IPVanish Threat Protection Pro: Complete Guide to Advanced Malware Defense & Alternatives
Introduction: The Evolution of VPN Security Beyond Connection
The cybersecurity landscape has undergone a fundamental transformation over the past five years. Traditional VPNs focused solely on encrypting your internet traffic and masking your IP address—essential features, certainly, but increasingly insufficient in an era where threats persist across multiple attack vectors simultaneously. IPVanish's announcement of Threat Protection Pro represents a significant shift in how VPN providers conceptualize security, moving beyond the "connection-based" model toward a more comprehensive threat mitigation ecosystem.
Malware represents one of the most persistent and evolving threats facing computer users today. According to industry research, approximately 350,000 new malware variants are detected daily, with attack vectors becoming increasingly sophisticated. Traditional antivirus software addresses malware primarily after a threat is identified, while VPN services have historically focused exclusively on network-level encryption. IPVanish's Threat Protection Pro attempts to bridge this gap, offering real-time malware detection and blocking capabilities powered by VIPRE's established antivirus technology—a combination designed to provide layered protection that operates continuously, regardless of whether you're actively using the VPN service.
The timing of this feature launch reflects broader industry trends. Consumers are increasingly aware that a comprehensive security posture requires multiple defensive layers. Your internet connection alone cannot protect you from malware embedded in files, executable downloads, or malicious websites attempting to execute code on your system. By integrating VIPRE's antivirus engine directly into the IPVanish ecosystem, the company is attempting to create a unified security platform that addresses both network-level threats and endpoint-level malware risks.
Understanding Threat Protection Pro requires examining not only what the feature does, but how it fits within your broader cybersecurity strategy. This comprehensive guide explores the technical capabilities, real-world applications, pricing structures, and alternative approaches to achieving similar protection levels. Whether you're evaluating IPVanish specifically or seeking the optimal combination of VPN and antivirus protection for your Windows device, this analysis provides the depth needed to make an informed decision.
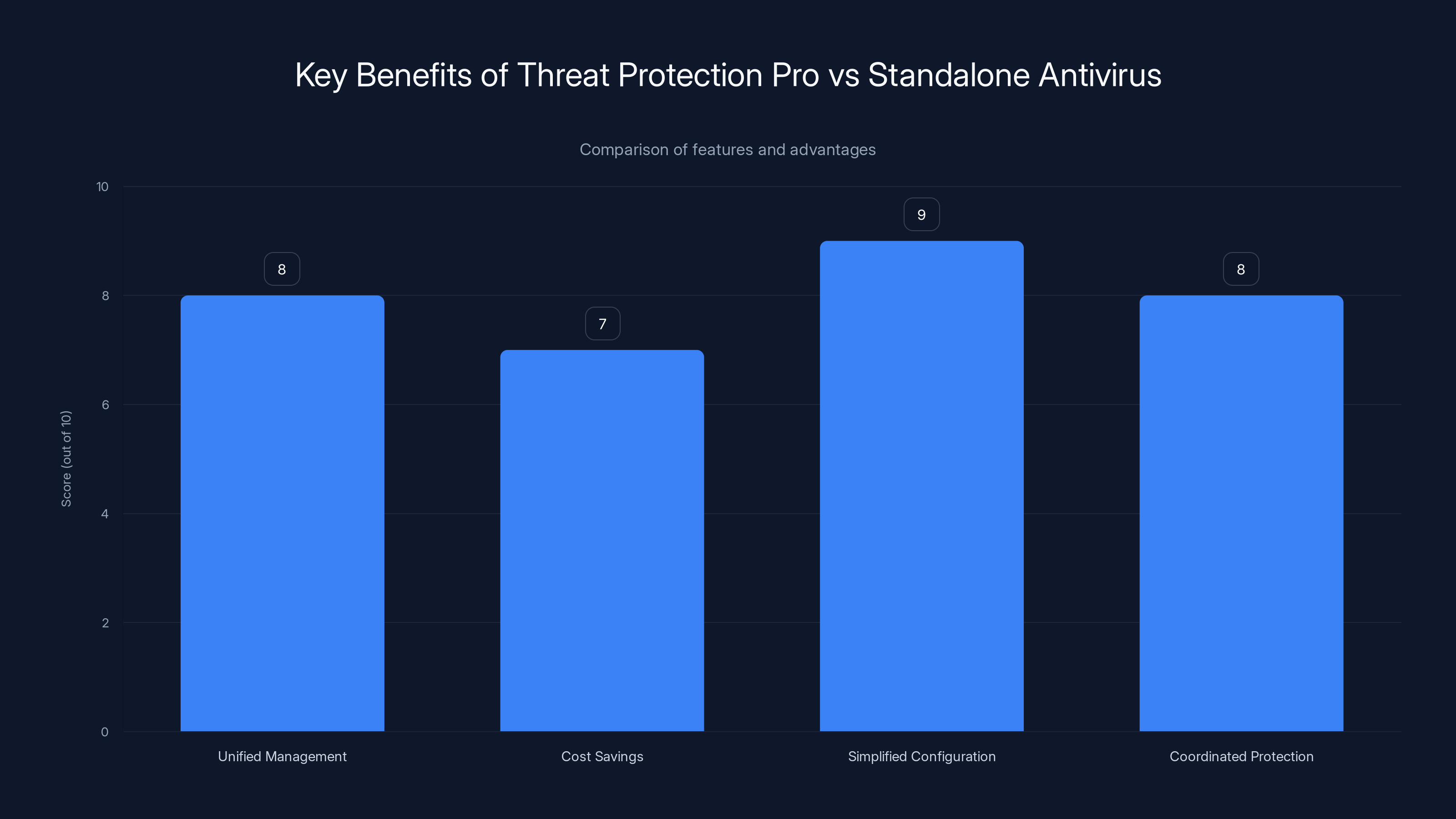
Threat Protection Pro offers significant advantages in unified management, cost savings, and simplified configuration over standalone antivirus solutions. (Estimated data)
What Is IPVanish Threat Protection Pro?
Core Functionality and Technical Architecture
Threat Protection Pro represents IPVanish's attempt to transcend the traditional VPN-only security model. At its core, this feature integrates VIPRE's antivirus detection engine directly into IPVanish's client software, creating a unified security application that performs simultaneous VPN encryption and malware scanning. Unlike traditional standalone antivirus software, Threat Protection Pro maintains continuous vigilance whether your VPN connection is active or dormant, addressing a critical vulnerability in conventional security architectures where malware protection often depends on separate, potentially less-coordinated systems.
The technical implementation leverages VIPRE's established reputation in the antivirus industry. VIPRE has maintained a significant market presence for over two decades, with particular strength in small business and consumer markets. Its detection engine utilizes multiple scanning methodologies: signature-based detection (identifying known malware patterns), heuristic analysis (identifying suspicious behavioral patterns that resemble known malware), and behavioral monitoring (tracking how programs interact with your system). By integrating this multi-method approach into IPVanish's interface, Threat Protection Pro theoretically provides more comprehensive coverage than either VPN encryption or standalone antivirus alone.
The protection extends across multiple threat categories: ransomware, trojans, worms, spyware, adware, rootkits, and potentially unwanted programs (PUPs). Threat Protection Pro scans files in real-time as they're accessed, downloaded, or executed, maintaining a dynamic defense posture that adapts to emerging threats as new signatures are added to VIPRE's threat database.
Current Limitations and Platform Availability
As of the announcement, Threat Protection Pro operates exclusively in beta on Windows devices. This platform limitation is significant because it excludes the macOS, Linux, and mobile operating system segments entirely. For security-conscious users running multiple operating systems—increasingly common in modern computing environments—this fragmented approach creates complications. You might achieve comprehensive protection on your Windows desktop while remaining without equivalent antivirus integration on your Mac laptop or Android device.
The beta designation carries important implications. Beta software, by definition, remains under active development with potential performance impacts, stability issues, or feature changes. Users enrolling in the beta program serve as quality assurance resources, identifying bugs and providing feedback before broader rollout. While participating in beta programs can provide early access to innovative features, it also introduces risk and uncertainty. Stability issues could potentially impact your VPN connectivity or antivirus responsiveness precisely when protection is most critical.
IPVanish has indicated plans to expand platform support beyond Windows, but specific timelines and rollout schedules remain unannounced. This suggests that comprehensive multi-platform coverage remains months away at minimum, potentially longer depending on development priorities and technical challenges.
Technical Deep Dive: How Threat Protection Pro Works
Real-Time Scanning Mechanisms
Threat Protection Pro implements real-time scanning through several interconnected processes that operate continuously in the background. When you download a file, the system immediately analyzes that file against VIPRE's threat signature database—a constantly updated catalog of known malware. This signature-matching process takes milliseconds and blocks confirmed threats before they can execute or spread.
Beyond signature matching, the system employs heuristic analysis, which examines file characteristics and behavior patterns to identify previously unknown malware variants. If a file exhibits suspicious characteristics—such as attempting to modify system registry entries in ways typical of malware, or displaying code obfuscation techniques commonly used in trojan distribution—the heuristic engine flags it for further analysis or quarantine. This approach proves particularly valuable against zero-day exploits, where malware has been newly discovered and no signature yet exists.
Behavioral monitoring represents the third scanning layer. Rather than focusing exclusively on files as static objects, behavioral monitoring observes how programs interact with your operating system in real time. If a seemingly legitimate application suddenly attempts to disable Windows Defender, modify security settings, or establish unauthorized network connections, the behavioral monitor recognizes these actions as potentially malicious regardless of the program's file integrity.
Integration with VPN Infrastructure
The integration between antivirus scanning and VPN functionality creates a unified security architecture. Your network traffic flows through IPVanish's encrypted VPN tunnels while simultaneously undergoing malware inspection. This dual protection means your downloads benefit from both network-level security (preventing man-in-the-middle attacks that could inject malware) and endpoint-level detection (catching malware that slips through network defenses).
The technical challenge in this integration involves managing performance overhead. Antivirus scanning, particularly real-time file monitoring, consumes CPU resources and can noticeably impact system responsiveness. VPN encryption similarly demands computational resources. Implementing both simultaneously without creating an unusable system requires careful optimization. IPVanish must balance comprehensive protection with maintaining reasonable performance—a technical tightrope that many security applications struggle to walk successfully.
Data flow architecture becomes critical here. Sensitive files passing through your system must be scanned for malware without unnecessarily exposing them to IPVanish's infrastructure. The implementation maintains strict separation between the antivirus scanning process and data routing, ensuring that your files are analyzed locally and malware threats are blocked before data ever leaves your device.
Threat Intelligence and Update Cycles
The effectiveness of any antivirus system depends fundamentally on the currency of its threat database. VIPRE maintains its threat signature database through continuous monitoring of global malware distribution networks, honeypots, and security researcher submissions. Threat Protection Pro accesses these updates automatically and continuously, with new signatures typically deployed multiple times daily.
The update mechanism operates transparently in the background. You never need to manually trigger updates or perform administrative actions—the system pulls new threat signatures based on VIPRE's internal release schedule. This automation represents a significant advantage over antivirus systems requiring manual updates, which users frequently neglect or postpone.
Unfortunately, IPVanish has not publicly disclosed specific details about update frequency, latency between new malware discovery and signature deployment, or the total size of VIPRE's threat database. These metrics directly impact protection effectiveness but remain unavailable for independent evaluation.
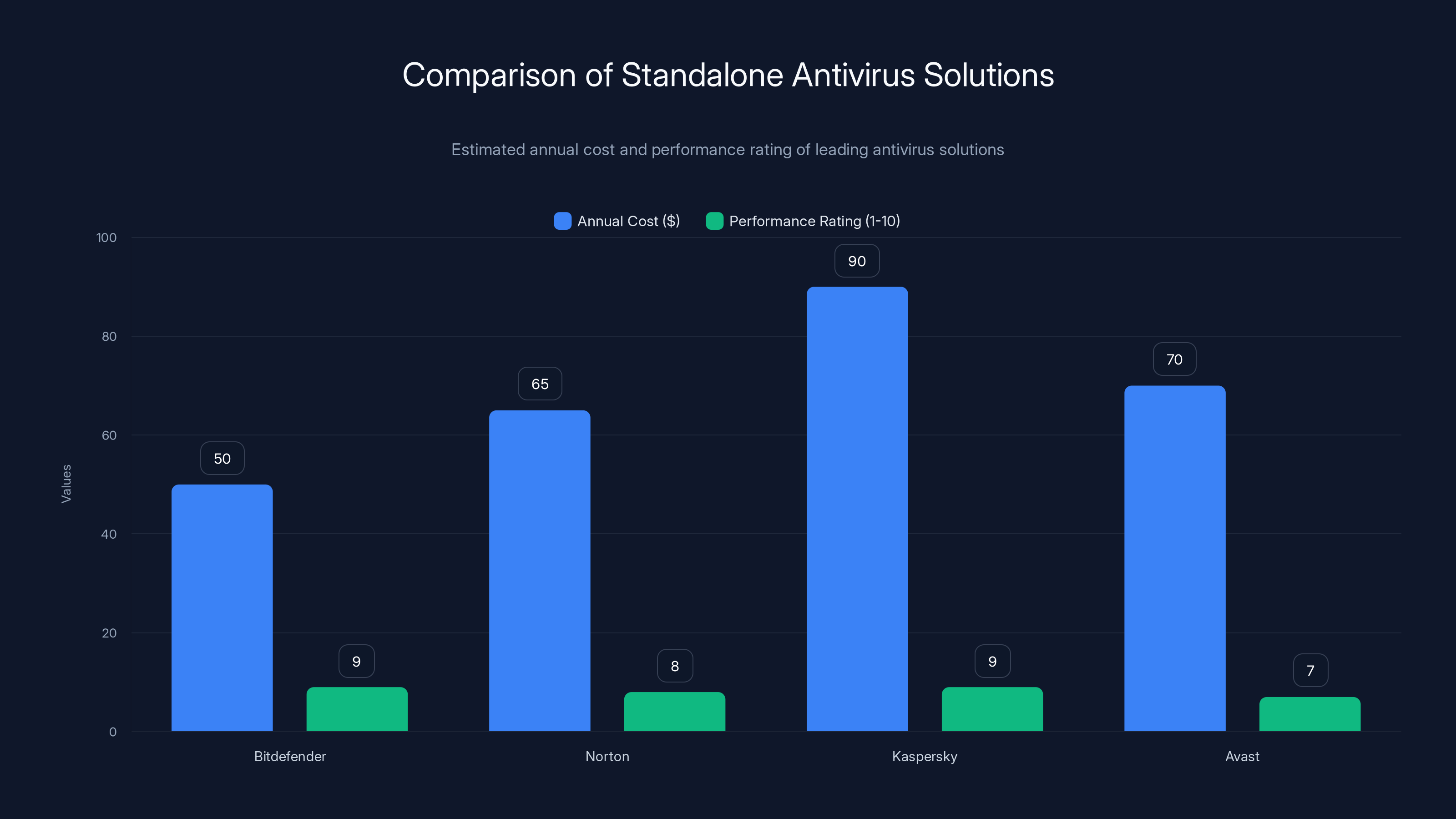
Bitdefender and Kaspersky offer high performance ratings at competitive costs, while Kaspersky is the most expensive. Estimated data based on typical market pricing.
Key Features and Capabilities Analysis
Comprehensive Malware Detection Categories
Threat Protection Pro addresses a broad spectrum of malware types, extending far beyond basic virus detection. Ransomware protection has become increasingly critical as these attacks target both individuals and organizations with devastating financial consequences. The system monitors for behavioral patterns typical of ransomware—mass file encryption, system resource consumption spikes, and suspicious file modification patterns—stopping attacks before they can encrypt your data.
Spyware and adware detection targets programs that compromise your privacy by harvesting personal information or flooding your system with unwanted advertisements. These threats often masquerade as legitimate software, making behavioral and heuristic analysis particularly valuable. Trojan detection focuses on programs that appear benign while harboring malicious payloads, with real-time monitoring catching suspicious activities before trojans can execute their intended functions.
Potentially unwanted programs (PUPs) represent a gray area between legitimate software and outright malware—programs that may be unwanted, tracking-heavy, or bundled with other unwanted software. Threat Protection Pro can identify and quarantine PUPs, allowing you to maintain a cleaner system focused on essential applications. Rootkit detection addresses one of the most dangerous malware categories, which burrow deep into operating system internals and hide from standard detection methods.
Web-Based Threat Blocking
Threat Protection Pro integrates phishing and malicious website detection into the browsing experience. As you navigate the internet, the system cross-references websites against databases of known phishing sites and malware distribution networks. If a website appears in threat databases, the system can block navigation or display warning messages, preventing you from unknowingly visiting dangerous sites.
This feature addresses a critical attack vector. Phishing remains one of the primary malware distribution methods, with attackers creating convincing replicas of legitimate websites to harvest credentials or distribute malware. Traditional VPN protection cannot distinguish legitimate websites from phishing replicas—both appear identical at the network level. By integrating website threat intelligence, Threat Protection Pro adds crucial web-based defense.
The effectiveness of web threat blocking depends on the currency and comprehensiveness of the malicious website database. New phishing sites and malware hosting infrastructure constantly appear faster than any database can catalog them. While Threat Protection Pro benefits from VIPRE's continuous monitoring, some advanced phishing and hosting operations inevitably escape detection.
Quarantine and Threat Remediation
When Threat Protection Pro identifies a threat, it doesn't immediately delete suspected files—doing so could cause system instability if false positives occur. Instead, the system moves threatened files to quarantine, isolated from the running system where they cannot execute or spread. Quarantined files remain accessible for review, allowing you to verify that detected items were genuinely malicious before permanent deletion.
The quarantine functionality includes detailed threat reporting. Each quarantined item includes metadata indicating the detection method (signature match, heuristic analysis, or behavioral monitoring), threat classification, and the file's location when detected. This transparency helps you understand your system's threat profile and identify potential attack vectors or malware sources.
Manual remediation options provide control over how the system handles threats. Rather than relying entirely on automatic responses, you can review flagged files and decide whether to delete, quarantine, or restore them. This granular control proves essential when dealing with potentially false positives—a particular concern when antivirus software becomes overly aggressive in threat identification.
VIPRE Antivirus Technology: The Underlying Engine
VIPRE's Market Position and Track Record
VIPRE has maintained a significant presence in the cybersecurity market since its founding, with particular strength among small businesses and individual consumers. The platform combines ease of use with comprehensive threat detection, prioritizing accessibility without sacrificing detection capability. By licensing VIPRE's technology rather than developing antivirus capabilities in-house, IPVanish gains access to a mature threat detection engine with established market credibility.
VIPRE's detection capabilities have consistently performed well in independent testing by organizations like AV-TEST Institute and Virus Total. The platform demonstrates particularly strong performance against common malware categories while maintaining relatively low false-positive rates—an important balance because excessive false positives degrade user trust and create frustrating experiences.
The decision to partner with VIPRE rather than other antivirus providers reflects strategic considerations. Alternative antivirus engines—Norton, McAfee, Kaspersky, Bitdefender—come with varying market reputations, licensing costs, and compatibility profiles. VIPRE's reputation for lightweight resource consumption and effective detection without excessive system overhead makes it well-suited for integration into a VPN client that already consumes system resources.
Detection Accuracy and False Positive Rates
Antivirus effectiveness depends on balancing two competing objectives: maximizing genuine threat detection while minimizing false positives that flag legitimate software as malicious. An overly aggressive system blocks legitimate programs and creates frustration, while an overly conservative system misses real threats. VIPRE attempts to achieve this balance through its multi-layered approach combining signatures, heuristics, and behavioral analysis.
Signature-based detection provides the highest confidence detections—files matching known malware signatures are definitively malicious. However, this approach only detects previously identified malware, making it ineffective against new threats. Heuristic analysis introduces some false positive risk because legitimate programs might employ techniques also used by malware authors. Behavioral monitoring carries similar risks, as unusual behavior might indicate either malware or unusual but legitimate activity.
IPVanish has not published specific detection rates or false positive metrics for Threat Protection Pro, making independent validation difficult. Users will need to monitor their own experiences during the beta period to evaluate whether the system achieves appropriate balance for their threat tolerance and use patterns.
Resource Efficiency and System Impact
Antivirus software traditionally represents one of the most resource-intensive security applications, with real-time scanning consuming significant CPU cycles and system memory. VIPRE's reputation for lightweight operation becomes particularly important when integrated with VPN software, as the combination could otherwise render systems sluggish and unresponsive.
The optimization challenge intensifies on lower-specification systems. A laptop with limited RAM and a processor from several years ago might struggle with the combined load of VPN encryption and continuous antivirus scanning. IPVanish's development team must optimize the integration to ensure acceptable performance across diverse hardware configurations.
Preliminary reports from beta testers regarding system impact will be crucial for evaluating whether Threat Protection Pro achieves acceptable performance balance. Even excellent threat detection becomes problematic if it renders your system unusable during normal operation.
Protection Across Different Attack Scenarios
Email-Based Malware Distribution
Email remains one of the primary malware distribution vectors. Threat Protection Pro addresses this through file scanning of email attachments and inline content. When you download an attachment or access email content containing embedded files, Threat Protection Pro analyzes those files for malware before they can be accessed or executed.
This protection extends beyond email clients to web-based email services like Gmail or Outlook Web Access. As files download through your browser, they undergo scanning before reaching your disk. This approach addresses a critical vulnerability in relying solely on email client-level protection, as many users access email through multiple interfaces.
The challenge with email-based protection involves dealing with false positives. Email security systems frequently flag legitimate business documents and compressed files as suspicious. Threat Protection Pro must navigate this balance, catching genuinely malicious emails without blocking essential business communications.
Drive-By Download Attacks
Drive-by downloads represent a sophisticated attack vector where visiting an infected website automatically initiates malware downloads without user knowledge or consent. These attacks exploit browser vulnerabilities or employ deceptive techniques to make users believe legitimate software is being installed. Threat Protection Pro's real-time file scanning catches downloaded malware before execution, preventing infection even if the initial website compromise occurs.
The combination of web-based threat blocking and file scanning provides layered defense. First, the system might block access to known malicious hosting infrastructure. Second, if a drive-by download somehow occurs from an unblocked source, real-time scanning catches the malware before it can execute. This defense-in-depth approach significantly reduces successful infection rates.
However, zero-day drive-by exploits—attacks using previously unknown website vulnerabilities—remain challenging for any antivirus system. Until security researchers discover and patch the underlying vulnerability, and until the website operator implements the patch, sophisticated attackers might achieve initial infections despite robust defenses.
Exploit Kit Attacks
Exploit kits represent commercially available attack tools that automatically identify and exploit vulnerabilities in web browsers, plugins, or operating systems. When your system visits a website hosting an exploit kit, the malicious code probes for known vulnerabilities and attempts to execute malware if exploitation succeeds. Threat Protection Pro's behavioral monitoring can catch exploitation attempts by observing suspicious system-level actions—though this represents a reactive defense against sophisticated attacks that might execute code before behavioral analysis identifies the threat.
Proactive defense against exploit kit attacks depends on keeping your operating system, browsers, and plugins fully patched. Threat Protection Pro provides valuable catching-up protection but cannot substitute for timely security updates. Users must maintain current software versions to defend against the latest exploit kits effectively.
Local Malware Execution and System Infection
Beyond preventing initial infections, Threat Protection Pro monitors malware attempting to execute on your already-infected system. If you somehow become infected despite preventive measures—perhaps through a sophisticated zero-day attack or a user action that bypasses security warnings—the behavioral monitoring system might catch the malware during its execution phase before it can establish persistence or launch its attack.
This reactive protection proves valuable but obviously inferior to preventive detection. Infections that reach the execution phase have already potentially compromised system integrity. Threat Protection Pro attempts to minimize damage once infection occurs, but prevention remains dramatically preferable.
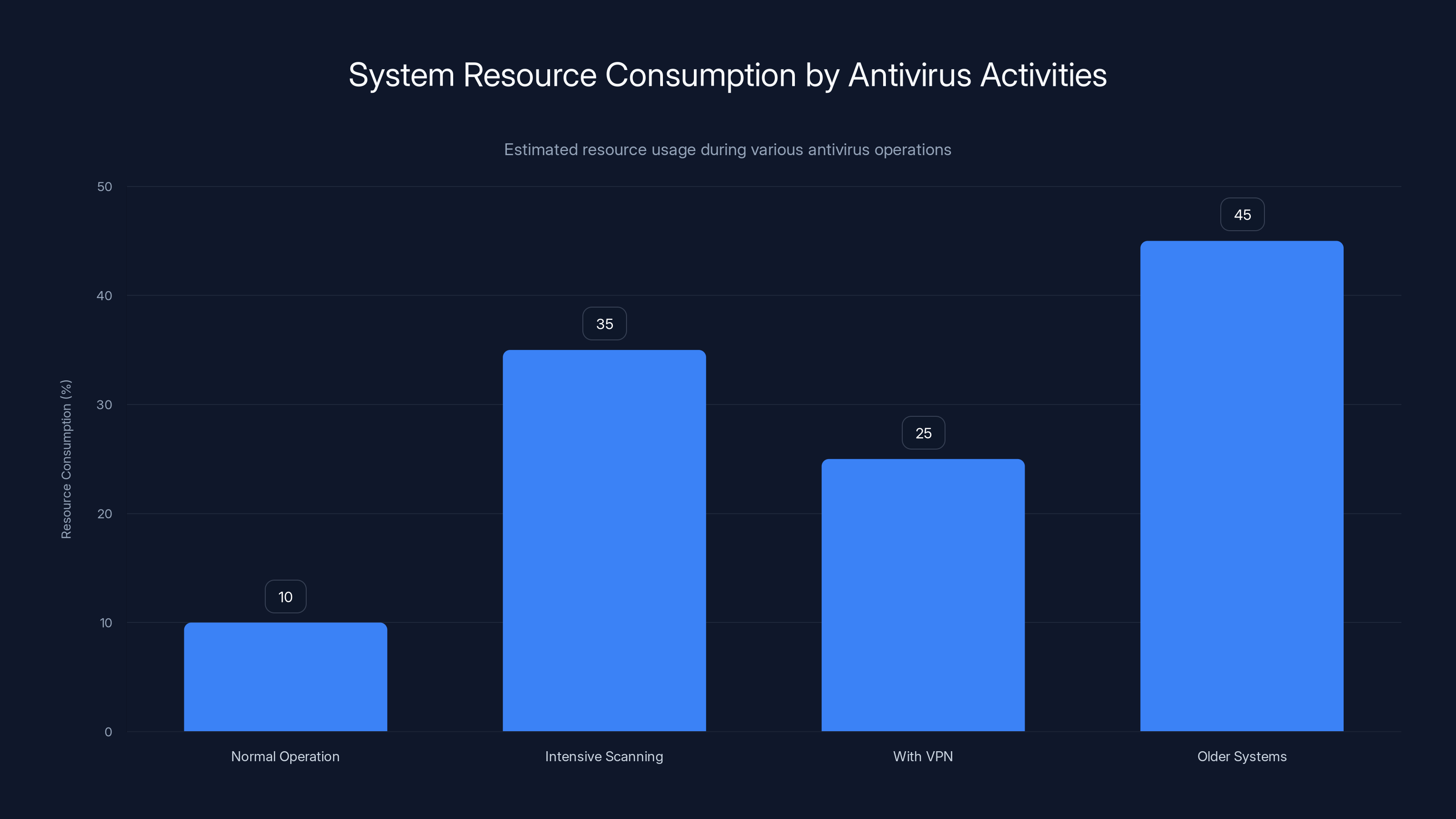
Antivirus activities typically consume 10% of resources during normal operations, peaking at 35% during intensive scans. VPN usage adds to this, especially on older systems. Estimated data.
Pricing and Subscription Models
Integration with IPVanish Subscription Plans
Threat Protection Pro remains available exclusively to existing IPVanish VPN subscribers. Rather than separate pricing, the feature currently exists as a beta addition to standard IPVanish subscription plans. This integration approach differs from traditional antivirus pricing, where you purchase protection separately.
IPVanish offers VPN subscriptions at various price points depending on commitment length. Monthly plans cost approximately
The pricing strategy suggests IPVanish intends to maintain Threat Protection Pro as included functionality for all subscribers once the feature reaches general availability, rather than segmenting users into "basic" and "pro" tiers. This approach differs from competitors like Surfshark, which offers antivirus as a paid add-on to standard VPN subscriptions.
Comparison to Standalone Antivirus Costs
Standalone antivirus software typically costs between
A user combining IPVanish VPN (
For users who didn't previously subscribe to either VPN or antivirus services, Threat Protection Pro bundling provides compelling value. For users already paying for both services separately, the integration reduces redundant spending. However, users highly invested in specific antivirus platforms might prefer maintaining their existing solution rather than switching antivirus engines.
Future Pricing Expectations
IPVanish has not announced pricing changes related to Threat Protection Pro's transition from beta to general availability. However, historical precedent suggests several potential scenarios. The company might maintain Threat Protection Pro as included functionality, or introduce tiered subscriptions where basic plans exclude antivirus while premium plans include it. Alternatively, IPVanish might add Threat Protection Pro as a paid $3-5 monthly add-on.
The beta period provides valuable market feedback for making these decisions. If user adoption proves enthusiastic and technical performance meets standards, inclusion in all plans becomes more likely. If integration challenges or user dissatisfaction emerge, the company might restrict availability to higher-tier subscriptions or offer it as optional premium functionality.
Installation, Setup, and User Experience
Beta Program Enrollment and System Requirements
Enrolling in the Threat Protection Pro beta requires an active IPVanish account on Windows devices. The process theoretically remains straightforward—enabling the beta feature within the IPVanish client and allowing the antivirus component to download and install. However, beta software frequently presents unexpected complications during installation, including compatibility issues with certain Windows versions, driver conflicts, or system configuration problems.
Minimum system requirements likely include Windows 10 or later, though specific processor, RAM, and storage specifications have not been publicly detailed. Systems with 4GB RAM or less might experience performance degradation with antivirus and VPN software running simultaneously. Users with exceptionally modern hardware should encounter minimal performance impact.
The installation process should detect and prevent conflicts with existing antivirus software. Running multiple antivirus programs simultaneously creates conflicts where each attempts to control the same system resources, typically resulting in one overriding the other or both becoming unstable. IPVanish likely includes checks to prevent users from accidentally enabling Threat Protection Pro while another antivirus application runs.
Dashboard and Reporting Interface
User experience depends heavily on how effectively IPVanish presents antivirus information within its VPN client interface. The challenge involves showing antivirus status and recent activity without overwhelming users unfamiliar with antivirus terminology or overly complex security metrics. Effective design presents threat information clearly while enabling power users to access detailed technical data.
The interface should display real-time protection status—indicating whether active scanning is running, whether recent threats were detected, and what quarantined items await review. Recent activity logs should show scanning history, detected threats, and remediation actions taken. For users prioritizing simplicity, a basic dashboard showing "protected" versus "at risk" status suffices. Advanced users require access to detailed threat analysis, file hashing, and technical metadata.
Notification management becomes critical to avoid alert fatigue. Excessive notifications distract users and reduce trust in security systems—users learn to ignore routine alerts and might miss genuinely important warnings. Threat Protection Pro should prioritize notifications around confirmed threats and critical actions requiring user decision-making, while suppressing routine scanning activity notifications.
Configuration and Customization Options
Users require flexibility in configuring antivirus behavior to match their threat tolerance and operational preferences. Critical configuration decisions include scanning frequency (continuous real-time scanning versus scheduled scans), which file types to scan (scanning all files versus targeting only executable types), and quarantine policies (automatic deletion of confirmed threats versus manual review).
Advanced users should have granular control over detection sensitivity, with the ability to adjust heuristic threshold settings, enable or disable behavioral monitoring, and customize which threat categories trigger alerts. White-listing functionality allows users to trust specific programs or file locations if they generate false positives. Experienced security professionals might need to disable certain scans when running sensitive operations or analyzing untrusted files intentionally.
Configuration options must balance flexibility with security. Overly conservative defaults that allow easy disabling of all protections compromise security. Conversely, overly aggressive defaults with limited customization frustrate power users and create support burdens as users struggle with legitimate functionality flagged as threats.
Performance Impact and System Resource Consumption
CPU and Memory Overhead Analysis
Real-time antivirus scanning inherently consumes system resources. Every file accessed by your operating system—whether from disk reads, downloads, or program installations—must be scanned, requiring CPU cycles and memory to maintain the scan engine and threat databases. The magnitude of this overhead depends on scanning implementation efficiency and hardware capacity.
On modern multi-core processors with adequate RAM, antivirus overhead typically ranges from 5-15% of available system resources during normal operation, with peaks reaching 30-40% during intensive scanning activities like system backups or complete disk scans. Older systems or those with limited resources might experience more noticeable performance degradation.
The combined overhead of VPN encryption plus antivirus scanning potentially reaches 20-30% of system resources on capable hardware, substantially increasing on resource-constrained systems. Users running demanding applications like video editing, 3D rendering, or virtual machines might notice reduced responsiveness with both services active.
IPVanish can minimize overhead through optimization efforts: implementing efficient scanning algorithms, leveraging multi-core processors effectively, using intelligent caching to avoid rescanning unchanged files, and employing background processing to minimize foreground impact. The extent to which Threat Protection Pro achieves these optimizations will significantly impact user satisfaction.
Disk I/O and Storage Impact
Beyond CPU and memory, antivirus operations impact disk input/output performance. Real-time scanning requires reading file contents from disk to compare against threat signatures and heuristic patterns. During periods of intensive disk activity—like large file downloads, software installations, or backup operations—antivirus scanning can substantially increase disk I/O latency, making these operations noticeably slower.
Storage capacity requirements for Threat Protection Pro include maintaining signature databases and quarantine areas. Modern malware signatures require approximately 500MB to several gigabytes of storage depending on detection comprehensiveness. Quarantine areas for storing suspected malware require additional space, scaling with how many threats are encountered.
Users on systems with solid-state drives (SSDs) experience less performance impact from disk operations than users with traditional mechanical drives (HDDs), as SSDs excel at the random-access patterns typical of antivirus scanning. Users with mechanical drives might notice more pronounced performance degradation during antivirus operations.
Real-World Performance Testing Methodology
Accurate performance assessment requires systematic testing across diverse scenarios. Controlled testing should measure performance baseline without Threat Protection Pro active, then with protection enabled, comparing metrics including: file copy speeds, application launch times, system boot times, file download speeds, and system responsiveness during typical operations.
Testing should encompass diverse hardware configurations: high-end systems with current-generation processors and abundant RAM, mid-range systems representative of most users, and older systems with limited resources. Results on lower-end hardware matter significantly because users with older computers are often least able to tolerate performance degradation.
Beta testers should document real-world experiences using Threat Protection Pro across actual workflows. Anecdotal reports about system responsiveness, application performance, and overall user experience provide valuable perspective complementing benchmark testing. Issues appearing only under specific usage patterns—like exceptionally high disk activity or specific software combinations—might emerge through real-world testing.

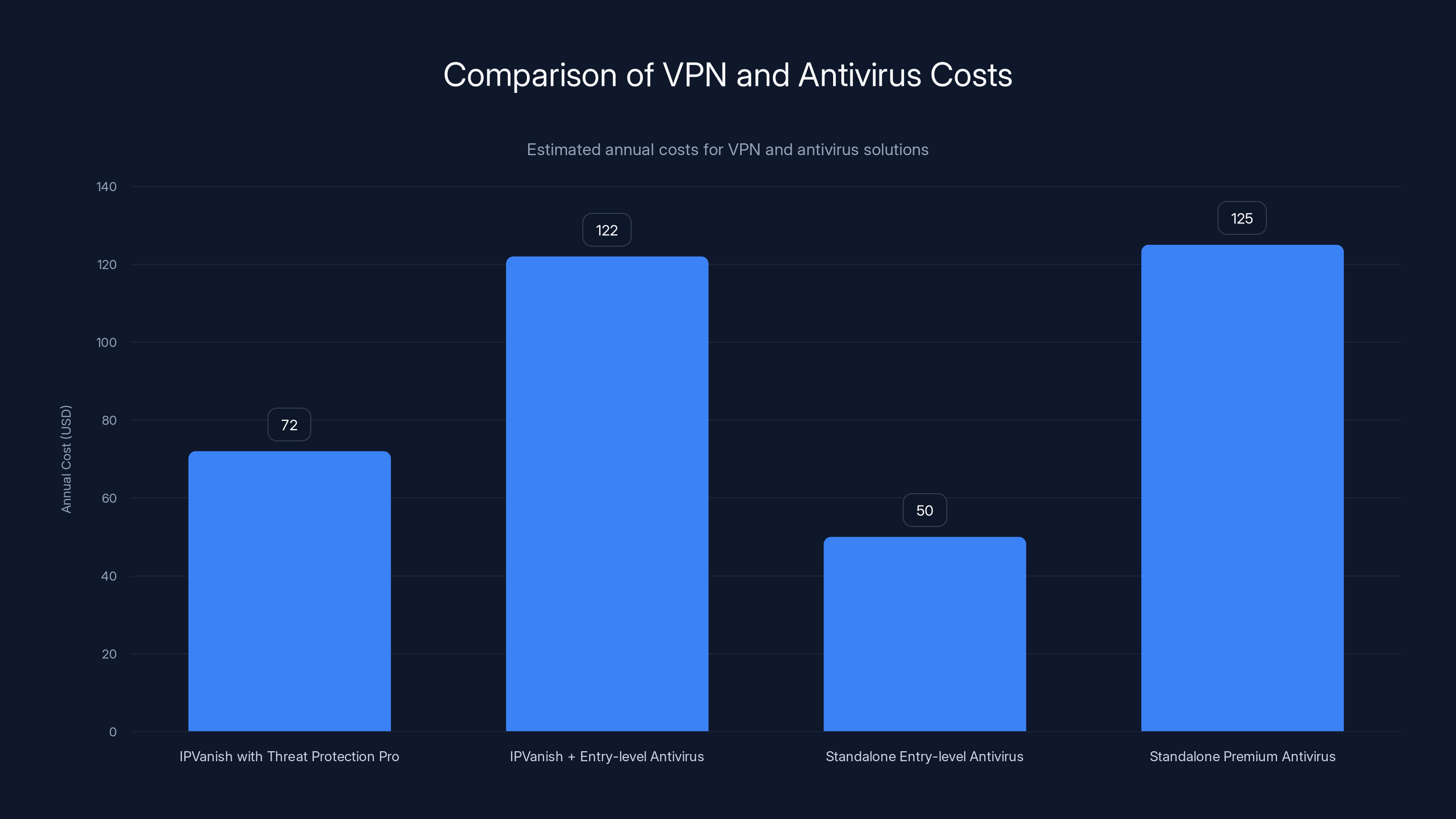
IPVanish's bundling of Threat Protection Pro with its VPN subscription offers significant cost savings compared to purchasing standalone antivirus solutions. Estimated data.
Security Effectiveness and Threat Detection Rates
Independent Testing and Certification Results
The credibility of antivirus systems depends significantly on independent testing by respected organizations. AV-TEST Institute, a leading independent testing organization, evaluates antivirus solutions through comprehensive testing including: detection rates on known malware samples, false positive rates on clean software, and protection efficacy against zero-day exploits. Virus Total provides another testing resource, allowing users to submit files for scanning by multiple antivirus engines simultaneously.
VIPRE's antivirus engine has achieved respectable results in independent testing, typically demonstrating 95-99% detection rates on malware samples while maintaining relatively low false positive rates. However, these metrics represent VIPRE's performance as standalone antivirus, not integrated within IPVanish Threat Protection Pro. The integration might impact detection rates either positively (through enhanced coordination with network-level protection) or negatively (through performance optimizations that reduce scanning thoroughness).
IPVanish should seek independent certification for Threat Protection Pro once the feature reaches general availability, providing objective validation of detection efficacy. Until such testing occurs, users must rely on beta user reports and VIPRE's underlying technology reputation.
Zero-Day and Advanced Threat Protection
Advanced persistent threats (APTs) and zero-day exploits represent the most challenging security problems. Zero-day attacks exploit previously unknown vulnerabilities, making signature-based detection impossible. Heuristic and behavioral analysis provide the primary defenses against zero-days, identifying unusual system activity patterns that suggest exploitation.
VIPRE's behavioral monitoring capability provides some zero-day protection, but sophisticated attackers continually develop techniques to evade behavioral detection. State-sponsored actors and advanced criminal organizations employ techniques designed specifically to bypass antivirus behavioral monitoring. Users seeking cutting-edge protection against advanced threats require additional measures beyond traditional antivirus: keeping systems meticulously patched, limiting administrative account usage, maintaining network segmentation, and employing threat intelligence monitoring.
Threat Protection Pro should be evaluated as part of a comprehensive security approach, not as standalone protection against advanced threats. The combination of network-level protection (via VPN), endpoint-level detection (via antivirus), behavioral monitoring, and proactive security practices creates robust defense. No single tool provides complete protection against sophisticated attackers.
Protection Against Emerging Threat Categories
Malware threat categories continuously evolve. Cryptominers that silently consume system resources, supply chain attacks that compromise legitimate software, and fileless malware that exists only in system memory rather than as files all represent emerging threat categories. VIPRE's detection capabilities must evolve to address these emerging threats effectively.
Cryptomalware detection requires identifying suspicious code execution and resource consumption patterns. Fileless malware detection requires monitoring memory and system call patterns that might escape disk-based antivirus scanning. Supply chain attacks present particular challenges because compromised legitimate software defeats traditional signature-based detection.
IPVanish must monitor VIPRE's evolution in addressing emerging threats, ensuring that Threat Protection Pro remains effective as the threat landscape changes. Regular updates and new detection methodologies will be essential for maintaining protection currency.
Comparison to Traditional VPN-Only Approach
Limitations of VPN-Only Security Models
Traditional VPNs encrypt internet traffic and mask IP addresses, providing important network-level protection. However, this protection has inherent limitations. A VPN cannot detect malware already present on your system. A VPN cannot prevent you from downloading malware from legitimate websites. A VPN cannot block malware residing in files you access locally. A VPN provides no protection against phishing attacks targeting credentials. The encrypted tunnel a VPN creates protects data in transit but offers no defense against data already compromised through malware infection.
Users who rely exclusively on VPN protection while neglecting endpoint-level antivirus create significant security gaps. A well-maintained VPN service provides excellent privacy by preventing ISPs from monitoring your traffic and blocking geographic restrictions through location spoofing. It provides security against network-level eavesdropping and man-in-the-middle attacks. But it provides no defense against the vast majority of malware distribution and infection vectors.
Benefits of Integrated Protection
Integrating antivirus capabilities directly within VPN clients creates several advantages over managing separate tools. Unified configuration and monitoring means you manage security through a single interface rather than coordinating multiple applications. Unified updates ensure both VPN and antivirus components remain current without managing separate update schedules. Potential performance advantages through optimized coordination—the VPN might provide faster inspection of network traffic, and the antivirus might prioritize scanning of VPN-downloaded files.
Psychologically, integration encourages more comprehensive security adoption. Users who might avoid installing separate antivirus software if uncertain about benefits or performance impact might embrace integrated protection included in their existing VPN subscription. This expanded protection adoption improves security ecosystem health by increasing the proportion of systems with endpoint-level malware defense.
When Separate Tools Might Remain Preferable
Despite integration benefits, scenarios exist where separate VPN and antivirus tools might remain preferable. Users heavily invested in specific antivirus platforms—perhaps for corporate compatibility or existing subscriptions—might prefer maintaining their established tool rather than switching. Users requiring antivirus features not present in Threat Protection Pro—like advanced forensics, behavioral analysis reporting, or specific enterprise features—might need specialized solutions.
Users managing macOS or Linux systems cannot use Threat Protection Pro despite having active IPVanish subscriptions, necessitating alternative antivirus solutions for those platforms. Users requiring comprehensive multi-platform protection across Windows, Mac, Linux, iOS, and Android need to carefully evaluate whether Threat Protection Pro's Windows-only availability fits their needs or creates problematic coverage gaps.
Users with exceptionally low-specification hardware might find that separate VPN and antivirus tools, if optimized appropriately, deliver better overall performance than integrated solutions. Specialized antivirus tools sometimes provide better optimization for specific hardware configurations than do integrated solutions attempting to serve diverse hardware.

Alternative Solutions and Competitive Landscape
Comprehensive Antivirus Solutions (Standalone)
The antivirus market offers numerous standalone solutions providing comprehensive protection independent of VPN services. Bitdefender Total Security combines advanced threat detection with excellent performance characteristics, typically available for $40-60 annually. The platform excels at balancing detection capability with system resource efficiency, making it suitable for diverse hardware configurations. Bitdefender's detection rates consistently rank among industry leaders, particularly for advanced threats.
Norton 360 Deluxe provides similarly comprehensive protection with the advantage of strong brand recognition and substantial marketing investment. Norton offerings typically cost $50-80 annually and include features like identity theft monitoring and social media monitoring alongside antivirus protection. The platform maintains reasonable system performance though some users report heavier resource consumption than competitors.
Kaspersky Total Security leverages decades of threat intelligence development, particularly strong against advanced persistent threats and sophisticated malware. Pricing reaches $80-100 annually, and availability varies by region due to geopolitical considerations. Kaspersky's threat database represents one of the largest in the industry, contributing to particularly strong detection rates.
Avast One offers a family-oriented suite including antivirus, VPN, password management, and additional security features at $60-80 annually. The multi-tool approach appeals to users wanting comprehensive security in one platform, though specialized tools sometimes outperform integrated solutions in specific functions.
VPN Services with Integrated Antivirus
IPVanish represents one approach to integrating antivirus within VPN services, but other providers offer similar functionality. Surfshark provides optional antivirus capability as a paid add-on (
Norton VPN, part of Norton 360's ecosystem, integrates VPN functionality directly within Norton's comprehensive antivirus suites. Users purchasing Norton protection automatically receive VPN access, creating integration more complete than IPVanish's separate VPN client approach. This integration appeals to users prioritizing unified security management.
Bitdefender Premium VPN similarly integrates VPN functionality within Bitdefender Premium subscriptions, though the VPN represents a secondary feature rather than Bitdefender's primary offering. This contrasts with IPVanish's primary VPN focus with antivirus as an added feature.
Trend Micro Maximum Security includes VPN functionality alongside comprehensive antivirus protection in a family-oriented subscription available for approximately $60-80 annually across Windows, Mac, iOS, and Android. The multi-platform approach appeals to users managing diverse device ecosystems.
Lightweight Antivirus for Performance-Sensitive Systems
Users prioritizing performance might prefer lightweight antivirus solutions accepting less comprehensive protection in exchange for minimal system overhead. Windows Defender/Microsoft Defender represents the built-in Windows antivirus that comes free with modern Windows installations. While basic compared to premium solutions, Windows Defender provides competent protection for most users and performs well on resource-constrained systems.
Malwarebytes focuses specifically on malware detection and removal, complementing Windows Defender's capabilities while adding specialized expertise. Many users employ Malwarebytes alongside lighter tools like Windows Defender, creating effective layered protection with minimal overhead. The approach costs approximately
AVG offers lightweight antivirus without excessive system requirements, suitable for older hardware. Detection capabilities are decent though not class-leading, and the platform includes various additional security tools. Annual subscriptions typically cost $30-50.
Enterprise and Advanced Security Suites
For users seeking enterprise-grade protection capabilities, solutions like CrowdStrike Falcon and SentinelOne provide sophisticated endpoint detection and response (EDR) capabilities beyond traditional antivirus. These platforms employ advanced behavioral analysis and threat intelligence monitoring but typically cost $500+ annually and target small businesses rather than individual consumers.
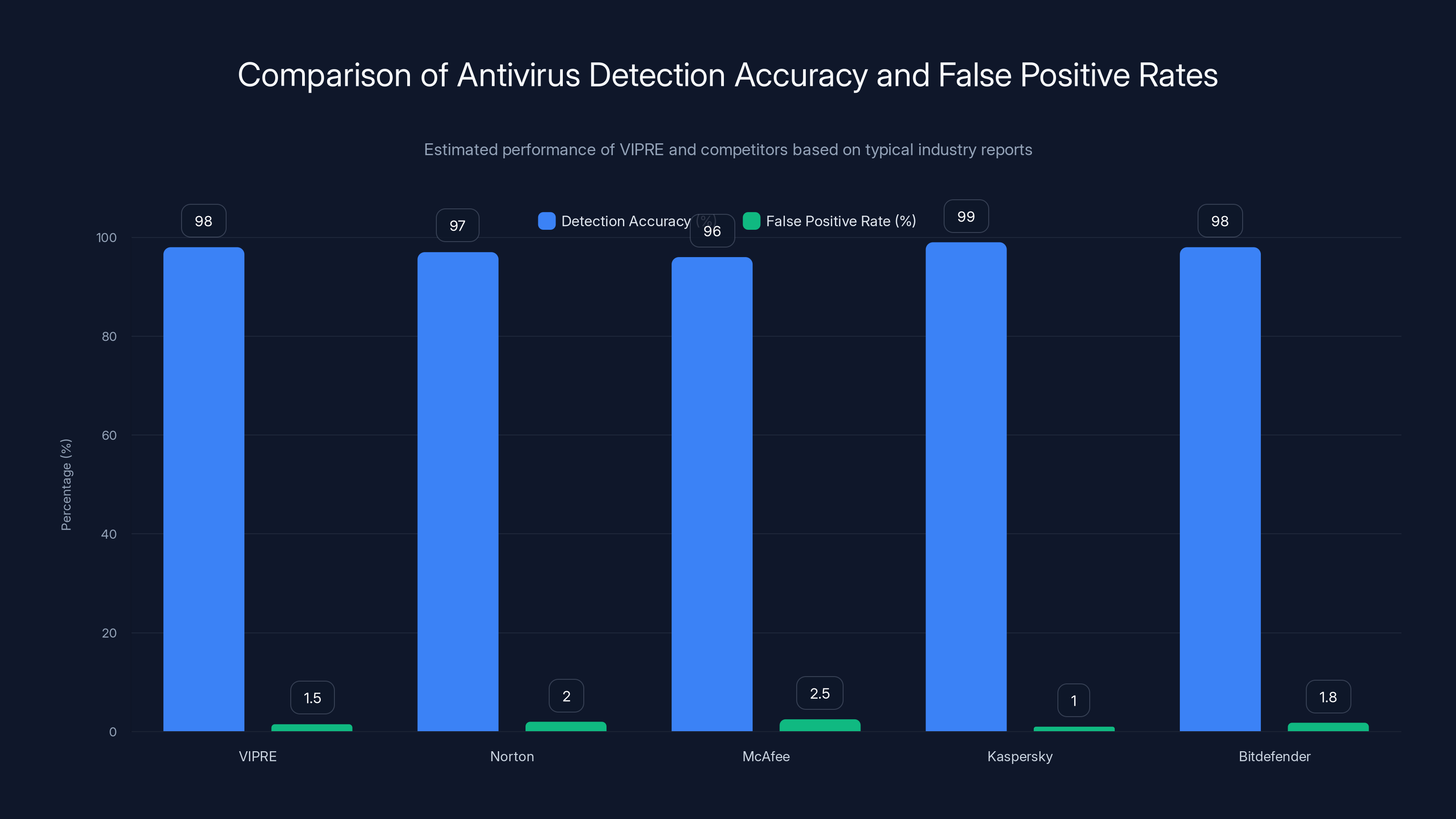
VIPRE demonstrates strong detection accuracy with a low false positive rate, making it a competitive choice among antivirus solutions. Estimated data based on typical industry performance.
Use Cases and Ideal User Profiles
High-Risk Users Requiring Comprehensive Protection
Users managing sensitive information—medical professionals, lawyers, financial advisors, or journalists—benefit substantially from integrated protection. The combination of VPN encryption and antivirus protection creates layered defense appropriate for professionals handling confidential data. These users typically pay for both VPN and antivirus separately anyway, making integration cost-effective.
Users in high-threat environments face persistent attack efforts from criminals, nation-state actors, or competitors. Financial executives managing significant assets, political activists in oppressive regimes, and business leaders protecting trade secrets all benefit from comprehensive protection. Threat Protection Pro provides practical defense as part of their broader security architecture.
Users conducting business in countries with significant cybercrime activity or compromised network infrastructure gain particular value from VPN encryption preventing ISP monitoring and malware inspection catching locally-distributed threats. Travelers conducting financial transactions from unfamiliar networks benefit from both components protecting their sensitive data and device integrity.
Privacy-Conscious Users Seeking Privacy Plus Protection
Many VPN users prioritize privacy above all else—preventing ISP monitoring, blocking geographic tracking, and avoiding data collection. These users often hold broader security concerns, recognizing that comprehensive protection requires both privacy and malware defense. The bundled Threat Protection Pro appeals to these users' holistic security philosophy without requiring separate tool management.
Users in countries with pervasive surveillance or content filtering often prioritize VPN services to circumvent censorship and maintain privacy. These same users face significant malware risks from compromised local networks and government-sponsored malware distribution. Integrated protection addressing both privacy and security needs suits their risk profiles effectively.
Budget-Conscious Users Seeking Economical Protection
Cost-effective security appeals to users with limited budgets, including students, retirees, and those in developing economies. The bundled approach—obtaining VPN and antivirus together at lower cost than separate subscriptions—provides comprehensive protection without stretching limited budgets. IPVanish's relatively low subscription costs combined with included antivirus create attractive value.
Small business owners managing multiple devices with limited IT budgets benefit from consolidated pricing. Rather than purchasing VPN subscriptions and antivirus licenses separately for each device, integrated solutions reduce total cost of ownership significantly.
When Threat Protection Pro May Not Be Ideal
Users with existing antivirus subscriptions through corporate policies or established relationships might not benefit from switching. Enterprise users with centralized security management requirements need tools providing administrative capabilities Threat Protection Pro might lack. Users managing exclusively macOS, Linux, or mobile devices cannot utilize the Windows-only feature, making alternative solutions necessary.
Users requiring specialized antivirus capabilities like forensic analysis, detailed behavioral reporting, or specific threat targeting might require dedicated antivirus tools. Advanced users needing granular control over detection tuning might find Threat Protection Pro's interface insufficiently detailed for their requirements.
Future Roadmap and Evolution Considerations
Anticipated Platform Expansion
IPVanish has indicated intentions to expand Threat Protection Pro beyond Windows to macOS, Linux, iOS, and Android platforms. This multi-platform expansion would transform the offering from a partial solution to comprehensive protection across typical user device ecosystems. Timeline and implementation approach remain unannounced, but historical precedent suggests platform expansion typically spans 6-18 months as development teams address platform-specific challenges.
MacOS implementation presents moderate complexity, as VIPRE technology must adapt to macOS architecture differences. Linux support might utilize different antivirus technology depending on licensing availability and community expectations around open-source tools. Mobile platform support—iOS and Android—represents the greatest challenge given platform restrictions around system access that antivirus engines typically require.
Expanded platform support will determine whether Threat Protection Pro becomes viable for users managing diverse device ecosystems or remains a Windows-specific supplement to other antivirus solutions.
Feature Enhancement Possibilities
Future iterations of Threat Protection Pro might incorporate additional security capabilities beyond traditional malware detection. Password management integration could check passwords against compromised credential databases. Parental controls could restrict access to inappropriate websites for family accounts. File encryption could protect sensitive files with password protection. Network monitoring could identify suspicious outbound connections from malware attempting to communicate with command-and-control servers.
Machine learning capabilities could enable more sophisticated threat detection by analyzing suspicious behavioral patterns even when exact signature matches don't exist. Integration with threat intelligence platforms could provide users detailed information about threats encountered and attack attribution.
These enhancements would position Threat Protection Pro as more comprehensive security solution rather than strictly antivirus feature, potentially justifying premium pricing if introduced as paid tier.
Potential Technology Evolution
The partnership between IPVanish and VIPRE might evolve as threat landscapes change. VIPRE could transition to entirely cloud-based threat detection, improving detection speed but introducing privacy considerations around analyzing files in the cloud. Alternatively, VIPRE might embrace machine learning more extensively, enabling detection of emerging threats before signature-based approaches identify them.
IPVanish might eventually develop its own antivirus technology rather than licensing VIPRE, providing greater control and potential product differentiation. Alternatively, the company might license different antivirus engines for different geographic markets, allowing localized threat targeting.
Implementation Best Practices and Optimization
Preparing Systems for Threat Protection Pro Installation
Before enabling Threat Protection Pro, ensure your Windows system fully updates—both operating system and all installed applications. Outdated systems with unpatched vulnerabilities present higher malware infection risks, but more importantly, system updates sometimes include security patches that antivirus integration depends on. Incompatibility issues arise more frequently when systems lack current patches.
Disable any existing antivirus software before installing Threat Protection Pro to prevent resource conflicts and detection conflicts. Most modern antivirus solutions provide uninstall utilities ensuring complete removal. Reboot your system after antivirus uninstallation to clear any lingering components from system memory.
Ensure at least 2-5GB of available disk space for Threat Protection Pro installation and signature database maintenance. Monitor available disk space regularly as quarantined malware accumulates—insufficient space could cause antivirus failures when disk becomes critically full.
Optimizing Performance and Detection
After installation, configure Threat Protection Pro's scanning schedule to avoid times when you require maximum system performance. If system performance is critical during business hours, schedule intensive scans for overnight periods when your computer runs idle. Real-time scanning continues regardless of schedule configuration, but scheduled deep scans can be deferred.
White-list critical applications in Threat Protection Pro's configuration if false positives cause legitimate software blocking. However, approach white-listing cautiously—white-listing reduces security by removing scanning from trust-listed applications. Only white-list applications you absolutely trust and have verified haven't been compromised.
Keep Threat Protection Pro enabled at all times. Disabling protection temporarily might seem convenient when installing software or performing system maintenance, but re-enabling protection afterward is easily forgotten. The brief period of unprotection represents when malware infection risks peak.
Monitoring and Maintenance
Review quarantine items regularly to identify patterns indicating malware sources or attack vectors. If all quarantined items trace to downloads from specific websites or email sources, investigate whether those sources represent compromised sites or whether your browsing or email habits expose you to unusually risky content.
Monitor Threat Protection Pro's update history to ensure new signatures download regularly. If signature updates stall—appearing days old when fresh updates should arrive daily—contact IPVanish support as update mechanism failures indicate protection currency problems.
Monitor system resource consumption to identify whether Threat Protection Pro's overhead remains acceptable. If system performance deteriorates substantially after enabling the feature, troubleshooting might identify specific applications, files, or activities triggering excessive scanning overhead.
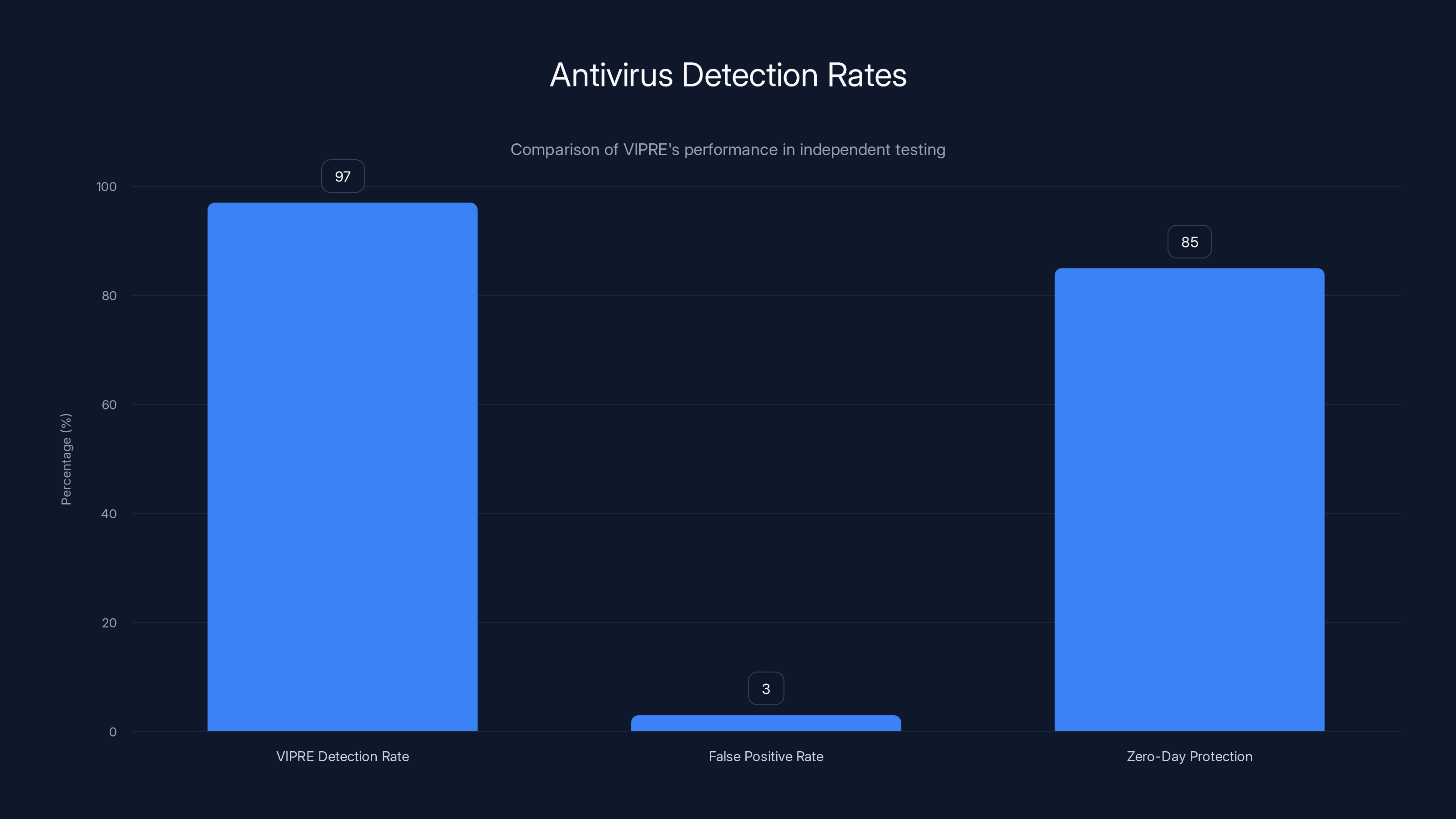
VIPRE demonstrates high detection rates of 95-99% with low false positives, but zero-day protection is less certain. Estimated data based on typical performance.
Migration Strategies from Other Antivirus Solutions
Transitioning from Established Antivirus Platforms
Users currently employing antivirus solutions like Kaspersky, Norton, or Bitdefender considering a switch to Threat Protection Pro should approach migration systematically. Document your current antivirus configuration, particularly white-lists, exclusions, and custom scanning settings. While Threat Protection Pro likely cannot directly import these configurations, understanding your current setup prevents functionality gaps during transition.
Execute the transition during a low-risk period when you won't need intensive antivirus performance—not during major software installations or when downloading critical files. Uninstall your current antivirus completely (following the provider's documented uninstall procedures), reboot, then enable Threat Protection Pro and allow its initial database download and scanning cycle to complete.
During the first week of using Threat Protection Pro, monitor its behavior closely. If false positives emerge blocking legitimate applications, document the specific applications and files to configure appropriate white-listing. If detection patterns differ substantially from your previous solution, investigate whether the change reflects actual differences in detection capability or merely different reporting formats.
Parallel Testing Before Full Migration
Risk-averse users might operate Threat Protection Pro in parallel with their existing antivirus briefly, allowing performance and detection validation before full migration. This approach requires careful configuration to prevent the antivirus systems from conflicting. Run one antivirus in real-time mode and disable real-time scanning in the other, using the second exclusively for on-demand scans to evaluate detection rates.
Parallel operation provides reassurance that Threat Protection Pro detects threats your current antivirus identifies, reducing concern about detection gaps during migration. However, parallel operation doubles antivirus overhead and consumes twice the disk space for virus definitions, making extended parallel operation impractical.
Rollback Procedures if Issues Arise
If Threat Protection Pro proves incompatible with your specific system configuration or usage patterns, rollback procedures should restore previous antivirus functionality. Document your current antivirus license key and installer before transitioning. If you need to rollback, disable Threat Protection Pro, uninstall it, and reinstall your previous antivirus using preserved installer files and license information.
Maintaining a system restore point before enabling Threat Protection Pro provides additional safety net. If installation introduces system stability issues, system restore could return your computer to a known-good state more quickly than troubleshooting.
Expert Recommendations and Best Practices
When Threat Protection Pro Represents the Right Choice
Threat Protection Pro makes sense for users who: (1) already subscribe to IPVanish and want to consolidate security tools into a single subscription, (2) prioritize simplicity and integrated management over specialized feature depth, (3) use primarily Windows devices and can accept platform limitations, (4) seek to reduce security spending by combining VPN and antivirus through unified subscription, and (5) trust VIPRE's detection capabilities and are comfortable with that technology choice.
Users fitting these profiles likely benefit from Threat Protection Pro's integration and bundled pricing. The feature addresses their core security needs while simplifying management and reducing costs compared to separate subscriptions.
When Separate Tools Remain Preferable
Users should maintain separate VPN and antivirus solutions if: (1) they require multi-platform protection and cannot accept Windows-only coverage, (2) they use enterprise antivirus solutions required by corporate policies, (3) they need specialized antivirus capabilities like forensic analysis beyond Threat Protection Pro's scope, (4) they prioritize performance and need to optimize VPN and antivirus separately for their specific hardware, or (5) they distrust VIPRE technology or prefer alternative detection engines.
These users face a choice between accepting partial protection gaps (using Threat Protection Pro on Windows while maintaining separate antivirus on other platforms) or maintaining comprehensive separate tool strategies. Most typically choose the latter for consistency and compatibility.
Future Reassessment Timeline
Users should reassess Threat Protection Pro's suitability periodically as the product evolves. Current assessment focuses on beta functionality on Windows alone. Once the feature reaches general availability and expands to additional platforms, reassessment might conclude differently. Performance improvements in subsequent versions might address concerns that emerged during beta testing. Pricing changes or feature additions might alter the value proposition.
Reassess annually or whenever making antivirus subscription renewal decisions, ensuring Threat Protection Pro remains your optimal choice given evolving needs and competitive offerings.

Security Best Practices Beyond Threat Protection Pro
Layered Defense Architecture
No single security tool provides complete protection, regardless of capabilities. Comprehensive security requires multiple overlapping defensive layers addressing different threat vectors. Threat Protection Pro addresses malware endpoint detection but doesn't prevent phishing attacks, protect against weak password compromise, or defend against social engineering. Implementing comprehensive security requires:
Authentication Security: Enable multi-factor authentication on all critical accounts (email, banking, social media). Weak passwords remain one of the most exploited security vulnerabilities, often enabling attacks faster than any technical defense.
Backup Strategy: Maintain offline backups of critical data protected against ransomware encryption. If malware somehow encrypts your files despite Threat Protection Pro, backups enable recovery without paying ransom.
System Patching: Keep Windows, browsers, plugins, and applications fully updated. Unpatched vulnerabilities remain the primary malware installation vector. Threat Protection Pro cannot protect against exploitation of vulnerabilities you haven't patched.
Cautious Browsing: Avoid visiting suspicious websites, opening email attachments from unknown senders, or downloading files from untrusted sources. The most effective security layer remains avoiding malware entirely through cautious behavior.
Network Segmentation: Isolate critical devices or accounts from general-purpose computing systems. If one device becomes infected, segmentation prevents malware spreading to sensitive systems.
User Education and Threat Awareness
Technology provides important protection, but users represent the largest vulnerability in any security architecture. Understanding social engineering tactics, recognizing phishing attempts, and maintaining security consciousness prevent many attacks before malware even enters your system.
Common attack vectors targeting users include: phishing emails impersonating trusted organizations, fake software updates delivering malware, misleading pop-ups claiming virus infections to trick users into downloading malicious tools, and social engineering gaining authorization to bypass security systems. Awareness of these tactics prevents many successful attacks.
Stay informed about current threats and attack trends. Technology news sources regularly report new threats and attack methodologies. Understanding emerging risks helps you adjust behavior—for example, additional caution when major software vulnerabilities are disclosed publicly.
Considerations for Different User Demographics
Small Business Owners and Entrepreneurs
Small business owners managing employee devices and company data face unique security challenges. Budget constraints often prevent sophisticated enterprise security infrastructure, but increasing business reliance on data requires protection. Threat Protection Pro's bundled approach provides economical protection for multiple employee devices through central IPVanish account management.
Small businesses benefit from integrated protection reducing complexity—employees need not manage separate VPN and antivirus subscriptions, simplifying security compliance monitoring. However, central management capabilities required for multiple employees might exceed what Threat Protection Pro's consumer-focused interface provides.
Remote Workers and Travel-Heavy Professionals
Remote workers often connect from residential networks, coffee shops, and hotels offering compromised connectivity security. VPN encryption protecting their connections combines perfectly with Threat Protection Pro's malware detection. These professionals typically handle sensitive information making comprehensive protection valuable.
Travel-heavy professionals connecting from diverse networks face unusual malware exposure from compromised public Wi-Fi and unfamiliar networks. The combination of VPN privacy protection and Threat Protection Pro's malware detection creates appropriate security for frequent travelers.
Students and Budget-Conscious Users
Students often operate on limited budgets, making the bundled approach economical compared to separate subscriptions. However, students frequently use multiple devices across Windows, Mac, and mobile platforms. Threat Protection Pro's Windows-only availability creates coverage gaps that might necessitate alternative solutions providing cross-platform protection despite higher cost.
Senior Citizens and Non-Technical Users
Less technically sophisticated users benefit from integrated protection reducing complexity. Rather than configuring separate VPN and antivirus tools, Threat Protection Pro provides all-in-one protection from a single interface. The simplified approach reduces the likelihood of misconfiguration or forgotten security measures.
However, users with limited technical knowledge might struggle with troubleshooting if Threat Protection Pro causes compatibility issues or false positive problems. Clear documentation and accessible support become essential for this demographic.
Competitive Positioning and Market Differentiation
IPVanish's Strategic Positioning
IPVanish competes in a crowded VPN market where price differentiation has compressed and feature offerings increasingly converge. Major competitors like ExpressVPN, NordVPN, and Surfshark all offer similar core VPN functionality at comparable pricing. By adding Threat Protection Pro, IPVanish differentiates through integrated security features competitors don't yet offer comprehensively.
The strategic intent appears clear: transform IPVanish from a pure VPN provider into a broader security solution, justifying subscription retention and reducing churn as customers recognize value beyond simple encryption. Users comparing IPVanish to competitor VPNs might decide that integrated malware protection justifies the choice despite potentially higher costs.
This positioning recalls the security suites approach utilized by Norton, McAfee, and others—bundling multiple security functions to create value greater than individual components. Whether Threat Protection Pro achieves similar market success depends on execution quality, performance optimization, and platform expansion.
Competitive Responses from Other VPN Providers
Competitors will inevitably respond to Threat Protection Pro. Surfshark's existing antivirus add-on positions it well to expand platform coverage or integrate the feature more deeply into core subscriptions. NordVPN has explored security feature expansion but might need new partnerships to match VIPRE integration. ExpressVPN's focus on pure VPN functionality might maintain their niche rather than pursue security bundling.
Alternatively, VPN providers might pursue different differentiation approaches—enhanced privacy features, dedicated IP addresses, specialized servers, or superior performance—rather than competing directly on integrated antivirus. This market segmentation could strengthen overall VPN adoption by offering diverse feature profiles serving different user priorities.
FAQ
What is Threat Protection Pro and how does it differ from standard VPN protection?
Threat Protection Pro is IPVanish's integrated antivirus feature powered by VIPRE antivirus technology. While traditional VPN protection encrypts your internet traffic and masks your IP address, Threat Protection Pro adds endpoint-level malware detection and blocking. This means you receive protection not just for data in transit, but also against malware on your device itself—a capability VPN-only services cannot provide. The integration means you get comprehensive security through a single subscription rather than managing separate VPN and antivirus tools.
How does real-time scanning work in Threat Protection Pro?
Real-time scanning continuously monitors your system for malware threats as they're accessed or executed. When you download files, the system immediately scans them against VIPRE's threat signature database containing known malware patterns. Beyond signature matching, the system employs heuristic analysis to identify suspicious file characteristics and behavioral monitoring to observe how programs interact with your operating system. If threats are detected, they're quarantined before execution, preventing infection and damage.
What are the main benefits of Threat Protection Pro compared to standalone antivirus?
Key benefits include unified management through a single subscription rather than maintaining separate VPN and antivirus tools, cost savings by bundling services together, simplified configuration with both security layers accessible from one interface, and coordinated protection where network-level VPN security complements endpoint-level antivirus detection. Additionally, users avoid the performance overhead and complexity of running multiple security applications simultaneously.
Which operating systems and devices currently support Threat Protection Pro?
As of the announcement, Threat Protection Pro is available exclusively in beta on Windows devices. IPVanish has indicated plans to expand to macOS, Linux, iOS, and Android platforms, but specific timelines have not been announced. This platform limitation represents a significant consideration for users managing multiple operating systems, as you would need alternative antivirus solutions for non-Windows devices while using Threat Protection Pro on Windows.
How does Threat Protection Pro's pricing compare to separate VPN and antivirus subscriptions?
Threat Protection Pro is currently included in IPVanish's standard subscription plans without additional cost during the beta period. IPVanish VPN subscriptions cost approximately
What is VIPRE and why did IPVanish choose it for Threat Protection Pro?
VIPRE is an established antivirus technology with decades of market presence, particularly strong among small businesses and individual consumers. IPVanish selected VIPRE for its reputation combining effective threat detection with relatively lightweight system resource consumption—important when integrated with VPN software that already consumes resources. VIPRE's proven detection capabilities and established track record make it a reliable foundation for Threat Protection Pro rather than IPVanish developing antivirus technology internally.
Can I use Threat Protection Pro alongside my existing antivirus software?
No, you should not run multiple antivirus applications simultaneously. Running two antivirus solutions creates conflicts where each attempts to control system resources, often resulting in instability or both becoming ineffective. You must uninstall your existing antivirus completely before enabling Threat Protection Pro. IPVanish's system should detect and prevent enabling Threat Protection Pro while another antivirus application is active, but manual uninstallation of your previous antivirus is essential for clean operation.
What impact will Threat Protection Pro have on my system performance?
Real-time antivirus scanning inherently consumes system resources including CPU, memory, and disk I/O. On modern systems with current processors and adequate RAM, overhead typically ranges from 5-15% of available resources during normal operation, with peaks reaching 30-40% during intensive scanning. Combined with VPN encryption overhead, total resource consumption might reach 20-30% on capable hardware. Older systems or those with limited resources might experience more noticeable performance degradation. System impact will become clearer as beta testers provide feedback on their specific hardware experiences.
How frequently are Threat Protection Pro's malware signatures updated?
VIPRE maintains continuously updated threat signature databases, with new malware signatures typically deployed multiple times daily as new threats are discovered and analyzed. Threat Protection Pro accesses these updates automatically without requiring manual intervention. However, IPVanish has not published specific update frequency details or latency between malware discovery and signature deployment. Once the feature reaches general availability, more detailed information about update mechanisms should become available.
What happens if Threat Protection Pro detects a threat on my system?
When threats are detected, they are moved to quarantine rather than immediately deleted. Quarantine isolates infected files from your running system where they cannot execute or spread, but keeps them accessible for review. Each quarantined item includes metadata indicating the detection method and threat classification. You can review quarantined items and decide whether to permanently delete, restore, or perform additional analysis. This approach prevents false positives from causing data loss while ensuring genuine threats cannot cause damage.
Is Threat Protection Pro suitable for protecting business and sensitive data?
Threat Protection Pro provides useful protection for business data as part of a comprehensive security strategy. The combination of VPN encryption protecting data in transit and antivirus detecting malware threats provides appropriate defense for many business scenarios. However, sensitive business data handling often requires enterprise-grade security solutions with advanced features like forensic analysis, detailed behavioral reporting, and centralized management capabilities that Threat Protection Pro might not provide. For highly sensitive data or regulated industries, consultation with IT security professionals is recommended to ensure compliance with security requirements.
How do I troubleshoot performance issues if Threat Protection Pro causes system slowdown?
If system performance degrades noticeably after enabling Threat Protection Pro, several troubleshooting steps might help: verify that scanning schedules don't overlap with critical work periods and adjust scheduling if possible, check that white-listing isn't excessively broad (reducing unnecessary scanning of trusted applications), monitor disk space to ensure sufficient room for operations (disk full conditions degrade performance dramatically), verify that background updates complete successfully, and consult IPVanish support if performance issues persist despite optimization attempts. In extreme cases, temporarily disabling real-time scanning to isolate whether it's the culprit might help identify whether the performance issue originates from Threat Protection Pro.
Conclusion: Making the Optimal Security Decision for Your Needs
IPVanish's introduction of Threat Protection Pro represents a meaningful evolution in how VPN providers conceptualize security, moving beyond network-level encryption toward comprehensive endpoint protection. By integrating VIPRE's established antivirus technology directly into the VPN client, IPVanish addresses a legitimate security gap—the fact that traditional VPN services cannot protect you from malware threats despite providing excellent privacy and network-level protection.
The value proposition proves compelling for specific user populations. Users who already subscribe to IPVanish and recognize security gaps in their current setup gain comprehensive protection without additional cost. Users seeking to consolidate security tools and reduce management complexity benefit from unified configuration and monitoring. Users operating primarily on Windows devices with relatively modern hardware should experience acceptable performance with both VPN and antivirus active. Budget-conscious users appreciate the cost savings from combining VPN and antivirus through a single subscription rather than maintaining separate tools and accounts.
However, Threat Protection Pro's current limitations create barriers to universal recommendation. The Windows-only availability excludes users managing macOS, Linux, or mobile devices from accessing integrated protection on those platforms. The beta status introduces uncertainty about stability and final feature set. The lack of independent security testing leaves detection capability and false positive rates unverified. Users deeply invested in specific antivirus platforms or requiring enterprise-grade security management capabilities might discover that specialized alternatives serve their needs better than integration compromises.
The broader security landscape encompasses numerous alternatives, from premium all-in-one suites like Bitdefender Total Security and Norton 360 Deluxe, to specialized antivirus solutions like Kaspersky and AVG, to lightweight options like Windows Defender paired with supplemental tools. The competitive environment remains dynamic, with multiple vendors pursuing integration strategies similar to IPVanish's approach. Users should evaluate Threat Protection Pro within this broader context, comparing not just to VPN-only alternatives but to comprehensive security solutions across the entire market.
Ultimately, optimal security decisions depend on your specific risk profile, device ecosystem, budget constraints, and technical comfort level. Threat Protection Pro deserves serious consideration for Windows-focused users already using or considering IPVanish VPN. The feature's evolution from beta to general availability and multi-platform expansion will determine whether it becomes a significant security platform or remains a niche addition to IPVanish's VPN service.
As you evaluate Threat Protection Pro, maintain realistic expectations about its role within your broader security strategy. No single tool provides complete protection against sophisticated attackers or eliminates all security risks. Threat Protection Pro excels at preventing common malware infections through layered detection while maintaining reasonable system performance. It complements but does not replace fundamental security practices: keeping systems patched, maintaining strong authentication, backing up critical data, and practicing cautious browsing behavior.
Monitor Threat Protection Pro's development closely if you fall within its target market. The beta period provides opportunity to evaluate performance and detection capability on your specific hardware before making long-term commitment. Participate in beta feedback if you enroll, as your experience helps IPVanish refine implementation and identifies issues requiring attention before general rollout.
For readers evaluating whether Threat Protection Pro fits your security needs: assess your current antivirus and VPN setup, honestly evaluate whether you actually maintain both services or rely exclusively on one, calculate your total security spending and how bundling might reduce costs, verify that Windows-only availability matches your device ecosystem, and consider whether IPVanish's integration approach appeals to you more than maintaining separate specialized tools optimized for specific functions.
The cybersecurity landscape continues evolving as threats become more sophisticated and users recognize that true security requires layered defenses addressing multiple attack vectors. Threat Protection Pro represents one strategic approach to meeting these emerging expectations. Whether it represents your optimal choice depends on factors unique to your situation—factors you're now better equipped to evaluate after this comprehensive analysis.
Remain vigilant about security in 2025 and beyond. Malware threats will continue evolving, new attack vectors will emerge, and comprehensive protection will require ongoing adaptation. Threat Protection Pro provides valuable protection as part of this adaptive security strategy, but only when implemented as one component of a broader security-conscious approach encompassing technology, behavior, and continuous learning.
Key Takeaways
- Threat Protection Pro integrates VIPRE antivirus with IPVanish VPN for layered malware protection beyond network encryption
- Real-time scanning uses signature matching, heuristic analysis, and behavioral monitoring to detect malware before execution
- Currently Windows-only beta feature with planned expansion to macOS, Linux, iOS, and Android platforms
- Bundled protection provides cost savings compared to separate VPN and antivirus subscriptions without additional fees
- Performance overhead typically 20-30% of system resources when both VPN and antivirus run simultaneously on capable hardware
- Comprehensive security requires multiple defensive layers; Threat Protection Pro is most effective as part of broader security strategy
- Alternative solutions like Bitdefender, Norton, and Kaspersky offer different approaches to integrated security
- Windows users primarily managing VPN needs receive strong value; multi-platform users require alternative solutions for non-Windows devices
Related Articles
- TikTok's Oracle Data Center Outage: What Really Happened [2025]
- Major Cybersecurity Threats & Digital Crime This Week [2025]
- Jeffrey Epstein's 'Personal Hacker': Zero-Day Exploits & Cyber Espionage [2025]
- Best Cheap VPN 2026: Complete Guide & Alternatives
- Polish Power Grid Breach: How Russian Hackers Exploited Default Credentials [2025]
- Bumble & Match Cyberattack: What Happened & How to Protect Your Data [2025]




