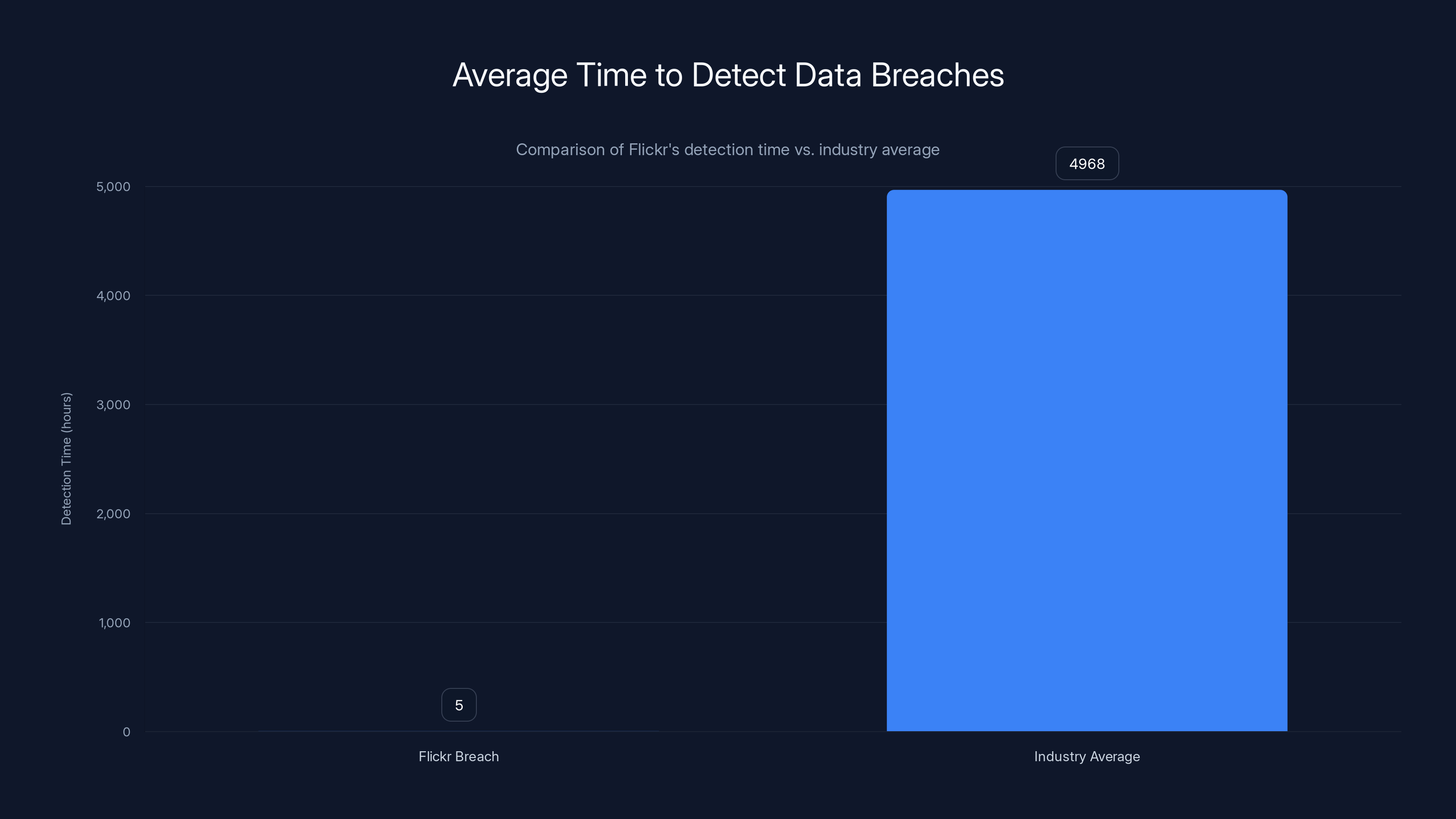
Flickr detected the breach within hours, significantly faster than the industry average of 207 days (4968 hours). This highlights their effective security monitoring.
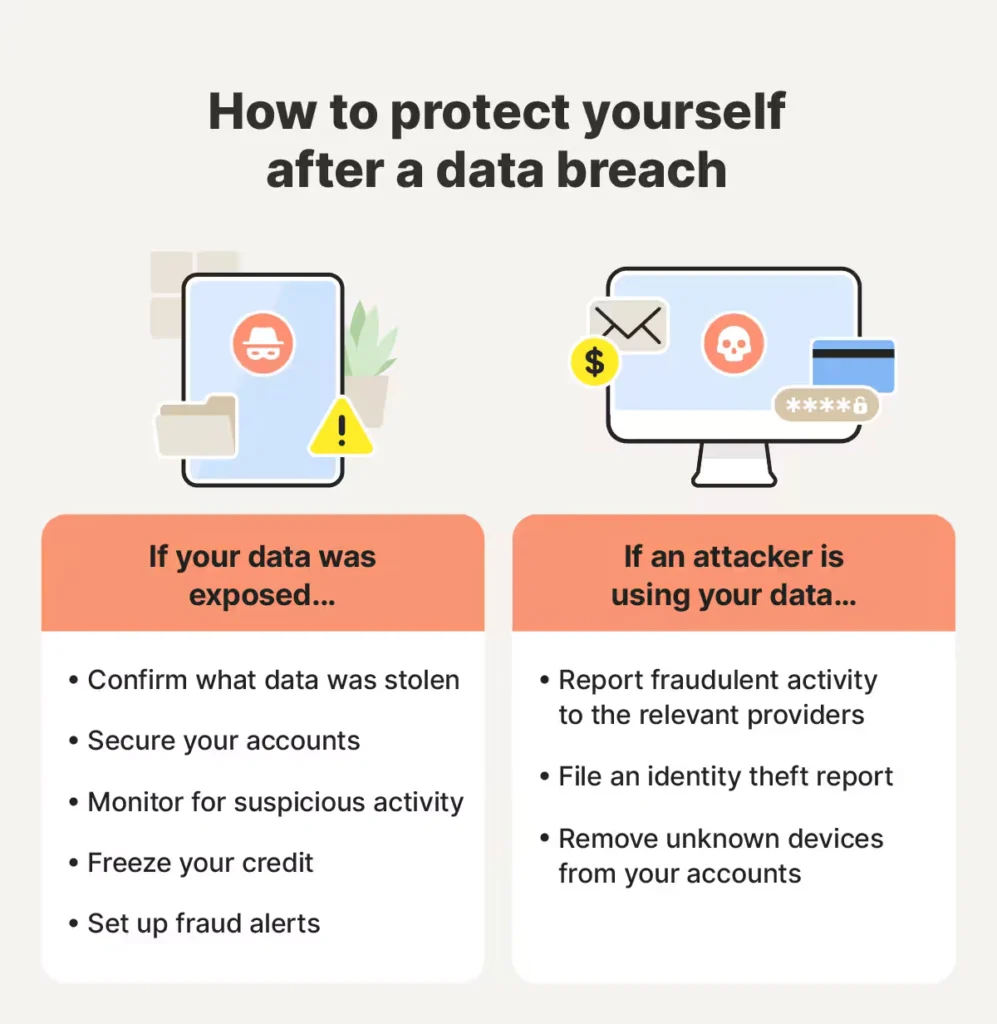
Immediate Actions: What to Do Right Now
If you're a Flickr user, here's what you should do immediately. These aren't suggestions—they're practical steps that reduce your risk.
Step 1: Change your Flickr password immediately
Even though Flickr says passwords weren't compromised, the attackers now have your email and username. They might attempt credential stuffing attacks (trying your email and common passwords on other sites). Using a unique, strong password for Flickr prevents them from accessing your account even if they try.
Your new password should:
- Be at least 16 characters long (longer is better)
- Include uppercase and lowercase letters, numbers, and symbols
- Not contain dictionary words or personal information
- Be completely different from passwords you use elsewhere
Example of a strong password: Kx 7#m P2@n L9$v Q4!b T6 (Don't use this exact one—make your own).
Step 2: Enable two-factor authentication
Two-factor authentication (2FA) means even if someone has your password, they can't access your account without a second verification method. Flickr supports 2FA through apps like Google Authenticator or Authy, or via SMS.
To enable 2FA on Flickr:
- Log into your Flickr account
- Go to Settings → Security
- Select your preferred 2FA method (authenticator app is more secure than SMS)
- Follow the setup wizard and save your backup codes in a safe place
Step 3: Review your account privacy settings
Flickr has granular privacy controls. Check what's publicly visible:
- Review who can see your email address (should be "Me" or "Nobody")
- Check if your profile information is public or private
- Review your photo visibility settings—consider making private any sensitive photos
- Disable automatic social media sharing if you use it
Step 4: Monitor for phishing emails
Be suspicious of any email claiming to be from Flickr. Look for these red flags:
- Generic greetings ("Dear User" instead of your actual name)
- Urgent language designed to make you act without thinking
- Links that don't match Flickr's official domain (if you hover, does it go to flickr.com?)
- Requests for passwords or financial information
- Poor grammar or unusual formatting
If you receive a suspicious email claiming to be from Flickr, report it to Flickr directly. Don't click links in the email.
Step 5: Update your security questions
If you set up security questions for account recovery, update them. Attackers might try to use publicly available information (like your hometown, first pet's name, or school) to guess answers.
Step 6: Check for account compromises
Use a service like "Have I Been Pwned" to check if this email address appears in any other known breaches. If it does, update those passwords too.
Longer-Term Protection: Building Resilience
Beyond the immediate response, you should implement broader security habits that protect you from future breaches.
Adopt a password manager: This is the single most important tool for account security. A password manager generates unique, complex passwords for every service and stores them encrypted. You only need to remember one master password. Services like Bitwarden (free), 1 Password, or Last Pass make this seamless.
Use email forwarding for sign-ups: Services like Simple Login or Duckduckgo's email masking let you create unique email addresses for different services. If one email gets compromised, only that service is affected. You can even revoke access to that email address without losing account access if you set it up correctly.
Enable 2FA everywhere: Apply two-factor authentication to every important account: email, banking, social media, work accounts. Authenticator apps (Google Authenticator, Authy) are more secure than SMS, which can be intercepted via SIM swapping attacks.
Monitor credit reports: Breaches that include names and locations can enable identity theft. Get free credit reports from each of the three bureaus (Equifax, Experian, Trans Union) at annualcreditreport.com. Consider placing a fraud alert or credit freeze if you're concerned.
Regularly audit your accounts: Every quarter, spend 30 minutes checking:
- What apps have access to your accounts
- Which emails are tied to which services
- Whether you still use each service
- If your profile information is still current
Be cautious with permissions: When you sign up for a new service using "Sign in with Google" or "Sign in with Facebook," check what permissions you're granting. Do they really need access to your location? Your contacts? Your browsing history?
Stay informed about breaches: Sign up for notifications from Have I Been Pwned to be alerted immediately if your email appears in future breaches. This gives you the first-mover advantage to change passwords before widespread exploitation.
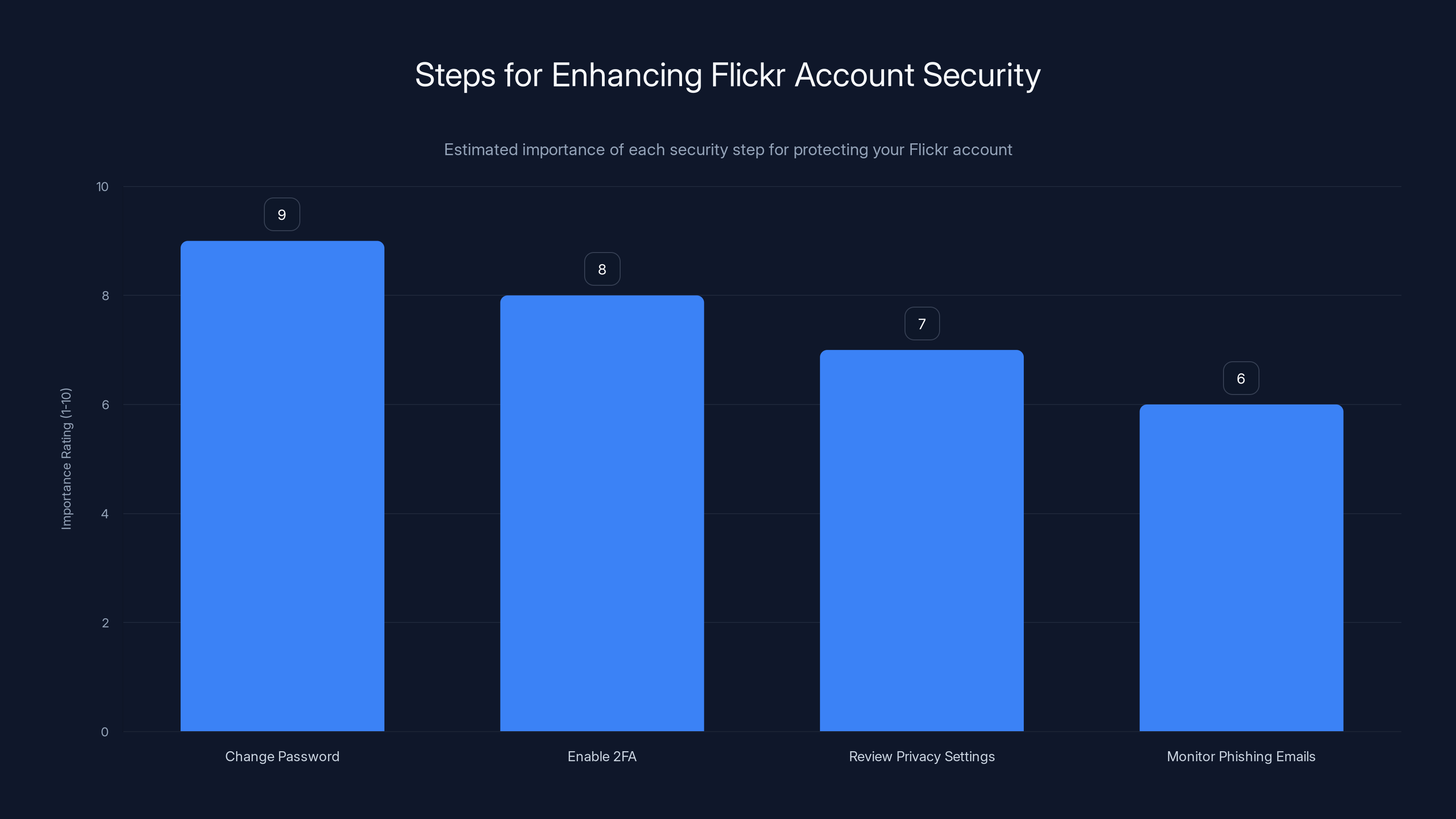
Changing your password and enabling two-factor authentication are the most critical steps to secure your Flickr account. Estimated data based on typical security practices.
The Bigger Picture: Why This Matters Beyond Flickr
The Flickr breach is one incident among thousands that happen annually. In 2024, there were over 2,000 publicly reported data breaches in the United States alone, affecting over 700 million individuals.
What makes Flickr noteworthy isn't the scale (relatively modest compared to major social networks) but the vector. This breach shows that even mature companies with established security practices face significant challenges when managing third-party vendors. Flickr probably has dedicated security teams, regular audits, and compliance frameworks. Yet an email vendor still got compromised.
This tells us something important: no company can completely prevent breaches. The goal isn't zero breaches (impossible). The goal is:
- Minimize what data you collect and retain
- Protect the data you do keep with encryption and access controls
- Detect intrusions quickly (Flickr did this well)
- Respond and communicate transparently (Flickr did this)
- Learn from the incident and improve
For regular users, this means accepting that breaches will happen and focusing on minimizing personal damage when they do.

Understanding GDPR and Data Privacy Impact
Flickr's notification mentioned contacting European and US data protection authorities. This suggests the breach affects users in Europe and the United States, triggering different regulatory frameworks.
Under the General Data Protection Regulation (GDPR), which applies to EU residents and EU-based companies, Flickr must:
- Notify affected individuals without undue delay
- Notify relevant authorities (data protection agencies) if the breach poses risk to rights and freedoms
- Conduct a "Data Protection Impact Assessment" to understand the breach's scope
- Demonstrate they had "appropriate technical and organizational measures" in place
- Be prepared for potential fines up to €20 million or 4% of global annual turnover, whichever is higher
In the United States, there's no single federal law comparable to GDPR. Instead, multiple state laws apply:
- California Consumer Privacy Act (CCPA)
- Virginia Consumer Data Protection Act (VCDPA)
- Illinois Biometric Information Privacy Act (BIPA)
- And laws in Massachusetts, Connecticut, Colorado, and others
These typically require notification within a specific timeframe (usually 30-60 days) and allow individuals to request what data was collected about them and request deletion.
Flickr's legal obligation to notify customers and authorities is driven by these regulations. Companies that violate data breach notification laws face significant penalties beyond the reputational damage.
For users, the regulatory framework provides limited direct benefit (you don't get money back, usually). But it does require companies to be transparent and, theoretically, incentivizes better security practices.

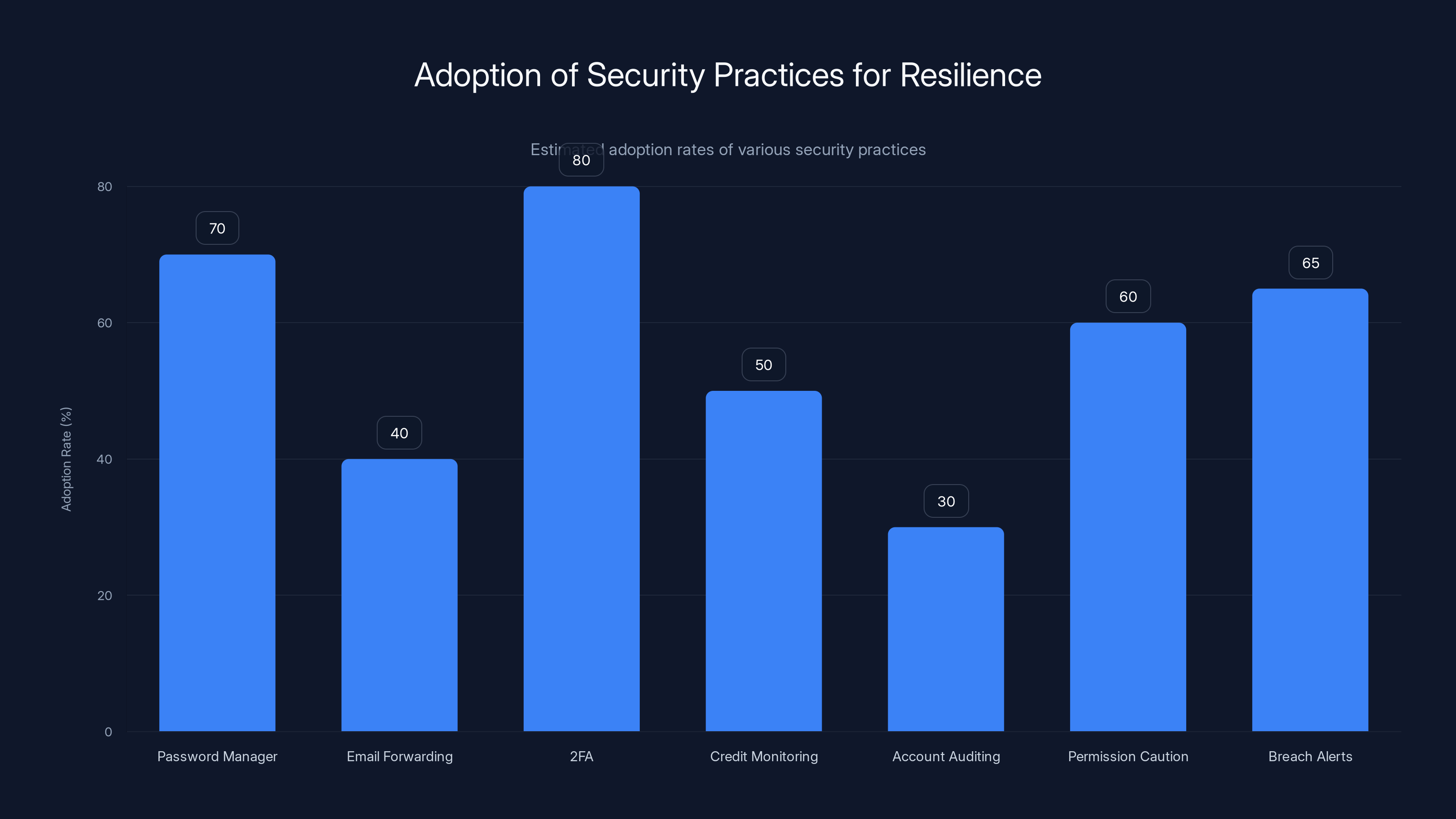
Adoption rates vary among security practices, with 2FA being the most widely adopted at 80%. Estimated data.
Flickr's History: This Isn't the Platform's First Security Issue
Flickr has been around since 2004, making it one of the oldest photo-sharing platforms still in operation (it predates Instagram by six years). It's also had its share of security issues.
In 2014, Yahoo acquired Flickr. In 2019, Yahoo suffered a massive breach affecting 3 billion accounts—one of the largest breaches in history. Flickr, as a Yahoo property, was caught up in that incident.
The platform has changed ownership multiple times:
- Started as an independent startup
- Acquired by Yahoo in 2006
- Spun out and sold to Smug Mug in 2018
Each transition brought changes to infrastructure, security practices, and organizational priorities. The current breach under Smug Mug's ownership is less severe than what happened in 2014, which suggests security practices have improved. But it also reminds us that even mature platforms remain vulnerable.
Smug Mug, Flickr's current owner, is a smaller company than Yahoo or the original Flickr startup. That means fewer resources for security, but potentially better focus and decision-making. The 2025 response (quick detection, transparent communication) suggests Smug Mug is taking security seriously.
What Flickr Says vs. What We Actually Know
It's important to distinguish between what Flickr has officially confirmed and what remains unclear.
Confirmed facts:
- A third-party email service provider was breached on February 5, 2025
- Names, emails, usernames, account types, IP addresses, and location data were exposed
- Passwords and financial information were not compromised
- Flickr detected the breach within hours
- Authorities and customers were notified
- No threat actors have claimed responsibility yet
- The stolen data hasn't appeared on dark web marketplaces (as of the notification)
What remains unclear:
- The exact number of affected users (Flickr hasn't disclosed this)
- Which specific email service provider was compromised (not named publicly)
- Whether the attacker had access to any historical data or just current records
- What the attacker actually downloaded vs. what they could have accessed
- How the attacker initially gained access to the vendor's systems
- Whether any data has been sold or shared privately
Flickr's lack of specificity about the email provider is interesting. Usually, companies disclose the vendor name (maybe not immediately, but within weeks). Not naming the vendor could mean:
- Legal negotiations are ongoing
- The vendor is too important to publicly embarrass
- Flickr hasn't fully investigated yet
- They're still working on getting permission from the vendor to disclose publicly
As time passes, more details will likely emerge. We'll probably learn:
- How the attacker initially compromised the vendor
- Whether other Flickr customers of that vendor were affected
- How the vendor's security practices fell short
- What specific systemic improvements Flickr is implementing
Alternatives and Decisions: Should You Leave Flickr?
Some users will decide this breach is a sign to move to a different platform. That's a legitimate response. Let's look at the alternatives.
Google Photos: Integrates with Android and Google's ecosystem. Free tier includes unlimited storage (compressed quality). Private by default. Major advantage: deep integration with Google services. Disadvantage: Google's data practices are controversial (they train AI models on photos, though you can opt out).
One Drive: Microsoft's cloud storage. Good integration with Windows and Office. Offers 5GB free. Disadvantage: less focused on photo sharing, more on backup and syncing.
Amazon Photos: Included with Amazon Prime membership. Unlimited storage for Prime members. Disadvantage: less powerful discovery and sharing features than Flickr.
i Cloud Photos: Apple's solution for i Phone users. End-to-end encrypted. Disadvantage: expensive, limited to Apple devices, minimal social features.
Smug Mug: The company that now owns Flickr. Premium-focused, paid-only. Excellent for professional photographers. Disadvantage: expensive ($10-20/month), smaller community.
500px: Photography community focused on high-quality images. Paid tiers. Smaller than Flickr but more curated audience.
Here's my honest take: the Flickr breach is serious, but it doesn't necessarily mean you should abandon the platform. The data exposed is embarrassing but not catastrophic (no passwords, no financial data). Flickr detected the breach quickly and responded transparently.
If you're a casual user with generic account information, staying put and implementing better security practices (password change, 2FA) might make sense.
If you're a professional photographer with sensitive content or client information, you might want to migrate to Smug Mug or another platform with stronger guarantees.
The decision depends on your risk tolerance and what you store on the platform.

Red Flags to Watch for Going Forward
If you decide to stay with Flickr, watch for these warning signs that might indicate ongoing problems:
Unexplained account activity: If you see uploads, comments, or edits you didn't make, your account may have been compromised. Change your password immediately.
Emails about unknown accounts: If you receive notifications about activity you didn't perform, log into Flickr and check your login history.
Suspicious third-party access: Review connected apps and integrations. Remove any you don't recognize.
Changes to profile information: If your bio, email, or display name changes without your action, someone may have access.
Follow-up phishing attempts: If you receive multiple emails trying to get you to "verify" information, mark them as phishing and report them.
Rumors of new breaches: Follow tech news and check Have I Been Pwned regularly. If another breach involving Flickr data occurs, you'll want to know quickly.
Flickr should provide transparency about these ongoing security measures. Watch for:
- Blog posts discussing security improvements
- Announcements about vendor security audits
- Updates to their security documentation
- Communications about mandatory password changes
If Flickr goes silent after this breach—no updates for months, no transparency about improvements—that's a red flag suggesting they're not taking security seriously.

The Bigger Lesson: Digital Hygiene Matters More Than You Think
The Flickr breach is ultimately a reminder that you can't rely on companies to protect you. You have to protect yourself.
No matter how sophisticated Flickr's internal security is, they can't control what happens at their vendors. No amount of corporate security spending can eliminate risk entirely. All they can do is minimize it and respond quickly when something goes wrong.
Your responsibility is to:
- Use strong, unique passwords for every service (with a password manager)
- Enable two-factor authentication on all important accounts
- Minimize what data you share with companies
- Monitor your accounts for suspicious activity
- Stay informed about breaches affecting you
- Assume breaches will happen and plan accordingly
Think of it like home security. You can have the best locks, alarm system, and security cameras, but that doesn't guarantee you'll never be burglarized. You also need to be aware of your surroundings, lock your doors, and not advertise when you're away.
Digital security works the same way. Technical controls matter, but behavioral discipline matters more.

FAQ
What data was exposed in the Flickr breach?
The breach exposed customer names, email addresses, usernames, account types, IP addresses, and general location information. However, passwords and financial information were not compromised. The breach traced back to a third-party email service provider, not Flickr's core systems, which is why passwords stored in their main database remained secure.
When did the Flickr breach happen?
The breach occurred on February 5, 2025, and was detected by Flickr's security team within hours. This rapid detection is noteworthy because the average time to identify a breach is 207 days. Flickr then notified customers, law enforcement, and data protection authorities.
How many Flickr users were affected?
Flickr has not disclosed the exact number of affected users. However, the platform has 35 million monthly active users across 190 countries, so the potential scope is significant. The company is likely still investigating the full extent of the breach.
Should I delete my Flickr account?
That depends on your risk tolerance and what you use the service for. If you're a casual user with minimal personal information, you can stay and implement security improvements (strong password, 2FA, privacy settings review). If you're a professional with sensitive content, migrating to another platform might be prudent. The breach itself doesn't necessarily warrant deletion unless you're no longer using the service anyway.
How can I check if my information was stolen?
Use the Have I Been Pwned service (haveibeenpwned.com) to check if your email appears in known breaches. For the Flickr breach specifically, check Flickr's official communications and your email for notifications from Flickr about the incident. Be cautious of emails claiming to be from Flickr asking you to verify information—verify by going directly to Flickr.com rather than clicking email links.
What should I do if I received a phishing email?
Do not click any links in the email. Do not enter your password or personal information. Forward the email to Flickr's abuse/security team, or report it to the FTC at reportphishing.ftc.gov. Delete the email from your inbox. If you're uncertain whether an email is legitimate, go directly to Flickr.com in your browser and check for official notifications from Flickr rather than trusting email content.
Is my Flickr password safe if I didn't change it?
Yes, your password was not exposed in this breach. However, you should still change it to a unique, strong password that you don't use elsewhere. This protects you against credential stuffing attacks where hackers use your email and common passwords to try account takeover on other services.
Can I claim compensation for this breach?
Under current US law, you generally cannot sue for damages from a data breach unless you can prove you suffered specific financial harm or identity theft. European residents may have stronger legal remedies under GDPR. Class action lawsuits sometimes emerge after major breaches. Check with Flickr for any official compensation programs they may offer.
What is two-factor authentication and why do I need it?
Two-factor authentication (2FA) requires two different methods to verify your identity when logging in: something you know (password) and something you have (authenticator app, security key, or SMS code). Even if hackers obtain your password, they cannot access your account without the second factor. It's the single most effective protection against account takeover.
How often should I check my accounts for suspicious activity?
Check at least monthly, or more frequently if you use the service regularly. Look for unexpected uploads, changes to profile settings, new connected apps, or login activity from unfamiliar locations. Set up login alerts if the platform offers them. Flickr allows you to view your login history and revoke session access.

Conclusion: Moving Forward with Better Security
The Flickr breach confirms something security experts have known for years: breaches are not if, but when. They'll happen again—to Flickr, to other platforms you use, and likely to companies whose breaches you'll never hear about.
But here's the thing: that doesn't mean you're helpless. The steps you take right now—changing passwords, enabling two-factor authentication, reviewing privacy settings—actually matter. They reduce your risk from this specific breach and from future incidents.
Flickr handled this breach reasonably well. Detection was fast. Communication was transparent. They didn't hide behind legal liability concerns (at least not publicly). They acknowledged the third-party vendor issue and promised improvements.
What's missing is ongoing accountability. Will Flickr publish security updates in the coming months? Will they detail how they're vetting vendors? Will they offer bug bounties to encourage security researchers to find vulnerabilities before attackers do? The next few months will reveal whether this was a genuine wake-up call or just crisis management.
For you, the action items are clear:
- Change your Flickr password to something strong and unique
- Enable two-factor authentication
- Review your privacy settings
- Watch for phishing emails
- Use a password manager to handle passwords across all services
- Enable 2FA everywhere, not just Flickr
These steps don't require special technical knowledge. They take maybe 30 minutes total. And they make a dramatic difference in your actual security posture.
The Flickr breach is a reminder that companies can't protect you alone. Your security depends on a combination of what platforms do (choose secure vendors, detect breaches quickly, respond transparently) and what you do (strong passwords, 2FA, awareness). Both matter. You can't control what platforms do, but you can absolutely control your own practices.
Start today. Don't wait for the next breach to become real to you.
Related Security Topics
If you're interested in protecting yourself better, explore these related areas:
- Data breach notification requirements and your rights
- How password managers work and which ones are trustworthy
- Setting up two-factor authentication on all your accounts
- Understanding encryption and why end-to-end encryption matters
- Recognizing and avoiding phishing attacks
- Credit freezes and fraud alerts
- Using a VPN to protect your IP address
- Stripping EXIF data from photos before uploading

Key Takeaways
- Flickr confirmed a February 2025 breach of a third-party email provider exposing names, emails, usernames, IPs, and locations for millions of users globally
- Passwords and financial information were NOT compromised, but exposed PII enables targeted phishing attacks with high success rates
- Immediate actions: change your Flickr password to something unique, enable two-factor authentication, review privacy settings, and watch for phishing emails
- Third-party vendor breaches represent a growing security challenge even for mature companies with sophisticated internal security practices
- Long-term protection requires password managers, two-factor authentication on all important accounts, regular account audits, and breach monitoring services
Related Articles
- Quishing: The QR Code Phishing Scam Taking Over [2025]
- Digital Squatting: How Hackers Target Brand Domains [2025]
- DNS Malware Detour Dog: How 30K+ Sites Harbor Hidden Threats [2025]
- Network Modernization for AI & Quantum Success [2025]
- How Roblox's Age Verification System Works [2025]
- Betterment Data Breach: 1.4M Accounts Exposed [2025]
![Flickr Data Breach 2025: What Was Stolen & How to Protect Yourself [2025]](https://tryrunable.com/blog/flickr-data-breach-2025-what-was-stolen-how-to-protect-yours/image-1-1770651954117.jpg)



