Under Armour Cyberattack 2025: What 7M Users Need to Know [Complete Guide]
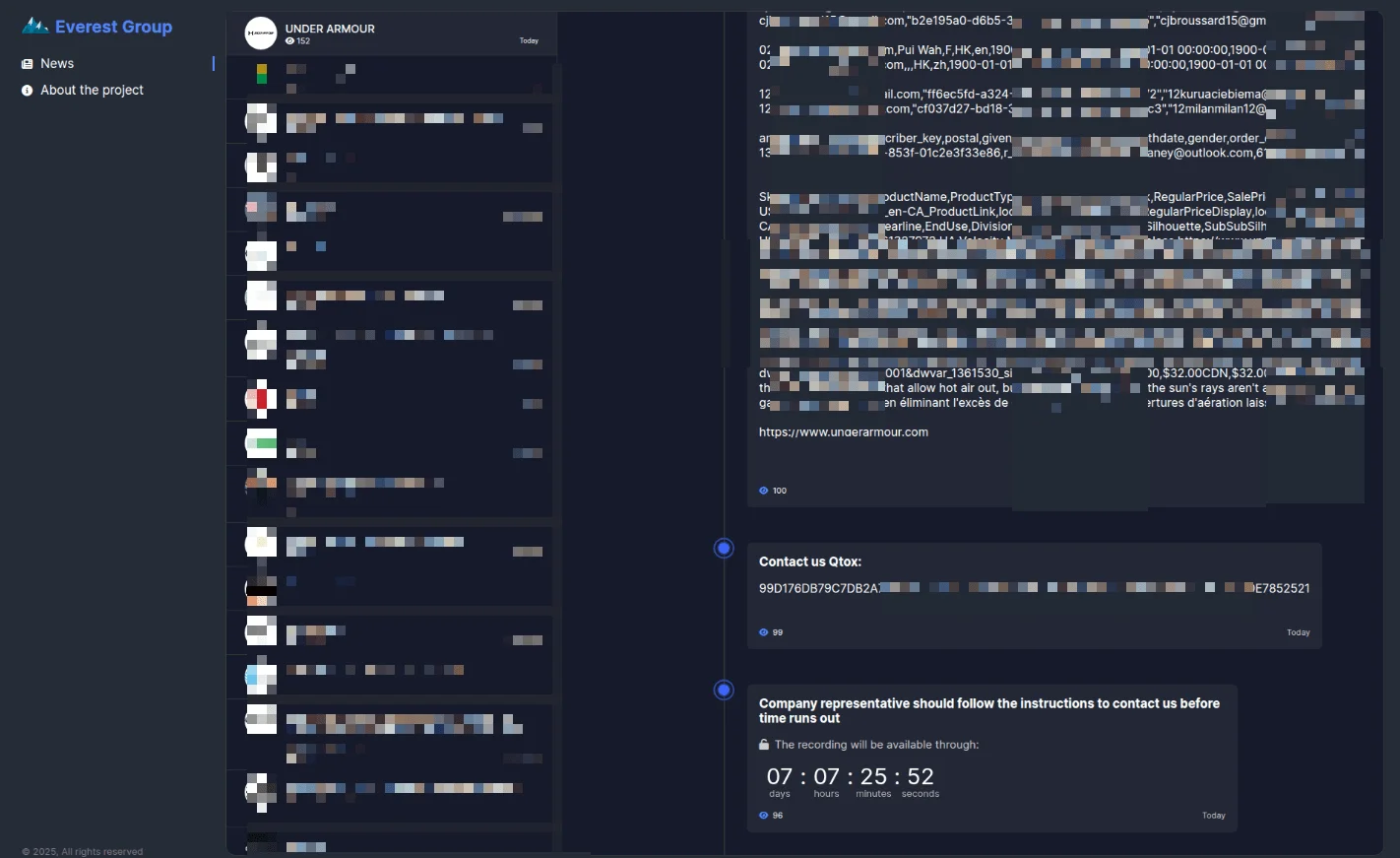
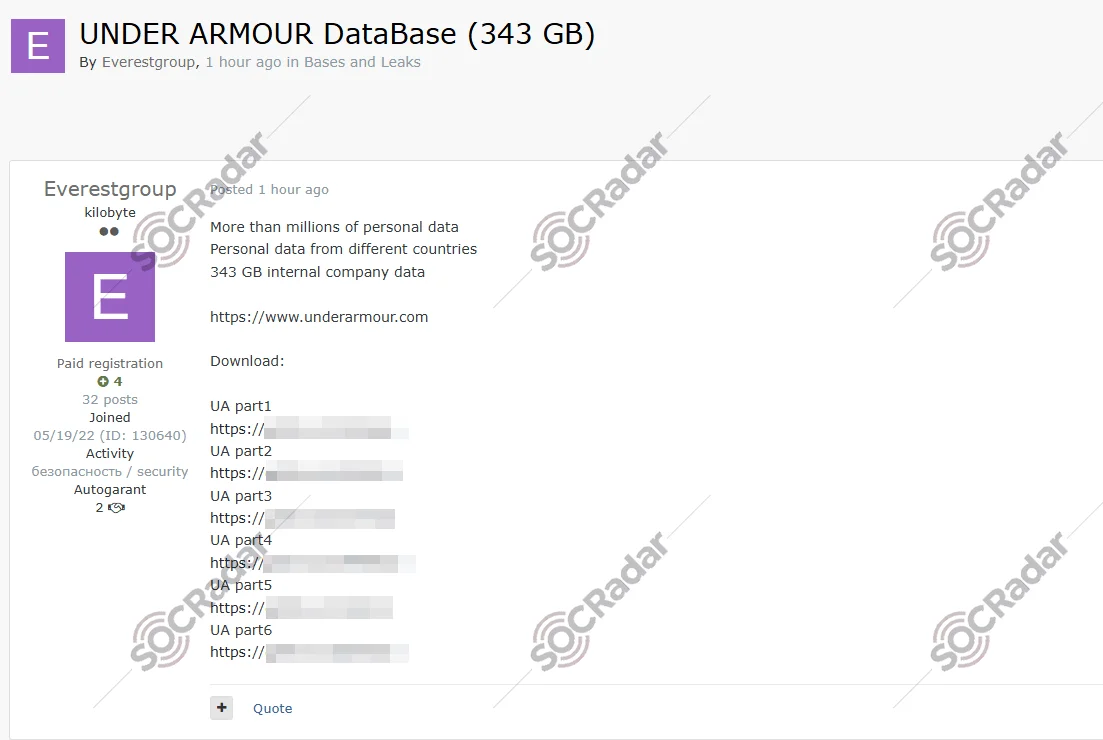
It's the middle of November 2025, and while most of the world was thinking about holiday shopping, a ransomware group called Everest quietly infiltrated Under Armour's systems and walked away with 72.2 million user accounts. Then the company went silent.
No press release. No statement to customers. No apology. Just radio silence while millions of people had their personal information—names, email addresses, birthdates, purchase history, loyalty program details, and possibly phone numbers—sitting in a digital vault controlled by criminals.
If you've ever bought anything from Under Armour, checked their app, or browsed their website while logged in, you need to read this. This isn't one of those breaches you can ignore. The data stolen here is specific, personal, and immediately useful to attackers. We're talking about information that makes phishing emails feel like they came from a friend, not a scammer.
Let's break down what actually happened, who's really at risk, and what you need to do right now to protect yourself.
TL; DR
- The Scale: Everest ransomware group claims to have stolen 72.2 million Under Armour user accounts as reported by The Register.
- What Was Stolen: Names, emails, birthdates, locations, purchase history, and possibly loyalty program details, phone numbers, and postal addresses according to TechRadar.
- The Timeline: Attack happened in November 2025; Everest demanded ransom, Under Armour refused to pay, and the group leaked the data on the dark web as noted by CYFIRMA.
- The Silence: Under Armour has not publicly confirmed or denied the breach as of press time as highlighted by Security Magazine.
- The Legal Action: A class action lawsuit has already been filed on behalf of affected customers as reported by Top Class Actions.
- What You Should Do: Check if your email is in the breach using Have I Been Pwned, enable two-factor authentication on your Under Armour account, monitor credit reports, and consider a credit freeze as advised by NerdWallet.
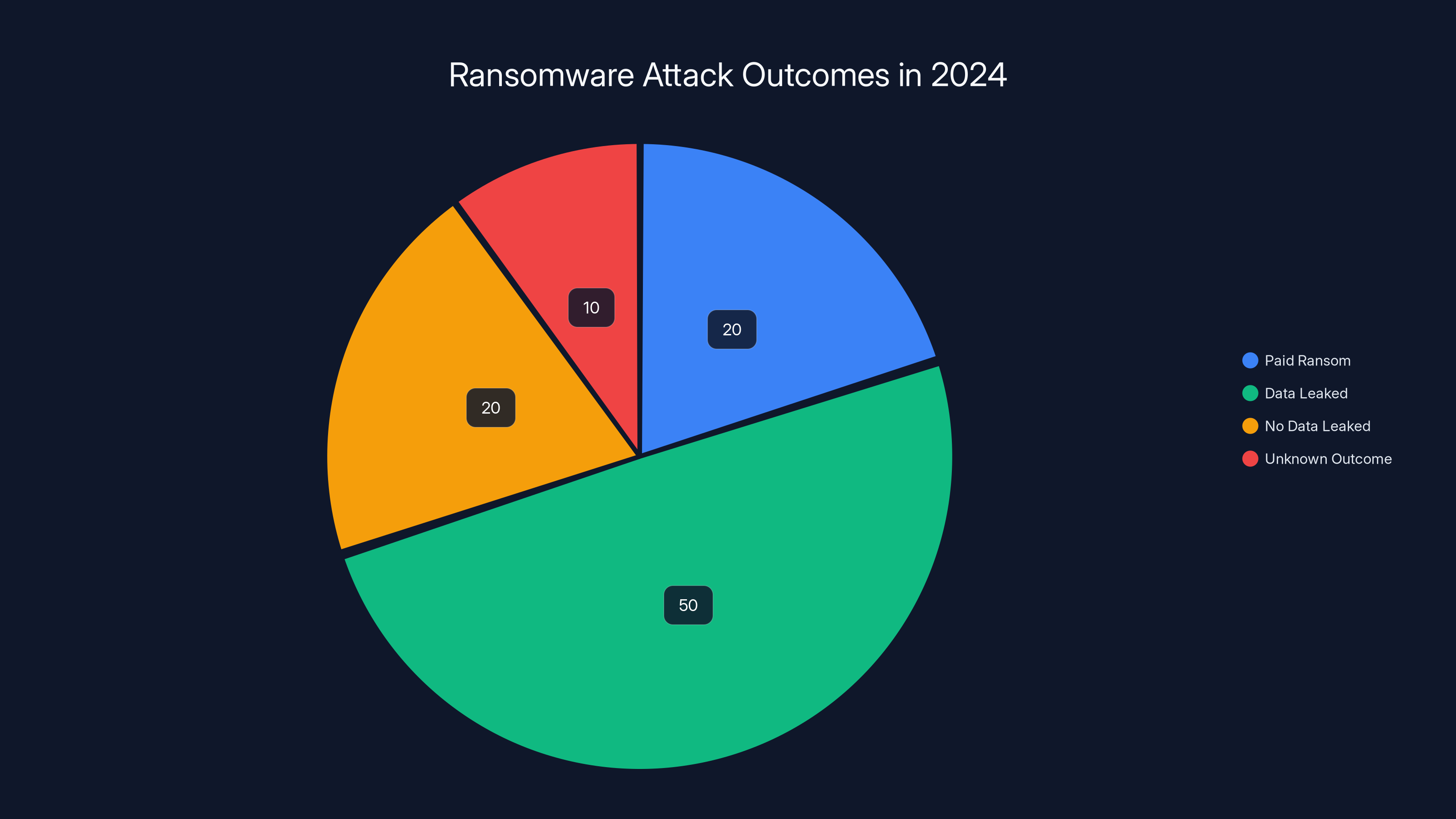
In 2024, an estimated 50% of organizations hit by ransomware had their data leaked, highlighting the prevalence of double-extortion tactics. (Estimated data)
How the Attack Actually Happened
The Under Armour breach didn't happen because of some zero-day vulnerability or advanced persistent threat that nobody could have stopped. It happened because a skilled ransomware operator saw an opportunity and took it.
Everest is what security researchers call a "veteran" ransomware group. This isn't their first rodeo. They've been operating since around 2023 and have hit everyone from healthcare providers to financial institutions. They know what they're doing, and they know what data is worth money as reported by The Register.
What makes Everest different from some other ransomware groups is their playbook. They don't just encrypt your data and demand money. They also exfiltrate sensitive information before locking everything down. This is the old double-extortion technique: pay us to unlock your systems, or we'll sell your customer data to the highest bidder as explained by Help Net Security.
In Under Armour's case, that's exactly what happened. Everest got in, found the customer database, copied 72.2 million records, and left. Then they turned to Under Armour and said: "Hey, pay us, or we're releasing this."
Under Armour apparently decided not to pay. Maybe they couldn't afford it. Maybe they didn't believe Everest actually had the data. Maybe they consulted with law enforcement and decided that paying would just encourage more attacks. Whatever the reason, Under Armour called Everest's bluff.
Everest wasn't bluffing. They leaked the data onto the dark web, where it eventually made its way to security researchers and services like Have I Been Pwned as noted by CYFIRMA.
The timing is interesting. November 2025 is right before the holiday shopping season when Under Armour would normally be making money hand over fist. Hitting them during this period was strategic. They knew Under Armour might be more motivated to pay quickly if their operational systems were locked down during peak sales season.
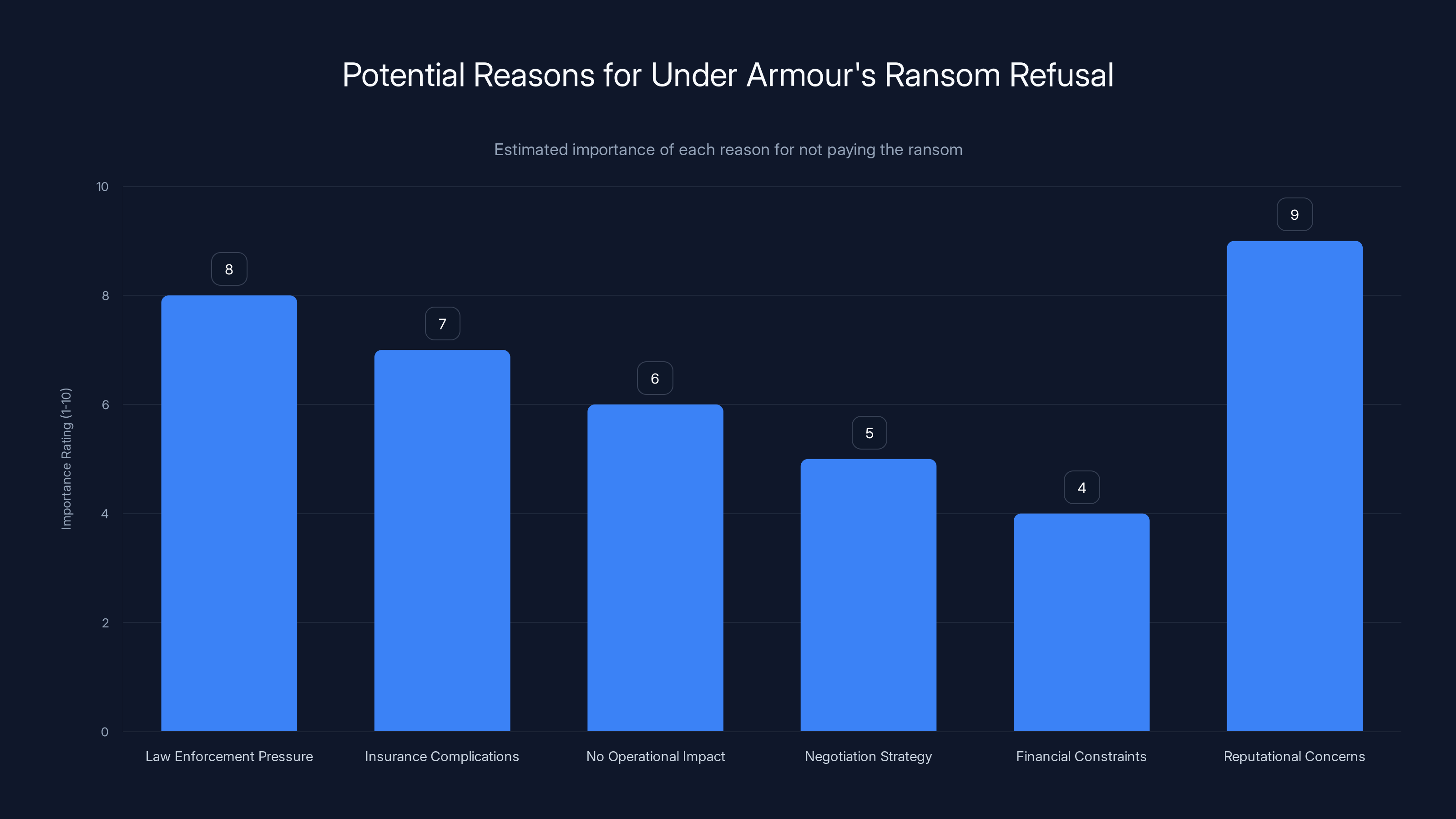
Reputational concerns and law enforcement pressure are estimated to be the most significant reasons for Under Armour's decision not to pay the ransom. Estimated data.
What Data Was Actually Stolen
This is where it gets personal. We're not talking about a list of random usernames. We're talking about a detailed database of real people with specific information that makes them targets for follow-up attacks.
According to Have I Been Pwned and the claims made by Everest, the stolen data includes:
- Full names: Makes phishing emails feel personal and legitimate
- Email addresses: The foundation of modern identity theft and phishing attacks
- Dates of birth: Useful for social engineering and identity verification attempts
- Genders: Helps attackers tailor their approach and craft more convincing phishing messages
- Locations: Physical addresses that can be used for targeted attacks, SIM swaps, or worse
- Purchase history: Shows what you bought, when you bought it, and how much you spent
- Loyalty program details: Your account numbers, accumulated points, and shopping preferences
- Postal addresses: Even more detailed location data
- Phone numbers: Enables SIM swapping, phone-based social engineering, and direct contact from attackers
- Preferred stores: Information about where you like to shop physically
Now, here's the important part: according to Cyber Insider, about 76% of the email addresses in the Under Armour breach were already exposed in previous breaches as reported by HIPAA Journal. That means for most people, their email address isn't exactly new to the hacker ecosystem.
But here's what's changed: those email addresses are now bundled together with incredibly specific personal information that wasn't available before. A hacker might have had your email from some random data breach. But now they have your email, your birth date, your location, where you like to shop, and how much money you spent on athletic gear.
That's a completely different threat profile.
This is why the "76% already exposed" statistic is somewhat misleading. Yes, the emails were already out there. But the supporting data—the stuff that makes a phishing attack actually work—is new and specific to Under Armour.

The Company's Complete Silence
One of the most infuriating aspects of this breach is that Under Armour hasn't said anything. Not a word. No statement. No acknowledgment. No apology. Nothing.
Their newsroom is quiet. Their social media accounts are quiet. Their press team apparently got the message to go dark.
This silence is actually illegal in many jurisdictions. Most U.S. states, the European Union, and many other countries have data breach notification laws that require companies to inform affected customers within a specific timeframe. We're talking days or weeks, not months as noted by HIPAA Journal.
If Under Armour is a public company (and it is), they also have obligations to inform investors about material risks and incidents that could affect their business. This breach definitely qualifies.
So why the silence? There are a few possibilities:
First, maybe they're still investigating. Companies sometimes wait to understand the full scope of an incident before making public statements. They want to know how deep the breach goes, what was actually stolen, and how many people are affected. Getting these details wrong and then having to issue corrections is embarrassing and damages credibility.
Second, maybe they're negotiating with Everest behind the scenes. Perhaps the silence is strategic. If they admit publicly that a breach happened, they lose leverage in negotiations. Criminals might demand a higher ransom if the company acknowledges the incident and faces legal pressure.
Third, maybe they consulted with legal counsel and were advised not to say anything. Some lawyers recommend silence during active investigations to avoid saying something that could be used against the company in court.
Fourth, and perhaps most cynically, maybe they're just hoping it goes away. If enough people don't know about the breach, maybe the legal liability is reduced. This is a terrible strategy, but it happens.
None of these explanations are good. None of them excuse the silence.
What we do know is that a law firm—Chimicles Schwartz Kriner & Donaldson-Smith—has already filed a proposed class action lawsuit on behalf of an affected customer named Orvin Ganesh. The suit alleges that Under Armour failed to protect customer data adequately and failed to notify customers of the breach in a timely manner as reported by Top Class Actions.
This lawsuit is going to cost Under Armour far more than it would have cost to pay Everest. Settlements in major data breach class actions typically range from tens of millions to hundreds of millions of dollars. And that's after the legal fees, the consulting fees, and the cost of the breach notification itself.
Silence isn't protecting Under Armour. It's making everything worse.
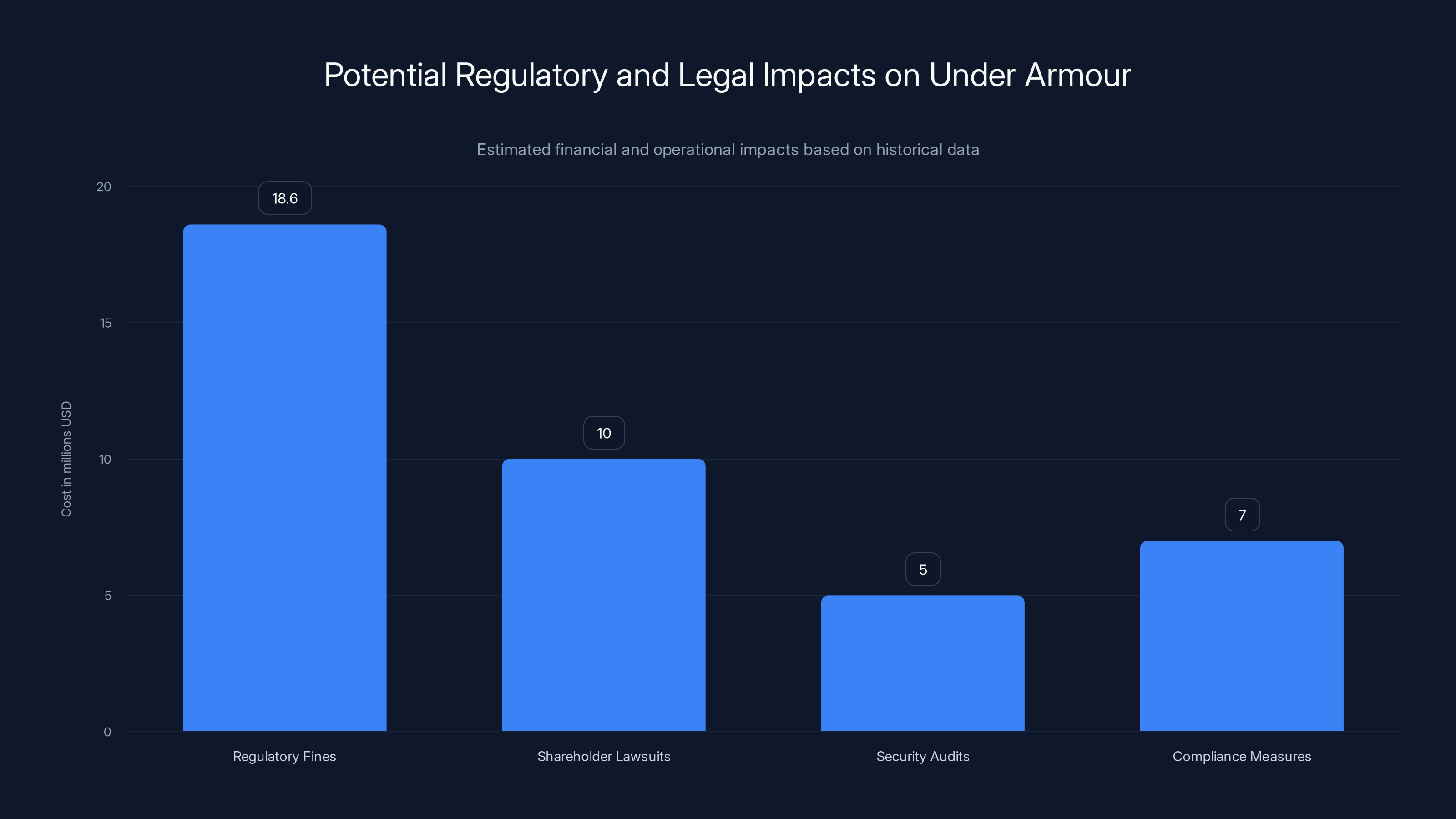
Estimated financial impacts of the Under Armour breach include regulatory fines, shareholder lawsuits, security audits, and compliance measures. These costs are based on similar historical cases. Estimated data.
Who's Actually at Risk
If you've ever had an Under Armour account, you're potentially at risk. That includes people who:
- Bought something from Under Armour's website or mobile app
- Created an account on their website but never made a purchase
- Signed up for their loyalty program (Map My Fitness rewards, for example)
- Registered with Under Armour on Map My Run, Map My Ride, or any of their other fitness apps
- Used any other Under Armour digital property that required an account
That's a massive pool of people. The company serves customers globally, so the affected population spans the United States, Europe, Asia, and beyond.
But not everyone faces the same level of risk. Your personal risk depends on several factors:
Whether your email was already exposed in previous breaches: If your email was already out there, the incremental risk from this breach is lower (but not zero). If this is the first time your email has been compromised, your risk is higher.
How unique your personal information is: If your name is John Smith and you were born on January 1st, it's harder for attackers to use your information to impersonate you. If your name is Shaniqua Jackson and you were born on December 25th, your information is more distinctive and easier to weaponize.
How much money you spend: Attackers often prioritize targets based on spending patterns. If your purchase history shows you spend
What other services you use: If you reuse your email across multiple platforms (which you shouldn't), attackers can use your Under Armour information to target those other accounts.
Your level of digital hygiene: If you keep your passwords unique, enable two-factor authentication, and monitor your accounts regularly, your risk is significantly lower than someone who doesn't.
Here's the harsh reality: if you're in this breach and you reused your Under Armour password anywhere else, that password is now compromised. Attackers will try that password against your email account, your bank account, your social media, everywhere.
The Phishing Threat
With 72.2 million people's personal information now in the wild, the phishing risk has skyrocketed.
Traditional phishing attacks are often obvious. They come from generic email addresses, use poor grammar, and try to trick you into clicking suspicious links. Most people delete them without a second thought.
But sophisticated phishing attacks—the kind that experienced attackers now have the tools to execute—are different. They're targeted, personalized, and specific.
Now that attackers have your name, email address, birthdate, location, and purchase history from Under Armour, they can craft an email that says something like:
"Hi [Your Name], we noticed unusual activity on your Under Armour account from [Some Location] on [Today's Date]. Your recent purchase of [Actual Product You Bought] was flagged as suspicious. Please verify your account immediately by clicking here."
Every single detail is accurate. The date, the location, the product—it all checks out. Your brain's threat detection systems say, "This email seems legitimate. This is from a company I actually do business with, about a transaction I actually made."
You click the link. You enter your password. You've just given attackers direct access to your account.
This is the real threat from this breach. Not the theoretical risk that someone might use your email for spam. The real threat is targeted, convincing phishing attacks that are extremely difficult to spot.
The sophistication of these attacks is about to increase. Attackers will likely combine the Under Armour data with information from other breaches to build even more detailed profiles. They'll know what you bought, where you live, when you made purchases, and what your digital footprint looks like across the internet.

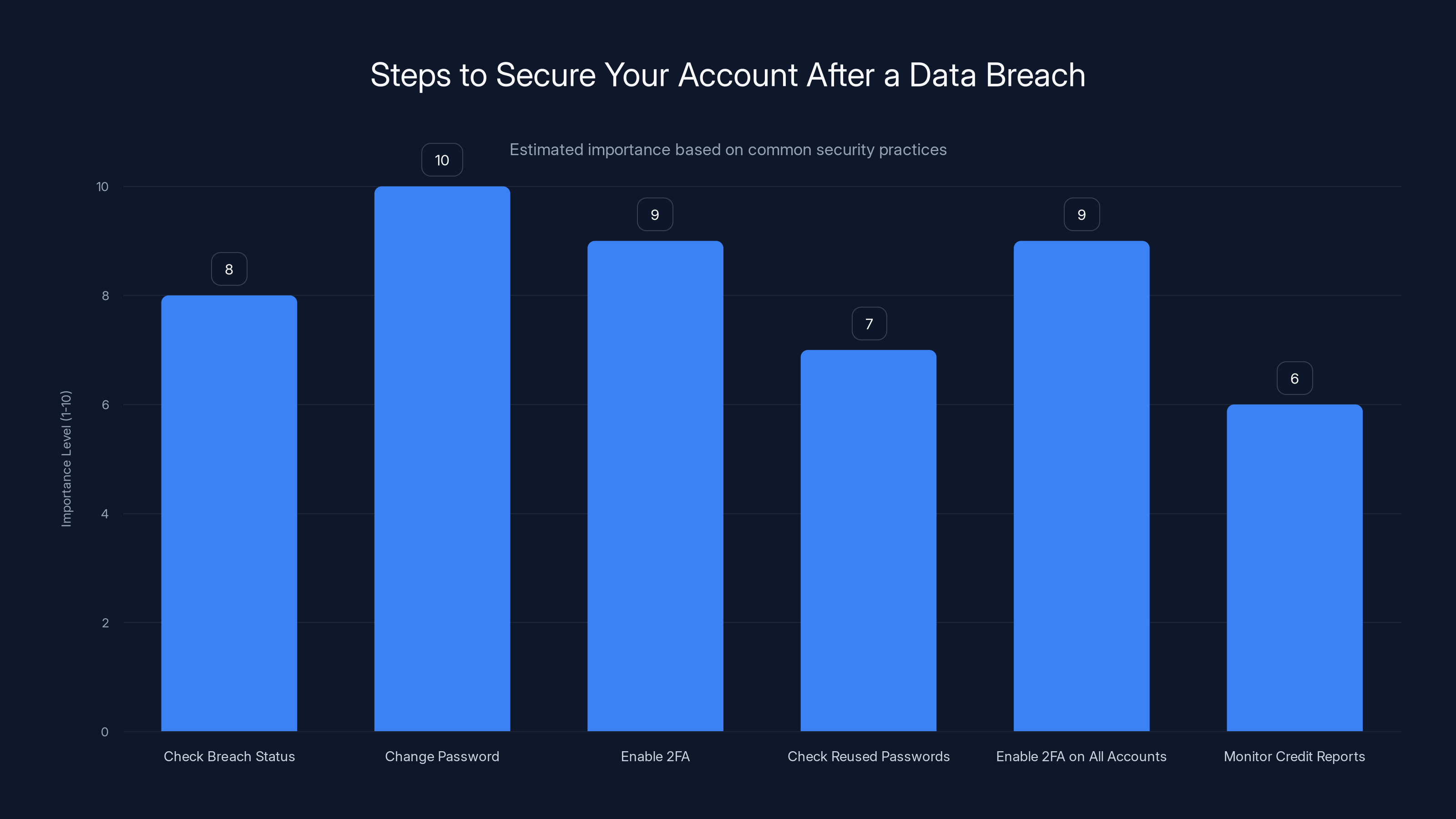
Changing your password and enabling two-factor authentication are the most critical steps to secure your account after a data breach. Estimated data.
How Under Armour's Systems Got Compromised
We don't have official details from Under Armour about exactly how Everest got in. The company hasn't released a detailed post-mortem, and they might never. But based on what we know about how Everest operates and what generally causes breaches of this scale, we can make some educated guesses.
The most common entry points for ransomware attacks like this are:
Exposed credentials: Someone at Under Armour had credentials (username and password) for a critical system. Those credentials were exposed in a previous breach, leaked on the dark web, or obtained through social engineering. Attackers either bought them or found them, and then used them to log into Under Armour's systems.
Unpatched vulnerabilities: Under Armour might have been running software with known security vulnerabilities that nobody bothered to patch. These vulnerabilities are public knowledge, and attackers actively scan the internet looking for systems that haven't been updated.
Poor access controls: Critical systems might have been accessible without proper authentication or from external networks. This is surprisingly common—companies sometimes expose database management tools or administrative interfaces to the internet without proper firewalls or access restrictions.
Phishing: An Under Armour employee might have clicked a malicious link in an email and installed malware on their computer. That malware gave attackers a foothold inside Under Armour's network.
Compromised third-party access: A vendor or partner company that had access to Under Armour's systems might have been compromised first, giving attackers a path into Under Armour's network.
Insecure APIs: Under Armour's mobile apps, website, or other services might have been making calls to backend systems through poorly secured APIs. Attackers could intercept these calls or exploit them to access the database directly.
Once inside, Everest probably spent time moving laterally through Under Armour's network, finding the customer database, accessing it, and copying the data. This process might have taken days or weeks. The longer an attacker stays inside a network without being detected, the more damage they can do.
The fact that Everest successfully exfiltrated 72.2 million records without being detected for long suggests that Under Armour's detection and response capabilities might not have been strong. Companies with mature security programs typically detect lateral movement and data exfiltration much faster.

The Everest Ransomware Group
Everest didn't just appear out of nowhere. This is a known threat actor that's been conducting targeted ransomware campaigns for years.
Everest emerged around 2023 and has been attributed to numerous high-profile attacks across multiple industries. They target organizations in healthcare, finance, manufacturing, retail, and technology. They're not indiscriminate—they carefully select targets based on company size, industry, and perceived ability to pay as reported by The Register.
What makes Everest distinctive is their operational security. They maintain active communication channels with victims. They have a data leak site where they publish information about companies that don't cooperate. They often appear to follow through on their threats, which gives them credibility in the criminal underworld.
Everest also seems to have access to sophisticated tools and techniques. Their ransomware is customized, their lateral movement is careful and deliberate, and their data exfiltration is large-scale and efficient. This isn't the work of amateurs or script kiddies. This is the work of a professional criminal organization.
They've also demonstrated willingness to work with other criminal groups. In some cases, they've partnered with affiliates who conduct the initial breach, then hand off to Everest for the ransomware deployment and negotiation phase. This division of labor allows them to scale their operations and conduct more attacks simultaneously.
The fact that Everest targeted Under Armour suggests they believed the company could pay a significant ransom. Under Armour is a multi-billion-dollar enterprise with the financial resources to fund a cybersecurity response budget. To a ransomware group, that's a high-value target.

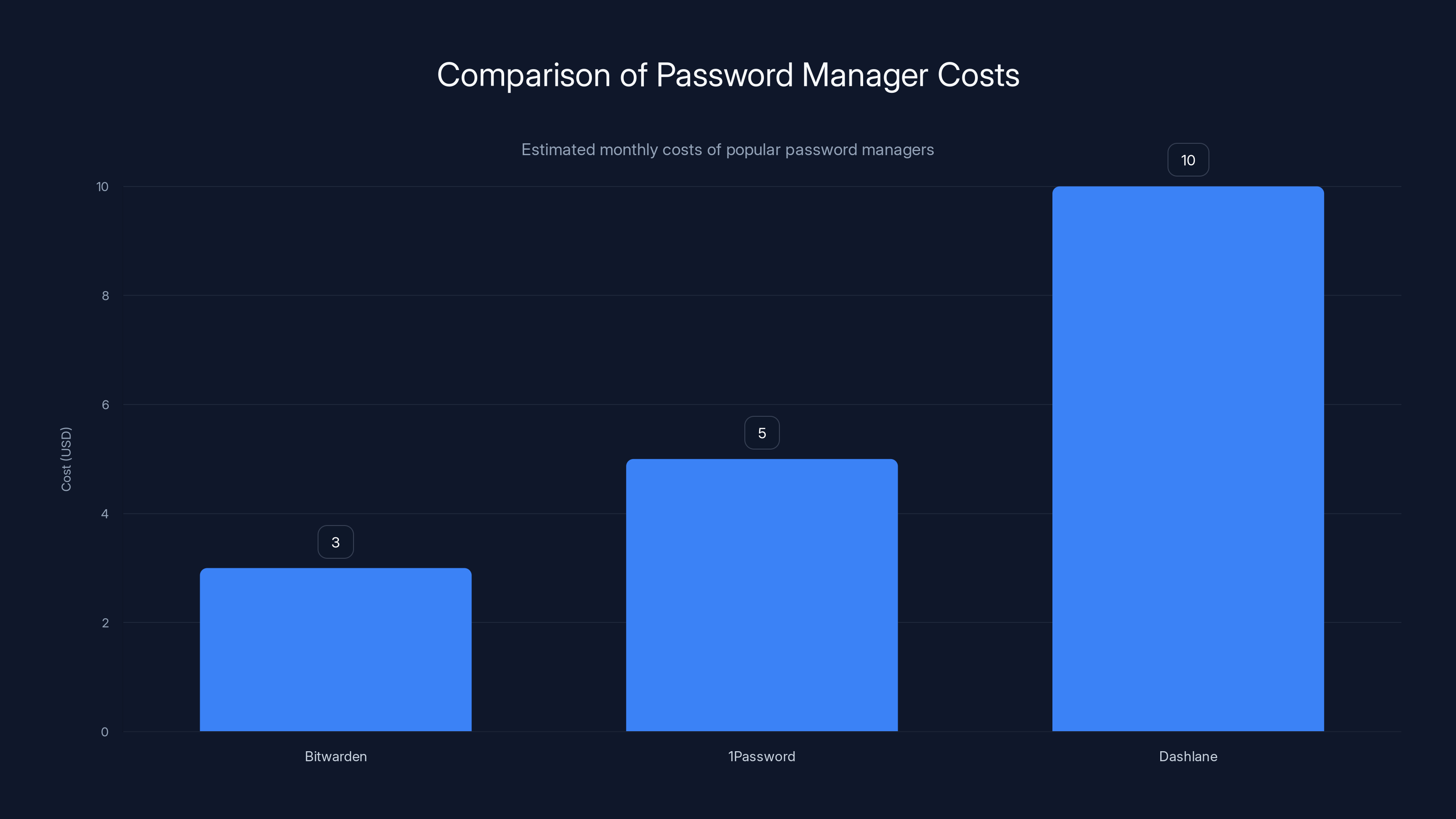
Estimated data shows that Bitwarden is the most affordable password manager at
Why Under Armour Likely Refused to Pay
We're speculating here, but there are several reasons why Under Armour might have decided not to pay Everest's ransom demand:
Law enforcement pressure: The FBI and other law enforcement agencies have increasingly been pressuring companies not to pay ransoms. Paying ransoms funds criminal enterprises and incentivizes more attacks. Under Armour might have decided to make a public stance against paying criminal actors.
Insurance complications: Under Armour's cyber insurance policy might have limitations on ransom payments, or the insurer might have advised against paying. Insurance companies are increasingly refusing to cover ransoms for certain types of attacks.
No operational impact: Unlike a healthcare provider where ransomware could literally stop people from getting medical treatment, Under Armour is an e-commerce and apparel company. They could probably continue operating even with compromised systems. This might have reduced the financial pressure to pay quickly.
Negotiation strategy: Sometimes, refusing to pay initially is a negotiation tactic. Companies might believe that the threat actor will eventually lower their ransom demand if they hold firm. This doesn't always work, as we saw with Under Armour.
Financial constraints: Let's be honest—maybe Under Armour just couldn't afford whatever Everest was asking for. Ransoms for attacks of this scale can reach tens of millions of dollars.
Reputational concerns: Paying a ransom is embarrassing. It's an admission that your security was inadequate. Under Armour might have decided that the reputational damage of refusing to pay was less severe than the reputational damage of admitting they paid millions to criminals.
Whatever the reason, the decision to not pay backfired spectacularly. Now Under Armour is facing a class action lawsuit, a public data breach, and permanent damage to customer trust.

The Class Action Lawsuit
The Chimicles Schwartz Kriner & Donaldson-Smith law firm has filed a proposed class action lawsuit on behalf of Under Armour customers. Here's what this means and where it might go:
What they're alleging: The lawsuit claims that Under Armour failed to implement adequate security measures to protect customer data, failed to monitor for unauthorized access, and failed to notify customers of the breach in a timely manner. It also alleges that Under Armour's silence has violated state breach notification laws as reported by Top Class Actions.
The potential damages: Class action settlements in data breach cases typically range from tens of millions to hundreds of millions of dollars. In some cases, companies have paid settlements exceeding $1 billion. The settlement amount usually depends on the number of people affected, the sensitivity of the data, and the defendant's ability to pay.
How class actions work: If the lawsuit is certified as a class action, any Under Armour customer affected by the breach is automatically included unless they opt out. They don't have to do anything. If the company settles or loses, the damages are distributed to affected customers. In many cases, individual customers receive a small payment (sometimes as little as $10-50 if the settlement pool is huge) plus the lawyers take a significant cut.
The timeline: Class action lawsuits can take years to resolve. We're talking 3-5 years or more. The lawsuit will go through discovery (where both sides exchange documents and take depositions), potential motion practice, and possibly trial. More likely, it will settle before going to trial.
The precedent: If this lawsuit succeeds, it sends a message to other companies: data breaches that result in customer data exposure will result in expensive lawsuits. This might finally motivate companies to invest more in cybersecurity.
From a practical standpoint, class action litigation is expensive for companies. Even if they win, the legal fees alone can run into the tens of millions. And if they lose or settle, the financial hit is even larger. This is exactly the kind of consequence that should make companies take security seriously.

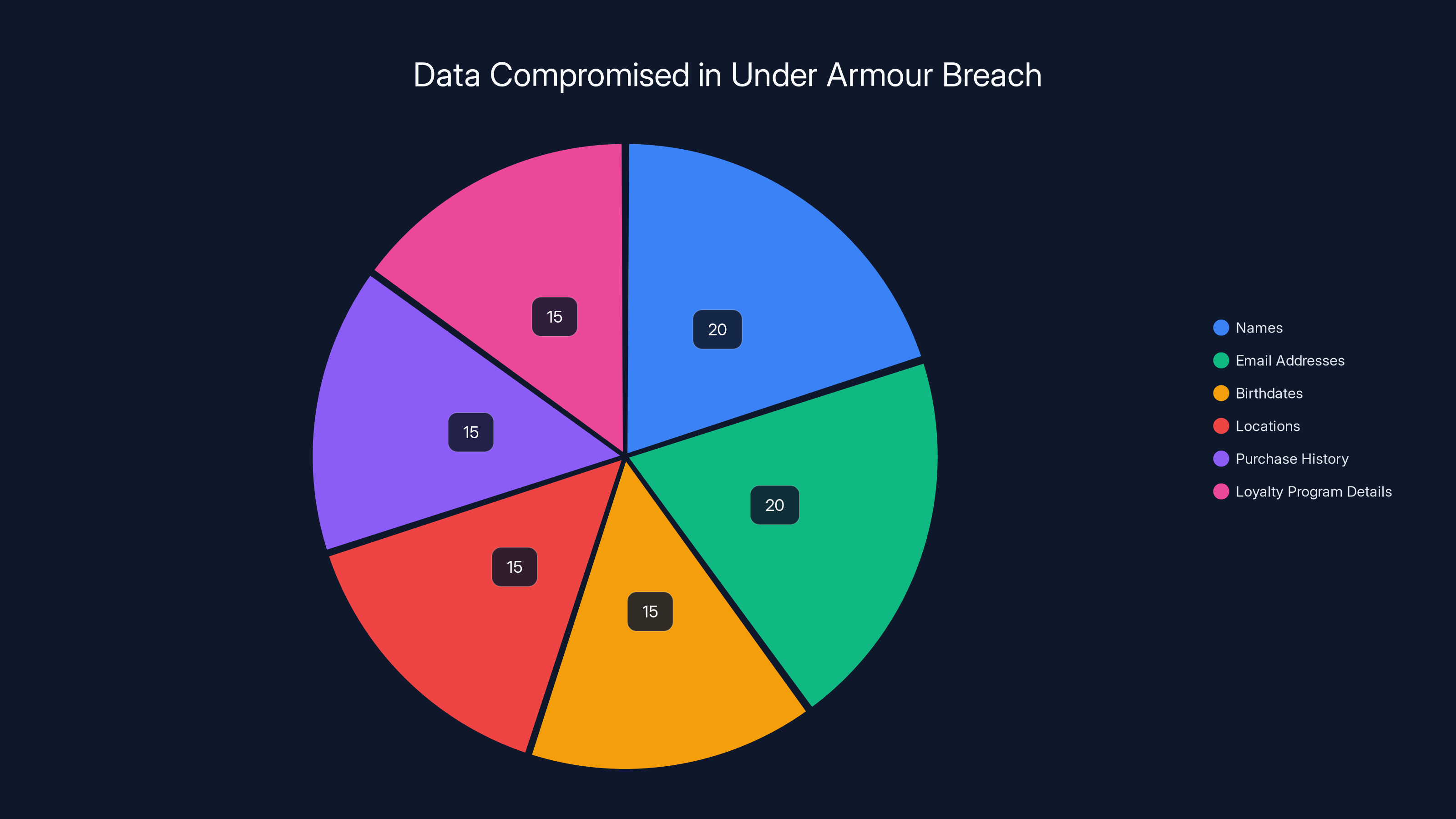
Estimated data distribution of the 72.2 million records compromised in the Under Armour breach. Each type of data represents a significant portion of the total breach.
What You Should Do Immediately
If you've ever had an Under Armour account, here are the specific steps you should take right now:
Step 1: Check if you're in the breach Go to Have I Been Pwned and enter your email address. The site will tell you if your email appears in the Under Armour breach (and any other known breaches). This is free and anonymous.
Step 2: Change your Under Armour password If you're in the breach, log into your Under Armour account immediately and change your password. Choose a strong, unique password that you don't use anywhere else. A strong password should be at least 16 characters and include uppercase letters, lowercase letters, numbers, and special characters.
Step 3: Enable two-factor authentication on your Under Armour account Two-factor authentication adds a second layer of security. Even if attackers have your password, they can't log into your account without the second factor (usually a code sent to your phone or generated by an authenticator app). Under Armour should have this option in their account settings.
Step 4: Check for reused passwords If you used the same password on your Under Armour account that you use anywhere else, you need to change those passwords too. Use a tool like Bitwarden or 1Password to check which accounts use the same password. This is critical—password reuse is how a single breach cascades into multiple account takeovers.
Step 5: Enable two-factor authentication on all critical accounts Your email account is the most critical. If attackers can get into your email, they can reset passwords on every other account you own. Your email should have the strongest security settings possible: unique password, two-factor authentication, and regular activity monitoring.
Enable two-factor authentication on financial accounts (banking, credit cards), social media accounts, and any other service that matters to you.
Step 6: Monitor your credit reports Under Armour's breach exposed birthdates and locations. This information, combined with your name, is enough to apply for credit cards or loans in your name. You can get free credit reports from Annual Credit Report.com once per year from each of the three major credit bureaus (Equifax, Experian, Trans Union).
Start checking your credit reports now. Look for accounts you don't recognize or hard inquiries from creditors you didn't contact. If you see fraud, dispute it immediately.
Step 7: Consider a credit freeze or fraud alert A fraud alert tells credit bureaus to call you before extending credit to anyone using your Social Security number. A credit freeze completely prevents anyone (except you) from accessing your credit report, which prevents criminals from opening new accounts.
Credit freezes are free and recommended for anyone affected by a breach of this scale. You can set up a freeze with each of the three major credit bureaus online. It takes about 10 minutes as advised by NerdWallet.
Step 8: Monitor your accounts regularly Set a reminder to check your bank accounts, credit cards, and other financial accounts at least weekly. Look for unauthorized charges. Most credit card companies will catch fraud and dispute it, but it's better to catch it yourself.
Step 9: Watch for phishing attacks Now that attackers have your personal information, expect to receive phishing emails that look legitimate. Be especially suspicious of emails from companies you actually do business with, because those are the ones attackers will use.
Remember: legitimate companies never ask you to "verify" your account or provide passwords via email. If you get a suspicious email, go directly to the company's website (type the URL yourself) and check your account from there.
Step 10: Consider identity theft protection Services like Lifelock or Identity Force monitor the dark web for your personal information and alert you if it's being sold. They typically cost $10-20 per month. This isn't strictly necessary if you're already monitoring your credit reports regularly, but it provides extra peace of mind.

Long-Term Data Breach Monitoring
Once you've taken the immediate steps, you need to establish a long-term monitoring routine.
Monthly credit report checks: Set a recurring monthly reminder to check one of your three credit reports (cycle through them, so you're checking a full report every three months). Use Annual Credit Report.com for free reports.
Quarterly password audits: Check your password manager (you're using a password manager, right?) and look for weak or reused passwords. Update them. Look for accounts you haven't accessed in a long time and consider deleting them.
Ongoing Have I Been Pwned monitoring: Have I Been Pwned lets you opt into breach notifications. You'll get an email if your address appears in any future data breaches. This is free and highly recommended.
Credit monitoring service: If you decide to use a service like Lifelock or Identity Force, make sure it includes dark web monitoring, credit freezing assistance, and identity theft insurance. The insurance is usually $1 million or more, which provides some protection if your identity is stolen.
Financial account monitoring: Check your bank accounts and credit cards at least weekly. Most financial institutions will send you alerts for large transactions or suspicious activity, but don't rely solely on those. Review your accounts directly.
The reality is that this breach is probably the first of many for people who were affected. Once your information is on the dark web, it stays there forever. You're essentially permanently added to criminals' mailing lists. They'll try to use your information to commit fraud, sell it to other criminals, or use it in phishing attacks.
So establish a routine and stick to it. Make security checks part of your regular digital hygiene. It's not paranoia—it's appropriate caution given what happened.

Industry Response and Regulatory Pressure
The Under Armour breach is likely to trigger significant regulatory and industry-wide responses.
Regulatory investigations: State attorneys general, the Federal Trade Commission, and potentially international regulatory bodies will likely investigate this breach. They'll look at whether Under Armour violated breach notification laws, whether their security practices were adequate, and whether they're being truthful about what happened.
Regulatory investigations can result in significant fines. In 2020, the FTC fined Marriott (which suffered a massive data breach) $18.6 million for failing to implement reasonable security and failing to notify customers of the breach in a timely manner. Similar fines are possible for Under Armour.
Shareholder lawsuits: Beyond the customer class action lawsuit, Under Armour shareholders might file lawsuits against the company's leadership, alleging that they failed to implement adequate cybersecurity measures and thereby exposed the company to this liability. These are separate from the customer lawsuits and can add significantly to the total legal burden.
Security audit demands: Regulators often demand that companies undergo independent security audits after breaches of this scale. Under Armour will likely be required to hire outside security firms to assess their entire infrastructure, conduct penetration testing, and identify vulnerabilities. These audits are expensive and can take months.
Required compliance measures: Regulators often mandate that companies implement specific security controls as part of settlement agreements. Under Armour might be required to implement things like multi-factor authentication for all customer accounts, real-time breach detection systems, or mandatory encryption of sensitive data.
Industry standards and benchmarking: This breach will be analyzed extensively by cybersecurity professionals. It will likely become a case study in security failures, discussed at conferences, published in security research, and used as a teaching tool for what not to do. This creates indirect pressure on other companies to improve their security practices.

How to Spot Scams Related to This Breach
Now that the breach is public, scammers are jumping at the opportunity to exploit people's fear and confusion.
Watch out for:
Fake "security" offers: Scammers will send emails claiming they can "protect your data" following the breach, then direct you to enter personal information or download malware.
Fake settlement notices: You might receive emails claiming you're eligible for a settlement payment from Under Armour. They'll ask you to click a link and "verify" your information. This is a phishing attack.
Fake Under Armour customer service: Scammers will pretend to be Under Armour support staff and call or email you asking to "confirm" your account details or reset your password. Legitimate companies don't contact you unprompted asking for passwords.
Dark web "data recovery" offers: Someone might try to sell you information about how to "get your data back" from the dark web. This is a scam. Once data is compromised, it's compromised. Nobody can "recover" it. Anyone claiming they can is lying.
Fake credit freeze services: Scammers will charge money for "premium" credit freeze services, when credit freezes are free.
If you're unsure whether something is legitimate, go directly to the official website (type the URL yourself, don't click a link) and look for information there. Or call the company's official customer service number (look it up independently, don't use a number from a suspicious email).

Broader Lessons for Companies
The Under Armour breach teaches several important lessons that apply to every organization:
Security is not optional: Under Armour is a successful, well-resourced company. They had the financial ability to invest in cybersecurity. They chose not to prioritize it sufficiently. This breach is their problem now—and it's a far more expensive problem than it would have been if they'd invested in security upfront.
Ransomware groups don't care about your industry: Everest targets everyone. They don't discriminate between healthcare providers, financial institutions, manufacturers, or retailers. If you collect customer data, you're a target. There's no "safe" industry.
Silence is not a strategy: By refusing to acknowledge the breach publicly, Under Armour made the situation exponentially worse. The lawsuit, the regulatory scrutiny, the reputational damage—all of it would have been reduced by early, transparent communication.
Scale matters: 72.2 million records is enormous. But more companies need to understand that any data breach is serious. Even a breach of 100,000 records can result in lawsuits, fines, and damage to customer trust.
Third-party risk is real: If this breach happened through a compromised vendor or partner, it highlights how critical it is to audit third-party access to your systems. Many companies don't properly segment network access for vendors, meaning that compromising one vendor gives attackers access to everything.
Data retention is dangerous: The bigger question is: why does Under Armour have 72.2 million customer records stored in a single accessible location? Do they really need to keep every customer's birthdate and address indefinitely? Companies should implement data minimization principles: collect the minimum necessary data, retain it only as long as necessary, and delete it when it's no longer needed.
Future Predictions: What's Next
Based on historical patterns, here's what we can expect to unfold:
Within 3-6 months: The class action lawsuit will move forward with discovery. Under Armour will be forced to disclose internal communications, security policies, and incident response documents. This will likely reveal incompetence or negligence that makes their position even worse.
Within 6-12 months: Regulatory bodies will issue formal findings and likely impose fines or mandated security improvements. Settlement discussions in the class action lawsuit might begin. Security researchers will publish detailed analysis of how the breach happened and what Under Armour did wrong.
Within 12-24 months: The lawsuit might settle for $50-200 million (rough estimate based on comparable breaches). Under Armour will be required to implement expensive security infrastructure improvements.
Long-term: This breach will become a case study in cybersecurity education. It will be discussed at security conferences, written about in security publications, and used to argue for stronger regulation of data collection and retention.
The Bigger Picture: Your Data Is Everyone's Target
Under Armour's breach isn't an anomaly. It's just the most recent high-profile example of a widespread problem.
Every company that collects customer data is potentially vulnerable to attacks. Hospitals, banks, retailers, social media companies, dating apps, fitness trackers—all of them are targets. Most of them have been breached at some point or will be eventually.
This means that as a consumer, you have to assume that your personal information is compromised. It's already out there somewhere. Your email address, your name, your address, your phone number—all of it has probably been stolen at some point by some company or another.
Given that reality, you have to take responsibility for your own security. Enable two-factor authentication on everything important. Use unique passwords for every account. Monitor your credit reports regularly. Stay alert for phishing attempts. Consider a credit freeze.
Companies aren't going to protect your data adequately. The Under Armour breach proves that even well-resourced, established companies can fail catastrophically. So you have to protect yourself.
It's not fair that you have to do this. You didn't choose to have your data stolen. But this is the world we live in.

FAQ
What exactly happened in the Under Armour breach?
A ransomware group called Everest infiltrated Under Armour's systems in November 2025 and stole 72.2 million customer records. The data included names, email addresses, birthdates, locations, purchase history, and loyalty program details. When Everest demanded a ransom and Under Armour refused to pay, the group leaked the data on the dark web as reported by The Register.
How do I know if my data was stolen?
Go to Have I Been Pwned (haveibeenpwned.com) and enter your email address. The site will tell you if your email appears in the Under Armour breach and any other known data breaches. You can also sign up for breach notifications so you'll be alerted if your email appears in future breaches.
Should I change my Under Armour password?
Yes, immediately. If your email is in the breach, log into your Under Armour account and change your password to something unique that you don't use anywhere else. Use a strong password with at least 16 characters including uppercase, lowercase, numbers, and special characters.
What information could attackers do with my data?
With your name, email, birthdate, and location, attackers can craft convincing phishing emails that target you specifically. They could attempt to social engineer your way into other accounts. With enough information, they might try to open credit accounts in your name or steal your identity. They could also sell your information to other criminals.
How long will this lawsuit take?
Class action lawsuits typically take 3-5 years or longer to resolve. The process includes discovery (exchanging documents and information), motions, possible trial, and settlement discussions. Many breach lawsuits settle before trial, which speeds up the timeline.
Can I sue Under Armour separately from the class action?
You have the right to opt out of the class action lawsuit and file your own lawsuit. However, most individual lawsuits are not viable because the damages per person are relatively small. The class action approach allows affected customers to collectively recover damages.
Should I put a credit freeze on my accounts?
Yes, a credit freeze is recommended for anyone whose personal information has been compromised. A credit freeze prevents anyone (except you) from accessing your credit report, which prevents criminals from opening new accounts in your name. Credit freezes are free and easy to set up with the three major credit bureaus as advised by NerdWallet.
Is my bank account at risk?
Your bank account is at risk if you reuse the same password on your bank account that you used on Under Armour, or if attackers use your personal information to commit identity theft. Monitor your bank accounts regularly for unauthorized transactions. Consider enabling two-factor authentication on your banking apps.
What should I do if I notice fraud on my accounts?
Contact your bank or credit card company immediately and report the fraudulent transactions. Most credit card companies will dispute unauthorized charges and issue you a new card. Also file a police report and place a fraud alert with the credit bureaus. This creates a record of the fraud and helps protect you from future identity theft.
Why hasn't Under Armour made a public statement about the breach?
Under Armour has remained silent, which likely violates breach notification laws in most jurisdictions. The silence might be a legal strategy to avoid making statements that could be used against them in court, or they might be hoping the breach goes away without media attention. Either way, the silence has made their legal and reputational situation worse as highlighted by Security Magazine.

Final Thoughts
The Under Armour cyberattack represents a critical moment where corporate negligence meets consumer vulnerability. When a company with the resources to implement robust security decides not to prioritize it, the result is 72.2 million people exposed to identity theft, fraud, and phishing attacks.
Your immediate responsibility is to protect yourself. Check if you're in the breach, change your password, enable two-factor authentication, monitor your credit, and stay alert for phishing attacks. These aren't optional steps—they're essential security hygiene in a world where major breaches happen regularly.
Beyond individual actions, this breach highlights the need for stronger regulatory oversight and corporate accountability. Companies need to face real consequences for security failures. The lawsuits, the fines, and the regulatory scrutiny that Under Armour will face should serve as a warning to every other company: invest in cybersecurity now, or pay far more later.
The good news is that security is ultimately manageable. You don't need to be paranoid or spend thousands on specialized protection. You need to be smart: unique passwords, two-factor authentication, regular monitoring, and healthy skepticism about unexpected emails or calls from companies asking for your information.
If you're affected by this breach, don't panic. But do take action. The sooner you secure your accounts and monitor your information, the lower your risk of becoming a victim of fraud or identity theft. And if you see suspicious activity, report it immediately.
This breach is unfortunate, but it doesn't have to define your security posture going forward. Take control of what you can control, and you'll be in a much stronger position to protect yourself.

Key Takeaways
- The Everest ransomware group stole 72.2 million Under Armour customer records including names, emails, birthdates, locations, purchase history, and loyalty program details following an attack in November 2025 as reported by The Register.
- Under Armour's silence on the breach violates breach notification laws in most jurisdictions and has triggered a class action lawsuit that could cost the company tens of millions in settlements as reported by Top Class Actions.
- The stolen data enables highly targeted phishing attacks—attackers now have the personal details needed to craft convincing, personalized emails that bypass traditional security awareness as highlighted by Security Magazine.
- Immediate protective actions include checking Have I Been Pwned for breach inclusion, changing your Under Armour password, enabling two-factor authentication, setting up a credit freeze, and monitoring credit reports regularly as advised by NerdWallet.
- About 76% of compromised email addresses were previously exposed, but the combination with specific personal details (birthdate, location, purchase history) creates a significantly higher identity theft risk as reported by HIPAA Journal.
Related Articles
- 1Password's New Phishing Prevention Feature [2025]
- PcComponentes Data Breach Denial: What Really Happened [2025]
- LastPass Phishing Scam: How to Spot Fake Support Messages [2025]
- 198 iOS Apps Leaking Private Chats & Locations: The AI Slop Security Crisis [2025]
- Under Armour 72M Record Data Breach: What Happened [2025]
- 1Password Phishing Protection: How the New Browser Feature Saves You [2025]
![Under Armour Cyberattack 2025: What 7M Users Need to Know [Guide]](https://tryrunable.com/blog/under-armour-cyberattack-2025-what-7m-users-need-to-know-gui/image-1-1769103469117.jpg)



