Taiwan's 2.5 Million Daily Cyberattacks: Understanding China's Cyber Hybrid War Strategy
The numbers are staggering. Taiwan's National Security Bureau published findings that left cybersecurity experts and policymakers genuinely alarmed: 2.63 million cyberattacks per day targeting the island's critical infrastructure in 2025. That's not a typo. That's not an estimate. That's nearly 960 million attacks in a single year, and it represents a 6% year-on-year increase from 2024 and a gut-wrenching 113% spike compared to 2023 when Taiwan first began official tracking.
This isn't random hacking activity. This isn't amateur threat actors testing defenses for sport. This is a coordinated, state-sponsored campaign of unprecedented scale designed to probe, infiltrate, disrupt, and ultimately paralyze the infrastructure that keeps a nation of 23.9 million people functioning.
Here's what makes this genuinely frightening: the attacks aren't random. They're synchronized with military operations. They coincide with political speeches. They align with moments of diplomatic significance. China isn't just attacking Taiwan's infrastructure—it's using cyberspace as a weapon in what officials now openly call "hybrid war," a coordinated blend of kinetic military threats, information operations, and persistent cyber intrusions designed to demoralize, destabilize, and potentially prepare the ground for more direct confrontation.
This article breaks down what Taiwan is facing, who's behind it, how the attacks work, and what it means for global cybersecurity. Because if it's happening in Taiwan, security analysts warn, it's coming to other allies next.
TL; DR
- Scale is unprecedented: Taiwan endured 2.63 million cyberattacks daily in 2025, up 113% since 2023 tracking began
- State-sponsored and coordinated: Chinese-linked groups like Volt Typhoon and Brass Typhoon conduct synchronized campaigns aligned with military operations
- Infrastructure at risk: Hospitals, banks, government agencies, and power systems are primary targets in this "hybrid war" strategy
- Timing matters: Attacks spike during military patrols (23 of 40 joint combat readiness patrols triggered cyberattacks) and political speeches
- Global implications: Taiwan's situation foreshadows cyber threats targeting other democracies and allied nations worldwide
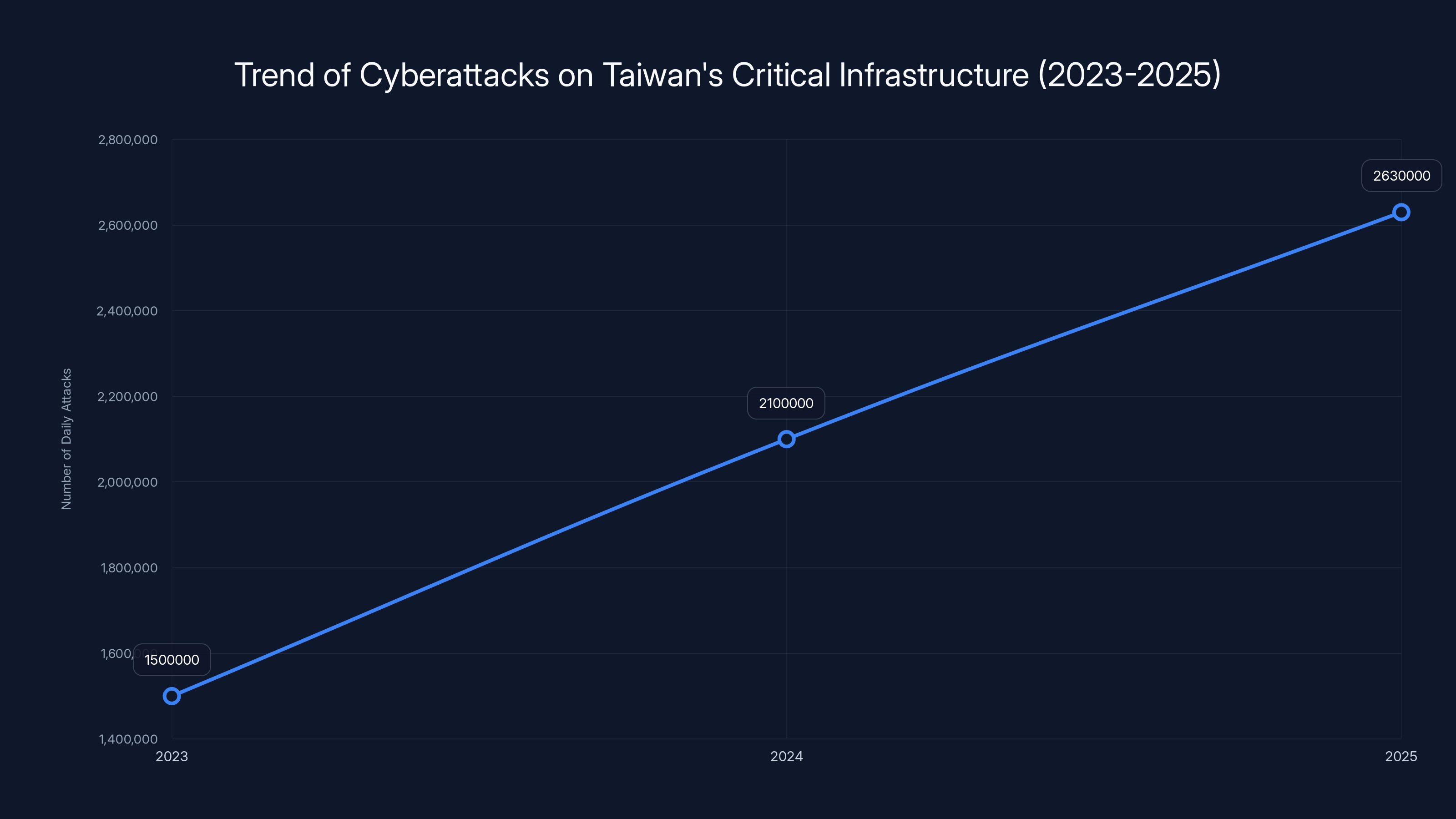
The number of daily cyberattacks on Taiwan's critical infrastructure has increased significantly from 2023 to 2025, highlighting a growing cybersecurity challenge. Estimated data based on narrative.
Understanding the Scale: What 2.63 Million Daily Attacks Actually Means
Let's put this number in human terms first. 2.63 million attacks per day equals roughly 30 attacks per second. If each attack took just one second to execute, a single cybersecurity analyst would need nearly 305 days of continuous, uninterrupted work to manually process one day's worth of attacks. That's impossible. That's intentional.
The number itself deserves context. In 2023, when Taiwan's National Security Bureau first began publishing official statistics, the number was significantly lower. By 2024, incidents against critical infrastructure organizations had already climbed. Then 2025 hit, and the trajectory became nearly vertical.
How Taiwan Counts and Measures Attacks
When Taiwan's National Security Bureau released this data, international observers immediately asked the obvious follow-up question: How are they defining an "attack"? Are they counting every single malicious packet? Every failed login attempt? Every port scan?
The answer matters because different counting methodologies produce wildly different numbers. Some governments count successful breaches. Others count detection events. Still others count any traffic from blacklisted IP addresses.
Taiwan's methodology counts incidents against critical infrastructure organizations: hospitals, banks, government agencies, power systems, telecommunications providers, and water utilities. They're not counting every suspicious packet flooding the internet backbone. They're focusing on directed threats against essential services that keep society functioning.
That distinction is crucial. It means the 2.63 million figure represents organized, focused attacks on systems that matter, not just background noise from internet scanning.
The 113% Increase: What Changed?
There are three possible explanations for this dramatic year-over-year jump, and they're not mutually exclusive:
First, China ramped up the actual attack volume. Political tensions increased, military rhetoric intensified, and Beijing allocated more resources and personnel to cyber operations. This is the most straightforward explanation, and probably the largest contributing factor.
Second, Taiwan improved its detection capabilities. In 2023, they might have been missing attacks that they caught in 2025. Better monitoring infrastructure, enhanced threat intelligence sharing, and more sophisticated detection tools could account for a significant portion of the increase. This isn't a bad thing—it means Taiwan's defenses are getting sharper—but it complicates the picture of whether attacks actually increased or detection improved.
Third, the definition or classification of what counts as an attack might have shifted. Taiwan's security bureaucracy, like all government agencies, evolves its reporting standards over time. A minor adjustment in how incidents are categorized could push numbers higher or lower.
Analysts generally agree the true answer involves all three factors, with the actual attack volume increase being the dominant driver.
Why Infrastructure, Why Now?
Critical infrastructure is the bullseye. Hospitals, banks, power grids, water systems, and telecommunications networks aren't just economically important. They're politically important. They're strategically important.
A successful cyberattack on Taiwan's power grid wouldn't just cause blackouts. It would cause panic. It would undermine confidence in the government. It would create chaos perfect for military operations. An attack on hospital systems would cause deaths, and deaths create political pressure.
China understands this calculus intimately. Which is why, according to Taiwan's National Security Bureau, the attacks intensified precisely during moments of strategic significance: military patrols, diplomatic events, political speeches, and symbolic anniversaries.
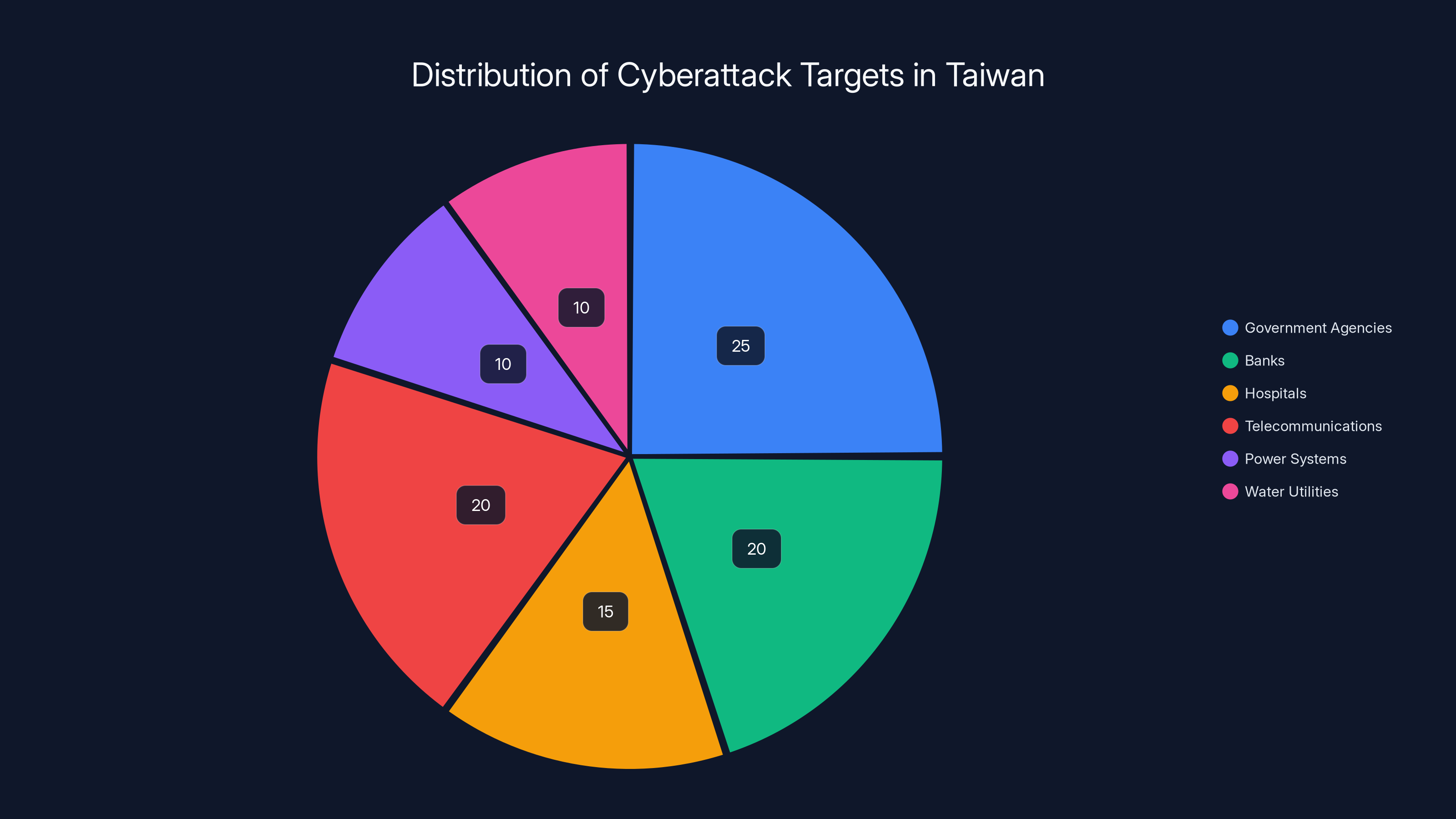
Estimated data shows government agencies and telecommunications are primary targets, reflecting their critical role in national security.
The Hybrid War Doctrine: Military + Cyber + Information
Taiwan's National Security Bureau released a statement that deserves quoting directly: "Such a trend indicates a deliberate attempt by China to compromise Taiwan's crucial infrastructure comprehensively and to disrupt or paralyze Taiwanese government and social functions."
That's not hyperbole from an alarmist agency. That's a technical assessment from a government institution tasked with national security. They're describing a comprehensive strategy, not sporadic attacks.
What Hybrid War Actually Means
Hybrid war isn't a new military concept, but it's been dramatically accelerated by technology. The idea is simple: combine military force, cyberattacks, information operations, economic pressure, and political subversion into a coordinated campaign designed to achieve political objectives without triggering a traditional military conflict.
It's deniable. It's persistent. It's hard to defend against. And it's becoming the template for great power competition in the 21st century.
China's hybrid war doctrine against Taiwan includes:
- Kinetic military operations: Joint combat readiness patrols with aircraft and naval vessels conducting provocative maneuvers near Taiwan's airspace and territorial waters
- Cyber operations: Coordinated attacks on critical infrastructure designed to probe defenses, steal intelligence, and prepare the battlefield
- Information warfare: Spreading disinformation through social media, state media, and controlled outlets to undermine confidence in Taiwan's government and create internal division
- Economic coercion: Trade restrictions, investment limitations, and market manipulation designed to create economic hardship
- Diplomatic pressure: Using China's growing international influence to isolate Taiwan and reduce recognition of its government
Each element reinforces the others. Military intimidation makes the population anxious. Information warfare amplifies that anxiety. Cyberattacks on hospitals and power systems feed the narrative that Taiwan's government can't protect its citizens. Economic pressure creates real hardship that makes the political message resonate.
It's a multi-vector attack on the integrity and viability of the Taiwanese state, and cyberattacks are a critical component.
Timing as a Signature: The Military-Cyber Connection
One detail from Taiwan's report jumped out to security analysts: the timing correlation. Of the 40 "joint combat readiness patrols" China conducted in 2025, cyberattacks followed in 23 cases. That's a 57% correlation rate. That's not coincidence. That's coordination.
Why would timing matter? Because it reveals the strategic thinking. A military patrol by itself sends a message: "We're willing to conduct operations near your territory." A cyberattack during that same window sends an additional message: "We can also strike your critical infrastructure while your military is distracted." Together, they create a sense of vulnerability and encirclement.
The same pattern emerged during political events. When President Lai Ching-te gave a speech marking his first year in office, cyberattacks spiked. When Vice President Hsiao Bi-khim spoke at a meeting with lawmakers at the European Parliament in November, cyberattacks spiked again.
This is psychological warfare using cyber tools. It's designed to create an association between Taiwan's political leadership and system vulnerability. The message, delivered through coordinated operations, is simple: "Your government can't protect you."
The Threat Actors: Volt Typhoon, Brass Typhoon, and State-Sponsored Espionage
Cyberattacks don't execute themselves. They're conducted by people, teams, and organizations. In Taiwan's case, multiple Chinese-linked threat groups have been identified as conducting operations aligned with Beijing's strategic interests.
Volt Typhoon: Infrastructure Reconnaissance at Scale
Volt Typhoon emerged in the mid-2020s as a particularly sophisticated threat actor focused on infrastructure reconnaissance. Unlike many cybercriminal groups that seek immediate financial gain, Volt Typhoon operates with a different objective: persistence and intelligence gathering.
Their modus operandi follows a predictable pattern:
- Initial compromise: Gain access through vulnerable credentials, unpatched systems, or social engineering
- Persistence: Install tools that allow long-term, undetected access to the network
- Reconnaissance: Map the target organization's network architecture, identify critical systems, and understand operational relationships
- Lateral movement: Move through the network to reach high-value targets like control systems and administrative networks
- Preparation: Place tools and backdoors that would allow rapid disruption if needed
Volt Typhoon doesn't steal data immediately. They gather intelligence slowly and deliberately. They're preparing the battlefield. When the order comes—if it ever comes—they're positioned to cause significant damage.
Security researchers have observed Volt Typhoon targeting critical infrastructure across multiple countries, but their focus on Taiwan has been particularly intense and systematic.
Brass Typhoon: Data Theft and Strategic Espionage
While Volt Typhoon focuses on infrastructure penetration, Brass Typhoon specializes in intelligence theft. This group targets sensitive government, military, and corporate data with precision.
Their operations align suspiciously well with Chinese national interests. When Taiwan announced military procurement plans, Brass Typhoon targeted the related procurement offices. When Taiwan negotiated trade agreements, they targeted economic ministries. When Taiwan conducted diplomatic outreach, they targeted foreign service networks.
This isn't random. This is coordinated state espionage using criminal infrastructure and deniability.
Salt Typhoon and Supply Chain Attacks
A third major threat actor in the Taiwan ecosystem is Salt Typhoon, which focuses on supply chain compromises and third-party access. Instead of directly attacking government or infrastructure targets, Salt Typhoon compromises companies that do business with those targets.
This is actually more dangerous in some ways. If you compromise the software supply chain, you don't need to break into thousands of organizations individually. You push malicious code to all of them at once through their trusted update mechanisms.
Taiwan has been particularly vulnerable to supply chain attacks because of its semiconductor industry. Taiwanese firms like TSMC, Media Tek, and Synopsys supply components to technology companies worldwide. Compromising one of these suppliers could affect systems globally.
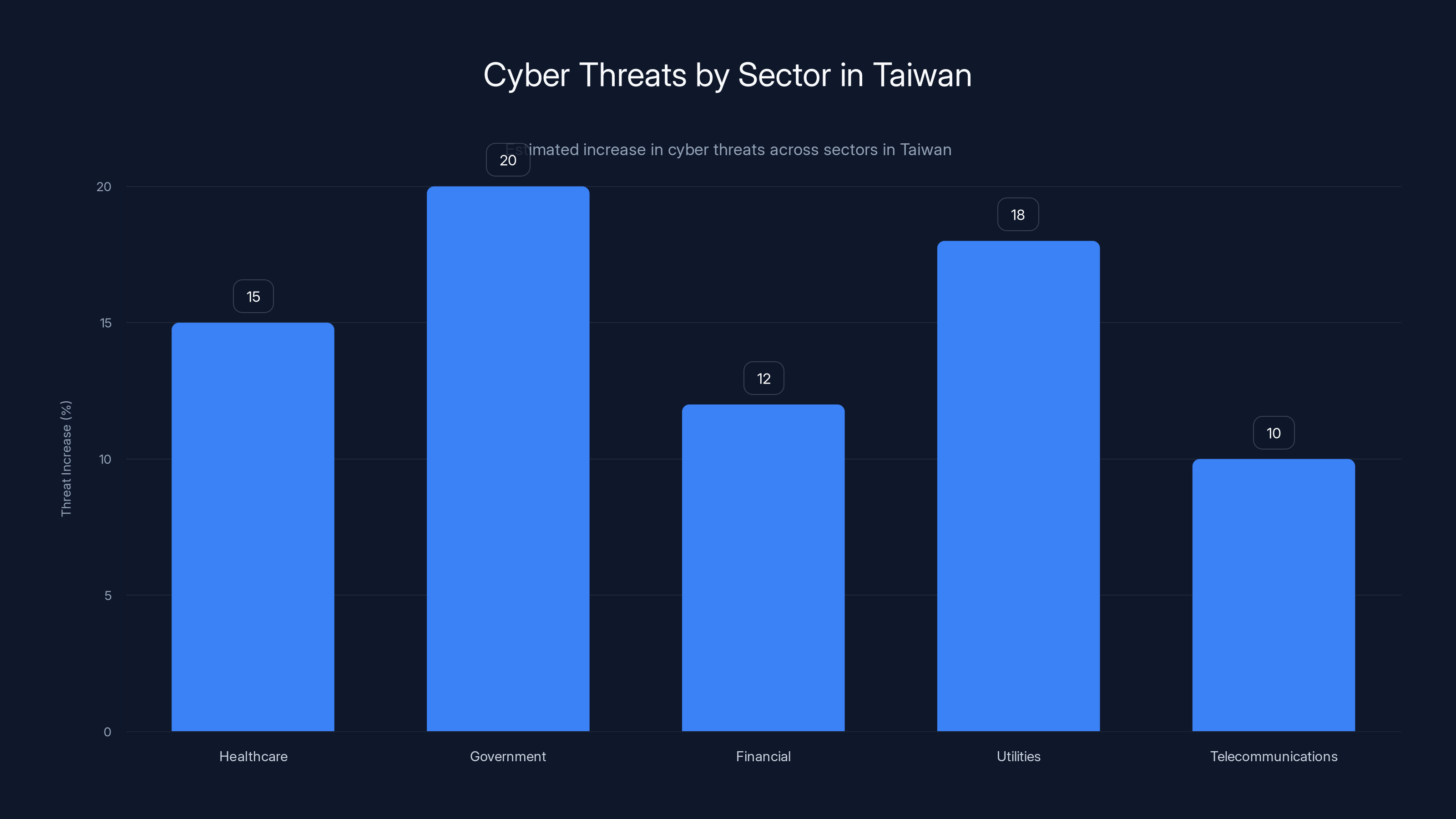
Healthcare and government sectors in Taiwan face the highest increase in cyber threats, with healthcare seeing a 15% rise year-over-year. Estimated data based on sectoral analysis.
Attack Categories: What Kind of Threats Is Taiwan Facing?
The 2.63 million daily attacks aren't all the same. They fall into distinct categories, each with different objectives and implications.
Reconnaissance Attacks: Mapping the Battlefield
Approximately 60-70% of detected attacks are reconnaissance-focused. These include port scans, service enumeration, and vulnerability scanning. Threat actors are mapping Taiwan's digital landscape like military engineers mapping terrain before invasion.
These attacks are relatively easy to detect and relatively hard to stop completely. A network can block a suspicious port scan from one IP address, but when you're facing attacks from thousands of sources using botnet infrastructure, blocking everything becomes impossible.
The goal isn't to compromise a system immediately. The goal is to discover weaknesses and understand what's out there.
Exploitation Attempts: Testing Defenses
About 20-30% of attacks involve actual exploitation attempts. Threat actors send crafted payloads designed to trigger known or suspected vulnerabilities. They test what works. They learn which systems are patched and which are vulnerable.
These attacks are more serious because they represent attempts to gain actual access. But they're also easier to defend against if you're diligent: keep systems patched, maintain updated security tools, and use network segmentation to limit the blast radius of successful compromises.
Credential Attacks: The Human Factor
The remaining 10-20% involve credential attacks: brute force password attempts, credential stuffing (using stolen passwords from other breaches), and phishing campaigns designed to capture credentials.
These attacks work because humans are the weakest link. Even in a well-defended organization, a single employee falling for a sophisticated phishing email can grant an attacker a foothold. And once you're inside, lateral movement to more privileged systems often becomes straightforward.

Taiwan's Defense Strategy: Detection, Deterrence, and Resilience
Taiwan isn't passive in the face of this threat. The National Security Bureau, along with the Cyber Security Center and other agencies, has implemented a multi-layered defense strategy.
Real-Time Threat Monitoring and Information Sharing
Taiwan has established the Information Sharing and Analysis Center (ISAC) for critical infrastructure sectors. Different industries—power, water, telecommunications, healthcare—share threat intelligence in real-time. When one organization detects a new attack pattern, it's reported to all others.
This creates a collective intelligence advantage. A malware strain targeting hospitals in one region is immediately catalogued and defenses are updated across the entire healthcare system before it can cause widespread damage.
The challenge is speed. Threat intelligence only works if it spreads fast enough to outpace the attack. Taiwan has made significant progress here, but adversaries are constantly evolving their tactics to stay ahead.
Incident Response Capabilities
Taiwan has established specialized incident response teams at national, sector, and organizational levels. When a significant attack occurs, specialized teams mobilize to contain the damage, eradicate the threat, and implement long-term fixes.
The government has invested heavily in training cybersecurity personnel, but like every nation, Taiwan faces a shortage of qualified experts. The demand for experienced incident responders exceeds the supply.
Infrastructure Hardening and Segmentation
Critical infrastructure systems are being progressively hardened through several measures:
- Network segmentation: Isolating operational technology networks from internet-connected systems
- Redundancy: Building backup systems and failover capabilities
- Air-gapping: Keeping the most critical systems completely disconnected from networks
- Security updates: Aggressive patching regimens for all critical systems
This is expensive and disruptive. It requires investment in new infrastructure, retraining of personnel, and operational changes. But it's necessary.
Workforce Development and Education
Taiwan has significantly increased cybersecurity education at universities and vocational schools. The government offers scholarships and incentives for students pursuing cybersecurity careers. The military and intelligence services have expanded their cyber operations units.
The numbers being trained still fall short of actual demand, but the trajectory is positive.

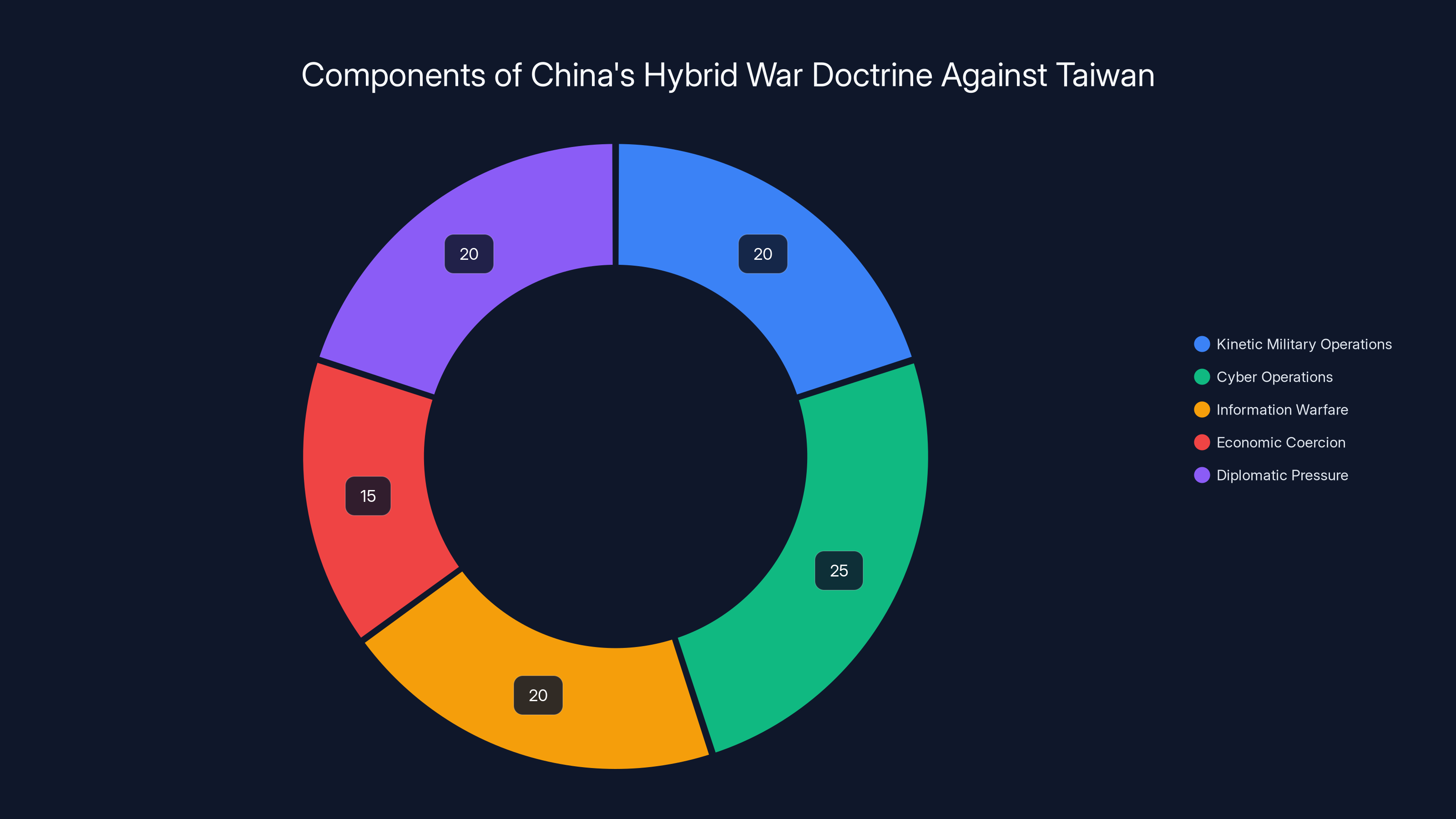
China's hybrid war against Taiwan involves a balanced effort across military, cyber, information, economic, and diplomatic strategies. Estimated data reflects the multifaceted nature of hybrid warfare.
China's Denial Game: Strategic Ambiguity and Information Operations
When Taiwan's National Security Bureau released this report with specific numbers and allegations, observers waited for China's response. It came, but not in the way many expected.
The Standard Response: Denial
China's typical response to cyberattack allegations is outright denial combined with counter-accusation. A Foreign Ministry spokesperson stated that China doesn't engage in cyberattacks and pointed to the United States as the world's "biggest cyber-bully."
This response serves multiple purposes:
- Domestic messaging: Audiences in China receive the message that the country is being attacked by hostile forces, reinforcing the narrative of external threat
- International plausible deniability: By denying involvement, China maintains a facade of respecting international norms while actual operations continue
- Muddying attribution: In cyberspace, attribution is never 100% certain. By raising doubt, China complicates international responses
The Strategic Ambiguity Advantage
China has strategically embraced ambiguity about its cyber operations. Government agencies, military units, intelligence services, and even private contractors blur the lines of responsibility. When a cyberattack occurs, determining whether it's directly ordered by the government, sanctioned by intelligence services, or conducted by patriotic criminals becomes nearly impossible.
This ambiguity is a feature, not a bug. It allows China to conduct aggressive cyber operations while maintaining technical deniability. If international pressure mounts, Beijing can claim the attacks were conducted by unauthorized actors.
Researcher Assessment vs. Government Claims
While China denies involvement, cybersecurity researchers have independently assessed that threat groups like Volt Typhoon and Brass Typhoon operate with resources and objectives that align with state sponsorship.
These assessments are based on:
- Targeting patterns: The choice of targets aligns perfectly with Chinese national interests
- Technical sophistication: The tools and techniques require significant development resources
- Operational security: The operational discipline suggests state-level training and oversight
- Language and cultural markers: Code comments, naming conventions, and operational patterns suggest Chinese language and cultural backgrounds
- Persistence of operations: Unlike criminal groups that move on when defenses improve, state-sponsored actors maintain operations across years and decades
US intelligence agencies, allied governments, and private sector security firms have all made similar assessments. The confidence level is high, even if not reaching the 100% certainty that would be required for formal attribution in a legal proceeding.

Global Context: Taiwan as a Testing Ground
Many security analysts argue that Taiwan isn't just a target—it's a laboratory. China is testing cyber warfare techniques, threat actor training methods, and operational concepts that could be applied against other targets.
The Taiwan Precedent for Other Allied Nations
If China successfully develops cyber capabilities to disrupt Taiwan's infrastructure, those same capabilities could theoretically be deployed against other allies. Japan, South Korea, Australia, and potentially even NATO members could face similar attacks.
Taiwan's experience offers a preview of what hybrid war looks like in a technologically sophisticated society. The lessons learned—by attackers and defenders alike—will shape cyber conflict for decades.
The US-Taiwan Alliance and Cyber Support
The United States has significantly increased cyber support to Taiwan, including:
- Intelligence sharing: Real-time threat intelligence about Chinese cyber operations
- Technical assistance: Helping Taiwan build detection and response capabilities
- Training and expertise: Seconding experienced cybersecurity professionals
- Equipment and tools: Providing advanced security technology and capabilities
But the US has deliberately avoided inserting itself as a defender for every attack. The goal is to help Taiwan develop indigenous, sustainable capabilities. This reflects a broader shift in US cyber strategy: instead of defending allies directly, help them defend themselves.
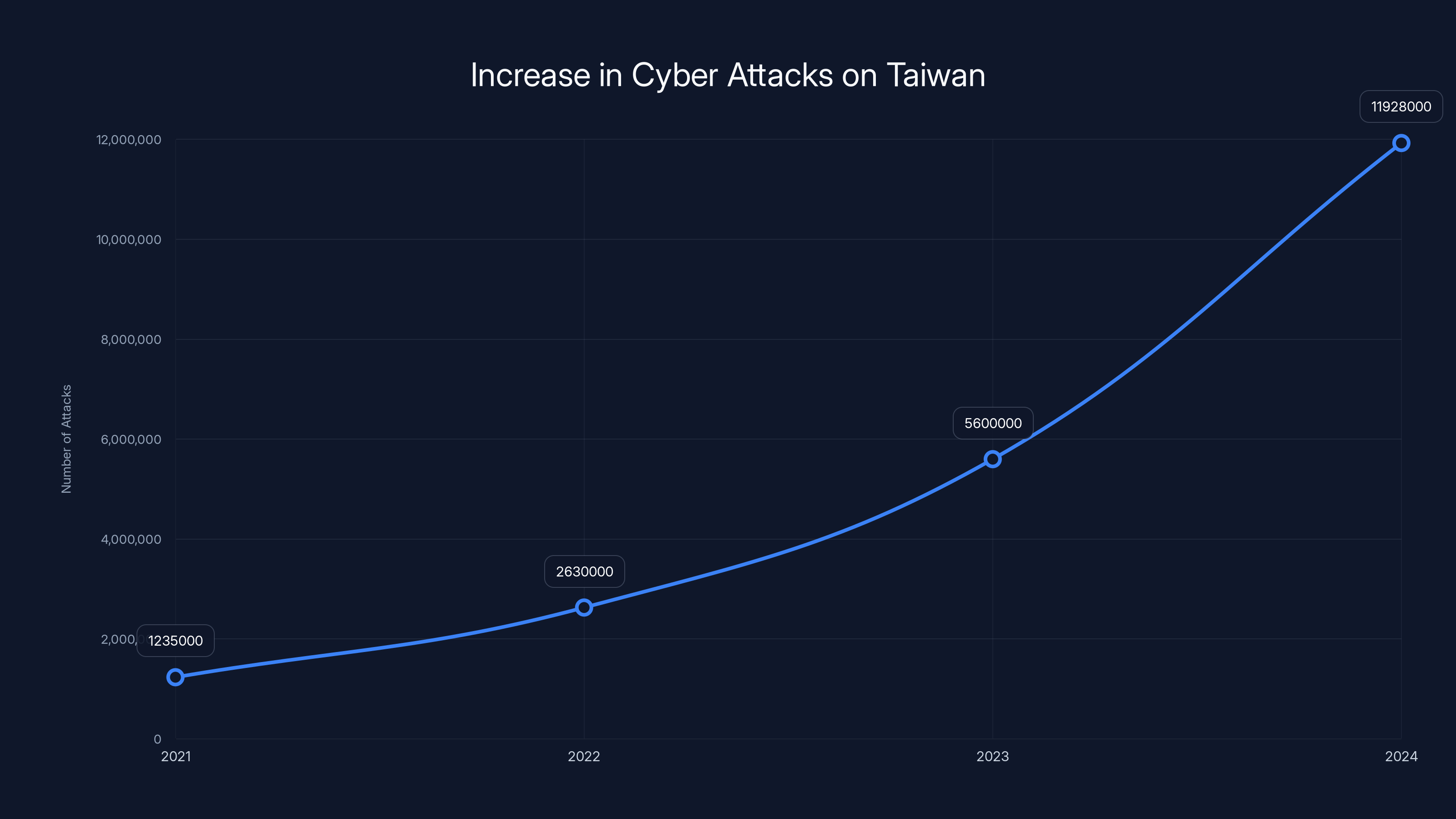
Taiwan has experienced a dramatic increase in cyber attacks, with daily incidents rising from 1.23 million in 2021 to an estimated 11.9 million by 2024, reflecting the growing threat of state-sponsored cyber warfare. Estimated data.
The Evolution of Chinese Cyber Capabilities: A Historical Perspective
China's cyber operations haven't always been this sophisticated. Understanding how they've evolved illuminates where they might be headed.
The Early Years: Opportunistic Attacks
In the 1990s and early 2000s, Chinese cyber operations were relatively unsophisticated. Attacks were often conducted by individuals or small groups with limited coordination. They targeted military networks, government agencies, and defense contractors seeking intellectual property theft.
These operations were effective—significant amounts of classified and proprietary information were stolen—but they were tactically limited and operationally disconnected.
The Professionalization Era: 2007-2015
Starting around 2007, Chinese cyber operations became noticeably more organized and professional. The sophistication of tools improved dramatically. Operational security practices hardened. Attack coordination became evident.
This period saw the emergence of what security researchers called "advanced persistent threats" or APTs. Groups like Comment Crew and Unit 61398 became infamous for their sophisticated espionage campaigns.
The professionalization coincided with organizational reforms and integration of cyber operations into military structures. This wasn't random hacker activity anymore. This was military operations.
The Current Era: Industrial-Scale Operations
Starting around 2018 and continuing to the present, Chinese cyber operations have scaled to industrial levels. The 2.63 million daily attacks against Taiwan represent the current state of that evolution: sophisticated, massive in volume, coordinated across multiple threat actors, and clearly aligned with strategic objectives.
These operations now include:
- Offensive operations: Active attacks designed to cause disruption
- Defensive operations: Detecting and blocking cyber threats from other nations
- Intelligence operations: Persistent espionage against government, military, and industry
- Supply chain operations: Compromising vendors and contractors
All of this happens simultaneously, often using the same infrastructure and personnel.
Sectoral Analysis: Who Gets Hit and How
Not all critical infrastructure sectors face equal cyber threats. Taiwan's experience varies dramatically by sector.
Healthcare and Hospital Systems
Hospitals are particularly attractive targets because attacks on them have immediate humanitarian consequences. A ransomware attack that encrypts hospital records doesn't just cause financial damage—it prevents doctors from accessing patient information, delays surgeries, and can lead to patient deaths.
Taiwan's healthcare system has been hit repeatedly with attacks designed to disrupt operations. The National Security Bureau assessed that hospital-targeting attacks increased 15% year-over-year, making healthcare the second-most-targeted sector after government.
Financial Institutions
Banks and financial institutions are targets for obvious reasons: they hold money and financial data. But Chinese attacks on Taiwanese banks haven't focused primarily on theft. Instead, they've focused on reconnaissance and disruption capabilities.
The assessment is that China wants to understand how Taiwan's financial system works, where the vulnerabilities are, and how quickly a coordinated attack could impact market confidence. A successful cyberattack on Taiwan's stock exchange, for instance, could cause economic shock waves globally.
Power and Water Utilities
Operational technology networks controlling power generation, distribution, and water systems are increasingly targeted. These systems are attractive because attacking them could cause physical damage and create humanitarian crises.
Defending power grid networks presents unique challenges because you can't simply take systems offline for patching. The grid needs to operate 24/7. This creates an inherent tension between security and availability.
Taiwan has invested heavily in power grid cybersecurity, but the utilities sector remains vulnerable.
Telecommunications
Telecom networks are critical for both civilian communications and military operations. Control over telecommunications could allow an attacker to:
- Monitor communications
- Disrupt communications
- Inject false information
- Create confusion during a crisis
Chinese cyber operations have particularly focused on telecom infrastructure, and penetrations have been discovered and remediated multiple times.

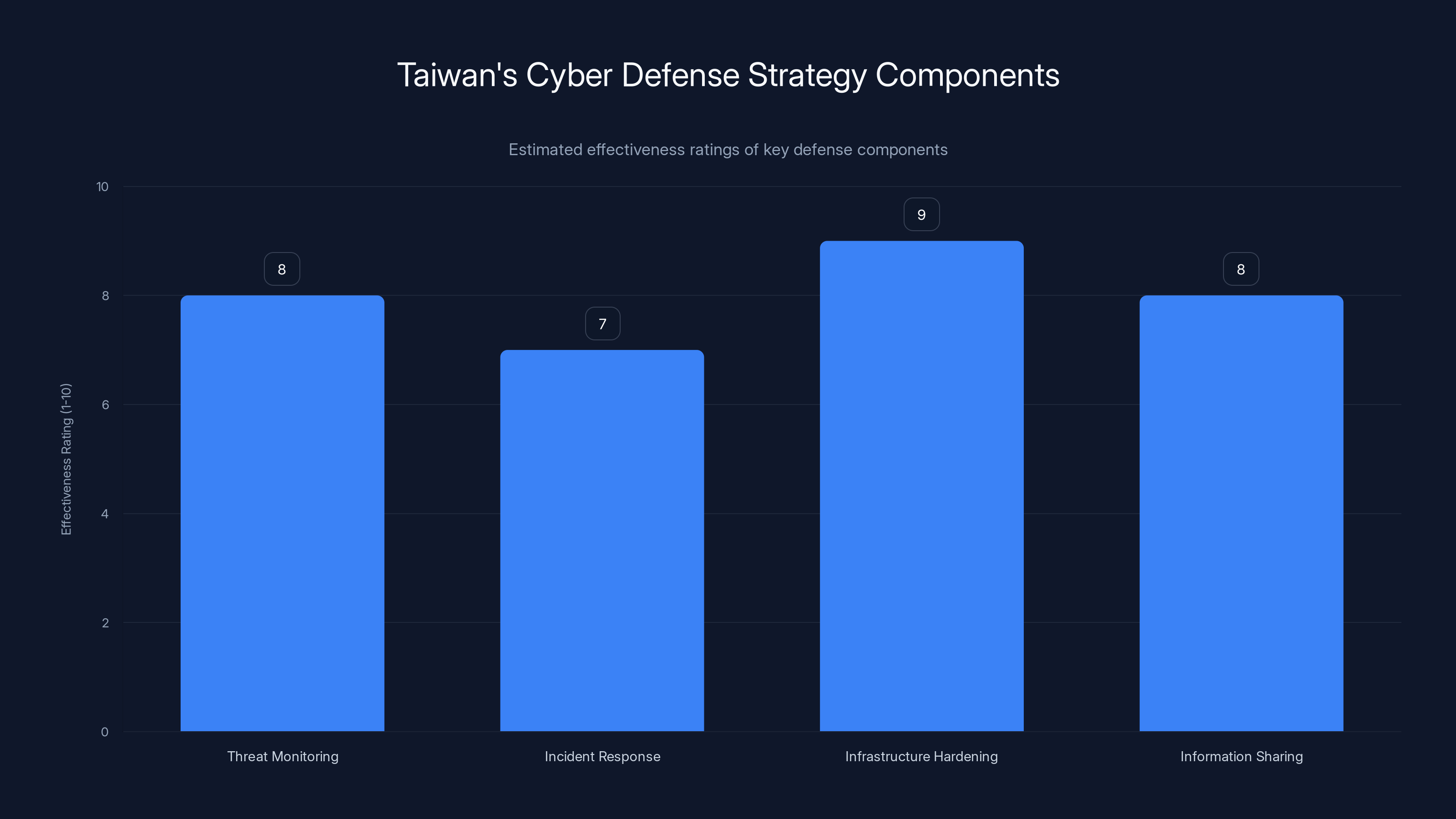
Taiwan's defense strategy emphasizes infrastructure hardening and real-time threat monitoring, both rated highly effective. Estimated data.
Defense Mechanisms: What Actually Works Against This Scale of Attack
Facing hundreds of millions of attacks yearly, Taiwan has had to implement defense strategies that work at massive scale.
Pattern Detection and Behavioral Analytics
Defending against 2.63 million daily attacks requires automation. Machine learning systems monitor traffic patterns and identify anomalies that suggest malicious activity. These systems can't catch everything, but they can significantly reduce the human workload and identify the most suspicious activity for human investigation.
The advantage of behavioral analytics is that it catches novel attacks. Traditional signature-based detection requires knowing about an attack before you can detect it. Behavioral systems detect when something is wrong, even if you've never seen that particular attack before.
Threat Intelligence Automation
When an attack is detected, information about it is automatically collected and fed into threat intelligence systems. Other organizations receive this information and can automatically update their defenses to detect similar attacks.
This automation is critical at scale. If humans had to manually process and disseminate threat intelligence, the system would bottleneck. Automation enables information to flow across the entire ecosystem in minutes rather than days.
Infrastructure Resilience Over Perfection
A key philosophical shift in Taiwan's defense strategy has been accepting that some attacks will succeed. Instead of trying to prevent 100% of attacks—an impossible task—the focus has shifted to ensuring that successful attacks don't cause catastrophic damage.
This means:
- Redundancy: If one system is compromised, backups can take over
- Segmentation: Compromise of one network segment doesn't lead to compromise of the entire organization
- Recovery capabilities: Even if an attack succeeds in causing disruption, systems can be recovered quickly
- Graceful degradation: Critical systems can continue operating at reduced capacity even if parts are offline
This shift from "prevent all breaches" to "ensure business continuity despite breaches" is more realistic and more effective.

The Broader Implications: What This Means for Global Cybersecurity
Taiwan's situation isn't unique. It's a preview of what's coming everywhere.
State-Sponsored Cyber Conflict as the New Normal
As geopolitical tensions increase, nation-states are investing heavily in cyber operations. Taiwan faces this threat because of its geographical location and political status. But similar threats are targeting:
- Eastern European nations in NATO facing Russian cyber operations
- US critical infrastructure facing attacks from multiple nation-states
- Japanese infrastructure facing increased attacks from China and North Korea
- Korean networks facing persistent North Korean operations
Cyber warfare isn't coming. It's here. Taiwan is simply experiencing it at the highest intensity.
The Attribution Problem
Taiwan's experience highlights a persistent problem in cyber defense: attribution. Even when you know you're being attacked and even when security researchers identify threat actors with high confidence, political attribution to nation-states requires evidence that meets a higher threshold.
China has deliberately designed its cyber operations to maintain this ambiguity. By using cutout organizations, delegating operations to contractors, and maintaining strategic ambiguity about what operations it authorizes, China ensures that any response must account for uncertainty about intent.
This works in China's favor. It allows operations to continue with lower risk of retaliation.
The Escalation Ladder
Another concerning implication of Taiwan's experience is understanding how cyber conflict escalates. What starts as reconnaissance can evolve into exploitation. Exploitation can evolve into persistent access. Persistent access can evolve into capability positioning for potential disruption.
Each step is reversible with enough effort and security investment. But if an adversary reaches the endpoint of that escalation—the ability to rapidly cause significant disruption—the defender loses. Deterrence becomes difficult when the attacker can cause damage faster than the defender can respond.
Taiwan is trying to stay ahead on this escalation ladder, but it's a continuous arms race.
Economic and Political Costs of Cyber Warfare
The impact of Taiwan's cyber war extends beyond direct damage from successful attacks.
Economic Costs
Defending against this volume of cyberattacks is expensive. Taiwan allocates significant government resources to cybersecurity. The private sector also invests heavily in security tools, personnel, and processes.
Additionally, the threat itself creates economic costs:
- Investment uncertainty: International investors are cautious about investing in Taiwan due to geopolitical risk
- Brain drain: Talented cybersecurity professionals are recruited by US, European, and other international companies, reducing local talent
- Supply chain costs: Defensive security measures increase the cost of doing business for Taiwanese exporters
These costs are real, even when attacks don't succeed.
Political and Psychological Impacts
Perhaps the most significant impact is psychological and political. Each attack that's detected and reported reinforces the narrative that Taiwan is under siege. Media coverage amplifies the message. Public confidence in government ability to protect citizens is tested.
This is exactly what China's hybrid war doctrine intends. By making attacks visible and coordinating them with military operations and political speeches, China amplifies the psychological impact beyond what the technical damage would suggest.
Taiwan's government has had to balance transparency about the threat with avoiding demoralizing the population or creating a sense of panic.

Future Outlook: What Comes Next?
Looking ahead, security analysts expect several developments in China's cyber operations against Taiwan.
Increased Sophistication
Attack capabilities will continue to increase in sophistication. This includes:
- Supply chain penetration: Deeper compromise of vendors and contractors
- Hardware-level implants: Attacks not just at the software level but at semiconductor and hardware level
- Cryptographic attacks: Development of quantum computing and post-quantum cryptography capabilities
- AI-enhanced operations: Machine learning to optimize attack strategies and evade detection
Geographic Expansion
Capabilities developed against Taiwan will be deployed elsewhere. Other nations will face similar attacks as China tests and refines its techniques on different targets with different defensive capabilities.
Escalation Risks
If a significant cyberattack causes major disruption—power outages, financial system failure, casualties from hospital system compromise—the risk of military escalation increases substantially. Cyber conflict could transition from a separate domain of competition to a precursor or accompaniment to kinetic conflict.
This escalation risk is what keeps military strategists awake at night. The line between cyber warfare and conventional warfare, once clearly defined, is increasingly blurred.
Recommendations for Taiwan and Other Targets
Based on Taiwan's experience, several recommendations emerge for any nation facing similar threats.
Invest in Indigenous Capability
While international support is valuable, nations must develop their own cybersecurity capabilities. This means:
- Education: Training domestic cybersecurity talent
- Research: Funding indigenous cybersecurity research and development
- Industry: Supporting private sector security companies
- Military: Developing military cyber operations capabilities
Dependence on a single ally for cyber defense creates vulnerabilities. Indigenous capability provides resilience.
Implement Comprehensive Defense-in-Depth
No single security tool or approach will stop advanced threats. Effective defense requires layered approaches:
- Preventative: Blocking attacks at the network perimeter
- Detective: Identifying attacks that make it past preventative measures
- Responsive: Containing and eradicating attacks that succeed
- Resilience: Maintaining operations despite successful attacks
Share Intelligence Freely
Threat intelligence only works when shared rapidly and comprehensively. Nations and industries must establish mechanisms for sharing detection information, attack patterns, and defensive solutions.
Prepare for Crisis Management
When—not if—major attacks succeed, the response must be rapid, coordinated, and pre-planned. This requires:
- Crisis playbooks: Pre-arranged procedures for different attack scenarios
- Inter-agency coordination: Clear roles and responsibilities across government
- Private sector coordination: Pre-established relationships with industry for rapid response
- Public communication: Pre-planned messaging to maintain calm and accurate information during crises
Conclusion: The New Reality of Statecraft
Taiwan's 2.63 million daily cyberattacks represent a fundamental shift in how great powers compete. Warfare no longer means soldiers and tanks exclusively. It means simultaneous attacks across multiple domains: kinetic, cyber, information, economic.
The scale and sophistication of attacks China conducts against Taiwan foreshadow what nations worldwide will increasingly face. The threat isn't hypothetical. It's not a future concern. It's here, now, measured in hundreds of millions of attacks annually.
Defense is possible. Taiwan demonstrates that despite years of sophisticated Chinese operations, critical infrastructure continues functioning. Hospitals still serve patients. Banks still process transactions. The power stays on.
But defense requires investment, preparation, and constant vigilance. It requires accepting that breaches will happen and building systems that are resilient despite breaches. It requires training and retaining cybersecurity talent in an environment where international recruitment constantly drains expertise.
Most importantly, it requires understanding that in the 21st century, national security depends critically on cyber security. Nations that fail to develop robust defenses will lose in great power competition, not with soldiers on battlefields but with bits and bytes in digital battlefields.
Taiwan is fighting that battle every single day. The world should be paying attention.
FAQ
What exactly constitutes a cyberattack in Taiwan's reporting?
Taiwan's National Security Bureau counts cyberattacks against critical infrastructure organizations—hospitals, banks, government agencies, power systems, telecommunications providers, and water utilities—as official incidents. This includes detected reconnaissance efforts, exploitation attempts, credential attacks, and intrusion attempts. Not every suspicious packet counts; the focus is on organized, directed threats against systems essential to national function.
How does Taiwan detect and respond to 2.63 million daily attacks?
Taiwan employs automated systems using machine learning and behavioral analytics to detect attack patterns without manual intervention. Threat intelligence is automatically collected and shared across critical infrastructure sectors through information sharing centers. Human incident response teams focus on the most suspicious activity, while automated defenses handle routine threats at scale.
Why does China coordinate cyberattacks with military operations?
Coordinating cyber operations with military activities creates a combined messaging effect. Military patrols demonstrate willingness to conduct operations near Taiwan's territory while simultaneous cyberattacks demonstrate vulnerability of critical infrastructure. Together, they reinforce the narrative that Taiwan cannot defend itself against China, serving as psychological warfare alongside kinetic demonstrations.
What is hybrid warfare and how does it apply to Taiwan?
Hybrid warfare combines military force, cyberattacks, information operations, and economic coercion in coordinated campaigns to achieve political objectives without triggering traditional warfare. China employs this doctrine against Taiwan using simultaneous military intimidation, cyber attacks on infrastructure, disinformation campaigns, and economic pressure to create an environment of vulnerability and demoralization.
Can attribution definitively prove China is responsible for these cyberattacks?
Attribution in cyberspace is never 100% certain due to deliberate misdirection and use of proxy infrastructure. However, cybersecurity researchers assess with high confidence that threat groups like Volt Typhoon and Brass Typhoon operate with state-level resources and target sets aligned with Chinese national interests. Technical indicators, operational patterns, and targeting choices support government attribution, though political attribution requires higher evidentiary thresholds.
What defensive strategies have been most effective for Taiwan?
Taiwan's most effective strategies include real-time threat intelligence sharing across sectors, network segmentation to limit breach impact, infrastructure redundancy to maintain operations despite attacks, aggressive patching and update regimens, and adoption of multi-factor authentication. Rather than trying to prevent all attacks, Taiwan focuses on ensuring that successful attacks don't cause catastrophic disruption through resilience and rapid response capabilities.
How is the United States supporting Taiwan's cyber defense?
The US provides real-time threat intelligence about Chinese operations, technical assistance in building detection capabilities, training and deployment of experienced cybersecurity professionals, and advanced security technology. The approach emphasizes building indigenous Taiwanese capabilities rather than directly defending Taiwan, reflecting a strategy of helping allies defend themselves rather than defending them directly.
What are the implications of Taiwan's cyberattack volume for other nations?
Taiwan's experience serves as a preview of state-sponsored cyber warfare at scale. As geopolitical tensions increase globally, other nations face similar threats: Eastern European NATO members from Russia, Japan and South Korea from China and North Korea, and US infrastructure from multiple adversaries. Understanding Taiwan's defensive challenges and approaches illuminates strategies for defending against coordinated, persistent, sophisticated cyber operations.
How do threat actors like Volt Typhoon operate differently from cybercriminals?
Threat actors like Volt Typhoon conduct long-term intelligence gathering and infrastructure reconnaissance rather than seeking immediate financial gain. Their operational objective is to establish persistent access, map network architecture, understand operational relationships, and position for potential future disruption. This patient, strategic approach differs from cybercriminal groups that monetize breaches quickly, making state-sponsored actors harder to detect and more dangerous long-term.
What makes Taiwan's critical infrastructure particularly vulnerable to cyberattacks?
Taiwan's critical infrastructure is vulnerable due to legacy systems with limited security capabilities, integration of information technology with operational technology without sufficient air-gapping, limited cybersecurity personnel compared to demand, and the challenge of maintaining security while ensuring 24/7 operational availability. Additionally, the sophistication and persistence of state-sponsored Chinese operations exceed defensive capabilities of many Taiwanese organizations operating independently.
The Broader Security Implications
Taiwan's cybersecurity crisis offers crucial lessons for the entire world. As digital infrastructure becomes increasingly central to national function, the vulnerability of that infrastructure to sophisticated, persistent, state-sponsored attacks becomes a central security concern.
The numbers themselves—2.63 million attacks daily, 113% increase year-over-year—represent an unprecedented scale of hostile cyber activity against a single nation's infrastructure. Yet Taiwan continues functioning. The power stays on. Hospitals serve patients. This resilience provides hope that defensive strategies can work.
But it also demonstrates that defense against determined state actors is expensive, continuous, and never complete. Nations must invest heavily, train personnel aggressively, share intelligence openly, and accept that in modern conflict, cybersecurity is national security. Taiwan is learning these lessons in real-time, at tremendous cost, and the rest of the world would be wise to learn from Taiwan's experience before facing similar threats.
The hybrid war has arrived. It's not coming in the future. It's happening now, measured in millions of daily attacks, and Taiwan is on the front lines.

Key Takeaways
- Taiwan endured 2.63 million cyberattacks daily in 2025, a 113% increase since 2023, targeting critical infrastructure including hospitals, banks, and government agencies
- Chinese-linked threat groups like Volt Typhoon conduct sophisticated, coordinated operations aligned with Beijing's strategic interests in infrastructure reconnaissance and data theft
- China synchronizes cyberattacks with military operations and political events, demonstrating a hybrid war doctrine combining kinetic, cyber, information, and economic components
- Taiwan's defense strategy emphasizes automation, threat intelligence sharing, infrastructure redundancy, and resilience over attempting to prevent all breaches
- Taiwan's experience foreshadows cyber threats facing other allied nations globally as state-sponsored operations become the dominant form of great power competition
Related Articles
- Critical Infrastructure Breach: Engineering Firm Hack Exposes US Utilities [2025]
- Digital Rights 2025: Spyware, AI Wars & EU Regulations [2025]
- ESA Cyberattack: What You Need to Know About the 200GB Breach [2025]
- Federal Cybersecurity Crisis: Why Government Digital Defense Is Collapsing [2025]
- Government Spyware Targeted You? Complete Action Plan [2025]
- Juice Jacking: How to Protect Your Phone from Public Charging Threats [2025]
![Taiwan's 2.5M Daily Cyberattacks: China's Hybrid War Strategy [2025]](https://tryrunable.com/blog/taiwan-s-2-5m-daily-cyberattacks-china-s-hybrid-war-strategy/image-1-1767650915119.jpg)



