Major Shipping Platform Exposed Customer Data, Passwords: What Happened [2025]
The shipping and logistics industry processes trillions of dollars in cargo every year. It's also become a prime target for hackers working alongside organized crime groups. Over the past year, security researchers have documented an alarming trend: coordinated cyberattacks on logistics companies designed to hijack shipments and redirect them into criminal distribution networks. A stolen shipment of electronics here, a diverted pallet of high-end cosmetics there. The scale is staggering, and the collusion between digital attackers and physical thieves is becoming increasingly sophisticated.
But while the industry has been on high alert about elaborate hacking campaigns, one relatively unknown U.S. shipping technology company had a different kind of problem: embarrassingly simple security failures that left its entire platform and customer data completely exposed to anyone on the internet.
The company is Bluspark Global, a New York-based firm whose shipping and supply chain platform, Bluvoyix, powers a significant portion of worldwide freight operations. We're talking about hundreds of major retailers, grocery chains, furniture manufacturers, and other Fortune 500-adjacent companies that rely on Bluvoyix to move and track products globally. Yet for months, security researcher Eaton Zveare found that Bluspark's systems contained five critical vulnerabilities that would have allowed any attacker to access customer data dating back to 2007, create unauthorized administrator accounts, and potentially hijack the entire shipping platform.
Here's what happened, why it matters, and what you need to know about the broader security crisis in logistics tech.
TL; DR
- Shipping platform vulnerability: Bluspark Global's Bluvoyix platform exposed plaintext passwords, unauthenticated APIs, and customer shipment records through basic security failures
- Scope of exposure: The vulnerabilities could have allowed attackers to access data for hundreds of major companies and decades of shipment records
- Detection challenges: Security researcher had to contact Tech Crunch and include the CEO's plaintext password in an email to get the company's attention
- Industry timing: The breach coincides with a documented rise in coordinated cargo theft campaigns targeting logistics companies
- Lessons learned: Even well-established companies providing critical infrastructure can have fundamental security oversights
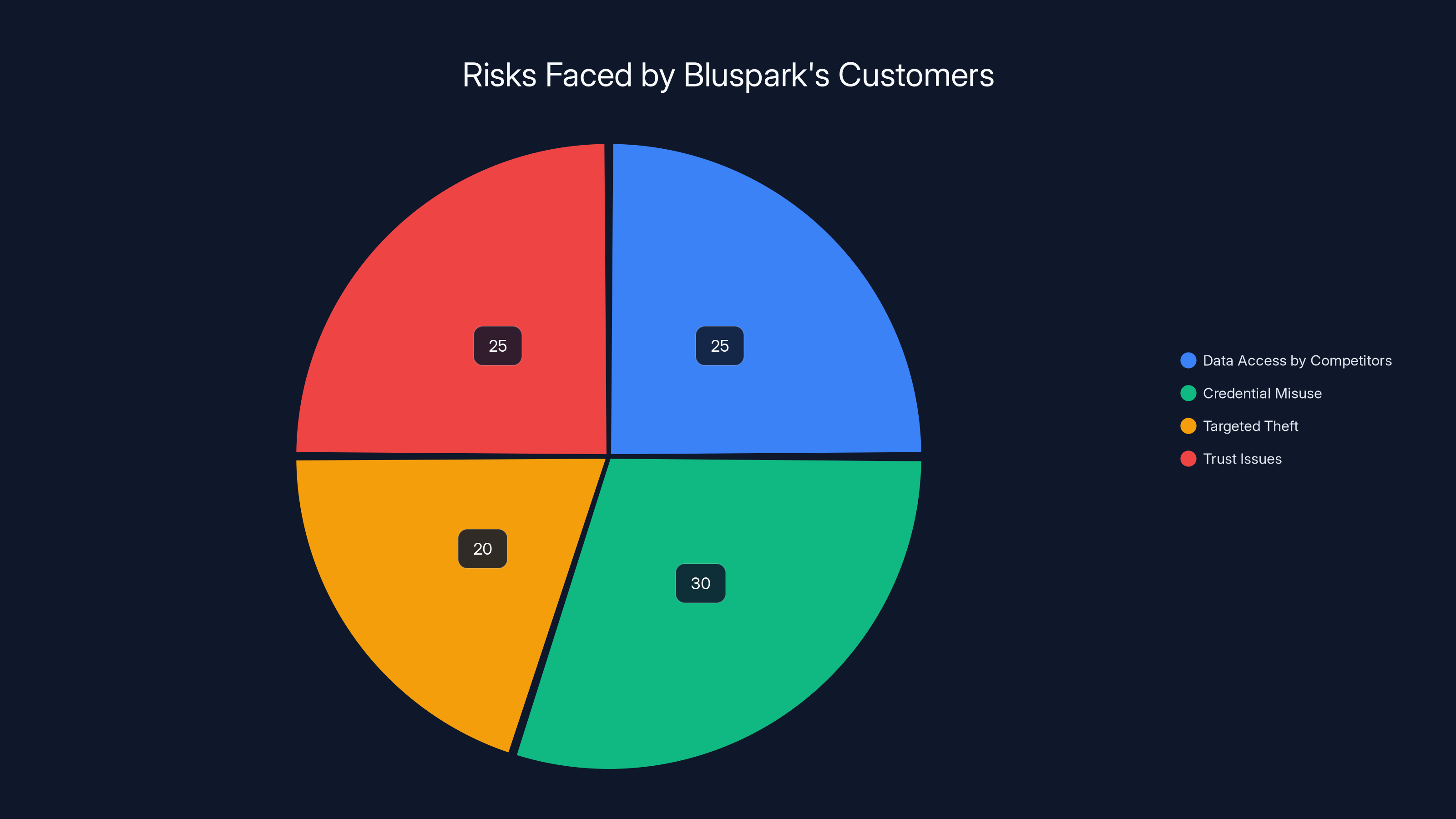
Estimated data shows that credential misuse poses the highest risk at 30%, followed by data access by competitors and trust issues, each at 25%.
The Discovery: How Simple APIs Exposed Everything
Security researcher Eaton Zveare didn't set out to find critical vulnerabilities in Bluspark's systems. He was simply doing research on a Bluspark customer's website when he noticed something in the page's source code. The customer had embedded a contact form that communicated with Bluspark's servers through an API.
APIs are the connectors between software systems. They're how your email client talks to Gmail's servers, how your weather app retrieves current conditions, or how a shopping cart on an e-commerce site processes your order. In this case, the contact form was designed to send customer inquiries through Bluspark's infrastructure to the customer's inbox.
But here's where the first problem emerged: the API code was embedded directly in the webpage itself. This meant that anyone viewing the page source—something every browser allows, every user can do—could see the API endpoint. More importantly, they could modify the code and send malicious requests through it.
Zveare took the next logical step. He pasted the API's web address directly into his browser.
What loaded was Bluspark's auto-generated API documentation page. This is a common practice in software development. Companies generate documentation that lists every command you can perform with an API—what parameters they accept, what data they return, and sometimes even provides a "test" feature so developers can try API calls directly from their browser.
This documentation page showed all the actions someone could perform: retrieve a list of users with access to the platform, create new user accounts, modify shipping records, and more. And crucially, it included a testing feature that would execute API commands.
Zveare tested whether the API actually required authentication. According to the documentation, it should have. But when he submitted a command to retrieve user account records, the API complied. It sent back a complete list of employee and customer account information, usernames, and passwords.
The passwords weren't encrypted or hashed. They were visible in plaintext. Including an account associated with the platform administrator.
The Cascade: How One Flaw Opened Every Door
Once Zveare had the list of API commands, he noticed something particularly dangerous. One command allowed the creation of new user accounts with administrator privileges. Since the API didn't actually require authentication, anyone could execute this command.
Zveare created a new administrator account and gained unrestricted access to Bluvoyix. With this access, he could view customer data going back nearly two decades—shipping records, manifests, tracking information, and the sensitive details about what products companies were moving through the global supply chain.
But the vulnerabilities didn't stop there. Even the access control system had a flaw. When users logged in, each API request was wrapped in a user-specific token meant to verify their permission to access that particular portal page. The token looked like it should be required.
It wasn't.
API requests went through perfectly fine without the token. This meant that even if attackers couldn't create an administrator account, they could still access data by simply stripping away or ignoring the token requirement. The authentication layer was cosmetic—it looked secure but did nothing.
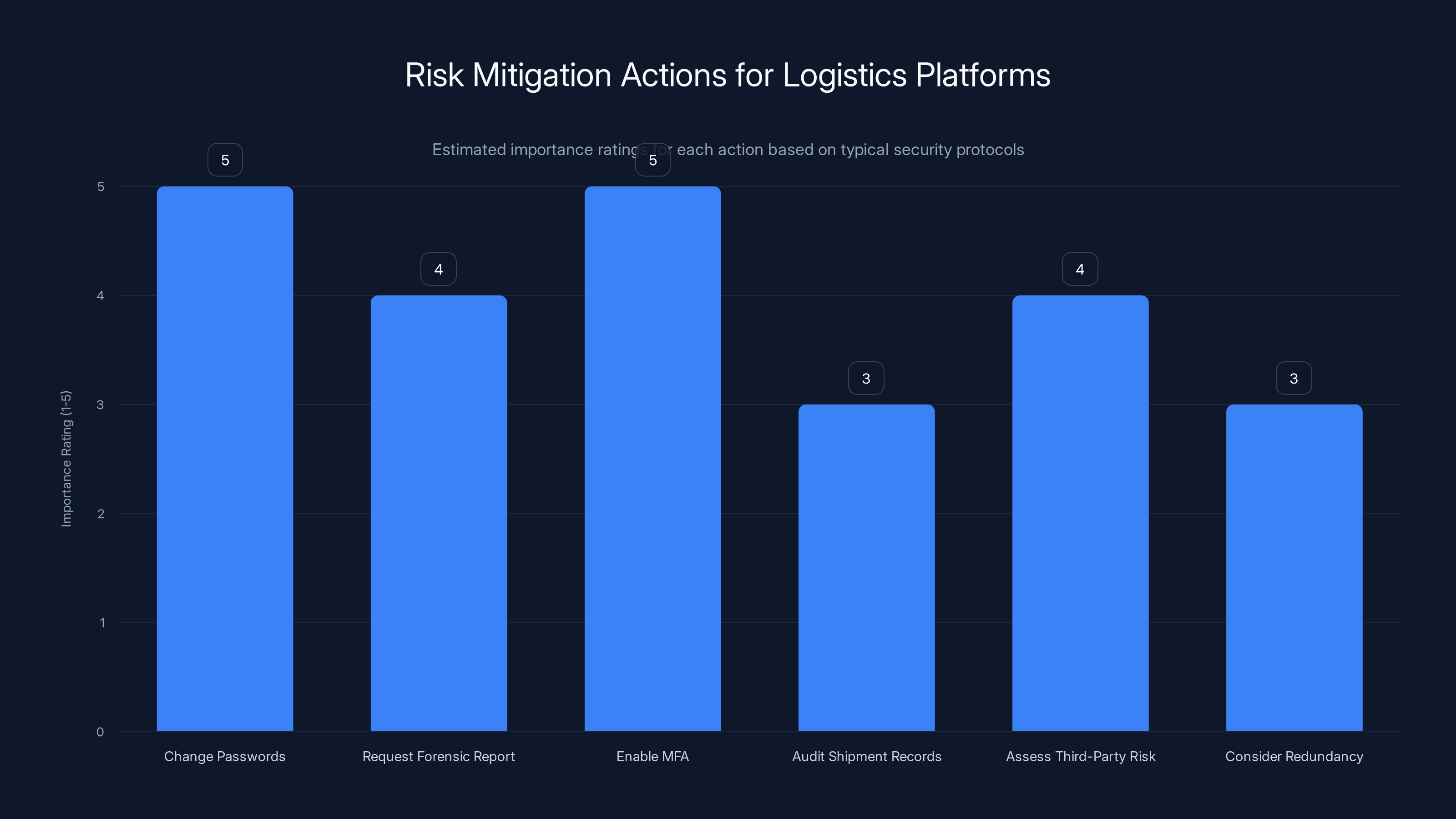
Changing passwords and enabling multi-factor authentication are critical steps, rated highest in importance, to mitigate risks in logistics platforms. (Estimated data)
The Five Vulnerabilities: A Breakdown
Zveare documented five distinct security flaws in Bluspark's platform:
1. Plaintext Password Storage
Passwords stored as plain readable text instead of encrypted hashes. Any attacker with database access could immediately log in as any user. This is a fundamental failure that no organization handling customer data should experience.
2. Unauthenticated API Access
The API returned sensitive information without verifying the user had legitimate access. Authentication checks existed in the code but didn't actually prevent unauthorized access.
3. Exposed API Endpoint in Frontend Code
The API address was visible to anyone viewing the page source. While not a vulnerability on its own, it removes the "security through obscurity" barrier and makes finding the API endpoint trivial.
4. Unrestricted Administrator Account Creation
The API allowed creating new user accounts with administrative privileges without any verification that the requester should have this capability.
5. Bypassable Authentication Tokens
User access tokens could be ignored or removed from requests while still receiving data. The token system gave the appearance of security without providing actual protection.
These aren't sophisticated, zero-day vulnerabilities that require years of research to discover. These are fundamental, textbook security failures taught in basic information security courses.
The Notification Problem: A Researcher's Frustration
Zveare acted responsibly. As a security researcher, he understood his obligation to notify the company before publicly disclosing the vulnerabilities. He reached out to the Maritime Hacking Village, a nonprofit organization focused on securing maritime and logistics infrastructure.
The Maritime Hacking Village tried to help. They attempted to notify Bluspark of the security flaws.
Weeks passed. No response.
Zveare sent multiple emails. Still silence. He tried voicemails. LinkedIn messages. Nothing.
Here's the critical problem: Bluspark had no obvious, functional security contact method. There was no security.txt file, no dedicated security email address, no clear way for researchers to report vulnerabilities. This forced Zveare into a position where he either had to stop trying or escalate.
He escalated. He contacted Tech Crunch, hoping that media pressure might get the company's attention.
Tech Crunch sent emails to Bluspark CEO Ken O'Brien and senior leadership. Crickets. They emailed a Bluspark customer, a major U.S. publicly traded retail company. Also no response.
It wasn't until Tech Crunch included a partial copy of O'Brien's plaintext password in a third email that someone finally responded. Within hours, a law firm representing Bluspark got back to them.

The Shipping Industry's Security Crisis Context
Bluspark's security failures didn't exist in isolation. They occurred against the backdrop of a documented, escalating crisis in logistics and supply chain security.
Over the past year, security researchers and law enforcement agencies have documented increasingly sophisticated attacks on shipping and logistics companies. These attacks aren't random or opportunistic. They're coordinated campaigns where digital attackers work directly with organized crime networks to target specific shipments.
The pattern is clear: hackers compromise logistics companies' systems, identify high-value shipments traveling to specific locations, and coordinate with theft rings to intercept and steal them. Luxury goods, electronics, pharmaceuticals, and other high-value cargo have been targeted.
In one notable case, a shipment of over 100,000 stolen vapes was recovered after being hijacked through a logistics company's compromised systems. In another, federal authorities documented the theft of premium lobster through supply chain manipulation. These aren't single-actor crimes. They're organized operations.
Against this threat landscape, a major platform used by hundreds of companies to coordinate shipping had five critical vulnerabilities exposed for months. The potential impact isn't just financial. If attackers had access to Bluvoyix, they could identify high-value shipments, monitor routing, and coordinate theft operations at scale.
The incident demonstrates how vulnerabilities in infrastructure layer technologies can create systemic risk across entire industries.

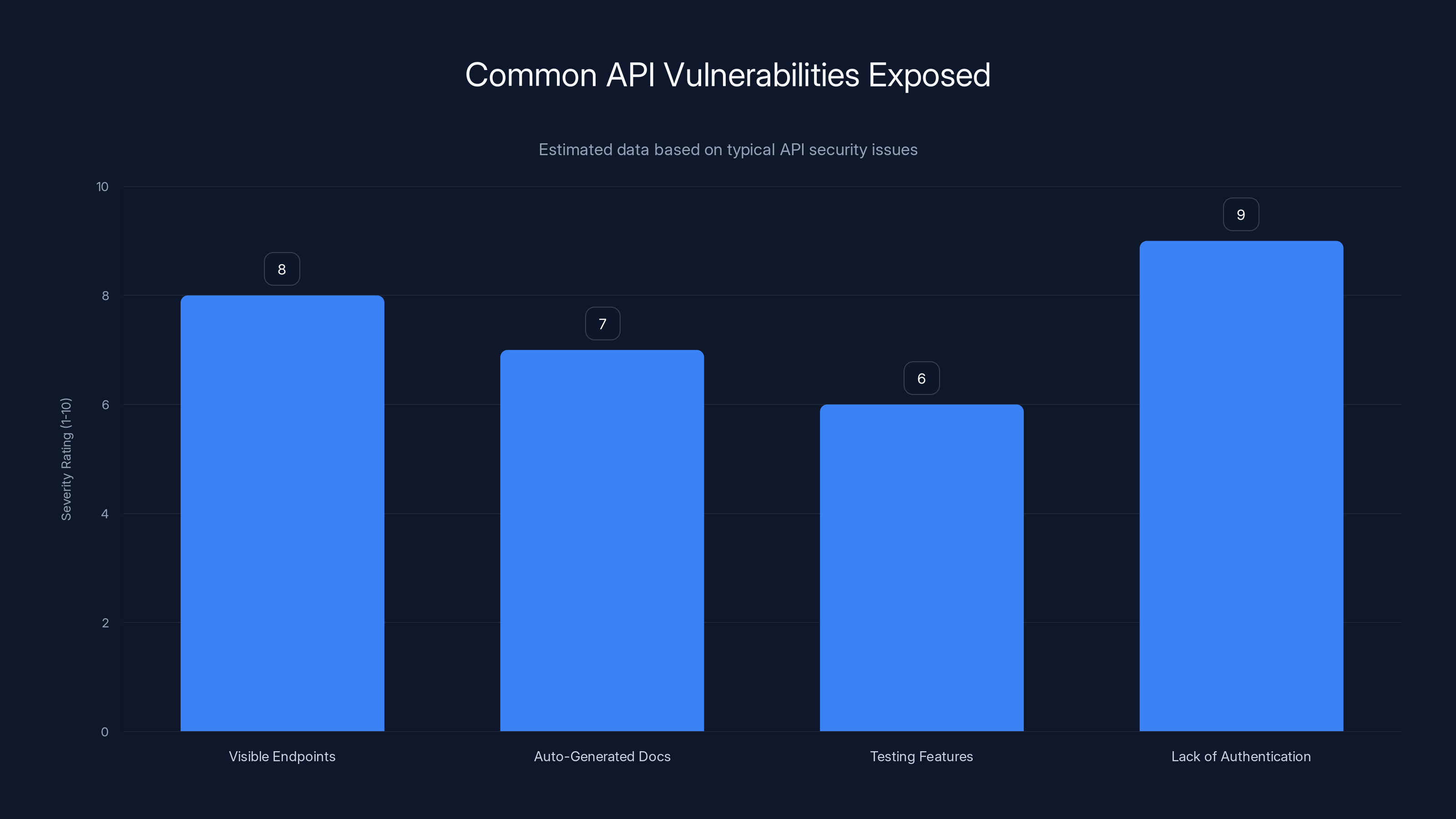
Estimated data shows that visible endpoints and lack of authentication are major API vulnerabilities, with severity ratings of 8 and 9 respectively.
What Was Actually Exposed: The Data Scope
Under the hood, what exactly was vulnerable? Zveare's access to the platform revealed:
Shipment Records and Tracking Data
Complete records of products being transported, including descriptions, quantities, values, origin points, and destinations. This information alone is valuable to organized crime. Knowing what products are being shipped where enables targeted theft.
Customer Information
Details about companies using Bluspark, including their business relationships, procurement patterns, and supply chain structure. For competitors, this is competitive intelligence. For criminals, it's targeting information.
Employee Credentials
Usernames and plaintext passwords for employees of companies using the platform. These credentials could be used to access customers' own systems, create a foothold for further attacks, or sold on the dark web.
Administrator Access
The ability to create new administrative accounts meant that attackers could maintain persistent access. They could cover their tracks, create backup accounts, and essentially own the platform long-term.
Historical Data
Bluspark retained shipping records going back to 2007. Attackers could analyze years of patterns, identify the most profitable routes and customers, and plan long-term operations.
The temporal aspect is crucial. If this vulnerability had been exploited, the exposure wouldn't have been just what was on the platform today. It would have been nearly two decades of supply chain intelligence.
Bluspark's Response: Patching and Explanations
Once Bluspark's leadership finally engaged with the issue, the company moved relatively quickly. Within days, they patched all five vulnerabilities.
They implemented proper authentication checks, encrypted password storage, disabled the unrestricted administrator account creation function, required valid authentication tokens, and removed the API endpoint from the frontend code.
In their statement to Tech Crunch, Bluspark acknowledged the security issues and confirmed they were resolved. However, the company didn't provide extensive details about how long the vulnerabilities existed, whether they detected any unauthorized access, or what compensatory measures they were taking for affected customers.
This lack of transparency is common but concerning. When vulnerabilities of this severity are discovered, organizations should conduct forensic investigations to determine if attackers accessed the system, what data was viewed, and whether any unauthorized changes were made.

The Incident Response Failure: Why It Took So Long
What's remarkable about this situation is how long it took for responsible disclosure to work. The standard responsible disclosure timeline is 90 days from initial notification to public disclosure. Zveare and the Maritime Hacking Village gave Bluspark much longer.
But the real failure is that Bluspark had no process to receive security reports. Most major technology companies maintain a security.txt file at a standard location (.well-known/security.txt) that lists how to report vulnerabilities. This is becoming an industry best practice.
Bluspark didn't have one.
With no official channel, Zveare had to contact the company through general corporate channels, where the report likely got lost in email spam, support tickets, or ignored by staff who didn't understand the severity.
This is a systemic problem in the shipping and logistics industry. Many companies in the sector are decades-old, built on legacy systems, and haven't modernized their information security practices. They don't have security researchers on staff, don't participate in bug bounty programs, and don't maintain public vulnerability reporting processes.
The result is that when researchers find security issues, they struggle to get management attention until the problem becomes public.

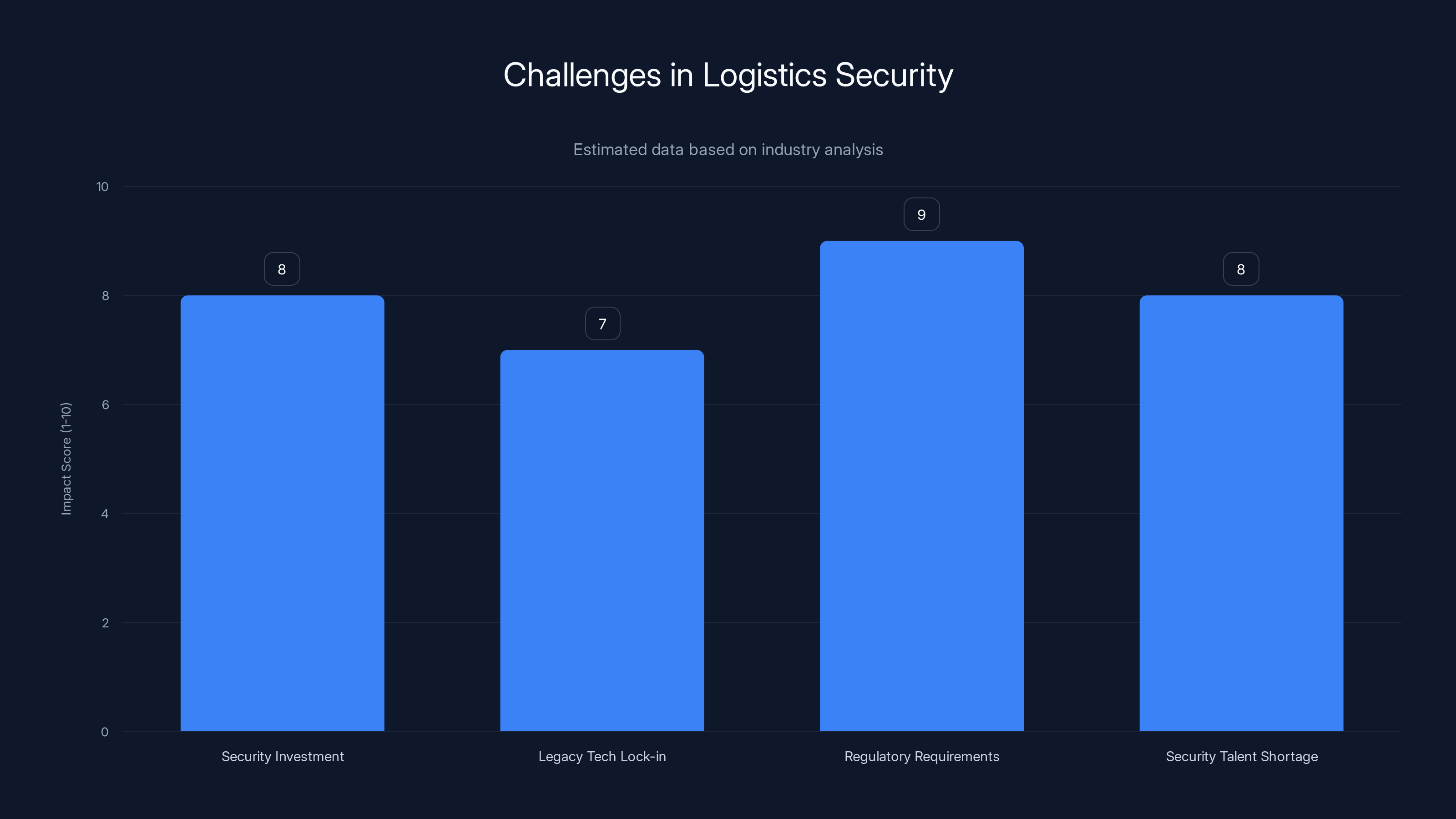
The logistics industry faces significant challenges in security, with regulatory requirements and security talent shortage being the most critical issues. Estimated data highlights the severity of these challenges.
Root Cause Analysis: How Did This Happen?
Several factors likely contributed to these vulnerabilities existing for so long:
Legacy Development Practices
Bluspark's platform may have been built over many years with security practices from an earlier era. Plaintext password storage and unauthenticated APIs might be remnants from the 2000s or early 2010s when these practices were more common (though still wrong).
Lack of Security Reviews
If the code had undergone a basic security review, these vulnerabilities would have been caught immediately. The absence of regular security assessments in the development process is a critical failure.
No Security Culture
Organizations with mature security cultures conduct threat modeling, do penetration testing, and make security a responsibility of every developer. Bluspark appears to lack this foundation.
Growth Without Security Investment
As the company expanded and took on hundreds of customers, security investment didn't keep pace with growth. The platform's importance increased, but its defenses didn't.
Outdated Technology Assumptions
The developers may have assumed that because Bluspark is not a household name, attackers wouldn't target it. This "security through obscurity" thinking ignores that attackers specifically target lesser-known infrastructure that handles valuable cargo.

Industry Implications: The Broader Crisis
Bluspark's vulnerabilities highlight a troubling reality: critical infrastructure in the shipping and logistics sector is often less secure than consumer-facing applications. A company that handles billions of dollars in cargo moves has fewer security resources than a typical SaaS startup.
This creates a dangerous risk asymmetry. Attackers are increasingly aware of this gap. They're investing in exploiting logistics companies precisely because security is weak and payoff is enormous.
The incident demonstrates several systemic issues:
1. Security Investment Gap
Logistics companies operate on thin margins. They'd rather invest in faster delivery than better security. Until there's regulatory pressure or industry liability, this calculus is unlikely to change.
2. Legacy Technology Lock-in
Many logistics platforms were built decades ago on technology stacks that have been patched and updated but never fundamentally redesigned. This creates a situation where fundamental security improvements are nearly impossible without rewriting core systems.
3. Lack of Regulatory Requirements
Unlike healthcare (HIPAA) or finance (SOX), shipping logistics has minimal security regulation. There's no requirement for security audits, penetration testing, or even basic vulnerability disclosure processes.
4. Shortage of Security Talent
Logistics companies struggle to hire and retain security professionals. A talented security engineer can earn 2-3x more in tech than in logistics, creating a talent drain.

Comparison to Other Recent Logistics Breaches
Bluspark isn't alone. The past two years have seen multiple security incidents affecting logistics infrastructure:
Port Authority Systems: Several port authorities have experienced cyberattacks that disrupted operations and exposed cargo manifests.
Customs Brokers: Companies that interface between importers and government customs have been breached, exposing detailed shipment data.
International Freight Forwarders: Smaller companies coordinating global shipments have faced ransomware attacks that encrypted booking systems.
The common thread: these aren't sophisticated, targeted attacks by advanced nation-state threat actors. They're often basic exploitation of known vulnerabilities by criminal organizations seeking financial gain.
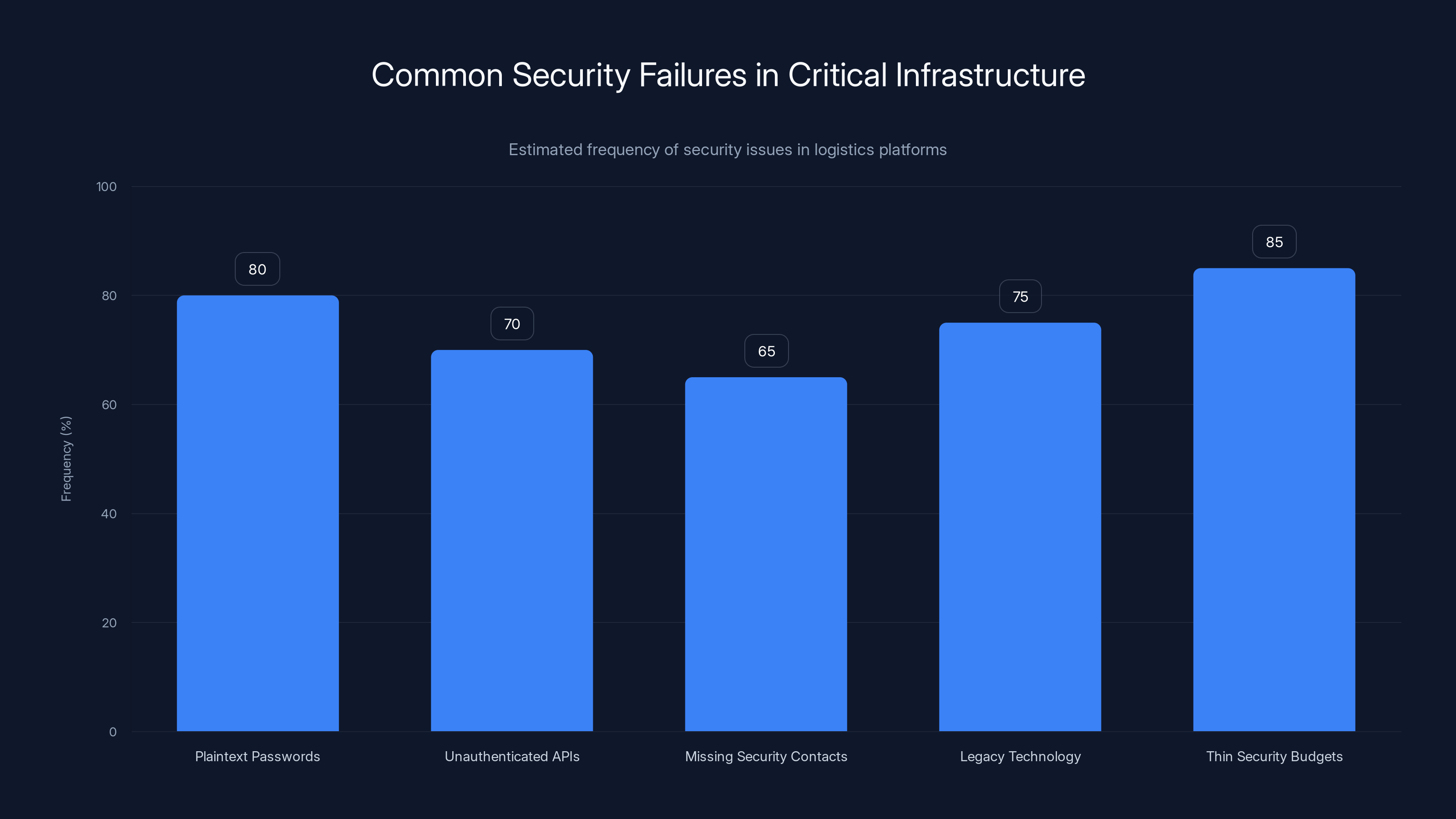
Estimated data shows that thin security budgets and plaintext passwords are the most common security failures in logistics platforms, highlighting a critical need for improved security practices.
What Customers Should Do: Risk Mitigation
If your company uses Bluspark or similar logistics platforms, this incident should prompt immediate action:
1. Change Passwords Immediately
Any password used on Bluspark should be changed. If your credentials were stored in plaintext, assume they're compromised. Change passwords on any other accounts using the same or similar passwords.
2. Request a Forensic Report
Demand that Bluspark provide forensic evidence of their investigation. Specifically: when was the system compromised, what data was accessed, were any changes made to shipment records, were unauthorized accounts created?
3. Enable Multi-Factor Authentication
When Bluspark reactivated services, did they implement multi-factor authentication? If not, insist on it. MFA would have prevented unauthorized access even with plaintext passwords.
4. Audit Shipment Records
Review your shipment history for any suspicious changes. If attackers had access to the platform, they could have modified shipping addresses or tracking data.
5. Assess Third-Party Risk
Understand what other vendors have similar access to your supply chain. One compromised platform is bad. Multiple single points of failure in your shipping infrastructure is worse.
6. Consider Redundancy
Evaluate whether you should diversify your logistics platform usage. Relying entirely on Bluspark means its security failures directly impact your operations.
The Role of Security Research: Getting Attention
One of the uncomfortable truths about cybersecurity is that many vulnerabilities only get fixed when someone is annoying enough about them.
Zveare did everything right. He found vulnerabilities, tried to report them responsibly, and only went public after months of being ignored. Yet it still took including the CEO's plaintext password in an email to get management attention.
This highlights why responsible disclosure doesn't work as a system when companies don't have proper incident response processes. The burden falls entirely on the researcher to escalate and create pressure.
Better practices would include:
- Security.txt files at well-known locations
- Dedicated security email addresses monitored 24/7
- SLAs for acknowledging vulnerability reports
- Bug bounty programs that incentivize responsible disclosure
- Public commitment to security research
Bluspark had none of these. They had to be shamed into action by the prospect of public reporting.
Technical Lessons: What Developers Should Learn
From a software development perspective, Bluspark's failures teach critical lessons:
Never Store Plaintext Passwords
Passwords must be hashed using strong algorithms like bcrypt or Argon 2. This is non-negotiable. There is no scenario where plaintext password storage is acceptable.
Require Authentication for All APIs
Every API endpoint must verify the user's identity and authorization before responding. This should be enforced at a framework level, not manually in each function.
Use Standard Authentication Protocols
Instead of custom token systems, use established standards like OAuth 2.0 or JWT. These have been thoroughly reviewed and have existing libraries that are battle-tested.
Test Authentication Bypass
During code review and testing, explicitly test whether removing authentication headers or tokens still allows access. This should be part of standard security testing.
Remove Sensitive Code from Frontend
API endpoints should never be embedded in client-side code. If the frontend needs to call an API, route it through your own backend proxy that can enforce authentication.
Document Security Practices
Develop clear documentation of how authentication, authorization, and data protection work in your system. This makes it easier to review, test, and maintain.
The Future: What Needs to Change
For the shipping industry to move away from these recurring security incidents, several changes need to happen:
Industry Standards
The shipping industry needs to adopt baseline security standards. These could be developed by industry associations or by government mandate. Every major logistics platform should meet minimum security requirements.
Insurance Requirements
Cyberinsurance providers should require security audits and penetration testing as conditions for coverage. This creates financial incentive for improvement.
Customer Pressure
Major shipping customers should demand security commitments from their vendors. When Fortune 500 companies make it a requirement for partnerships, vendors will invest in it.
Regulatory Oversight
Government should consider security regulation for critical infrastructure in supply chain management, similar to what exists in banking and healthcare.
Talent Development
Logistics companies should offer competitive salaries for security roles and invest in training. Building security culture starts with having security expertise.

FAQ
What exactly was exposed in the Bluspark breach?
Bluspark's Bluvoyix platform exposed plaintext passwords for employees and customers, shipment records dating back to 2007, user account credentials, and the ability to create unauthorized administrator accounts. The vulnerabilities allowed attackers to access data for hundreds of major companies without authentication.
How long did the vulnerabilities exist before being discovered?
The specific timeframe for how long the vulnerabilities were present isn't definitively known, but security researcher Eaton Zveare discovered them in October 2024. Bluspark had patched the flaws by the time Tech Crunch published the story several months later, but the company never disclosed exactly when the vulnerabilities were first introduced.
Why didn't Bluspark respond to initial security reports?
Bluspark had no formal security contact process or security.txt file. When researchers tried to report vulnerabilities through general corporate channels, their reports went unanswered. The company only responded when media attention was threatened and specific evidence of the breach was included in communications.
What are the risks for Bluspark's customers?
Customers face multiple risks: their shipment data may have been accessed and mapped by competitors or criminals, employee credentials could be used for further attacks, shipping routes and high-value cargo could be targeted for theft, and their trust in the platform's security is now questionable. Customers should change passwords, request forensic investigation details, and evaluate alternative shipping platforms.
Is plaintext password storage still common in 2024-2025?
While less common among modern cloud-native companies, plaintext password storage still exists in legacy systems and older software. However, it's virtually universal that plaintext passwords indicate a company with poor security practices. This storage method was considered unacceptable even 15 years ago.
How can companies prevent similar vulnerabilities?
Companies should implement security code review, regular penetration testing, API authentication frameworks enforced at the platform level, password hashing using strong algorithms like bcrypt or Argon 2, multi-factor authentication, and clear security incident reporting processes including a security.txt file and dedicated security contact email.
What is an unauthenticated API?
An unauthenticated API is an endpoint that doesn't verify the identity or authorization of the user making requests. It will respond to any request, from anyone, without checking if they should have access. This is a critical security failure as it treats all data as public, even if it's sensitive.
How does this relate to the broader cargo theft problem?
Bluspark's exposure during a period of documented coordinated cargo theft campaigns is particularly dangerous. With access to the platform, attackers could identify high-value shipments, learn routing information, and coordinate with theft rings to intercept cargo. The vulnerabilities created a potential bridge between digital access and physical theft operations.
What should I do if my company uses Bluspark?
Immediately change any passwords used on the platform. Request that Bluspark provide a detailed forensic report showing whether unauthorized access occurred. Enable multi-factor authentication if available. Audit your recent shipment records for suspicious changes. Consider diversifying your logistics platform usage to reduce dependency on a single vendor.
Has the shipping industry improved security since this incident?
The incident occurred in late 2024 and became public in early 2025, so widespread industry improvement hasn't had time to materialize. However, it has raised awareness among major customers about their vendors' security practices. Some shipping companies are now asking for security certifications and audit reports before signing contracts with logistics providers.
Conclusion: A Wake-Up Call for Critical Infrastructure
The Bluspark incident isn't remarkable for being a sophisticated cyberattack. It's remarkable for being the opposite: five trivial security failures that exposed an entire critical infrastructure platform used by hundreds of major companies.
Plaintext passwords. Unauthenticated APIs. Missing security contact processes. These aren't zero-day exploits. They're basic oversights that shouldn't exist in any company handling customer data.
Yet they did exist. And they went unfixed for months despite responsible attempts to report them. Only when media attention became inevitable did the company finally act.
This pattern repeats across the shipping and logistics industry. Critical infrastructure, thin security budgets, legacy technology, and minimal regulatory oversight combine to create recurring vulnerabilities.
The concerning part is that we know how to fix this. Better security practices are well-documented. The tools exist. What's missing is prioritization and accountability.
For companies operating in logistics and supply chain management, the Bluspark incident should serve as a clear signal: customers are increasingly aware that security failures in your platform directly affect their operations and competitive advantage. Major customers will demand better security practices. Insurance companies will require it. Eventually, regulation may mandate it.
The question isn't whether shipping platforms will improve their security. It's whether they'll do it proactively before the next incident, or reactively after the next breach becomes public. Based on history, the answer is probably both. Some will learn and invest in security. Others will wait until they're forced.
For everyone else—if you rely on logistics platforms for your supply chain, treat vendor security the same way you treat vendor reliability. Ask the hard questions. Demand evidence. Don't assume that because a company handles billions in cargo, they've secured their systems properly. This incident proves they often haven't.
The digital and physical supply chains are merging. As they do, security failures in one instantly become vulnerabilities in the other. Protecting your supply chain means demanding that every platform in it treats security as a fundamental requirement, not an afterthought.
Key Takeaways
- Bluspark Global's shipping platform exposed plaintext passwords, customer data, and decades of shipment records through five basic security vulnerabilities
- An unauthenticated API allowed attackers to retrieve sensitive data and create unauthorized administrator accounts without any credentials
- The company had no security contact process, forcing the researcher to escalate through media and include the CEO's password in an email to get attention
- The breach occurred during a documented rise in coordinated cargo theft campaigns, making the exposure particularly dangerous for supply chain infrastructure
- The incident reveals systemic security weaknesses in the logistics industry driven by legacy technology, thin budgets, and lack of regulatory oversight
![Major Shipping Platform Exposed Customer Data, Passwords: What Happened [2025]](https://tryrunable.com/blog/major-shipping-platform-exposed-customer-data-passwords-what/image-1-1768406910968.jpg)



