How to Protect Your iPhone and Android Device From Spyware [2025]
Your smartphone knows everything about you. Where you go, who you talk to, what you search for at 2 AM, which apps drain your attention, every password you've typed, every photo you've taken. It's the most intimate device most people own.
Now imagine someone else having access to all of that. Not a hacker who stole your password. Someone with software that sees and hears everything in real-time, even through encrypted messaging apps like WhatsApp and Signal. That's what spyware does.
For years, sophisticated spyware like Pegasus operated in the shadows, targeting only the most high-profile victims: journalists, dissidents, politicians, and business leaders. But things are changing. In recent months, researchers have documented spyware like Predator being deployed through increasingly clever methods. The US Cybersecurity and Infrastructure Security Agency (CISA) issued warnings that adversaries are actively leveraging commercial spyware against mobile users. Apple and Google have scrambled to patch zero-day vulnerabilities that experts believe were used to plant malware on selected devices.
Here's what makes this crisis different: spyware doesn't require you to click a suspicious link or download a weird app anymore. Modern spyware can infect your phone through a zero-click attack, meaning your device becomes compromised without any action from you. You could be entirely vigilant and still get hit.
The good news? You're not helpless. Understanding how spyware works, recognizing the signs of infection, and implementing the right security measures can significantly reduce your risk. This guide walks you through everything you need to know to protect yourself.
TL; DR
- Spyware is evolving: Modern attacks no longer require user interaction (zero-click exploits)
- Detection is hard but possible: Watch for overheating, sudden slowdowns, camera/mic activity, and official threat notifications from Apple or Google
- Prevention is your best defense: Keep your OS updated, avoid suspicious links and apps, and use security features like Apple's Lockdown Mode
- High-risk individuals need more: Journalists, activists, and business leaders should consider additional security measures and monitoring
- Your data is weaponizable: Compromised devices can expose personal information that gets used against you offline

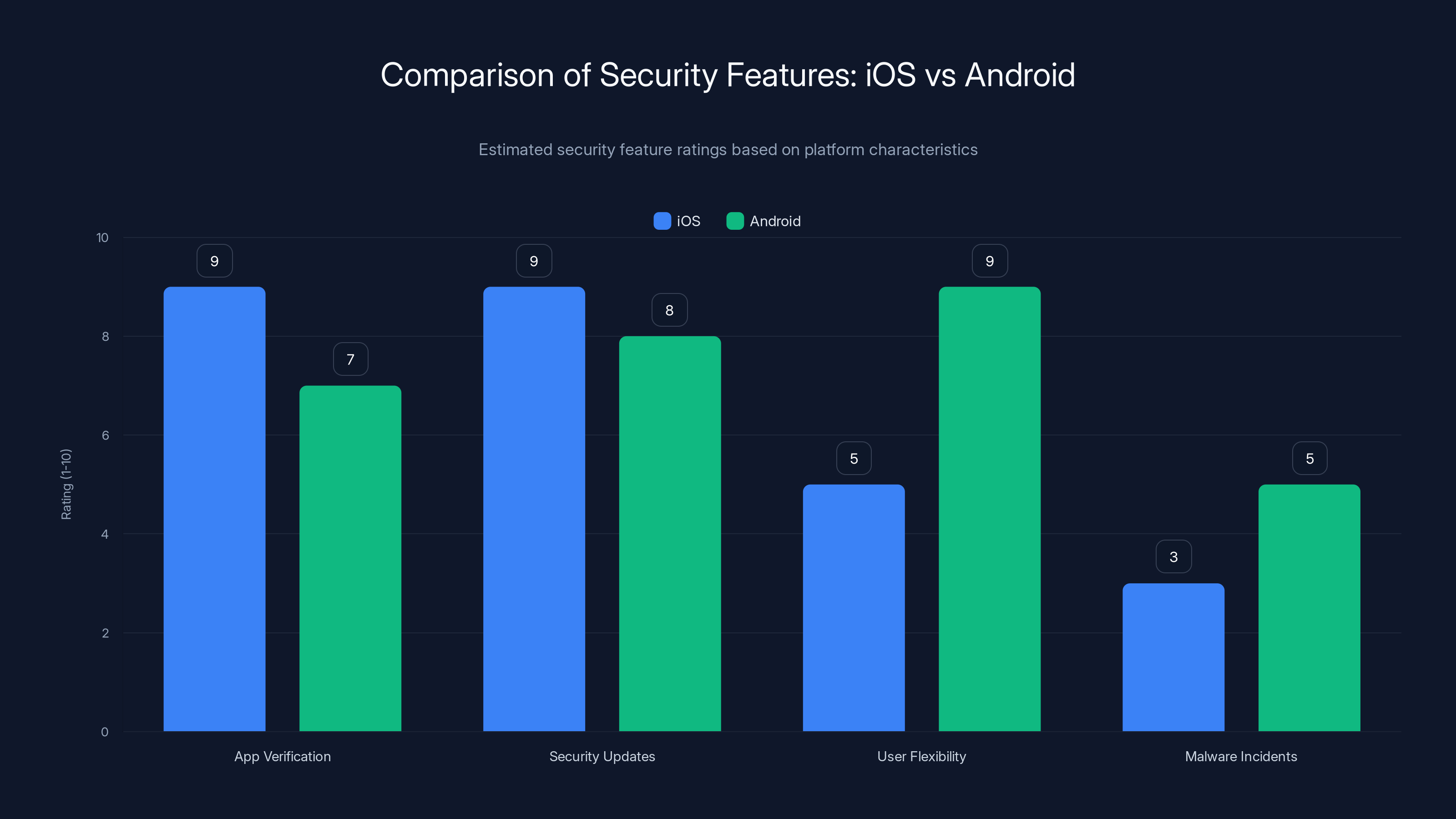
iOS scores higher in app verification and security updates due to its closed ecosystem, while Android offers more user flexibility. Estimated data.
Understanding the Spyware Landscape
Spyware isn't new, but the sophistication and distribution methods have evolved dramatically. To protect yourself, you need to understand what you're up against.
What Spyware Actually Does
Sophisticated spyware operates at the system level, giving attackers complete visibility into your device. They can read your messages, including those in encrypted apps. They can watch your banking logins, monitor your notifications before you even see them, and access any app on your phone. Some variants record audio through your microphone without you knowing, take screenshots of your screen, and track your location in real-time.
The dangerous part isn't just the technical capability. It's the asymmetry. You have no idea you're being watched. The attacker sees everything. There's no notification, no indication, no way to know unless you undergo forensic analysis of your device.
This creates a chilling effect. Thai activist Niraphorn Onnkhaow, targeted 14 times by Pegasus spyware between 2020 and 2021 during Thailand's pro-democracy protests, eventually stepped back from activism entirely. She knew her private communications and location data could be weaponized against her. The spyware doesn't just steal information—it changes behavior. It silences people.
The Different Types of Spyware Attacks
Spyware infects devices through multiple vectors. Understanding these attack methods helps you recognize and avoid them.
Zero-click attacks are the nightmare scenario. Your phone becomes infected without you doing anything wrong. You don't need to click a link, download an app, or interact with the malware in any way. An exploit chain—a sequence of vulnerabilities strung together—silently deploys the spyware. In December, Google researchers detailed how an exploit chain was used to install Predator spyware this way. Zero-click attacks are extremely difficult for average users to prevent because they don't require user action.
Link-based attacks remain common because they work. Attackers send you a text message, email, or social media message with a malicious link. Click it, and malware downloads onto your device. These are easier to prevent if you're careful, but they're also easy to fall for if the link looks legitimate.
Malicious apps are another entry point. An app looks legitimate, has reviews, maybe even copies the real app's branding. But it's actually malware. Many users don't realize the risk because apps can be hidden or branded to look official.
Image-based attacks hide malware inside image files. Someone sends you what appears to be a normal photo, but opening or downloading it activates the exploit.
Browser vulnerabilities are a frequently overlooked attack surface. Your browser can be exploited without you visiting a suspicious site. Sometimes it happens while visiting legitimate websites that have been compromised.
Browser extensions represent an emerging threat. Research has shown millions of users installing seemingly harmless browser extensions that actually become surveillance devices. What looks like a productivity tool or security extension turns into a backdoor.
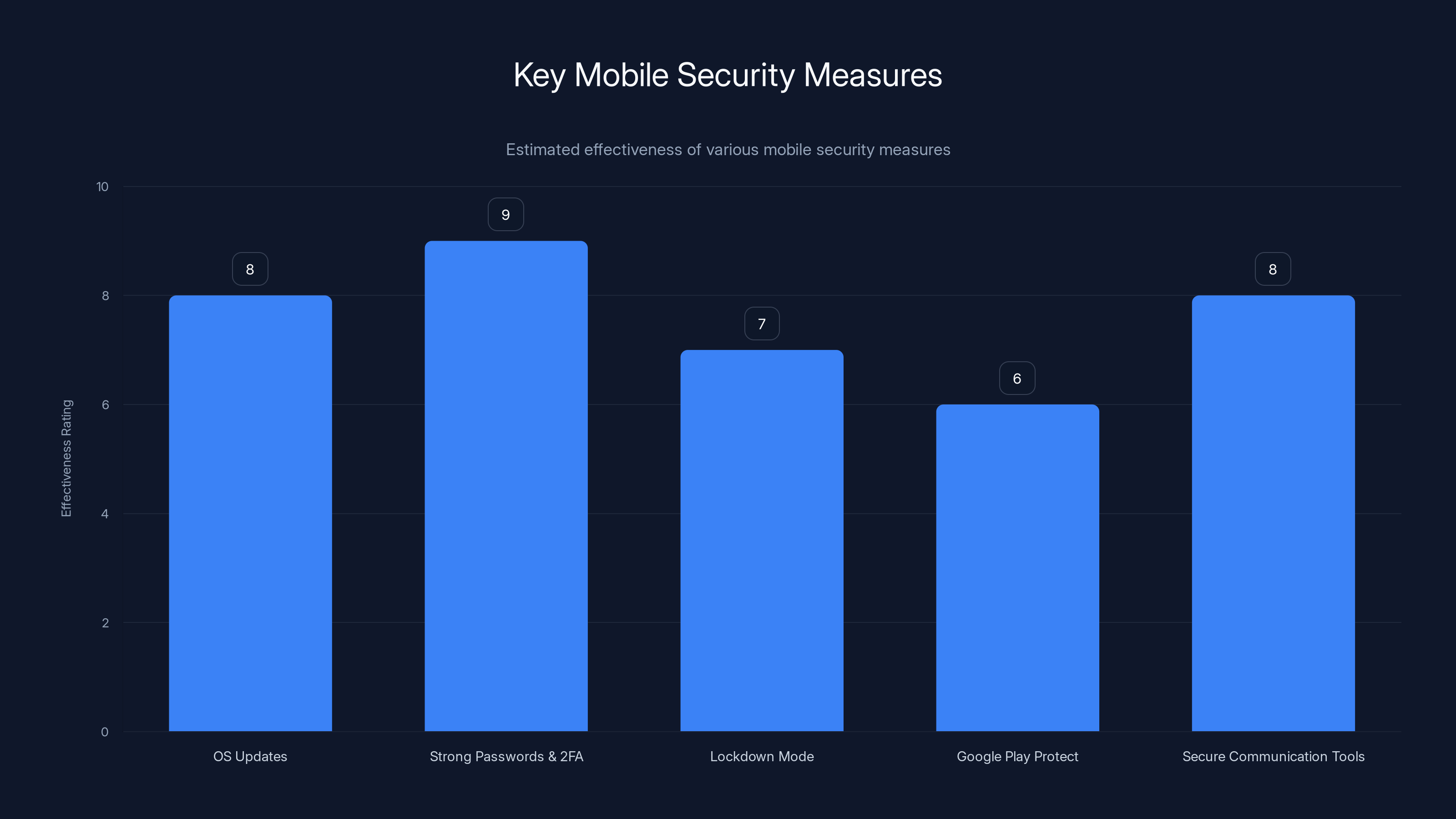
Estimated data shows that basic security practices like OS updates and strong passwords with 2FA are highly effective, while advanced measures like Lockdown Mode are crucial for high-risk individuals.
Who Gets Targeted and Why
Understanding the targeting patterns helps you assess your personal risk level.
High-Risk Groups
Historically, spyware has targeted specific groups: human rights activists, investigative journalists, political dissidents, and government officials in authoritarian regimes. These targets make sense from an attacker's perspective—they pose a threat to someone's power.
But the landscape is broadening. Rebecca White, a researcher at Amnesty International focusing on targeted surveillance, explains that while governments claim spyware targets only criminals and terrorists for national security, the reality is different. "Human rights activists, journalists, and many others across the world have been unlawfully targeted with spyware," she notes. "In this way, spyware can be used as a tool of repression—to silence people speaking truth to power."
Data stolen from a compromised phone gets weaponized. Leaked private communications can destroy careers or relationships. Location history reveals safe houses or private meetings. Contact lists identify colleagues and sources. For activists and journalists, spyware isn't just about surveillance—it's about silencing dissent.
Expanding Threat Surface
A newer trend concerns security researchers: spyware is moving beyond activism and politics into the corporate world. Attackers are targeting government officials, financial IT workers, and business leaders. The motivation isn't always political—it's often financial or competitive.
Cole, a security researcher, observed that spyware is hitting "a wide range of society." Increasingly, it's used beyond intelligence gathering to steal credentials for enterprise access. A compromised executive's email account can provide access to an entire company's systems.
Your Personal Risk Assessment
Most people aren't targeted by sophisticated spyware. That's not complacency talking—it's statistics. Sophisticated spyware campaigns are expensive and typically reserved for high-value targets. But that doesn't mean you're safe.
Your risk depends on several factors: Do you work in journalism, activism, or government? Are you involved in a sensitive business sector? Have you been threatened online or received suspicious communications? Do you live in a country with restricted freedoms?
Even if you're not a traditional "high-risk" target, the threat surface is expanding. Commercial spyware tools are becoming more affordable and accessible. Nation-states aren't the only threat anymore.
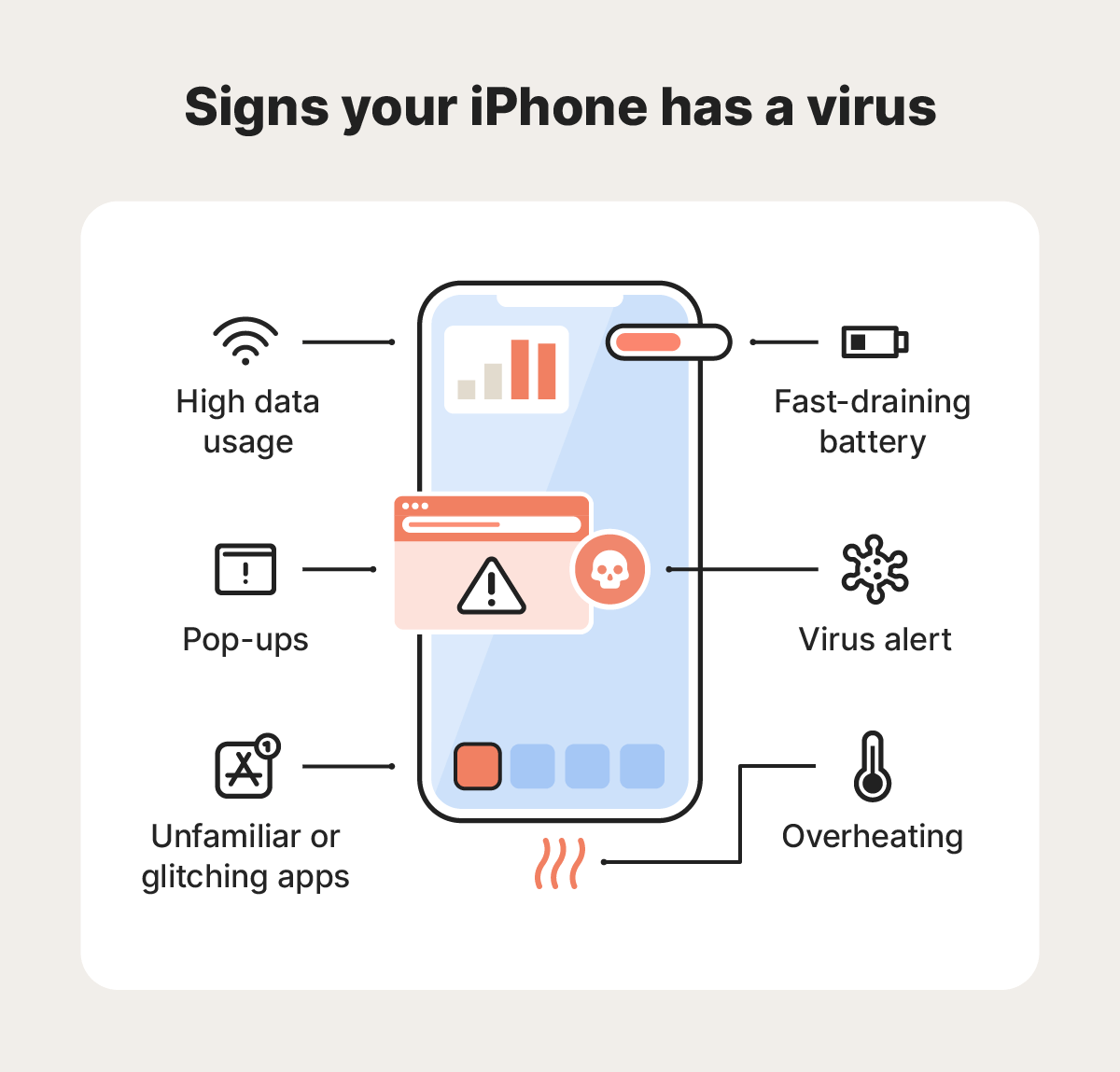
Recognizing the Signs of Spyware Infection
The most insidious aspect of sophisticated spyware is that it's designed to be invisible. But invisible doesn't mean undetectable if you know what to look for.
Performance Changes
Your smartphone is fast. Processors in modern phones are incredibly powerful. So when performance degrades noticeably, something's wrong.
If your iPhone or Android device starts overheating without heavy usage, that's a red flag. Spyware constantly processes data, attempting to capture information and transmit it. This generates heat and drains battery at abnormal rates. If you're not streaming video, gaming, or using intensive apps, but your phone feels warm, investigate.
Sudden slowdowns are another indicator. Apps take longer to launch. Scrolling feels sluggish. The interface becomes unresponsive. This doesn't necessarily mean spyware—it could be low storage, too many background apps, or a degraded battery. But it's a sign something needs investigation.
Battery drain that accelerates is worth examining. Your phone lasts two days normally, then suddenly it's dead by afternoon. Spyware constantly running in the background consumes significant battery. Again, this could have other causes, but it's worth considering.
Connectivity Anomalies
Spyware needs to transmit data, which means it generates unusual network activity. You might notice:
- Unexpected cellular or data usage spikes
- Increased latency or slower internet speeds
- Unusual Wi-Fi behavior or unexpected network disconnections
- Dramatic increases in data during periods when you're not actively using your phone
Check your data usage in Settings. On iOS, go to Settings > Cellular or Settings > Mobile Data. On Android, go to Settings > Network & Internet > Mobile Network > Mobile data usage. If your data usage is significantly higher than normal, and you haven't changed your usage patterns, investigate which apps are consuming data.
Hardware Activation
More obvious (but still rare with sophisticated spyware) is the camera or microphone activating when they shouldn't be.
On iPhone, iOS 14 and later show indicators when apps access your camera or microphone. A small dot appears in the top-right corner of the screen. Watch for this indicator appearing when you're not using apps that require camera or microphone access.
On Android, the indicator system varies by device and Android version, but many modern phones show notification dots or indicators in the status bar.
If your phone's light turns on when the camera or microphone is accessed, you might see it in dim lighting. This is a clear sign something is accessing your hardware.
Official Threat Notifications
The clearest indicator of spyware infection is an official threat notification from Apple, Google, or Meta (which owns WhatsApp).
Apple sends notifications to users it believes have been targeted by "mercenary spyware," which Apple defines as spyware operated by private companies on behalf of nation-states or state-supported actors. When you receive this notification, you should absolutely take it seriously. This isn't a phishing attempt or false alarm. Apple doesn't send these notifications lightly because false alarms could cause panic.
Google and Meta use similar threat notification systems. If you receive an official notification from any of these companies, assume your device may be compromised.
Behavioral Indicators
Sometimes the indicators are behavioral rather than technical.
If you've shared sensitive information only through encrypted channels, but that information appears publicly or reaches your adversary, your device may be compromised. If colleagues or friends have been targeted with spyware, there's increased likelihood you're a target too. If you've received threats online, someone may actually be following through on those threats with surveillance.
These behavioral indicators don't prove compromise, but they increase suspicion and should prompt deeper investigation.
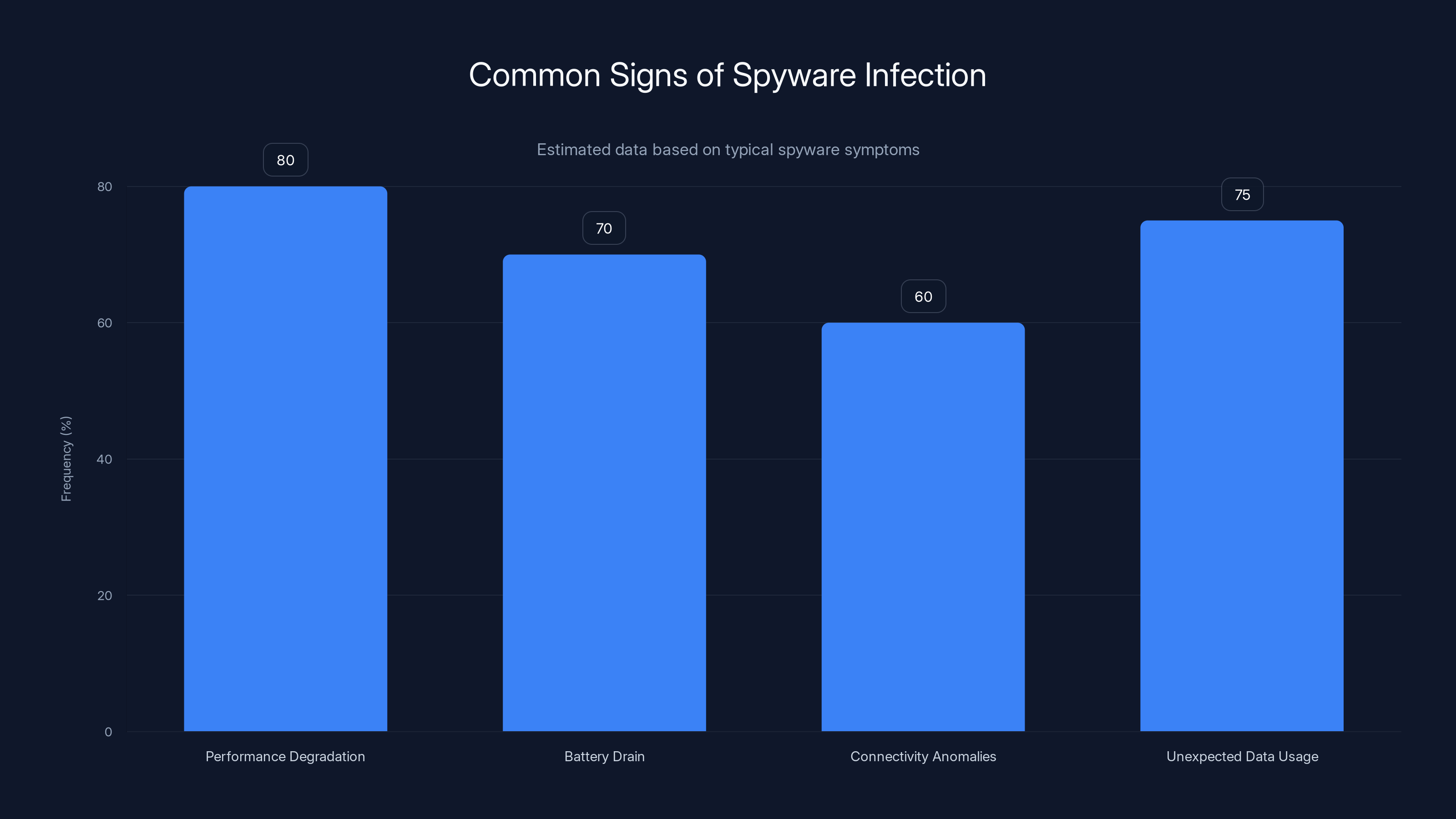
Performance degradation and unexpected data usage are common signs of spyware infection, with estimated frequencies of 80% and 75% respectively. Estimated data.
Apple's Lockdown Mode: Maximum Security at a Cost
Apple has weaponized the phrase "privacy is a human right" into actual product features. For users who believe they're at serious risk of targeted attacks, Lockdown Mode represents the most comprehensive protection available on iOS.
What Lockdown Mode Does
Lockdown Mode fundamentally changes how your iPhone operates. It's not a light security setting—it's a dramatic hardening of your device's security posture, with corresponding impacts on functionality.
When enabled, Lockdown Mode:
- Restricts most message attachments: Incoming attachments in messages are blocked unless they're from contacts. This prevents exploitation through malicious image files or document attachments
- Blocks incoming FaceTime calls from unknown contacts: Only people in your contacts can call you via FaceTime, preventing attacks through video calling exploits
- Limits web browser functionality: Complex web features that could be leveraged for exploitation are restricted
- Prevents wired connections to computers and accessories: If your phone is physically connected to a compromised computer, attackers can't exploit the connection
- Restricts Apple ID sign-in: You can't sign in to Apple ID on new devices or web browsers, preventing account takeover
- Disables some productivity features: SharePlay, notifications from senders outside your contacts, and certain accessibility features are restricted
The philosophy is clear: Apple is removing attack surface by removing functionality. Every feature that could be exploited is either restricted or eliminated.
How to Enable Lockdown Mode
Enabling Lockdown Mode on your iPhone is straightforward:
- Open Settings
- Navigate to Privacy & Security
- Scroll to the bottom and select Lockdown Mode
- Tap "Turn On Lockdown Mode"
- Confirm your choice
You'll need to verify your identity (Face ID, Touch ID, or passcode). Once enabled, Lockdown Mode stays active until you manually disable it.
The Trade-offs
Here's where security and usability collide. Lockdown Mode works, but it makes your iPhone less of a smartphone and more of a hardened security appliance.
You can't receive attachments in messages. Want to share a photo with a friend via iMessage? They can't send it—it will be blocked. Need to receive an important document? Blocked unless it's from a contact.
FaceTime becomes contactless only. Your boss calls to schedule a meeting? If they're not in your contacts, you miss the call.
Shared Playback features are disabled, meaning you can't watch videos together with friends over FaceTime. Web browsing becomes more restricted. Some accessibility features stop working.
For most people, these trade-offs are unacceptable for daily use. But for people who believe they're genuinely at risk of nation-state surveillance, the loss of functionality is a worthwhile price.
When to Use Lockdown Mode
Apple recommends Lockdown Mode for:
- Journalists and activists in high-risk regions
- People working with sensitive political information
- Business leaders whose companies are targets of espionage
- Anyone who has received an official threat notification
- Families of high-profile individuals
If you're in these categories and have the technical sophistication to deal with restricted functionality, Lockdown Mode should be your baseline security posture.
For everyone else, Lockdown Mode is probably overkill for daily use. But it's worth understanding it exists and enabling it temporarily if you believe you're under attack.

Android Security Features and Best Practices
Android users face a different security landscape. Android's open nature means greater flexibility and customization, but also more potential attack vectors.
Google Play Protect
Google built security into Android at the OS level through Google Play Protect. This system scans apps before you install them and monitors your device for malicious behavior.
Google Play Protect doesn't catch everything. It's not Lockdown Mode. But it does provide baseline protection by:
- Scanning apps before download from Google Play Store
- Monitoring installed apps for malicious behavior
- Automatically removing dangerous apps
- Blocking installation of apps from untrusted sources
Google Play Protect is enabled by default on most Android devices. You can verify it's active by going to Settings > Security > Google Play Protect.
The Importance of Security Updates
Android updates are released regularly, but device manufacturers and carriers control when they're pushed to your device. Some devices receive updates immediately. Others wait weeks or months.
These updates patch vulnerabilities that attackers actively exploit. When you delay updates, you leave yourself exposed to known, weaponized exploits.
Make this simple rule: install security updates within 48 hours of receiving the notification. Don't wait for a convenient time. Security updates are more important than any other activity on your device.
On Android, check for updates in Settings > About Phone > System Update or Settings > System > System Update depending on your device.
App Permissions Management
Android's app permission system allows granular control over what each app can access.
Many apps request permissions they don't need. A flashlight app shouldn't need access to your contacts. A calculator shouldn't need location access. Yet apps often request broad permissions anyway—sometimes out of poor design, sometimes maliciously.
Audit your app permissions regularly. Go to Settings > Apps > Permissions. Review each permission category (Camera, Microphone, Location, Contacts, etc.) and see which apps have access. Deny access to apps that don't need it.
Further, understand the difference between "While Using the App" and "Always Allow" for location and microphone permissions. Most apps should only have "While Using the App" permissions.
Side-loading Risk
One major difference between Android and iOS: Android allows installation of apps from sources other than Google Play Store. This is called side-loading.
Side-loading offers flexibility. You can install apps that Google doesn't allow in the Play Store, or test beta versions. But it also introduces risk. An attacker could distribute malicious apps disguised as legitimate ones.
General rule: only install apps from Google Play Store. If you need to side-load an app, ensure you completely trust the source and understand the risks.
If you do side-load apps, at minimum verify the app's signature and confirm you're downloading from the legitimate developer's website, not a third-party repository.
Android's Built-in Security Dashboard
Android's Security & Privacy dashboard provides visibility into your device's security status.
Access it through Settings > Security. Here you can see:
- Security status and any detected threats
- Recent security scans
- App security information
- Find My Mobile (for locating your device)
- Screen lock settings
Review this dashboard monthly. If any threats are detected, Google Play Protect provides options to remove them.

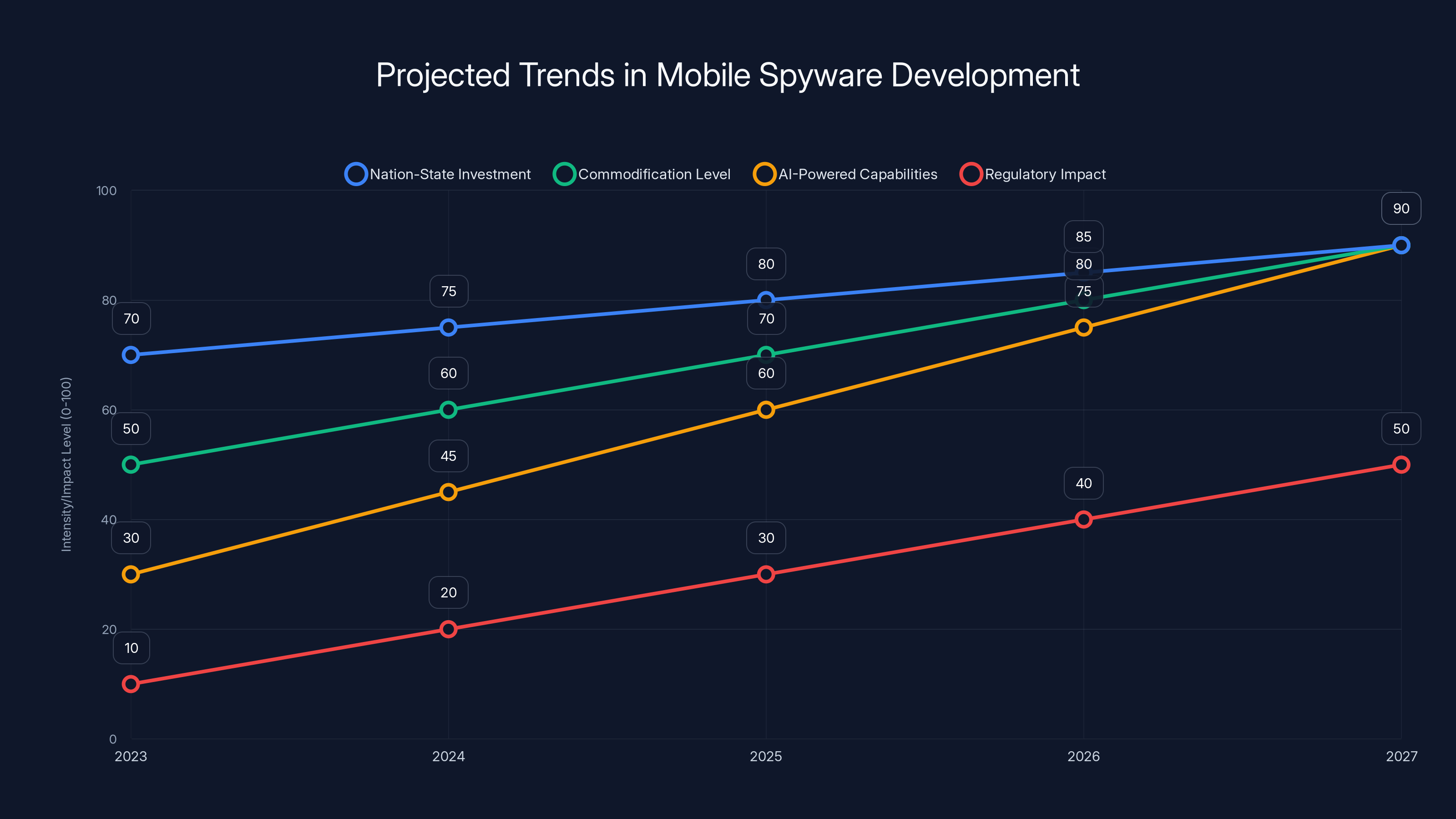
The line chart illustrates projected trends in mobile spyware development, highlighting increasing nation-state investment, commodification, and AI integration, while regulatory impacts are expected to grow but remain limited. Estimated data.
Essential Security Practices for Every User
Regardless of your risk level or device type, these practices form the foundation of mobile security.
Keep Your OS and Apps Updated
This isn't sexy advice, and it's hard to overstate its importance. Every update patches vulnerabilities. Attackers weaponize known vulnerabilities. If you're running outdated software, you're vulnerable to attacks that developers have already fixed.
For iOS: Go to Settings > General > Software Update and install updates immediately when available.
For Android: Go to Settings > About Phone > System Update (or System > System Update depending on manufacturer) and install updates immediately.
Set your device to update automatically if possible. iOS allows automatic updates in Settings > General > Software Update > Automatic Updates. Android offers similar settings depending on manufacturer.
Use Strong, Unique Passwords
Your phone's security is only as strong as your authentication. If someone gains access to your Apple ID or Google Account, they can reset your phone remotely, bypass security features, or access your data.
Use strong passwords (16+ characters, mix of uppercase, lowercase, numbers, symbols) for both your Apple ID and Google Account. Better yet, use a password manager like 1Password or Bitwarden to generate and store complex passwords.
Don't reuse passwords across accounts. If one account is compromised, attackers immediately try the same password on other accounts. A unique password per account contains the damage.
Enable Two-Factor Authentication
Two-factor authentication (2FA) means someone needs both your password and a second verification method to access your account. Even if an attacker steals your password, they can't access your account without the second factor.
For Apple ID: Enable 2FA in Settings > [Your Name] > Password & Security > Two-Factor Authentication.
For Google Account: Enable 2-Step Verification in your Google Account settings.
Use authenticator apps like Google Authenticator, Microsoft Authenticator, or Authy rather than SMS-based 2FA when possible. SMS can be intercepted through SIM swap attacks.
Avoid Suspicious Links and Downloads
Link-based spyware still works because people click links. If you receive a text message from "your bank" asking you to verify your account by clicking a link, don't click it. Go to your bank's app or call their customer service number directly.
The same applies to emails and social media messages. Legitimate companies rarely ask you to click links to verify information. If they do, verify through official channels before clicking.
Be especially careful with shortened URLs (bit.ly, tinyurl, etc.) because you can't see where they actually go. Hover over them to see the full URL before clicking.
Only Use Official App Stores
Android users should stick to Google Play Store. iOS users should stick to the Apple App Store. While both stores have malicious apps occasionally, they're far safer than third-party stores or direct APK downloads.
Before installing any app, check:
- Who's the developer? Is it the official developer?
- How many reviews does it have? Are reviews suspiciously positive?
- What permissions does it request? Does it need those permissions?
- When was it last updated? Outdated apps may have unpatched vulnerabilities

Advanced Protection Strategies
For high-risk individuals, basic security measures aren't enough. Consider these additional protections.
Device Isolation
If you're handling extremely sensitive information, consider maintaining separate devices: one for sensitive work, one for everything else. Compromise of the everyday device doesn't expose sensitive work.
This might sound excessive, but journalists working in hostile environments, activists, and government officials often maintain multiple devices with different purposes.
Secure Communication Tools
Not all messaging apps are created equal. Signal, developed specifically for secure communication, provides end-to-end encryption by default. WhatsApp also uses end-to-end encryption, though it's closed-source.
For sensitive communications, use apps specifically designed for security: Signal, Wire, or Briar. These apps are open-source and regularly audited by security researchers.
That said, remember the spyware vulnerability: sophisticated spyware can read messages even in encrypted apps because it operates at the OS level, above the app layer.
Regular Device Monitoring
For people who believe they might be targeted, consider periodic forensic analysis of your device. Services like Access Now provide security assessments for journalists and activists.
Forensic analysis is thorough and expensive, so it's typically done every 6-12 months rather than continuously. But for high-risk individuals, knowing definitively whether you've been compromised is worth the cost.
Network Monitoring
Advanced users can set up network monitoring to detect unusual data transmission. This involves technical knowledge but can reveal if your device is connecting to suspicious servers or transmitting data abnormally.
Tools like Wireshark allow you to capture and analyze network traffic. If you see your device transmitting data to unfamiliar IP addresses, especially during idle periods, that's suspicious.
Physical Security
Spyware installation sometimes requires physical access to your device. If your phone is left unattended in public, at a border crossing, or in a hostile environment, someone might attempt to install malware.
Never leave your device unattended in locations where you don't trust the surroundings. Don't allow your phone to be taken away "for inspection." At border crossings, some authorities request access to phones—you have the right to refuse, though there may be consequences.
If you're traveling to a hostile country, consider using a burner phone (cheap, temporary device) for essential communications and leaving your primary phone behind.

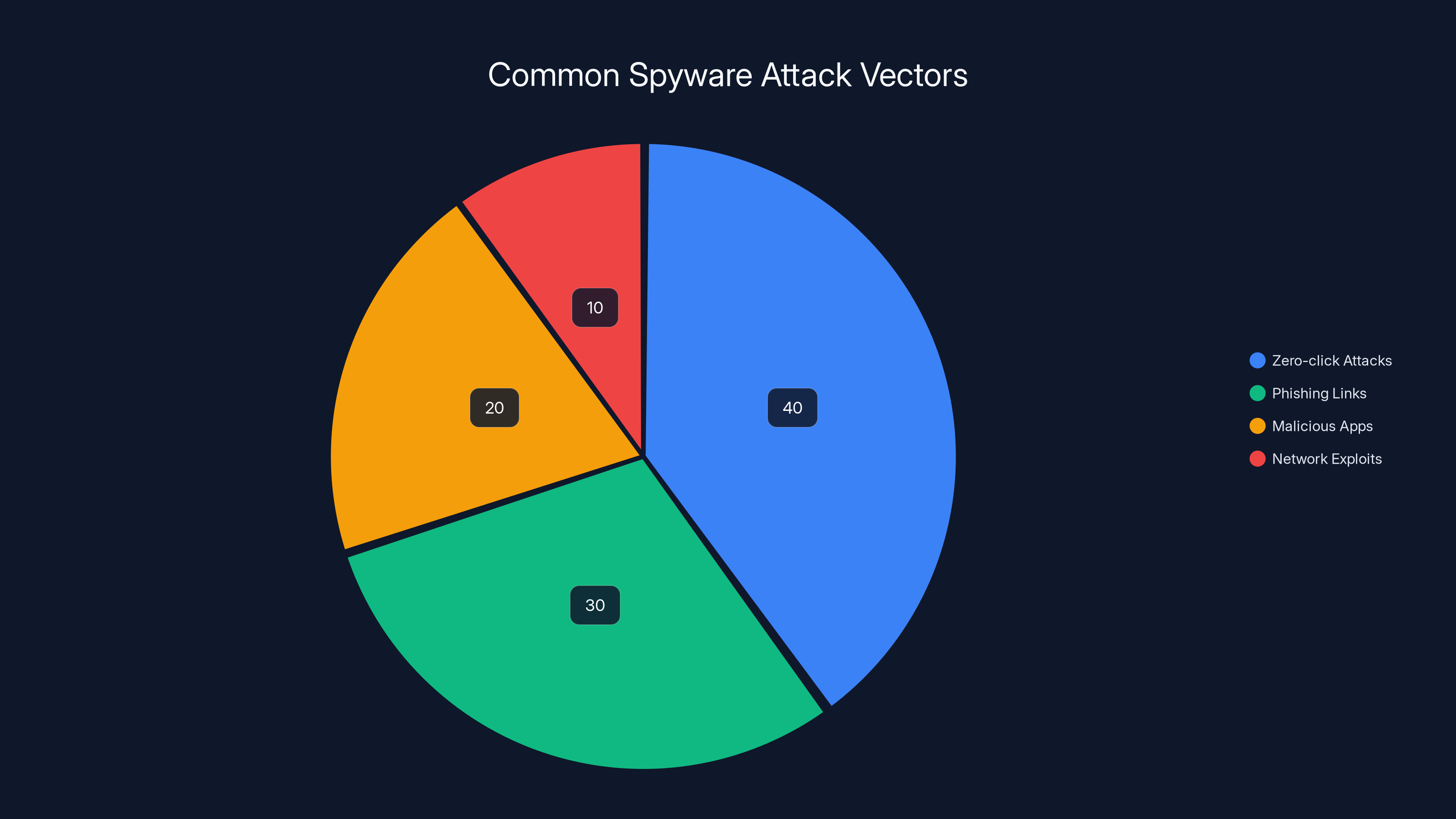
Zero-click attacks are estimated to account for 40% of spyware infections, highlighting their significant threat. Estimated data.
Understanding the Broader Threats
Spyware exists within a larger ecosystem of mobile security threats. Understanding other threats helps you maintain overall security.
Phishing and Social Engineering
Spyware isn't always technically sophisticated. Sometimes the attacker's first step is convincing you to reveal information or click a link through social engineering.
Phishing is designed to look like legitimate communication from a trusted company. "Verify your Apple ID" emails look authentic. "Confirm your bank account" texts look real. But they're designed to trick you into revealing credentials.
Defense: Never click links in unsolicited emails or texts claiming to be from companies you use. Go to the company's official website or app directly.
Man-in-the-Middle Attacks
When you use public Wi-Fi, an attacker on the same network can intercept unencrypted communication. This is called a man-in-the-middle attack.
Defense: Use a VPN (Virtual Private Network) on public Wi-Fi. Services like ExpressVPN, ProtonVPN, or Mullvad encrypt your traffic so no one on the Wi-Fi network can see what you're doing.
Credential Compromise
If your Apple ID or Google Account password is compromised, an attacker can access your iCloud or Google Cloud data, reset your phone, or lock you out of your account.
Defense: Use strong, unique passwords and enable two-factor authentication as discussed earlier.
SIM Swap Attacks
Attackers contact your mobile carrier, convince them you're you, and transfer your phone number to a new SIM card they control. This gives them access to SMS-based 2FA codes.
Defense: Request a PIN or password from your carrier to authorize SIM transfers. Don't use SMS-based 2FA; use authenticator apps instead.

What to Do If You Suspect You're Compromised
If you believe your device might have spyware, immediate action is critical.
Step 1: Don't Panic, But Act Quickly
Take the situation seriously but don't rush into decisions that might harm you. If you're a journalist or activist, immediate exposure could put you in danger. Secure yourself first.
Step 2: Stop Using Sensitive Information
If you're compromised, don't enter passwords, access banking apps, or handle sensitive communications on the suspect device. An attacker can see everything.
For essential communications, use a device you're confident is clean.
Step 3: Change Your Passwords from a Different Device
Change your Apple ID, Google Account, and critical service passwords (email, banking, social media) from a device you trust isn't compromised.
Do this from a computer or a different phone. Don't change passwords from the suspect device.
Step 4: Contact the Authorities
If you believe you're a victim of espionage, contact law enforcement. In the US, report to the FBI. In other countries, contact your national police or intelligence agency.
Provide details about suspicious activity, threats you've received, and when the compromise may have started.
Step 5: Seek Professional Help
If you're a high-risk individual, contact organizations like Access Now (accessnow.org) or the Electronic Frontier Foundation (eff.org) that provide digital security assistance to journalists, activists, and human rights defenders.
These organizations can assess your device, provide guidance, and connect you with appropriate resources.
Step 6: Consider Device Replacement
For sophisticated spyware, there's no guaranteed removal method besides factory reset. And even factory reset isn't always reliable against nation-state-level exploits.
If you're confident you're compromised, the safest option is replacing your device. Factory reset and restore from backup might reinstall the malware if the exploit is sophisticated enough.
Buy a new device, set it up from scratch (don't restore from backup immediately), and use it with the security practices outlined above.
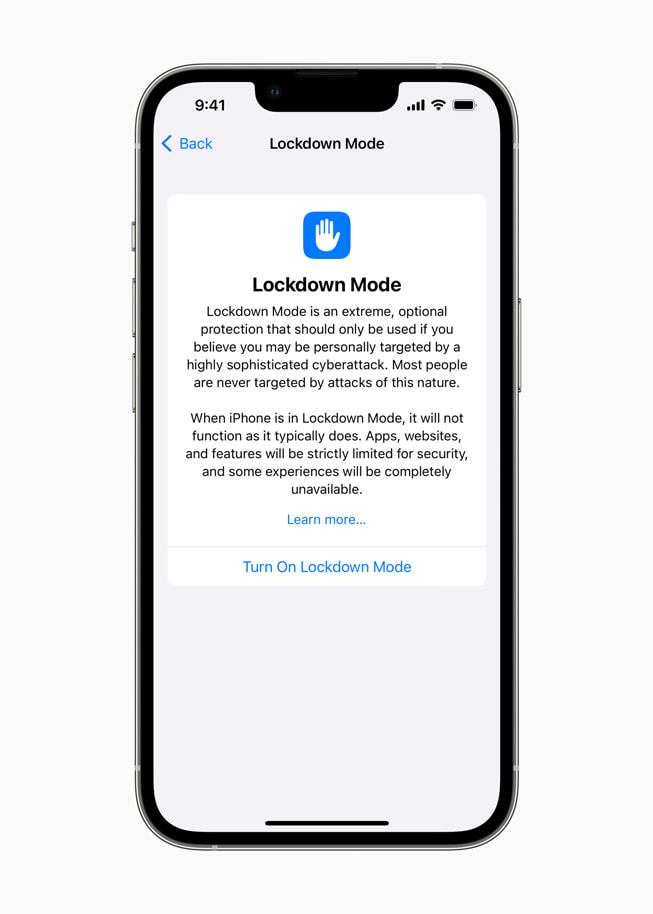
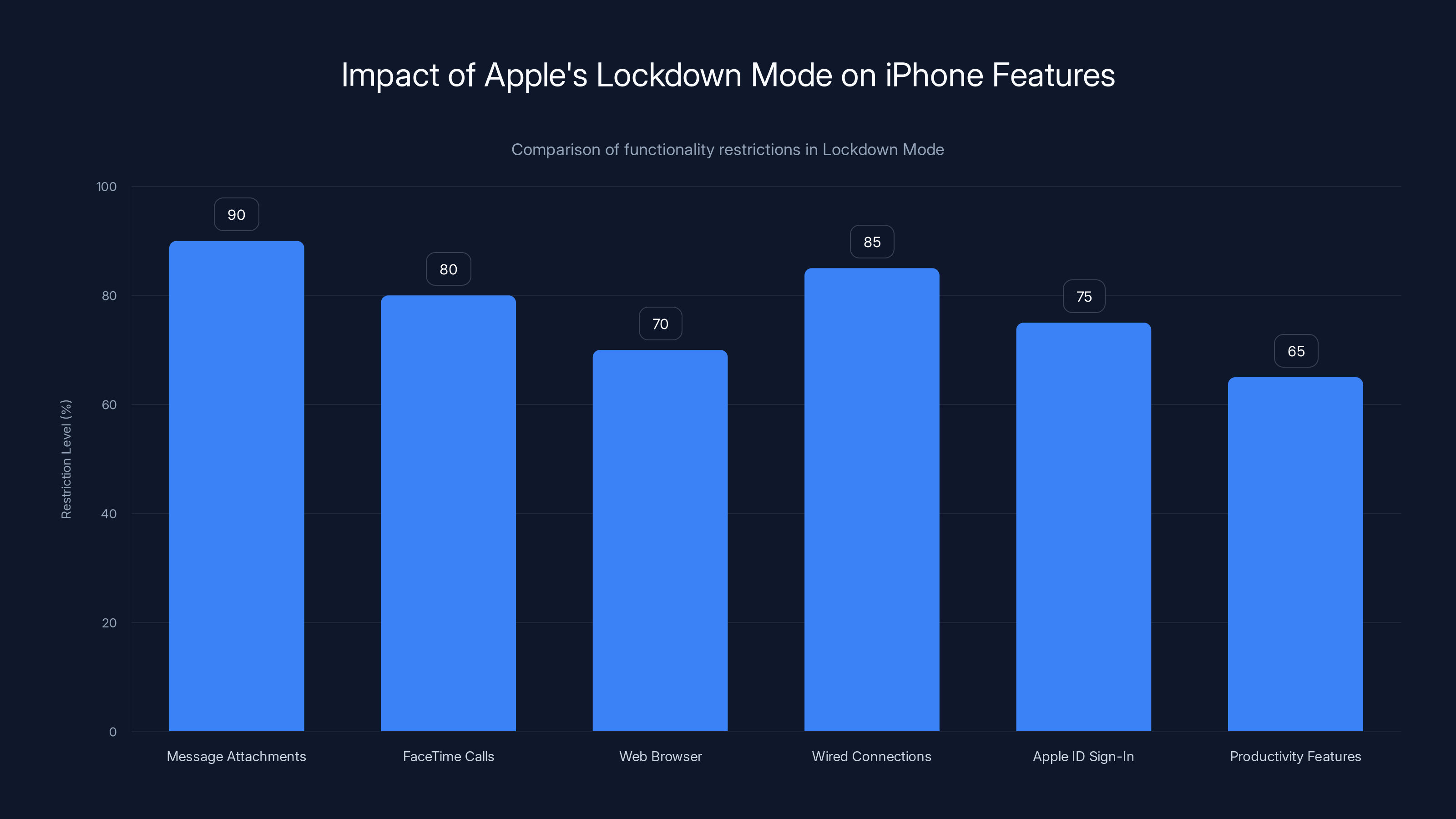
Lockdown Mode significantly restricts various iPhone functionalities to enhance security, with message attachments and wired connections being the most restricted. Estimated data.
The Future of Mobile Spyware
The landscape continues to evolve, and future threats will look different from today's spyware.
Nation-State Arms Race
Governments are investing heavily in mobile exploitation capabilities. As security improves, attackers invest more. This creates an arms race where security features are deployed, exploits are discovered, patches are released, and new exploits are developed.
This trend suggests that mobile spyware will remain a persistent threat for the foreseeable future. No operating system will ever be completely secure because security and usability are constant trade-offs.
Commodification of Spyware
Tools like Pegasus were once available only to governments. But the landscape is changing. More spyware tools are being developed by private companies and sold commercially. This commodification lowers the barrier to entry for non-state actors.
As spyware becomes cheaper and more accessible, the range of potential victims expands. It's no longer just dissidents and journalists who face targeting. Business leaders, families of prominent figures, and potentially anyone deemed valuable enough becomes a potential target.
AI-Powered Monitoring
Future spyware will likely incorporate AI capabilities. Rather than just recording and transmitting raw data, AI could analyze data in real-time to identify interesting information. This makes the surveillance more efficient and more dangerous.
Sophisticated spyware could use AI to identify passwords as they're typed, predict which information might be valuable, or summarize conversations to highlight key points.
Regulatory Changes
Governments are beginning to restrict spyware sales. The US, EU, and other countries have implemented or are implementing regulations around commercial spyware. But enforcement remains weak, and determined actors can still acquire tools.
Longer-term, regulation will likely make sophisticated spyware harder to obtain, but it won't eliminate the threat. Nation-states will continue developing spyware regardless of regulations.
Building a Security Mindset
Ultimately, protecting yourself from spyware requires thinking differently about your device and your data.
Most security advice treats security as a feature you add to your life. "Install this app, enable this setting, and you'll be secure." But real security comes from understanding your threat model and making deliberate choices.
Start by asking: What am I protecting? Is it my personal privacy? My professional information? My physical safety? Different answers require different security postures.
Next: Who might want to compromise me? Random criminals, competitors, my government, an ex-partner? Your threat model determines which protections matter most.
Finally: What am I willing to sacrifice for security? Time? Convenience? Functionality? No security measure is free. Understanding your acceptable trade-offs helps you make informed decisions.
This security mindset isn't about paranoia. It's about being intentional. Every app you install, every permission you grant, every link you click is a choice. Making these choices consciously, with awareness of potential consequences, is the foundation of real security.
Spyware is a real threat, and it's getting more sophisticated. But you're not helpless. Armed with knowledge, practical security measures, and a security-conscious mindset, you can dramatically reduce your risk.
Start today: check your app permissions, enable 2FA on your critical accounts, and install the next security update your device offers. These steps won't eliminate risk, but they'll make you a much harder target, and that's what matters.

FAQ
What is spyware and how does it differ from regular malware?
Spyware is a specific type of malware designed to secretly monitor and report your device activity to an attacker. Unlike regular malware that might steal data through ransomware or destroy files, spyware operates invisibly with the goal of comprehensive surveillance. It's designed to be persistent and undetectable, giving attackers real-time access to your messages, location, audio, and more, even within encrypted apps.
How do zero-click attacks work and can I prevent them?
Zero-click attacks exploit previously unknown vulnerabilities (called zero-days) to silently install spyware without any user interaction required. Unlike traditional attacks that require you to click a link or download a file, zero-click attacks can compromise your device simply by receiving a message or being nearby. Prevention is extremely difficult for regular users since no action triggers the attack. Your best defenses are keeping your operating system updated, enabling security features like Lockdown Mode on iOS, and using official threat notifications from Apple or Google as indicators that something may be wrong.
Is my iPhone really safer than Android from spyware?
Neither iOS nor Android is inherently "safer" from spyware, but they have different security models. iOS uses a closed ecosystem where Apple controls software distribution, which provides advantages for security patching and app verification. Android's openness creates more flexibility but also more potential attack vectors. Apple states it hasn't seen widespread malware attacks against iOS in the wild, only targeted nation-state spyware. Both platforms receive regular security updates and have built-in protections. The real difference is your behavior: you're safer on either platform if you keep the OS updated, avoid suspicious apps, and use strong authentication.
What should I do if I receive an official threat notification from Apple or Google?
Take the notification seriously. These aren't false alarms or phishing attempts. Apple and Google only send threat notifications when they have evidence that your device was targeted by mercenary spyware (sophisticated government-backed surveillance tools). First, immediately enable Lockdown Mode on iOS or ensure you're fully updated on Android. Change your passwords for Apple ID, Google Account, and critical services from a different device. Stop handling sensitive information on the compromised phone. Contact organizations like Access Now for professional digital security assistance. Consider whether you need forensic analysis before resetting the device.
Can factory reset really remove spyware from my device?
Factory reset can remove most spyware, but sophisticated nation-state level spyware might persist even after reset if it has compromised the bootloader or firmware. For the vast majority of threats, factory reset followed by careful restoration (from cloud backup or setting up as new) will remove the malware. However, if you believe you're targeted by government-level spyware, forensic analysis before reset is recommended. After reset, set up your device from scratch rather than restoring from backup immediately, then restore data gradually while monitoring behavior.
Which messaging apps are truly secure from spyware?
Signal and WhatsApp both use strong end-to-end encryption by default, making them much better than alternatives like SMS or plain-text messaging. However, this encryption only protects messages in transit. Sophisticated spyware operating at the system level can still read messages because it intercepts them before encryption or after decryption on your device. For truly sensitive communications, use those apps with the understanding that if your device itself is compromised, encryption provides no protection. Open-source apps like Briar or Wire offer additional transparency, but they still can't protect against OS-level spyware.
How often should I update my phone's security?
Install security updates within 48 hours of receiving notifications. Don't wait for a convenient time. Security updates patch vulnerabilities that attackers actively exploit. Enable automatic updates in your device settings whenever possible so updates install overnight without disrupting your day. For critical systems and apps, check for updates at least monthly beyond automatic updates. Security is an ongoing practice, not a one-time installation.
Are VPNs effective protection against spyware?
VPNs encrypt your internet traffic, which protects against attackers on your Wi-Fi network from seeing what you're doing online. However, VPNs don't protect against spyware. If malware is installed on your device, it operates at the system level and can see your activity before encryption or after decryption. VPNs are useful for privacy on public Wi-Fi but shouldn't be your primary spyware defense. Use a reputable VPN provider (not free services) when on public Wi-Fi, but understand it's not protection against spyware itself.
How much of a risk is spyware for regular people not involved in activism or journalism?
For most people, sophisticated nation-state spyware targeting is extremely unlikely. These campaigns are expensive and reserved for high-value targets. However, commercial spyware is becoming more accessible and could be used for corporate espionage, extortion, or personal stalking. Additionally, the definition of "high-risk" is expanding. The best approach is practicing good hygiene with basic security measures (updates, strong passwords, 2FA, cautious app installation) which protect against most threats without requiring extreme measures like Lockdown Mode. Assess your actual threat model rather than assuming either no risk or maximum risk.
Key Takeaways
- Spyware is real and evolving: Sophisticated tools like Pegasus and Predator demonstrate that mobile surveillance is a persistent, evolving threat affecting journalists, activists, and increasingly, business leaders
- Zero-click attacks are the nightmare scenario: Modern spyware doesn't require user error; your device can be compromised without clicking anything suspicious
- Detection is difficult but possible: Watch for overheating, performance degradation, unusual data usage, and especially official threat notifications from Apple or Google
- iOS and Android both have defenses: Lockdown Mode on iOS provides maximum protection with usability trade-offs; Android relies on Google Play Protect, regular updates, and permission management
- Basics matter most: Keeping your OS updated, using strong unique passwords with 2FA, and avoiding suspicious links prevents the vast majority of mobile malware
- High-risk individuals need advanced measures: Journalists, activists, and business leaders should consider Lockdown Mode, secure communication tools, and periodic forensic analysis
- Data is weaponizable: Stolen personal information can be used against you offline, which is why prevention is far better than remediation
- No device is 100% secure: Security is a process, not a state. Stay vigilant with ongoing practices rather than relying on one-time configuration
Related Articles
- Government Spyware Targeted You? Complete Action Plan [2025]
- Should You Use a VPN Browser? Complete Guide [2025]
- Essential Cybersecurity Habits for 2026: Expert Guide [2025]
- Juice Jacking: How to Protect Your Phone from Public Charging Threats [2025]
- Holiday Email Scams 2025: How to Spot and Stop Them [Updated]
- Best Cybersecurity Journalism 2025: Stories That Defined the Year
![How to Protect iPhone & Android From Spyware [2025]](https://tryrunable.com/blog/how-to-protect-iphone-android-from-spyware-2025/image-1-1767436555829.jpg)



