Massiv Android Malware: How Fake IPTV Apps Steal Banking Data [2025]
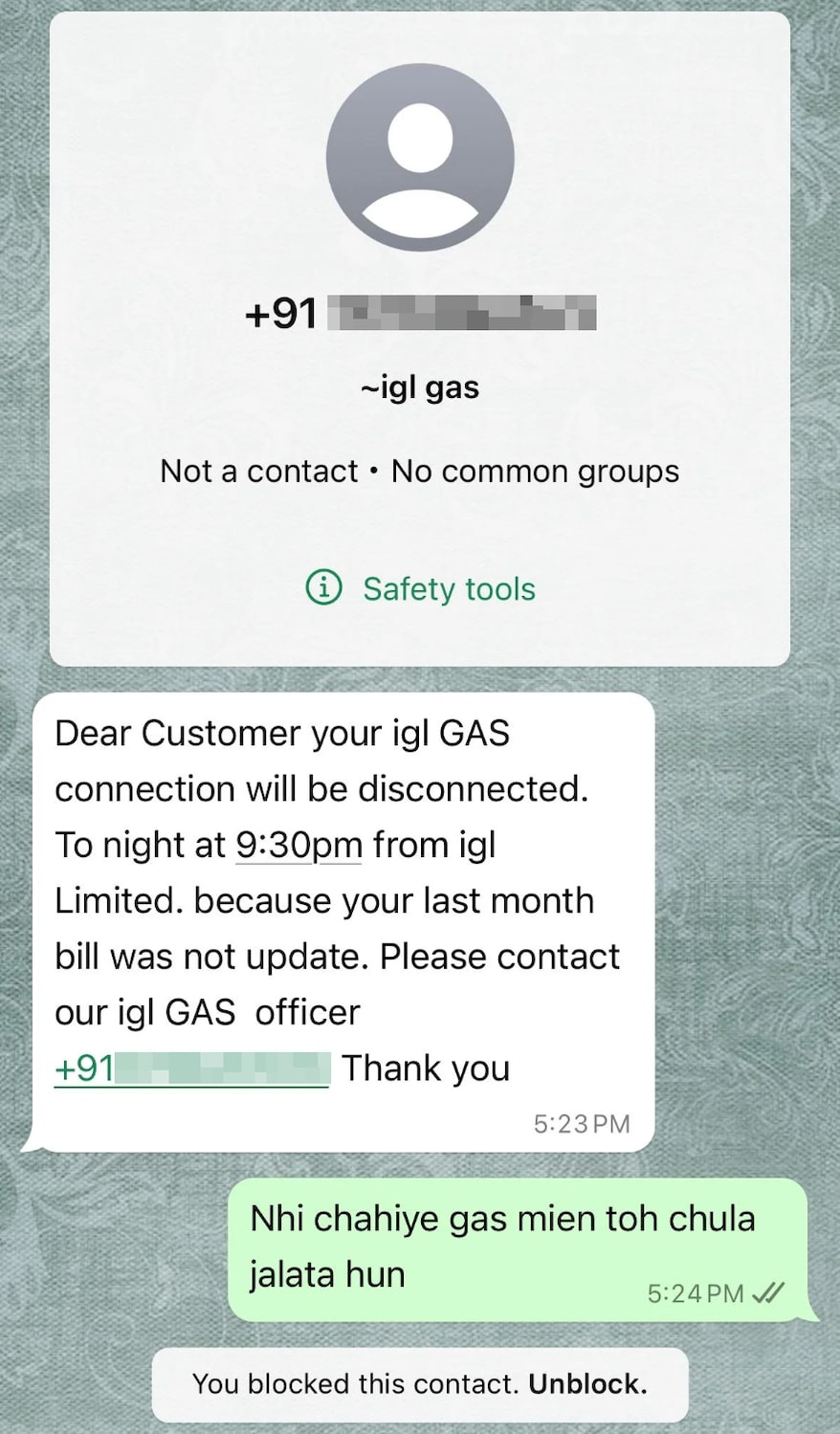
You're scrolling through your favorite streaming app store, looking for a decent IPTV application to watch some shows. You find one that looks legit, has decent reviews, and downloads quickly. What you don't know is that you've just invited a sophisticated banking trojan into your phone—and it's about to drain your bank account in ways you never thought possible.
This isn't some hypothetical scenario. It's exactly what's happening right now to thousands of Portuguese users who've downloaded an app called Massiv. Security researchers at Threat Fabric recently exposed this malware campaign, and what they found is genuinely disturbing. We're talking about a banking trojan that doesn't just steal your credentials and move on. It's smart enough to create fake bank accounts in your name, apply for loans you never requested, and launder money through your identity while you sleep.
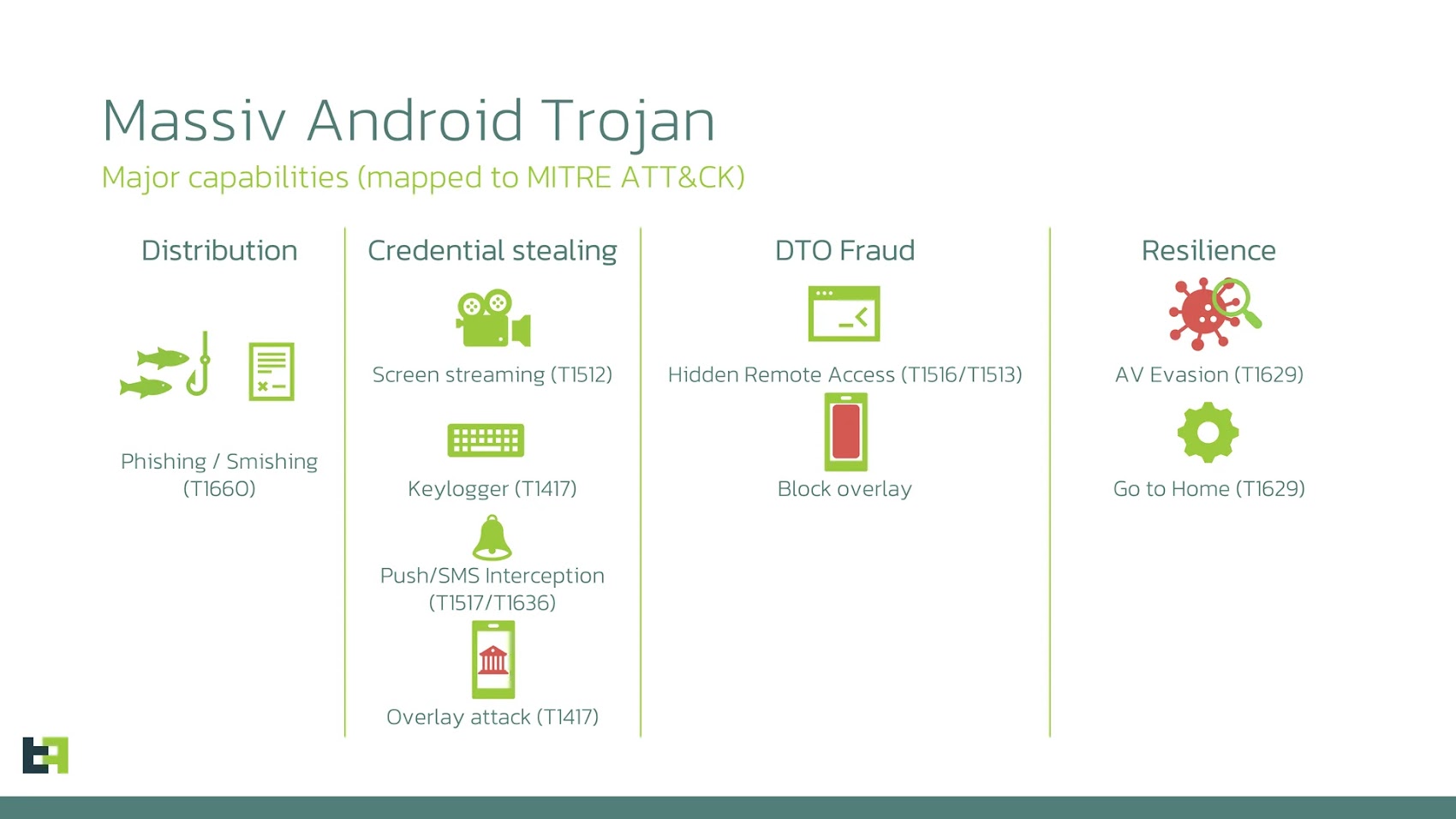
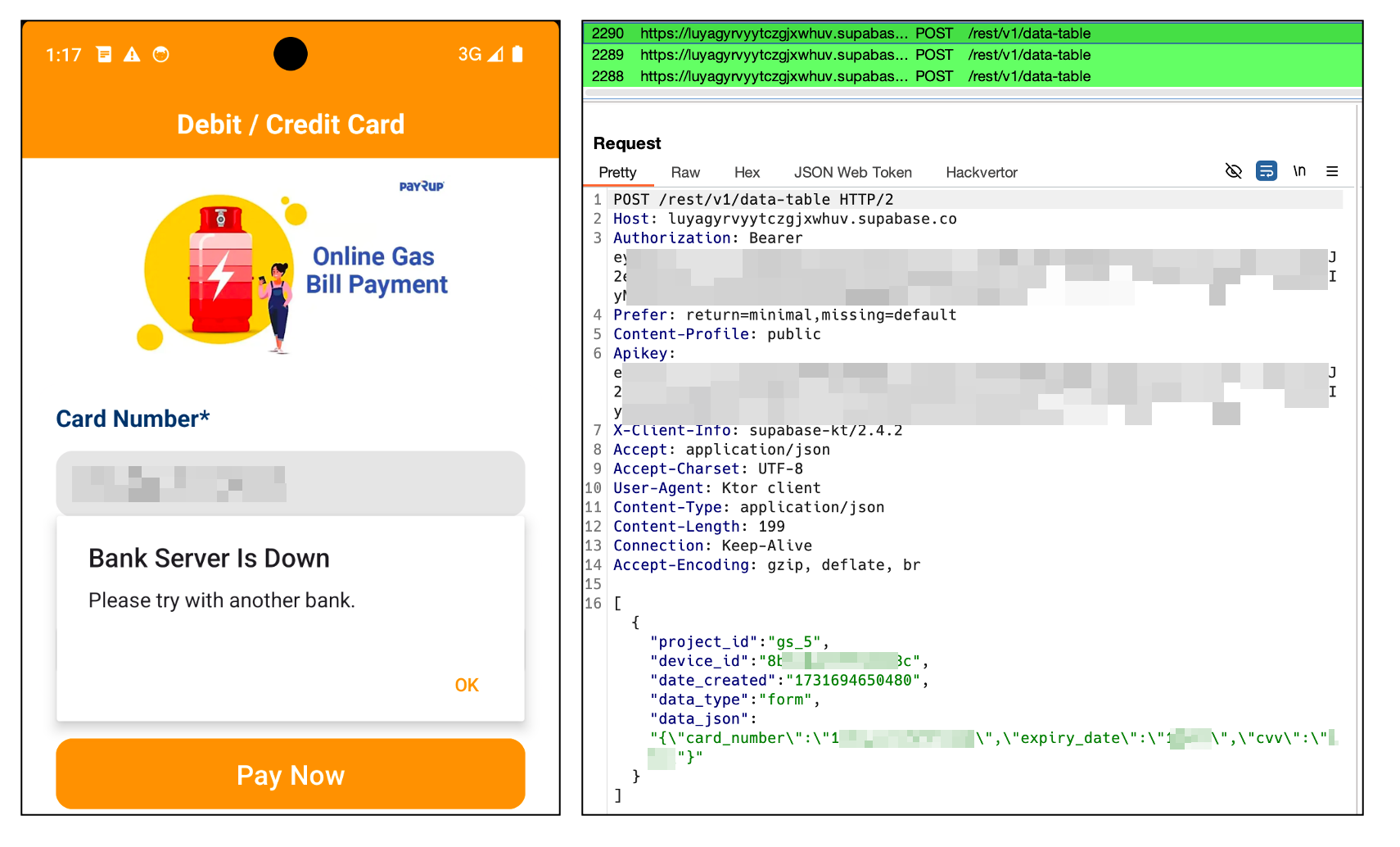
The thing that makes Massiv different from typical Android banking malware is its sophistication. It doesn't rely on simple phishing tactics or basic credential theft. Instead, it uses screen overlays, keylogging, accessibility service abuse, and advanced data extraction techniques to completely compromise your financial security. And because it's disguised as a legitimate IPTV app, most people never see it coming.
In this deep dive, we're breaking down exactly how Massiv works, why IPTV apps have become the malware delivery mechanism of choice, and most importantly, how you can protect yourself from falling victim to this or similar attacks. We'll also explore the broader trend of fake apps targeting specific countries, the financial devastation they cause, and what security experts recommend you do right now.
TL; DR
- Massiv is a sophisticated banking trojan disguised as a legitimate IPTV streaming application targeting Portuguese users
- The malware steals banking credentials using screen overlays, keylogging, and abuse of Android's Accessibility Service
- Attackers create fraudulent bank accounts in victims' names, apply for loans, and conduct money laundering operations
- IPTV apps are increasingly used as malware delivery vectors because they're not available on official app stores, forcing users to install from untrusted sources
- The threat uses advanced evasion techniques that bypass standard security protections built into banking applications
- Victims face financial devastation including debt from unauthorized loans and accounts they never opened

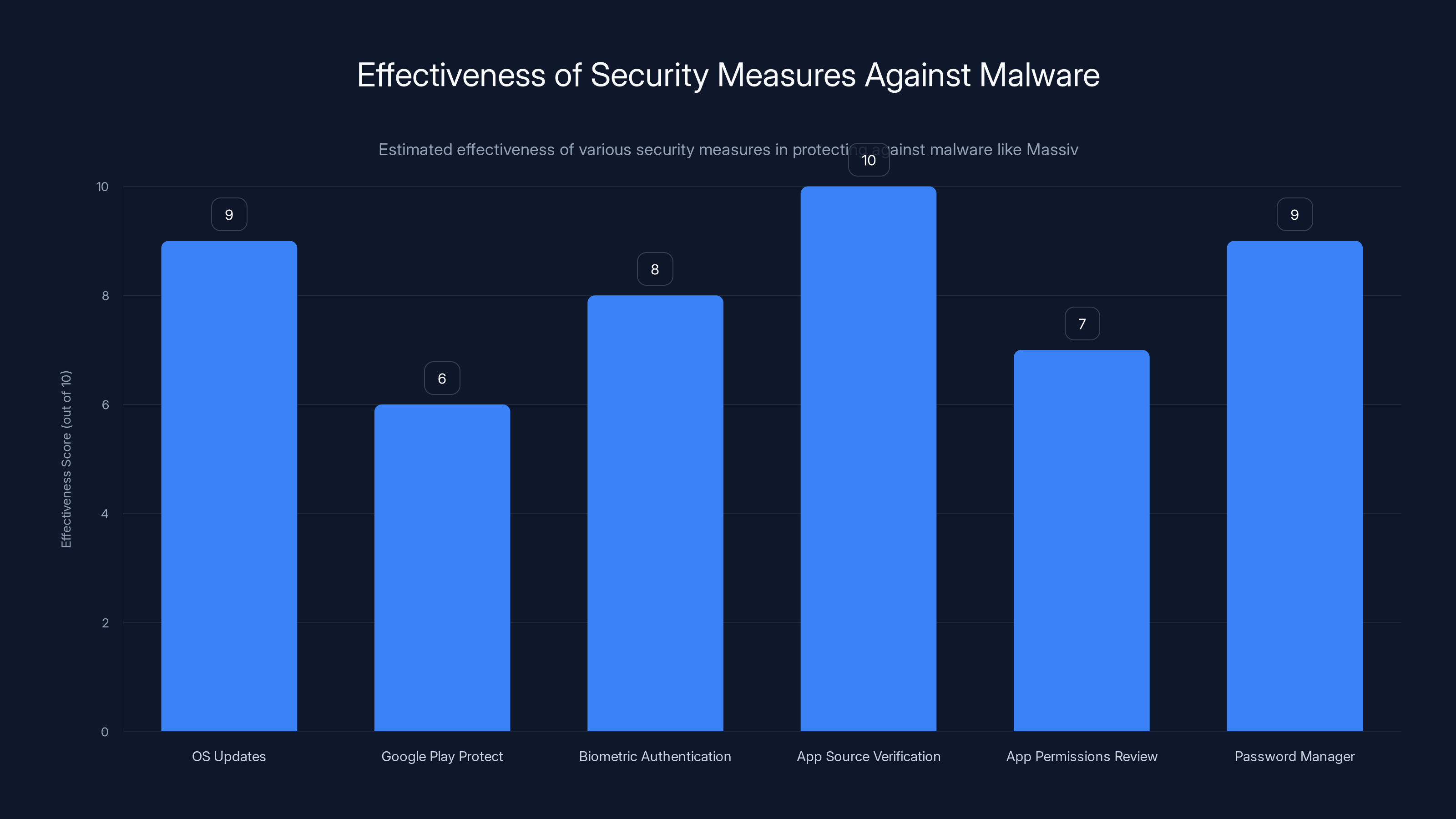
OS updates and app source verification are the most effective security measures against malware like Massiv. Estimated data.
Understanding the Massiv Banking Trojan Attack
When Threat Fabric security researchers first identified Massiv, they were shocked by how thoroughly it had been engineered. This isn't some script-kiddie's weekend project. This is a professional-grade banking trojan that combines multiple attack vectors into a single, devastating package.
Here's what happens when you install Massiv thinking you're getting a legitimate IPTV application. The app itself might actually work as advertised for the first few days. You can watch some streaming content, browse channels, and think everything is normal. But in the background, Massiv is working overtime to compromise your device and steal everything valuable.
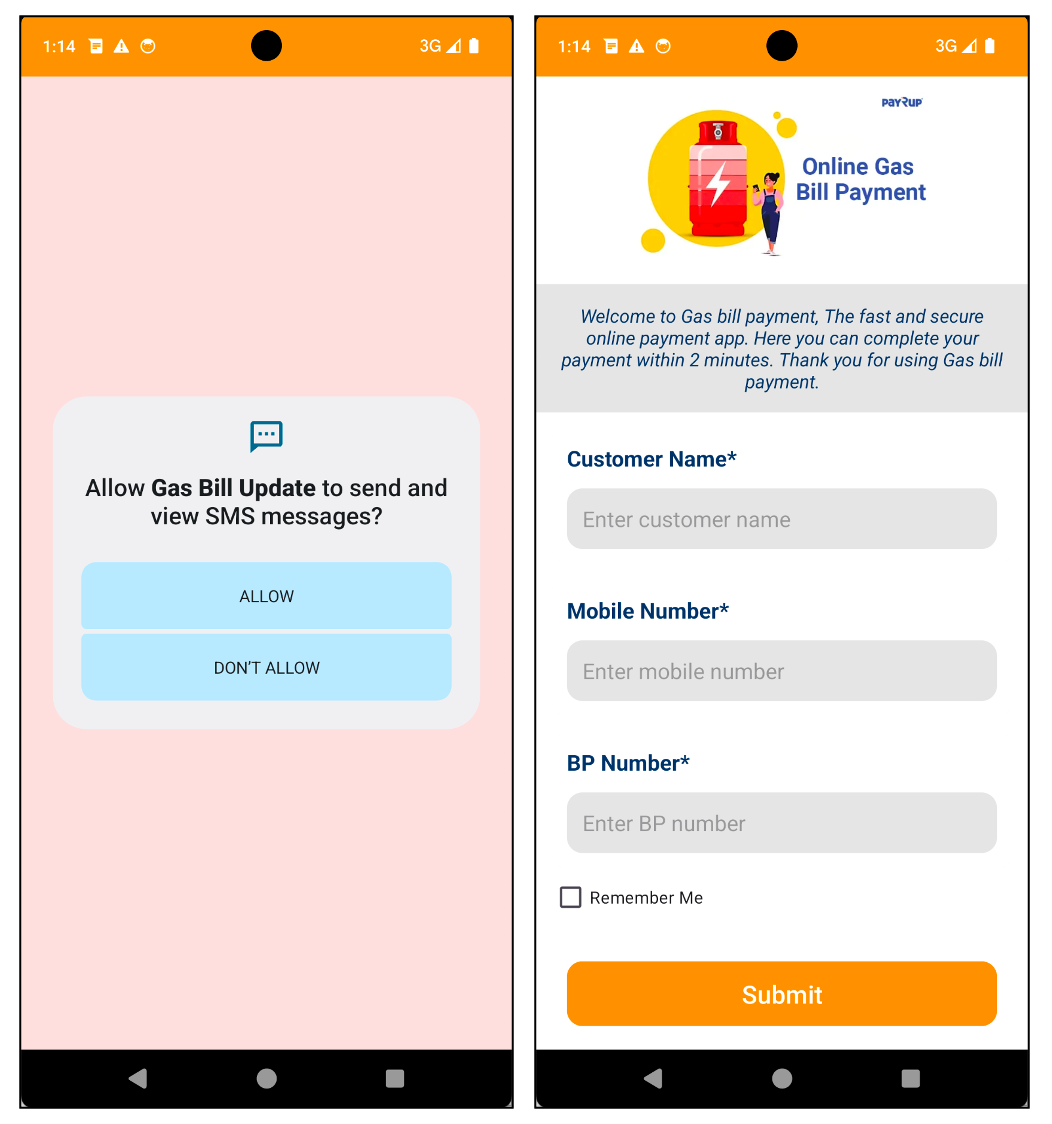
The malware requests access to Android's Accessibility Service, which is a legitimate feature designed to help people with disabilities navigate their phones. But in Massiv's hands, it becomes a surveillance tool. Once granted, the Accessibility Service access gives the malware the ability to see everything happening on your screen, capture every keystroke, and understand the structure of every app interface you interact with.
This is where things get scary. The malware can see your online banking interface, understand where the password field is, capture your keystrokes as you type, and even understand what buttons you're pressing and in what order. Traditional banking security relies on protecting the screen from being captured, but Massiv doesn't need to capture your screen. It just needs to know what's being displayed and what you're interacting with.
How Screen Overlays Enable Modern Banking Fraud
Screen overlays are one of the oldest tricks in the mobile malware playbook, but they've been refined to an art form by modern attackers. Massiv uses overlays to display fake login screens that look identical to your actual banking app. When you're about to log into your bank, the overlay activates and you see a screen that's completely indistinguishable from the real thing.
You enter your credentials thinking you're logging into your bank. The fake overlay captures your username and password. Then, after a slight delay, it closes and you see the real banking app login screen. You might think it was just a momentary glitch, enter your credentials again, and successfully log in. You have no idea you've already given your credentials to the attackers.
The sophistication here is that the overlay doesn't just appear randomly. Massiv watches what you're doing on your screen. When it detects that you're launching your banking app, it activates the overlay at exactly the right moment. This is possible because of the Accessibility Service access we mentioned earlier. The malware knows the exact state of your device and can predict your actions.
Keylogging and Real-Time Data Extraction
Beyond screen overlays, Massiv also uses traditional keylogging to capture everything you type. This is particularly dangerous when combined with the Accessibility Service, which can see what fields are being filled and understand the context of every keystroke.
So when you're entering your banking credentials, Massiv doesn't just capture the keys you pressed. It understands that you pressed keys in the password field of your banking app, on a specific date, at a specific time, on a specific banking platform. This contextual information allows attackers to immediately know which credentials they've captured and on which account.
The real-time data extraction capability means that Massiv isn't just recording information for later analysis. It's sending the stolen data to attacker-controlled servers in real-time, giving the criminals immediate access to your credentials so they can start their attack before you even realize something is wrong.

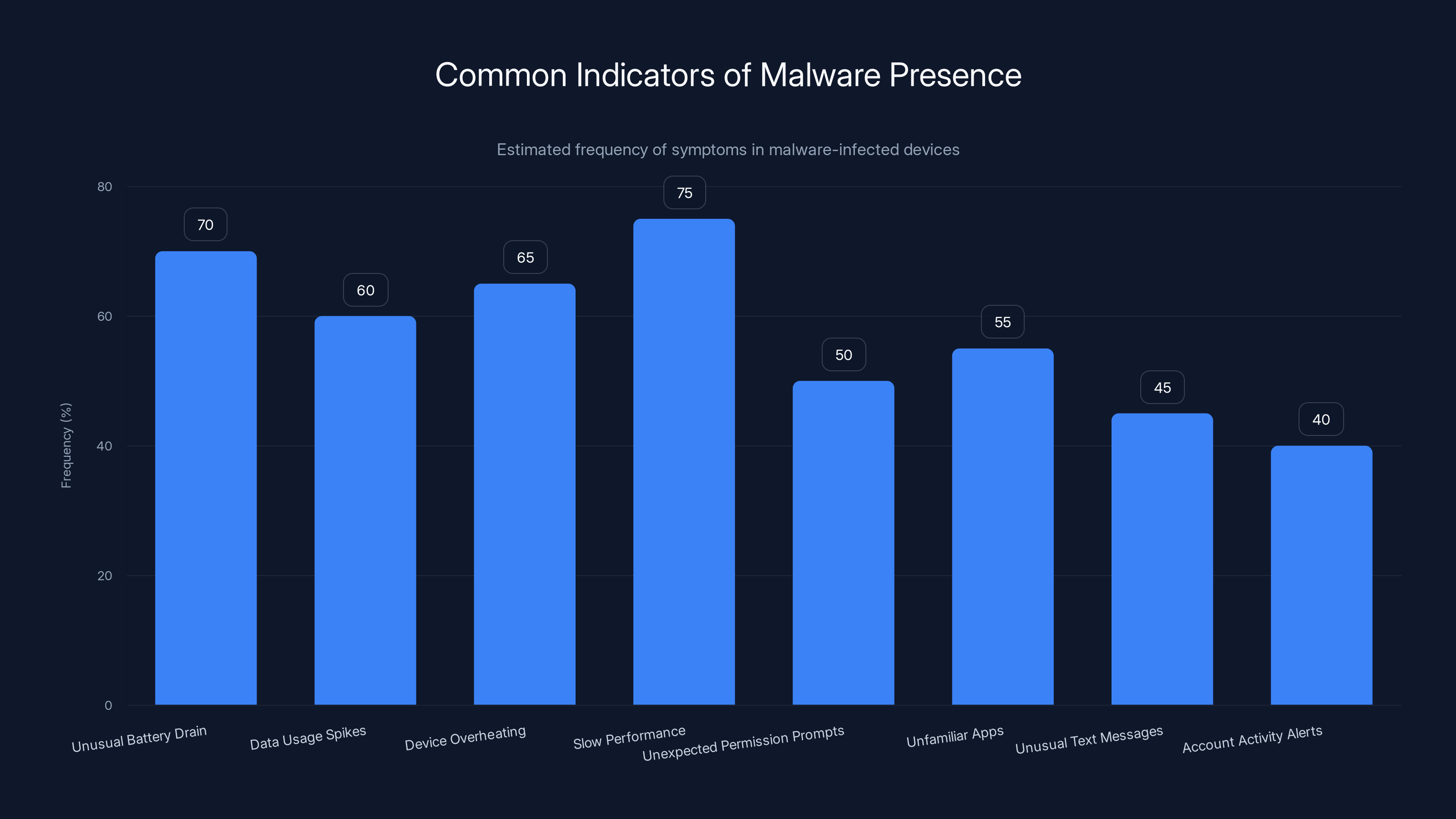
This chart estimates the frequency of common indicators of malware presence in devices. Slow performance and unusual battery drain are the most frequently observed symptoms. Estimated data.
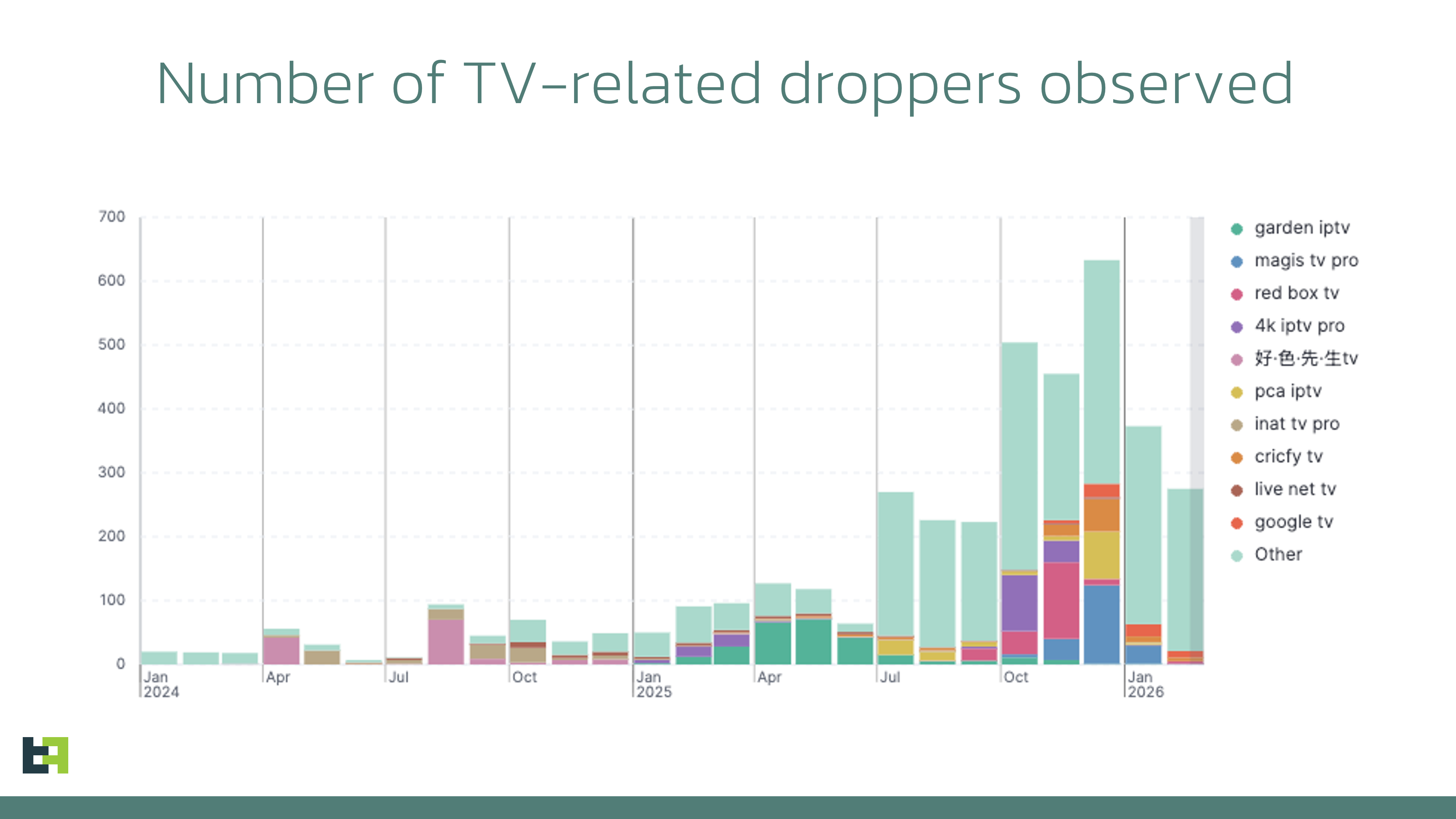
The IPTV App Delivery Method: Why Crooks Love It
You might wonder why attackers chose to disguise Massiv as an IPTV application. The answer reveals something important about the mobile app ecosystem and how it's exploited by criminals.
IPTV apps, which stand for Internet Protocol Television, are technically illegal in most countries because they typically provide access to copyrighted content without payment. This means they can't be distributed through Google Play Store, Apple's App Store, or any official app store. Anyone wanting an IPTV app has to download it from unofficial sources, third-party websites, or community forums.
This is exactly where attackers want you. When you're downloading from unofficial sources, you're already accepting some level of risk. The ecosystem is wild, unregulated, and perfect for hiding malware. There's no app review process, no security scanning, no verification of app integrity. You download an APK file, install it, and hope for the best.
IPTV apps are particularly attractive as delivery vectors for another reason: they actually work. Massiv isn't just a malware wrapper with no functionality. It provides real IPTV streaming capabilities, so users don't immediately suspect something is wrong. In fact, the app functioning correctly makes users more likely to keep it installed, give it permission requests, and trust it with sensitive data.
The psychological aspect is important too. People know that IPTV apps are technically illegal, so they're less likely to report them to authorities or app stores. If your pirated streaming app starts acting weird, are you really going to contact your bank or file a police report? Criminals are counting on this shame factor to keep their victims silent.
Why Official App Stores Fail to Protect Users
You might think: "Well, I only download apps from Google Play Store, so I'm safe." Unfortunately, that's not entirely true. While Google does scan apps for malware before they're approved, the scanning process isn't perfect. Attackers are constantly developing new obfuscation techniques that evade detection.
Moreover, for apps that are explicitly against store policies (like IPTV apps), there's no option to download from official channels at all. Users are forced to choose between not having the app or taking the risk of unofficial sources. Most people choose the risk.
Google has been cracking down on malware in recent years, but they're facing an increasingly sophisticated enemy. New variants of banking trojans are appearing constantly, and by the time a malware variant is identified and added to detection signatures, new variants have already been deployed.
How Attackers Use Stolen Credentials: The Money Laundering Angle
Now we get to the part that's truly devastating for victims. Stealing credentials is just the first step in Massiv's attack chain. What happens next is where the real financial damage occurs.
Once attackers have your banking credentials, they don't immediately try to drain your account. That would be too obvious and would trigger fraud alerts. Instead, they use your credentials to do something far more insidious: they create entirely new bank accounts in your name.
Think about that for a moment. The attackers now have access to your personal information (name, address, identification documents), your banking credentials, and access to your phone. They use this combination to apply for bank accounts at institutions you've never heard of, financial services you've never used, and credit lines you never approved.
Because they have your credentials and can intercept your SMS messages (some advanced variants of banking trojans can), they can complete the verification process without you knowing. The new accounts are set up and ready to go, and the only person who knows about them is the attacker.
The Loan Application Nightmare
Here's where it gets worse. Attackers use these fake accounts as a stepping stone to apply for loans. They take out loans in your name, using the fake accounts as the application point. Since these loans are theoretically in your name, and since modern loan applications are increasingly done online without in-person verification, the loans get approved.
The attacker receives the loan money, transfers it to money mules (people who receive stolen funds and transfer them to the criminals for a cut), and then disappears. You're left holding the bag, literally in debt for loans you never applied for, never approved, and never received the money from.
Imagine the shock of discovering that you now owe €50,000 to a bank you've never heard of for a loan you never requested. Your credit score is destroyed. You can't get a mortgage, a car loan, or a business loan. You might even face legal action from the banks for defaulting on payments.
Money Laundering and Fraud Account Networks
Beyond loans, attackers use the fake accounts as part of larger money laundering networks. Criminal organizations receive money from various illegal activities (drug trafficking, stolen credit cards, ransomware payments, etc.). They need to launder this money, make it seem like it came from legitimate sources.
By having multiple accounts in victims' names, they can move money through these accounts, mixing it with legitimate transactions, and gradually moving it to accounts they control. From the outside, it looks like normal banking activity. An account holder is receiving deposits, making transfers, receiving income. But in reality, it's all dirty money flowing through your name.
Victims often don't discover this fraud for weeks or months, by which time millions of euros have flowed through their accounts, and their financial reputation is destroyed.
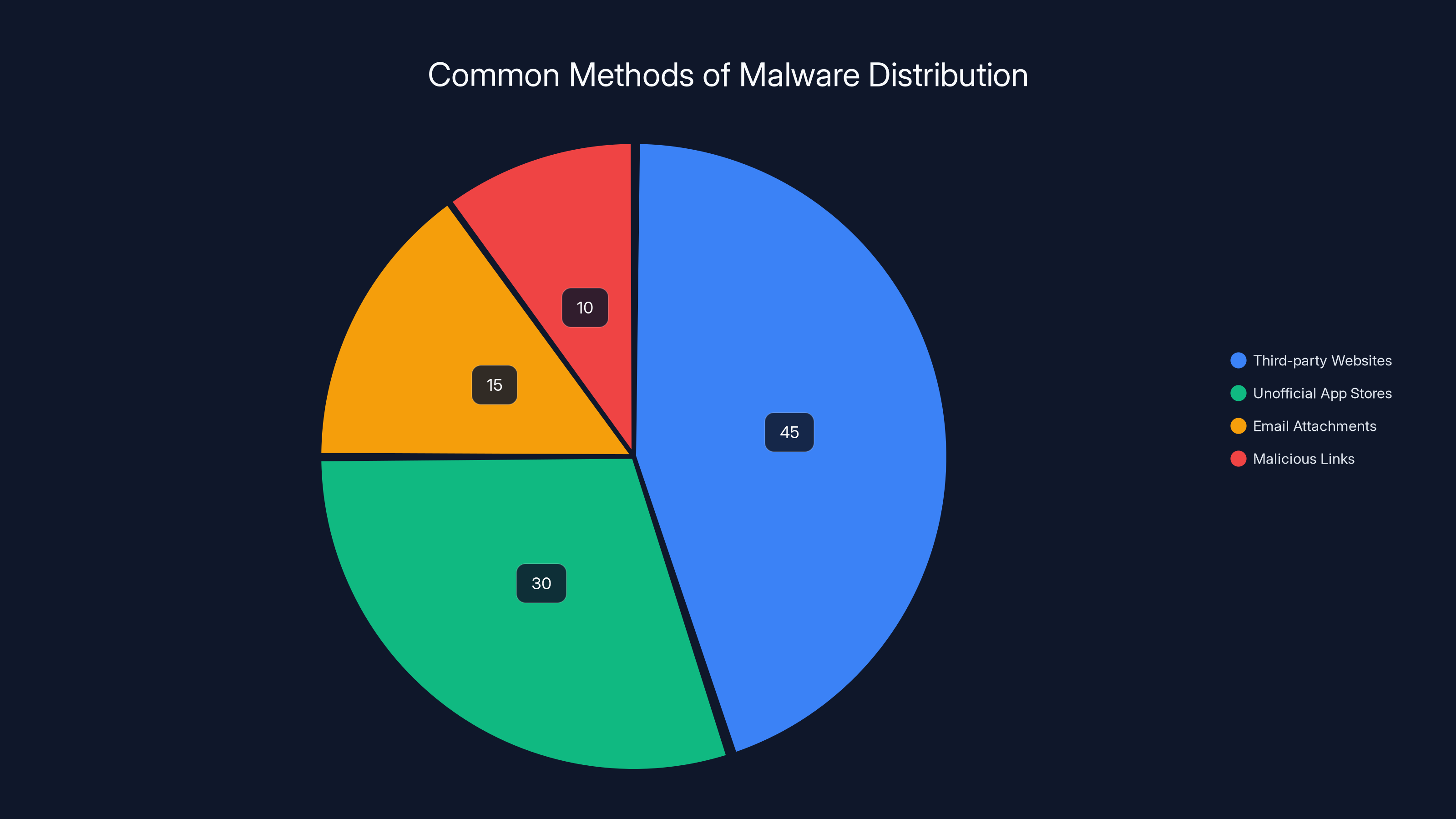
Estimated data shows that third-party websites are the most common method for distributing Android malware like Massiv, followed by unofficial app stores.
Technical Details of Massiv's Attack Infrastructure
To understand how dangerous Massiv is, you need to understand its technical architecture. This isn't a simple trojan that just steals passwords. It's a sophisticated piece of malware that has been engineered to maximize damage and evade detection.
Massiv uses a modular architecture, meaning different components of the malware can be updated, modified, or replaced without requiring the entire app to be reinstalled. This allows attackers to add new functionality, improve detection evasion, or change their attack vectors as defenses improve.
The malware communicates with command and control servers using encrypted channels. This means even if your network traffic is monitored, it's difficult to see what information is being exfiltrated. The encryption also makes it harder for security researchers to analyze what data is being stolen.
Accessibility Service Abuse: The Core Attack Vector
Accessibility Service in Android is designed to help users with disabilities navigate their phones. Apps can use it to read the screen content aloud, magnify text, or provide other accessibility features. It's a powerful API that provides detailed information about what's happening on the screen.
Massiv abuses this by requesting Accessibility Service permissions, which most users don't understand and simply grant. Once granted, the malware can:
- See every element on the screen and understand its purpose
- Detect when specific apps are launched
- Capture the content of input fields
- Understand button positions and functionality
- Monitor user interactions in real-time
- Intercept and modify screen content
This is more powerful than simple screen capture because it gives the malware a semantic understanding of what's on the screen. It doesn't just see pixels; it understands that there's a password field at coordinates X, Y that belongs to app Z.
Defending Against Accessibility Service Abuse
One of the problems with Accessibility Service abuse is that it's incredibly difficult to defend against without breaking the feature for legitimate uses. Android has improved permission controls in recent versions, but attackers are always finding new ways to trick users into granting permissions.
Some banking apps now detect when Accessibility Service is enabled and refuse to work, on the theory that if you need Accessibility Service, you probably have accessibility needs but shouldn't be using the banking app anyway. This is a controversial approach because it actually prevents people with disabilities from using banking apps.
Better solutions involve detecting suspicious behavior patterns—like Accessibility Service accessing banking apps frequently, or keystroke monitoring being used in conjunction with banking app access—and alerting users or blocking the malicious activity.
Regional Targeting: Why Portuguese Users?
Massiv targets Portuguese users specifically, which reveals something interesting about how modern banking trojans are deployed. Attackers don't launch global campaigns against everyone. They identify regions where they believe they can have the most success.
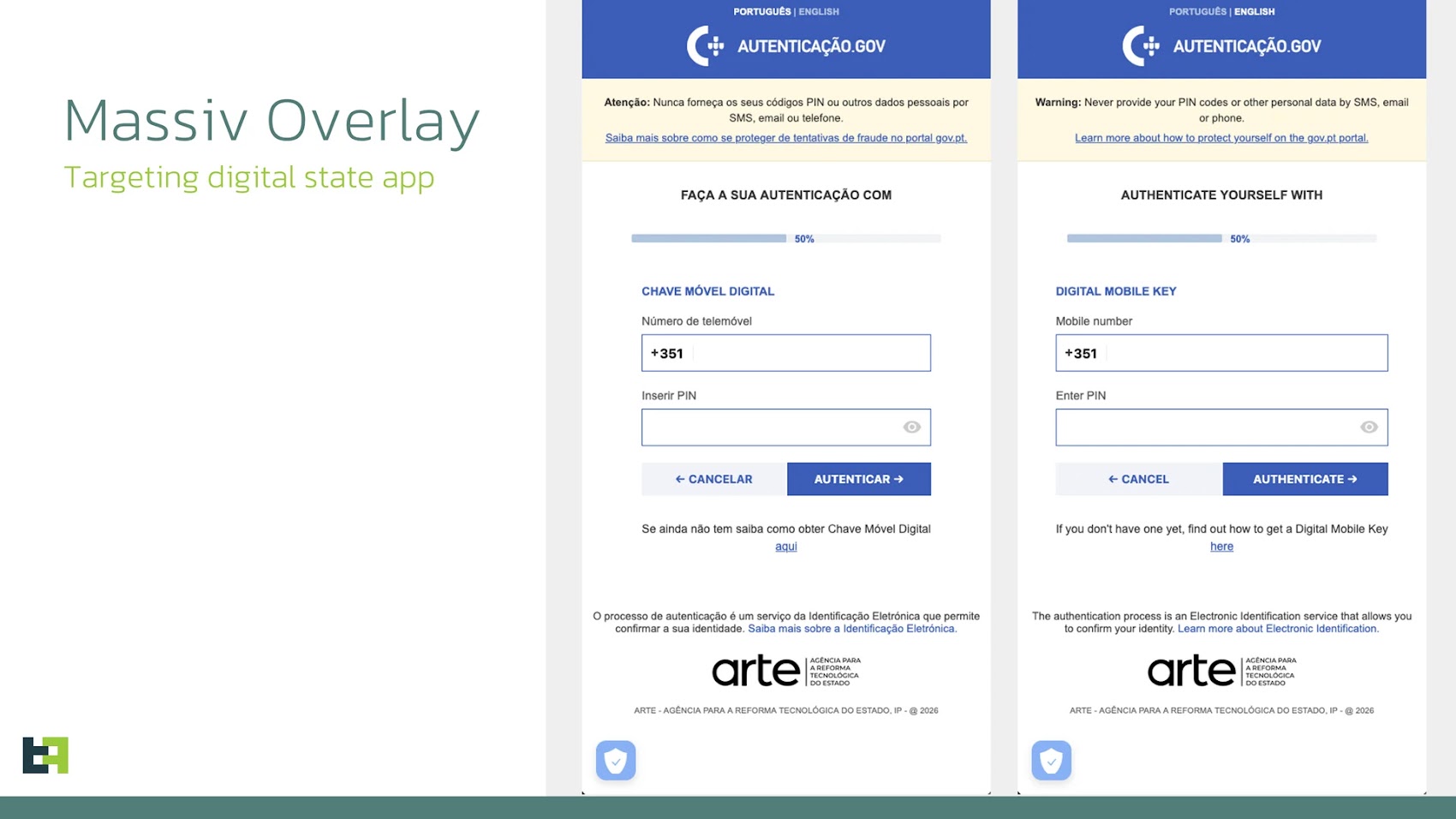
Portugal was chosen for several reasons. The country has relatively high smartphone penetration and good internet infrastructure, so mobile banking is common. Portuguese banks have specific security systems like Chave Móvel Digital (Mobile Key), a digital authentication signature system that Massiv specifically targets.
Moreover, Portugal may have fewer advanced cybersecurity resources than larger countries like Germany or France. Not because Portuguese companies aren't competent, but simply because larger markets might have more security professionals and infrastructure dedicated to cybercrime prevention.
Regional targeting also allows attackers to customize their attack. They research the most popular banks in the region, study their security systems, and develop targeted overlays that perfectly mimic the banking interfaces their victims use. A Portuguese user sees overlays that look exactly like their actual bank's interface, making them far more convincing than generic overlays would be.
Targeting Chave Móvel Digital
Chave Móvel Digital is a legitimate authentication system used by Portuguese banks and government services. It provides two-factor authentication for sensitive transactions. Massiv specifically targets this system because breaking it gives attackers access to the highest-security transactions.
If an attacker can intercept or simulate Chave Móvel Digital authentication, they can perform transactions that normal credential theft wouldn't allow. This is why security researchers were so alarmed—Massiv goes after the authentication methods that are supposed to prevent exactly this kind of fraud.
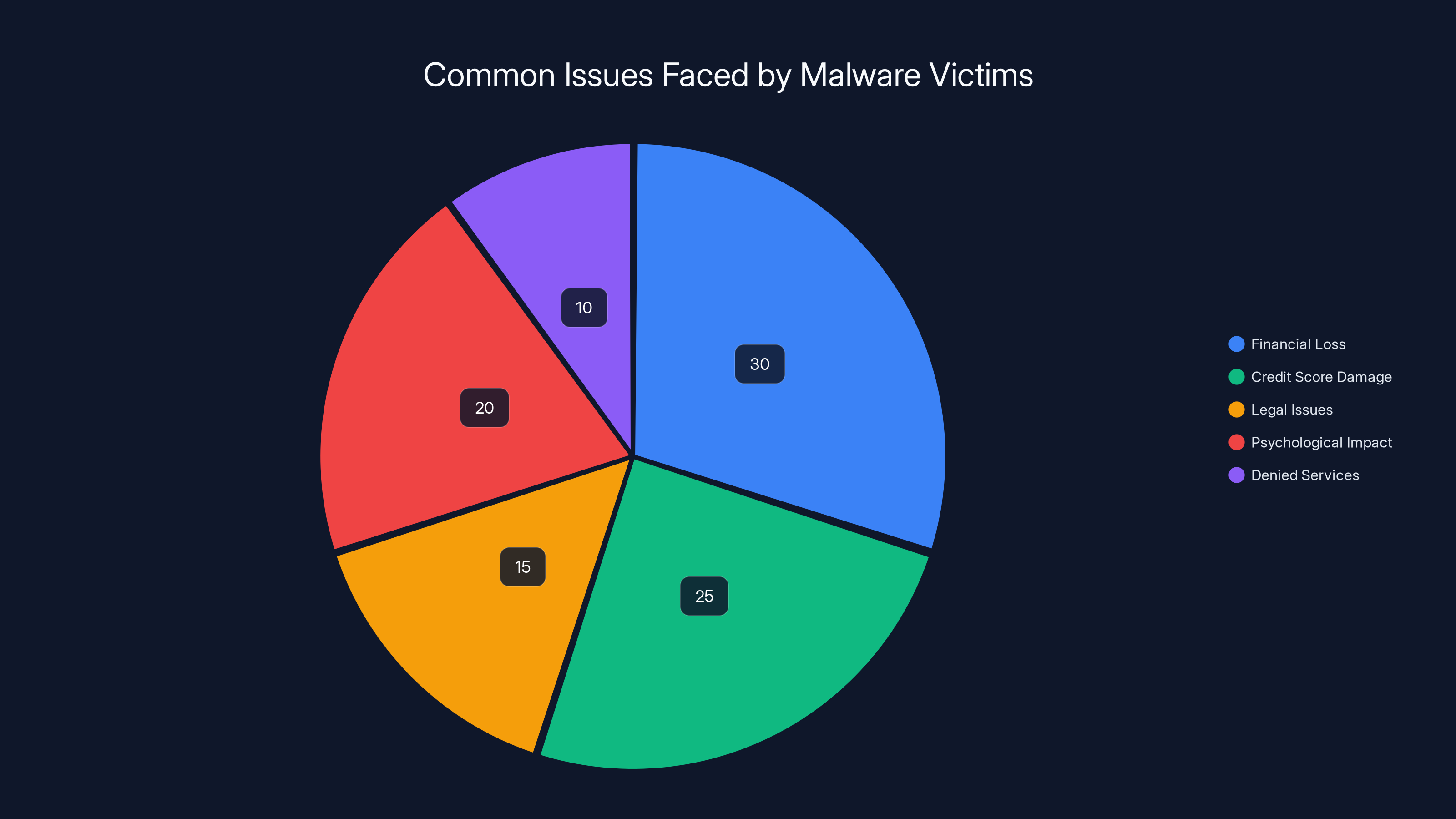
Estimated data shows financial loss and credit score damage are the most common issues faced by victims of Massiv malware, followed by psychological impacts.
The Banking Information Extraction Process
Understanding exactly how Massiv extracts banking information provides insight into why traditional security measures fail against this type of malware.
When you interact with your banking app, you generate data at multiple levels. There's the visual level (what you see on the screen), the input level (what you type), the behavioral level (how you navigate), and the semantic level (what you intend to do).
Traditional banking security has historically focused on protecting the visual level. Banks implement screen capture prevention, so malware can't take a screenshot of your login screen. But Massiv doesn't need screenshots. It works at the semantic level.
By understanding what fields are on the screen (through Accessibility Service), where they're located, and what data is being entered into them, Massiv can extract the same information without ever capturing the visual display. It's like someone describing a conversation to you versus you listening to a recording—either way, you get the information.
The extraction happens in real-time, which means Massiv can adapt to different banking interfaces, handle additional authentication steps, and respond to unexpected prompts. If a bank adds a CAPTCHA, Massiv might submit it and try again, or it might notify the attacker who can manually complete the authentication.
Multi-Factor Authentication Bypasses
One of the most concerning aspects of Massiv is how it handles multi-factor authentication (MFA). Even if your bank requires a one-time password (OTP) sent to your phone, Massiv can intercept it.
Some advanced variants of banking trojans like Massiv can:
- Monitor your SMS messages in real-time
- Intercept OTP codes before you even see them
- Monitor your email for account confirmation messages
- Watch for push notifications related to banking
- Detect and handle authentication app prompts
The attackers are essentially sitting in the middle of your authentication flow, watching everything you do, intercepting everything sent to you, and responding appropriately. From your perspective, everything looks normal. From the attacker's perspective, they have complete access.
This is why security experts now recommend using push-based authentication (where you approve a login on a separate app) or hardware security keys, which are much more difficult for malware to intercept.

Comparing Massiv to Other Banking Trojans
Massiv isn't the first sophisticated banking trojan, and it won't be the last. Understanding how it compares to other threats helps illustrate how banking malware has evolved.
Earlier banking trojans like Zeus and Spy Eye focused primarily on credential theft and screen capture. They were effective, but relatively crude by modern standards. When banks added screen capture protection, those trojans became less effective.
Modern trojans like Massiv have evolved. They don't rely on screen capture. Instead, they use Accessibility Service, they inject code into legitimate apps, they perform on-device fraud (manipulating the screen without capturing it), and they use multiple attack vectors simultaneously.
Compared to trojans like Albiriox (which targets over 400 financial apps), Massiv is more region-specific and appears to be a more advanced variant. Compared to trojans that abuse Android's overlay capabilities, Massiv combines overlays with sophisticated data extraction and real-time attack coordination.
The key innovation with Massiv is that it combines multiple attack vectors into a unified package. It's not just an overlay attack, or just keylogging, or just Accessibility Service abuse. It's all of these working together, plus professional-grade infrastructure, plus money laundering capabilities.

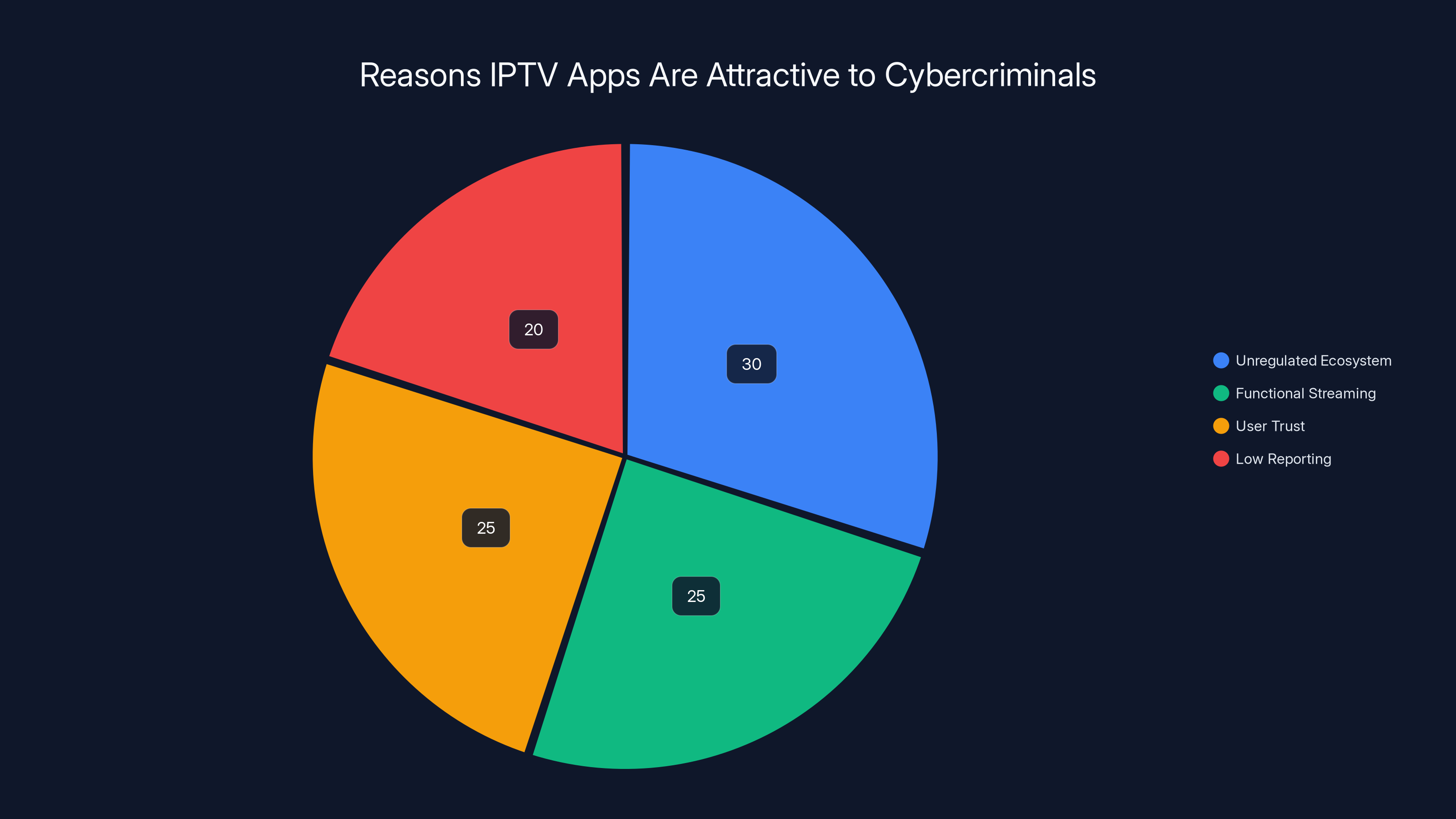
IPTV apps are attractive to cybercriminals due to their unregulated nature, functional streaming capabilities, user trust, and low reporting rates. Estimated data.
How to Detect Massiv and Similar Malware
The challenge with Massiv is that it's designed to be invisible. It looks like a legitimate app, it provides functionality (IPTV streaming), and it doesn't show obvious signs of malicious behavior.
However, there are some red flags you can watch for:
Unusual Battery Drain - Malware running in the background consuming your device's resources will drain your battery faster than normal. If your phone is losing 10-15% of battery per hour when you're not actively using it, something is wrong.
Data Usage Spikes - Check your mobile data usage in Settings. If you notice unusual data consumption, especially at odd hours when you're not using your phone, that's a sign that malware is sending data to external servers.
Device Overheating - Running sophisticated malware requires computational resources. If your phone is hot when it shouldn't be, that's a sign something is running in the background.
Slow Performance - Malware consuming resources will make your device sluggish. If apps are taking longer to load, or your phone is generally slower than usual, that's suspicious.
Unexpected Permission Prompts - If apps keep asking for permissions they shouldn't need, that's a red flag. Banking apps shouldn't need camera access, for example.
Unfamiliar Apps - Check your app list. If there are apps you don't remember installing, that's concerning. Malware sometimes installs additional apps.
Unusual Text Messages - If you receive strange SMS messages or see messages in your sent folder that you don't remember sending, someone might have access to your phone.
Account Activity Alerts - If your banks are sending you notifications about activity you didn't perform, you've definitely been compromised.
The problem is that Massiv is specifically designed to avoid these red flags. It might not drain your battery noticeably. It might send data in small increments that don't trigger data usage alerts. This is why detection is so difficult.
Security Measures and Protection Strategies
Given how sophisticated Massiv is, what can you actually do to protect yourself? The answer involves multiple layers of defense because no single security measure is foolproof.
Device-Level Security
First, keep your Android operating system updated. Google releases regular security patches that patch vulnerabilities that malware like Massiv exploits. If you're still running Android 10 or 11, you're significantly more vulnerable than if you're running Android 14.
Enable Google Play Protect, which is Android's built-in malware scanning service. While it's not perfect, it's better than nothing. You'll find it in Settings > Google > Manage Your Google Account > Security.
Enable biometric authentication (fingerprint or face recognition) for sensitive apps. Even if malware has your credentials, it can't bypass your fingerprint. Most banking apps support this, and you should definitely enable it.
App-Level Security
Don't download apps from unofficial sources. This is the single most important security measure. If you want an IPTV app, accept that you might not have access to one, or use legitimate streaming services like Netflix, Disney+, or others.
Review app permissions carefully before installing anything. If an app asks for Accessibility Service access and it's not an accessibility app, that's a huge red flag. Same with access to your SMS messages, contacts, or location.
Once you've installed an app, regularly review its permissions. Go to Settings > Apps > Permissions and see what each app has access to. Revoke permissions that don't make sense.
Behavioral Security
Don't use the same password for multiple accounts. If Massiv steals your password for one bank, you don't want the attacker to have access to your other banks too.
Use a password manager to generate and store unique, complex passwords for each account. This way, even if one password is compromised, your other accounts are safe.
Enable two-factor authentication on all accounts that support it, especially email and banking. Two-factor authentication makes it much harder for attackers to access your accounts even if they have your password.
Don't open suspicious email links or download files from unknown senders. Even if Massiv isn't distributed via email in your region, other malware is. Email is still one of the primary malware distribution vectors.
Financial Security
Monitor your bank accounts regularly. Check your account activity at least weekly. Most banks now offer real-time transaction notifications; enable these on all your accounts.
Set up low-balance alerts so you're notified if too much money leaves your account unexpectedly. Set up transaction limits so that anything over a certain amount requires additional authentication.
Fork your credit reports annually from each of the three bureaus (Experian, Equifax, Trans Union). In Portugal, check CEMPE (Central Registry of Credit Obligations). If someone has opened fraudulent accounts in your name, you'll see them on your credit report.
Consider freezing your credit if you believe you've been targeted. This prevents anyone from opening new accounts in your name, though it also means you can't open new legitimate accounts without unfreezing first.
Network-Level Security
Use a trusted VPN service when connecting to public Wi-Fi. Public Wi-Fi is completely unencrypted, so anyone on the same network can see your traffic. A VPN adds encryption so no one can see your banking credentials even if they're sniffing the network.
Avoid mobile banking on public Wi-Fi entirely if possible. Wait until you're on your home network or cellular data.
Disable automatic Wi-Fi connection. By default, Android remembers Wi-Fi networks you've connected to and automatically reconnects. This can be exploited by attackers who set up fake Wi-Fi hotspots with the same names.
Turn off Bluetooth when you're not using it. Bluetooth can be exploited by attackers within range to install malware or exfiltrate data.

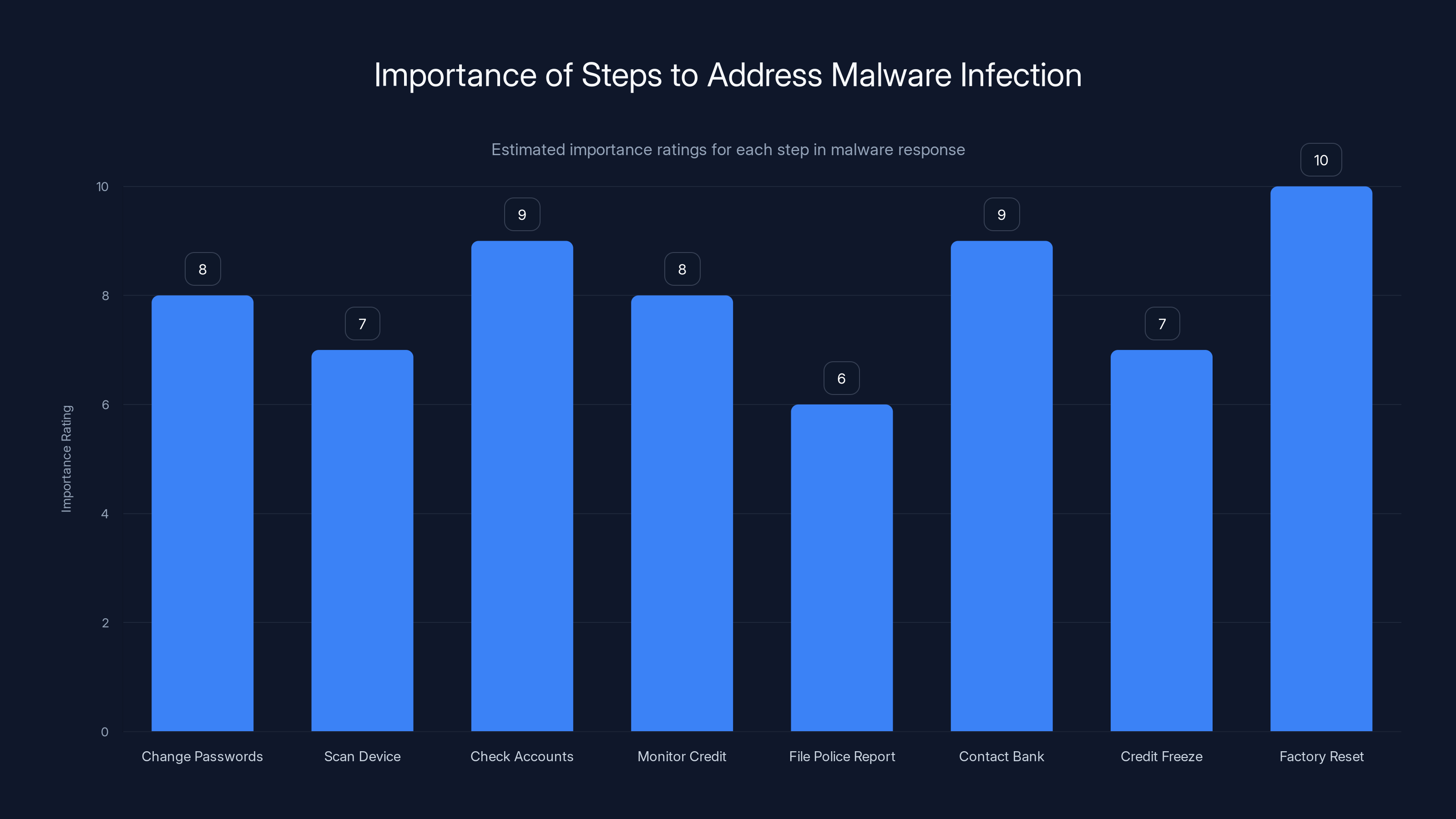
Factory resetting your device is rated as the most crucial step (10/10) to ensure complete malware removal, while filing a police report is less critical (6/10). Estimated data based on typical security recommendations.
The Role of Antivirus and Mobile Security Apps
You might be wondering: shouldn't a good antivirus app catch Massiv? The answer is complicated.
Antivirus apps can catch malware, but they have limitations. Massiv is constantly being updated and modified, so antivirus signatures become outdated. By the time an antivirus company identifies Massiv and creates a detection signature, new variants have already been deployed.
Moreover, antivirus apps themselves require permissions to be effective. They need access to examine your installed apps, monitor your system, and scan files. If you give a malicious antivirus app (fake antivirus apps are themselves a major malware vector) these permissions, you're giving the malware everything it needs to compromise your device.
That said, a reputable antivirus app from a trusted company (Kaspersky, Bitdefender, Norton, Trend Micro) is better than nothing. These companies have large security teams constantly analyzing new threats and updating their detection capabilities.
But you should be aware of the limitations. A good antivirus might catch 90% of known malware, but Massiv is designed to evade detection. It's obfuscated, it's updated frequently, and it's specifically designed to look like a legitimate app.
The best approach is defense in depth: don't install apps from untrusted sources (so you're never exposed to Massiv in the first place), monitor your accounts carefully (so you catch fraudulent activity immediately), and use a reputable antivirus as an additional layer of protection.

The Broader Context: Why Banking Trojans Keep Evolving
Massiv didn't appear in a vacuum. It's part of a larger trend of banking trojans becoming more sophisticated, more geographically targeted, and more integrated with money laundering operations.
The profitability of banking malware means that organized crime groups invest heavily in development. A single successful banking trojan campaign can net millions of euros. That kind of money incentivizes professional development, continuous improvement, and sophisticated infrastructure.
Moreover, as traditional banking security improves, trojans evolve to defeat that security. Banks added screen capture prevention, so trojans started using Accessibility Service. Banks added overlay detection, so trojans started using on-device fraud techniques. Banks improved credential protection, so trojans started targeting the authentication infrastructure itself.
It's an arms race, and it shows no signs of slowing down.
The Money Laundering Industry
What makes Massiv particularly dangerous is that it's not just about stealing credentials. It's integrated into a larger money laundering operation. The attackers aren't working alone. They're part of a larger criminal ecosystem that includes money mules (people who receive stolen funds), money launderers (who make dirty money look clean), and organized crime groups (who coordinate the entire operation).
This infrastructure is expensive to build and maintain, but extremely profitable. The more money a group can launder, the more valuable the infrastructure becomes. That's why they're investing in sophisticated malware like Massiv.
Law Enforcement Response
Law enforcement agencies worldwide have made significant progress against banking malware in recent years. Europol, the FBI, and various national agencies have disrupted botnet infrastructure, arrested malware developers, and prosecuted money mule networks.
But they're fighting a losing battle without cooperation from users. If users don't report fraud, if they don't update their systems, if they keep installing apps from untrusted sources, malware continues to thrive. Law enforcement can take down one command and control server, but the attackers just set up another one.

Real-World Consequences: Victim Stories
To truly understand the impact of Massiv and similar malware, you need to hear from people who've been victimized.
Many Portuguese victims of Massiv discovered the attack months after it occurred. They'd notice unusual charges on their credit card statement, or their bank would contact them about suspicious activity. By that point, thousands of euros might have been stolen, loans might have been taken out in their name, and their credit score might have been destroyed.
The recovery process is nightmarish. Victims have to:
- Contact their banks to report fraudulent accounts and transactions
- File police reports with local law enforcement
- Contact credit agencies to dispute fraudulent accounts
- Work with banks to prove they didn't authorize the fraudulent loans
- Hire lawyers in some cases to fight the fraud
- Monitor their credit reports for years to ensure no additional fraud occurs
Some victims have reported being denied mortgages because of the fraudulent accounts and loans that appeared on their credit reports. Others have faced years of dealing with debt collection agencies trying to collect on loans they didn't take out.
The psychological impact is significant too. Victims report feeling violated, anxious, and distrustful of technology. Some stop using mobile banking entirely and go back to in-person transactions, which is exactly what the attackers want.
Future Evolution of Banking Trojans
The banking malware landscape continues to evolve. Researchers predict several trends:
Increased Use of Machine Learning - Future trojans might use AI to better predict user behavior, more accurately simulate legitimate banking interfaces, and more effectively evade detection.
Targeting of Cryptocurrency - As cryptocurrency adoption increases, trojans will increasingly target crypto wallets and exchange accounts. The irreversible nature of crypto transactions makes them attractive to attackers.
Integration with Io T - Smart home devices are increasingly connected but often poorly secured. Future trojans might use Io T devices as part of their botnet infrastructure.
Supply Chain Attacks - Rather than targeting users directly, attackers might compromise legitimate app developers and inject malware into official apps before they're released.
Biometric Spoofing - As biometric authentication becomes more common, trojans will develop techniques to spoof fingerprint and face recognition systems.
The key is that attackers are constantly innovating. By the time a defense is deployed, attackers are already working on ways to overcome it.
Essential Steps to Take Right Now
If you're concerned you might be infected with Massiv or similar malware, here's what you should do immediately:
-
Change Your Passwords - Use a different device (computer or tablet) to change all your passwords. Use unique, complex passwords for each account. If you think you've been compromised, don't assume a simple password change is enough, but it's a necessary first step.
-
Scan Your Device - Use a reputable antivirus app to scan your device. While it might not catch everything, it's worth doing. Download the antivirus app on the same device if you suspect infection, but be aware this carries some risk. Alternatively, use a computer to download the antivirus app and install it via USB.
-
Check Your Accounts - Log into your bank accounts and review all transactions. Look for charges you didn't authorize. Check for new accounts you didn't create. Most banks have a way to dispute fraudulent charges; use it.
-
Monitor Your Credit - Check your credit report from all three bureaus. Look for accounts you didn't create, inquiries you didn't authorize, or other signs of fraud.
-
File a Police Report - Document everything and file a police report with your local law enforcement. Get a report number for your records.
-
Contact Your Bank - Inform your bank of the suspected fraud. They can flag your account, monitor for suspicious activity, and potentially reverse fraudulent charges.
-
Consider a Credit Freeze - If you're very concerned about your credit, freeze it so no one can open new accounts in your name without unfreezing first.
-
Factory Reset (Nuclear Option) - If you're very confident you're infected and you've taken backups of important data, consider factory resetting your phone to completely remove any malware. Be aware this will delete all data on your phone unless you've backed it up elsewhere.

FAQ
What is Massiv Android malware exactly?
Massiv is a sophisticated banking trojan disguised as a legitimate IPTV streaming application. It targets Portuguese users by combining screen overlays, keylogging, and abuse of Android's Accessibility Service to steal banking credentials, create fraudulent accounts in victims' names, and facilitate money laundering operations. The malware is particularly dangerous because it not only steals credentials but also enables attackers to take out loans and open accounts entirely without the victim's knowledge or consent.
How does Massiv infect Android devices?
Massiv is distributed as a fake IPTV app that users download from untrusted sources, not from the official Google Play Store. IPTV apps provide access to copyrighted content and are illegal in most countries, forcing users to download from third-party websites, forums, and unofficial sources where there's no security review process. Once installed, the app requests permissions including Accessibility Service access, which most users grant without understanding the implications. This is when the malware becomes active and begins stealing data.
What happens if I install Massiv on my phone?
If you install Massiv, the malware will begin monitoring your device immediately. It will grant itself Accessibility Service access (if you approve the permission), which allows it to see everything on your screen, capture your keystrokes, and understand the structure of every app you use. It will display screen overlays that mimic your banking app to steal your credentials, monitor your banking sessions in real-time, and send your data to attacker-controlled servers. Within weeks, attackers might have opened fraudulent bank accounts in your name, applied for loans, and begun laundering money through your accounts.
How can I tell if I'm infected with Massiv?
Detecting Massiv is difficult because it's designed to be invisible, but watch for signs like unusual battery drain, unexpected data usage spikes, slower device performance, unfamiliar apps you don't remember installing, or unusual account activity notifications from your bank. Check your Accessibility Service settings to see if any unfamiliar apps have access. Monitor your bank accounts regularly for unauthorized transactions. Check your credit report to see if unauthorized accounts have been opened. If you notice any of these signs, you likely need to take immediate action.
Can my antivirus app protect me from Massiv?
Reputable antivirus apps from companies like Kaspersky, Bitdefender, or Norton can provide some protection by identifying and removing known malware variants, but they have limitations. Massiv is constantly updated and modified to evade antivirus detection, and by the time a detection signature is created, new variants have already been deployed. Antivirus is one layer of defense, but prevention is better than cure—only downloading apps from official app stores and carefully reviewing permissions is more effective than relying on antivirus to catch malware after it's installed.
What should I do if I think I've been infected with Massiv?
If you suspect infection, immediately change all your passwords from a different device using unique, complex passwords. Scan your device with a reputable antivirus app. Check all your bank accounts and credit reports for unauthorized accounts or transactions. File a police report and notify your bank of the suspected fraud. Monitor your credit report regularly for months or years afterward. Consider freezing your credit to prevent attackers from opening new accounts. If you're very confident about the infection, you can do a factory reset to completely remove the malware, but back up important data first to a separate device.
Is my i Phone safe from Massiv?
Yes, Massiv is Android-only malware and cannot infect i Phones. i OS's security model is different from Android and makes this type of malware much more difficult to develop. That said, i Phone users aren't immune to all threats. They should still download apps only from the official App Store, carefully review permissions, and monitor their accounts for fraud. Additionally, malware targeting i OS likely exists but works differently than Android trojans due to i OS's more restrictive architecture.
Why are Portuguese users specifically targeted?
Portuguese users are targeted by Massiv because Portugal has high smartphone penetration and common mobile banking usage, making it a profitable target. Additionally, Portuguese banks use specific security systems like Chave Móvel Digital that attackers have studied and developed techniques to defeat. Regional targeting allows attackers to customize their attacks, research local banks, and develop overlays that perfectly mimic the banking interfaces Portuguese users actually use, making their attacks more convincing and effective.
Can I still use IPTV apps safely?
No IPTV app is completely safe if downloaded from unofficial sources. While not all IPTV apps contain malware, the distribution method through untrusted sources means there's always risk. The safest approach is to avoid IPTV apps entirely and use legitimate streaming services like Netflix, Disney+, Prime Video, or others. If you choose to use IPTV apps despite the risk, at minimum use a burner device you don't use for banking, keep it completely separate from devices with sensitive data, and never grant Accessibility Service or permission to access SMS.
What's the difference between Massiv and other banking trojans?
Massiv combines multiple attack vectors (screen overlays, keylogging, Accessibility Service abuse, real-time data extraction) and integrates them with money laundering operations. While other trojans like Zeus focused primarily on credential theft, and Albiriox targets over 400 financial apps, Massiv is specifically designed for regional targeting in Portugal and goes beyond credential theft to actually create fraudulent accounts and facilitate money laundering. The sophistication and professional infrastructure make it particularly dangerous compared to older-generation banking trojans.
Conclusion: Staying Safe in an Evolving Threat Landscape
Massiv represents a new generation of banking malware that's more sophisticated, more integrated with criminal infrastructure, and more destructive than previous threats. It's not just about stealing your credentials—it's about completely taking over your financial identity and using you as a puppet in a larger money laundering operation.
The reality is that perfect security doesn't exist. No antivirus will catch everything. No security measure is foolproof. But you can dramatically reduce your risk by making smart choices: download apps only from official app stores, carefully review permissions, monitor your accounts regularly, and keep your devices updated.
The good news is that Massiv is geographically targeted at Portuguese users, so if you're outside Portugal, your risk is lower. But the techniques Massiv uses aren't unique—similar trojans exist in other regions targeting other populations. The malware ecosystem is global and constantly evolving.
The most important thing you can do is stay informed and vigilant. Know what you're installing on your device. Know what permissions you're granting. Know what to look for if something seems off. And if you do fall victim to this kind of malware, report it to your bank, your law enforcement, and your credit agencies immediately.
Banking trojans like Massiv are profitable because they work. They steal millions of euros annually because users fall victim to them. But an informed user who's aware of the threats and takes preventive measures is a much harder target. Make yourself a hard target, and criminals will likely move on to easier prey.
The arms race between security and malware will continue. But by staying informed, staying careful, and staying vigilant, you can keep your financial identity secure in an increasingly dangerous digital landscape.

Key Takeaways
- Massiv is a sophisticated banking trojan disguised as a fake IPTV app targeting Portuguese users with advanced credential theft techniques
- The malware abuses Android's Accessibility Service to monitor screen content, capture keystrokes, and bypass security protections
- Attackers use stolen credentials to create fraudulent bank accounts in victims' names, apply for loans, and facilitate money laundering
- IPTV apps are preferred malware delivery vectors because they're illegal and force users to download from untrusted sources with no security review
- Protection requires multi-layered defense: only download from official app stores, monitor account activity regularly, freeze credit if targeted, and keep devices updated
- Detecting Massiv is difficult because it's designed to operate invisibly, but signs include unusual battery drain, data spikes, slower performance, and suspicious account activity
Related Articles
- Google Rejected 1.75M Android Apps and Banned 80K Developers in 2025 [Data]
- Mac Security & Antivirus Protection Guide [2025]
- CarGurus Data Breach: 1.7M Records Stolen by ShinyHunters [2025]
- Best Home Antivirus Software & Protection [2025]
- Billions of Exposed Social Security Numbers: The Identity Theft Crisis [2025]
- Keenadu Android Backdoor: Firmware Malware Threat [2025]
![Massiv Android Malware: How Fake IPTV Apps Steal Banking Data [2025]](https://tryrunable.com/blog/massiv-android-malware-how-fake-iptv-apps-steal-banking-data/image-1-1771598299714.jpg)



