Google Rejected 1.75M Android Apps and Banned 80K Developer Accounts in 2025: Here's What It Means
Google dropped a jaw-dropping security report at the start of 2025, and the numbers are frankly staggering. The company rejected nearly 1.75 million Android apps from the Play Store and permanently banned over 80,000 developer accounts for violations. On top of that, Google blocked 255,000 apps from accessing sensitive user data.
But here's the thing—these numbers actually tell a more nuanced story than they first appear. Yes, 1.75 million rejections sounds enormous. But it's actually down from previous years. The real story isn't just about the scale of enforcement; it's about how enforcement is working, why the numbers are dropping, and what this means for developers, users, and the mobile app ecosystem moving forward.
Let me walk you through the data, break down what Google's doing differently, and explain why you should care about this whether you're a developer, security researcher, or just someone who uses Android every day.
TL; DR
- Google rejected 1.75 million apps in 2025 for policy violations—down from higher numbers in previous years
- 80,000+ developer accounts were permanently banned, preventing bad actors from republishing malicious apps
- 255,000 apps blocked from accessing sensitive user permissions like camera, location, and contacts
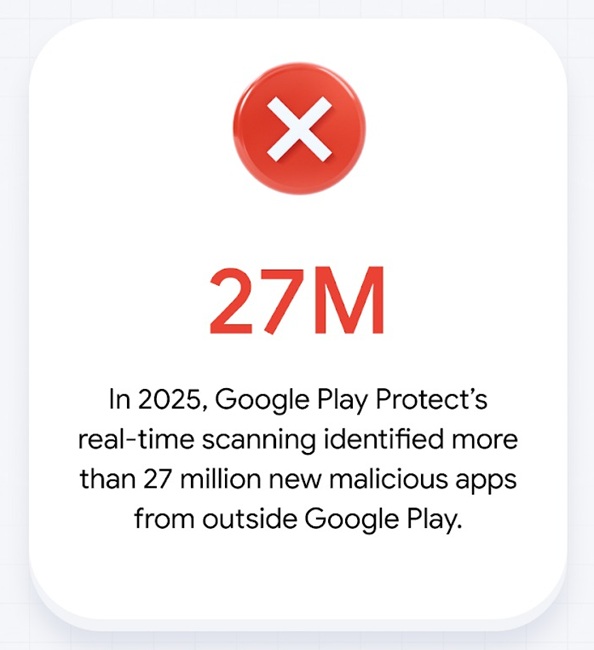
- Play Protect scanned 350 billion apps daily, identifying over 27 million malicious apps outside the Play Store
- Gen AI-powered review systems now catch complex malicious patterns faster than human reviewers alone
- The trend is positive: fewer apps need rejection because Google's preventive measures are working upstream
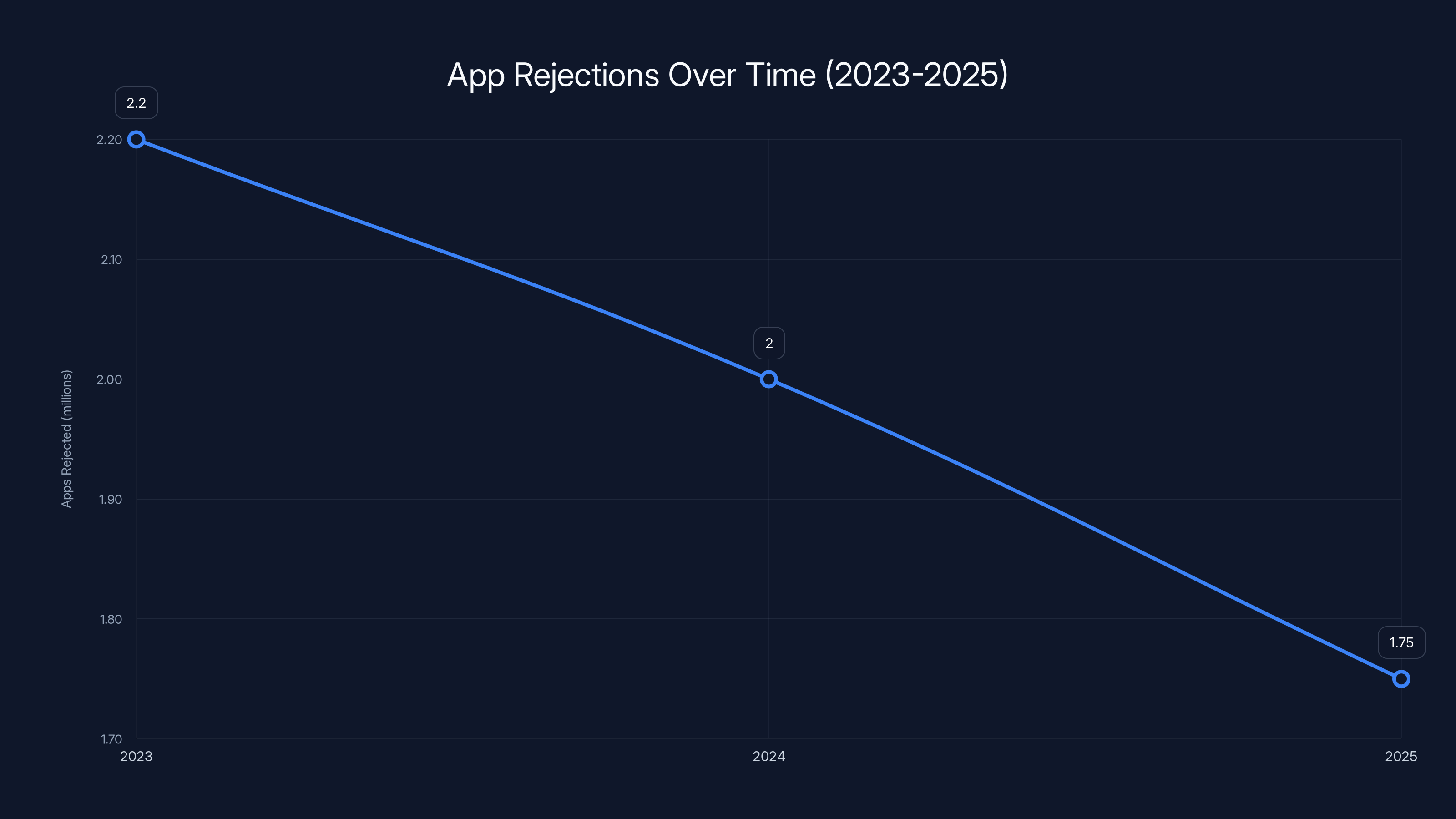
The chart shows a declining trend in app rejections from 2023 to 2025, suggesting improved preventive measures or better evasion tactics by developers.
The Scale of Android Security Enforcement in 2025
When you hear "1.75 million apps rejected," your first instinct might be panic. That's a lot of malicious software. But context matters—and Google's actually been clearer about the context in 2025 than in previous years.
Let's talk about what this number really represents. Google runs more than 10,000 safety checks on every single app submitted to the Play Store. These aren't quick scans. They're comprehensive evaluations that check for malware, privacy violations, policy breaches, and suspicious behavior patterns. If an app fails even one critical check, it gets rejected.
The 1.75 million figure includes apps rejected for many different reasons. Some are outright malware designed to steal data. Others are legitimate apps with minor policy violations—maybe they're using deprecated APIs, or they're requesting permissions they don't actually need. The largest category? Apps designed to bypass Google's security systems or hide their true functionality.
What's interesting is that this number is lower than 2024, when Google rejected approximately 2 million apps. And it's significantly lower than 2023 figures. This suggests Google's preventive measures are actually working. Instead of catching malicious apps after they're submitted, Google is now stopping bad actors before they even reach submission.
The 80,000 developer accounts banned tell an even more important story. These aren't one-time violations. These are accounts belonging to developers who repeatedly attempted to publish harmful apps, evade detection, or violate policies. By banning these accounts, Google prevents the "whack-a-mole" problem where a single bad actor creates multiple accounts to republish rejected apps under different names.

Why the Rejection Numbers Are Actually Dropping
This is where the story gets interesting. The conventional wisdom would be that more apps mean more rejections. But that's not what's happening. The Play Store rejection rates are going down, and it's not because fewer malicious apps are being submitted—it's because Google's catching them earlier in the process.
Google introduced several policy enforcement mechanisms in recent years that prevent bad apps from ever making it to submission:
Mandatory pre-review checks require developers to complete security assessments before submitting apps. This forces developers to think about security upfront, not as an afterthought. Legitimate developers appreciate this. Bad actors see the friction and abandon their efforts.
Developer verification requirements mean that developers submitting apps must verify their identity and business information. This eliminates the anonymity that malicious developers rely on. When you can't hide behind fake identities, you can't easily republish rejected apps under new accounts.
API access controls restrict apps from using sensitive Android APIs without explicit justification. An app doesn't need root access to send notifications. A flashlight app doesn't need your location data. By forcing developers to justify sensitive permissions, Google catches suspicious behavior patterns immediately.
The combination of these upstream controls means fewer bad apps make it to the submission stage. So the rejection numbers drop, but security actually improves. It's prevention, not punishment.
Google also saw fit to be more transparent about what happens after rejection. They provide detailed rejection explanations, guidance on how to fix violations, and clear pathways to appeal. This benefits legitimate developers who made honest mistakes while making it harder for malicious developers to iterate quickly.
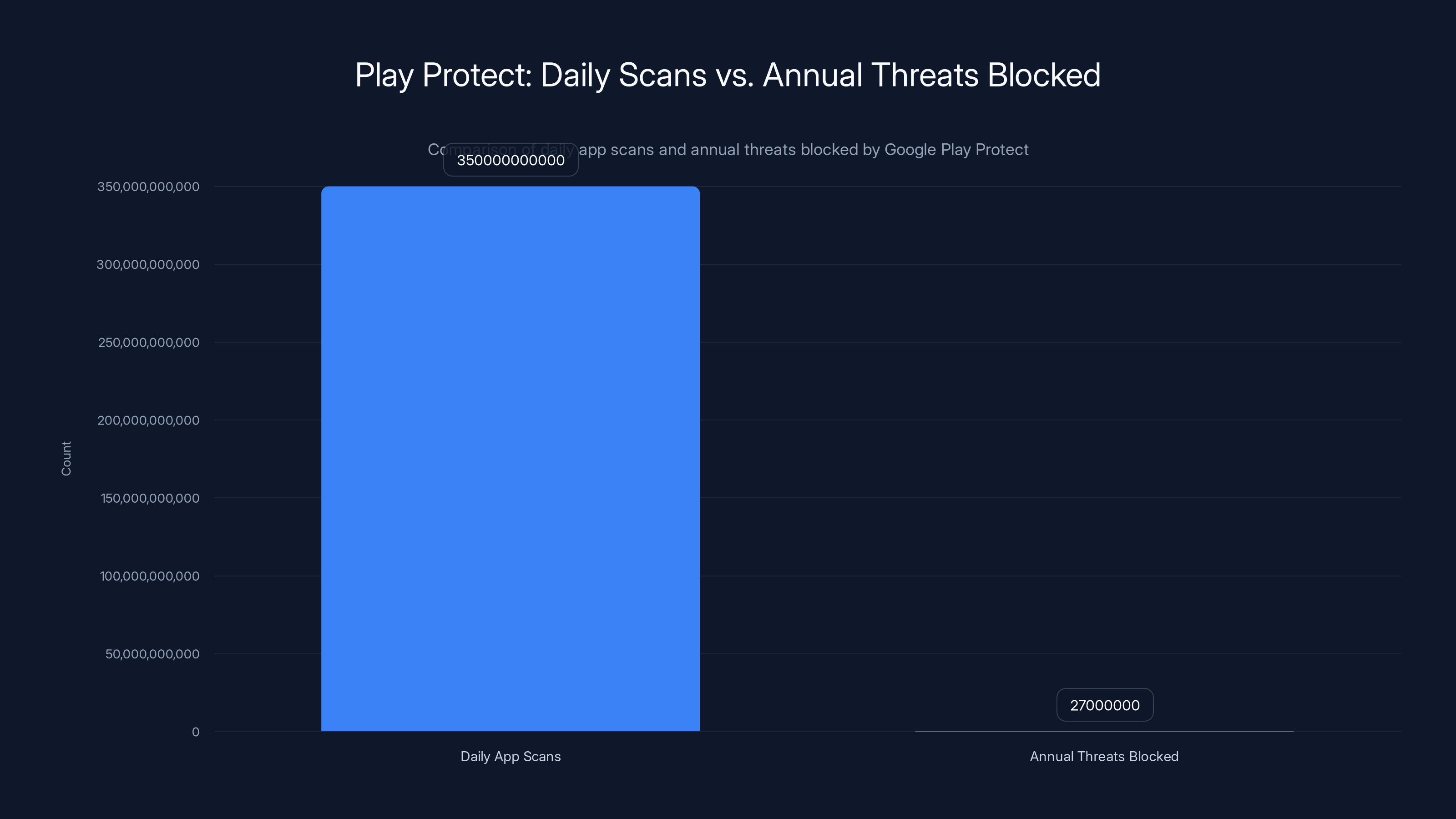
Google Play Protect performs 350 billion app scans daily, identifying 27 million threats annually. This highlights the vast scale of app scanning compared to the number of threats blocked.
The Shift to AI-Powered Review Systems
Here's a significant change in 2025: Google integrated Generative AI models into the app review process, while keeping human reviewers in the loop. This isn't about replacing human judgment—it's about augmenting it.
Why does this matter? Because malicious apps are getting smarter. Modern malware doesn't just steal data anymore. It uses sophisticated obfuscation techniques, chains multiple permission requests together to avoid triggering alerts, and sometimes doesn't even activate its malicious payload until weeks after installation.
Traditional rule-based detection systems struggle with this. They look for known patterns, but complex new malware creates unknown patterns. Gen AI models, trained on millions of legitimate and malicious apps, can spot behavioral anomalies that human reviewers might miss.
Here's how the AI-assisted review process works in practice:
- Automated scanning analyzes app code, permissions, networking behavior, and embedded libraries
- Gen AI pattern recognition identifies complex or unusual behavioral chains that might indicate hidden malicious intent
- Risk scoring assigns apps a probability of being harmful based on detected patterns
- Human review focuses on high-risk apps and edge cases where the AI is uncertain
- Final decision combines AI recommendation with human judgment
This hybrid approach is crucial. AI catches the complex stuff. Humans provide context and judgment. The result is faster reviews and better accuracy.
Google claims this integration has significantly accelerated the review process while maintaining security standards. Apps that previously took days to review now get reviewed in hours because the AI does the heavy lifting of pattern matching.
The 255,000 Apps Blocked from Sensitive Data Access
Now let's talk about the apps that weren't rejected outright but were blocked from accessing sensitive user data. This is actually more interesting than the total rejection numbers because it shows a shift in enforcement strategy.
Instead of banning an app completely, Google now has granular controls. An app might be technically acceptable under Play Store policies, but if it's requesting camera access, location data, and contact access without legitimate reason, Google can revoke those specific permissions.
This affected 255,000 apps in 2025. Some of these apps probably didn't understand the new privacy rules. Others were deliberately trying to access more data than necessary, hoping the user wouldn't notice or would grant permissions without reading carefully.
What's significant about this approach is it protects users without completely removing apps from the ecosystem. If you've already installed an app that's now blocked from accessing certain permissions, the app still works—it just can't access your camera or location data even if the user grants permission.
This is particularly important for legacy apps. An app built in 2018 might have been following the privacy rules at the time, but those rules have evolved significantly. Rather than removing the app entirely, Google gives developers time to update it. If they don't comply within a set period, the app faces removal.
Play Protect: 350 Billion Daily Scans and 27 Million Threats Blocked
Let's zoom out and look at the bigger picture. Google's Play Protect is running 350 billion app scans every single day. Let that number sink in for a moment. That's not 350 billion devices. That's 350 billion individual app scans.
In 2025, Play Protect identified over 27 million new malicious apps from outside the Play Store. These are apps people tried to install from third-party sources, sideloaded APKs, or alternative app stores. Google detects them and warns users.
Let's think about what this means. The official Play Store has roughly 4 million apps. Google scanned the equivalent of 87 times that many apps in a single day. And it caught 27 million new malicious apps across the year.
This creates an interesting situation. Users who stick to the official Play Store are reasonably safe. Users who sideload apps or use alternative stores face significantly higher malware risk. Play Protect catches most of the dangerous stuff, but "most" isn't the same as "all."
The numbers also tell us something important about the size of the malware ecosystem. There are clearly people working full-time to create malicious Android apps. The fact that Google finds millions of new ones every year suggests this is a substantial criminal enterprise.
What's less clear is whether Play Protect's detection rate is actually 100% or whether some malware gets through. Google doesn't publish false negatives—only what it catches. So we know Play Protect blocks 27 million threats, but we don't know if those represent 90% of all threats or 99%.
Regardless, the trend is clear. For the average user, staying on the official Play Store and keeping their device updated provides robust protection.

Google bans approximately 220 developer accounts daily, reflecting their proactive stance against malicious activities. Estimated data based on annual ban reports.
Developer Account Bans: Permanent Consequences for Bad Behavior
The 80,000+ permanent developer account bans are honestly the enforcement mechanism I'm most impressed by. It's not flashy, but it's incredibly effective.
Here's why: malicious app developers operate on thin margins. They create an app, upload it to the Play Store, and try to monetize it (either through ads, in-app purchases, or by stealing user data) before Google catches them. When Google rejects the app, they create a new account and try again under a different name with slight modifications.
By permanently banning developer accounts, Google breaks this cycle. A bad actor can't just keep creating new accounts indefinitely. After enough violations, their identity is blacklisted.
Google's gotten more aggressive about this in recent years. They cross-reference developer information, phone numbers, payment methods, and device fingerprints. When they ban an account, they often ban the person behind multiple accounts simultaneously.
Developer bans aren't just reactive—they're also preventive. When someone knows a permanent ban is coming after repeated violations, they're less likely to start the game in the first place.
But there's a trade-off. Sometimes legitimate developers get caught in the net. Maybe they made honest mistakes, or maybe they were hacked, and someone else used their account to publish malicious content. When this happens, Google's appeal process becomes crucial. The company does handle appeals, but the process can be slow and frustrating for innocent developers.
Over 80,000 accounts banned in a year is a significant number. That's roughly 220 accounts per day. For context, that means Google's trust and safety team is processing, investigating, and acting on over 200 accounts daily. The logistics of this alone are impressive.

Spam Ratings and Review Bombing: Fighting Manipulation at Scale
One aspect of App Store security that doesn't get enough attention is rating and review manipulation. Developers sometimes pay for fake positive reviews to boost visibility. Competitors pay for fake negative reviews to damage rankings. Bad faith users leave bombs of one-star reviews.
Google's anti-spam protections blocked 160 million spam ratings and reviews in 2025. That's spam content removed from the visible ecosystem.
More specifically, Google prevented apps targeted by review bombing from experiencing the average 0.5-star rating drop these attacks typically cause. This is important because many users make download decisions based on ratings. When competitors artificially tank an app's rating, honest users lose trust in the real reviews.
How does Google catch this? Multiple signals:
Temporal analysis flags when an app suddenly receives hundreds of new reviews in a short time. Legitimate review patterns are gradual.
Geographic clustering identifies when reviews come from the same IP range or devices, suggesting coordinated fake accounts.
Content analysis uses NLP to spot generic or repetitive review text that appears thousands of times.
User behavior signals track whether reviewers have actually installed and used the app or if they're just rating.
Payment tracing identifies when reviewers were paid to leave reviews through linking to payment services.
Removing 160 million spam reviews requires sophisticated infrastructure. But it also directly improves user trust in the Play Store ecosystem. If ratings are reliable, users are more confident in their download decisions.

The Privacy-Forward Approach: Data Safety Sections and Permission Controls
Google's also shifted enforcement toward a privacy-forward model in 2025. Instead of just checking if apps are malicious, Google's now deeply auditing whether apps request excessive permissions.
The Data Safety section on every Play Store listing now discloses exactly what data an app collects and how it uses that data. This came from regulations like the EU's Digital Markets Act and growing user privacy concerns.
But Google went beyond just disclosure. They created Play Policy Insights tools available in Android Studio that help developers understand what permissions their app actually needs versus what it requests. Many apps request permissions defensively—"just in case"—without genuine need.
Google's enforcement now penalizes this. If an app is in the productivity category but requests access to your contacts, payment methods, and microphone, that's suspicious. Google will flag it for review.
What's interesting is this aligns incentives. Developers who truly respect user privacy now have a competitive advantage on the Play Store because Google's algorithms give preference to apps that request only necessary permissions.
Over the past two years, Google's said that this initiative has "significantly reduced" privacy-invasive permission requests. While they don't publish exact metrics, the trend is clear from user feedback and third-party analyses.
This privacy-forward approach is probably more important for long-term Android security than app rejections. Malware tries to be invisible. Privacy violations are often in plain sight—developers just bet users won't notice or won't care.
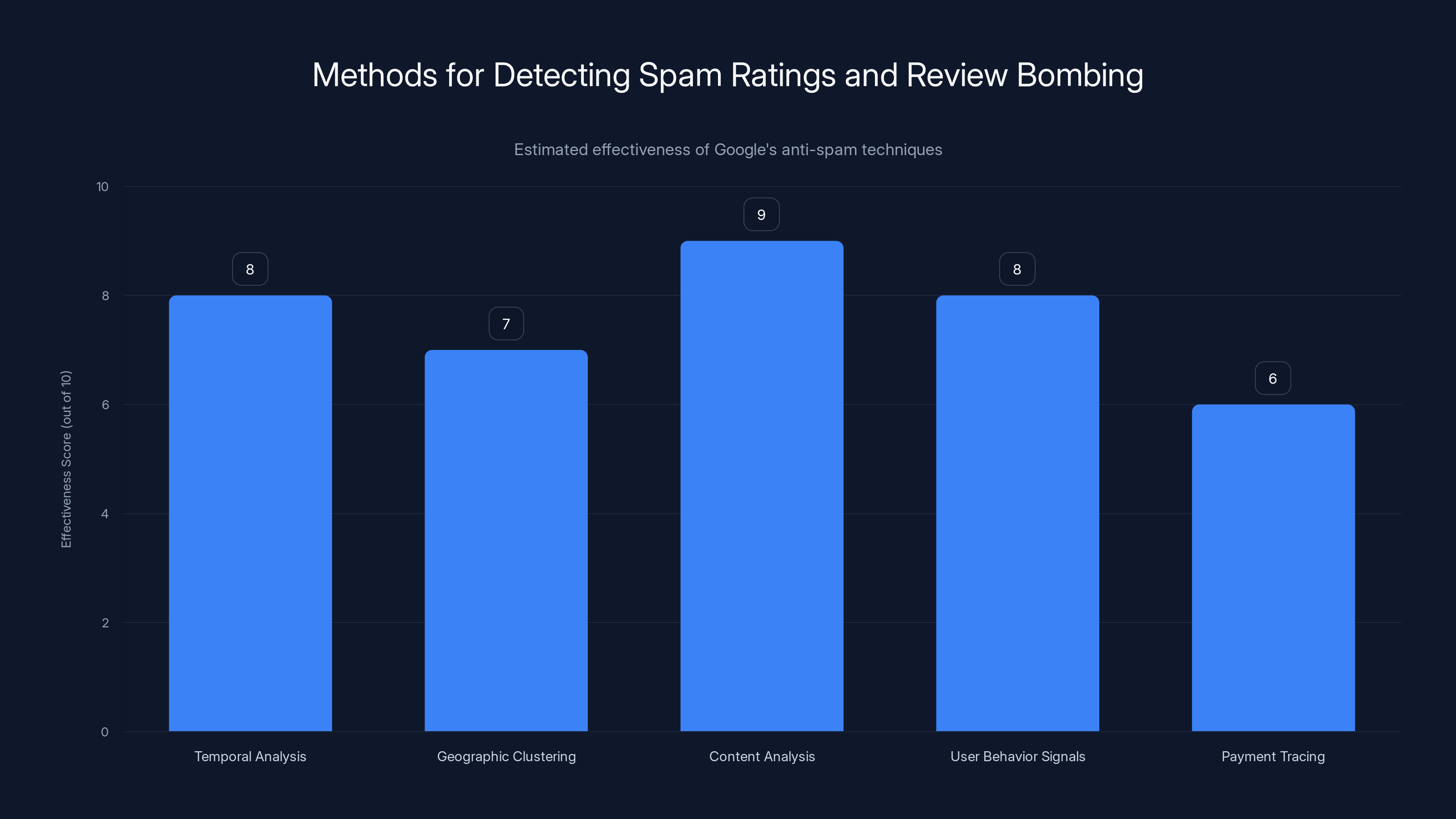
Google employs various methods to detect and prevent spam ratings and review bombing. Content analysis is estimated to be the most effective technique, scoring 9 out of 10 in effectiveness. (Estimated data)
Comparing 2025 Numbers to Historical Enforcement Data
To understand what 1.75 million rejections means, we need context from previous years:
| Year | Apps Rejected | Developer Accounts Banned | Trend |
|---|---|---|---|
| 2023 | ~2.2 million | Unknown | Baseline |
| 2024 | ~2.0 million | Unknown | Slight decrease |
| 2025 | 1.75 million | 80,000+ | Notable decrease |
The pattern is clear: rejection numbers are declining. This could mean two things:
Optimistic interpretation: Google's preventive measures are working. Bad apps aren't making it to submission in the first place.
Pessimistic interpretation: The bad guys are getting better at evading detection. Fewer apps are being caught, but more malicious apps are slipping through.
The evidence suggests the optimistic interpretation is more accurate. Google's transparency about the mechanisms (mandatory pre-review, developer verification, API restrictions) makes sense. And the fact that independent security researchers haven't reported a spike in undetected malware in the Play Store suggests the system is working.
But it's worth being skeptical. Google has incentives to make the Play Store look safe—it's part of their ecosystem. We can't be 100% certain that fewer rejections equal better security without independent verification.

How Different App Categories Are Affected by Enforcement
Enforcement doesn't affect all app categories equally. Some categories face significantly higher rejection rates:
Finance and payment apps face the strictest review because they handle user money. Bank-grade security reviews are standard, not exceptional.
Health and fitness apps handling medical data face heightened privacy audits following HIPAA and similar regulations.
Kids' apps face completely separate review processes with additional security and privacy requirements.
Messaging and communication apps face scrutiny around encryption and data retention because they handle sensitive communications.
Utilities and productivity apps (like flashlight or weather apps) face enforcement because they often request excessive permissions for simple functions.
The last category is where most of those 255,000 permission-blocked apps likely came from. A weather app doesn't need location data updated 24/7. A calculator doesn't need microphone access. When Google finds these patterns, it blocks them.

The Role of APK Scanning and Code Analysis
Google doesn't just look at what an app claims to do. It analyzes the actual compiled code before deployment. This catches obfuscation techniques, hidden libraries, and behavioral patterns that could indicate malicious intent.
APK (Android Package Kit) scanning involves:
- Decompilation and code analysis to understand what the app actually does
- Library scanning to check for known malicious libraries or vulnerable versions
- Network behavior analysis to see what servers the app communicates with
- Dynamic analysis in sandboxed environments to watch how the app behaves when run
- Machine learning pattern recognition to flag unusual behavior chains
This multi-layered approach catches apps that might look legitimate on the surface but contain hidden malicious functionality.
The fact that Google employs all these techniques for 10,000+ checks per app explains why rejection rates are lower. If you're a legitimate app developer, you'll probably pass. If you're trying to hide malicious functionality, you'll probably get caught.

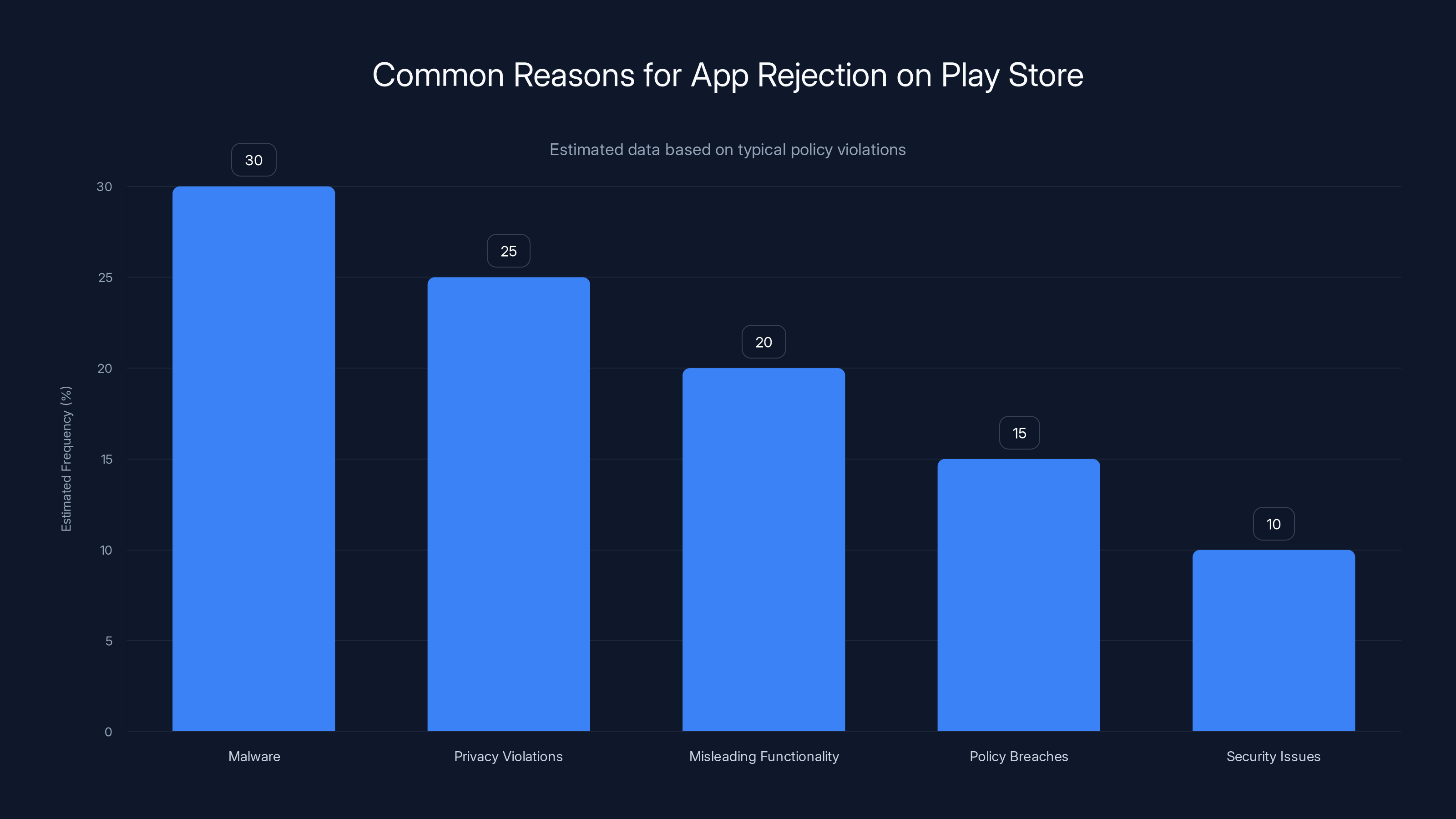
Malware and privacy violations are the most common reasons for app rejection on the Play Store, accounting for over half of the cases. (Estimated data)
What This Means for App Developers
If you're developing apps for Android, Google's 2025 enforcement tells you something clear: playing by the rules is increasingly important. You can't rely on flying under the radar.
Legitimate developers should focus on:
Requesting only necessary permissions: Don't ask for location if your app doesn't use it. Google's tools help you audit permission requests.
Proper code signing and validation: Ensure your identity is verified through Play Console. This builds trust and prevents impersonation.
Clear privacy policies: Disclose what data you collect and why. The Data Safety section isn't optional anymore.
Regular security audits: Have your code reviewed for vulnerabilities before submission. This catches issues before Google does.
Respecting API deprecations: Google regularly updates Android APIs. Legacy code using deprecated APIs raises red flags.
Developers who follow these practices report smooth approval processes. Those who cut corners face rejections, delays, and sometimes account bans.

What This Means for Users
If you install apps exclusively from the official Play Store and keep your device updated, the 2025 enforcement data suggests you're reasonably protected. Google's security measures are working.
But it's not foolproof:
Sideloaded apps bypass Google's review entirely. Don't sideload apps unless you absolutely trust the source.
Third-party app stores offer less scrutiny than the Play Store. Alternative stores sometimes host rejected apps.
Legitimate apps with privacy violations might pass Google's review but still collect more data than you'd want. Check the Data Safety section.
Zero-day vulnerabilities might exist in even thoroughly reviewed apps. Update your Android OS regularly.
The reality is that perfect security doesn't exist. But choosing the Play Store and staying updated gets you most of the way there.

Looking Ahead: Google's 2025-2026 Security Roadmap
Google's announced future enforcement focuses on:
Developer verification expansion: Making mandatory identity verification more robust across all regions and account types.
AI-driven anomaly detection: Expanding Gen AI systems to catch more complex behavioral patterns.
Real-time threat intelligence: Sharing threat data more rapidly with manufacturers and security partners.
Privacy sandbox improvements: Creating new app architectures that don't require extensive permission requests.
The trajectory suggests Google will continue tightening standards while trying to keep approval friction manageable for legitimate developers.

The Bigger Picture: Why App Enforcement Matters
Android powers roughly 3 billion devices worldwide. Every rejected app and banned developer represents a potential threat to millions of people.
Google's enforcement matters because it's the primary protection between users and malicious developers. No single enforcement mechanism is perfect. But when combined—mandatory verification, API controls, AI scanning, human review, and sanctions against bad actors—the system becomes reasonably robust.
The declining rejection numbers don't mean security is weakening. They suggest the system is becoming more predictive. Instead of catching malicious apps after submission, Google's stopping them before they're submitted.
That's a fundamental shift. It's the difference between jail sentences and crime prevention.

FAQ
What counts as a policy violation for app rejection from the Play Store?
App rejections can happen for malware, privacy violations, misleading functionality, policy breaches, and security issues. Google lists over 100 specific policy violations including apps that impersonate others, handle payment insecurely, violate user privacy, or contain exploits. The specific policy depends on the app category, but all rejections receive detailed explanations from Google.
How does Google's Gen AI integration improve the app review process?
Gen AI models analyze app code and behavior patterns to identify complex malicious intent that traditional rule-based systems miss. The AI handles pattern matching and risk scoring, while human reviewers focus on high-risk apps and edge cases requiring judgment. This combination speeds up reviews from days to hours while improving accuracy for detecting sophisticated malware.
Can developers appeal a Play Store rejection?
Yes, developers can appeal rejections within 30 days. The appeal process is available through the Play Console and requires explaining how the app addresses the violation. Google reviews appeals and either overturns the decision or provides additional guidance. However, repeat violations or appeals that don't address the underlying issue may lead to permanent account bans.
What's the difference between an app being rejected and having permissions blocked?
Rejected apps are removed from the Play Store entirely. Apps with blocked permissions can still exist and be installed, but they're prevented from accessing sensitive data like camera, location, or contacts. This granular approach protects user privacy without completely removing apps, giving developers time to comply with updated policies.
How does sideloading affect Android security compared to using the Play Store?
Sideloaded apps bypass Google's 10,000+ safety checks and Play Protect scanning. While Play Protect can warn you about malicious sideloaded apps after the fact, it can't prevent installation like the Play Store does. Sideloading should only be done with apps from sources you absolutely trust.
What does the Data Safety section show and why does it matter?
The Data Safety section discloses what data an app collects (location, contacts, payment info, etc.), how it uses that data, and whether it shares data with third parties. This information is now required for all apps and helps you make informed download decisions. If an app's data collection seems excessive for its function, that's a red flag.
How often does Google scan apps for malware?
Google's Play Protect scans 350 billion apps daily, checking for new threats and monitoring installed apps. This continuous scanning means threats are detected and users warned relatively quickly. However, entirely new malware variants may evade detection briefly before patterns are recognized and added to threat databases.
What happens to developers with permanently banned accounts?
Permanently banned developers are blacklisted from the Play Store ecosystem. Google cross-references payment methods, phone numbers, and device fingerprints to prevent banned individuals from creating new accounts. Repeat violations across multiple accounts guarantee escalating consequences including permanent bans that cover the entire person, not just individual accounts.

Key Takeaways for Android Security in 2025
The numbers Google released in 2025 tell a story of evolving enforcement. Fewer rejections don't mean fewer threats—they mean threats are being caught earlier, at the prevention stage rather than the rejection stage.
For developers, the message is clear: follow the rules or face consequences. For users, the message is equally clear: stick to the official Play Store, keep your device updated, and be cautious about permissions.
The 1.75 million rejections, 80,000 account bans, 255,000 permission blocks, and 27 million Play Protect detections represent a massive security operation. Whether you work in app development, security research, or just use Android devices, these numbers matter. They tell you how seriously Google takes the security of its ecosystem.
The real question going forward isn't whether the numbers are high or low—it's whether Google's preventive approach is actually preventing the threats that matter. The evidence suggests it is. But eternal vigilance remains security's price.

Related Articles
- Google's AI Malware Detection on Play Store in 2025 [Guide]
- Google Play's AI Defenses Block 1.75M Bad Apps in 2025 [Analysis]
- Keenadu Android Backdoor: Firmware Malware Threat [2025]
- EU Parliament's AI Ban: Why Europe Is Restricting AI on Government Devices [2025]
- EU Parliament Bans AI on Government Devices: Security Concerns [2025]
- Apple's E2EE RCS Messages: Encrypted iPhone-Android Texting [2025]
![Google Rejected 1.75M Android Apps and Banned 80K Developers in 2025 [Data]](https://tryrunable.com/blog/google-rejected-1-75m-android-apps-and-banned-80k-developers/image-1-1771598140913.jpg)



