The Bumble and Match Cyberattack: Everything You Need to Know
Just when you thought your dating profile was safe, two of the biggest names in online dating got hit hard. Shiny Hunters, the notorious hacking group that's been making headlines for months, allegedly breached both Bumble and Match Group—and they didn't just take a little data. They're claiming thousands of internal documents, confidential files, and system access. If you've got an account on either platform, or on Badoo and BFF (which Bumble owns), this matters to you.
Here's what makes this attack different from your typical data breach. Shiny Hunters isn't just grabbing customer databases and ransom-demanding their way to a payday. They've shifted tactics. Instead of encrypting systems and holding them hostage, they're stealing data and threatening to sell it. It's cheaper, faster, and frankly, just as profitable. And major corporations are scrambling to figure out what to do about it.
The breach isn't some random technical failure either. It started with a phishing attack on a contractor account—a classic human engineering play that reminds us why security training matters at every level of an organization. One compromised credential led to network access, which led to internal documents, which led to this very real threat to millions of people's dating profiles and personal information.
What's particularly concerning is that this attack reflects a broader shift in how hackers operate. Ransomware gangs used to demand money to decrypt your files. Now they're copying everything first, encrypting second (or not at all), and leveraging the threat of public disclosure as their main weapon. It's a business model that's spreading through the criminal underground, and companies everywhere are only beginning to understand how serious it is.
We're going to walk through exactly what happened, what data might be at risk, what both companies are saying about it, and what you should actually do about it right now. Because understanding the threat is the first step to protecting yourself.
TL; DR
- Shiny Hunters claimed responsibility for breaching both Bumble and Match Group in a sophisticated phishing and data exfiltration attack
- Bumble says member accounts, profiles, and messages weren't accessed, though thousands of internal documents were stolen
- Match confirmed the breach after Bloomberg reporting, indicating contractor account compromise
- The attack pattern reflects a dangerous shift: Hackers now prioritize data theft over ransomware encryption, making companies vulnerable even without traditional ransomware locks
- You should monitor your accounts closely and enable two-factor authentication on all dating app profiles immediately

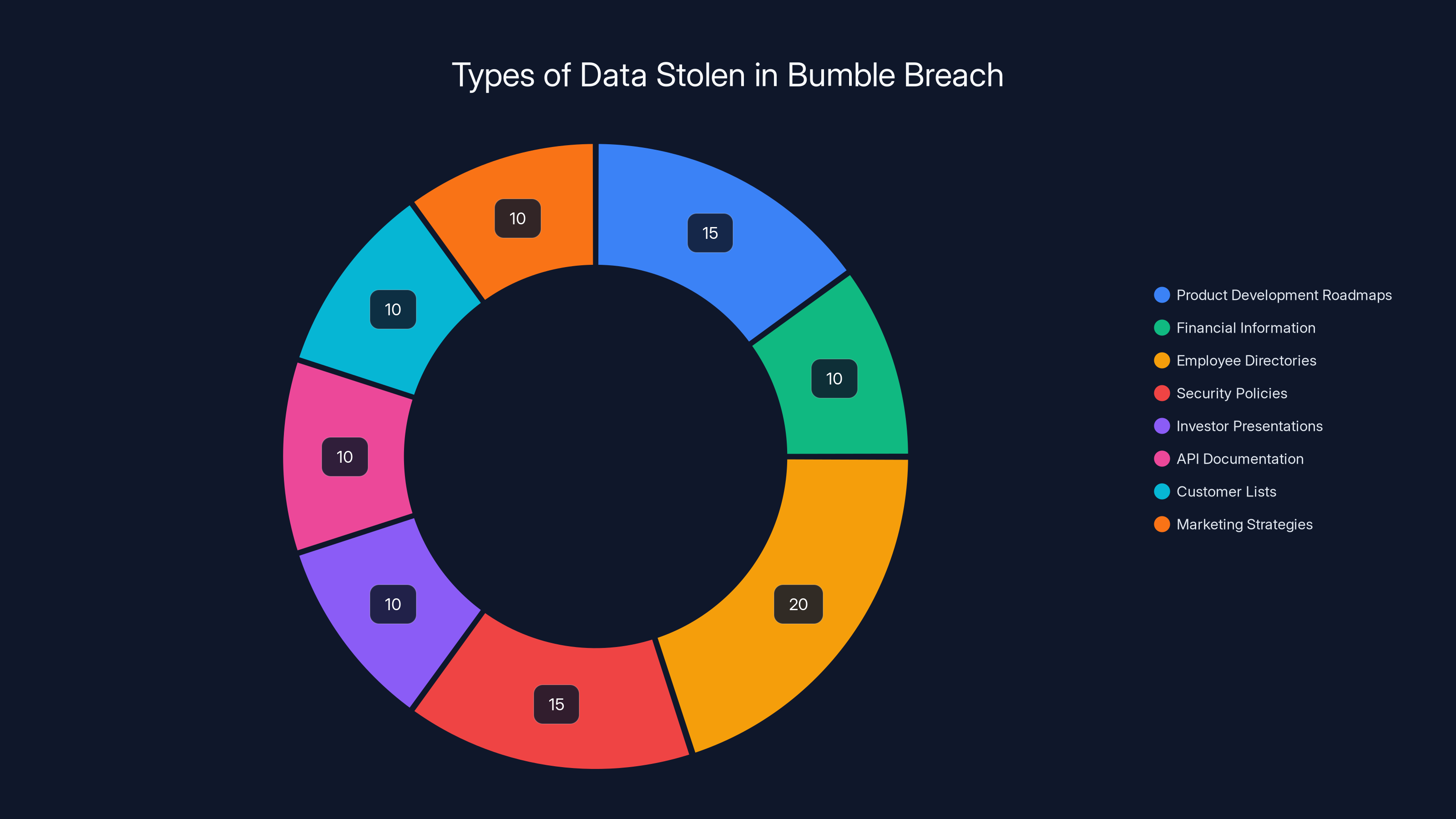
The breach involved various internal documents, with employee directories and security policies being significant portions. Estimated data based on typical document distribution.
Who is Shiny Hunters and Why Should You Care?
Shiny Hunters isn't some random hacker working from a basement in Eastern Europe. They're a sophisticated threat group with a track record of targeting enterprise companies. Over the past few weeks, they've made headlines by breaching multiple major corporations, and they've been remarkably vocal about their activities—posting evidence on dark web sites and building what looks like a deliberate marketing strategy around their capabilities.
The group started as a traditional ransomware operation. That meant they'd break into your network, encrypt all your files, and demand money to unlock them. It's the criminal equivalent of holding your business hostage. But somewhere along the way, Shiny Hunters did the math and realized something: stealing data is more profitable than locking it up.
Here's why that matters. Ransomware is loud. Your systems go down. Everyone notices. You call law enforcement. You get federal agents involved. But data theft? That's quiet. A hacker copies your confidential documents, your employee records, your customer data, and slips out the back door. Nobody knows until the data shows up on a website or gets sold to competitors. And by then, the attacker's already halfway to their next target.
Shiny Hunters has also been targeting specific industries and companies strategically. They've gone after Okta (a major identity and access management platform that millions of companies rely on), Microsoft, and various single sign-on (SSO) providers. Why? Because breaking into those systems gives you keys to hundreds of other companies. One Okta breach can cascade into thousands of compromised client companies. It's strategic thinking, not random target selection.
The threat to enterprises is significant. The group has reportedly targeted hundreds of organizations with phishing and vishing (voice phishing) attacks, specifically going after IT and tech support staff. They're making phone calls claiming to be from support teams, or sending emails that look legitimate enough to fool people. And it works often enough that they keep doing it.
What makes Shiny Hunters particularly dangerous is their operational tempo. They're not slow. They're not methodical in a way that gives you months to detect them. They get in, copy what they want, and get out. In Bumble's case, they claim to have focused specifically on documents marked as restricted or confidential, which suggests they knew what they were looking for. They targeted Google Drive and Slack—the places where companies actually store sensitive information.

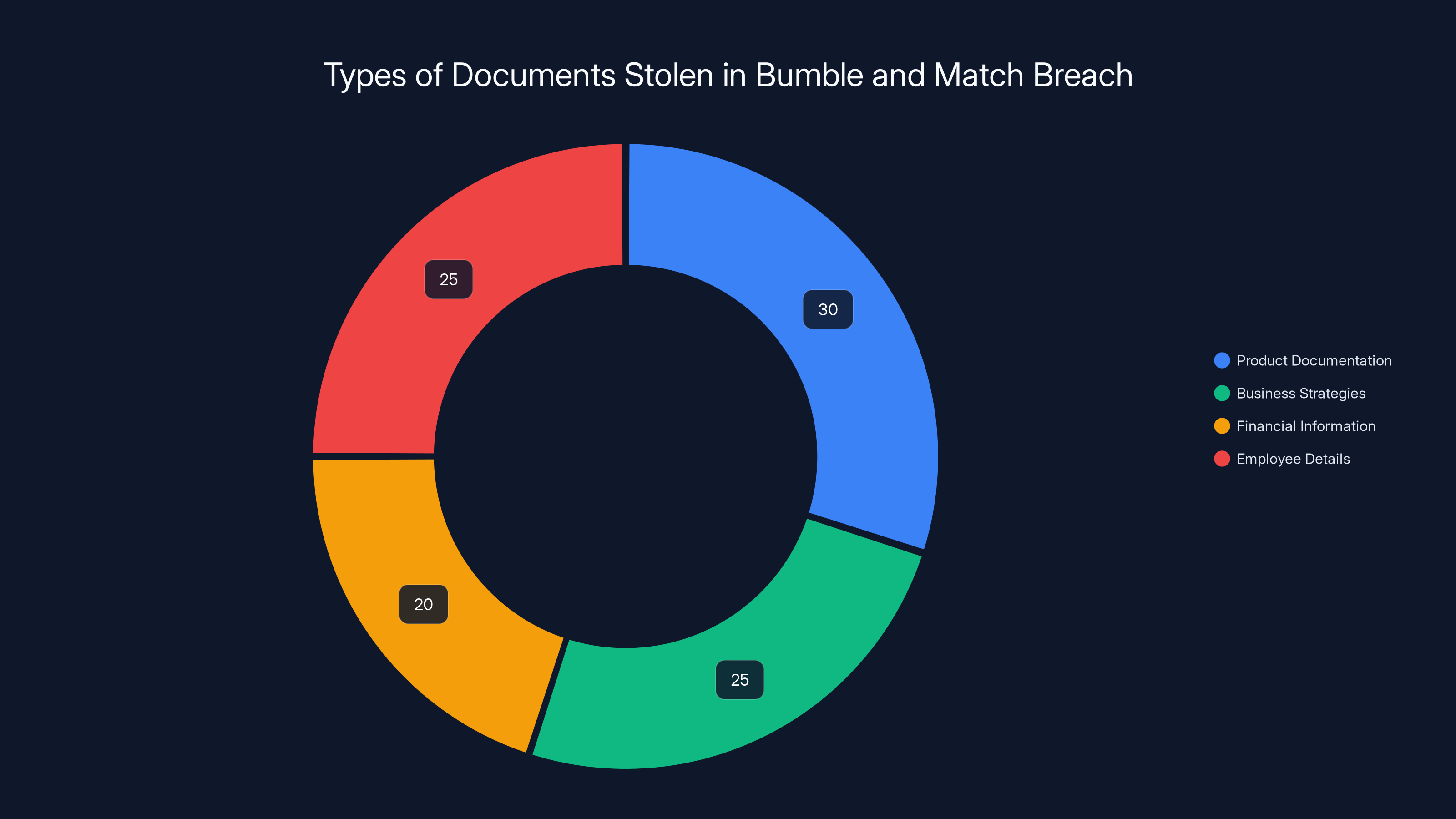
Estimated data suggests a balanced distribution of stolen documents, with product documentation and employee details being slightly more prevalent. Estimated data.
The Attack Timeline: How It Happened
Understanding how the breach unfolded is crucial because it reveals vulnerabilities that probably exist at thousands of other companies right now.
The attack started, innocuously enough, with a contractor. One of the contractors who works with Bumble had their account compromised through a phishing attack. This is the crucial detail everyone overlooks: the attacker didn't hit Bumble's main network directly. They came through the supply chain. Contractors have access, but they're often less carefully monitored than full-time employees. Their accounts may not have the same security controls. Their training might be less rigorous. And that's exactly what happened here.
Once the contractor account was compromised, the attacker had a legitimate foothold on Bumble's network. They weren't an external entity trying to break through a firewall anymore. They were an authenticated user. That changes everything about detection and response. Your security systems are designed to block outsiders, but an authenticated user inside your network? That's much harder to spot.
From there, the attacker made what they claim was brief unauthorized access to a limited portion of Bumble's network. They focused on stealing files from Google Drive and Slack—both cloud-based services where companies casually store sensitive information. The documents they copied were specifically marked as restricted or confidential, which suggests they weren't just grabbing everything. They were strategic about what they took.
According to Bumble's official statement, the unauthorized access was brief. The company detected the compromise, kicked the attacker out, and contacted law enforcement. Bumble's security team also stated that they don't believe the attackers accessed the member database, member accounts, the Bumble application itself, direct messages, or user profiles. If that's true, then the core product—the thing that contains users' personal information—remained secure.
But here's where it gets murky. Shiny Hunters posted to their data leak site claiming they'd stolen thousands of internal documents. Bumble says those documents came from Google Drive and Slack, not from the production database. That's a meaningful distinction. Internal documents are sensitive in different ways than customer data. They might contain product roadmaps, investor information, employee details, security policies, or business strategies. But they're not the dating profiles and personal information that users enter into the app.
The timeline is important: the breach itself wasn't months-long. It was quick and focused. That suggests the attacker had prior reconnaissance—they knew what they were looking for and where to find it. That kind of intelligence usually comes from inside information, detailed reconnaissance, or both.
What Data Was Actually Stolen?
This is where the distinction between what Shiny Hunters claims and what actually happened becomes critical.
According to Shiny Hunters' own posting on their data leak site, they stole thousands of internal documents from Bumble. Specifically, they claim they took documents marked as restricted or confidential from Google Drive and Slack. That's a much narrower scope than it sounds like when you first hear the headline "Bumble breached."
Internal documents might include things like:
- Product development roadmaps showing features in progress
- Financial information and business metrics
- Employee directories and personnel information
- Security policies and procedures (ironically, sometimes the thing that helps hackers)
- Investor presentations and business plans
- API documentation and technical architecture details
- Customer lists and partnership agreements
- Marketing strategies and campaign plans
None of that is customer data. None of that is your dating profile, your messages, or your personal information. Bumble's claim that member accounts, profiles, and messages weren't accessed actually holds up logically with what Shiny Hunters claims to have stolen.
But—and this is important—that doesn't mean users are completely safe. If Shiny Hunters got their hands on API documentation or technical architecture, that information could be used to plan future attacks. If they stole employee directories, that information could be used for targeted phishing against other employees. If they got security policies, they'll know exactly what the company's security controls are and how to avoid them next time.
For Match Group specifically, the breach appears to be limited to the contractor access scenario. Bloomberg's reporting indicated that a contractor account was compromised, limited access was gained, but the scope was more constrained than what happened at Bumble.
The real question is: how much of what Shiny Hunters claims to have is actually valuable? Dark web forums are full of hackers who claim to have massive datasets and sell partial, outdated, or outright fabricated information. The group's credibility is based on delivering what they claim, but without independent verification, it's impossible to know exactly what they have and what they're exaggerating.

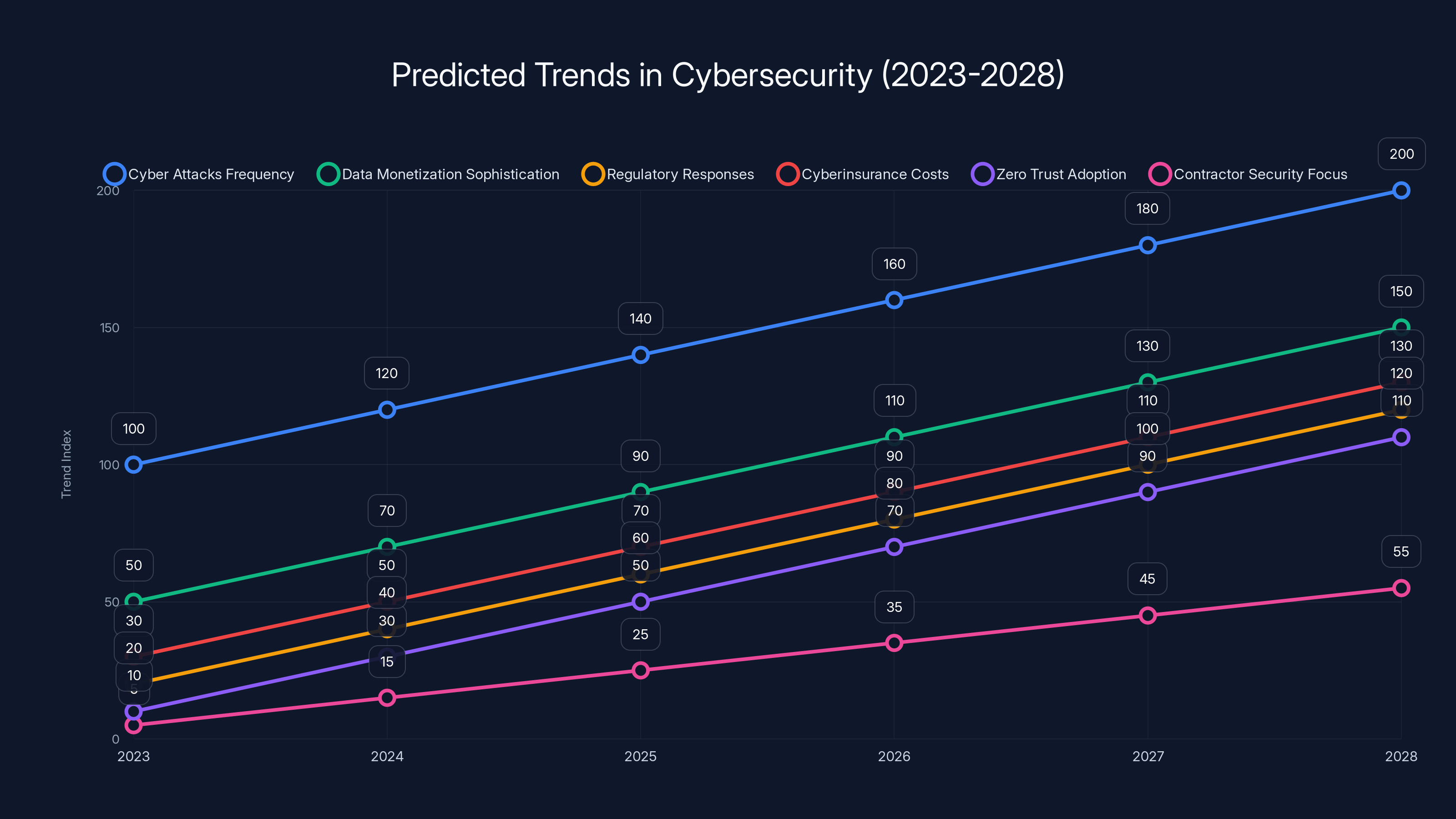
Estimated data shows increasing trends in cyber attacks, data monetization, regulatory responses, insurance costs, zero trust adoption, and contractor security focus from 2023 to 2028.
The Shift from Ransomware to Data Theft: What It Means
One of the most important aspects of this attack is what it represents about the evolution of cybercrime. Shiny Hunters started as a ransomware group, and that business model is giving way to data exfiltration. This isn't just a shift in tactics for this one group—it's a trend across the entire ransomware landscape.
Traditional ransomware works like this: attackers break in, encrypt your files, and demand payment for the decryption key. The problem (from the attacker's perspective) is that it's loud. Your company's systems go offline. You notice immediately. Employees can't work. Customers notice services are down. You call law enforcement. The FBI gets involved. Insurance companies get involved. You might pay, might not. But there's a lot of friction.
Data exfiltration is quieter. Copy the data. Don't encrypt anything. The company doesn't notice for days or weeks because everything still works normally. By the time the breach is discovered, the attackers are gone. And now the attacker has leverage: "Pay up or we sell this data, or we leak it to competitors, or we publish it publicly."
From a criminal economics perspective, this is more profitable. Ransomware demands might be
Other ransomware groups are following suit. The criminal ecosystem is competitive. If one group figures out that data theft is more profitable, others will copy the model. What we're seeing now is a transition across the entire landscape.
This has serious implications for enterprise security. Companies were starting to understand ransomware defense. They invested in backups, network segmentation, and incident response plans. But data exfiltration is harder to defend against. You can't back your way out of a data theft. You can't just restore from backup and be done with it. Once the data's stolen, it's stolen, and your only leverage is hoping the attacker is more interested in selling it back to you than selling it publicly.

Why Phishing and Vishing Are So Effective
The breach started with a phishing attack on a contractor's account. This is the critical vulnerability in modern security infrastructure. No matter how much money you spend on firewalls, intrusion detection, and threat intelligence, if someone clicks the wrong link and enters their credentials, it's game over.
Phishing is effective because it attacks the human layer, which is basically undefendable at scale. Yes, companies run security training. But humans are busy. They're distracted. They get hundreds of emails per day. And attackers have gotten really good at making phishing emails look legitimate. A sophisticated phishing email might actually come from a company domain (if the attacker compromises an internal email account first). It might use company branding, company logos, and reference real internal tools or processes.
Vishing—voice phishing—is even more insidious because it's harder to detect and harder to document. Someone calls claiming to be from IT support, or from the contractor company, or from an integration partner. They say something's wrong and they need to verify your credentials. They sound professional. The caller ID looks legitimate (spoofing is trivial). And they're just asking for a password reset, which seems totally normal in a work context.
Shiny Hunters specifically targets IT and support staff because those roles have access to critical systems and are expected to handle authentication and access regularly. An IT person getting a call about "unusual account activity" from someone who sounds official is primed to cooperate. The attack exploits the fundamental tension in security: you need people to be helpful and responsive to legitimate requests, but that same helpfulness can be exploited.
The warning to enterprises is clear: watch for individuals calling claiming to be IT or tech support, especially if they're asking to verify credentials, reset passwords, or confirm access. This is exactly how Shiny Hunters has been operating, and the approach has proven devastatingly effective.

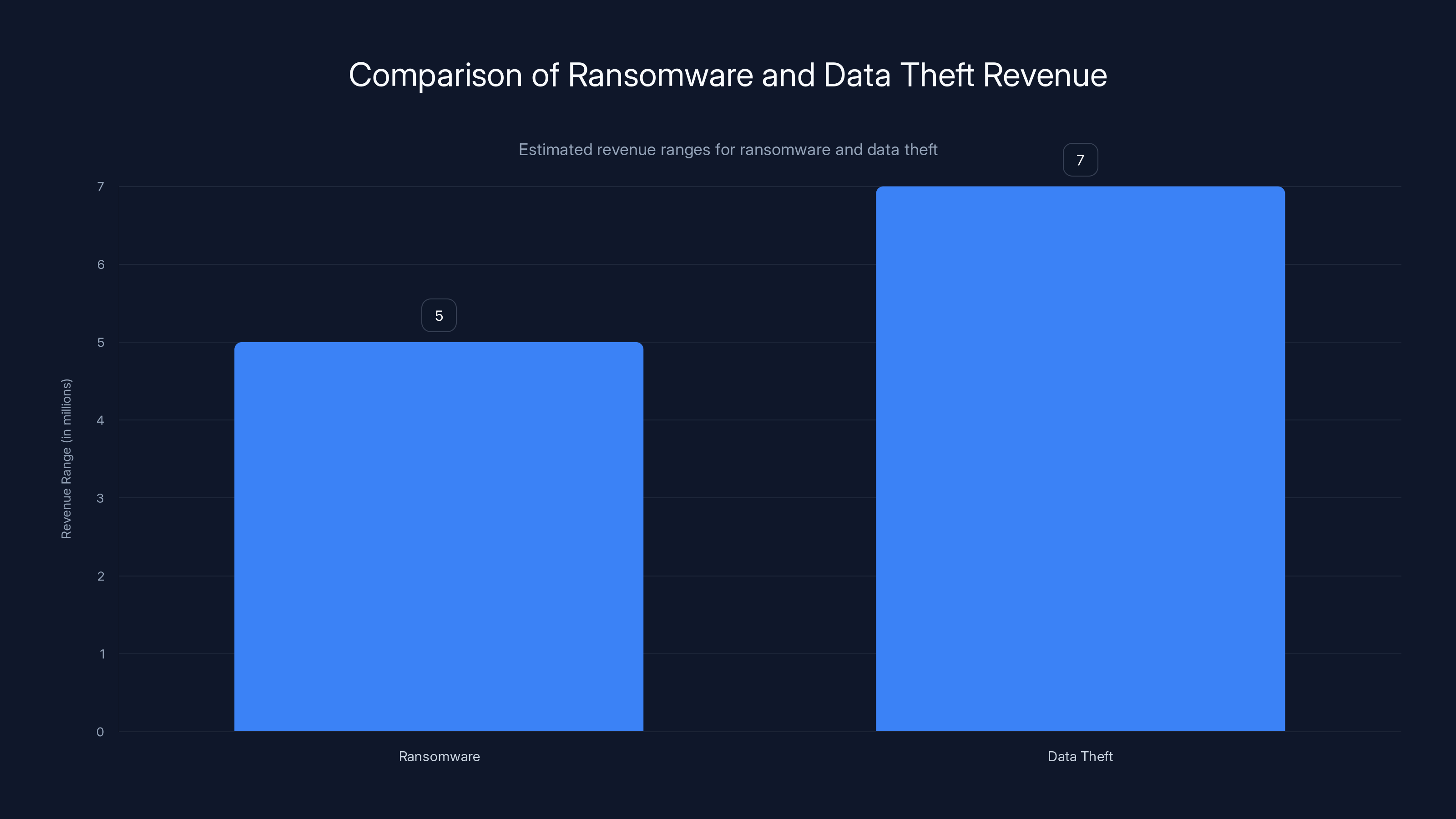
Estimated data shows that data theft can generate similar or higher revenue compared to ransomware, with less operational overhead. This shift is driven by the quieter nature of data theft, allowing criminals to target multiple victims unnoticed.
Bumble's Response and Damage Control
Bumble's official response to the breach has been relatively measured, which makes sense from a business perspective. The company doesn't want to cause panic among its user base if the core customer data wasn't actually compromised.
The company confirmed that a contractor's account was compromised through phishing. They disclosed this to law enforcement and worked with authorities to investigate. Bumble's statement, as reported by Bloomberg, emphasized that they don't believe member accounts, profiles, direct messages, or the Bumble application itself were accessed. The stolen data, according to Bumble, was limited to internal documents from Google Drive and Slack.
From a legal and regulatory perspective, this is significant. If user data wasn't actually accessed, the company's liability exposure is much lower. They may not need to send breach notification letters to millions of users (which is expensive and bad for PR). They may not face regulatory fines under GDPR or state privacy laws. They may not face lawsuits from users claiming their personal information was compromised.
But here's the political problem Bumble faces: Shiny Hunters is claiming credit and posting evidence of what they stole. Even if the user data wasn't touched, the fact that internal documents and confidential files were stolen is itself a significant breach. It undermines confidence in the company's security practices. It suggests that if the attacker could get this far, maybe they did access user data and Bumble just hasn't discovered it yet.
Bumble is also dealing with the reputational aspect. Dating apps are inherently about trust—trusting that your matches are real, that your conversations are private, that your personal information is safe. A security breach damages all of that trust. Even if no actual user data was stolen, the psychological damage is done. Users will wonder if the company is being truthful, if there's more to the story, if their data could be at risk.
The company's decision to contact law enforcement early and be relatively transparent about the breach (compared to some companies) suggests they're trying to manage the narrative and appear cooperative. But managing a data breach PR situation is nearly impossible. The story is out, Shiny Hunters has posted evidence, and users are understandably concerned.

Match Group's Confirmation and Escalation
Match Group owns multiple dating apps beyond just Match—the company operates Tinder, Ok Cupid, Hinge, and numerous other dating platforms. When the breach story broke, Match Group confirmed the incident but provided limited details.
According to Bloomberg's reporting, Match's experience was similar to Bumble's: a contractor account was compromised, limited access was gained to the network, and the company worked with law enforcement. But the details Match shared publicly were sparse, which is standard for companies dealing with active law enforcement investigations.
Match Group's situation is complicated because the company operates such a massive portfolio of dating apps. If one app is compromised, the reputational damage extends to all of them. Users of Match, Tinder, Ok Cupid, and other properties all start wondering if their data is at risk. That's why Match Group's response emphasizes investigation, cooperation with authorities, and the limited nature of the breach.
One interesting angle is that Match Group is reportedly one of the largest dating app companies globally, with millions of users spread across multiple apps and countries. A breach of this magnitude (even if limited to internal documents) affects regulatory bodies in the US, Europe, and other regions with strict privacy laws. That's why both companies would be in contact with regulators as well as law enforcement.
The fact that both Bumble and Match were hit in similar ways (phishing, contractor access, data exfiltration) suggests this is part of a broader campaign, not isolated incidents. Shiny Hunters appears to be systematically targeting major companies across multiple industries, using the same playbook repeatedly.
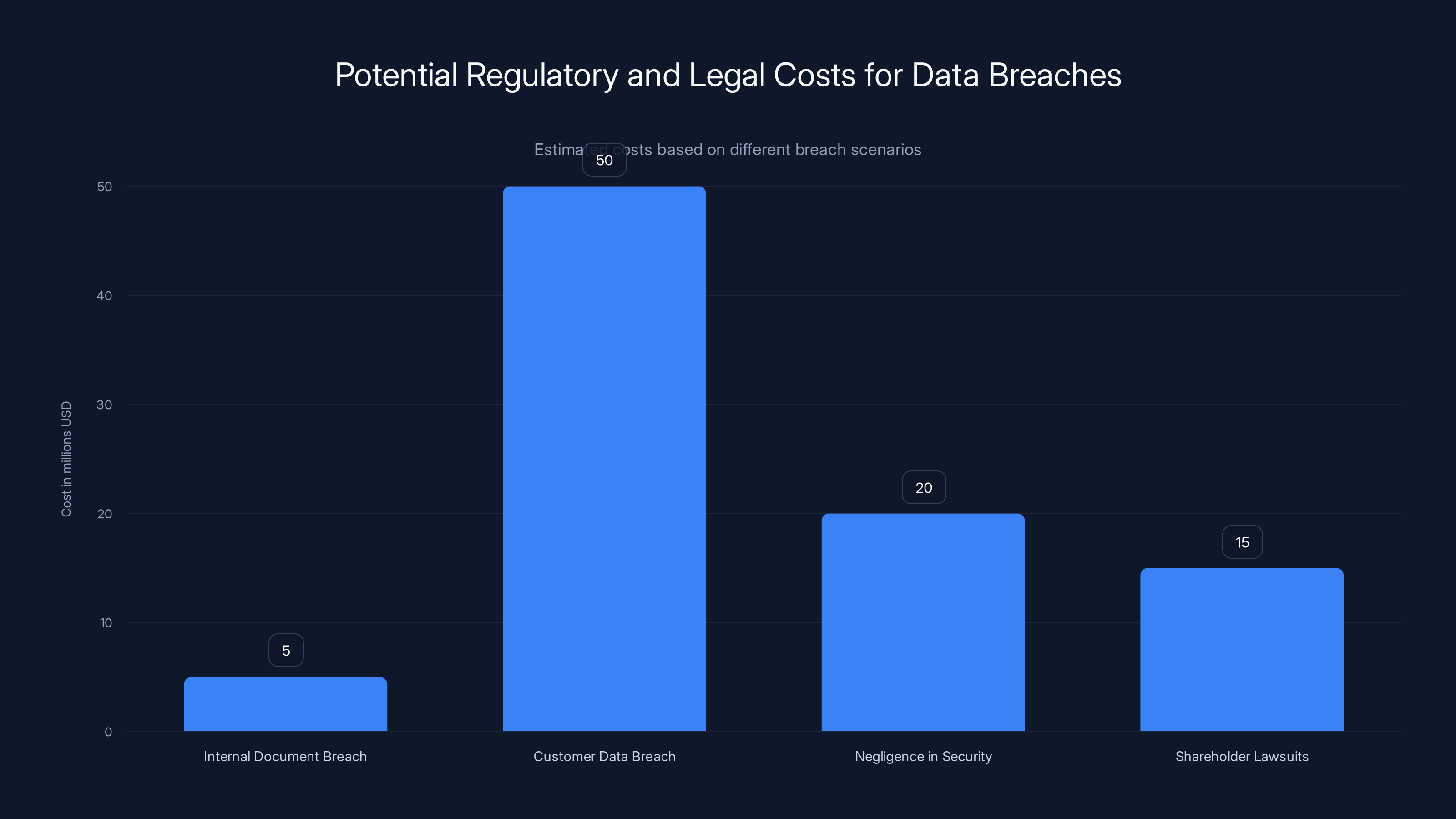
Estimated costs show that customer data breaches are significantly more expensive than internal document breaches. Regulatory scrutiny and negligence can also lead to substantial financial implications.
The Broader Threat Landscape: Why These Companies?
Shiny Hunters' choice of targets reveals something about their strategy and capabilities. They've gone after Okta (identity and access management), Microsoft (cloud infrastructure), dating apps, and various other enterprises. What do these have in common?
Okta and similar SSO providers are valuable targets because compromising them gives access to hundreds of client companies simultaneously. One breach cascades into thousands of compromised organizations. Microsoft access is similarly valuable because so many companies depend on Microsoft infrastructure. But dating apps? Why target Bumble and Match specifically?
First, dating apps store sensitive personal information: real names, phone numbers, photos, location data, message history, relationship preferences, and more. From an identity theft perspective, this data is valuable. From a harassment or blackmail perspective, it's even more valuable. Someone's dating profile, combined with their workplace information, combined with other data, could enable targeted harassment.
Second, dating app companies have substantial funding and should theoretically have good security. But the fact that they were compromised through contractor phishing suggests their security, while perhaps adequate for their products, wasn't sufficient for the threat landscape they operate in. This is a common pattern: well-funded companies get breached because they haven't maintained security at the same pace as threats have evolved.
Third, the reputational damage from a dating app breach is significant. The publicity is guaranteed. It's a story that affects millions of regular people, not just enterprise security professionals. Shiny Hunters gets attention by hitting consumer-facing companies. It demonstrates capability, which can be leveraged for future ransom demands or intimidation.
The threat pattern also suggests Shiny Hunters has good intelligence about company infrastructure. They knew about the contractor setup, they knew about Google Drive and Slack being used for sensitive documents, and they knew what kind of documents would be valuable to steal. That intelligence could come from previous network reconnaissance, information from insiders, or just deep knowledge of how modern companies operate (spoiler: most use Google Drive and Slack for confidential stuff).

What About Your Personal Data? The Real Risk Assessment
Let's be direct: if you have a Bumble or Match account, here's what you should realistically be concerned about.
The immediate risk is low. Both companies have stated, and available evidence supports, that the actual customer databases weren't accessed. Your dating profile, your messages, and your account information weren't stolen. That's genuinely good news.
The second-order risk is moderate. If Shiny Hunters stole internal documents and technical architecture information, that knowledge could be used to plan future attacks. They now understand how these companies structure their networks, where they store data, and what security controls exist. That information has value in planning a more targeted attack down the road.
The third-order risk is behavioral. Many people will become more cautious about what information they share on dating apps. They'll stop using video messages or sending location information. They'll use less detailed profiles. The breach chills user engagement, which affects the companies' businesses even if no data was directly stolen.
What you should actually do:
- Enable two-factor authentication on your dating app accounts immediately if the option is available
- Review your profile information and consider removing sensitive details that aren't necessary
- Monitor your accounts for suspicious activity
- Check your credit and watch for signs of identity theft unrelated to the dating app
- Be cautious about credential reuse—don't use the same password for dating apps that you use elsewhere
- Don't panic—the sky isn't falling, but vigilance is warranted
The most dangerous thing you could do right now is nothing. The second most dangerous thing is overreacting with excessive caution that cripples your ability to use the services you want to use. The balance is: reasonable security practices, awareness, and monitoring.
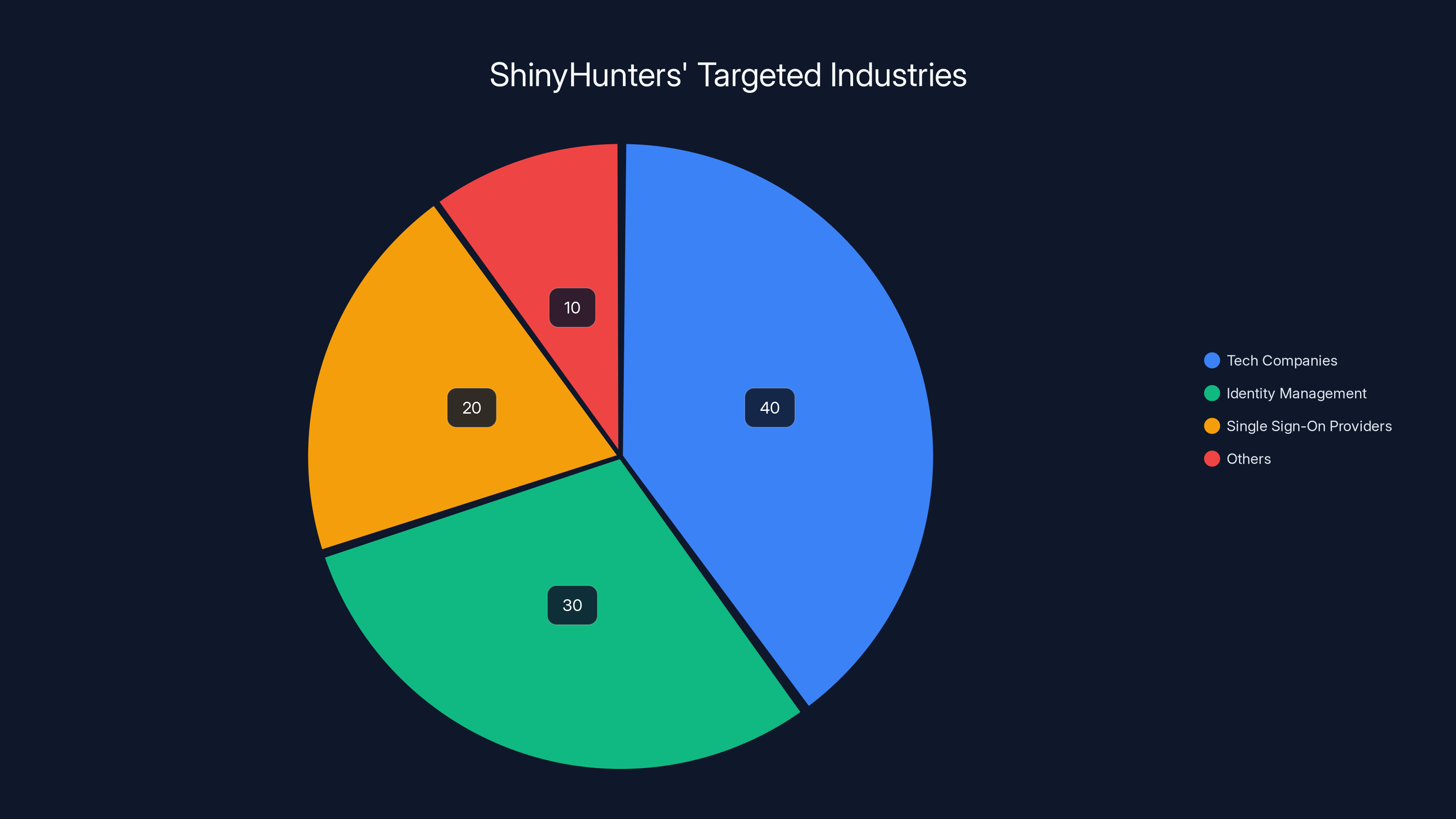
Estimated data shows ShinyHunters primarily targets tech companies and identity management platforms, highlighting their strategic focus on high-impact breaches.
How Contractor Access Became the Weak Link
One of the most important lessons from this breach is that contractors are a significant security vulnerability, and most companies don't treat them that way.
Contractors are part of your organization, but not quite. They might not get the same security training. They might not be subject to the same access controls. They might not be monitored as carefully. And from a security perspective, they're often the weakest link.
Why? Because contractors are distributed. They might work from home. They might use their own devices. They might work for multiple companies simultaneously, which means their device could be compromised at a completely different company and then used to attack you. They're not full-time employees with corporate devices and corporate security infrastructure. They're external resources with varying security hygiene.
Companies also tend to grant contractors access without the same rigor they'd apply to employees. The thinking goes: they're only here for a specific project, they only need access to a limited set of systems, so it's fine to skip some of the security procedures. But that "skip some procedures" approach is exactly what attackers exploit.
In Bumble's case, the contractor was phished. This suggests:
- The contractor may not have received regular security training
- The contractor's account may not have had the same monitoring and anomaly detection as employee accounts
- The contractor's account may not have required multi-factor authentication (a surprisingly common oversight)
- Once compromised, the contractor's account could move laterally through the network without triggering alerts
The solution is to treat contractor security with the same seriousness as employee security. That means:
- Regular security training for all contractors, including phishing awareness
- Mandatory multi-factor authentication regardless of role
- Network segmentation so contractor accounts have limited blast radius
- Monitoring and alerting on contractor account activity
- Periodic access reviews ensuring contractors still need the access they have
- Offboarding that actually happens when the contractor leaves
Most companies do some of this. Few do all of it consistently. That's the vulnerability.

The Dark Web and Data Sales: What Happens Next
Shiny Hunters has posted evidence of their breach on their data leak site. This is part of the intimidation and monetization strategy. Once data is posted as proof, the negotiation can begin. The attacker can offer to delete it in exchange for payment, or to keep quiet about it, or to sell it to the highest bidder.
For internal corporate documents, the value varies. API documentation might be worth thousands because it reveals system architecture. Employee directories might be worth less (that information is often publicly available in various forms). Financial information and investor presentations are extremely valuable. Customer lists could be worth significant money.
On dark web marketplaces, various actors are interested in different things. Competitors might pay for strategic information. Hackers might pay for technical documentation to plan future attacks. Researchers might analyze the data (academics, journalists, security professionals). Blackmailers might use employee information to target individuals.
The point is: once data is stolen, it has a market. Even if Bumble or Match pay a ransom or negotiate for deletion, there's no guarantee the data won't be resold or leaked anyway. Once something's on the dark web, controlling its distribution is nearly impossible.
This is why data theft is so profitable compared to traditional ransomware. You don't need the company to pay immediately. You can monetize the data in multiple ways, over extended periods, to multiple parties. It's a business with real economics that reward efficiency and scale.

Lessons for Enterprise Security: What Needs to Change
The Bumble and Match breaches are instructive because they follow a pattern we're seeing repeatedly: sophisticated attackers using basic techniques with devastating effect.
Phishing and vishing aren't new. They're not cutting-edge attacks. They're old-school social engineering. Yet they work because humans are humans. You can't patch human psychology. You can't update the brain like you update software.
But you can build organizational practices that make humans less effective attack vectors:
1. Zero Trust Architecture
Traditional security says: trust is inside the firewall. If someone's on the internal network, they're trusted. That model is broken. Zero trust says: verify every access request, regardless of whether it's internal or external. Every contractor's access should be monitored like an external API call.
2. Privileged Access Management
Not all accounts should have the same level of access. Contractors should have minimal access—just enough to do their specific job. If a contractor only needs access to one application, they shouldn't have access to Google Drive, Slack, and the entire internal network.
3. Multi-Factor Authentication Everywhere
Password phishing works because passwords are the only thing protecting the account. With MFA, even if the password is stolen, the account is still protected. Companies that mandate MFA have dramatically lower breach rates. There's no good reason not to require it.
4. Monitoring and Anomaly Detection
If a contractor account suddenly starts downloading thousands of files from Google Drive at 3 AM, that's anomalous. It should trigger an alert. Most companies have the tools to do this. They just don't configure them properly or don't have the resources to respond when alerts fire.
5. Data Classification and Segmentation
Not all data is equally sensitive. Confidential documents should be stored separately from general business documents. Access to confidential documents should be restricted and monitored. If a contractor account tries to access Google Drive folders they've never accessed before, that's suspicious.
6. Incident Response Planning
Both Bumble and Match had incident response plans (they were able to detect the breach, investigate, and coordinate with law enforcement). Companies without this infrastructure take months to notice breaches. The detection and response speed is critical.
The brutal truth is that no company is going to achieve perfect security. Attackers only need one way in. Defenders need to block every way in. That asymmetry is structural. But companies can make breaches more expensive and difficult, which pushes attackers toward easier targets.

Regulatory and Legal Implications Going Forward
Both Bumble and Match operate in jurisdictions with strict privacy regulations. In Europe, GDPR applies. In the US, various state laws apply (California Consumer Privacy Act, for example). In other countries, additional regulations exist.
The good news for these companies is that the breach appears limited to internal documents, not customer personal data. If customer data wasn't accessed, the notification requirements are more limited. The bad news is that regulators don't care much about what the company claims—they care about demonstrating negligence in security practices.
A contractor account compromised through phishing, with access to internal documents, could be viewed as negligent security practices by regulators. Why didn't the company require MFA? Why weren't contractor access rights more restricted? Why weren't sensitive documents stored with better access controls?
Both companies will likely face increased regulatory scrutiny, audits, and potentially fines. The specific amounts depend on the jurisdiction and whether actual customer data was compromised. But even without customer data being stolen, the breach will result in regulatory costs.
From a legal liability perspective, the companies need to clearly document their investigation, their findings, and their remediation steps. If they discover later that more data was stolen than initially thought, the liability exposure increases significantly. If they can demonstrate they conducted a thorough investigation and implemented proper security fixes, the liability is more limited.
There's also potential liability to customers and stakeholders. If customers' data was compromised, lawsuits are likely (even if improbable to win). If investors claim they were misled about security practices, shareholder suits could follow. The legal exposure extends far beyond just the regulatory fines.
How to Protect Yourself as a User
You can't control what companies do with their security infrastructure, but you can control how you use dating apps.
Immediate Steps:
- Enable two-factor authentication if available on your account
- Use a strong, unique password that you don't use anywhere else
- Review your profile and remove sensitive information (exact location, workplace details, phone number, etc.)
- Check for suspicious activity on your account
- Monitor your credit through the major bureaus
Ongoing Practices:
- Don't share identifying information in messages until you've verified someone is legitimate
- Be cautious about video calls and voice calls with people you don't know—this is where scams often happen.
- Don't click links in messages from matches (malware and phishing).
- Consider using a separate phone number or email for dating apps if possible.
- Assume that any information you put in a dating app is not fully secure—because it isn't.
- Keep your app updated to the latest version (which might include security patches).
The goal isn't to be paranoid. The goal is to accept that dating apps, like all internet services, involve some risk. You can minimize that risk through reasonable practices without giving up the ability to use the service.
The Bigger Picture: Supply Chain Security
This breach highlights a larger issue in enterprise security: supply chain vulnerability. Attackers don't always go after the big target directly. Sometimes they go after vendors, contractors, and suppliers.
A contractor with access to your network is part of your supply chain. So are your cloud providers, your Saa S vendors, your integrations, and your partners. If any of them are compromised, you could be compromised indirectly.
The security industry is trying to address this through frameworks like Software Bill of Materials (SBOM) and vendor security assessments. But fundamentally, you can't fully control the security practices of companies you depend on. You can only:
- Vet vendors for security practices
- Limit their access to what they actually need
- Monitor their activity
- Have response plans if they're compromised
Bumble and Match presumably did some of this, but clearly not comprehensively. The fact that a contractor was successfully phished and could access sensitive documents suggests the supply chain risk management could be better.
For enterprises, this means: you need a vendor security program. You need to know who has access to your systems, what they can access, and how you'd respond if they were compromised. Most companies have this on a spreadsheet somewhere. Few actually maintain it actively.

What's Next? Predictions and Trends
Based on the pattern we're seeing, here's what we can expect going forward:
1. More Attacks, Same Methods
Shiny Hunters and similar groups will continue targeting companies because phishing and contractor account compromise work. Until companies change their practices systematically, the attacks will continue.
2. Data Monetization Will Get More Sophisticated
Attackers will get better at extracting value from stolen data. Instead of demanding a ransom, they'll sell it to multiple parties, lease access to it, or use it to plan follow-on attacks. The market for stolen corporate data will mature.
3. Regulatory Responses Will Increase
Governments are getting serious about data security. The EU's Digital Operational Resilience Act (DORA), US state privacy laws, and international regulations will increase requirements and penalties. Companies will be forced to invest more in security just to comply with regulations.
4. Insurance Costs Will Rise
Cyberinsurance (which covers breach notification, investigation, and liability costs) is already becoming more expensive. As breaches continue, premiums will rise and coverage will get more restrictive. Companies will be forced to improve security to get affordable insurance.
5. Zero Trust Adoption Will Accelerate
Big companies (especially financial services, government, and tech) are adopting zero trust architecture. This will create a competitive advantage in security and will pressure smaller companies to follow.
6. Contractor Security Will Become a Major Focus
Once companies realize that contractors are a consistent attack vector, we'll see more investment in contractor security practices. But this will take years to implement across the industry.

FAQ
What exactly was stolen in the Bumble and Match breach?
According to both companies and the attacker's claims, thousands of internal documents from Bumble were stolen, primarily from Google Drive and Slack. These documents were marked as restricted or confidential but did not include member databases, user accounts, profiles, or direct messages. Match Group experienced a similar but more limited breach. The specific contents haven't been fully disclosed, but they likely include product documentation, business strategies, financial information, and employee details.
Did my personal dating profile get compromised?
Based on statements from both Bumble and Match, member accounts, profiles, and messages were not accessed during this breach. However, given that internal documentation was stolen, there's a small possibility that future targeted attacks could use that information to compromise user data. For now, the immediate risk to your personal profile is low, but you should still enable two-factor authentication and monitor your account.
How did the attackers get inside the companies' networks?
The breach began with a phishing attack on a contractor's account. The contractor clicked a malicious link or entered credentials on a fake website, allowing the attacker to gain access to their account. Since the contractor account had access to the internal network, the attacker could then move laterally to Google Drive and Slack where sensitive documents were stored. This is a common attack pattern that highlights the importance of contractor security.
Should I delete my dating app account?
Deleting your account is unnecessary and probably overkill. The companies have stated that user data wasn't compromised, and no evidence suggests it was. Instead, take reasonable precautions: enable two-factor authentication, use a strong unique password, and review your profile to remove sensitive information you don't need to include. If you're concerned about ongoing security, you can reduce the amount of personal information in your profile without deleting the account entirely.
What is Shiny Hunters and why are they dangerous?
Shiny Hunters is a sophisticated cybercriminal group that started as a ransomware operation but has shifted to data exfiltration and theft. They're dangerous because they target large enterprises, they're technically skilled, they operate strategically, and they use phishing and social engineering effectively. Rather than just encrypting files (traditional ransomware), they steal data and threaten to sell or leak it if the company doesn't pay. They've targeted hundreds of organizations and are part of a broader trend in cybercriminals moving away from traditional ransomware.
How can companies prevent attacks like this from happening?
Companies can reduce risk by implementing zero trust architecture (verifying every access request), requiring multi-factor authentication for all accounts (including contractors), restricting contractor access to only what they need, implementing network monitoring to detect anomalous activity, properly classifying and securing sensitive data, and conducting regular security training. However, no security is perfect, and attackers will always find new ways in. The goal is to make attacks more expensive and difficult, not impossible.
Is there a way to know if my data was actually stolen and sold?
You can monitor dark web forums and data leak sites where stolen information is typically posted, but this requires technical knowledge or specialized tools. More practically, you can use free services like Have I Been Pwned (which aggregates known breaches) or monitor your credit reports. Most importantly, watch for signs of identity theft like unexpected bills or accounts you didn't open. If a company confirms your data was stolen, they're usually required to notify you, so you don't have to be the detective.
What's the difference between a phishing attack and vishing?
Phishing is sending deceptive emails to trick someone into clicking a malicious link or entering credentials. Vishing (voice phishing) is the same social engineering attack, but by phone. In this case, Shiny Hunters used phishing emails to compromise contractor accounts. They've also been using vishing to target IT and support staff at other companies. Vishing is often more effective because it's harder to verify the caller's identity and people are trained to be helpful when someone calls claiming to be from support.
Should I be worried about other data breaches I've been part of?
Yes, but contextualize your worry. Breaches are common, and if your data has been stolen, it's already stolen—worry won't change that. What you can control is how you respond: use strong unique passwords for each service, enable two-factor authentication where available, monitor your credit regularly, and watch for signs of identity theft. If you've been in multiple breaches, the risk compounds (because someone could combine datasets to get more complete information about you), so security practices become even more important.
What will happen to Shiny Hunters and the stolen data?
That depends on law enforcement effectiveness. Cybercriminal groups operating from countries without extradition treaties are very difficult to prosecute. The FBI and international law enforcement are investigating, but actually bringing charges and convictions is rare. The stolen data will likely be sold on dark web marketplaces to various buyers. Some of it might be published publicly by the attackers to demonstrate capability or intimidate other companies. Some might be held for ransom. The attackers probably won't be prosecuted anytime soon.

Conclusion: What This Breach Really Means
The Bumble and Match breach is important, but not for the reasons the headlines suggest. It's not a catastrophic loss of personal dating data that will compromise millions of people's privacy (though that would be bad). Instead, it's a demonstration of a dangerous trend: sophisticated attackers using basic techniques with devastating effect.
Phishing isn't new. Contractor accounts as weak links isn't new. Stolen internal documents aren't quite as damaging as stolen customer data, but they're still valuable to attackers planning future attacks. What's new is the scale, the sophistication of the targeting, and the brazen way groups like Shiny Hunters are operating with seemingly no concern for consequences.
For users of dating apps, the practical response is simple: reasonable security practices, awareness, and monitoring. Don't panic. Don't overreact. But also don't ignore the breach. Enable two-factor authentication. Use strong passwords. Monitor your account. Be alert to signs of identity theft.
For enterprises, the lesson is harder: contractor security matters. Supply chain risk is real. Phishing training alone doesn't solve the problem. You need technical controls (MFA, network segmentation, monitoring), operational practices (access reviews, incident response), and cultural change (security is everyone's responsibility, not just the security team's).
The future of cybersecurity isn't flashy. It's not sophisticated zero-day exploits or AI-powered attacks. It's basic blocking and tackling: strong authentication, least privilege access, monitoring, and incident response. The companies that get these fundamentals right will be harder to breach. The ones that don't will continue to make headlines.
Shiny Hunters succeeded because Bumble had a gap in contractor security. Fix that gap, and you make their job much harder. Scale that fix across an organization, and you actually improve your security posture. It's not perfect. Nothing is. But it's an effective use of limited security resources.

Key Takeaways
- ShinyHunters breached both Bumble and Match through a phishing attack on contractor accounts, stealing thousands of internal documents but not confirmed user data
- The attack reflects a dangerous industry trend: cybercriminals shifting from ransomware encryption to data theft, which is quieter, more profitable, and harder to detect
- Contractor accounts represent a critical security vulnerability because they often bypass the same security controls applied to employee accounts
- User personal data (profiles, messages, account credentials) was not confirmed to be accessed, but internal documents with technical architecture could enable future attacks
- Effective defense requires zero trust architecture, mandatory multi-factor authentication, contractor access restrictions, network monitoring, and proper data classification
Related Articles
- Device Protection Beyond Hardware: Securing Your Digital Identity [2025]
- Google's War on Residential Proxies: How IPIDEA's Network Collapsed [2025]
- Are VPNs Really Safe? Security Factors to Consider [2025]
- Upwind Security's $250M Series B: Runtime Cloud Security's Defining Moment [2025]
- Why Brits Fear Online Privacy But Trust the Wrong Apps [2025]
- FBI Seizes RAMP: The Collapse of Ransomware's Last Stronghold [2025]
![Bumble & Match Cyberattack: What Happened & How to Protect Your Data [2025]](https://tryrunable.com/blog/bumble-match-cyberattack-what-happened-how-to-protect-your-d/image-1-1769715578675.jpg)



