Malicious Chrome Extensions Spoofing Enterprise Platforms: The Complete Threat Guide [2025]
Introduction
You're working from home. Mid-morning, you click on what looks like your company's Workday login page. Nothing seems off. The interface matches perfectly. You enter your credentials, hit enter, and move on with your day. Two hours later, your IT team sends an urgent message: your account was just accessed from three countries simultaneously.
This scenario isn't hypothetical. It's exactly what happened to employees across enterprises and multinational organizations when they installed browser extensions spoofing Workday, NetSuite, and SuccessFactors. Security researchers at Socket uncovered five malicious Chrome extensions that had been quietly stealing authentication tokens, session credentials, and sensitive organizational data for years.
What makes this threat particularly dangerous isn't just the technical sophistication—it's the trust factor. People install extensions thinking they're helpful tools, never realizing they've invited a trojan horse into their browser. When the attack vector is something as ordinary as a browser plugin, detection becomes exponentially harder.
This comprehensive guide breaks down exactly what happened, how these extensions operated, what vulnerabilities they exploited, and most importantly, how you can protect your organization from similar attacks. We'll cover detection strategies, remediation steps, and systemic security practices that prevent credential theft at scale.
TL; DR
- The Attack: Five Chrome extensions impersonated legitimate HR and ERP platforms, stealing credentials and enabling full account takeover
- The Scale: Downloaded 2,739 times across enterprises and multinational organizations before removal from Chrome Web Store
- The Duration: Some extensions operated for over four years before detection
- The Risk: Session hijacking, credential theft, and administrative interface blocking created scenarios where security teams couldn't remediate breaches
- The Current Status: Removed from Chrome Web Store but still distributed on third-party software download sites
Part 1: Understanding the Threat Landscape
The Five Malicious Extensions and Their Names
The extensions identified by security researchers were:
- Data By Cloud Access Tool
- Access 11
- Data By Cloud 1
- Data By Cloud 2
- Software Access
These names were deliberately chosen to sound legitimate, technical, and innocuous. "Data By Cloud Access Tool" suggests it's some kind of cloud data utility. "Access 11" sounds like it could be a productivity numbering system. None of them screamed malicious intent. That's the point.
The naming strategy is crucial to understanding how these extensions evaded detection for so long. They didn't announce themselves as threats. They simply looked like ordinary tools that a developer, finance professional, or HR administrator might install to streamline their workflow.
Why These Platforms Were Targeted
Workday, NetSuite, and SuccessFactors aren't random targets. These platforms are used by mid-size to large organizations, enterprises, and multinational corporations for mission-critical functions: HR management, payroll processing, financial operations, and supply chain management.
A single successful account takeover in one of these systems could grant an attacker access to:
- Employee personal data (names, addresses, social security numbers, bank account information)
- Financial records and transaction histories
- Payroll systems and compensation data
- Procurement and vendor information
- Confidential business operations and strategic planning documents
- Access credentials to downstream systems connected to the ERP
The economic impact is staggering. A compromised ERP system in a Fortune 500 company could result in millions of dollars in damages, regulatory fines (GDPR, CCPA violations), loss of customer trust, and operational disruption lasting weeks or months.
The Download Numbers: Deceivingly Small
On the surface, 2,739 total downloads across five extensions seems small. That's not a widespread campaign, right? Wrong.
Consider the targeting: these extensions weren't advertised on Reddit or TikTok to millions of random users. They targeted specific employee profiles at specific organizations. If even 500 of those 2,739 downloads were employees at enterprise organizations, the damage potential is enormous.
One compromised CFO at a multinational corporation who has access to financial systems and spending authority represents more risk than 1,000 downloads from random home users. Quality of targets matters more than quantity when you're conducting targeted credential theft.

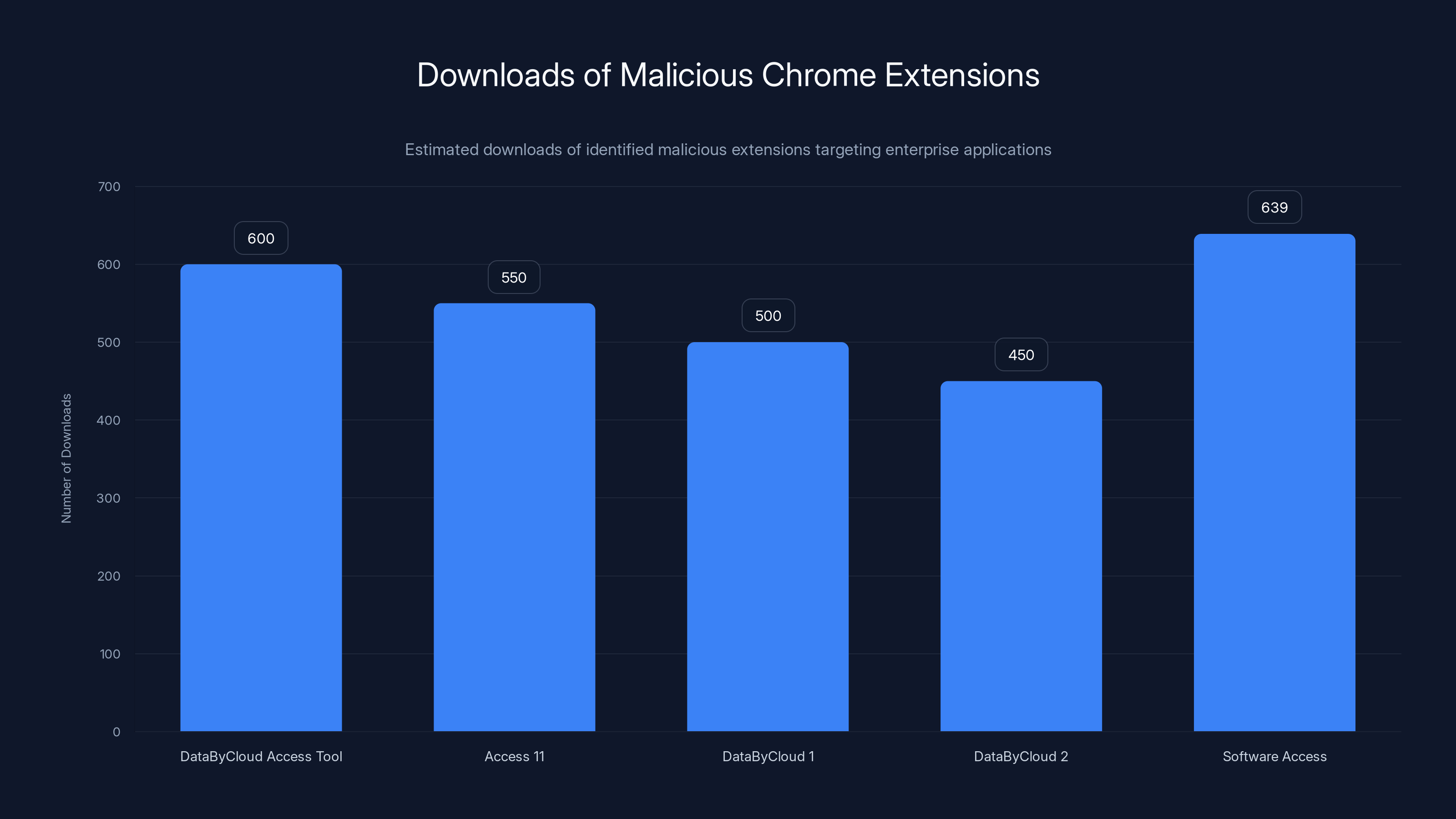
The five malicious Chrome extensions were downloaded approximately 2,739 times collectively, posing significant security risks to enterprises. Estimated data.
Part 2: Technical Analysis of the Attack Methods
Credential Theft Mechanisms
The primary goal of these extensions was credential harvesting. Here's how they worked:
When a user visited a legitimate Workday, NetSuite, or SuccessFactors login page, the malicious extension would inject a custom login form overlay or intercept the credentials as they were typed. The extension captured:
- Username and email address
- Password
- Multi-factor authentication tokens (if enabled)
- Company identifier or organization code
- Session cookies
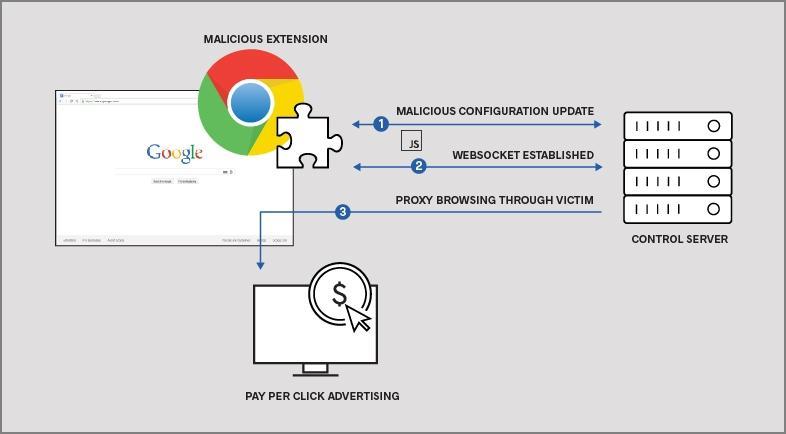
The harvested credentials were immediately transmitted to attacker-controlled servers. The user never knew anything was wrong. The login typically proceeded normally because the extension forwarded the credentials to the actual service, creating the illusion that everything worked as intended.
This is a critical detail: the extensions didn't block login attempts or cause errors. They silently duplicated credentials in the background while allowing normal operation to continue. Detection required active monitoring of authentication logs or behavioral analysis of account access patterns.
Session Hijacking and Token Interception
Beyond credential theft, these extensions performed session hijacking. Here's the distinction and why it matters:
Once a user successfully authenticated, the browser stored a session token or cookie that proved authentication without requiring re-entry of the password. This token might last hours, days, or weeks depending on the organization's security policy.
The malicious extensions captured these session tokens and transmitted them to attacker infrastructure. Now the attacker possessed a valid, authenticated session that could be replayed from any location, at any time, without triggering password reset requirements.
Session tokens are harder to detect than password theft because:
- The legitimate user's account shows normal activity (they're still logged in)
- The attacker's activity appears to originate from the same session
- Many organizations don't log individual API calls or transactions, only session starts
- Security teams often ignore multiple simultaneous sessions if they assume they're from the user's phone and computer
Administrative Interface Blocking
The most sophisticated aspect of these extensions was their ability to block incident response. When a security team detected unauthorized access and attempted to terminate sessions or revoke credentials, the extensions would intercept and prevent these administrative actions.
Here's the scenario that created maximum havoc:
- Security team detects unauthorized access to a compromised account
- Team attempts to click "Terminate all sessions" in the admin panel
- The extension intercepts this action and prevents it from executing
- The administrator sees no error message—it just appears the action didn't register
- Administrator repeats the action, assuming it was a temporary glitch
- Meanwhile, the attacker maintains access through the session token captured by the extension
This created a scenario where security teams couldn't remediate breaches through normal channels. They couldn't terminate sessions, revoke credentials, or disable accounts because the extension actively blocked these remediation attempts.
The only way to fully remove the attacker's access was to:
- Uninstall the malicious extension
- Clear all browser cache and cookies
- Force password resets
- Revoke session tokens at the application level
- Audit all account activity during the compromise window
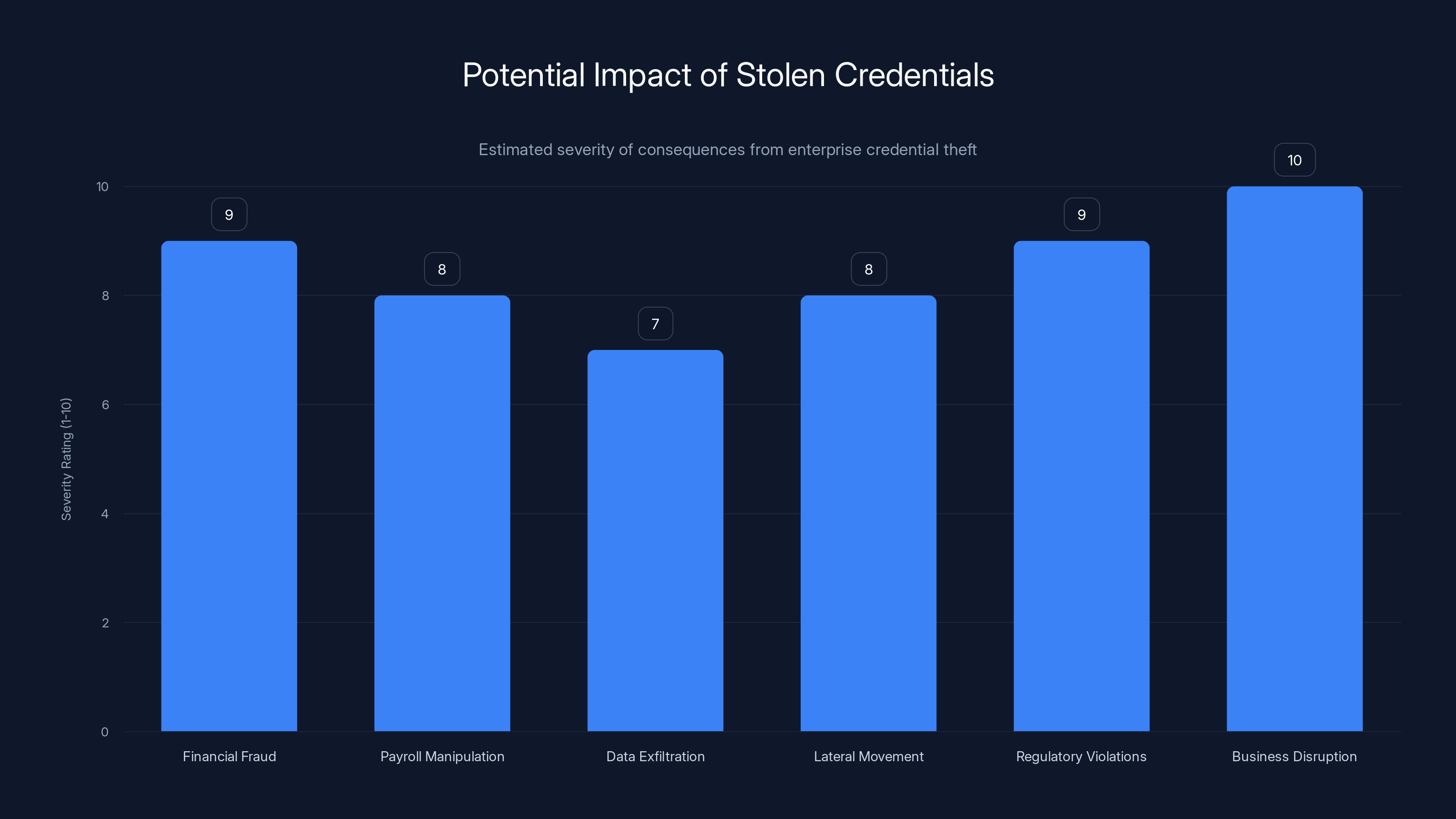
Business disruption and regulatory violations are among the most severe consequences of stolen credentials, with potential for significant financial and operational impact. (Estimated data)
Part 3: How These Extensions Infiltrated Organizations
Distribution Channels and Download Sources
The extensions were initially distributed through the official Chrome Web Store. This is crucial because the Chrome Web Store carries Google's implicit trust. Users reasonably assume that extensions available on the official store have undergone some level of vetting.
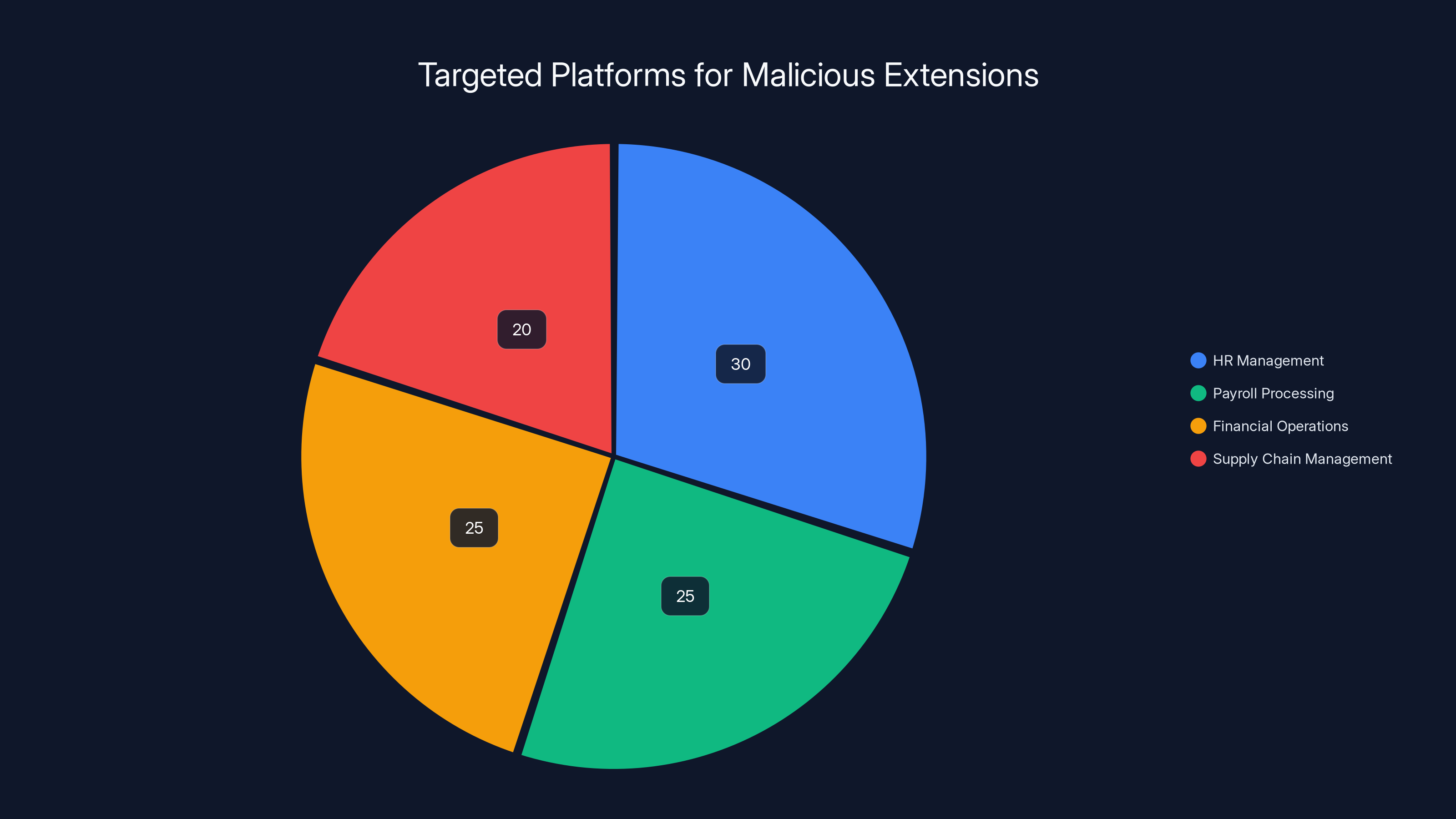
The extensions were removed from the Chrome Web Store once discovered, but they quickly migrated to third-party software download sites like Softonic, SourceForge, and similar platforms. These sites are notorious for hosting malicious and compromised software because they prioritize availability and profit over security verification.
Users searching for "Workday extension" or "NetSuite Chrome addon" would find these malicious versions prominently ranked in search results, ahead of legitimate solutions.
Social Engineering and Disguise Tactics
These extensions used several tactics to appear legitimate:
Naming Similarity: "Data By Cloud" could be confused with legitimate cloud tools. "Software Access" sounds like a generic productivity utility.
Icon Mimicking: The extensions used icons similar to the platforms they targeted, making them appear as official extensions for those services.
Permission Requests: The extensions requested permissions that seemed reasonable for their stated purpose (read/write to web pages, access network requests, modify headers). Users rarely deny extension permissions because the implications aren't immediately clear.
Installation Timing: Many were installed years ago when browser extension security awareness was lower. Users who installed them in 2020 or 2021 never thought to audit their extensions in 2024.
Company Internal Distribution: Some users reported being directed to these extensions through internal company communications (emails, documentation) that made them appear to be officially endorsed solutions. This suggests the attackers either compromised internal communication channels or sent convincing phishing emails impersonating IT departments.
The Long Tail of Distribution
Some extensions had been published more than four years prior to discovery. This means:
- Hundreds of employees at various organizations had them installed
- Credentials from multiple organizations had been stolen
- The extensions survived multiple Chrome updates without being flagged
- Users who installed them and later left those companies might still have them installed on their personal machines
The longevity of the campaign suggests attackers were operating with significant patience and sophistication. They weren't trying to maximize downloads in a short-term smash-and-grab campaign. They were building long-term access to enterprise environments.
Part 4: Impact Assessment and Real-World Consequences
What Attackers Could Do With Stolen Credentials
Once attackers possessed valid credentials and session tokens from enterprise users, the potential impact expanded dramatically:
Financial Fraud: Access to NetSuite allowed manipulation of financial records, creation of fraudulent purchase orders, unauthorized wire transfers, and diversion of funds to attacker-controlled accounts.
Payroll Manipulation: Workday access enabled attackers to modify employee payroll, create ghost employees, adjust tax withholdings, or redirect direct deposits.
Data Exfiltration: HR systems contain social security numbers, dates of birth, addresses, banking information, and employment history for thousands of employees. This data is worth
Lateral Movement: Compromised enterprise accounts often have integrated access to downstream systems: email, file storage, development repositories, customer databases, supply chain management systems. One compromised ERP credential could become a pivot point for attacking dozens of other systems.
Regulatory Violations: Unauthorized access to personal data of EU citizens triggers GDPR obligations to notify regulators and affected individuals. Fines can reach 4% of global revenue or €20 million, whichever is greater.
Business Disruption: An attacker with full Workday access could lock out legitimate administrators, delete critical records, or corrupt data in ways that take weeks to recover from.
The Unique Danger of Administrative Interface Blocking
Most malware operates on the assumption that, eventually, security teams will detect it. Traditional malware tries to hide its tracks and evade detection.
These extensions took a different approach: they assumed detection was inevitable, so they prepared for it. By blocking remediation attempts, they extended their access window beyond the point where security teams discovered them.
This created a scenario described by Socket researchers: "The combination of continuous credential theft, administrative interface blocking, and session hijacking creates a scenario where security teams can detect unauthorized access but cannot remediate through normal channels."
Imagine being a CISO discovering that your security team's ability to respond to breaches has been compromised. That's uniquely stressful.
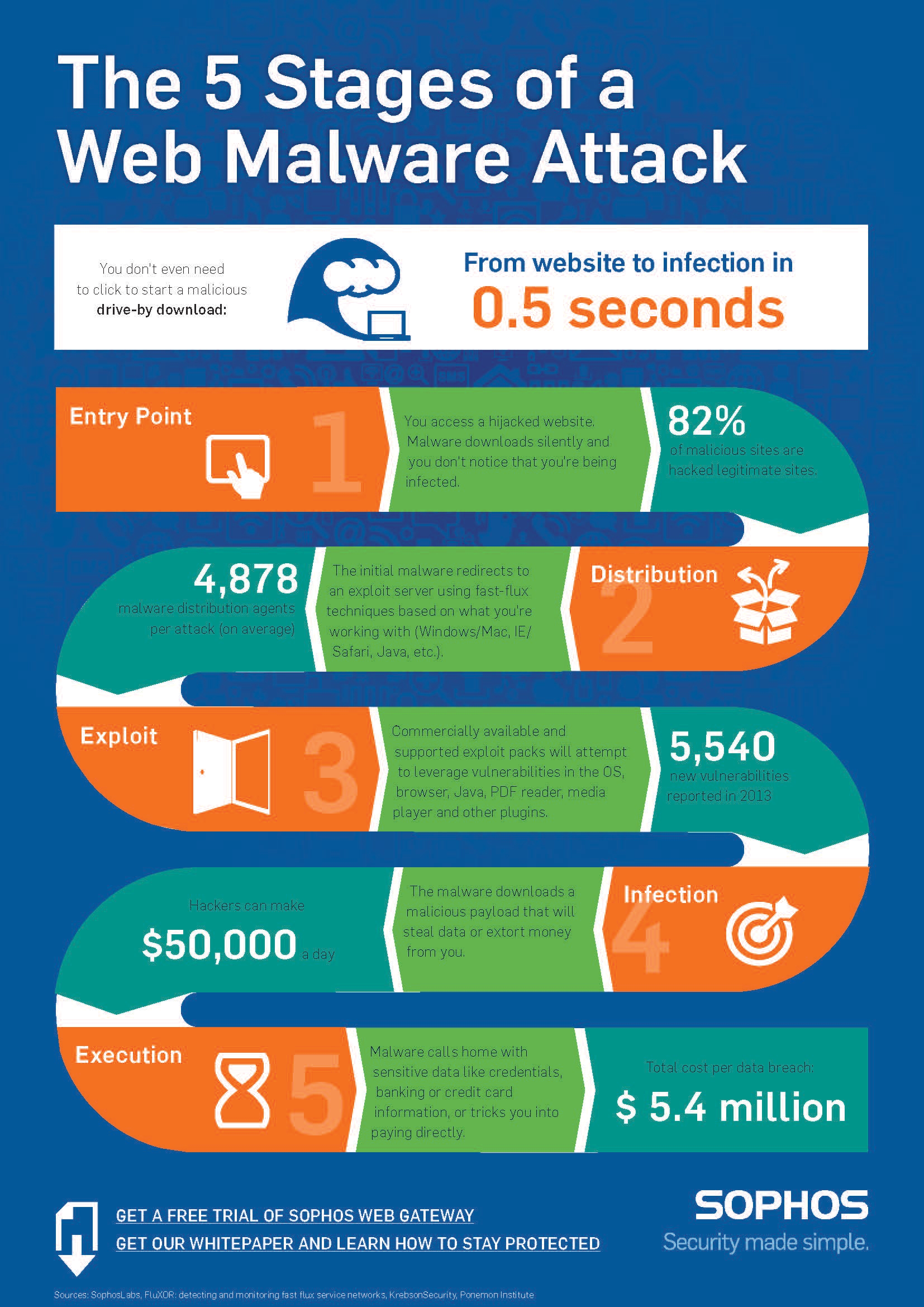
Estimated data shows HR management platforms are most targeted due to the sensitive nature of employee data. Estimated data.
Part 5: Detection Methods and Red Flags
How to Identify Suspicious Extensions
Before diving into technical detection, start with basic hygiene:
1. Browser Extension Audit
Open Chrome's extension manager (chrome://extensions) and review every single extension. Ask yourself:
- Do I recognize this extension?
- Do I actively use it?
- When was it last updated?
- Does it have a legitimate publisher?
- Does it have an unreasonable number of permissions?
Extensions that haven't been updated in years are suspicious. Browser security evolves constantly. If an extension hasn't been touched by its developers in 24+ months, it's abandoned and potentially vulnerable.
2. Permission Analysis
Click each extension and review its permissions. Specifically look for:
- Modify network requests: This allows intercepting HTTPS traffic and injecting code
- Read and change all data on websites you visit: This is extremely broad and rarely necessary
- Access your data on secure sites: This is a major red flag
- Access your private data for all sites: Only trust this for password managers or very specific tools
If an extension claims to be a "Workday helper" but requests permission to access data on all websites, that's suspicious.
3. Publisher Verification
Click the publisher name and verify it's a real company. Look for:
- Official website that's professional and up-to-date
- LinkedIn company page with employees
- GitHub presence with actual code repositories
- Press coverage or industry presence
Fake publishers often have minimal online presence outside the Chrome Web Store.
Technical Detection Indicators
Network Traffic Analysis
If your organization uses network monitoring, look for Chrome processes making unexpected HTTPS connections to unknown domains. Malicious extensions typically exfiltrate data to:
- Newly registered domains (WHOIS registration within 30 days of campaign start)
- IP addresses associated with bulletproof hosting providers
- Domains with unusual TLDs (.ru, .cn, .top, .xyz)
- Domains with redirection services or URL shorteners
Browser History and Downloads
Check browser history and download locations. Malicious extensions sometimes download additional payloads. Look for:
- Executable files downloaded from unfamiliar sources
- Files with suspicious names like "update.exe" or "system.jar"
- Multiple downloads within short time windows
- Downloads to unusual locations like AppData or %Temp%
Account Access Logs
Review your Workday, NetSuite, or SuccessFactors access logs for:
- Login attempts from unusual geographic locations
- Failed login attempts followed immediately by successful ones
- Account access during non-business hours
- Simultaneous sessions from different IP addresses
- API access patterns inconsistent with typical user behavior
Many enterprise systems allow exporting access logs to CSV. Comparing logs across teams can reveal patterns of unauthorized access.
Behavioral Red Flags
User-Reported Symptoms
Train your team to recognize and report:
- Password resets they didn't initiate
- Account lockouts without attempting to login
- Notifications of account activity they didn't perform
- Missing browser tabs or data
- Unexpected redirects when accessing HR or finance systems
- System warnings they've never seen before
IT Team Observations
- Support tickets about "slow Workday access" (could indicate extension overhead)
- Users reporting that password reset didn't resolve account issues
- Failed administrative attempts to revoke sessions (remediation blocking)
- Multiple users from the same department reporting similar extension recommendations

Part 6: Remediation and Incident Response
Immediate Actions for Suspected Compromise
If you suspect your organization was affected, time is critical. Follow this sequence:
Step 1: Identify All Affected Users (1-2 hours)
Contact your IT team or security operations center with this information:
- List of users who downloaded malicious extensions (check Chrome Web Store records if possible)
- Dates of extension installation
- User roles and system access levels
- Organizations or business units affected
Step 2: Disable Affected Accounts (Immediately)
For users with confirmed installation:
- Disable accounts in your identity management system
- Terminate all active sessions in HR and ERP systems
- Revoke API tokens and developer credentials
- Disable service accounts that user might have had access to
This is aggressive, but temporary disablement is necessary to prevent lateral movement.
Step 3: Force Password Resets (Immediately)
- Reset passwords for all affected users
- Use a temporary strong password generated by your system
- Require password change on next login
- Send password reset links through secure channels (not email if email was compromised)
Step 4: Clear Browser State (Immediately)
Affected users must:
- Uninstall all extensions (not just the malicious ones—full clear)
- Clear browser cache, cookies, and browsing history
- Clear autofill data
- Restart their browser completely
- Reinstall only essential, verified extensions
Step 5: Review Account Activity (2-4 hours)
Export and analyze account activity during the suspected compromise window:
- All logins and failed login attempts
- All administrative actions (permission changes, user creation, configuration changes)
- All financial transactions or HR data modifications
- All data exports or API calls
- All email forwarding rules created
Look for:
- Actions inconsistent with job responsibilities
- Changes made during off-hours or unusual times
- Bulk data exports
- Configuration changes that disabled security features
Step 6: Isolate and Preserve Evidence (Immediately)
Don't just delete the extension or user account. Preserve evidence:
- Export affected user's browser history
- Preserve browser cache and cookies (store securely)
- Screenshot browser extension settings and manifest
- Archive email sent by the user during compromise period
- Export extension source code from Chrome if still possible
Step 7: Engage External Resources (Immediately)
- Contact your incident response team or hire external forensics firm
- Notify your legal team (breach notification may be required)
- Contact your cyber insurance carrier
- Prepare for potential regulatory notifications (GDPR, CCPA, etc.)
- Consider law enforcement notification if fraud or large-scale data theft occurred
Long-Term Remediation
Comprehensive Threat Hunting
Work with your SOC or security team to hunt for:
- Other malicious extensions currently installed across your organization
- Indicators of compromise (IOCs) related to known attacker domains
- Command and control communication patterns
- Credential sharing or reuse indicators
- Lateral movement attempts from compromised accounts
System-Level Access Review
- Audit permissions for affected users' accounts
- Verify no persistent backdoors were installed
- Check for new user accounts created by attackers
- Review and rotate service account credentials
- Verify integrity of critical business processes
Communication and Notification
- Notify affected employees clearly about what happened and what they should do
- Explain the remediation steps and timeline
- Provide identity protection services if personal data was accessed
- Communicate with customers if their data might have been affected
- Prepare for media inquiries and regulatory interactions

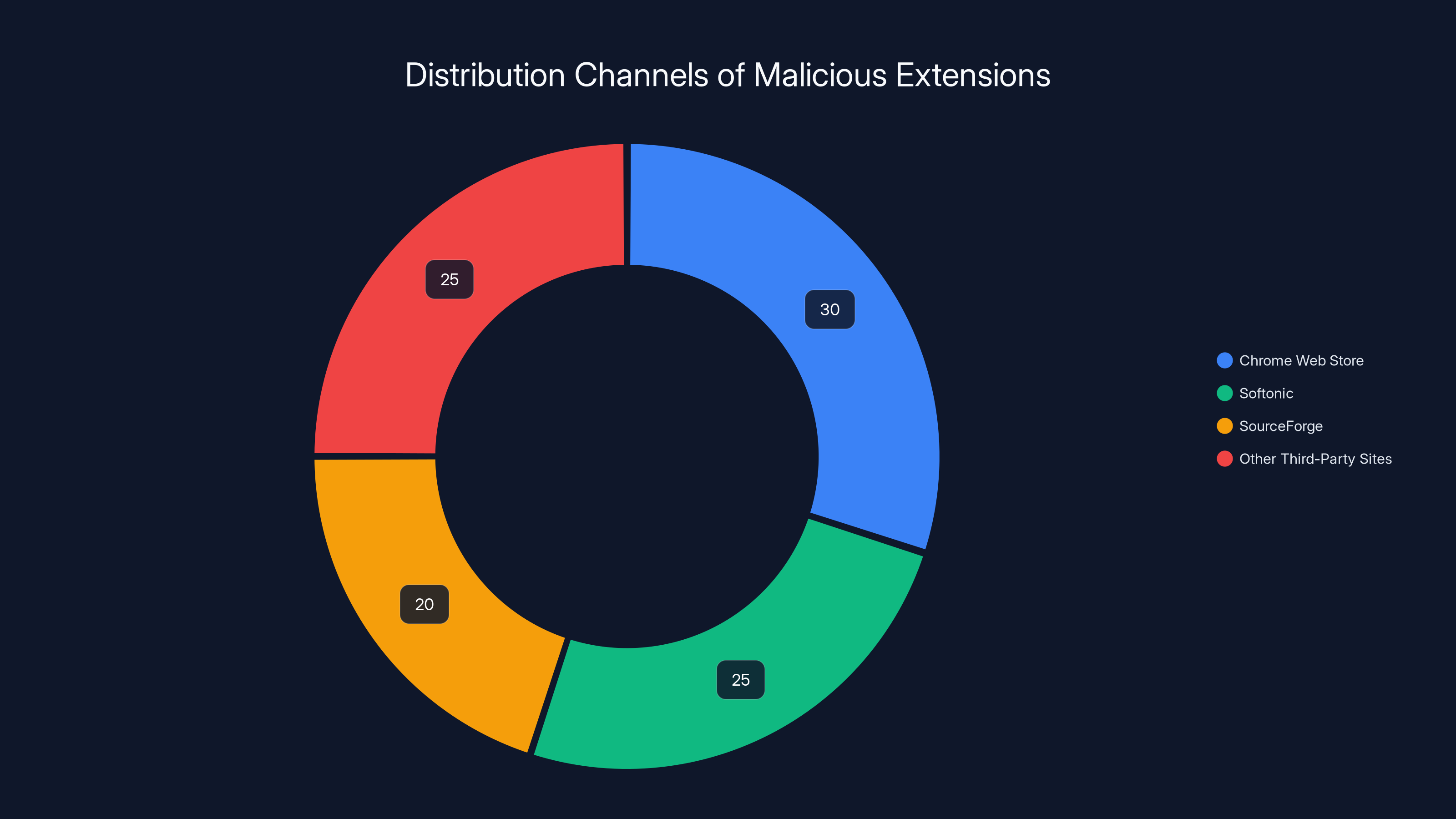
Estimated data shows that while the Chrome Web Store initially hosted these extensions, a significant portion also spread through third-party sites like Softonic and SourceForge, known for less stringent security checks.
Part 7: Systemic Security Controls to Prevent Future Incidents
Browser Extension Governance
Most organizations have zero formal policy around browser extensions. This is a critical gap.
Implement Extension Allowlisting
Use mobile device management (MDM) or enterprise browser management tools to:
- Maintain an approved list of extensions
- Block installation of all others automatically
- Audit extension usage across the organization
- Push security updates to extensions centrally
- Remove extensions that become vulnerable
Google Workspace administrators can enforce extension policies through the Admin Console. Microsoft 365 organizations can use Edge Enterprise policy management.
Extension Security Assessment Process
Before approving extensions for company use:
- Review publisher credibility and history
- Analyze requested permissions (principle of least privilege)
- Check vulnerability databases and security forums
- Review privacy policy carefully
- Test in isolated environment before enterprise rollout
- Establish regular review cycle (quarterly at minimum)
User Training and Awareness
- Educate users about extension risks in onboarding
- Remind about extension audit in quarterly security communications
- Create clear policy about approved vs. prohibited extensions
- Explain why extension governance matters (use real examples)
- Make it easy to report suspicious extensions
Identity and Access Controls
Multi-Factor Authentication for Critical Systems
ERP and HR systems should require MFA for all users, with particular rigor for administrators. Even if credentials are stolen, MFA makes it harder for attackers to gain access.
Better yet: implement conditional access that requires additional verification when:
- Login originates from new geographic location
- Multiple login attempts in short timeframe
- Simultaneous sessions from different locations
- Access to sensitive data exports or configurations
Session Management
- Implement short session timeouts (15-30 minutes for sensitive systems)
- Require re-authentication for sensitive actions (data export, configuration changes)
- Log all session starts and terminations
- Implement automatic session termination for suspicious activity
- Prevent concurrent logins from multiple locations
Credential Monitoring
Subscribe to dark web monitoring services that alert when your organization's credentials appear in data breaches or attacker forums. Services like Scylla, 4iQ, or similar providers constantly scan underground forums and databases.
Network and Endpoint Security
DNS Filtering
Implement DNS-level blocking of known malicious domains. This prevents extensions (and other malware) from communicating with command and control servers.
Services like Cloudflare One, Cisco Umbrella, or Zscaler provide enterprise-grade DNS security.
Endpoint Detection and Response (EDR)
Deploy EDR tools like Microsoft Defender for Endpoint, CrowdStrike Falcon, or SentinelOne to monitor for:
- Suspicious browser process behavior
- Unusual network connections from browser
- Downloaded executable files
- Unusual system changes
Web Application Firewall
Deploy a WAF in front of critical applications (Workday, NetSuite, etc.) that monitors for:
- Credential stuffing attempts
- Session hijacking patterns
- Unusual API access patterns
- Geographic anomalies
- Admin action blocking attempts
Part 8: Insider Threat Considerations
Could This Have Been an Insider?
While these extensions appear to be externally created and distributed, some security researchers have speculated whether inside knowledge played a role in their development.
Consider the sophistication:
- Deep knowledge of how Workday, NetSuite, and SuccessFactors function
- Understanding of their API structures and authentication mechanisms
- Knowledge of administrative remediation workflows (to block them)
- Access to legitimate enterprise environments to test against
This could indicate:
- Insider involvement: A current or former employee of Workday/NetSuite/SAF helped develop these extensions
- Contractor/vendor compromise: A contractor or vendor to these companies had access to internal information
- Previous breach: The attackers previously breached one of these companies and extracted technical information
- Social engineering: The attackers socially engineered employees at these companies to understand internal systems
- Public documentation: The extensions were developed using only publicly available technical information (most likely scenario)
Regardless of the root cause, this underscores the importance of treating your own employees' security as critical. Insiders with legitimate access combined with malicious intent are devastating.
Vetting External Extensions in Your Organization
Beyond just blocking unapproved extensions, consider whether certain users actually need particular extensions at all.
For Workday, NetSuite, and SuccessFactors access: users shouldn't need extensions. The web applications themselves should have all necessary functionality. Any extension claiming to improve these systems should be viewed with extreme suspicion.
If a department head insists they need a particular extension and can't articulate why, that's a signal to investigate further.

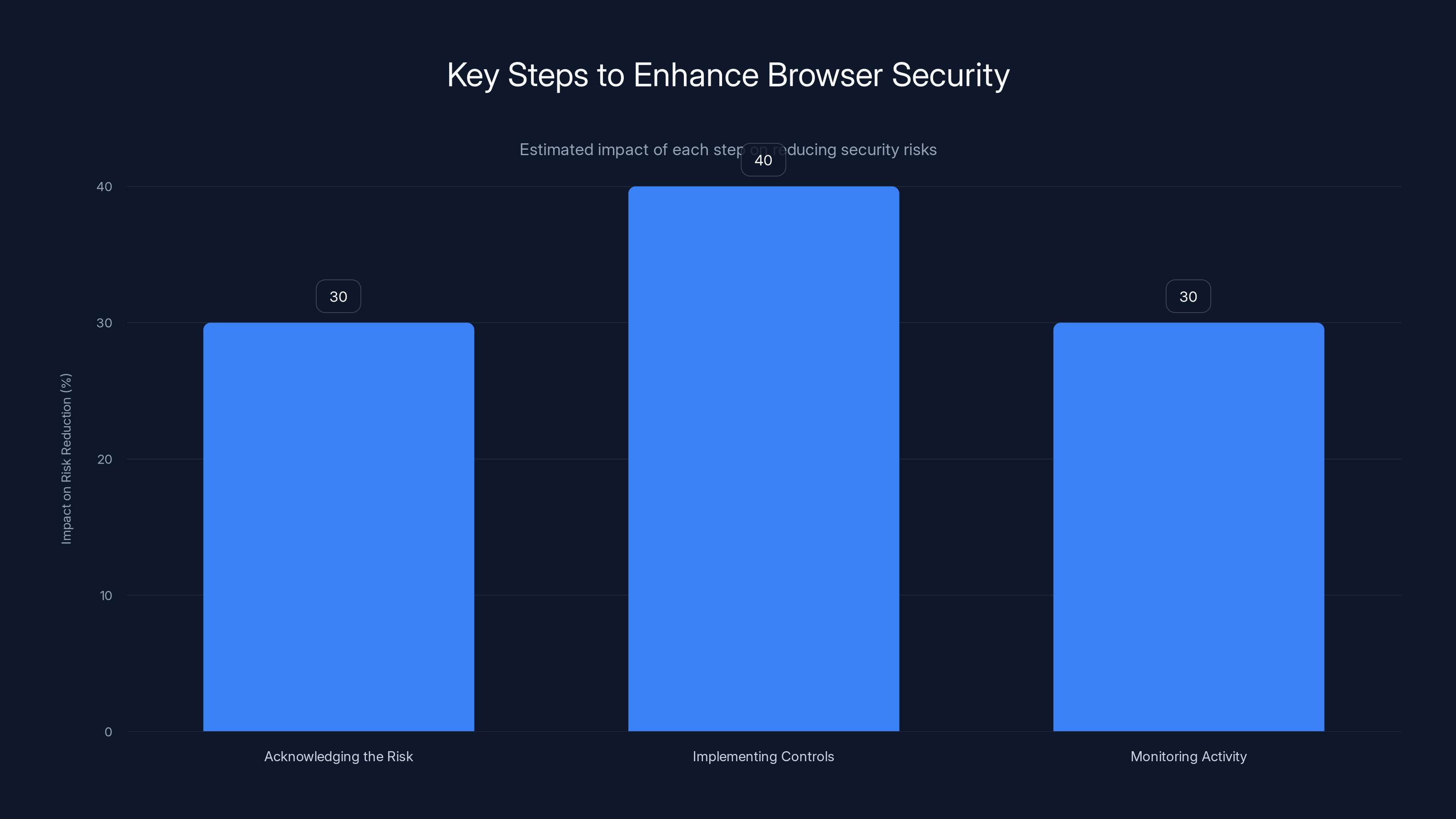
Implementing controls has the highest estimated impact on reducing security risks, followed by acknowledging the risk and monitoring activity. Estimated data based on typical organizational practices.
Part 9: The Broader Context: Why Extensions Remain a Security Weak Point
Why Browser Extension Security Lags
Browser extensions remain a significant security challenge because of fundamental architectural decisions made when they were created:
Permissiveness by Design
Browser extensions require broad permissions to be useful. An extension that can only access one specific website is limiting. Developers want to build powerful tools that work across the web. This creates a permission problem: either extensions are useless or they're dangerous.
Chrome's permission model has improved with manifest v3, but many extensions still operate under manifest v2 with extensive permissions.
Limited User Understanding
Most people don't understand what browser extensions are, what permissions they're requesting, or what they can theoretically do. When someone clicks "yes" to extension installation, they're not making an informed security decision—they're just clicking through a dialog.
Long Tail of Unmaintained Code
Thousands of extensions in the Chrome Web Store are abandoned by their developers. They don't receive security updates. They don't adapt to new browser versions. They become attack vectors simply because no one is actively maintaining them.
Store Moderation Challenges
Google's Chrome Web Store has millions of extensions. Manual review is impractical. Automated scanning can detect obvious malware, but sophisticated threats that masquerade as legitimate tools slip through.
The Future of Browser Extension Security
Manifest V3 Improvements
Google's manifest v3 specification for Chrome extensions restricts some dangerous capabilities:
- Web Request API limitations (harder to intercept traffic)
- Restricted DOM manipulation
- Required privacy policy disclosure
- Stronger content security policy requirements
However, these changes also restrict legitimate use cases, and attackers are already finding workarounds.
Zero-Trust Browser Architecture
Concept: every extension is treated as potentially untrustworthy. The browser:
- Requires explicit approval for each sensitive action
- Sandboxes extension execution
- Monitors extension behavior continuously
- Automatically disables extensions showing suspicious patterns
- Requires verified digital signatures from trusted publishers
This is technically feasible but would require significant changes to existing architectures.
Behavioral Analysis and ML Detection
Rather than static analysis of extension code (which misses sophisticated threats), security systems could use machine learning to detect behavioral anomalies:
- Extensions that modify authentication pages
- Extensions that communicate with domains unrelated to their stated purpose
- Extensions that read sensitive data they shouldn't need
- Extensions that perform administrative actions

Part 10: Industry Response and Regulatory Implications
How Major Platforms Responded
When Socket's research was disclosed publicly, both Google and the affected companies responded:
Chrome Web Store Removal
Google's security team removed all five extensions from the Chrome Web Store immediately upon notification. The company also implemented additional automated detection to prevent similar extensions from being published in the future.
However, this demonstrates a reactive posture. Detection came from external security researchers, not Google's internal monitoring.
Workday, NetSuite, and SAP Response
The companies published security advisories and recommended users:
- Uninstall any third-party extensions claiming to improve their systems
- Use official browser extensions only (if available)
- Reset passwords if they suspected compromise
- Review account activity for unauthorized access
While appropriate, these advisories came after the fact. Ideally, they would have actively monitored for extensions impersonating their services.
Regulatory and Compliance Implications
GDPR and Data Breach Notification
If these extensions resulted in exposure of personal data of EU residents, companies were legally obligated to:
- Notify EU data protection authorities within 72 hours
- Notify affected individuals without undue delay
- Implement corrective measures
The GDPR fine for failing to notify can reach €10-20 million or 2-4% of global revenue.
CCPA and State Privacy Laws
If US residents' data was compromised, similar notification requirements apply under California's CCPA and similar laws in other states (VCCPA, CTDPA, MTDPA, etc.).
SOC 2 and Audit Implications
Companies claiming SOC 2 compliance must show they have:
- Controls over third-party software installation
- Monitoring and logging of critical systems
- Incident response capabilities
- Regular security assessments
This incident highlights gaps that would be discovered in SOC 2 audits.
Cyber Insurance
Insurance claims related to extension-based attacks would likely be covered under cyber liability policies, assuming:
- The organization had basic security controls in place
- They responded appropriately once notified
- They didn't have unreasonable delay in notification
However, organizations that failed to implement extension governance might face claim denials or reduced payouts.
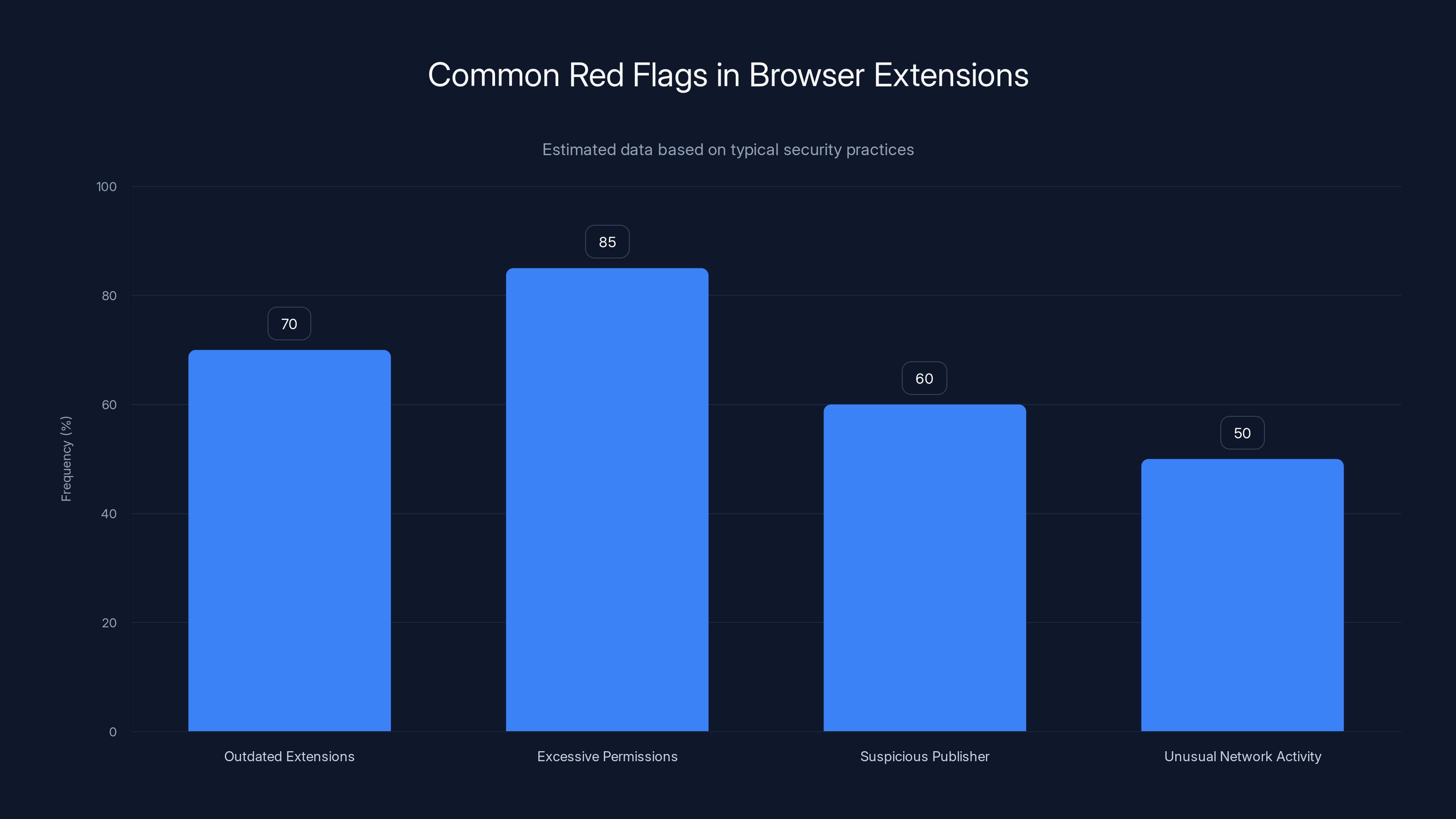
Excessive permissions and outdated extensions are the most common red flags in browser extensions. Estimated data.
Part 11: Lessons for Enterprise Security Teams
The Organizational Gaps These Extensions Exploited
Gap 1: Lack of Browser Extension Governance
Most organizations have policies for server security, network security, and application security. Browser extension governance is absent from the vast majority of security programs.
This is understandable—five years ago, browser extensions seemed like a minor threat vector. Today, they're a primary attack surface for enterprise credential theft.
Gap 2: Insufficient Endpoint Monitoring
Many organizations monitor servers and network appliances but have limited visibility into what's actually running on employee computers. If your SOC can't see that a malicious extension is installed, they can't detect or respond to the threat it poses.
Gap 3: Inadequate Access Logging
ERP and HR systems are often logging authentication events but not analyzing them. Security teams weren't regularly reviewing access logs to identify:
- Unusual geographic patterns
- Simultaneous sessions
- Failed administrative actions
- Off-hours access
Gap 4: Slow Incident Response Procedures
From discovery to full remediation, response procedures should be practiced and efficient. Organizations that first heard about these extensions from news articles rather than their own detection had already failed this test.
Gap 5: Limited User Security Awareness
Employees who understand security risks are less likely to install suspicious extensions. Training matters. Regular reminders matter. Creating a security culture where employees report suspicious tools matters.
Building a Mature Security Program
Establish Baseline Expectations
Your organization should have clarity on:
- What software and extensions are approved for company use
- What permissions are acceptable
- How extensions will be monitored and audited
- What users should do if they suspect a threat
- How quickly security can respond to incidents
Layer Multiple Defenses
Single-layer defenses fail. Multiple overlapping layers increase detection and prevent single points of failure:
- Network layer (DNS filtering, WAF)
- Endpoint layer (EDR, antivirus)
- Browser layer (extension management)
- Application layer (MFA, logging, conditional access)
- User layer (training, awareness)
Regular Testing and Tabletops
Conduct regular exercises:
- Red team exercises testing extension-based attacks
- Incident response tabletops practicing breach response
- Phishing simulations with extension recommendations
- System security reviews of critical applications
Theory is nice. Practice is what builds muscle memory for your team.
Metrics and Accountability
Measure what matters:
- Number of unapproved extensions detected and removed
- Time to detect compromise (should be hours, not months)
- Time to full remediation after discovery
- Percentage of users completing extension audits
- Percentage of critical systems with MFA enabled
Dashboard these metrics. Present them to leadership. Tie them to security program maturity ratings.

Part 12: Practical Checklist for Organizations
Immediate Actions (This Week)
- Audit all extensions installed across your organization
- Remove any extensions not on approved list
- Check for Data By Cloud, Access 11, Data By Cloud 1, Data By Cloud 2, and Software Access specifically
- Review extensions installed on executive and admin accounts specifically
- Document your current extension landscape (spreadsheet with user, extension, install date, purpose)
Short-Term Actions (This Month)
- Develop formal browser extension policy
- Create approved extension list
- Deploy MDM/browser management tools to enforce policy
- Enable MFA on all HR and ERP systems
- Implement DNS filtering for known malicious domains
- Train users on extension risks
- Set up alerts on anomalous ERP/HR access patterns
Medium-Term Actions (This Quarter)
- Implement EDR tools on all endpoints
- Deploy WAF in front of critical applications
- Conduct incident response tabletop for extension-based attack
- Establish credential monitoring subscription
- Audit all admin accounts and their extension usage
- Review and optimize session management policies
- Implement automated threat hunting for extension-related IOCs
Long-Term Actions (This Year)
- Build extension security assessment process
- Achieve SOC 2 compliance with specific extension controls
- Migrate to manifest v3 extensions where possible
- Implement zero-trust architecture considerations
- Conduct annual security assessment of extension landscape
- Establish metrics and dashboard for extension-related security indicators
Part 13: Red Flags to Train Your Team On
What Every Employee Should Know
Your front-line defense is your employees. They interact with applications and extensions daily. They notice when something seems off. But they need to know what "off" means.
Red Flags for Extensions
- "I found this extension that makes Workday faster"
- "Someone recommended this NetSuite plugin"
- "This extension appeared in my Chrome when I updated something"
- "An email said we should install this HR tool"
- "This extension's permissions seem weird, but I installed it anyway"
Train employees to report these immediately, without judgment.
Red Flags for Account Access
- "I got a password reset email I didn't request"
- "Someone else seems to be using my account"
- "I see login notifications from places I haven't been"
- "My ERP admin functions aren't working"
- "Someone told me they can't access a file I shared"
Red Flags in System Behavior
- Unexpected redirects on company websites
- Login pages that look slightly different
- Timeouts or slowness when accessing sensitive systems
- Pop-ups or security warnings you've never seen
- Browser acting sluggish or hot (CPU intensive)
Creating a Safe Reporting Culture
The biggest threat to security is when employees notice red flags but don't report them because they're afraid of:
- Looking stupid ("I probably installed malware")
- Getting in trouble ("Will I be fired for clicking the wrong thing?")
- Wasting IT's time ("Is this really important?")
Counter this by:
- Creating a clear, non-punitive reporting channel
- Celebrating reports of suspicious activity
- Sharing (anonymized) outcomes from reports that led to discoveries
- Making it easier to report than to ignore (one click, not a form)
- Recognizing that security is everyone's job
Part 14: Vendor and Third-Party Risk Management
Extending Security Beyond Your Walls
This incident also highlights the risk of third-party software distribution. Softonic, SourceForge, and similar sites aren't inherently evil, but they have:
- Minimal curation
- Financial incentives to maximize downloads
- Limited security vetting
- Difficulty enforcing removal of compromised software
When your organization uses cloud services (Workday, NetSuite, etc.), you're trusting those vendors' security. But you're also exposed to attacks on users accessing those services.
Vendor Assessment Questions
When evaluating vendors (whether Workday, your MDM provider, or anyone else):
- What's your security incident history? (Ask for specific incidents)
- What's your incident response time? (Should be hours, not days)
- Do you monitor for impersonation attacks? (These extensions are examples)
- What security certifications do you maintain? (SOC 2 Type II minimum)
- Can you provide security documentation and audit reports?
- What's your vulnerability disclosure and patch timeline?
- Do you conduct regular security assessments?
- What's your data breach notification process?
Supply Chain Risk Management
Extensions are part of your software supply chain. Other parts include:
- Vendor software and SaaS applications
- Open source libraries in your code
- APIs and integrations
- Contractor-developed code
- Third-party service providers
Each represents a potential attack surface. Your organization should have:
- Inventory of all software in use
- Assessment of security posture of each vendor
- Monitoring for known vulnerabilities in third-party code
- Regular audits and penetration testing of integrations
- Incident response procedures for compromised vendors
Part 15: Future-Proofing Your Security Program
Emerging Threats on the Horizon
AI-Generated Malicious Extensions
As AI tools become more capable, attackers will use them to:
- Automatically generate large numbers of plausible-looking extensions
- Adapt extension code to evade detection
- Create phishing lures targeting specific organizations
- Generate documentation making extensions seem legitimate
Defense: Behavioral monitoring becomes even more important than static analysis. Machine learning detection of anomalous extension behavior will be critical.
Browser Fingerprinting and Evasion
Malicious extensions will adapt to detect when they're being analyzed or monitored, similar to how malware behaves differently in sandboxes.
Defense: Assume evasion and build detection that works against evasion-aware threats.
Privilege Escalation Through Extensions
Today's extensions operate at browser user privilege level. Tomorrow's might exploit browser vulnerabilities to gain system-level access.
Defense: Sandboxing browsers at the OS level, updating browsers frequently, and monitoring for privilege escalation attempts.
Multi-Stage Extension Attacks
Extensions that appear benign initially but become malicious after installation or after receiving remote commands.
Defense: Continuous monitoring of extension behavior, not just installation verification.
Building Organizational Resilience
Resilience isn't about preventing all attacks. It's about detecting attacks quickly, responding effectively, and recovering completely.
Your organization should be able to:
- Detect extension-based attacks within hours, not weeks or months
- Contain the attack to prevent lateral movement
- Investigate thoroughly to understand what was accessed or exfiltrated
- Remediate completely so the attacker can't regain access
- Learn from the incident to prevent recurrence
This requires investment in people, processes, and tools. But the cost of a compromise in a major ERP system far exceeds the cost of prevention.

FAQ
What are malicious Chrome extensions targeting Workday and NetSuite?
Malicious Chrome extensions are browser add-ons designed to steal credentials and enable account takeover for enterprise applications like Workday, NetSuite, and SuccessFactors. Five specific extensions (Data By Cloud Access Tool, Access 11, Data By Cloud 1, Data By Cloud 2, and Software Access) were discovered by security researchers at Socket. They operated for years before detection, with some published more than four years prior, and were downloaded approximately 2,739 times across enterprises and multinational organizations.
How do these malicious extensions steal credentials?
These extensions inject custom login forms or intercept credentials as users type them into legitimate Workday, NetSuite, or SuccessFactors login pages. The captured username, password, MFA tokens, and session cookies are immediately transmitted to attacker-controlled servers. The extensions then forward the legitimate credentials to the actual service, so users experience normal login—never realizing their credentials were stolen. This silent duplication of credentials is what made detection extremely difficult.
What makes session hijacking more dangerous than password theft?
Session hijacking is more dangerous because it doesn't require password resets to remediate. Once an attacker captures a session token or cookie, they can reuse it to maintain access to an account even after the user logs out. Session tokens often remain valid for hours or days, giving attackers an extended access window. Additionally, session-based access can appear to be the legitimate user's activity, making it harder for security teams to distinguish unauthorized access from normal usage patterns.
Can I detect these extensions myself?
Yes, you can perform a basic audit by opening Chrome's extension manager at chrome://extensions and reviewing each installed extension for: unfamiliar names, lack of recent updates, overly broad permissions (especially "modify all data on websites you visit"), and unverifiable publishers. However, sophisticated malicious extensions can masquerade as legitimate tools and still operate silently. Technical detection requires network monitoring tools, access log analysis, or endpoint detection and response (EDR) solutions that your organization's IT team should implement and monitor.
Are these extensions still available for download?
They were removed from the official Chrome Web Store immediately when discovered, but they migrated to third-party software distribution sites like Softonic and SourceForge where they may still be available. The key takeaway: never download browser extensions from third-party sites. The only legitimate source for Chrome extensions is the official Chrome Web Store, and even there, users should verify the publisher's legitimacy and read reviews carefully before installation.
What should I do if I think I installed one of these extensions?
Uninstall the extension immediately, then perform these steps: clear your browser cache and cookies completely, force a password reset for your Workday/NetSuite/SuccessFactors accounts (obtain the reset through an official channel, not email), check your account's active sessions and terminate all of them, review your account's login history and recent activity for unauthorized access, and contact your IT security team to report the incident. They can analyze your account for signs of compromise and determine if further remediation is necessary.
How can organizations prevent these kinds of attacks?
Organizations should implement a formal browser extension governance program that includes: maintaining an approved list of extensions and blocking all others (using MDM tools), requiring multi-factor authentication on critical systems like ERP platforms, monitoring network traffic and endpoint behavior for suspicious activity, implementing regular security training for employees about extension risks, and conducting regular audits of installed extensions. Additionally, enabling detailed access logging and reviewing those logs regularly can help detect compromised accounts quickly, before attackers cause significant damage.
What are the financial and regulatory consequences of these attacks?
A successful compromise of an ERP system can result in millions of dollars in direct damages (fraudulent transactions, data theft), plus additional costs from incident response, forensics, regulatory fines, and customer notification. Under GDPR, companies can face fines up to 4% of global revenue or €20 million for failing to protect personal data. Under CCPA and other state privacy laws, similar notification requirements and penalties apply. Additionally, affected companies must notify customers and regulators, manage reputational damage, and likely face shareholder liability and class action lawsuits.
How long could these extensions have compromised my organization?
The extensions were discovered by external researchers after operating for multiple years—some were published over four years prior to discovery. This means if your organization had an employee who installed one of these extensions, the compromise window could have been 12+ months. During that entire period, any actions performed by affected user accounts could have been performed by an attacker. This underscores the critical importance of checking browser extension installation dates and suspicious activity logs, not just current status.

Conclusion: Building Security Into Your Browser Environment
Browser extensions represent an enormous blind spot for most enterprise security programs. We focus on servers, networks, and applications while largely ignoring the one tool almost every employee uses for hours every day: their web browser.
These five malicious extensions—operating undetected for years, stealing credentials from thousands of employees at enterprises and multinational organizations—illustrate how costly this oversight can be. A single compromised account in a Workday or NetSuite system can cascade into a company-wide catastrophe: fraudulent financial transactions, stolen employee data, regulatory violations, and operational disruption.
The technical sophistication of these extensions deserves respect. They didn't just steal credentials—they actively blocked remediation, understanding that security teams would eventually detect them and attempting to prevent teams from responding effectively. This shows attackers that were thinking beyond the initial compromise, planning for the eventual discovery, and architecting persistence.
But here's the thing: none of these extensions required zero-day exploits or sophisticated vulnerability research. They exploited a simple truth: most organizations don't have any governance around browser extensions at all. If you install anything, it works. No questions asked. No review process. No continuous monitoring.
Addressing this is entirely within reach. It's not expensive. It doesn't require exotic technology. It requires:
-
Acknowledging the risk: Extensions are software. Software can be malicious. Your organization needs policies governing software installation and use.
-
Implementing controls: Deploy mobile device management or browser management tools to enforce an approved extension list. Start small—you don't need hundreds of approved extensions. Start with the ones people actually need.
-
Monitoring activity: Implement endpoint detection and response. Monitor access logs for suspicious patterns. Set up alerts for unusual access. The goal is to detect compromise in hours, not months.
-
Educating users: Employees are your first line of defense. Train them to recognize red flags. Make it easy for them to report suspicious activity. Create a culture where security is a shared responsibility.
-
Planning for incidents: Assume compromise will happen. Have procedures ready. Practice incident response. Know your escalation paths and response timelines.
The organizations that will succeed long-term are those that recognize browser security as a critical component of their overall security program—equal in importance to server security, network security, and application security.
Your enterprise platform vendors (Workday, NetSuite, SAP) have done their part by removing these malicious extensions. But they can't protect you from extensions that masquerade as productivity tools. That responsibility falls on you and your security team.
Start today. Open chrome://extensions. Take a hard look at what's installed. Ask yourself: do I know what each of these does? Do I trust the publisher? Is it actually necessary? If the answer to any of those is "no," delete it.
Then talk to your IT and security teams about building a formal extension governance program. It will be the best security investment you make this year.
Ready to strengthen your security program? Start with these essentials:
- Schedule an audit of all extensions across your organization
- Implement multi-factor authentication on critical systems
- Deploy endpoint detection and response tools
- Create formal policies and training for extension usage
Your future self will thank you when you catch the next attack before it becomes a nightmare.

Key Takeaways
- Five malicious Chrome extensions spoofed Workday, NetSuite, and SuccessFactors to steal credentials and enable account takeover attacks on enterprise employees
- These extensions operated undetected for over four years, with some downloaded across hundreds of organizations, demonstrating the critical gap in browser extension governance
- Session hijacking combined with remediation blocking created scenarios where security teams detected compromises but couldn't remediate them through normal channels
- Organizations must implement comprehensive browser extension governance including allowlisting, MFA on critical systems, and endpoint detection to prevent similar attacks
- Detection and remediation require multi-layered approach: network monitoring, endpoint detection, access log analysis, credential monitoring, and fast incident response procedures
Related Articles
- Most Spoofed Brands in Phishing Scams [2025]
- LinkedIn Comment Phishing: How to Spot and Stop Malware Scams [2025]
- Critical Cybersecurity Threats Exposing Government Operations [2025]
- Supreme Court Hacker Posted Stolen Data on Instagram [2025]
- Massive Phishing Campaign Targets Middle East Officials, Activists, Journalists [2025]
- Cisco CVE-2025-20393 Critical Vulnerability Finally Patched [2025]



