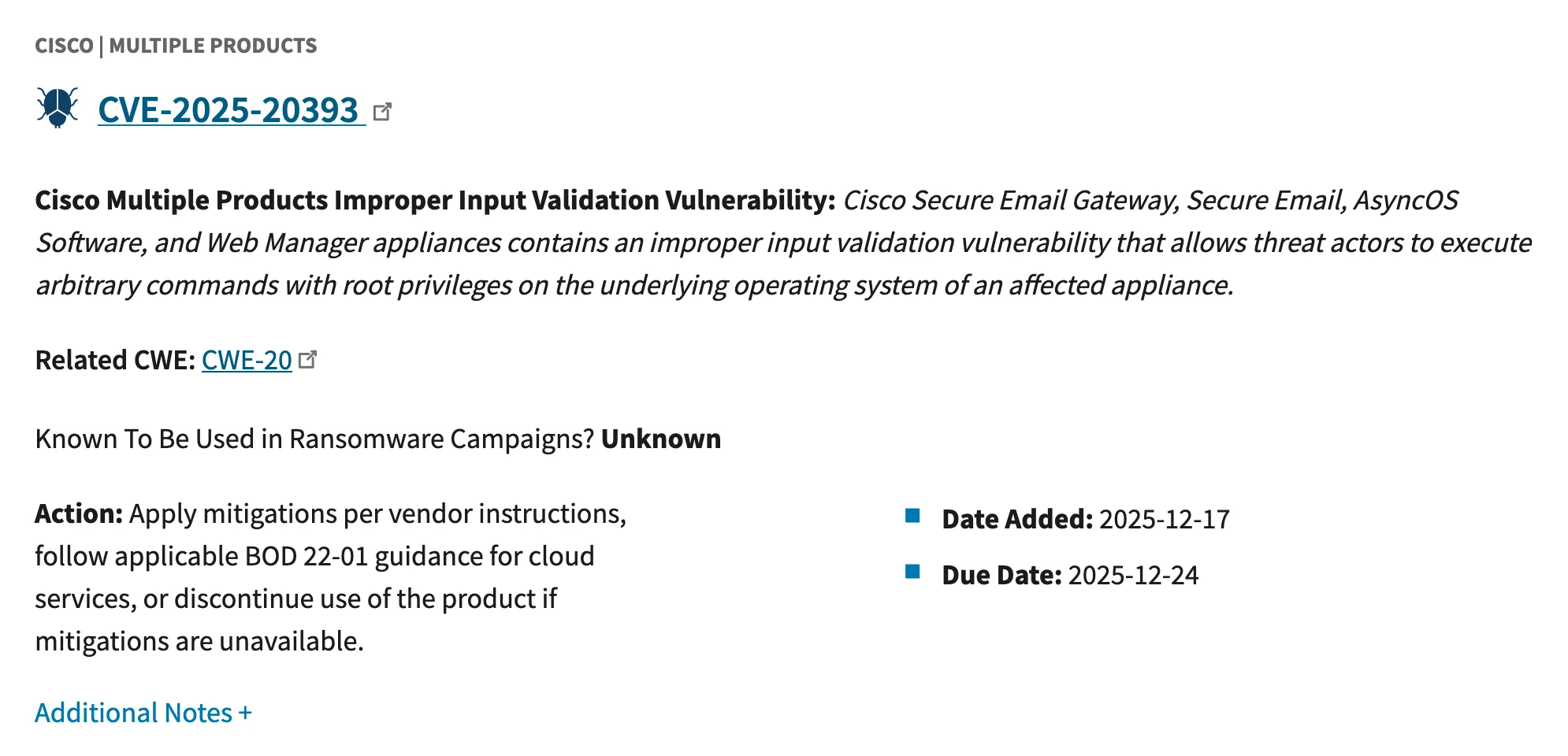
Cisco CVE-2025-20393: Critical Email Security Vulnerability Finally Patched [2025]
A critical remote code execution vulnerability that affected millions of users worldwide has finally received a patch. For weeks, Chinese state-sponsored threat actors exploited this maximum-severity flaw in Cisco's email security products without detection or remediation. Now that the patch is available, organizations need to understand what went wrong, why the response took so long, and most importantly, how to protect their infrastructure right now.
TL; DR
- Critical RCE Flaw (CVE-2025-20393): Affects Cisco Secure Email Gateway (SEG) and Secure Email and Web Manager (SEWM) appliances with a perfect 10/10 severity score as detailed in Help Net Security.
- Active Exploitation Timeline: Chinese threat actors (APT41, UAT-9686, UNC5174) exploited this vulnerability since at least late November 2025 using Aquashell backdoor and persistence mechanisms, as reported by SOCRadar.
- Patch Now Available: Cisco released comprehensive updates removing persistence mechanisms, but the extent of global compromise remains unknown, according to SOC Prime.
- Persistence Risk: Attackers installed multiple tools (Aquashell, Aqua Tunnel, Chisel, Aqua Purge) to maintain long-term access to email systems.
- Immediate Action Required: Organizations must apply patches immediately and audit email systems for signs of compromise or unauthorized access.

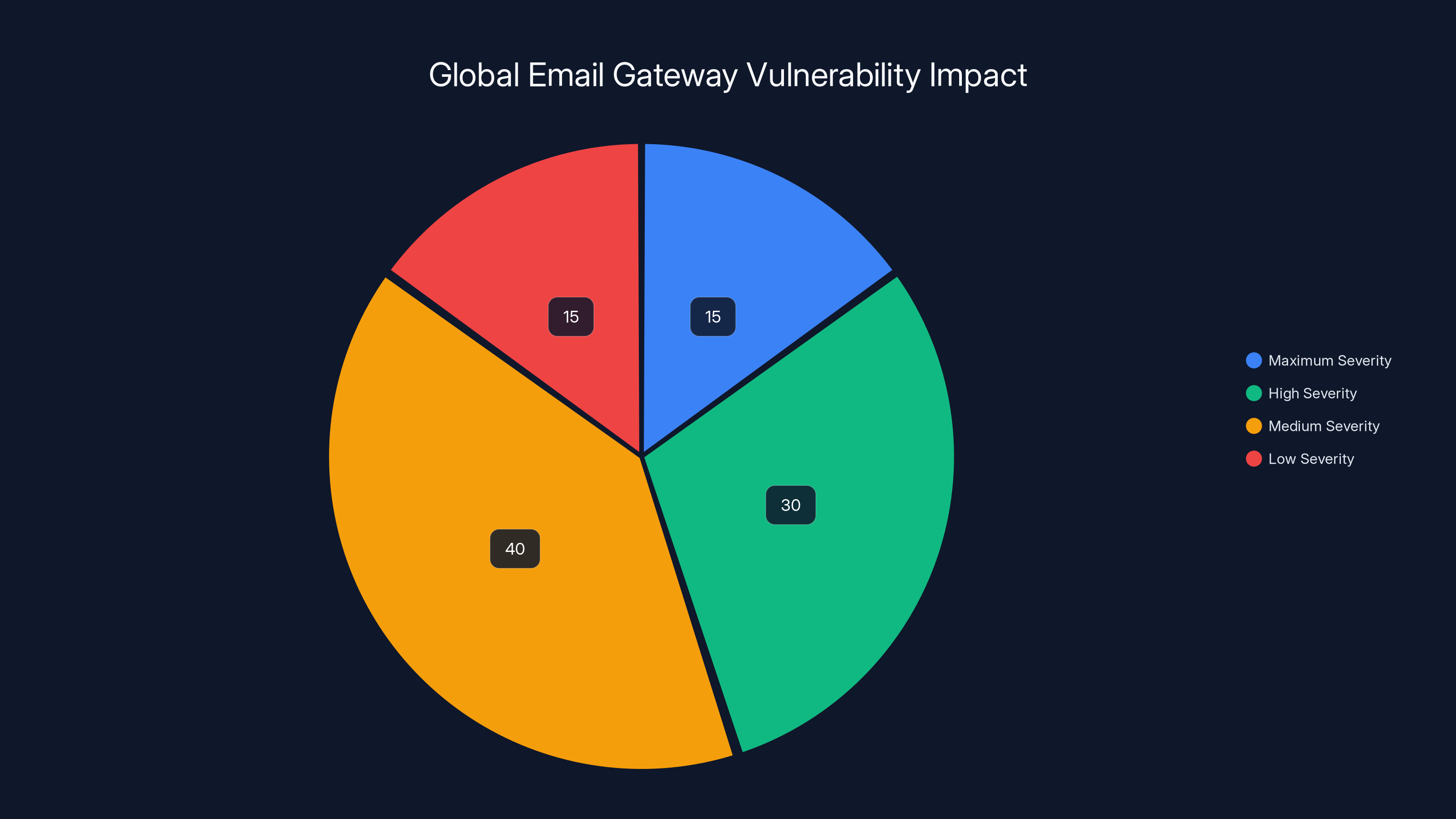
Estimated data shows that maximum severity vulnerabilities like CVE-2025-20393 account for 15% of email gateway vulnerabilities in 2025, highlighting the critical risk posed by such flaws.
Understanding CVE-2025-20393: The Maximum-Severity Email Gateway Flaw
In mid-December 2025, Cisco disclosed what many in the cybersecurity community feared: a maximum-severity vulnerability in its widely-deployed Secure Email products that was already being exploited in the wild. The vulnerability, cataloged as CVE-2025-20393, carries a CVSS score of 10/10, which represents the highest possible severity rating. This perfect score isn't hyperbole or marketing; it reflects the brutal reality of what attackers could do with this flaw, as explained by Arctic Wolf.
The vulnerability exists in Async OS, the underlying operating system powering Cisco's Secure Email Gateway and Secure Email and Web Manager appliances. These aren't obscure products relegated to a handful of enterprises. Secure Email Gateway alone protects email infrastructure for thousands of organizations globally, making this vulnerability a potential nightmare scenario for IT security teams.
What makes CVE-2025-20393 particularly dangerous is the type of access it grants. An unauthenticated attacker can exploit this flaw remotely to execute arbitrary commands with root-level privileges on the affected appliance. Root access means complete system compromise: read any file, modify any setting, install backdoors, exfiltrate data, or pivot to other network segments. For an attacker, this is the digital equivalent of having a master key to every door in a building.
The attack doesn't require sophisticated social engineering, phishing, or user interaction. There's no "click here to get compromised" moment. The vulnerability is unauthenticated, meaning an attacker positioned on the network can trigger it without providing valid credentials or sending specially crafted messages. This eliminates traditional security layers like credential-based access controls.
Cisco's official statement confirmed what security researchers feared: "This attack allows the threat actors to execute arbitrary commands with root privileges on the underlying operating system of an affected appliance." The straightforward wording masks the severity. Root command execution on a critical infrastructure device means total compromise.
The Async OS Operating System and Email Appliances
Async OS powers several product lines across Cisco's security portfolio. It's purpose-built for email processing, threat detection, and network security. Unlike general-purpose operating systems, Async OS is optimized for handling massive volumes of email traffic while applying security scanning, threat intelligence, and policy enforcement.
The architecture includes multiple processing layers: initial SMTP connection handling, content scanning, attachment analysis, reputation checking, and policy application. A vulnerability in Async OS itself bypasses all these layers. It's like finding a vulnerability in the building's foundation that lets you skip all security checkpoints on every floor.
Cisco markets these appliances specifically to organizations handling sensitive information: financial institutions, healthcare providers, government agencies, and large enterprises. The installed base includes some of the world's most critical infrastructure. When a CVE-2025-20393-level vulnerability affects this product, it's not a minor issue to patch during the next maintenance window. It's an emergency requiring immediate action.
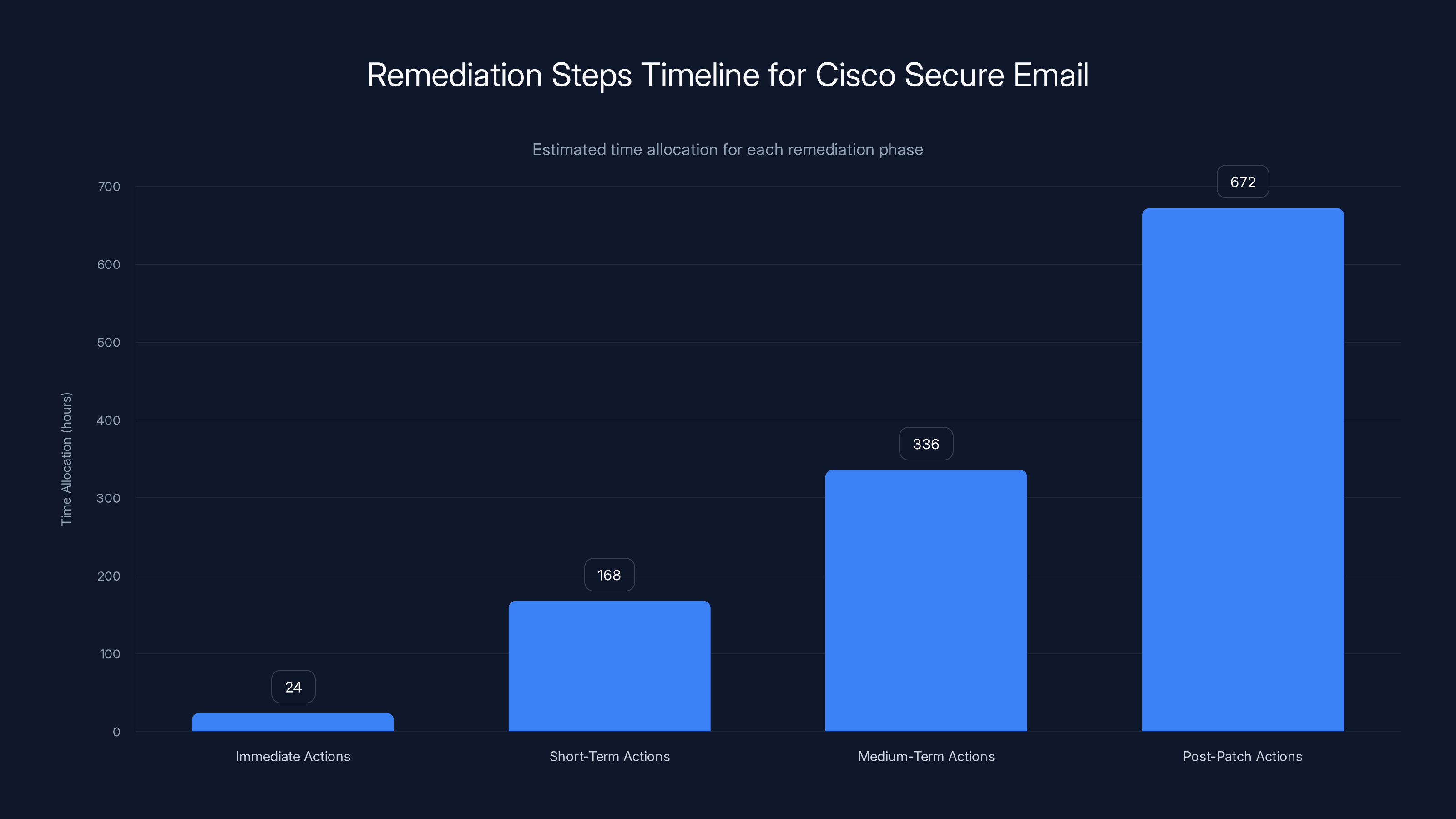
Estimated data showing the time allocation for each remediation phase, with immediate actions requiring the least time and post-patch actions requiring ongoing attention.
The Chinese Threat Actor Campaign: APT41, UAT-9686, and UNC5174
Within days of Cisco's initial disclosure, cybersecurity researchers from multiple firms reported that Chinese state-sponsored threat actors were already exploiting this vulnerability. The campaign involved at least three distinct threat groups tracked by different names across the security industry: APT41, UAT-9686, and UNC5174. Some evidence suggests these groups may share overlapping operations or coordinate activities, though attribution remains complex, as noted by Bleeping Computer.
What's remarkable is the timeline. Cisco disclosed the vulnerability in mid-December 2025. Reports emerged showing Chinese threat actors had been exploiting it since at least late November 2025. That's a gap of several weeks where the vulnerability was actively being weaponized while organizations remained unaware.
This timeline raises uncomfortable questions. How did Chinese intelligence services obtain information about CVE-2025-20393 before Cisco's public disclosure? The possibilities include: advance knowledge through intelligence sources, detection of Cisco's internal development and testing, or independent discovery of the same vulnerability. Regardless of the source, the fact that attackers had operational capabilities deployed before public awareness suggests this wasn't a last-minute zero-day. The planning and tooling required to mount coordinated attacks across multiple Cisco deployments takes time.
APT41: Financially-Motivated State Operators
APT41 occupies a unique position in the threat landscape. This Chinese-affiliated group conducts both state-sponsored espionage operations and financially-motivated cybercrime, sometimes in parallel. They're known for sophisticated attacks against healthcare, telecommunications, technology, and public sector organizations. APT41 brings substantial resources and patience to their operations, often maintaining access to networks for months or years before extracting value.
APT41's involvement in CVE-2025-20393 exploitation fits their operational profile: targeting critical infrastructure, seeking long-term persistence, and maintaining intelligence collection capabilities. Unlike ransomware gangs who want quick paydays, APT41 values sustained access for espionage and competitive intelligence.
UAT-9686 and UNC5174: Additional Attribution Complexity
Different cybersecurity firms use different naming conventions for threat groups. UNC designations (Uncategorized) are used by some researchers when they can confirm a group exists but lack sufficient data for formal attribution. UAT-9686 appears to be a tracked group with specific operational characteristics.
The existence of multiple group names exploiting the same vulnerability could indicate several scenarios: different Chinese intelligence agencies conducting independent operations, regional divisions within a larger group, or different firms tracking the same attackers under different names. This complexity in attribution is actually common with major vulnerabilities. A high-value target attracts multiple threat actors simultaneously.
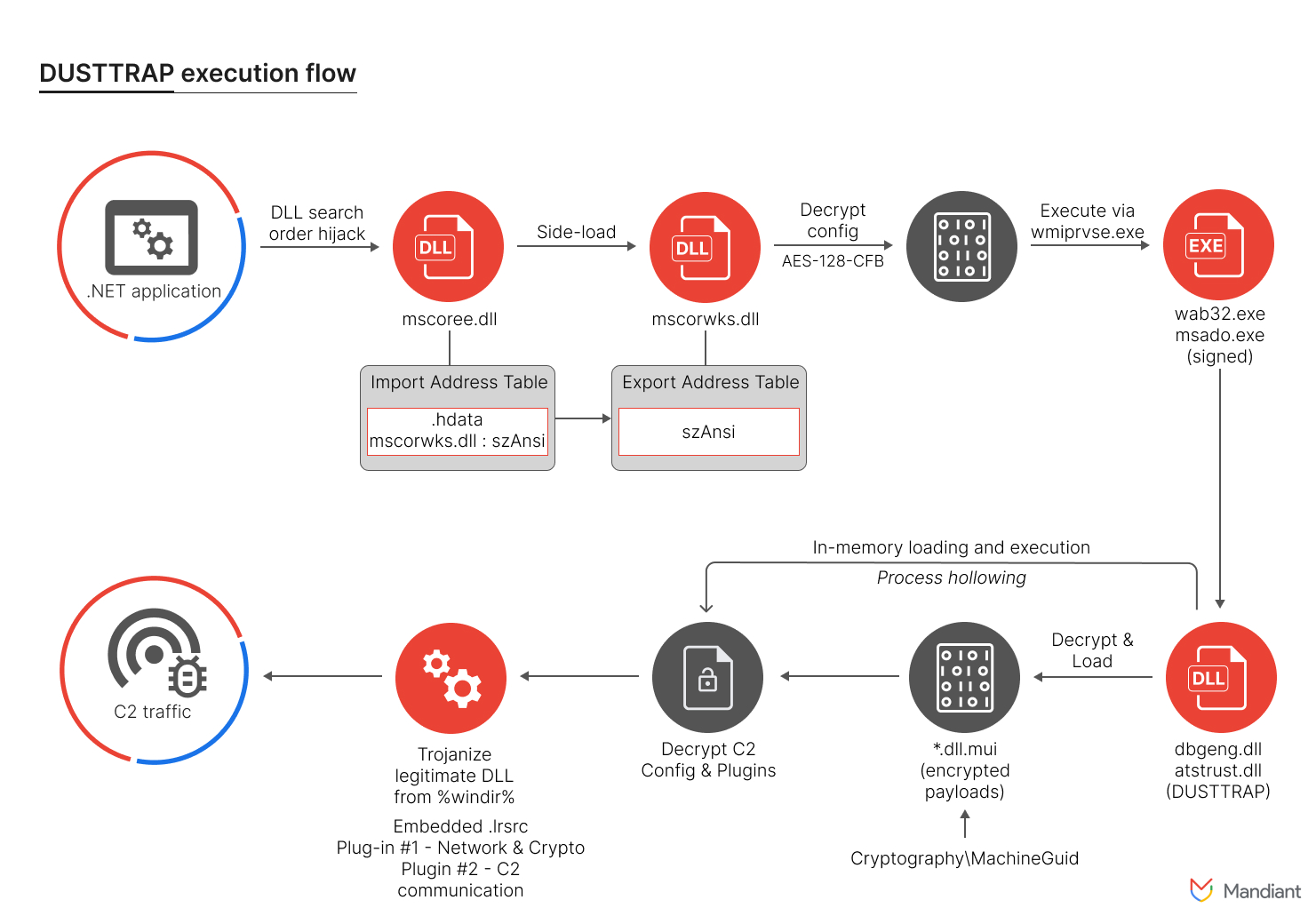
Aquashell Backdoor: The Persistence Mechanism
What made this campaign particularly concerning wasn't just the initial compromise, but the tools deployed to maintain persistent access. Cisco and security researchers identified several tools used to maintain control over compromised appliances, as detailed by Talos Intelligence.
Aquashell: Python-Based Persistence
Aquashell is a Python-based backdoor specifically designed to maintain persistent access to Cisco appliances. This isn't a generic remote access trojan. It's purpose-built for the target environment, suggesting significant engineering effort and specific knowledge of Cisco systems.
The use of Python is significant. Cisco email appliances run variants of Linux/Unix operating systems that natively support Python. By writing the backdoor in Python, attackers avoid the need to compile platform-specific binaries, making deployment simpler and reducing the risk of detection from file analysis tools looking for suspicious binaries.
Aquashell provides threat actors with multiple capabilities:
- Command execution: Run arbitrary shell commands with root privileges
- Interactive shell access: Maintain reverse shell sessions back to attacker-controlled servers
- File transfer: Exfiltrate data from the compromised appliance
- Process management: Start, stop, or modify running processes
- Credential harvesting: Access email configurations and authentication systems
- Lateral movement: Use the compromised appliance as a pivot point into the network
The sophistication here is notable. This isn't a commodity backdoor downloaded from the dark web. This is custom tooling developed specifically for this operation, indicating substantial resources and expertise.
Aqua Tunnel: SSH-Based Reverse Tunneling
Aqua Tunnel implements reverse SSH tunneling, a technique that allows attackers to create encrypted communication channels from the compromised appliance back to attacker-controlled servers. Why is this important? Many organizations implement network monitoring that watches outbound connections. A reverse SSH tunnel encrypts the traffic, making it invisible to standard network detection systems.
Reverse SSH tunneling also bypasses firewall rules in an elegant way. Instead of the attacker initiating inbound connections (which firewalls typically block), the compromised system initiates outbound SSH connections to attacker infrastructure. The firewall sees this as normal outbound traffic to legitimate SSH ports.
Once the tunnel is established, attackers can tunnel other traffic through it, effectively creating a VPN connection to the compromised network. They can then access internal systems, databases, and services without appearing to connect directly.
Chisel: Multi-Protocol Tunneling
Chisel is a legitimate open-source tool (not malware) that provides tunneling capabilities over HTTP and Web Socket connections. By using Chisel, attackers further obfuscate their command and control traffic, making it blend with legitimate web traffic. This is a common evasion technique: using legitimate tools rather than custom malware.
Chisel's flexibility allows attackers to tunnel multiple protocols, not just SSH. They can tunnel SOCKS proxies, RDP, or custom protocols, giving them flexible access to internal systems.
Aqua Purge: Log Destruction
Aqua Purge is a log-clearing utility designed to remove evidence of the attack. This is crucial for attackers attempting to maintain long-term access without detection. By removing or modifying logs, they prevent security teams from finding evidence of the compromise during standard security audits or investigations.
Log destruction is a classic indicator of sophisticated attackers. Immediately after gaining access, they move to sanitize evidence. If a security team can't find logs showing the initial compromise, they can't understand the scope of the breach or determine what data was accessed.
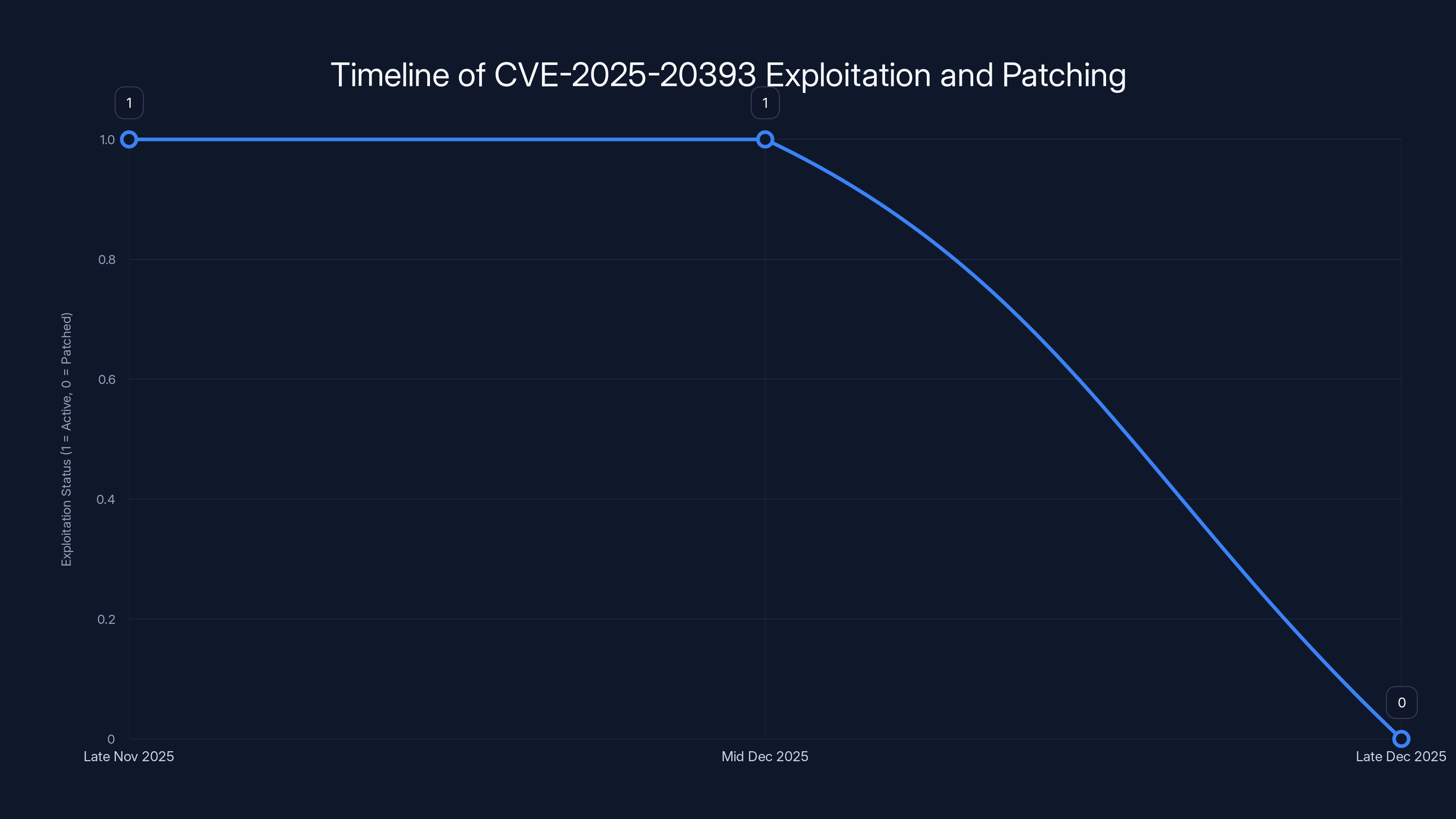
The CVE-2025-20393 vulnerability was actively exploited for approximately 4-6 weeks from late November to late December 2025 before patches were available. Estimated data.
The Timeline: Exploitation Before Disclosure
Understanding when attacks began and when Cisco became aware is crucial for understanding the scope of the problem.
November 2025: Exploitation Begins
According to security researchers, Chinese threat actors began exploiting CVE-2025-20393 in late November 2025. At this point, Cisco had either not discovered the vulnerability or was conducting internal testing. Organizations running Cisco Secure Email products had no awareness that their systems were under active attack. No patches existed. No security advisories existed. The window was open for exploitation, as detailed by Cybersecurity News.
Mid-December 2025: Public Disclosure
In mid-December, Cisco made the vulnerability public, assigning CVE-2025-20393 and releasing initial security guidance. However, the initial guidance didn't include patches. Cisco advised hardening measures while engineering teams worked on fixes. This created an uncomfortable gap where organizations knew about the vulnerability but couldn't patch it.
The public disclosure also triggered a cascade of events. Security researchers immediately began analyzing the vulnerability, trying to understand its nature. Other threat actors beyond the initial Chinese groups likely took notice, realizing they could also exploit unpatched systems.
Late December 2025: Patch Release
Cisco finally released patches addressing the vulnerability. However, by this point, the damage was done. Cisco acknowledged in their advisory that "ongoing investigation has revealed evidence of a persistence mechanism implanted by the threat actors to maintain a degree of control over compromised appliances."
Translation: Attackers had weeks to install backdoors, and even after patching the initial vulnerability, removing those backdoors would require additional investigation and remediation.
Post-Patch: Remediation Challenge
Cisco's official statement acknowledged the challenge: "These updates also remove persistence mechanisms that may have been installed during a related cyberattack campaign." This suggests the patches themselves include code that detects and removes backdoors. However, not all organizations apply patches immediately, and some may have already been compromised before they were even aware of the vulnerability.

Impact Assessment: How Many Organizations Were Compromised?
The honest answer is: nobody knows for certain. Cisco hasn't disclosed the number of affected organizations, and likely doesn't have complete visibility into the scope. This creates a frustrating situation for IT teams trying to understand their risk.
Known Compromised Systems
Security researchers have confirmed attacks against Cisco Secure Email Gateway and Secure Email and Web Manager instances. These are enterprise-grade appliances, not small deployments. Organizations running them tend to be larger enterprises, government agencies, financial institutions, and other high-value targets.
Estimated Total Exposure
Cisco has installed tens of thousands of Secure Email Gateway appliances globally. Even if only a fraction of those were compromised, we're talking about hundreds or thousands of organizations with potentially breached email systems. For each compromised email gateway, attackers gained access to:
- All inbound email (visibility into what's coming in)
- All outbound email (visibility into what organization is sending)
- Stored messages and archives
- User credentials and authentication systems
- Internal network topology information
- Integration details with other systems
For attackers conducting intelligence gathering, this is extraordinarily valuable. An email gateway is a window into every communication within an organization.
Why Full Visibility Is Impossible
Cisco wouldn't know about every compromise unless organizations reported them. But here's the problem: many organizations don't discover breaches for months or years. The attackers using Aquashell specifically installed tools to hide their presence (Aqua Purge log deletion). They had no incentive to be noisy or trigger alerts.
Some organizations may have been compromised, never detected it, and still don't know. Their email systems are potentially still being monitored by Chinese intelligence services.
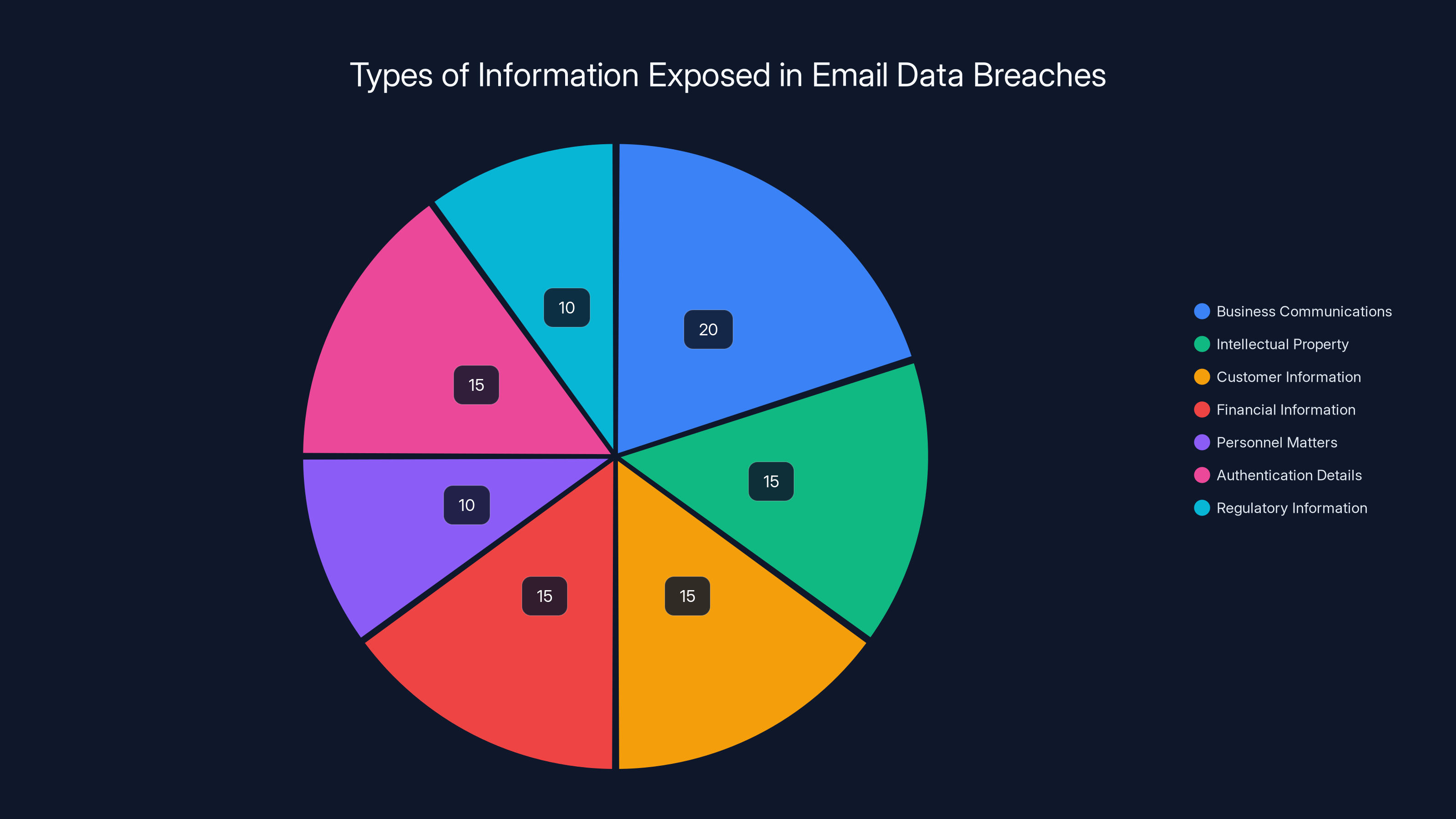
Business communications and intellectual property are the most exposed information types in email data breaches, each accounting for approximately 20% of the exposure. (Estimated data)
Technical Details: How the Vulnerability Works
While Cisco hasn't released complete technical details to prevent trivial exploitation, security researchers have analyzed the vulnerability enough to understand its general nature.
The Attack Vector
The vulnerability allows unauthenticated remote code execution through Async OS. The specific mechanism isn't fully public, but the attack vector is likely one of the following:
- Network protocol vulnerability: A flaw in how Async OS handles SMTP, HTTP, or other network protocols
- Input validation failure: Improper sanitization of user-supplied input allowing command injection
- Design flaw: A fundamental issue in how Async OS processes email or configurations
- Authentication bypass: A method to achieve authenticated functionality without credentials
Unauthenticated remote code execution vulnerabilities are rarest but most dangerous. An attacker needs no credentials, no special position on the network, and ideally no user interaction. They simply send a crafted request to the vulnerable service, and code execution happens automatically.
Why Root Privileges Matter
Many vulnerabilities grant limited access. Maybe they let you read files as an unprivileged user or crash the service. CVE-2025-20393 grants root privileges, the highest level of system access on Unix/Linux systems.
Root access means:
- No restrictions: Ability to read, write, or delete any file
- No audit: Ability to disable logging and remove evidence
- No limits: Ability to consume unlimited system resources
- Complete control: Ability to modify the operating system itself
- Persistence: Ability to install rootkits that survive restarts
Root privileges essentially mean the attacker owns the system completely.
The Async OS Attack Surface
Async OS is running services that must be network-accessible to function: SMTP for email receiving, HTTP/HTTPS for web management interfaces, and various APIs for integration. Each of these is a potential attack surface.
The vulnerability is likely in one of these exposed services, allowing an attacker to send a specially crafted request that the service processes incorrectly, leading to command execution.
Why Did It Take So Long to Patch?
Cisco disclosed the vulnerability in mid-December but didn't immediately release patches. This gap lasted several weeks, during which time active exploitation continued. Why?
Complexity of the Fix
Async OS powers multiple Cisco product lines with variations in configuration, deployment scenarios, and dependencies. A patch must work across all these variations without breaking existing functionality. Testing a fix across hundreds of different configurations takes time.
Supply Chain Dependencies
Cisco may have dependencies on third-party libraries or components that needed updating. These dependencies may have had their own testing and release cycles.
Enterprise Software Challenges
Cisco's products are mission-critical infrastructure for many organizations. An incorrect patch could disable email systems for thousands of companies. The engineering team must be absolutely certain the fix works before releasing it.
Competing Priorities
Large organizations like Cisco face multiple security issues simultaneously. Engineers and testing resources are finite. Balancing the immediate need to fix a critical zero-day with other development priorities is a real challenge.
Regulatory and Communication Requirements
Cisco must coordinate with government agencies, customers, and security teams before releasing patches. This coordination takes time and involves extensive communication to ensure proper remediation.
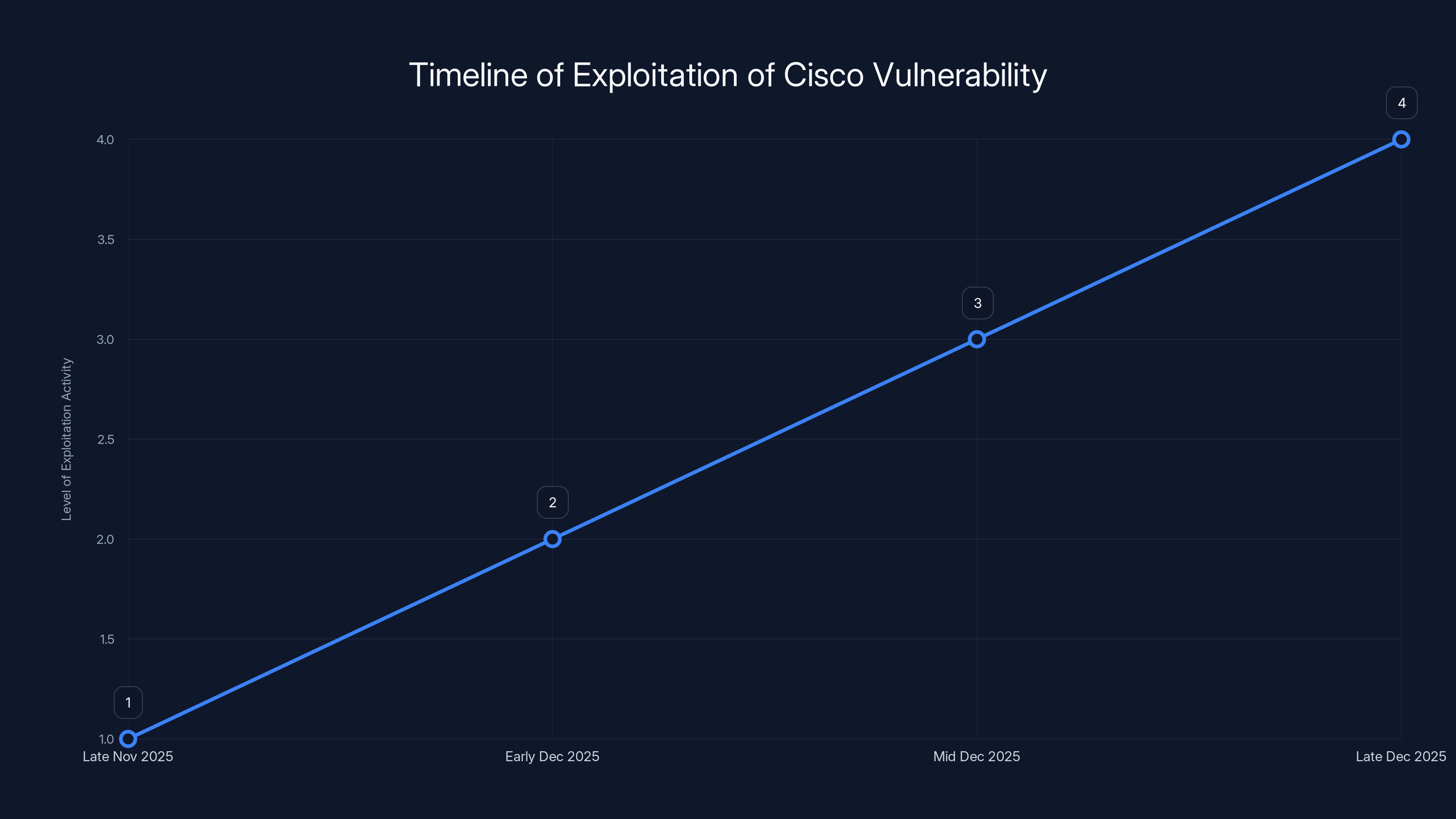
Estimated data shows that Chinese threat actors began exploiting the vulnerability weeks before Cisco's public disclosure, highlighting the need for proactive cybersecurity measures.
Scope of Email Data Exposure
For organizations that were compromised, the implications extend far beyond the technical compromise of a device. Email systems contain organizational secrets.
Types of Information Exposed
- Business communications: Contract negotiations, strategy discussions, financial plans
- Intellectual property: Technical specifications, product roadmaps, research data
- Customer information: Client lists, personal data, account details
- Financial information: Pricing, supplier contracts, payment details
- Personnel matters: Salary information, performance reviews, hiring decisions
- Authentication details: Credentials for internal systems, API keys, access tokens
- Regulatory information: Compliance reports, audit findings, legal correspondence
An email system is essentially a map of everything important happening in an organization.
The Value to Chinese Intelligence
Understanding why Chinese threat actors targeted this vulnerability requires understanding what they gain. Cisco Secure Email Gateway deployments are concentrated at organizations handling valuable intelligence:
- Financial institutions with merger and acquisition information
- Technology companies with product roadmaps and research
- Healthcare organizations with patient data and research
- Government agencies with classified communications
- Defense contractors with weapons system information
For Chinese intelligence services, compromising email gateways at these organizations provides unparalleled access to strategic information.
Attack Kill Chain: From Exploitation to Persistence
Understanding how attackers moved from initial vulnerability exploitation to establishing persistence helps organizations understand what to look for during incident response.
Stage 1: Initial Exploitation
The attacker sends a specially crafted request to the Cisco appliance, triggering the CVE-2025-20393 vulnerability. The appliance executes the attacker's code with root privileges. At this stage, the attacker has execution capability but hasn't established persistence.
Stage 2: System Reconnaissance
Once achieving code execution, the attacker runs commands to gather information about the system: operating system details, running processes, network configuration, connected systems, and installed software. This reconnaissance helps them understand the system architecture and identify how to maintain access.
Stage 3: Persistence Establishment
The attacker deploys persistence mechanisms:
- Creates hidden user accounts with root privileges
- Installs Aquashell backdoor in a hidden directory
- Modifies startup scripts to execute backdoor code
- Installs Aqua Tunnel for reverse SSH access
- Configures Aqua Purge to delete logs showing these changes
- Sets up automatic execution to re-establish access if services restart
Stage 4: Access Optimization
The attacker establishes multiple access vectors:
- Aquashell provides direct command execution
- Aqua Tunnel creates encrypted communication channel
- Chisel provides flexible tunneling for accessing other systems
- Multiple backdoors ensure that losing one doesn't lose access
Stage 5: Post-Compromise Activity
With persistence established, the attacker can now:
- Access email messages through appliance APIs
- Exfiltrate messages of interest
- Monitor ongoing communications
- Establish access to internal systems behind the email gateway
- Create additional backdoors on discovered systems
- Maintain long-term intelligence collection capability
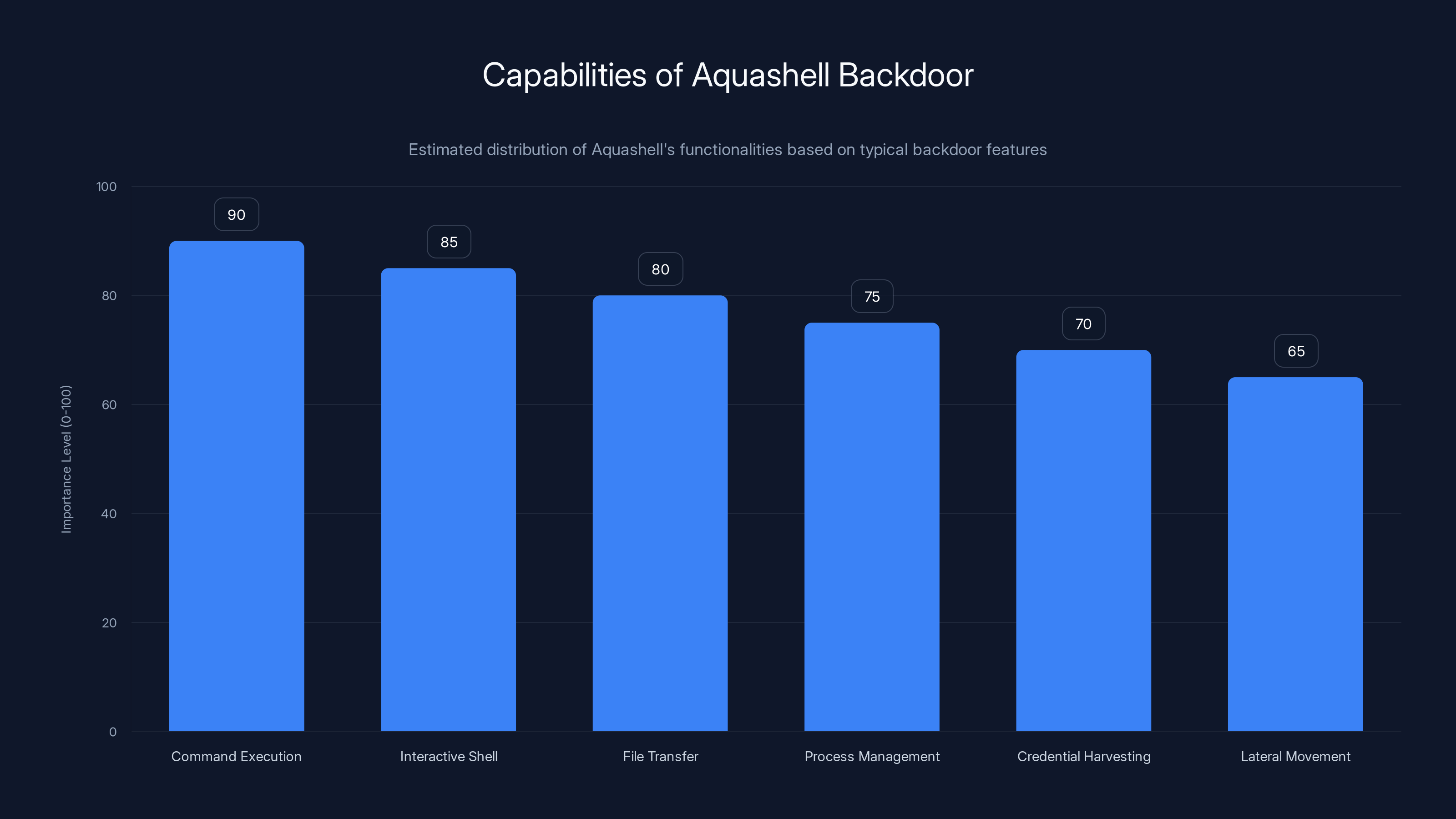
Aquashell's command execution and interactive shell access are its most critical features, highlighting its focus on maintaining control and exfiltrating data. Estimated data based on typical backdoor functionalities.
Cisco's Response and Patch Details
When Cisco finally released patches, they included several important components.
What the Patch Addresses
The primary patch fixes the Async OS vulnerability itself, preventing the initial exploitation vector. Organizations that apply the patch before compromise will be protected from initial exploitation.
Persistence Mechanism Removal
Cisco recognized that simply patching the vulnerability wasn't sufficient. Organizations that had already been compromised still had attackers inside through installed backdoors. The patch includes additional functionality to detect and remove common persistence mechanisms:
- Scanning for unauthorized user accounts
- Checking for suspicious startup scripts
- Identifying known backdoor files
- Removing known persistence mechanisms
Implementation Challenges
Applying patches to critical infrastructure appliances presents challenges:
- Downtime requirements: Patches often require system restarts
- Testing needs: Organizations must test patches in lab environments first
- Update windows: Large organizations schedule patches during maintenance windows
- Rollback plans: In case a patch causes problems, rollback procedures must be prepared
These realities mean that even after patches are released, significant time lapses before all vulnerable systems are patched.

Indicators of Compromise: How to Detect Attacks
Organizations that suspect they may have been compromised can look for specific indicators of compromise (IOCs) and suspicious behaviors.
File System Indicators
- Unusual Python scripts in unexpected directories
- Hidden files or directories (names starting with dots)
- Suspicious startup scripts modified recently
- Unexpected user accounts with root privileges
- Log files with recent modifications or deletions
Process Indicators
- Python processes running with unusual command lines
- SSH processes with suspicious parent processes
- Processes listening on unexpected ports
- High network activity from the appliance
- Processes consuming unusual amounts of resources
Network Indicators
- Outbound connections to suspicious IP addresses
- Reverse SSH connections initiated from the appliance
- Unusual DNS queries to external domains
- High-volume data transfers to external systems
- Connections to known command and control servers
Log Indicators
- Missing or deleted logs covering specific time periods
- Unexplained gaps in audit logs
- Failed login attempts followed by successful unusual access
- Suspicious commands in system logs
- Evidence of log file modifications
Remediation Steps: What Organizations Should Do Now
For organizations operating Cisco Secure Email products, immediate action is necessary.
Immediate Actions (Within 24 Hours)
- Determine if you're affected: Check your inventory of Cisco products to identify Secure Email Gateway or Secure Email and Web Manager instances
- Check current versions: Compare installed versions against Cisco's advisory to see if your systems are vulnerable
- Enable enhanced logging: Increase logging verbosity to capture comprehensive evidence if attacks occur
- Review access controls: Verify that only authorized administrators can access email appliances
- Segment the network: Ensure email appliances aren't directly accessible from untrusted networks
Short-Term Actions (1-2 Weeks)
- Develop a patch plan: Create a schedule for applying patches, prioritizing critical systems
- Test patches in lab: Before production deployment, validate patches don't break existing functionality
- Prepare rollback procedures: Document how to revert patches if problems occur
- Schedule maintenance windows: Coordinate patch deployment with business requirements
- Notify stakeholders: Inform business leaders about the vulnerability and remediation plan
Medium-Term Actions (2-4 Weeks)
- Deploy patches: Begin production deployment according to your schedule
- Verify patch installation: Confirm patches were applied successfully
- Test functionality: Verify that email flow and security features work correctly after patching
- Monitor systems closely: Watch for any unusual behavior indicating problems with patches
Post-Patch Actions (4+ Weeks)
- Conduct forensic investigation: If you suspect compromise, engage incident response team
- Review email logs: Look for evidence of unauthorized access or data exfiltration
- Monitor for persistence: Watch for indicators of compromised systems trying to re-establish access
- Notify affected parties: If you discover compromise, notify affected users and regulatory bodies as required
- Implement additional security: Consider additional monitoring, segmentation, or authentication controls

Broader Security Implications
CVE-2025-20393 highlights several troubling trends in cybersecurity.
The Vulnerability Disclosure Gap
The gap between vulnerability discovery by attackers and public disclosure by vendors creates windows where organizations are unknowingly vulnerable. This CVE-2025-20393 timeline is not unique. Months-long gaps between initial exploitation and patch availability are becoming common with critical infrastructure vulnerabilities.
Nation-State Targeting of Email Infrastructure
Email systems are increasingly targeted by nation-states because they're windows into organizational intelligence. Unlike financially-motivated cybercriminals who want quick paydays, nation-states are playing a longer game. They're willing to maintain access for months or years to gradually exfiltrate valuable information.
The Sophistication of Chinese Operations
The tooling deployed (Aquashell, Aqua Tunnel, Aqua Purge) suggests significant engineering resources and deep knowledge of target systems. This isn't script-kiddie level activity. This is sophisticated, well-resourced espionage operations.
The Persistence Challenge
Even after patching the initial vulnerability, removing persistence mechanisms installed by sophisticated attackers is challenging. Organizations must assume that if they were compromised, cleaning the system completely requires comprehensive investigation and potentially rebuilding affected systems from scratch.
Lessons for Critical Infrastructure
CVE-2025-20393 provides important lessons for organizations protecting critical systems.
Assume Breach Mentality
Assuming you've been breached and planning accordingly changes how you architect security. If attackers are in your email system, what can you do to detect them, contain them, and minimize damage?
Network Segmentation
Critical infrastructure should be segmented so that compromising one system doesn't give attackers direct access to everything. An email gateway compromise shouldn't immediately compromise internal databases or development systems.
Enhanced Monitoring
Detecting sophisticated attackers requires more than basic log monitoring. Behavioral analytics, anomaly detection, and threat hunting capabilities help identify attackers who are deliberately hiding their presence.
Incident Response Readiness
Organizations should assume they'll eventually face compromises and should pre-plan incident response procedures. When an incident occurs, clear procedures, trained team members, and prepared tools significantly reduce damage.
Threat Intelligence Sharing
Organizations discovering compromises should share information with peers and security agencies. The more organizations know about current attack tactics and tools, the better they can defend against them.
Industry Response and Future Outlook
The cybersecurity community is still analyzing the full impact of CVE-2025-20393 and what it means for future vulnerabilities.
Increased Focus on Email Security
Email gateway vulnerabilities are now receiving elevated attention from security researchers. The success of CVE-2025-20393 exploitation will likely attract more research effort toward finding similar vulnerabilities in other vendors' products.
Regulatory Pressure
Government agencies and regulators are likely to increase requirements for vulnerability disclosure timelines, forced patching procedures, and incident notification. The gap between Cisco's initial awareness and patch availability may trigger regulatory scrutiny.
Vendor Accountability
Organizations are questioning why Cisco didn't have patches available immediately upon public disclosure. This pressure may force vendors to pre-develop patches before public disclosure, reducing the vulnerability window.
Defense Advancements
Security vendors are developing detection capabilities specifically for Aquashell and related backdoors. Antivirus and endpoint detection and response tools are being updated with signatures and behavioral detections.
Critical Infrastructure Vulnerability Management
CVE-2025-20393 raises broader questions about how critical infrastructure vulnerabilities are managed.
Zero-Day Ecosystems
Zero-day vulnerabilities represent the ultimate currency in cybersecurity. They're sold, traded, and hoarded by various actors. When multiple nation-states have the same zero-day, it suggests either independent discovery or someone in a position to distribute knowledge to allies.
Supply Chain Intelligence
The rapid exploitation of CVE-2025-20393 suggests attackers may have intelligence about Cisco's vulnerability discovery or testing processes. Supply chain security extends not just to code and components but to knowledge and timing.
The Vulnerability Lifecycle
The complete lifecycle from discovery to patching to deployment can take many months. During all these stages, vulnerabilities remain exploitable. The challenge for organizations is getting ahead of attackers in this timeline.

Best Practices for Email Security
Beyond patching CVE-2025-20393, organizations should implement comprehensive email security practices.
Defense in Depth
Don't rely solely on the email gateway. Layer multiple security controls:
- Network segmentation: Isolate email systems from critical infrastructure
- Authentication: Implement multi-factor authentication for admin access
- Encryption: Encrypt email in transit and at rest
- Monitoring: Comprehensive logging and alerting on unusual activity
- Backup and recovery: Maintain independent backups of email data
Access Control
Limit who can access email systems:
- Principle of least privilege: Users and services get minimum necessary access
- Just-in-time access: Temporary elevated access that expires
- Activity logging: Every administrative action is logged and reviewed
- Separation of duties: No single person has complete control
Threat Hunting
Don't wait for attacks to find you:
- Proactive searching: Hunt for indicators of compromise even if no alerts trigger
- Threat intelligence: Know what current attackers are doing and look for similar activity
- Red teaming: Periodically test your defenses as attackers would
- Analysis of anomalies: Investigate unusual behaviors even if they don't match known attack patterns
FAQ
What exactly is CVE-2025-20393 and why is it so dangerous?
CVE-2025-20393 is a remote code execution vulnerability in Cisco Async OS with a perfect 10/10 severity score. It allows unauthenticated attackers to execute arbitrary commands with root privileges on Cisco Secure Email Gateway and Secure Email and Web Manager appliances. Root access means complete system compromise including the ability to read all email, install backdoors, and pivot to other network systems. The danger is compounded by the fact that it affects critical email infrastructure that many organizations depend on, and it was actively exploited for weeks before patches were available.
How long were systems vulnerable to active exploitation before patches were available?
Chinese threat actors were exploiting CVE-2025-20393 since at least late November 2025, while Cisco didn't release patches until late December 2025. This represents approximately 4-6 weeks of active exploitation before patches were available. During this entire period, organizations had no way to protect their systems if they were unaware of the vulnerability. Even after Cisco's initial disclosure in mid-December, the patch gap lasted several additional weeks, creating a dangerous window for exploitation.
What persistence mechanisms did attackers install, and how can organizations detect them?
Attackers deployed multiple tools for maintaining persistent access: Aquashell (Python-based backdoor), Aqua Tunnel (reverse SSH tunnel), Chisel (multi-protocol tunneling), and Aqua Purge (log clearing utility). Organizations can detect these by monitoring for unusual Python processes, unexpected user accounts with root privileges, suspicious startup scripts, outbound connections to suspicious IP addresses, and unexplained gaps in system logs. Cisco's patches include detection and removal capabilities for these known persistence mechanisms, but comprehensive investigation may be necessary if compromise is suspected.
Should my organization apply the patch immediately, or can it wait for the next maintenance window?
This should be treated as an emergency requiring immediate patching, not a standard maintenance cycle patch. The vulnerability carries maximum severity, was actively exploited for weeks, and affects critical email infrastructure. That said, patching must be done carefully: test patches in lab environments first, prepare rollback plans in case patches cause problems, and schedule maintenance windows that minimize email service disruption. But the goal should be patching within days, not weeks or months.
How can organizations determine if they were compromised by this vulnerability?
Organizations should conduct forensic investigation looking for indicators of compromise: unusual user accounts, suspicious Python scripts, modified startup scripts, evidence of log deletion, outbound connections to known attacker IP addresses, and performance anomalies. Security logs covering the period from late November onward should be reviewed. If log deletion is suspected, examine filesystem timestamps for evidence of tampering. Engaging professional incident response teams experienced with email system forensics is recommended if compromise is suspected.
What should organizations do if they discover they were compromised through CVE-2025-20393?
If compromise is discovered, organizations should immediately: 1) Isolate the affected appliance from the network if possible, 2) Preserve all logs and evidence for forensic investigation, 3) Engage incident response professionals, 4) Scan all email messages and attachments for signs of attacker activity, 5) Change all credentials for systems the email appliance could access, 6) Notify affected users of potential email compromise, 7) Notify regulatory bodies and legal counsel about notification obligations, 8) Conduct comprehensive investigation to determine scope of data accessed, and 9) Implement additional monitoring to detect if attackers re-establish access.
Are other Cisco products vulnerable, or just the Secure Email products mentioned?
Cisco's advisory specifies Secure Email Gateway (SEG) and Secure Email and Web Manager (SEWM) appliances. However, these vulnerabilities in Async OS are specific to these products. Other Cisco products may have different vulnerabilities, but this specific CVE-2025-20393 issue is limited to Async OS-based email security appliances. Organizations running other Cisco products should still maintain patching discipline but aren't at risk from this specific vulnerability.
How can organizations reduce their risk from similar vulnerabilities in the future?
Organizations should implement several practices: 1) Maintain inventory of all security appliances and products, 2) Subscribe to vendor security advisories for immediate notification of new vulnerabilities, 3) Implement network segmentation so email appliance compromise doesn't compromise entire network, 4) Establish rapid patching procedures for critical infrastructure with testing and rollback plans, 5) Implement enhanced monitoring and threat hunting capabilities, 6) Conduct regular security assessments and penetration testing, 7) Establish incident response procedures before incidents occur, and 8) Participate in threat intelligence sharing to learn about attacks before they affect your organization.
Why did it take weeks for Cisco to release patches after disclosure?
Patching critical infrastructure appliances requires extensive testing across multiple configurations, versions, and deployment scenarios. A faulty patch could break email systems for thousands of companies, making rigorous testing essential. Cisco must also coordinate with customers, government agencies, and security teams before release. Supply chain dependencies, engineering resource constraints, and the need to ensure patches work across the entire product ecosystem contribute to the timeline. However, the gap between disclosure and patch availability is concerning and may trigger future regulatory requirements for faster patch timelines.

Conclusion: The Ongoing Battle Against State-Sponsored Threats
CVE-2025-20393 represents a watershed moment for email security. The vulnerability's maximum severity rating, weeks-long exploitation window, and deployment of sophisticated persistence mechanisms highlight how targeted nation-states can be when pursuing organizational intelligence.
What makes this vulnerability particularly concerning is not the technical nature of the flaw itself, but the broader implications it reveals about cybersecurity's current state. Critical infrastructure remains vulnerable for weeks or months between initial exploitation and public remediation. Nation-states have the resources and sophistication to develop purpose-built tools like Aquashell that are specifically engineered for target environments. Organizations deploying critical security products must assume that if they're targeted by sophisticated adversaries, they'll eventually be compromised.
The organizations that moved fastest to apply patches, conduct forensic investigations, and implement additional monitoring are the ones who will minimize damage. Those that delayed patching or failed to investigate potential compromises face much greater risk.
Cisco's eventual release of patches that detect and remove persistence mechanisms represents good security engineering, but it also acknowledges a troubling reality: patches often arrive too late to prevent initial compromise. The best defense isn't waiting for vendors to fix vulnerabilities; it's assuming compromise will happen and architecting systems accordingly.
For IT teams responsible for email systems, CVE-2025-20393 should be an urgent wake-up call. Email gateways aren't just important components; they're windows into organizational intelligence. If attackers are inside your email system, they have visibility into everything that matters to your organization.
The immediate action items are clear: patch affected systems as quickly as possible, investigate potential compromises, and implement additional monitoring and segmentation. Longer-term, organizations need to rethink how they approach critical infrastructure security. Nation-state threat actors aren't going away. The question is whether organizations will continue to be reactive (patching after exploitation and compromise) or become proactive (implementing defenses that work even when systems are compromised).
The choice, ultimately, belongs to each organization. But the clock is ticking, and every day without patches or investigation is another day potential attackers remain inside systems with complete access to organizational intelligence.
Use Case: Automate security incident reporting and documentation when vulnerabilities like CVE-2025-20393 are discovered in your infrastructure.
Try Runable For FreeKey Takeaways
- CVE-2025-20393 carries a perfect 10/10 severity score and allows unauthenticated remote code execution with root privileges on Cisco email appliances
- Chinese threat actors exploited this vulnerability for 4-6 weeks starting in late November 2025 before patches were available, deploying Aquashell backdoors and persistence mechanisms
- Email gateways are high-value targets for nation-state espionage because they provide complete visibility into organizational communications
- Organizations must patch immediately, conduct forensic investigations to detect compromise, and implement layered security controls beyond single vulnerability patches
- The broader implication is that critical infrastructure remains vulnerable during extended windows between exploitation and patch availability, requiring organizations to assume breach and architect defenses accordingly
Related Articles
- N8n Ni8mare Vulnerability: What 60,000 Exposed Instances Need to Know [2025]
- X Platform Outage January 2025: Complete Breakdown [2025]
- WordPress Plugin Security Flaw: Complete Guide to Staying Safe [2025]
- Major Shipping Platform Exposed Customer Data, Passwords: What Happened [2025]
- VoidLink: The Chinese Linux Malware That Has Experts Deeply Concerned [2025]
- VoidLink: The Advanced Linux Malware Reshaping Cloud Security [2025]
![Cisco CVE-2025-20393 Critical Vulnerability Finally Patched [2025]](https://tryrunable.com/blog/cisco-cve-2025-20393-critical-vulnerability-finally-patched-/image-1-1768581494714.jpg)



