EU GDPR Fines Hit €1.2bn in 2025: A Year of Record Breaches and Enforcement
Last year was brutal for data protection. European regulators didn't mess around in 2025, and if you're running any kind of digital business that touches EU customer data, you need to understand what happened and why.
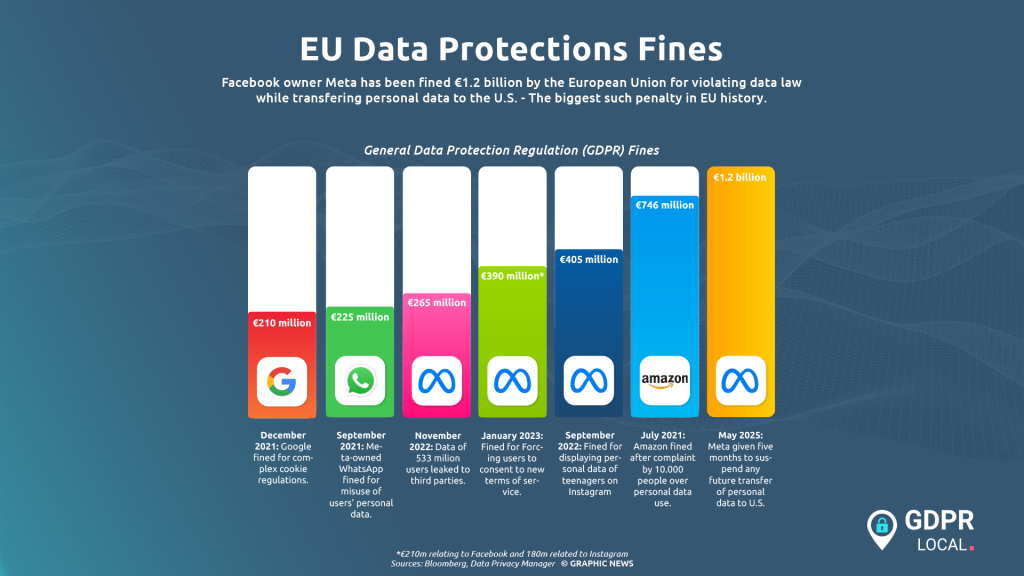
Here's the headline: European authorities issued over €1.2 billion in GDPR fines throughout 2025. That alone is shocking. But what really got everyone's attention was something even more alarming underneath those numbers: personal data breach reports jumped 22% year-over-year, hitting an average of 443 notifications every single day starting January 28, 2025. This was the first time breach notifications exceeded the 400 daily average since GDPR went into force back in 2018, as reported by BankInfoSecurity.
Let me be honest with you. If you thought GDPR enforcement was getting easier or that regulators were slowing down, the 2025 data says otherwise. The fines stayed steady at around €1.2 billion (comparable to 2024), but the volume of breaches exploded. That's not a sign of compliance improving. That's a warning that threats are multiplying faster than defenses can catch up.
What makes 2025 particularly interesting is that the data tells a more nuanced story than just "more breaches equals stricter fines." Instead, regulators are becoming more selective about which breaches they penalize heavily. Ireland issued the single biggest fine of 2025: a €530 million penalty against Tik Tok. Meanwhile, tech giants continue to dominate the penalty list, with nine of the ten largest GDPR fines in history going to major technology companies, according to Statista.
In this comprehensive breakdown, we'll walk through what actually happened in 2025, why breaches spiked the way they did, which companies got hit hardest, and most importantly, what you need to do to protect yourself and your data.
TL; DR
- €1.2 billion in fines: European regulators maintained enforcement levels from 2024, with no major increase despite rising threat activity
- 443 daily breach notifications: A 22% jump year-over-year marks the first time breaches exceeded 400/day since GDPR inception
- Ireland leads enforcement: The country issued the biggest 2025 fine (€530M to Tik Tok) and has accumulated €4.04 billion total since GDPR began
- Tech giants pay the most: Big Tech companies account for 9 of the 10 largest GDPR fines ever, signaling regulators' priority targets
- Multiple attack vectors: Geopolitical tensions, new technologies, and emerging laws all contributed to the 2025 breach surge
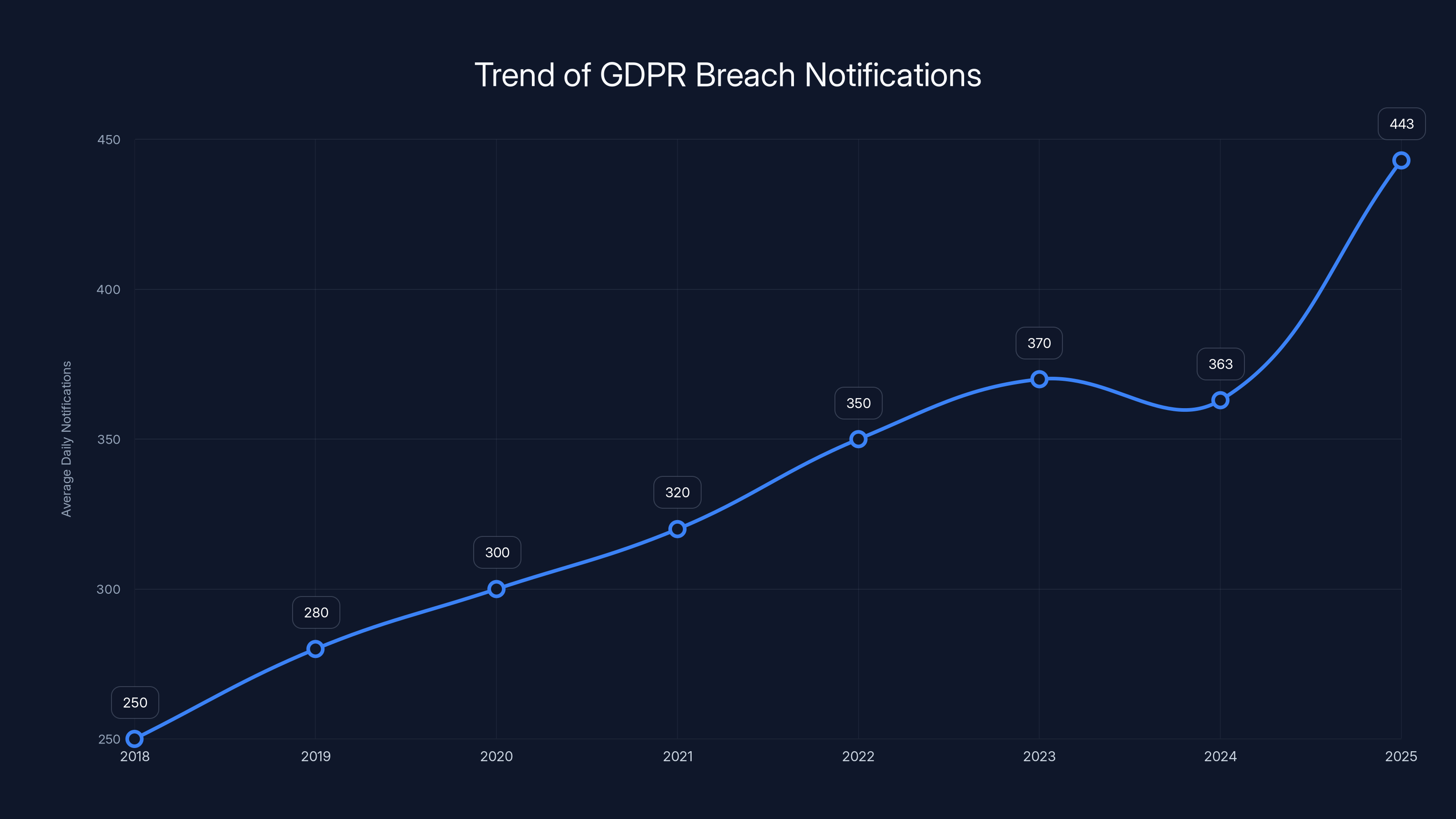
The number of daily GDPR breach notifications has steadily increased, reaching 443 in 2025, a 22% increase from 2024. Estimated data.
The €1.2 Billion Fine Figure: What It Actually Means
When you hear "€1.2 billion in fines," your first instinct might be to think enforcement is getting tougher. But the reality is more complicated than that.
The €1.2 billion figure represents total GDPR-related penalties issued across the entire European Union and affiliated jurisdictions throughout 2025. That sounds enormous until you compare it to 2024, which also saw approximately €1.2 billion in fines. So essentially, enforcement levels held steady. There wasn't a dramatic spike in penalties, even though breach reports absolutely exploded, as noted by The Register.
This discrepancy tells us something important: regulators are becoming more strategic. They're not fining every breach. They're targeting specific violations with maximum impact. When they do issue fines, they're making them count. Tik Tok's €530 million fine in 2025 exemplifies this approach. That single penalty represents roughly 44% of the entire year's total fine amount.
Think about what that means for your organization. If you have a massive data breach but it doesn't attract regulatory attention, you might face zero fines. But if you operate in certain sectors (social media, finance, healthcare) or you're a Big Tech company that regulators have already targeted, a single violation could cost you hundreds of millions.
The stability of the overall fine amount also reflects something interesting about how GDPR enforcement actually works. Many of the fines issued in any given year relate to violations discovered or investigated in previous years. There's a lag between when a breach happens, when regulators discover it, and when they finally impose penalties. So 2025's €1.2 billion partly reflects breaches from 2023 and 2024 that authorities were still processing, as detailed by Infosecurity Magazine.
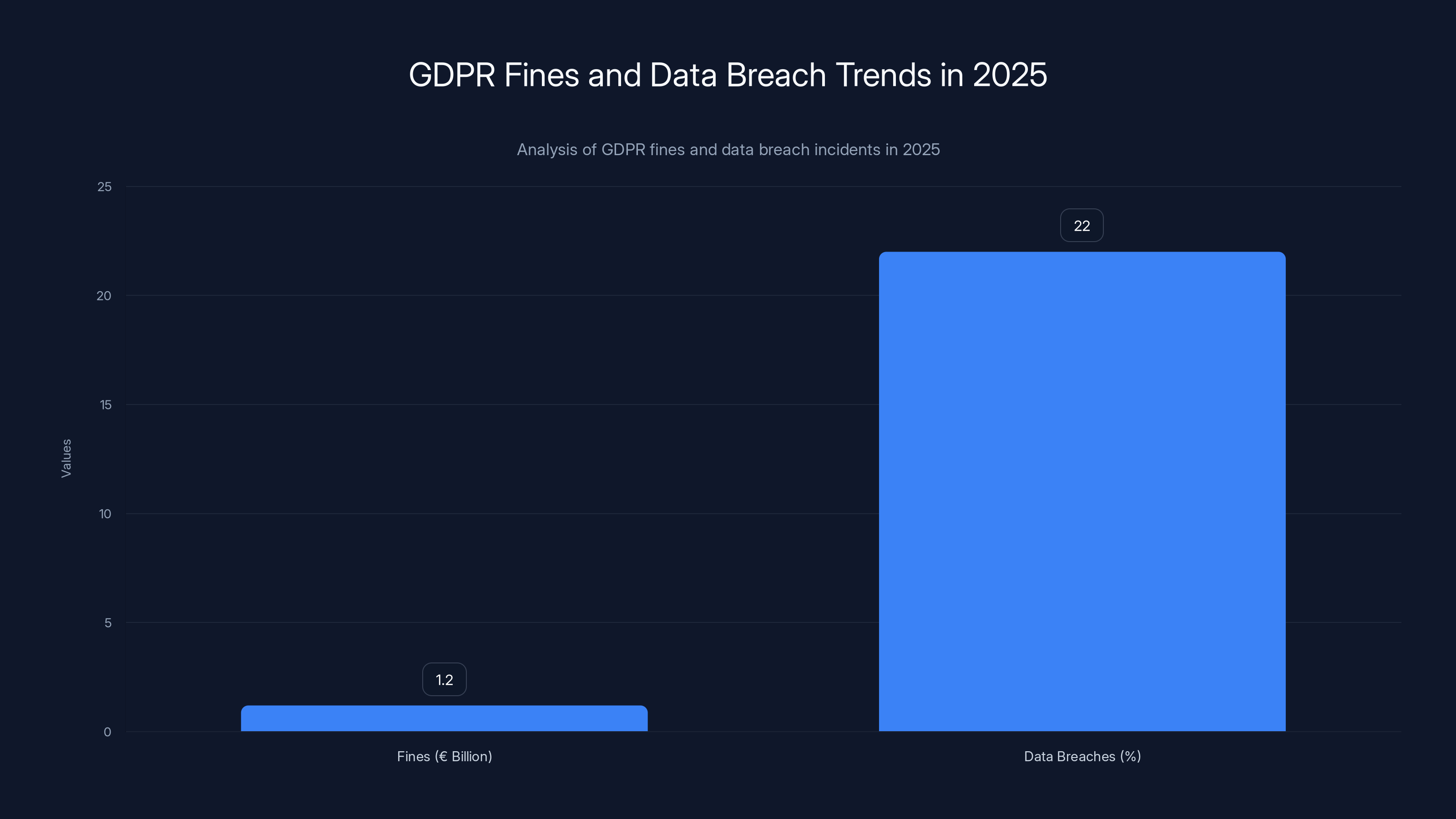
In 2025, GDPR fines totaled €1.2 billion, while data breaches increased by 22%, highlighting a gap between enforcement and breach incidents. Estimated data.
The Real Story: 22% Spike in Data Breach Notifications
Forget the stable fine numbers for a moment. The genuinely alarming development in 2025 was the explosion in data breach notifications.
European regulators received an average of 443 personal data breach reports every single day starting January 28, 2025. Let that number sink in. That's roughly 160,000 breach notifications per year if the pace continues, as reported by BankInfoSecurity.
Compared to 2024, this represented a 22% increase. More significantly, 2025 marked the first year that daily breach notifications exceeded 400 since GDPR came into force in 2018. That's seven years of accumulating regulatory infrastructure, compliance awareness, and security investment, yet breaches are accelerating, not slowing down.
What caused this explosion?
Geopolitical Tensions: 2025 was marked by increased international instability. Nation-state actors escalated cyber-espionage campaigns targeting European infrastructure. Private companies caught in the crossfire faced compromised systems and stolen data. These weren't always sophisticated attacks requiring zero-day exploits. Some were brute-force attacks on poorly secured remote access systems or spear-phishing campaigns targeting employees with administrative access.
New Technologies Providing Attack Tools: Threat actors gained access to more capable hacking tools and automation platforms. AI-powered vulnerability discovery tools made it easier to scan networks for weaknesses. Generative AI systems helped attackers craft more convincing phishing emails. Automated exploit frameworks reduced the technical skill required to launch attacks. In some cases, just having better tools didn't require more sophisticated threat actors.
New Regulatory Requirements: This is the counterintuitive one. The EU introduced new incident notification requirements and mandatory reporting timelines for certain breach types. Many organizations that previously didn't report incidents (or reported them quietly) now had legal obligations to notify regulators. This didn't necessarily mean more breaches occurred. It meant more breaches were being reported.
Supply Chain Vulnerabilities: Companies got hit not just through direct attacks but through compromised third-party vendors. A breach at a managed IT services provider could affect dozens of client companies simultaneously. A vulnerability in widely-used business software could create massive cascading breaches across multiple sectors.
The mathematics of the breach surge are worth understanding. If you're managing data for millions of EU residents, your probability of experiencing at least one reportable incident in 2025 was substantially higher than previous years. Organizations with hundreds of thousands of records faced almost certain breach exposure at some point during the year.
Ireland's Dominance: €4.04 Billion and Counting
If you've noticed that most of the biggest GDPR fines seem to come from Ireland, you're paying attention to something real.
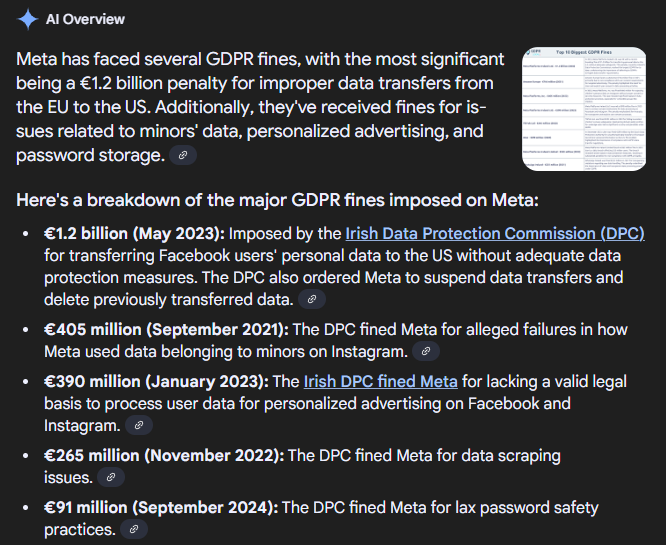
Ireland issued €4.04 billion in GDPR fines since the regulation came into force, accounting for roughly 34% of all GDPR penalties globally. That's extraordinary given that Ireland represents about 1% of the EU's population. The reason is straightforward: Ireland is home to European headquarters for Meta, Google, Amazon, Apple, and numerous other tech giants. These companies fall under Irish regulatory jurisdiction because their European data processing operations are headquartered in Dublin, as highlighted by Infosecurity Magazine.
In 2025 specifically, Ireland issued the largest single fine of the year: €530 million against Tik Tok. That penalty dwarfed penalties from other regulators. The next-largest fines that year came from other jurisdictions but were significantly smaller in comparison.
What makes Ireland's regulatory approach distinct?
Aggressive Interpretation of GDPR: Irish regulators have shown a willingness to interpret GDPR requirements broadly. Where other regulators might view certain practices as gray areas, Ireland's Data Protection Commission tends toward strict interpretation. This aggressive stance has resulted in massive fines for what might constitute "grey area" violations in other jurisdictions.
Focus on Big Tech: Ireland explicitly prioritizes enforcement against large technology companies. The logic is clear: big fines against major companies create headline-grabbing deterrence, while minor fines against small businesses get ignored. One €530 million fine attracts far more compliance attention than 500 fines of €1 million each.
Data Transfer Issues: A significant portion of Ireland's largest fines relate to international data transfer practices. When European companies transfer customer data to the United States or other jurisdictions, they must have legal mechanisms in place to ensure adequate protection. Ireland regulators have been particularly strict about validating these mechanisms, especially after the "Schrems II" ruling questioned the adequacy of the US-EU Privacy Shield framework.
Meta's History with Irish Regulators: Meta (Facebook, Instagram) has been hit with multiple record-breaking fines from Irish authorities. The company's €1.2 billion fine in 2021 and subsequent multi-billion euro penalties reflect a pattern of violations related to data transparency, user consent, and cross-border data transfers. In 2025, as the company continues its operations in Ireland, regulatory scrutiny remains intense, according to HIPAA Journal.
For organizations outside the EU, Ireland's enforcement actions matter because they set precedents. When Irish regulators fine Meta for inadequate data transfer protections, that sends a message to every other company conducting similar activities. The fine isn't just about what Meta did wrong. It's about establishing the regulatory interpretation that all companies must follow.
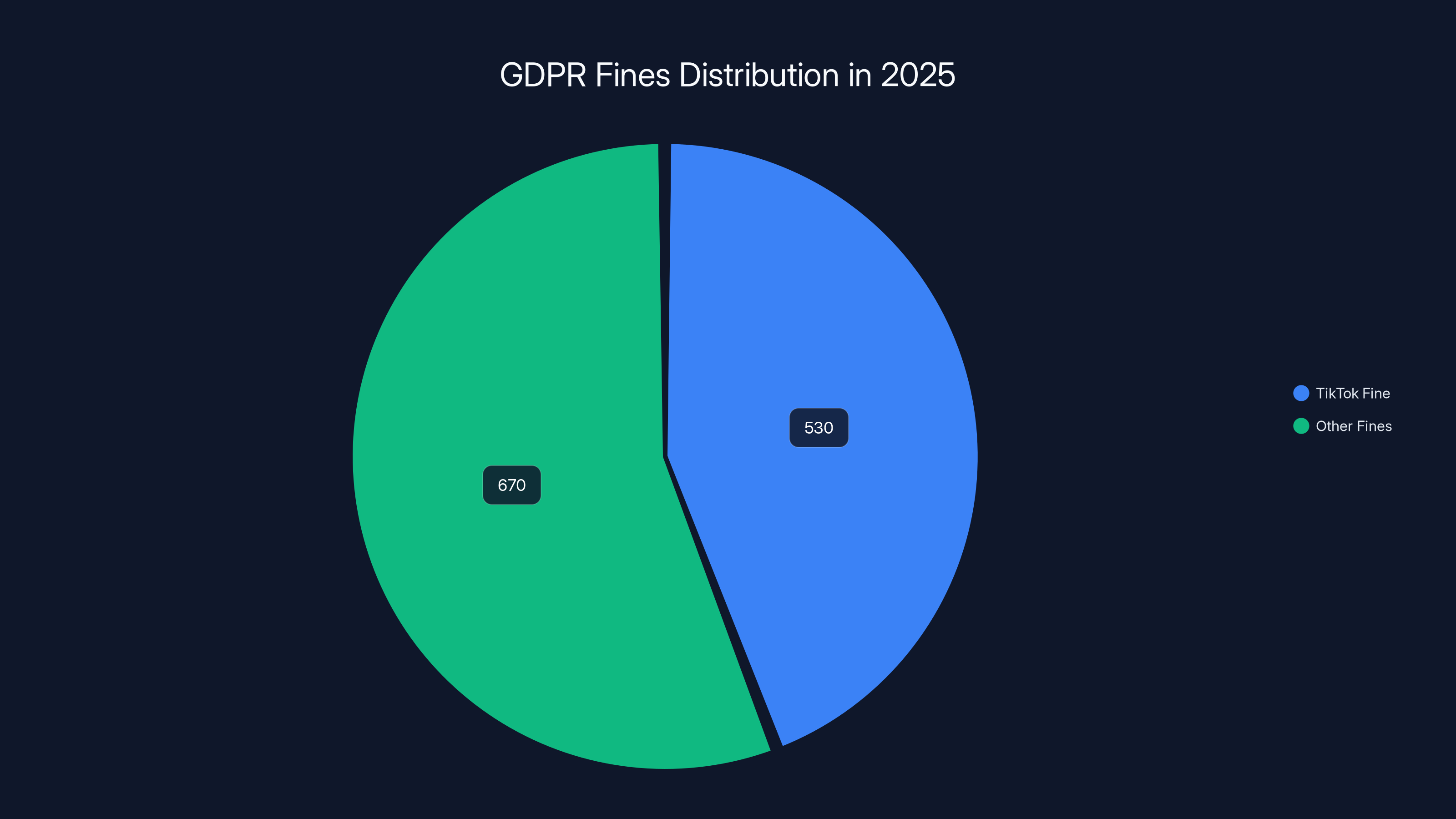
In 2025, TikTok's fine accounted for 44% of the total €1.2 billion GDPR fines, highlighting targeted regulatory action.
Tech Giants and the Concentration of Penalties
When regulators talk about GDPR enforcement, they don't mean equal distribution across company sizes. The data tells a stark story: tech giants are paying almost all of the biggest fines.
Nine of the ten largest GDPR fines ever issued have gone to Big Tech companies. Meta, Google, Amazon, Apple, Microsoft, and similar companies appear repeatedly in lists of largest penalties. Meanwhile, thousands of smaller companies commit GDPR violations with minimal fines or warnings, as reported by SentinelOne.
Why this concentration?
Scale of Data Processing: Large tech companies process the personal data of billions of people globally. A single violation affecting their European user base can impact tens of millions of individuals. When regulators calculate fines, they consider the scale of the violation. A data breach affecting 50 million people gets penalized more heavily than one affecting 50,000 people.
Visibility: Tech giants can't operate quietly. Their practices get scrutinized by regulators, journalists, security researchers, and competitors. A privacy violation at Google becomes headline news. The same violation at a small marketing firm might go unnoticed. Visibility drives enforcement.
Market Power and Regulatory Priority: Regulators view large tech companies as powerful market actors whose practices have outsized influence. If Meta violates GDPR, it potentially affects behavior across the entire social media industry. If a small startup commits the same violation, it affects only that startup's users. Regulators logically prioritize enforcement against actors with the most market influence.
Resource Asymmetry: Big Tech has armies of lawyers. They fight regulatory actions aggressively, challenging fines in court, appealing decisions, and demanding extended legal proceedings. This visibility and contestation attracts more regulatory attention. In contrast, smaller companies often accept modest fines to avoid costly legal battles.
Repeated Violations: The same companies appear on the enforcement list repeatedly. Meta has been fined dozens of times for different violations. Google has received major penalties for multiple distinct issues. This pattern suggests that once a company is flagged as a problem actor, regulators scrutinize all its activities more carefully, resulting in more violations being detected and penalized.
For mid-market and small companies, this concentration of penalties presents both risk and opportunity. The risk: you might assume that since you're not a mega-corporation, you'll avoid major fines. The opportunity: regulators currently have limited resources to chase small violations, meaning you have breathing room to achieve compliance without facing million-euro penalties.
Geopolitical Tensions as a Breach Driver
Here's something that typically doesn't get mentioned in corporate compliance discussions: international conflict directly increases data breach risk.
In 2025, rising geopolitical tensions created multiple pathways to increased breaches. Nation-state actors escalated cyber-operations against other countries' critical infrastructure and private sector targets. Proxy forces and private contractors engaged in cyber-warfare. Economic sanctions and counter-sanctions drove companies to take greater security risks to continue operations in restricted markets.
Direct Attacks on Infrastructure: Governments explicitly targeted private company infrastructure as part of broader geopolitical strategies. Power grid attacks, telecommunications disruptions, and targeted breaches of companies in specific sectors became tools of statecraft. European companies found themselves caught in the crossfire between larger powers.
Increased Espionage: Nation-states increased investment in corporate espionage. Rather than stealing military secrets, they focused on intellectual property, competitive information, and market intelligence. Data that would never appear on intelligence agency priorities five years ago suddenly became high-value targets.
Inadequate Preparation: Many companies hadn't planned for the level of cyber-attack sophistication deployed in 2025. Their security assumed typical criminal actors looking for credit card numbers or credentials to sell. Instead, they faced adversaries with nation-state resources, funding, and persistence. The mismatch between assumed threat and actual threat created massive breach opportunities.
Third-Party Compromise: Rather than attacking a big company directly, adversaries compromised smaller vendors serving that company. A threat actor might not be able to breach Google's network, but could compromise a regional ISP serving Google offices, or a business-class software company Google subscribed to. Each compromise created cascade breaches.
This geopolitical dimension matters for your compliance planning. If you operate in sectors considered strategically important (energy, telecommunications, critical infrastructure), you face elevated cyber-attack risk regardless of your security posture. You're being targeted not by criminals looking for profit, but by coordinated state actors with political objectives.

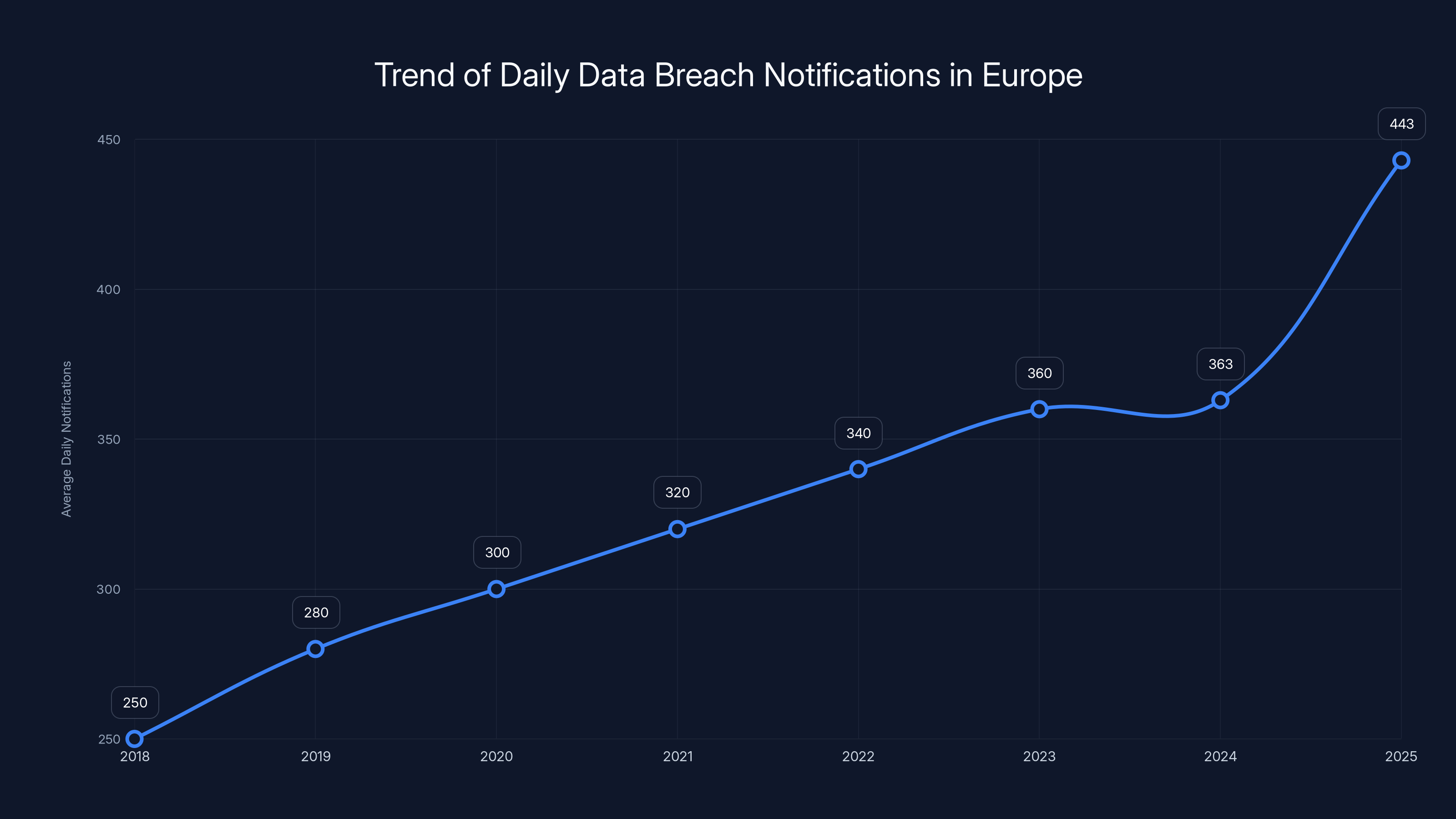
The chart illustrates a significant rise in daily data breach notifications, peaking at 443 in 2025, a 22% increase from 2024. Estimated data for 2018-2023.
New Technologies Weaponized by Threat Actors
2025 saw a fundamental shift in how attackers operate, driven by new technologies that democratized hacking and made sophisticated attacks accessible to moderately skilled adversaries.
Generative AI for Phishing Campaigns: Gen AI made spear-phishing extraordinarily effective. Attackers used large language models to craft personalized phishing emails that sounded exactly like legitimate internal communications. They incorporated company-specific details scraped from public sources, referenced real employees, and matched communication style with uncanny accuracy. Traditional user awareness training proved inadequate against phishing this sophisticated.
The numbers bear this out. In organizations that reported breaches in 2025, phishing represented the initial attack vector in roughly 45% of incidents. That percentage would be far lower if attackers still had to manually write convincing emails.
Vulnerability Discovery Automation: Security researchers and attackers alike gained access to AI-powered vulnerability scanning tools that could analyze code, network configurations, and system setups far more comprehensively than manual approaches. When an attacker gained initial network access (usually through phishing), they could rapidly scan for exploitable weaknesses across the entire infrastructure, identifying security gaps that human-based assessments might miss.
Exploit Automation Frameworks: Once a vulnerability was identified, attackers didn't need to manually develop exploits. Framework systems like Metasploit (and newer competing tools) provided pre-built exploits for thousands of known vulnerabilities. An attacker with basic scripting knowledge could weaponize those exploits. The barrier to entry for conducting sophisticated attacks dropped dramatically.
Credential Stuffing at Scale: Attackers obtained massive databases of compromised usernames and passwords from previous breaches, then used automated tools to test those credentials against thousands of companies' VPN systems, cloud services, and web applications. A single reused password that users employed at multiple services created instant access to corporate networks.
For organizations, this technological shift meant that traditional security approaches became obsolete. Perimeter defenses, firewalls, and intrusion detection systems caught obvious attack attempts but struggled against sophisticated adversaries using AI-augmented techniques. The technical difficulty of breaking into well-defended networks dropped while the sophistication of available attacks increased.
New Laws and Incident Notification Requirements
Paradoxically, stricter privacy laws contributed to the spike in reported breaches. Not because more breaches occurred, but because more breaches had to be reported.
The EU expanded incident notification requirements in 2024 and 2025, requiring organizations to report specific categories of breaches that previously fell into gray areas. Where an organization might have previously conducted an internal investigation and forgotten about a minor incident, they now had legal obligations to notify regulators within specific timeframes.
Expanded Notification Thresholds: Regulators lowered the bar for what constitutes a "reportable breach." Previously, an organization might not report an incident affecting 100 people if the data didn't include financial information. Under new requirements, certain types of data became reportable in even small quantities. Behavioral data, health information, location data, and other sensitive categories triggered notification obligations even when affecting small populations.
Mandatory Reporting Timelines: Organizations faced strict deadlines for notifying regulators. Previously, companies had flexibility in timing. Under updated requirements, many had to report within 72 hours of discovering a breach. This compressed timeline forced organizations to report breaches while investigations were still ongoing, sometimes before they fully understood what happened.
Public Disclosure Requirements: More breaches required not just regulatory notification but public disclosure to affected individuals. Organizations couldn't quietly pay settlement fees and move on. They had to announce breaches publicly, creating media attention and regulatory scrutiny.
These legal changes artificially inflated breach notification numbers. The 22% increase in reported breaches partly reflects more breaches actually occurring, but also reflects previously unreported breaches being forced into the notification pipeline by stricter legal requirements.
For compliance purposes, this means that improving your breach detection and response capabilities directly increases your regulatory reporting burden. Better security means fewer breaches, but also means that breaches you do detect are more likely to meet notification thresholds. You can't simultaneously improve breach detection and reduce regulatory reporting requirements.
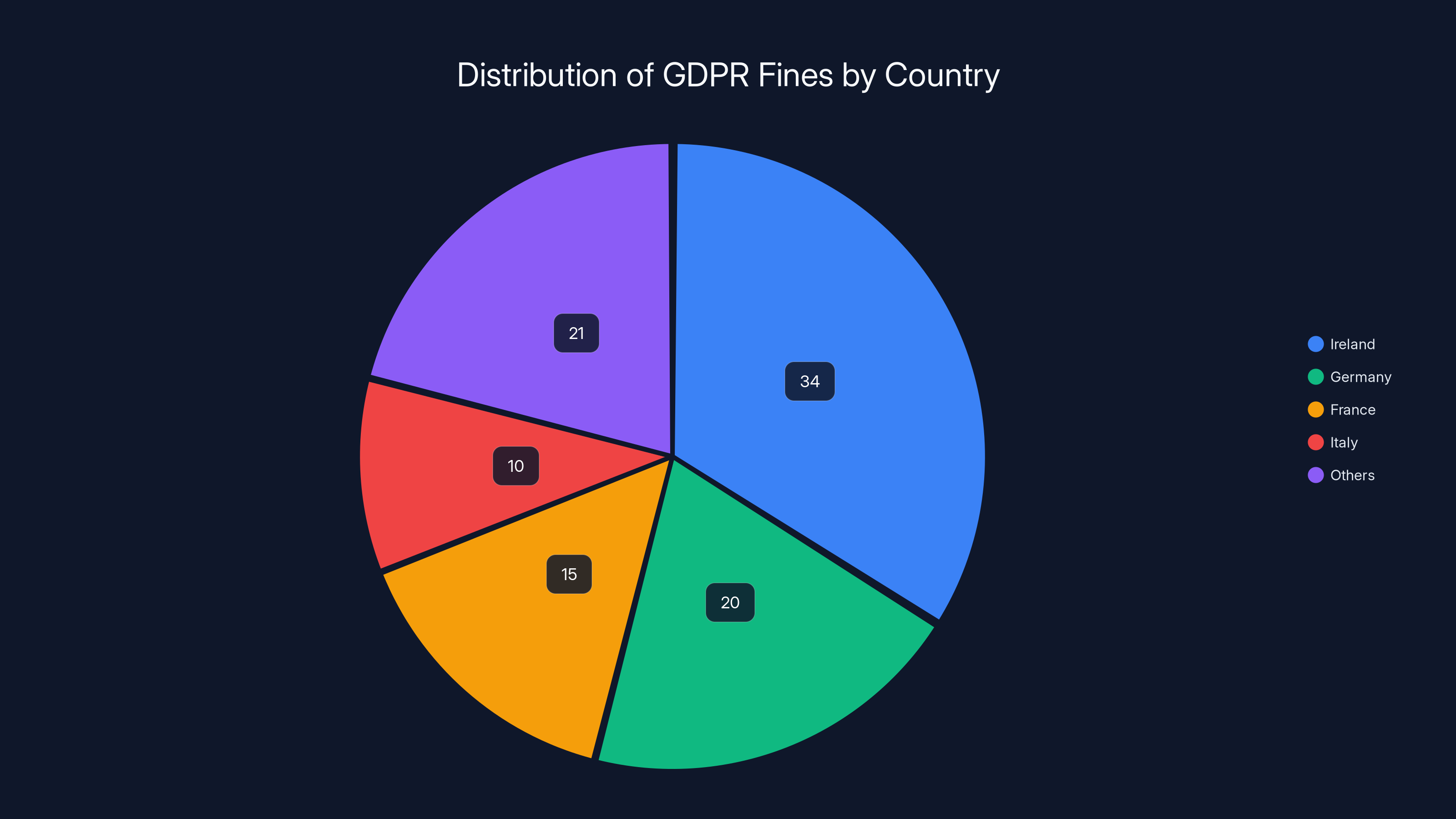
Ireland accounts for 34% of global GDPR fines, highlighting its aggressive regulatory stance, especially against big tech companies. Estimated data.
Supply Chain Breaches and Third-Party Risk Explosion
One of the most consequential developments in 2025 was the pattern of breaches propagating through supply chains.
Organizations increasingly discovered that their own security posture mattered less than their vendors' security. A breach at a single third-party service provider could compromise dozens of client organizations simultaneously.
Managed Service Provider Compromises: Companies specializing in IT management for mid-market clients fell victim to sophisticated attacks. When these service providers were compromised, their clients faced cascading breaches. A criminal organization that successfully penetrated one MSP's network gained access to the infrastructure of dozens of client companies simultaneously.
Think about the regulatory implications. If your organization contracts with an MSP and that MSP gets breached, your organization likely faces GDPR obligations to notify regulators and affected individuals. You can't claim that the breach wasn't your responsibility because a vendor was negligent. Under GDPR Article 28, you remain liable even for vendor breaches.
Software Supply Chain Vulnerabilities: Vulnerabilities in widely-used business software created massive attack surface. A vulnerability in a popular accounting software, email platform, or CRM system could compromise thousands of organizations using that software. In several 2025 incidents, software vendors released patches for vulnerabilities that attackers had already exploited against production systems. Organizations running older versions discovered breaches weeks or months after the vulnerability was disclosed.
Hardware Supply Chain Contamination: Some breaches traced back to compromised hardware. Threat actors had modified network switches, routers, or other infrastructure before it was delivered to organizations. Once installed, the compromised hardware provided persistent backdoor access.
Cloud Provider Incidents: Several major cloud providers experienced incidents that exposed customer data. When your critical data lives in cloud infrastructure and that infrastructure gets breached, your organization immediately faces incident response obligations regardless of the provider's security measures.
For your organization, supply chain risk means that perfect internal security isn't sufficient. You must audit vendors, validate their security controls, establish incident notification requirements in contracts, and maintain incident response plans for vendor breach scenarios.
Calculate the math: if you use 50 different software vendors, each with a 10% annual probability of suffering a material security incident, your probability of facing at least one vendor breach increases substantially. Most organizations significantly underestimate third-party risk because it's not under their direct control.
Regulatory Strategy: Selective Enforcement for Maximum Impact
Despite stable fine totals, 2025 demonstrated a shift in regulatory strategy. Authorities moved from broadly distributed, modest penalties toward concentrated, blockbuster fines designed to create maximum deterrence.
Bigger Fines Against Bigger Players: The €530 million Tik Tok fine exemplifies this strategy. Rather than issuing moderate fines against dozens of platforms, regulators issued a headline-grabbing penalty that created international news coverage. The message was clear: platform companies face massive exposure for specific violations.
Targeted Sector Focus: Different regulators prioritized different sectors. Some focused heavily on financial services, others on technology platforms, still others on healthcare providers. Organizations in unfocused sectors sometimes got minimal scrutiny despite serious compliance gaps.
Precedent-Setting Cases: Regulators brought enforcement actions not just to punish specific violations but to establish interpretations of GDPR that would guide future compliance. When Irish authorities fined Meta for data transfer practices, they signaled that similar practices across the industry would face similar treatment.
Resource Constraints: European regulators operate with limited budgets and staff. They can't investigate every breach or violation. Instead, they strategically focus resources on investigations that will generate maximum deterrence effect. One major fine against a famous company creates more compliance behavior change than dozens of smaller fines against unknown companies.
This selective enforcement creates an incentive structure that favors smaller companies. As long as you're not operating at scales that attract regulatory attention, compliance risk is lower. But as your company grows, your regulatory exposure increases non-linearly. You move from likely being ignored to potentially being a focus of regulatory attention.
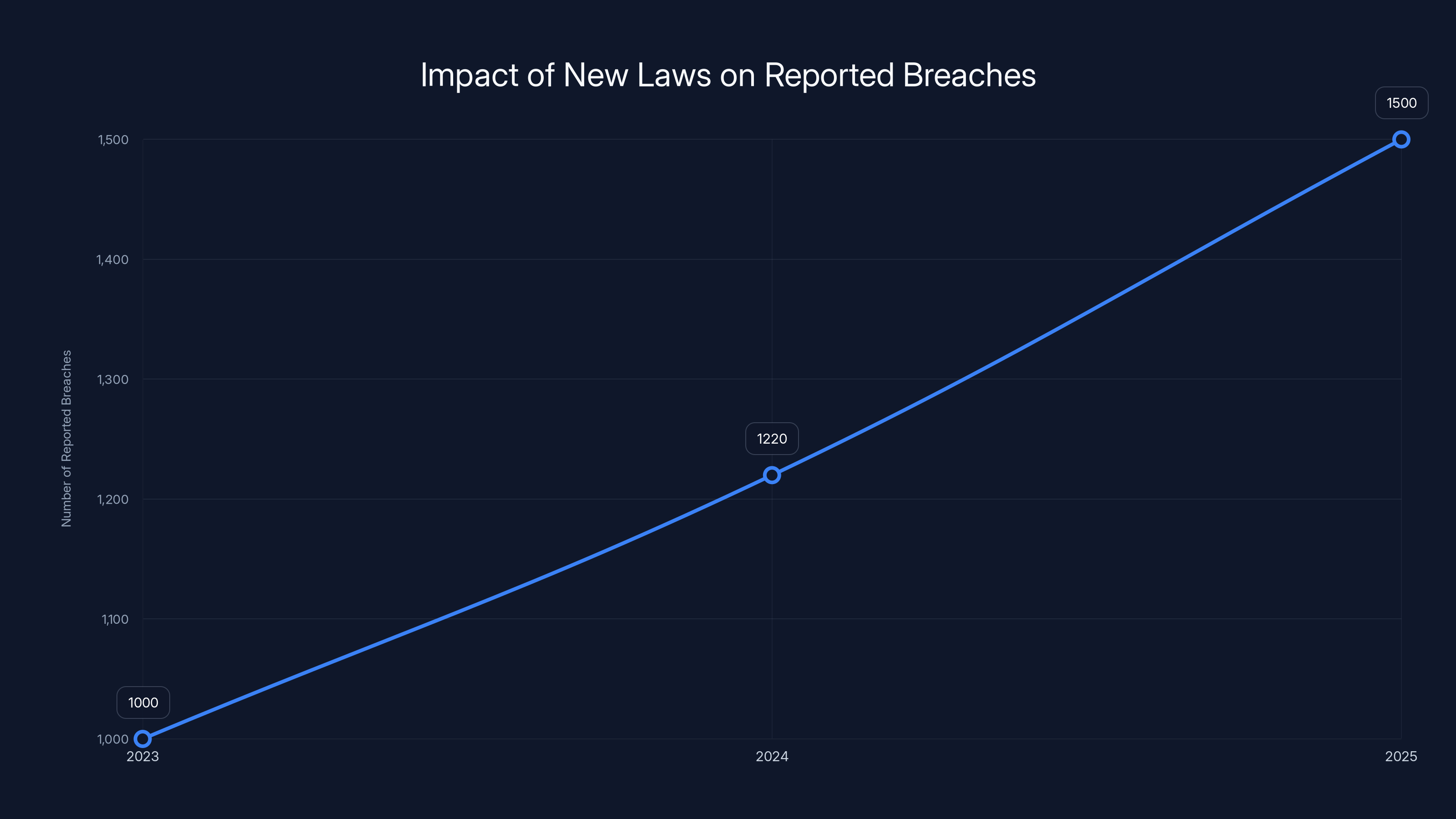
The introduction of stricter notification requirements in 2024 and 2025 is estimated to have increased reported breaches by 22% in 2024 and further in 2025. Estimated data.
Tik Tok's €530 Million Fine: A Case Study in Regulatory Strategy
The Tik Tok fine deserves detailed examination because it exemplifies 2025's regulatory approach.
Irish authorities fined Tik Tok €530 million for multiple violations related to child safety, data protection of minors, and processing practices. The fine was unprecedented for a social media platform, signaling that regulators would treat child protection violations as among their highest priorities.
What Tik Tok Did Wrong: Tik Tok processed extensive data about minors without adequate safeguards. The platform collected behavioral data, location information, and usage patterns from users identified as under 18 years old. The company's systems for distinguishing adult from minor users proved inadequate. The company failed to implement technical and organizational measures appropriate for processing data of young people.
Why This Fine Mattered: The Tik Tok fine established a precedent. Every social media platform, messaging app, and user-generated content platform now understands that inadequate child protection mechanisms carry enormous financial exposure. The fine was large enough to impact business decisions, not merely absorbed as a cost of operations.
Regulatory Doctrine Shift: The fine reflected a shift in regulatory thinking. Rather than treating child data protection as one GDPR compliance requirement among many, regulators began treating it as a primary enforcement priority. Organizations processing data involving minors face elevated scrutiny and exposure to severe penalties.
Messaging Beyond the Fine: Regulators used the Tik Tok fine to send messages to policymakers, other platforms, and international observers. The message: the EU takes child safety seriously and will use regulatory power to enforce protection requirements, even against powerful international companies.
For your organization, the lesson is that regulatory enforcement priorities shift. What's a secondary compliance concern one year might become a primary focus next year. Building flexible compliance infrastructure and monitoring regulatory announcements keeps you ahead of enforcement trends.

The Data Breach Notification Pipeline: From Incident to Report
Understanding the 443 daily breach notifications requires understanding what happens after a breach occurs.
When an organization discovers a breach, it doesn't immediately appear in regulatory statistics. Instead, it enters a multi-week pipeline involving investigation, notification, and regulatory reporting.
Discovery Phase: An organization discovers an intrusion through intrusion detection systems, security monitoring, user complaints, or third-party disclosures. The discovery triggers formal incident response procedures.
Investigation Phase: The organization determines what data was accessed, how long the attacker had access, and whether the data poses risk to affected individuals. This investigation often takes weeks. The organization must preserve evidence, analyze logs, interview staff, and reconstruct the attack.
Notification Decision Phase: The organization assesses whether the breach meets notification thresholds. Does it affect enough people? Does it involve sensitive data? Does it pose real harm risk? This assessment determines whether regulatory notification is required.
Regulatory Notification Phase: If notification is required, the organization submits formal incident notification to relevant data protection authorities. Timelines vary by jurisdiction but often require reporting within 72 hours of discovery.
Public Disclosure Phase: If affected individuals number above certain thresholds, the organization publishes public breach disclosures. This timing often lags regulatory notification.
Post-Breach Phase: Regulatory authorities may initiate investigations into the breach, requesting additional information and evaluating whether the organization violated GDPR requirements.
The 443 daily notifications represent incidents at various stages of this pipeline. Some are fresh discoveries just reported to regulators. Others are breaches reported weeks or months earlier that reached the regulatory system after investigation.
For your organization, understanding this pipeline helps you prepare. When you discover a breach, you'll have a compressed timeline (often 72 hours) to investigate, assess notification requirements, and report to regulators. Preparation during non-breach times makes this timeline achievable. Improvisation during an active incident makes it nearly impossible.

Sector-Specific Impact: Healthcare, Finance, and Technology
Not all sectors experienced equal breach increases in 2025. Different industries faced different threat landscapes and regulatory priorities.
Healthcare: Medical organizations faced sophisticated ransomware attacks combined with new emphasis on protecting health data. When attackers encrypted healthcare systems, hospitals faced dual pressure: restore service immediately or risk patient harm, or comply with attacker demands quickly. This pressure often resulted in ransoms being paid before full breach assessment occurred. Healthcare organizations faced increased GDPR fines for inadequate security measures that made them vulnerable to ransomware. Several major hospital networks reported breaches affecting millions of patient records.
Financial Services: Banks, insurance companies, and fintech services experienced targeted attacks as attackers recognized the value of financial data. Regulatory attention intensified on financial sector GDPR compliance. Several banks were fined for inadequate controls around third-party vendor access. The sector saw increased focus on authentication security, multi-factor authentication gaps, and credential management.
Technology and Saa S: Cloud providers and Saa S companies faced dual burden: their own security vulnerabilities exposed their own customers' data, and they were often implicated in supply chain compromises affecting other companies. Several major incidents in 2025 involved Saa S provider compromises that cascaded to affect thousands of customer organizations.
Retail and E-Commerce: E-commerce companies experienced both direct attacks targeting payment data and supply chain compromises affecting connected services. The expansion of digital commerce created expanded attack surfaces. Several major retailers discovered breaches affecting millions of customers' payment card information.
Manufacturing: Industrial companies increasingly connected operational technology (OT) systems to information technology (IT) networks for integration purposes. This integration created new attack surfaces. Breaches affecting manufacturing operations sometimes resulted in the destruction of intellectual property and production delays alongside regulatory exposure.
Different sectors also faced different regulatory enforcement intensities. Healthcare has historically received high regulatory attention for breaches affecting sensitive health information. Financial services faces rigorous oversight around security controls and fraud prevention. Technology companies face enforcement focused on data transfer mechanisms and vendor management.

Compliance Costs and the ROI Question
With €1.2 billion in fines, organizations might assume that compliance investments are justified by cost avoidance. The math is more complex.
The €1.2 billion total was concentrated in a handful of massive fines. Most breached organizations faced no regulatory fines at all. Many settled violations through commitments to improve practices rather than financial penalties. Only organizations meeting specific criteria (processing large-scale data, operating in prioritized sectors, failing to demonstrate good-faith compliance efforts) faced major financial exposure.
Compliance Investment vs. Risk: Your organization should calculate compliance investment based on your actual breach probability and realistic fine exposure. A small healthcare provider with 5,000 patient records faces different risk profile than a large platform processing millions of users' data. Compliance spending should scale accordingly.
Breach Prevention Value: The strongest financial case for compliance spending is breach prevention. Every breach prevented eliminates notification costs, regulatory investigation costs, legal fees, and potential fines. For many organizations, breach prevention value exceeds fine avoidance value.
Operational Resilience: Paradoxically, GDPR compliance investment often improves operational resilience against broader cyber threats. Encryption, access controls, logging, and security monitoring—all required for GDPR compliance—also protect against ransomware, theft, and sabotage. The compliance investment delivers multiple returns.
Competitive Advantage: Organizations demonstrating strong compliance may attract customers prioritizing data protection. Companies losing competitive bids due to weak security posture gain competitive advantage from compliance improvements.
Calculate your compliance ROI formula:
For most organizations, this formula yields positive ROI even excluding fine avoidance. Adding fine avoidance value improves the ROI further.

Building a Compliance Infrastructure for 2025 and Beyond
Given the 2025 threat landscape, what specific steps should organizations take?
Data Inventory and Classification: Start with comprehensive understanding of what personal data you process, where it's stored, who accesses it, and what safeguards protect it. Without this foundation, all other compliance efforts are guesswork.
Breach Detection and Response: Implement detection systems that identify breaches faster than manual discovery. Establish incident response procedures that let you notify regulators within required timeframes. Test these procedures regularly.
Vendor Management: Audit your significant vendors' security practices. Establish contractual requirements for incident notification. Maintain plans for responding to vendor breaches affecting your systems.
Access Control: Implement the principle of least privilege across your organization. Users should access only data needed for their specific role. Strong authentication, particularly multi-factor authentication, prevents credential compromise from creating system access.
Encryption: Encrypt sensitive data at rest and in transit. Encryption limits harm when breaches occur. Even if attackers steal encrypted data, they can't access it without decryption keys.
Privacy by Design: Build data protection into new systems from inception rather than adding it after the fact. When designing new processes involving personal data, incorporate privacy protections into requirements, architecture, and implementation.
Staff Training: Phishing and social engineering represent massive attack vectors. Regular security awareness training that specifically addresses GDPR requirements and breach notification obligations improves employee understanding and reduces breach probability.
Monitoring and Logging: Implement systems that log access to personal data and unusual system activities. These logs prove invaluable during breach investigations. Many incidents go undetected for weeks because organizations lack visibility into data access patterns.

Looking Ahead: 2026 and Beyond
What trends should you watch as regulatory and threat environments continue evolving?
AI Regulation Intersection: The EU is implementing the Artificial Intelligence Act alongside GDPR. Organizations building AI systems must now navigate both regulations. GDPR requires transparency about data processing. The AI Act requires transparency about algorithmic decision-making. The intersection creates complex compliance requirements.
International Data Transfer Scrutiny: Regulations governing data transfers to the United States continue evolving. Future judicial decisions or regulatory actions could create new restrictions on where organizations can process EU resident data. Maintaining flexibility in infrastructure location provides protection against future changes.
Sector-Specific Regulations: Beyond GDPR and the AI Act, specific sectors face growing regulation. Digital Services Act, Digital Markets Act, and other EU regulations add compliance layers beyond privacy protection. Organizations in regulated sectors must integrate multiple regulatory frameworks into compliance programs.
Regulatory Resource Expansion: Regulatory authorities have been pushing for expanded budgets and staff. If successful, enforcement intensity could increase. Greater regulatory capacity means more investigations, more fines, and more compliance scrutiny across more organizations.
Threat Escalation: Nation-state actors and sophisticated criminal organizations continue upgrading their capabilities. AI-augmented attacks will become standard. Organizations failing to maintain pace with threat evolution face increasing breach probability.
Supply Chain Standards: Regulators increasingly view supply chain security as a compliance requirement, not an operational detail. Future regulations may impose explicit standards on vendor security practices. Organizations should begin implementing vendor security standards now rather than waiting for regulatory mandates.
The Sustainability of Current Enforcement Levels
A final question worth considering: can European regulators sustain current €1.2 billion enforcement levels while managing 443 daily breach notifications?
Resourceing constraints suggest that the current approach—high-impact large fines against prominent companies, minimal attention to smaller violations—may be sustainable. Regulators can conduct handful of major investigations while processing thousands of routine notifications through simplified processes.
But if enforcement priorities shift toward broader compliance monitoring and smaller fine distribution, resources could become severely strained. Currently, regulators can afford to focus only on big targets because the return on enforcement effort is high. Extending enforcement to smaller violations requires proportionally more regulatory resources.
For organizations, this suggests a compliance window. If you're currently below regulatory attention thresholds, you have time to improve compliance before enforcement intensifies. But as your organization grows or as regulatory capacity increases, compliance gaps become increasingly expensive.

FAQ
What is GDPR and why do EU fines matter globally?
The General Data Protection Regulation (GDPR) is EU privacy legislation requiring organizations to protect personal data of EU residents with specific safeguards, transparent practices, and user rights. EU fines matter globally because many organizations process EU resident data regardless of location. A company operating outside the EU must still comply with GDPR when handling data of people in the EU, facing potential fines up to €20 million or 4% of annual revenue, whichever is greater. This extraterritorial reach means GDPR affects virtually all organizations handling customer data internationally.
How do the 443 daily breach notifications compare to previous years?
The 443 daily breach notifications represent a 22% increase compared to 2024 and mark the first time notifications exceeded the 400 daily average since GDPR came into force in 2018. This means regulators processed approximately 160,000 breach notifications in 2025, compared to roughly 131,000 in 2024. The increase reflects multiple factors: geopolitical tensions driving more attacks, new technologies enabling more sophisticated breaches, and expanded regulatory requirements mandating reporting of incidents that previously went unreported.
Why do tech companies face the largest GDPR fines?
Tech companies face the largest fines because they process personal data at massive scale. A single violation affecting millions of users gets penalized more heavily than the same violation affecting thousands of users. Additionally, regulators view tech companies as market leaders whose practices influence industry standards, making enforcement against them more impactful. Tech companies also attract regulatory attention due to high visibility, sophisticated legal challenges, and patterns of repeated violations that suggest ongoing compliance problems rather than isolated incidents.
What should organizations do immediately to improve GDPR compliance?
Start by conducting a data inventory: document what personal data you process, where it's stored, and who accesses it. Then implement or strengthen breach detection and incident response procedures to enable timely regulatory notification if breaches occur. Audit your third-party vendors' security practices, particularly vendors accessing sensitive data. Implement multi-factor authentication and encryption for data at rest and in transit. Finally, conduct staff training focused on GDPR requirements and breach notification obligations, with particular emphasis on preventing phishing attacks that constitute the most common breach vector.
How can organizations calculate their likely GDPR fine exposure?
GDPR fines scale based on violation severity and revenue impact. For intentional violations, fines reach up to €20 million or 4% of annual global revenue, whichever is greater. For negligent violations, the cap is €10 million or 2% of revenue. Regulators also consider factors including: number of affected individuals, data sensitivity, duration of violation, organization size, compliance history, and whether the violation was reported voluntarily or discovered by regulators. Most organizations won't face major fines, but companies processing millions of EU residents' data and demonstrating compliance negligence face substantial exposure. Calculate your potential fine as a percentage of annual revenue to understand realistic exposure.
What role do geopolitical tensions play in breach trends?
Geopolitical tensions increase breach risk through multiple mechanisms. Nation-state actors conduct targeted cyber-espionage against companies in strategic sectors. Conflict creates urgency causing organizations to accept security risks they'd normally reject. Sanctions regimes force companies to find workarounds that bypass normal security controls. Proxy forces and criminal actors conducting operations funded by competing nations escalate sophistication and frequency of attacks. Additionally, conflict diverts defensive resources. Companies operating in regions affected by conflict must shift cybersecurity budgets toward defensive measures, reducing capacity for proactive compliance and security improvements elsewhere.
How do third-party vendor breaches affect organizational GDPR liability?
Under GDPR Article 28, organizations remain liable for data breaches affecting data processed by vendors acting on the organization's behalf. If your vendor gets breached, you must notify regulators and affected individuals as if the breach occurred in your own systems. You can't delegate GDPR compliance responsibility to vendors. However, you can demonstrate that you selected vendors carefully, established security requirements in contracts, and monitored vendor compliance. This due diligence reduces regulatory exposure but doesn't eliminate your liability for vendor breaches. Organizations should maintain incident response plans specifically for vendor breach scenarios.
What compliance investments deliver the highest ROI for organizations?
For most organizations, breach prevention delivers higher ROI than fine avoidance. Preventing a single major breach saves notification costs, investigation costs, legal fees, customer relationship damage, and potential fines. Investments in detection systems, access controls, and encryption protect against breaches generally, not just GDPR violations. These investments therefore provide multiple returns: GDPR compliance, operational resilience, ransomware protection, and data security. For organizations with limited compliance budgets, prioritizing breach prevention over exhaustive GDPR documentation typically delivers superior value. Pair breach prevention investments with vendor management, since third-party compromises represent major breach vectors.
How should organizations approach data transfer outside the EU?
Transferring personal data of EU residents outside the EU requires specific legal mechanisms. The Standard Contractual Clauses (SCCs) provide the current framework, but their validity faces ongoing legal challenges. Organizations must conduct transfer impact assessments evaluating whether recipient countries' laws provide adequate protection. United States data transfers face particular scrutiny due to legal access by US government agencies. Organizations should regularly review transfer mechanisms, monitor legal developments, and maintain flexibility to adjust processes if current transfer mechanisms become invalid. For sensitive data, consider whether processing can occur within the EU, eliminating transfer requirements.
What indicators suggest an organization will face regulatory enforcement action?
Regulatory enforcement often follows patterns. Organizations attracting enforcement attention typically: process large volumes of EU resident data, operate in prioritized sectors (technology, healthcare, finance), have established compliance problems evidenced by user complaints or previous investigations, or face third-party reports of violations. Additionally, high-profile breaches and public criticism often trigger regulatory scrutiny. Organizations operating quietly in less regulated sectors with modest data volumes face minimal enforcement probability. However, as you grow, your enforcement exposure increases non-linearly. Growth into prioritized sectors or high-volume data processing elevates regulatory risk regardless of compliance quality.

Conclusion
2025 delivered a critical message to organizations handling EU resident data: the threat landscape is escalating faster than most compliance programs improve.
The €1.2 billion in fines sounds dramatic until you understand that it represents enforcement stability despite a 22% explosion in data breaches. That discrepancy reveals the real story: regulators have limited resources and strategic focus. They're not trying to fine every organization. They're trying to deter major actors through high-impact penalties while processing routine violations through administrative procedures.
For your organization, this creates both risk and opportunity. The risk is obvious: if you operate at scale or in prioritized sectors, regulatory enforcement exposure is real. But the opportunity is subtler. Smaller organizations, organizations in less-regulated sectors, and organizations demonstrating genuine compliance efforts still fly largely under enforcement radar. You have time to improve compliance before attention focuses on your sector.
The practical response isn't complicated. Start with the fundamentals: understand your data, detect breaches quickly, respond appropriately to violations, manage vendor relationships, and train staff. These basics prevent most breaches and demonstrate sufficient compliance effort to avoid the harshest regulatory treatment.
Monitor regulatory trends in your specific sector. The enforcement priorities that shaped 2025 may shift in 2026. A sector that received minimal enforcement attention last year might become heavily scrutinized this year. Staying ahead of trends beats scrambling to comply after enforcement intensifies.
Invest in compliance infrastructure that scales with your organization's growth. The compliance program sufficient for a 100-person company doesn't work for a 1,000-person company processing millions of users' data. Building scalable systems early prevents painful redesigns later.
Finally, maintain perspective. GDPR compliance enables you to respect user privacy, build customer trust, and operate sustainably. It's not just regulatory theater. Organizations that view compliance as a fundamental business principle rather than a compliance checkbox build better relationships with customers and face less regulatory friction.
The 443 daily breach notifications and €1.2 billion in fines represent real organizations, real violations, and real consequences. Use them as motivation to implement the compliance practices that keep your organization from becoming the next cautionary tale or regulatory enforcement example.
The time to improve is now, before enforcement priorities shift toward your sector or your organization grows into regulatory focus areas. Build compliance infrastructure today. Your future self will thank you when you're not managing a crisis breach investigation or explaining GDPR violations to regulators.

Key Takeaways
- €1.2 billion in GDPR fines held steady in 2025 despite 22% surge in data breach notifications, showing selective regulatory enforcement focused on high-impact targets
- Ireland's €530 million TikTok fine exemplified shift toward concentrated penalties against major tech platforms, with Ireland accounting for €4.04 billion of all GDPR fines since 2018
- Geopolitical tensions, new attack technologies, and expanded breach notification requirements converged to drive 443 daily breach notifications—unprecedented levels since GDPR inception
- Tech giants face outsized enforcement exposure with 9 of 10 largest GDPR fines targeting major technology companies, signaling regulatory prioritization of market-leading actors
- Organizations should prioritize breach prevention, vendor management, and access controls over exhaustive documentation—practical compliance delivers higher ROI than bureaucratic compliance theater
Related Articles
- TikTok's US Future Settled: What the $5B Joint Venture Deal Really Means [2025]
- Epic and Google's $800M Secret Deal: What It Means for Android [2025]
- Epic vs Google Settlement: What Android's Future Holds [2025]
- Meta's Child Safety Case: Evidence Battle & Legal Strategy [2025]
- UK VPN Ban Explained: Government's Online Safety Plan [2025]
- PcComponentes Data Breach Denial: What Really Happened [2025]
![EU GDPR Fines Hit €1.2bn in 2025: What You Need to Know [2025]](https://tryrunable.com/blog/eu-gdpr-fines-hit-1-2bn-in-2025-what-you-need-to-know-2025/image-1-1769168274329.jpg)



