Qilin Ransomware Gang Hits Tulsa Airport: What You Need to Know [2025]
Last week, security researchers uncovered something that should worry you. A Russian-speaking ransomware gang called Qilin claimed responsibility for breaching Tulsa International Airport, one of the busiest commercial airports in the central United States. They didn't just steal data—they're using it as leverage, dropping samples of sensitive files on the dark web as proof. According to a report by Cyfirma, this attack is part of a broader trend of increasing ransomware threats.
This isn't some random attack on a random target. Qilin has become one of the most prolific ransomware threats operating today. In 2025 alone, they've allegedly hit over 1,000 organizations globally. That's roughly three breaches per day. By January 2026, they'd already claimed 50+ victims. The Tulsa attack is just the latest domino to fall, as noted in Cybernews.
What makes this case particularly important isn't just the scale. It's what it reveals about how modern ransomware operations work, who's behind them, and what we're all doing wrong when it comes to protecting critical infrastructure. If an airport like Tulsa can be compromised, yours likely can be too.
Here's the thing: most people think ransomware is just about money. Pay the ransom, get your files back, move on. But that's not how it works anymore. Groups like Qilin operate under what's called a RaaS model—ransomware-as-a-service. They're not just criminals. They're running a business. A sophisticated, well-organized business that's stealing data from thousands of organizations every year and selling access to the highest bidder, as explained in SiliconANGLE.
In this guide, we're breaking down everything you need to know about the Tulsa airport attack, the Qilin group, how they operate, and most importantly, what you can do to protect yourself and your organization.
TL; DR
- Qilin breached Tulsa International Airport and leaked 18 samples of sensitive data as proof, including employee IDs, financial records, and executive communications, as detailed in TechRadar.
- The group claims 1,000+ breaches in 2025 and 50+ in January 2026 alone, making them one of the most active ransomware threats globally, according to Cyfirma.
- Qilin operates as a RaaS (ransomware-as-a-service) model, with unknown affiliates conducting attacks on behalf of the criminal organization, as reported by Cybernews.
- Leaked data includes PII, financial documents, governance records, and vendor information that can be used for identity theft, fraud, and corporate espionage, as noted in HIPAA Journal.
- The airport serves 3+ million passengers annually and contributes an estimated $6 billion to the regional economy, making this attack a critical infrastructure concern, as highlighted by Cyfirma.
- No ransom demand has been publicly disclosed, but Qilin historically demands millions from high-value targets, as discussed in SiliconANGLE.
- Critical response steps include incident notification, forensic investigation, law enforcement reporting, and credit monitoring for affected employees, as recommended by Wiz.io.
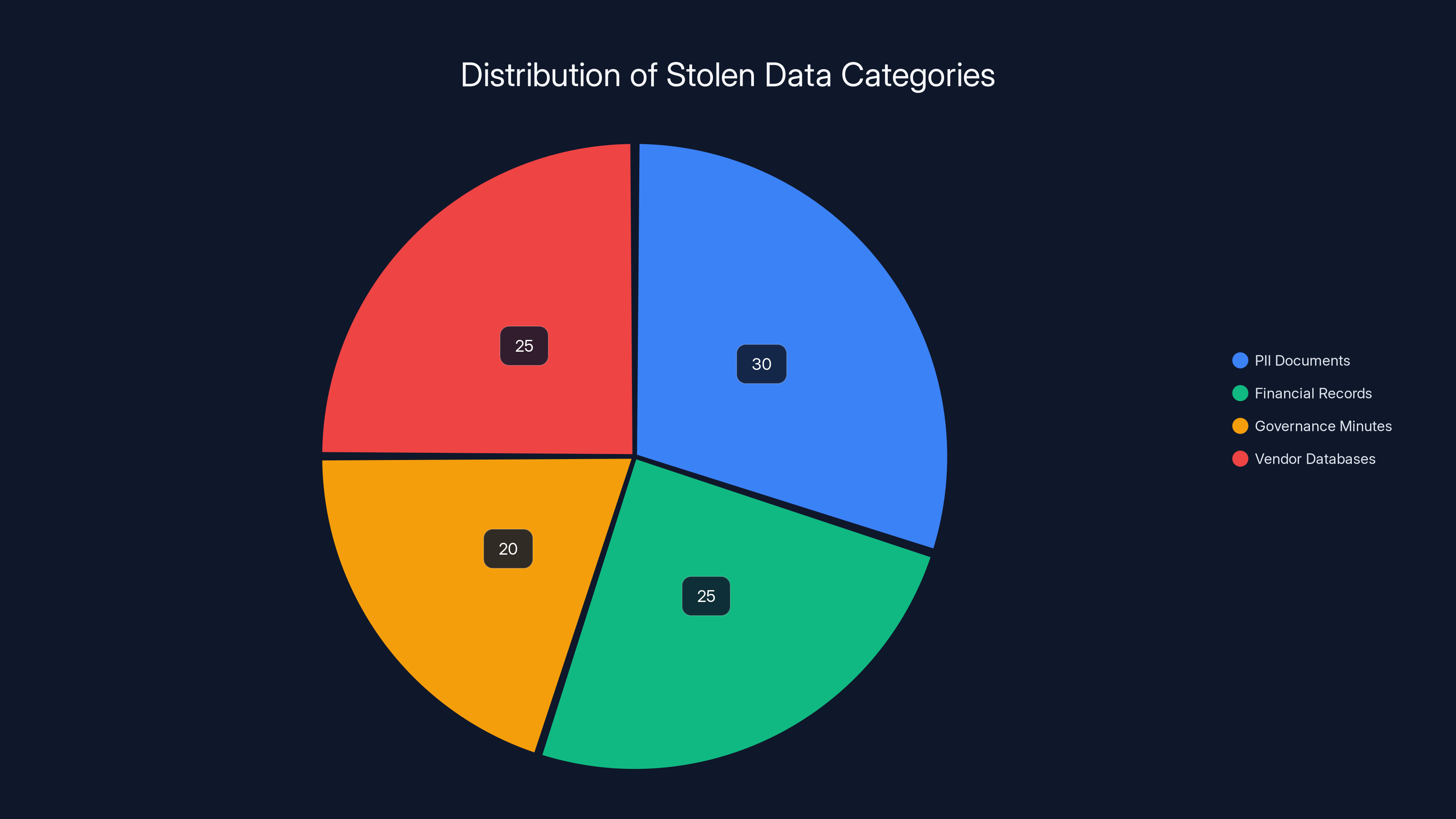
Estimated data shows a balanced distribution of stolen data categories, highlighting the varied risks each type poses. Estimated data.
What Happened at Tulsa International Airport
On a routine day in early 2025, cybersecurity researchers monitoring dark web activities noticed something alarming. The Qilin ransomware gang had posted a new victim to their public leak site. The target: Tulsa International Airport in Oklahoma, as reported by Cybernews.
But this wasn't just a name on a list. Qilin did what they always do when they want to prove they're serious—they included samples. Eighteen different files pulled directly from the airport's systems. These weren't random documents. They were carefully selected to demonstrate exactly how deep into the organization they'd penetrated.
What was in those files?
Security researchers who examined the leaked samples found executive emails. The kind of sensitive internal communications that no organization wants public. There were also email chains between airport executives and what researchers described as "high-level banking officials." These aren't casual conversations. In the airport context, these are likely discussing critical financial decisions, contracts, and infrastructure investments.
The sample dump also included employee identification documents. Driver's licenses. Passports. These are the kinds of personally identifiable information (PII) that criminals can use immediately for identity theft, fraudulent loan applications, or selling on dark web marketplaces.
But it goes much deeper. The leaked documents included annual budget spreadsheets and revenue projections. Confidentiality agreements and non-disclosure agreements that reveal what contracts the airport has. Telehealth reports suggesting which employees are dealing with health issues. Meeting minutes from governance sessions. Insurance documents. Banking communications. Tenant databases showing which companies operate at the airport. Vendor revenue sheets revealing which partners the airport relies on. Even court case documents suggesting ongoing disputes.
The timeline tells you something important
When researchers analyzed the leaked files, they noticed something: the documents dated from 2022 through 2025. This isn't old data that someone had sitting around. Some of these files are from just weeks before the public announcement. That means Qilin had active access to the Tulsa airport's systems for years. They weren't in and out quickly. They were dug in, collecting intelligence, deciding what to steal, and waiting for the right moment to make their move, as noted in Cyfirma's report.
Why is this timeline important? Because it suggests that the airport's security teams didn't catch them. They didn't notice suspicious activity. The attackers moved through systems, copied sensitive data, and prepared for potential extortion without triggering any major alarms. That's a massive red flag for every organization thinking they're protected.
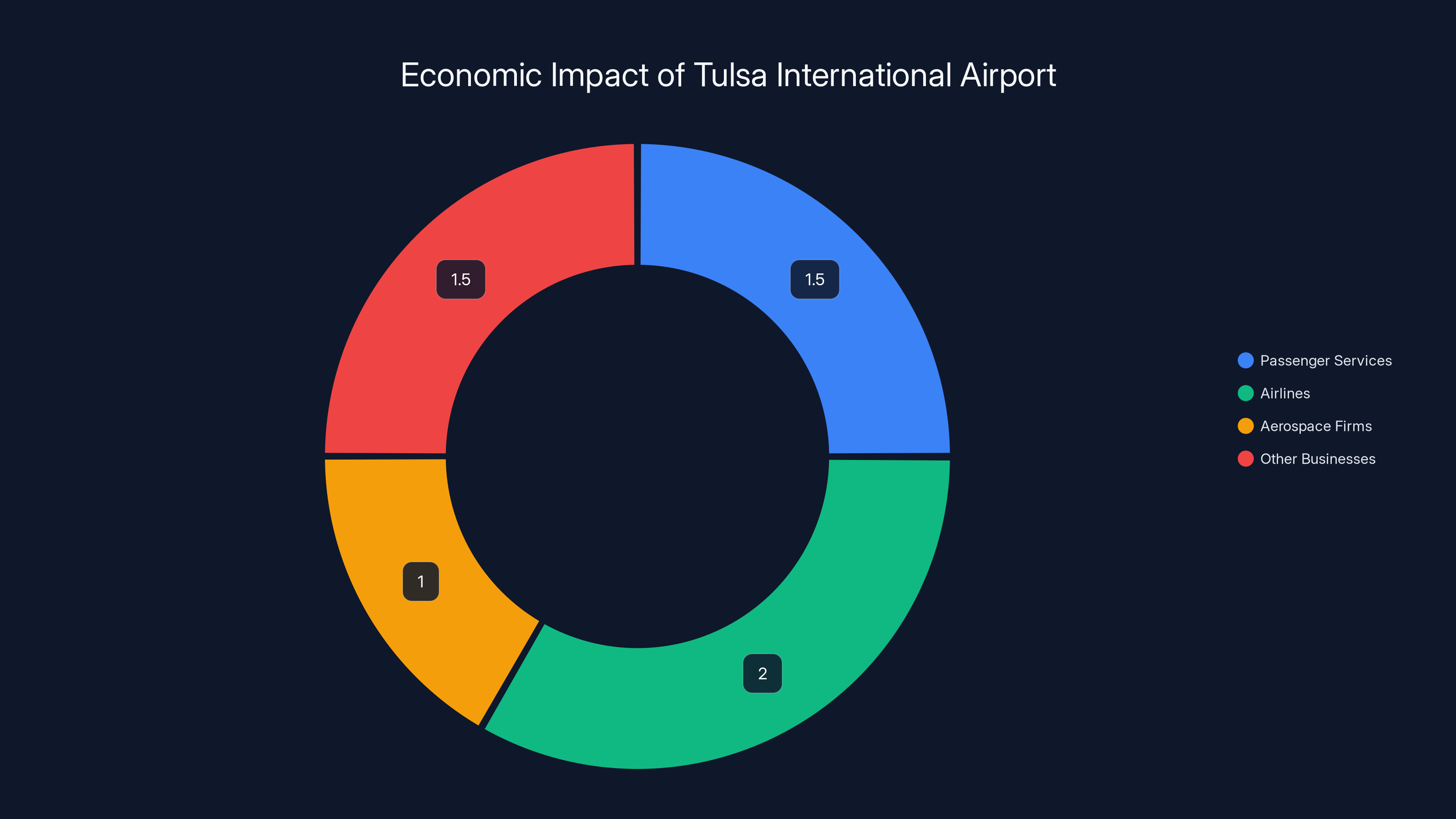
Tulsa International Airport contributes approximately $6 billion annually to the regional economy, supporting diverse sectors such as passenger services, airlines, aerospace firms, and other businesses. (Estimated data)
Who Is Qilin and How Dangerous Are They?
Qilin first appeared on the threat landscape around four years ago. Nobody knew much about them at first. They were just another ransomware group among dozens operating out of Russia and Eastern Europe. But over that time, they've evolved from a minor player to one of the most dangerous criminal organizations targeting businesses worldwide, as detailed in Cyfirma's intelligence report.
The explosive growth
What makes Qilin different from other ransomware groups is their scale and organization. In 2025, security researchers tracking the group documented over 1,000 successful breaches. That's not a typo. One thousand organizations compromised in a single year. By the time we hit January 2026, they'd already added 50+ more victims to their list, as reported by Cybernews.
To put that in perspective: that's roughly three successful breaches every single day. Every morning you wake up, Qilin has probably compromised another organization. A hospital. A financial services company. A retailer. A government agency. A transportation hub. The scope is breathtaking.
How they operate
Qilin isn't one hacker sitting in a basement somewhere. They run what the security industry calls a RaaS operation—ransomware-as-a-service. Think of it like an Uber for cybercrime. The core Qilin team handles the business operations, manages the infrastructure, develops the malware, and maintains the leaked data sites. But the actual attacks? Those are conducted by affiliates.
These affiliates are essentially contractors. Independent hackers or hacking groups who buy access to Qilin's ransomware toolkit, deploy it against targets, and then split the ransom payments with the main organization. The Qilin team typically takes 20-30% of whatever ransom gets paid. The affiliates keep the rest, as explained in SiliconANGLE.
This model has several advantages for the criminal organization. First, it provides deniability. When law enforcement investigates, they're chasing down affiliate hackers, not the core Qilin team. Second, it scales infinitely. Instead of hiring more people, you just recruit more affiliates. Third, it distributes risk. If an affiliate gets arrested, the core organization is still operational.
The identities of Qilin's affiliates remain unknown to security researchers and law enforcement. The group uses sophisticated operational security, anonymous payments through cryptocurrency, and regularly changes their infrastructure. They're not operating recklessly. They're running a professional criminal enterprise.
Why Qilin targets what they target
Qilin isn't indiscriminate. They're strategic. They target organizations that are most likely to pay large ransoms. That means organizations with significant revenue, critical operational needs, and insurance policies that cover ransomware payments.
Airports fit this profile perfectly. An airport that can't function loses money every single hour it's down. Airlines can't land planes. Passengers miss flights. Vendors can't operate. The economic pressure to restore operations quickly is enormous. That pressure translates into ransom payments.
Qilin also likely knows that critical infrastructure—including transportation systems—operates under regulatory requirements that mandate disclosure and recovery timelines. An airport that gets hit on a Thursday probably needs to notify regulators by the following Tuesday. They need their systems operational by Friday. That compression creates desperation, and desperate organizations pay whatever it takes.
The Tulsa Attack in Context: Why Airports Are Targets
You might wonder why a ransomware group would target an airport at all. Aren't there easier targets? The answer is more calculated than you'd think.
Critical infrastructure means critical leverage
Tulsa International Airport isn't a mega-hub like Dallas-Fort Worth or Atlanta. It's a mid-size commercial airport. But mid-size doesn't mean unimportant. The airport handles approximately 80 flights per day across carriers including Southwest, American, Delta, and United. It serves more than 3 million passengers annually, as highlighted in Cyfirma's report.
Beyond the passenger numbers, consider the economic impact. The airport supports an estimated 40,000 jobs across airlines, airport operations, aerospace firms, and related businesses. The total economic contribution to the region is roughly $6 billion annually.
Now imagine what happens if those systems go down. Planes can't land. Passengers are stranded. Airline operations are disrupted not just at Tulsa but across the entire network. Cargo isn't moving. Maintenance schedules are blown. The ripple effects are massive.
The ransom calculation
When Qilin targets an airport, they're not just thinking about the organization itself. They're thinking about the broader ecosystem. The airport's insurance policy probably covers ransomware incidents. The organization's budget can absorb a seven-figure payment. The stakeholders—airlines, passengers, the community—all create pressure for quick resolution.
In cases where ransom demands have been publicly disclosed, airport ransomware attacks have typically resulted in demands ranging from
Why pay that much? Because the cost of non-payment is higher. An airport shutdown for a week costs more than a ransom payment. The operational, economic, and reputational damage becomes unbearable.
The information asymmetry problem
Another reason airports are attractive targets: attackers often have better information about airport systems than the airport does.
Airports run incredibly complex networks. Passenger systems connect to baggage systems, which connect to security systems, which connect to operational systems, which connect to financial systems. There are hundreds of vendors and contractors with varying levels of system access. An attacker who can compromise one vendor might get access to the entire ecosystem.
Moreover, airport IT departments are often stretched thin. They're managing legacy systems that date back decades, running alongside modern cloud infrastructure, all of which need to work together seamlessly. Legacy systems don't get security updates frequently. Modern systems sometimes prioritize speed over security. The gap between these systems creates vulnerability.
Qilin likely spent weeks or months mapping the airport's network before deploying ransomware. They probably knew which systems were monitored, which weren't. Which backups existed, where they were stored, and whether they were properly isolated. By the time they actually deployed the ransomware, they'd already planned exactly how to make recovery difficult.

The pie chart illustrates the distribution of different types of data stolen during the Tulsa airport attack. Financial documents and operational data make up the largest portions of the breach. Estimated data.
What Data Was Actually Stolen and Why It Matters
When you look at that list of stolen documents—executive emails, employee IDs, financial records, governance minutes, vendor databases—it's tempting to think of it as just data. But that's wrong. Each category of stolen data represents a different potential harm.
Personally Identifiable Information (PII)
The employee IDs, driver's licenses, and passports are immediately valuable to criminals. On dark web marketplaces, a legitimate-looking driver's license can sell for
A criminal with your name, address, date of birth, and government ID number can commit identity fraud. They can apply for credit cards in your name. They can file tax returns and claim refunds. They can open bank accounts. They can take out loans. The damage from identity fraud typically takes years to recover from and costs victims thousands of dollars.
For the airport's employees, the stolen IDs mean they're now at risk. The airport should have sent notices to affected employees weeks ago. They should offer credit monitoring services. Many haven't done this proactively.
Financial and Revenue Documents
The budget spreadsheets and revenue projections reveal how much money the airport makes, where that money comes from, and what operations are most profitable. Competitors could use this to undercut pricing. Hackers could use it to inform ransom demands.
The vendor revenue sheets are particularly sensitive. They show which companies the airport relies on, how much the airport pays them, and what profit margins vendors are working with. A vendor that's making 5% margins is more vulnerable to coercion. A competitor knowing those margins could undercut by 2% and eliminate the vendor entirely.
Governance and Meeting Minutes
Meeting minutes from governance sessions reveal internal debates, decision-making processes, and sometimes disagreements between leadership. Competitors gain intelligence about the airport's strategic direction. Activists could use the information for leverage. Regulators could target specific decisions that were discussed.
Banking Communications
Emails between airport executives and banking officials are potentially the most sensitive. These communications likely discuss credit facilities, revolving lines of credit, debt covenants, and financial negotiations. A hacker with access to these communications could potentially manipulate financial relationships, demand leveraged access to accounts, or use the information to conduct sophisticated social engineering.
Healthcare Information
Telehealth reports suggest employees were receiving telehealth services through the airport's benefits program. These reports could reveal medications employees are taking, diagnoses they've received, and health conditions they're managing. This information is protected under HIPAA in many cases, but once it's leaked on the dark web, the protection doesn't matter. Criminals can use health information for blackmail, extortion, or targeted social engineering.
The cascading impact
What makes this comprehensive data theft particularly damaging is that it's not siloed. A criminal with all of this information together can construct a complete picture of how the airport operates, who makes decisions, what vulnerabilities exist, and how to apply pressure.
They could contact a vendor and say, "We know you make 5% margins and you're dependent on this airport for 40% of your revenue. If you don't transfer $50,000 to this cryptocurrency wallet, we're releasing your revenue data and your contract terms to competitors."
Or they could contact an employee and say, "We know you were recently prescribed anxiety medication according to your telehealth records. We have your medical information. We also have your home address and your government ID. Cooperate with us or we're releasing this information."
This is how comprehensive data theft escalates beyond the initial ransom demand. It creates ongoing vulnerability and ongoing opportunities for extortion.

The RaaS Business Model Explained
To understand why Qilin is so successful, you need to understand how they make money. And that means understanding the RaaS business model.
Ransomware-as-a-Service operates like any legitimate software business, except the software is designed to encrypt your files and the business model is extortion.
How the affiliate model works
Qilin doesn't employ hackers. Instead, they recruit affiliates through dark web forums and private channels. A potential affiliate might see a post: "Qilin RaaS recruiting. Proven track record. 30% payout. Secure infrastructure. Apply here."
The affiliate applies. If approved, they gain access to Qilin's infrastructure. This includes the ransomware builder (tools to customize the malware for specific targets), the command and control servers (infrastructure to communicate with infected machines), the negotiation platform (where ransom demands are made and discussed), and the payment processing system (typically using cryptocurrency to receive ransom payments).
Once the affiliate has access to these tools, they're responsible for finding targets, breaching them, deploying ransomware, and negotiating ransom payments. Qilin stays in the background.
When ransom is paid, the cryptocurrency goes into a wallet. Qilin extracts their percentage—typically 20-30%—and the remaining funds go to the affiliate. The beauty of this model for Qilin is that they scale infinitely without increasing their infrastructure costs proportionally.
Revenue streams beyond ransom
But Qilin doesn't just make money from ransom payments. They run a sophisticated operation with multiple revenue streams.
Second, they operate a data marketplace. Once data is stolen and the organization refuses to pay ransom, Qilin doesn't delete the data. They sell it. Competitors might pay for intelligence. Fraudsters might pay for employee data. Identity theft rings might pay for PII. The leaked documents from Tulsa are probably already on sale on dark web marketplaces.
Third, they likely sell access to their RaaS platform itself. New ransomware groups sometimes license Qilin's technology instead of developing their own. Qilin makes money from those licenses.
Fourth, some reports suggest RaaS groups like Qilin have begun offering "protection" services to organizations that have been compromised. Pay us money, and we won't release your data. This is essentially pure extortion on top of the ransomware extortion.
Why the model is so difficult to disrupt
Law enforcement faces a fundamental problem with RaaS operations: they're distributed. You can arrest one affiliate, but there are dozens more. You can shut down one command and control server, but the infrastructure is distributed across multiple countries. You can try to trace cryptocurrency payments, but modern money laundering through mixers and exchanges makes that nearly impossible.
Moreover, the affiliates often don't know who the core Qilin team members are. So arresting an affiliate doesn't give you actionable intelligence about the organization itself. The core team knows this, which is why they tolerate some law enforcement pressure. They know their affiliate network provides a buffer.

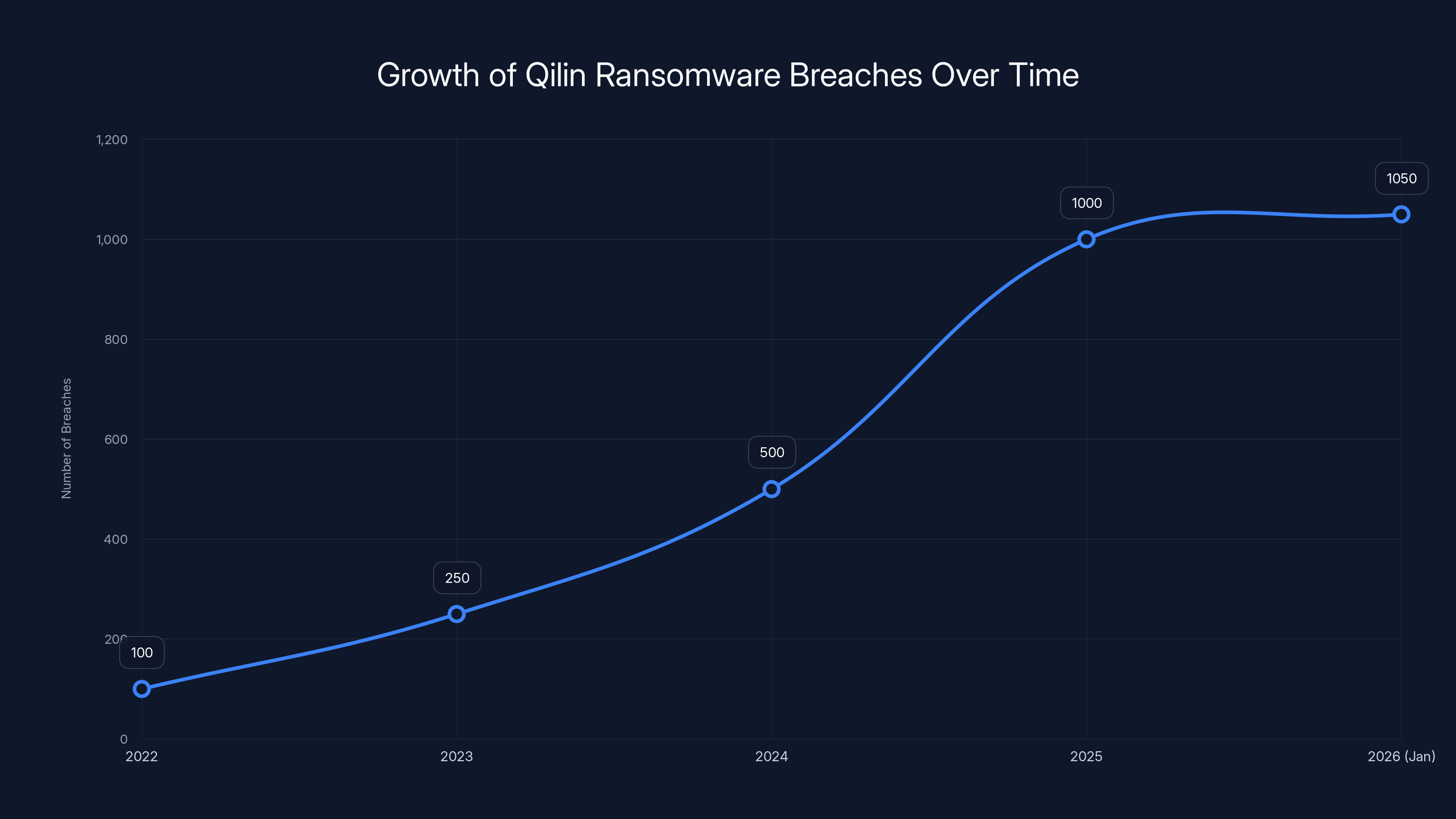
Qilin's breach numbers have grown exponentially, reaching over 1,000 successful breaches in 2025 alone. Estimated data highlights their rapid expansion in the cybercrime landscape.
How Qilin Initially Breached the Airport
We don't know exactly how Qilin got into Tulsa International Airport's systems. The airport hasn't released technical details of the breach. But based on how similar attacks typically unfold and the timeline of the compromise, we can make some educated inferences.
The most likely initial access vector: Phishing
Statistically, the most common way ransomware groups gain initial access to networks is through phishing. An employee receives an email that appears to come from a trusted source—maybe a vendor, maybe IT support, maybe a partner organization. The email contains a link or an attachment.
The employee clicks the link or opens the attachment. Malware executes. The attackers now have a foothold inside the network.
For an organization like an airport, phishing is particularly effective because there are hundreds of employees. You don't need to trick a security expert. You just need to trick someone who's busy, someone who isn't trained, someone who doesn't think before clicking.
Secondary possibilities: Compromised credentials or unpatched systems
Phishing often isn't the attacker's only option. Qilin might have obtained employee credentials from a previous data breach at another organization. An employee at Tulsa airport might have reused their password from LinkedIn or Twitter. That password gets compromised, and the attacker tries it against the airport's systems. It works.
Alternatively, Qilin might have exploited an unpatched vulnerability. Airports typically run a mix of modern and legacy systems. A legacy baggage system from 2005 probably doesn't receive security patches regularly. If Qilin discovered a vulnerability in that system, they could exploit it directly without needing to compromise an employee.
Lateral movement and persistence
Once Qilin had initial access—whether through phishing, credentials, or a vulnerability—they didn't immediately deploy ransomware. Instead, they moved laterally through the network.
Lateral movement means accessing other systems from the infected machine. An attacker might compromise a workstation, then use that workstation to access servers. They might elevate their privileges gradually. They might install backdoors to maintain access if their initial foothold is detected and removed.
For Qilin, this lateral movement phase likely lasted weeks or months. They were mapping the network, identifying valuable data, disabling backups, and ensuring they had multiple ways to maintain access.
During this time, they were also searching for backup systems. Here's the critical insight: if an organization has good backups that are isolated from the network, ransomware is much less damaging. You can just restore from backup. So attackers target backups first. Qilin probably found the airport's backup systems and either deleted them or encrypted them alongside the production systems.
The final preparation phase
When everything was ready—backups disabled, data copied to Qilin's servers, command and control infrastructure established—they deployed the actual ransomware. The ransomware encrypted the critical systems that would cause maximum disruption. Not everything got encrypted, just the systems that matter most.
Once systems were encrypted, the ransom note appeared. It probably directed the airport to contact Qilin through a secure chat platform on the dark web. Qilin would then demand a specific amount—likely millions of dollars—and provide proof by releasing sample files.
But the Tulsa airport hasn't publicly disclosed a ransom demand. That suggests they either refused to negotiate, began paying, or are still in active negotiations. The silence is telling.

Critical Infrastructure Under Siege
The Tulsa attack isn't an isolated incident. It's part of a broader pattern: critical infrastructure is being systematically targeted by ransomware groups.
Why critical infrastructure matters
Critical infrastructure means systems that directly impact public safety, economic stability, or essential services. That includes power grids, water treatment systems, hospitals, emergency services, and transportation networks.
When these systems go down, people suffer immediately. A hospital ransomware attack means surgeries are delayed. Patients die because records are inaccessible. An electric grid attack means homes go without power. A water treatment attack means communities can't trust their water supply. A transportation attack means people are stranded.
This isn't abstract. When the Colonial Pipeline got hit with ransomware in 2021, the entire Eastern seaboard faced fuel shortages. When hospitals in Ireland were hit with ransomware, surgeries were postponed and patients were diverted to other facilities. When the Port of Los Angeles was hit with ransomware, shipping was disrupted.
The ransomware surge in transportation
Airports, railways, ports, and other transportation infrastructure are facing increasing ransomware pressure. Airports specifically have been hit frequently because they're lucrative targets with immediate pressure to pay.
Recent airport ransomware attacks include incidents at major international airports. These attacks typically follow the pattern we see at Tulsa: initial compromise, months of undetected access, lateral movement to critical systems, backup destruction, and then the ransomware deployment.
Why critical infrastructure is vulnerable
Critical infrastructure has unique vulnerabilities. First, a lot of it was built decades ago, before cybersecurity was a consideration. The systems were designed for a trusted environment where everyone inside the fence was assumed to be trusted.
Second, critical infrastructure often prioritizes availability over everything else. An airport can't afford a security update that requires downtime. So they patch slowly. Legacy systems sometimes don't get patched at all.
Third, critical infrastructure is often run by organizations that understand their domain expertly but lack cybersecurity expertise. An airport operator knows how to move planes and passengers efficiently. They don't necessarily know how to secure networks against sophisticated attackers.
Fourth, critical infrastructure often relies on specialized software that's not updated frequently and sometimes runs on operating systems that are no longer supported. A baggage system might run on Windows XP or custom Unix systems that haven't been maintained in years.
The regulatory response is too slow
Governments and regulatory bodies are trying to respond. The CISA (Cybersecurity and Infrastructure Security Agency) has issued guidance. The TSA (Transportation Security Administration) has issued security directives for airports and aviation. But these are often recommendations, not requirements. And even when they are requirements, compliance timelines are measured in years, not months.
Meanwhile, ransomware groups like Qilin are moving at internet speed. They're adapting their tactics constantly. By the time a regulation is written, the threat landscape has already evolved beyond what the regulation addresses.

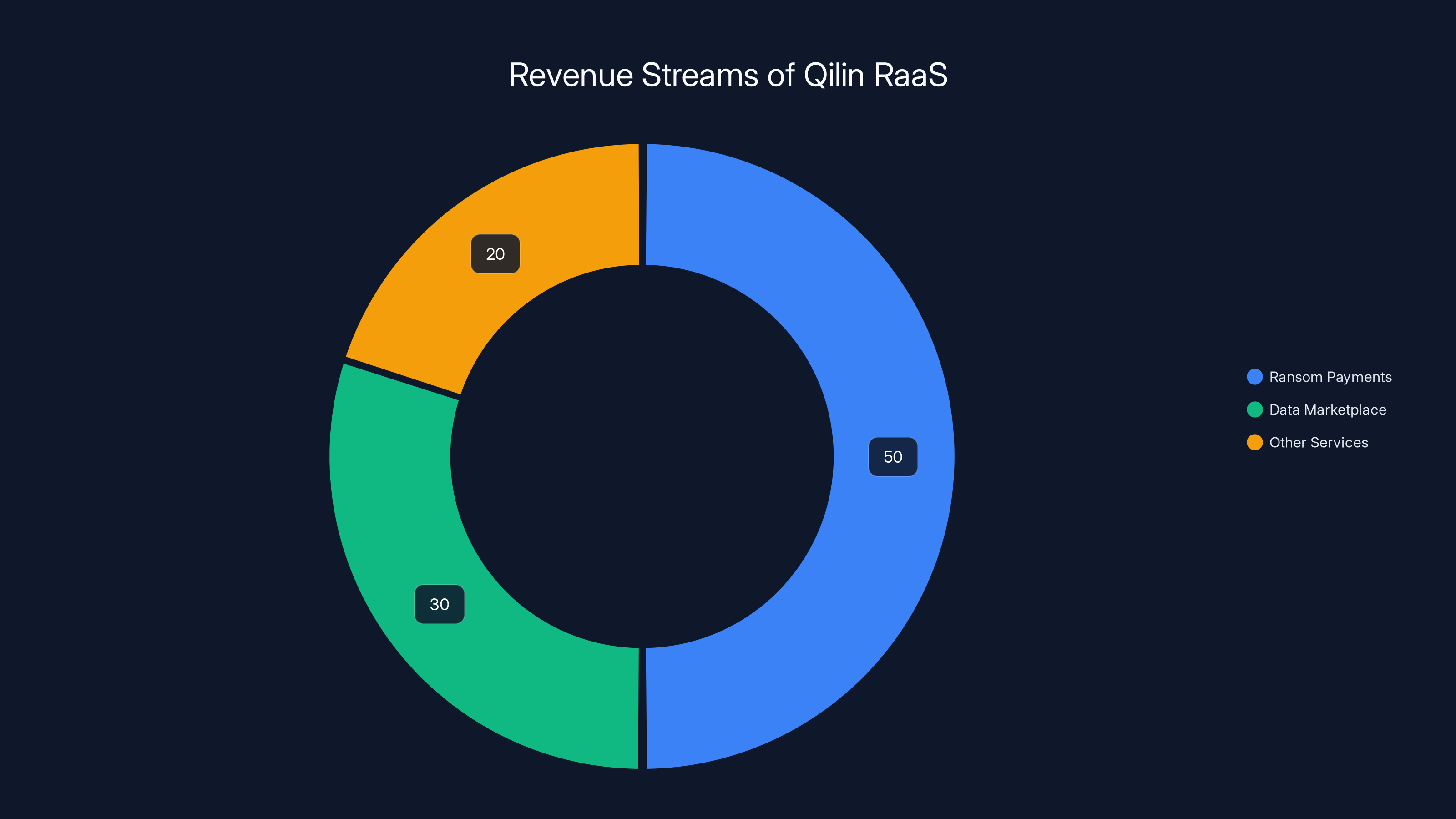
Estimated data shows that Qilin's revenue primarily comes from ransom payments (50%), followed by a significant portion from selling stolen data (30%). Other services contribute to the remaining 20%.
The Response So Far and What's Missing
Tulsa International Airport presumably launched an incident response the moment they discovered the breach. But here's what we don't know—and what the public hasn't been told.
What incident response should have included
A proper incident response to a ransomware attack should include several phases:
First, containment. This means disconnecting infected systems from the network, preventing further lateral movement, and identifying the scope of the compromise. This needs to happen fast—within hours, not days.
Second, forensics. This means investigating how the breach happened, what systems were accessed, what data was stolen, and how long the attackers had access. This requires experts who understand network forensics and can reconstruct the attack timeline.
Third, notification. Organizations are required by law to notify affected individuals and regulatory agencies when their personal data has been compromised. For employees with stolen government IDs and health information, the airport should have notified them immediately.
Fourth, remediation. This means fixing the vulnerabilities that allowed the breach in the first place, updating systems, strengthening security controls, and ensuring the attacker can't get back in.
Fifth, recovery. This means restoring systems from clean backups, validating that systems are working correctly, and resuming operations.
What's been publicly disclosed
As of now, the Tulsa airport hasn't issued a formal statement about the attack. That's unusual. When major organizations are breached, they typically issue statements. The silence could mean several things:
They might still be in active incident response. They might be negotiating with Qilin. They might be working with law enforcement. They might be waiting for guidance from their legal and insurance teams.
Or they might not have gone public because they've handled it quietly. Some organizations that are breached never announce it unless they're required to by law.
The regulatory notification requirement
Under various state laws and the Health Insurance Portability and Accountability Act (HIPAA), affected individuals have rights to notification. If the airport stored healthcare information (through its employee telehealth program), they're likely required to notify affected employees.
They should also file a breach report with their state's attorney general. Some airports have done this proactively. Others have fought it.
What's still missing: Transparency
One thing that would help the broader security community protect themselves: the airport sharing technical details of how they were breached. Not operational details that would endanger current systems, but enough information for other airports and transportation operators to understand the attack pattern.
When organizations get breached and publicly discuss the technical details, it helps everyone else defend. But many organizations are reluctant to do this. They worry about liability. They worry about their reputation. They worry about follow-up attacks from the same group or copycat attacks from other groups.

How Organizations Get Caught in Qilin's Crosshairs
Qilin doesn't attack randomly. They're strategic about target selection. Understanding what makes an organization attractive to them can help you assess your own risk.
Size and revenue
Qilin targets organizations large enough to have significant revenue but not so large that they have enterprise-grade security. They want organizations with budgets in the
An airport in a mid-size city hits that sweet spot. Hundreds of millions in annual budget. Significant annual revenue. But probably not the kind of security you'd find at a Fortune 500 company or a government agency.
Industry and leverage
Qilin targets industries where downtime creates immediate pressure. Hospitals. Financial services. Retailers. Manufacturers. Transportation. These industries can't afford to be down for long. The economic loss from a day of operations is enormous. That loss creates pressure to pay ransom.
Industries where downtime is less critical—think marketing firms or consulting companies—are less attractive. They can function in degraded mode. They can work with offline backups. Ransom demands meet resistance.
Insurance and financial capacity
Qilin knows which industries typically have insurance that covers ransomware. Hospitals often do. Airports often do. Retailers often do. The presence of insurance changes the negotiation dynamics. A victim with insurance is more likely to pay ransom because the payment comes from their insurance company.
Vulnerability indicators
Qilin likely monitors security indicators. They track which organizations patch regularly and which don't. They watch for public disclosures of vulnerabilities in common systems. They monitor job postings for security officer positions—if a company is hiring aggressively for security, it might indicate they just suffered a breach and are trying to improve.
They search for organizations using outdated software. Legacy systems that haven't been updated in years are more vulnerable. They look for organizations with weak network segmentation—if the entire network is on one flat network, lateral movement is easy.
Recon and monitoring
Before Qilin attacks, they probably spend time doing reconnaissance. They might search for publicly available information—DNS records, IP ranges, technology stacks. They might monitor network traffic. They might search the dark web for any leaked credentials associated with the target.
They definitely monitor the organization's social media and public announcements. They look for signs of security incidents, security team changes, or announcements about security initiatives. These are often signs that an organization's security posture has been through a change.
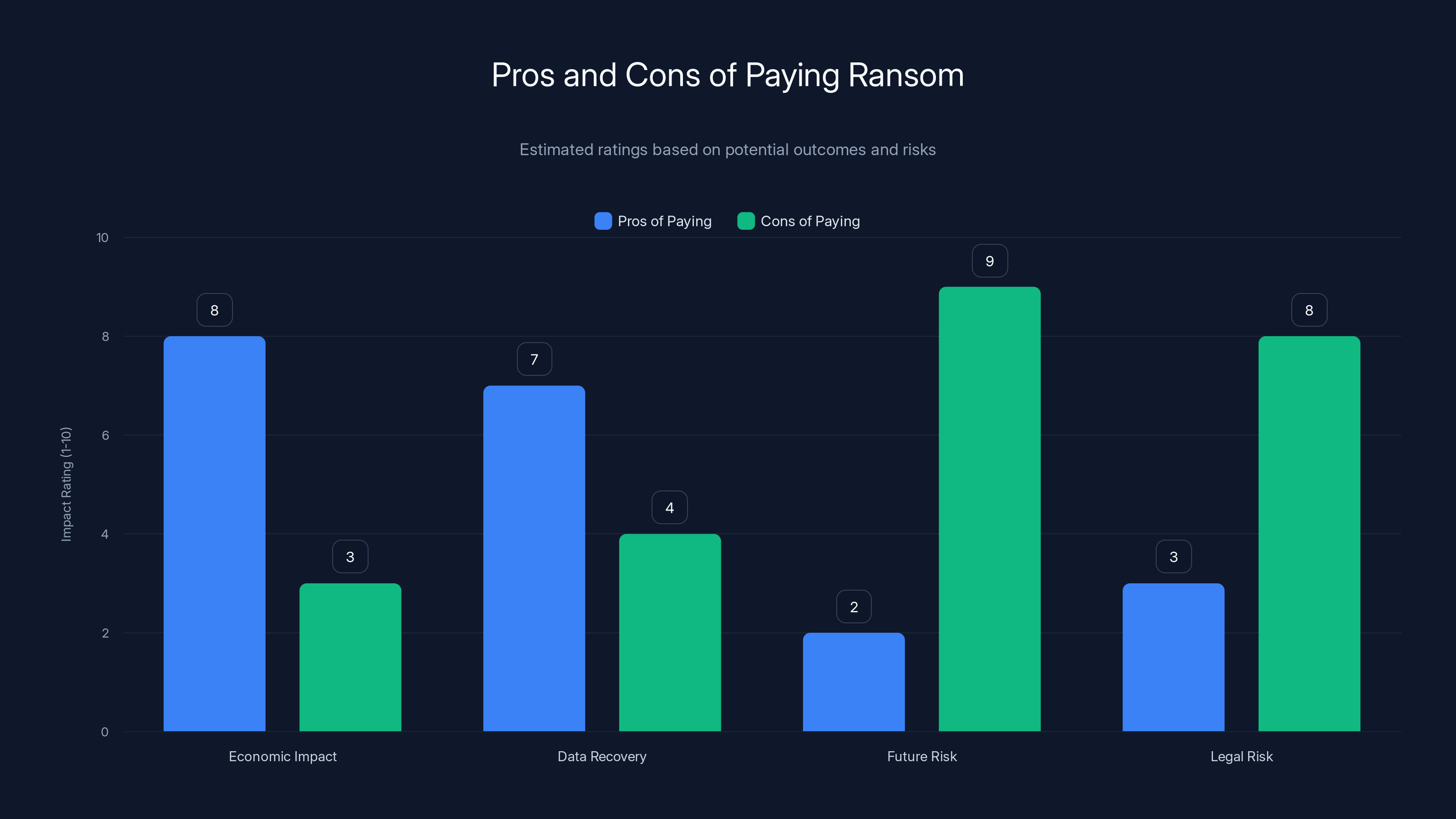
Paying ransom may offer short-term economic relief and faster data recovery, but it significantly increases future risk and legal complications. (Estimated data)
The Ransom Payment Question: To Pay or Not to Pay
One of the most difficult decisions an organization faces when hit with ransomware is whether to pay the ransom. This is where corporate leadership, insurance companies, law enforcement, and external advisors often disagree.
The case for paying
From a purely business perspective, paying ransom sometimes makes economic sense. If the ransom demand is
Ransom payments also come with a decryption key. Sometimes it works. Systems get decrypted and restored faster than rebuilding from backups.
Ransom payments might also prevent the sale of stolen data. Qilin claims that if you pay ransom, they won't sell the stolen data. Whether they actually honor this is debatable, but it's part of their negotiation script.
The case against paying
But there are significant arguments against paying ransom, even from a pure business perspective.
First, paying ransom funds criminal organizations. That money finances future attacks on other organizations. By paying, you're directly enabling harm to others.
Second, there's no guarantee that paying ransom results in recovery. Qilin might provide a decryption key that's broken. They might demand payment in multiple installments and disappear after the first. They might sell the data anyway. There's no contract protection because you're dealing with criminals.
Third, paying ransom makes your organization a target for future attacks. Qilin now knows you're willing to pay. They're likely to attack you again with an even higher ransom demand.
Fourth, many insurance policies won't cover ransom payments if the payment violates sanctions laws. If Qilin operates under sanctions (operating from or having ties to countries under U.S. sanctions), paying might violate OFAC regulations and result in criminal penalties.
What law enforcement recommends
The FBI and other law enforcement agencies consistently recommend against paying ransom. They argue that it perpetuates the problem. They argue that many organizations can recover without paying by using backups and incident recovery procedures.
The real situation at Tulsa
We don't know if Tulsa paid ransom. The airport hasn't disclosed whether they negotiated, what demand was made, or whether payment occurred. If they did pay, it was probably a substantial amount—potentially millions of dollars. If they didn't pay, it likely took them weeks or months to recover systems.
The silence suggests one of two things: either they're still working on recovery, or they've recovered but don't want to disclose the details publicly.

Defensive Strategies Against RaaS Attacks
If your organization wants to defend against Qilin and similar RaaS groups, you need a comprehensive strategy. There's no single tool or technique that stops ransomware. Instead, you need multiple layers.
Backup and recovery
The most important defense against ransomware is having backups. If you have clean backups that are isolated from your network, ransomware can't encrypt them. You can restore from backup and be back in business.
The key word is isolated. Backups need to be on different storage systems, preferably with limited network access. A backup that's stored on a network share is vulnerable. A backup that's stored on a separate tape drive or a cloud storage system with limited credentials is much safer.
Organizations should test their backup recovery regularly. An untested backup might not work when you need it. You should be able to recover a system from backup in minutes, not days.
Network segmentation
If an attacker breaches one system, they shouldn't automatically have access to everything. Network segmentation means dividing your network into separate zones. A breach in the guest network shouldn't give access to the backend financial systems.
For an airport, this means separating the passenger-facing systems from operational systems. Separating IT systems from OT (operational technology) systems. Restricting how these zones can communicate with each other.
This slows down lateral movement. Even if an attacker compromises a workstation, they can't immediately access critical systems.
Endpoint protection
Endpoints—laptops, desktops, servers—are where ransomware typically executes. Endpoint protection means installing security tools that detect and block malware before it can do damage.
This includes antivirus software, behavioral analysis tools, and exploit protection. But it also includes keeping systems patched. Most ransomware exploits vulnerabilities that have been patched. Organizations that patch regularly are far less likely to get compromised.
Email security
Since phishing is the most common initial access vector, email security is critical. This means filtering email for malicious links and attachments. It means scanning attachments for malware. It means flagging emails from external senders.
But it also means training. Employees who understand phishing are much less likely to click malicious links. A security-aware workforce is one of your best defenses.
Threat hunting and monitoring
Detecting a breach quickly is critical. The sooner you detect an attacker, the less damage they can do. This means monitoring for suspicious activity—unusual file access, unusual network traffic, unusual system behavior.
It means hunting for indicators of compromise. Checking your systems for signs that they've been breached. Looking for attacker tools, unauthorized accounts, unusual scheduled tasks.
This requires expertise. You need people who understand how attackers move through networks and what signs to look for.
Incident response planning
When a breach happens, you need to know what to do. Incident response plans document the steps: who to notify, how to preserve evidence, how to contain the compromise, how to communicate internally and externally.
An incident response plan is useless unless it's tested. You should run drills where you pretend a ransomware attack has occurred and walk through your response procedures.
Security culture
Ultimately, the best defense is a security culture where employees understand their role in protecting the organization. A workforce that's aware of phishing. That questions unusual requests. That reports suspicious activity. That understands why security policies exist.
Building this culture requires investment in training, regular communication, and leadership buy-in. But the return on investment is enormous.

What Affected Employees Should Do
If you're an employee at Tulsa International Airport or any organization that's been breached, your personal information is now at risk. Here's what you should do.
First, expect notification
Your employer should notify you if your personal data has been compromised. This notification might come by email, mail, or a combination. It should explain what information was compromised and what steps to take.
If you don't receive notification within 60 days of the breach discovery, you might need to follow up. The airport should have contact information for affected employees.
Second, monitor for identity theft
With your PII exposed, criminals might try to steal your identity. Monitor your credit reports. You can get a free credit report from each of the three major bureaus (Equifax, Experian, TransUnion) once per year at AnnualCreditReport.com.
Place a fraud alert on your credit reports. This requires credit companies to verify your identity before opening new accounts. It's free and takes a few minutes.
Consider a credit freeze if you're particularly concerned. This prevents new credit from being opened in your name. It's more restrictive than a fraud alert but provides stronger protection.
Third, enroll in credit monitoring if offered
Most organizations that suffer a breach offer free credit monitoring to affected individuals. The airport should offer this. Credit monitoring services alert you if someone tries to open an account in your name, take out a loan, or engage in other fraudulent activity.
Enroll even if you think you don't need it. The monitoring is usually free and covers you for a year or more.
Fourth, be wary of phishing
Criminals with your personal information might contact you directly. They might email you pretending to be the bank. They might call pretending to be the airport's HR department. They might try to get you to click a link or provide additional information.
Be skeptical. Verify requests by contacting organizations directly using numbers or emails you know are legitimate. Don't click links in unsolicited emails.
Fifth, consider additional protective measures
If you're particularly concerned, you might consider additional protective measures. Identity theft insurance. Passwordless authentication. VPN services. These aren't necessary for everyone, but they can provide additional peace of mind.
The Broader Industry Implications
The Tulsa attack tells us something important about the security landscape in 2025. We're not winning against ransomware. The attackers are getting more sophisticated, more organized, and more effective.
Ransomware is becoming less ransom-based
Interestingly, ransomware groups like Qilin are shifting business models. Ransom recovery is becoming less reliable as organizations improve backups. Instead, they're shifting toward pure extortion: steal the data, threaten to sell it, demand payment whether or not ransomware is deployed.
This means that even organizations with great backups are at risk. You could recover all your files without paying ransom, but the attacker still has your data and still makes the threat.
Critical infrastructure vulnerability
We're seeing that critical infrastructure is vulnerable in ways we didn't fully appreciate. An airport is essential to the region's economy. Compromising it affects not just the airport, but airlines, vendors, passengers, and the broader community.
Government agencies are beginning to recognize this. New regulations will likely impose stricter security requirements on critical infrastructure. But regulations always lag behind threats.
The skill gap
Most organizations lack the expertise to defend against sophisticated attackers. A mid-size airport probably has 5-10 IT people. Maybe one focuses on security. Qilin has hundreds of people who focus exclusively on attacking.
There's a skill imbalance. The attackers are more sophisticated, more specialized, and more organized than the defenders. Closing this gap requires investment: hiring security experts, training staff, implementing advanced tools.
International cooperation challenges
Qilin operates from Russian-speaking countries, likely with state tolerance if not state involvement. Law enforcement in the U.S. can indict members of the group, but extradition is unlikely. Cyber sanctions might apply, but enforcement is difficult.
International cooperation on cybercrime enforcement remains weak. Countries don't share intelligence effectively. Mutual legal assistance treaties are slow. Meanwhile, ransomware groups operate at internet speed.

What 2025 Teaches Us About Ransomware Evolution
As we move through 2025, several trends are becoming clear about how ransomware is evolving.
Professionalization
Ransomware groups are becoming more professional and corporate-like. They have dedicated teams for initial access, lateral movement, data exfiltration, negotiations, and operations. They have customer service teams that respond to ransom negotiation messages. They have financial teams managing payment processing.
This professionalization makes them more effective but also creates more points of vulnerability. More people involved means greater risk of operational security failures.
Specialization
We're seeing more specialization in the ransomware ecosystem. Some groups focus exclusively on initial access. They breach organizations and sell access to other groups. Other groups buy that access and deploy ransomware. This division of labor makes it harder to track who's actually conducting attacks.
Speed
Attackers are moving faster. The time from initial compromise to ransomware deployment is shrinking. What used to take months now takes weeks. What takes weeks might soon take days. Faster attacks mean faster detection is critical.
Data-centric attacks
We're seeing attacks that focus purely on data theft, without any ransomware component. The attacker steals data and makes threats. No encryption. This bypasses many defensive measures that focus on preventing ransomware encryption.
Supply chain attacks
Ransomware groups are increasingly targeting vendors and suppliers. If you compromise a software vendor that serves hundreds of companies, you can deploy ransomware across all of them at once. The SolarWinds attack (not ransomware, but demonstrating the supply chain principle) showed how effective this can be.

Recommendations for Organizations
If you're responsible for security at an organization—particularly critical infrastructure—here's what you should prioritize in 2025.
Immediate priorities
First, audit your backup systems. Ensure backups are isolated, tested, and can be recovered quickly. This is your most important defense.
Second, patch critical systems. Establish a patch management program. Know what systems are unpatched and what vulnerabilities exist. Prioritize patching systems that are exposed to the internet.
Third, implement email filtering and security. Block emails from known phishing campaigns. Scan for malicious attachments. Train employees on phishing recognition.
Medium-term priorities
First, implement network segmentation. Separate critical systems from less critical systems. Restrict lateral movement.
Second, establish a security monitoring program. Monitor networks for suspicious activity. Implement logging and alerting.
Third, develop an incident response plan. Document your response procedures. Test them regularly.
Long-term priorities
First, mature your security program. Move from reactive (responding to incidents) to proactive (preventing incidents). Invest in security culture, training, and expertise.
Second, engage with law enforcement and share threat intelligence. Understanding what threats you face helps you defend against them.
Third, consider cyber insurance. It's not a substitute for good security, but it helps financial recovery if an incident occurs.

FAQ
What is Qilin ransomware?
Qilin is a Russian-speaking ransomware group that operates as a ransomware-as-a-service (RaaS) platform. They develop ransomware malware and provide it to affiliates who conduct attacks on behalf of the organization. Qilin takes a percentage of ransom payments (typically 20-30%) and the affiliates keep the remainder. The group has claimed over 1,000 successful breaches in 2025 alone, making them one of the most prolific ransomware threats globally.
How did Qilin breach Tulsa International Airport?
The exact initial access vector hasn't been officially disclosed by the airport, but based on typical Qilin attack patterns, the breach likely started with phishing emails sent to airport employees. Once an employee was compromised, attackers conducted lateral movement to access more critical systems, disabled backups, exfiltrated sensitive data, and eventually deployed the ransomware. The entire process likely took weeks or months before the ransomware was deployed, based on the dated evidence of documents stolen between 2022 and 2025.
What data was stolen in the Tulsa airport attack?
Qilin released 18 sample files demonstrating they had accessed executive emails, employee government IDs and driver's licenses, annual budget spreadsheets, revenue projections, confidentiality and non-disclosure agreements, telehealth reports, governance meeting minutes, insurance documents, banking communications, tenant databases showing which companies operate at the airport, vendor revenue sheets, and court case documents. This comprehensive data set reveals how the airport operates and can be used for identity theft, corporate espionage, and ongoing extortion.
Why would a ransomware group target an airport specifically?
Airports are attractive ransomware targets for several reasons: they operate critical infrastructure with immediate business impact, downtime costs millions of dollars per hour, they typically have insurance that covers ransomware incidents, they have significant budgets that allow ransom payment, they serve thousands of employees and passengers creating extensive data, and they rely on complex interconnected systems with potential security gaps. The economic pressure to restore operations quickly creates strong incentive to pay ransomware demands.
What is ransomware-as-a-service (RaaS)?
Ransomware-as-a-service is a business model where a criminal organization develops and maintains ransomware malware and supporting infrastructure, then leases this platform to affiliates who conduct attacks. Affiliates pay subscription fees and/or profit-sharing arrangements to use the RaaS platform. The core organization maintains the infrastructure, negotiation platforms, and payment processing. The affiliates conduct the actual hacking and negotiation. This distributed model makes law enforcement disruption difficult and allows the core organization to scale without directly hiring attackers.
Should organizations pay ransomware demands?
Most law enforcement agencies and security experts recommend against paying ransomware demands. Paying funds criminal organizations, incentivizes future attacks against your organization and others, doesn't guarantee recovery or prevention of data sale, and may violate sanctions laws if the group operates from sanctioned countries. Organizations with good backups can typically recover without paying. However, some organizations calculate that the cost of downtime exceeds the ransom demand and choose to pay. This is a business decision that requires input from leadership, insurance, law enforcement, and security teams.
How can organizations defend against ransomware attacks?
Organizations should implement multiple defensive layers including: isolated and tested backup systems that are not accessible from the network, regular system patching to close vulnerabilities, network segmentation to limit lateral movement, email filtering and security to prevent phishing, endpoint protection including antivirus and behavioral analysis, employee security awareness training, and incident response planning. No single control stops ransomware, but multiple layers significantly reduce risk. Regular testing and updating of these controls ensures they remain effective.
What should employees do if their personal data was stolen in a breach?
Employees should monitor their credit reports by obtaining free annual reports from all three bureaus, place a fraud alert on their credit files to require identity verification for new accounts, enroll in free credit monitoring services offered by their employer, watch for phishing attempts from criminals using their personal information, be skeptical of unexpected communications requesting personal or financial information, and consider credit freezes if they're particularly concerned about identity theft. Employees should also ensure their passwords are unique and use multi-factor authentication on important accounts.
How is Qilin different from other ransomware groups?
Qilin differentiates itself through scale (claiming 1,000+ breaches in 2025), operational sophistication (running a structured RaaS business with different specialized teams), professionalization (offering customer service and negotiation platforms), and profitability (generating millions in revenue through ransom payments and data sales). They also demonstrate persistence, maintaining access to compromised systems for months while they collect data and prepare leverage. Their business model with distributed affiliates provides resilience against law enforcement disruption.
What is critical infrastructure and why is it vulnerable to ransomware?
Critical infrastructure includes systems essential to public safety, economic stability, and essential services: power grids, water treatment, hospitals, emergency services, and transportation networks. These systems are vulnerable to ransomware because they often rely on legacy systems built decades ago before cybersecurity was a consideration, prioritize availability over security requiring slow patching processes, run specialized software that's not regularly updated, and are operated by organizations with domain expertise but sometimes limited cybersecurity expertise. Additionally, downtime creates immediate critical impact, pressuring organizations to pay ransomware demands quickly.

Conclusion
The Qilin ransomware group's breach of Tulsa International Airport reveals uncomfortable truths about where we are in the cybersecurity landscape in 2025. This wasn't some sophisticated zero-day attack that only the world's best security teams could have detected. This was a relatively standard ransomware compromise that probably started with a phishing email, followed by months of undetected access, backup destruction, and then encryption.
The scale is what's striking. Qilin claims over 1,000 breaches in 2025. That's not hyperbole or marketing. That's roughly three successful attacks per day. Some are probably false claims, but even if only half are real, that's still one of the largest sustained cyber campaigns in history.
What makes Qilin particularly dangerous isn't just their volume. It's their professionalization. They're not script kiddies running off-the-shelf tools. They're running a structured criminal business with specialized teams, customer service, profit-sharing arrangements, and multiple revenue streams. They've taken ransomware from a cottage industry to an enterprise-scale operation.
For organizations like Tulsa International Airport, the implications are sobering. This wasn't about advanced persistent threats or zero-day exploits. This was about fundamental security failures: probably inadequate backup isolation, slow patch management, insufficient monitoring, limited network segmentation. These are the basics. And they failed.
The broader implication is that we're losing this fight. Ransomware is becoming more prevalent, more sophisticated, more costly. Organizations are increasing security spending, but attackers are outpacing defense. The gap between attacker capability and defender capability is widening, not narrowing.
What needs to happen? First, organizations need to obsess over the fundamentals. Backups. Patching. Monitoring. Training. Not flashy new technologies, but the blocking and tackling of security.
Second, we need faster incident response. The time from breach detection to containment needs to be measured in hours, not weeks. This requires better monitoring, faster decision-making, and pre-planned response procedures.
Third, we need better information sharing. When Tulsa gets hit and doesn't disclose technical details of how they were breached, every other airport has to learn from their own breach. Information sharing accelerates defensive improvements.
Fourth, we need law enforcement and international cooperation to make consequences for these activities real. Right now, ransomware operators face minimal consequences because they operate from countries where they're tolerated or protected. That needs to change.
Finally, we need to accept that perfect security is impossible. The goal isn't to prevent all breaches. The goal is to make breaches as costly and risky as possible for attackers. Better backups mean ransom won't work. Better monitoring means faster detection and lower impact. Better incident response means faster recovery. Better security culture means fewer employees fall for phishing.
The Tulsa attack isn't a novel threat. It's a reminder that the basics still matter. And most organizations are failing the basics. If you're responsible for security at your organization, this should be a wake-up call. Audit your backups. Check your patches. Review your monitoring. Test your incident response. These aren't fancy security initiatives. They're table stakes.
Qilin will continue attacking. They're too profitable to stop. But organizations can dramatically reduce their risk by getting the fundamentals right. The question is whether they'll do it before they become Qilin's next victim.
Try Runable for automating your security response documentation, incident reports, and notification templates. AI-powered automation can help teams generate comprehensive security communications and policy documents faster.

Key Takeaways
- Qilin operates a sophisticated RaaS business model claiming 1,000+ breaches in 2025, roughly three successful attacks per day globally
- The Tulsa airport breach exposed 18 samples of sensitive data including employee IDs, financial records, governance documents, and healthcare information spanning 2022-2025
- Airports are prime ransomware targets because downtime costs millions per hour, creating strong economic incentive to pay ransom demands quickly
- The typical Qilin attack unfolds over weeks or months with phishing initial access, lateral movement, backup destruction, data exfiltration, and ransomware deployment
- Critical infrastructure vulnerability requires fundamental security improvements: isolated backups, regular patching, network segmentation, email security, and continuous monitoring
- Affected employees should monitor credit reports, place fraud alerts, enroll in credit monitoring, and remain vigilant against identity theft and phishing for years after a breach
Related Articles
- Grubhub Data Breach 2025: What Happened and How to Protect Yourself [2025]
- TriZetto Provider Solutions Breach: 700K+ Affected [2025]
- FBI Seizes RAMP Cybercrime Forum: What Happened & What It Means [2025]
- FBI Seizes RAMP: The Collapse of Ransomware's Last Stronghold [2025]
- Microsoft Office CVE-2026-21509 Security Flaw: What You Need to Know [2025]
- Sandworm's Poland Power Grid Attack: Inside the Russian Cyberwar [2025]
![Qilin Ransomware Gang Hits Tulsa Airport: What You Need to Know [2025]](https://tryrunable.com/blog/qilin-ransomware-gang-hits-tulsa-airport-what-you-need-to-kn/image-1-1770052407895.jpg)



